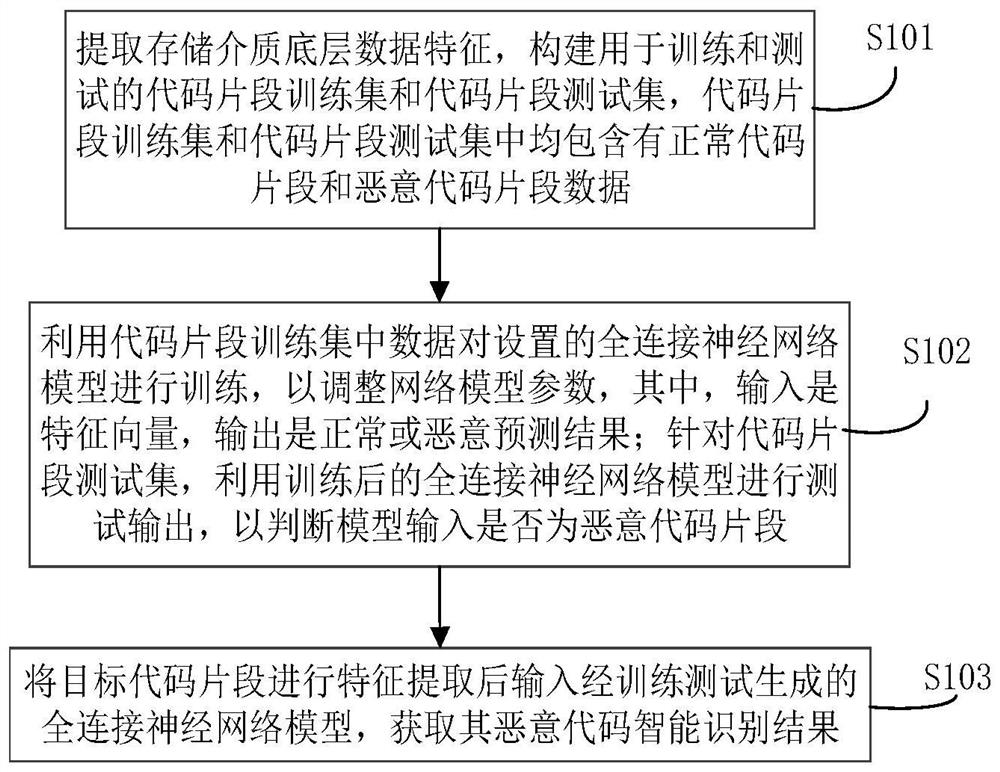
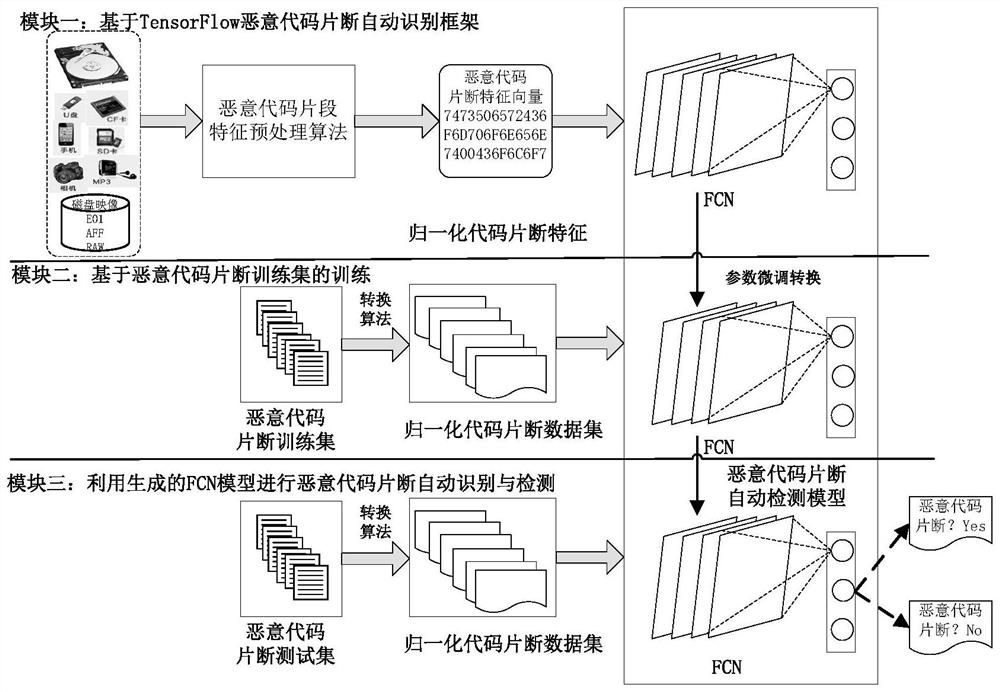
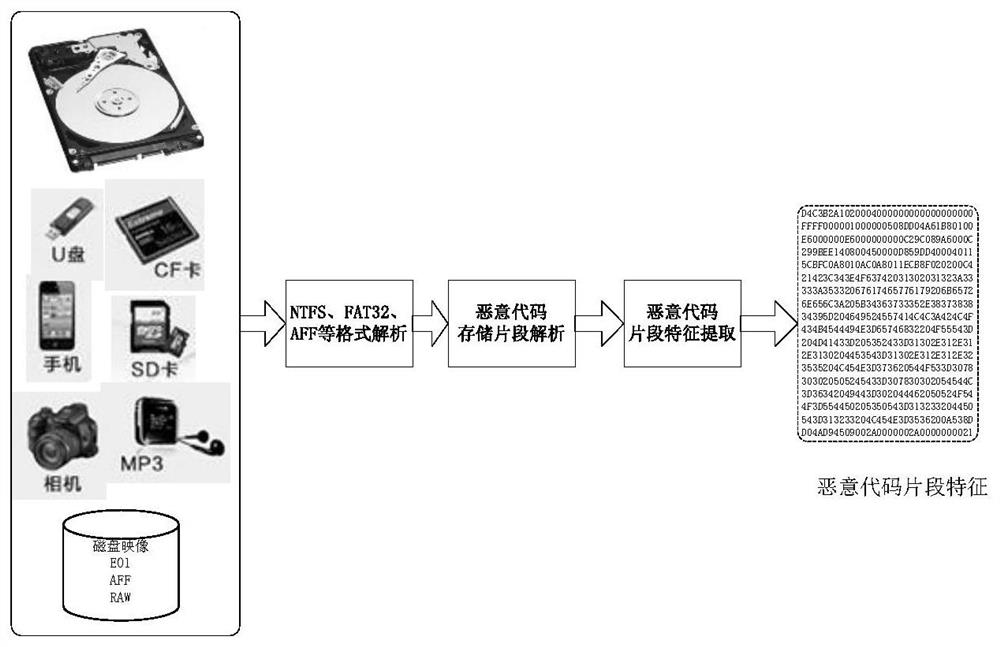
Intelligent malicious code fragment evidence obtaining method and system
A technology of malicious code and code fragments, applied in the field of digital forensics, which can solve the problems of complex forensics analysis, differences in evidence analysis of criminal events, and reduction in the number of closed cases.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0032] In order to make the purpose, technical solution and advantages of the present invention more clear and understandable, the present invention will be further described in detail below in conjunction with the accompanying drawings and technical solutions.
[0033]The research on automatic forensics technology has achieved preliminary research results. Some scholars have discussed the necessity and importance of highly automated digital forensics, and analyzed the advantages of automated forensics. In addition, in order to improve the automation of forensic analysis, button-type automatic forensic functions have been added to classic forensic suites, such as EnCase, Forensic ToolKit, AutopsyForensic Browser and other full-featured forensic tool suites that allow forensic investigators to click Which button can carry out preliminary and even some complex investigative analysis tasks. These popular tools strive to make the job of forensic investigators easier and improve t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com