Patents
Literature
197results about How to "Avoid calling" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
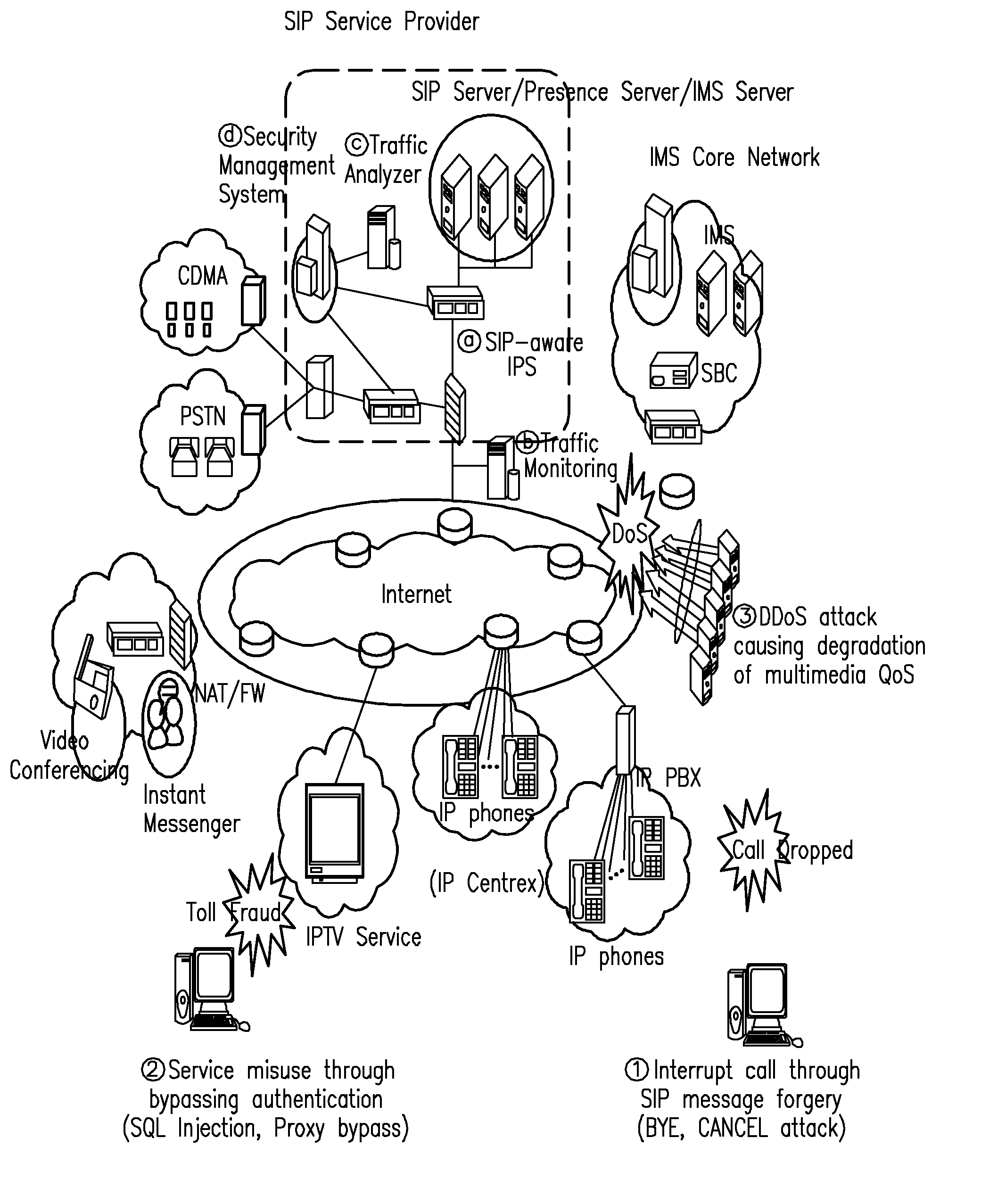
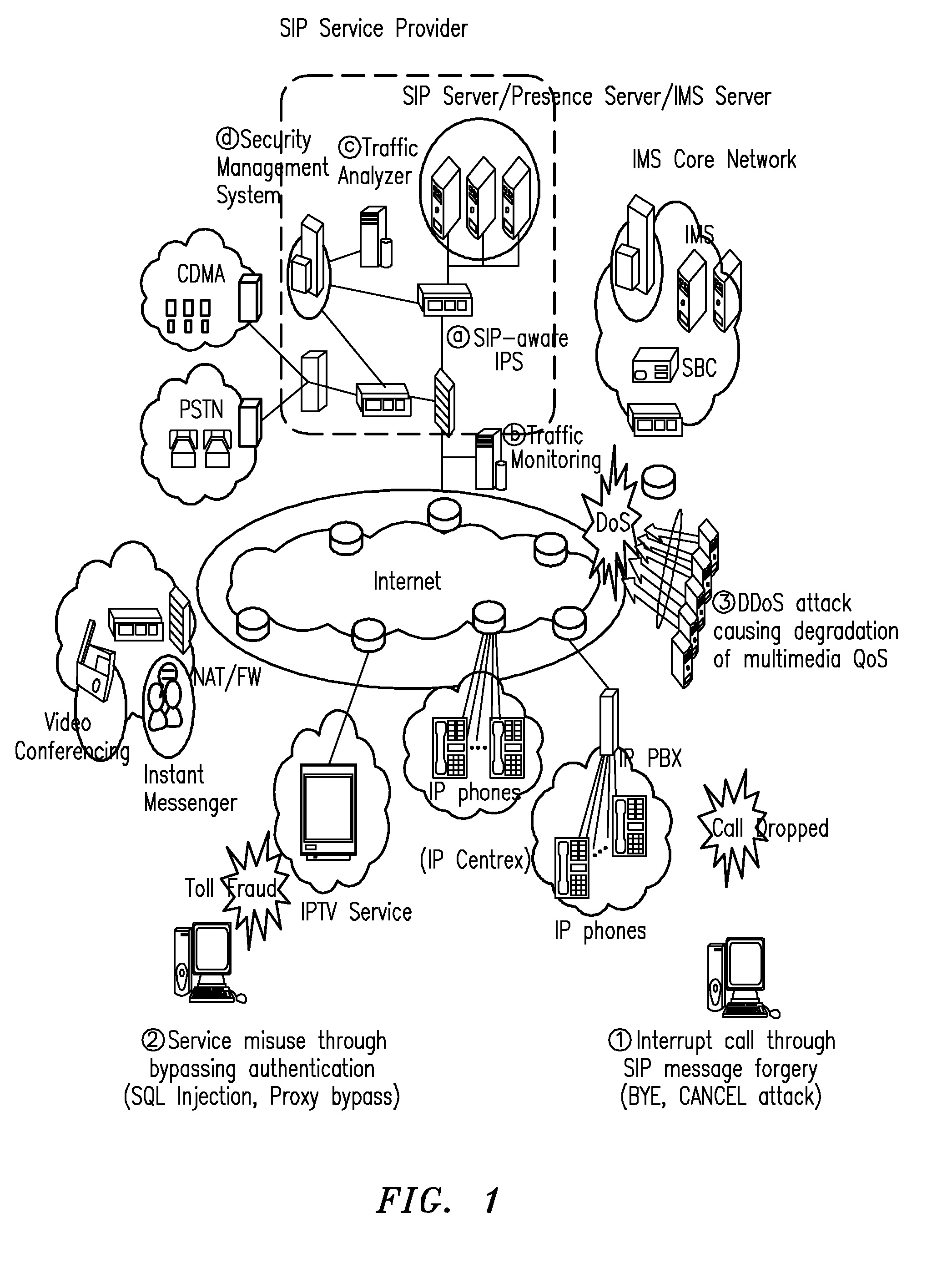
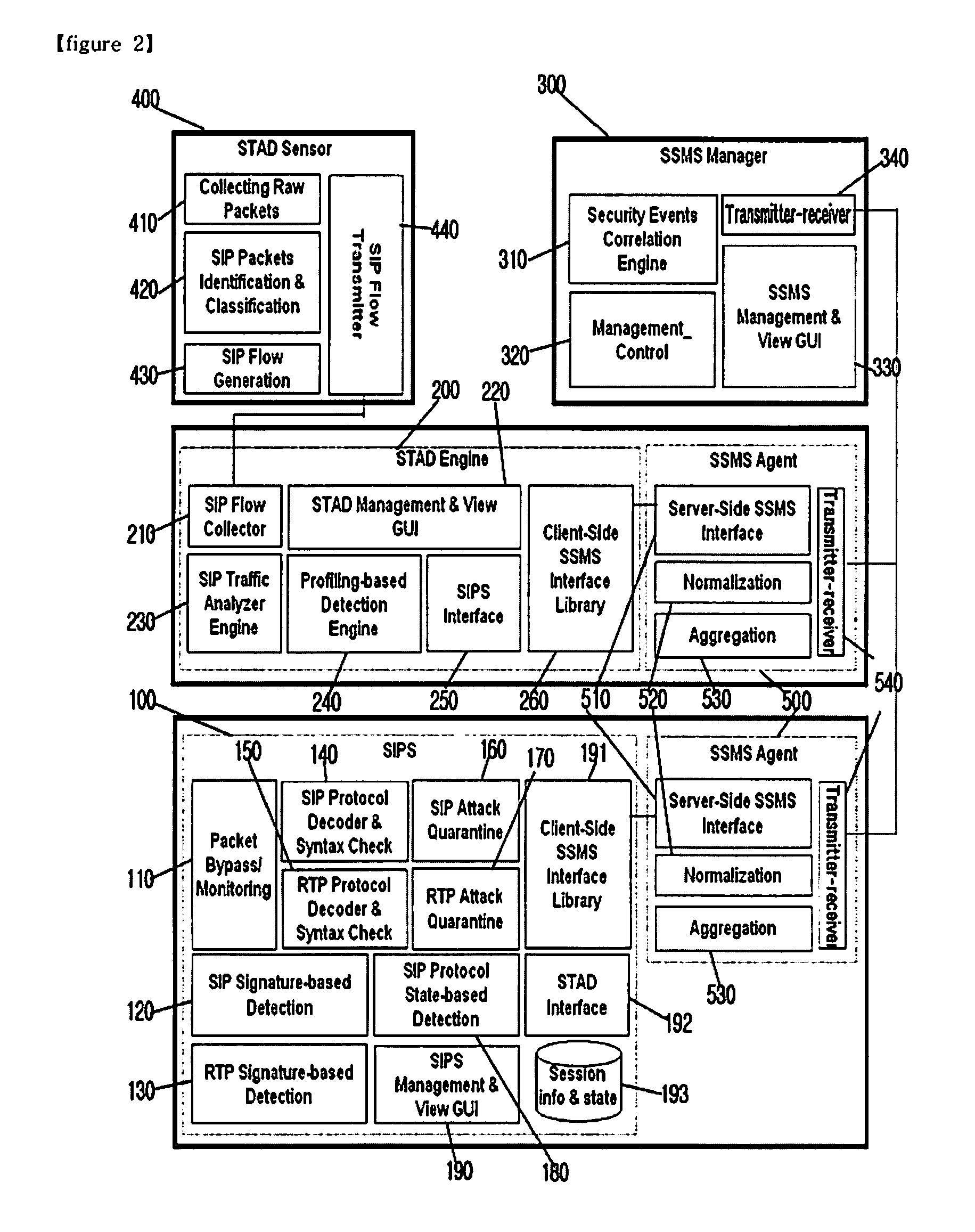
Sip intrusion detection and response architecture for protecting sip-based services
InactiveUS20100154057A1Without degrading qualityAvoid callingMemory loss protectionError detection/correctionTraffic capacitySession Initiation Protocol
The present invention relates to a Session Initiation Protocol (SIP) intrusion detection and response architecture for protecting SIP-based services, and more specifically, to an SIP intrusion detection and response architecture for protecting SIP-based services, in which SIP-based attacks of a new type can be coped with by detecting the SIP-based attacks and SIP traffic anomalies and managing an SIP-aware security device without degrading quality of multimedia, and signal and media channels can be examined through an SIP-aware intrusion prevention system (IPS) for the purpose of preventing an attacker from hindering a call through manipulation of an SIP message and session-hijacking among legitimate users and attempting a toll fraud by detouring authentication.
Owner:KOREA INTERNET & SECURITY AGENCY
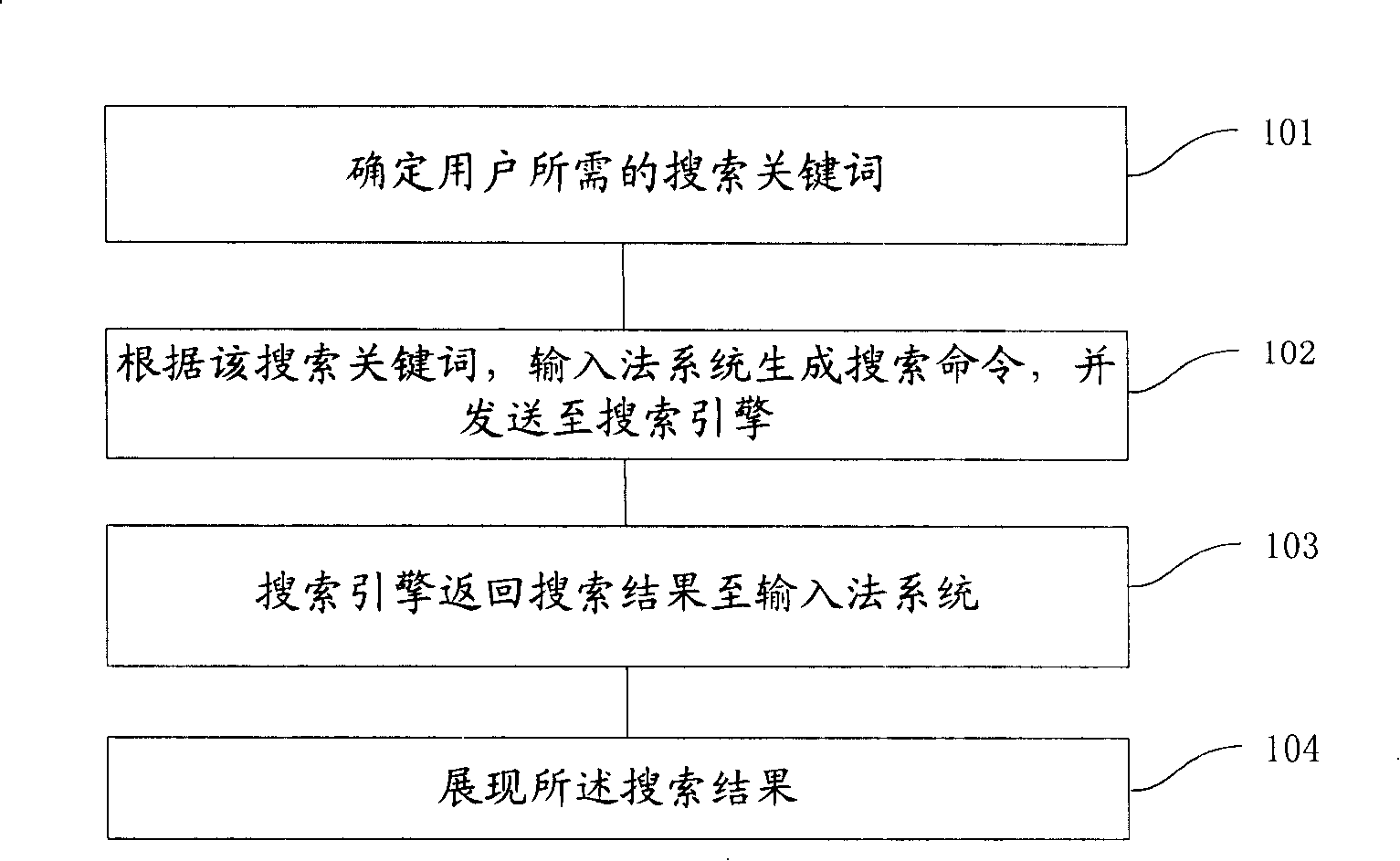
Convenient information search method, system and an input method system
ActiveCN101231636AImprove search efficiencyReduce stepsSpecial data processing applicationsInternet searchingInternet search engines
The invention provides a method and a system for searching information, as well as an input method system, wherein, the method for searching the information comprises the following steps that: a searching keyword required by a user is determined; according to the searching keyword, the input method system generates a searching command, which is sent out to a searching engine; the searching enginereturns the searching result to the input method system; the searching result is displayed. The invention can greatly improve the searching efficiency, reduce the operation steps of the user, and avoid the invalid data exchange and the invalid data processing. For some simple searching results, the invention can also directly call the display of an affiliated window or candidate word window, thereby a browse is avoided to be called, thus saving the resources of the system and calculating the sources. The invention is applicable to various internet searching engines as well as various local searching engines, and is also applicable to various searching tools or searching websites.
Owner:BEIJING SOGOU TECHNOLOGY DEVELOPMENT CO LTD
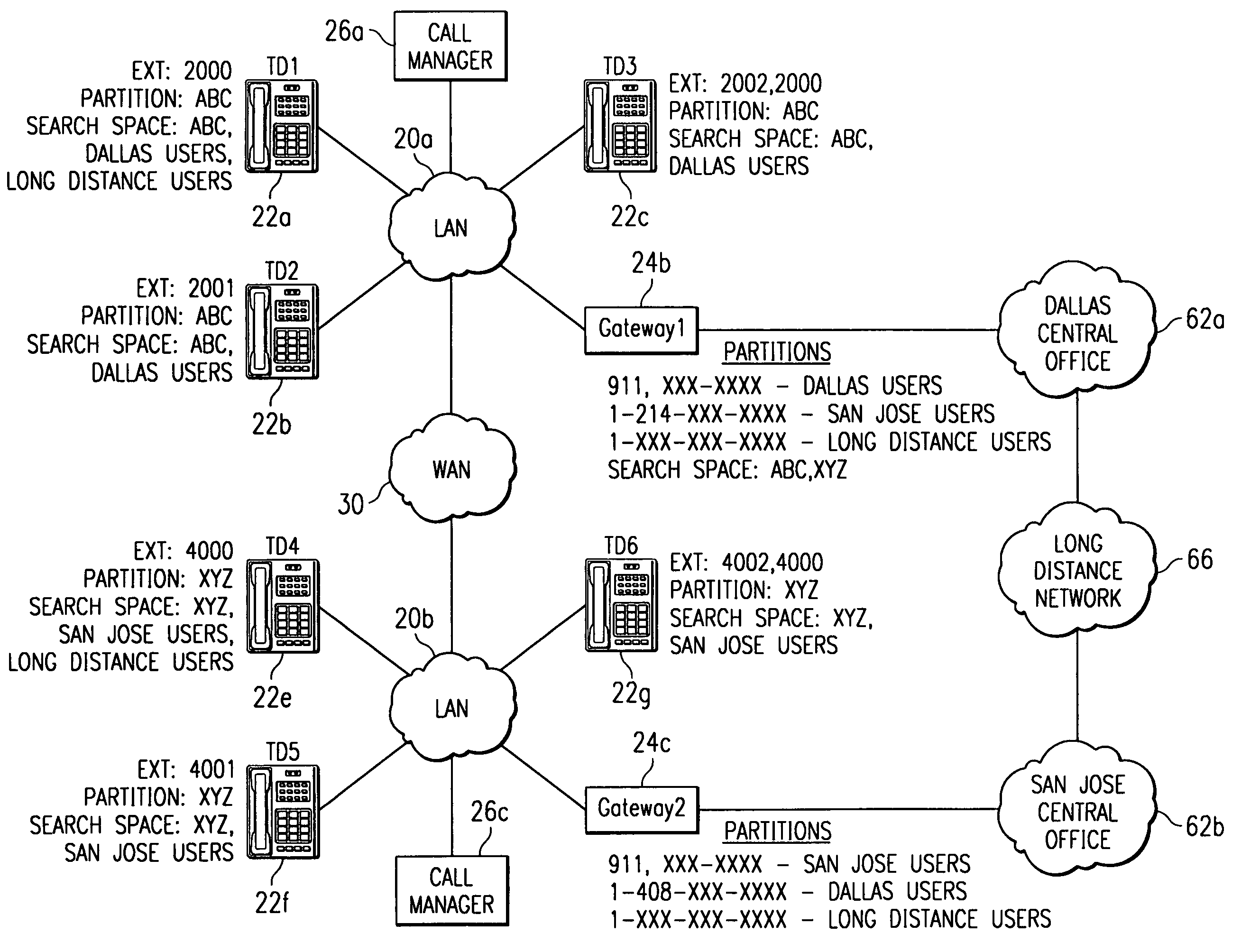
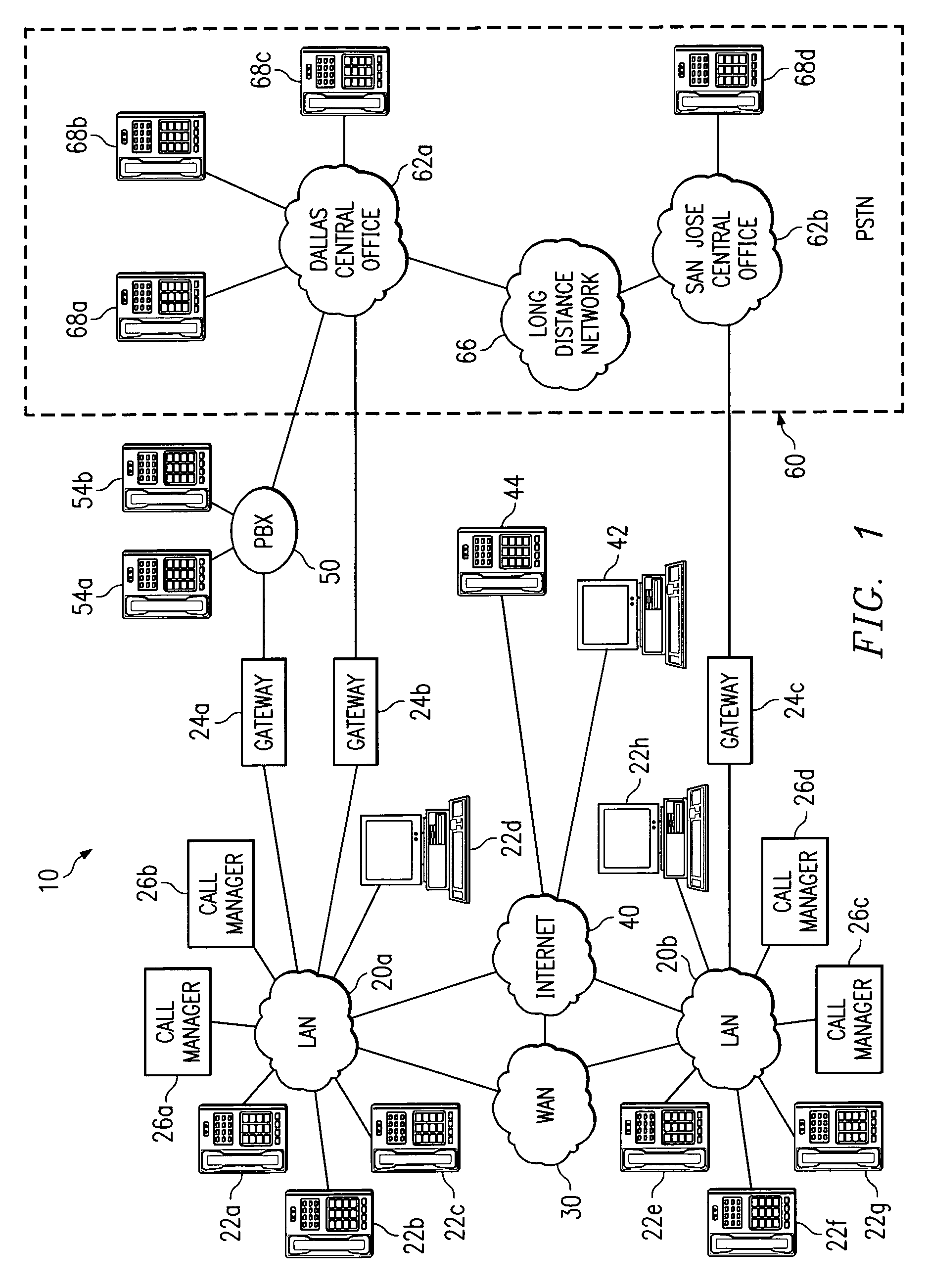
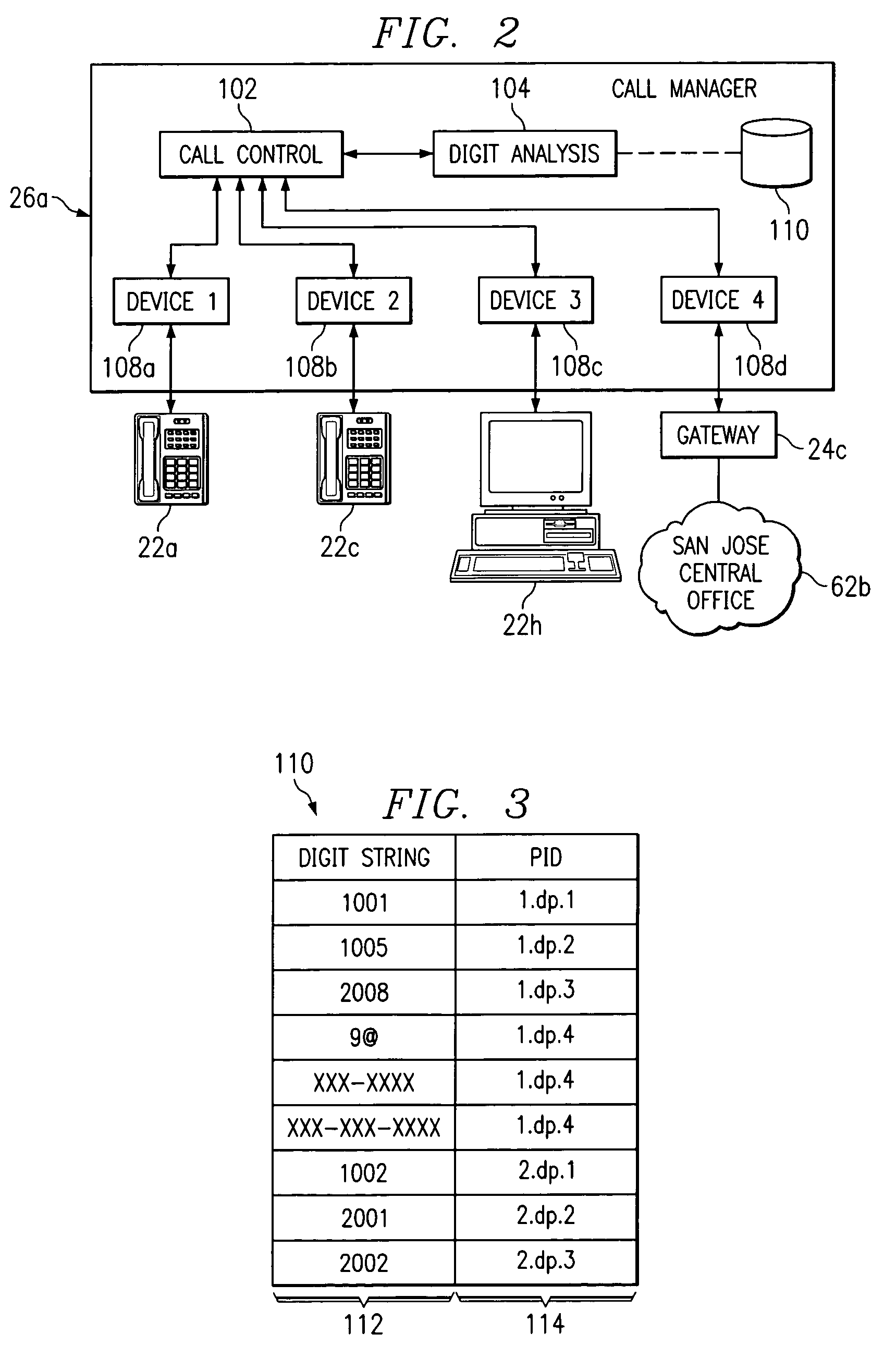
System and method for routing calls using dialing partitions
InactiveUS7359368B1Eliminates and reduces disadvantageEliminates and reduces and problemData switching by path configurationNetwork connectionsTelecommunicationsCall management
A method of routing calls using dialing partitions includes receiving a call request at a first call manager from a first device coupled to a packet-based network. The call request includes a telephone number that is associated with a second device coupled to the packet-based network. The method also includes accessing a dialing partition table based on a partition search space associated with the first device. The method further includes determining a routing target that is associated with one or more telephone numbers in the dialing partition table that match the telephone number in the call request. In addition, the method also includes communicating the call request to the routing target.
