Android application program protection method based on Dex2C and LLVM
A technology for application programs and protected objects, applied in the field of virtualization, can solve problems such as reduced efficiency and insufficient protection capabilities, and achieve the effect of raising the threshold, avoiding reflective calls and redundant loop operations, and preventing reverse cracking
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
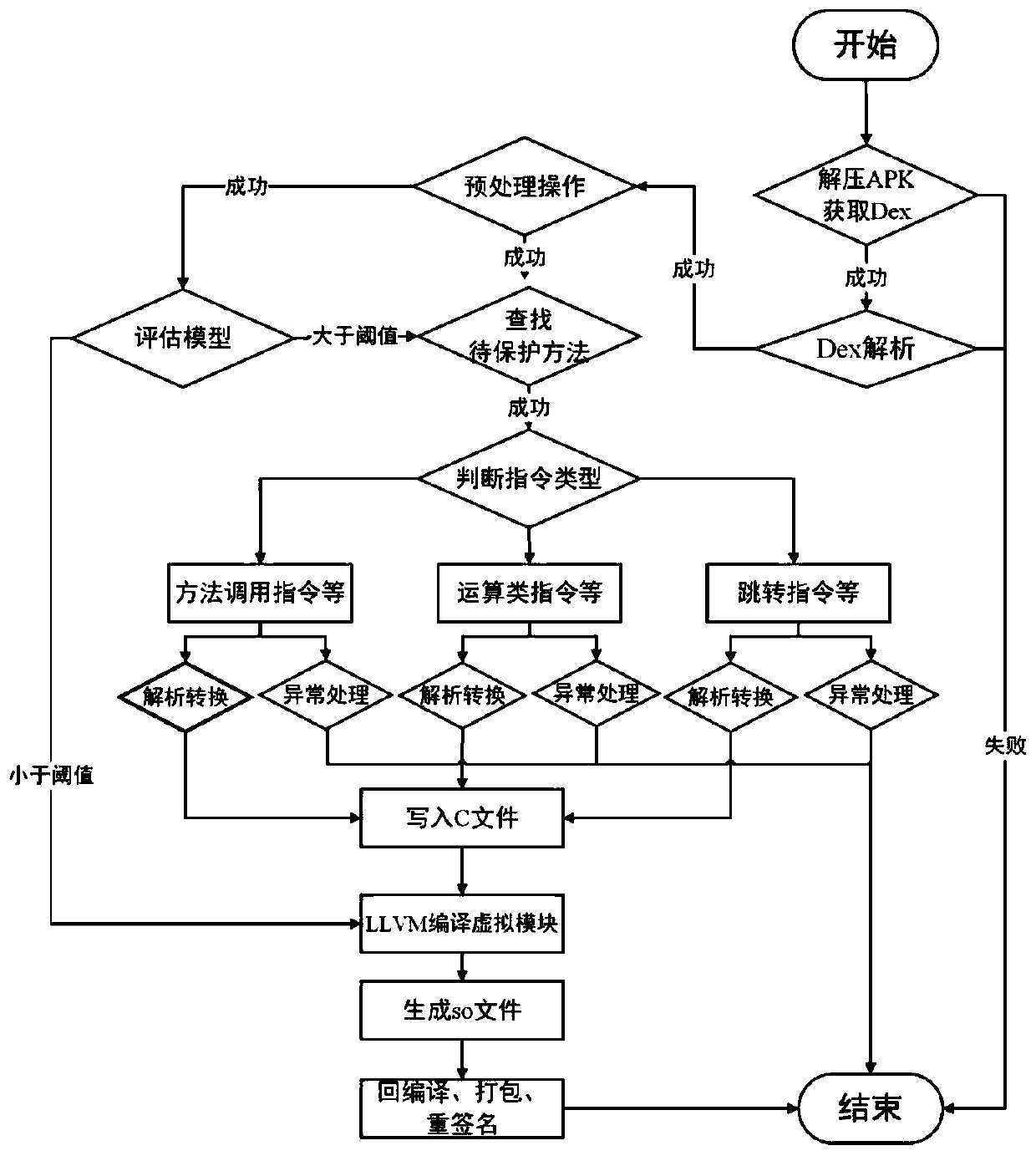
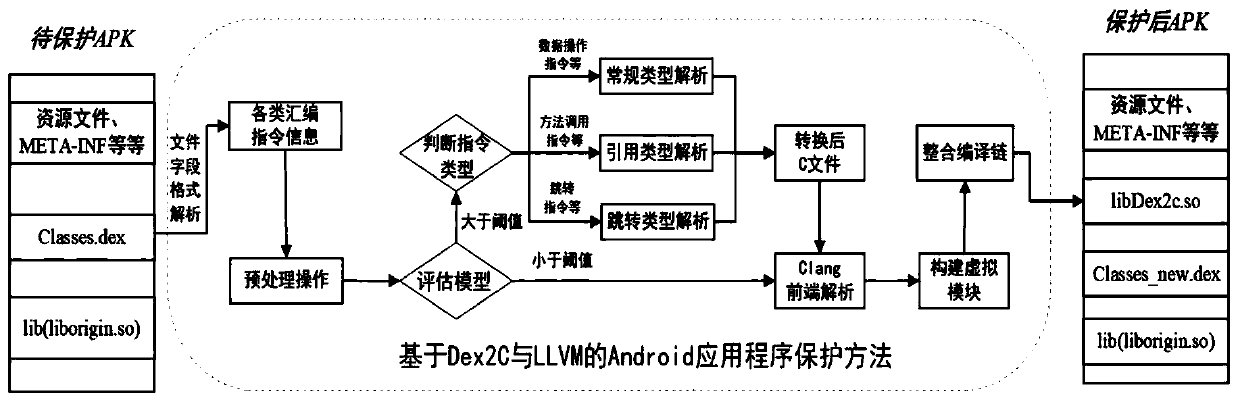
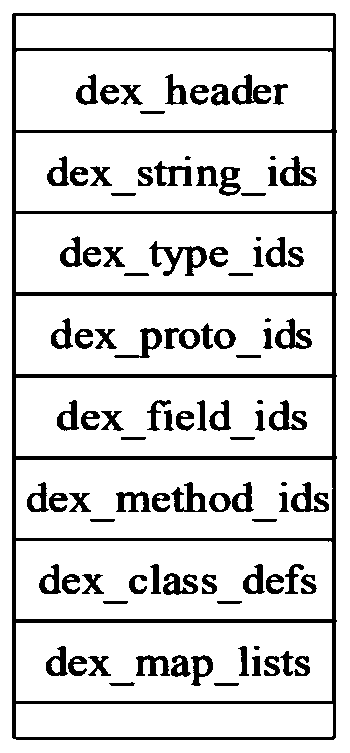
[0041]The present invention proposes an Android application program protection method based on Dex2C and LLVM, the core of which is to convert the method to be protected in the Dex layer into corresponding C code and use LLVM-based virtualization during compilation. Dex2C first decompresses the APK file and parses the Dex file to obtain the Node node information of each instruction, and then converts the function declaration and function body. This solution designs three conversion logics for 256 assembly instructions, compiles the converted C code through the LLVM virtualization module, forms a virtualized binary So file specific to the CPU architecture, and repackages and signs to generate a new APK. The application program protected by the present invention can effectively reduce the volume of APK and improve the execution efficiency of APK on the one hand; on the other hand, it can also increase the reverse attack cost of malicious attackers on the Dex layer and the local l...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com