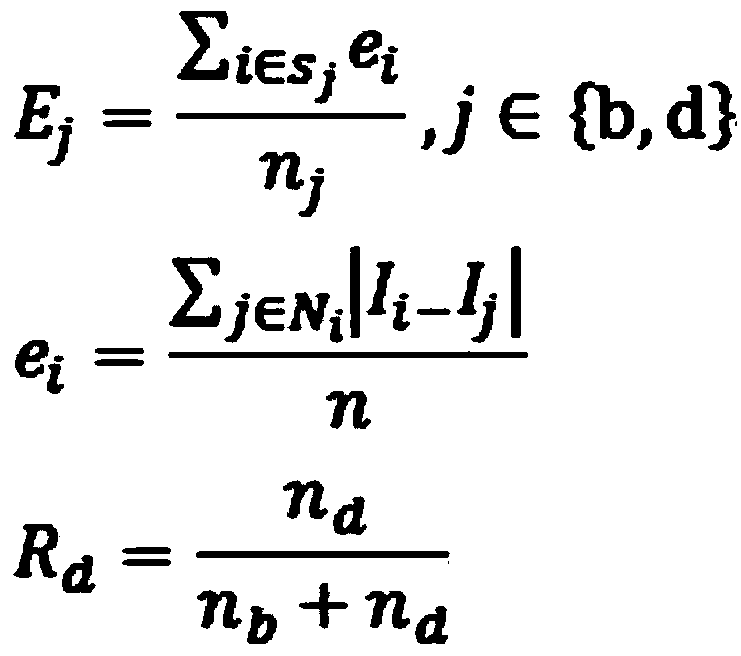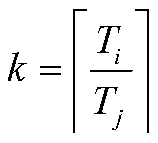Patents
Literature
106results about How to "Reduce operating overhead" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
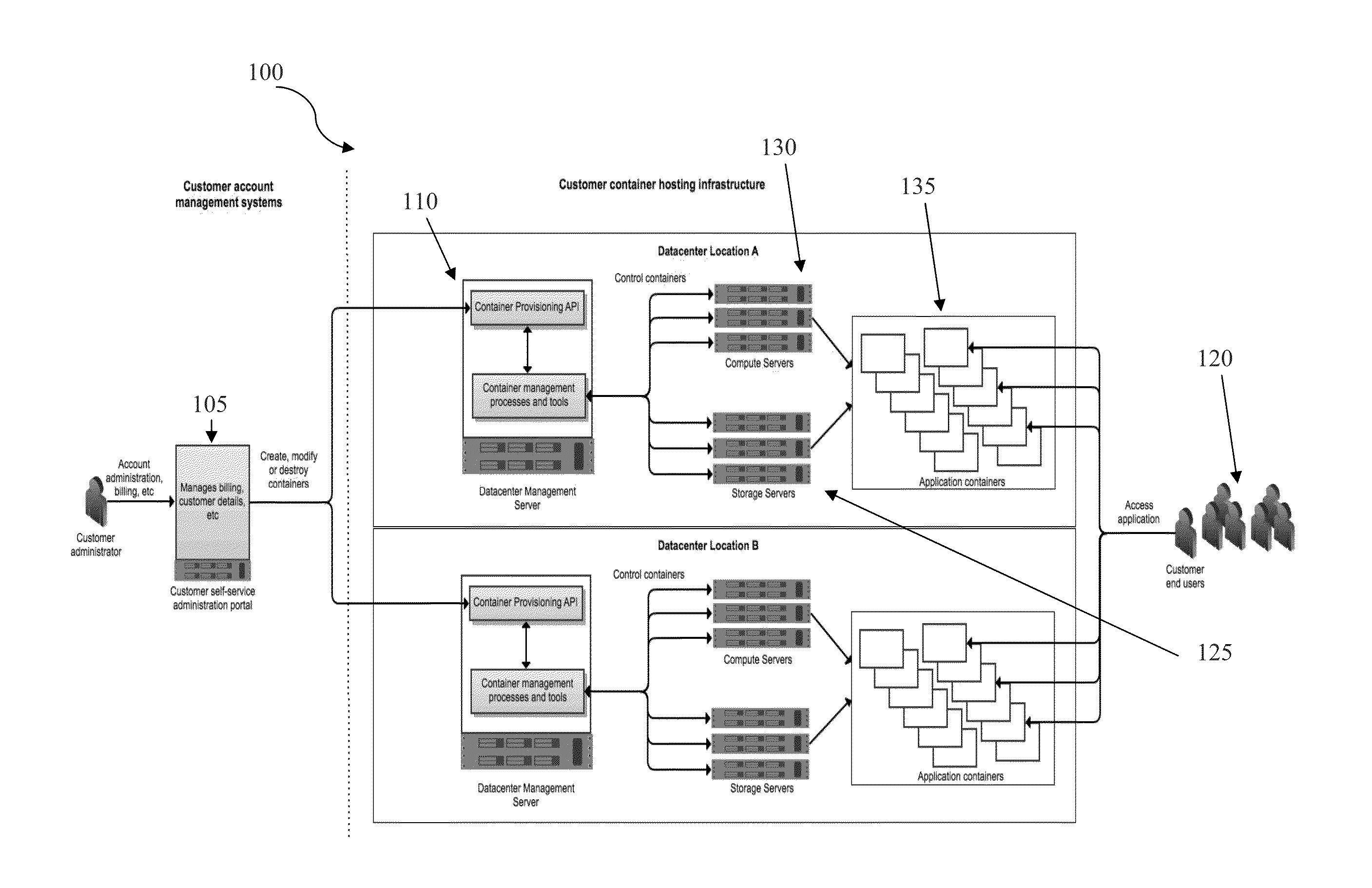
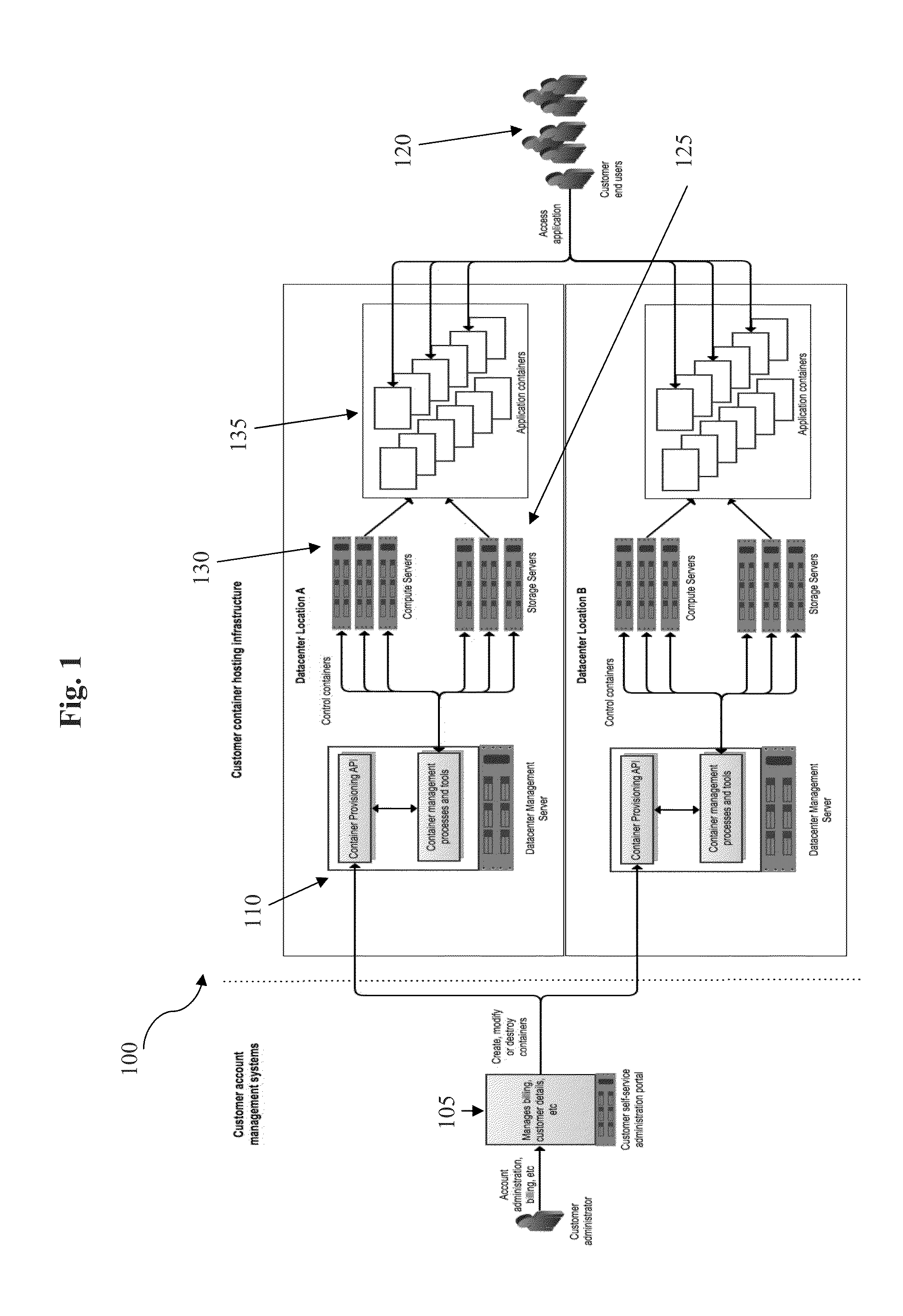
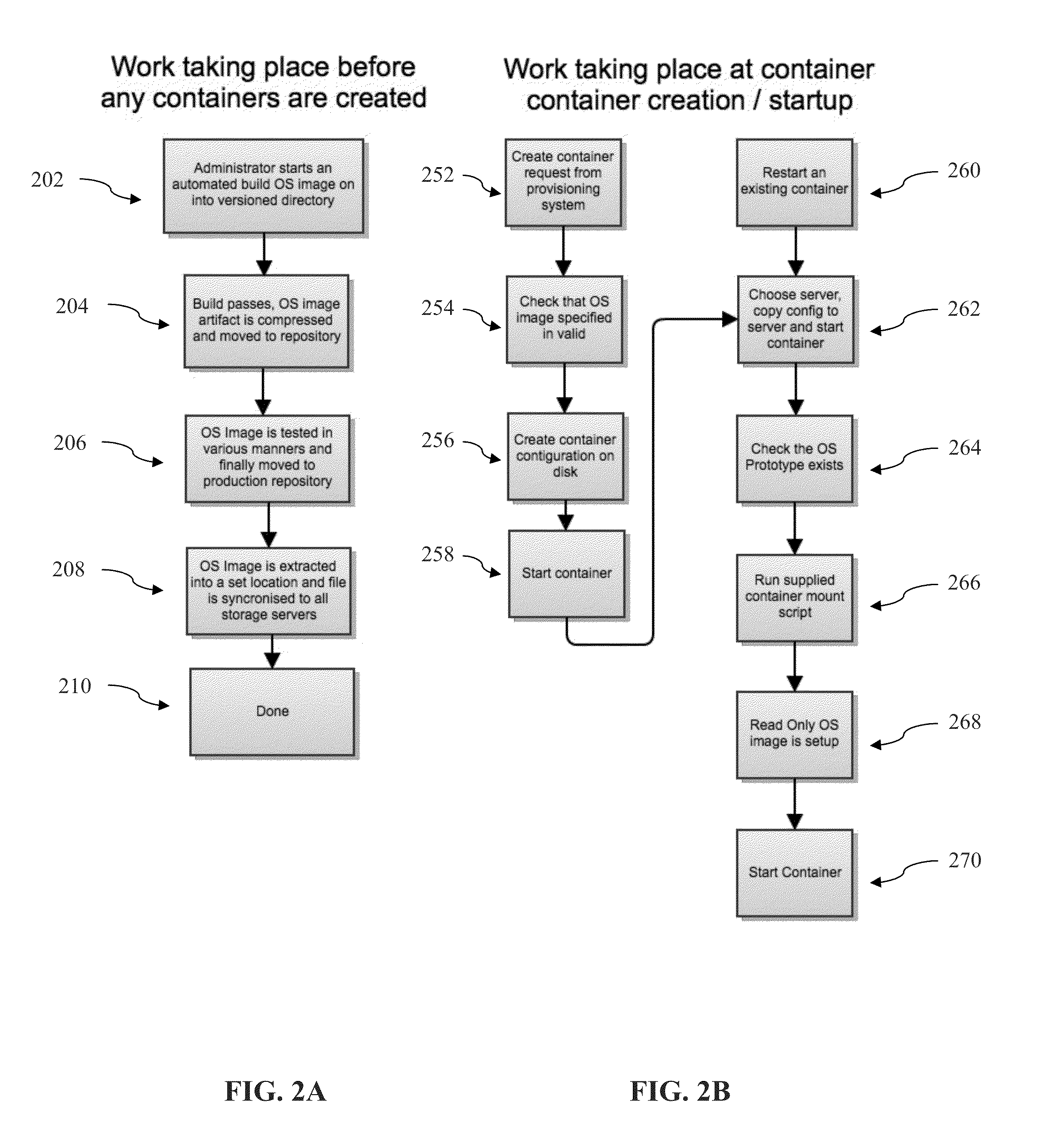
Efficient hosting of virtualized containers using read-only operating systems
ActiveUS20140053150A1Reduce resource usageReduce operating overheadSoftware simulation/interpretation/emulationMemory systemsComputer hardwareVirtualization
A single operating system image is shared among multiple running virtualized containers such that each running container interacts with underlying shared files and resources in system storage. Each container running on a server are provided the same image, which remains consistent among the containers. Each image is named and versioned and each container is configured in a manner that defines which underlying image is used when the container is started. When updates to the image are made, a new image is be generated, and the containers are be switched to the new image by changing configuration properties associated with the container and restarting the container.
Owner:ATLASSIAN
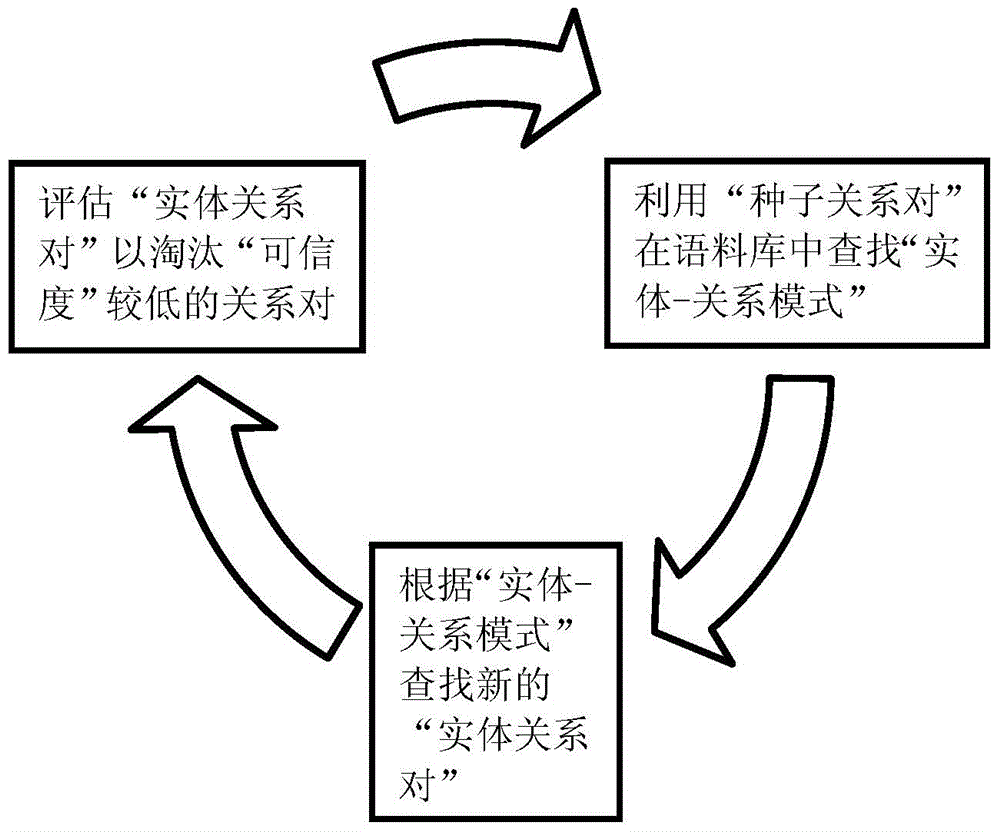
Method for extracting relations among named entities in Internet massive data and system thereof
ActiveCN104933164AImprove recallImprove scalabilityWeb data indexingSpecial data processing applicationsThe InternetEntity relation extraction
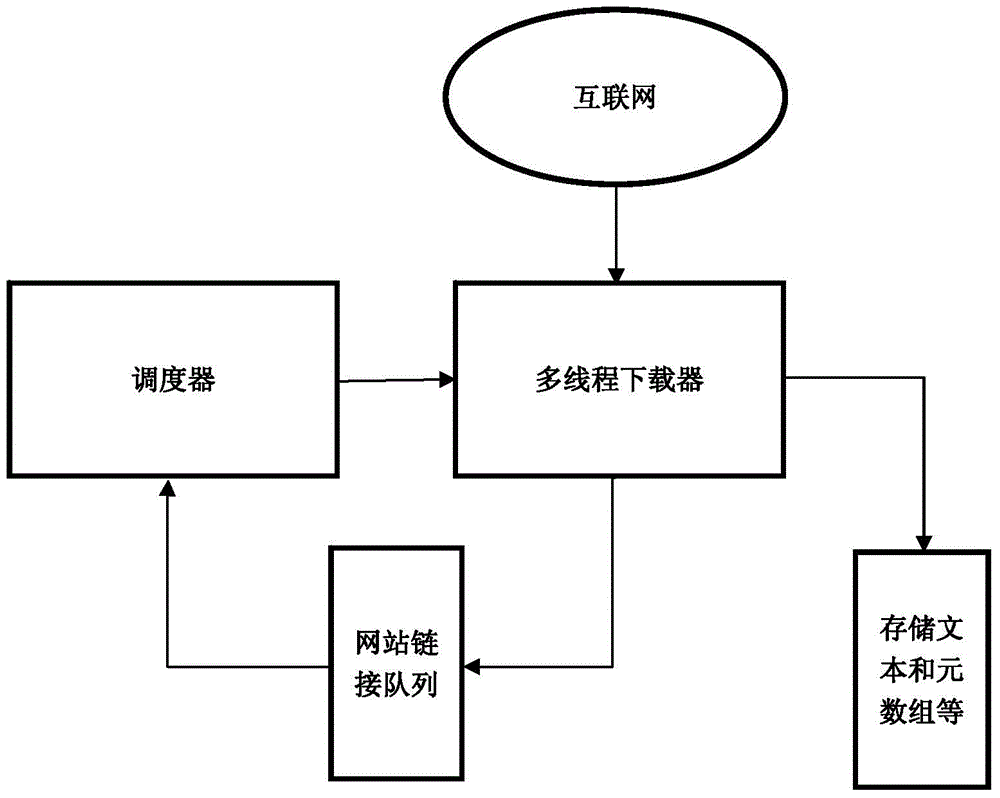
The invention discloses a method for extracting relations among named entities in Internet massive data. The method comprises the following steps: crawling network information and constructing a corpus; preprocessing texts; extracting keywords representing short document features; acquiring 'entity-relation modes' representing entity relations; annotating the relations, and finding new 'entity-relation pairs' from a large quantity of unstructured texts by using the modes; and evaluating the entity-relation pairs. The invention also discloses a system for implementing the method for extracting the relations among the named entities in Internet massive data. The system comprises a network information crawling module, an information preprocessing module, a feature word extraction module and an entity relation extraction and evaluation module. The method and the system have the advantages of greater convenience in extension of a relation lookup system, high running efficiency and the like.
Owner:SOUTH CHINA UNIV OF TECH
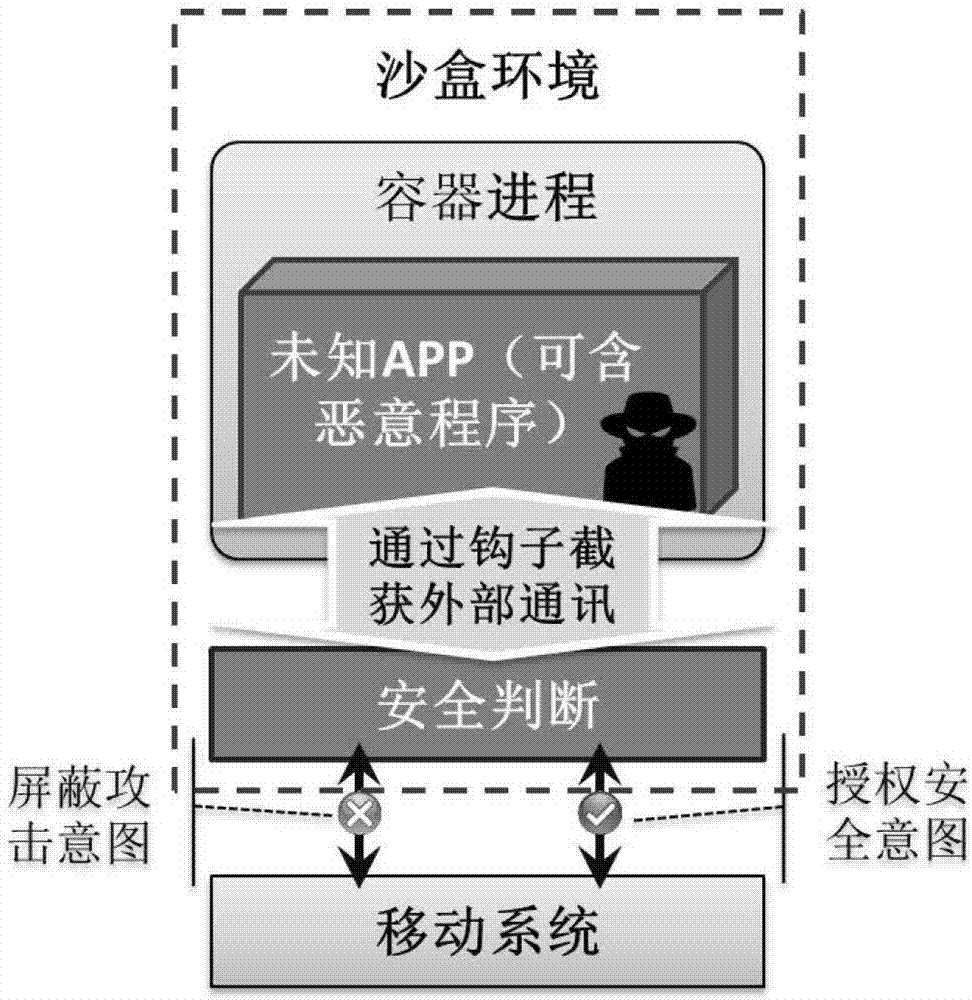
Root-permission-free safe virtual mobile application program running environment system, method and application
InactiveCN106897611ARun program securityPrevent movementPlatform integrity maintainanceOperational systemAccess time
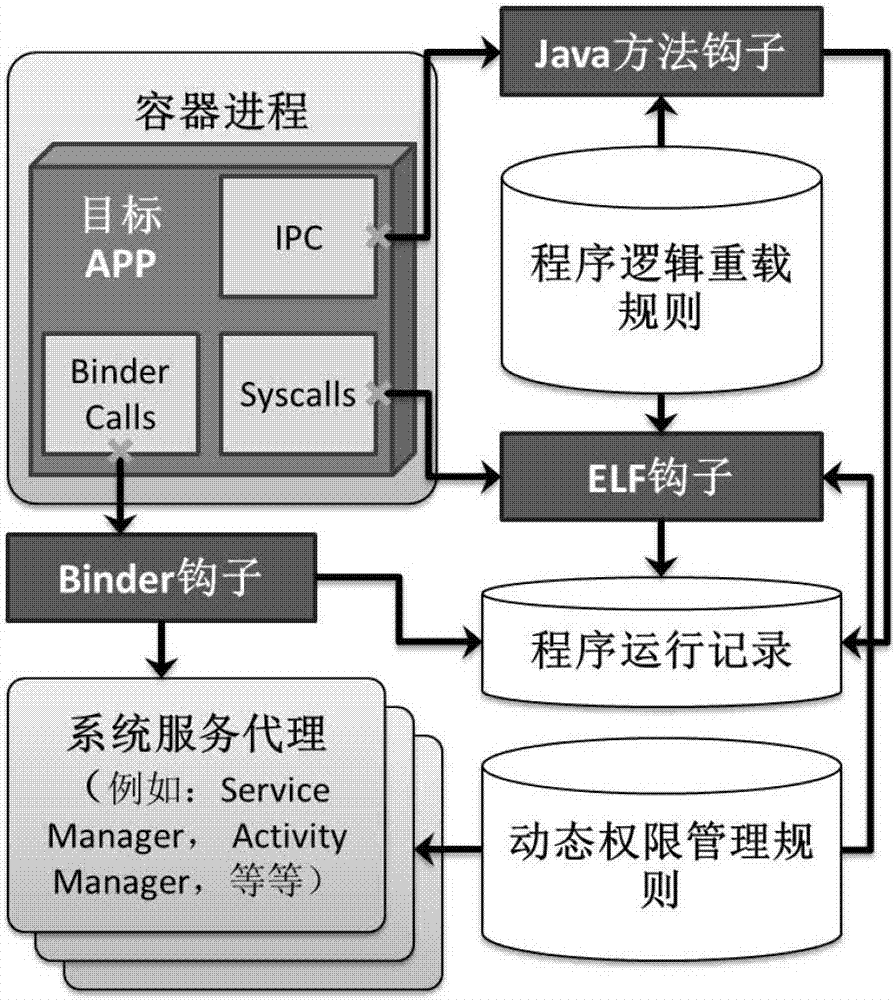
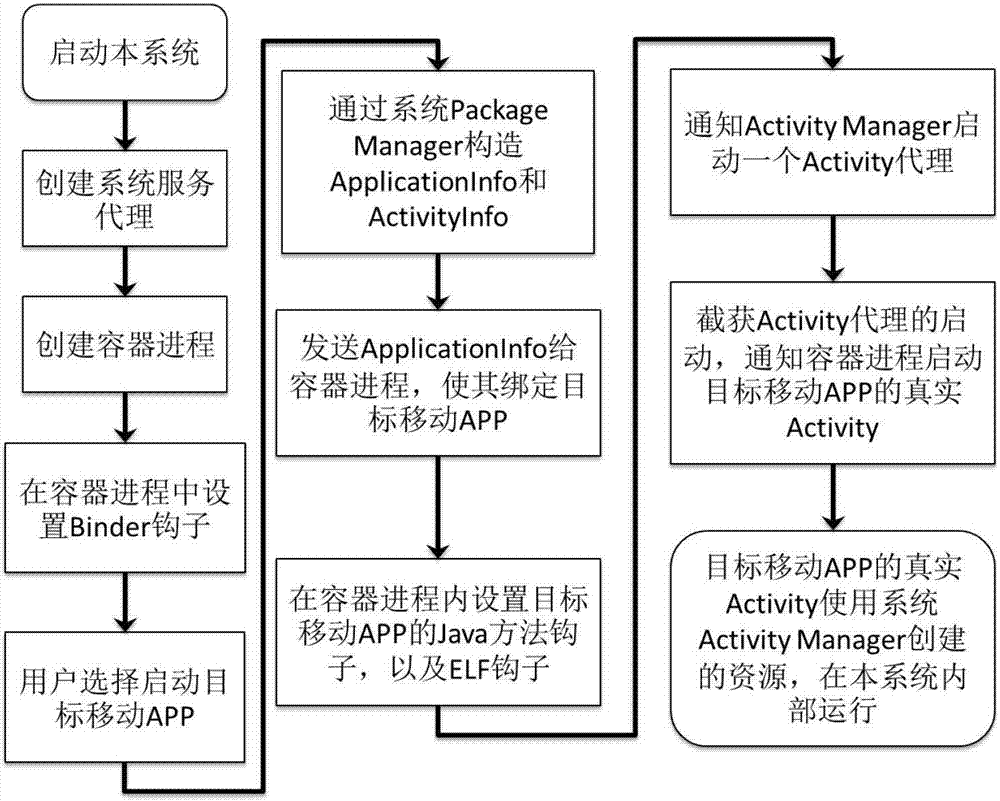
The invention discloses a root-permission-free safe virtual mobile application program running environment system, method and application. A user opens a virtual running environment control program and selects a target mobile application program; a container process loads the target application program; a hook is arranged in the container process, and communication and interface calling of the target application program and an operation system is dynamically intercepted through the hook method; a proxy service agents target application program and operation system interaction according to a request for intercepting communication and interface calling; a safety module analyzes the target application program and operation system interaction, and dynamic permission control over the interaction is achieved through the proxy service; a log module records all system access time and contents, and bases are provided for further safety analysis. The system is a safe virtual environment which can directly run in an existing Android system and support and protect running of target mobile programs, the running cost is low, root permission does not need to be obtained, the existing Android system does not need to be modified, and compatibility and applicability are high.