Owner:CISCO TECH INC
Automated programmable medication reminder and dispensing system
InactiveUS20060215495A1Avoid callingElectric indicationOral administration deviceComputer hardwareCare giver
An integrated medication reminder apparatus for providing audible reminder messages at predetermined times includes a clock means for generating real time signals, a voice recorder / playback means for recording and playing voice reminder messages, a sleep-mode means for generating a communications signal for communication with a secondary communications device, and an acknowledgement means for generating acknowledgement signals. A controller receives the real time signals and communications signal, establishes communications with the secondary communications device, instructs the voice recorder / playback means to send and play the reminder messages at the secondary communications device at predetermined times, and initiates a phone call to a designated care-giver via a locally connected telephone, in the absence of an acknowledgement signal after a voice reminder message has been played, and optionally, if removable a pill box of a pill dispenser coupled to the reminder apparatus is not removed and reinserted in a timely manner.
Owner:SAFETY RESPONSE SYST
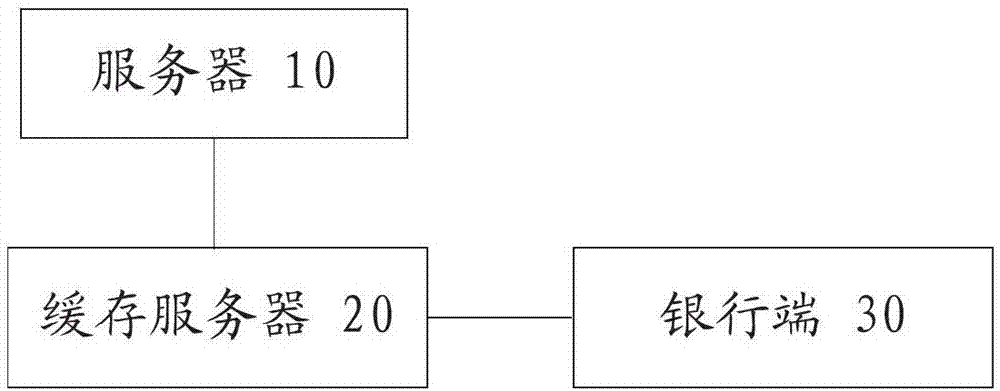
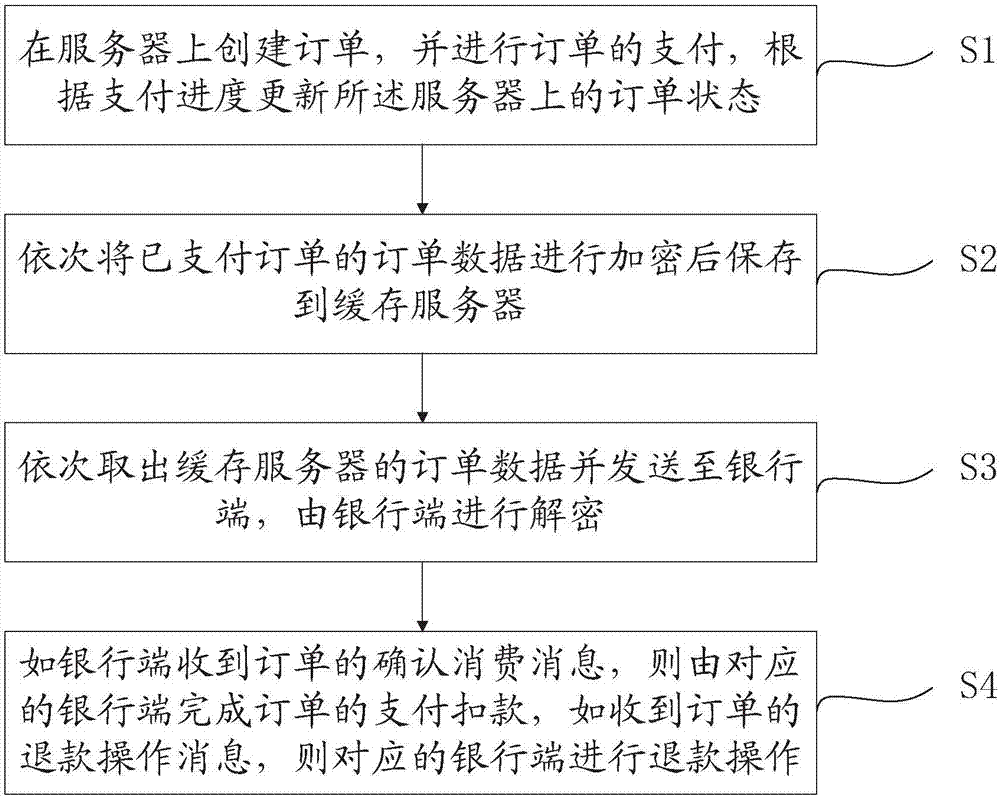
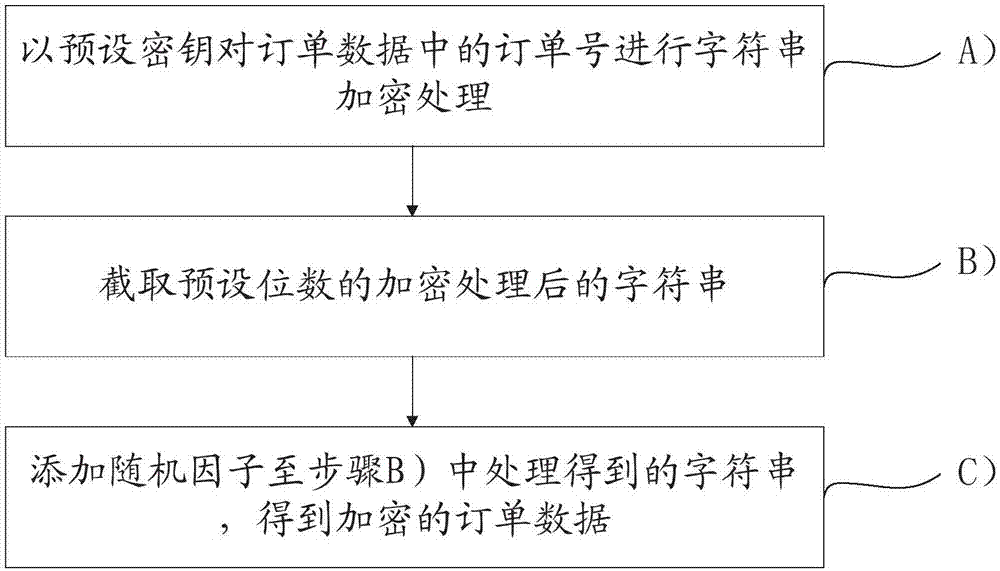
Service consumption payment information processing method and system
InactiveCN106204000AAvoid callingQuick call handlingPayment architectureInformation processingPayment
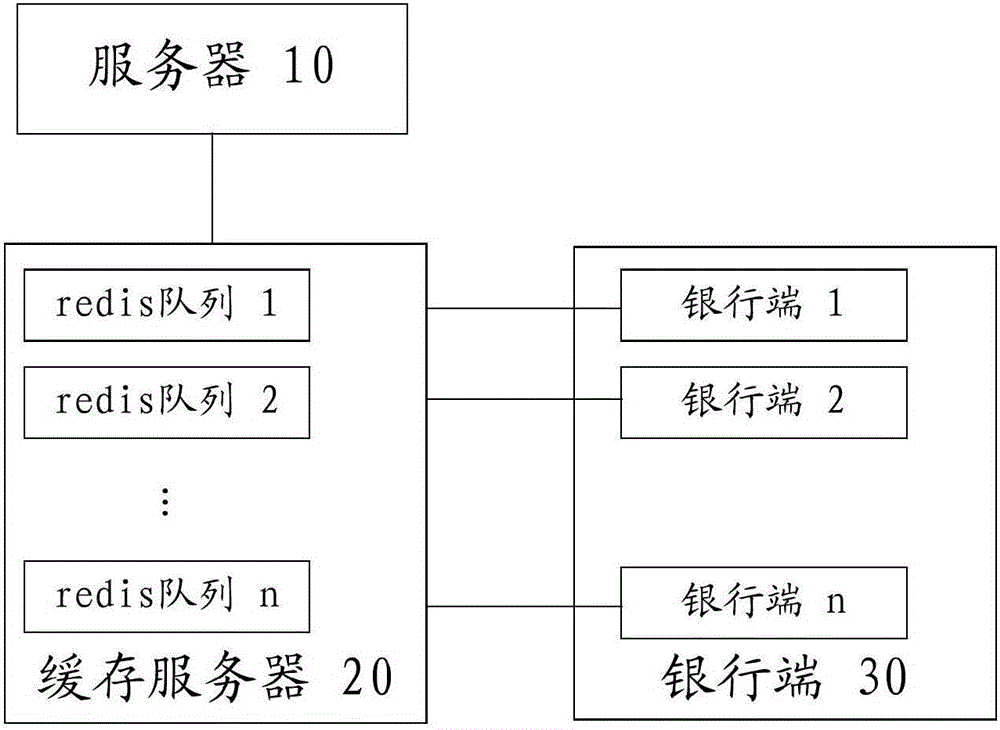
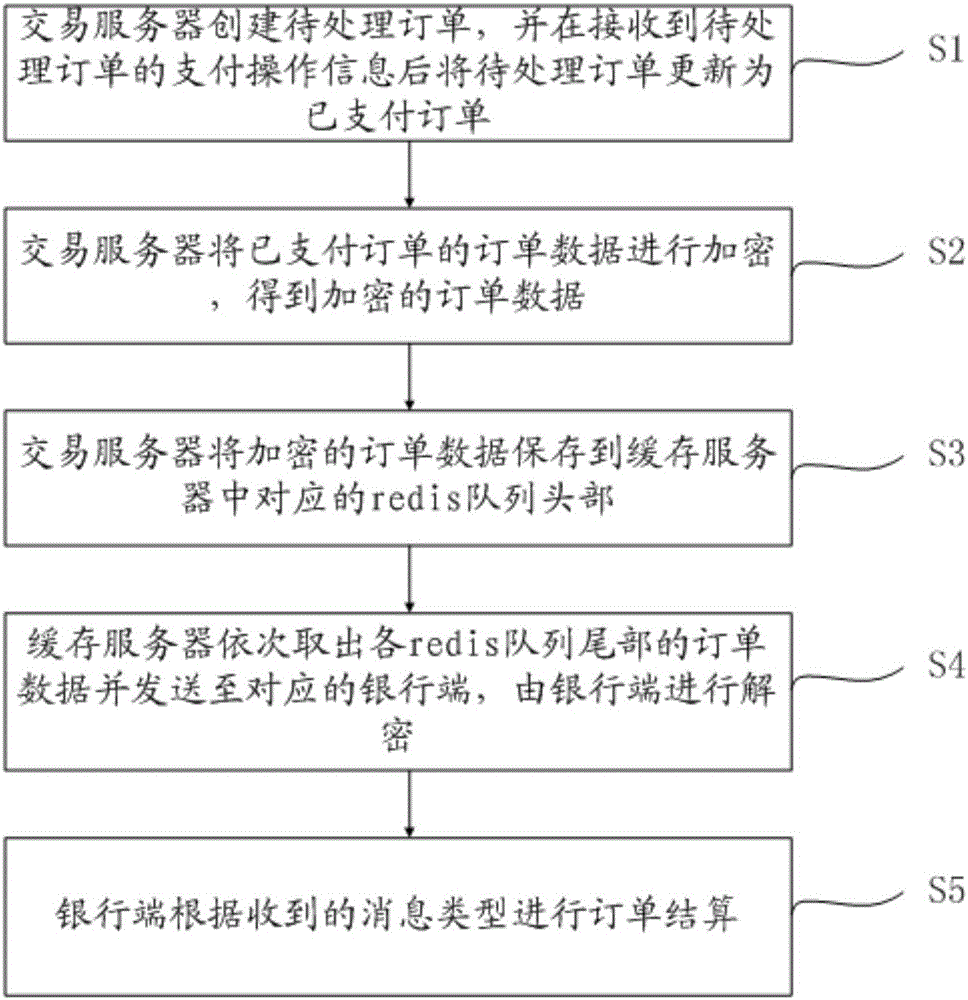
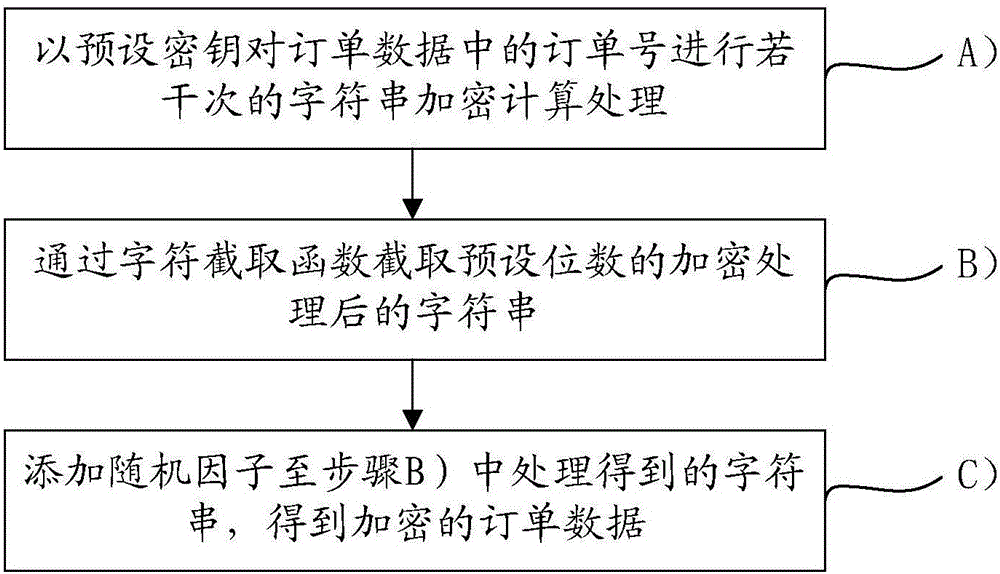
The invention provides a service consumption payment information processing method and system. The method includes a step S1 that a transaction server creates an order to processed after receiving a purchase operation information, and updates the order to processed as a paid order after receiving payment operation information; a step S2 that the transaction server encrypts order data of the paid order and obtains the encrypted order data; a step S3 that the transaction server saves the encrypted order data to a head portion of a redis queue corresponding to a bank end for completing the order payment in a cache server; a step S4 that the cache server takes out order data at the tail portion of each redis queue in sequence and transmits to the corresponding bank end for decryption; and a step S5 that the bank end settles the order according to the type of a received message. The method and system cache the order data through the cache server, so that the bank end can process the order data sequentially, and the pressure of the transaction server to process and query the database is reduced.
Owner:康存乐付保数据科技(上海)有限公司
Operating system allowing running of real-time application programs, control method therefor, and method of loading dynamic link libraries
InactiveUS20050144608A1Avoid callingResource allocationProgram loading/initiatingOperational systemExternal reference
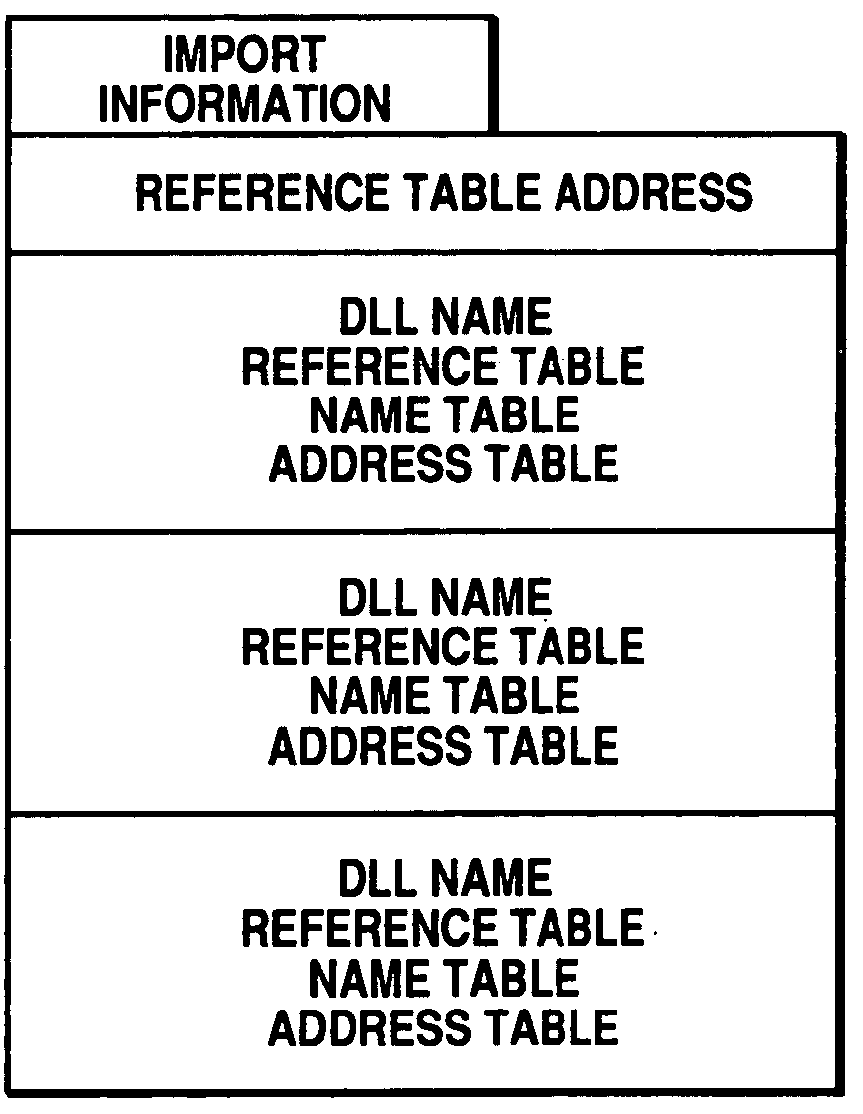
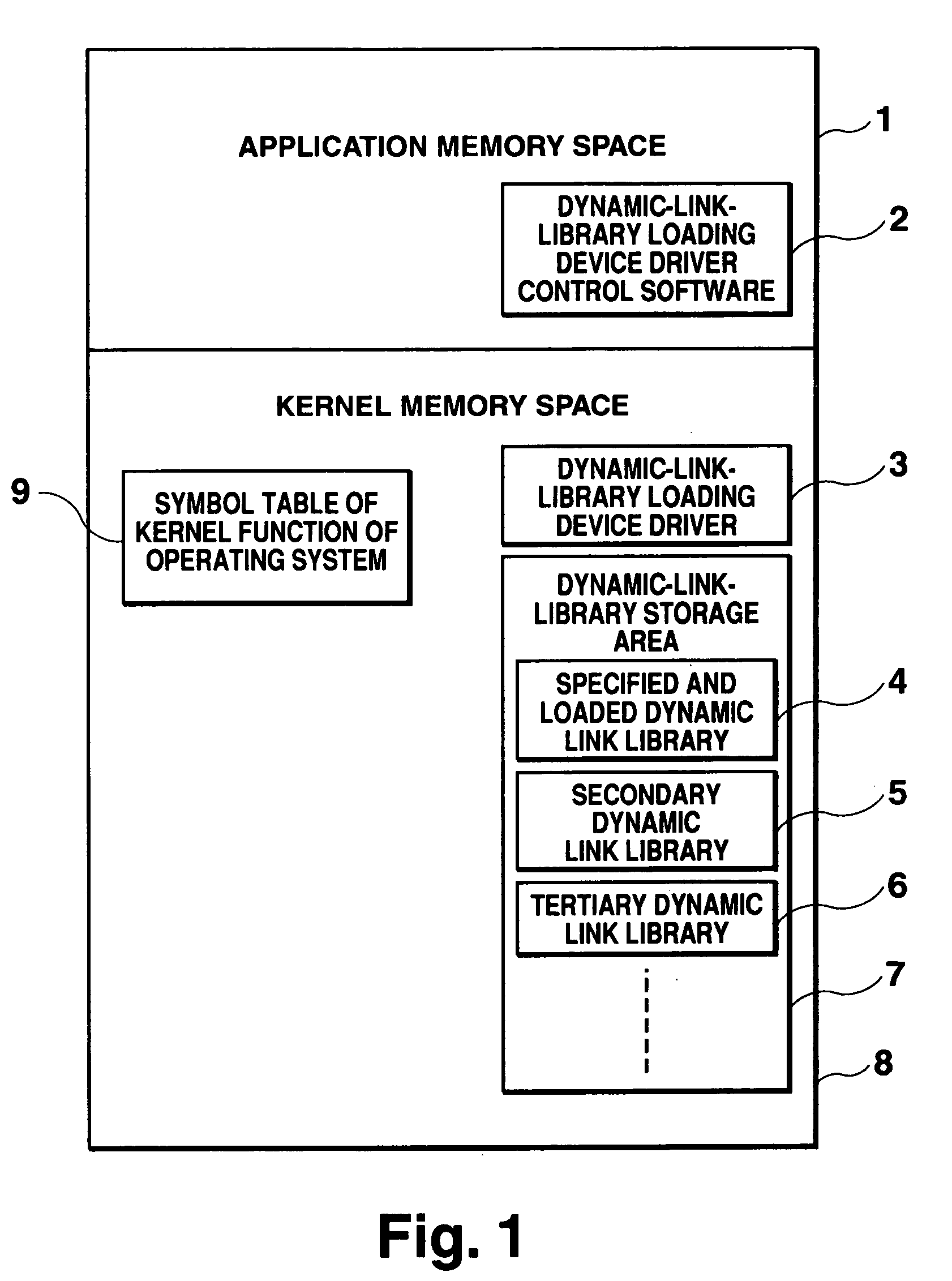
The present invention provides a device driver that loads dynamic link libraries, which include the RTOS function and real-time applications, into the kernel space and starts the dynamic link libraries. The RTOS function and real-time applications are configured as dynamic link libraries. The device driver loads into the kernel space a dynamic link library and other dynamic link libraries referenced by the dynamic link library, adjusts address information on the basis of relocation information, resolves external references, acquires symbol information indicating a start function, and starts the start function.
