Patents
Literature
49 results about "Fraudulent Data" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
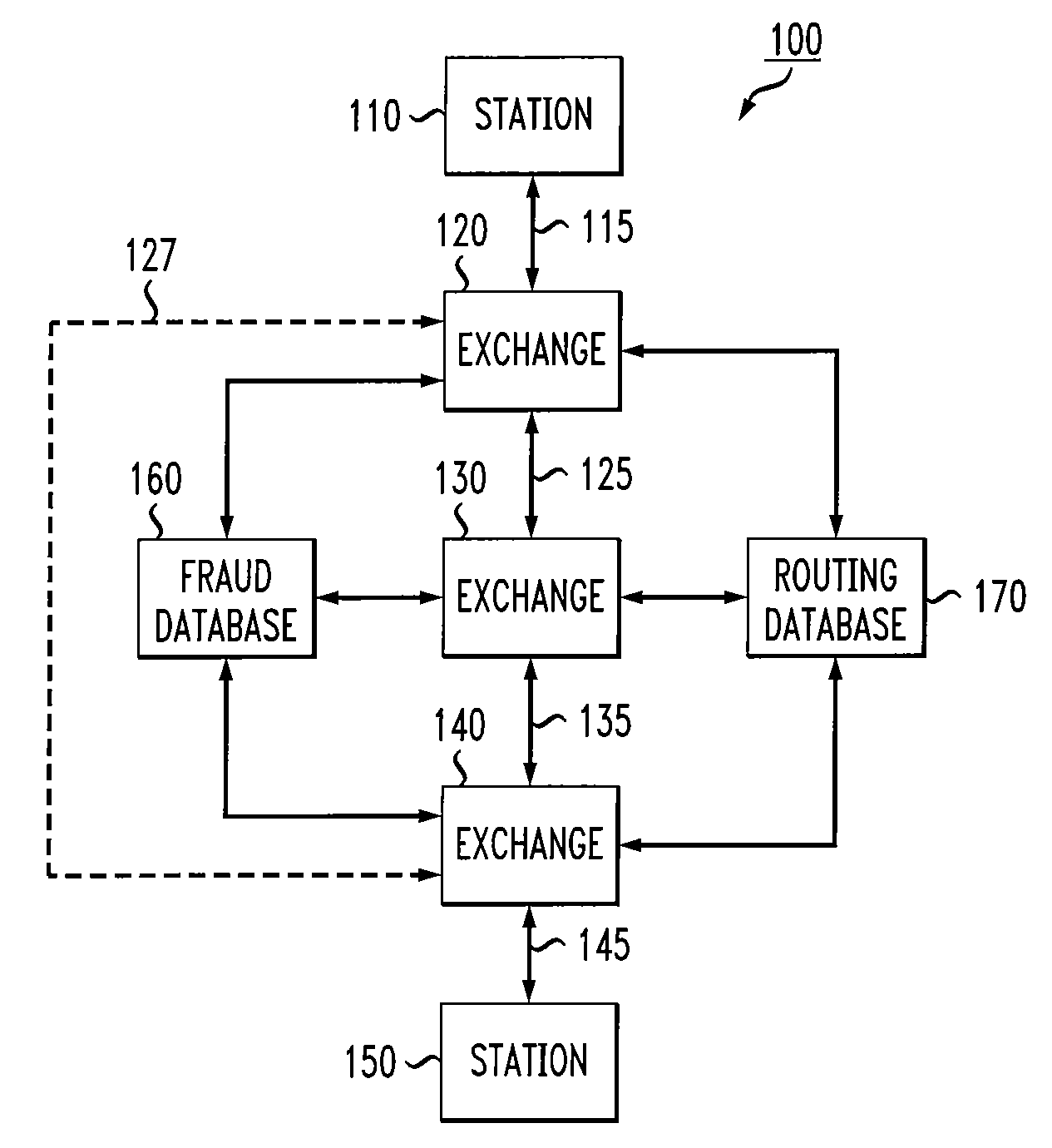
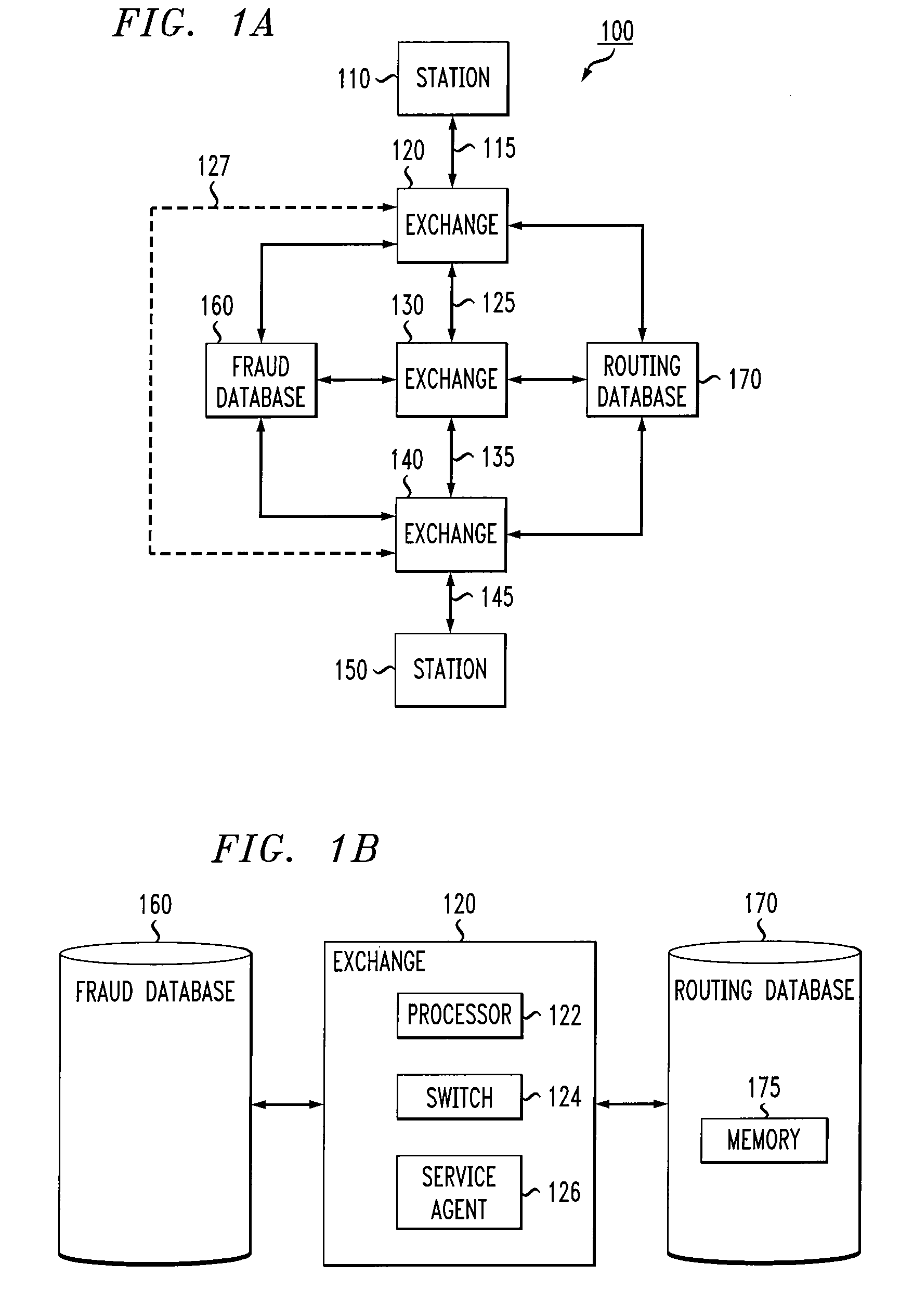
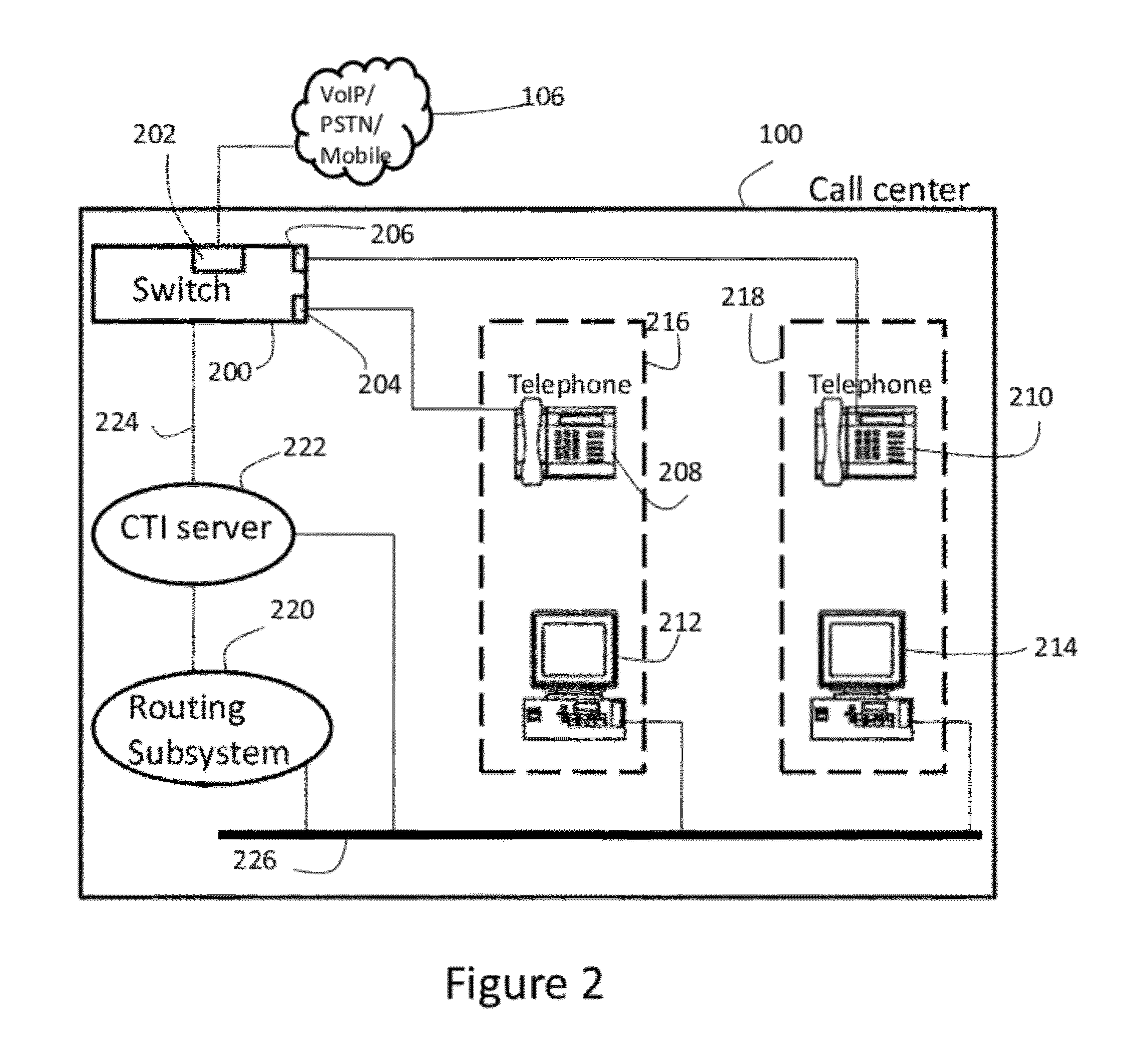
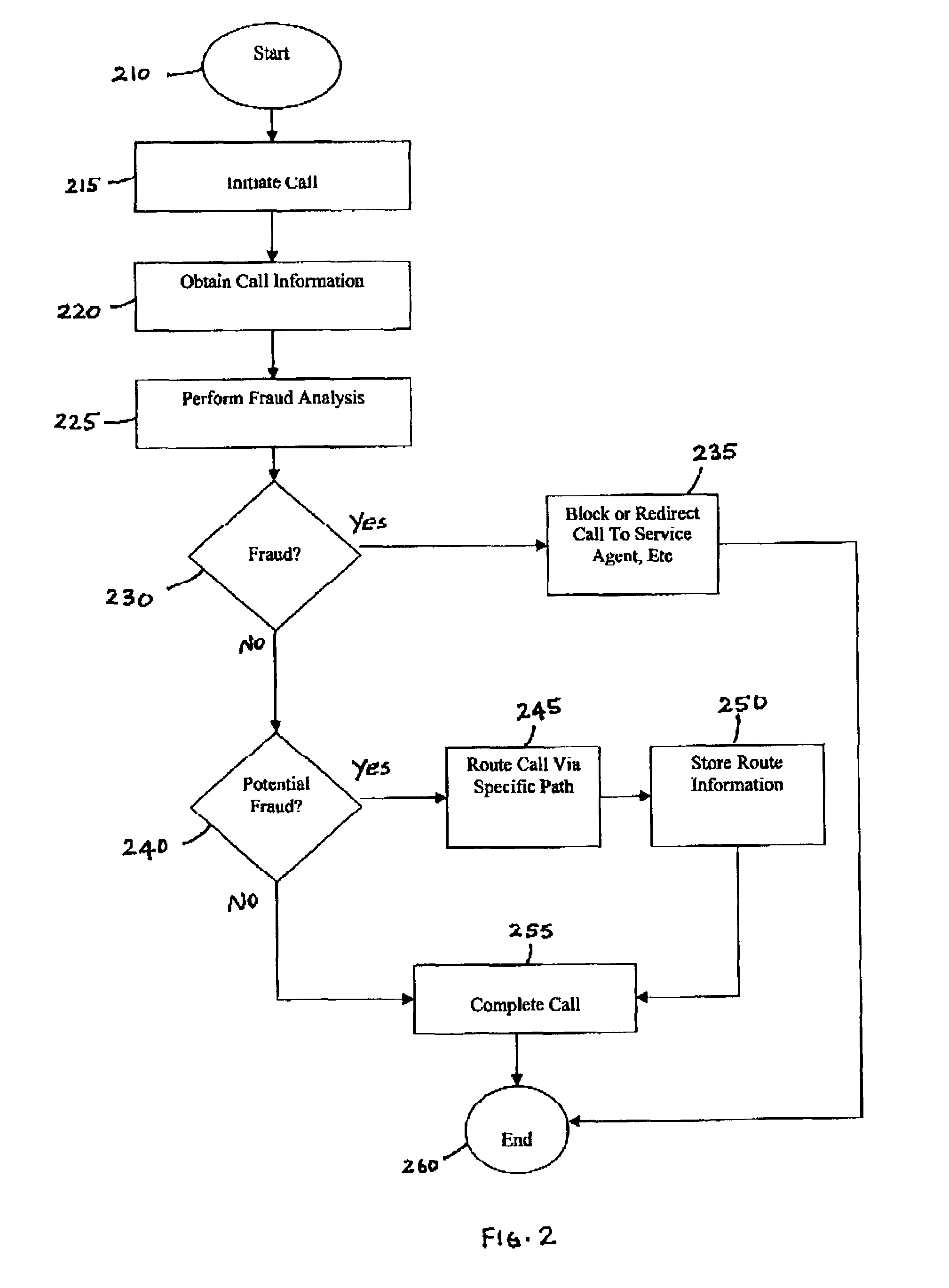
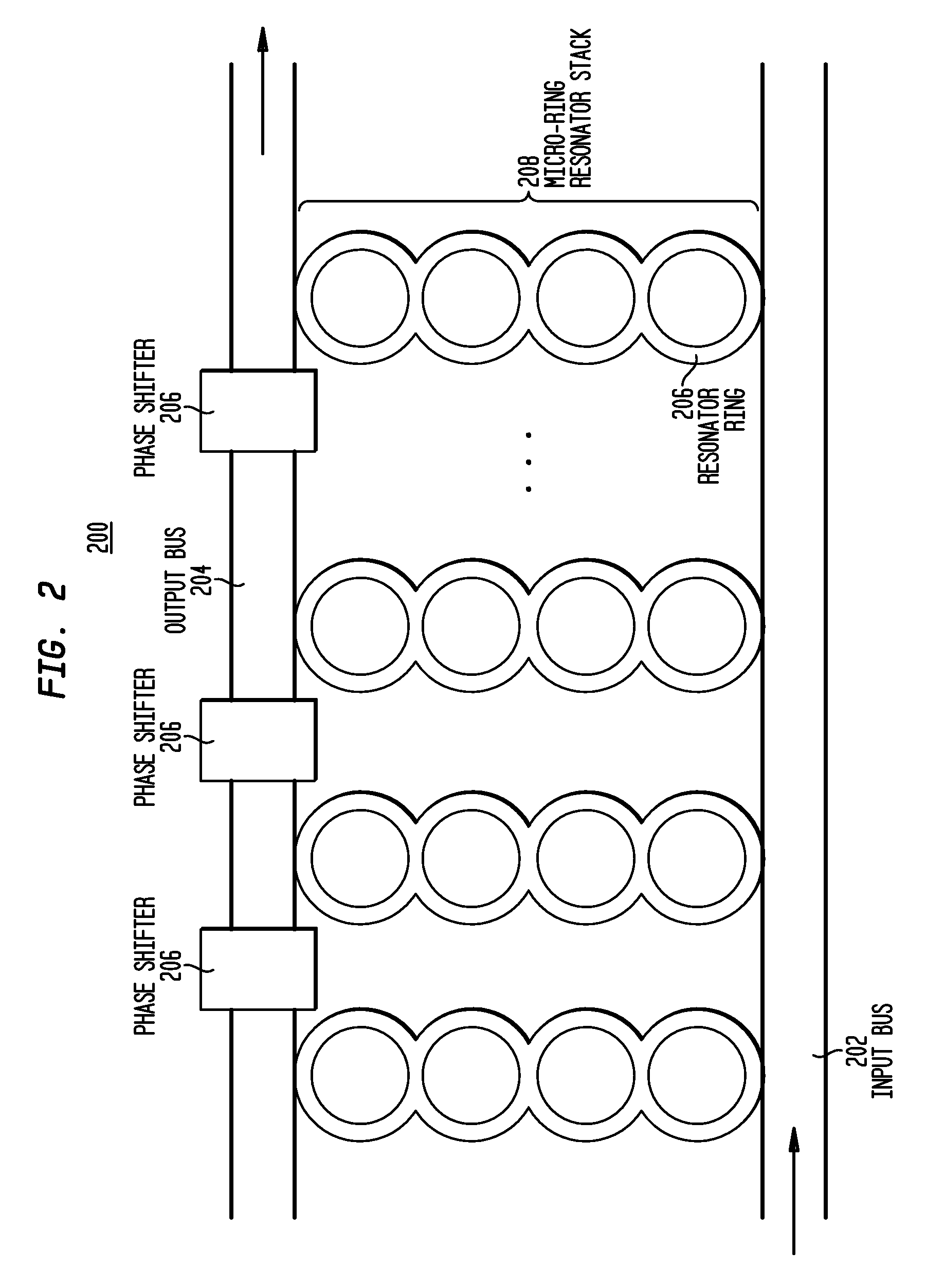
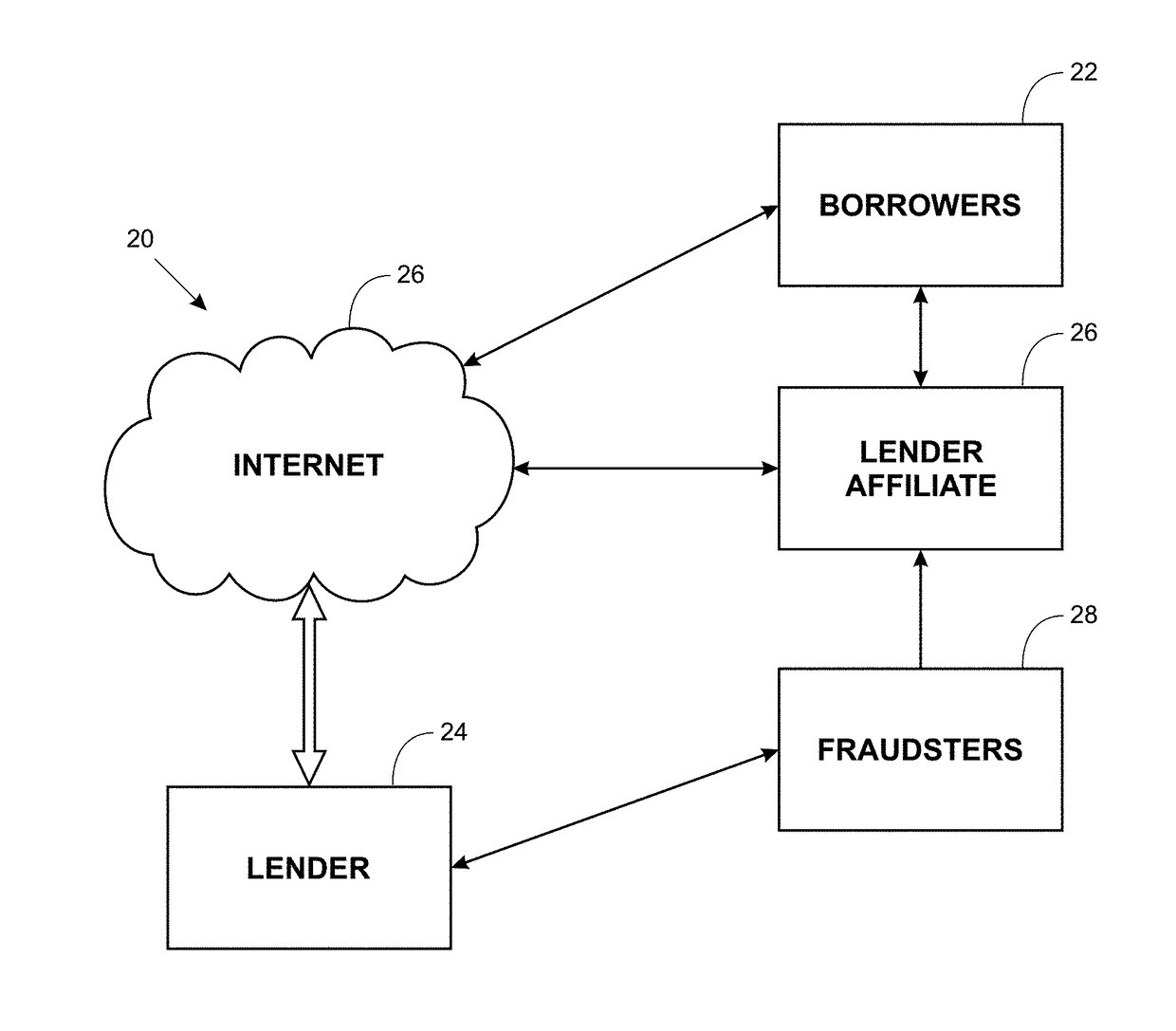
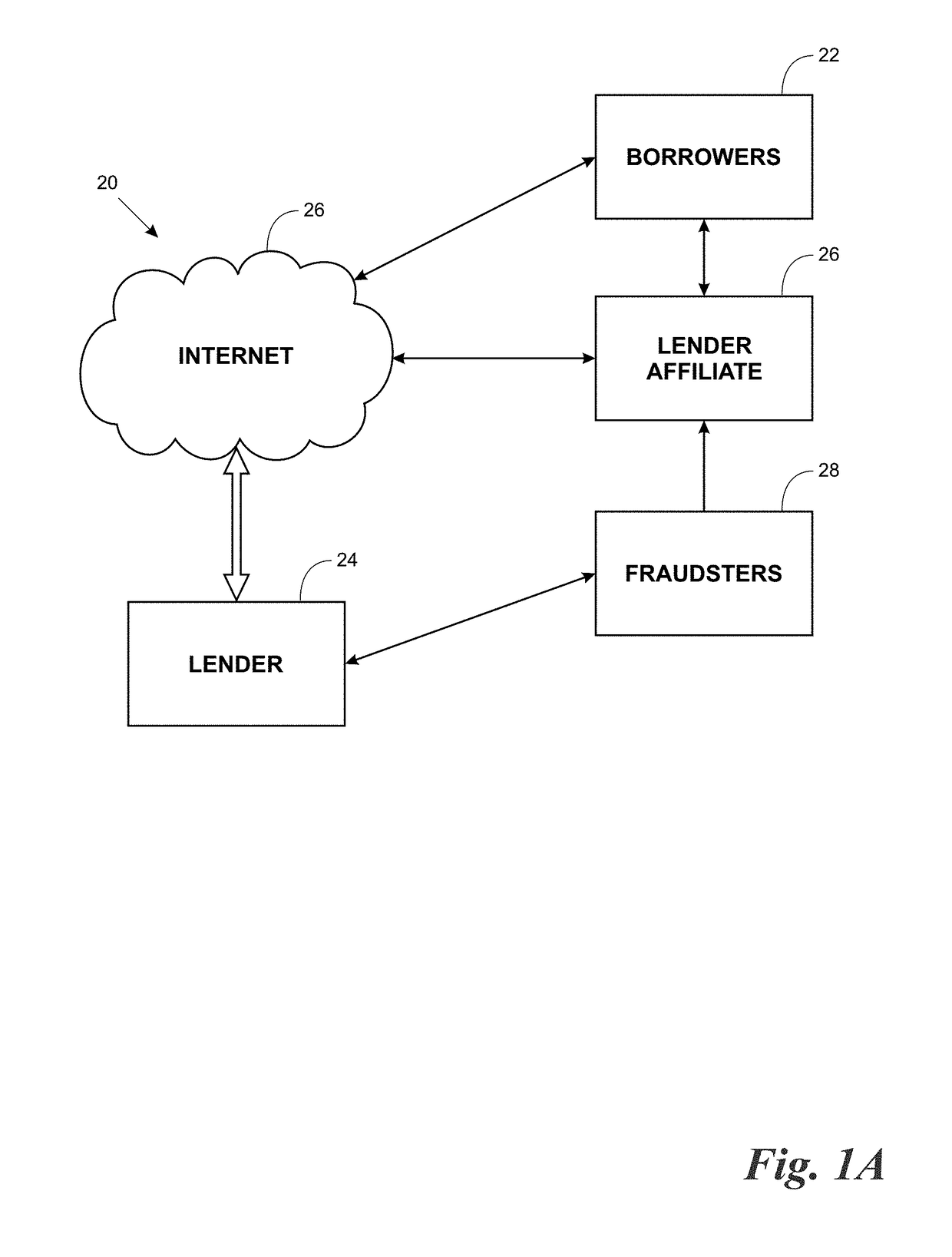
Call routing method
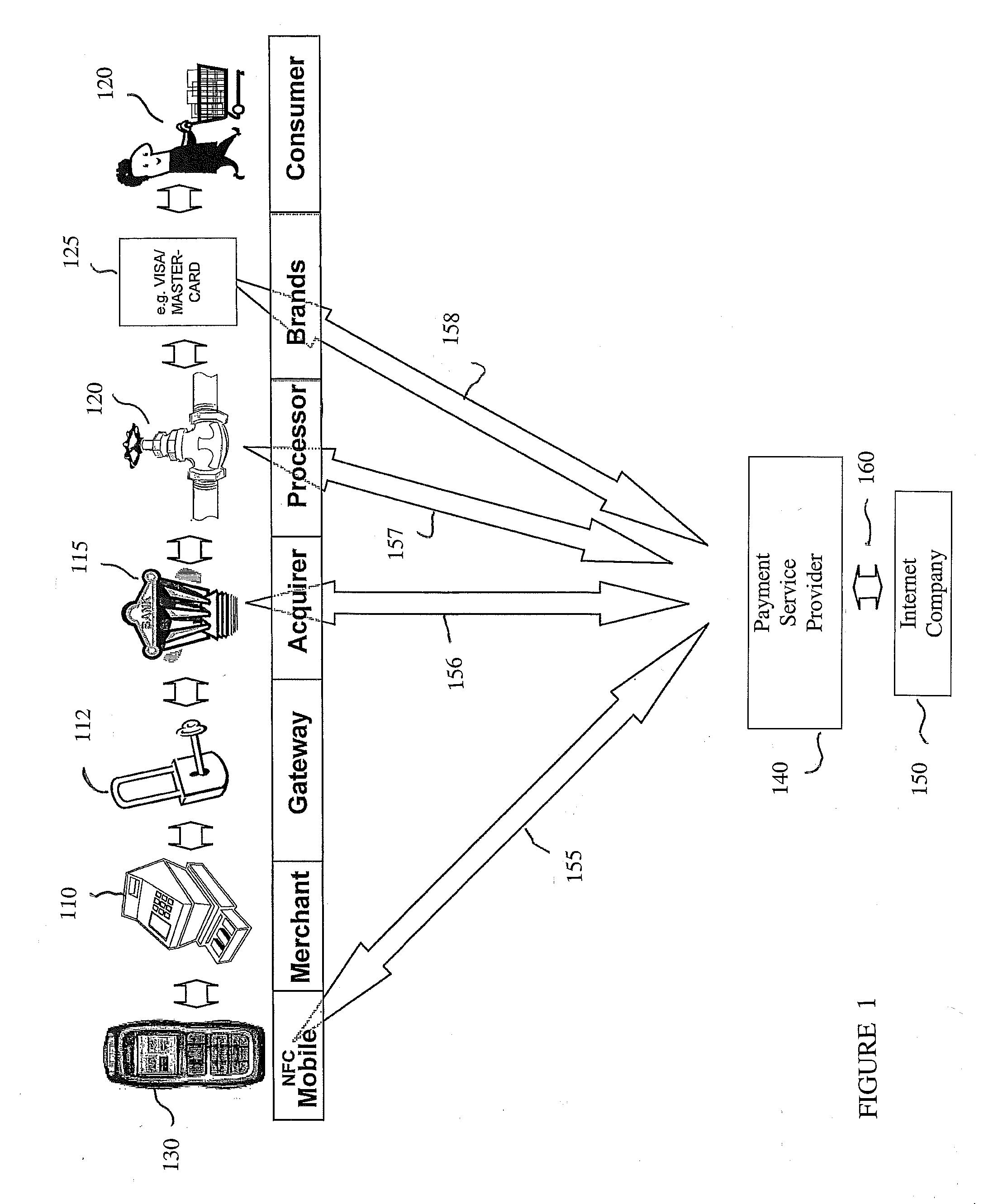
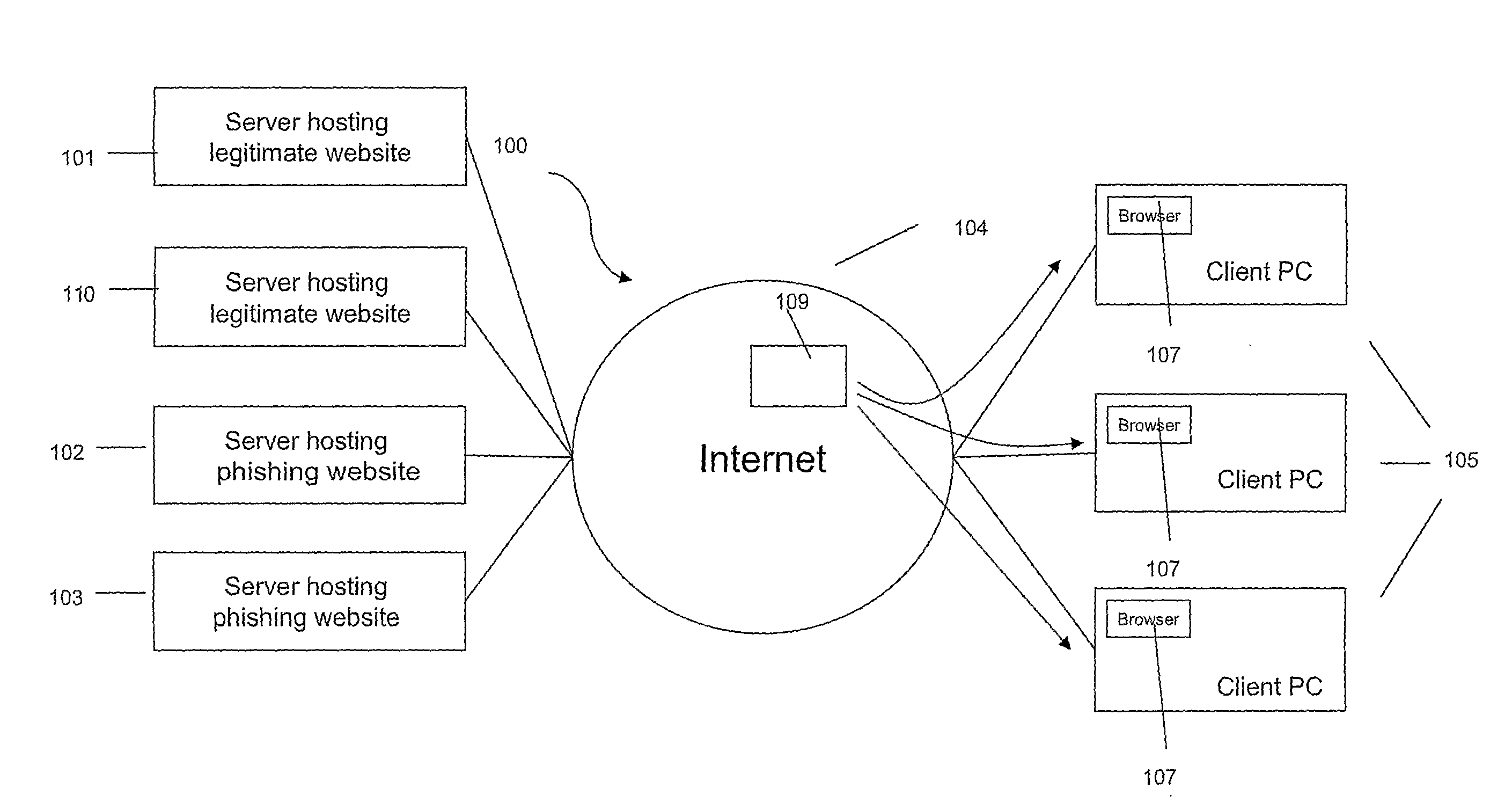
ActiveUS20080101571A1Interconnection arrangementsUnauthorised/fraudulent call preventionCall routingData bank
Owner:AT&T INTPROP II L P
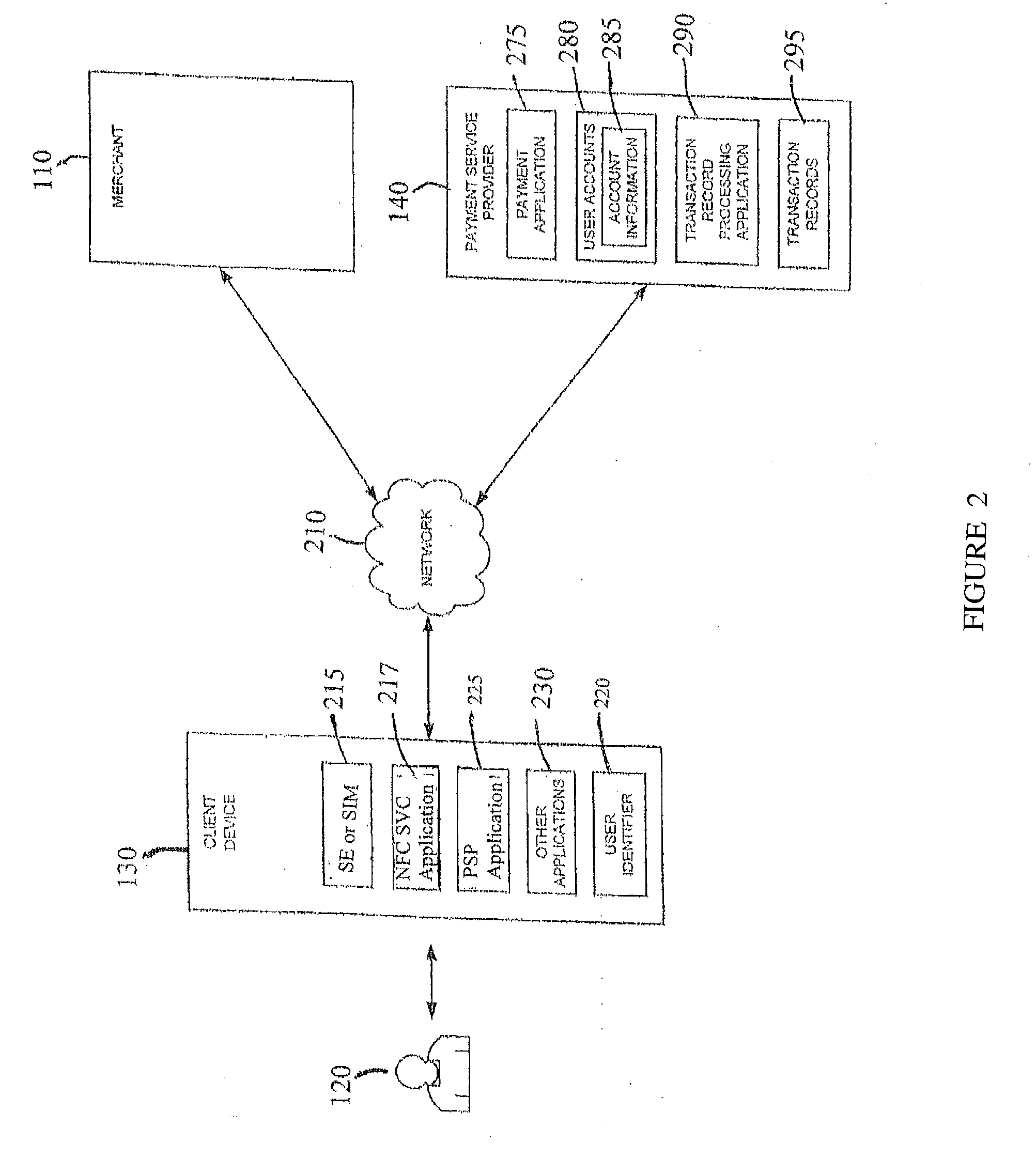
Mobile User Identify And Risk/Fraud Model Service
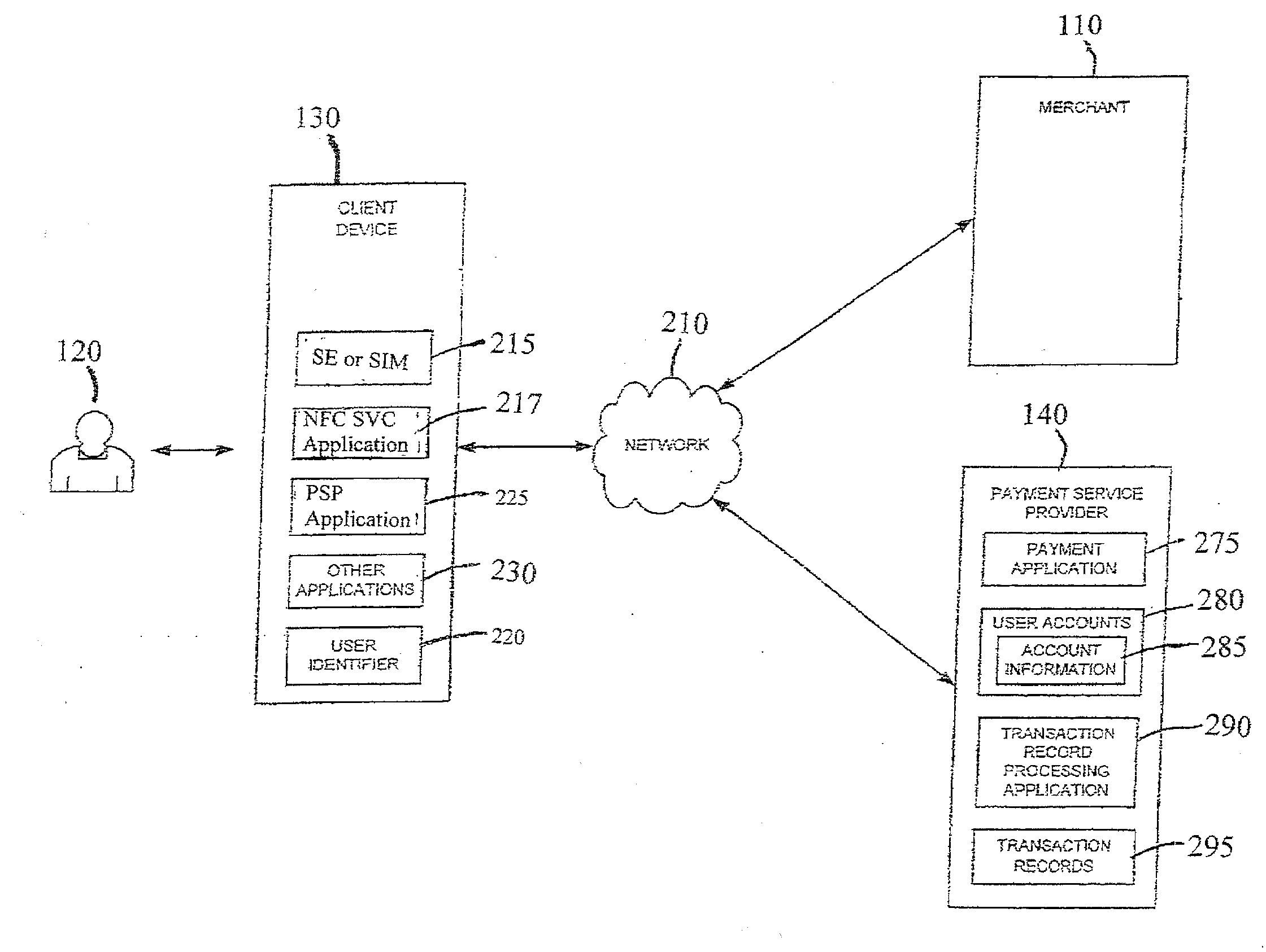
InactiveUS20090307778A1Risk dataGeneration of riskDigital data processing detailsAnalogue secracy/subscription systemsIdentity theftBluetooth
Transactions using, for example, Near Field Communication (NFC), Bluetooth, online, or other applications, may pose a risk of fraud or identity theft. According to an embodiment, a method of evaluating transaction information in view of potential fraud and / or risk includes receiving transaction information at a remote location. The method also includes correlating the received transaction information with user data maintained at the remote location. The method further includes generating a score and / or risk or fraud data based on the correlating. Such transactions may be facilitated by a payment service provider. Related methods, devices, and systems are also disclosed.
Owner:PAYPAL INC
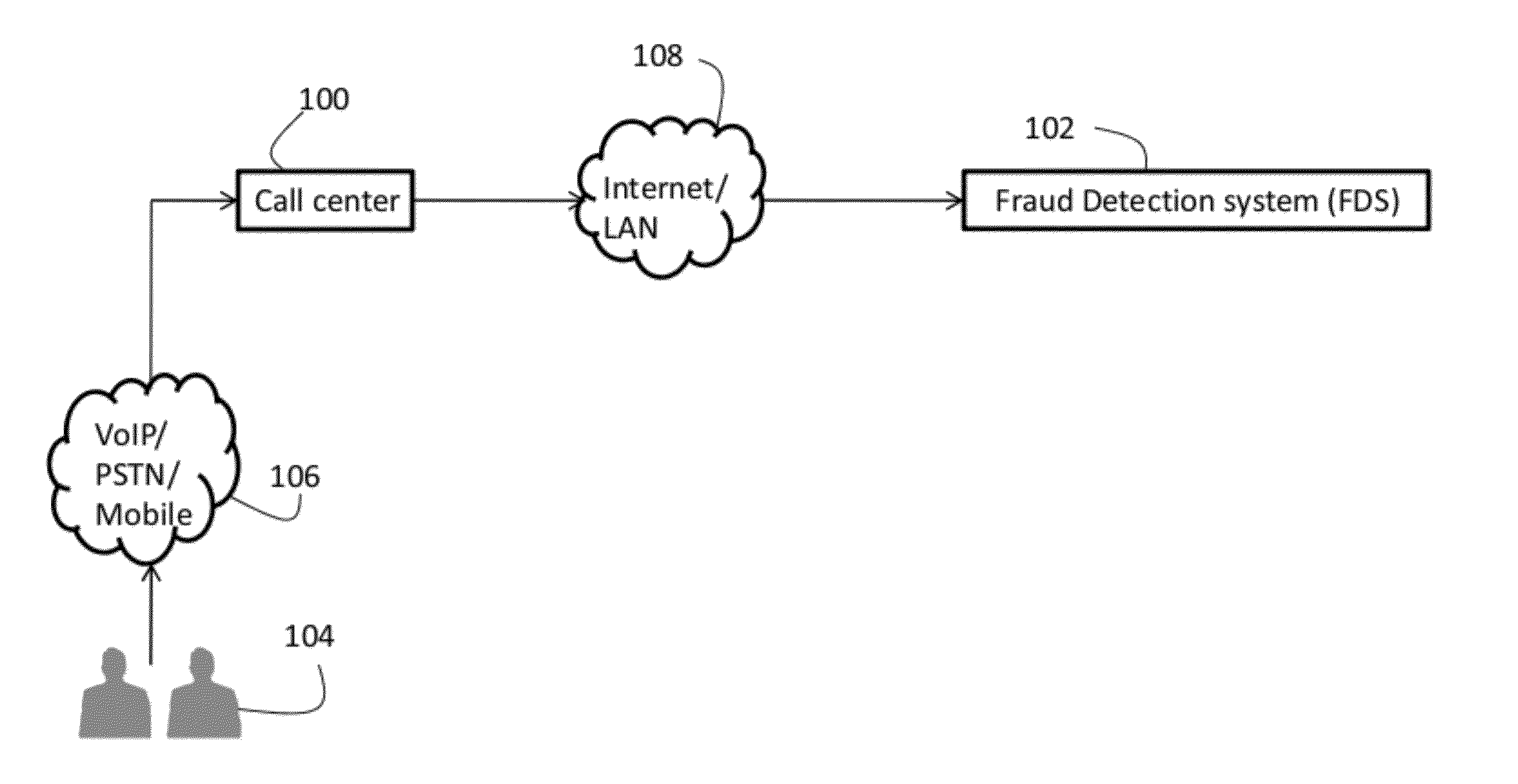
Systems, methods, and media for determining fraud patterns and creating fraud behavioral models
