Prime number generating method applied to cryptology application
A technology of prime number generation and cryptography, which is applied in the field of prime number generation in cryptography applications, can solve the problems of long prime number generation time of primality detection cycle times, achieve the effects of reducing primality detection cycles and improving operation speed and time
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
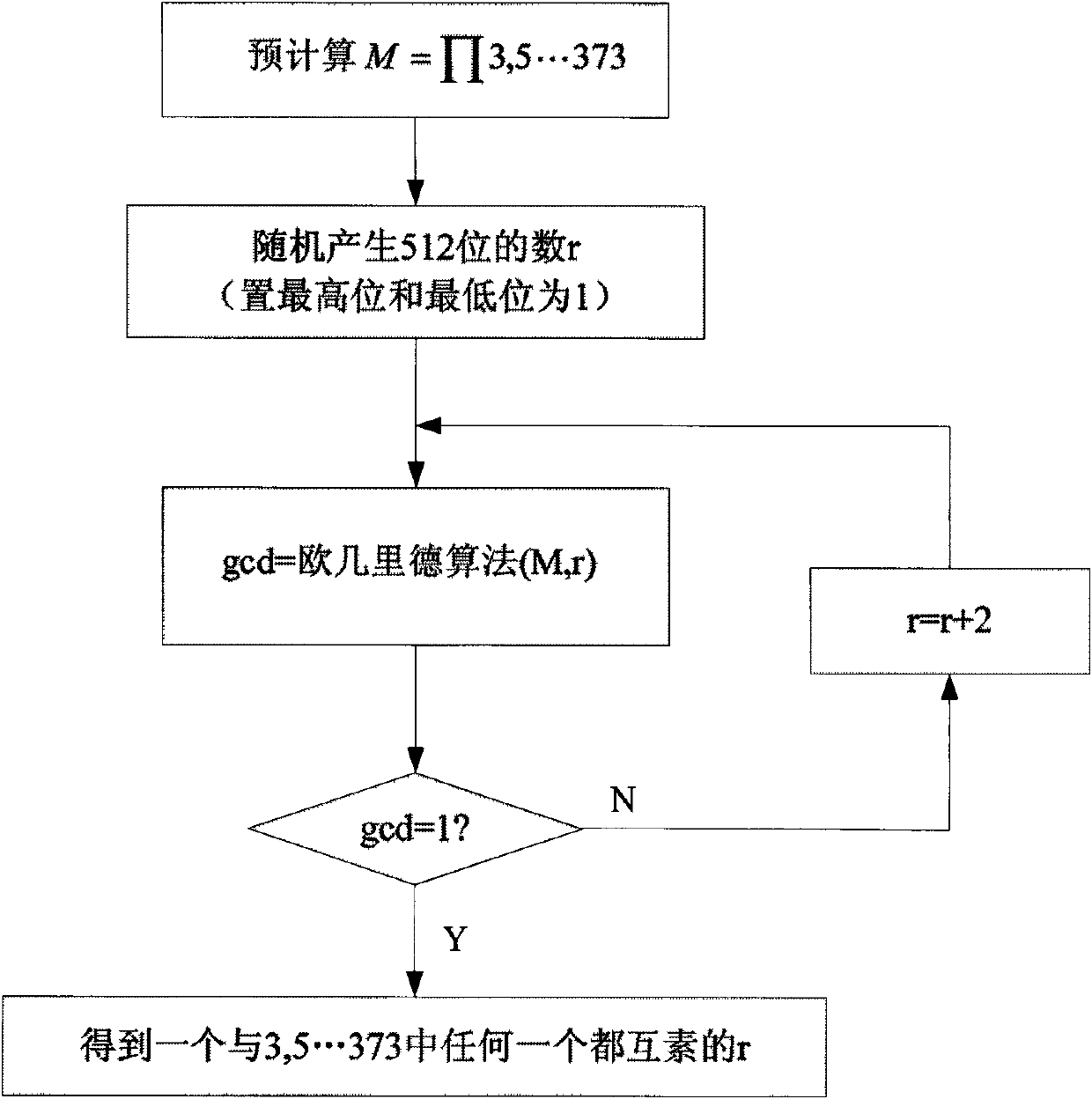
[0024] In the method for generating prime numbers suitable for cryptography applications, the purpose of pre-checking the prime numbers is to calculate the greatest common divisor of the product of the data to be pre-checked and all selected prime numbers. Let gcd be the product M of the data r to be pre-detected (that is, the number to be detected) and the selected prime number greatest common divisor of . If gcd is equal to 1, it means that r and M are mutually prime, then all factors contained in r and M are also mutually prime, that is, r is not p 1 ,p 2 …p n a multiple of any of them. For the control flow of pre-detection of prime numbers, please refer to figure 1 .