Owner:OKUMA CORP
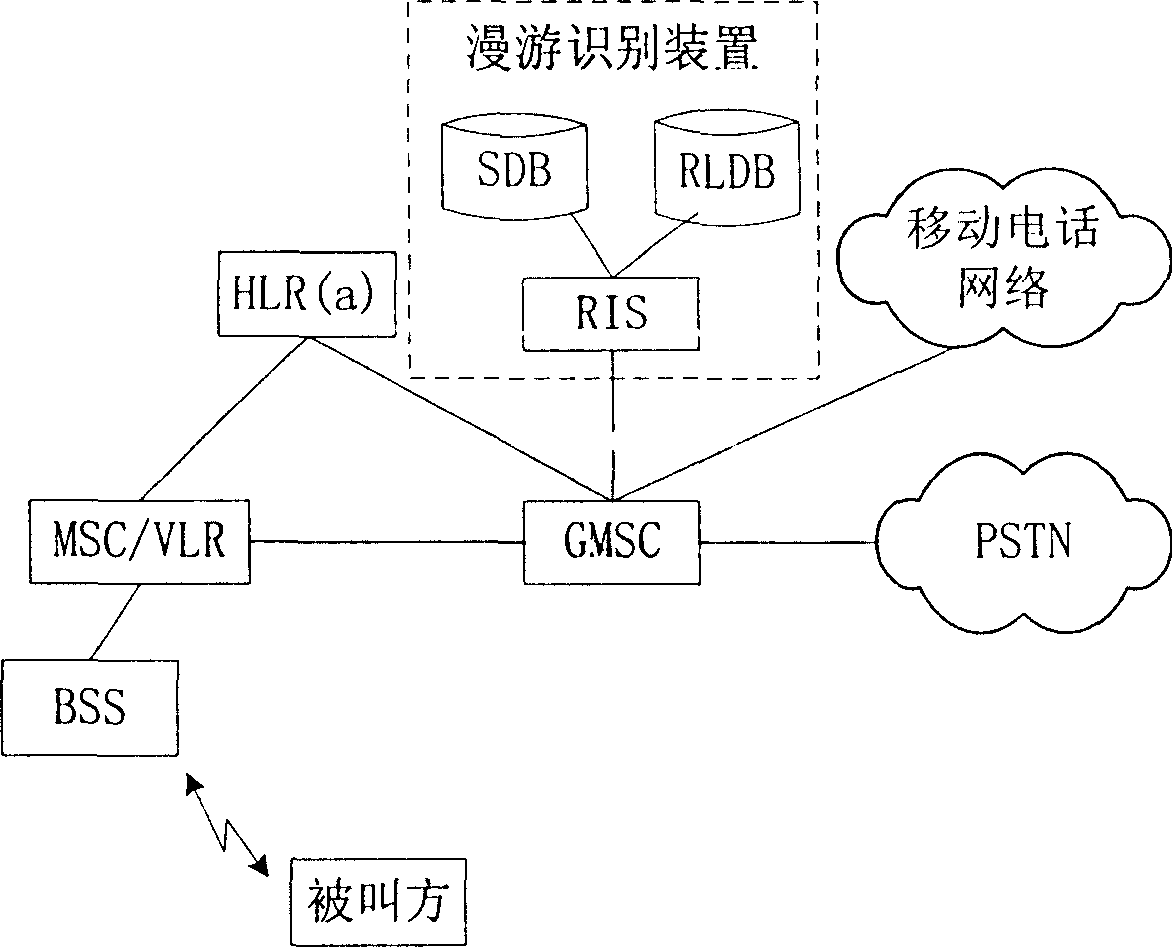
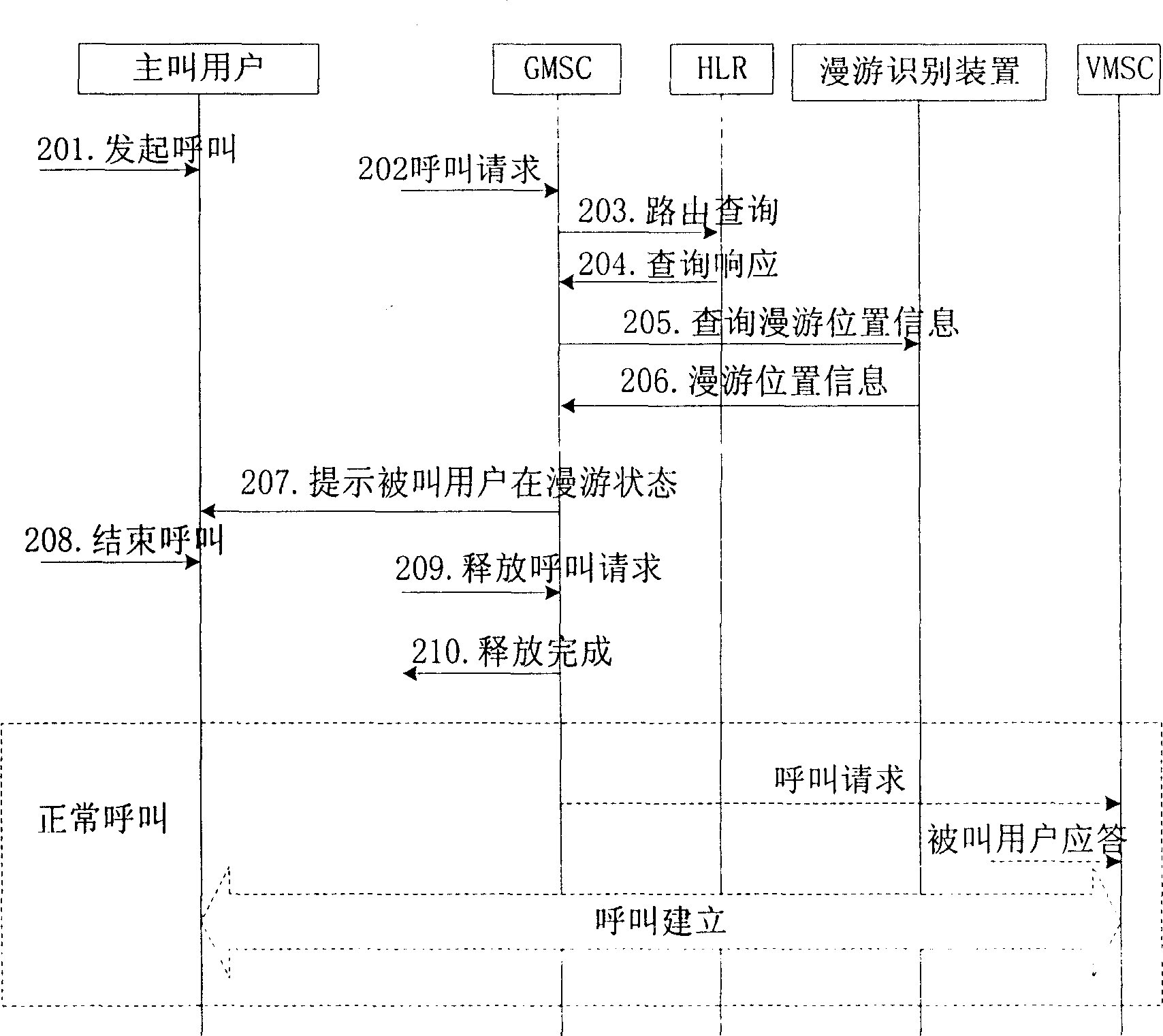
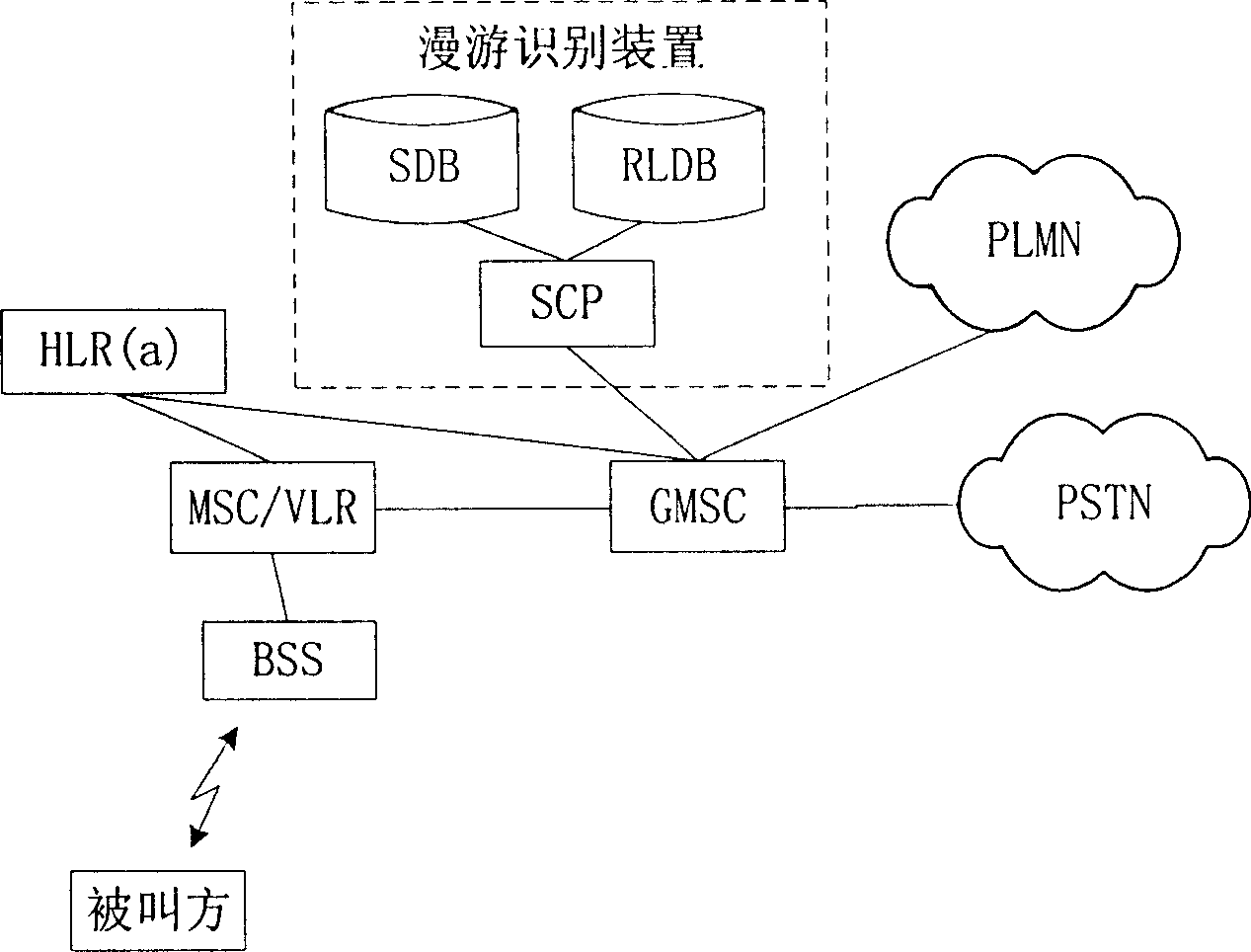
Method and system for indicating roam status of called party
InactiveCN1917692AAvoid callingSave money on roaming callsRadio/inductive link selection arrangementsAutomatic exchangesTelecommunications
The method comprises: the calling side initiates a call to the called side; the network side receives the call to the called side and decides if the called side is at roaming state; if yes, sending the information about the called side being at roaming state to the calling side to prompt him, and when called side is at roaming state, determining the roaming area where the called side locates at; finally, adding the information describing the roaming position of called side into the roaming state information, and sending it to the calling side. The invention also reveals a system for indicating the roaming state of user.
Owner:HUAWEI TECH CO LTD
Media gate link right discriminating method
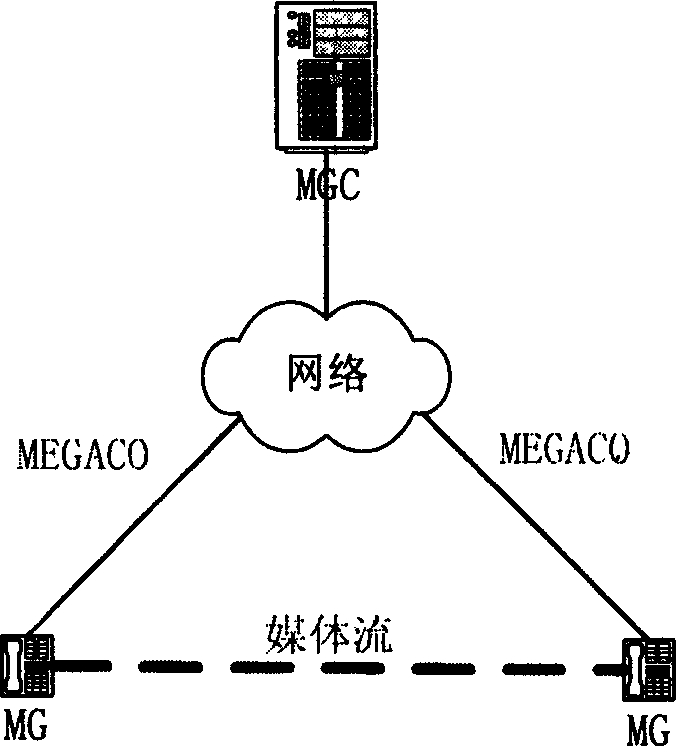
InactiveCN1581858AAvoid callingSolve the problem of illegal callsUser identity/authority verificationNetwork connectionsDigital signatureCall setup
The method includes following steps: initial cipher key is assigned for validating initial digital signature for both parties between media network gateway and media network gateway controller; media network gateway initiates registration signaling to media network gateway controller for registering together with parameters and digital signature for generating shared cipher key; media network gateway controller generates shared cipher key by using validated legal parameters and digital signature; the said controller sends generated parameters and digital signature and life time of shared cipher key setup through modifier command; media network gateway generates shared cipher key after validating validity of digital signature; in following each call and reply message, shared cipher key is utilized for signature and validating each other between media network gateway and media network gateway controller. Shared cipher key is updated regularly.
Owner:ZTE CORP
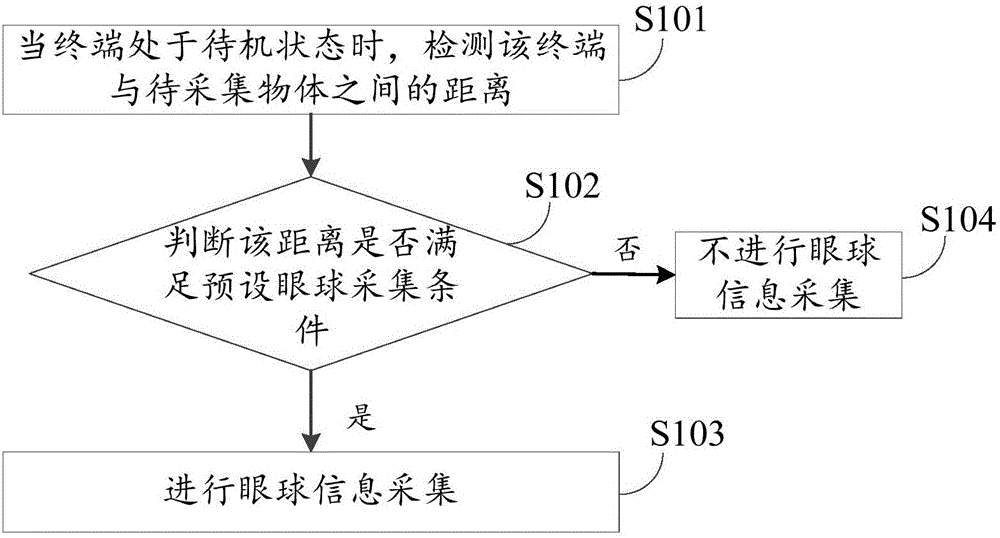
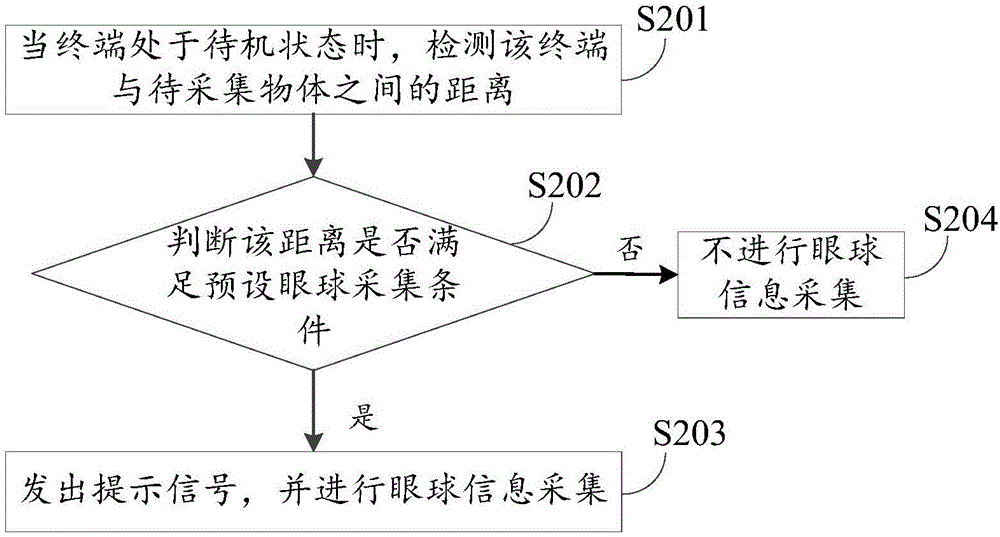
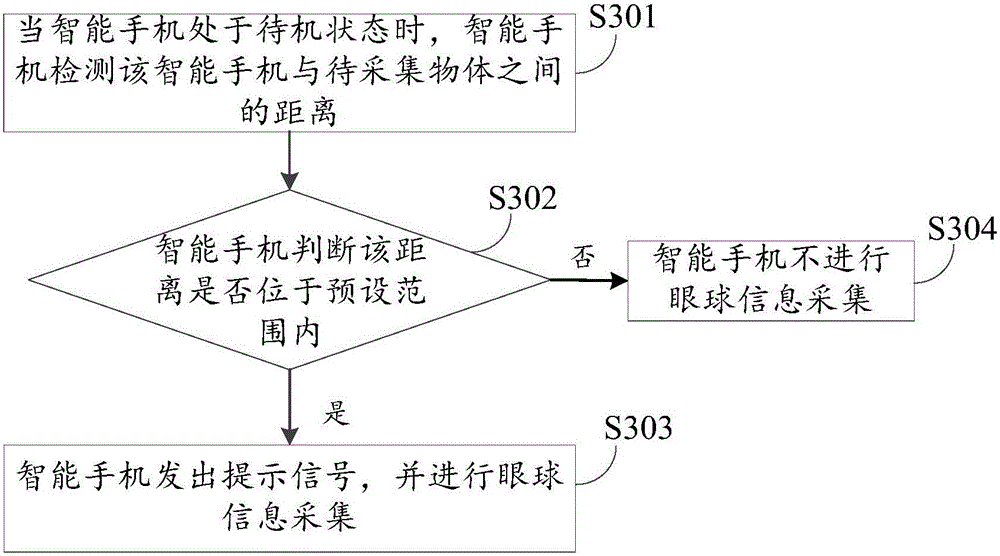
Acquisition method and device of eyeball information
InactiveCN105809139AReduce power consumptionAvoid callingAcquiring/recognising eyesPower supply for data processingComputer visionArtificial intelligence
The invention provides an acquisition method and device of eyeball information. The acquisition method of the eyeball information comprises the following steps: when a terminal is under a standby state, detecting a distance between the terminal and an object to be acquired, wherein the object to be acquired is positioned in the detectable range of the terminal; judging whether the distance meets a preset eyeball acquisition condition or not; and if a judgment result shows that the distance meets the preset eyeball acquisition condition, carrying out eyeball information acquisition. Since the acquisition method and device of the eyeball information detects the distance between the terminal and an object which is close to the terminal under the standby state to determine whether an infrared camera is started to carry out eyeball information acquisition, a phenomenon that the infrared camera is called all the time under the standby state can be avoided, and the power consumption of the terminal is lowered while an unlocking speed is improved.
Owner:GUANGDONG OPPO MOBILE TELECOMM CORP LTD
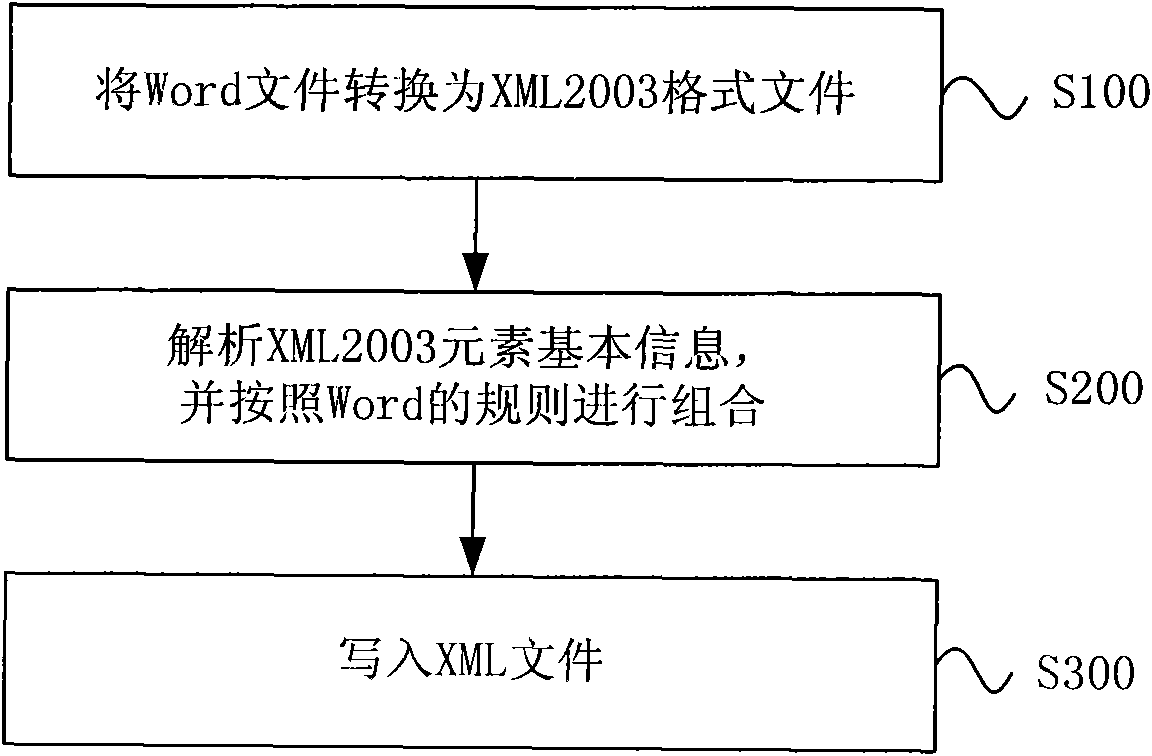
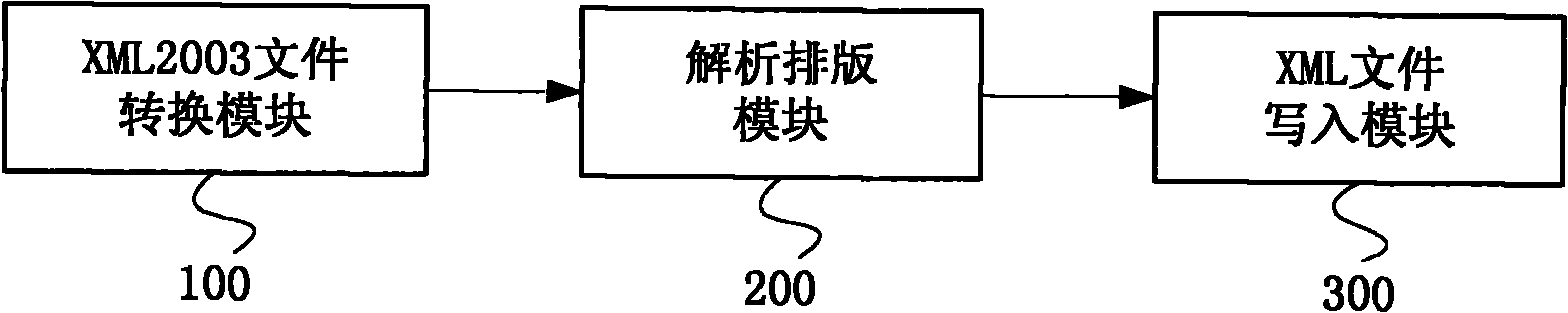
Method for analyzing Word file information and system thereof
InactiveCN101980183AAnalysis Efficient and StableAvoid callingSpecial data processing applicationsDocument preparationXML
The invention discloses a method for analyzing Word file information and a system thereof. The method comprises the following steps of: converting a Word file to be analyzed into an intermediate file of a document in a Word_XML2003 format; analyzing the basic information of elements in the document in the Word_XML2003 format; combining the information obtained from analyzing according to a rule of Word; and writing analyzed and combined objects into an XML file. Because the document in the Word_XML2003 format is used as the intermediate file and combination is performed according to the rule of the Word after analyzing the document in the Word_XML2003 format, attribute loss cannot be caused when complicated elements are analyzed, a Com interface is prevented from being called frequently, system resources are saved, the Word file information in all formats is analyzed highly effectively and stably, and the method is particularly suitable to be used when the Word file information of various editions need to be analyzed in batches.
Owner:WONDERSHARE TECH CO LTD
Payment information processing method and system and prepaid card processing method with performance bond insurance mechanism
InactiveCN107369012AAvoid callingQuick call processingPayment architectureInformation processingMessage queue
A prepaid card processing method with performance bond insurance mechanism includes a message queue subscription message is pushed to a settlement bank and complete order information corresponding to a prepaid card after payment of a consumer is received; in each consumption link, a merchant terminal sends consumption task list information to a third party processing platform, the third party processing platform acquires clearing amount through the task list ID and the clearing amount needs to be pushed to the settlement bank for fund settlement, and the order sum of a paid order is split into different channels. The prepaid card processing system is a whole set of information management integrated application software system solving a prepaid card performance bond insurance problem. Through deal by deal, person by person, process by process saving and feeding back of information of prepaid card issuing enterprises or merchants and seamless joint with an insurance company core service system, a third party payment mechanism fund payment system and a bank fund supervision system, application of the mechanism of prepaid card performance bond insurance is ensured.
