Method and device of two-side authentication secret key negotiation based on certificateless
An authenticated key agreement, certificateless technology, applied in the field of two-party authenticated key agreement based on certificateless, can solve complex certificate management issues and other issues
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
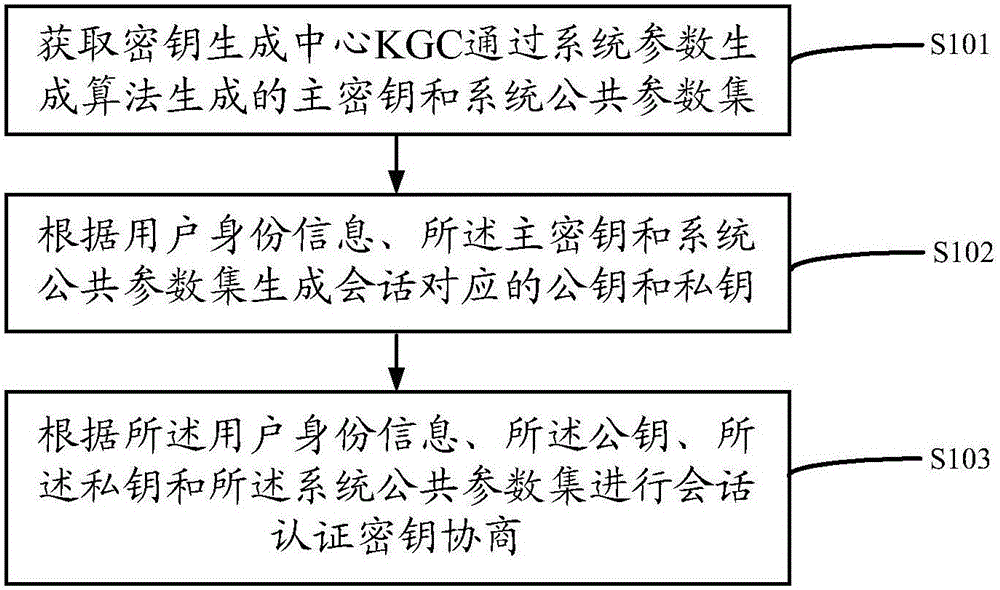
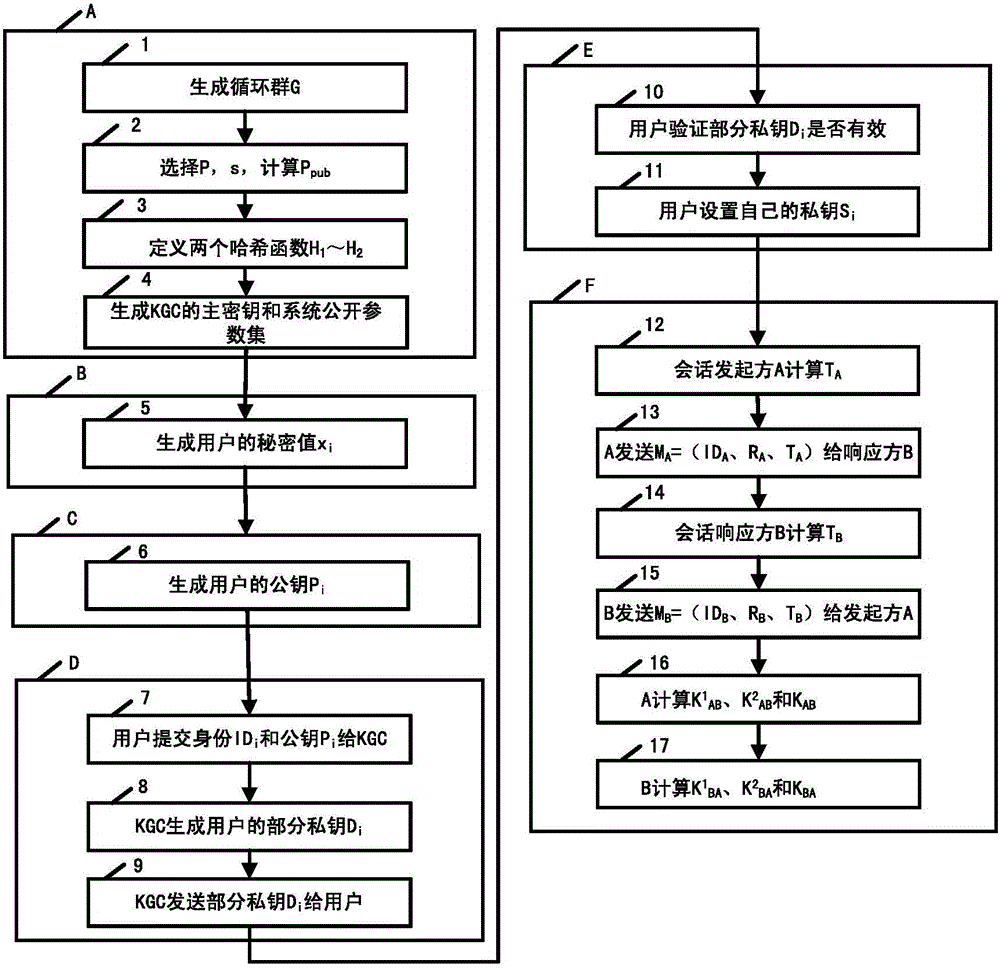
[0150] The entities involved in the system of this embodiment are as follows:
[0151] (1) KGC: Responsible for system parameter generation, namely the KGC master key and system public parameter set, and a trusted third party that produces part of the user's private key;
[0152] (2) User A: the original initiating entity of the session;
[0153] (3) User B: the response entity of the session;
[0154] image 3 It is a schematic flowchart of Embodiment 2 of a method for two-party authentication key negotiation based on no certificate provided by the present invention, and the specific steps are as follows:
[0155] Step A, generate KGC master key and system public parameter set; specific steps are as follows:
[0156] Step 1: KGC operation system parameter production algorithm: KGC according to the set security parameters k∈Z + , select two k-bit large prime numbers p and q and satisfy q|p-1, and generate a prime field elliptic curve E / F P Additive cyclic group G with upp...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com