Patents
Literature
31results about How to "Highly secure" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
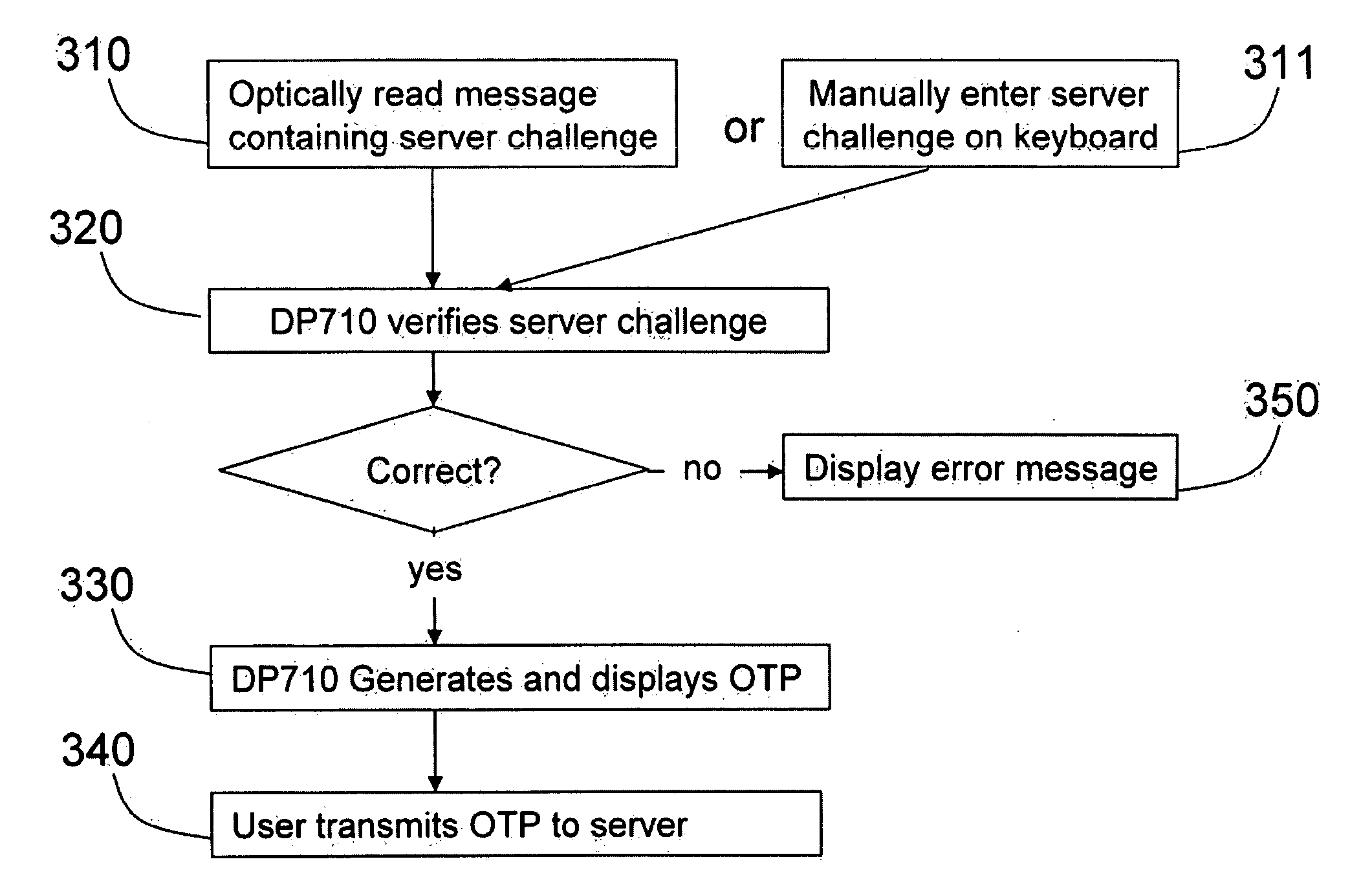
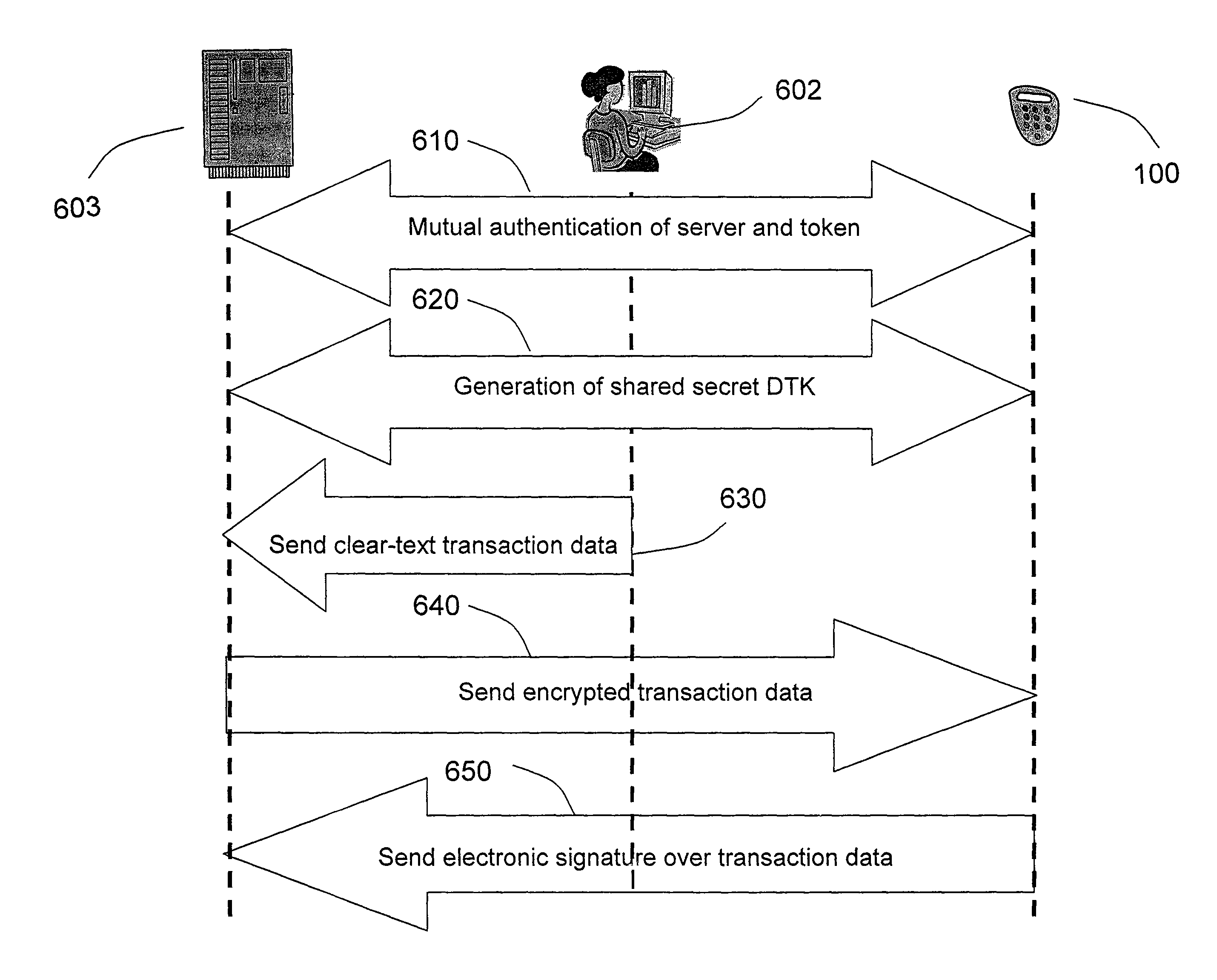
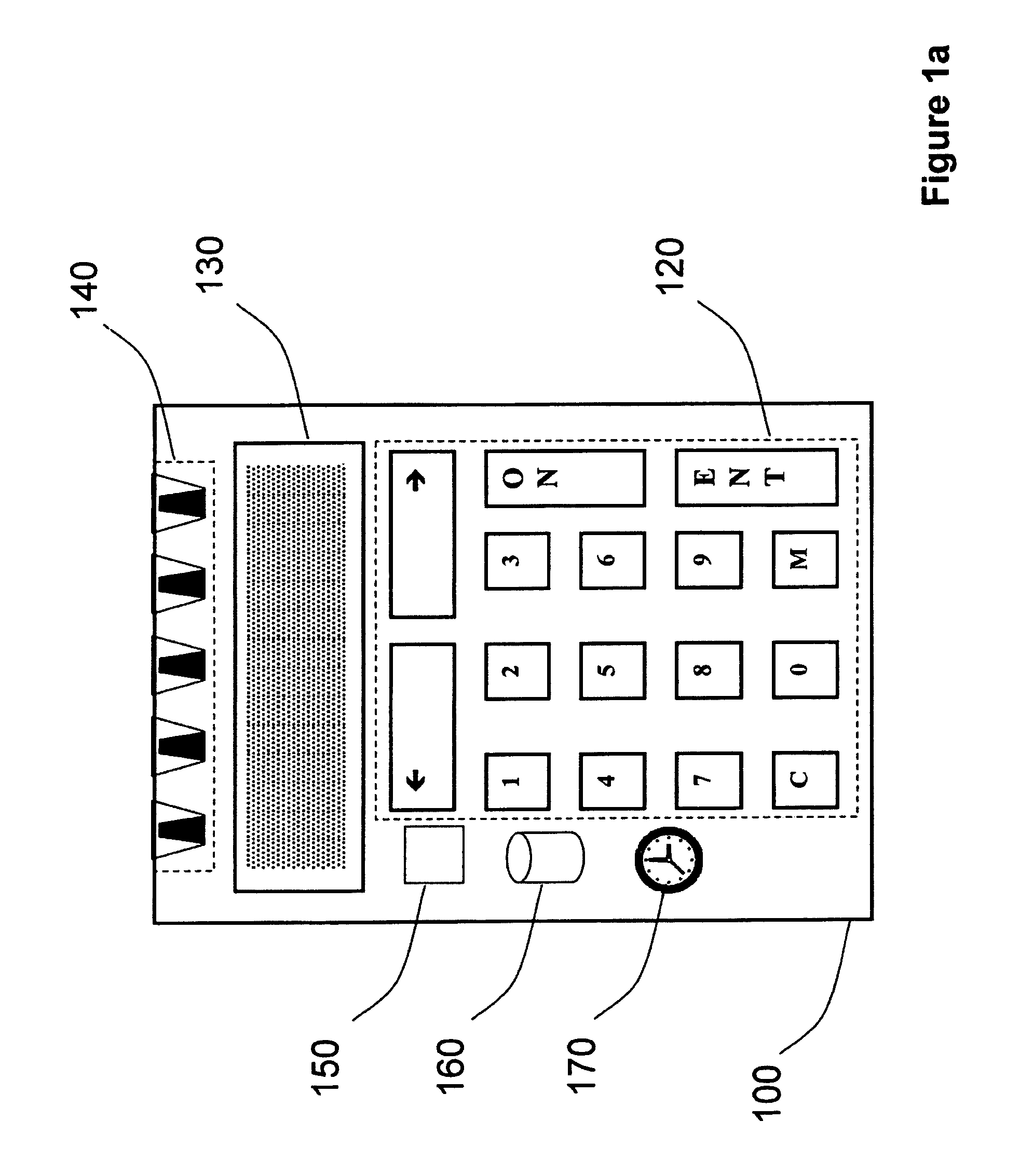
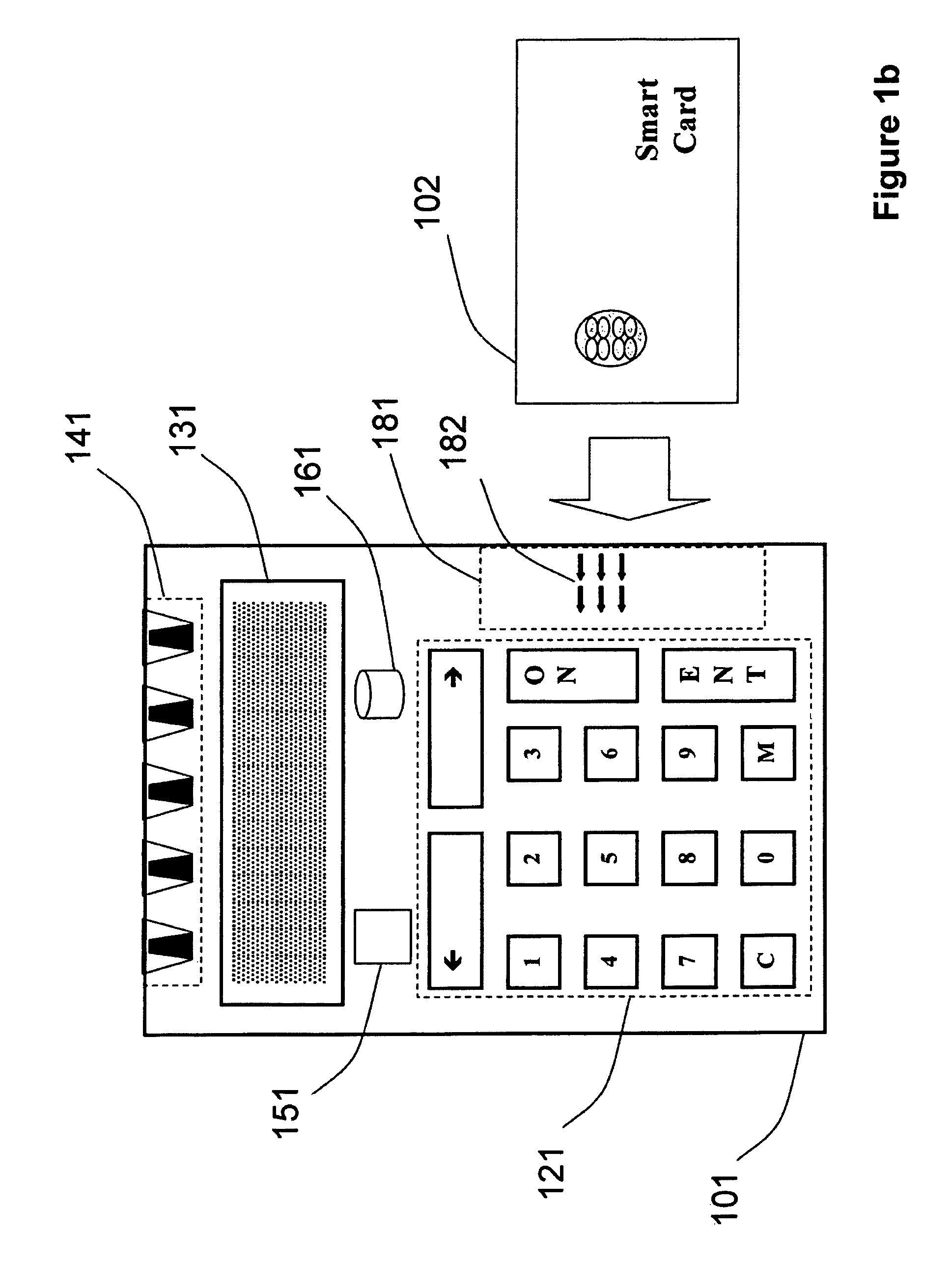
Strong authentication token generating one-time passwords and signatures upon server credential verification
ActiveUS20090235339A1Transfer size reductionHighly secureDigital data processing detailsMultiple digital computer combinationsInternet privacyTransaction data