Owner:康存乐付保数据科技(上海)有限公司
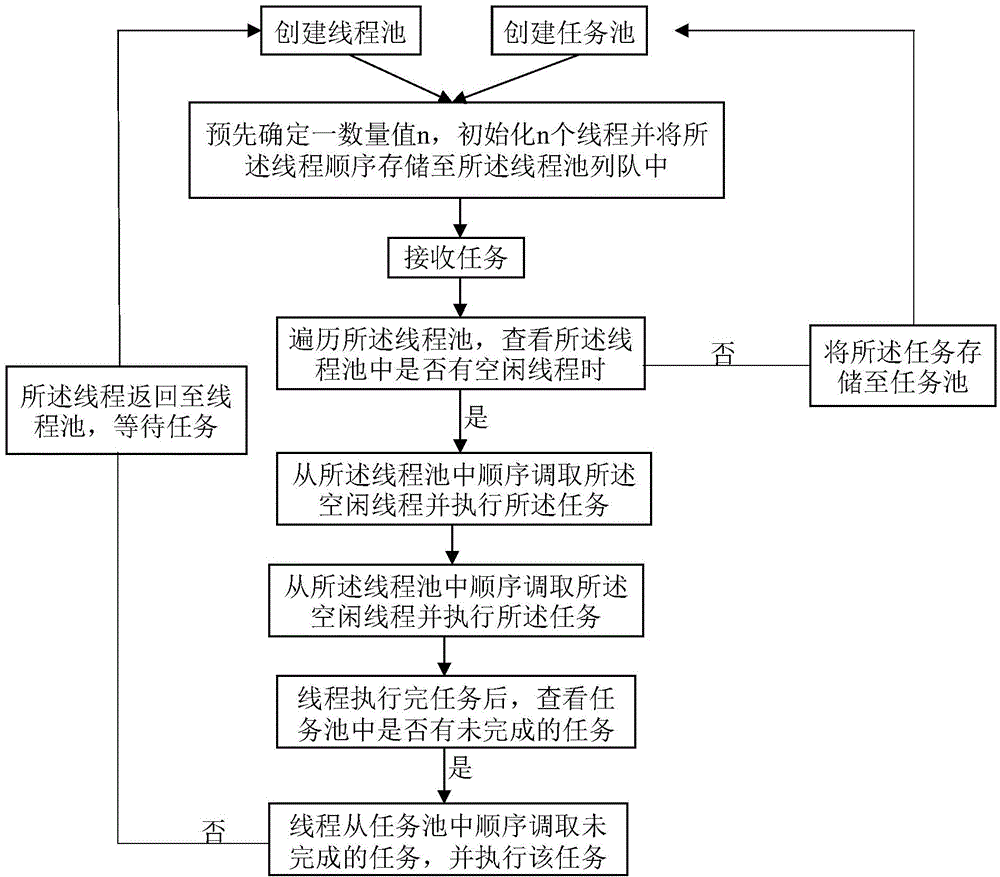
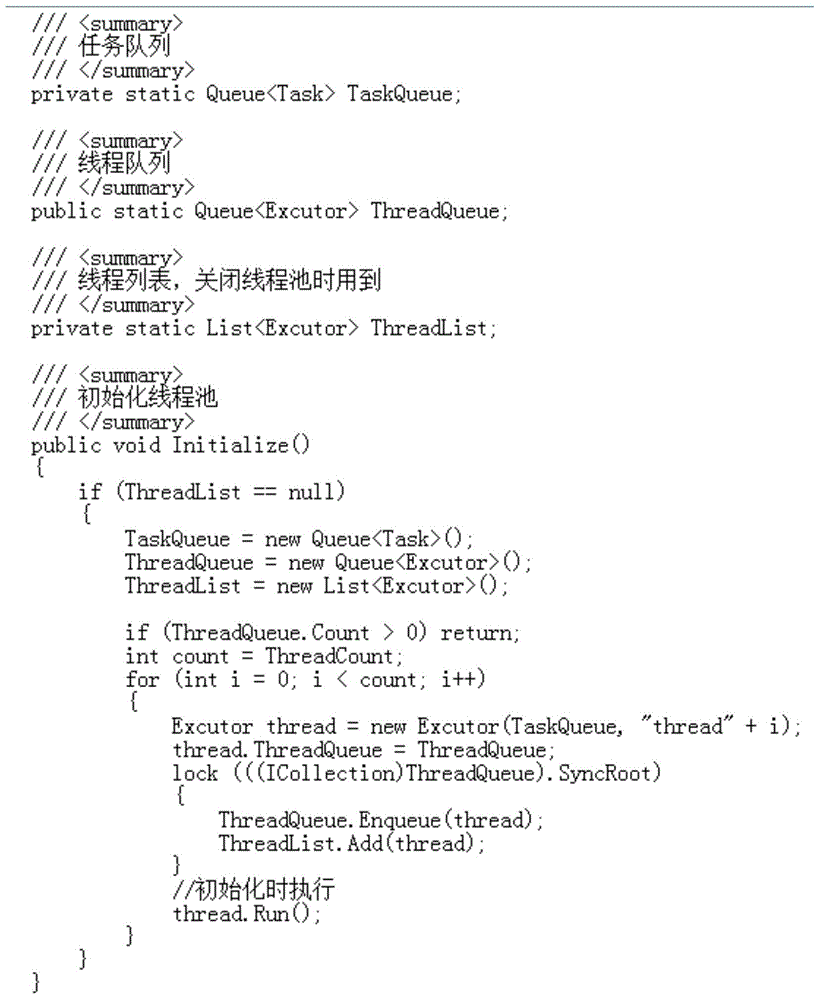
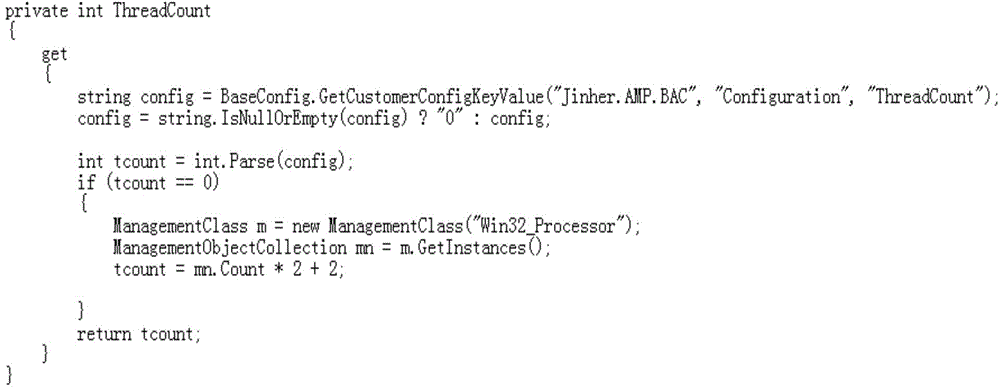
Task allocation method based on thread pool
The present invention provides a task allocation method based on a thread pool. The method comprises: S1, creating a thread pool and a task pool; S2, predetermining a numerical value n, initializing n threads and sequentially storing the threads into a queue of the thread pool; S3, after tasks are received, traversing the thread pool, and if idle threads exist in the thread pool, sequentially calling the idle threads from the thread pool and executing the tasks; and if no idle threads exist in the thread pool, sequentially storing the tasks into a queue of the task pool. The present invention provides a multi-thread task allocation method which can sufficiently utilize existing hardware resources, implements software multi-task parallel execution and can be repeatedly used for each task executor, solves the problems of operation performance, usability and the like of software, and avoids the problem of resource waste caused by creation calling and switching of threads.
Owner:BEIJING JINHER SOFTWARE
Method of transferring user state by using portable communication terminal short messege
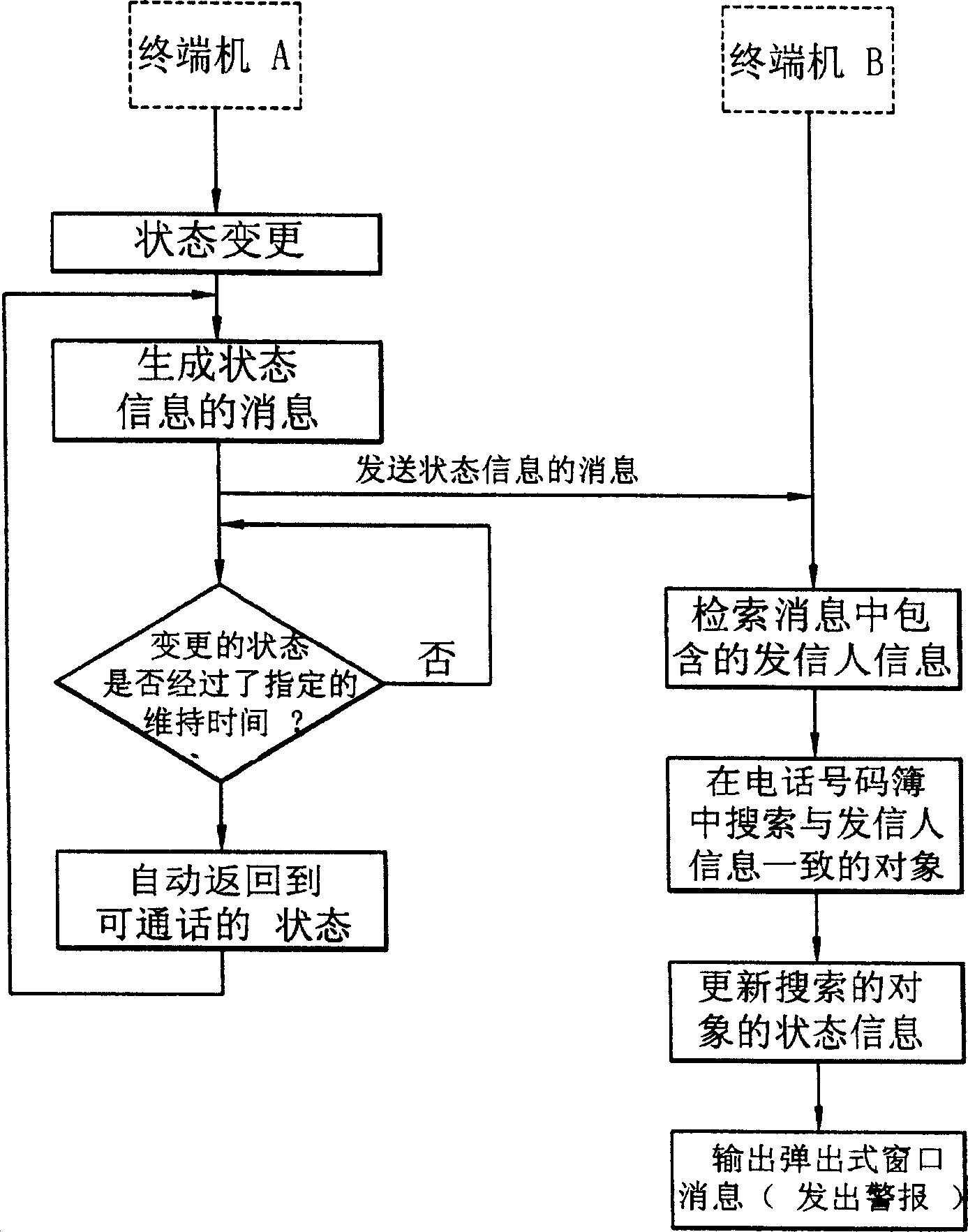
InactiveCN1728734AAvoid callingSubscriber signalling identity devicesRadio/inductive link selection arrangementsComputer hardwareTelephone terminal
The invention discloses a method of transferring user state information by using portable communication terminal short message, which can automatically send the user state information to persons in particular group of the telephone directory, thereby the person receiving the state information can avoid unnecessary call to phone terminal. The invention comprises the following steps: when the user changes the state information of portable communication terminal, automatically generating a message including the changed state information; sending the generated state information message to pre-designated user; when receiving the above-mentioned state information massage, the user terminal searches the telephone directory and updates the related communication state information.
Owner:INSPUR LG DIGITAL MOBILE COMMUNICATIONS CO LTD
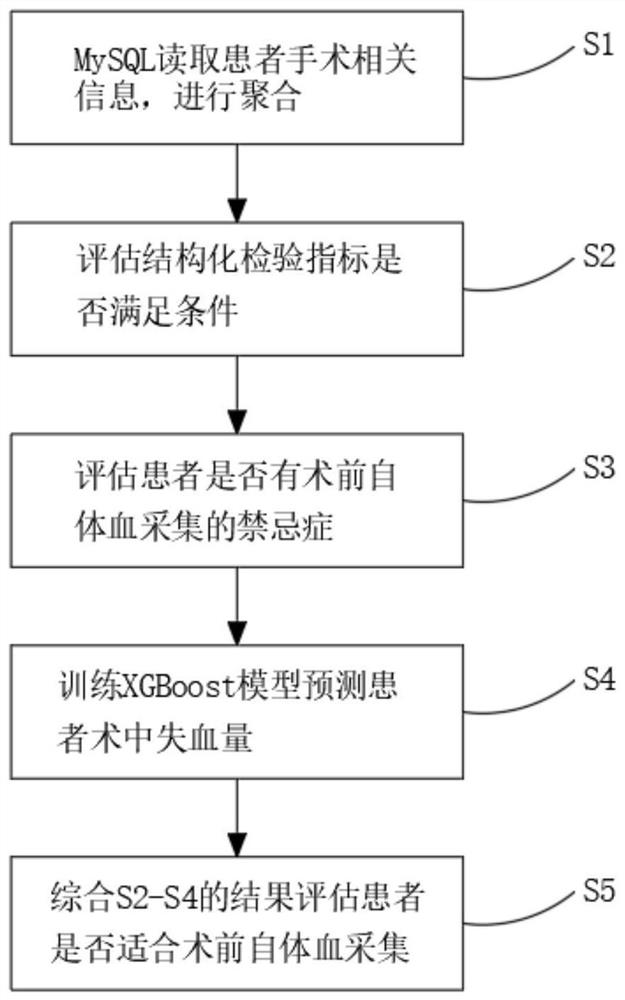
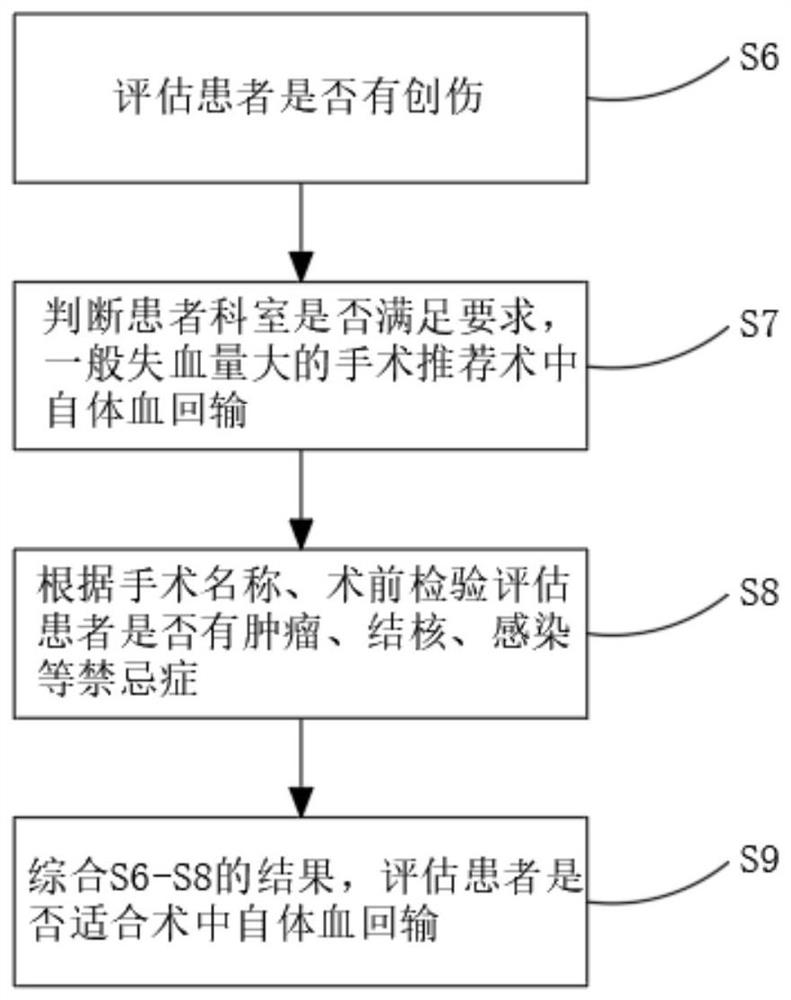
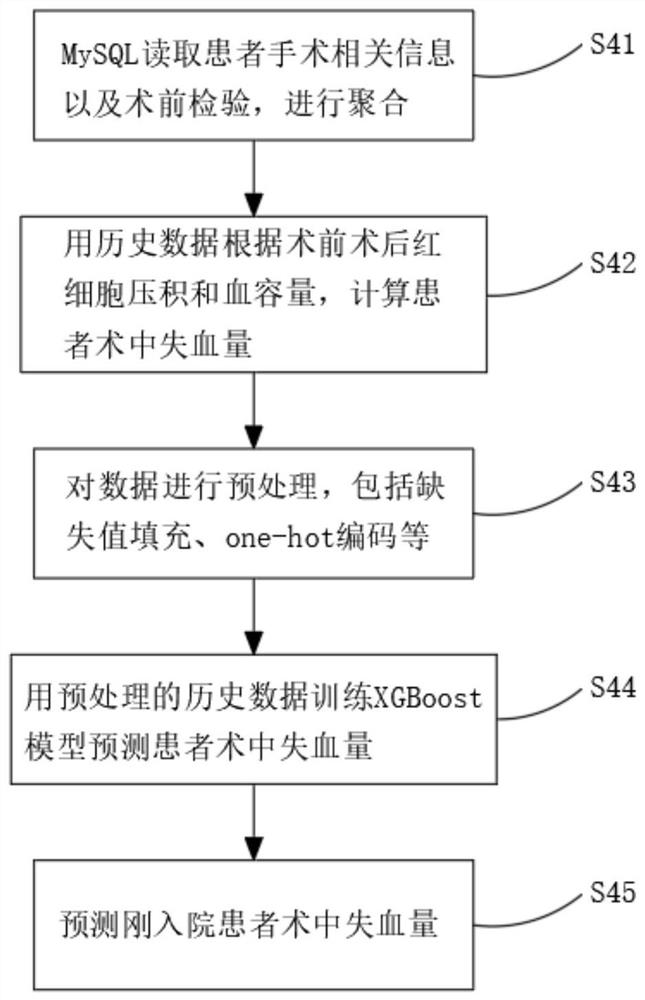
Detection and evaluation method applicable to blood management of perioperative patients
ActiveCN111724910AImprove work efficiencyAvoid callingMedical simulationMedical data miningDiseaseBlood coagulations
The invention relates to the technical field of medical treatment, and discloses a detection and evaluation method applicable to blood management of perioperative patients. The method comprises the following specific steps: S1, reading admission records, nursing documents, blood routine examination results and blood coagulation and biochemical information of a patient from a MySQL database, and conducting aggregating; and S2, evaluating whether the structured test indexes of the patient meet requirements on preoperative autologous blood collection or not. According to the invention, a doctor in a blood transfusion department can be helped to understand the blood use law of a single disease in each department of the hospital, and the doctor can be helped to formulate an optimal blood transfusion path through optimal postoperative hemoglobin analysis; clinical doctors can know the conditions of anemia and blood coagulation functions of the patient before an operation, and timely and pertinently treat the patient to ensure smooth operation in the operation, and rehabilitation of the patient can be accelerated; a doctor is helped to know an autologous blood collection scheme and intraoperative recovery feasibility in advance, the use probability of allogeneic blood is greatly reduced, and the risk of various adverse reactions is reduced.
Owner:北京和兴创联健康科技有限公司
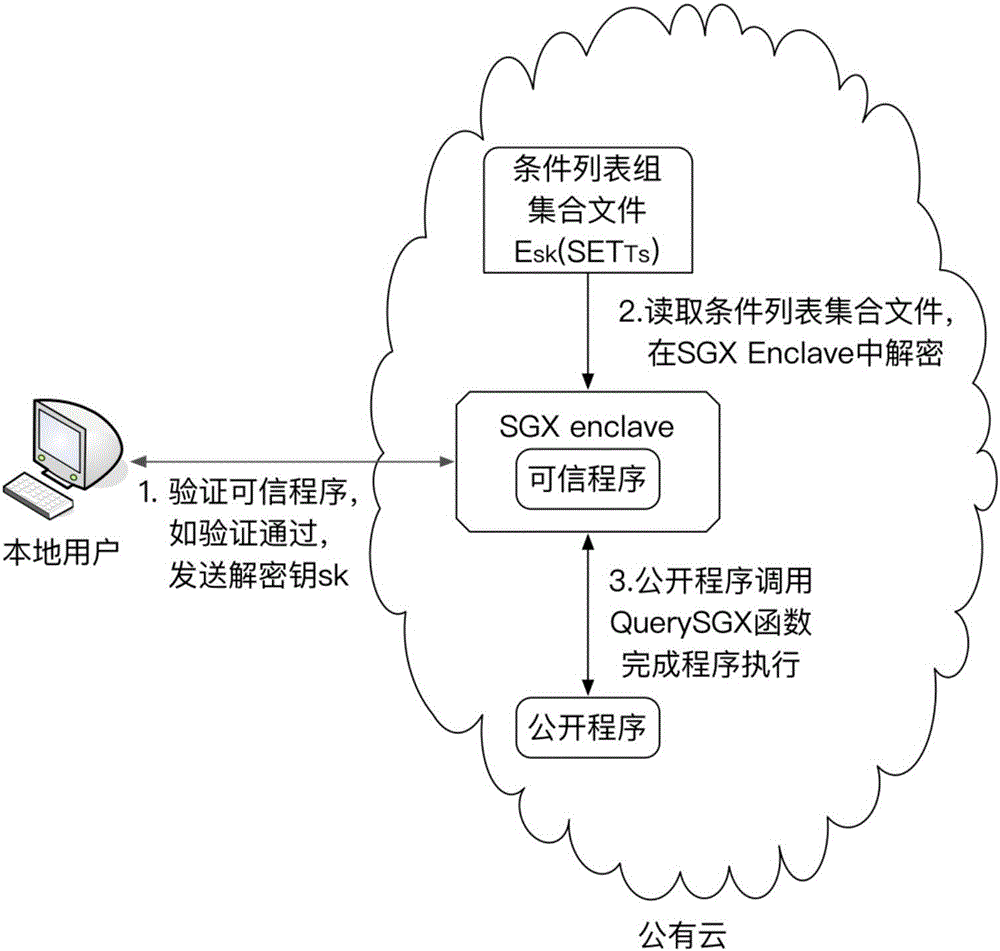
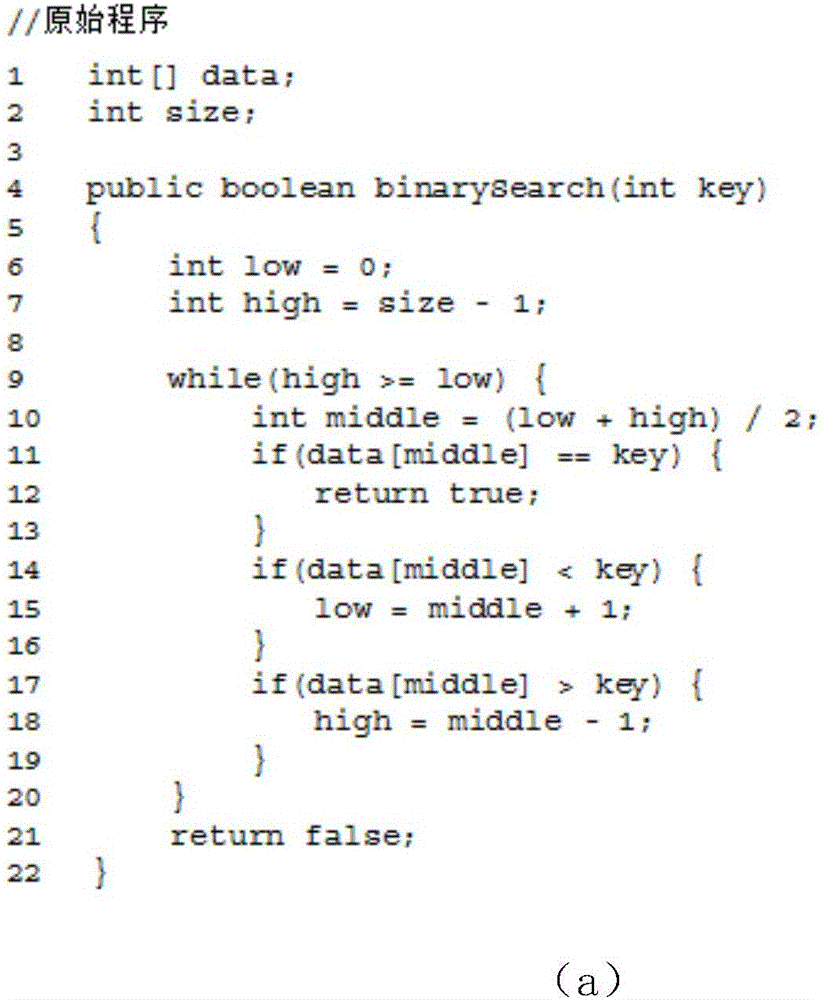
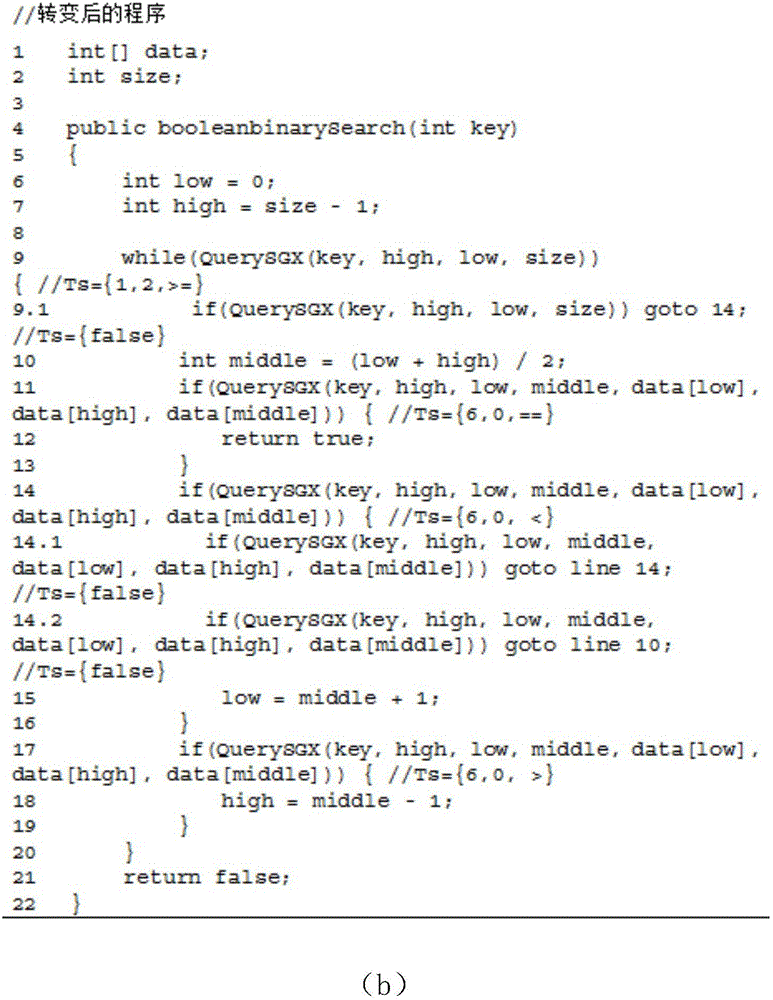
Control flow hiding method for remote computing
ActiveCN106845168AReduce operating overheadAchieve real hiddenSoftware designTransmissionControl flowIntel processor
The invention discloses a control flow hiding method for remote computing. The method includes the following steps that original programs are divided into the open programs, the confidence programs and condition list group set files, the SGX function of the safe execution environment of a sixth-generation Intel processor is used for performing program branching statement condition judging in a confidence region with the hardware protection function, and therefore real hiding of program branching statement conditions is achieved.
Owner:XIDIAN UNIV
Method for receiving and processing network video streams in real time
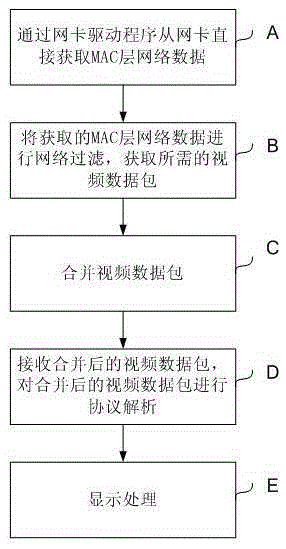
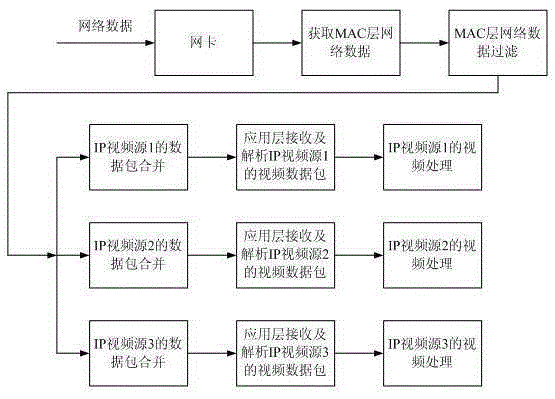
InactiveCN105392053AShort processReduce occupancySelective content distributionPacket lossNetwork data
The invention discloses a method for receiving and processing network video streams in real time. The method includes the following steps that: A, MAC layer network data are directly obtained from a network card driving program; B, network filtering is performed on the obtained MAC layer network data, so that required video data packets can be obtained; C, the video data packets are fused; D, a fused video data packet is received, and protocol analysis is performed on the fused video data packet, so that protocol header data and tail data can be removed; E, and display processing is performed on the protocol header data and tail data-removed video data packet. The method of the invention has high processing efficiency, and can reduce the occupation of the resources of a CPU and avoid packet loss.
