Patents
Literature
32 results about "Binding number" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
THE BINDING NUMBER The binding number of a graph G, bind(G), is the largest number c such that I I'(X)J > min(c I X 1, 1 G 1) for every X C V(G); i.e., it is the minimum value of I I'(X)I/I X I taken over all non-empty sets X of vertices such that l'(X) =A V(G).
Method for safely calling session initiation protocol (SIP) terminal based on bound number authentication mechanism
ActiveCN103166962AGuaranteed mobilityRealize anti-theft functionTransmissionSecurity arrangementComputer terminalAuthentication
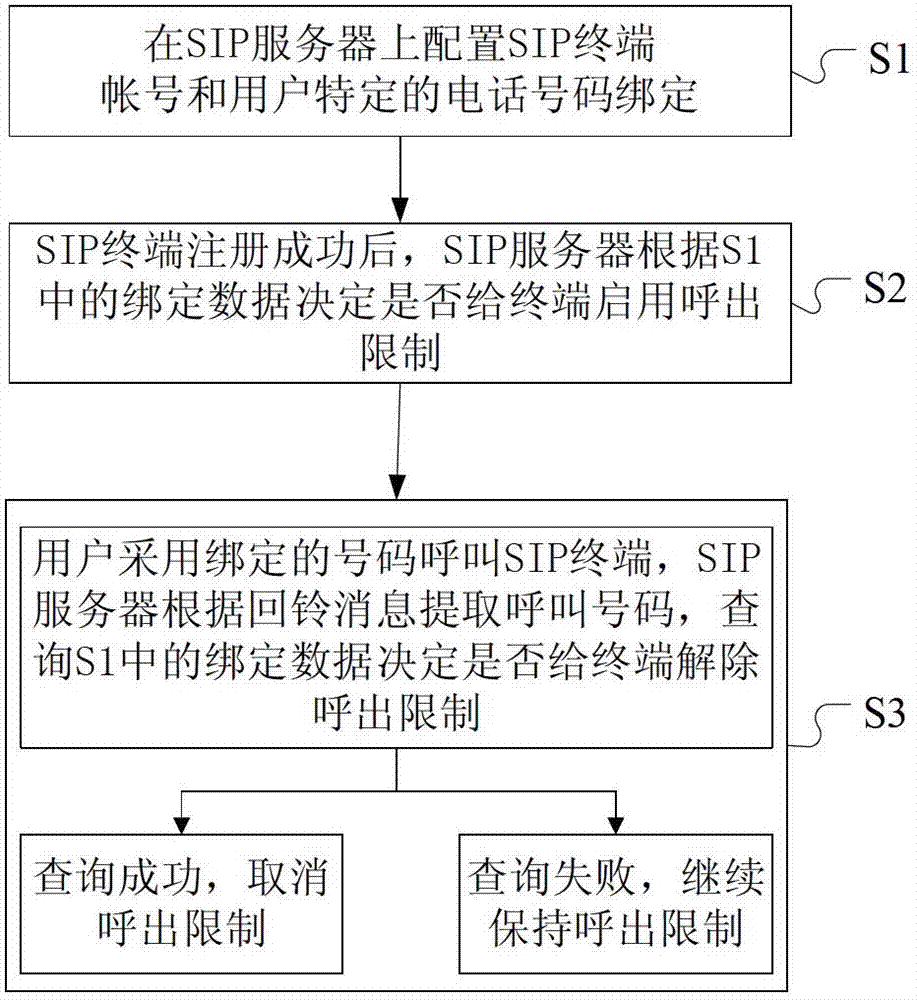
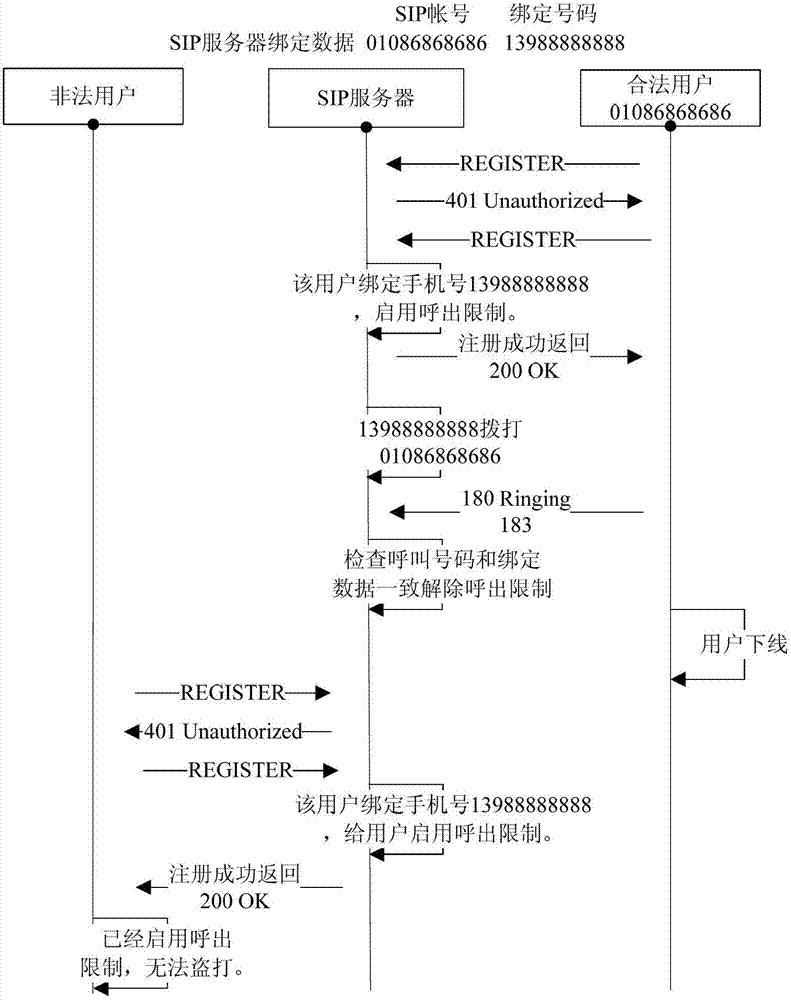
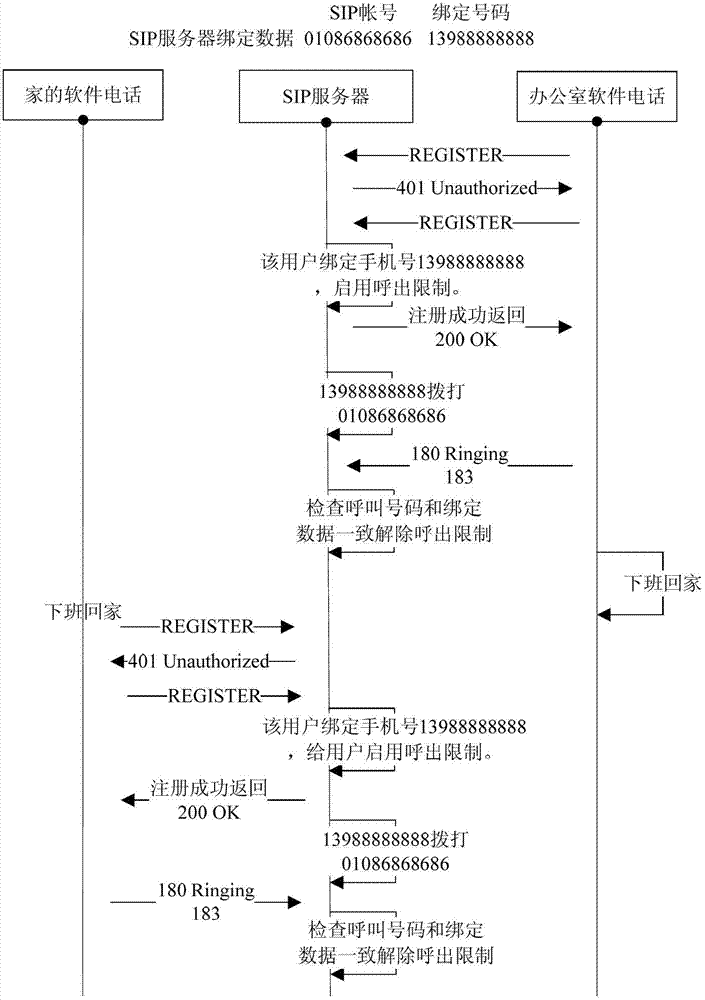
The invention provides a method for safely calling a session initiation protocol (SIP) terminal based on a user bound number authentication mechanism. The method comprises the following steps that: a user template is arranged on an SIP server, and an SIP account number is bound with a specified telephone number of a user; a user sends a login request out, and the SIP server searches the corresponding user template after receiving the login request; if the template does not exist, normal registration process is performed; if the template exists, the SIP server starts a call limit for the user; after a receiving authority is acquired, the corresponding SIP terminal corresponding to the user is required to be called by using the bound telephone number through the SIP server; if the SIP server detects that the corresponding SIP terminal is called by using the telephone number bound in the template, the call limit of the SIP terminal is lifted; and if the corresponding SIP terminal is not called by using the bound telephone number, the call limit is kept. By the method, a phenomenon that an illegal user has a free call on other's expenses through an illegal means can be effectively avoided, the SIP terminal can selects to refuse an authentication call of the telephone number, and additional telephone expenses cannot be generated.
Owner:GUANGDONG TELEPOWER TELECOM TECH
Method and device for realizing crossnetwork roaming of multimode mobile phone
ActiveCN102238504AImplement call controlSeamless roamingCommmunication supplementary servicesNetwork data managementRoamingMobile phone
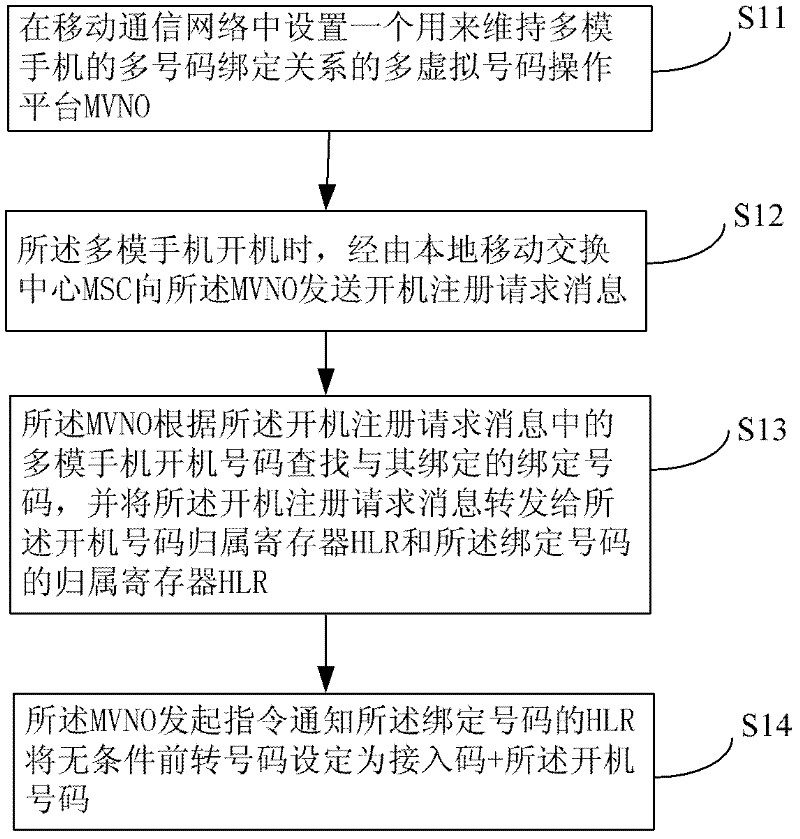
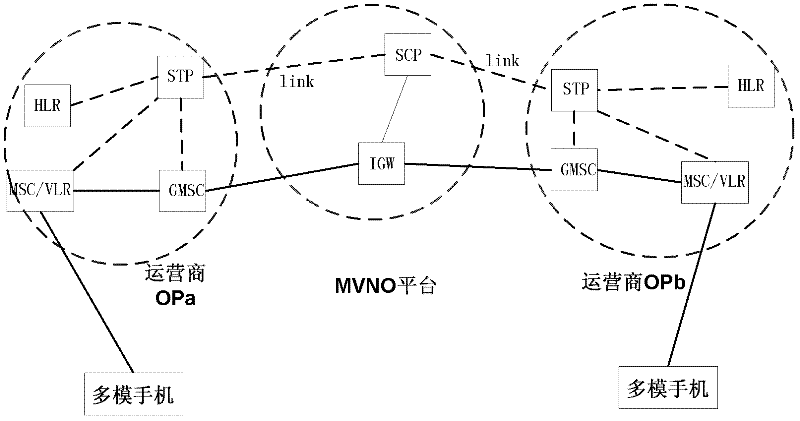
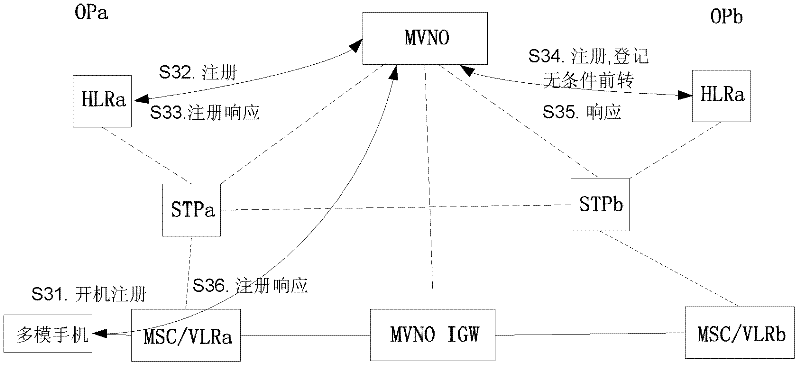
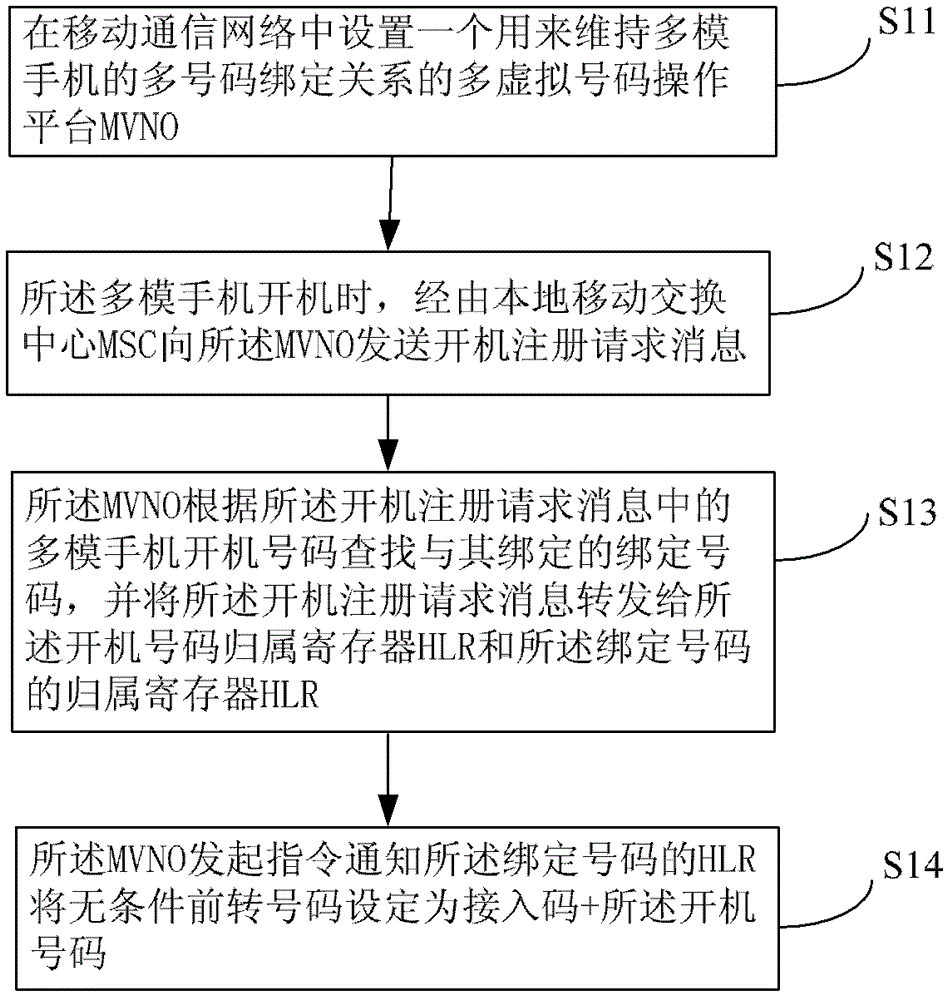
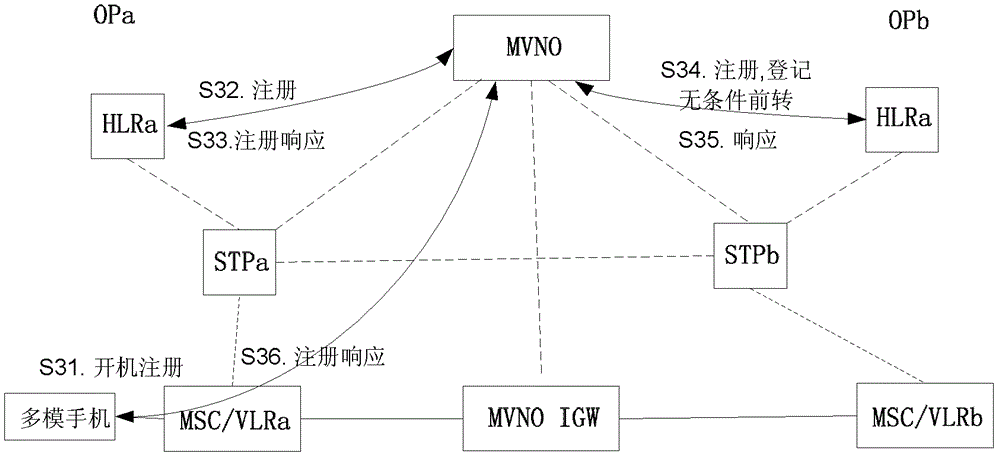
The invention discloses a method and device for realizing crossnetwork roaming of a multimode mobile phone. The method for realizing crossnetwork roaming of the multimode mobile phone comprises the following steps that: 1. a multiple virtual number operation (MVNO) platform used for maintaining the multi-number binding relationship of the multimode mobile phone is arranged in a mobile communication network; 2. when the multimode mobile phone is powered on, a power-on registration request message is sent to the MVNO through a local mobile switching center (MSC); 3. the MVNO searches a number bound with a power-on number of the multimode mobile phone in the power-on registration request message according to the power-on number, and forwards the power-on registration request message to a home location register (HLR) of the power-on number and a home location register (HLR) of the bound number; and 4. the MVNO initiates an instruction to inform the HLR of the bound number to set the unconditional forwarding number as an access code and the power-on number.
Owner:ZTE CORP
Voiceprint identity authentication device and authentication optimization method and system
InactiveCN107481736AImprove clarityImprove visibilitySpeech analysisDeep belief networkFeature vector
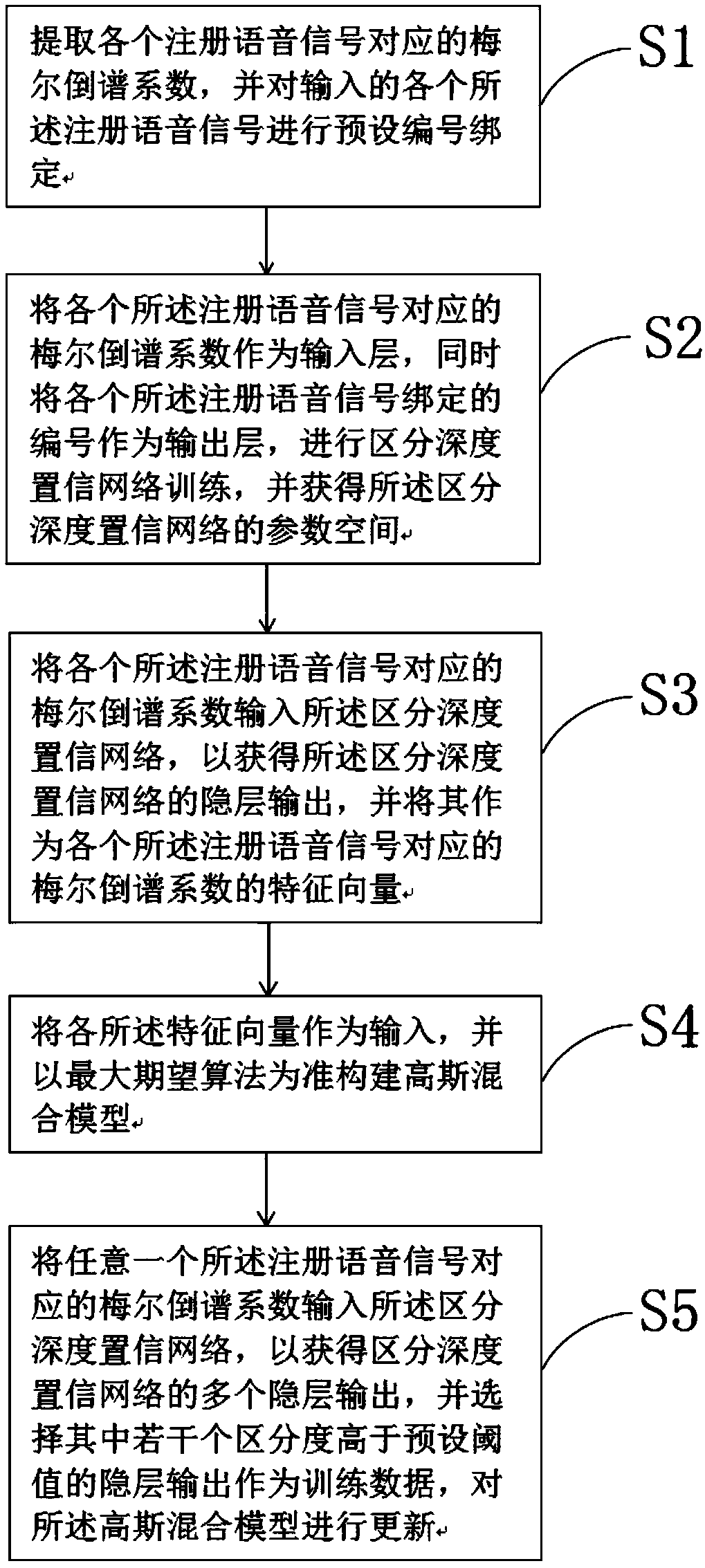
The invention discloses an authentication optimization method of a voiceprint identity authentication device. The authentication optimization method comprises the steps that the Mel-frequency cepstral coefficients corresponding to registration voice signals are extracted and preset number binding is performed on the Mel-frequency cepstral coefficients; the Mel-frequency cepstral coefficients act as an input layer and the bound numbers act as an output layer to perform differentiated deep belief network training and acquire the parameter space; the Mel-frequency cepstral coefficients are inputted to the differentiated deep belief network to acquire the hidden layer output to act as the feature vectors; all the feature vectors act as the input to construct a Gaussian mixture model; and the corresponding Mel-frequency cepstral coefficient of any registration voice signal is inputted to the differentiated deep belief network to acquire multiple hidden layer outputs, and the hidden layer outputs of which the degree of distinction is higher than the preset threshold are selected to act as the training data to update the Gaussian mixture model. The following spontaneously changed voice signal of the registrant acts as the raining data to update the Gaussian mixture model so as to be more adaptive to the present sound production state of the registrant, and the recognition rate can be guaranteed.