The invention defines a strong authentication token that remedies a vulnerability to a certain type of social engineering attacks, by authenticating the server or messages purporting to come from the server prior to generating a one-time password or transaction signature; and, in the case of the generation of a transaction signature, signing not only transaction values but also transaction context information and, prior to generating said transaction signature, presenting said transaction values and transaction context information to the user for the user to review and approve using trustworthy output and input means. It furthermore offers this authentication and review functionality without sacrificing user convenience or cost efficiency, by judiciously coding the transaction data to be signed, thus reducing the transmission size of information that has to be exchanged over the token's trustworthy interfaces
Owner:ONESPAN NORTH AMERICA INC
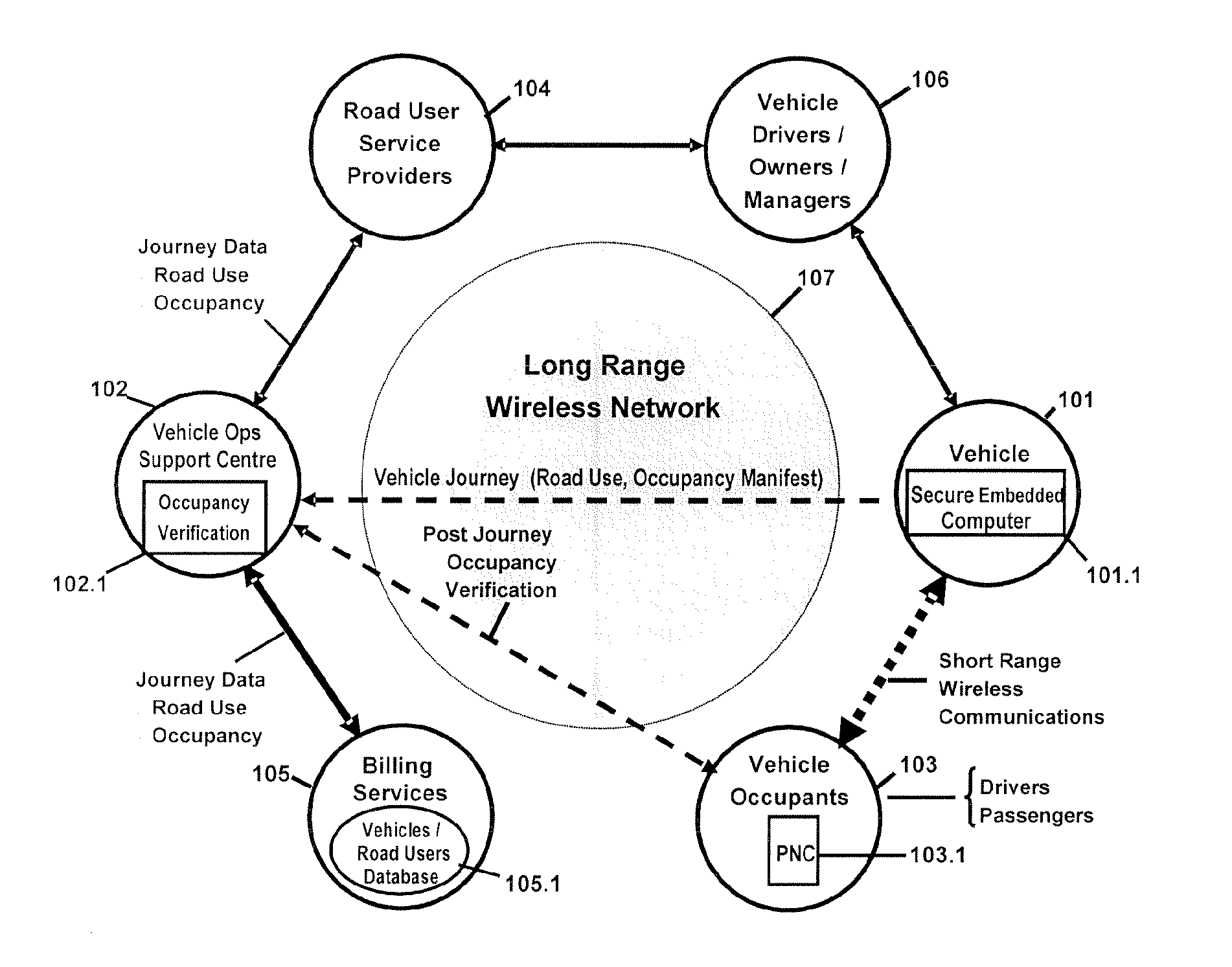
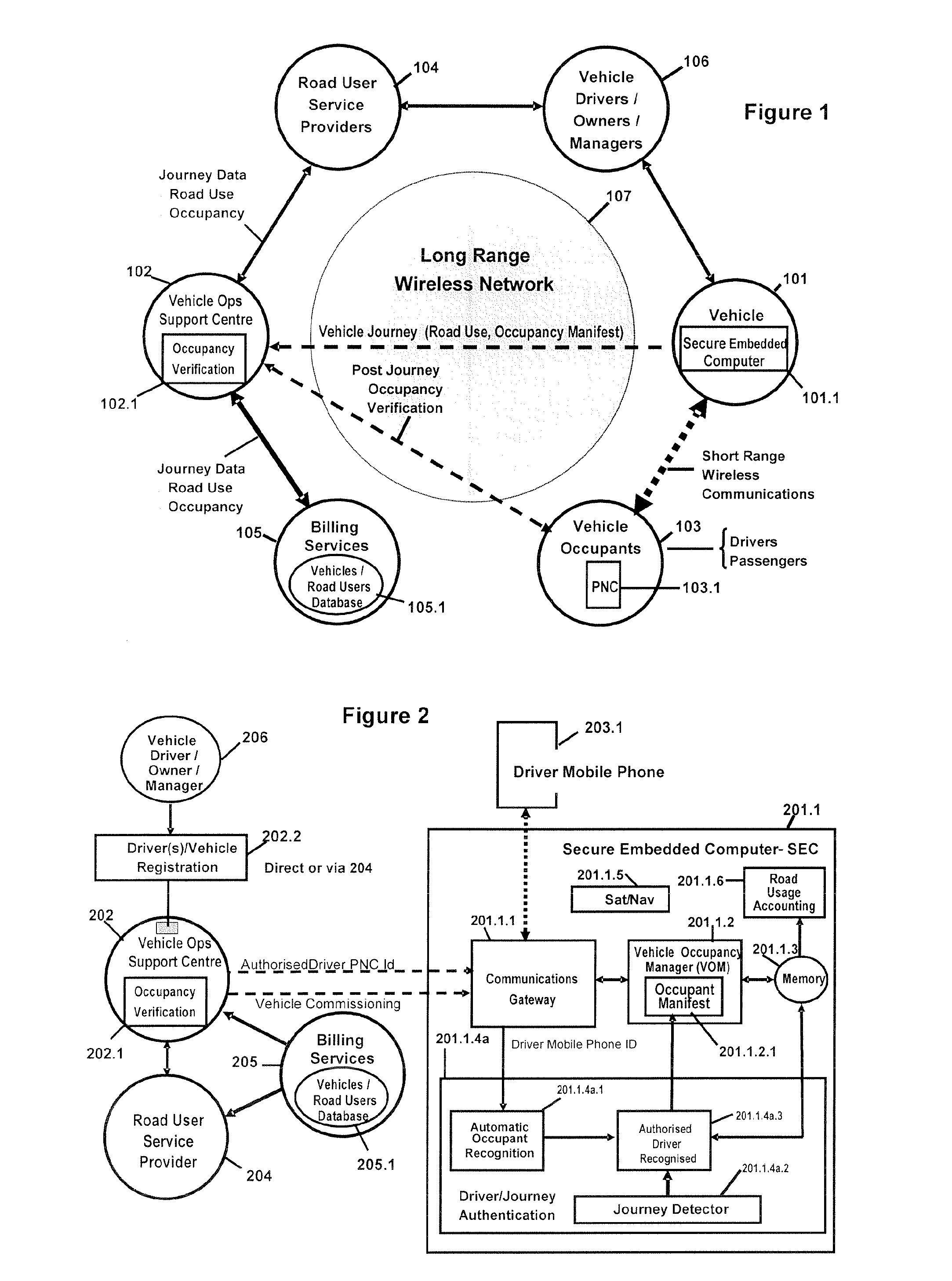
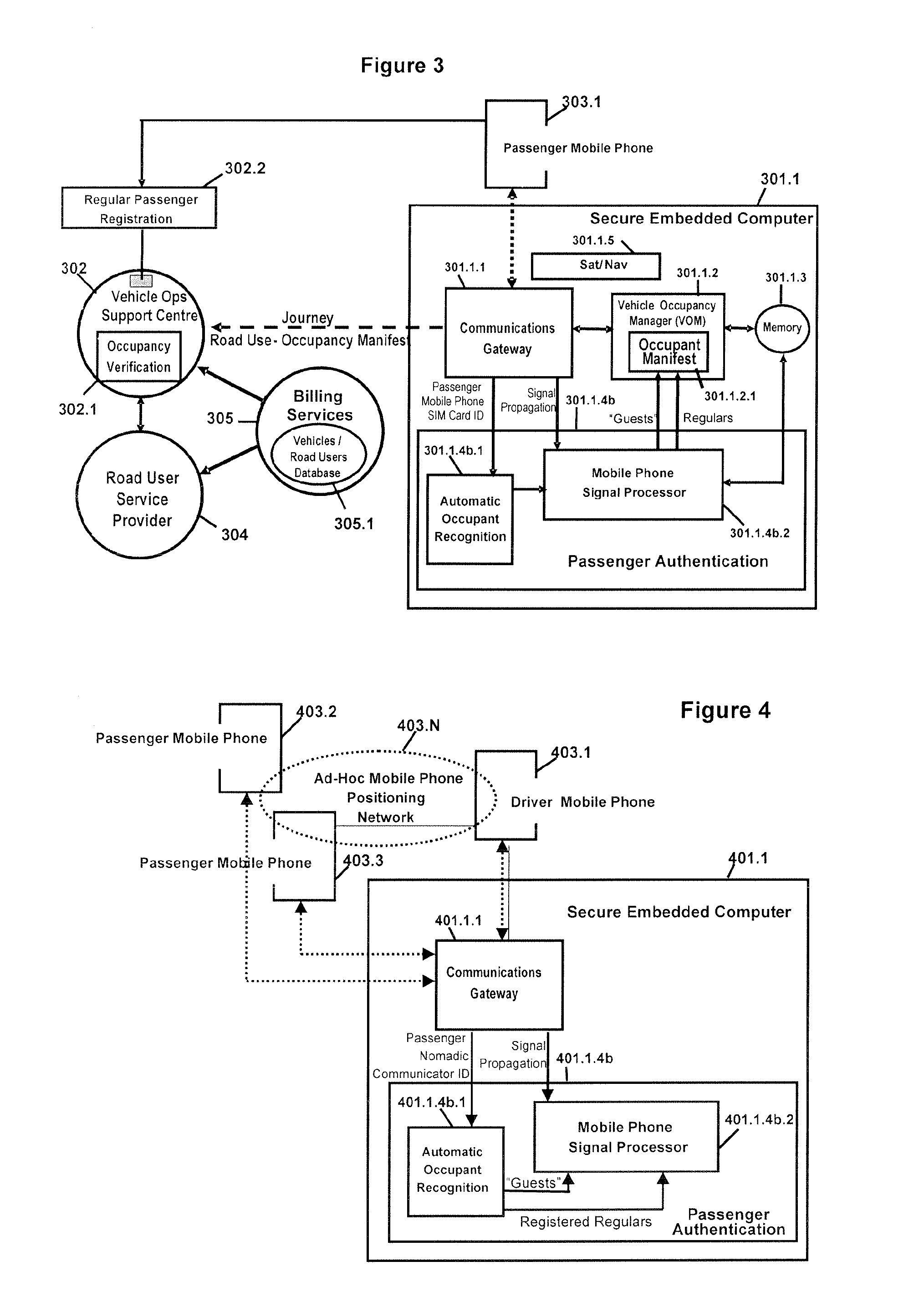
Occupancy Declaration/Verification For Passenger Transport Conveyances
InactiveUS20100201505A1Improve performanceHighly robustComplete banking machinesRoad vehicles traffic controlAirplaneDecision-making
The present invention relates to a secure method and enabling processes to: (1) through the use of personal nomadic communicators (PNCs) to automatically declare passenger occupancy in transport conveyances including but not limited to road vehicles, aircraft, trains, marine vessels, (2) monitor and assess the pattern of physical movements of passenger PNCs prior to, during, and after their use of such transport conveyances, (3) verify and record passenger occupancy based on such assessments and any suspicious patterns suggesting fraudulent declarations through the improper use and placement of PNCs not belonging to passengers, and (4) transfer occupancy data to management systems which utilise passenger occupancy as a factor in decision making including but not limited to determining occupancy related entitlements to the operators / owners / managers of transport conveyances.