Owner:SHANGHAI VIAMAX TECH
File data consistency updating method for memory file system
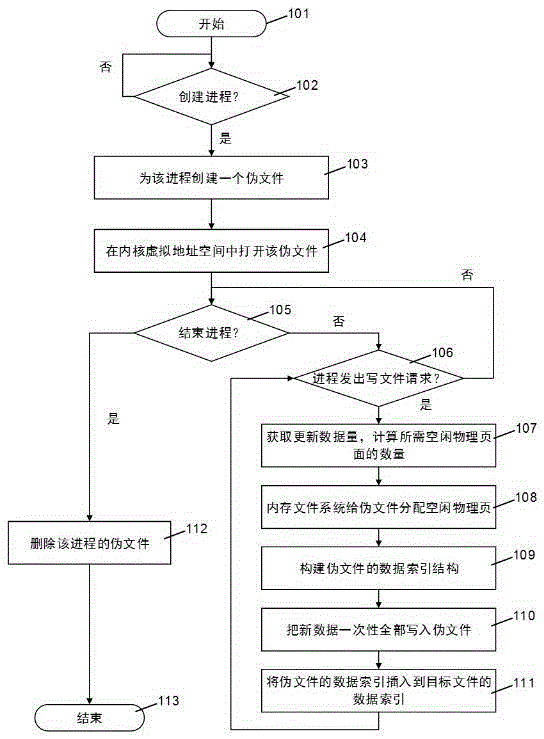
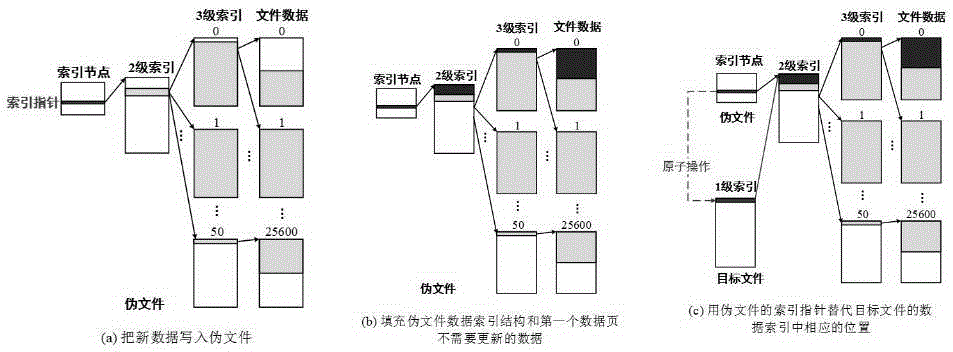
ActiveCN105404667ANo consistency issuesGuaranteed Update Consistency CasesSpecial data processing applicationsFile systemTerm memory
The present invention discloses a file data consistency updating method for a memory file system. The method comprises the following steps: 1. a system opening a dummy file for a process in a kernel space during initialization of the process; 2. the process requesting to update a 'target file', and a memory file system allocating all required physical memory for the dummy file once according to a to-be-updated data volume; 3. constructing a data structure of an index data page in the dummy file, wherein the data structure is called a 'data index'; 4. calling a data copy function once to write all new data into the dummy file once; 5. inserting the data index of the dummy file into a corresponding position in a data index of the target file by using an atomic operation; and 6. terminating the process, and deleting the dummy file corresponding to the process. The file data consistency updating method for the memory file system has advantages of avoiding calling the data copy function and performing the atomic operation for too many times with regard to an update operation with a relatively large data volume, and achieving relatively high performance while file data updating consistency is ensured.
Owner:CHONGQING UNIV
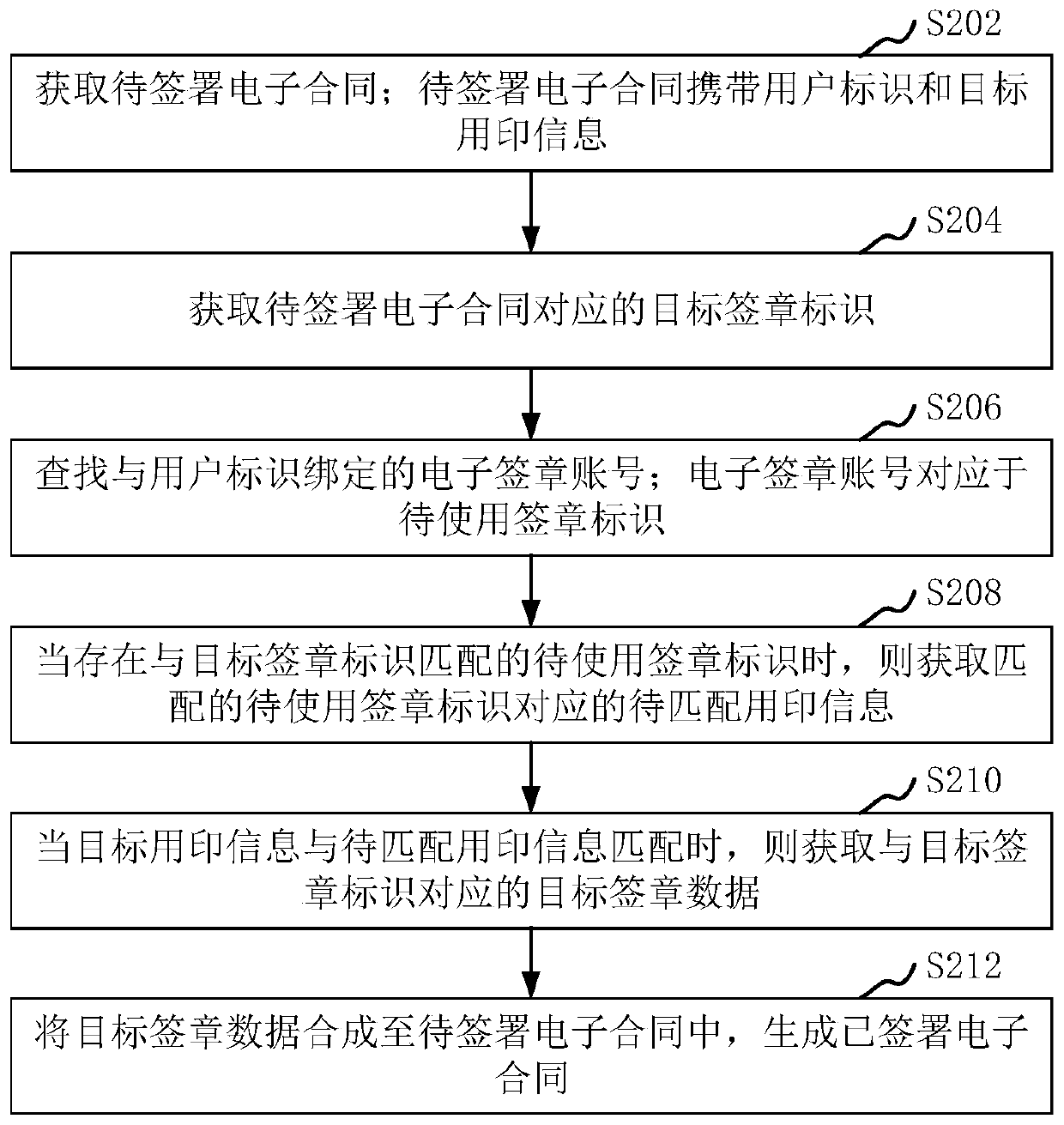
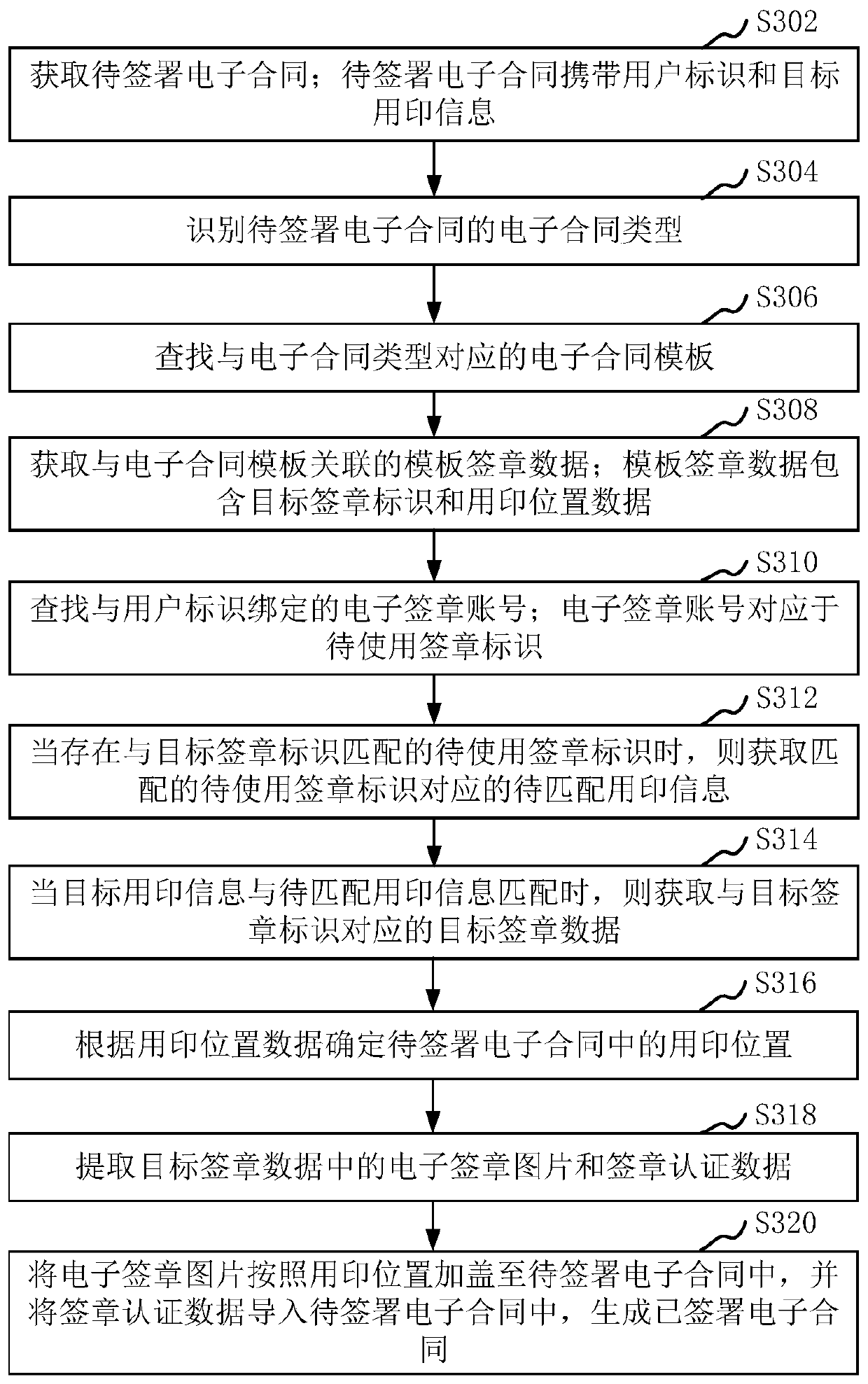
Electronic contract signing method and device, computer device and storage medium
The invention relates to an electronic contract signing method and device, a computer device and a storage medium. The method comprises the steps of obtaining a to-be-signed electronic contract; wherein the to-be-signed electronic contract carries a user identifier and target stamping information; obtaining a target signature identifier corresponding to the to-be-signed electronic contract; searching an electronic signature account bound with the user identifier; wherein the electronic signature account corresponds to a signature identifier to be used; when the to-be-used signature identifiermatched with the target signature identifier exists, obtaining to-be-matched seal use information corresponding to the matched to-be-used signature identifier; when the target seal use information ismatched with the to-be-matched seal use information, obtaining target signature data corresponding to the target signature identifier; and synthesizing the target signature data into the to-be-signedelectronic contract to generate a signed electronic contract. By adopting the method, the electronic contract signing business process is optimized, and the electronic signature can be correctly called.
Owner:ONE CONNECT SMART TECH CO LTD SHENZHEN
Method, mobile terminal and system for data encryption
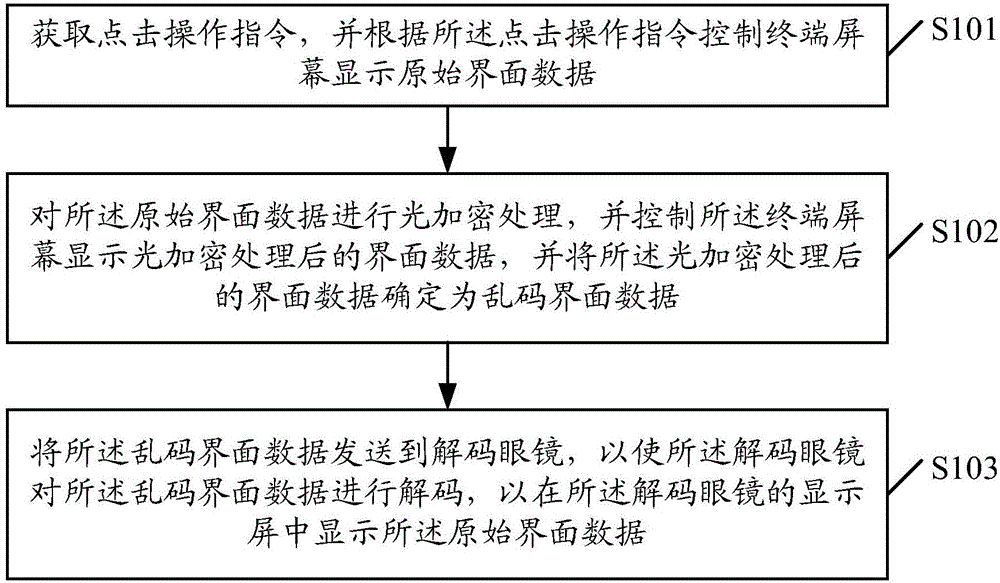
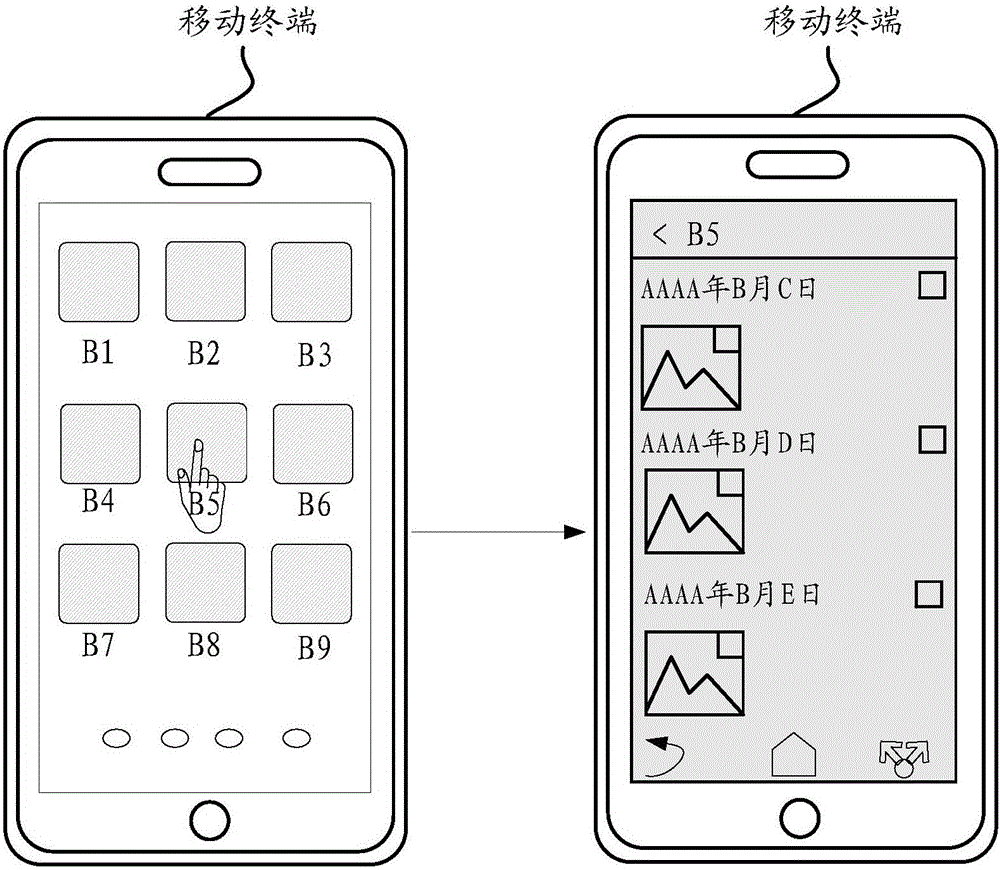
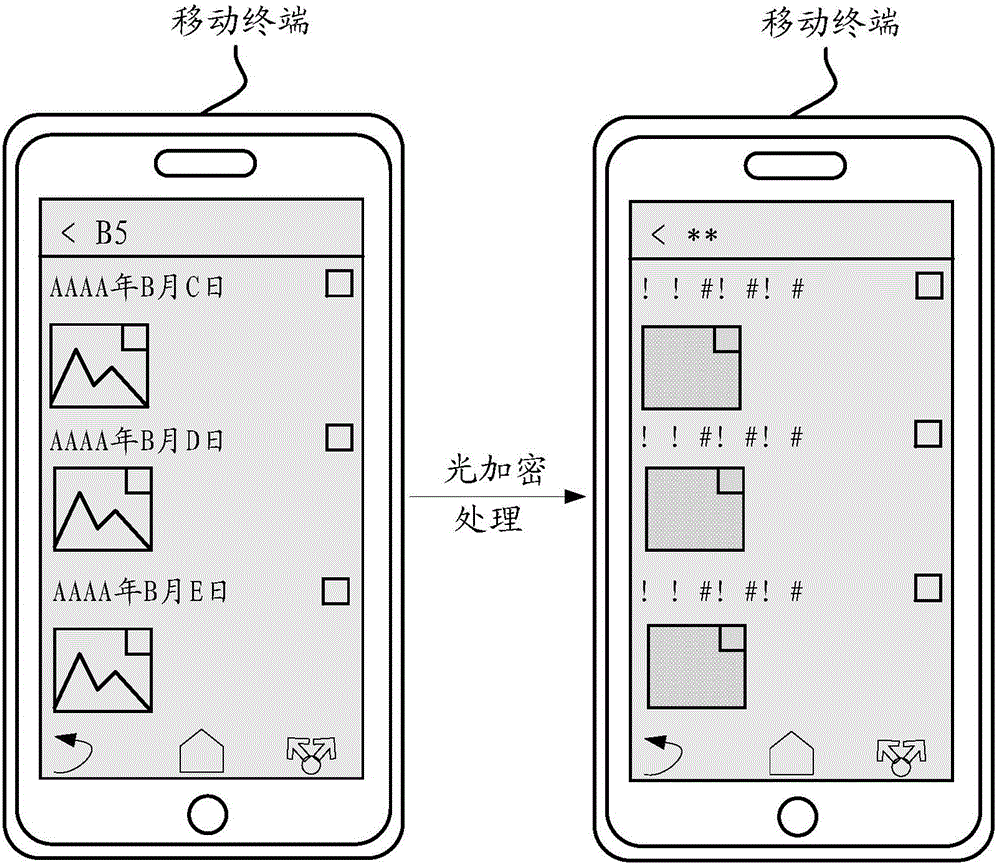
ActiveCN106650467AAvoid viewingAvoid callingDigital data protectionInternal/peripheral component protectionComputer hardwareEyewear
The embodiment of the invention discloses a method for data encryption and a corresponding mobile terminal and system. The method comprises the steps of obtaining a click operation command, and controlling a terminal screen to display original interface data according to the click operation command; conducting light encryption treatment on the original interface data, controlling the terminal screen to show the interface data after the interface data is subjected to light encryption treatment, and determining the interface data which is subjected to light encryption treatment as messy code interface data; sending the messy code interface data to a pair of decoding glasses, so that the decoding glasses conduct decoding on the messy code interface data, and the original interface data can be shown in a display screen of the decoding glasses. According to the method, the mobile terminal and system for data encryption, the privacy and safety of private information of a user can be strengthened, and the encrypted original interface data can be obtained through the decoding glasses so as to make it convenient for the user to conduct query on the private information in the terminal screen.
Owner:YULONG COMPUTER TELECOMM SCI (SHENZHEN) CO LTD
Traditional Chinese medicine ear diagnosis image processing method and device
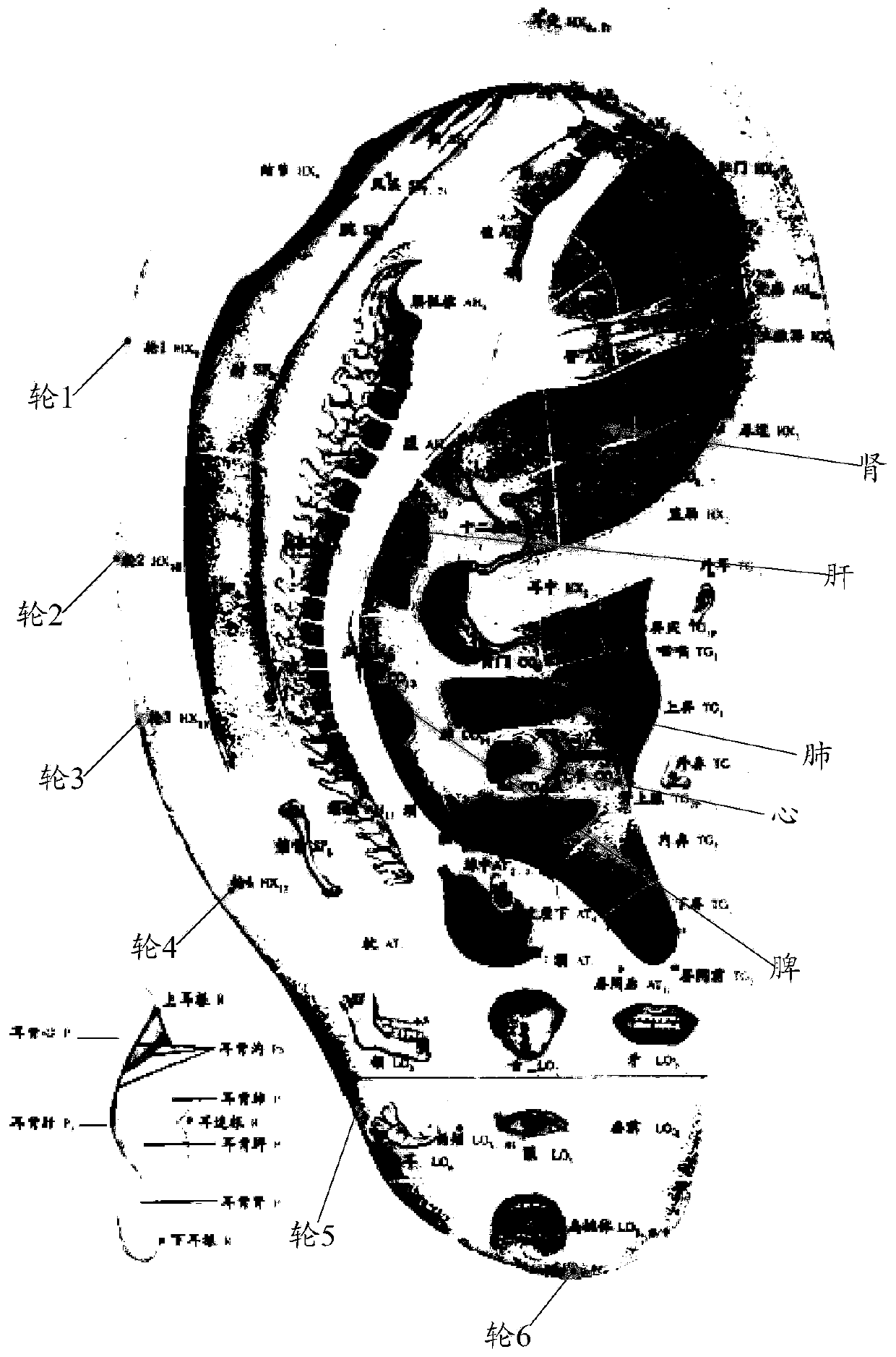
ActiveCN110349140AOvercome the problem of inaccurate judgmentImprove user experienceImage enhancementImage analysisImaging processingMedicine
The invention discloses a traditional Chinese medicine ear diagnosis image processing method and device. The traditional Chinese medicine ear diagnosis image processing method comprises the followingsteps: acquiring an ear image of a user; performing three-dimensional reconstruction on the ear image to form an ear three-dimensional model; carrying out fan-shaped segmentation on the ear three-dimensional model by taking the ear middle part of the ear three-dimensional model as a center to obtain an auricular concha region image; determining five-color features of each concha region image according to the pixel information of each concha region image, extracting the five-color features in each concha region image and converting the five-color features into concha features; extracting three-dimensional surface features and converting the three-dimensional surface features into auricle morphological features; and sending the ear color features and the auricle morphological features withinthe preset acquisition frequency to a preset SVM classifier to perform ear diagnosis disease state classification, and outputting the classified data to a preset ear diagnosis database for storage. According to the traditional Chinese medicine ear diagnosis image processing method and device, quantitative reference data can be provided for ear diagnosis, and the ear diagnosis disease state can beautomatically identified.