Owner:JIN GUANG +1
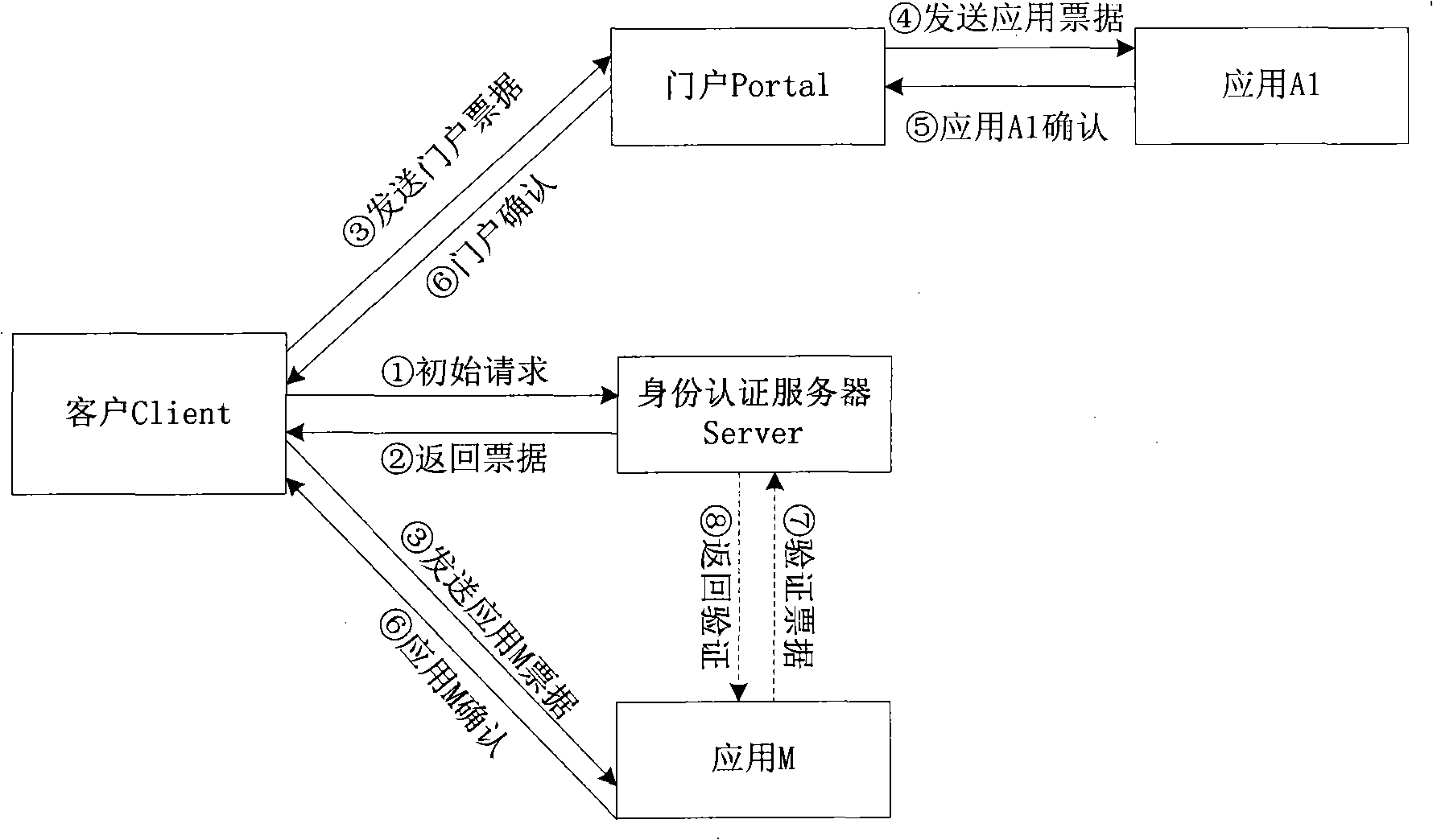
Single-point login method under point-to-point model
ActiveCN101286843AReduce the burden onImprove operational efficiencyPublic key for secure communicationUser identity/authority verificationService modeSecure channel
The invention relates to a single sign-on method in a point to point mode. Being different from the existing single sign-on method based on a customer server mode, the method manages the single sign-on life cycle of a customer by using valid period of certificate of the customer, and the customer can sign on for a plurality of times with single certification. The method completes the cross-certification of an application system and an identity certification server; the shared encryption key of communication parties is initialized, and a safe channel between the customer and the application system is established. Through the the identity certification server and the cross-certification of the application system, any application system can independently carry out identity certification, thus weakening the status of a central identity certification server, avoiding the defect of single-point failure in traditional customer / service mode and being characterized by low cost for system operation, high efficiency and good safety performance.
Owner:江西省电力信息通讯有限公司
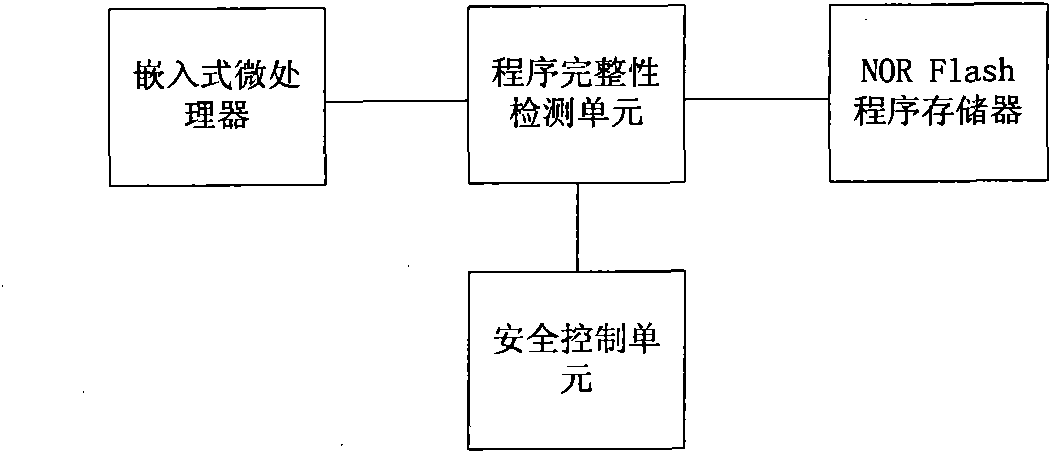
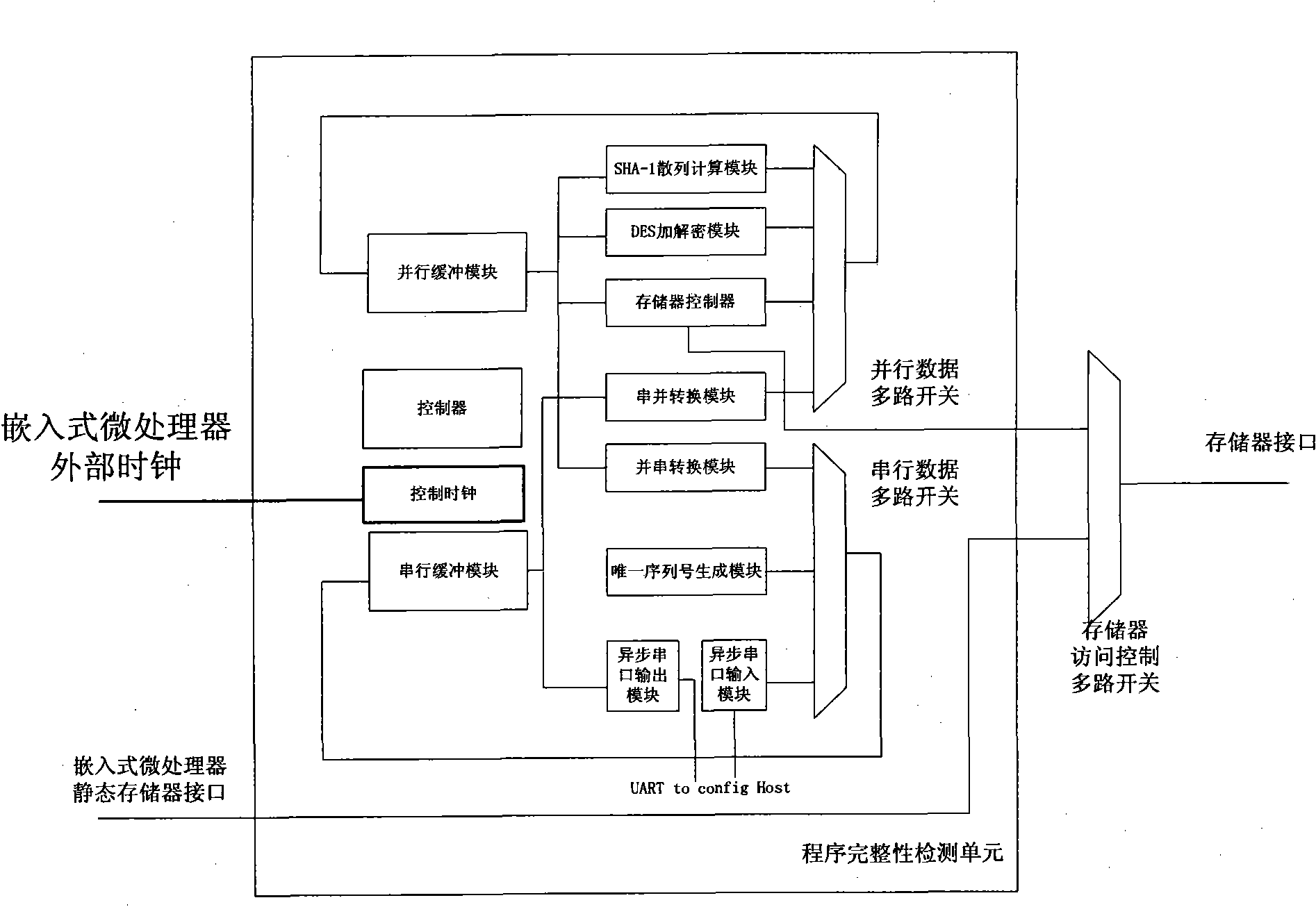
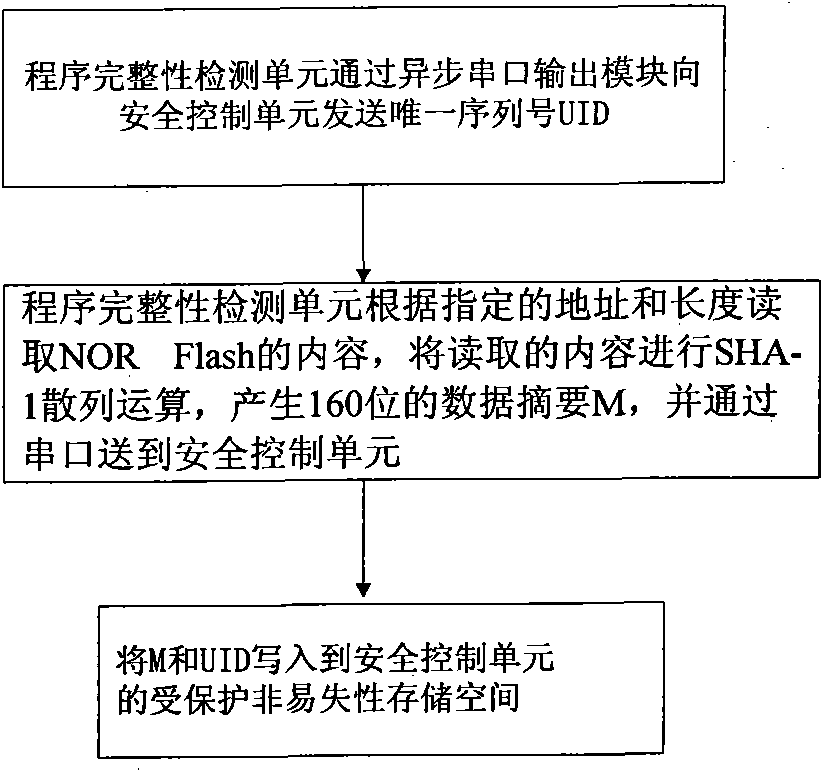
Embedded-type system for ensuring completeness of program and realization method thereof
InactiveCN101882189AEasy to tamper withEasy to implementDigital data protectionHash functionRunning time
The invention discloses an embedded-type system for ensuring the completeness of a program, which comprises an embedded-type microprocessor, a storage device, a program completeness detection unit and a safety control unit wherein: the program completeness detection unit is used for detecting content of an appointed area of the storage device before the running, utilizing a standard hash function to calculate the hashed value of the area in the appointed area, for encrypting the hashed value and for transmitting the hashed value to the safety control unit; and the safety control unit is used for storing a correct hashed value of the content in the appointed area of the storage device, for comparing the correct hashed value with a running time hashed value which is transmitted by the completeness detection unit, and for judging whether the appointed area is altered. The invention also discloses a realization method of the embedded-type system for ensuring the completeness of the program, which comprises a configuration process and a running time detection process. The embedded-type system solves the safety problem that the code in the conventional system is easy to be altered, has the advantages of universality, low cost, less running expenditure and the like, and is particularly suitable for ensuring the completeness of the most basic trusted root of the embedded-type system.
Owner:SOUTH CHINA UNIV OF TECH
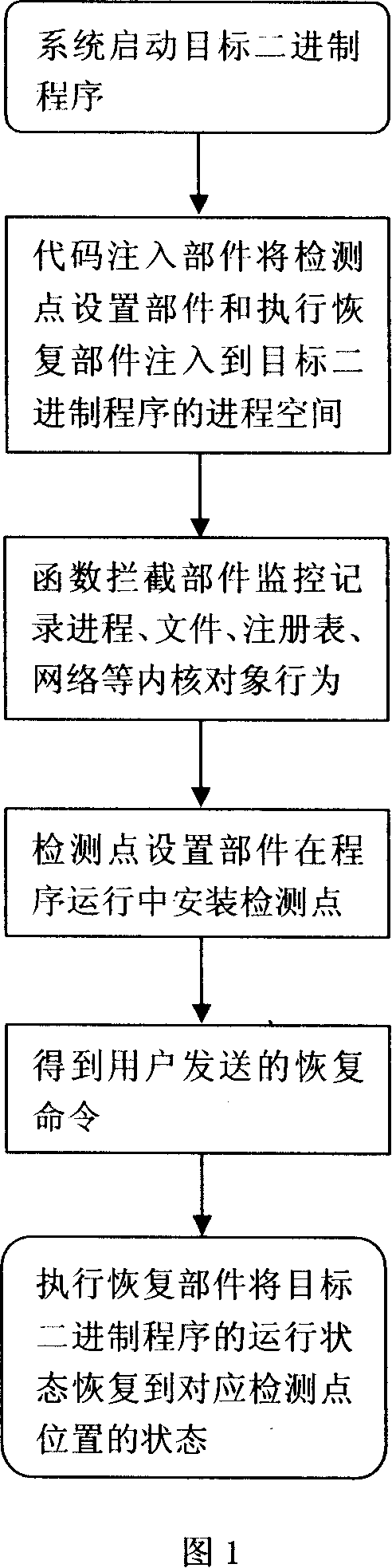
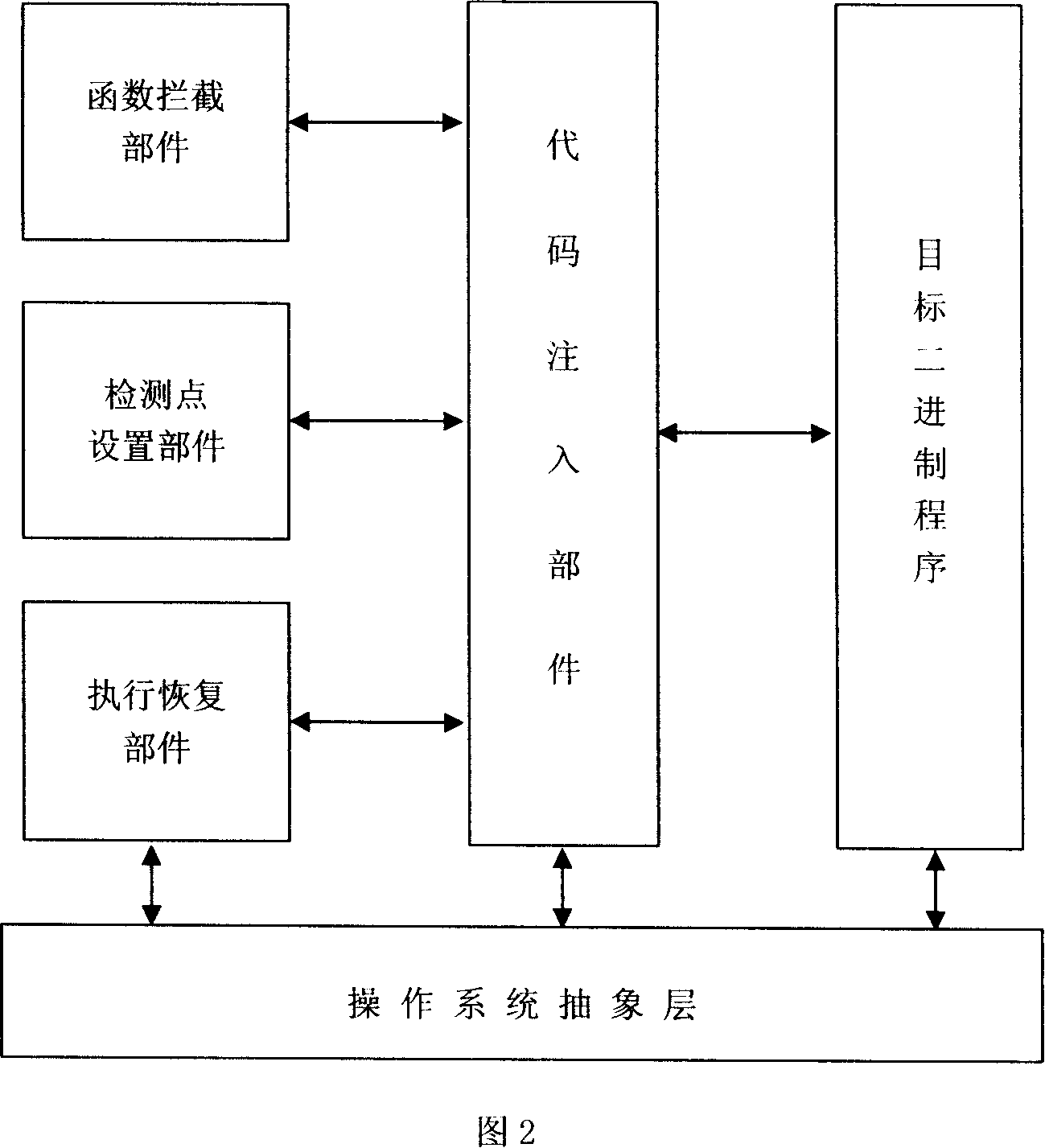
Method for performing recovery and playback when running software
InactiveCN101154185AGood operating environmentReduce operating overheadSoftware testing/debuggingPoint setSoftware
The invention relates to a method of carrying out restoration and playback when a computer binary program operates. The system consists of a code filling part, a function interception part, a monitoring point setting part and an executive restoration part. The method is that the system starts the target binary program, the code filling part fills the monitoring point setting part and the executive restoration part into the process space of the target binary program; the action of inner cores such as a process, a file, a registration form, a network, etc. is monitored and recorded through the function interception part; monitoring points are arranged by the monitoring point setting part in the operating process of the program; after the executive restoration part gets a restoration command, the operating state of the target binary program is restored to the state corresponding to the position of the monitoring points by the executive restoration part. The invention is applicable for the analysis and fault-tolerance of an unknown binary program, and is applicable for improving the efficiency of analyzers and supporting the analysis and repair of errors in the operation of software.
Owner:UNIV OF ELECTRONIC SCI & TECH OF CHINA
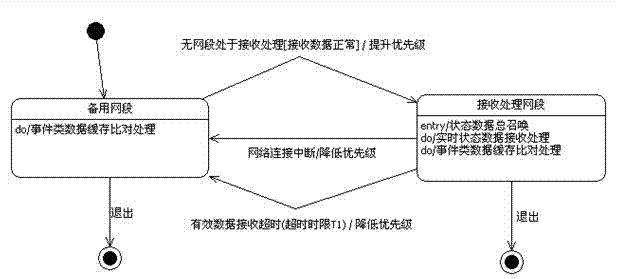
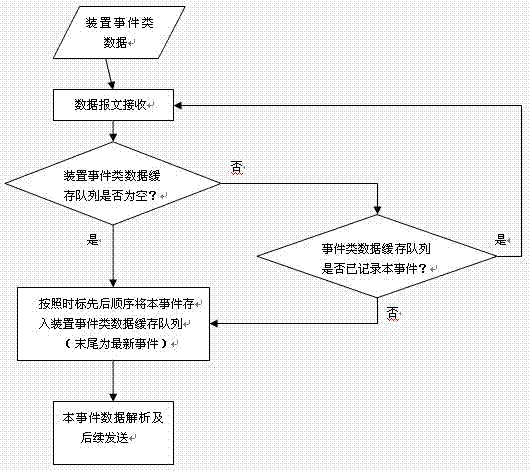
Method for synchronously receiving and processing real-time data under dual-network redundancy mechanism
ActiveCN102833119ASimplify processing logicReduce operating overheadCircuit arrangementsData switching networksReal time data transmissionReal-time computing
The invention relates to a method for synchronously receiving and processing real-time data under a dual-network redundancy mechanism. According to the real-time data transmission requirements and characteristics of dual-network redundancy mechanism of an automatic system of a transformer substation, a network segment inter-zone time limit dynamic priority selection strategy, a network segment automatic handoff trigger active summoning strategy and an event list cache comparing strategy to realize screening and synchronization of the dual-network real-time uploaded data to guarantee the receiving and processing of the station level and ensure that the station level can timely acquire the effective data without losing, and effectively screen and separate the redundant, repeated and even abnormal uploaded data.