Owner:HONARY SOUROUSH +1
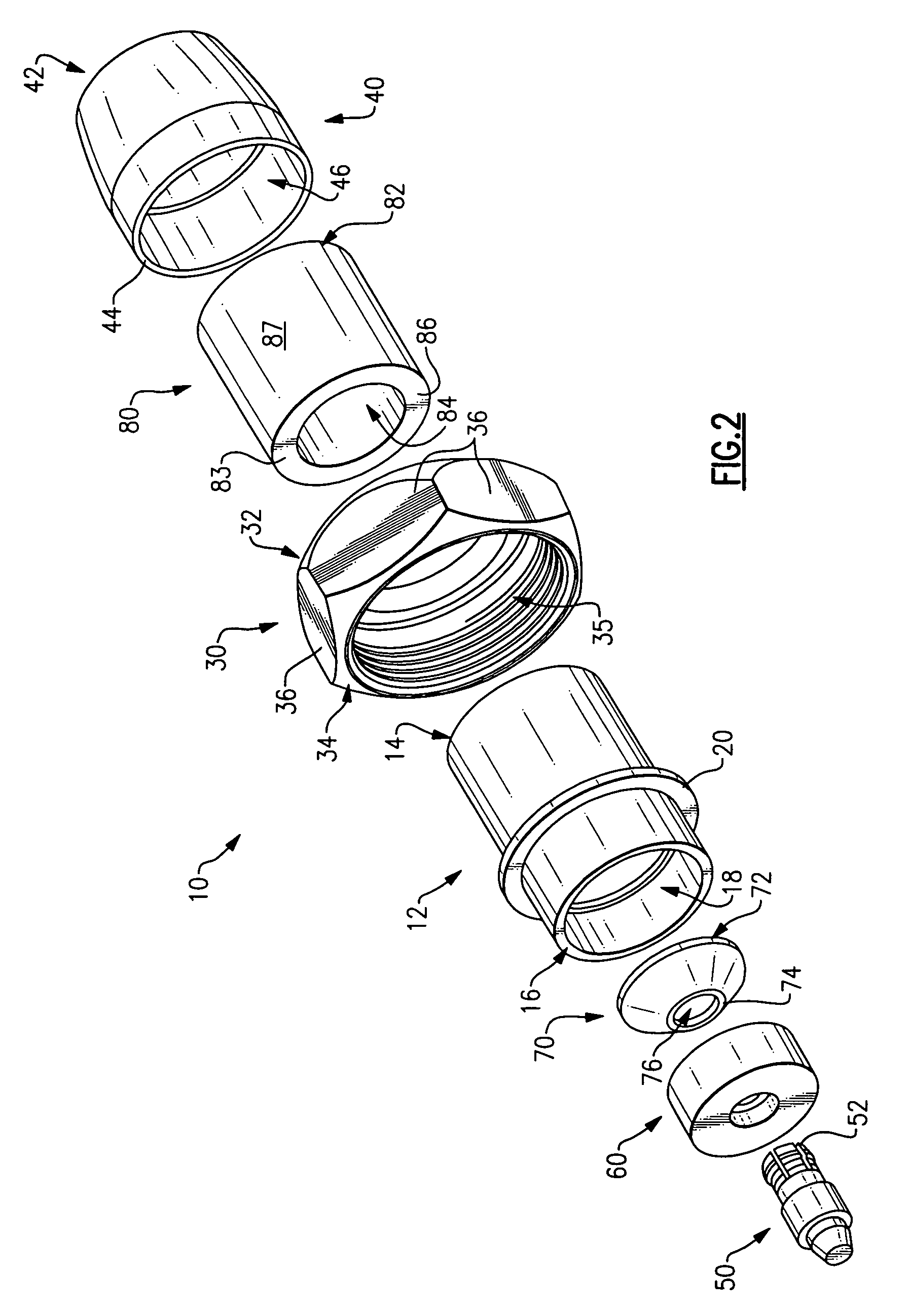
Compact compression connector with flexible clamp for corrugated coaxial cable
InactiveUS7311554B1Low stress engagementHigh precisionElectrically conductive connectionsTwo pole connectionsEngineeringLow stress
A compression connector for the end of a segment of corrugated coaxial cable is provided wherein the compression connector includes a clamp that is both flexible and conductive so as to enable a highly precise and secure, yet low stress engagement of the connector to the segment of corrugated coaxial cable.
Owner:JOHN MEZZALINGUA ASSOC INC
Strong authentication token generating one-time passwords and signatures upon server credential verification
ActiveUS8302167B2Transfer size reductionHighly secureDigital data processing detailsMultiple digital computer combinationsInternet privacyTransaction data
The invention defines a strong authentication token that remedies a vulnerability to a certain type of social engineering attacks, by authenticating the server or messages purporting to come from the server prior to generating a one-time password or transaction signature; and, in the case of the generation of a transaction signature, signing not only transaction values but also transaction context information and, prior to generating said transaction signature, presenting said transaction values and transaction context information to the user for the user to review and approve using trustworthy output and input means. It furthermore offers this authentication and review functionality without sacrificing user convenience or cost efficiency, by judiciously coding the transaction data to be signed, thus reducing the transmission size of information that has to be exchanged over the token's trustworthy interfaces.
