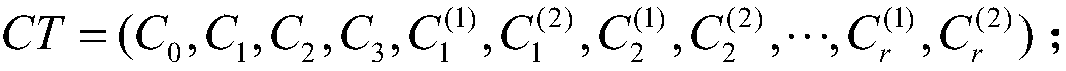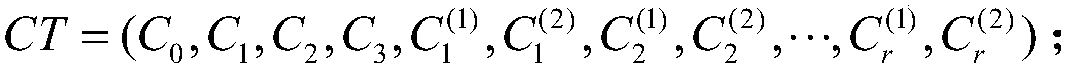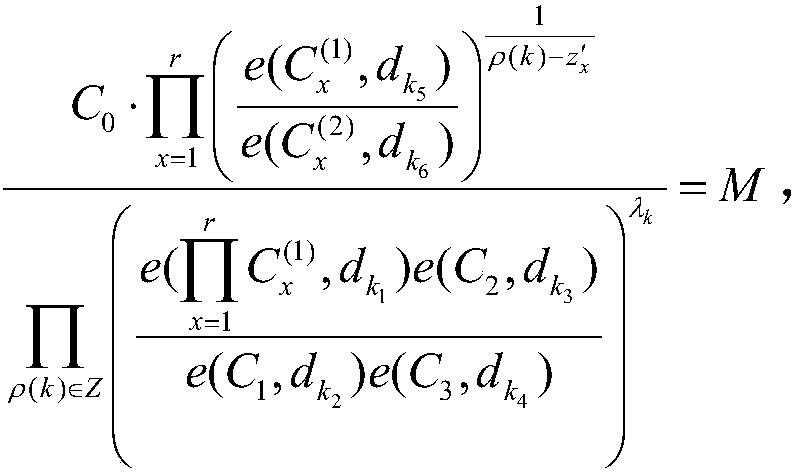Attribute-based encryption method of revocable key policy in standard model
A technology of attribute encryption and standard model, applied to the usage of multiple keys/algorithms and key distribution, it can solve the problems of system parameter growth, poor scalability, fixed number of users, etc., and achieve the effect of protecting privacy.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
[0133] A Reversible Key Policy Based on Attribute-Based Encryption of Composite Order in Standard Model
[0134] Step 1. System Setup
[0135] 1) Input the security parameter λ, the complete set of attributes Z N , composite number N=p 1 p 2 p 3 And bilinear pair e:G×G→G T ;
[0136] 2) The key generation center PKG randomly selects a, t∈Z N , Calculate u = g t ;
[0137] 3) The PKG output system parameters of the key generation center are:
[0138] Params={N,G,G T ,e,g,h,u,v,w,e(g,g) a}, the master key is MSK=a.
[0139] Step 2. User Key Generation
[0140] 1)(A m×n ,ρ) is the LSSS scheme, A m×n for ZN m×n matrix on A i Represents the matrix A m×n The i-th row of ρ(i)∈Z N Indicates row A i The attributes obtained by ρ mapping, where i∈{1,2,···,m};
[0141] 2) The key generation center PKG randomly selects r, α 1 ,···,α m ,β 1 ,···,β m ,v 2 ,···,v n ∈ Z N , defining the vector Calculate A i secret share of For i∈{1,2,···,m}, compute Then th...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com