ActiveUS20120072453A1Digital data processing detailsUser identity/authority verificationData scienceFraudulent Data
Systems, methods, and media for analyzing fraud patterns and creating fraud behavioral models are provided herein. In some embodiments, methods for analyzing call data associated with fraudsters may include executing instructions stored in memory to compare the call data to a corpus of fraud data to determine one or more unique fraudsters associated with the call data, associate the call data with one or more unique fraudsters based upon the comparison, generate one or more voiceprints for each of the one or more identified unique fraudsters from the call data, and store the one or more voiceprints in a database.
Owner:VERINT AMERICAS
Method for detecting fraudulent frame sent over an in-vehicle network system
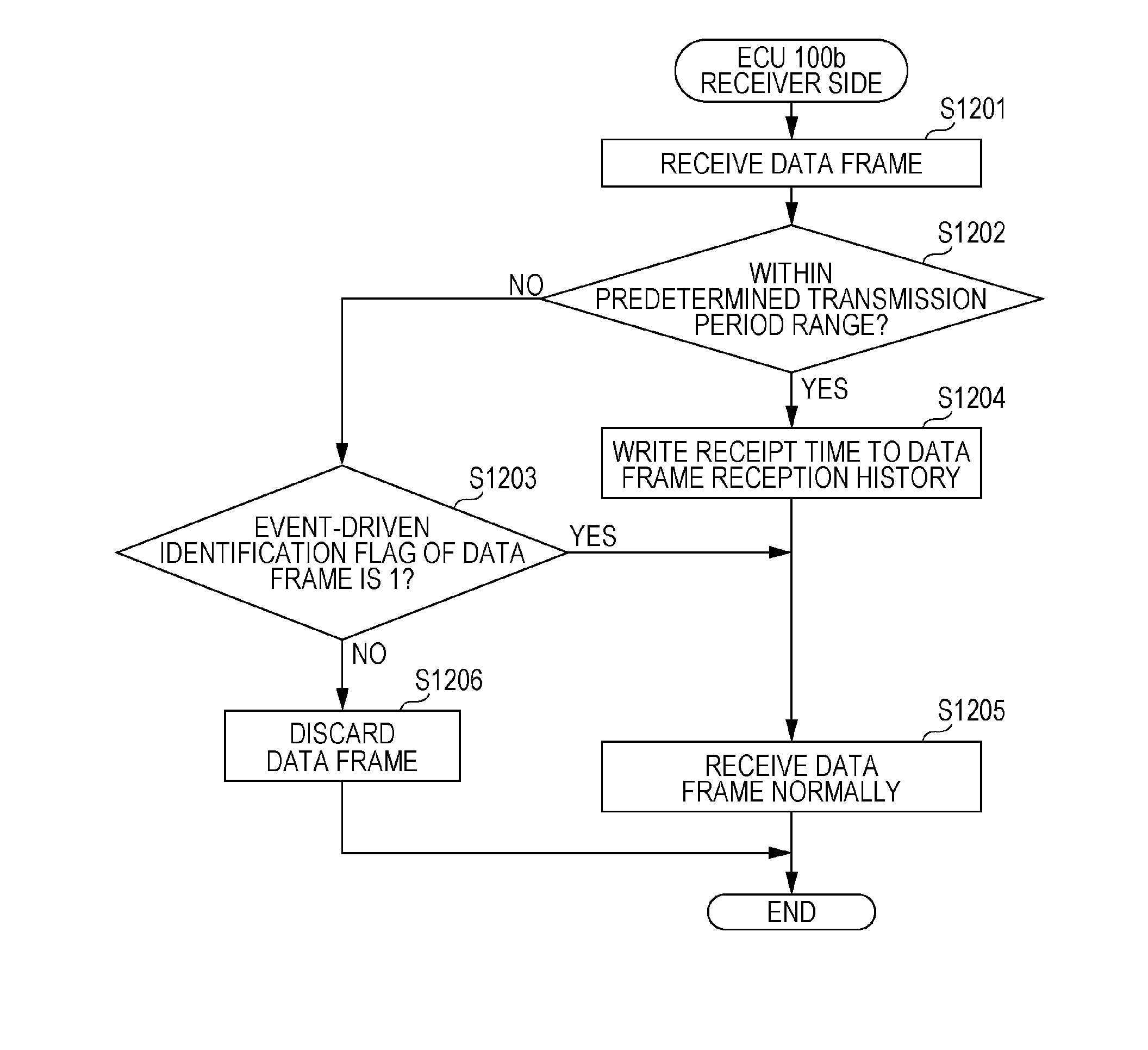
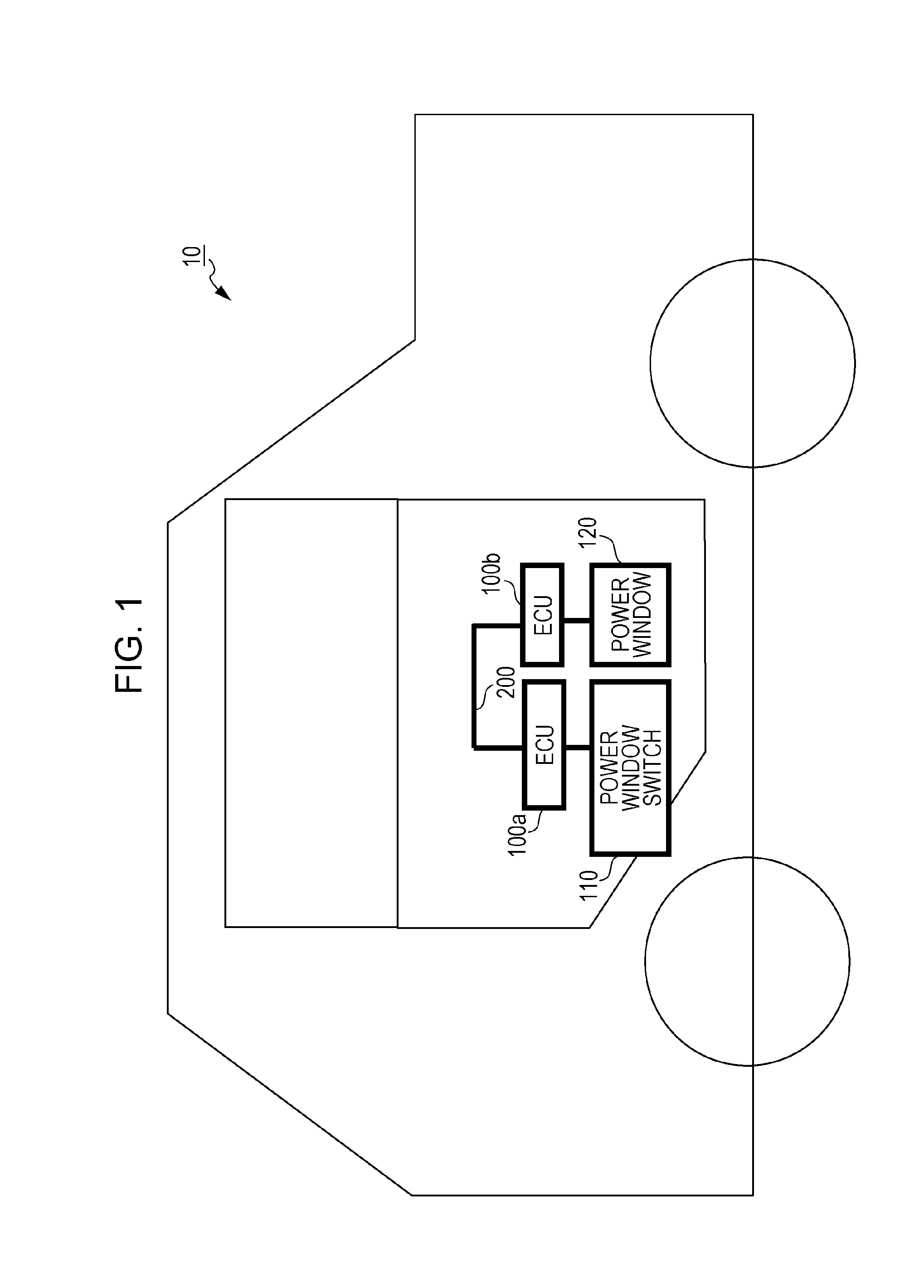
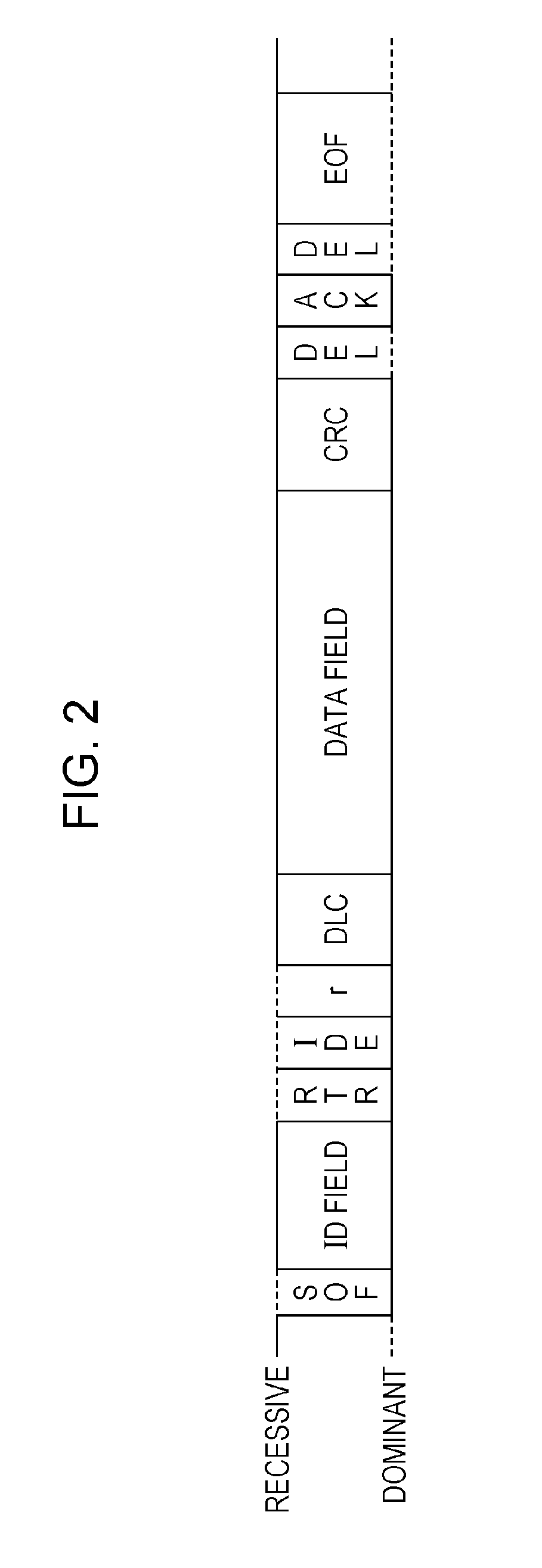
ActiveUS20160205194A1Easy loadingHigh processing loadElectric/fluid circuitSpecial data processing applicationsArea networkIn vehicle
A fraud detection method for use in an in-vehicle network system including a plurality of electronic control units that communicate with one another via a bus in accordance with Controller Area Network (CAN) protocol is provided. The method includes receiving at least one data frame sent to the bus, verifying a specific identifier in the received data frame only if the received data frame does not follow a predetermined rule regarding a transmission period and a state of a vehicle having the in-vehicle network system mounted therein is a predetermined state, detecting the received data frame as an authenticated data frame if the verification is successful, and detecting the received data frame as a fraudulent data frame if the verification fails.
