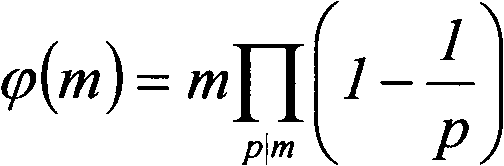A Fast Generation Method of Prime Number Family Applicable to the Application of Information Encryption Technology
A prime number family, fast technology, applied in the fields of information security and cryptography, it can solve the problems of long computing time, no invention, and inability to provide more choices for key algorithms, so as to achieve rapid generation and enhanced optionality. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
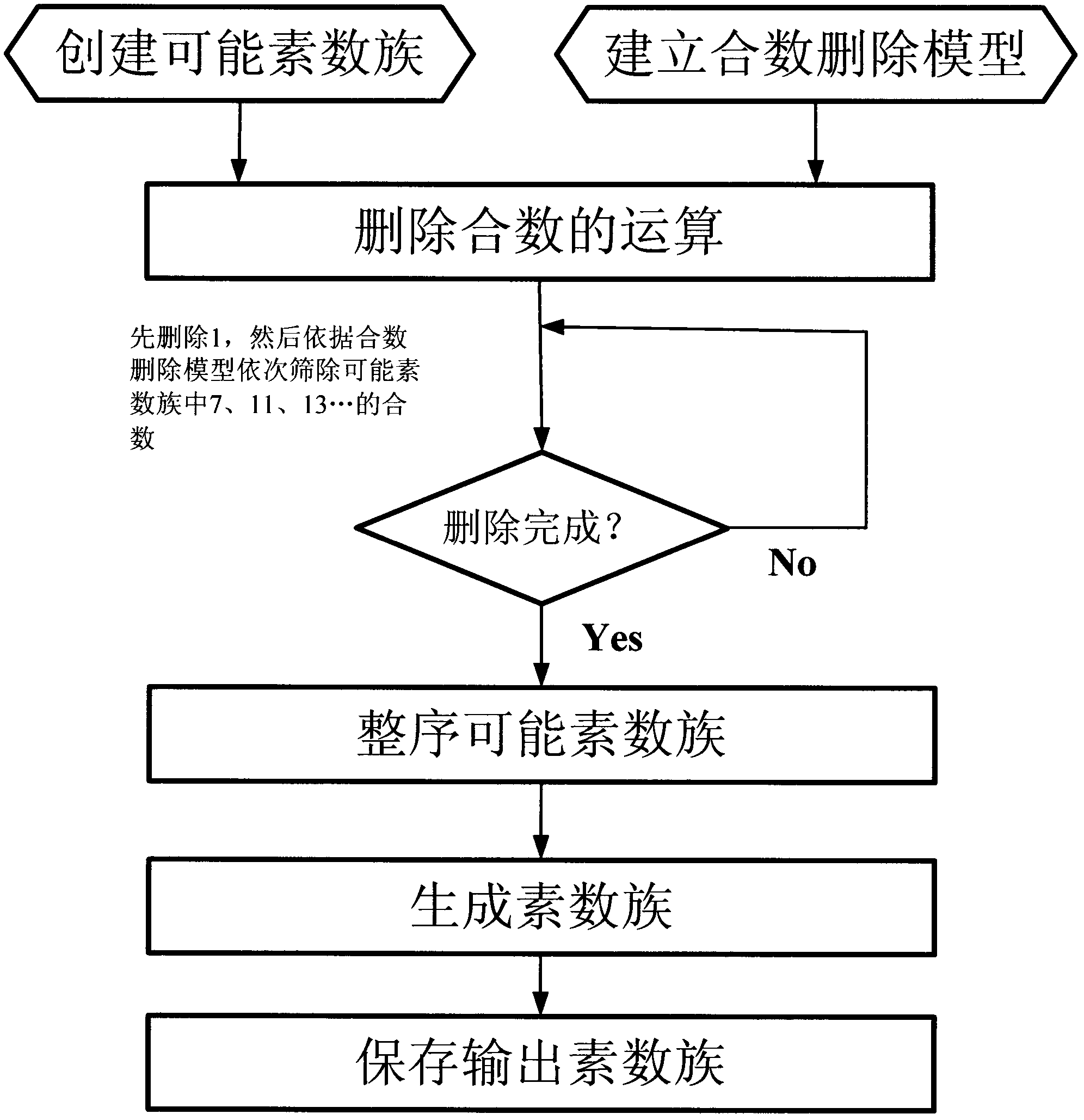
[0036] A kind of prime number family rapid generation method applicable to the application of information encryption technology of the present invention is realized by adopting the following technical scheme:
[0037] Step 1, compress positive integers, and establish a reduced residual system modulo M=30. Choose M=30 as the modulus, seek its congruence class for positive integers, and make its reduced remainder system, by the Euler function
[0038]
[0039] have to
[0040] Thus, eight arithmetic progressions can be formed;
[0041] Step 2, establish the family of possible prime numbers. Take a representative number a from each of the eight categories that are mutually prime with the modulus M=30 1 ,...,a 8 , which in turn are
[0042] 1, 7, 11, 13, 17, 19, 23, 29
[0043] Therefore, the prime numbers p above 7 can be represented by the contracted residual system modulo M=30, that is
[0044] P = ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com