Owner:GUANGDONG UNIV OF TECH
Method Of Data Analysis
InactiveUS20080208946A1Accurate detectionFacilitate data analysisDigital data processing detailsDigital computer detailsData setData profiling
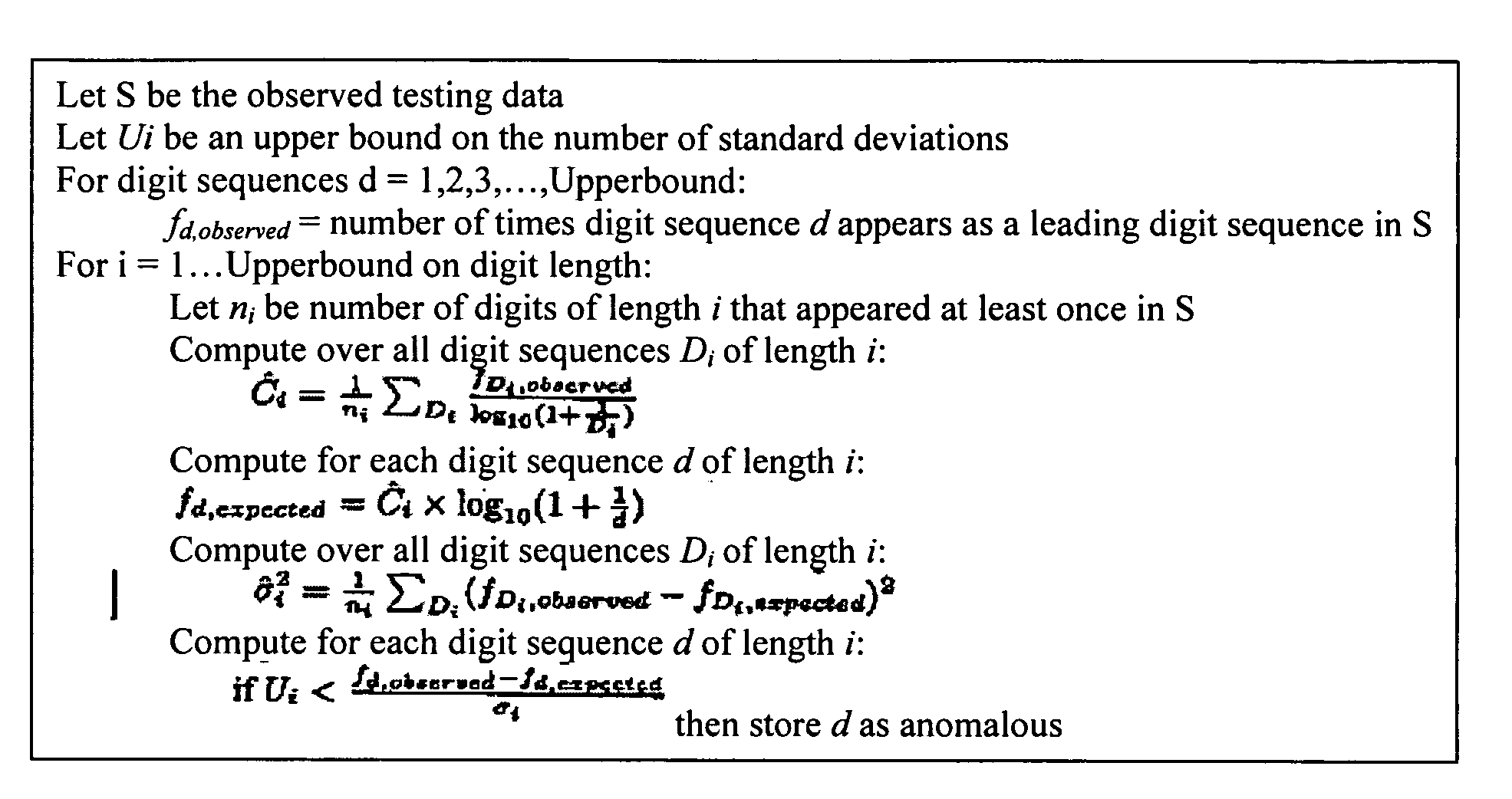
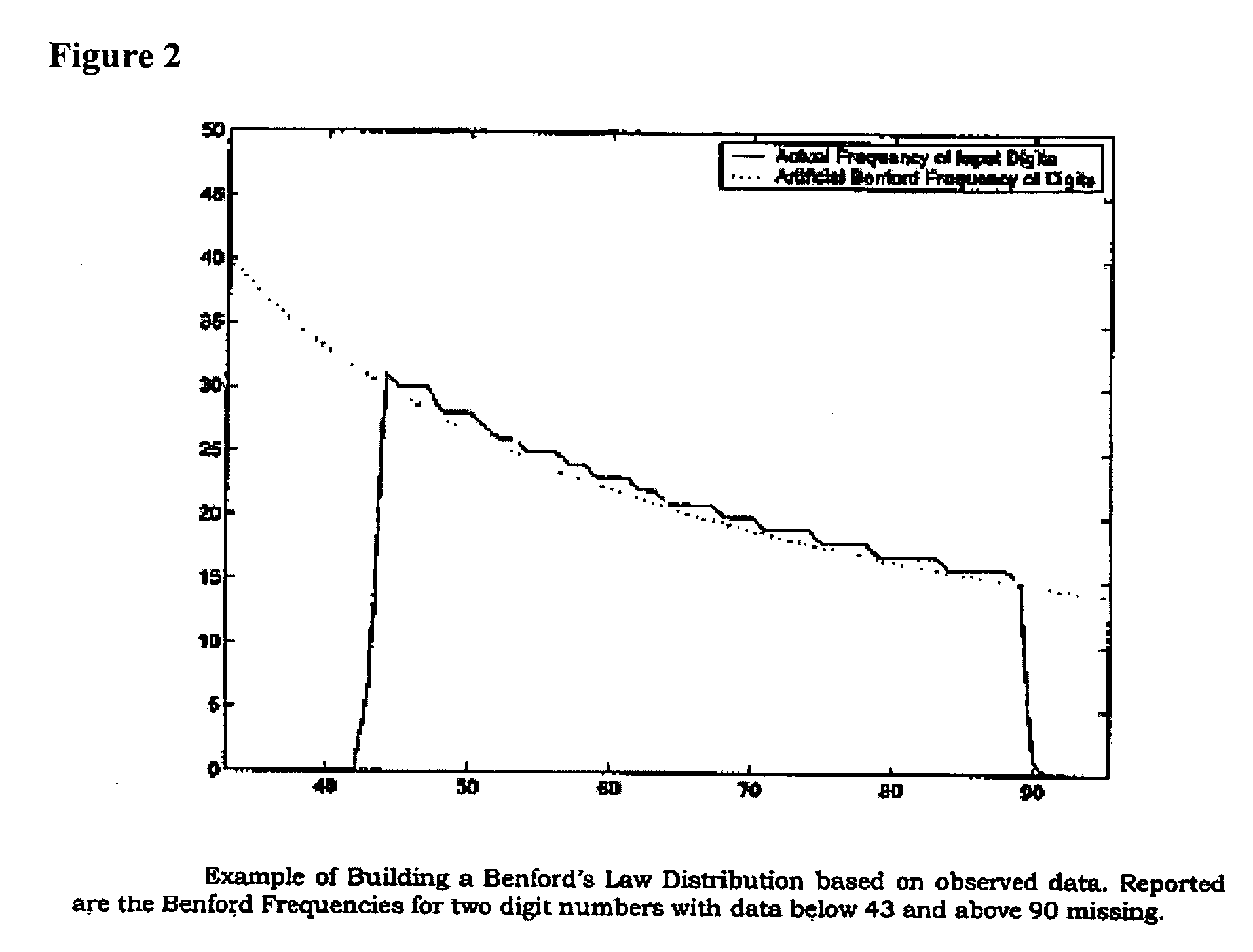
A method of analysis of incomplete data sets to detect fraudulent data is disclosed. The method comprises computing constant values for various leading digit sequence lengths, computing artificial Benford frequencies for the digit sequence lengths, computing a standard deviation for each of the sequence lengths, and flagging any digit sequences in the data set that deviate more than an upper bound number of standard deviations from the artificial Benford frequencies, the upper bound used to determine if the observed data deviates enough to be considered anomalous and potentially indicative of fraud or abuse.
Owner:BORITZ J EFRIM +1
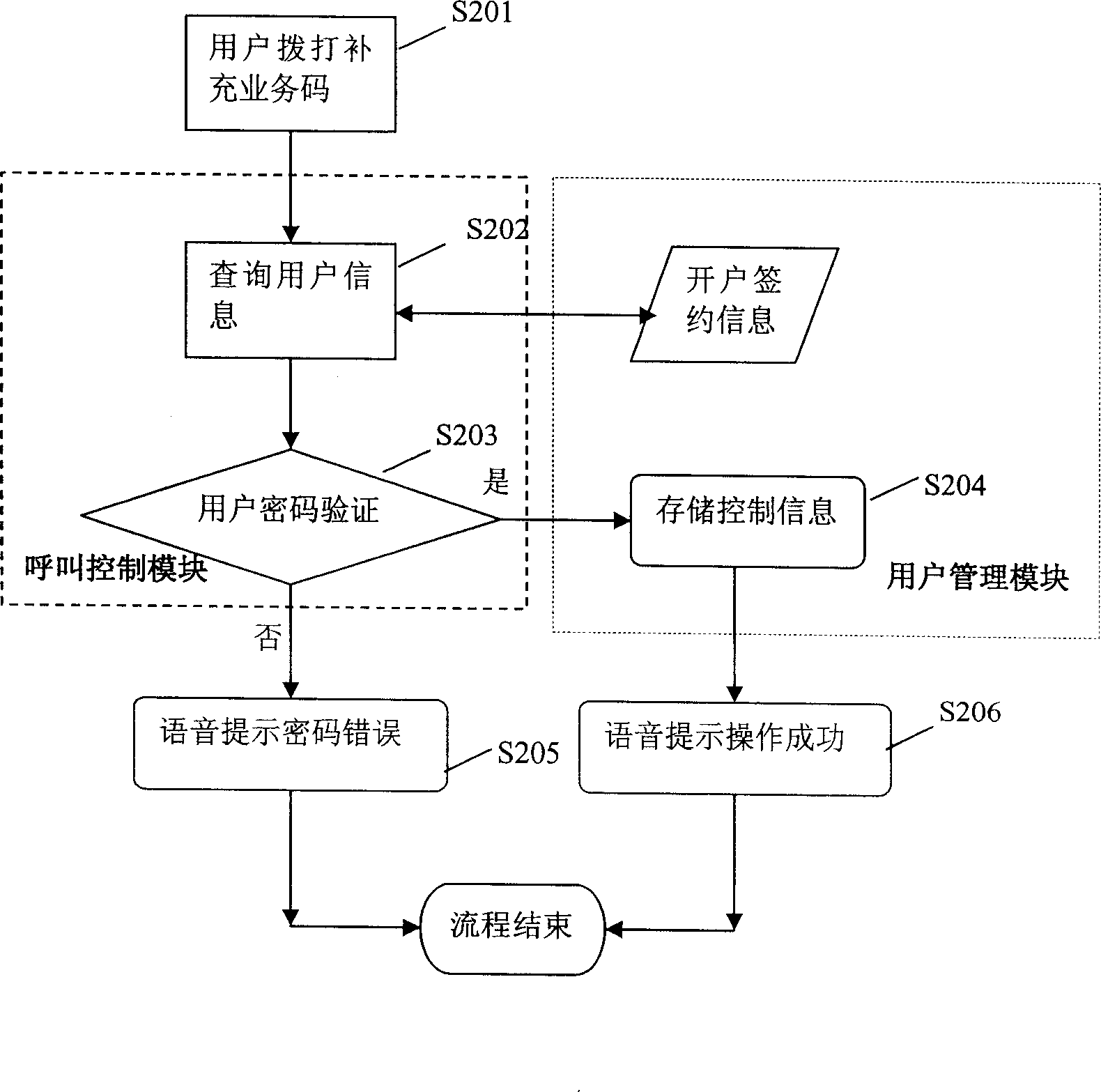
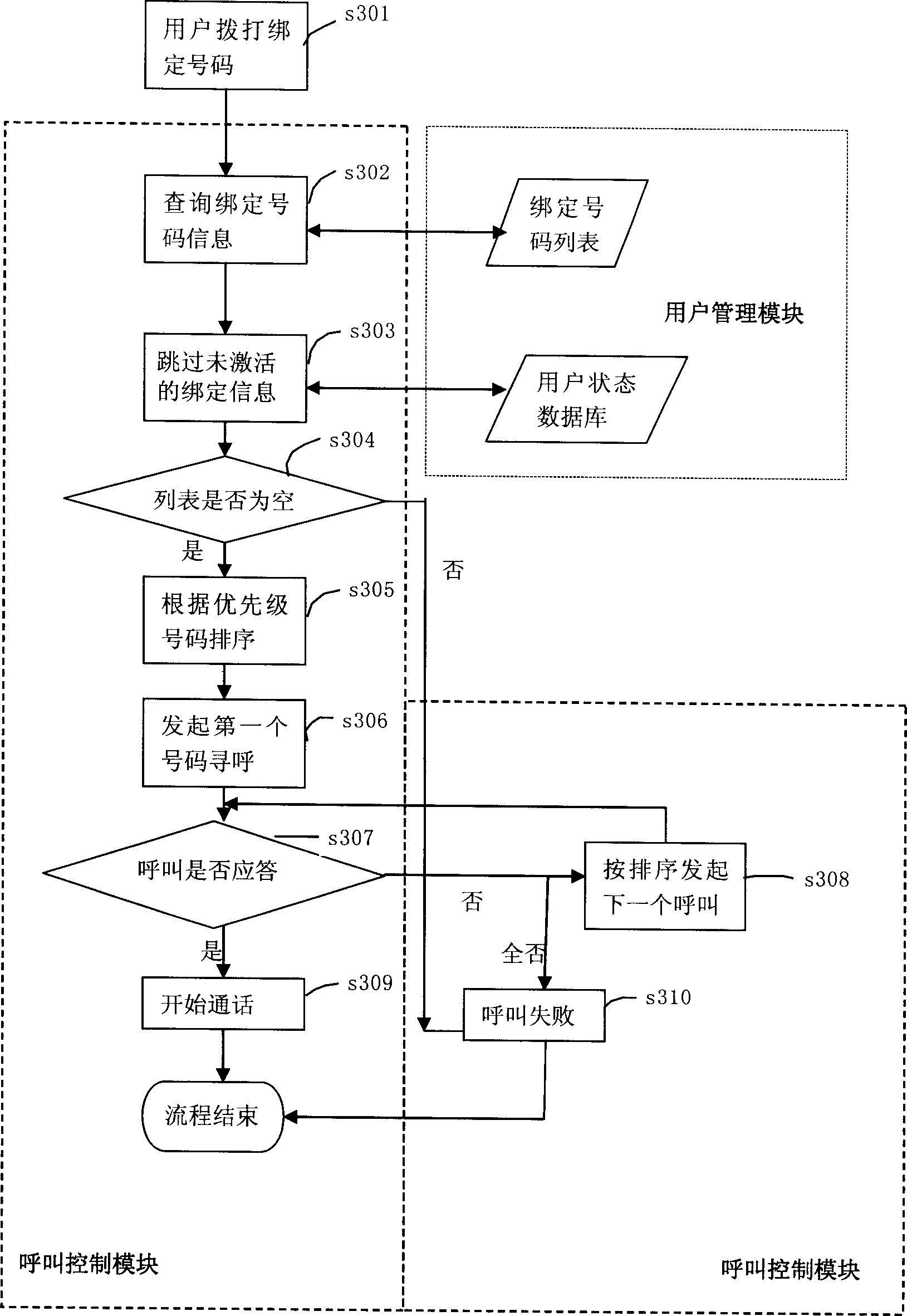
Number binding method and method for calling thereby
InactiveCN1863250AEasy to findSave phone billsNetwork topologiesSpecial service for subscribersCall controlWireless local loop
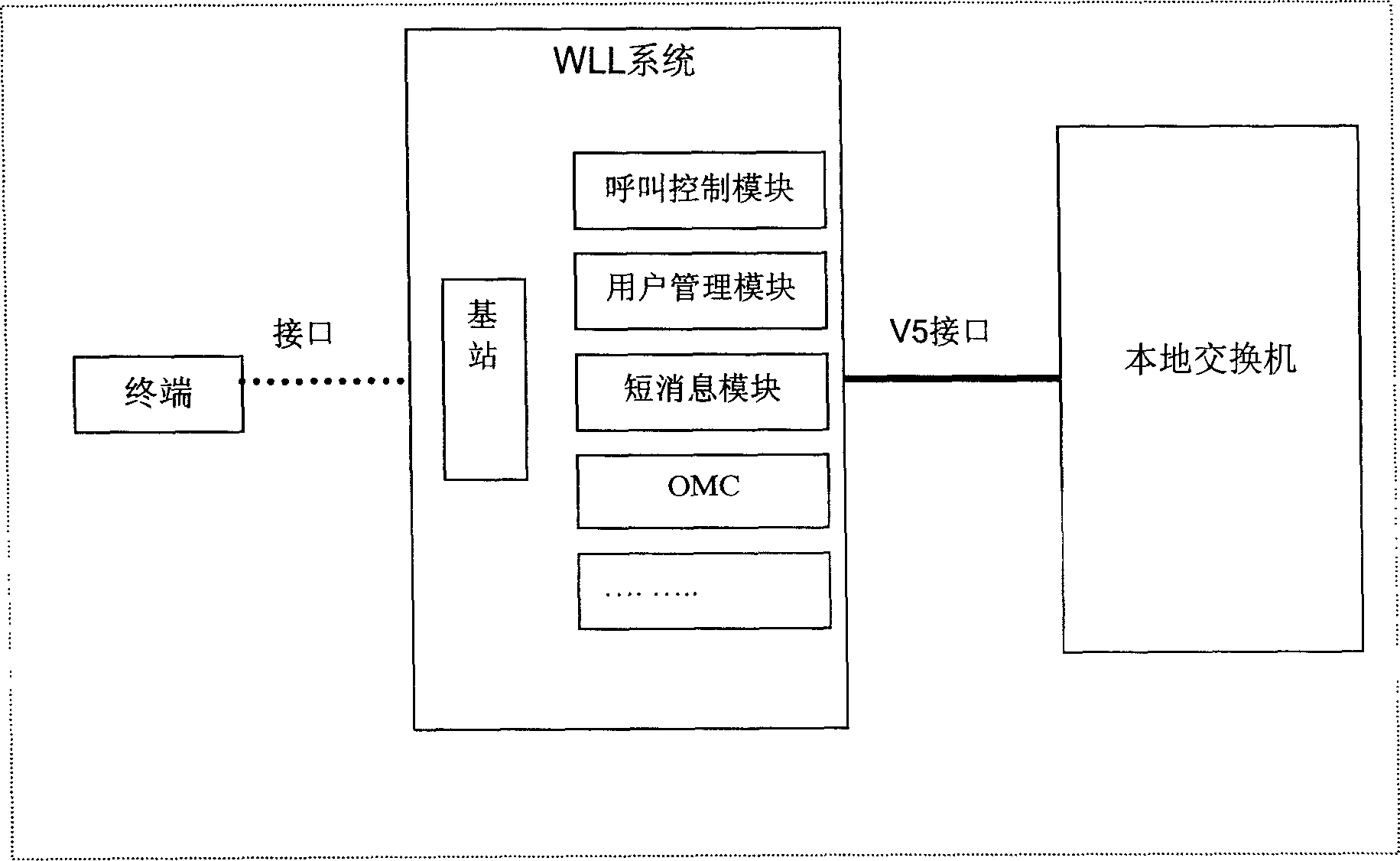
The invention discloses a number binding method based on wireless local loop (WLL) system and a calling method using the binding method, where the WLL system comprises call control module and user management module, and the number binding method comprises: 1) the user management module provides a binding number for a user; 2) the user binds his plural numbers with the binding number through the call control module and the user management module. And the invention provides convenient calling service of plural user numbers, saving user call fees. And it can provide more perfect service and simultaneously increase benefits of an operator.