Owner:WUYI UNIV
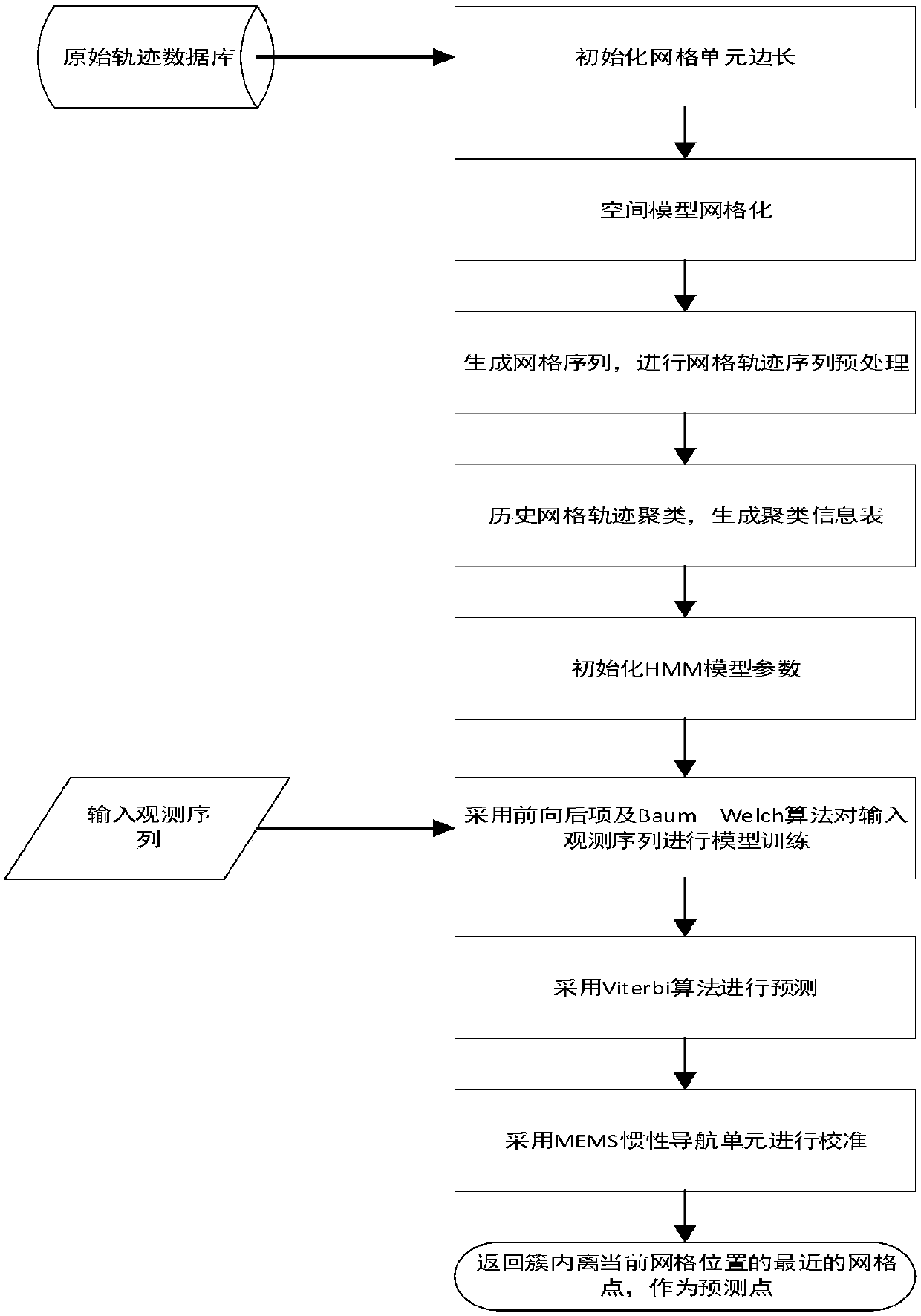
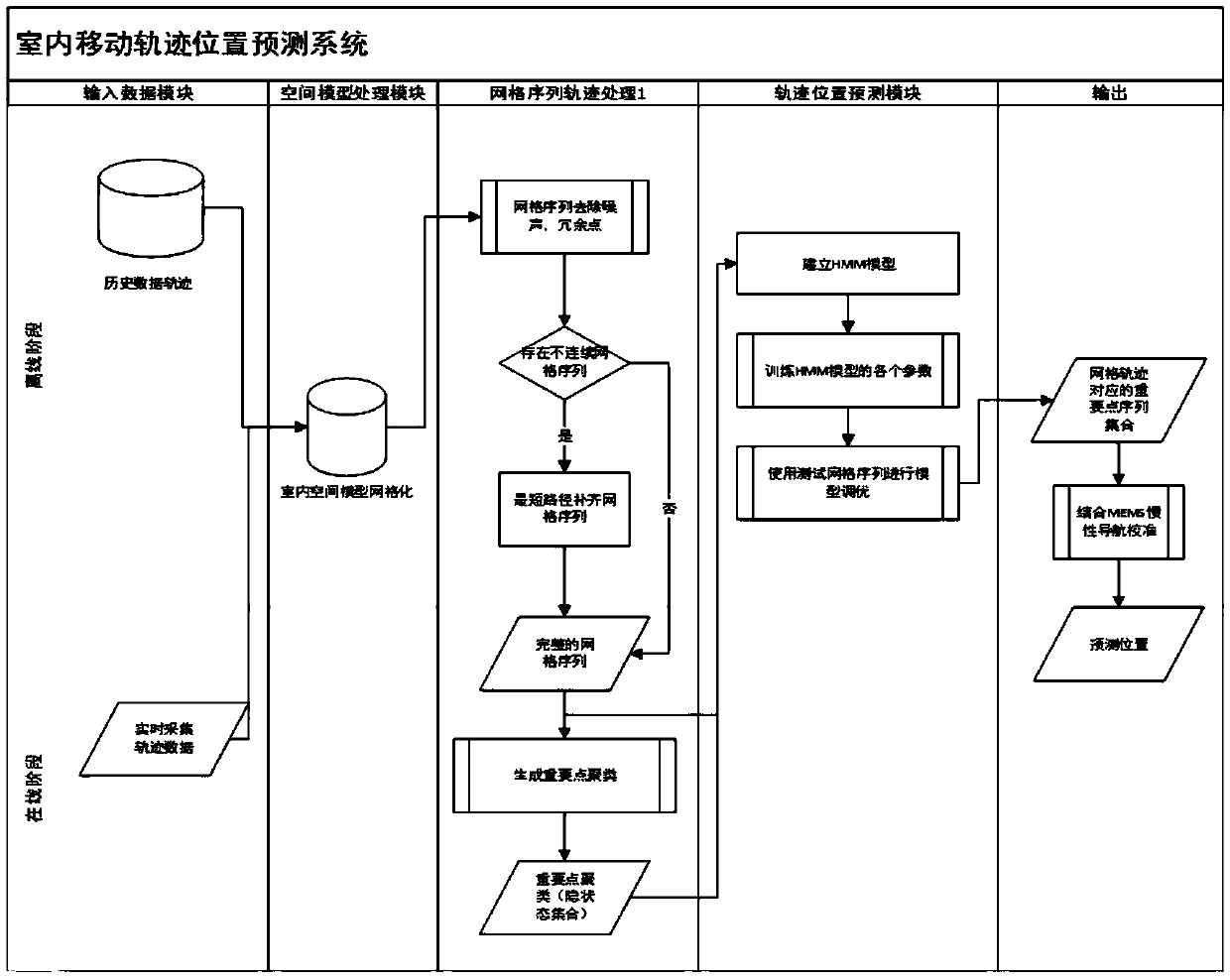
Method for predicting indoor movement trajectory data based on HMM model
ActiveCN108882172AAvoid callingReduce the number of hidden statesParticular environment based servicesLocation information based serviceAlgorithmData management
The invention belongs to the field of indoor movement trajectory management and prediction, and specifically provides a method for predicting indoor movement trajectory data based on an HMM model, which is used for realizing prediction based on HMM trajectory data in an indoor space. The method provided by the invention comprises the following steps: firstly, based on a historical trajectory sequence, taking the minimum Euclidean distance between consecutive non-repetitive points of the historical trajectory sequence as a side length of a mesh unit, performing hierarchical meshing on an indoorspace model to generate a mesh space; based on the mesh space, projecting the historical trajectory data to generate a mesh sequence, and preprocessing the mesh sequence to generate a historical meshtrajectory database; then, performing clustering on the basis of a DBSCAN algorithm to generate a clustering information database, and constructing the HMM model according to an clustering information table; and finally, based on the trained HMM model, using a Viterbi algorithm to perform prediction. The invention provides an indoor trajectory data position prediction method, which effectively improves the accuracy of the predicted trajectory data, and further optimizes the performance of an indoor trajectory data management system.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
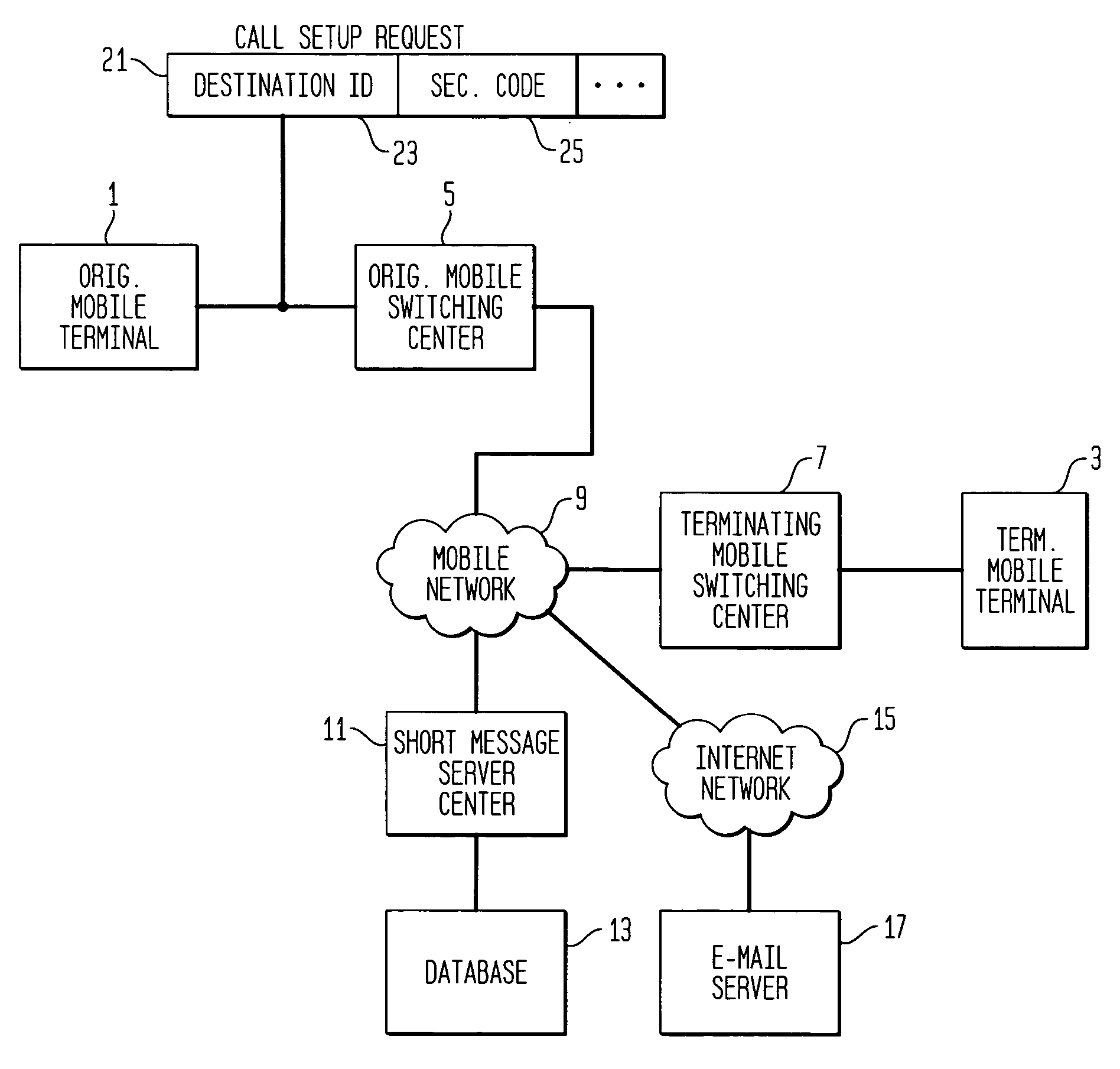
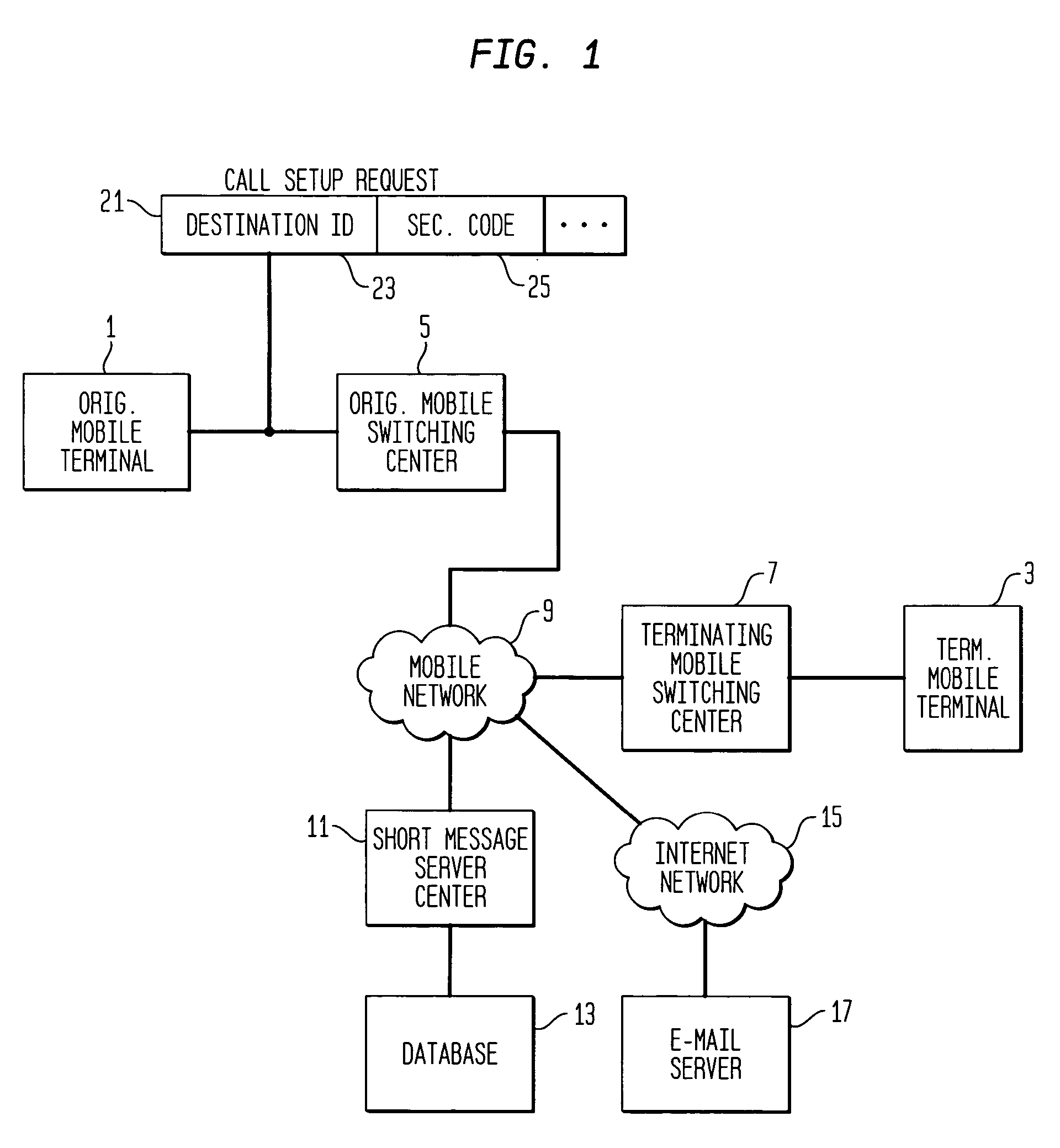
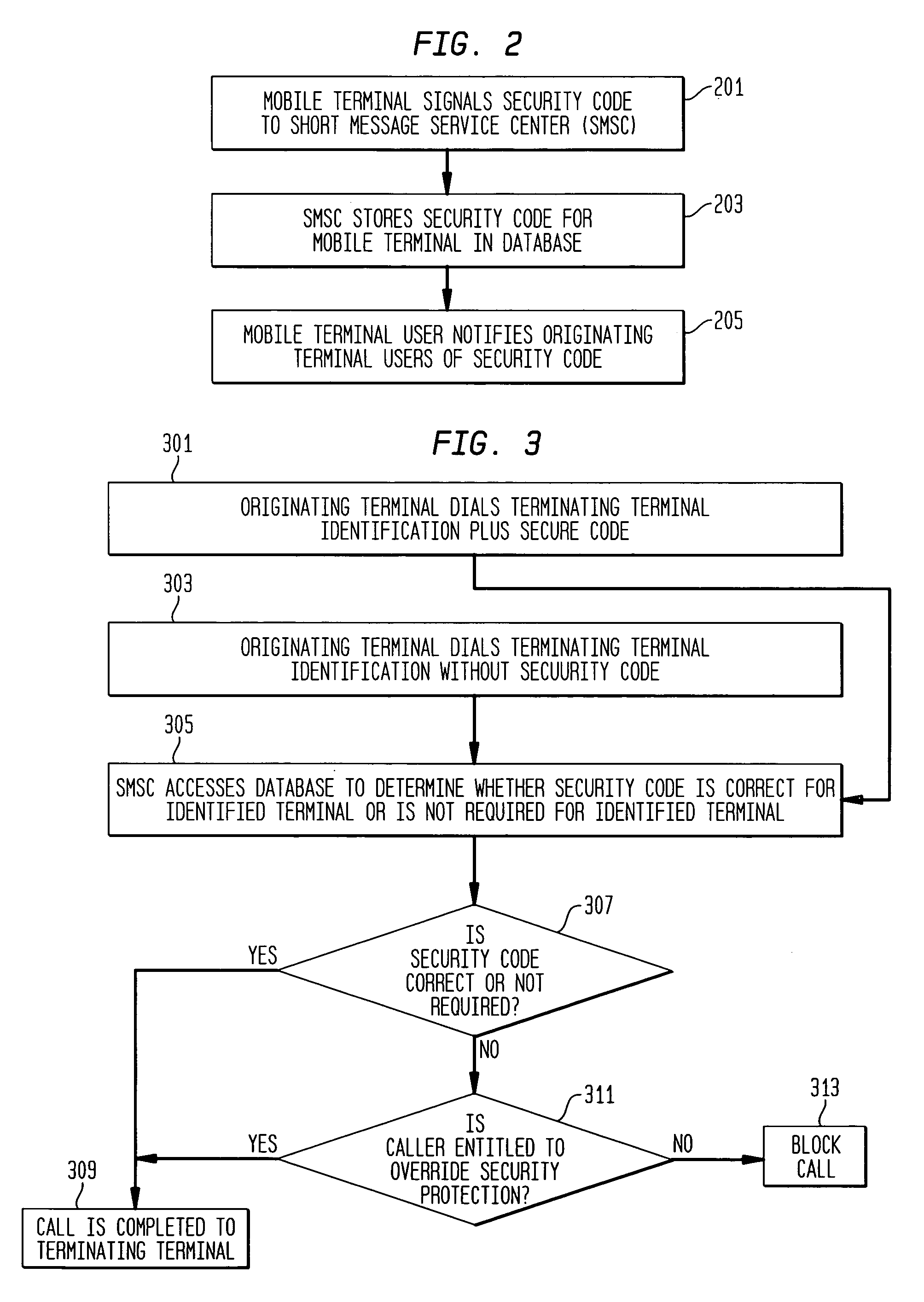
Blocking spam messages
InactiveUS20060135168A1Avoid placingAvoid callingAccounting/billing servicesUser identity/authority verificationComputer hardwareTelecommunications network
A method and apparatus for blocking unwanted and unsolicited messages (spam) in telecommunications networks. A terminating terminal is assigned a security code. In order to access the terminating terminal, the caller must supply this security code as well as the identification of the called terminal. If the correct security code has not been supplied with the call, the call is blocked. Advantageously, a called party can block all calls or messages except those originating from users who have been supplied with this security code.
Owner:LUCENT TECH INC
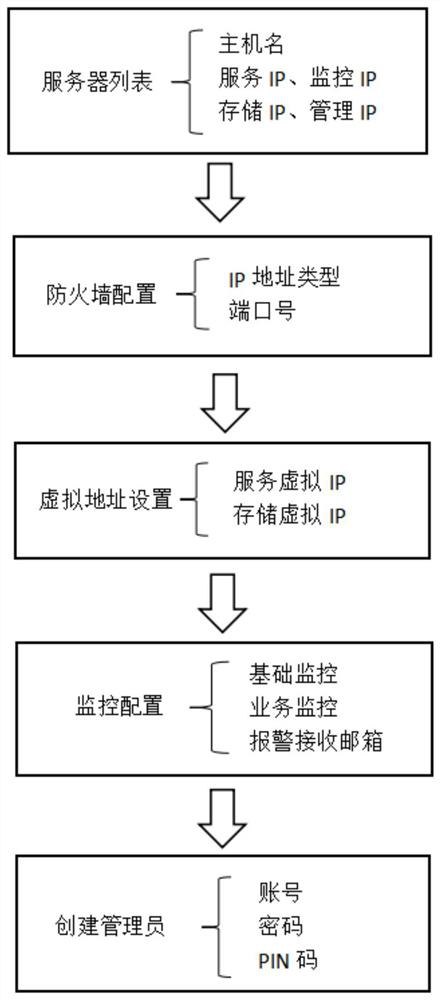
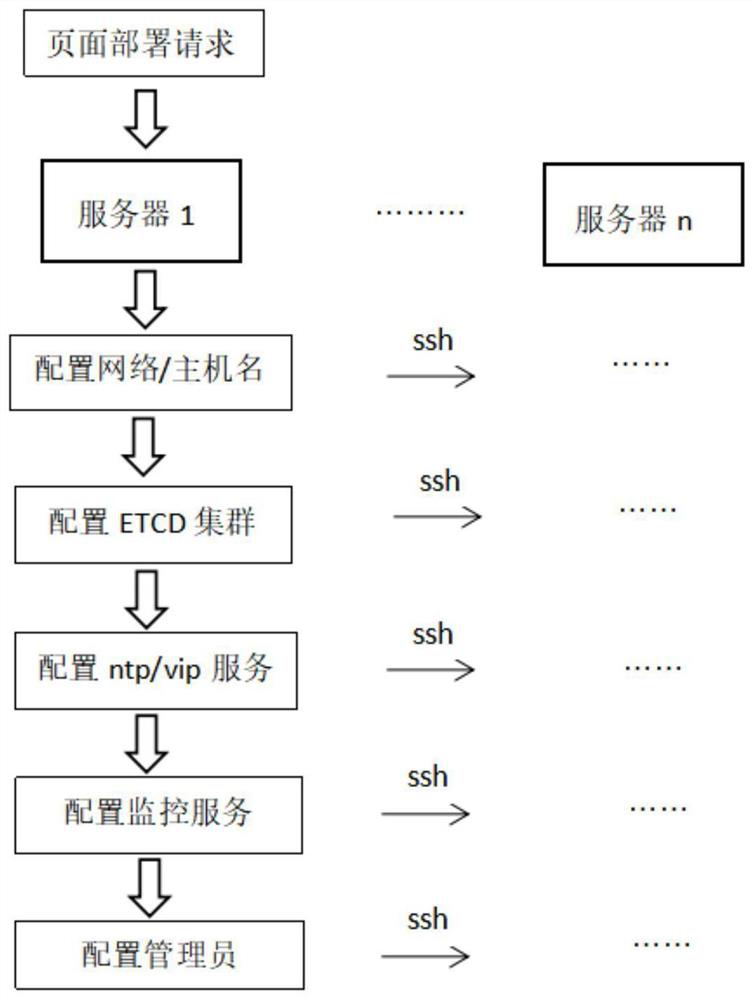
Method for automatically deploying high-availability cluster of service system based on ansible
ActiveCN112491606AAvoid misuse of interventionImprove deployment success rateData switching networksService systemComputer security
The invention discloses a method for automatically deploying a high-availability cluster of a service system based on ansible, which comprises the following steps: setting all servers of the cluster in a local area network, and setting a deployment IP (Internet Protocol) of each server, so that the server at the rear end accesses a deployment page at the front end through the deployment IPs respectively, and the server comprises four different types of network cards, the system comprises a monitoring network card, a service network card, a storage network card and a management network card, configuration information is input into the deployment page and a page deployment request is generated; the method comprises the steps that a server is selected as a deployment main node, an android script is generated according to a specified server list and corresponding information in configuration information, the deployment main node obtains a page deployment request and executes the deploymentstep of the android script according to the configuration information, and meanwhile an SSH protocol is used for sending execution commands of the same step to other servers in a cluster through a deployment IP. The deployment success rate is improved, maintenance of operation and maintenance personnel is facilitated, and the working efficiency is improved.
Owner:湖南麒麟信安科技股份有限公司
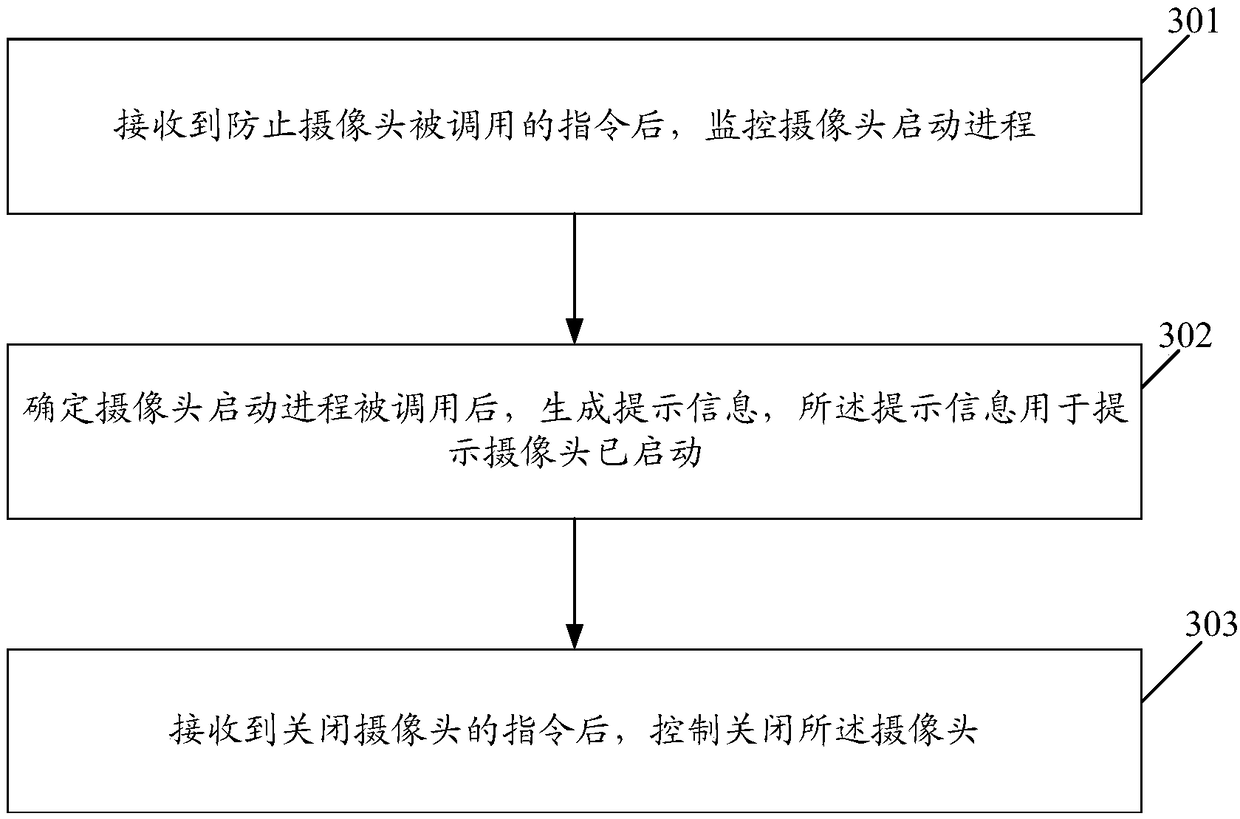
Camera control method, terminal and computer storage medium
InactiveCN109190369AAvoid callingGuaranteed privacy and securityPlatform integrity maintainanceCamera controlSurveillance camera
The embodiment of the invention discloses a camera control method, a terminal and a computer storage medium. The method comprises the steps of: monitoring a camera startup process after receiving an instruction to prevent the camera from being called; after determining that the camera startup process is invoked, generating a prompt message, and using the prompt message for prompting that the camera has been started; after receiving the instruction of turning off the camera, controlling the camera to be turned off. After the camera startup process is illegally called, a prompt message can be generated to prompt a user to turn off the camera, thereby preventing the camera startup process from being illegally cal, and ensuring the privacy security of the user.