Owner:PANASONIC INTELLECTUAL PROPERTY CORP OF AMERICA
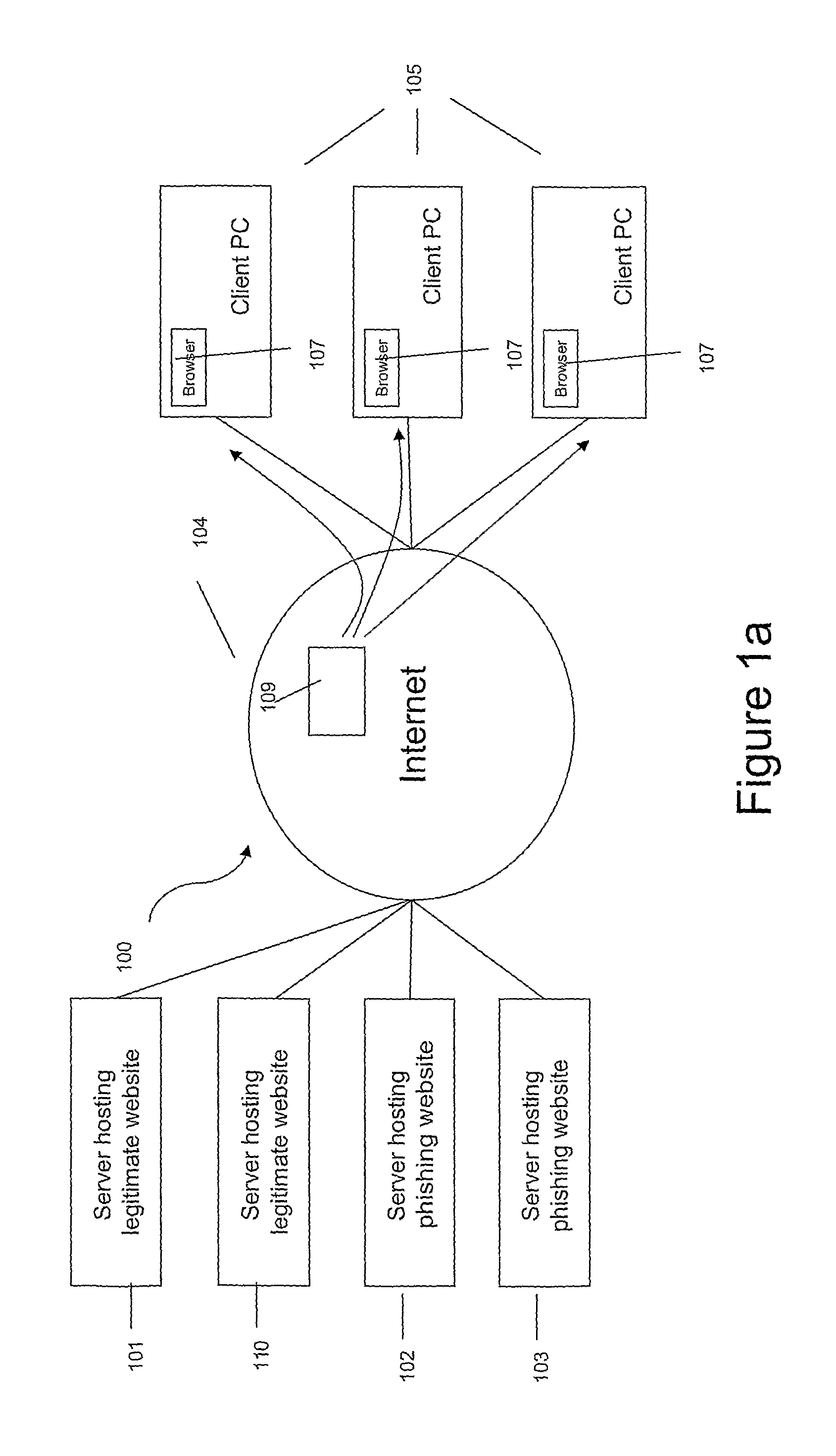
Fraudulent Page Detection
ActiveUS20120023566A1Assist in detectingDigital data processing detailsUser identity/authority verificationWeb pageComputer science
Owner:SENTRYBAY
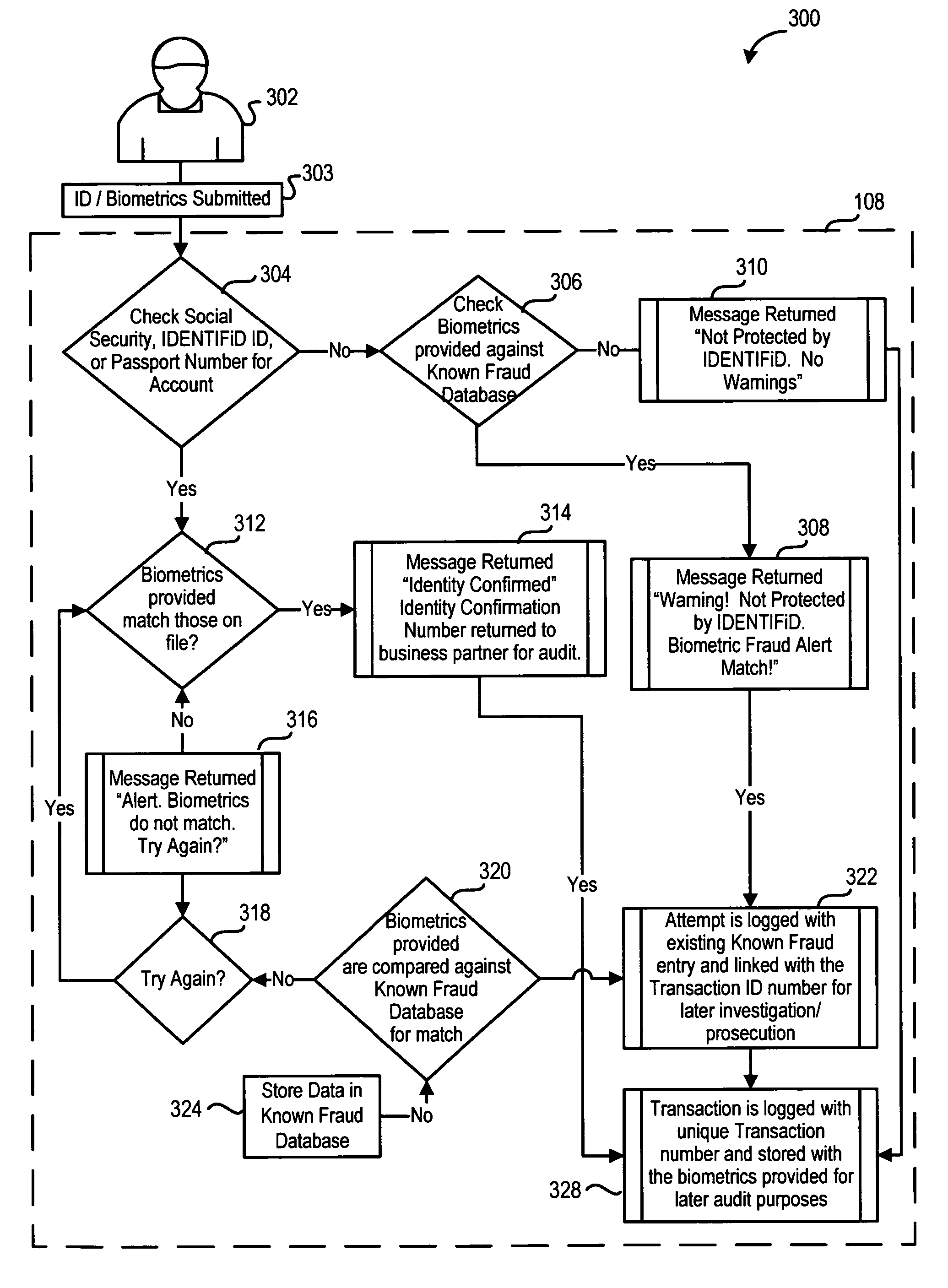
Identity verification system
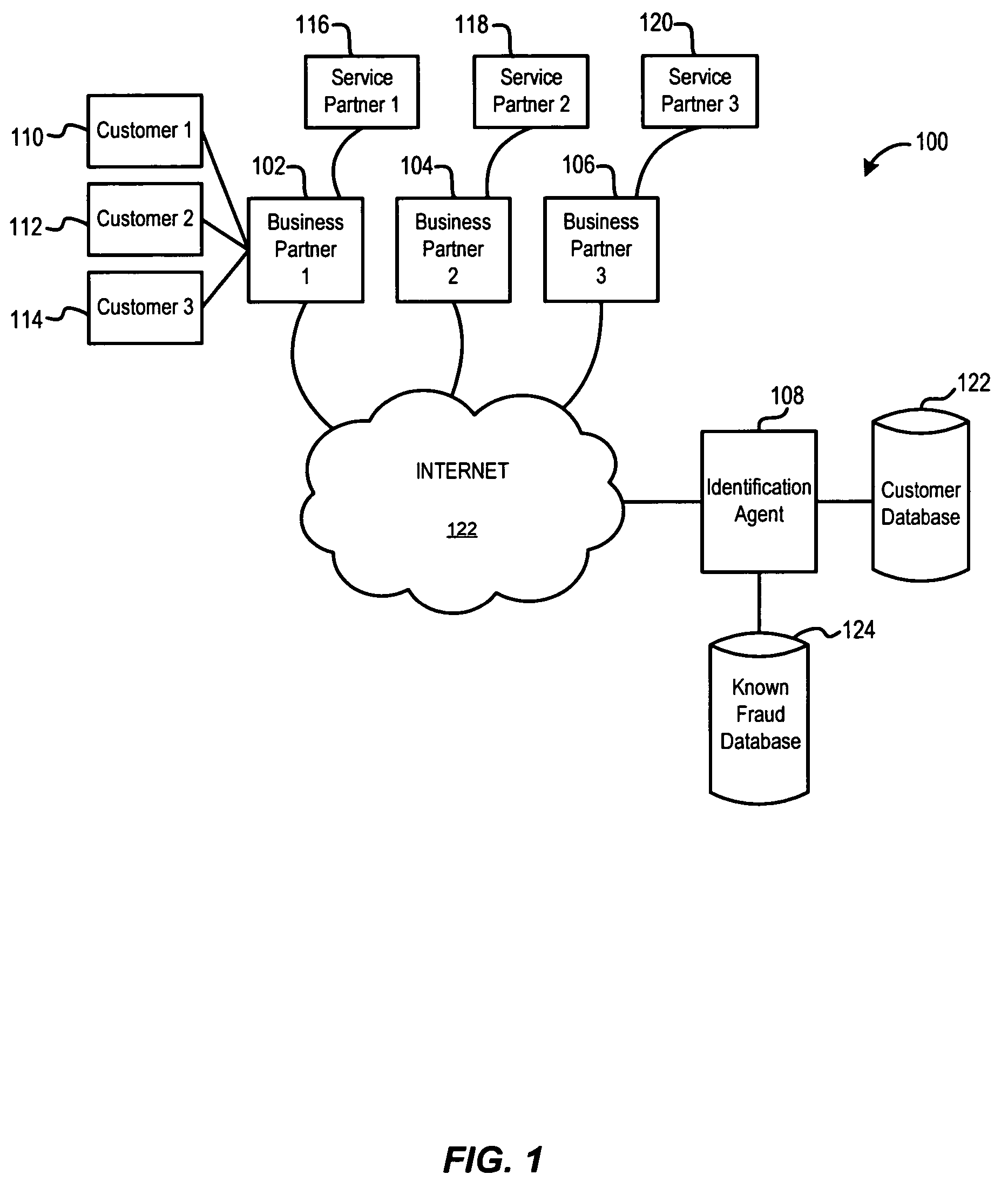
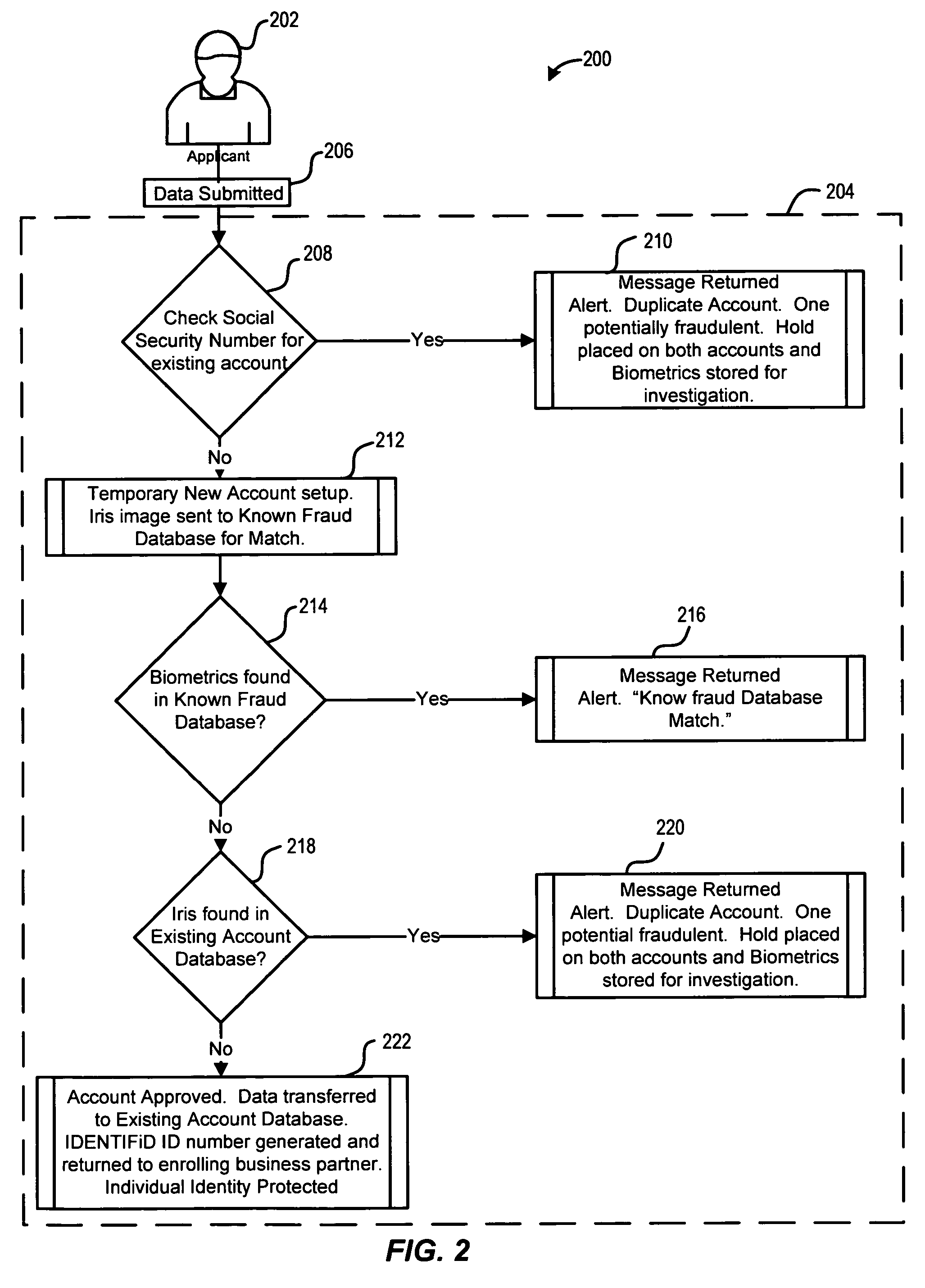
ActiveUS7779457B2Easy access to dataElectric signal transmission systemsDigital data processing detailsElectronic systemsBiometric data
An electronic system is provided to confirm the identity of an individual or customer. The confirmation process permits businesses and other entities to access a preapproved list of authorize customers for purposes of preventing identity theft or fraud. Biometric data obtained from the person of the customer is compared against an authorized version of customer biometric data for this purpose. Even if an individual customer is not an authorized customer, the biometric data may be compared to a known fraud database to see if this individual has perpetrated past instances of fraud.
Owner:IDENTIFID LLC
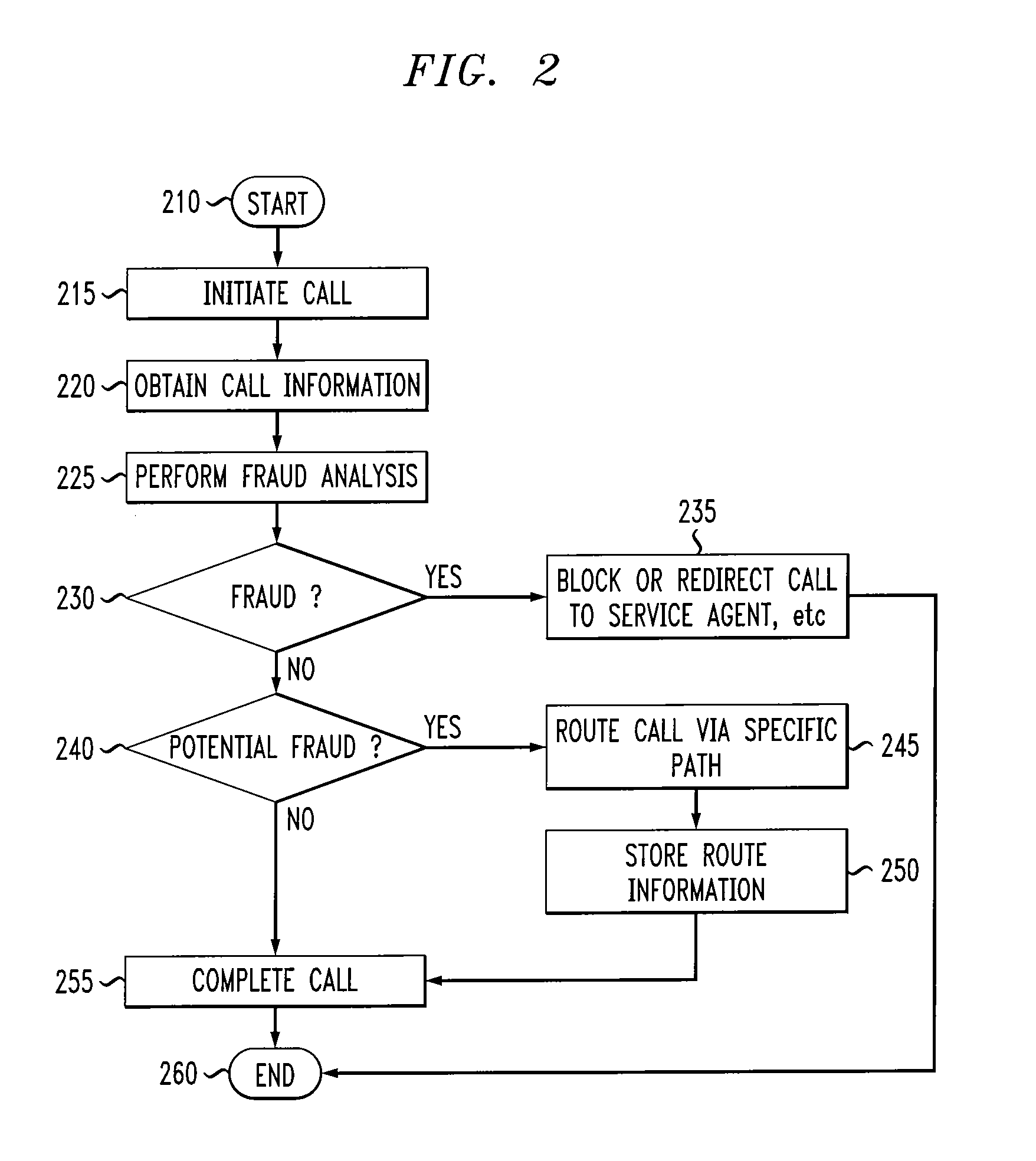
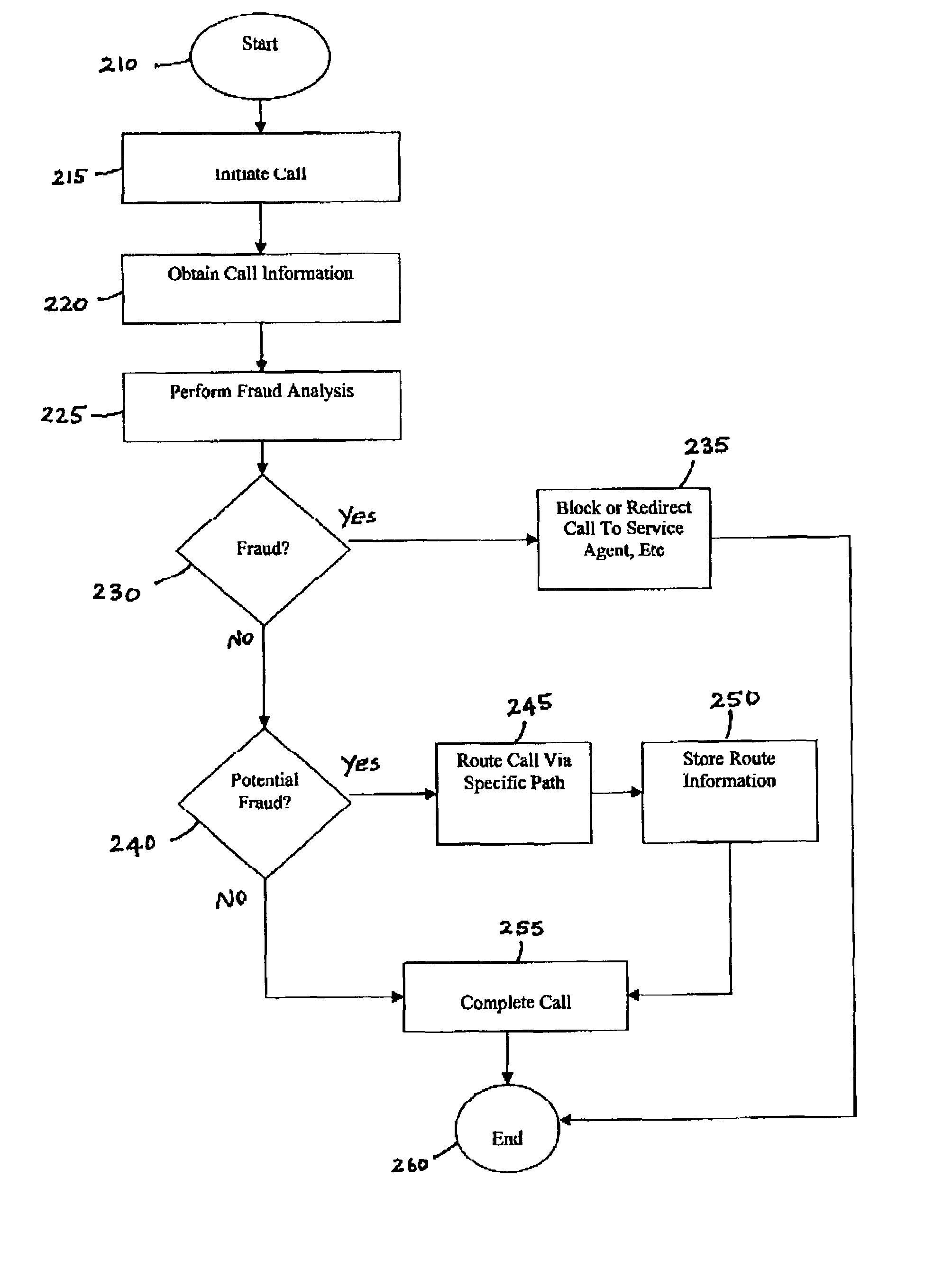
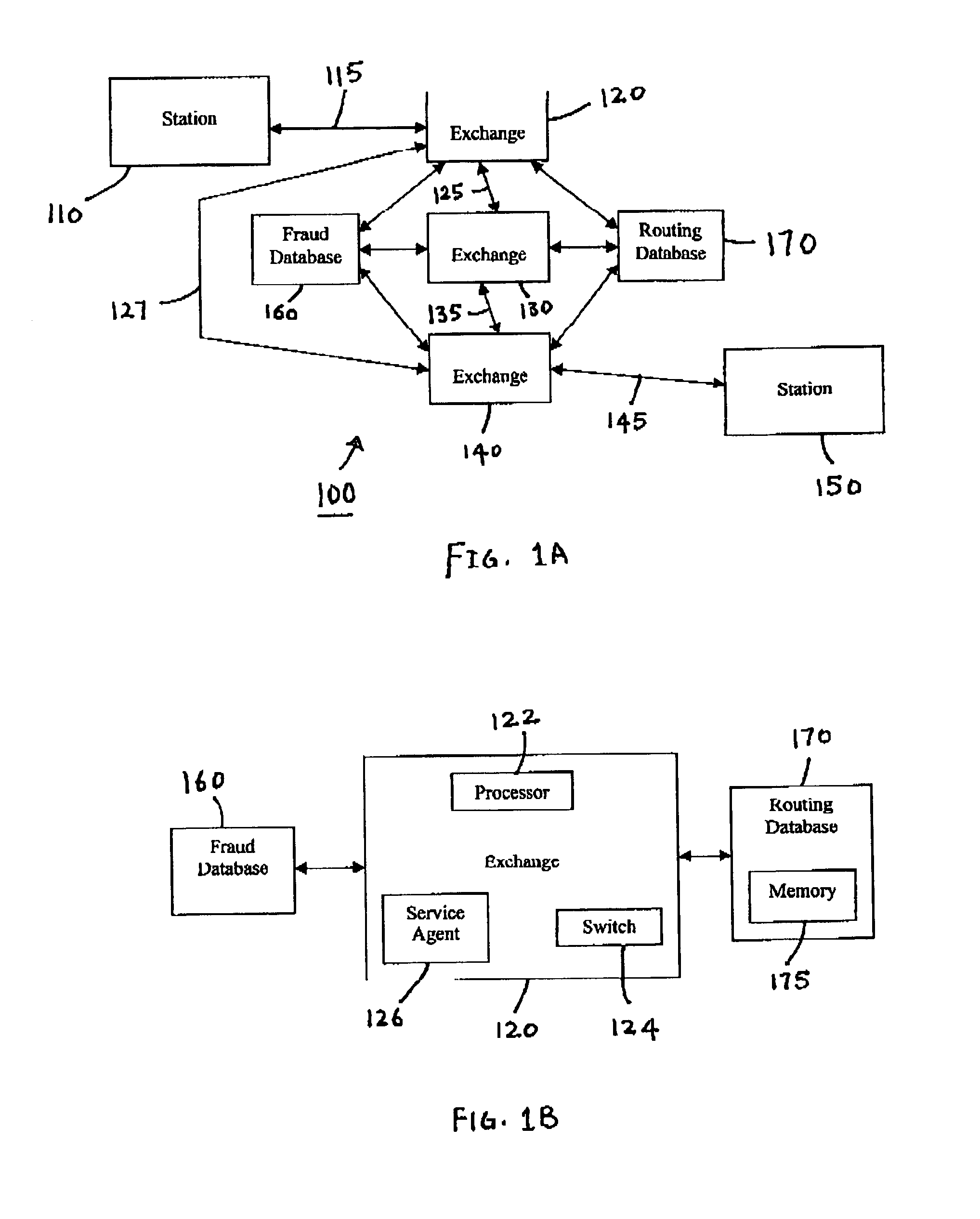
Call routing method
InactiveUS7327837B1Completion of call is preventedBlock completeInterconnection arrangementsAutomatic exchangesCall routingData bank
A call processing method is disclosed. A first station initiates a call to a second station. Call information associated with the initiated call is evaluated by comparing the call information with information in a fraud database. Completion of the call is prevented if the evaluation results in a finding of fraud. If the evaluation results in no finding of fraud, the call is completed to the second station via a routing path obtained from a routing database. If the call being completed is deemed to be a call of interest, the routing path obtained from the routing database for completing the call is stored.