Owner:HUAWEI TECH CO LTD
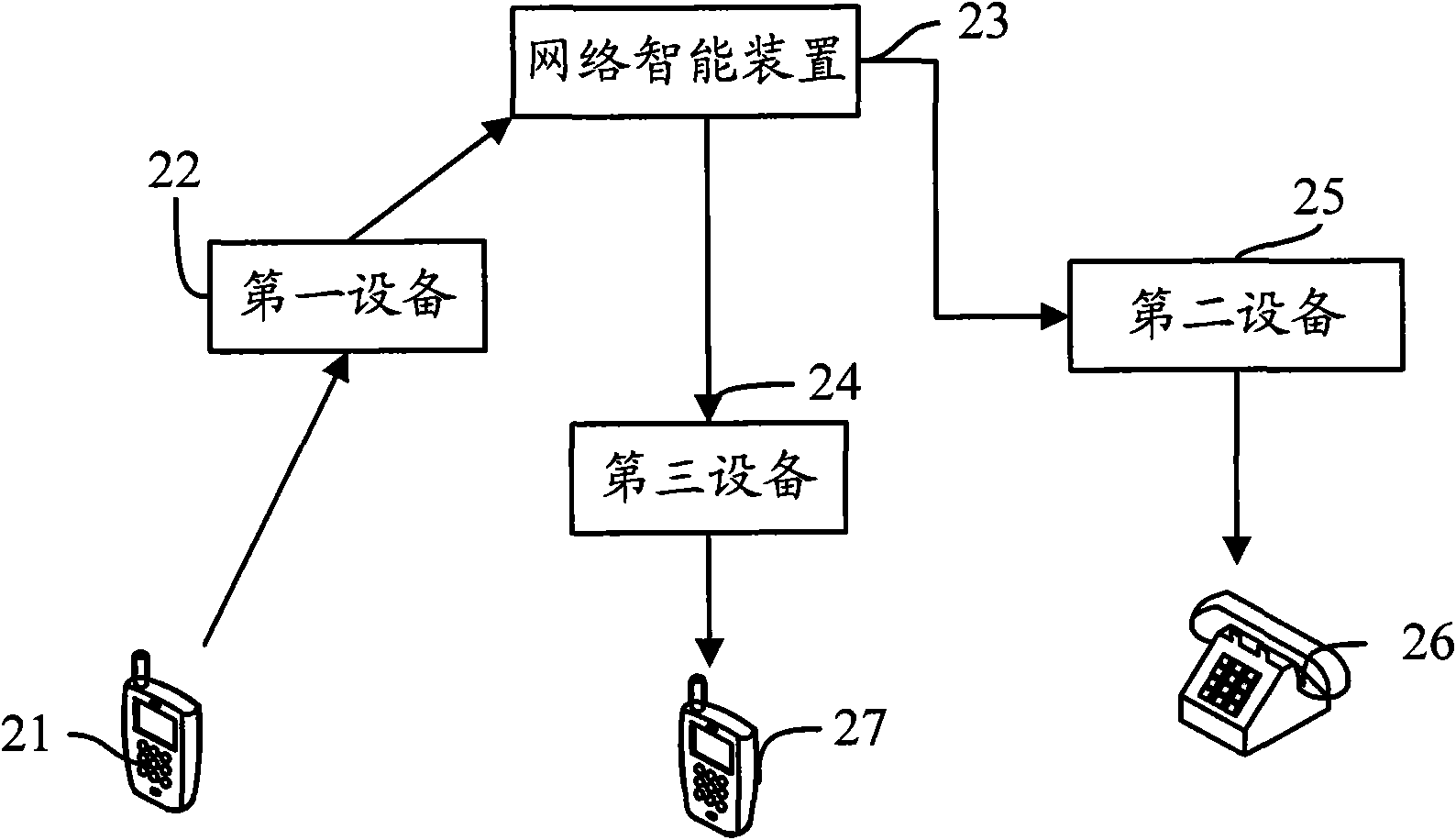
Method for realizing one number service, apparatus thereof and system thereof
ActiveCN102469425AReduce on-timeImprove user experienceCommmunication supplementary servicesNetwork data managementComputer terminalComputer science
The invention provides a method for realizing a one number service, an apparatus thereof and a system thereof. The method comprises the following steps: a network intelligent apparatus receives a call request to a second terminal initiated by a first terminal; the network intelligent apparatus inquires at local whether the second terminal signs the one number service or not, and if the one number service is signed, the apparatus acquires a binding number which is in simultaneous vibration / sequential vibration with the second terminal, wherein, a terminal corresponding to the binding number is a third terminal; the network intelligent apparatus initiates a first call to the third terminal and a second call to the second terminal, wherein, the second call carries mark information of a triggered one number service. According to a scheme of the present invention, connection duration of a calling mobile phone answering of the one number service can be reduced, and usage experience of a user is improved.
Owner:CHINA MOBILE GRP BEIJING
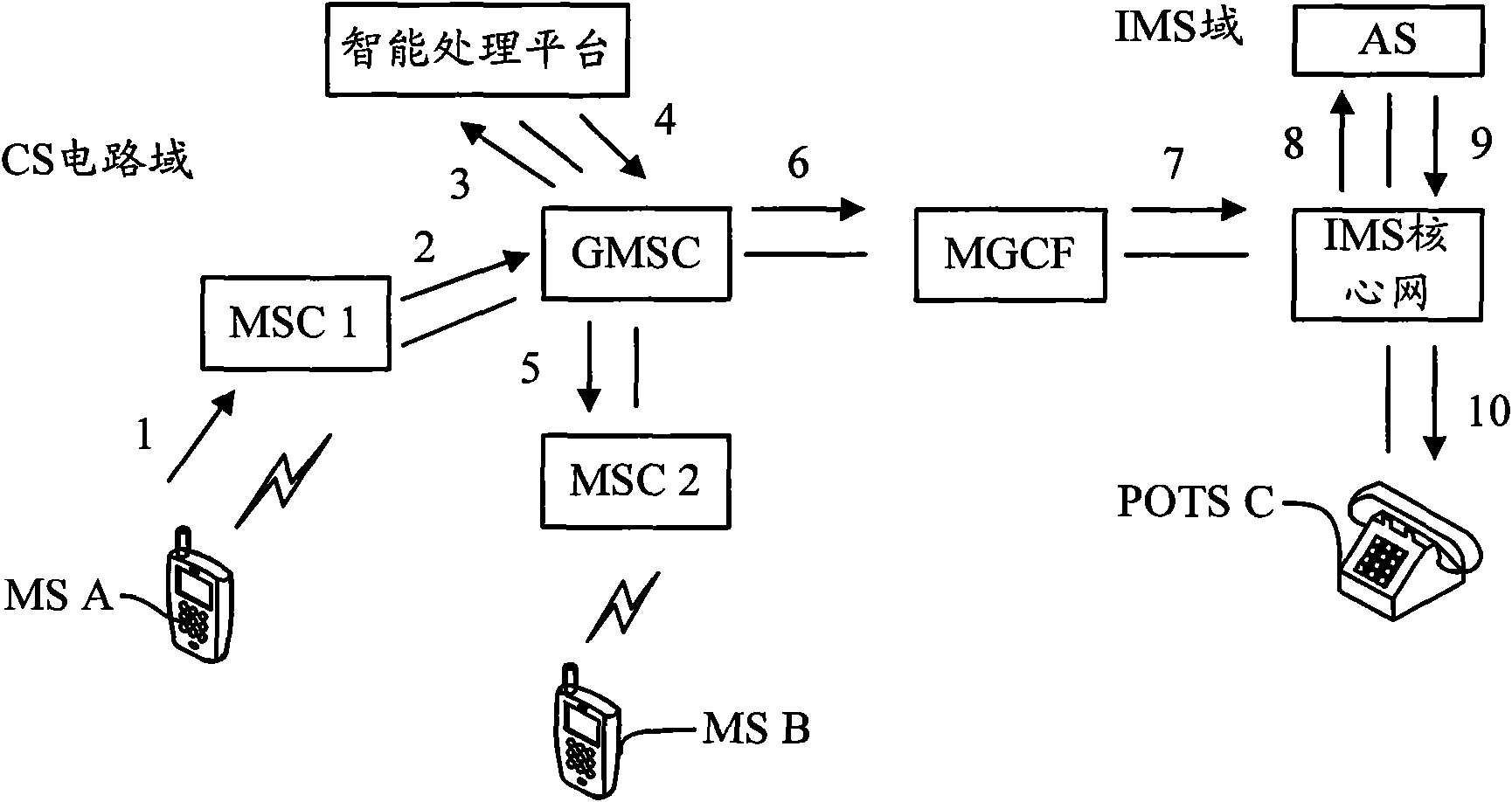
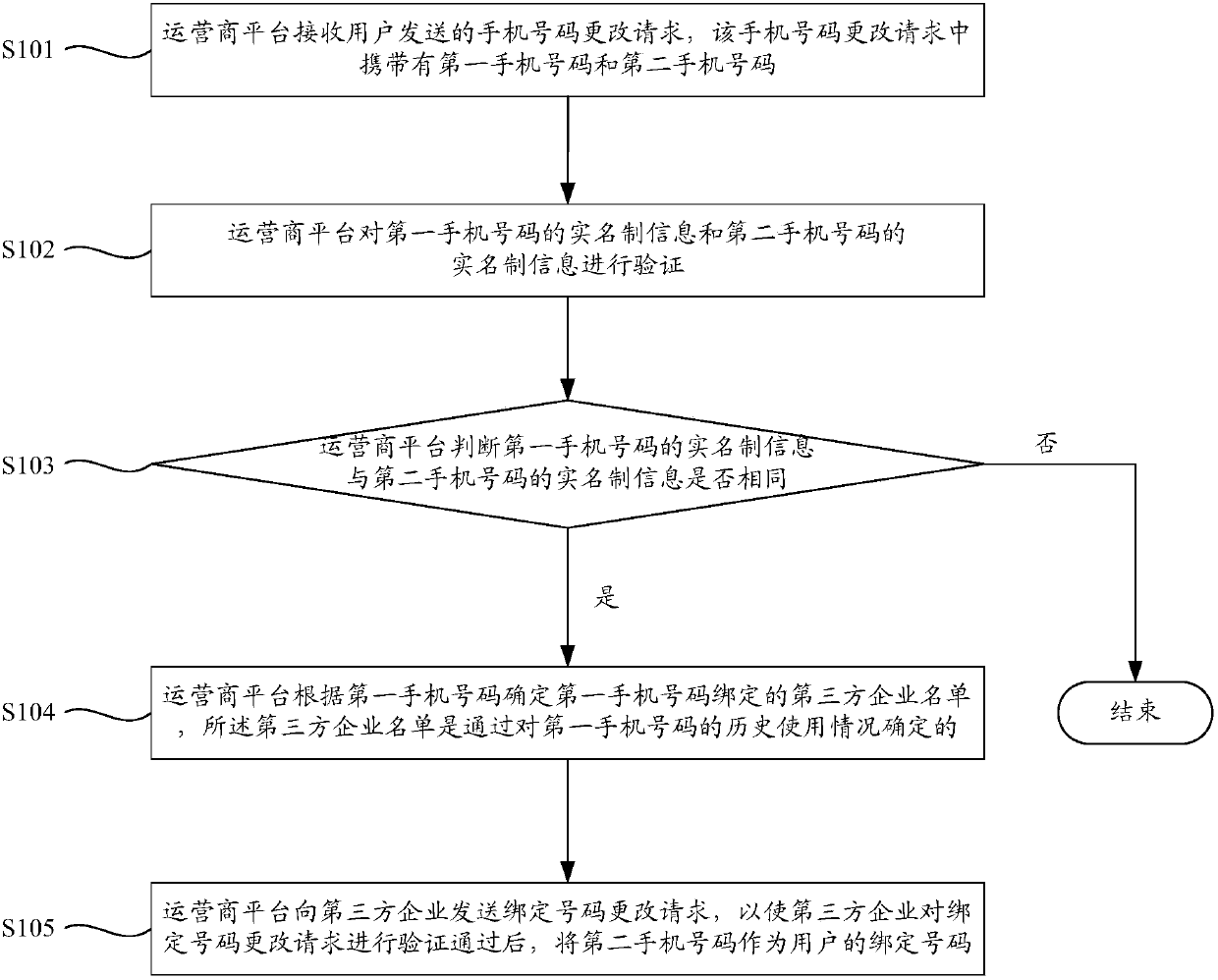
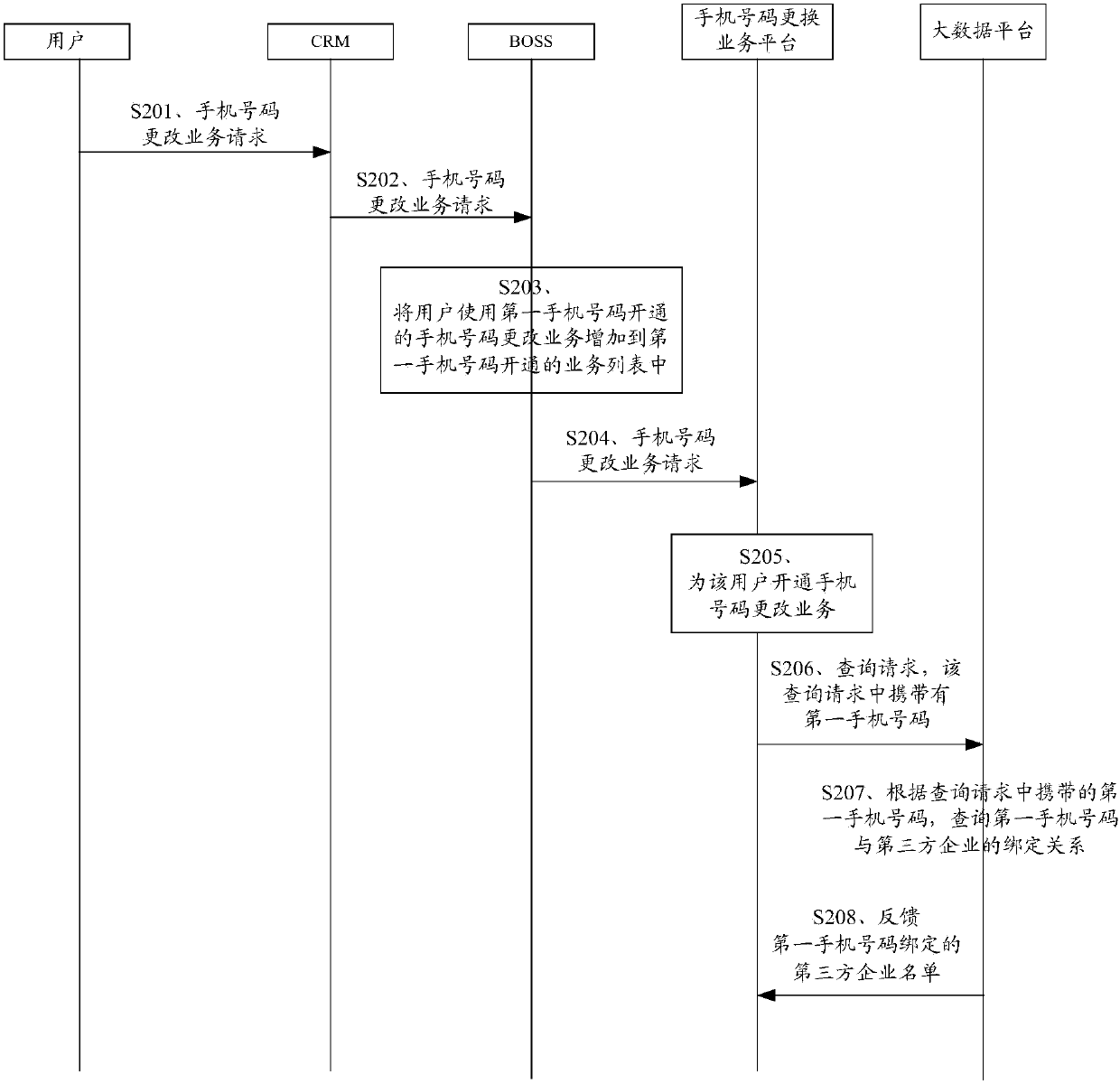
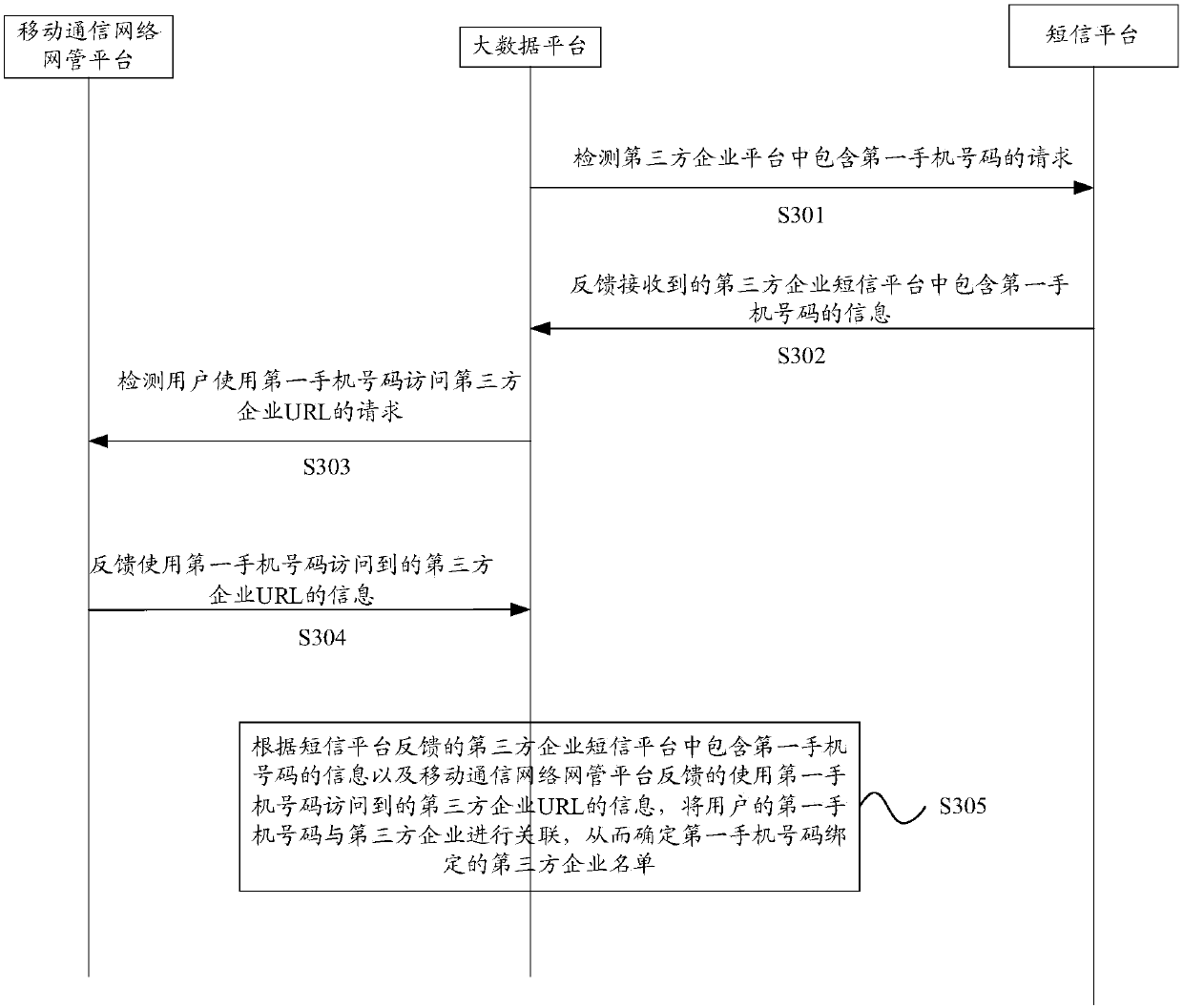
Method and device of changing bound cellphone number
Embodiments of the invention relate to the technical field of communication, and particularly relate to a method and a device of changing a bound cellphone number. The method comprises the steps thatan operator platform firstly receives a cellphone number changing request sent by a user, then determines a list of third-party enterprises bound with a first cellphone number after successful verification of real-name system information of the first cellphone number and real-name system information of a second cellphone number, and finally, after the third-party enterprises verify a bound numberchanging request successfully, the second cellphone number is used as a bound number of the user. According to the method, the list of the third-party enterprise bound with the first cellphone numberis determined after the real-name system information of the user is verified, and the real-name system information of the first cellphone number and the real-name system information of the second cellphone number of the user are verified by using a user cellphone number real-name system information base of the operator, so that security risks like personation and tampering are prevented.