Owner:NUBIA TECHNOLOGY CO LTD
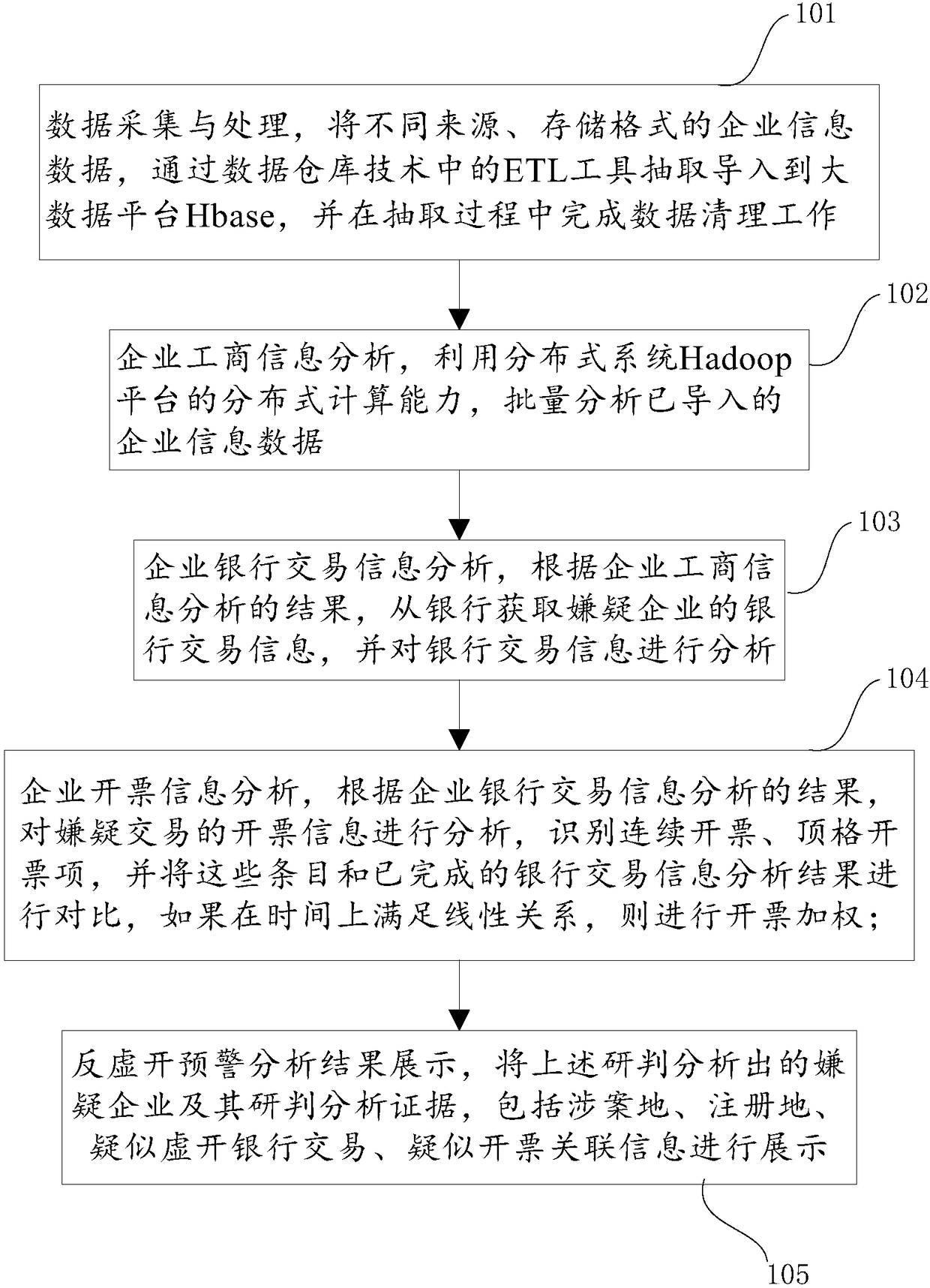
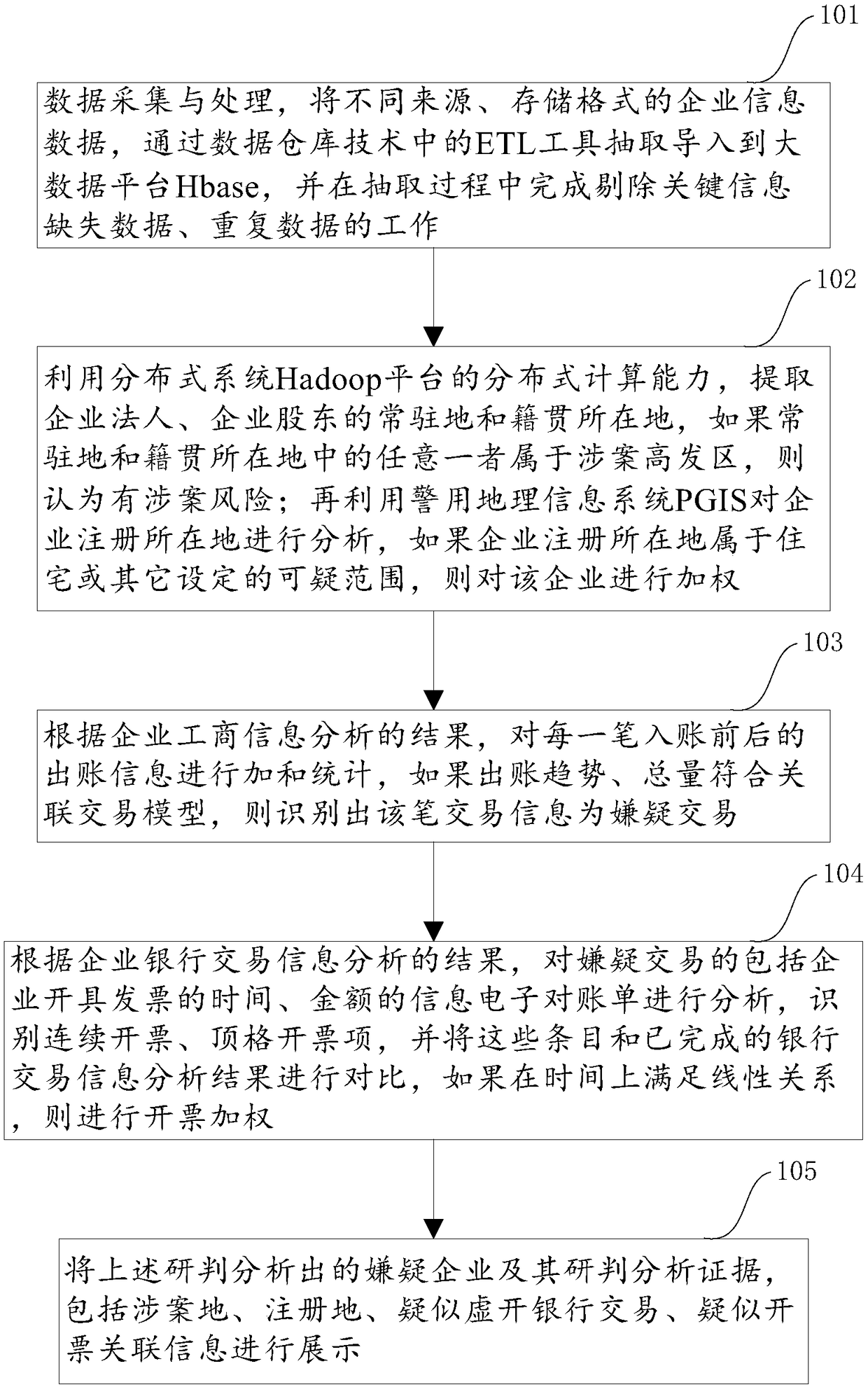
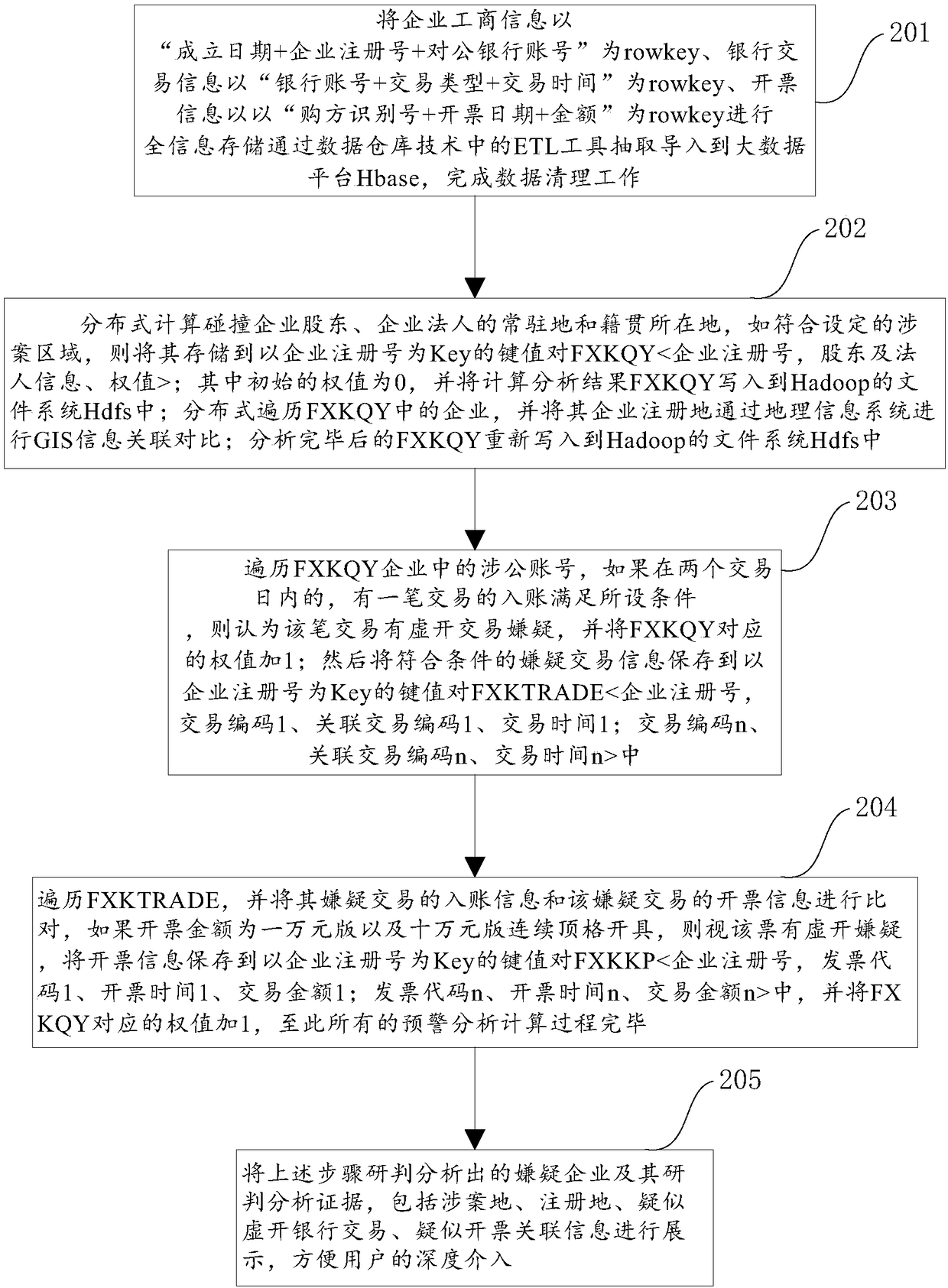
Early-warning analysis method and system of false invoicing of value-added tax invoices
ActiveCN108595621AReduce redundancyImprove analysisBilling/invoicingSpecial data processing applicationsInformation analysisData platform
The invention discloses an early-warning analysis method and system of false invoicing of value-added tax invoices. The method mainly includes the following steps: data collection and processing, enterprise industrial / commercial-information analysis, enterprise bank transaction information analysis, enterprise invoicing information analysis and anti-false-invoicing early-warning analysis result display. The system mainly includes a data collection and processing module, an enterprise industrial / commercial-information analysis module, an enterprise bank transaction information analysis module,an enterprise invoicing information analysis module and an analysis result display module. By using the early-warning analysis method and system of false invoicing of the value-added tax invoices of the invention, unobtrusive publicly-related bank account transaction information retrieval can be avoided, a large amount of related data can be comprehensively stored and analyzed by using distributed-storage and distributed-computing capability of a big-data platform, early-warning study and judgment algorithms can also be quickly expanded by scalability, which the same have, when a new clue is discovered, accuracy of analysis results can be improved, and counting analysis time can also be reduced.
Owner:TAIHUA WISDOM IND GRP CO LTD
Method and device for call handling
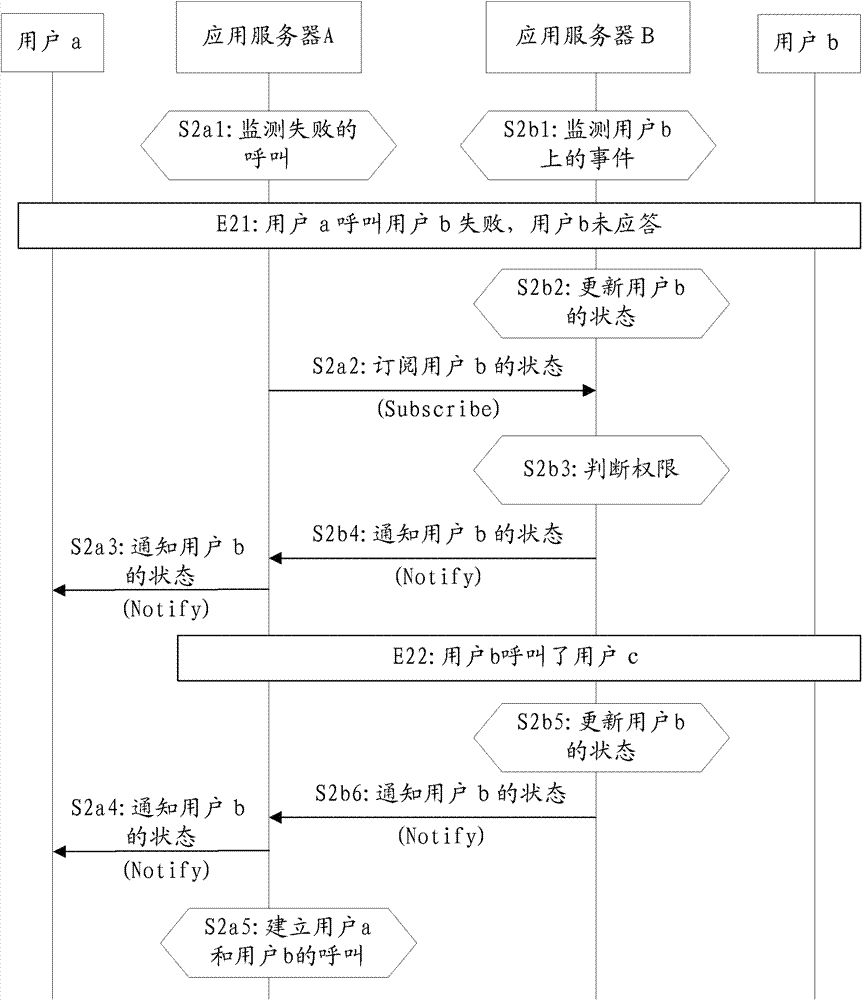
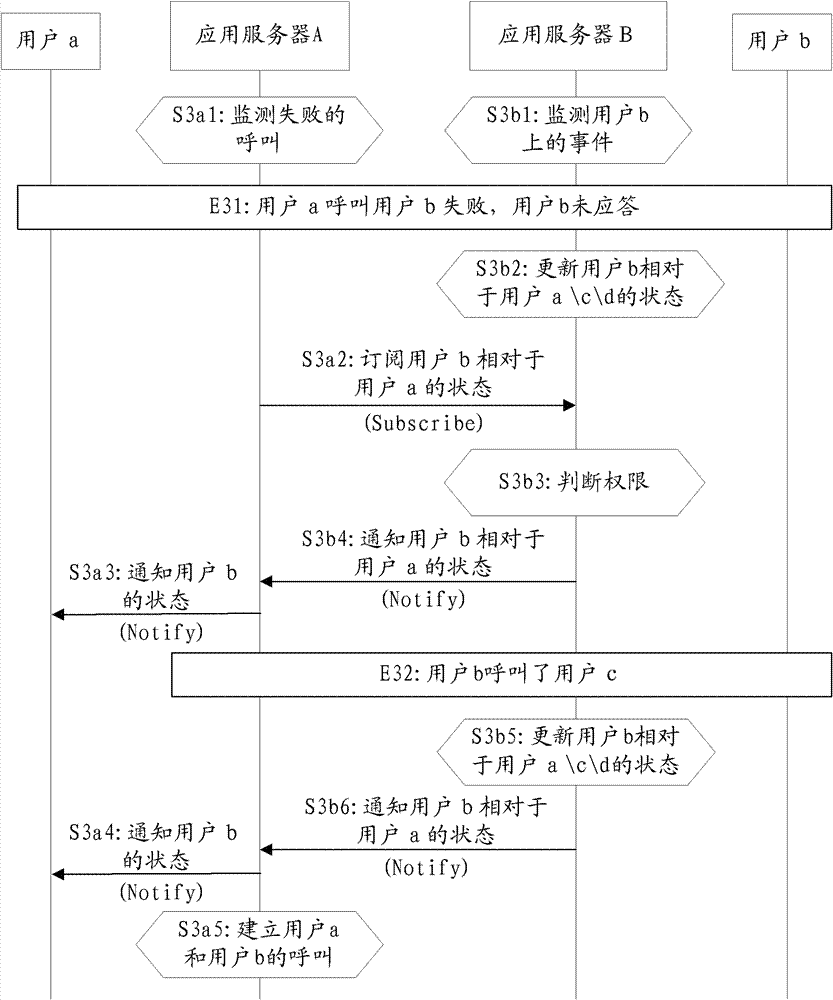
InactiveCN102769835AAvoid callingSave network resourcesConnection managementCommmunication supplementary servicesApplication serverCore network
The invention provides a method for call handling. The method for call handling includes that an application server on a calling party side monitors a call initiated to a user in a current district, and when a failed call is monitored, the application server on the calling party side positively transmits a subscription request to an application server on a called party side so as to subscribe the called state; and the application server on the called party side monitors user events in the district thereof, positively reckons the called state according to the monitored events and informs the application server on the calling party side of the called latest state. Therefore, a calling party can know the state of a called party timely and accurately, and the communication establishment success rate can be increased. Moreover, the called party can have different states for different calling parties. Different from the prior art, the method has the advantages that a core network can reckon the state of the user positively and timely rather than passively waits for notices of the user, and more states can be provided, so that more information can be provided.
Owner:ALCATEL LUCENT SAS
System and method for providing cellular telephone service during cluster testing
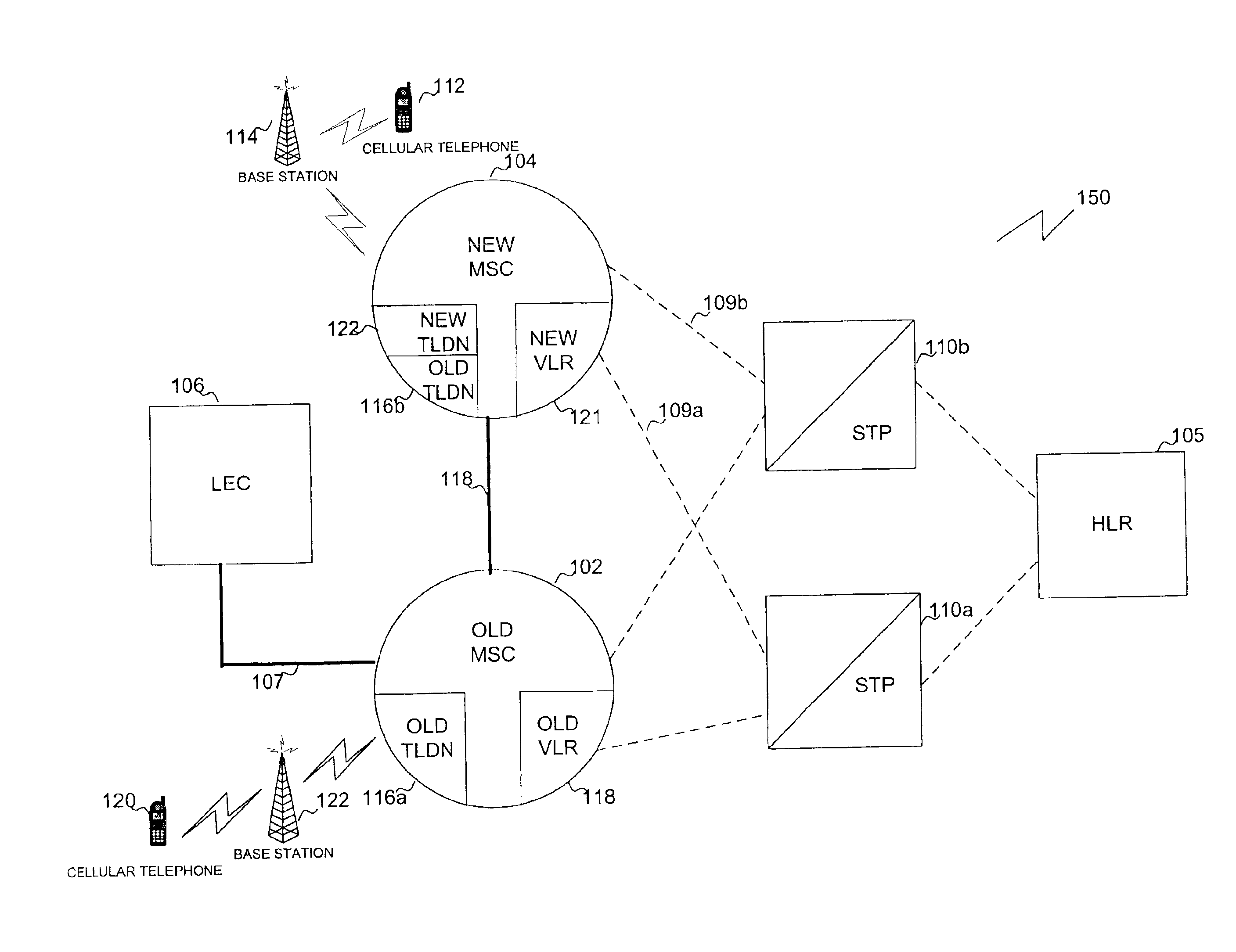
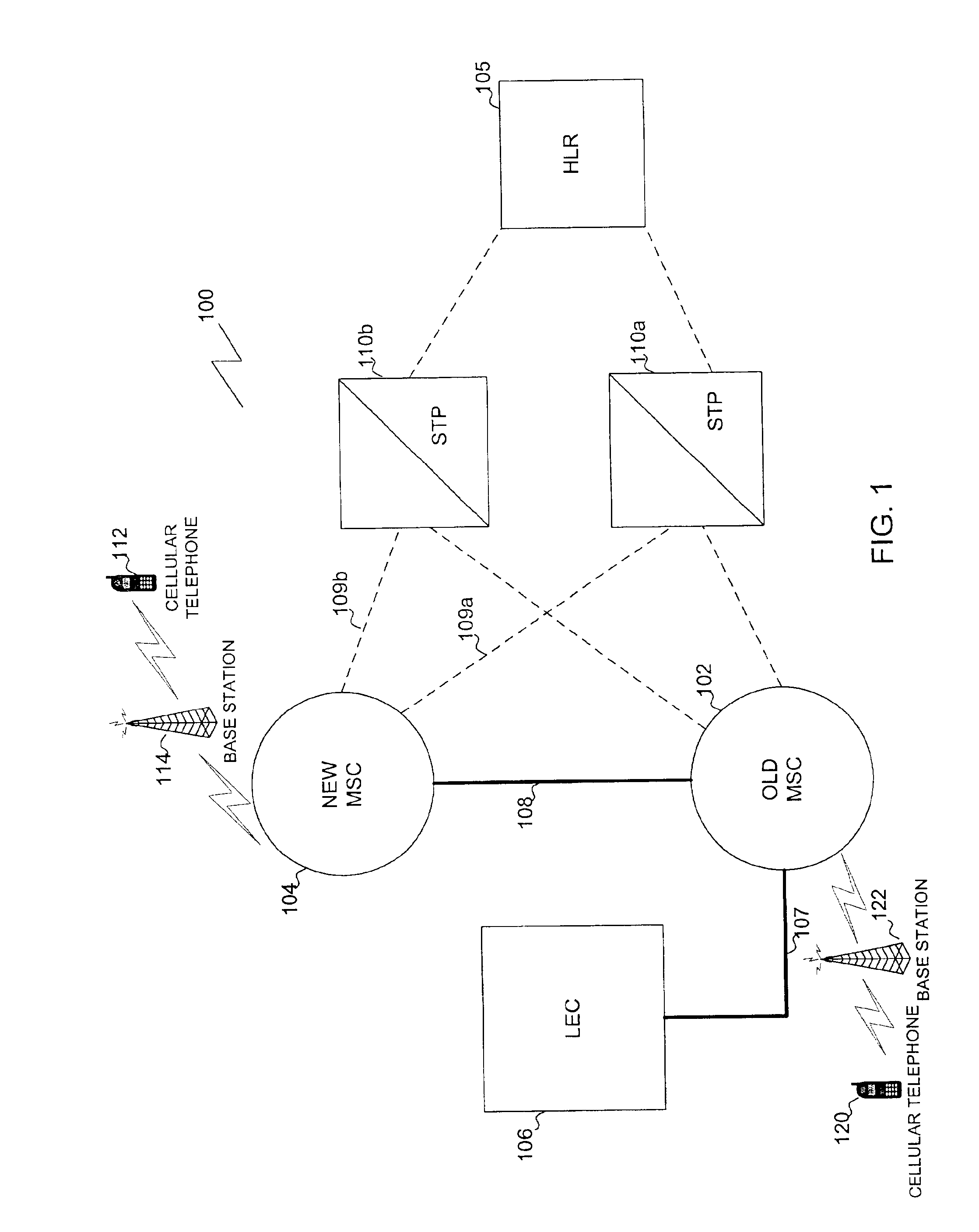
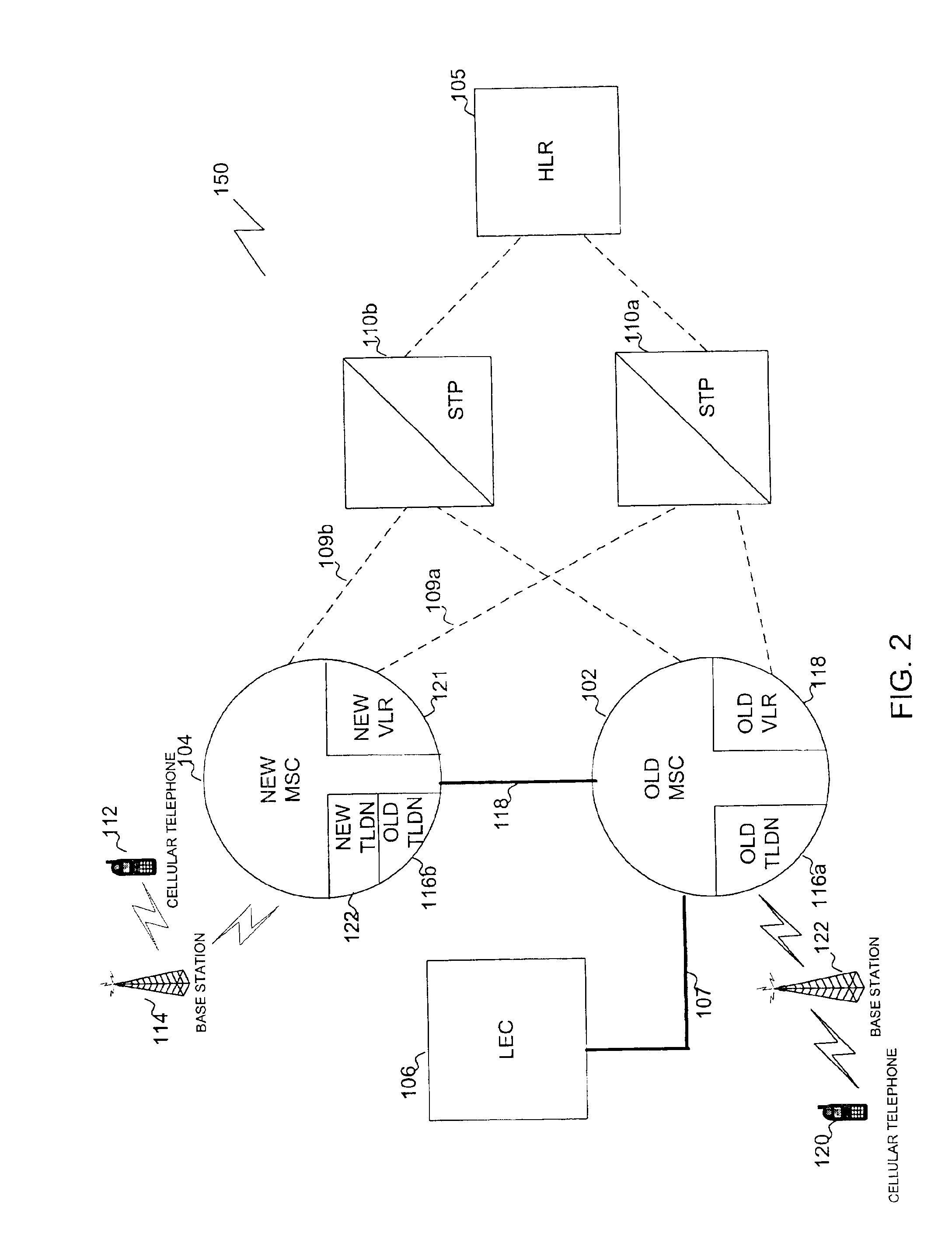
InactiveUS6879811B1Avoid callingSpecial service for subscribersRadio/inductive link selection arrangementsEngineeringCellular telephone
A cellular telephone system provides coverage during cluster testing in which a new mobile switching center (MSC) that is to replace an old MSC is cut into the cellular telephone system for testing. A trunk group is built between the old MSC and the MSC. In addition, a signaling link is built between the old MSC and the new MSC. The new MSC is also assigned a unique point code to differentiate the new MSC from the old MSC during testing. In addition, the new MSC is provided with a new range of temporary local dialing numbers (TLDNs) for use during cluster testing.