Owner:AMERICAN TELEPHONE & TELEGRAPH CO
Systems, methods, and media for determining fraud patterns and creating fraud behavioral models
ActiveUS9203962B2Data processing applicationsSpecial service for subscribersModel systemData science
Systems, methods, and media for analyzing fraud patterns and creating fraud behavioral models are provided herein. In some embodiments, methods for analyzing call data associated with fraudsters may include executing instructions stored in memory to compare the call data to a corpus of fraud data to determine one or more unique fraudsters associated with the call data, associate the call data with one or more unique fraudsters based upon the comparison, generate one or more voiceprints for each of the one or more identified unique fraudsters from the call data, and store the one or more voiceprints in a database.
Owner:VERINT AMERICAS
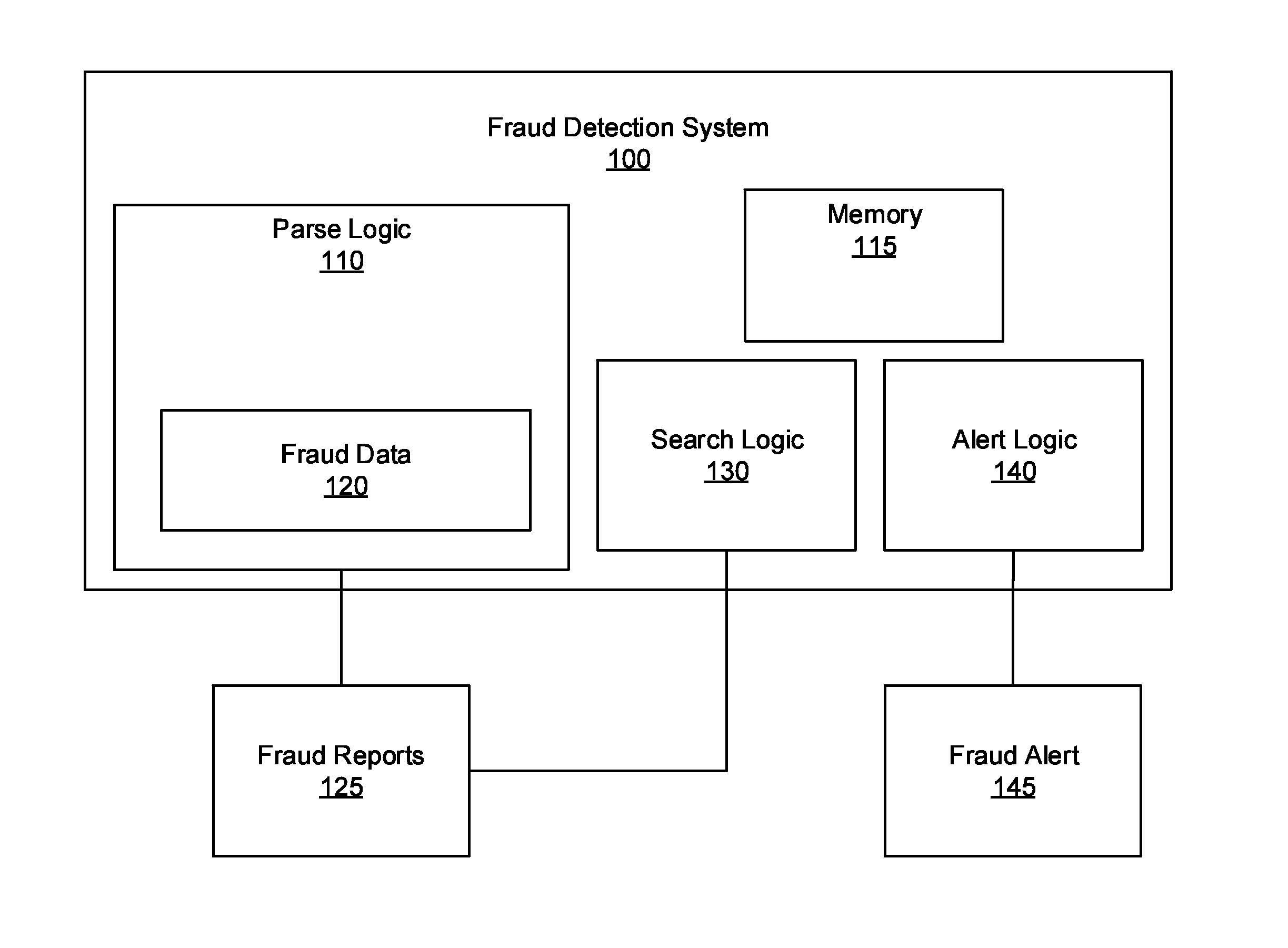
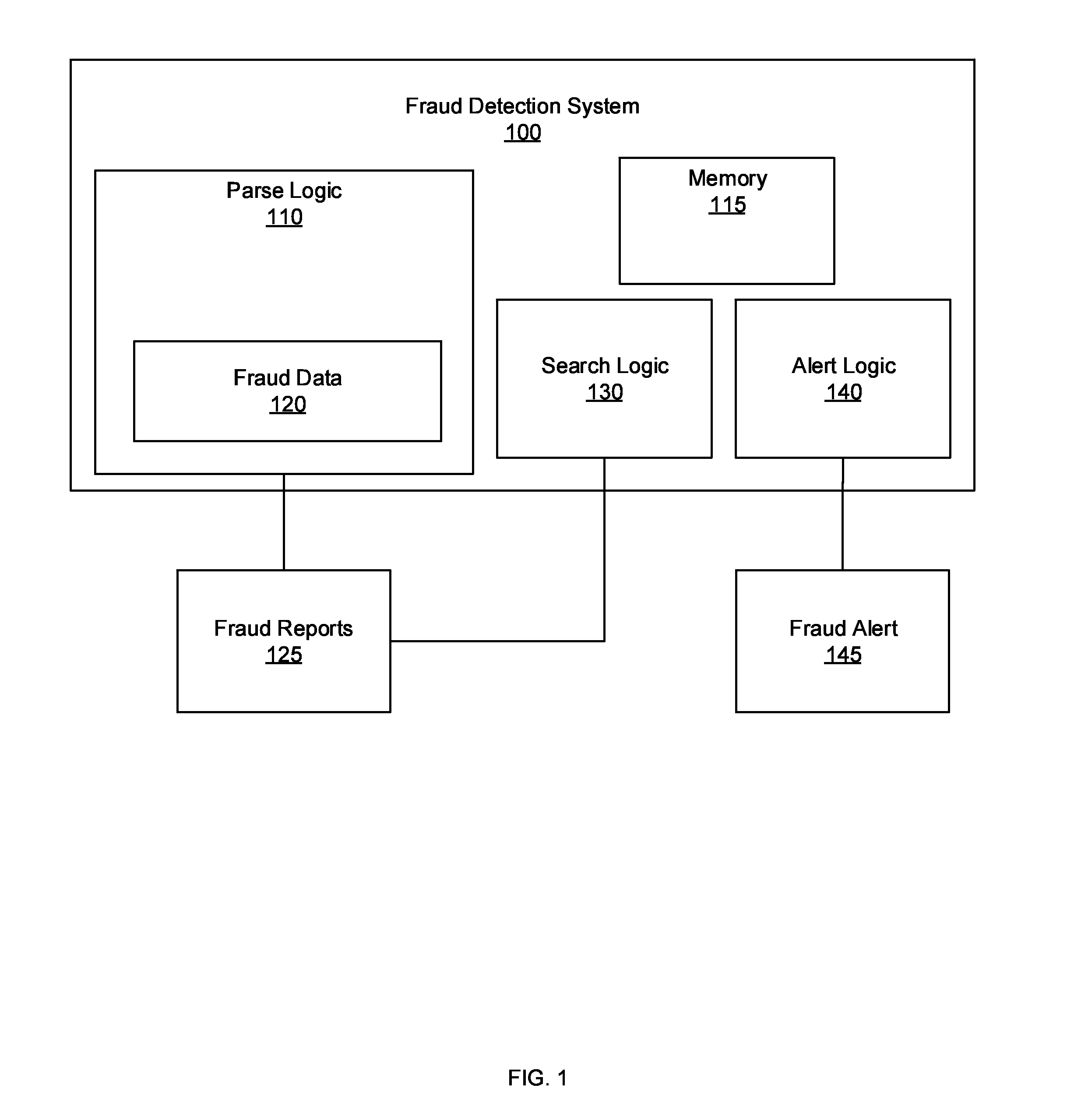
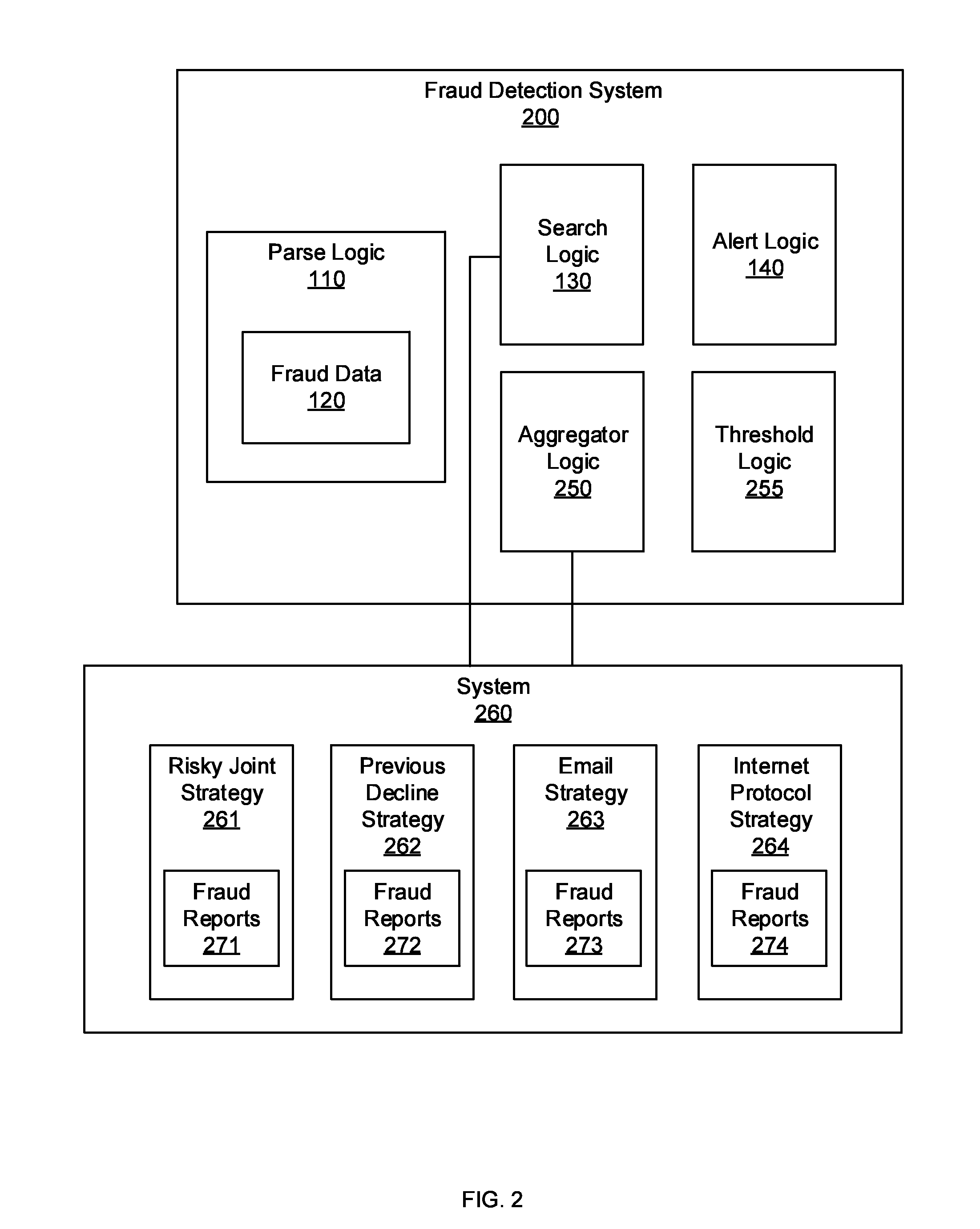
Automated secondary linking for fraud detection systems
ActiveUS20160044048A1Limit its exposure to fraudLess timeMemory loss protectionError detection/correctionData miningFraudulent Data
Systems, methods, and other embodiments associated with automated secondary linking for fraud detection systems. According to one embodiment, a system includes a parsing logic configured to receive an incoming fraud report based on a first fraud detection strategy. The parse logic is also configured to parse the incoming fraud report into fraud data. The system further includes a search logic configured to search a set of fraud reports to identify instances of the fraud data. The system also includes an alert logic configured to generate an alert in response to an instance of the fraud data being identified in the set of fraud reports.
Owner:WELLS FARGO BANK NA
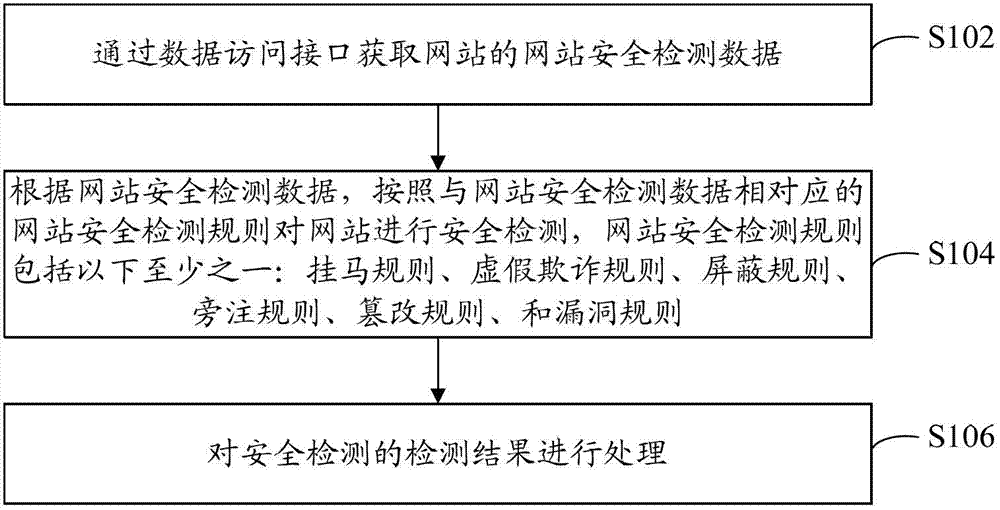
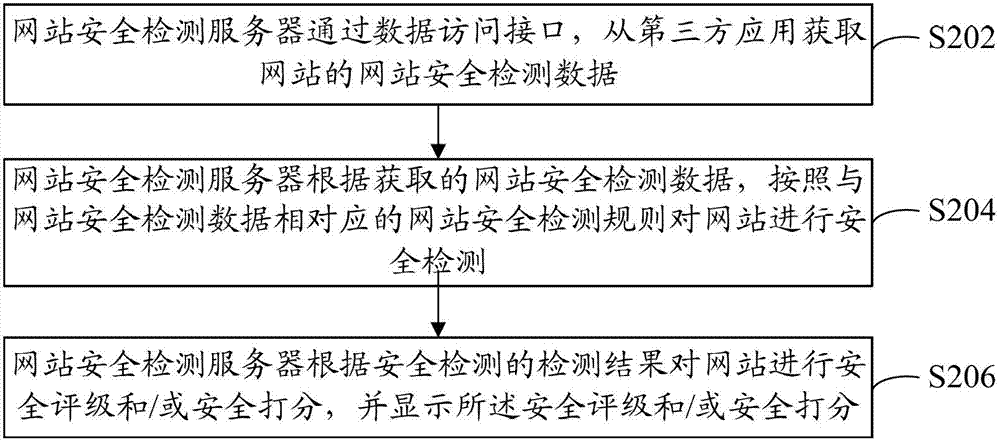
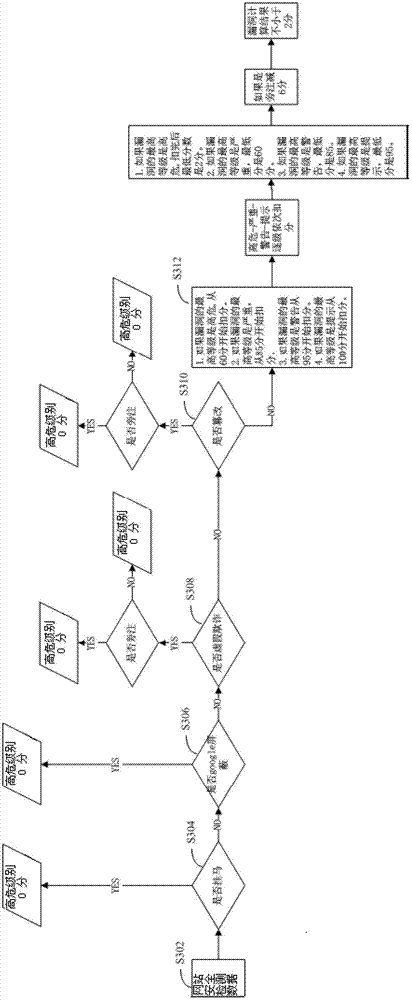
Detection method and device of website security
The application provides a detection method and device of website security. The detection method of website security comprises the following steps of: obtaining website security detection data of a website through a data access interface, wherein the website security detection data comprises at least one of Trojan Horse data, false data, search mask data, margent data, tampering data and vulnerability data; detecting the security of a website according to a website security detection rule corresponding to the website security detection data as well as the website security detection data, wherein the website security detection rule comprises at least one of a Trojan Horse rule, a false rule, a mask rule, a margent rule, a tampering rule and a vulnerability rule; and processing the security detection results. Through the application, the overall security situation of the website can be known by website managers and website users, and the security of the website can be effectively ensured.
Owner:BEIJING QIANXIN TECH
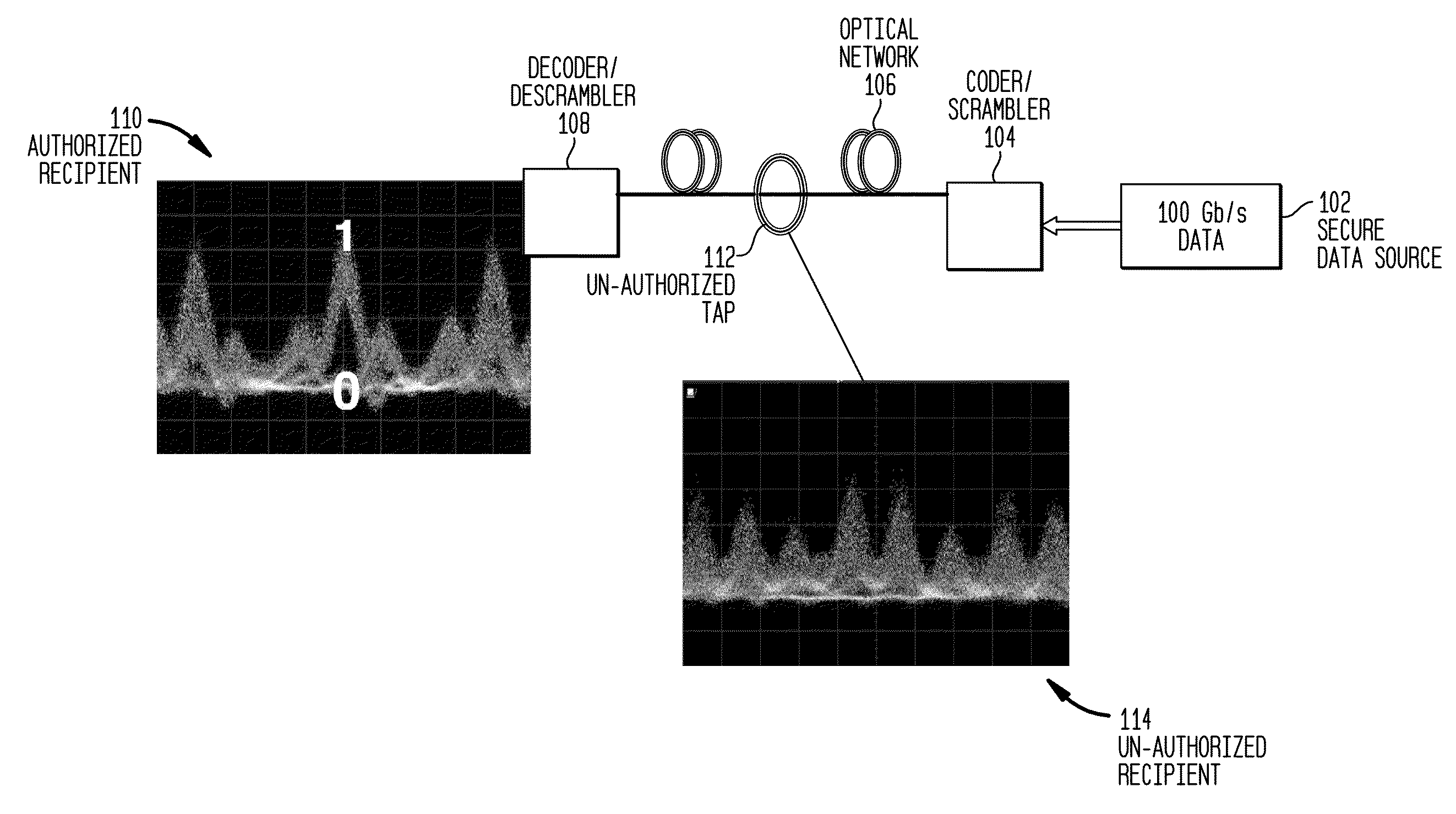
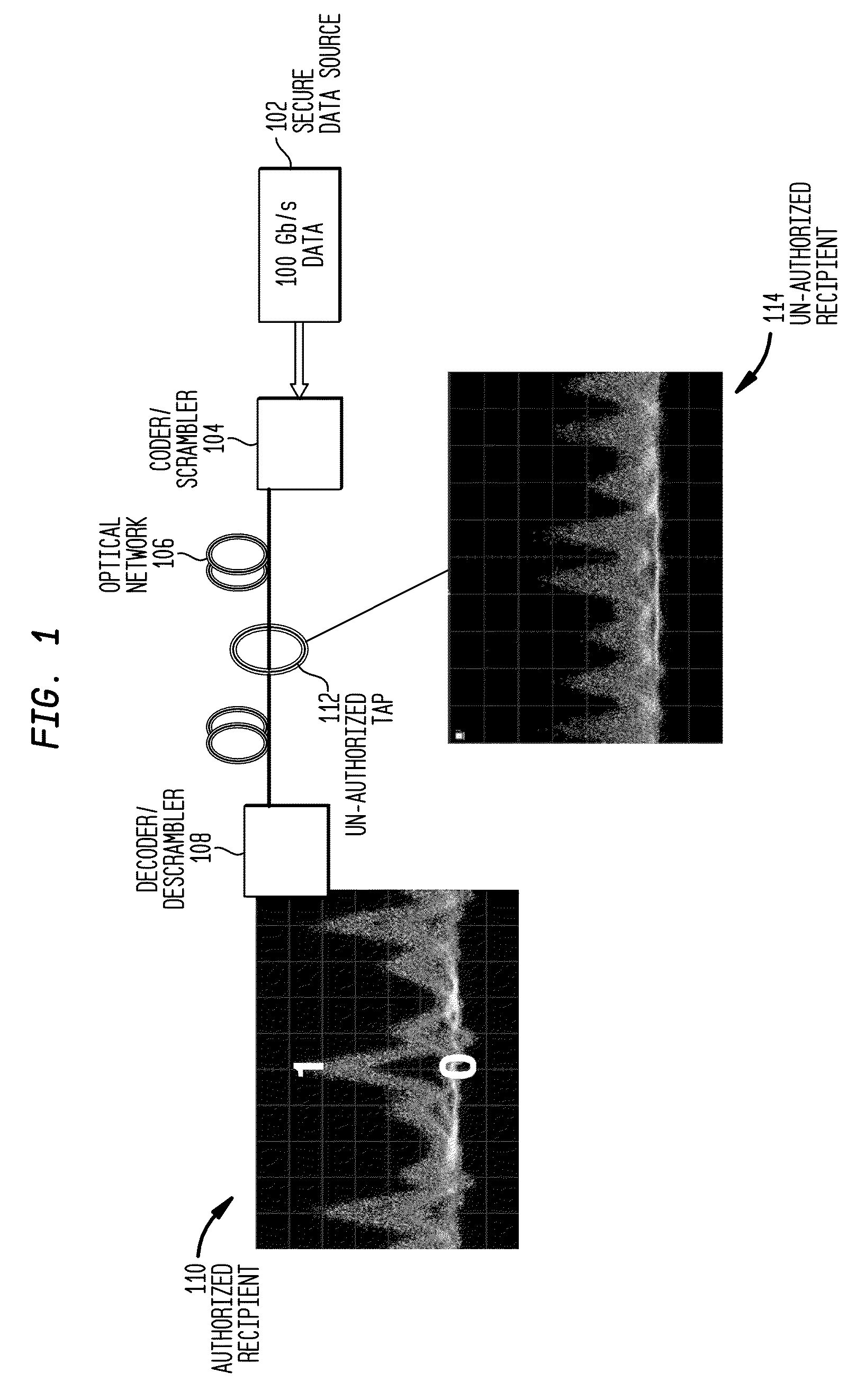
Method and System for OCDM-Based Photonic Layer Security Robustness to Spoof Data Integrity
InactiveUS20100074444A1Secret communicationElectromagnetic transmission optical aspectsData integrityOptical data transmission
A system and method is provided for identifying fraudulent data in an optical data transmission. The system and method includes scrambling an encoded data signal using dynamically changing scramble code; transmitting the scrambled encoded data signal over a network; descrambling the scrambled encoded data signal using a descramble code corresponding to a compliment of the dynamically changing scramble code; analyzing the descrambled encoded data signal to search for a region of low error between descrambled data and noise; notifying of a possible spoofing attempt when a region of low error is not found; and decoding the descrambled encoded data signal using a compliment of phase codes originally used for encoding the encoded data signal in order to generate a decoded signal to retrieve a desired data signal when a region of low error is found.