Owner:CHINA MOBILE GROUP SHAIHAI +1
A method for dual-mode, dual-card and dual-idle terminal to realizing single number
InactiveCN101242601AImprove experienceFix billing issuesRadio/inductive link selection arrangementsTelephone set constructionsDual modeNetwork switch
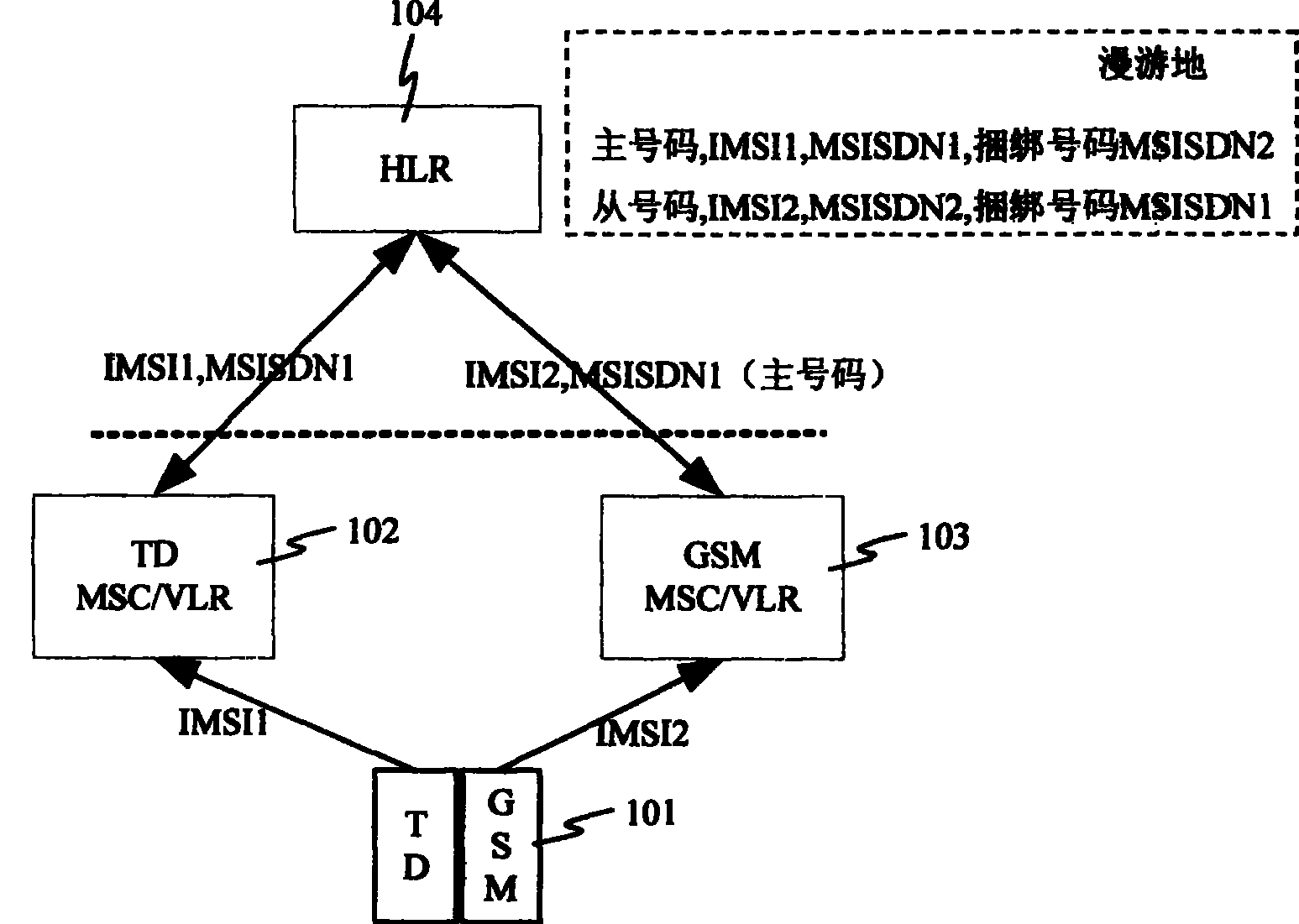
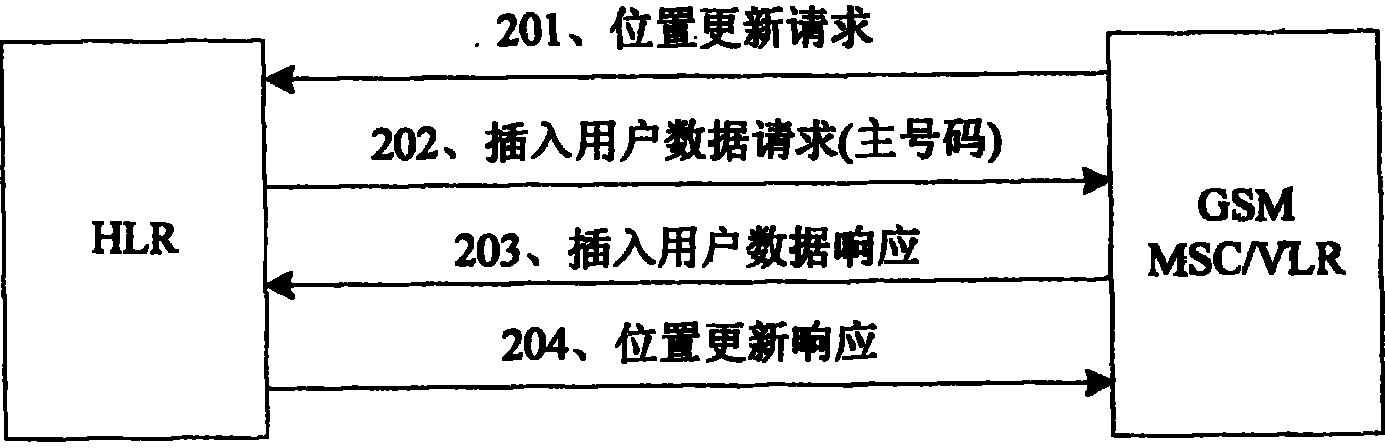
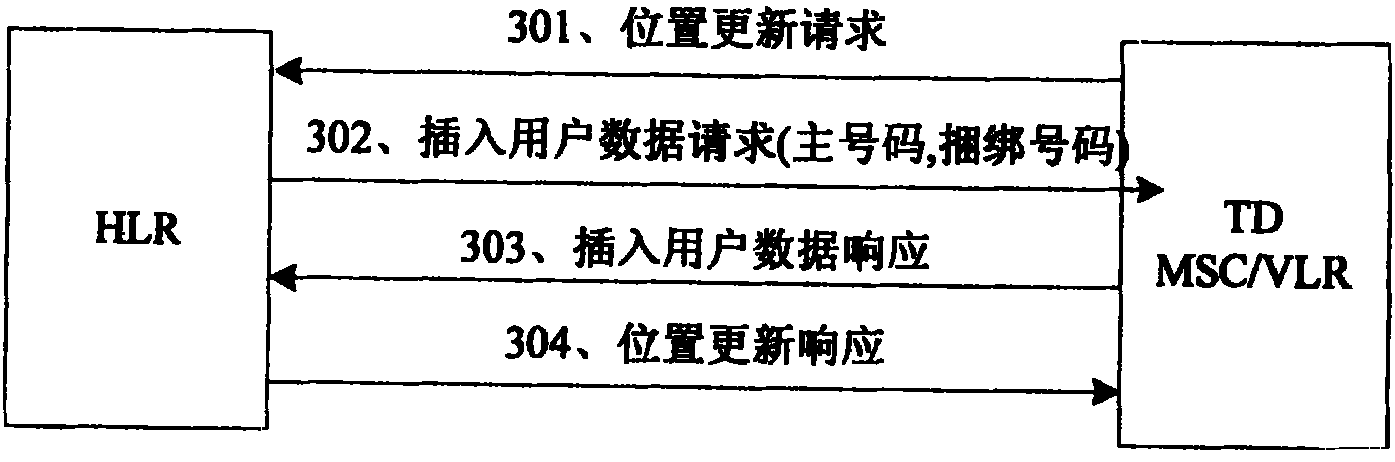
The invention discloses a method for realizing single number in a double mode double terminal double standby terminal, double card, including step one, establishing relation between master number and slave number on HLR; step two, using bound number of current user record as master number by HLR and synchronizing the same to VLR in GSM networks when location being updated and / or data being recovered in GSM networks; synchronizing number of current user record to VLR in TD networks when location being updated and / or data being recovered in TD networks; step three, acquiring route information in GSM networks by HLR and HLR in GSM networks, and completing routing service of the called and / or network switching service according to the route information in GSM networks services of the same are carried out. Application of the inventive method realizes routing service of the called and network switching service of double mode double terminal double standby user, and solves accounting problem of multiple numbers.
Owner:ZTE CORP
Safety control method for stage-outputting and multi-path monitoring of depositor bank account capital
The invention discloses a safety control method for stage-outputting and multi-path monitoring of depositor bank account capital, belonging to the field of financial safety. A capital account is divided into multi-stages; each stage has different functions. A plurality of special passwords for capital transferring and monitoring are set; the capital is transferred between each stage by a fixed phone and a mobile phone with binding numbers; and a special person can be set for monitoring the capital outputting; the times and sequences of each monitoring phone can be changed so as to ensure the safety of enormous capitals; moreover, the departments like the public security in the location of a received account for the outputted capital can be authorized to monitor the capital, and ensure the owner of the account to be true, legal and pursuable. The depositor can employ traditional modes (signature, original passwords, fingerprints, and the like) for using the capital transferred to a quasi-output stage. When the mobile phone is used, the information like the original passwords and the account number is not needed to be used, thus being capable of preventing a wireless signal from being intercepted and captured to blow the gaff; therefore, the goal of theft prevention can be realized by transferring the passwords and monitoring the outputted capitals under a hidden situation.
Owner:杨莉华
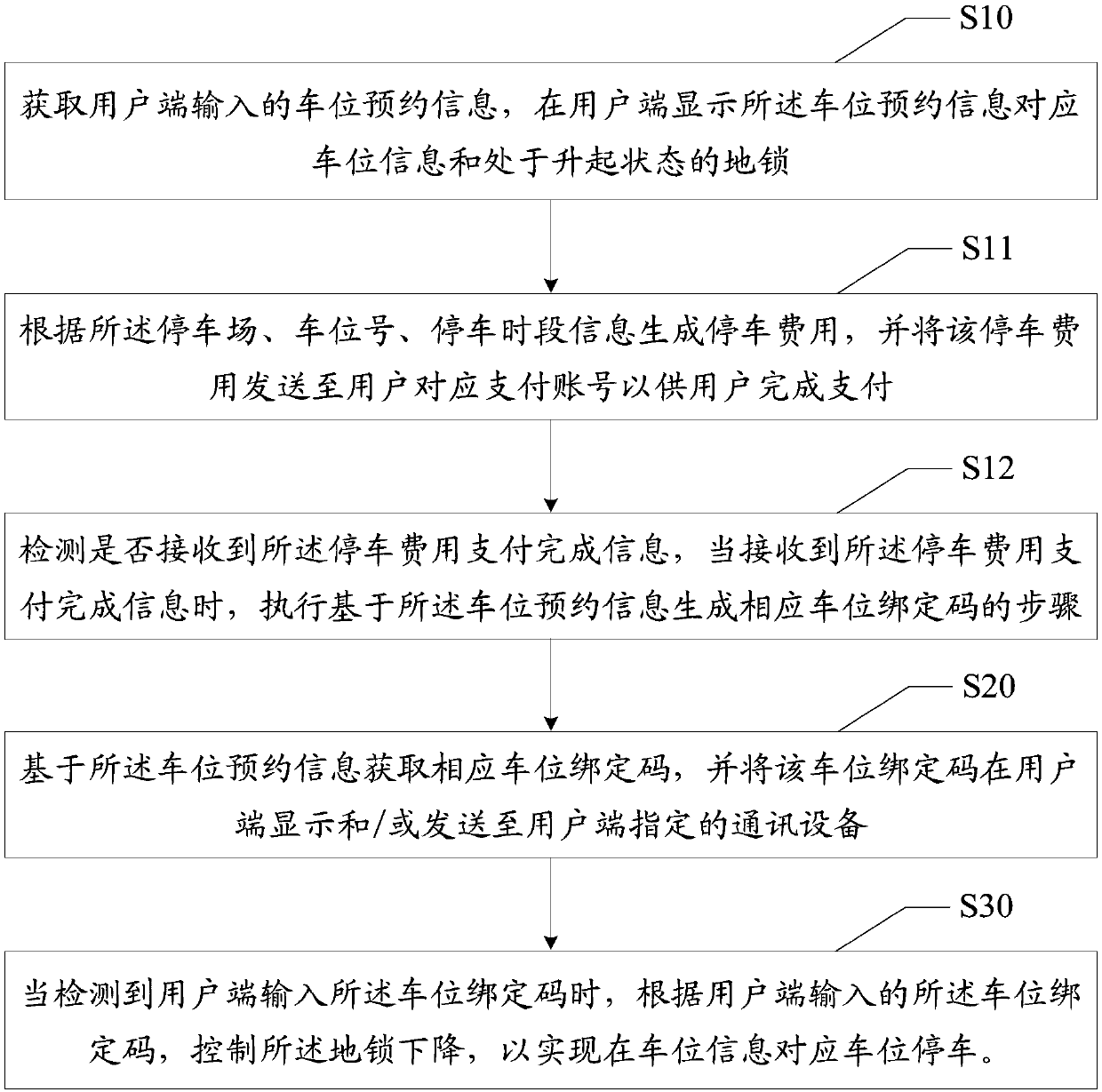
Parking space lock control method and device
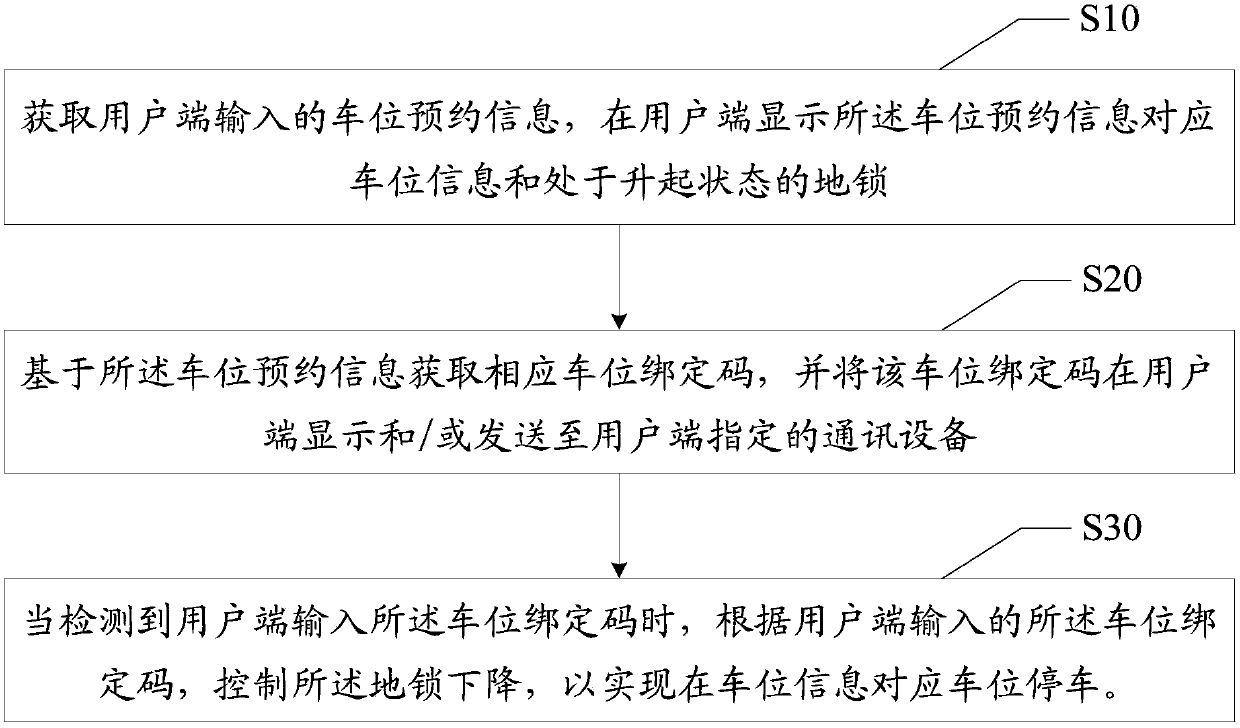
InactiveCN107730661AImprove the parking experienceEfficient managementTicket-issuing apparatusReservationsParking spaceReal-time computing
The invention discloses a parking space lock control method and device. The parking space lock control method comprises the following steps: acquiring parking space reserve information input from a user side, and displaying a lock of which parking space information corresponds to the parking space reserve information and which is positioned in a rising state by the user side; acquiring a parking space binding number corresponding to the parking space reserve information, and displaying the parking space binding number at the user side and / or transmitting the parking space binding number to communication equipment specified by the user side; controlling the lock to descend according to the parking space binding number input by the user side when the parking space binding number input by theuser side is detected, thereby parking at a parking space corresponding to the parking space information. According to the parking space lock control method disclosed by the invention, the technicalproblems in the prior art that user parking experience is poor and parking space management is difficult because a parking space lock cannot be unlocked in time even when the parking space is not occupied by other person can be solved.
Owner:XIAN IRAIN IOT TECH SERVICES CO LTD
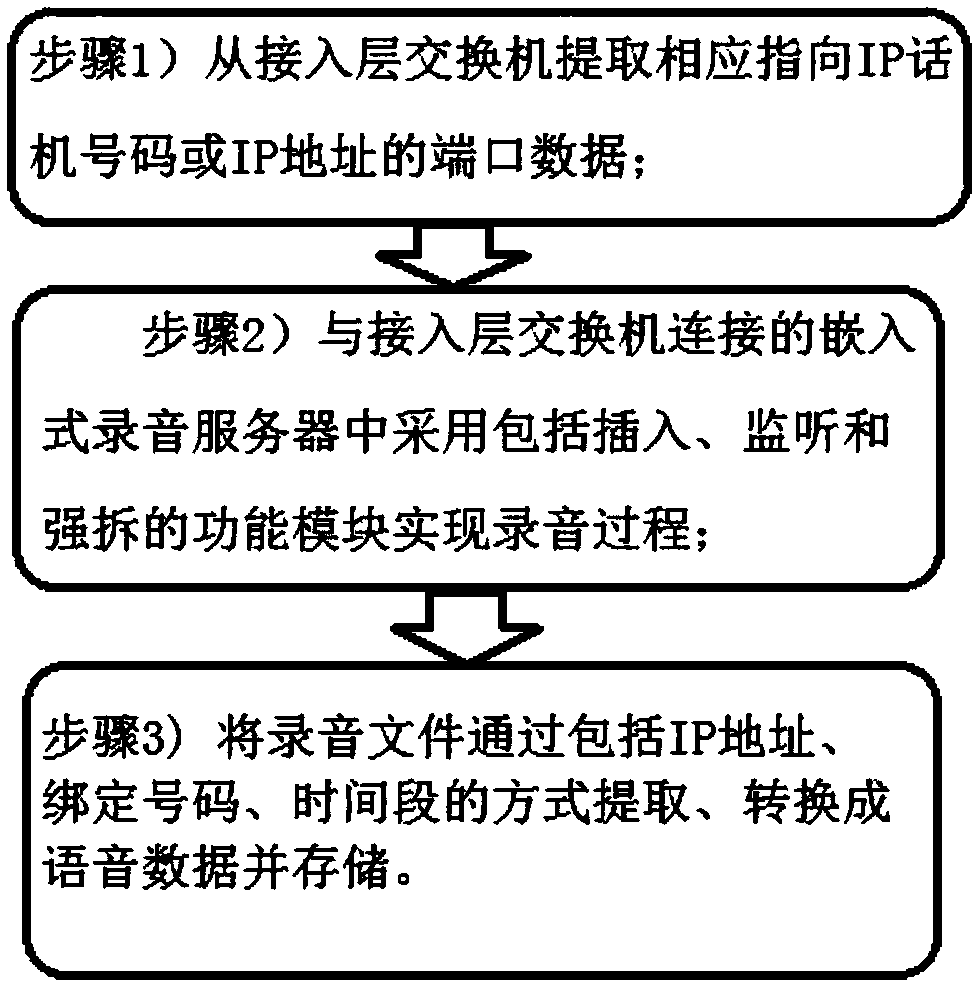
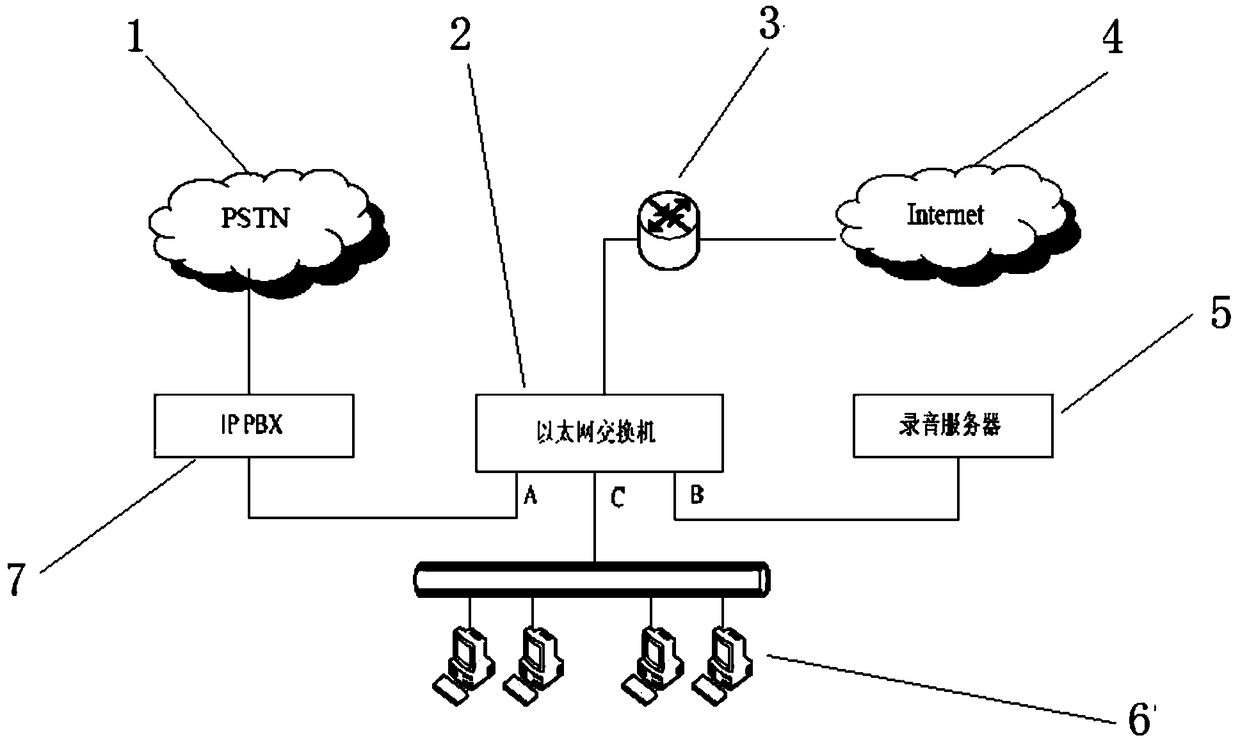
Access layer embedded IP recording method and a system based on softswitch
InactiveCN109218540AReduce volumeReduce power consumptionSpecial service for subscribersTelephone service networksIp addressData access layer
The invention discloses an access layer embedded IP recording method and an access layer embedded IP recording system based on softswitch. The method comprises the following steps: (1) extracting portdata corresponding to IP telephone number or IP address from the access layer switch; (2) extracting port data corresponding to IP telephone number or IP address from the access layer switch; (3) extracting port data corresponding to IP address from the access layer switch. 2) the embedded recording server connected with the access layer switch adopts a functional module including insertion, monitoring and forced disassembly to realize the recording process; Step 3) The recording file is extracted in a manner including an IP address, a binding number and a time period, and is converted into voice data storage. The scheme of the invention no longer adopts the traditional server plus software structure, but adopts the embedded structure based on the professional chip, so that the volume issmaller and exquisite, the power consumption is lower, the performance is more stable, the deployment is more convenient and the cost is lower. After the device is deployed in the access layer or terminal, the realization and extraction of the recording can be more convenient, and the coordination and management between departments can be more flat and efficient. Therefore, the device has a largerapplication field and foreground.
Owner:STATE GRID SHANDONG ELECTRIC POWER +1
Method for protecting bank account fund security and multiple specific applications thereof
InactiveCN102402774APrevent leakageLeak preventionComplete banking machinesFinanceBank accountPassword
The invention discloses a method for protecting bank account fund security and multiple specific applications thereof, and belongs to the field of financial security. The method comprises the following steps of: dividing accounts into multiple levels with different functions; setting a few fund transfer and monitoring passwords, transferring funds among the levels by using a fixed phone number of bound numbers, a monitoring phone and a mobile phone, setting multiple persons to monitor the output funds, and authorizing departments of public security and the like of the output fund receiver accounts to monitor the funds, thus ensuring reality, legality and traceability of account possessors. When the mobile phone is used, information such as original passwords, accounts and the like does not need to be used or sent, so that radio signals can be prevented from being divulged by intercepting; the password can be used and monitored under the concealed condition, and the deposited amount is used as the other password, so that the theft-proof purpose is fulfilled, and the theft behaviors of thieves such as secret photography, hobbyhorses, exchange and the like completely lose effect; and by the method, a large amount of financial fraud, depositor hijacking, bribery, absconding with money, tax evasion and malicious overdraft cases can be reduced.