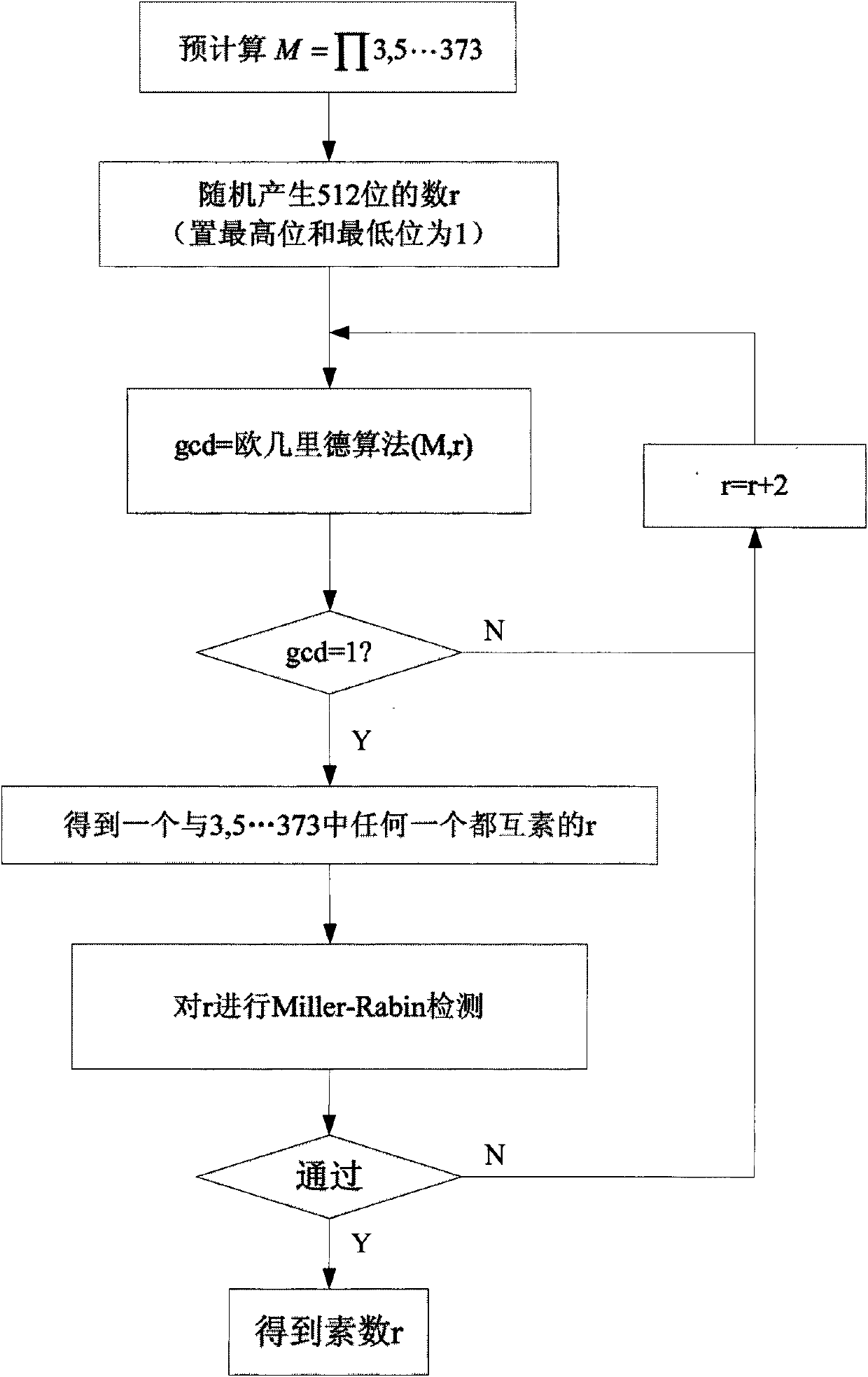
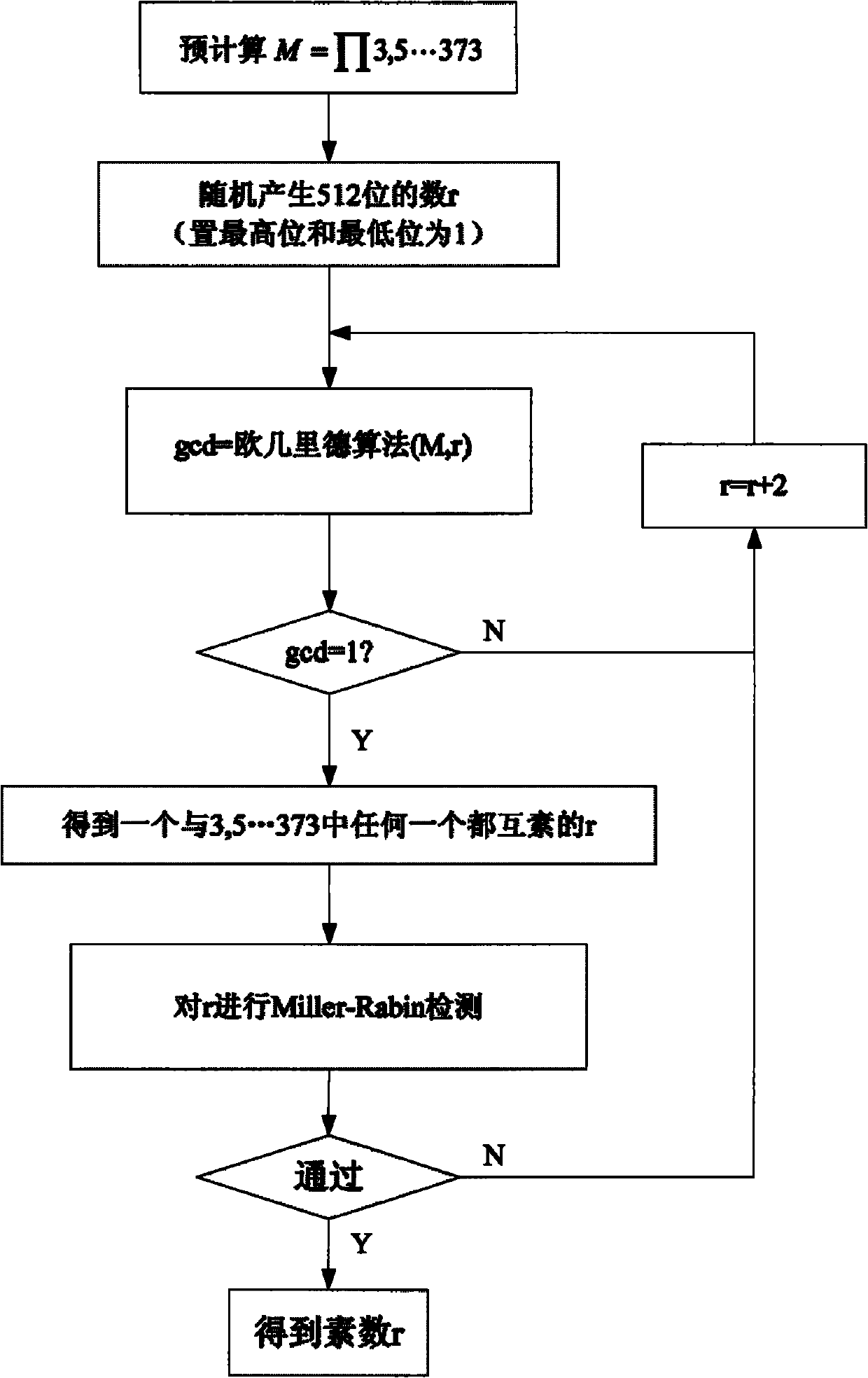
[0025] figure 2 It is a specific embodiment of the prime number generation method suitable for cryptography applications, wherein the generated prime number is 512 bits, and the prime number within 373 is used for the pre-detection operation. The generation algorithm of the greatest common divisor a...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com