Owner:TELCORDIA TECHNOLOGIES INC
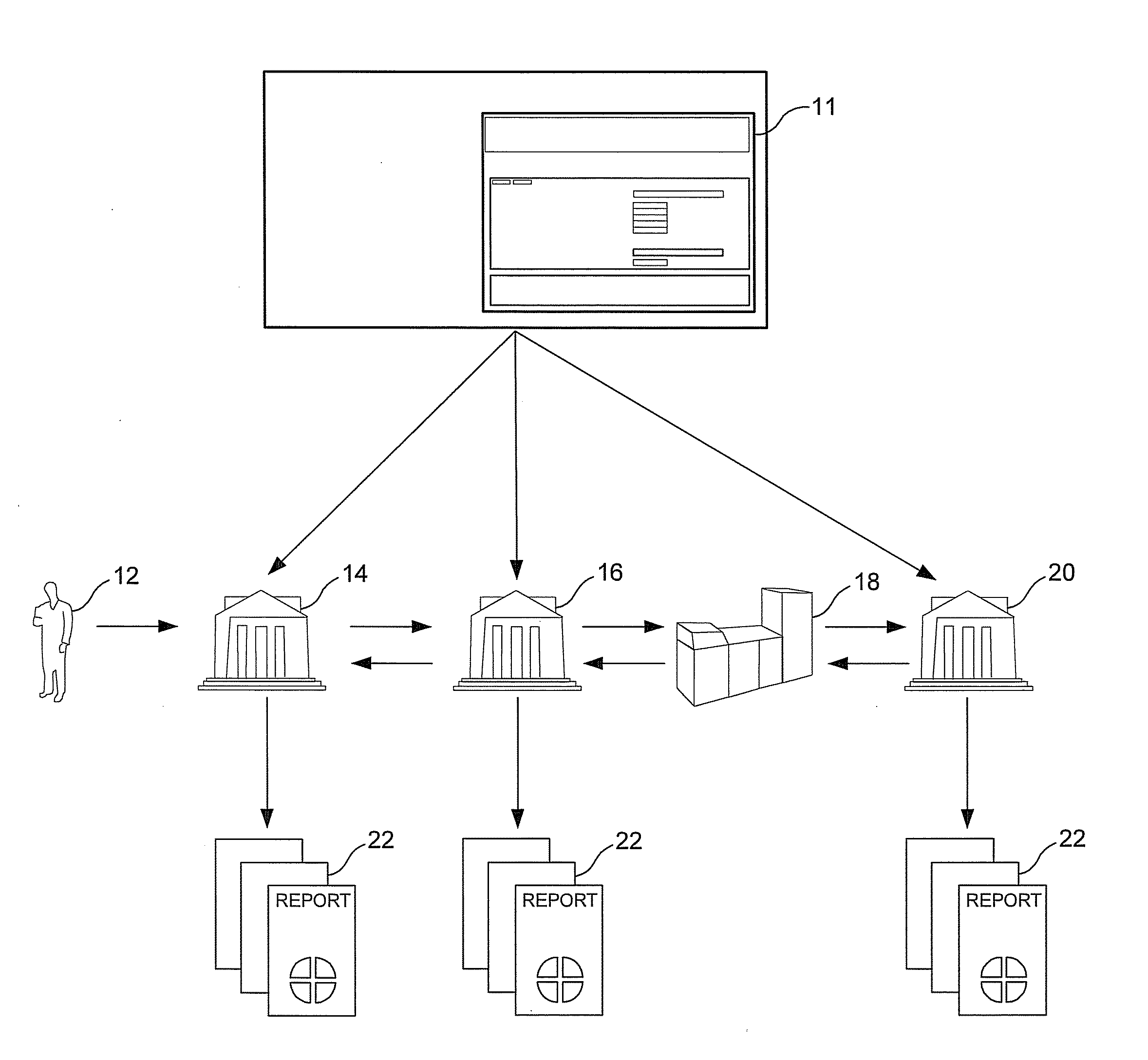
System and method for providing reference cost of fraud data related to financial presentation devices that are presentable to providers of goods or services
A system for providing industry-wide reference cost of fraud data related to financial presentation devices that are presentable to providers of goods and services is provided. A fraud assessment module executable by a processor of the system receives, from multiple business entities, sales data and operating cost data both related to financial presentation devices. The fraud assessment module determines, based on the received data, the reference cost of fraud data including a direct fraud loss, fraud operating cost and opportunity cost for use by individual entities as benchmark cost of fraud data.
Owner:VISA INT SERVICE ASSOC
Fraudulent user identification method, fraudulent user identification device and electronic equipment
PendingCN112348519AAccurate identificationImprove forecast accuracyProtocol authorisationData setFinancial transaction
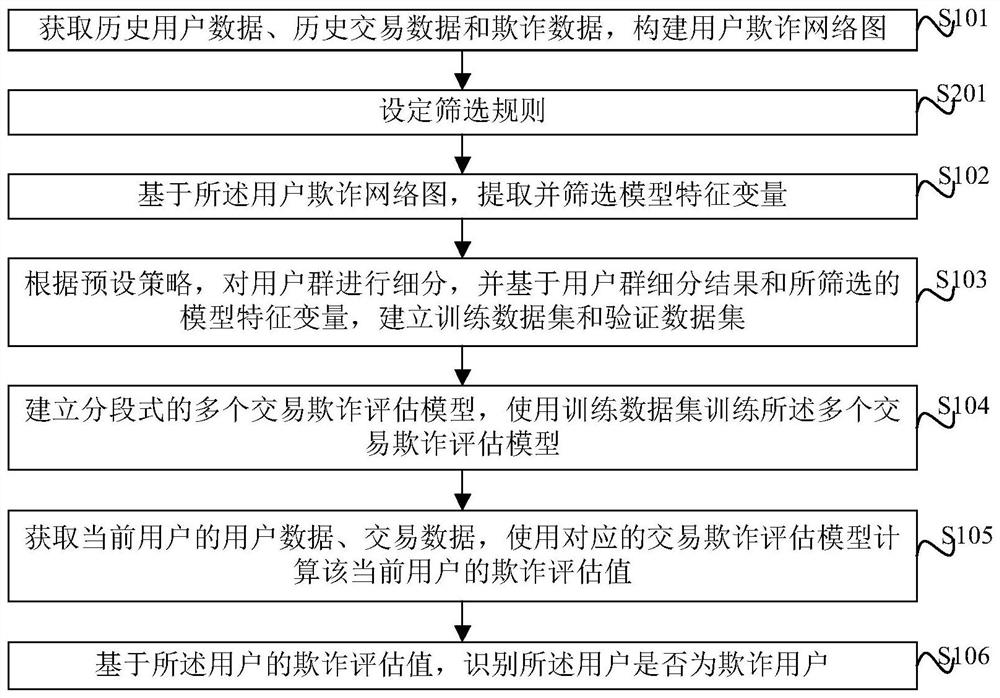
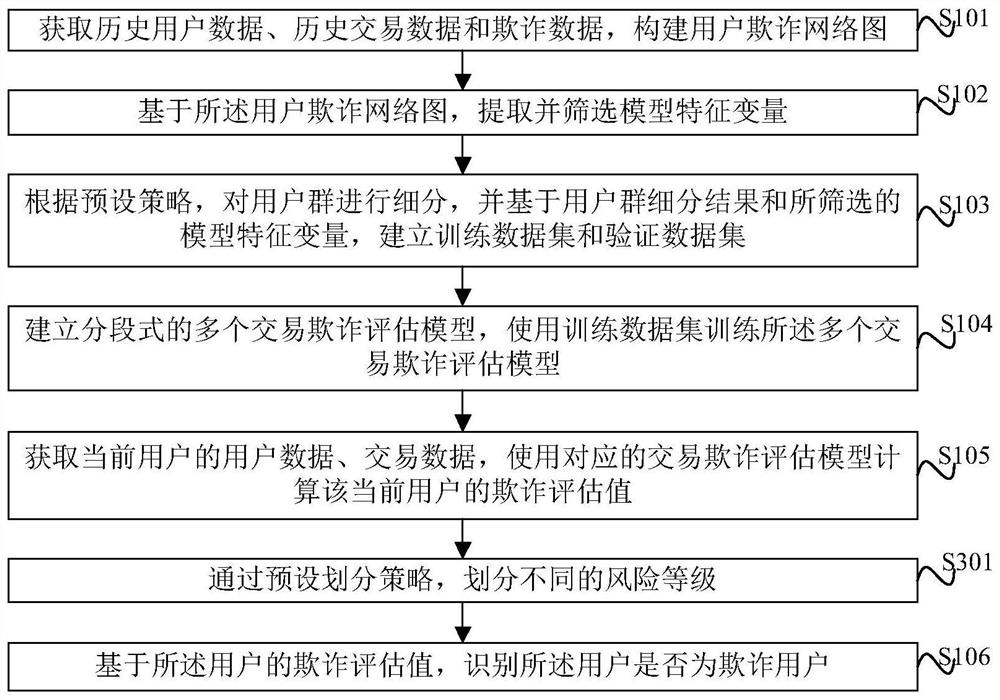
The invention provides a fraudulent user identification method, a fraudulent user identification device and electronic equipment. The method comprises the steps of obtaining historical user data, historical transaction data and fraud data, and constructing a user fraud network graph; based on the user fraud network graph, extracting and screening model characteristic variables; subdividing the user group according to a preset strategy, and establishing a training data set and a verification data set based on a subdivision result of the user group and the screened model characteristic variables; establishing a plurality of segmented transaction fraud evaluation models, and training the transaction fraud evaluation models by using the training data set; obtaining user data and transaction data of a current user, and calculating a fraud evaluation value of the current user by using the corresponding transaction fraud evaluation model; and identifying whether the user is a fraudulent userbased on the fraudulent evaluation value of the user. According to the method, fraudulent clients can be identified more accurately, the fraudulent probability identification accuracy is effectively improved, and the model prediction precision is improved.
Owner:SHANGHAI QIYUE INFORMATION TECH CO LTD
Method Of Data Analysis
InactiveUS20080208946A1Accurate detectionFacilitate data analysisDigital data processing detailsDigital computer detailsData setData profiling
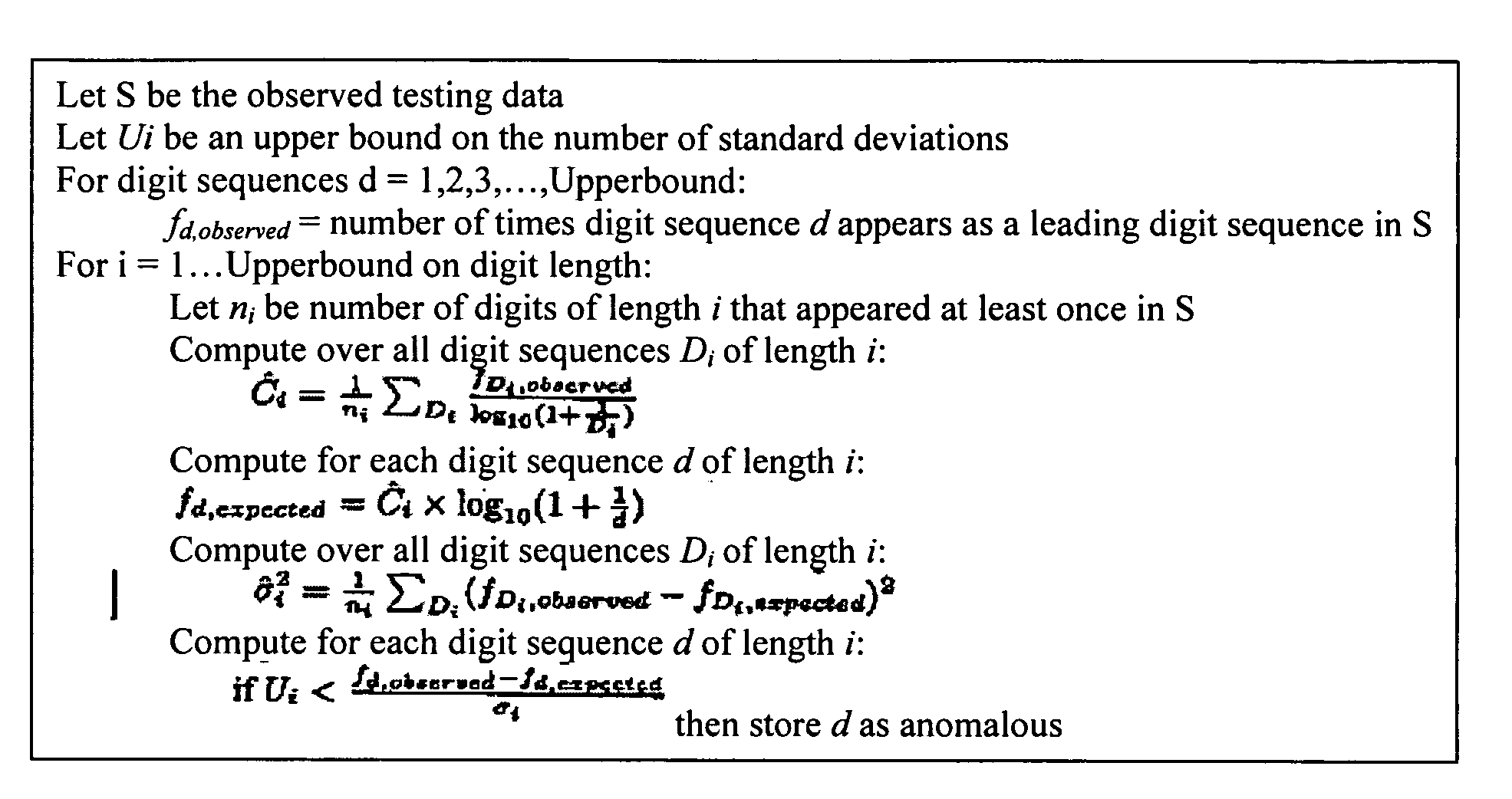
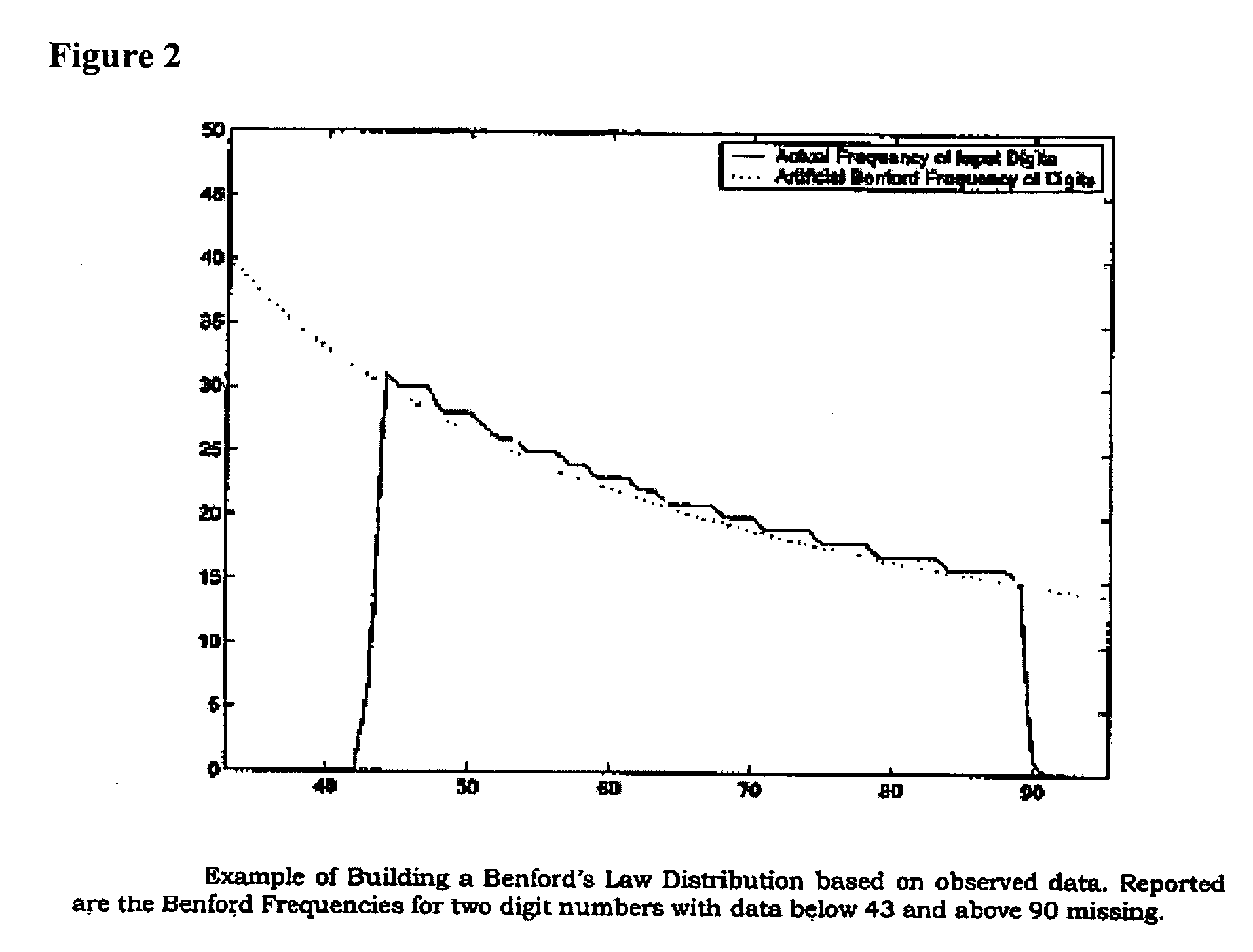
A method of analysis of incomplete data sets to detect fraudulent data is disclosed. The method comprises computing constant values for various leading digit sequence lengths, computing artificial Benford frequencies for the digit sequence lengths, computing a standard deviation for each of the sequence lengths, and flagging any digit sequences in the data set that deviate more than an upper bound number of standard deviations from the artificial Benford frequencies, the upper bound used to determine if the observed data deviates enough to be considered anomalous and potentially indicative of fraud or abuse.
Owner:BORITZ J EFRIM +1
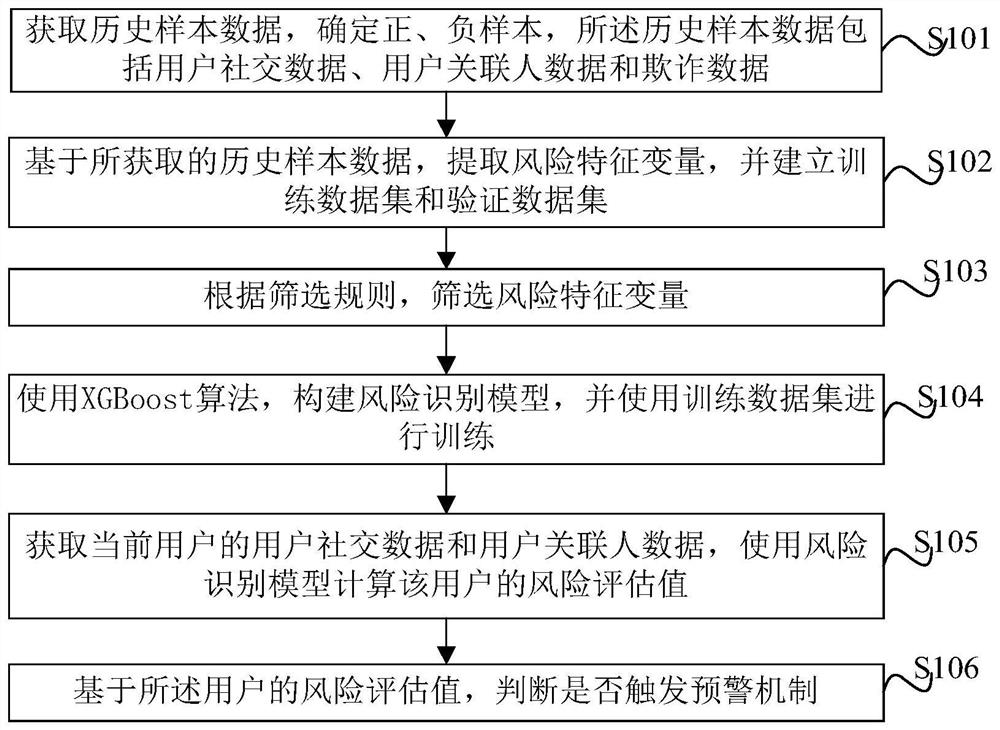
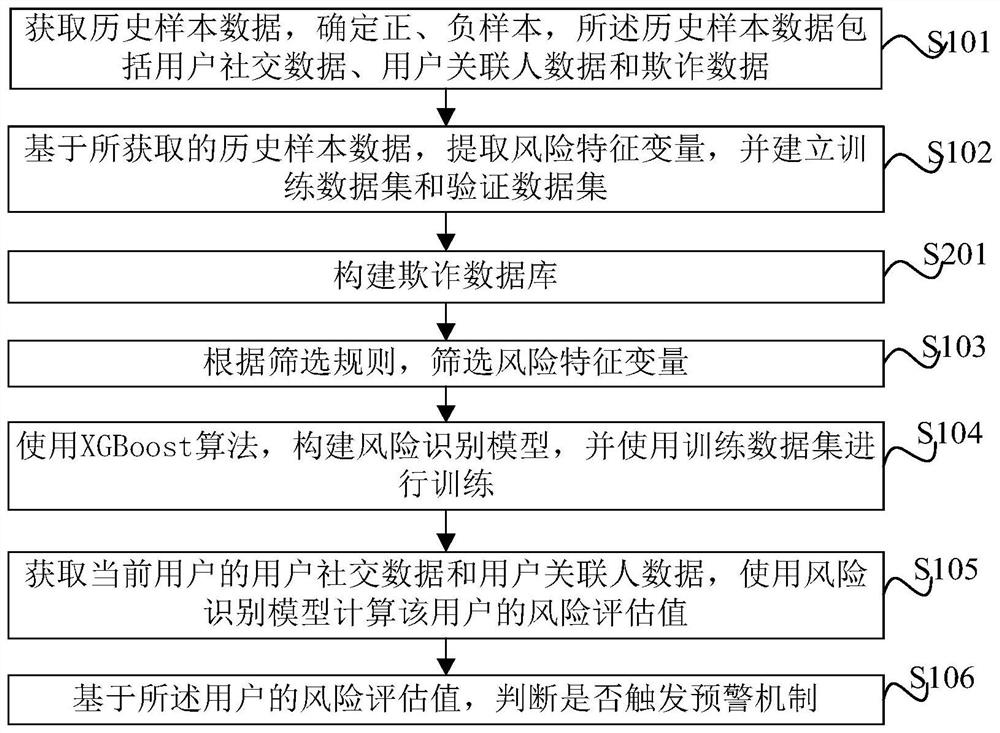
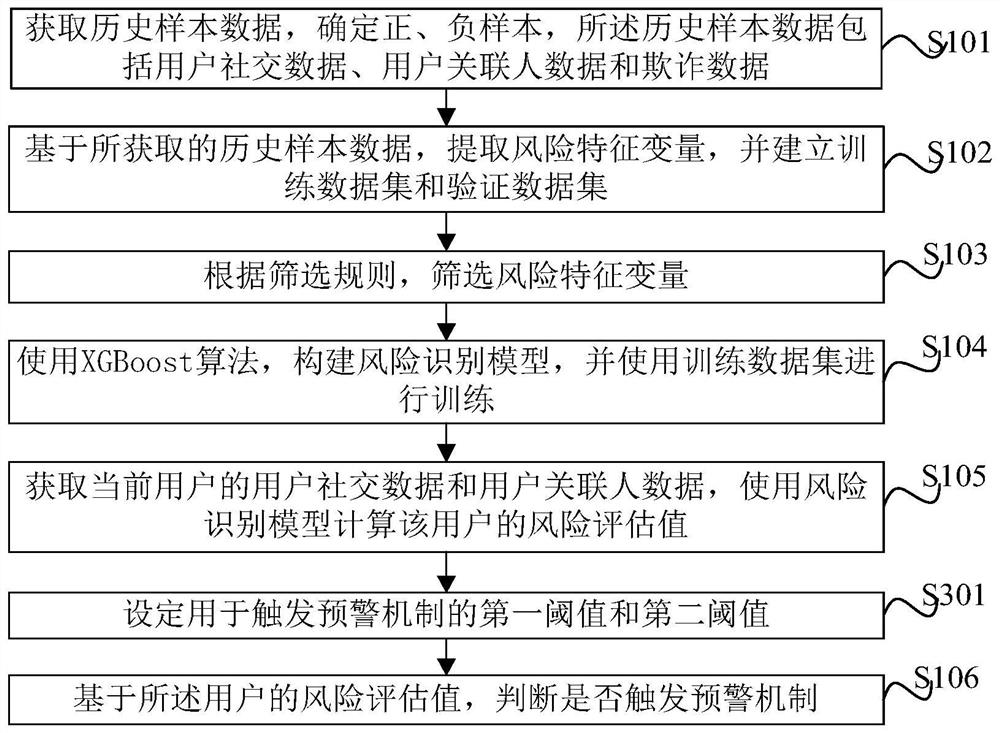
Risk assessment method and device based on XGBoost and electronic equipment
PendingCN112348520AAdded Amplified Risk FeaturesHigh precisionDigital data information retrievalFinanceData packData set
The invention provides a risk assessment method and device based on XGBoost and electronic equipment. The method comprises steps: acquiring historical sample data, and determining positive and negative samples, wherein the historical sample data comprises user social data, user associated person data and fraud data; based on the obtained historical sample data, extracting risk characteristic variables, and establishing a training data set and a verification data set; screening risk characteristic variables according to a screening rule; constructing a risk identification model by using an XGBoost algorithm, and performing training by using the training data set; obtaining user social data and user associated person data of a current user, and calculating a risk assessment value of the userby using the risk identification model; and judging whether to trigger an early warning mechanism or not based on the risk assessment value of the user. According to the method and device, the risk condition of the user can be accurately evaluated, the fraudulent user is effectively identified, the model precision is improved, over-fitting is avoided, and the evaluation effect is remarkably improved.