Owner:杨莉华
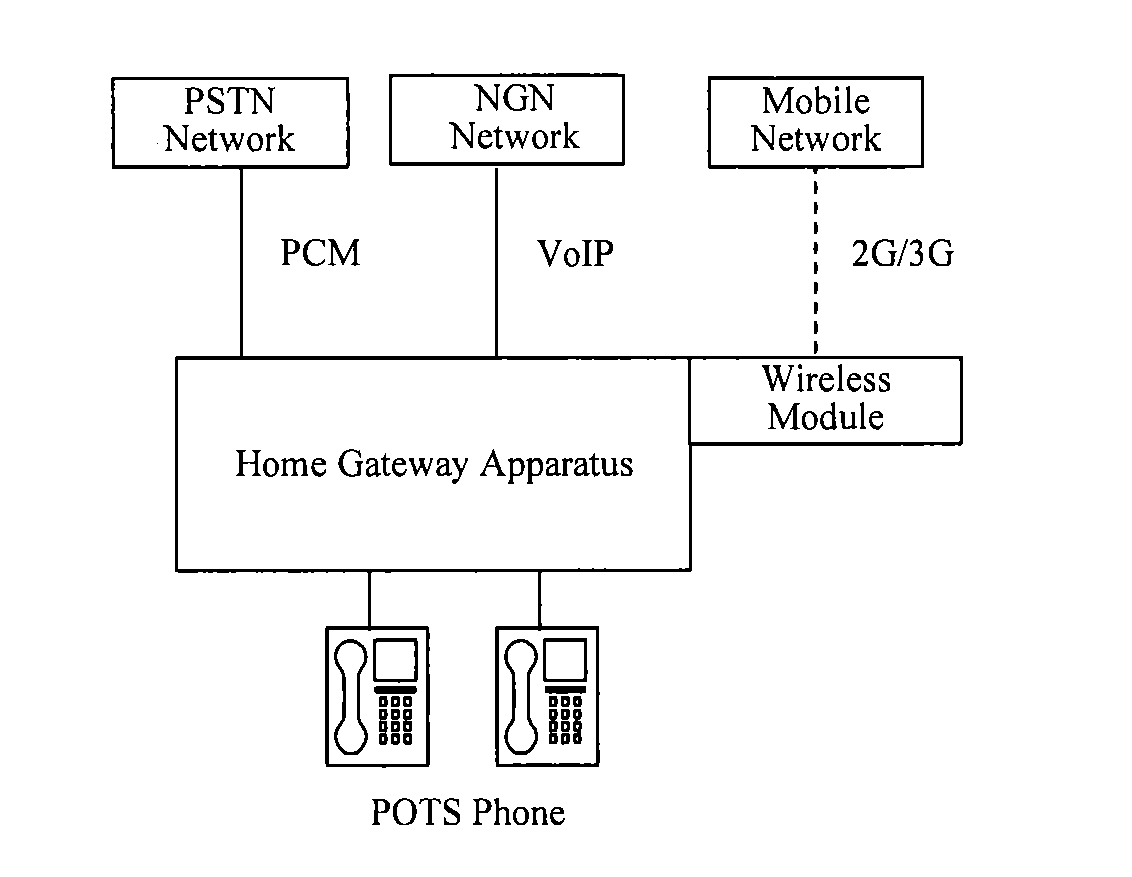
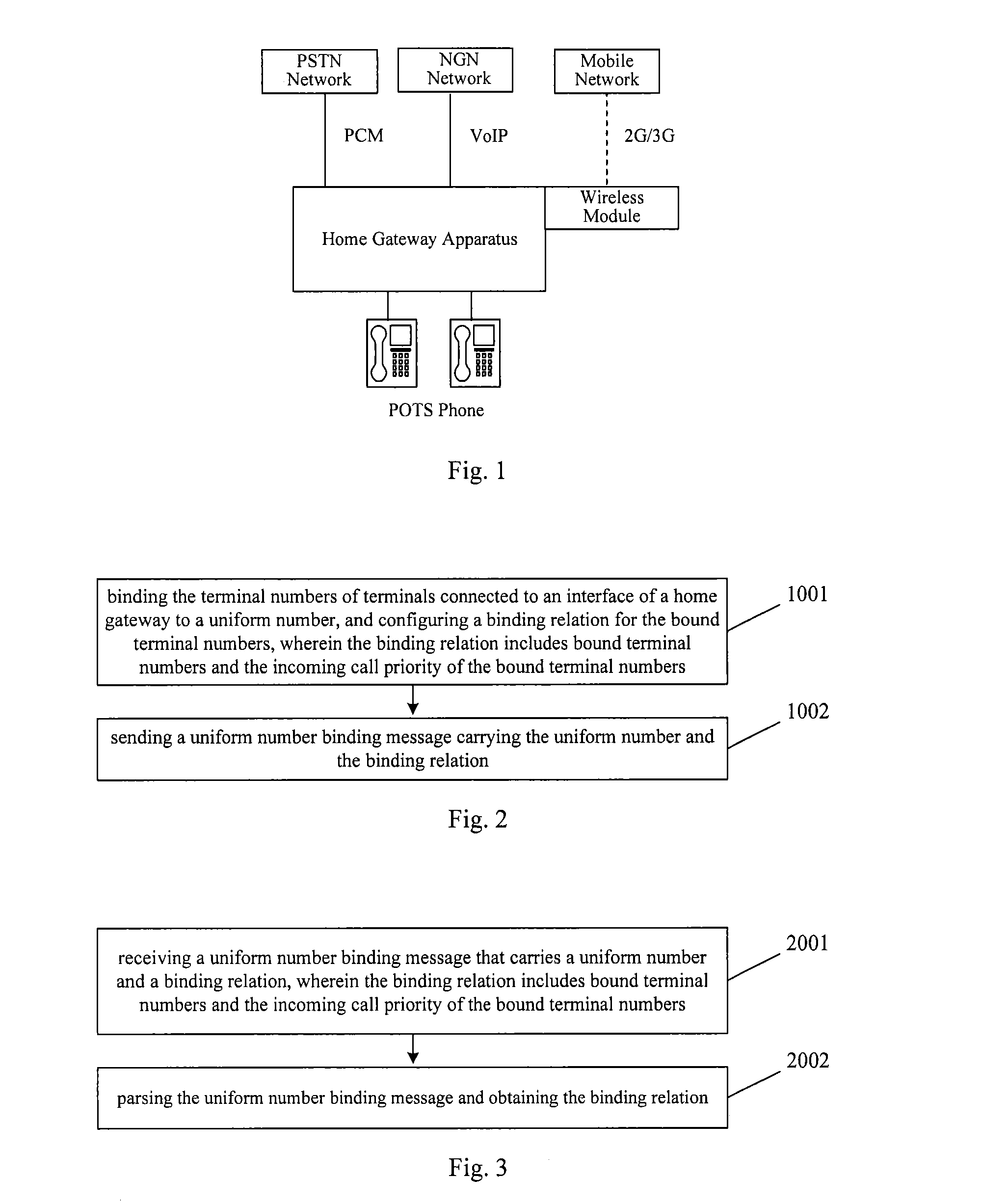
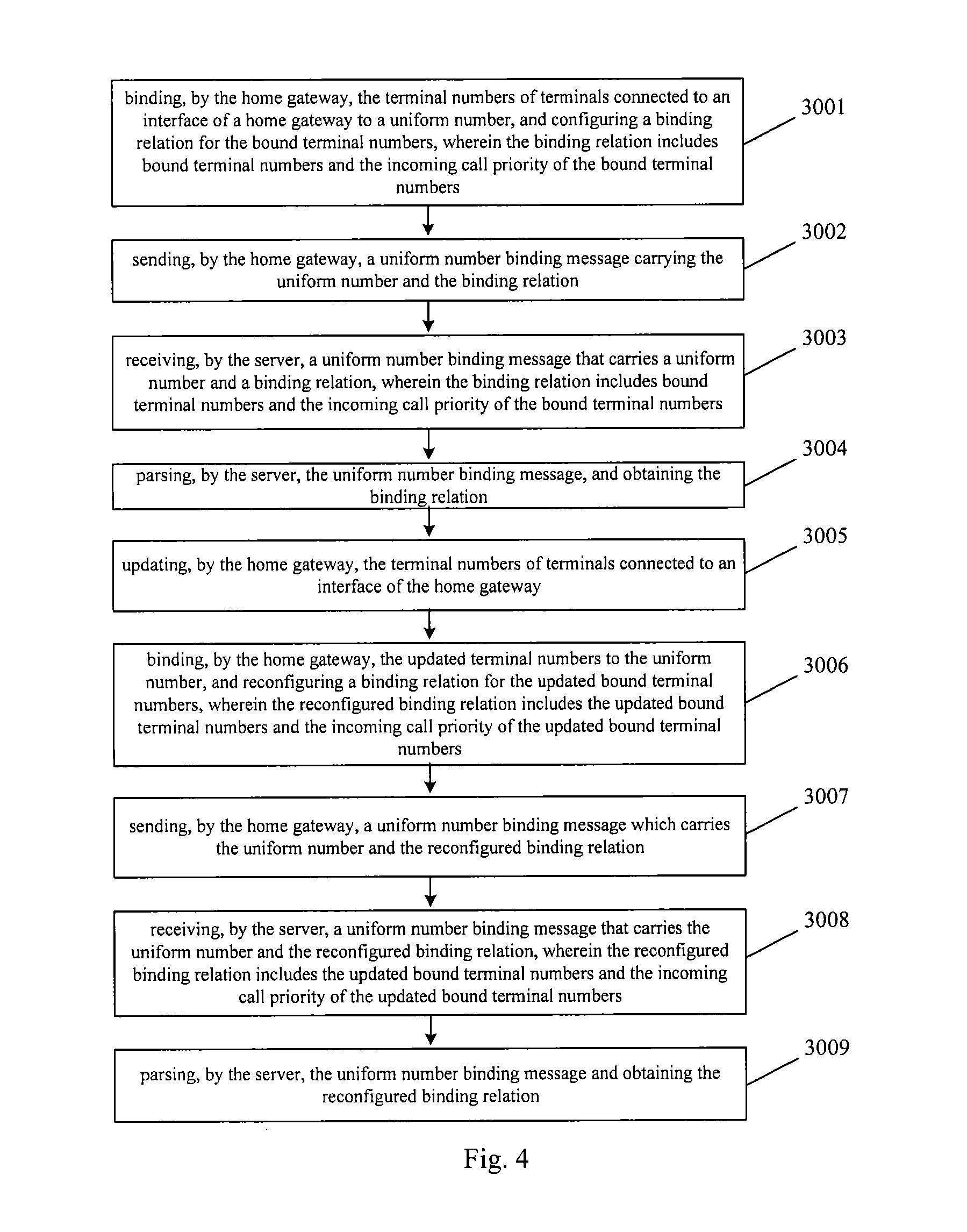
Method, device and system for uniform number communication on a home gateway
ActiveUS20130079023A1Improve user experienceReduce maintenance workloadInterconnection arrangementsSpecial service for subscribersAuto-configurationComputer terminal
The embodiments of the invention disclose a method, a device and a system for uniform number communication and relate to the technology field of mobile communication. The application of the uniform number service on a home gateway can be optimized by automatically configuring a uniform number and the incoming call priority of the bound numbers on the home gateway, and thus the user experience is improved and simultaneously the maintenance workload is reduced. The method for the uniform number communication includes the following steps: binding the terminal numbers of the terminals which are connected to an interface of the home gateway to a uniform number; configuring binding relation for the bound terminal numbers, wherein the binding relation includes the bound terminal numbers and the incoming call priority of the bound terminal numbers; and sending a uniform number binding message that carries the uniform number and the binding relation.
Owner:HUAWEI DEVICE CO LTD
PEG binding number detection method of PEG modifier protein
ActiveCN108267590AAccurate analysisEasy to operateElectrophoretic profilingPreparing sample for investigationRepeatabilityMole ratio
The invention relates to a PEG binding number detection method of PEG modifier protein. The PEG binding number detection method comprises the following steps of after treating a sample of PEG modifierprotein to be detected, totally releasing PEG, detecting the mass of PEG, and through the mole ratio of the protein and PEG, calculating the binding number of PEG in the PEG modifier protein. The method is applicable to different protein types and different PEG modifier types, particularly the protein complex in stereoscopic structure and large in molecular weight and steric hindrance and modified by PED, and by means of other existing methods, it is difficult to accurately analyze the PEG binding number. Moreover, the method is easy to operate and high in repeatability and can accurately analyze the PEG binding number of the PEG modifier protein.
Owner:ZONHON BIOPHARMA INST
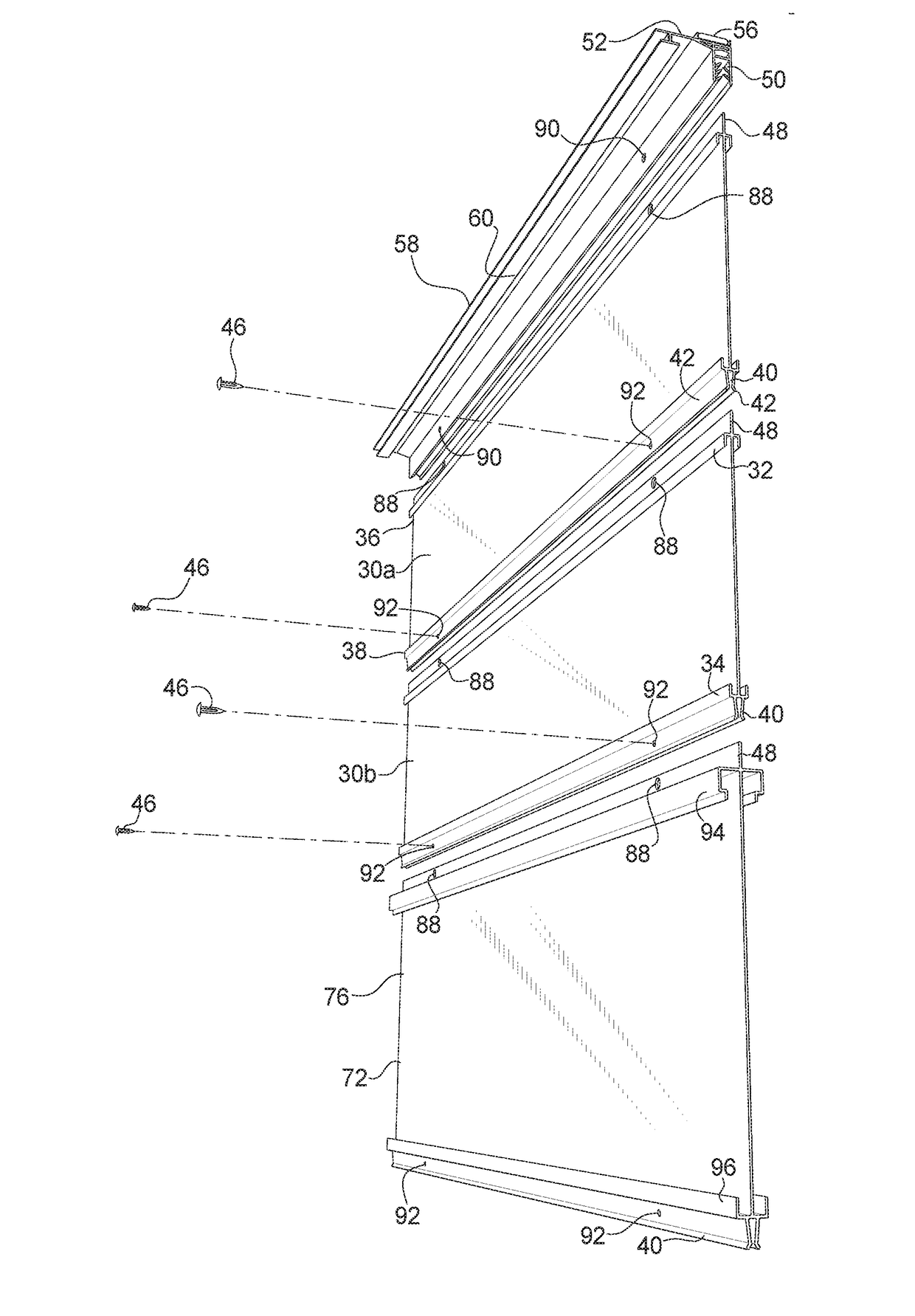
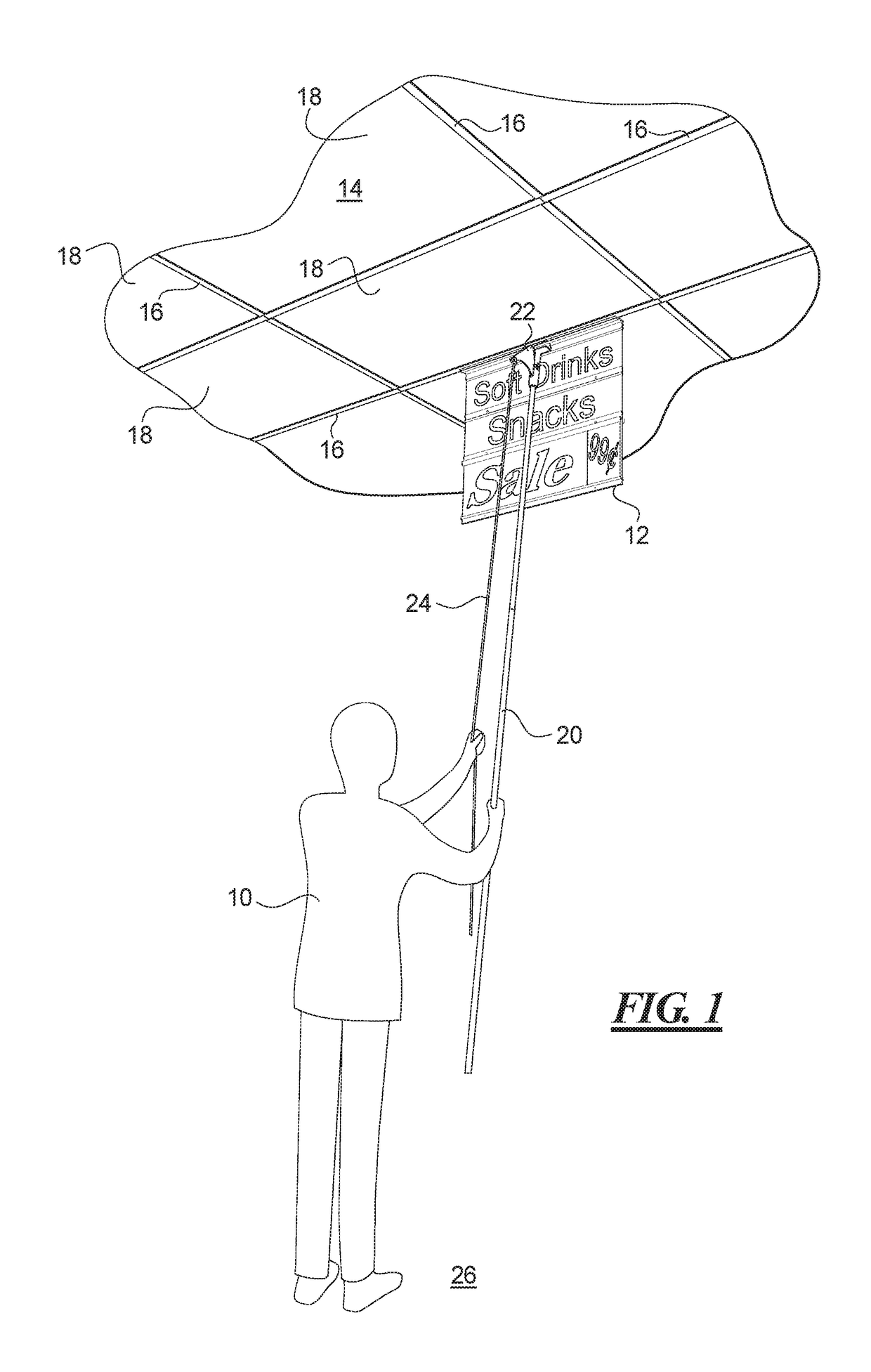
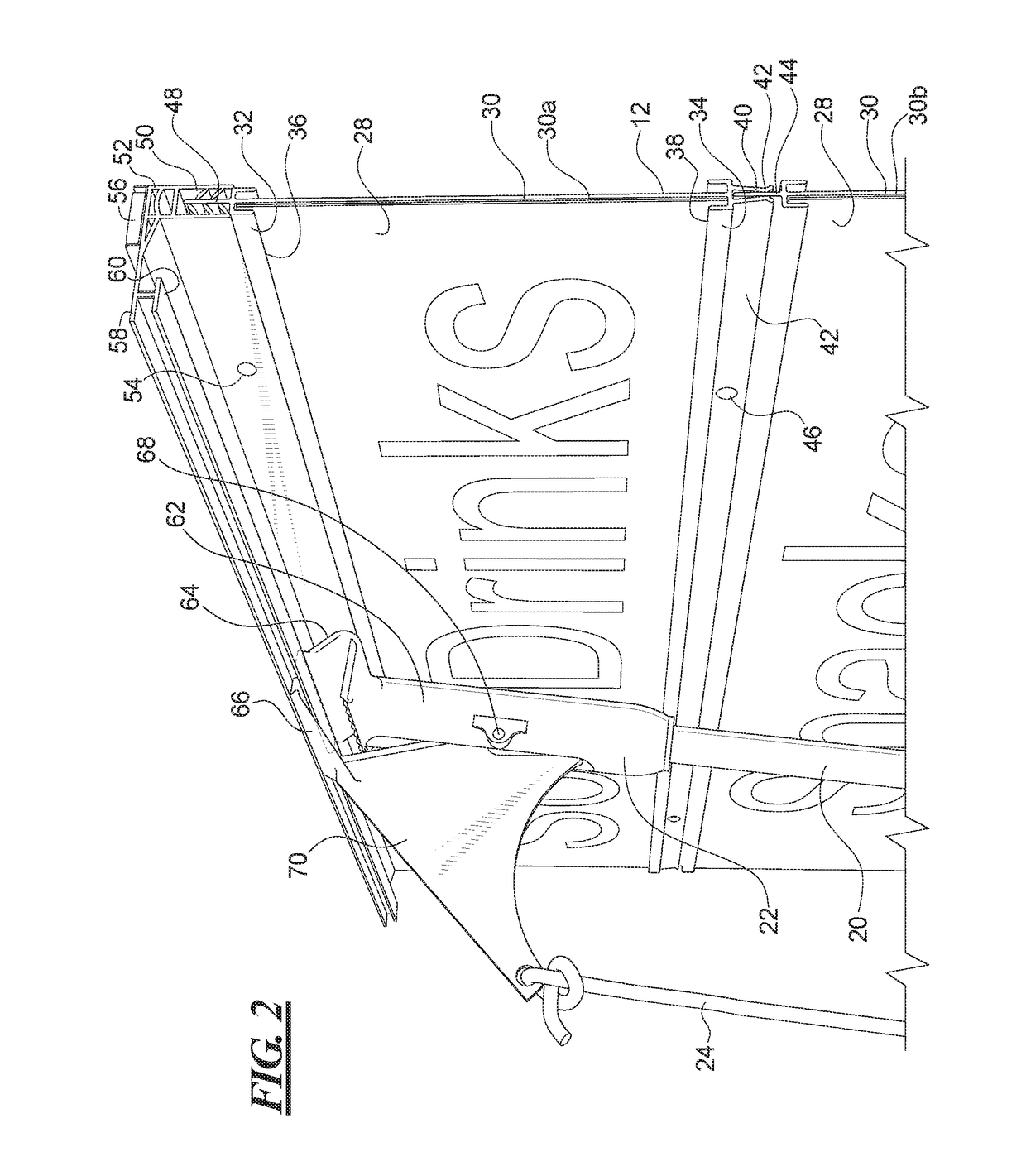
Modular flush-mount sign channel track system and method
ActiveUS20170103686A1Quicker and less-expensive to formNot easy to damageMachine supportsSecuring devicesFlangeGrippers
A system and method for magnetically mounting a sign flush at a ceiling, window, or wall location that includes modular panels that are removably connected to one another to form a sign board stack. The sign board stack is mounted or unmounted from a prominent display location using a pole end gripper without the need for a ladder. The sign stack extends from a mounting strip having a holder at which the sign stack is fastened, and the gripper engages the mounting strip at an offset grasping portion disposed laterally of the holder. The panels have flanges at the top edge to fit into the holder of the mounting strip and clips at the bottom edge to hold a flange of a panel connected below it. Channel tracks are formed on the panels to hold strip sign elements, some of which may include accordion or spiral bound numbers or messages.