Owner:ONESPAN NORTH AMERICA INC
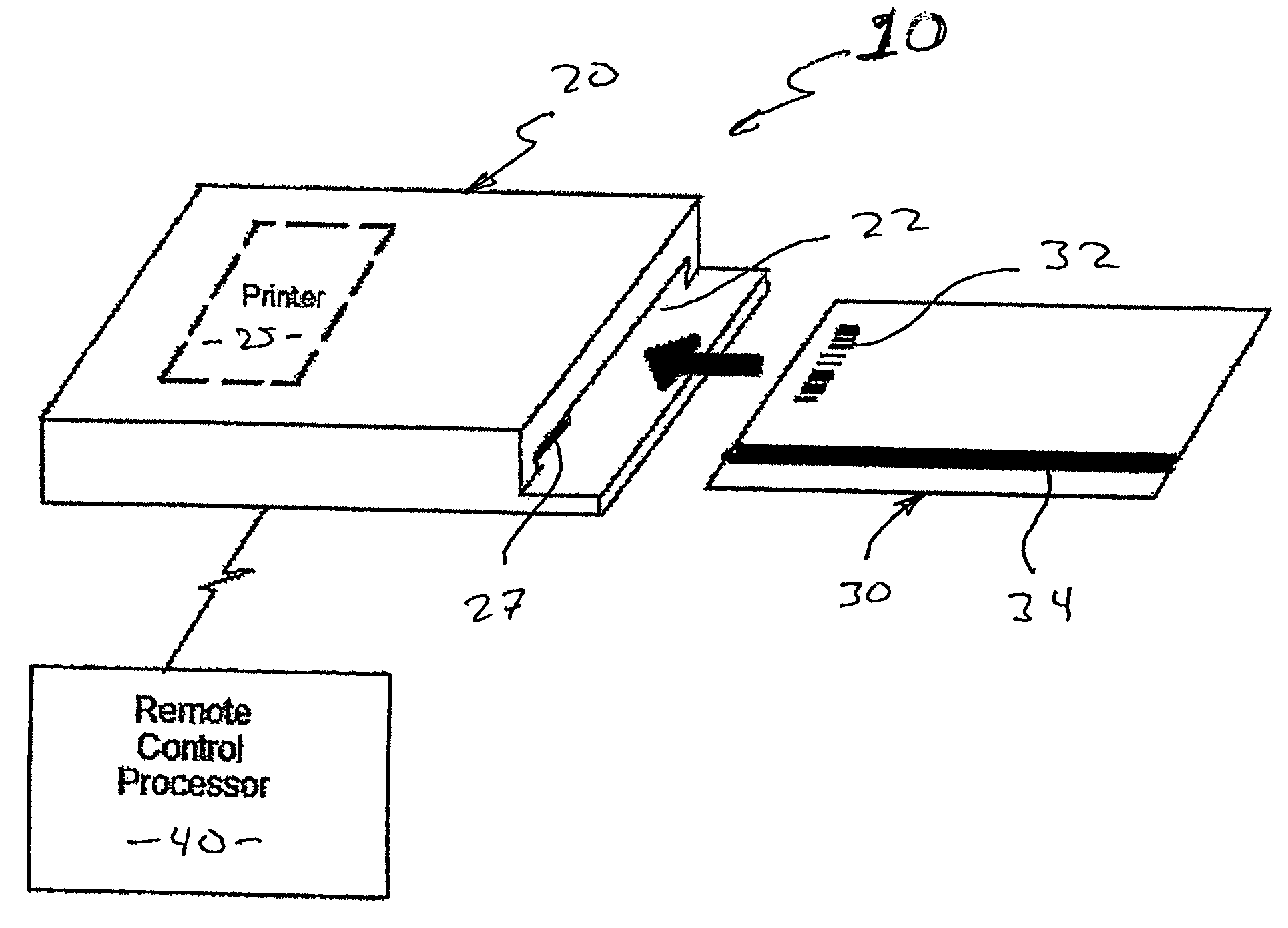