Owner:南京国电南自轨道交通工程有限公司
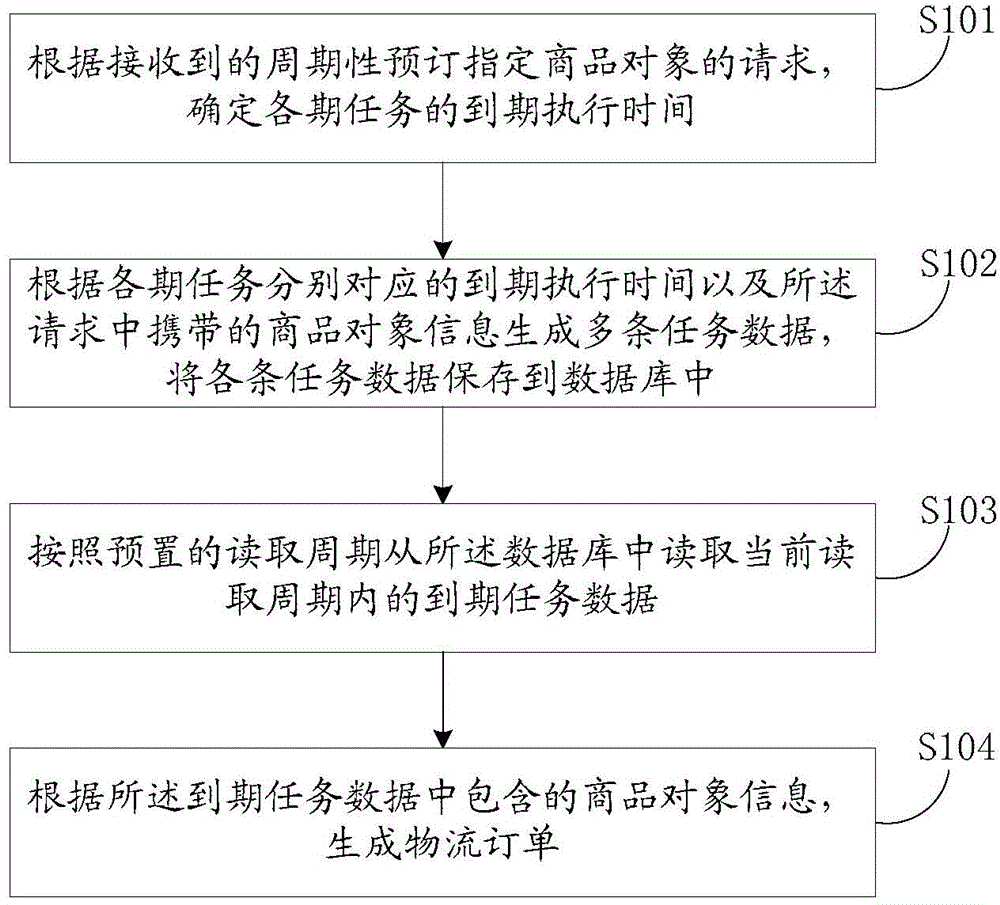
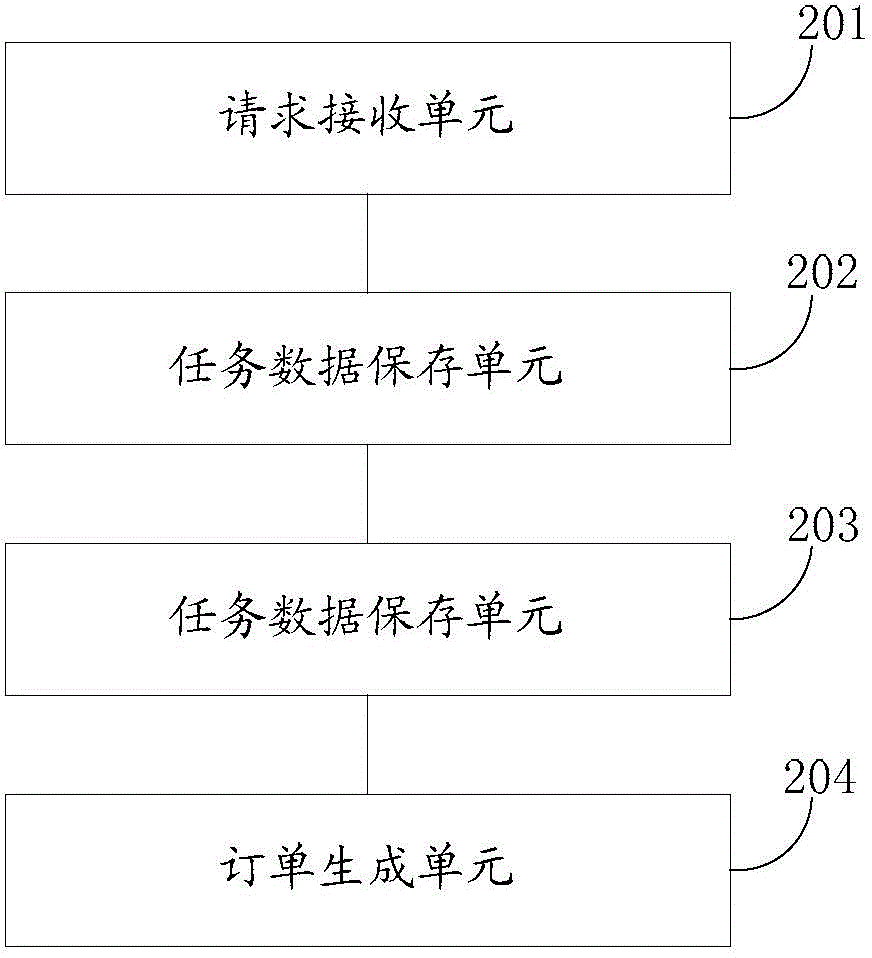
Method and system for processing periodic order information
InactiveCN104951852AReduce operating overheadBuying/selling/leasing transactionsResourcesApplication serverE-commerce
A method and a system for processing periodic orders placed by e-commerce user. A server system is used to determine execution times of multiple tasks of placing orders according to a user request received for placing periodic orders of a selected product. The server system generates and stores into a database the periodic tasks. Application servers read from the database, due tasks and execute the read due tasks to create logistic orders for shipping the product. The user periodically receives ordered product at specified times, without a need to re-order.
Owner:ALIBABA GRP HLDG LTD
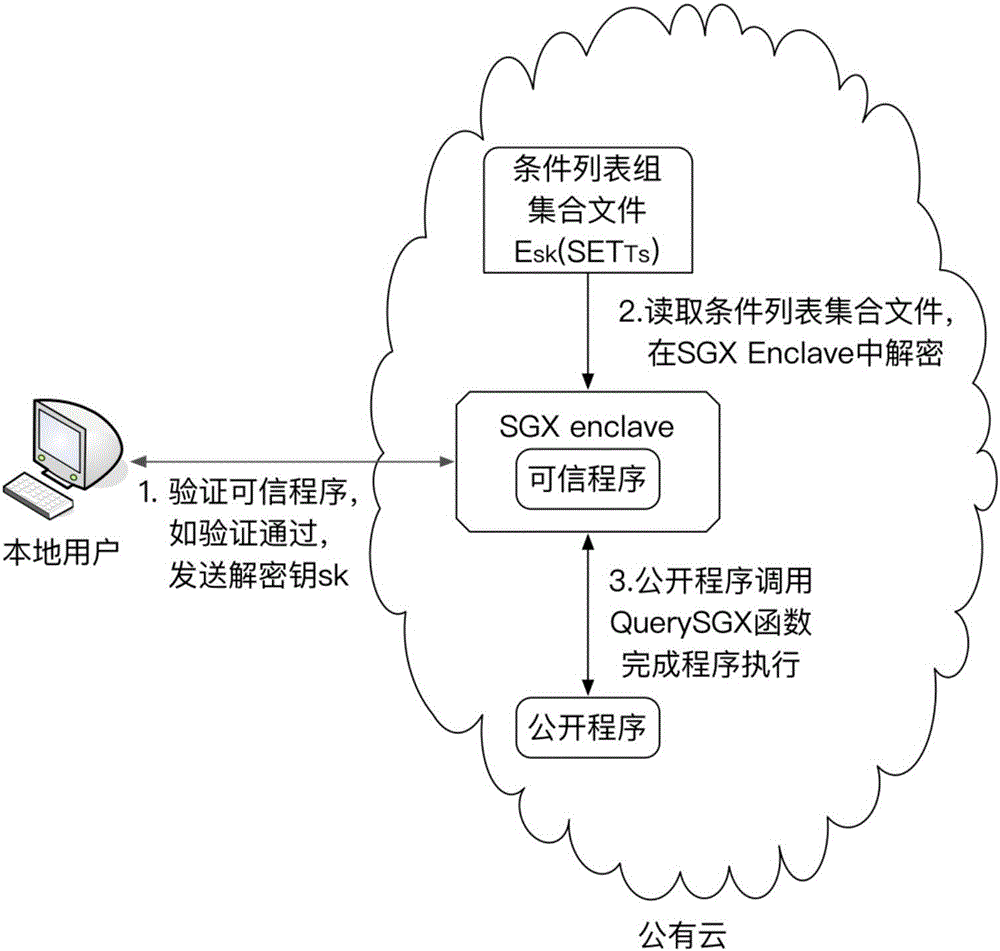
Control flow hiding method for remote computing
ActiveCN106845168AReduce operating overheadAchieve real hiddenSoftware designTransmissionControl flowIntel processor
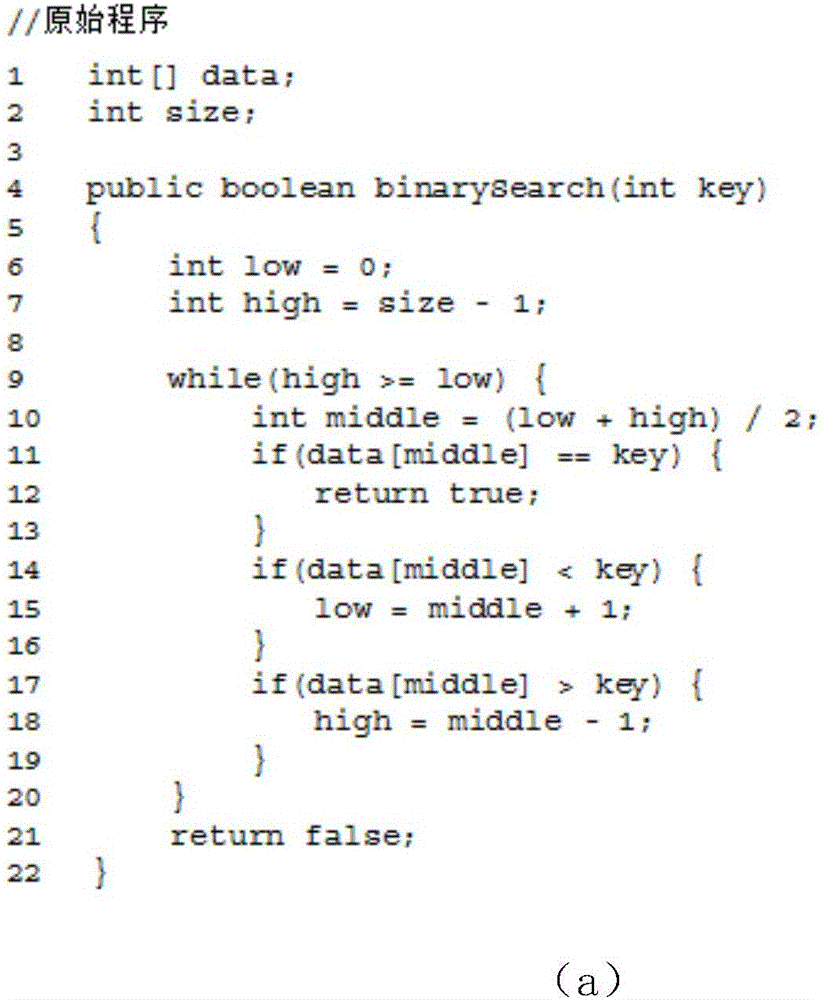
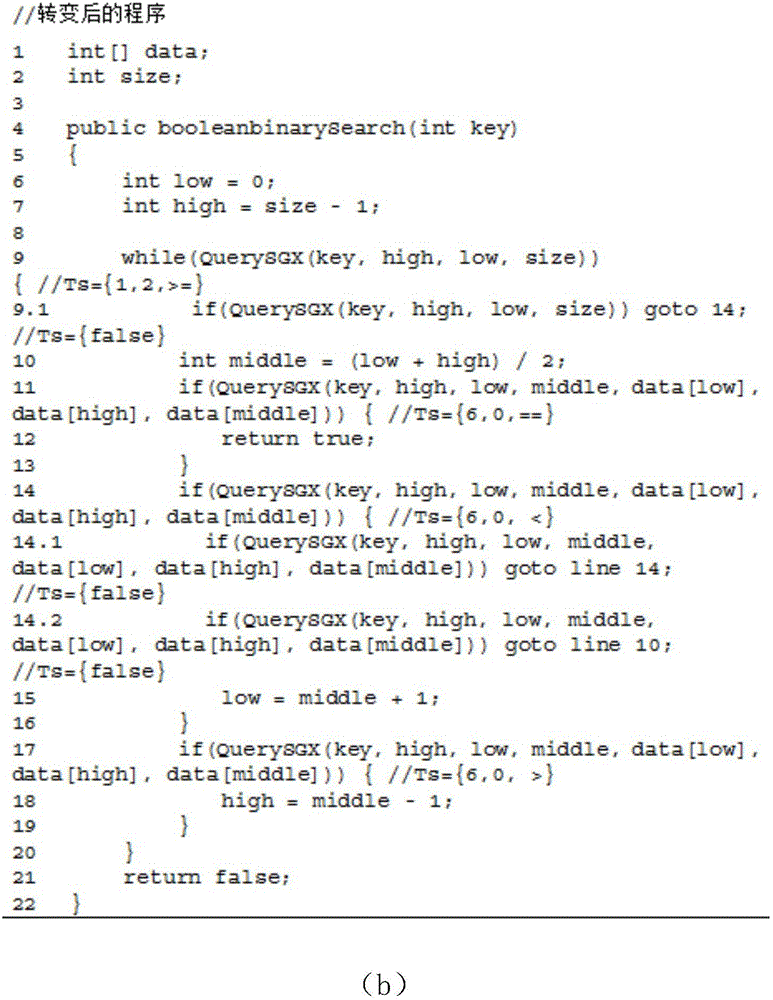
The invention discloses a control flow hiding method for remote computing. The method includes the following steps that original programs are divided into the open programs, the confidence programs and condition list group set files, the SGX function of the safe execution environment of a sixth-generation Intel processor is used for performing program branching statement condition judging in a confidence region with the hardware protection function, and therefore real hiding of program branching statement conditions is achieved.
Owner:XIDIAN UNIV
Grid-oriented configurable data transmission method and system
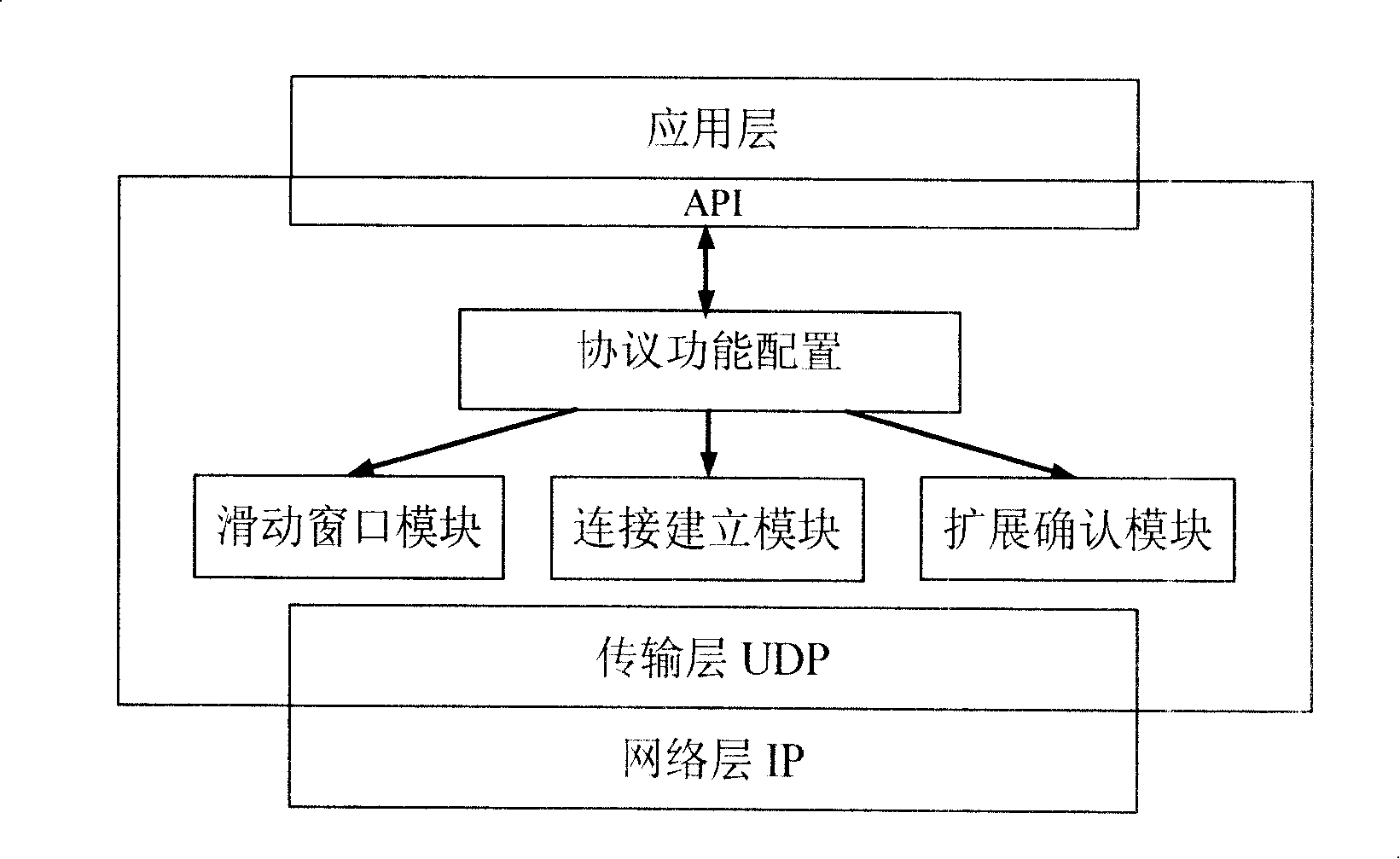
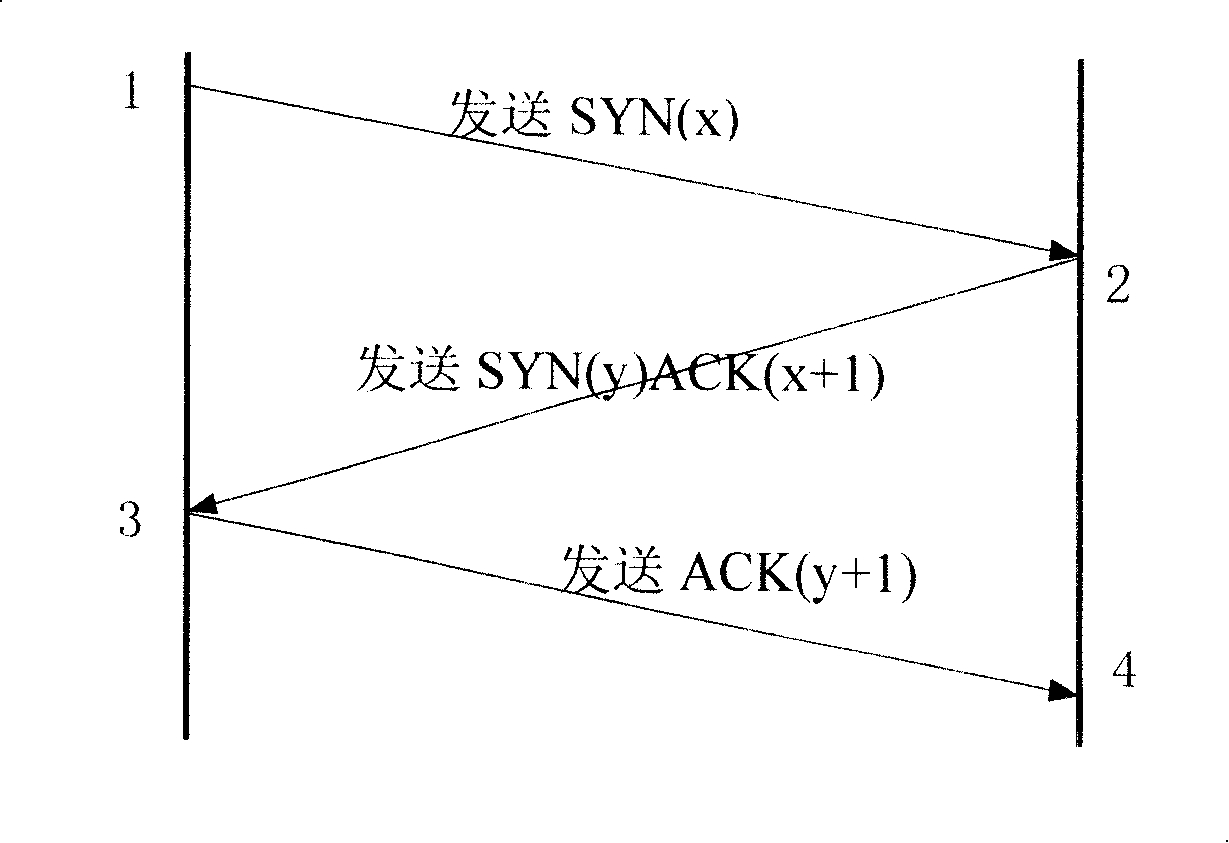
InactiveCN101212401AControl sending speedStable rateData switching networksReliable transmissionEngineering
The invention discloses a transmission system of grid-oriental configurable data which solves the problems of insufficient reliability existing in the prior protocol and high spending of the system operation. The invention comprises the following processes: data communication connection is built between two parties of the communication with a mode of three times handshake; when a fault occurs, the linkage of permanent connection is closed; a receiving and sending synchronization and a flow controlling of the information are carried out by a sliding window; in the data transmission protocol, an authentication technology is adopted for assuring the reliable transmission of the data. The invention, through the receiving and sending synchronization and the flow controlling of the information carried out by the sliding window, achieves function of stabilizing the rate, resending the lost packet and transmitting in sequence. The protocol realizes flow controlling. When the receiver has a value which increases to a right value in the receiving window, the receiver then sends a window notice to the sender under the condition of that the receiving window can be zero for a longer time in a large flow. Through effective controlling carried out for controlling a sending rate of the sender, the phenomenon of occurrence of an over congestion in the network in big flow can be avoided.
Owner:ZTE CORP
Neural network training method and device, image classification method, equipment and medium
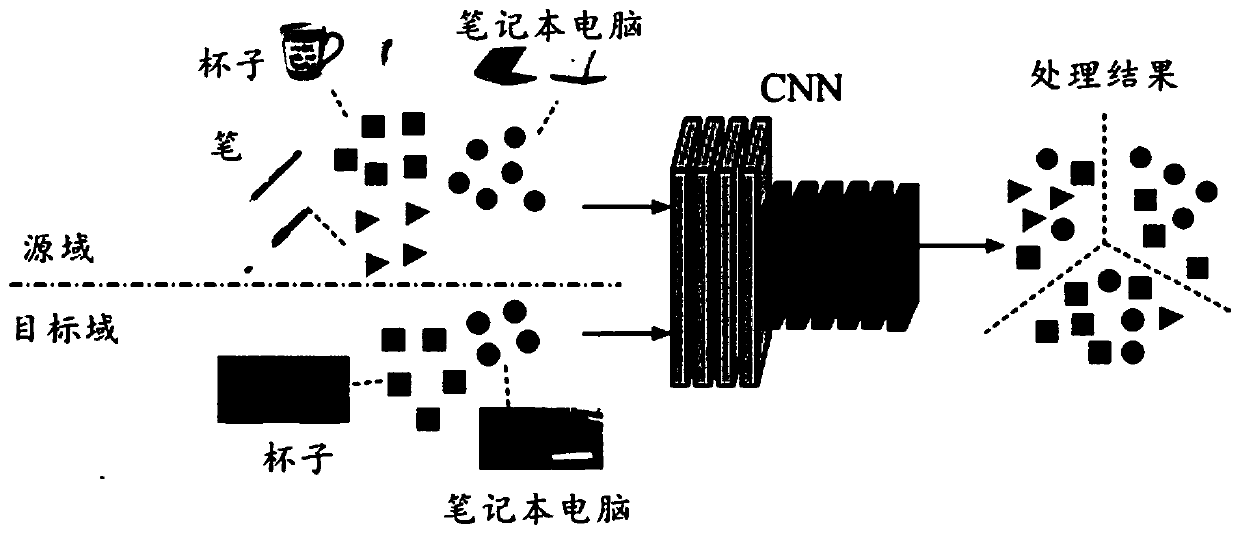
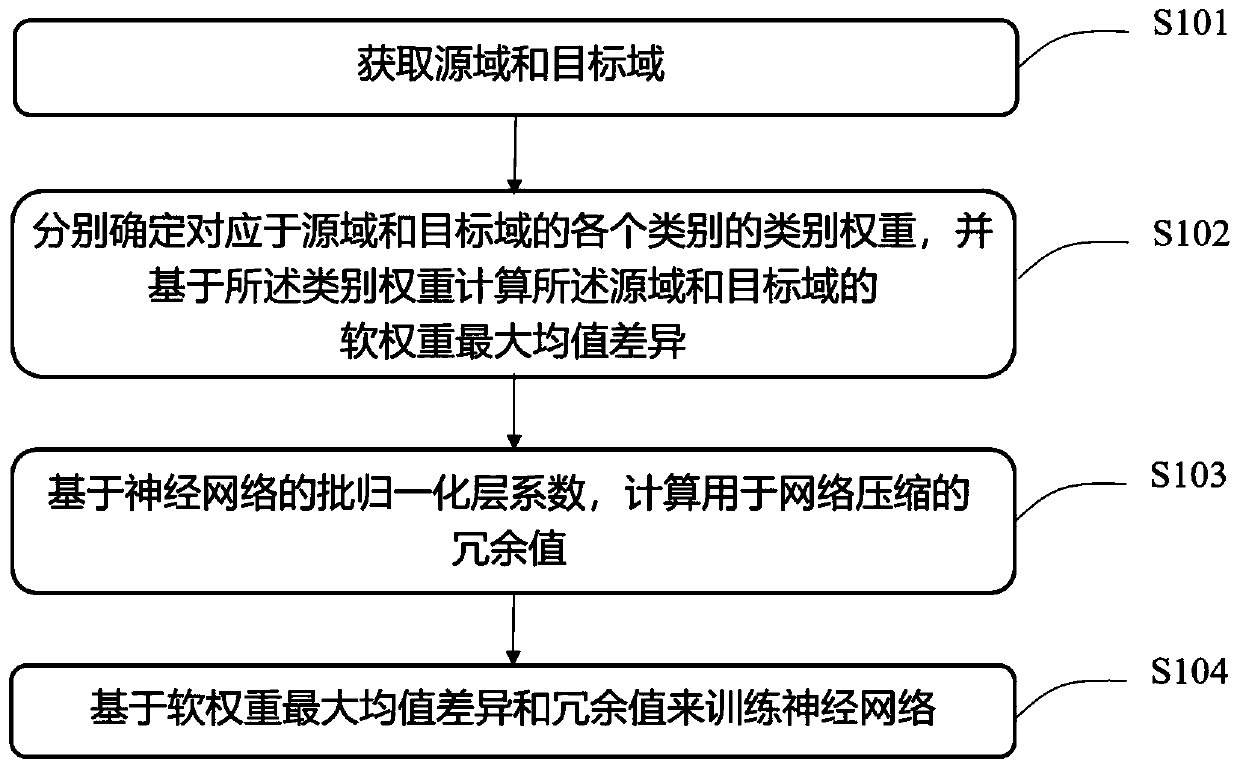
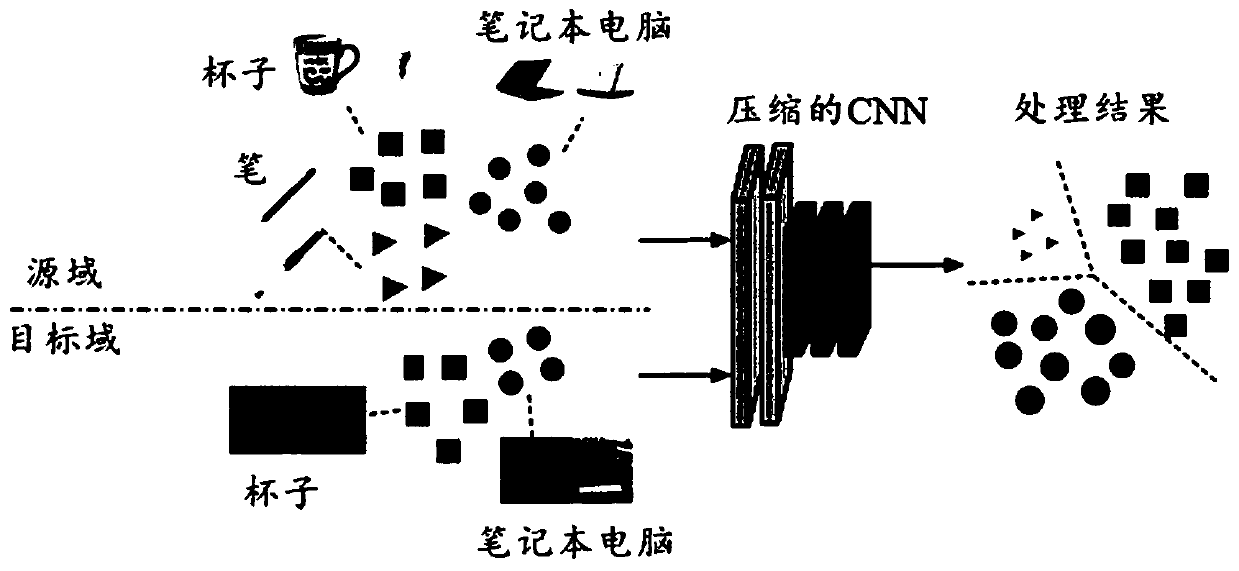
PendingCN111275175AReduce redundancyImproving Transfer Learning EffectsMachine learningNeural architecturesClassification methodsMachine learning
The invention provides a neural network training method and device, an image classification method and device and a medium. The neural network training method comprises the steps that a source domainand a target domain are acquired, the source domain comprises a plurality of first samples, and the target domain comprises a plurality of second samples; respectively determining category weights ofvarious categories corresponding to the source domain and the target domain, and calculating the maximum mean value difference of soft weights of the source domain and the target domain based on the category weights; calculating a redundancy value for network compression based on the batch normalization layer coefficient of the neural network; and training the neural network based on the soft weight maximum mean difference and the redundant value.