Owner:SHANGHAI QIYUE INFORMATION TECH CO LTD
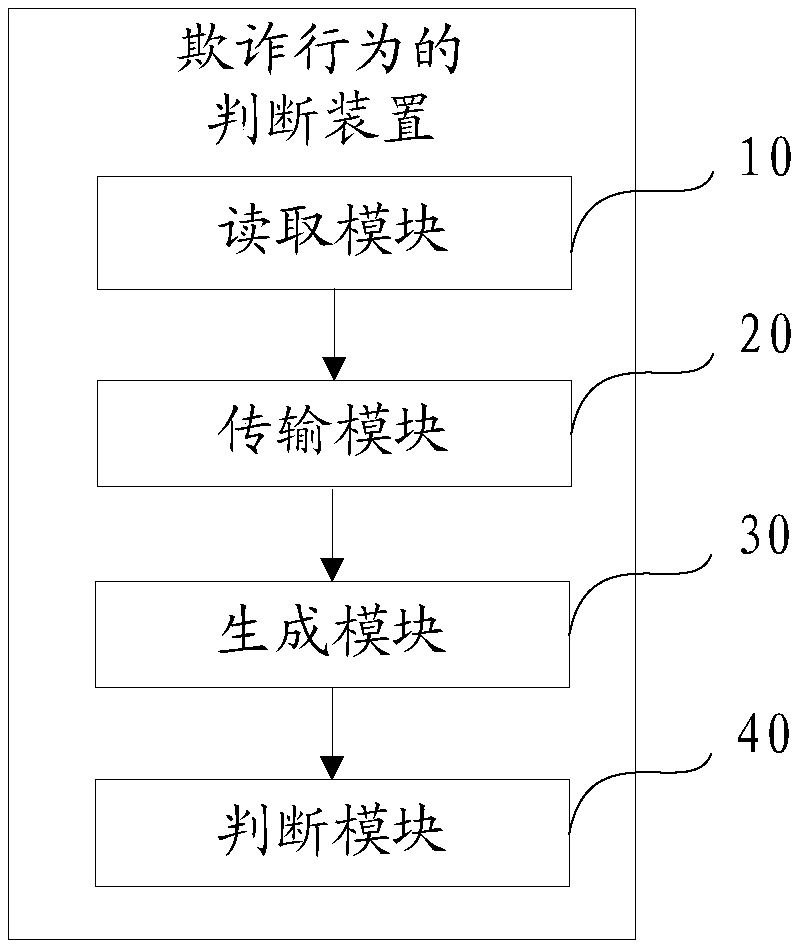
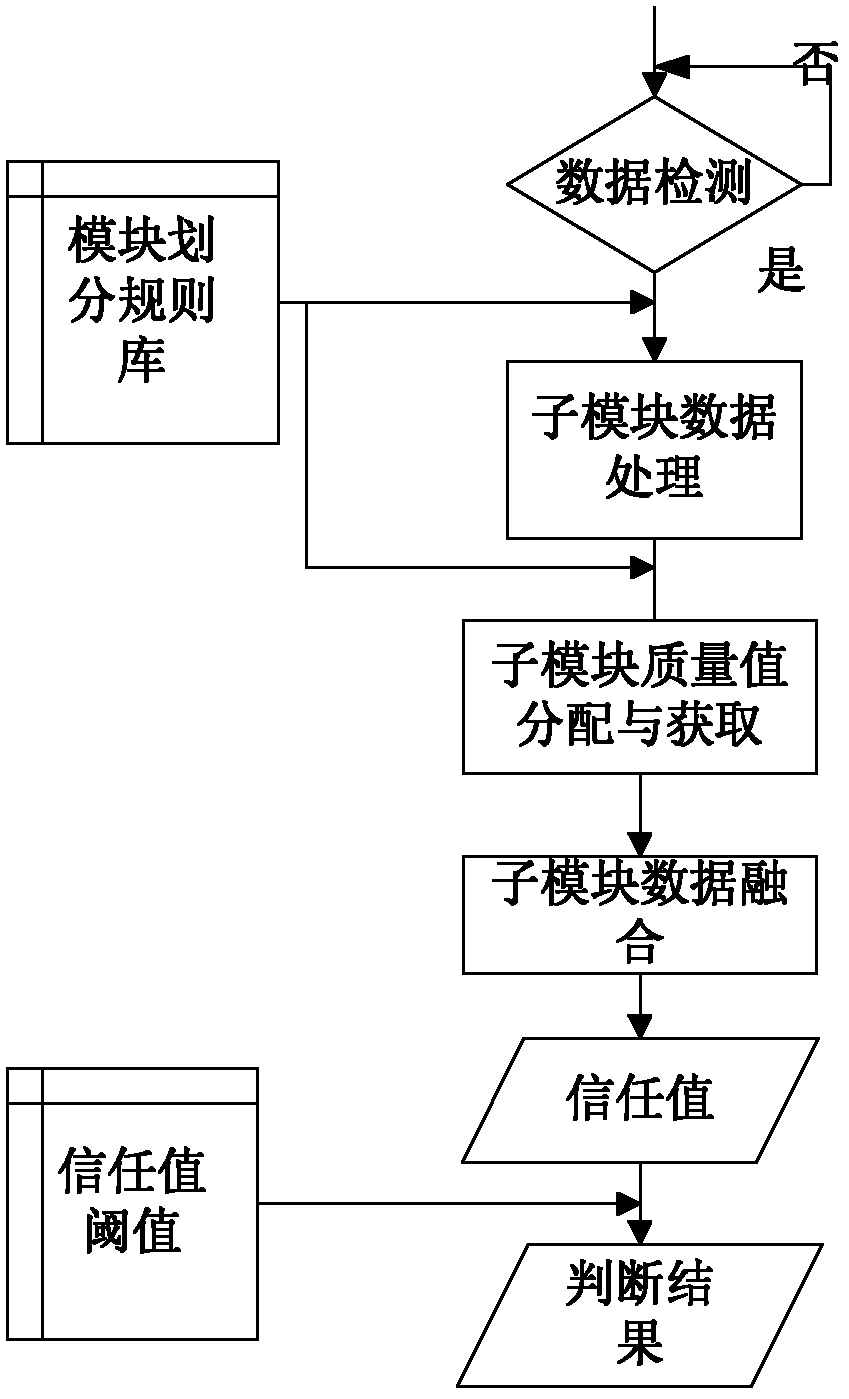
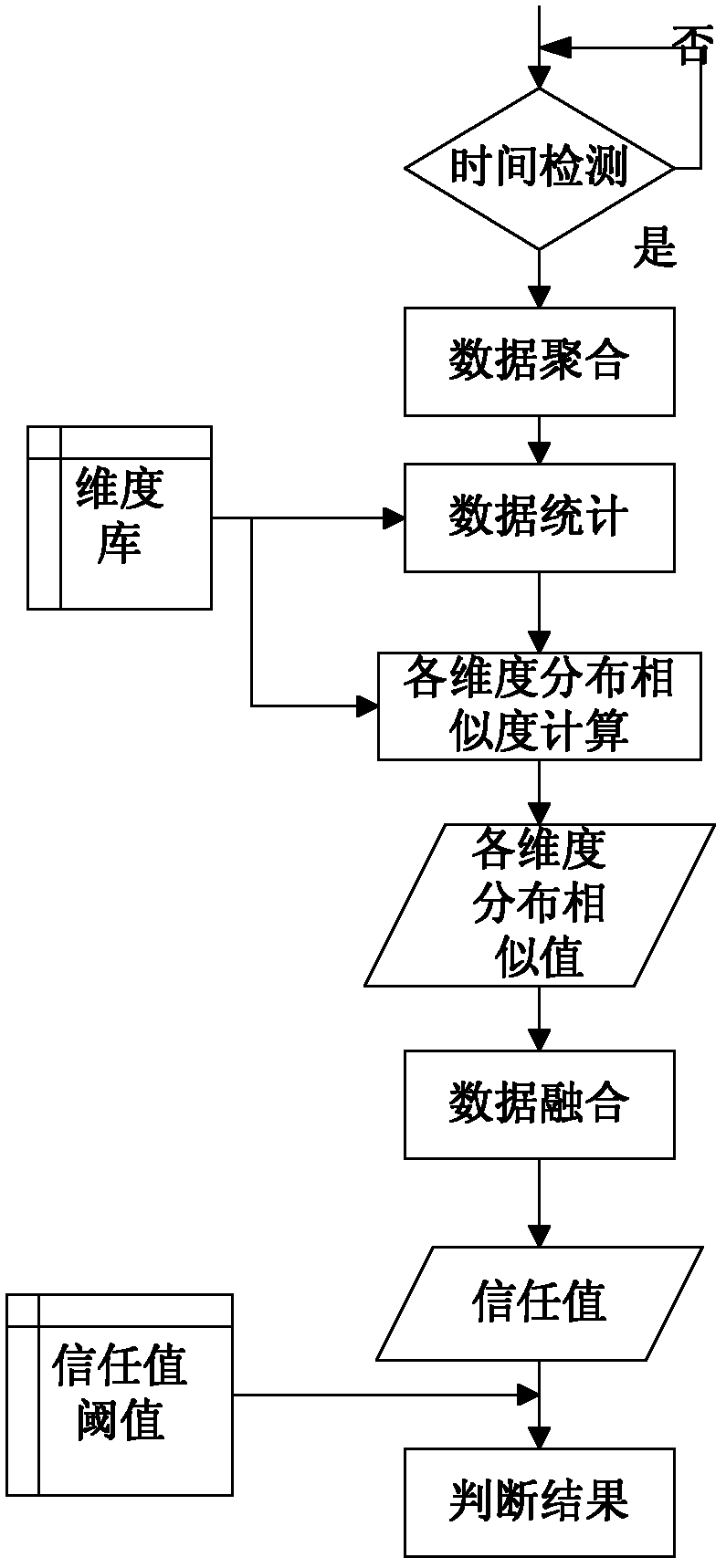
Method, apparatus, apparatus and computer-readable storage medium for judging fraudulent behavior
The invention discloses a judging method, a device, a device and a computer-readable storage medium for fraudulent behavior. The method comprises the following steps: reading fraudulent data in a preset anti-fraudulent platform, classifying and screening the fraudulent data to generate various types of fraudulent sample data; The data of each fraud sample is transmitted to the preset learning model to form a plurality of fraud models. When the operation behavior of the user account is detected, the operation data is generated and a target fraud model corresponding to the operation data is determined. The operation data is transferred to the target fraud model, and whether the operation behavior is fraud or not is judged according to the similarity between the target fraud data and the operation data in the target fraud model. Because the fraud sample data comes from the fraud data of the preset anti-fraud platform, the target fraud model generated based on machine learning can judge the fraud behavior more accurately. At that same time, the fraud model can be update with the fraud data to avoid artificial setting and facilitate the judgment of new fraud behavior.
Owner:ONE CONNECT SMART TECH CO LTD SHENZHEN
Recognition processing method of data
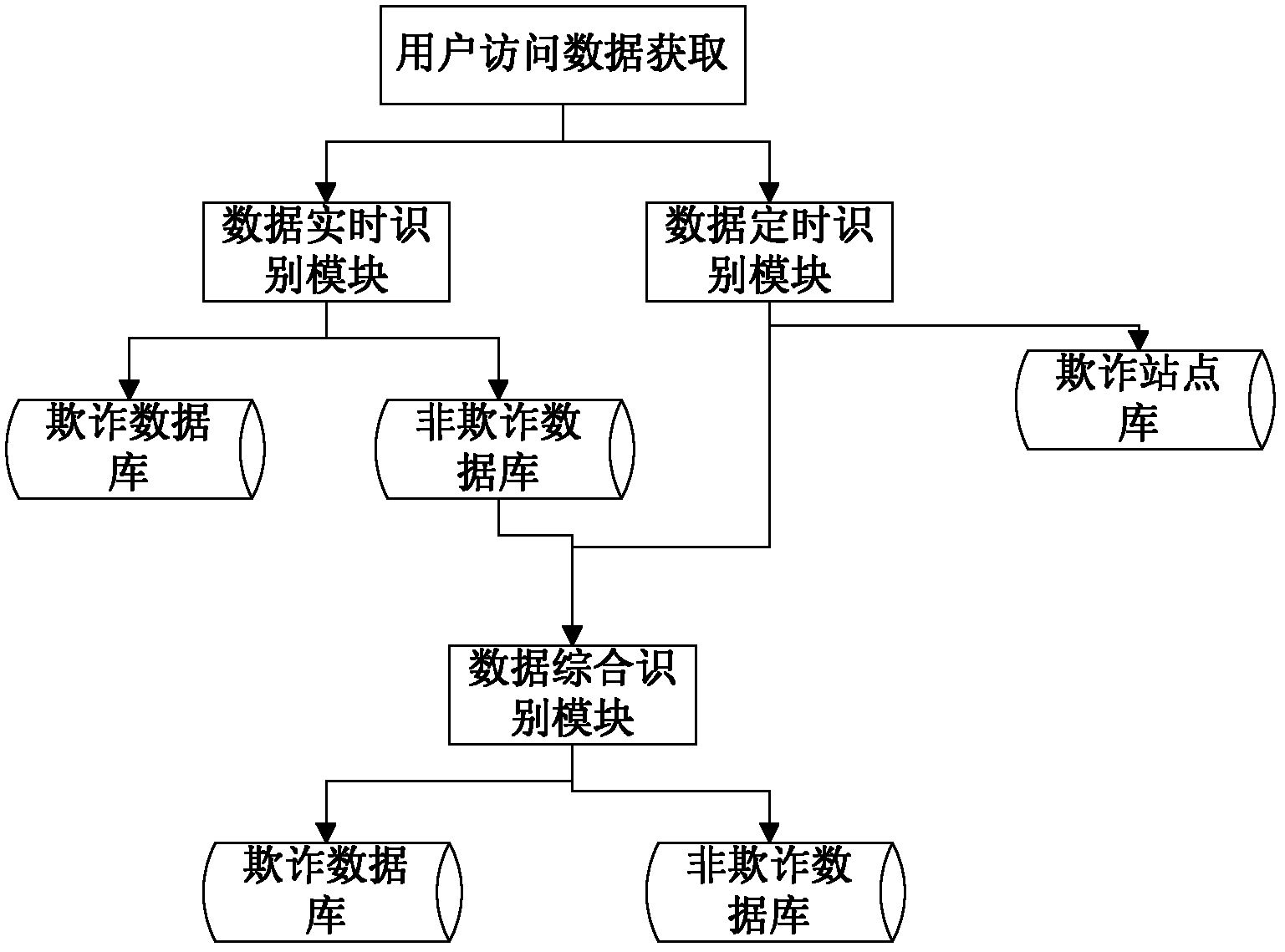
ActiveCN102663021AQuick responseGuaranteed accuracyTransmissionSpecial data processing applicationsComplete dataPattern recognition
The invention discloses a recognition processing method of data, comprising the following steps: step S10 of recognizing the data in real time, and respectively storing fraud data, non-fraud data and data corresponding trust values into a database; step S11 of recognizing the data periodically, storing a fraud site into a fraud site database, and distributing obtained site trust values to the data under the side at the same time; step S12 of comprehensively recognizing the data, recognizing and judging the data stored in the non-fraud database in real-time recognition again according to the trust values acquired in a periodically-recognizing stage. The method provided by the invention forms a set of complete data recognition mechanism through organically combining data real-time recognition periodical recognition and data comprehensive recognition based on data fusion, respond to clients fast through an effective recognition method on the basis of acquired user access data, and simultaneously ensure accuracy and comprehensiveness for recognition.
Owner:ZHEJIANG PANSHI INFORMATION TECH
Fraudulent page detection
Owner:SENTRYBAY
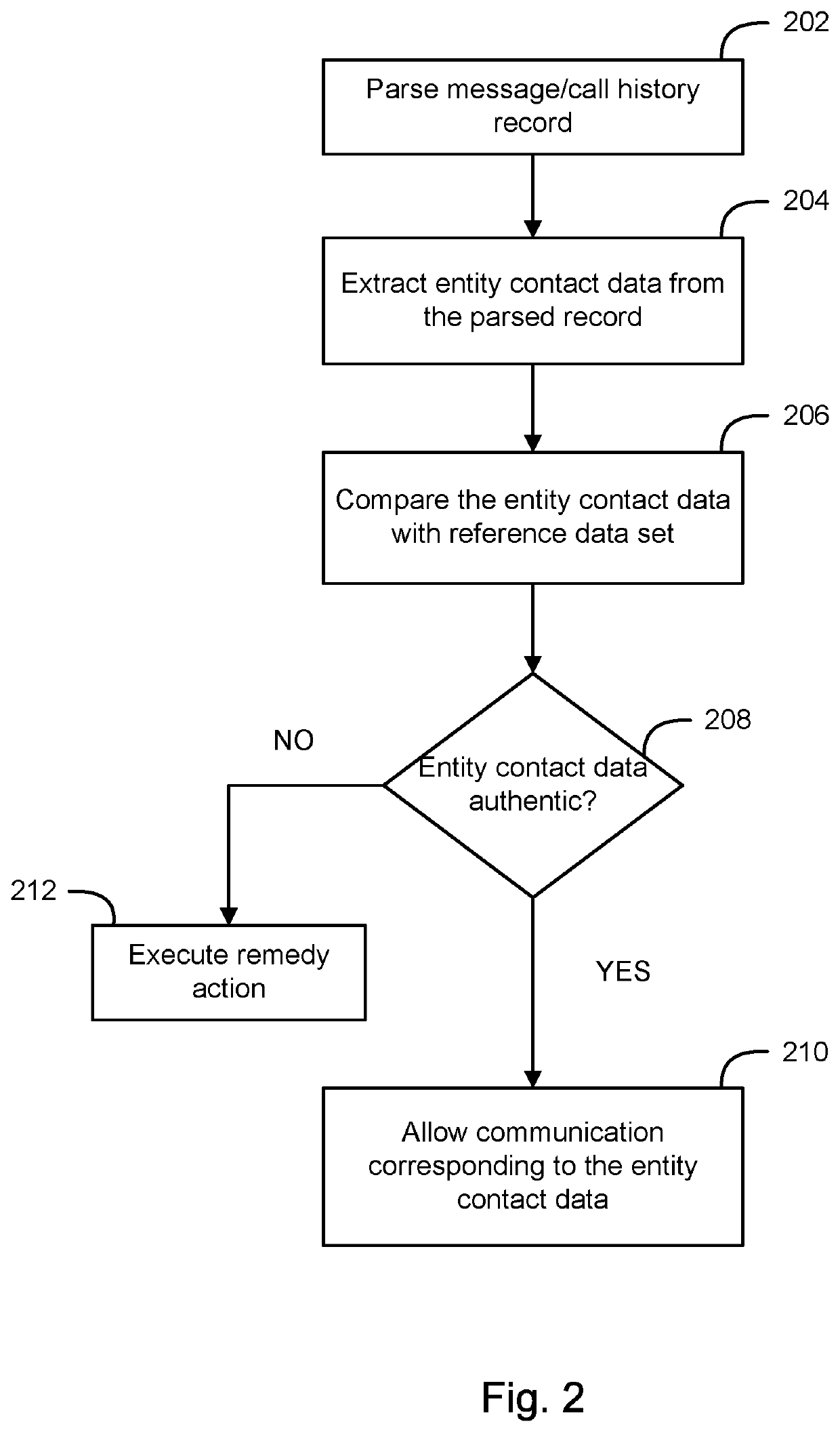
Dynamically providing safe phone numbers for responding to inbound communications
A system and method for dynamically providing safe call back numbers to use to respond to an inbound communication, the method comprising parsing message records from a message server, analyzing the message records for untrustworthy phone numbers by comparing content of the message records to a reference data set that is retrieved from a database, the reference data set including genuine and fraud data wherein the genuine and fraud data includes entities and contact information corresponding to the entities, determining untrustworthy phone numbers in the message records from the analysis, and generating remedy actions based on the determination of the untrustworthy phone numbers.
Owner:YOUMAIL
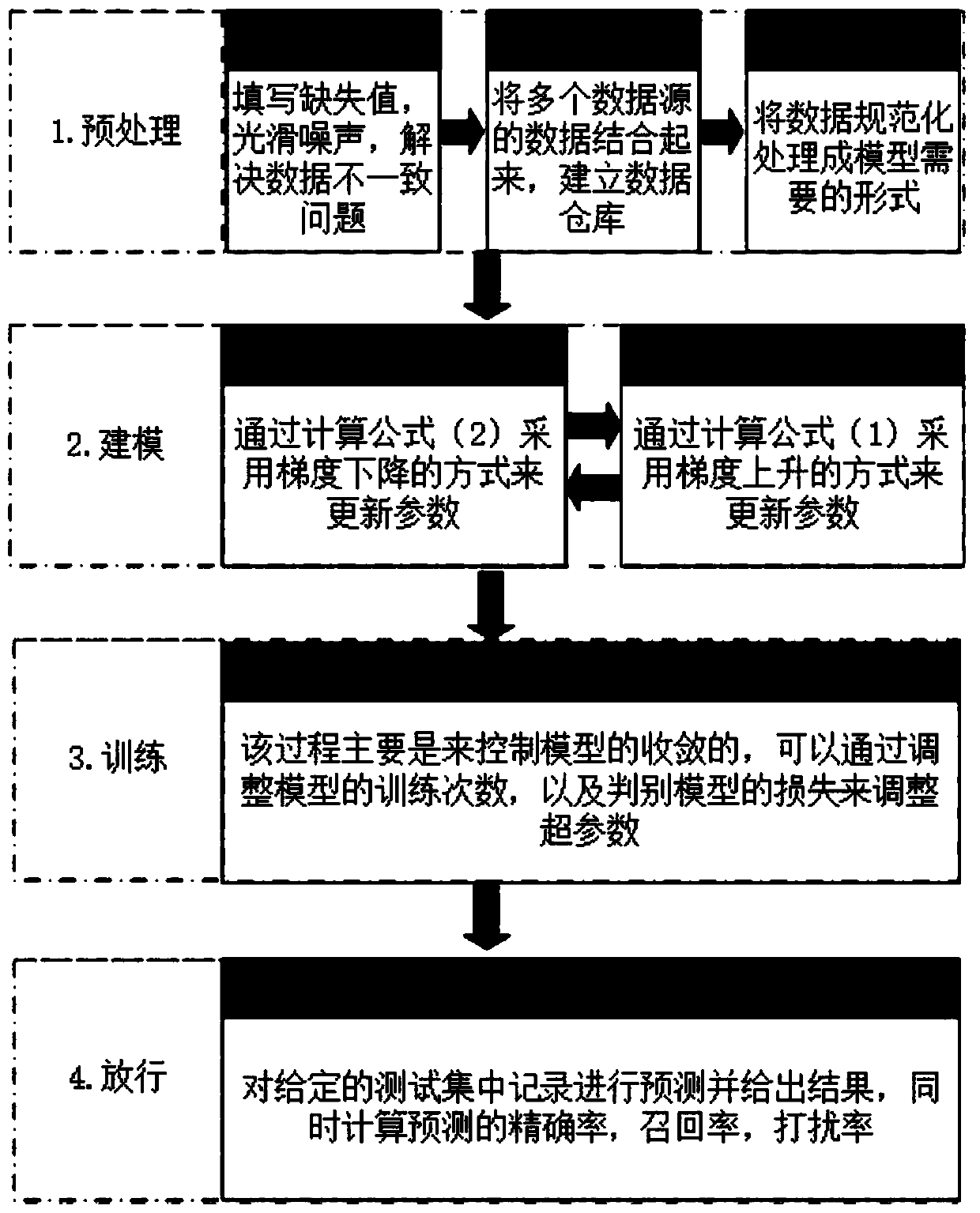
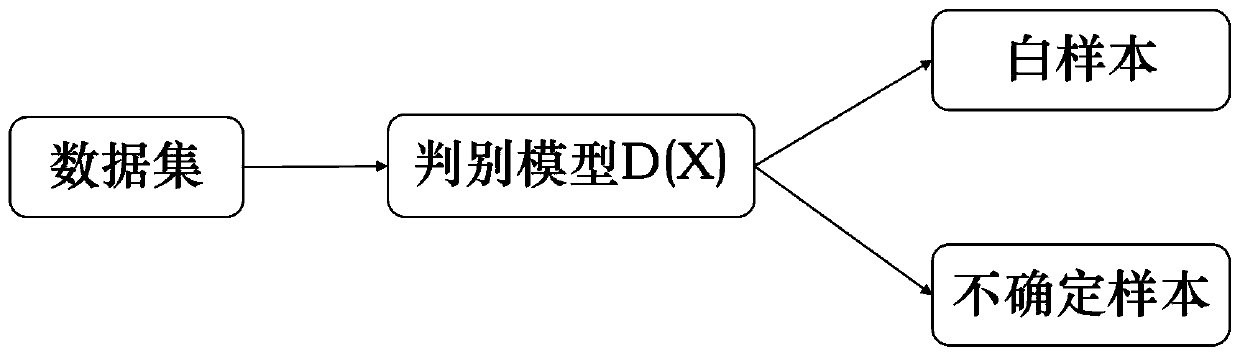
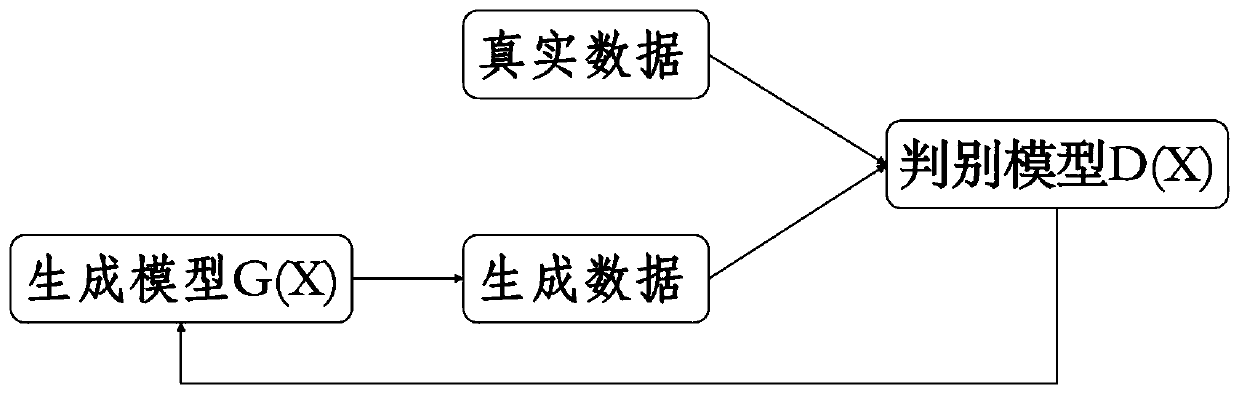
Trusted electronic transaction release mechanism based on generative adversarial network
The invention discloses a trusted electronic transaction release mechanism based on a generative adversarial network. The method is characterized by comprising, the transaction distribution of normalusers is learnt by using the generative adversarial network by using a large amount of non-fraudulent data based on a reverse idea; the obtained discrimination model can better identify non-fraud data, so that a release mechanism can be adopted for credible electronic transactions, and the remaining data which cannot be discriminated are delivered to the prediction model for prediction, so that alarge amount of time can be saved.
