Bilateral authentication and data interaction security protection method based on CPK (Combined Public Key Cryptosystem)
A two-way authentication and security protection technology, applied in secure communication devices, digital transmission systems, user identity/authority verification, etc., can solve the problems of user data leakage, poor system security, and difficulty in deciphering, and achieve good security and Ease of use, flexible upgrade, simple and convenient deployment
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0020] In order to make the object, technical solution and advantages of the present invention clearer, the present invention will be further described in detail below in conjunction with the embodiments and accompanying drawings.
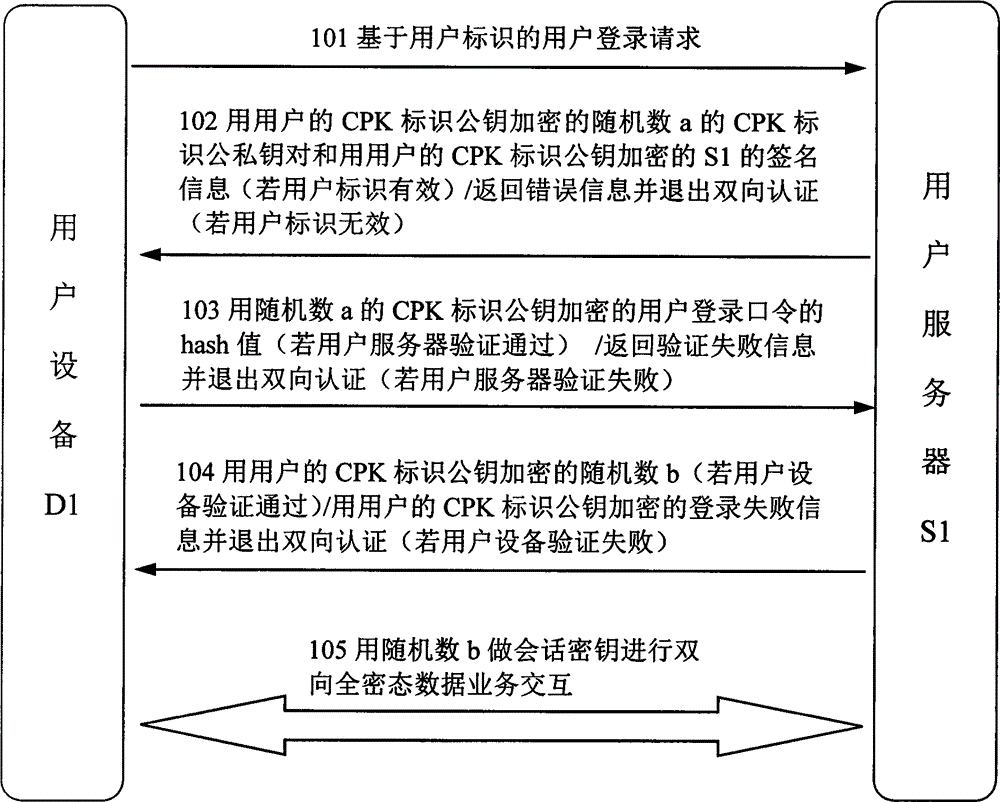
[0021] The present invention provides a two-way authentication between an Internet user server (S1) and a user device (D1) and a method for security protection of all data interaction, using the existing CPK identification authentication technology to realize the whole process of all data in a fully encrypted state Information exchange.
[0022] When the user needs to use the user server (S1), the user needs to register on S1, and submit the user identification and authentication user private information required by S1. User private information includes user identification, user login password, ID card number, telephone terminal number, email address and other private information for identifying and authenticating users, which will vary depending o...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com