Control flow hiding method for remote computing
A remote computing and control flow technology, applied in the computer field, can solve problems such as high overhead, reduce operating overhead, avoid cross-cloud or cross-host function calls, and achieve real hidden effects
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
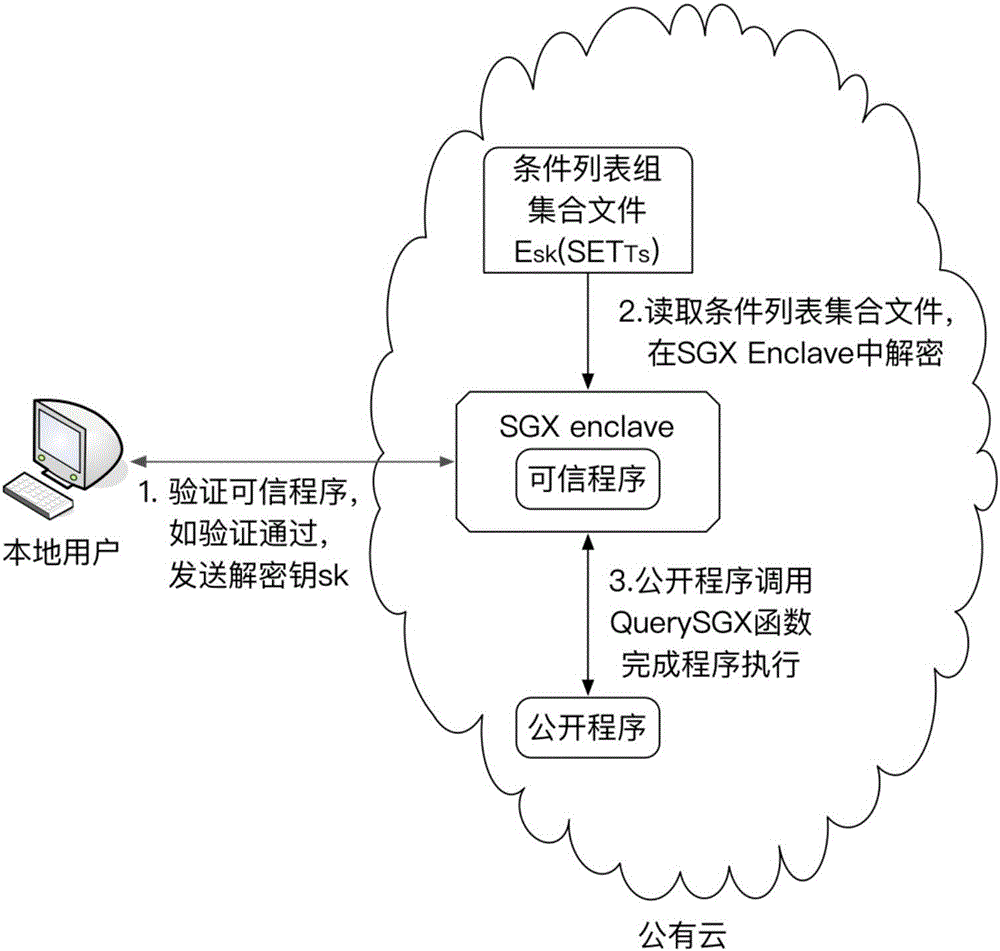
[0047] The present invention will be further described below by means of the accompanying drawings and examples.