Owner:TENCENT TECH (SHENZHEN) CO LTD
A detection method and system for mobile terminal short message interception type malicious code
InactiveCN102291697AAvoid lostOther factors have little influenceMessaging/mailboxes/announcementsSecurity arrangementPresent methodDynamic monitoring
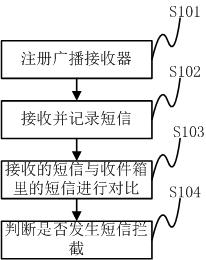
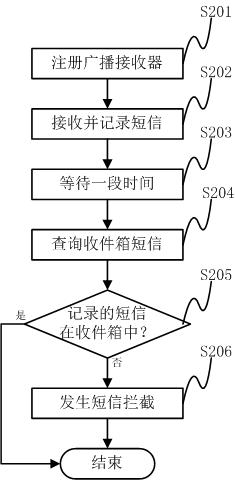
The invention discloses a detection method of mobile terminal short message intercepting type malicious code, comprising: registering a broadcast receiver in the mobile terminal system; using the broadcast processing function of the broadcast receiver to record all short messages newly received by the mobile terminal; After the set time, use all the short messages in the inbox of the mobile terminal to match all the short messages recorded by the broadcast processing function one by one; if the short messages recorded by the broadcast processing function fail to match the short messages in the inbox, the broadcast processing function The recorded short messages with unsuccessful matching are intercepted by malicious codes, and there are short message intercepting malicious codes in the mobile terminal system. The invention also discloses a detection system of mobile terminal short message interception type malicious code. The method and system can automatically run dynamic monitoring, detect malicious codes immediately when the interception occurs, and have more accurate detection and judgment results, and at the same time, the running cost is smaller, and the performance of the system is hardly affected.
Owner:SHENZHEN ANZHITIAN INFORMATION TECH
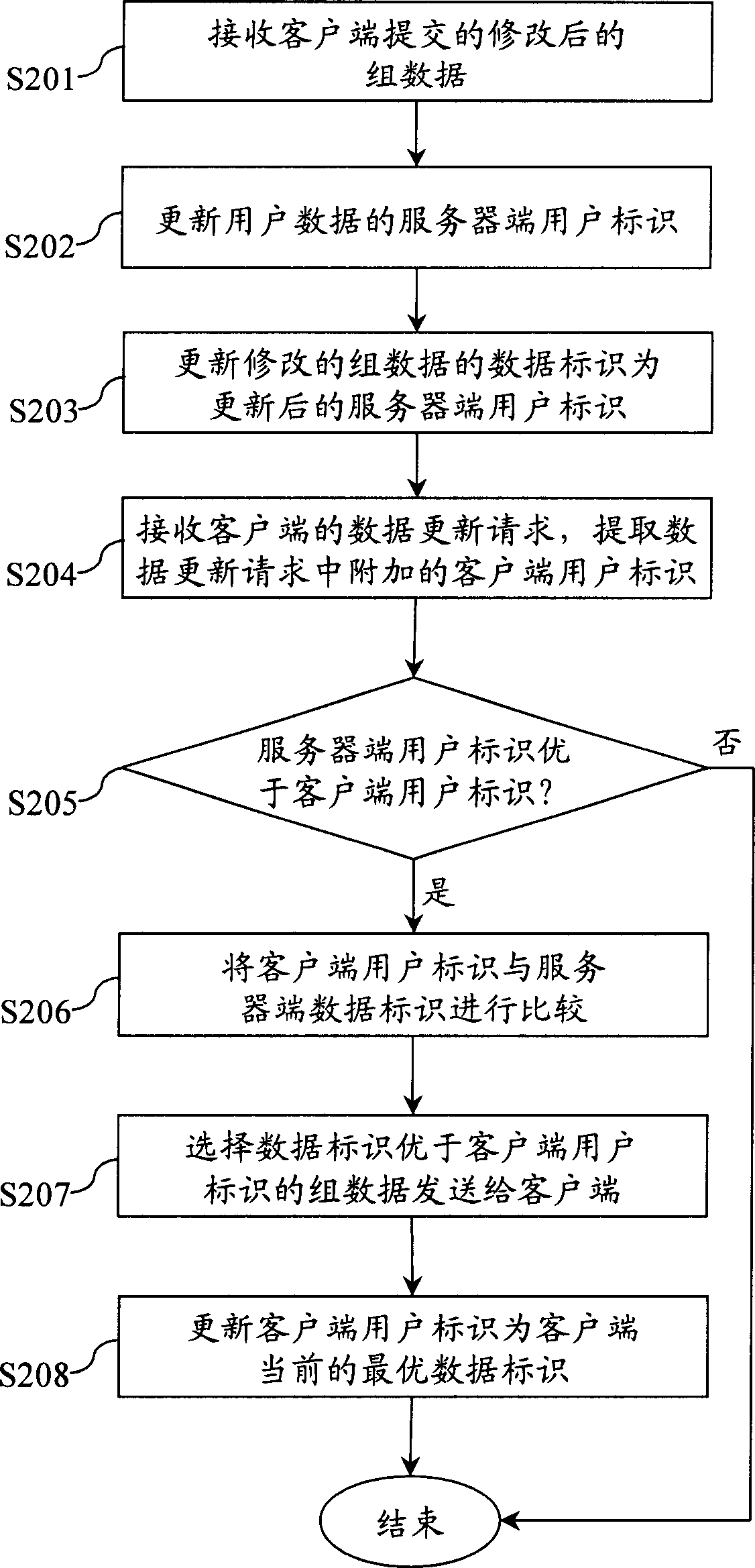
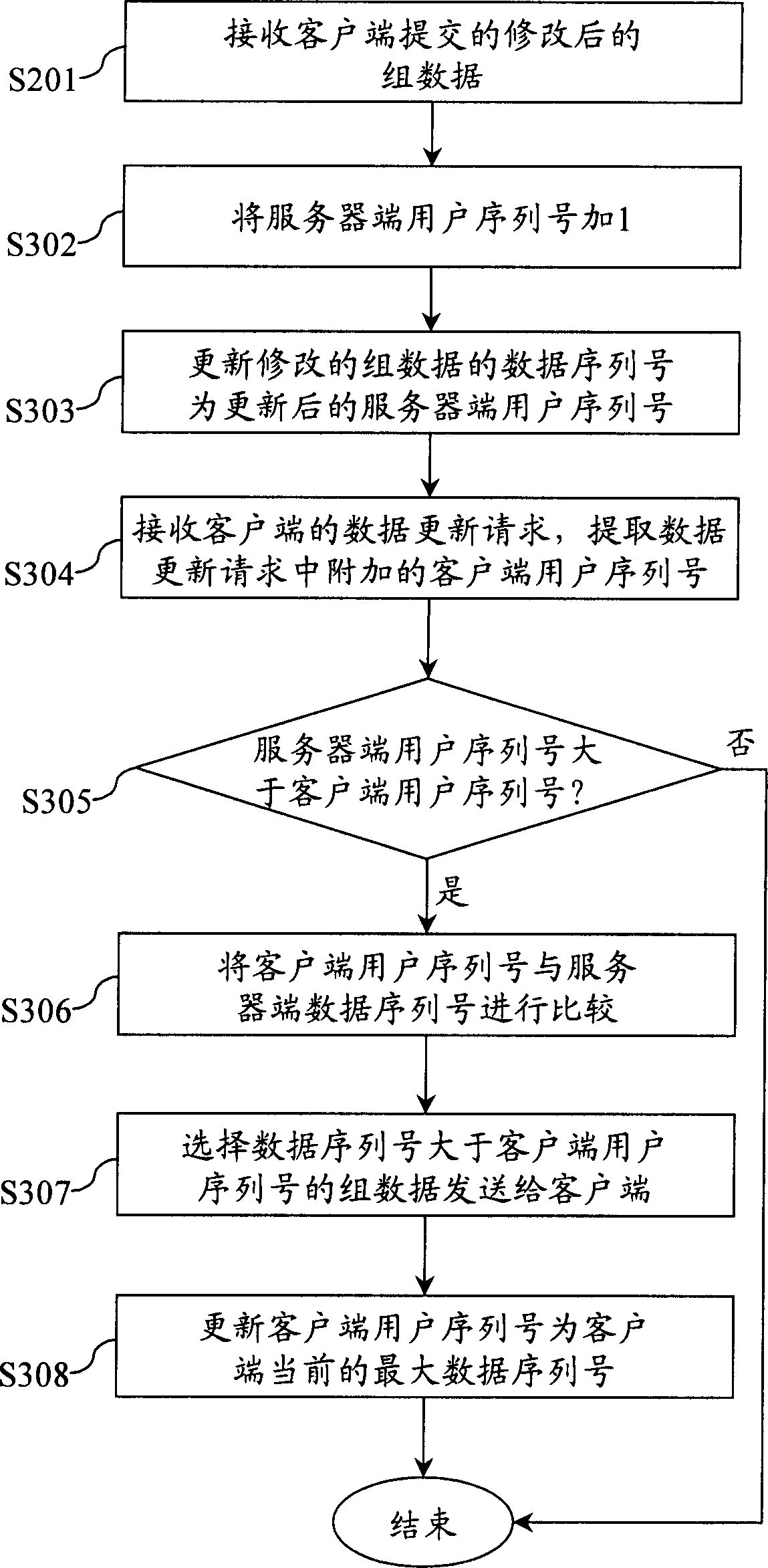
Method and system for user data transaction in communication system
ActiveCN1825797AReduce operating overheadGuaranteed uptimeData switching networksCommunications systemInternet privacy
This invention provides a method and a system for user data refreshment in a communication system, which optimizes user data refreshments by setting data ID of multi-data and user ID. When the customer end requests for refreshing user data, only a customer end user ID is added to the user data refreshment request of the server, which compares the data ID of the server end and the user ID at the customer end to judge the multi-data needed to be refreshed and selects the multi-data of the data ID of the server end superior than the user ID of the customer end when needing refreshing user data and sends it to the customer end to finish the refreshment.
Owner:TENCENT TECH (SHENZHEN) CO LTD
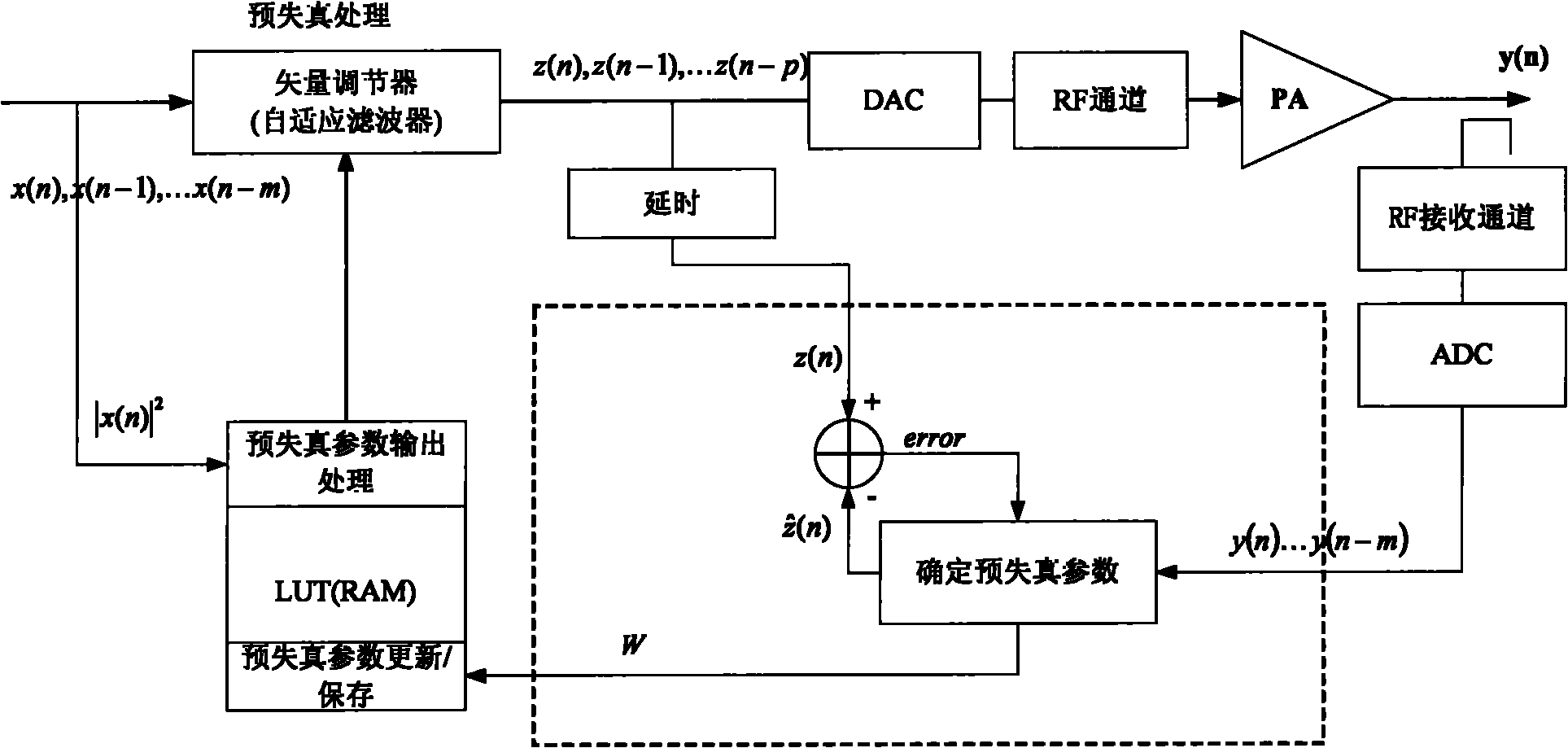
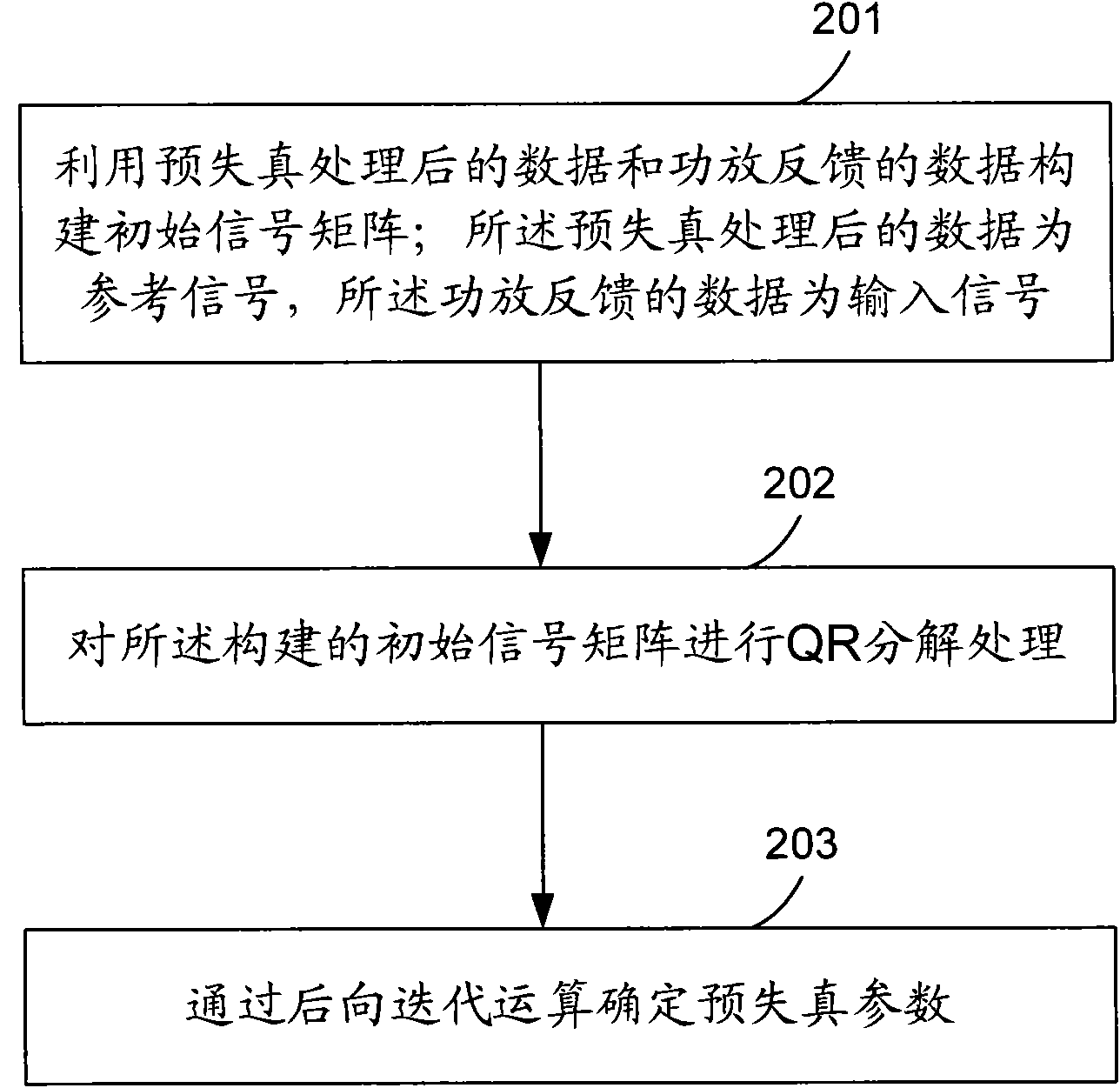
Predistortion parameter processing method and device
ActiveCN101771639AReduce computationReduce operational complexitySynchronous/start-stop systemsQR decompositionWorkload
The invention provides a predistortion parameter processing method and a device; wherein the method comprises the following steps: an initial signal matrix is built by utilizing data which carries out predistortion treatment and power amplification feedback data after periodic filtering processing begins; the data which carries out predistortion treatment is a reference signal, and the data for power feedback is an input signal; QR decomposition processing is carried out to the built initial signal matrix, and the predistortion parameters are determined by carrying out backward iteration operation to the matrix which carries out the QR decomposition; by adopting the method and the device, the arithmetic workload and the arithmetic complexity can be effectively reduced; in addition, the determined predistortion parameters begin to be stored from Nth sampling point symbol, so as to well save the expenses of the system operation.