Owner:TONGJI UNIV
Fraud detection system
InactiveUS20170255995A1Simple systemHigh precisionFinanceData switching networksComputer scienceMultiple layer
A system and method is disclosed for detecting fraudulent loan applications. The system is based upon multiple layers of detection in which anomalies are detected by analyzing the loan data and the borrower browser configuration for anomalies indicative of fraud. A plurality of fraud detection layers are used which when taken together provide a synergistic approach to detecting fraudulent data.
Owner:BLUE GLOBAL LLC
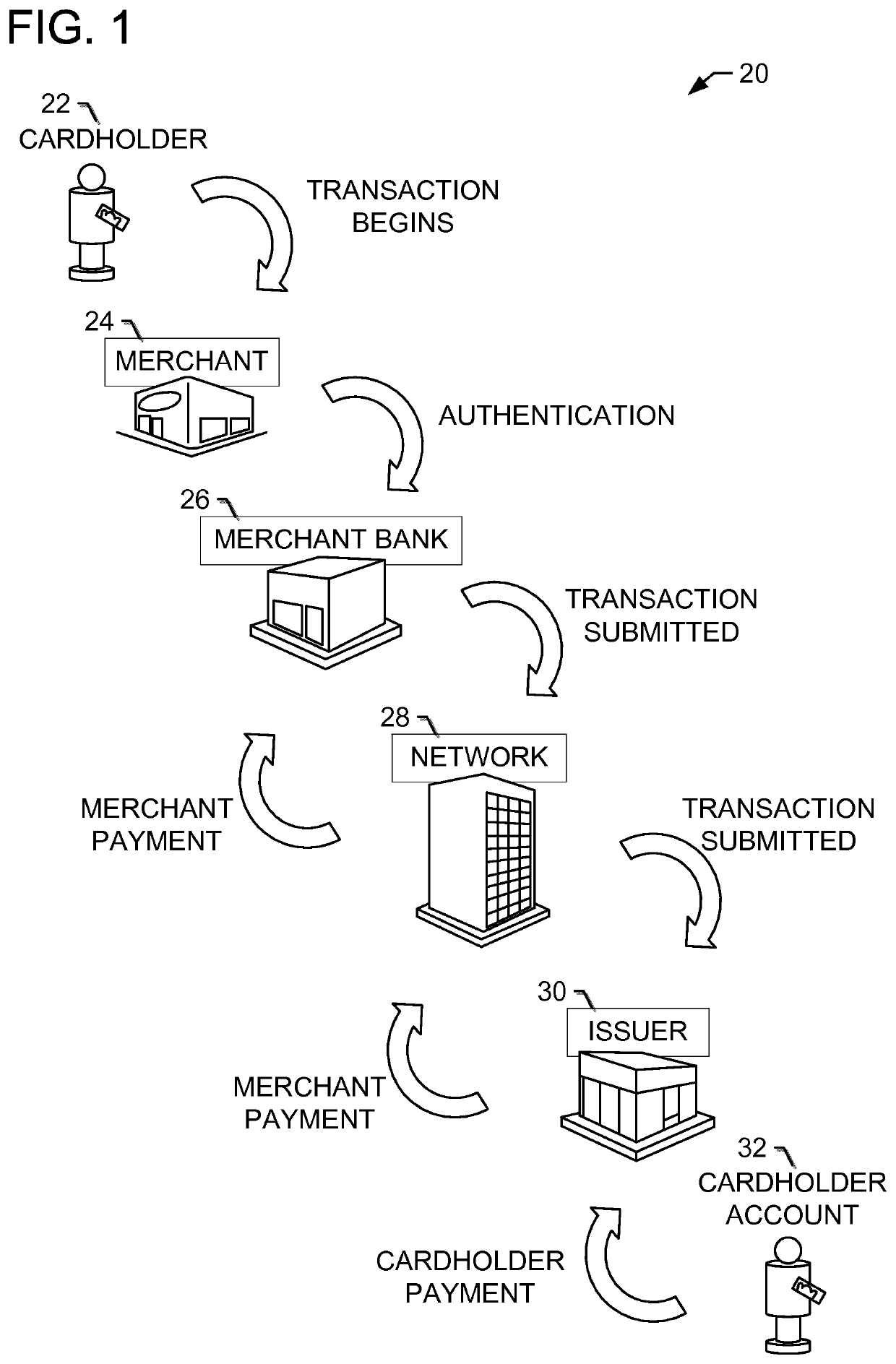
System and method for detecting fraudulent network events
A computing device for detecting fraudulent network events in a payment card transaction network is provided. The computing device includes a processor and a display device. The computing device is programmed to receive a first plurality of fraud data elements associated with a plurality of payment card transactions from a fraud detection system. The computing device is also programmed to generate a first graph from the first plurality of fraud data elements. The computing device is further programmed to receive a first plurality of data elements associated with the plurality of payment card transactions from a second system. The computing device is also programmed to generate a second graph from the first plurality of data elements and display both of the first graph and the second graph simultaneously to a user on the display device, such that the user to detect fraudulent events in the payment card transaction network.
Owner:MASTERCARD INT INC
Method for detecting fraudulent frame sent over an in-vehicle network system
ActiveUS10158717B2Easy loadingEfficiently and appropriately detectingDigital data processing detailsUser identity/authority verificationArea networkIn vehicle
A fraud detection method for use in an in-vehicle network system including a plurality of electronic control units that communicate with one another via a bus in accordance with Controller Area Network (CAN) protocol is provided. The method includes receiving at least one data frame sent to the bus, verifying a specific identifier in the received data frame only if the received data frame does not follow a predetermined rule regarding a transmission period and a state of a vehicle having the in-vehicle network system mounted therein is a predetermined state, detecting the received data frame as an authenticated data frame if the verification is successful, and detecting the received data frame as a fraudulent data frame if the verification fails.
Owner:PANASONIC INTELLECTUAL PROPERTY CORP OF AMERICA
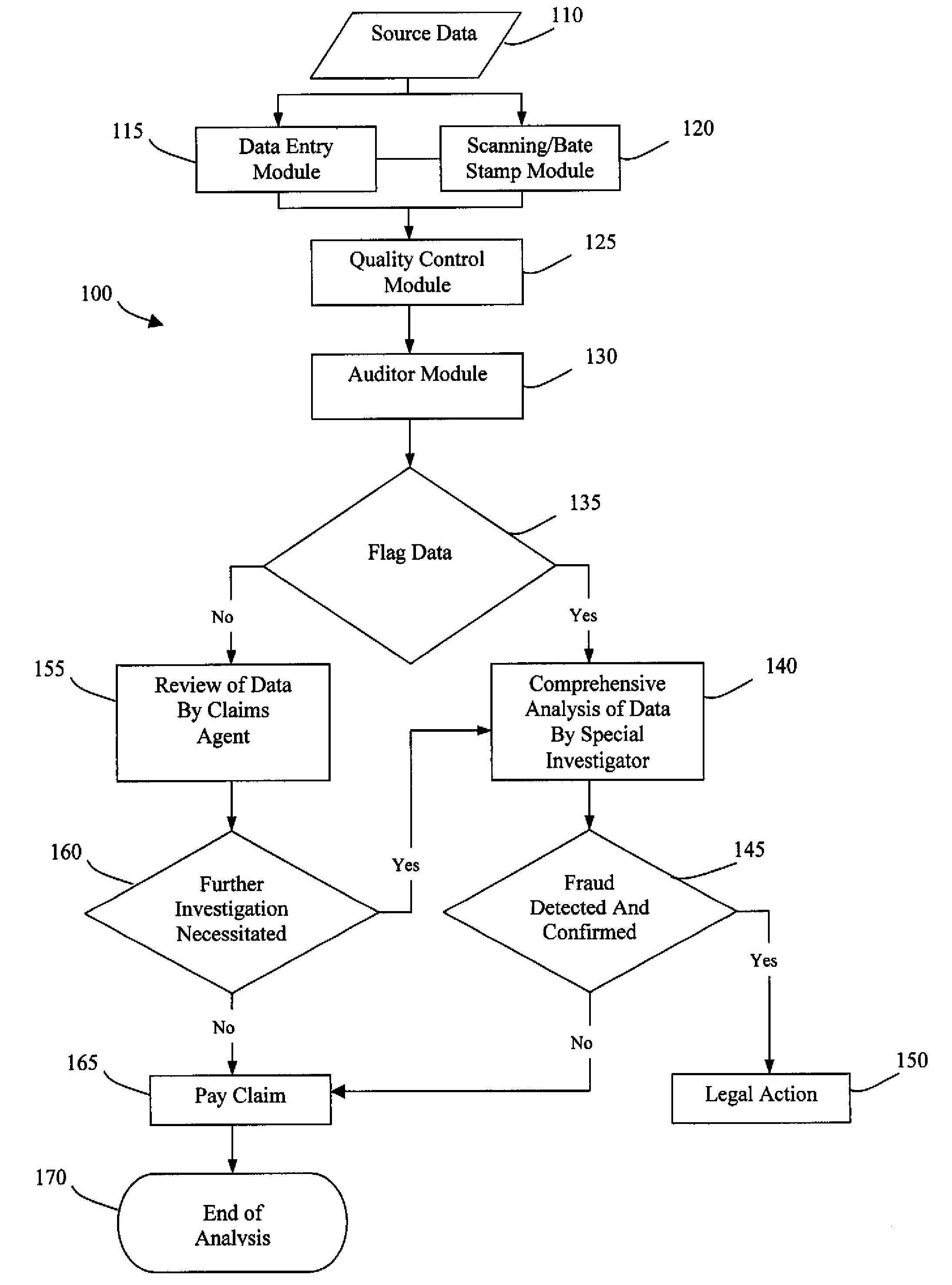
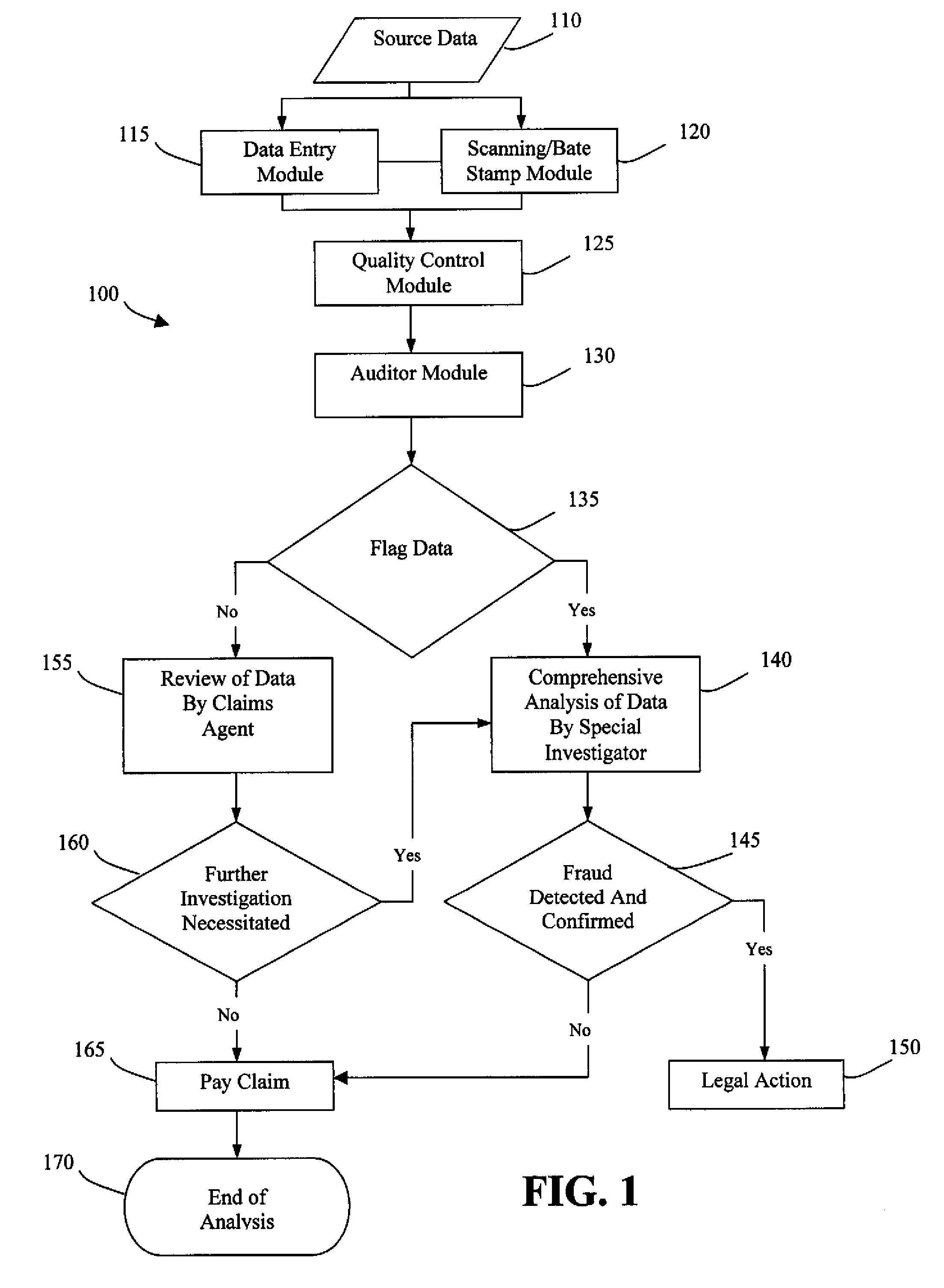
System and method for detecting healthcare insurance fraud
InactiveUS20080140599A1Easy to readEffectively and proficiently reviewMedical data miningFinanceGraphicsData mining
The invention comprises a method and system of detecting and identifying fraud arising from a healthcare claim. The system includes a storage means for storing a data base containing source data related to a healthcare claim. A memory means is used for storing a set of user-defined rules for detecting and identifying fraud. A processing means is coupled to the storage means for comparing the source data to the set of rules in the memory means. If the source data violates the set of rules, the relevant portion of the source data is identified and flagged as fraudulent data. The flagged data is then forwarded to a special investigator for a comprehensive analysis. The fraudulent data is transformed to graphs and charts to illustrate patterns so that the fraud is easily detected and identified.
Owner:PACHA DEBRA +2
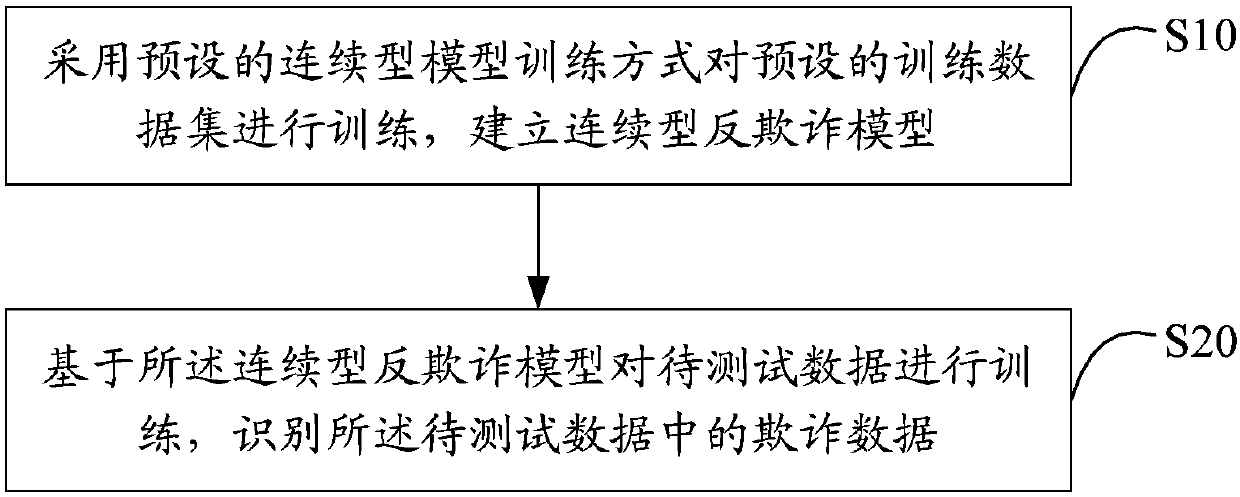
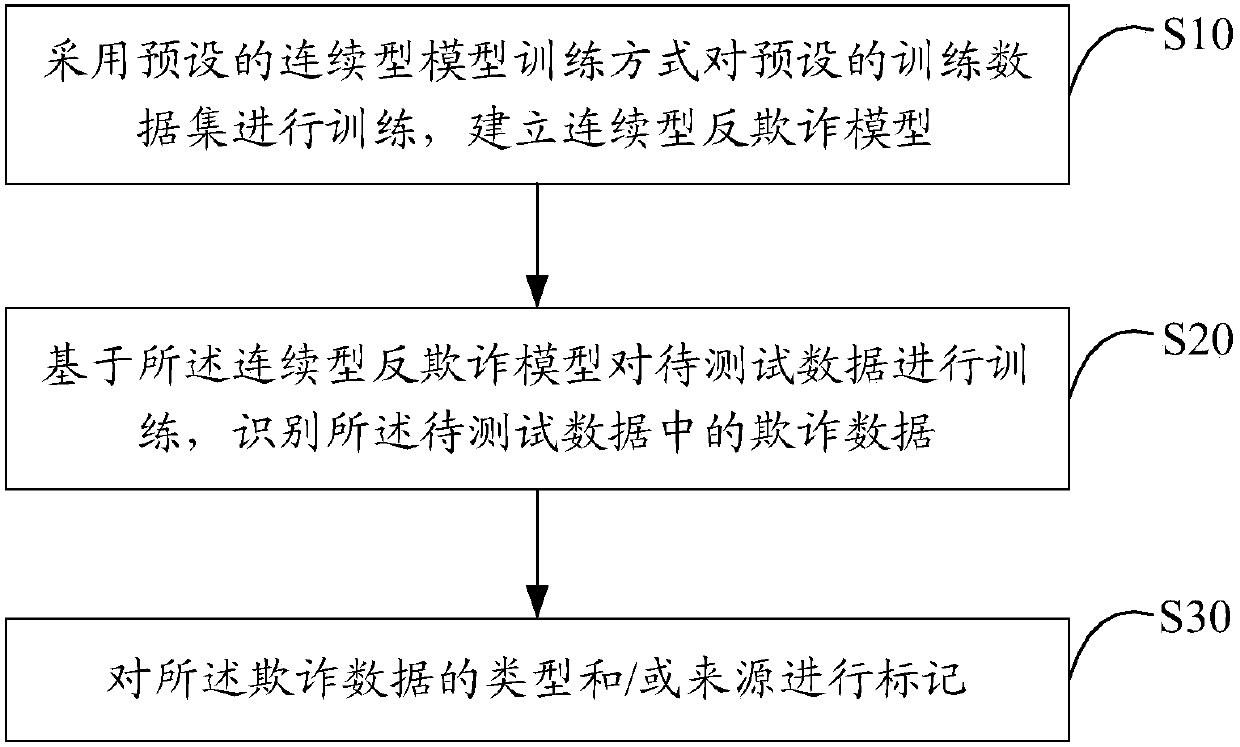
A fraudulent data identification method and device
ActiveCN107657453AImprove recognition accuracyImprove recallFinanceProtocol authorisationData setIdentification device
The invention provides a fraudulent data identification method comprising the steps of training a preset training data set by using a preset successive type model training mode to build a successive type anti-fraud model; training to-be-tested data by using the successive type anti-fraud model to identify fraudulent data in the to-be-tested data. The invention also provides a fraudulent data identification device. Based on the characteristic that fraudulent data in to-be-tested data are non-balanced data, the successive type anti-fraud model is used for analyze and identify fraudulent data inthe to-be-tested data; compared with a common single model, the successive type anti-fraud model can improve the identification accuracy and recall rate of fraudulent data, more accurately judge fraudcases and reduce the range and cost of manual checking.
Owner:PING AN TECH (SHENZHEN) CO LTD
Credit card fraud identification method
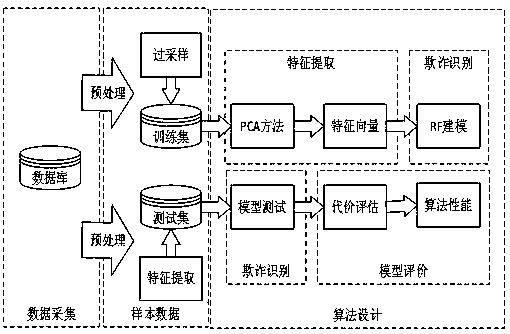
InactiveCN110321950AQuick collectionEasy to handleFinanceCharacter and pattern recognitionFeature vectorCost evaluation
The invention discloses a credit card fraud identification method, and relates to the technical field of credit cards. The identification method comprises the following steps: after desensitizing acquired data, dividing the acquired data into a training set and a test set; adding part of noise to the fraudulent data in the training set, generating new fraudulent data, adding the new fraudulent data into the training set, and solving the problem of imbalance of the training set; a PCA method is adopted to perform feature extraction on the training set and the test set, and after feature vectorsare obtained, adopting an RF algorithm to construct a classifier according to feature data of the training set; importing the test set feature data into an RF classifier to identify and classify fraudulent transactions; and finally, evaluating the classification result by using a cost evaluation method to obtain the performance of the fraud identification method. According to the method, information can be quickly collected and preprocessed, and meanwhile, new fraud data is generated and added into a training set; modeling and classification are convenient to achieve, meanwhile, data evaluation can be achieved, and efficiency is improved.
Owner:HARBIN UNIV OF SCI & TECH
Malicious group determination method and device, electronic equipment and storage medium
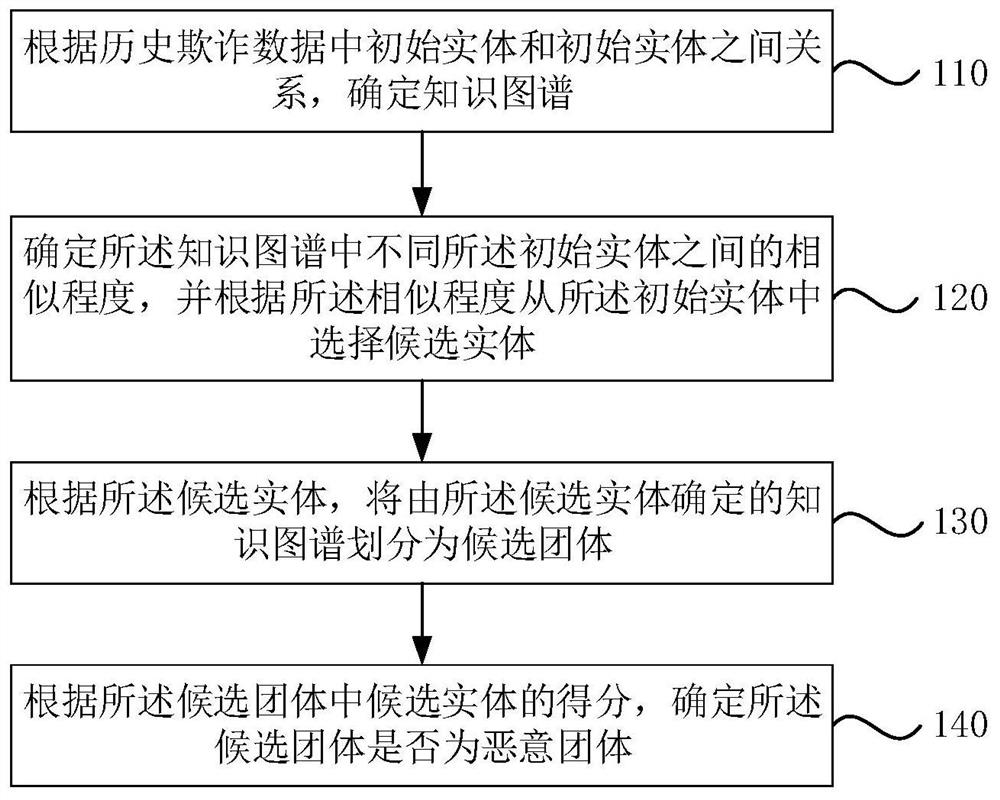
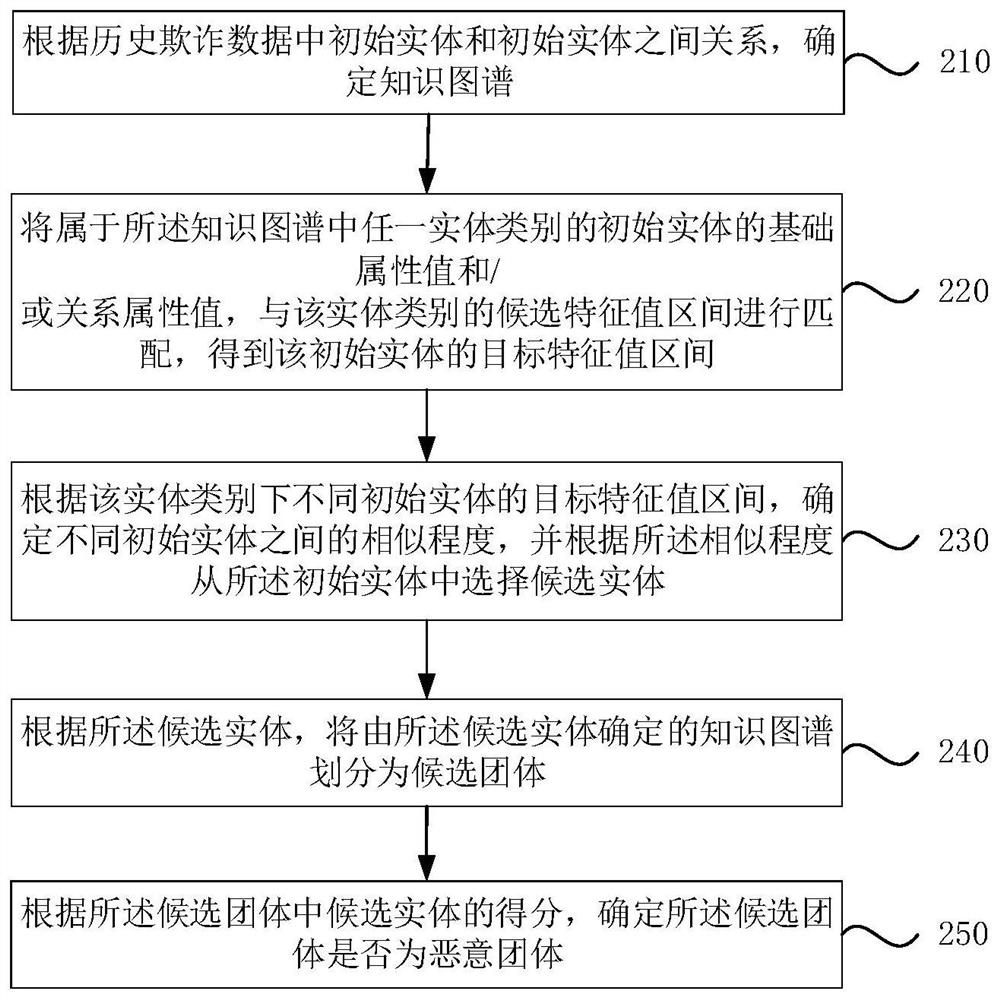
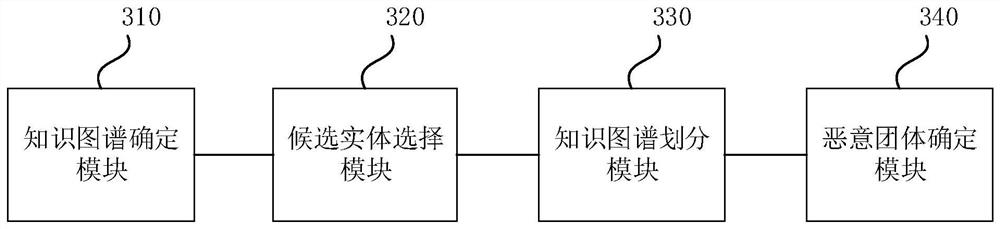
PendingCN112163096AImprove determination efficiencyImprove accuracyFinanceSpecial data processing applicationsRisk ControlKnowledge graph
The embodiment of the invention discloses a malicious group determination method and device, electronic equipment and a storage medium. The method comprises the steps of determining a knowledge graphaccording to a relationship between initial entities in historical fraud data; determining the similarity degree between different initial entities in the knowledge graph, and selecting candidate entities from the initial entities according to the similarity degree; according to the candidate entities, dividing the knowledge graph determined by the candidate entities into candidate groups; and determining whether the candidate group is a malicious group or not according to the score of the candidate entity in the candidate group. By running the technical scheme provided by the embodiment of the invention, the problems that a single-dimensional risk control strategy is difficult to acquire malicious gang behaviors in multiple directions, the occurrence time of the malicious gang behaviors is short, and malicious gangs are difficult to effectively discover and deploy the strategy in a short time can be solved, and the risk control efficiency is improved. The effect of improving the efficiency and accuracy of malicious group determination is achieved.
