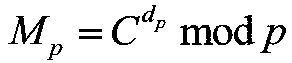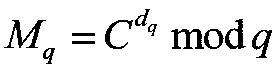Safe outsourcing calculation method applied to RSA decryption
A computing method and security outsourcing technology, applied in the field of security outsourcing computing, can solve the problem of time-consuming RSA decryption process
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
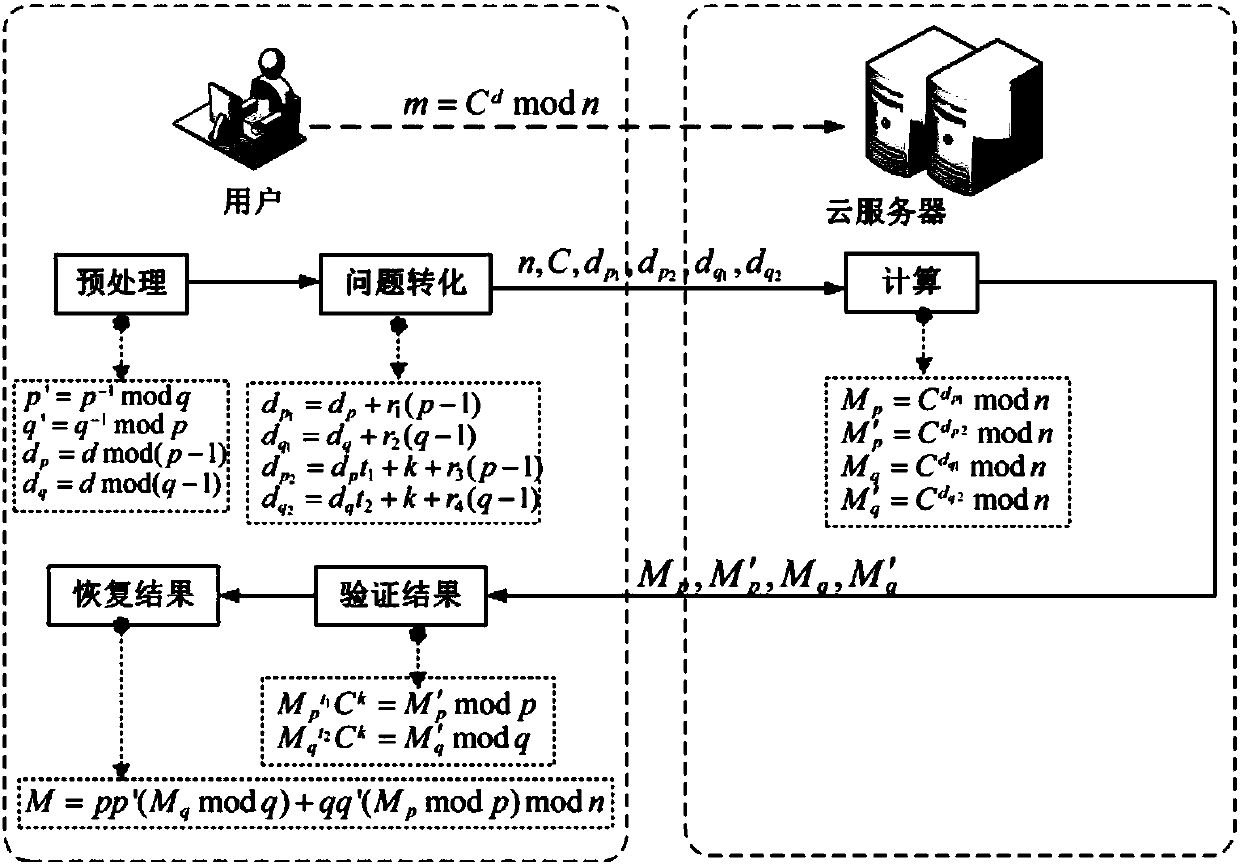
[0050] The application subjects of the security outsourcing algorithm applied to RSA decryption provided by the present invention include users and cloud servers. What the user owns is a device with limited resources, so that the user cannot complete the calculation task with a large amount of calculation. The cloud has almost unlimited computing energy, which can provide users with on-demand resource usage rights. When users use outsourced computing, they hope that the outsourced computing task m=C d modn, but to protect the data from being acquired by entities other than the user, first preprocess the data and then transform the problem. Send the preprocessed and converted data and computing tasks to the cloud server. After receiving the computing tasks and data sent by the user, the cloud server performs calculations according to the requirements of the computing tasks. After the calculation is completed, the calculation result is sent to the user. Thereafter, the user ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com