Owner:DATANG MOBILE COMM EQUIP CO LTD
Task scheduling method and device for low overhead in edge computing
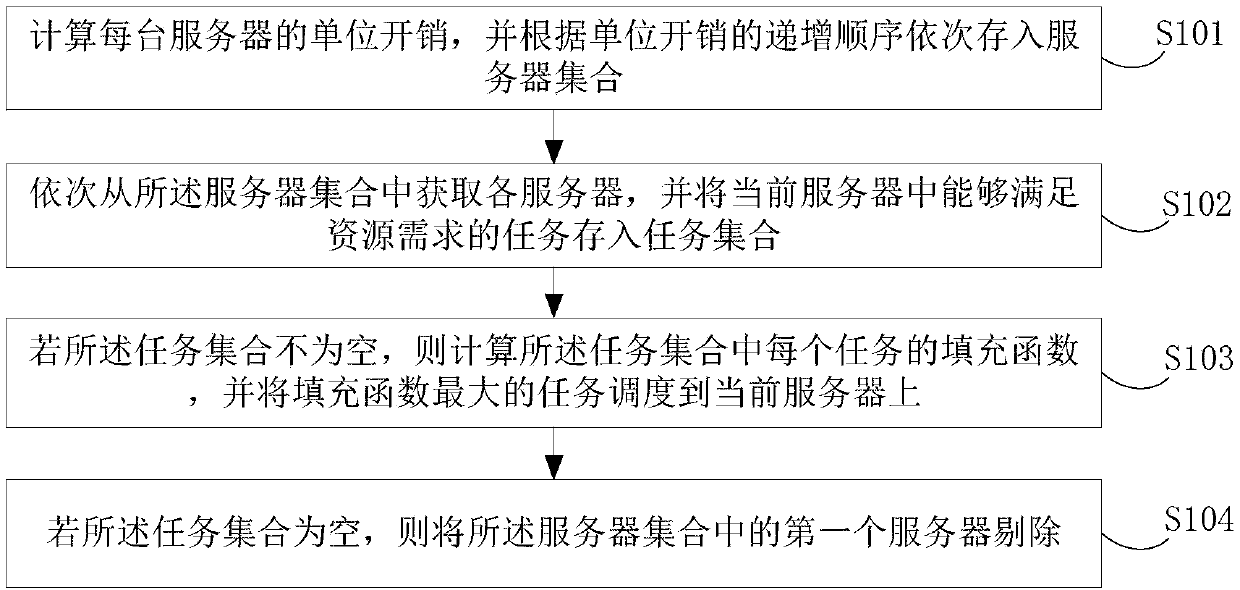
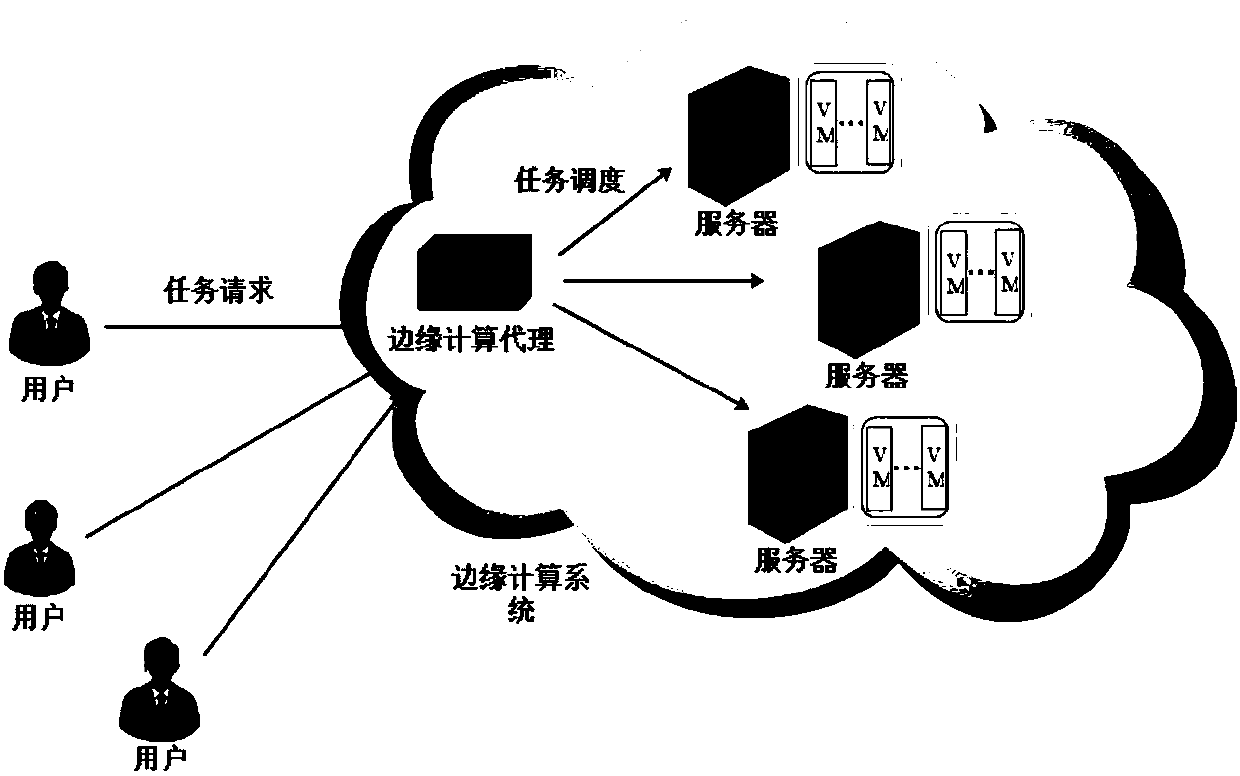
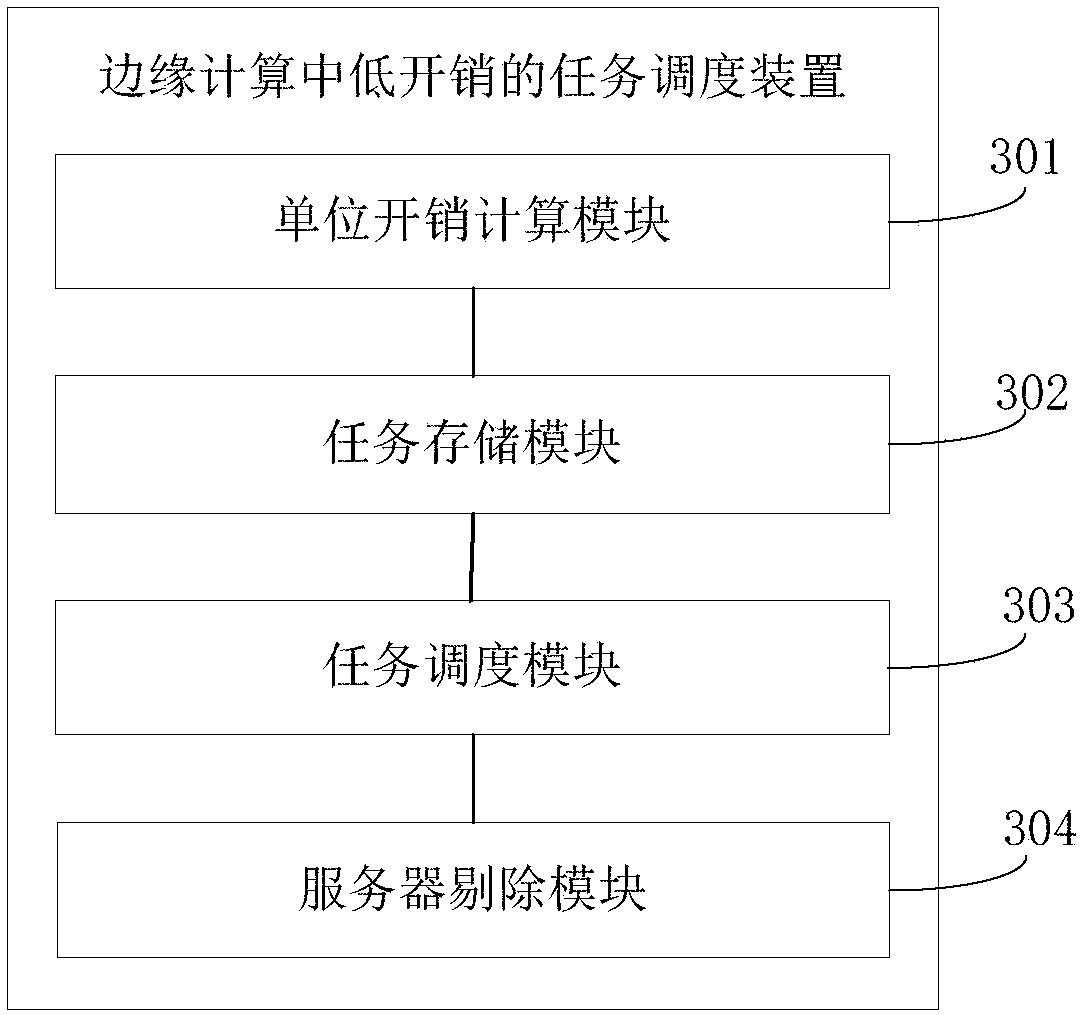
ActiveCN108304256AReduce operating overheadProgram initiation/switchingResource allocationEdge computingLow overhead
The embodiment of the invention discloses a task scheduling method and a task scheduling device for low overhead in edge computation. The task scheduling method comprises the following steps of: calculating unit overhead of each server, and sequentially storing the unit overhead into a server set according to the ascending order of unit overhead; acquiring each server from the server set in sequence, and storing the task capable of meeting the resource requirement in the current server into a task set; if the task set is not void, calculating the filled function of each task in the task set, and scheduling the maximum task of the filled function to the current server; If the set of tasks is void, rejecting the first server in the server set. Through sorting the unit overhead of the server,the task scheduling method for low overhead in edge computation sequentially selects the server with the minimum unit overhead to process task and obtain, the original task scheduling scheme, and theoriginal scheduling scheme is further optimized by judging whether the task set is void so as to perform different operations, and the running overhead of the server can be effectively reduced.
Owner:BEIJING INFORMATION SCI & TECH UNIV
Vehicle shadow eliminating method based on multi-feature fusion
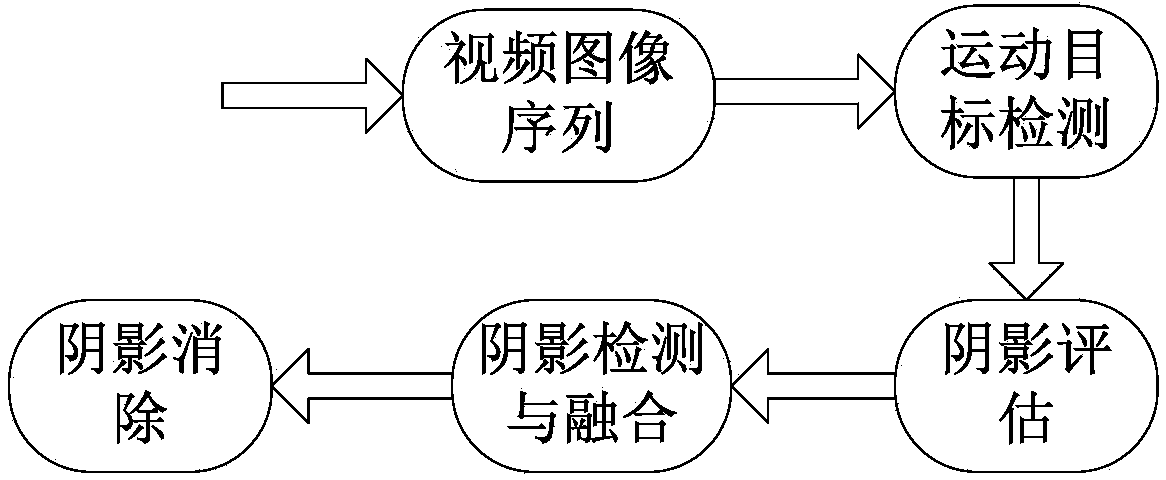
InactiveCN104299210AReduce operating overheadSimple methodImage enhancementImage analysisMorphological processingTraffic scene
The invention provides a vehicle shadow eliminating method based on multi-feature fusion. The vehicle shadow eliminating method comprises the following steps that (1), image sequences are read to obtain a current frame; (2), background modeling is carried out, a frame difference method is used for extracting vehicle foregrounds for a background frame and the current frame, and binarization processing and morphological processing are carried out on the foregrounds; (3), shadow assessment is carried out on a moving target area; (4), shadow detection is carried out on a vehicle foreground area, and detection is carried out on the basis of color features and edge features to obtain a plurality of candidate shadow areas; (5), the candidate shadow areas are fused to obtain a final shadow area; (6), in the vehicle foreground area, the shadow areas are eliminated, and real target vehicles are left. According to the vehicle shadow detecting algorithm based on multi-feature fusion, a shadow detecting method based on a single feature has limitation, and can not be applied to all traffic scenes, and therefore the vehicle shadow eliminating method with the universality is achieved by fusing a plurality of features.
Owner:TONGJI UNIV
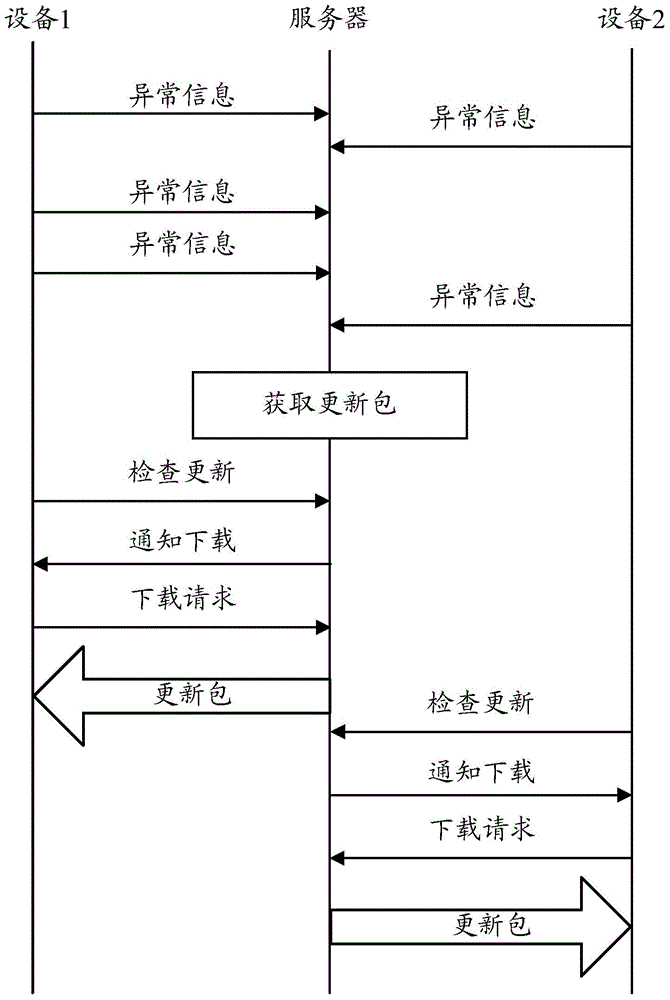
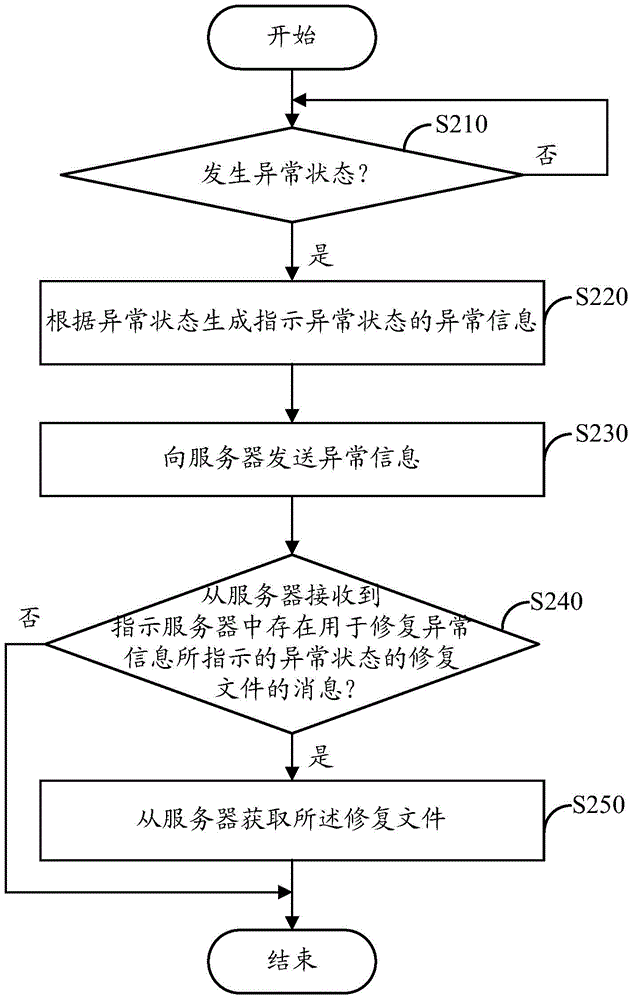
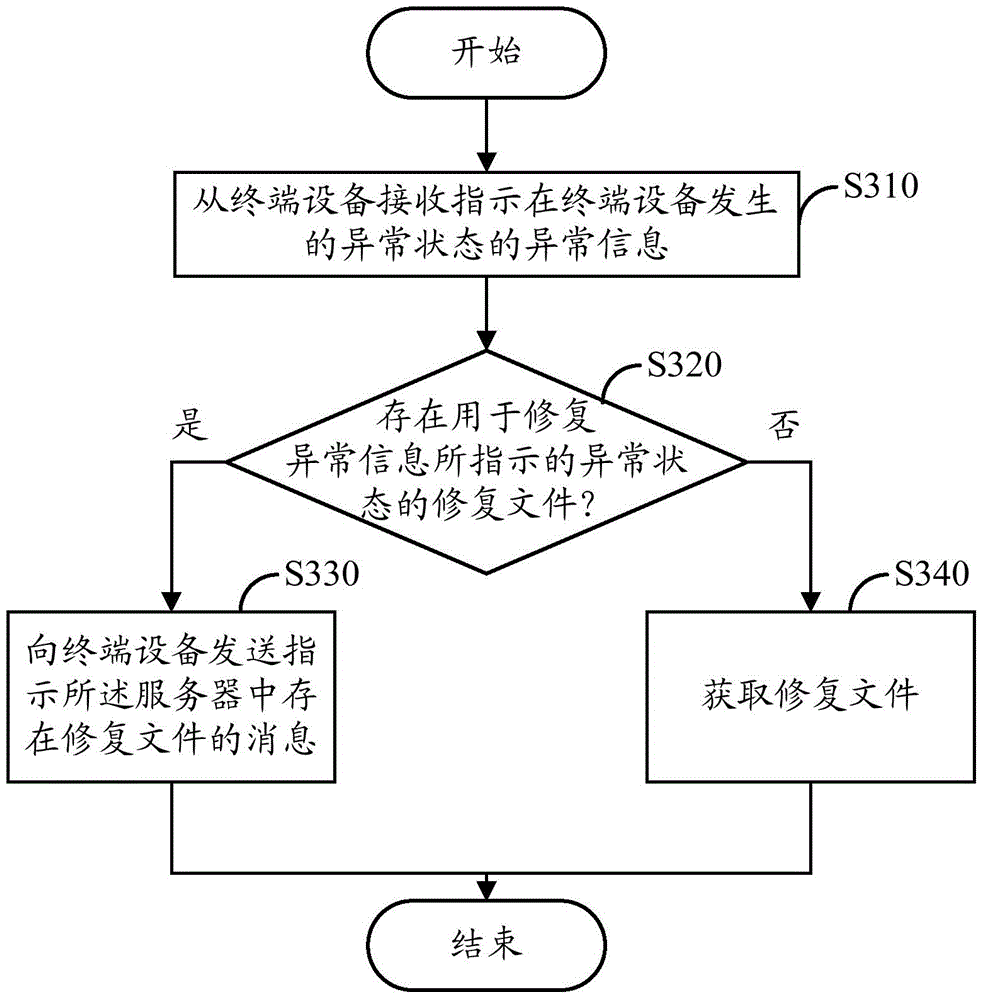
Exception handling method, terminal equipment and server
InactiveCN104683154AReduce development costsReduce operating overheadData switching networksComputer hardwareTerminal equipment
The invention provides an exception handling method executed in terminal equipment, an exception handling method executed in a server, the terminal equipment and the server. The exception handling method executed in the terminal equipment comprises the following steps: monitoring an exceptional state existing in the terminal equipment; according to the exceptional state, generating exceptional information indicating the exceptional state; sending the exceptional information to the server; when a message which indicates that a repair file for repairing the exceptional state indicated by the exceptional information exists in the server is received from the server, acquiring the repair file from the server. According to the exception handling method, the terminal equipment and the server, when the terminal equipment has the exceptional state, the repair file in allusion to the exceptional state can be acquired in time, so that influence of the exceptional state on a user experience is inhibited to the maximum extent, the development cost of the terminal equipment is reduced and the operating expense of the terminal equipment is saved.
Owner:LENOVO (BEIJING) LTD
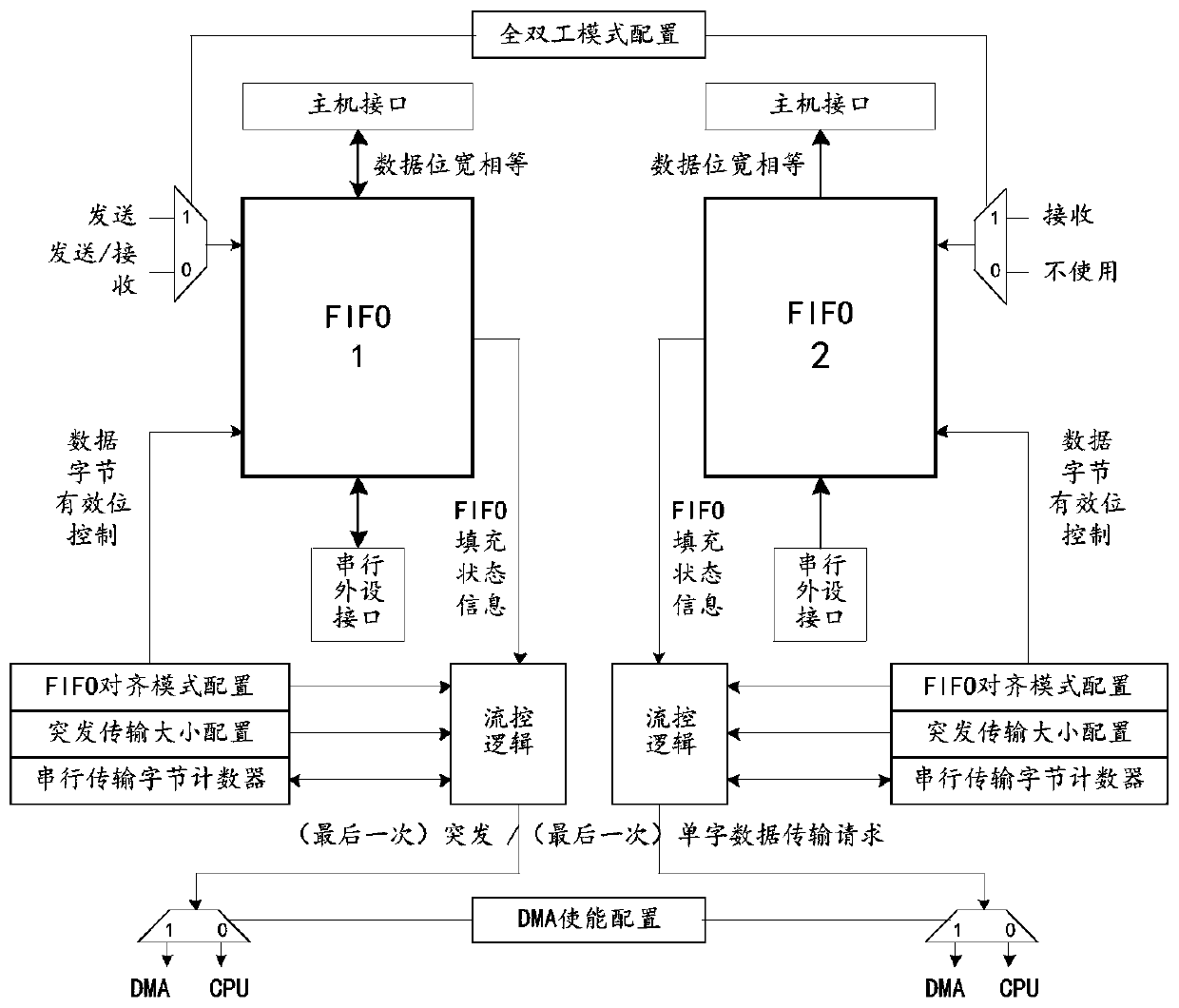
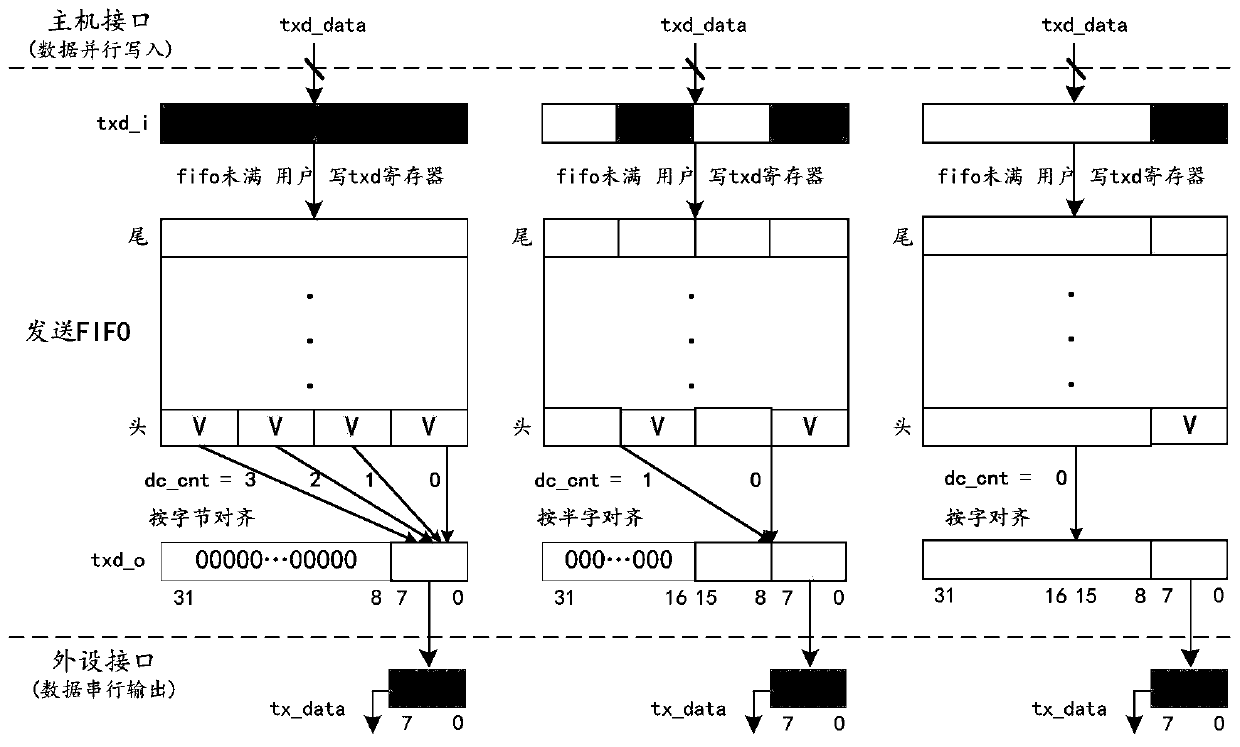
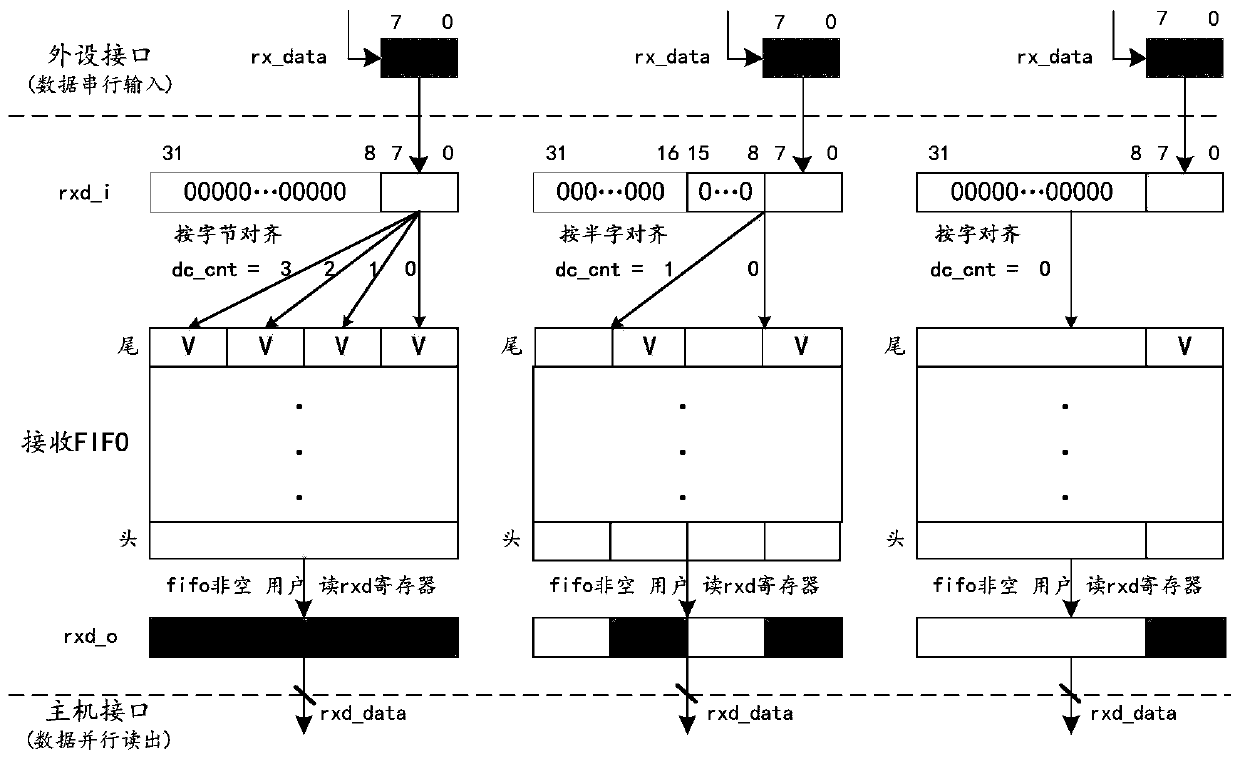
Flow control type FIFO cache structure and method for uniformly configuring data significant bits
ActiveCN110188059AReduce Auxiliary Operations OverheadAvoid overflow errorsElectric digital data processingLeast significant bitData transmission
The invention discloses a flow control type FIFO cache structure and method for uniformly configuring the data significant bits, and the structure comprises a first FIFO and a second FIFO, and the first FIFO and the second FIFO are jointly connected to a full-duplex mode configuration register which is used for selecting a full-duplex mode or a half-duplex mode. According to the invention, the data transmission efficiency with a host interface can be improved, the overhead of data integration through software is reduced, and the flow control mode of hardware management is designed, so that theoverflow phenomenon of FIFO is avoided.