Owner:K INT
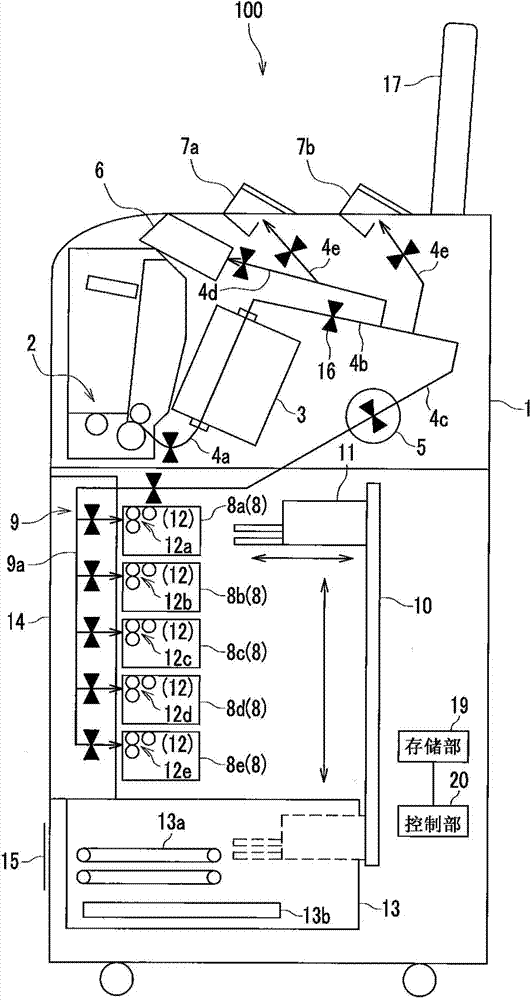
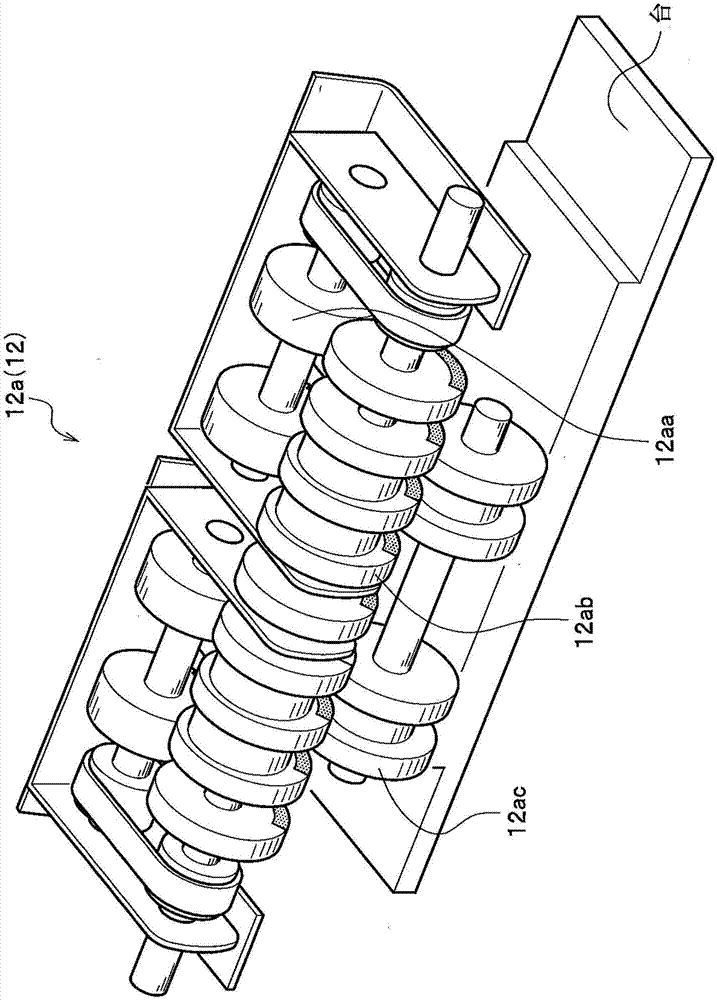
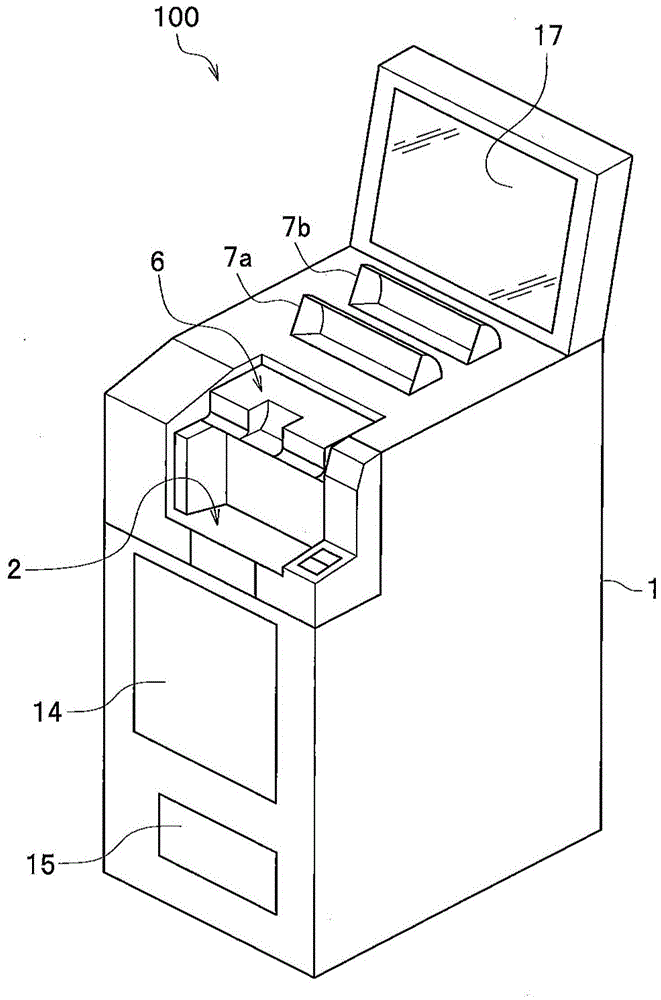
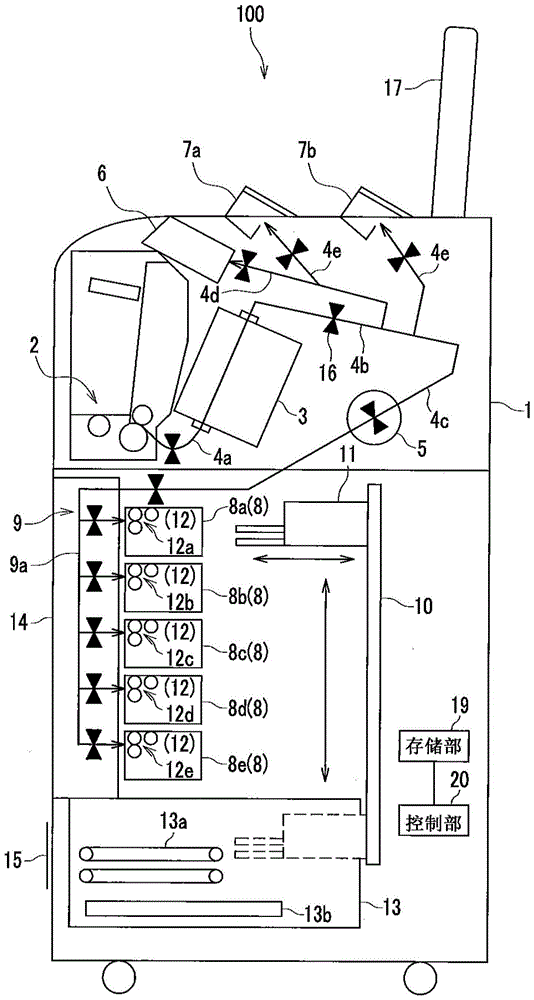
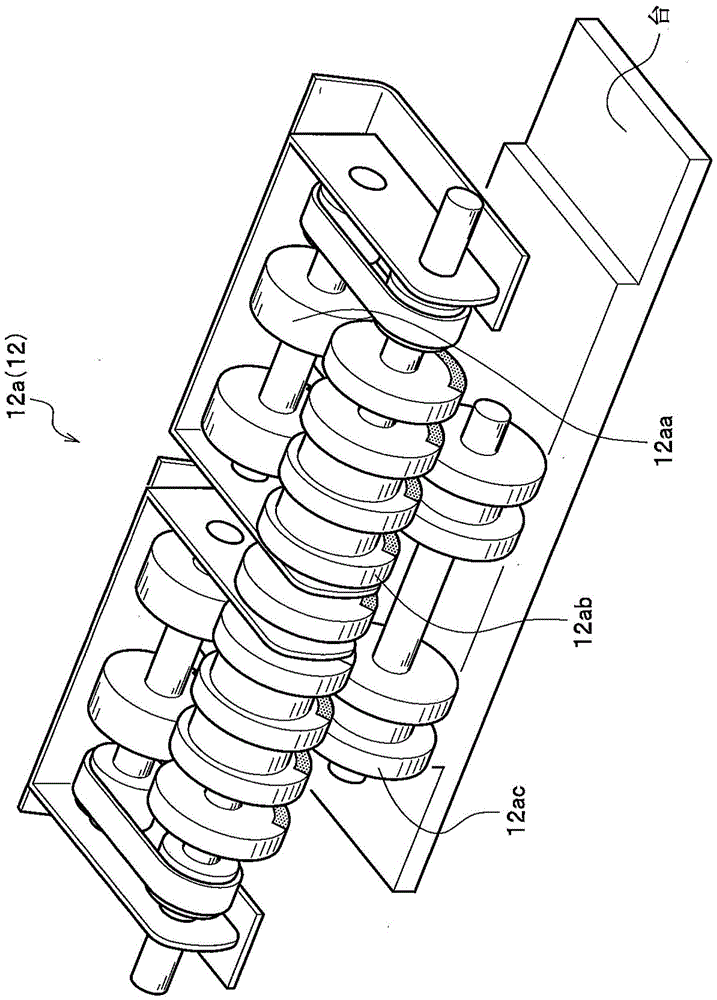
Paper page processing device
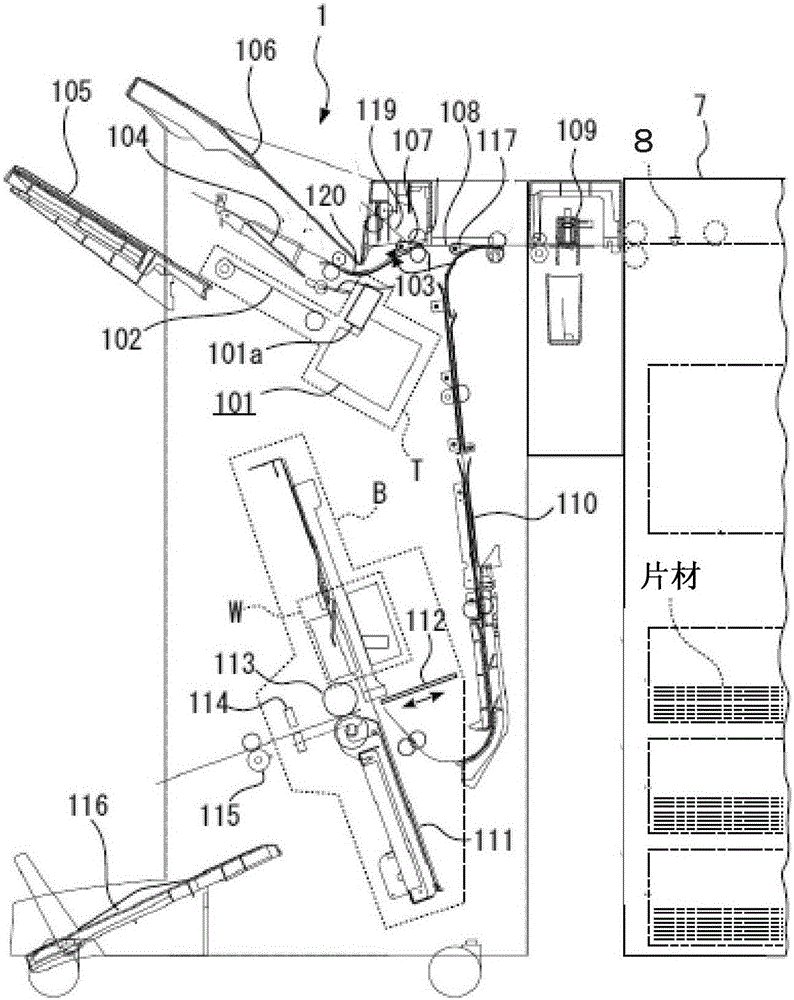
The invention provides a paper page processing device which takes out remaining pages not up for a binding number very conveniently. The paper page processing device comprises a housing. A paper page inputting part is arranged in the housing for paper pages to be put in. A storing part is arranged in the housing for keeping the inputted paper pages until the number of the paper pages reaches the number for binding. A separation part is arranged to separate remaining paper pages. A transportation track is externally arranged on the housing to transport already separated paper pages. The separation part separates remaining paper pages left in the storing part when a business deal is normally completed or the paper pages are transported wrongly.
Owner:OKI ELECTRIC IND CO LTD
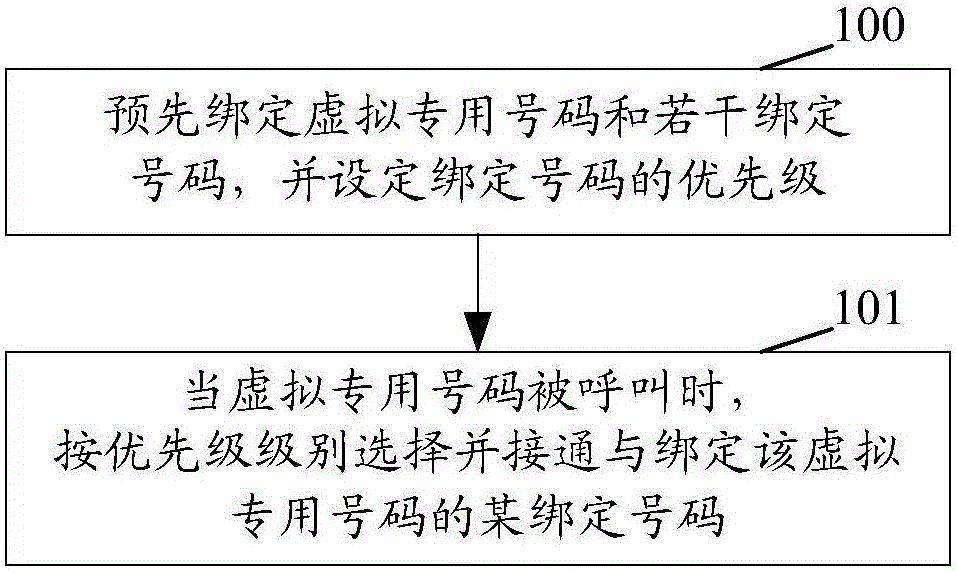
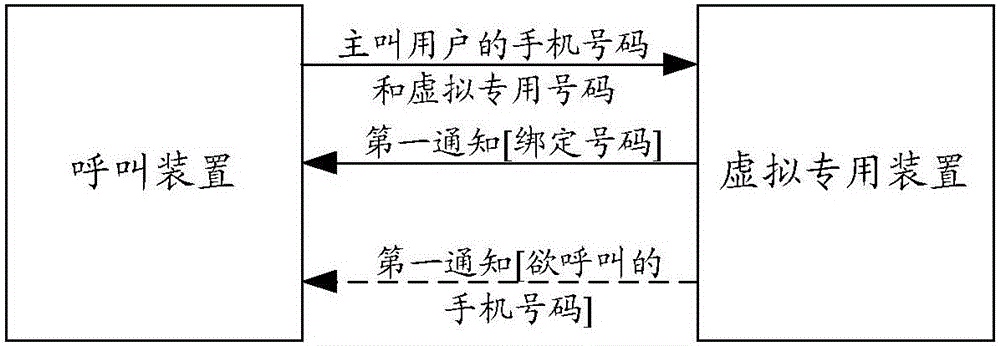
Call realization method and system, virtual special device and calling device
InactiveCN105101134AMeet call needsAvoid missed connectionsCommmunication supplementary servicesSimulationBinding number
The invention discloses a call realization method and system, a virtual special device and a calling device. The method comprises the following steps: binding virtual special number and a plurality of binding numbers in advance, and setting priority of the binding numbers; and when the virtual special number is called, selecting and connecting some binding number bound with the virtual special number according to the priority level. According to the method, the calling need of a small-size customer service team is met; any user can realize communication with the customer service team members by merely calling the virtual special number directly; and the problem of call missing is prevented well.
Owner:CHINA UNITED NETWORK COMM GRP CO LTD
A method, device and system for realizing one number service
ActiveCN102469425BReduce on-timeImprove user experienceCommmunication supplementary servicesNetwork data managementComputer scienceMobile phone
The invention provides a method for realizing a one number service, an apparatus thereof and a system thereof. The method comprises the following steps: a network intelligent apparatus receives a call request to a second terminal initiated by a first terminal; the network intelligent apparatus inquires at local whether the second terminal signs the one number service or not, and if the one number service is signed, the apparatus acquires a binding number which is in simultaneous vibration / sequential vibration with the second terminal, wherein, a terminal corresponding to the binding number is a third terminal; the network intelligent apparatus initiates a first call to the third terminal and a second call to the second terminal, wherein, the second call carries mark information of a triggered one number service. According to a scheme of the present invention, connection duration of a calling mobile phone answering of the one number service can be reduced, and usage experience of a user is improved.
