Method and system for managing account information
a technology for managing account information and accounts, applied in the field of consumers' account information management, can solve problems such as identity theft, identity theft risk, and consumer questioning whether
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
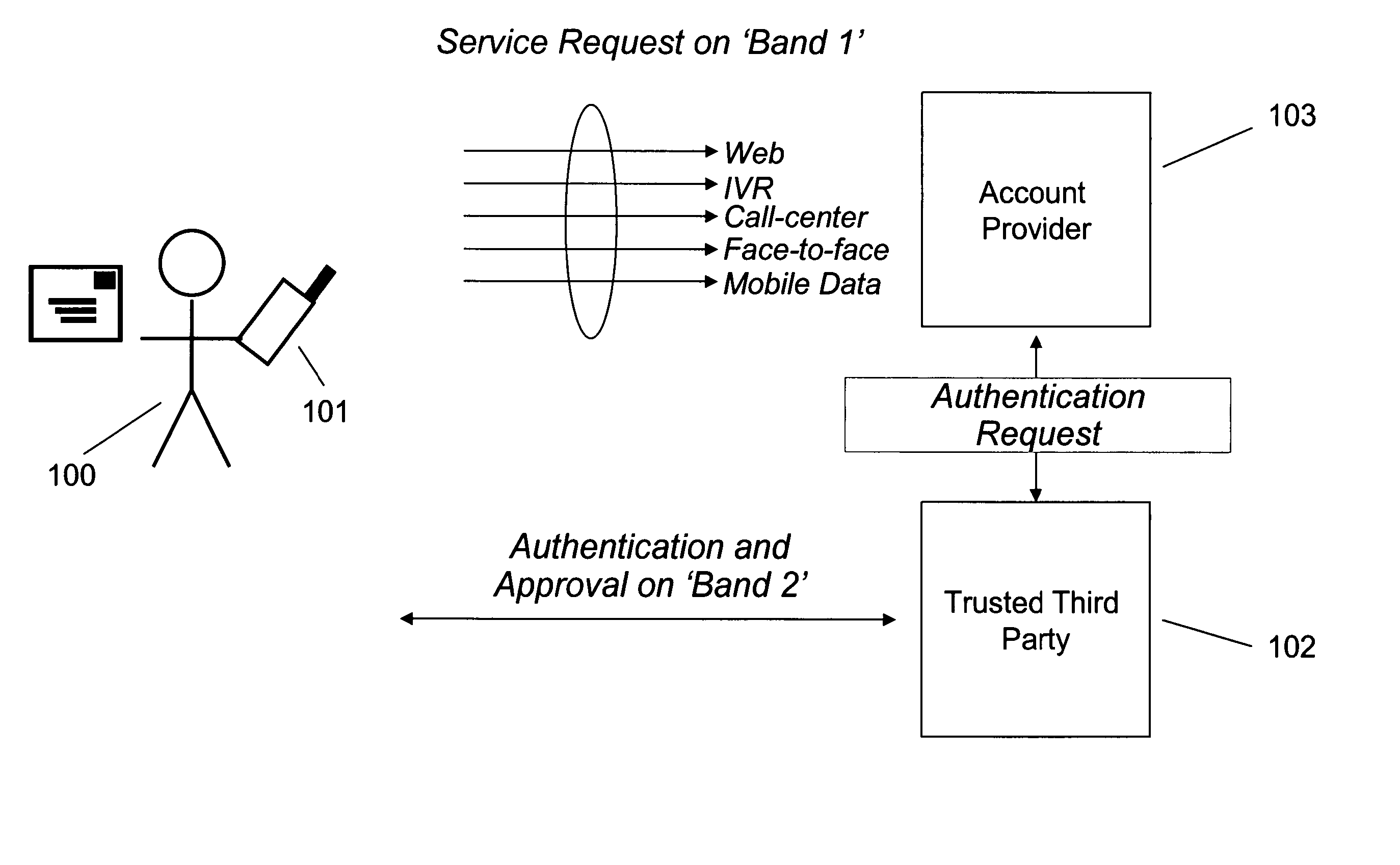
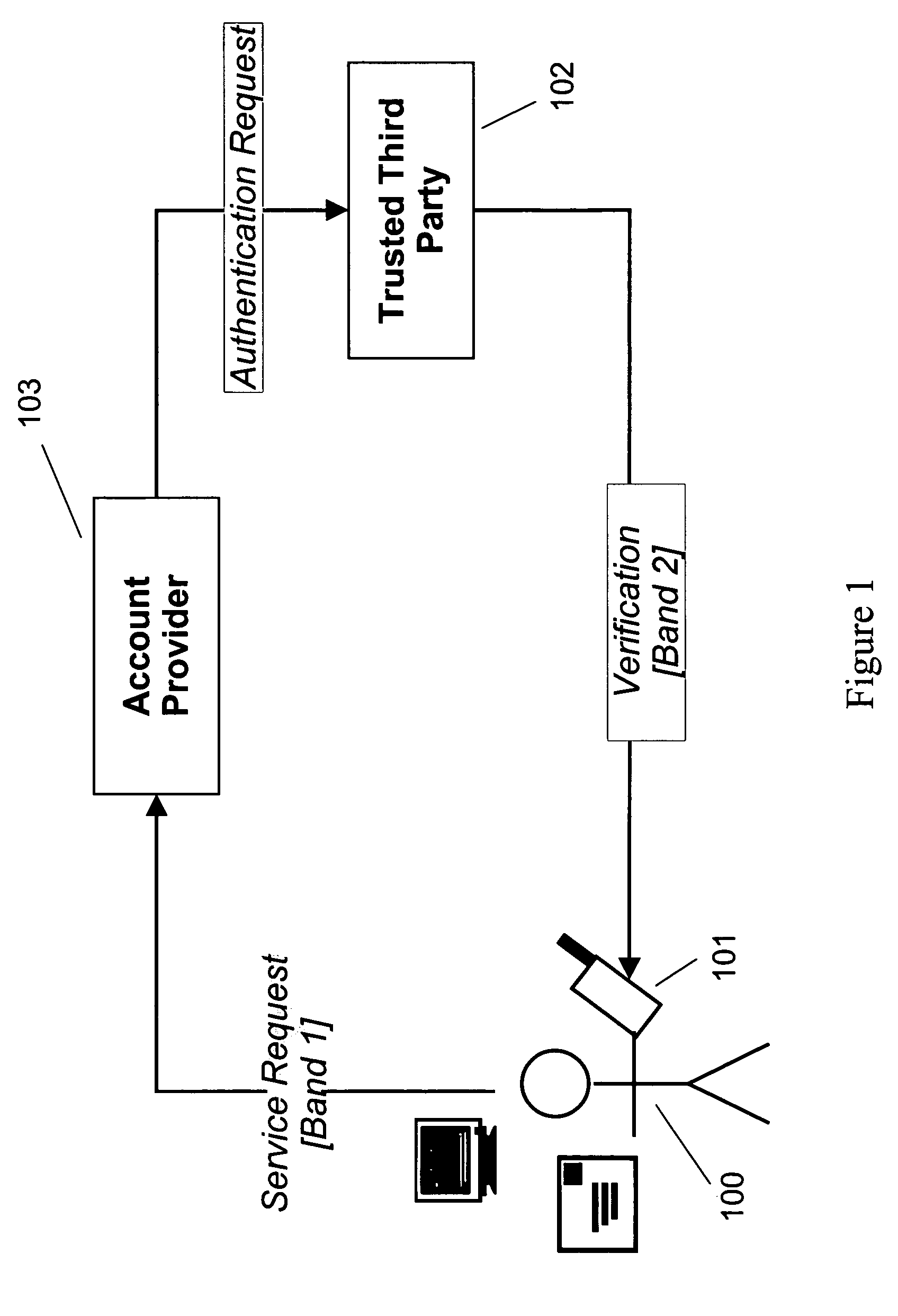
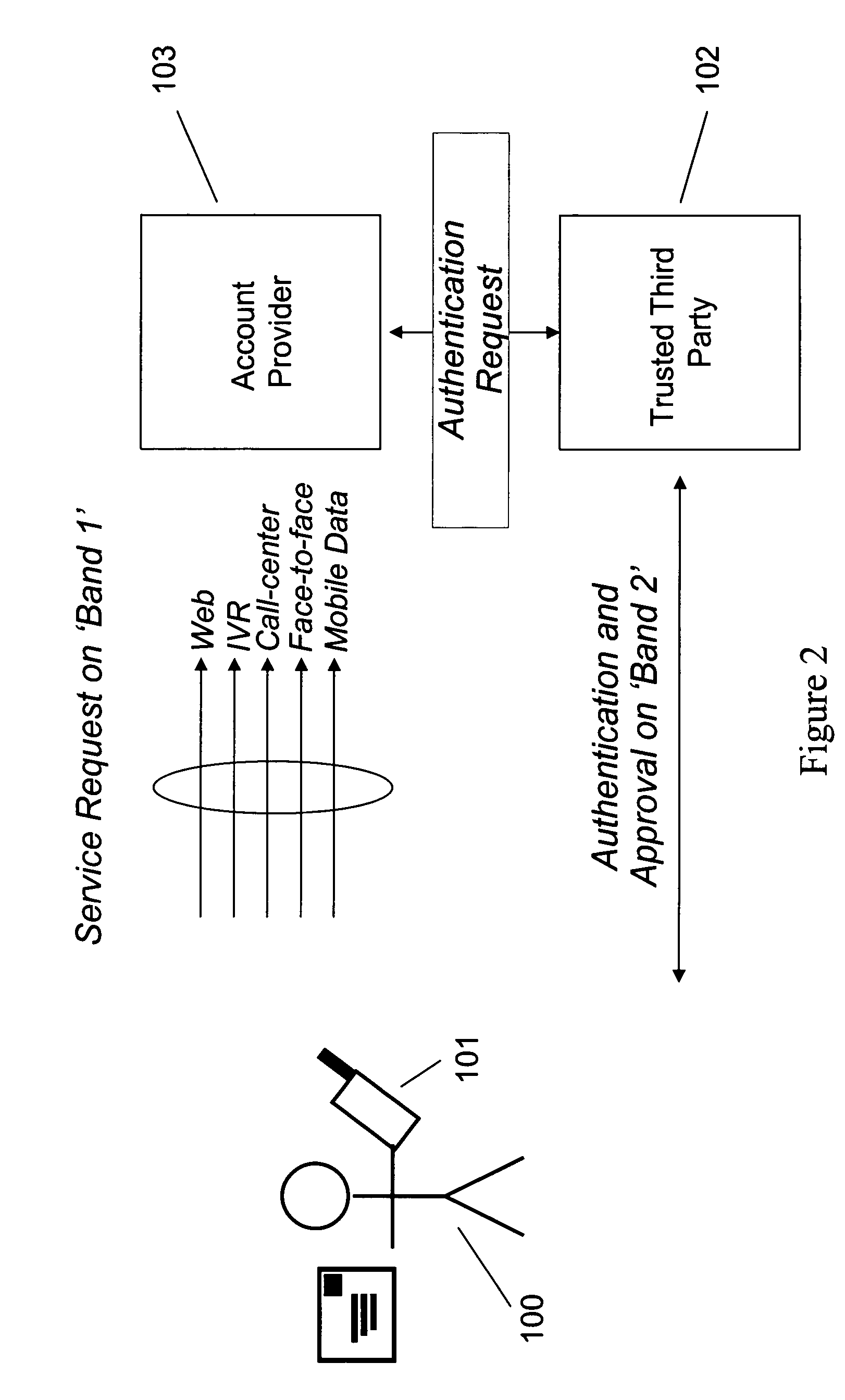
[0024] The present invention is an improved method and system for managing a consumer's account information. The invention may be used in connection with transactions between consumers on the one hand and financial institutions, banks, merchants, healthcare providers, governmental entities or any other party engaged in transactions with consumers in which identifying information is exchanged. Accordingly, the words “financial institution,”“bank,”“merchant,”“healthcare provider,” and “governmental entity” are used interchangeably herein. Similarly, the words “organization,”“enterprise,”“corporation,”“company,”“venture” and “operation” are used interchangeably herein and can be used to describe private organizations or governmental entities and are not meant to be limiting.
[0025] A “user,”“consumer” or “subscriber” may be a human user or may be a software process that is configured to access an electronic account.
[0026] An “account provider” can be an organization that provides its ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com