Owner:XIAN MICROELECTRONICS TECH INST
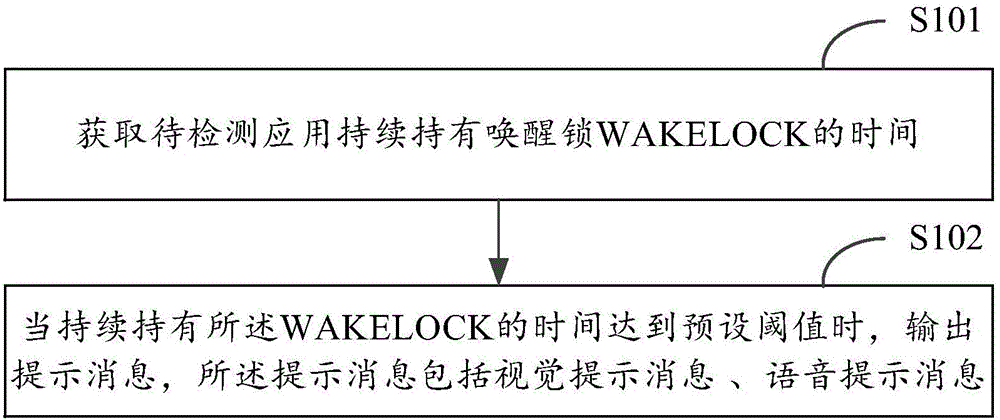
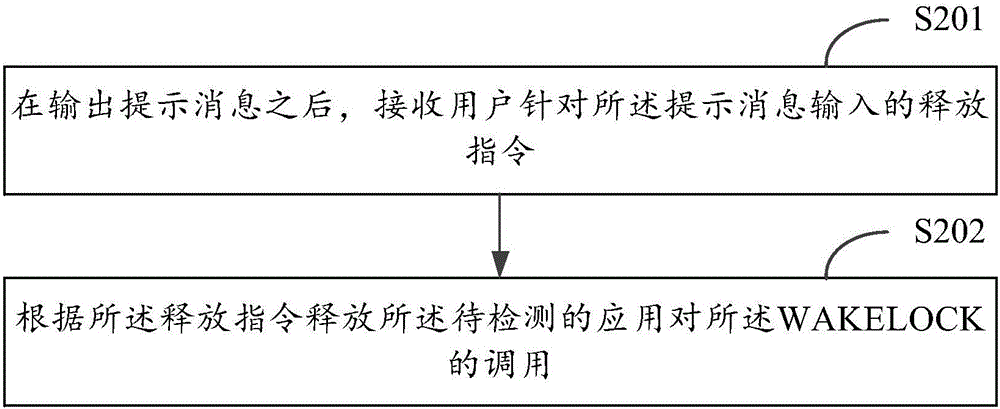
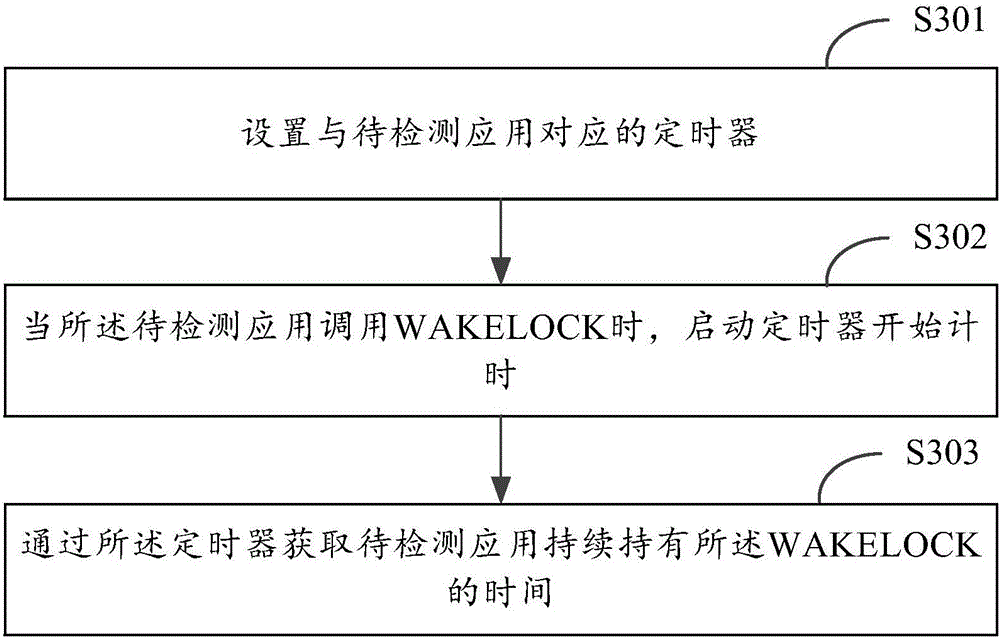
Processing method and device of lock holding of application
ActiveCN105807894AReduce misunderstandingGet TimePower supply for data processingComputer scienceIntelligent equipment
The invention discloses a processing method and device of the lock holding of an application. The method comprises the following steps: obtaining time for an application to be detected to continuously hold a WAKELOCK; and when the time for continuously holding the WAKELOCK achieves a preset threshold value, outputting a prompt message, wherein the prompt message comprises a vision prompt message and a voice prompt message. The intelligent equipment can output the prompt message when the time for the application to be detected to continuously hold the WAKELOCK achieves the preset threshold value so as to bring convenience for users to know the consumption situation of equipment power consumption and reduce the misunderstanding of the user on the power consumption of the equipment.
Owner:BEIJING XIAOMI MOBILE SOFTWARE CO LTD
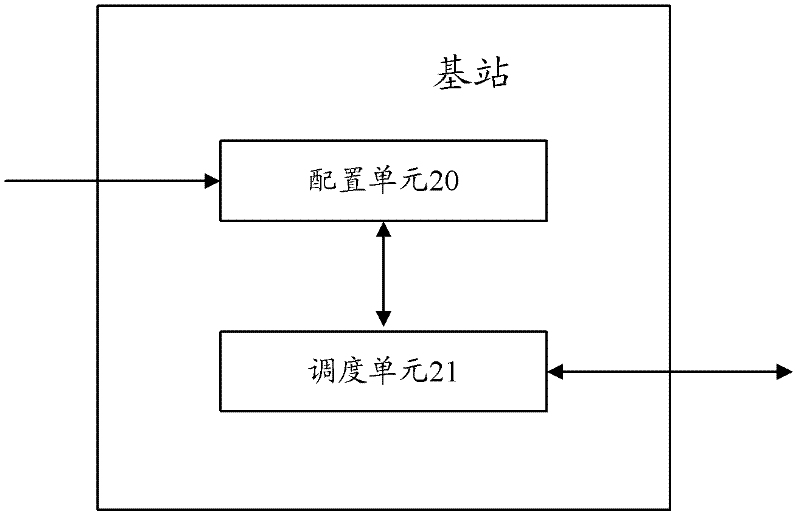
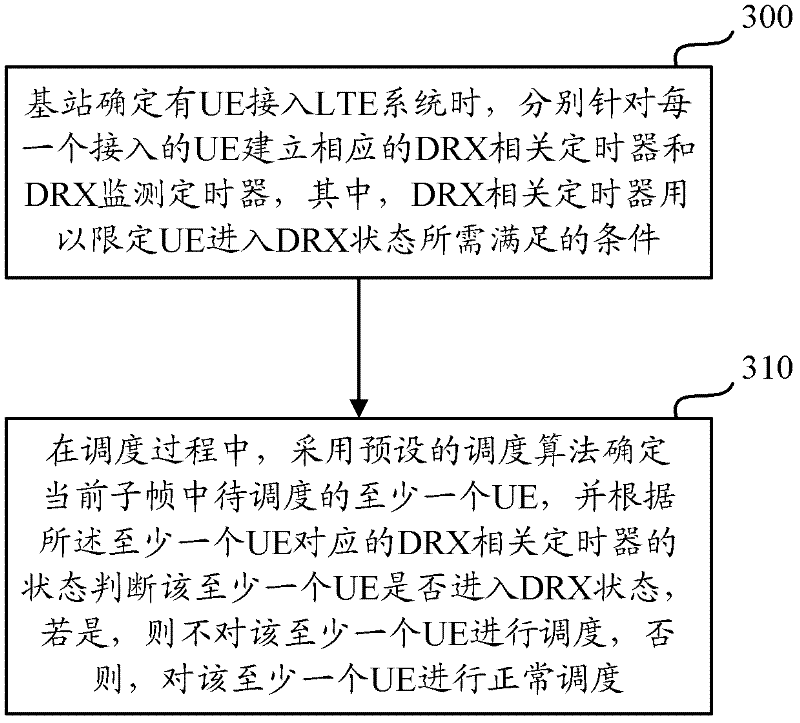
A method and device for realizing drx function
ActiveCN102264148AReduce operating overheadImpact capacityConnection managementTimerDiscontinuous reception
The invention relates to the field of communication and discloses a method and a device for realizing a discontinuous reception (DRX) function, which are used for lowering operation cost of a system on the premise of not increasing equipment cost and not influencing cell capacity. The method comprises the following steps of: establishing DRX related timers for user equipment (UE) by using a base station when the UE accesses the system; and judging whether to schedule the UE or not only according to the states of the DRX related timers of the current UE to be scheduled in the current subframe before scheduling, instead of determining the states of the DRX related timers of all the UE. Therefore, by the method and the device, the operation cost of a network side can be effectively saved, resource waste of the system is avoided, the equipment cost of the network side cannot be increased, and the user capacity of cells cannot be influenced.
Owner:DATANG MOBILE COMM EQUIP CO LTD
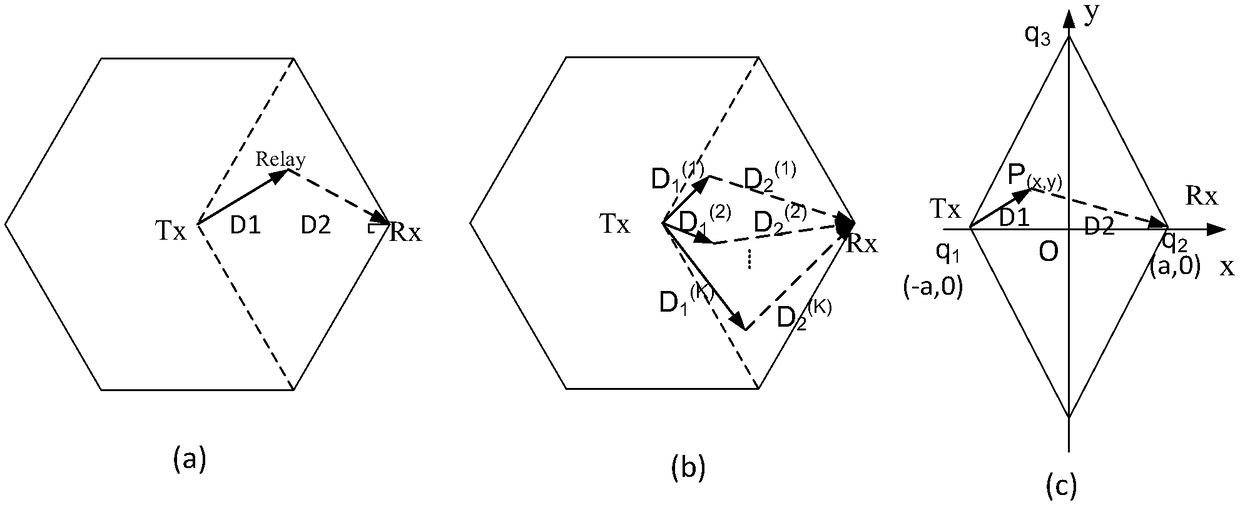
A stochastic cooperative communication method based on geometrical probability method
InactiveCN109068345AReduce implementation complexityGuaranteed transmission capacityNetwork topologiesData switching networksSystem capacityNormal density
The invention discloses a random cooperative communication method based on a geometrical probability method. The SCCGP model in a cellular network is proposed, and the definition of end-to-end path loss and system capacity is given. The distance loss of two random relay channels is deduced, and the approximate cumulative distribution function of the random distance distribution is simplified. Thenthe capacity of random cooperative communication in SCCGP mechanism is deduced, and the probability density function of user capacity interruption is deduced. At the same time, the calculation methodof the minimum number of relay nodes required to satisfy certain connection requirements is proposed. The SCCGP model is extended to wireless ad hoc networks. By using one or more relay nodes, the cumulative distance distribution function of two random relay paths is derived, and the cumulative distribution function of user capacity in stochastic cooperative communication is obtained. In the SCCGP model proposed by the invention, the theoretical analysis model and the derivation of the system capacity distribution are all based on any number of relay paths, and the SCCGP model has universality.
Owner:NORTHWESTERN POLYTECHNICAL UNIV
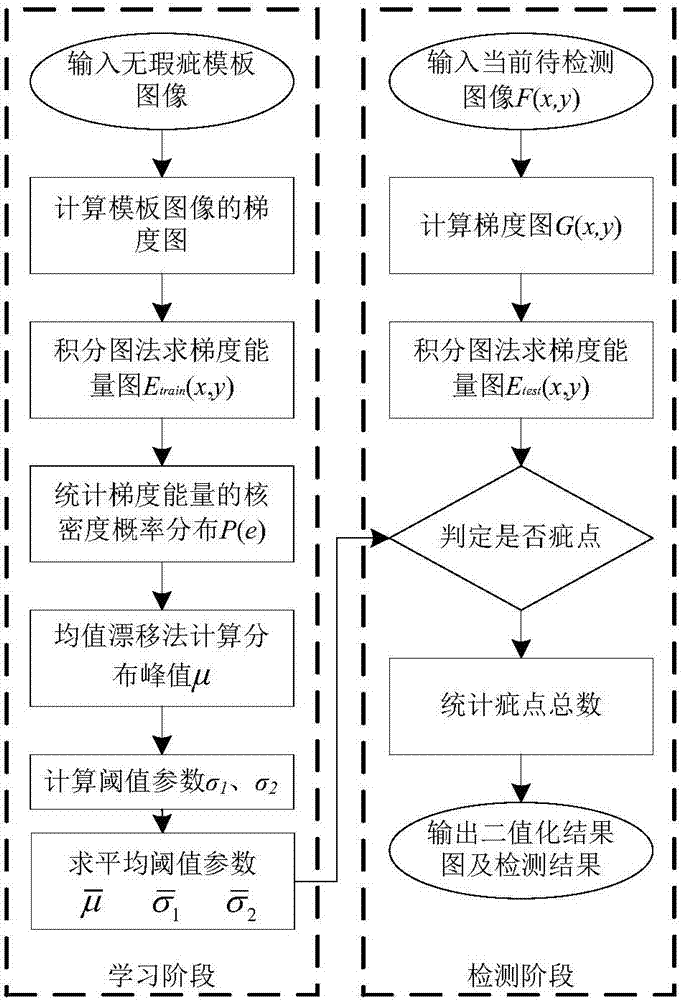
Integral graph algorithm-based fabric flaw detection method
ActiveCN107240086AAutomatic segmentationAccurate segmentationImage enhancementImage analysisPeak valueSelf adaptive
An integral graph algorithm-based fabric flaw detection method is disclosed. An integral graph algorithm is used for rapidly extracting statistical characteristics of gradient energy, and the statistical characteristics of gradient energy are used for flaw detection; image learning operation on a flawless template is performed, statistics are run on characteristic distribution of the gradient energy, distribution peak values are extracted, threshold parameters are calculated in a self-adaptive manner and used for distinguishing subsequent flaws, gradient energy of a window where each pixel point of an image to be detected is positioned can be calculated via the integral graph algorithm, whether a current pixel point is a defect point can be determined based on the threshold parameters, and whether the current image is a flawed fabric can be determined after statistics are run on a total quantity of flaw points of the whole image. According to the method disclosed in the invention, based on principles of accelerated operation of integral graphs, the characteristic distribution of the gradient energy of the fabric image can be rapidly extracted, real time detection of fabric flaws can be realized, the peak values of the distribution are calculated, the self-adaptive threshold parameters for flaw determination are obtained, and accurate segmentation of fabric flaws can be realized. Via the method, real-time property and high accuracy can be ensured.
Owner:南通大学技术转移中心有限公司
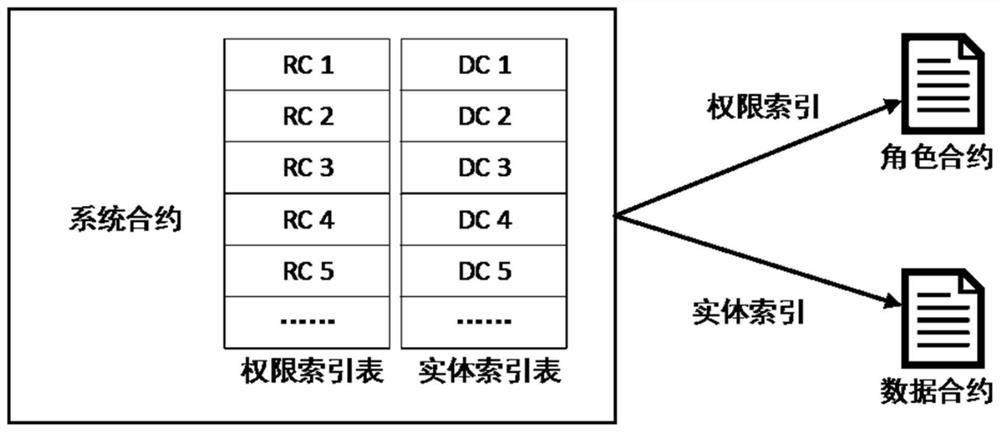
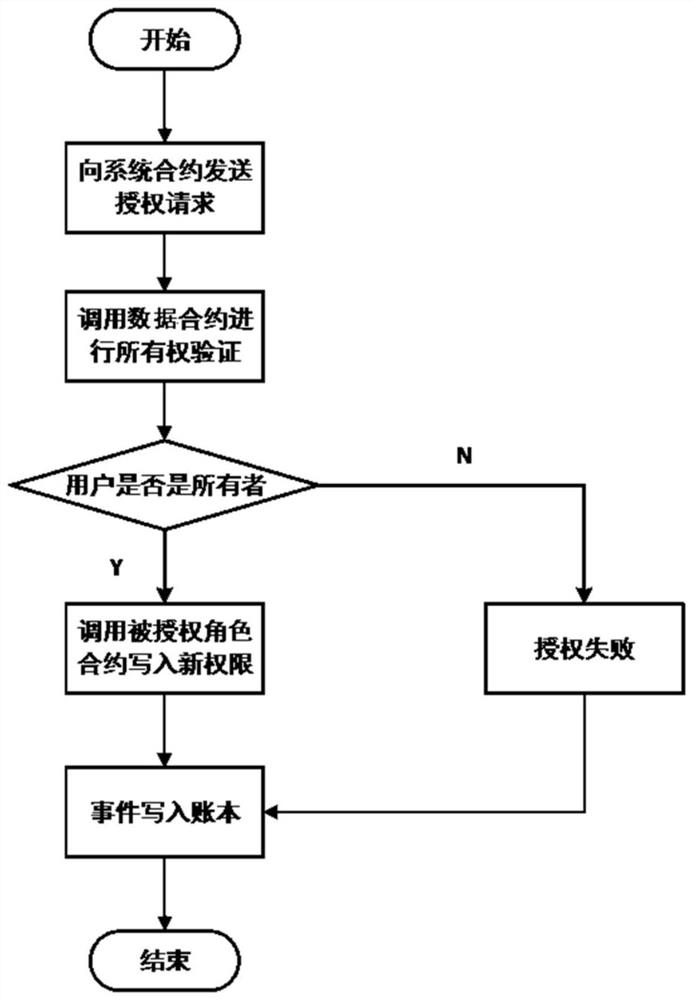
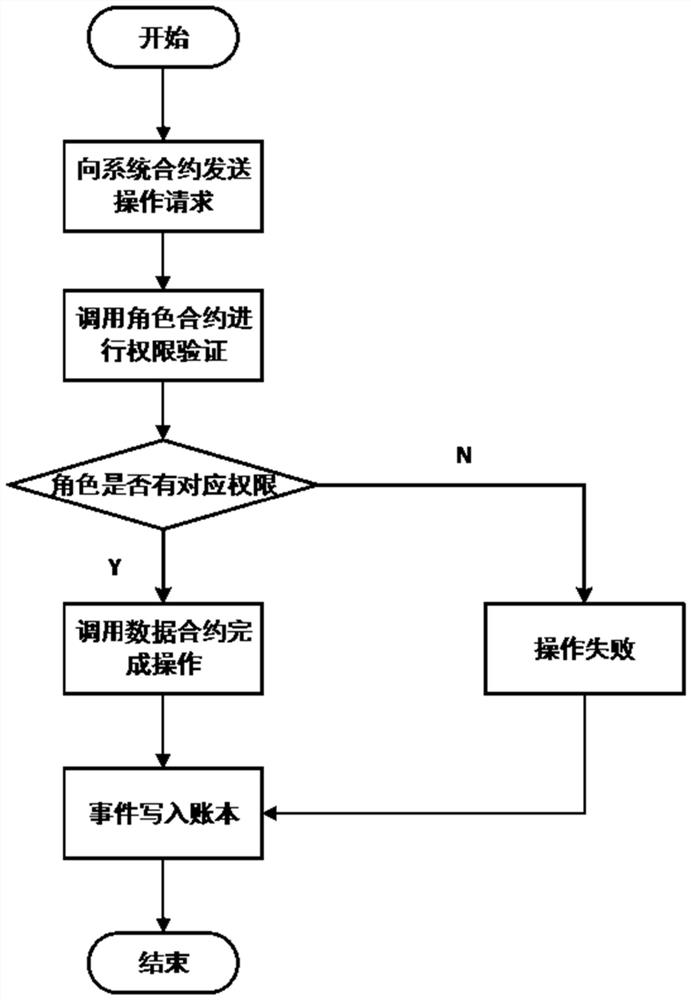
Supply chain access control system and method based on public chain smart contract
ActiveCN111797374AMeet traceability requirementsEffective data sharingDigital data authenticationManufacturing computing systemsControl systemFinancial transaction
The invention relates to a supply chain access control system based on a public chain smart contract, which is used for access control in a block chain traceability scene. According to the system, anRBAC model is adopted, and the system comprises a system contract SC, role contracts RC and data contracts DC. The RBAC model comprises four types of agents which are associated with one another and an operation set OP, and the four types of agents are respectively a user agent u, a role agent r, a permission agent p and an object agent ob. The system contract SC is used for managing a user agentu, the role contracts RC are used for managing a role agent r and a plurality of permission agents p, and the data contracts DC are used for managing the object agent ob. The deployment transaction ofthe system contract SC serves as an entrance of the RBAC model and is firstly linked, and the multiple role contracts RC and the multiple data contracts DC are respectively called by the system contract SC. Compared with the prior art, the system has the advantage that data sharing convenience, data privacy security and the like are ensured at the same time.