Owner:CHINA MOBILE GRP BEIJING
Construction method of nano-drug carrier based on nucleic acid
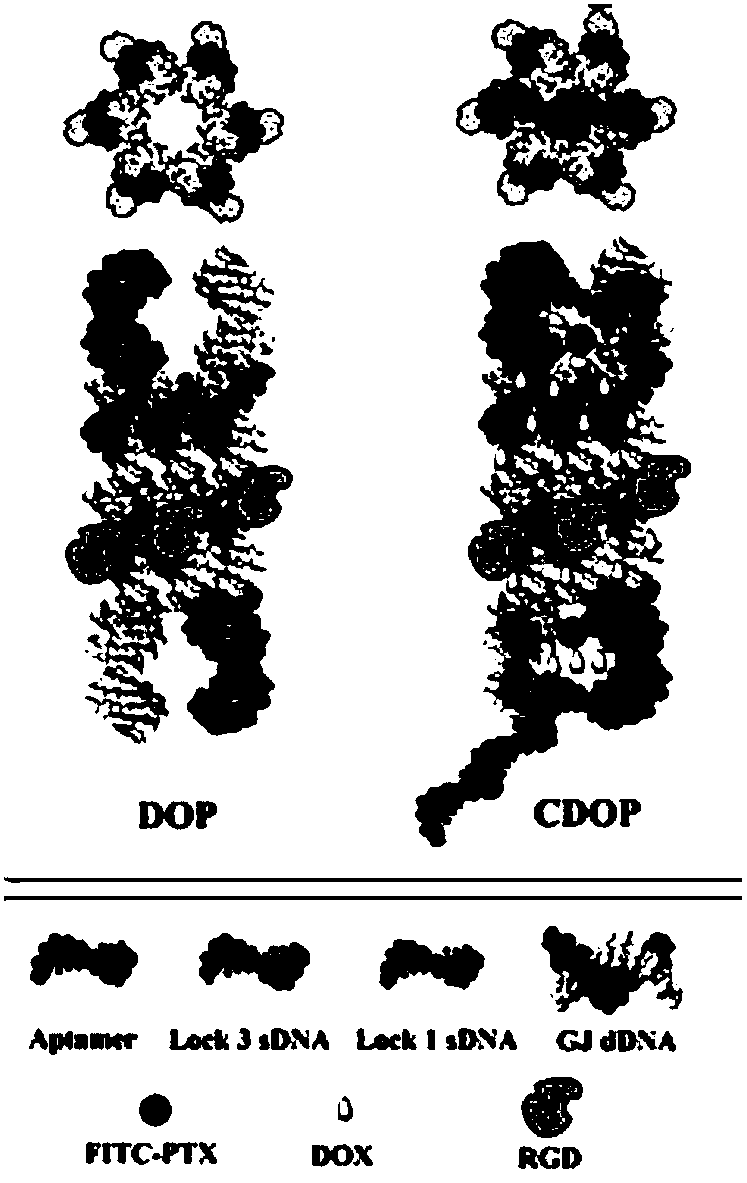
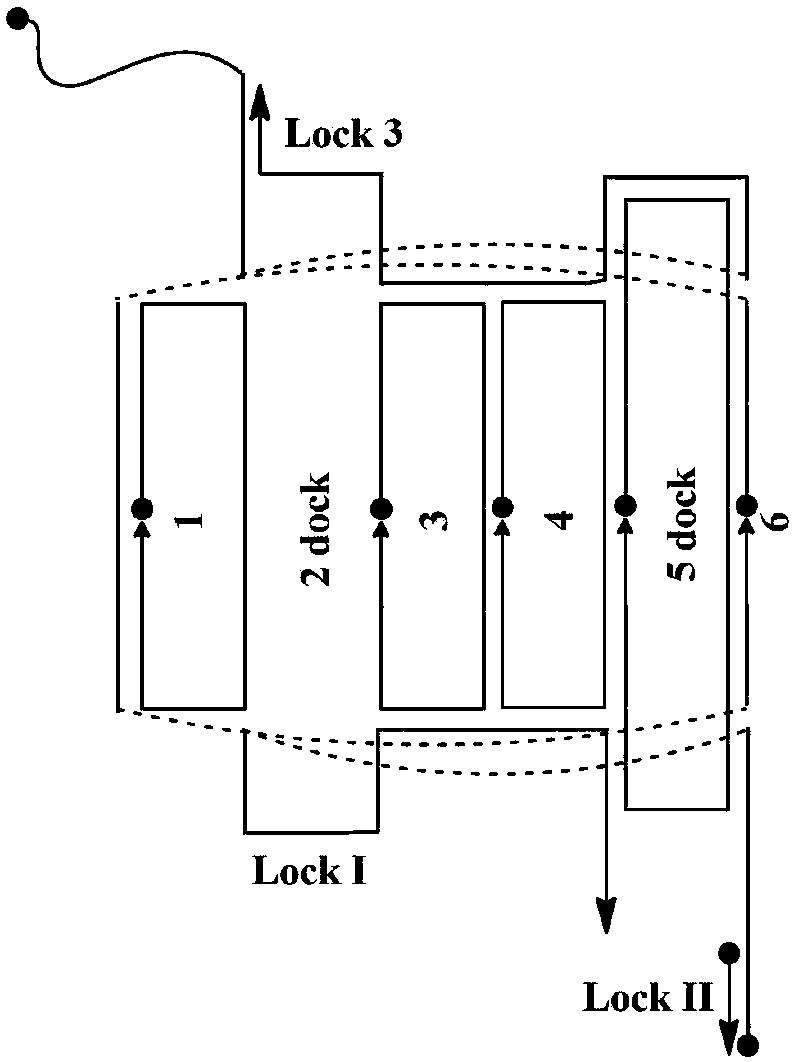
ActiveCN108187062AImprove bioavailabilityHigh biosecurityOrganic active ingredientsPharmaceutical non-active ingredientsSingle strandRigid structure
The invention discloses a construction method of a nano-drug carrier based on nucleic acid. The drug carrier is of a columnar rigid structure that six groups of double helixes are mutually twisted; acolumnar going-through hole, which is 1.8-2nm in diameter, is formed in the middle of the columnar rigid structure; two ends of the carrier are blocked by locked nucleic acid single strands lock1 andlock3; one part of a blocking sequence lock3 at one end is a complementary sequence of a target aptamer mRNA; measured by dynamic light scattering, the overall length of the carrier is 40+ / -4.3nm; when the target aptamer mRNA exists in cells, an entropy substitution process occurs since the number of paired bases between the target mRNA and the lock3 is much greater than a binding number between the lock3 and basic structural ports of the carrier, so that one end of the carrier is opened, and drugs in the carrier are released. According to the construction method provided by the invention, bytaking the nucleic acid existing in an organism as a raw material, a pairing situation between the bases can be regulated and controlled through artificial design, so that the nucleic acid is converted into a shape-controllable origami structure through three-dimensional folding, and the basic carrier for drug loading is obtained.
Owner:QINGDAO UNIV OF SCI & TECH
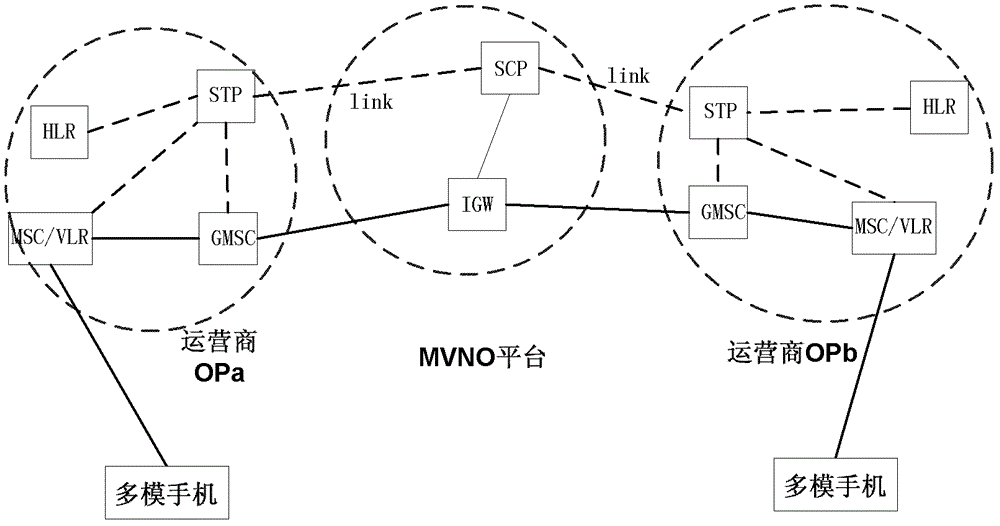
Implementation method and device for multi-mode mobile phone roaming across networks
ActiveCN102238504BImplement call controlSeamless roamingCommmunication supplementary servicesNetwork data managementMobile communication networkMobile phone
A method for implementing cross-network roaming of multi-mode mobile phone and a device thereof. The method includes: step I, providing a multi-virtual number operation platform (MVNO) for maintaining the multi-number binding relationship in a multi-mode mobile phone in a mobile communication network; step II, when the multi-mode mobile phone starts up, sending a start-up register request message to the MVNO via a local mobile switching center (MSC); step III, the MVNO searching for a bound number bound therewith according to the multi-mode mobile phone start-up number in the start-up register request message and forwarding the same to a start-up number home location register (HLR) and the HLR of the bound number; and step IV, the MVNO initiating an instruction to notify the HLR of the bound number to set a non-conditional forward number as access code + the start-up number. By way of the present invention, seamless roaming of the multi-mode mobile phone is realized among different operator networks.
Owner:ZTE CORP
Sheet post-processing apparatus and sheet post-processing method
The invention relates to a sheet post-processing apparatus and a sheet post-processing method which can continuously receive a certain number of print indicated sheets and perform binding process. The sheet post-processing device includes a storage portion, an adhesive binding portion, and a controller; the storage portion stores an allowable binding number of sheets at one time; the adhesive binding portion binds each fed sheet with glue and adhesive-binds the sheets; the controller calculates a remaining number of sheets, according to the number of print indicated sheets and the allowable binding number of sheets, compares the number of print indicated sheets and the preset remaining number of sheets, and sets a first mode if the remaining number of sheets is less than the preset remaining number of sheets, wherein the first mode allows the adhesive binding portion to use the number of print indicated sheets as a bundle to perform binding.
Owner:KK TOSHIBA +1
Immunoassay method and immunoassay apparatus
The invention provides an immunoassay method and an immunoassay apparatus capable of further reducing errors due to non-target substances. A detector measures a measurement specimen and detects information regarding the binding number of carrier particles included in the measurement specimen. A controller classifies, based on the information regarding the binding number, particles included in the measurement specimen into groups, the groups being classified in accordance with the binding numbers. Further, for each classified group, the controller performs either one of a first removing process for removing, from a processing target, data of non-target substances different from the carrier particles, and a second removing process for removing, from the processing target, data of the non-target substances through a process different from the first removing process, and obtains information regarding the agglutination degree of the carrier particles, based on data of the carrier particles obtained by performing the removing process.
Owner:SYSMEX CORP
Method for implementing multiple phone numbers for one phone set
ActiveCN100477822CHigh trafficCommmunication supplementary servicesNetwork data managementTelecommunicationsBinding number
Number associative cell sets up correspondence between numbers published to outside and numbers used inside network. In time of treating a call, numbers used inside network are in use for binding numbers published to outside. When user in multiple phone numbers for one phone set a call, exchange unit triggers the call to the number associative cell. Under control of the associative cell, the exchange unit switches the call to an exchange unit corresponding to the called number, which is switched to the called terminal. When calling number launches a call to numbers published to outside, the exchange unit corresponding to the calling number switches the call to the number associative cell. Looking up correspondence between numbers published to outside and numbers used inside network, the number associative cell changes the number published to outside to number used inside network. Through exchange unit corresponding to numbers used inside network, called terminal is switched.
Owner:HUAWEI TECH CO LTD
A communication method between a functional machine and an intelligent machine
InactiveCN104038911BGet through social communication communication issuesKeep abreast of the location status at any timeMessaging/mailboxes/announcementsData switching networksComputer networkSpeech sound
The invention discloses a communication method between a functional machine and a smart machine. The smart machine is installed with a smart machine client, and the smart machine is bound to the service number by following a service account and performing a corresponding binding operation on the WeChat of the smart machine. Its own number and the function phone number of the other party to be communicated. After the WeChat terminal is successfully bound, the corresponding binding relationship will be established on the server; it is divided into two types: the function phone sends voice messages and sending locations to the smart phone, and WeChat sends the bound function phone The number sends voice messages and inquires about the location of the function phone, and the smart phone sends voice messages and inquires about the location of the function phone; this method enables the user of the function phone to chat with the user of the smart phone through WeChat via WeChat; at the same time, it can also achieve real-time positioning and trajectory query Function.
Owner:林江榕
A method for dual-mode, dual-card and dual-idle terminal to realizing single number
InactiveCN101242601BImprove experienceFix billing issuesTelephone set constructionsWireless communicationDual modeComputer terminal
The invention discloses a method for realizing single number in a double mode double terminal double standby terminal, double card, including step one, establishing relation between master number and slave number on HLR; step two, using bound number of current user record as master number by HLR and synchronizing the same to VLR in GSM networks when location being updated and / or data being recovered in GSM networks; synchronizing number of current user record to VLR in TD networks when location being updated and / or data being recovered in TD networks; step three, acquiring route information in GSM networks by HLR and HLR in GSM networks, and completing routing service of the called and / or network switching service according to the route information in GSM networks services of the same arecarried out. Application of the inventive method realizes routing service of the called and network switching service of double mode double terminal double standby user, and solves accounting problemof multiple numbers.
Owner:ZTE CORP
Binding method of elevator external-call display panel, electronic equipment and storage medium
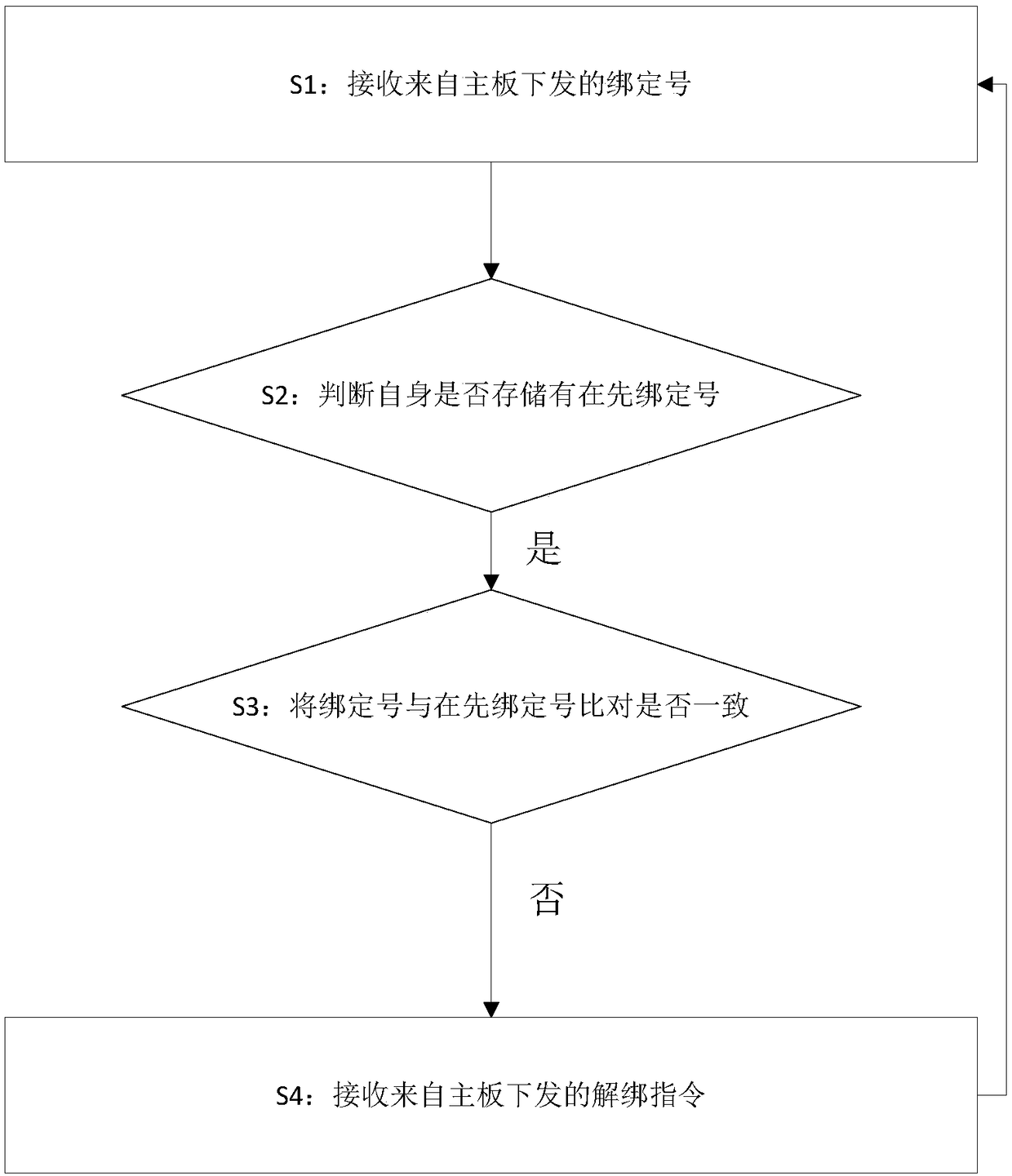
InactiveCN108328439AEasy to controlCan not be replaced at willElevatorsEngineeringElectric equipment
The invention discloses a binding method of an elevator external-call display panel. The binding method is characterized by comprising the following steps that receiving is conducted, specifically, abinding number issued by a main board is received; judging is conducted, specifically, whether a preceding binding number is self-stored or not is judged, if yes, a comparison step is carried out, andif not, the binding number is stored to be the preceding binding number; comparison is conducted, specifically, whether the binding number and the preceding binding number are consistent or not is compared, if yes, communication is established, and if not, alarming is conducted; and unbinding is conducted, specifically, an unbinding instruction issued by the main board is received, the precedingbinding number is eliminated, and then the receiving step is repeated. According to the binding method, the external-call display panel needs to compare the binding number, and can establish communication with the elevator main board only under the situation that the binding number is consistent with the binding number of the elevator main board, otherwise, a corresponding breakdown is prompted, therefore, an elevator can be better managed and controlled, and the external-call display panel and the elevator main board cannot be replaced and exchanged at will.