Owner:BELLSOUTH INTPROP COR
Dynamic library calling method and device, electronic device and storage medium
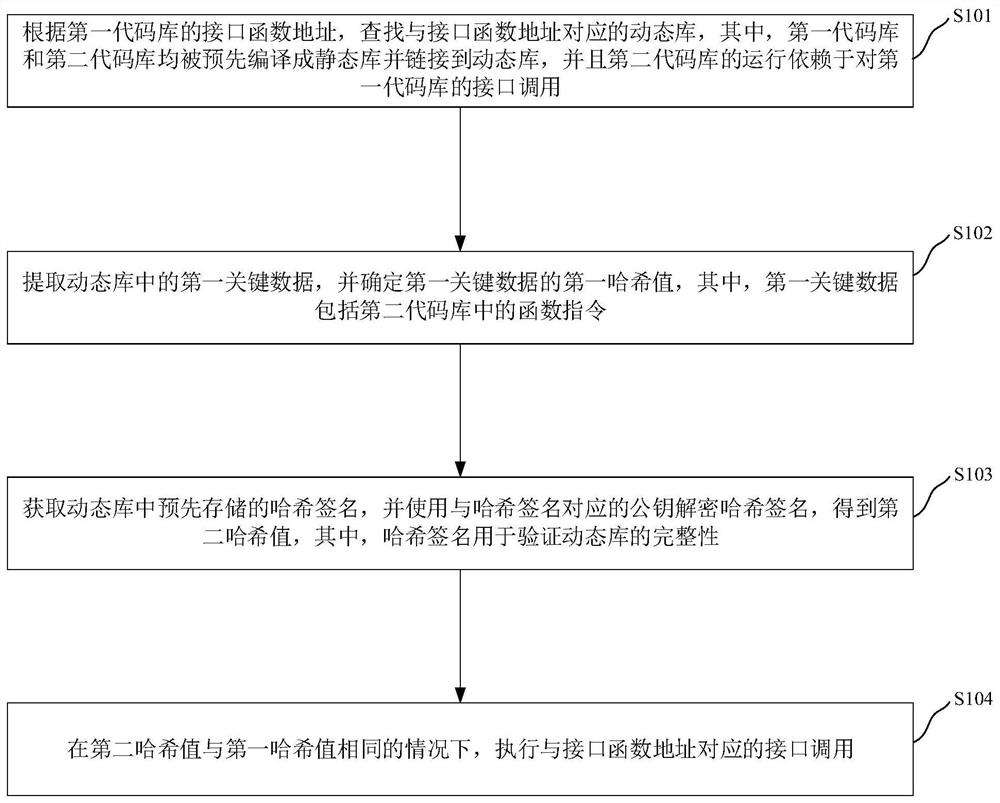
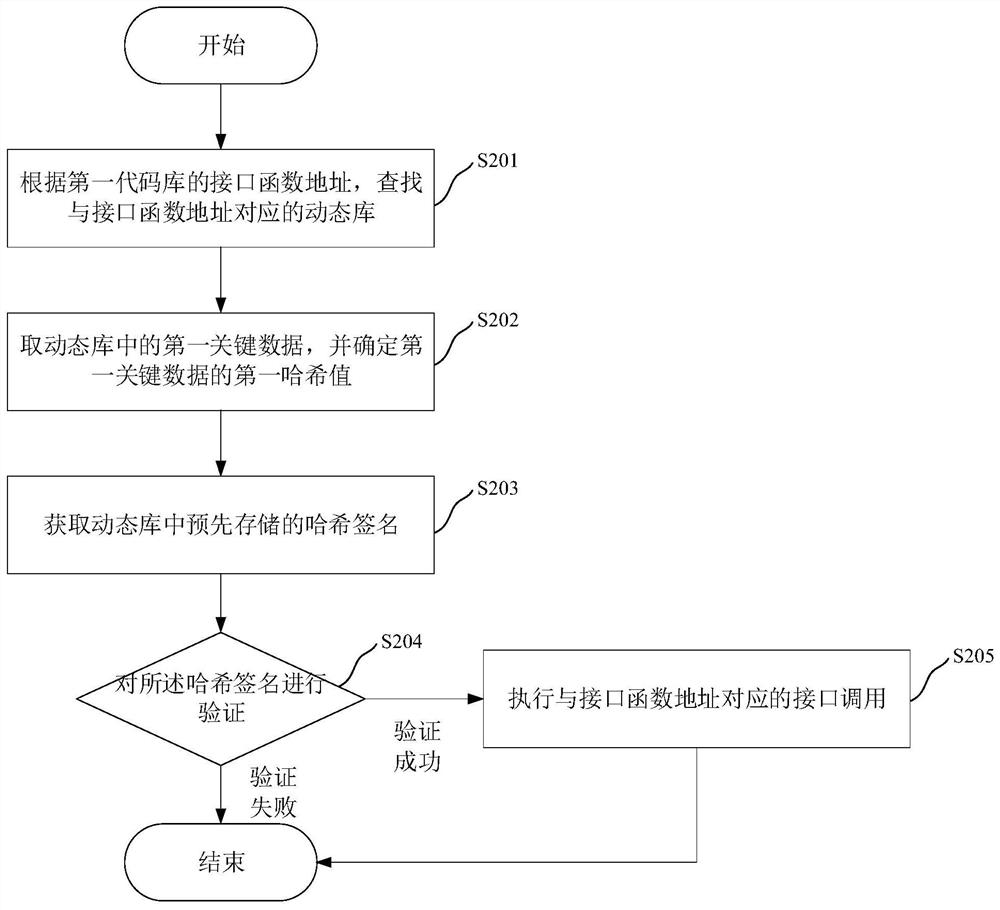
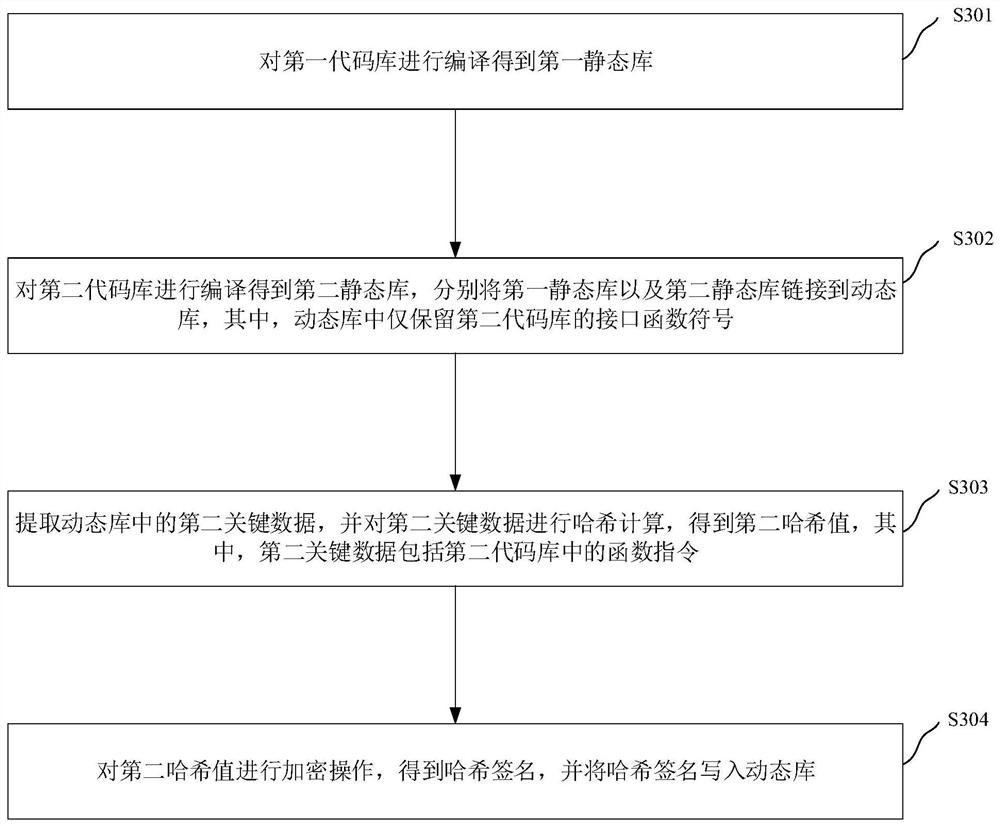
PendingCN112434286ALow securityPrevent from being calledDigital data protectionPlatform integrity maintainanceEngineeringCommon key
The invention relates to a dynamic library calling method and device, an electronic device and a storage medium, and the method comprises the steps: searching a dynamic library corresponding to an interface function address according to the interface function address of a first code library, wherein the first code library and a second code library are be pre-compiled into a static library and to be linked to the dynamic library, and the operation of the second code library depends on the interface calling of the first code library; extracting first key data in the dynamic library, and determining a first hash value of the first key data; acquiring a hash signature pre-stored in the dynamic library, and decrypting the hash signature by using a public key corresponding to the hash signatureto obtain a second hash value; and under the condition that the second hash value is the same as the first hash value, executing interface calling corresponding to the interface function address. Through the method and the device, the problem of low security caused by calling of the dynamic library under the unauthorized condition in the related technology is solved, and the technical effect of preventing the dynamic library from being called under the unauthorized condition is achieved.
Owner:ZHEJIANG DAHUA TECH CO LTD
Hand gesture recognition method, terminal and storage medium
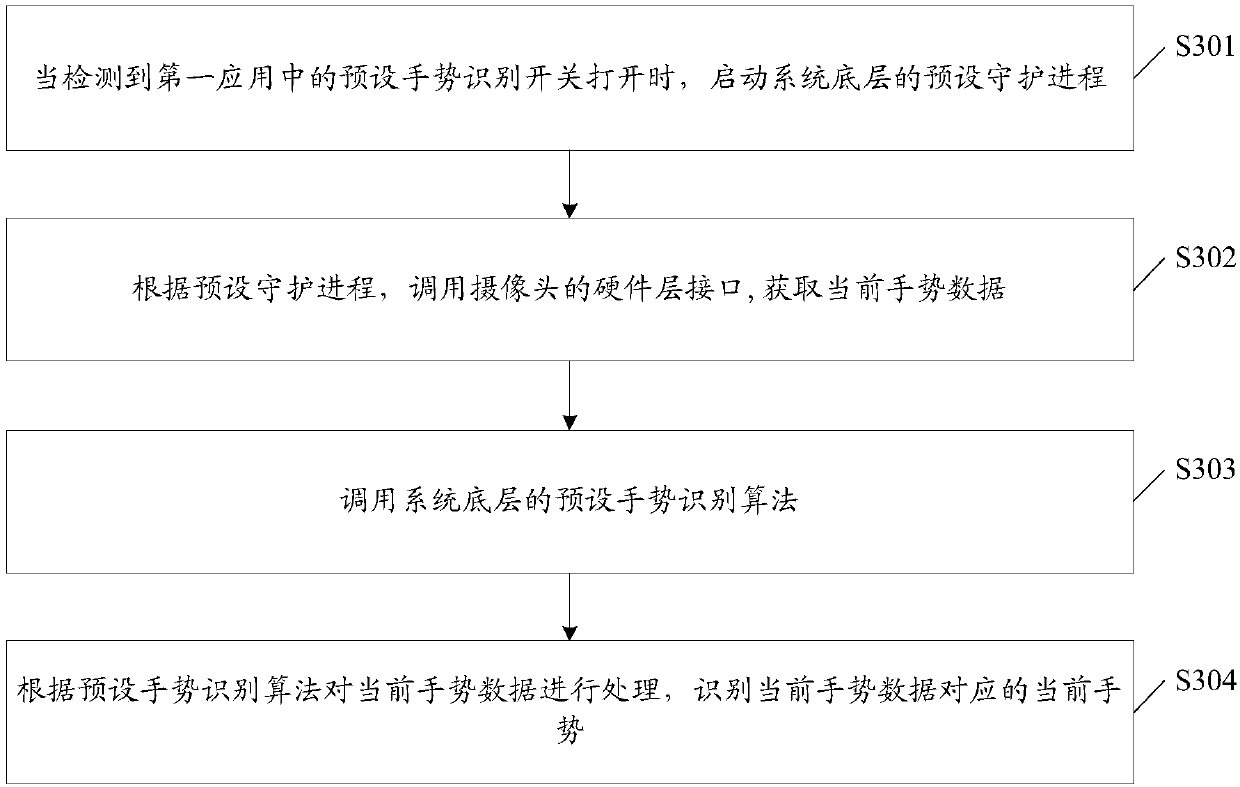
InactiveCN107844759AReduce memory consumptionImprove execution efficiencyCharacter and pattern recognitionLayer interfaceRecognition algorithm
The invention discloses a gesture recognition method. The method includes the following steps that: when it is detected that a preset hand gesture recognition switch in a first application is switchedon, the preset daemon process of the bottom layer of a system is started; the hardware layer interface of a camera is called according to the preset daemon process, current hand gesture data are acquired; the preset hand gesture recognition algorithm of the bottom layer of the system is called; and the current hand gesture data are processed according to the preset hand gesture recognition algorithm, a current hand gesture corresponding to the current hand gesture data is identified. The present invention also provides a terminal and a computer readable storage medium. With the above technical schemes of the invention adopted, the execution efficiency of the implementation of the hand gesture recognition of the terminal is improved on the whole.
Owner:NUBIA TECHNOLOGY CO LTD
Apparatus and method for preventing call from being dropped in mobile communication system
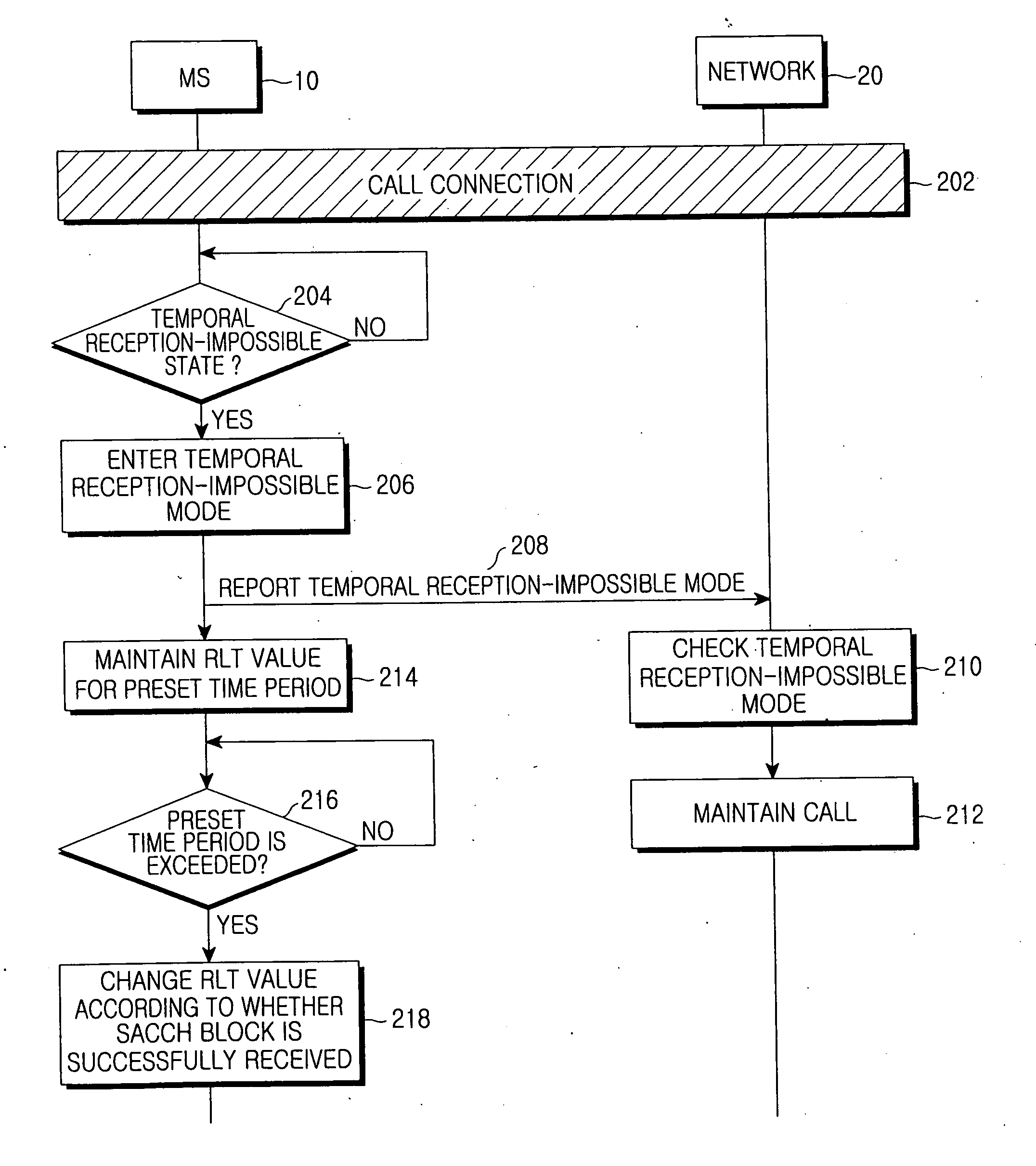
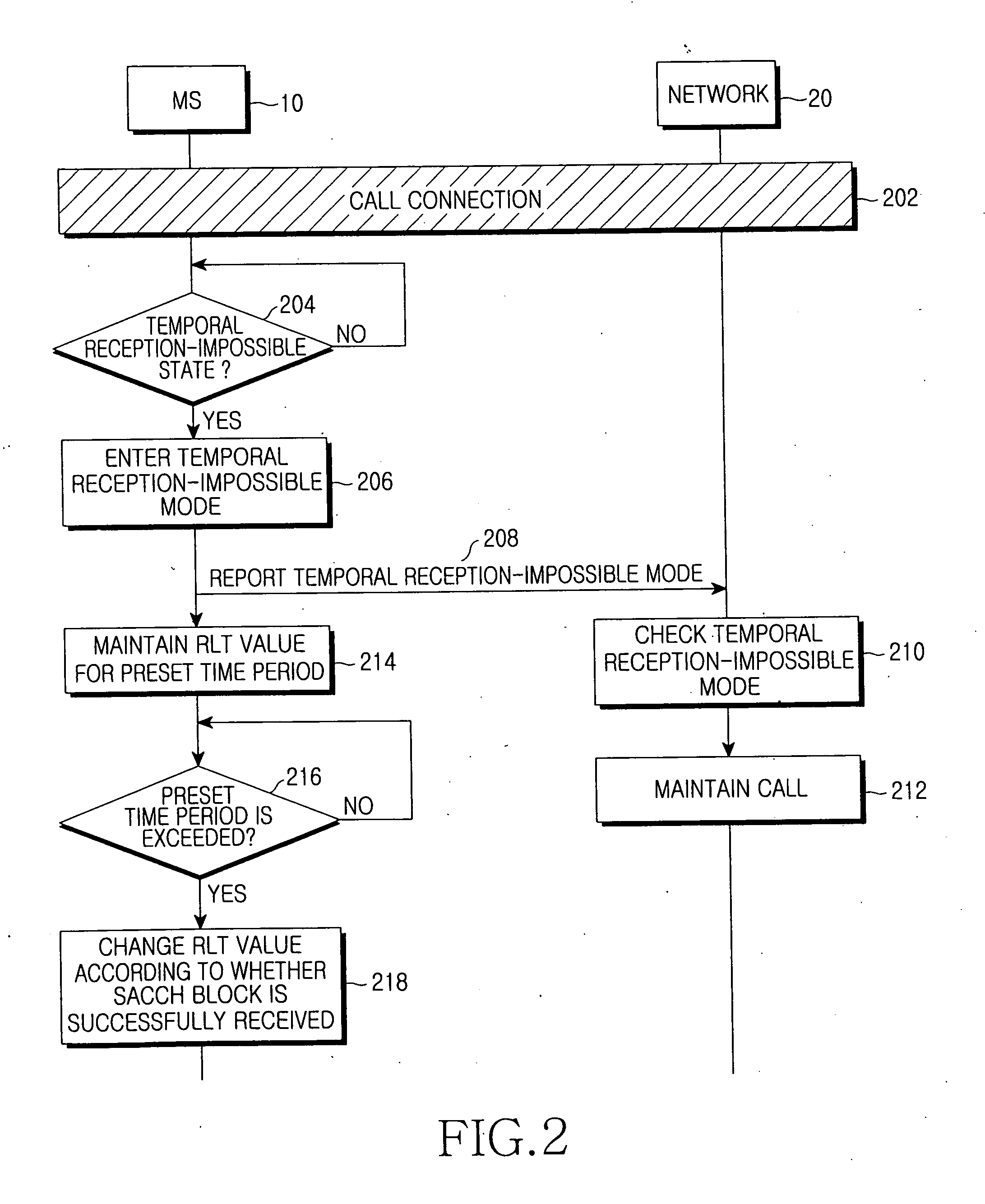
InactiveUS20070173250A1Avoid callingError preventionConnection managementTelecommunicationsTime segment
Disclosed is an apparatus for preventing a call from being dropped in a mobile communication system, including a Mobile Station (MS) for reporting a temporal reception-impossible mode to a network if the MS enters a temporal reception-impossible state in a state where a call has been connected, and maintaining a Radio Link Timeout (RLT) value during a preset time period; and the network for maintaining the call with the MS during a preset time period after the temporal reception-impossible mode is reported from the MS. According to the apparatus, a call is maintained during a preset time period when an MS is in a temporal reception-impossible state, so that it is possible to prevent a call from being dropped.
Owner:SAMSUNG ELECTRONICS CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com