Owner:浙江同善人工智能技术有限公司
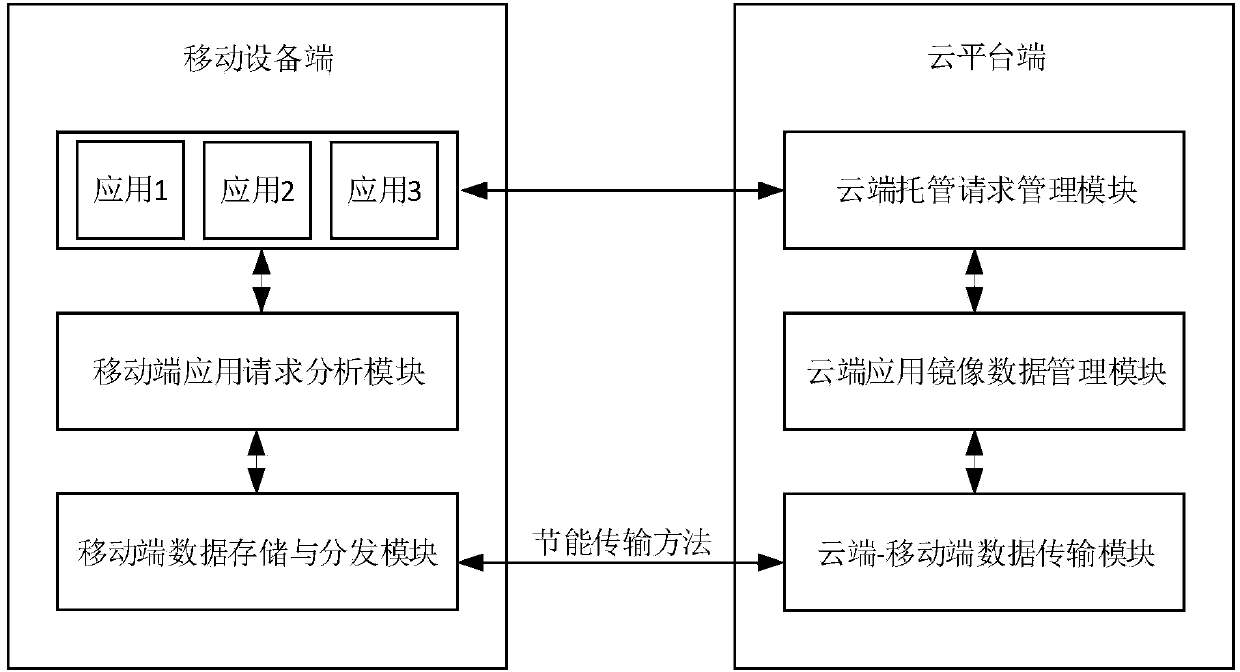
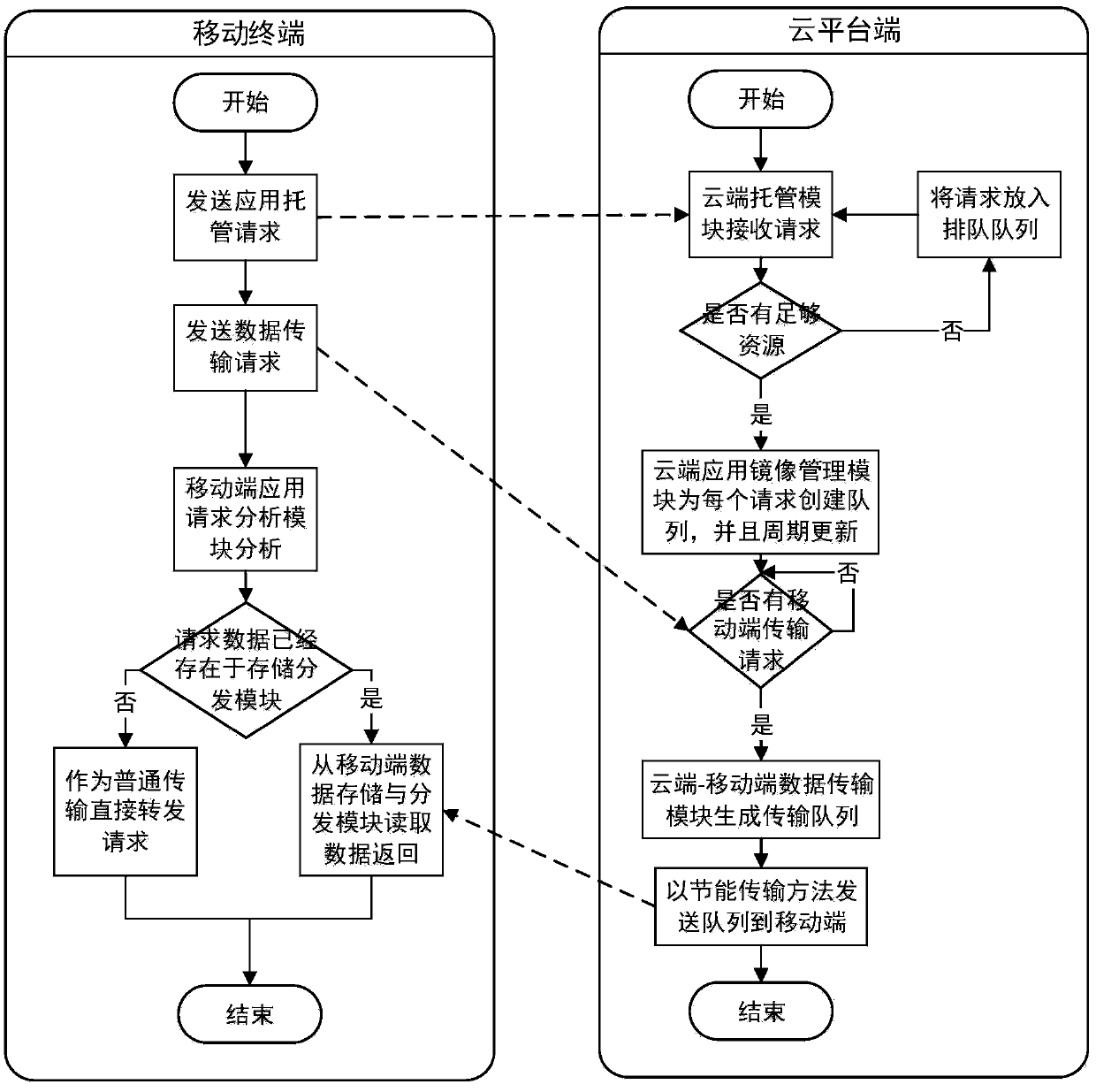
Energy-saving transmission method oriented to mobile cloud computing and middleware system
ActiveCN103731484AReduce operating overheadReduce overheadEnergy efficient ICTTransmissionMobile endMirror image
The invention discloses an energy-saving transmission method oriented to mobile cloud computing and a corresponding middleware system. A cloud end hosting request management module is used for receiving and processing a mirror image hoisting request of a mobile end, a cloud end application mirror image data management module manages data updating and deleting of a mobile application mirror image, a cloud end-mobile end data transmission module achieves energy-saving data transmission between a cloud platform and the mobile end, a mobile end data storage and distribution module stores the data transmitted through the cloud end and distributes the data to different mobile applications, and a mobile end application request analysis module analyzes data requests of the mobile applications, and feeds back corresponding data from the storage module. The energy-saving transmission method oriented to mobile cloud computing and the corresponding middleware system can well lower high transmission energy consumption under a wireless network bandwidth unstable environment, improves the performance of a mobile end battery and improves user experience of a data pre-taking program at the same time.
Owner:HUAZHONG UNIV OF SCI & TECH
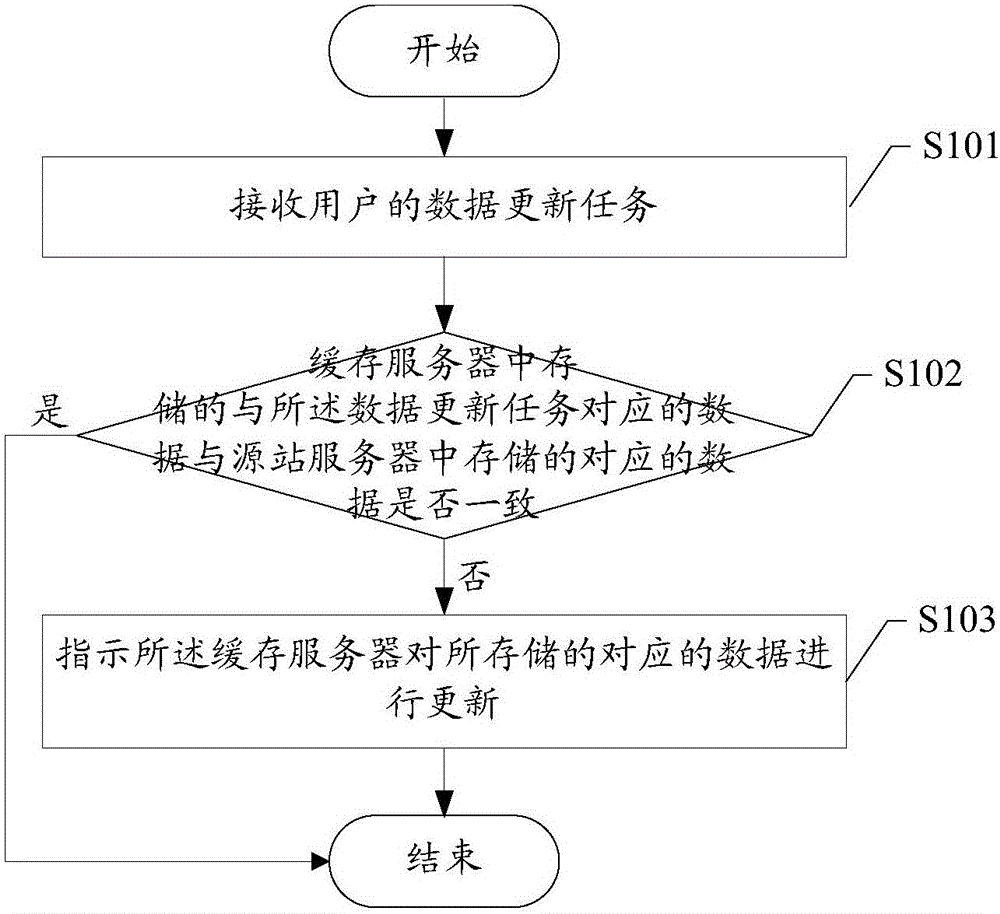
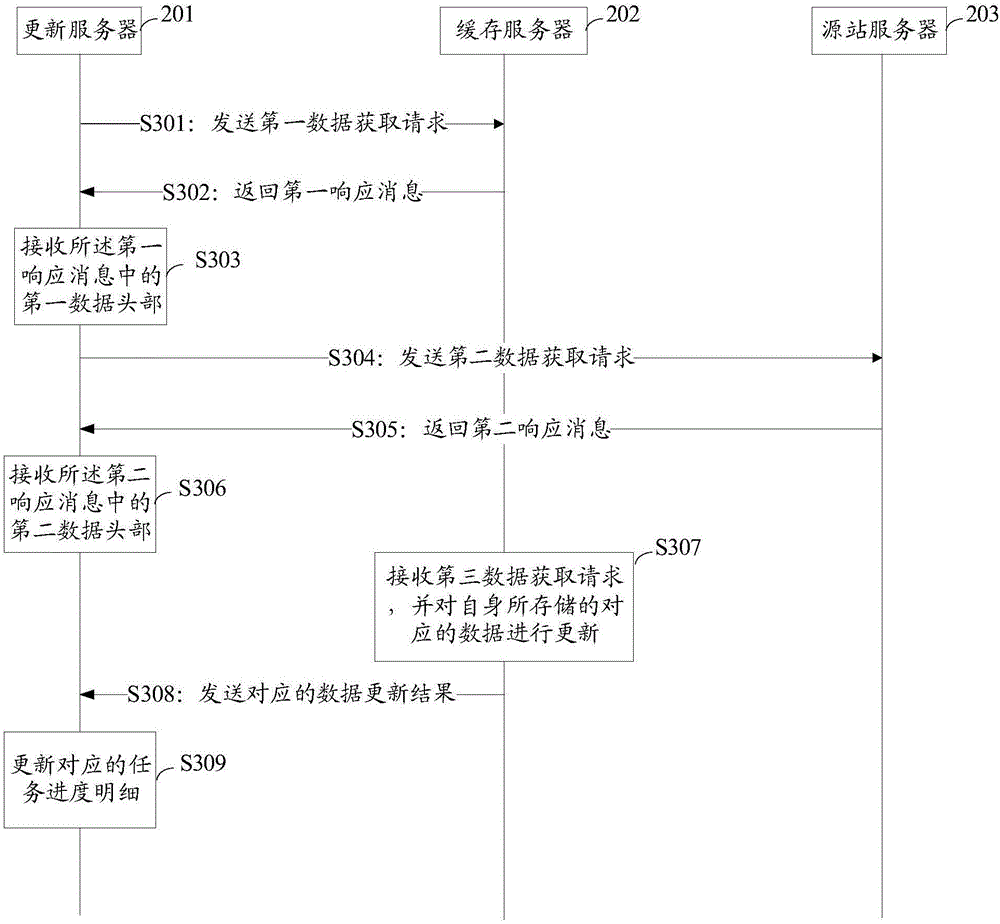
A caching server, an updating server and a data updating method
Provided are a caching server, an updating server and a data updating method. The data updating method comprises the steps of judging whether or not corresponding data stored in the caching server coincides with the corresponding data stored in a source station server when a data updating task is received; and when it is judged that the corresponding data stored in the caching server does not coincide with the corresponding data stored in the source station server, instructing the caching server to update the stored corresponding data. The above scheme can reduce the running cost and save the resources when updating of the data in the caching server is carried out.
Owner:SHANGHAI DNION INFORMATION & TECH
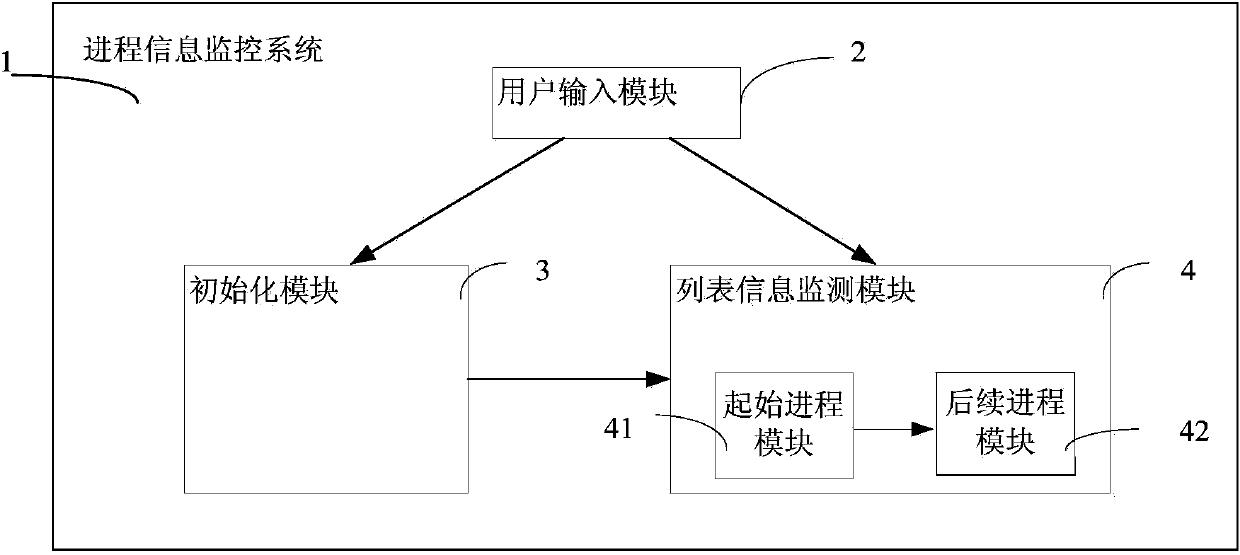
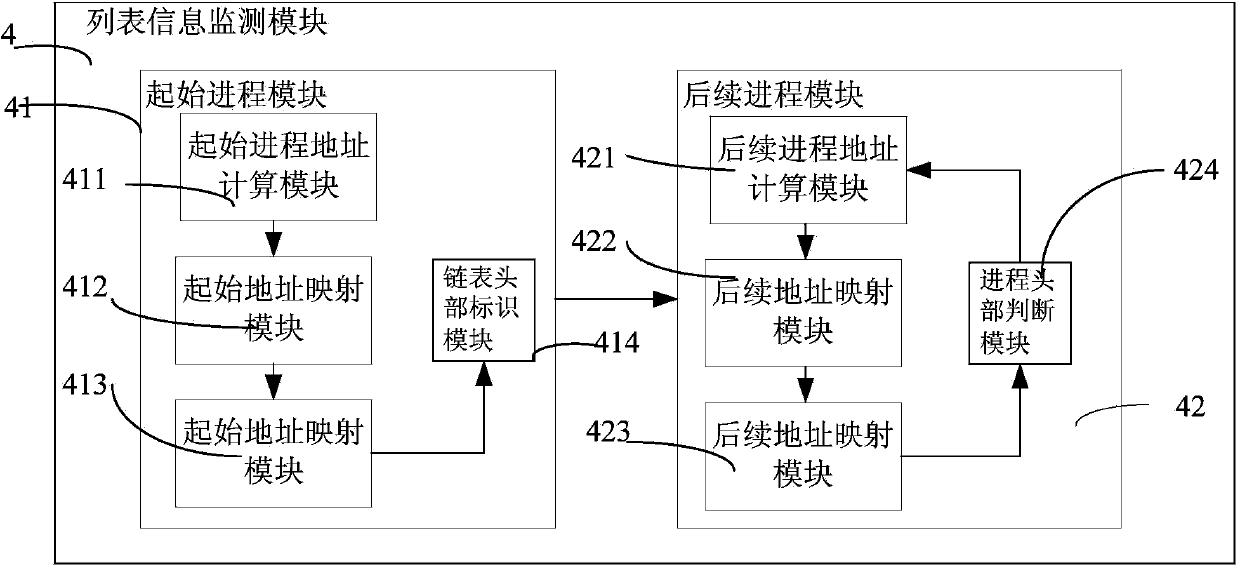
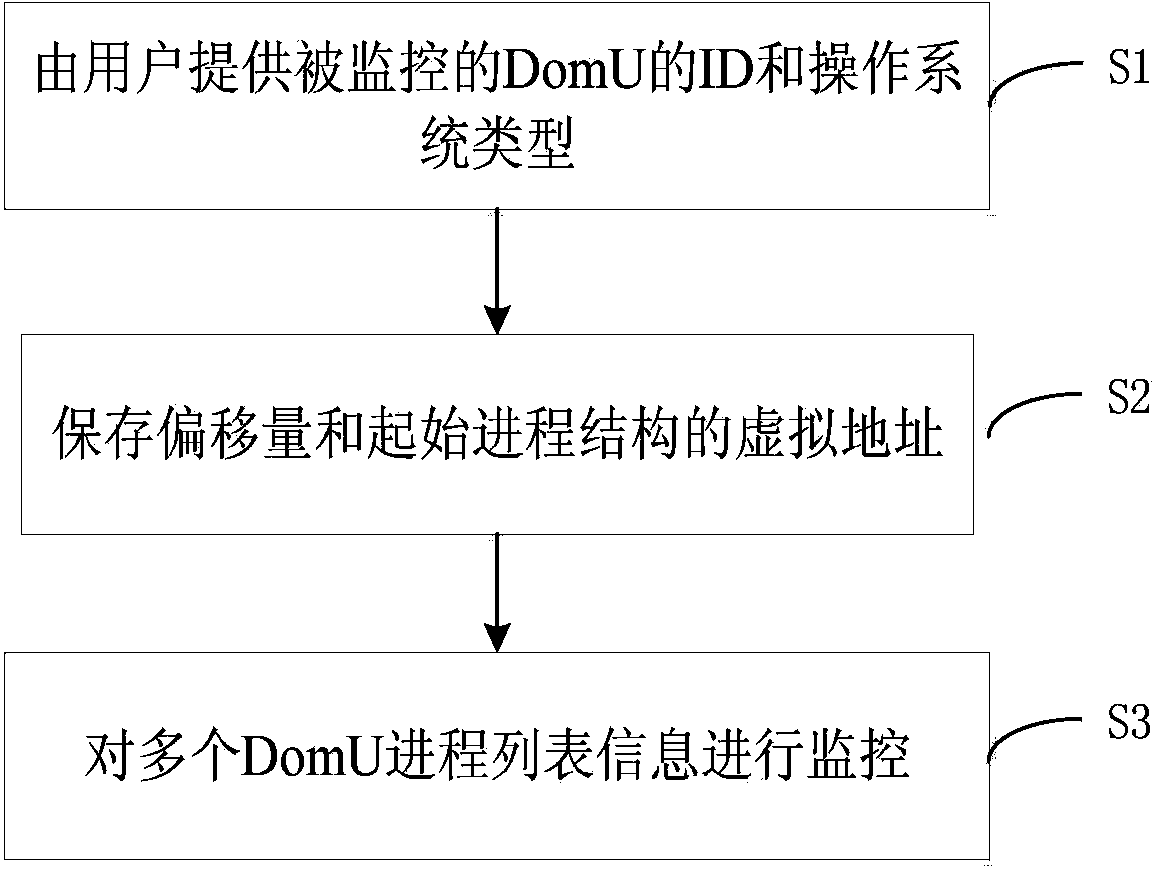
Process information monitoring system and method in virtual environment
ActiveCN103744851AReduce overheadReduce operating overheadPlatform integrity maintainanceProgram controlSystem deploymentVirtualization
The invention discloses a process list information monitoring system and method in a virtual environment. The process list information monitoring system is deployed in a privilege virtual machine, and is used for monitoring process list information of a plurality of client virtual machines. The process list information monitoring system comprises a user input module, an initialization module and a list information monitoring module, wherein according to the user input module, a user provides the ID and the type of an operating system of each monitored client virtual machine, the initialization module is used for storing the offset and the virtual address of a starting process structure, and the list information monitoring module is used for monitoring process list information of the client virtual machines.
Owner:INST OF COMPUTING TECH CHINESE ACAD OF SCI +1
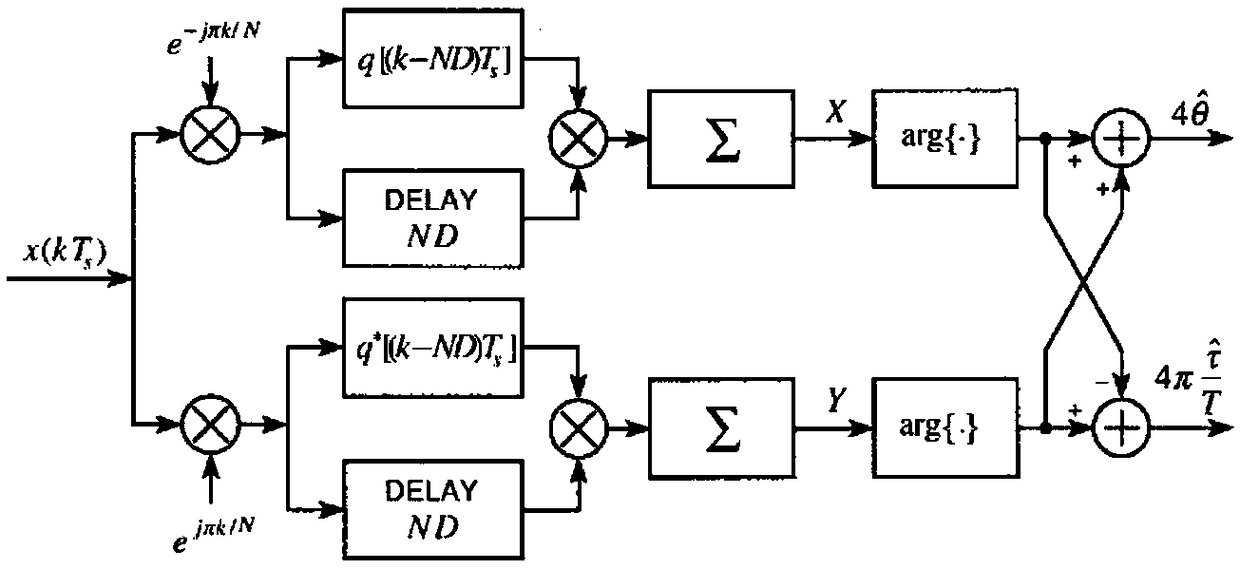
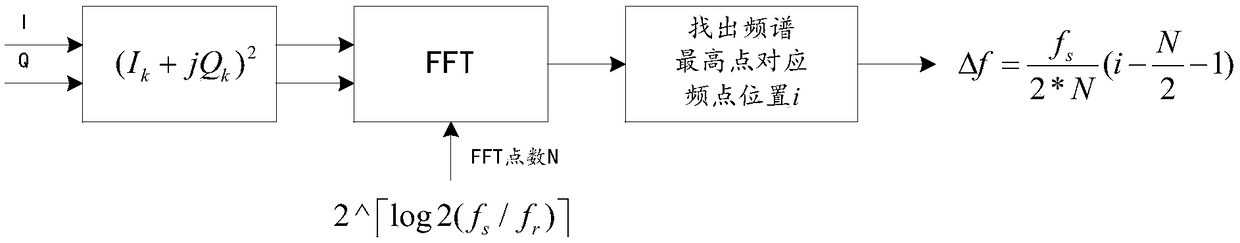
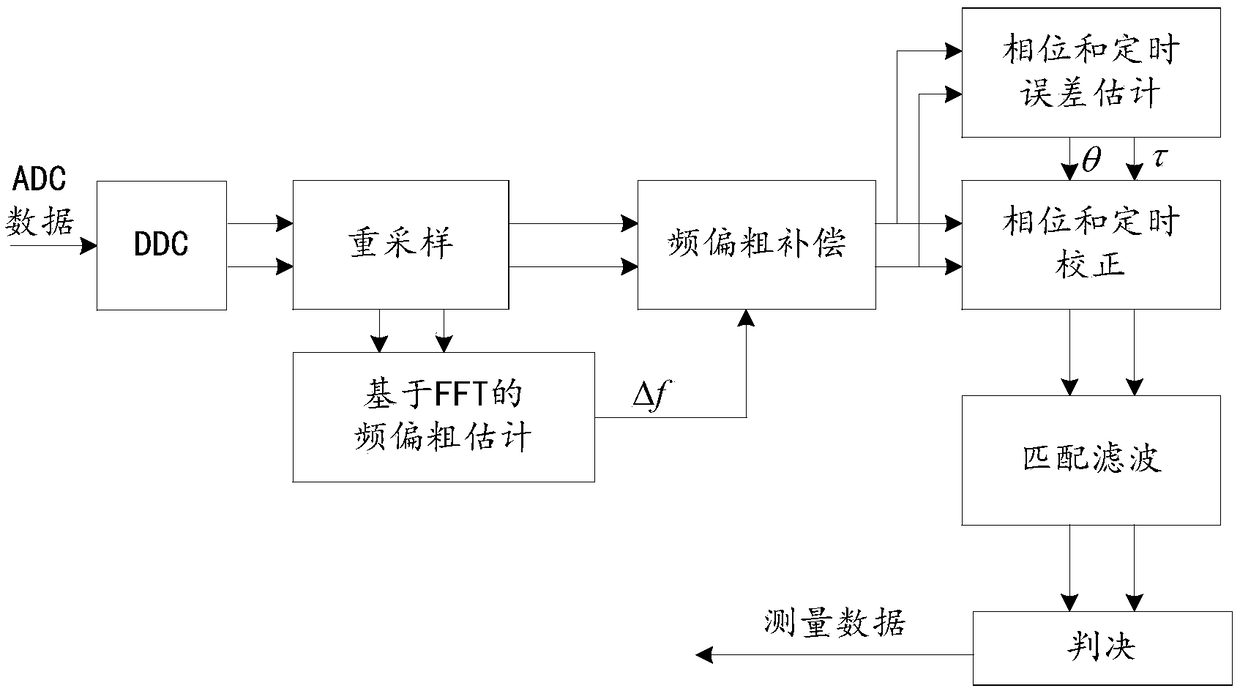
A carrier frequency offset estimation method of a baseband signal and a device thereof
ActiveCN109067680ASimple calculationHigh carrier frequency offset estimation accuracyCarrier regulationFrequency spectrumCarrier frequency offset
A carrier frequency offset estimation method of baseband signal and device thereof, the carrier frequency offset estimation method comprises the steps of baseband signal acquisition, complex signal calculation, complex signal frequency spectrum shifting, complex signal resampling, useful spectrum line frequency point sequence number acquisition and carrier frequency offset estimation, etc. As thecomplex signal after spectrum shifting is resampled, the sampling rate of the system can be matched to a fixed value, so that FFT processing with a fixed number of points can be adopted to obtain a spectral sequence including useful spectral lines, so that the system can obtain the frequency point number corresponding to the useful spectral line without increasing the number of FFT points, but also simplifies the calculation process of obtaining the frequency point serial number. On the premise of guaranteeing the higher precision of carrier frequency offset estimation, it can speed up the processing speed, further reduce the calculation time and the running cost of the system, and finally help to improve the real-time performance of OQPSK signal in demodulation processing and carrier frequency offset estimation processing.