Owner:杭州句力科技有限公司
A Copper Wire Bundle Kidnapped
Owner:ANHUI YUSHENG HAOHAN ELECTRONICS TECH
Method for updating double-module mobile phone network binding number
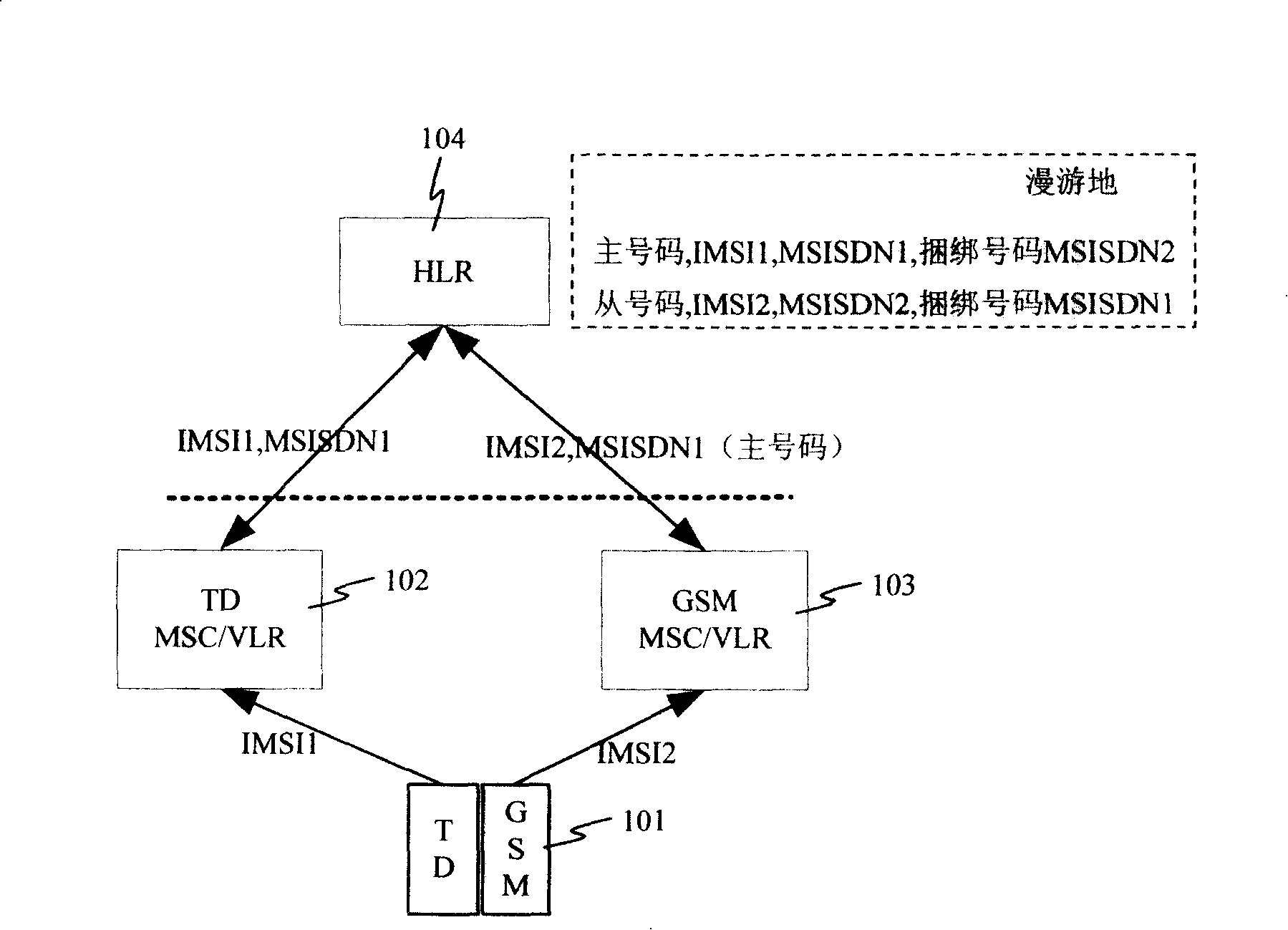
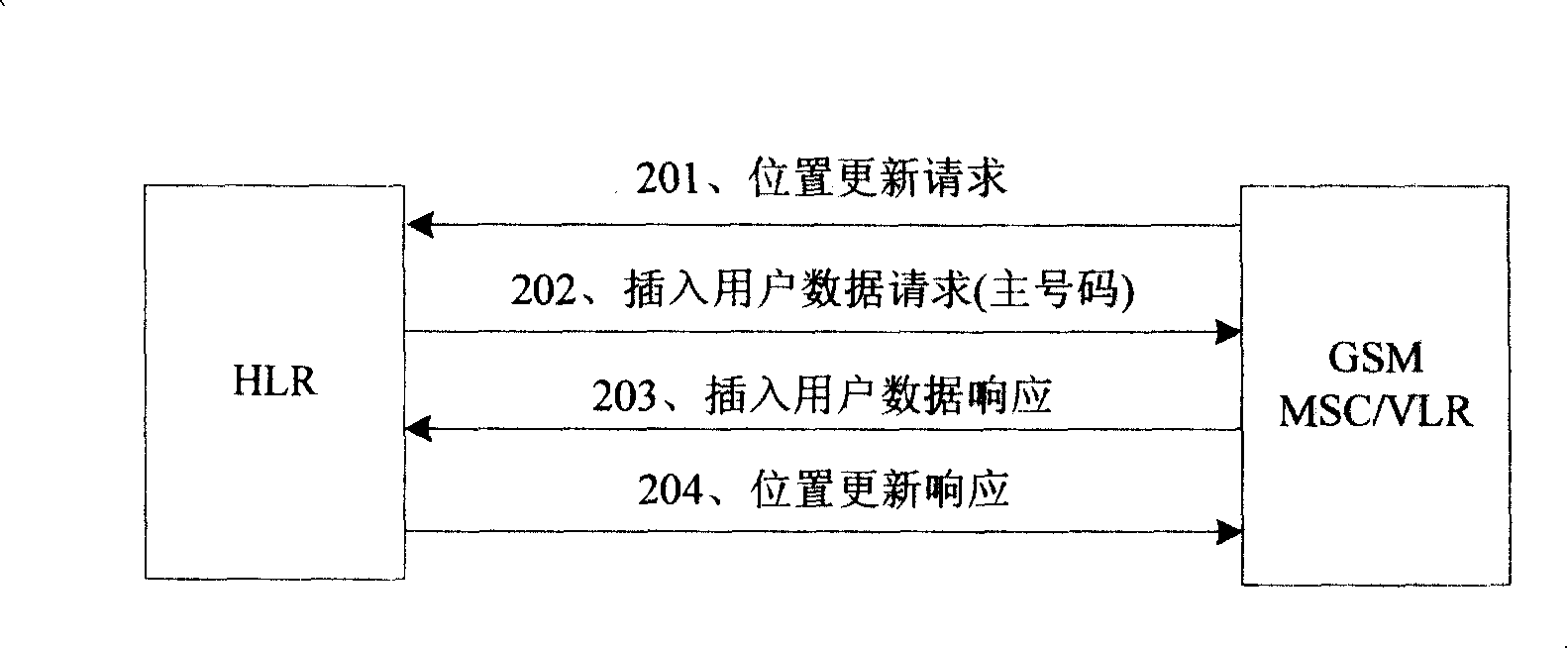
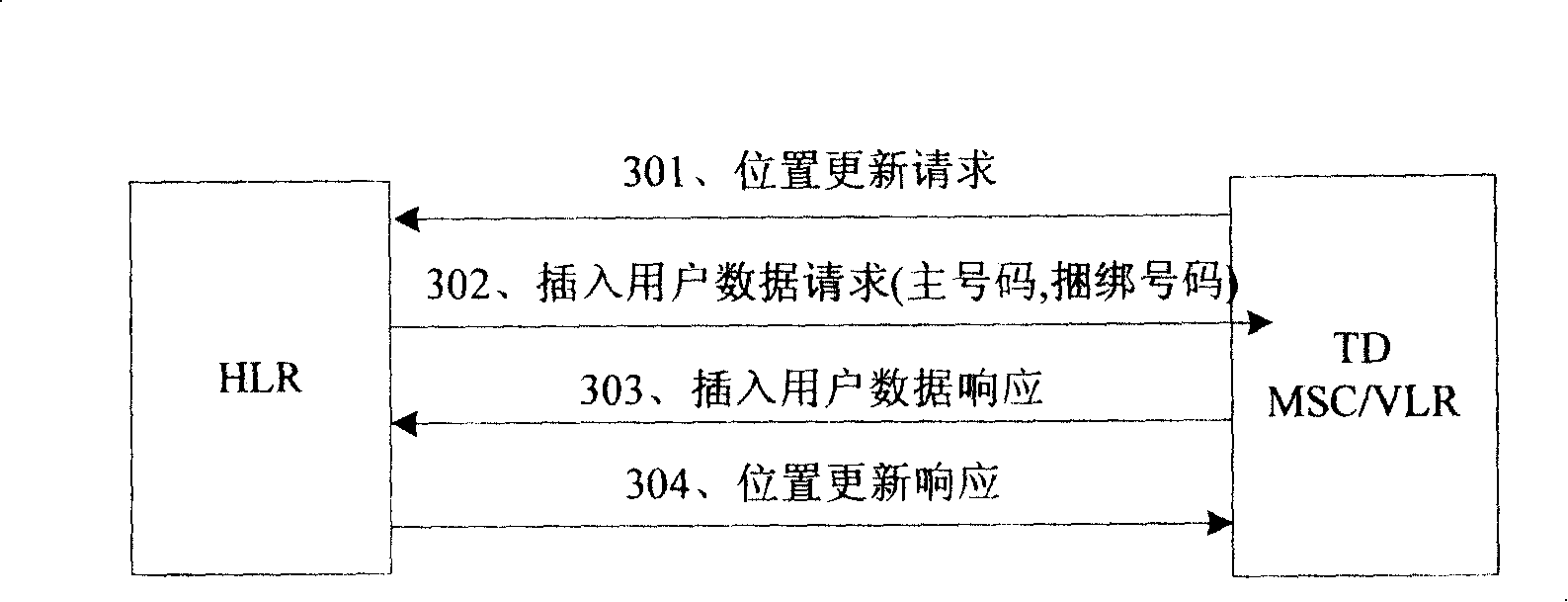
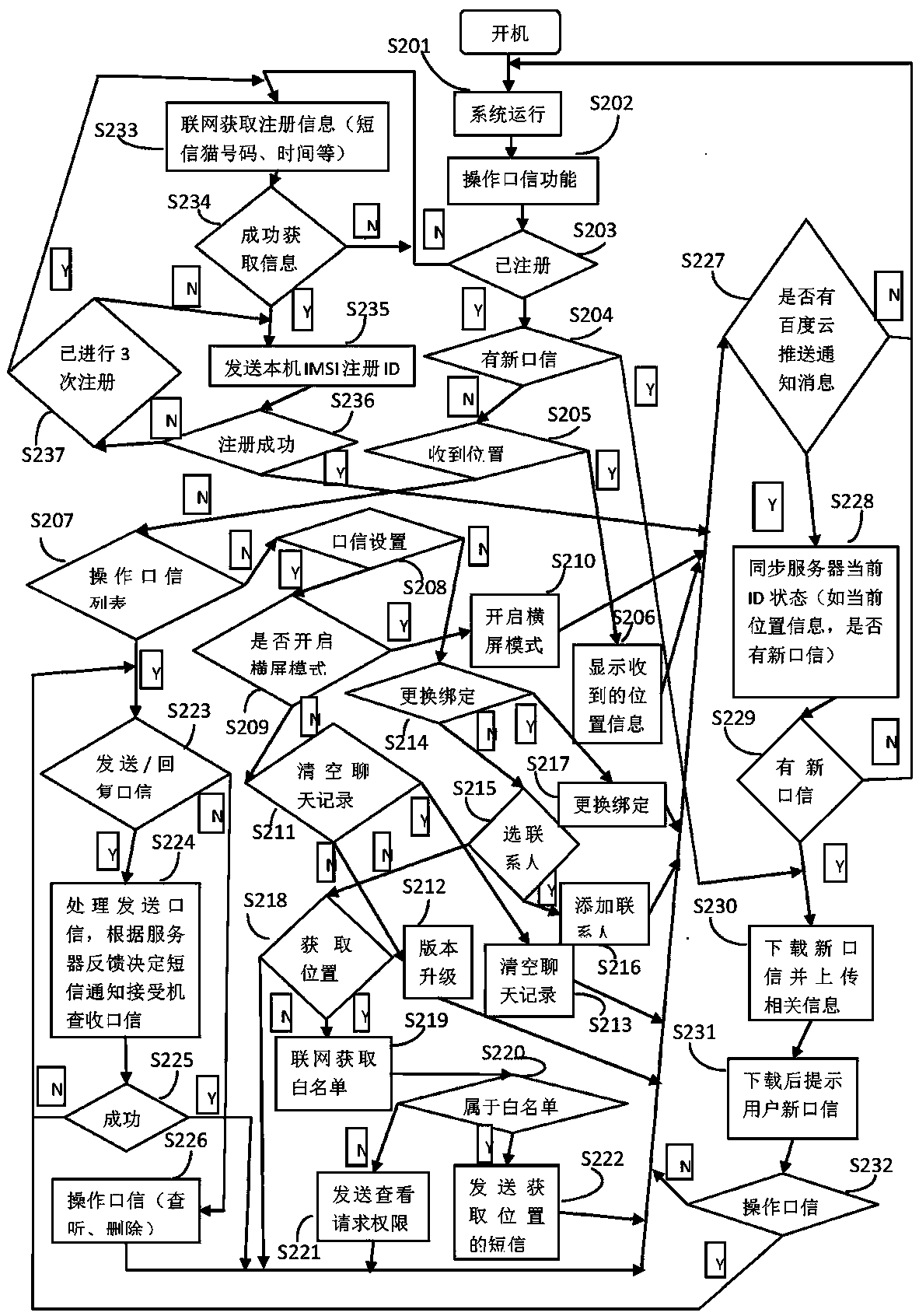
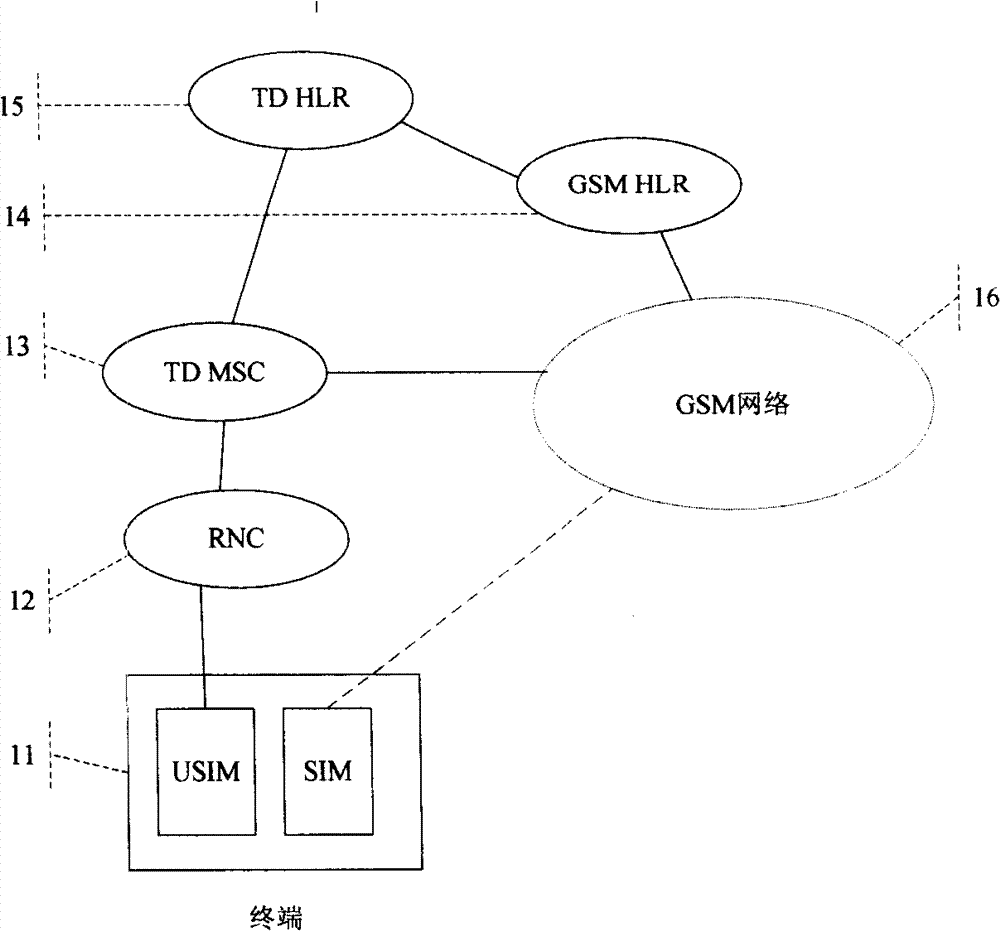
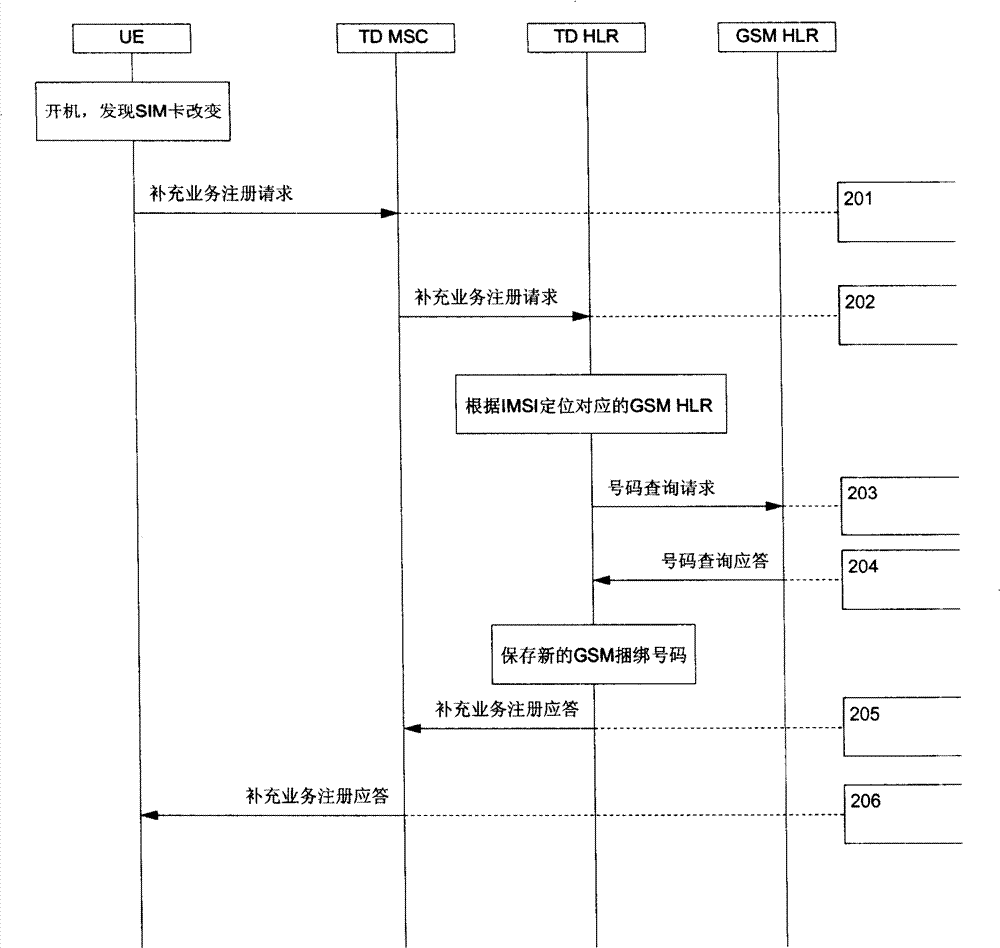
The invention discloses a method for updating a bond telephone number of a dual-mode handset network, comprising: a starting terminal, sending supplementary service registration message comprising IMSI information of a terminal SIM card to TD MSC; transmitting the information to TD HLR by TD MSC; positioning TD HLR to the GSM HLR of the IMSI information according to configured IMSD telephone number and HLR relationship, and sending telephone number query message to GSM HLR comprising the IMSI information; sending telephone query answer to TD HLR comprising the GSM ISDN number associated with the IMSI by GSD MLR; storing the telephone number by TD HLR as the new GSM bond number for the terminal. The invention is capable of updating bond GSM telephone number for terminal by TD-SCDMA network.
Owner:ZTE CORP
A method, device and system for processing mobile phone numbers for secondary sales
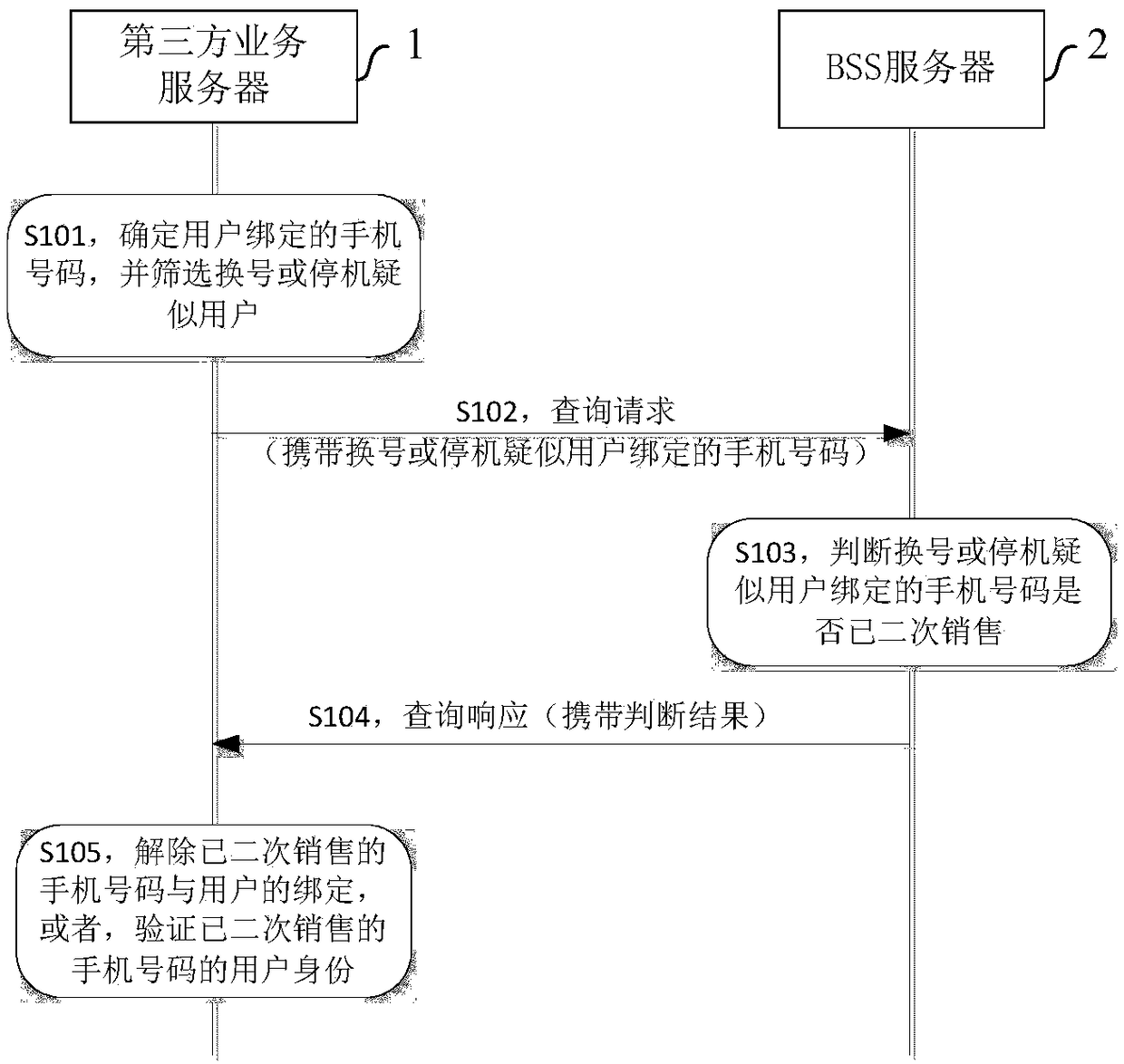
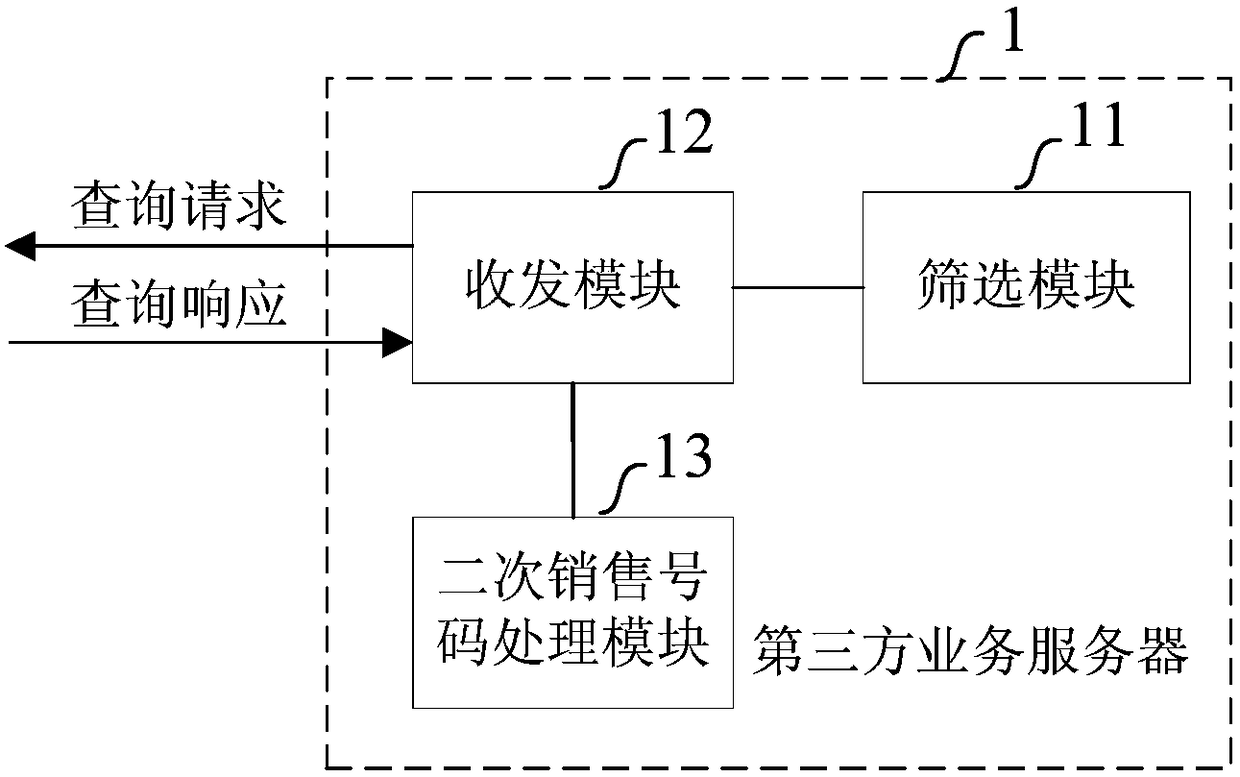
ActiveCN105657683BSave resourcesReduce risk of leakageSpecial service for subscribersSupervisory/monitoring/testing arrangementsThird partyMobile Telephone Number
The invention provides a processing method, a processing device and a processing system for secondary mobile phone number selling. The processing method, the processing device and the processing system for secondary mobile phone number selling have the advantages that a user with large mobile phone number change or ceasing probability is selected through analysis and screening of users' big data information of a third-party service platform (E-commerce website and / or mobile internet application), a bound number of the user on a third-party service server is transmitted to a telecommunication operator to enable a BSS (business support system) server of the telecommunication operator to judge whether the bound number is subjected to secondary selling or not, and the third-party service server unbinds the mobile phone number of the user or re-authenticate the identity of the user according to a judgment result of the bound number; since the third-party service server is used for identifying and screening of suspected secondarily sold mobile phone numbers, so that the BSS query range is narrowed, in other words, user information quantity transmitted between the third-party service server and a BSS is decreased, network resources are saved and user information leakage risks can be reduced.
Owner:CHINA UNITED NETWORK COMM GRP CO LTD
Paper processing device
The invention provides a paper page processing device which takes out remaining pages not up for a binding number very conveniently. The paper page processing device comprises a housing. A paper page inputting part is arranged in the housing for paper pages to be put in. A storing part is arranged in the housing for keeping the inputted paper pages until the number of the paper pages reaches the number for binding. A separation part is arranged to separate remaining paper pages. A transportation track is externally arranged on the housing to transport already separated paper pages. The separation part separates remaining paper pages left in the storing part when a business deal is normally completed or the paper pages are transported wrongly.
Owner:OKI ELECTRIC IND CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com