[0048] Step 1, obtain the user program, and convert the user program into a three-address code program;
[0049] Described three address code program comprises 1 statement, wherein any one statement is s i , i=1, 2, ... I, I are natural numbers greater than or equal to 1, statement s i by J branch statements x j and M non-branching statements y m Composition, j=1,2,...J, m=1,2,...M, Jj It is: if (a OP b) goto L; a, b are branch statements x j variable, OP is a comparison operation, which is one of the six operations (>, =, i |i=1,2,...I};
[0050] branch statement x j The unique number is l j ; non-branch statement y m The number is l j ;
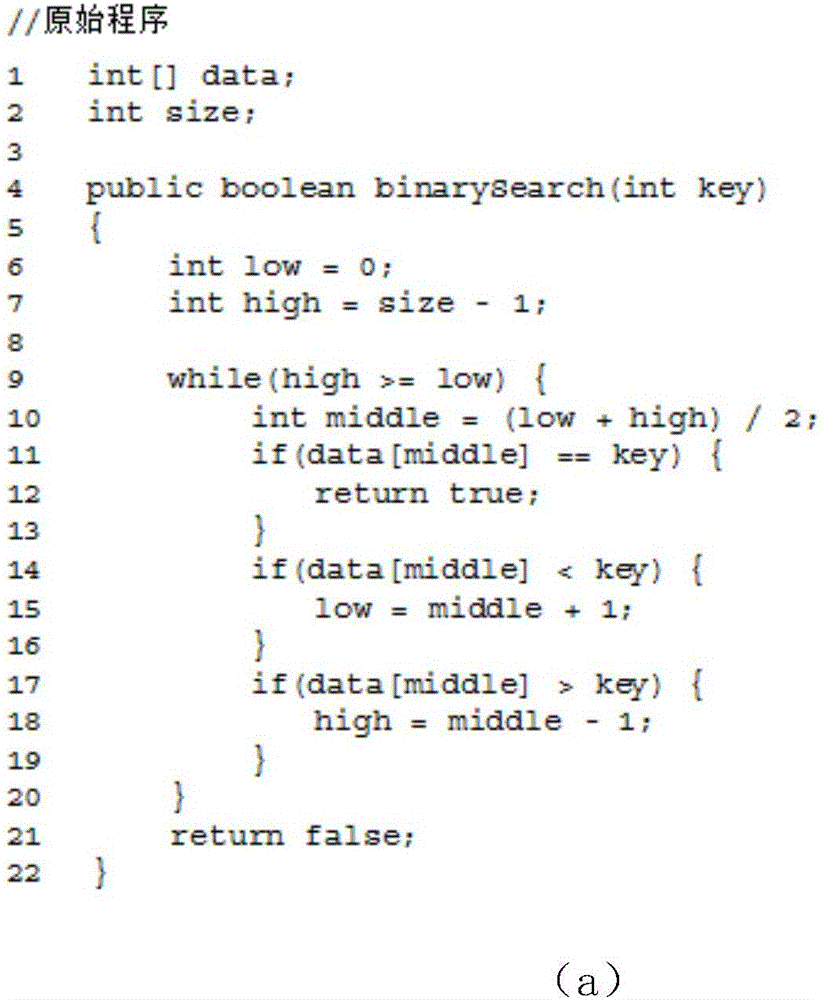
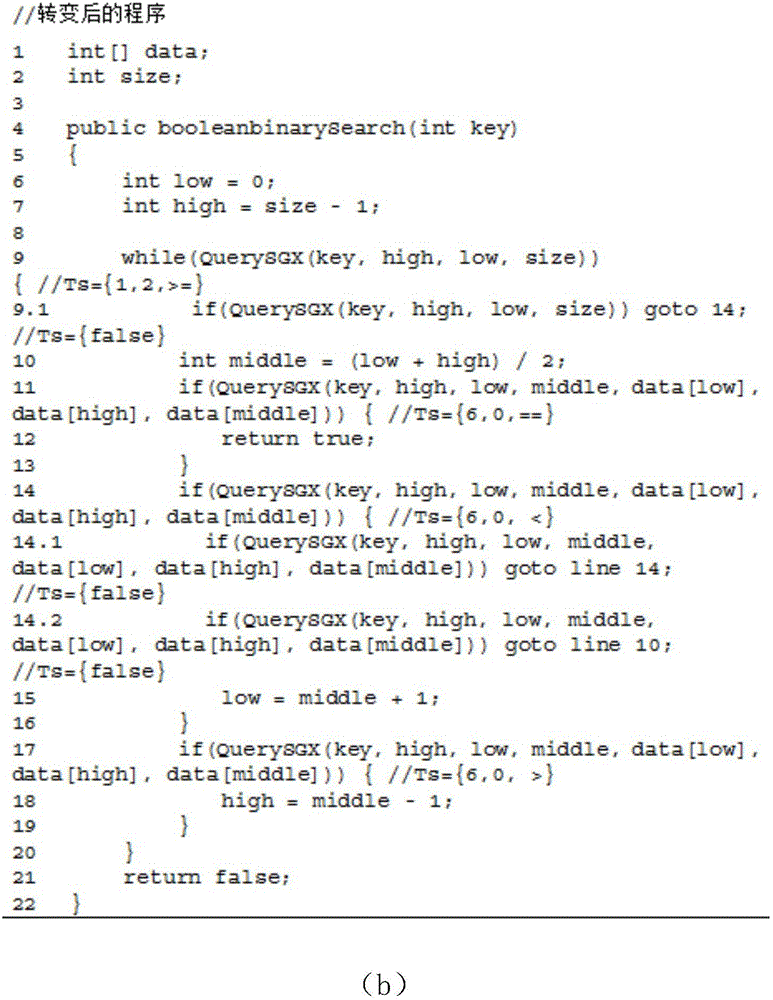
[0051] The statement s in this embodiment i Refers to: any statement in the program, such as figure 2 int size; int low=0 in (a).
[0052] The branch statement x in this embodiment j Refers to: the selection state...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com