Owner:CHINA CONSTRUCTION BANK
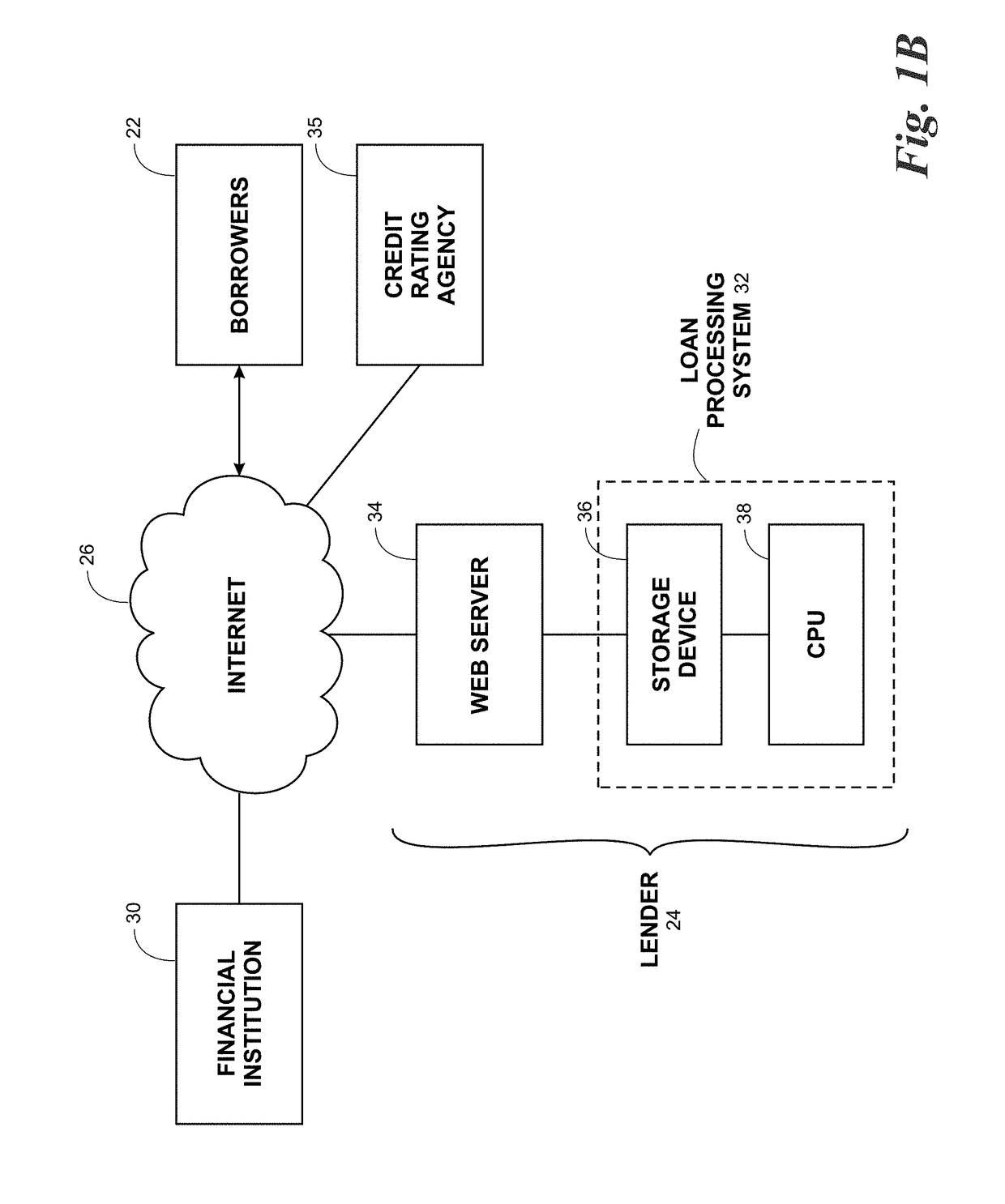
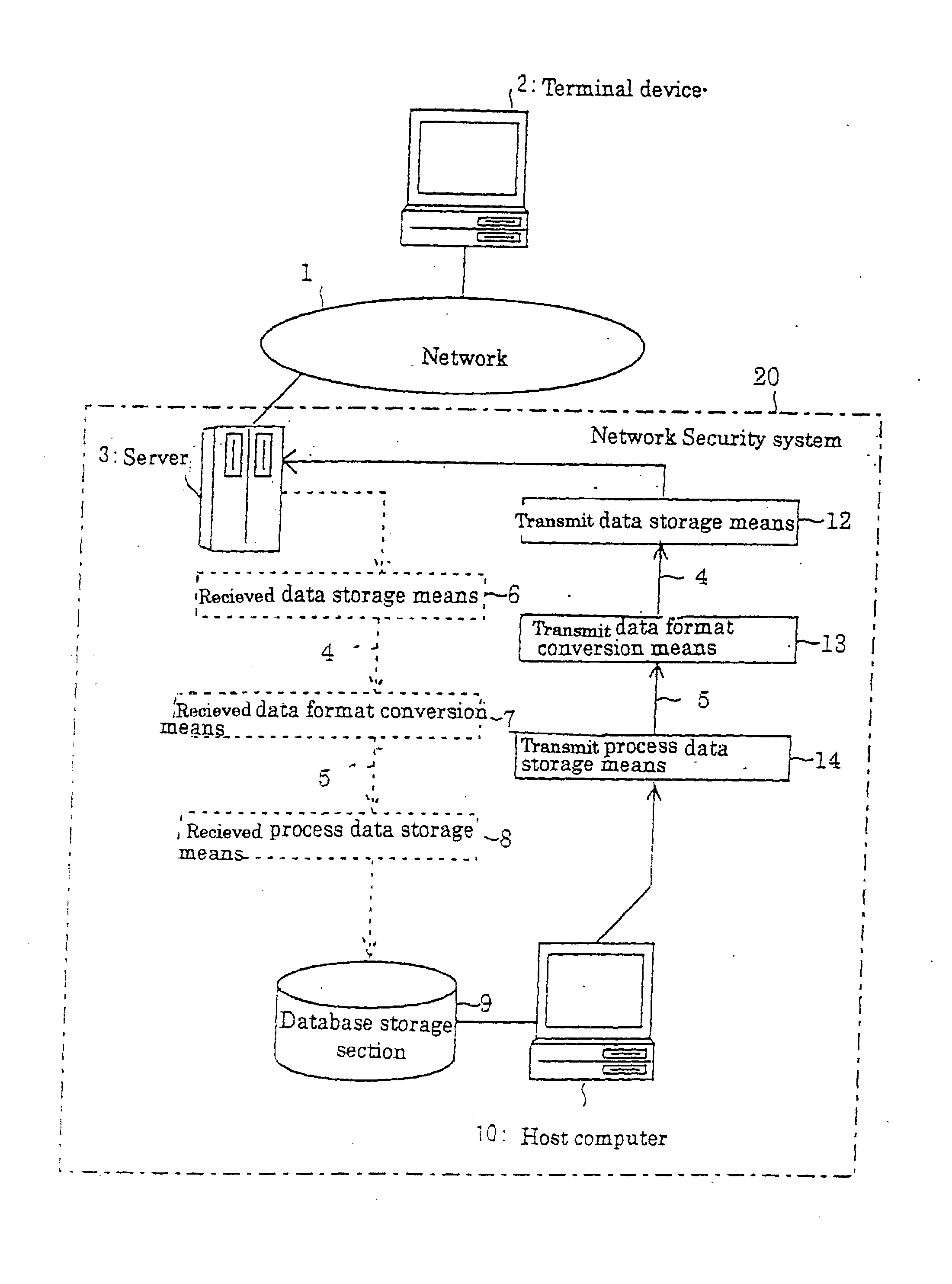
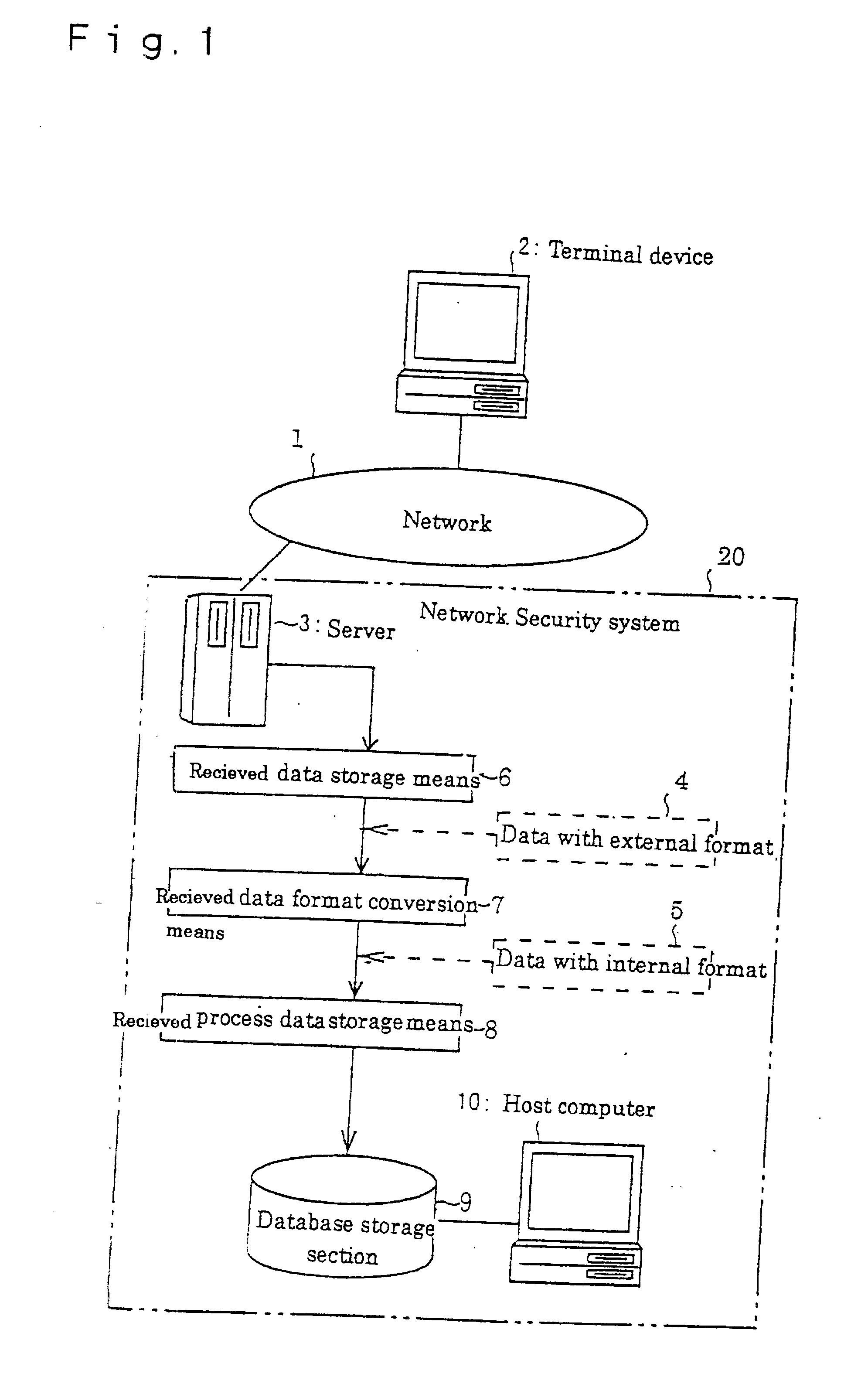
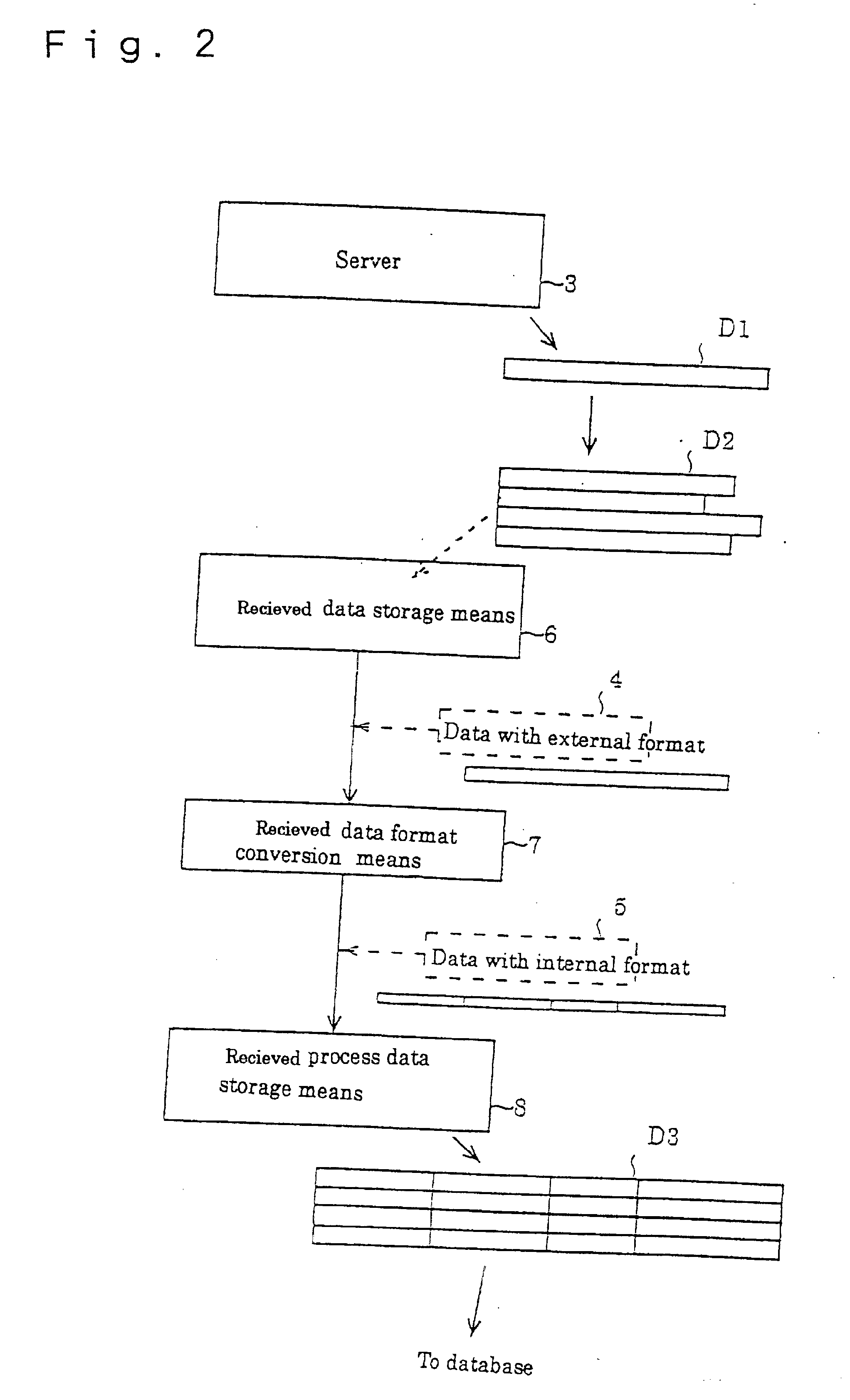
Network security system
InactiveUS20020124186A1Digital computer detailsUnauthorized memory use protectionNetwork security policyData format
ordering information is received by the server 3 through the network 1, when the order is placed by a user. The received data storage means 6 stores data with an external format 4 the server received. The received data format conversion means 7 converts data with an external format 4 stored in the received data storage means 6 to data with an internal format 5, and must be stored in the received process data storage means 8. The host computer 10 administrates the orders using the data with the internal format 5 stored in the received process data storage means. By the construction stated above, fraudulent data can be eliminated as the received data format conversion means 7 can convert data with an external format 4 to data with reliable internal format 5.
Owner:SEIKO EPSON CORP +1
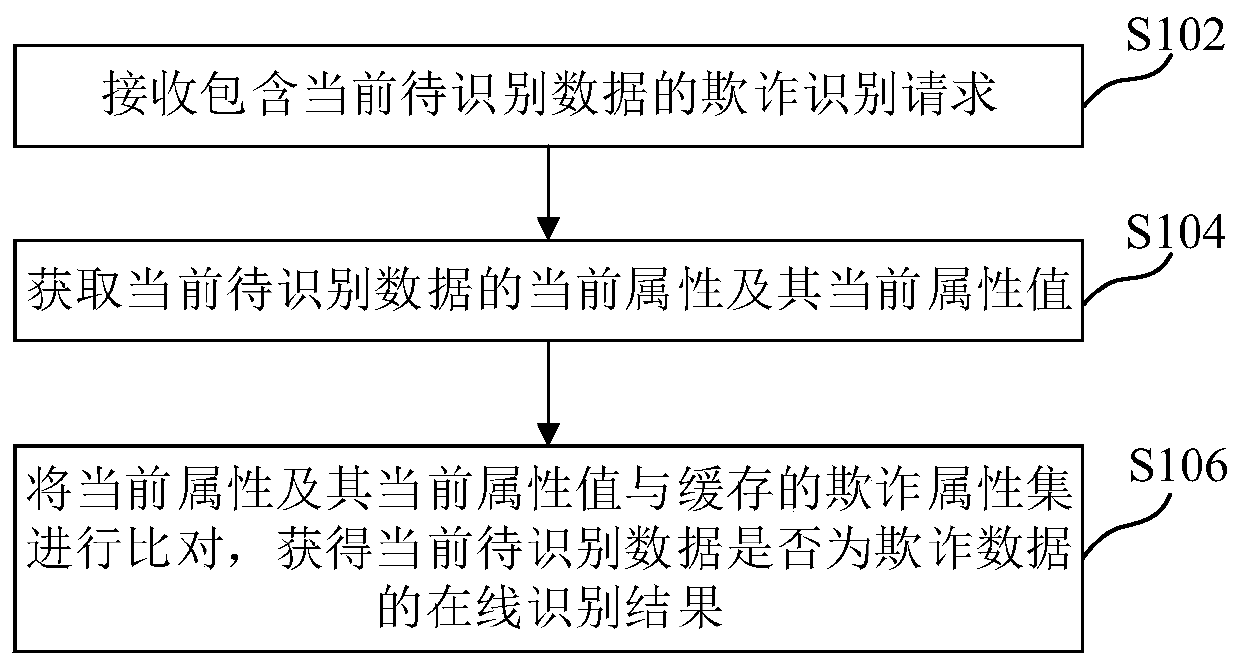
Online fraud identification method and device, medium and electronic equipment
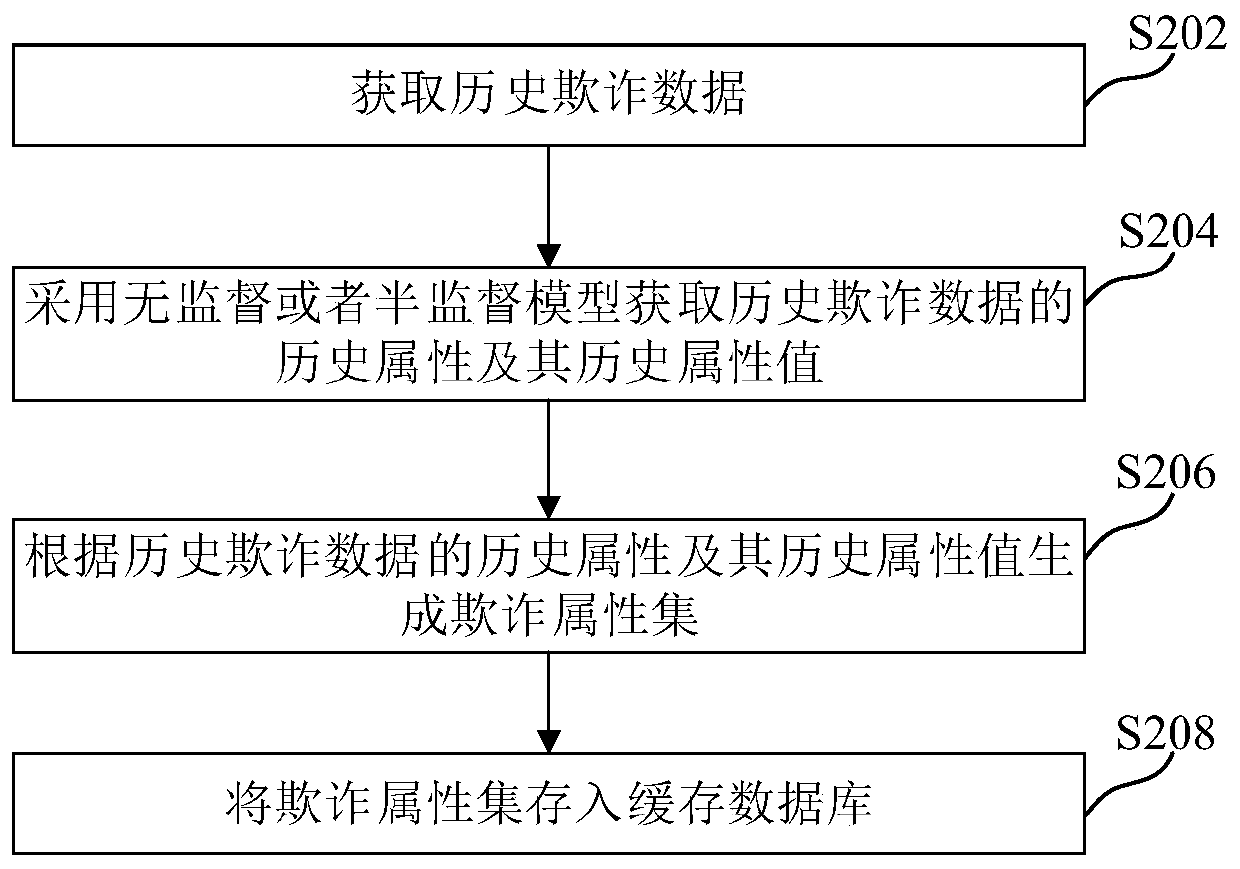
ActiveCN110322254ASimple and convenient online fraud detectionMachine learningCommerceData miningFraudulent Data
The embodiment of the invention provides an online fraud identification method and device, a computer readable storage medium and electronic equipment, and relates to the technical field of computers,and the method comprises the steps: receiving a fraud identification request containing current to-be-identified data; obtaining a current attribute and a current attribute value of the current to-be-identified data; and comparing the current attribute and the current attribute value with a cached fraudulent attribute set to obtain an online identification result whether the current to-be-identified data is fraudulent data or not. In the technical scheme of the embodiment of the invention, the current attribute of the current to-be-identified data and the current attribute value of the current to-be-identified data are acquired and then compared with the cached fraud attribute set, so that fraud identification of the current to-be-identified data is realized, and online fraud identification can be simply and conveniently carried out without changing a modulo graph relationship network.
Owner:TONGDUN HLDG CO LTD
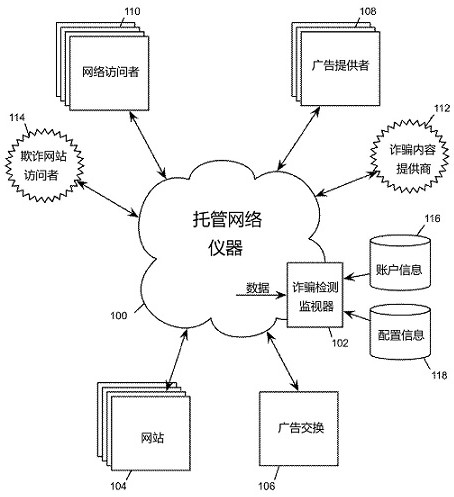
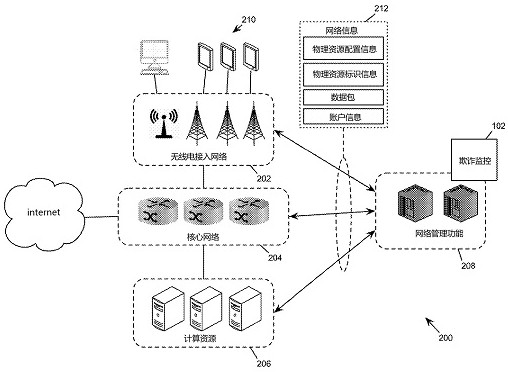
Fraud monitoring program
A fraud monitoring procedure in a management network is provided. A fraud monitoring program uses meter data, configuration data, and account information of the network to detect fraudulent activitiesin the network, such as fraudulent advertisements or other types of fraudulent data traffic, including fraudulent responses (such as fraudulent clicks) to advertisers. A fraud monitor receives configuration data and identification data of the network physical resources. The fraud monitor receives instrument data of data packet flow in the network. The fraud monitoring program receives account information of a network user. The fraud monitor analyzes the instrumentation data to detect the violation of a fraud detection policy that prevents malicious or fraudulent online advertising campaign based on the configuration data, the identification data, or the account information.
Owner:詹春婷
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com