Owner:SHENZHEN CITY SIGLENT TECH
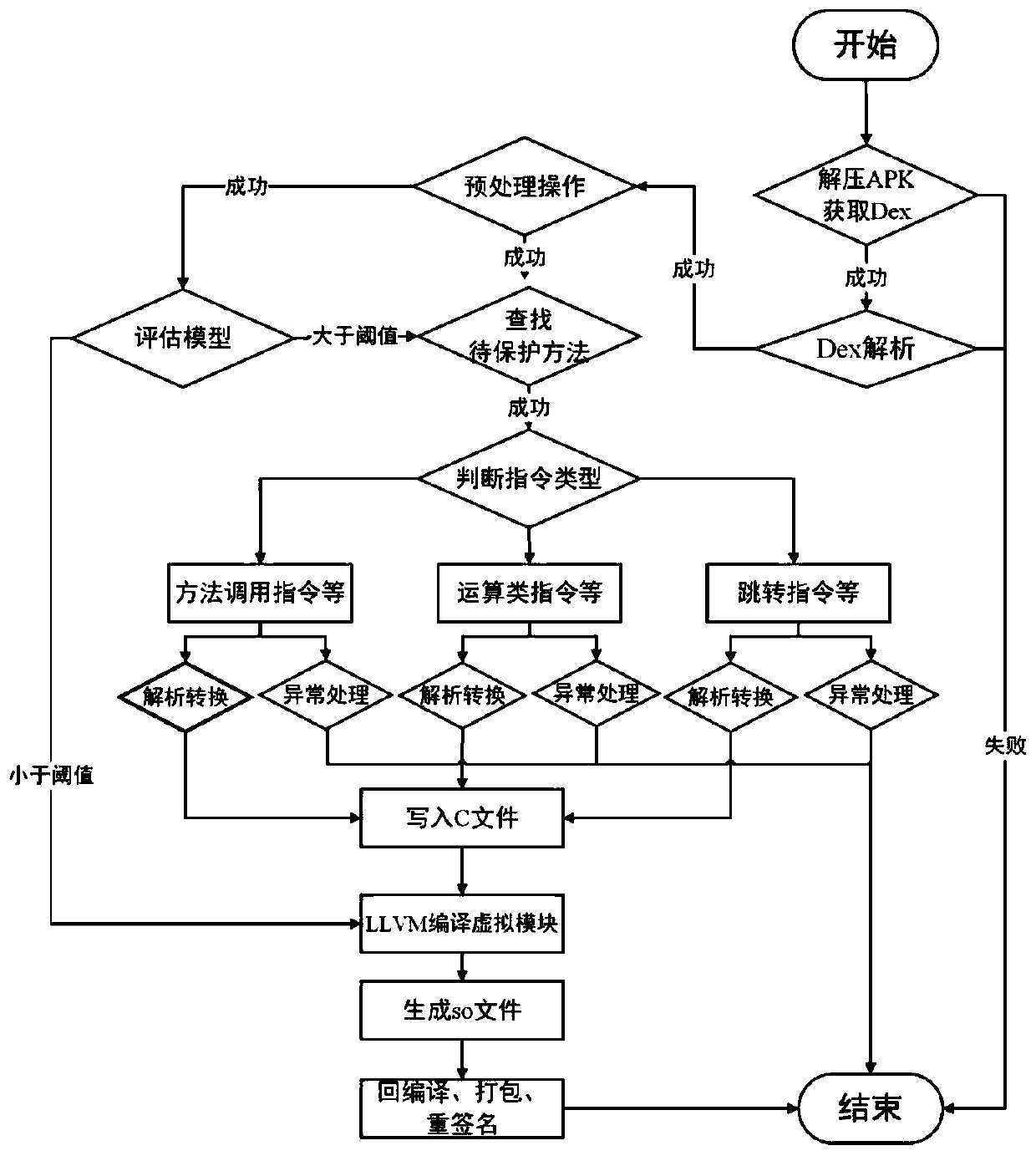
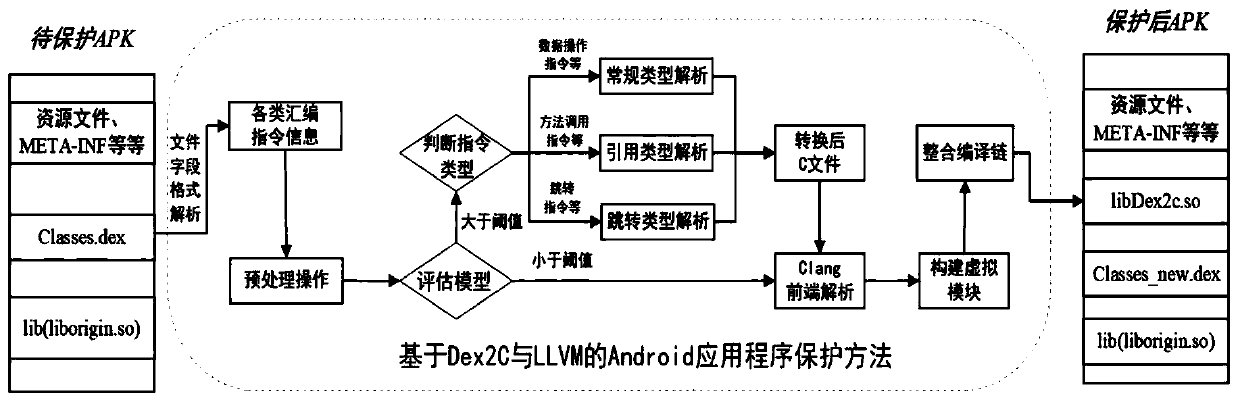
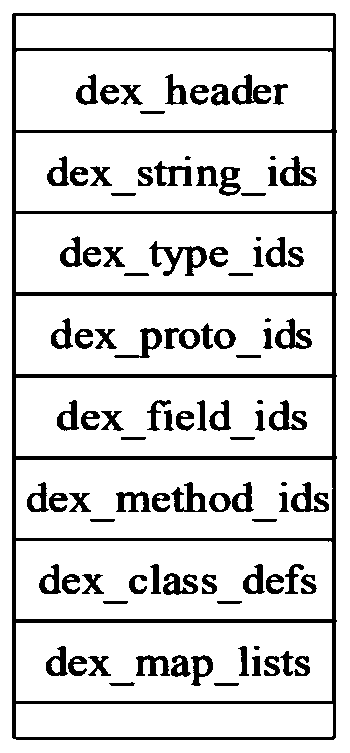
Android application program protection method based on Dex2C and LLVM
ActiveCN110245467AAvoid loopingRedundant cycle operationProgram/content distribution protectionVirtualizationModel selection
The invention discloses an Android application program protection method based on Dex2C and LLVM. The method comprises the following steps: decompressing an APK to obtain and analyze a Dex file, obtaining all necessary information, capable of recovering C codes, of each assembly instruction; selecting whether to carry out Dex2C conversion or not according to the evaluation model, and if the Dex2C conversion exceeds a threshold value, carrying out Dex2C conversion: carrying out conversion preprocessing operation, including searching a to-be-protected method, inserting assembly instruction statements, establishing an adjacency relation of instructions and the like, and selecting one of the three sets of conversion logics one by one according to the type of the assembly instruction to carry out conversion; achieving virtualization during compiling based on the LLVM, and if the threshold value is not exceeded, executing an LLVM compiling virtualization module directly; after the So file is generated through the framework, repackaging and signing are carried out, and generating the APK with the equivalent function. According to the invention, the protection methods of the Dex layer and the local layer are combined, on one hand, the execution efficiency of the APK can be improved, and on the other hand, the attack difficulty and cost of malicious attackers are greatly improved.
Owner:NORTHWEST UNIV(CN)
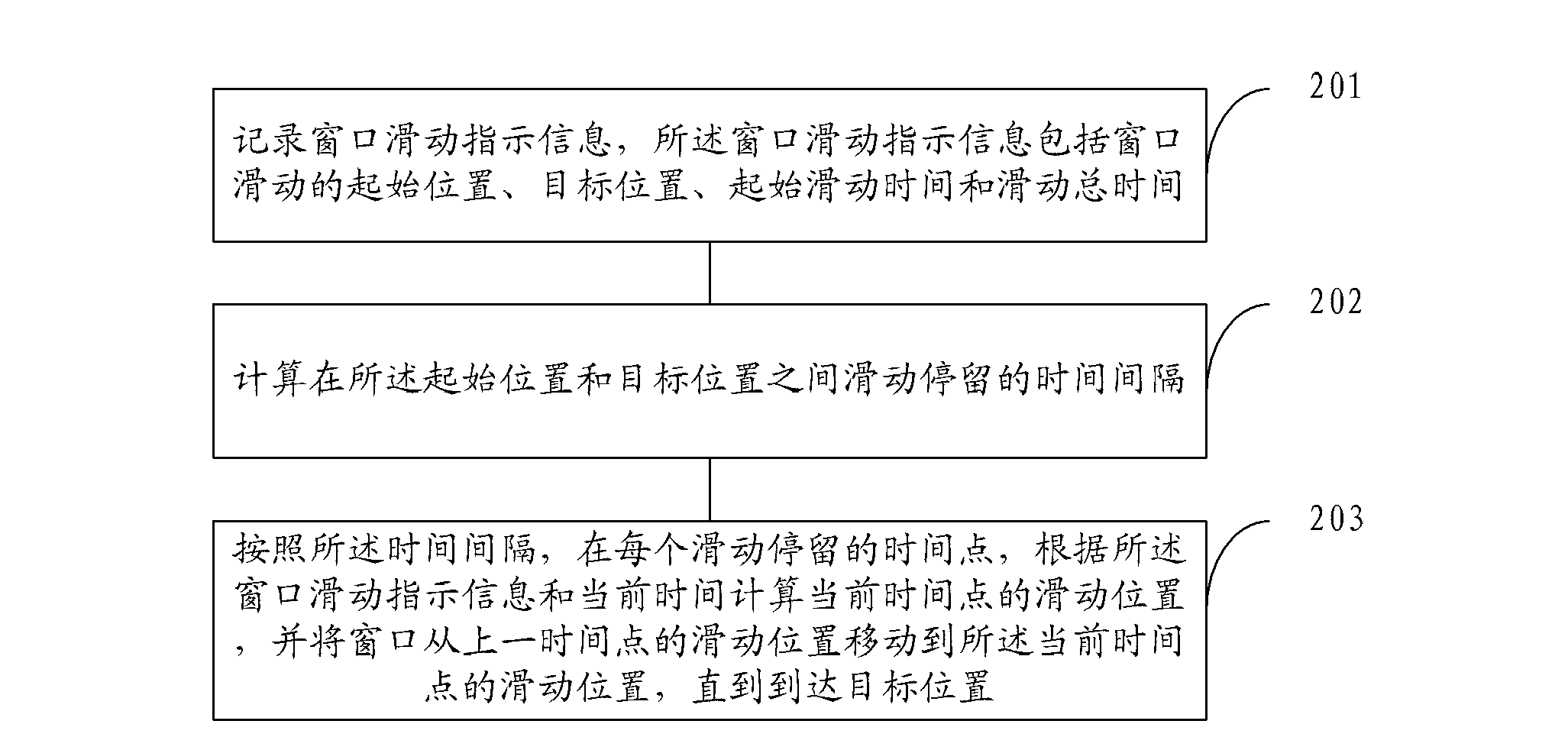
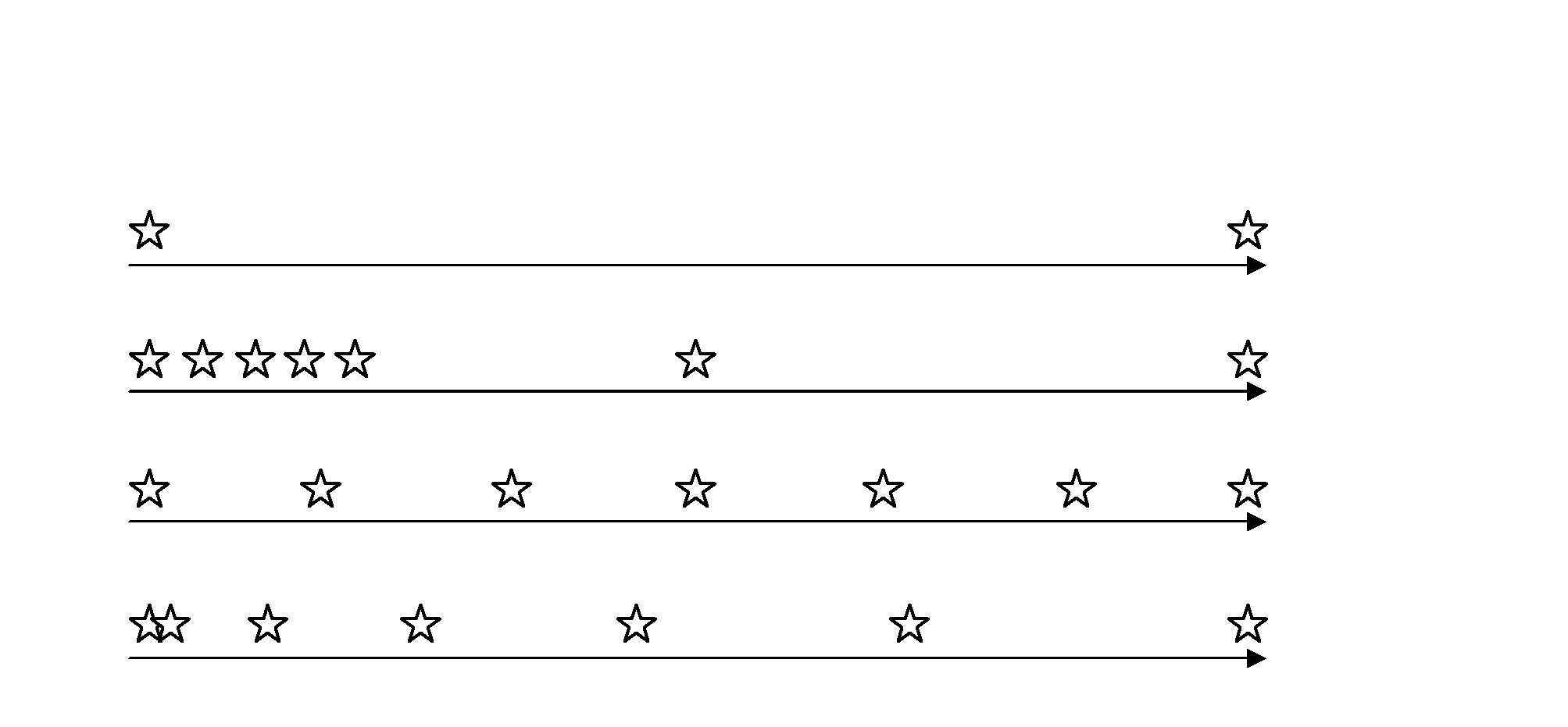
Window sliding method and window sliding device
ActiveCN103257798ATo attract users' attentionSignificant change effectSpecific program execution arrangementsInput/output processes for data processingSlide windowComputer science
The invention provides a window sliding method and a window sliding device, and aims to solve the problems about window data stagnation or obvious data variation caused by instant moving. The window sliding window method includes: recording window sliding instruction information which includes a start position, a target position, start sliding time and total sliding time of window sliding; calculating time intervals of sliding stop between the start position and the target position; and according to the time intervals, at the time point of every sliding stop, moving a window from the slide position at the previous time point to the slide position to the current time point till the target position is reached according to the window sliding instruction information and the currently calculated slide position of the current time point. Several points are selected for stopping during the window sliding process, so that a human-eye recognizable and visual sliding effect can be generated on a screen when the window slides.
Owner:ALIBABA GRP HLDG LTD
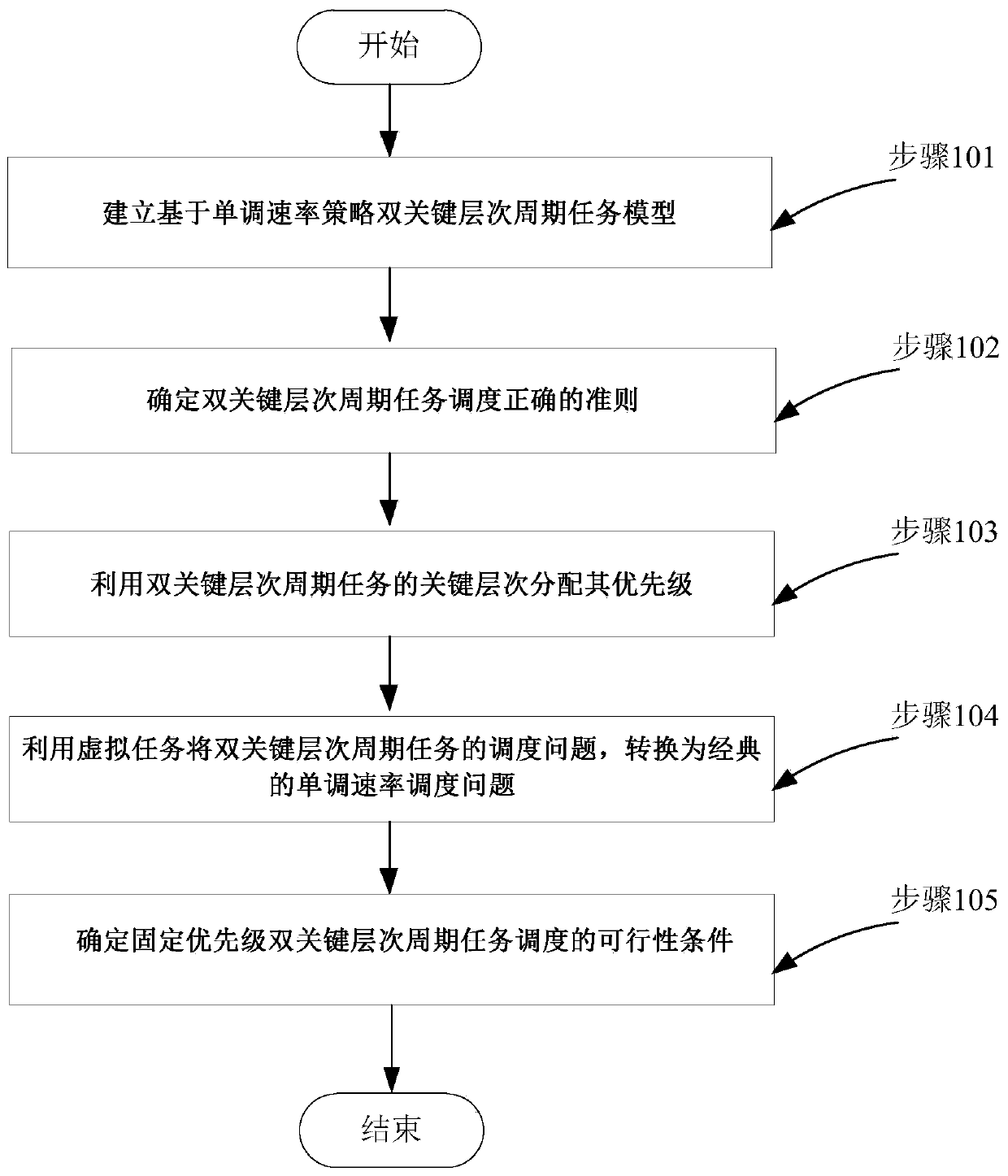
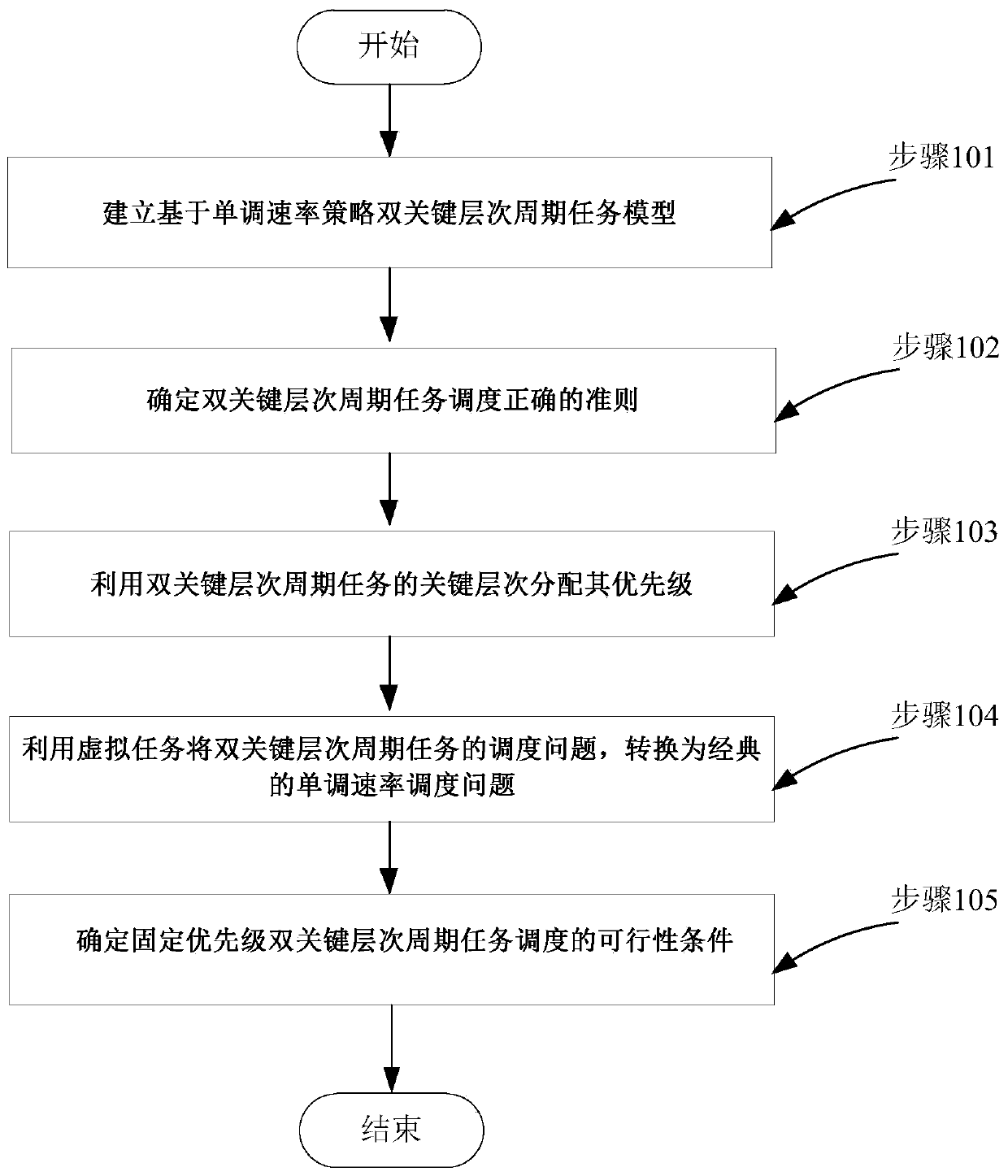
Fixed priority hybrid key system scheduling method based on virtual tasks
ActiveCN109918185AReduce operating overheadReduce time complexityProgram initiation/switchingTime complexityDistributed computing
The invention discloses a fixed priority hybrid key system scheduling method based on virtual tasks. The method comprises the following steps: establishing a double-key-level periodic task model basedon a monotonous rate strategy; determining a criterion that the dual-key hierarchical periodic task scheduling is correct; distributing the priority of the dual-key-level periodic task by utilizing the key levels of the dual-key-level periodic task; converting the scheduling problem of the double-key-level periodic task into a classical monotonous rate scheduling problem by using the virtual task; and determining feasibility conditions of the fixed-priority double-key-level periodic task scheduling. According to the method, the scheduling problem of the fixed-priority double-key-level periodic task is converted into the classical monotonous rate scheduling problem through the method for constructing the virtual task, the time complexity of double-key-level periodic task scheduling is effectively reduced, and a simple and efficient solution is provided.
Owner:HUAQIAO UNIVERSITY
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com