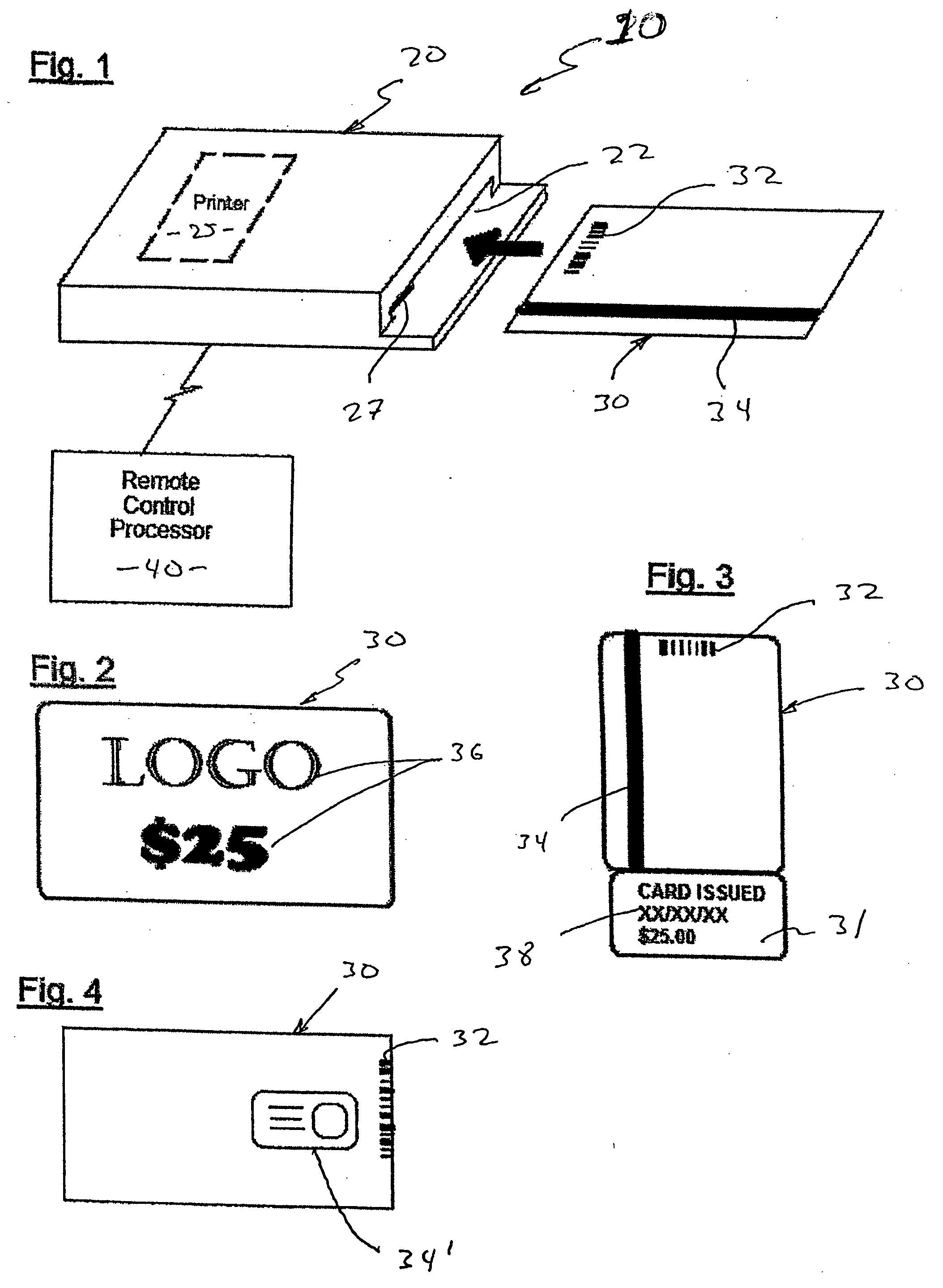
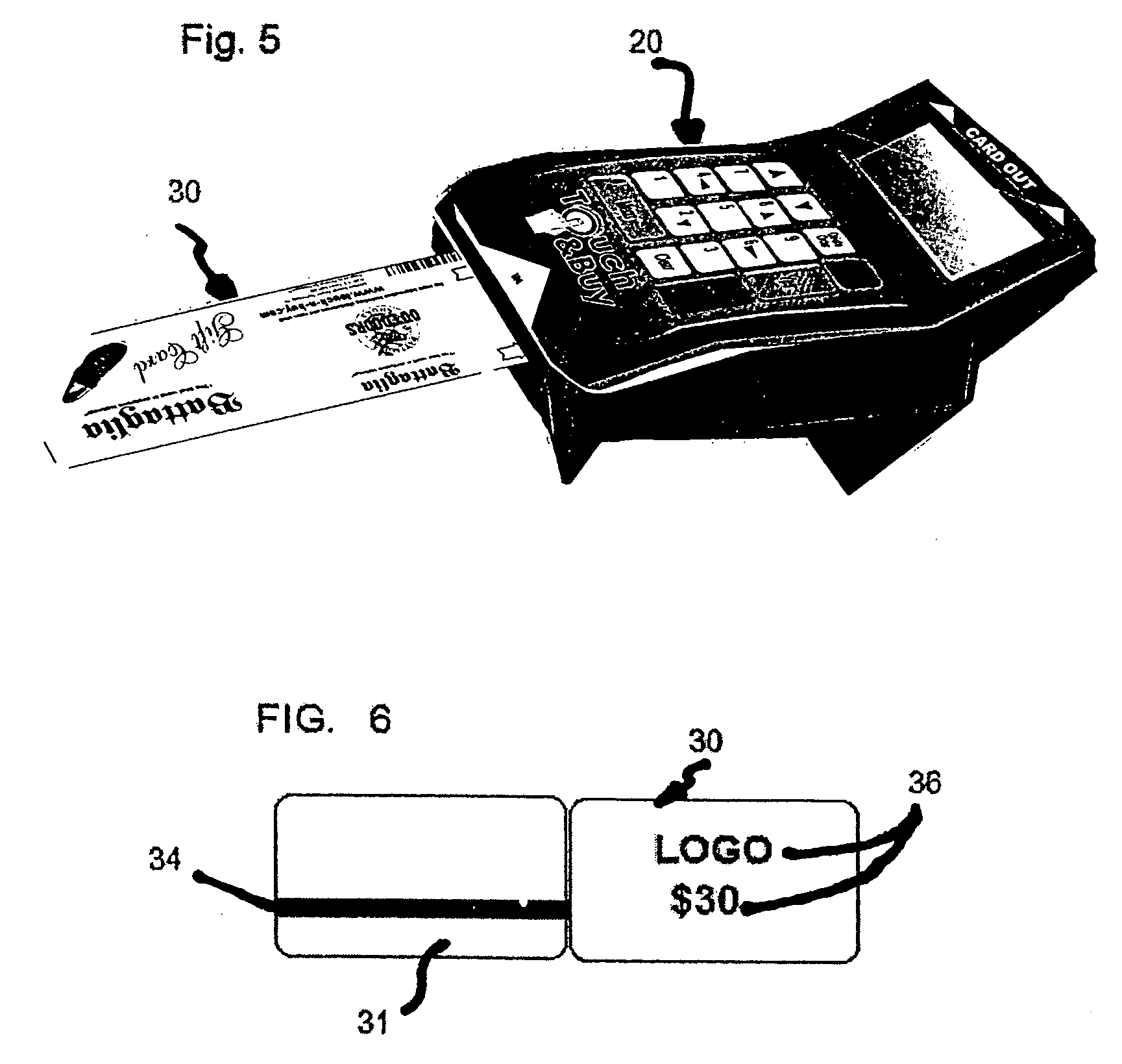
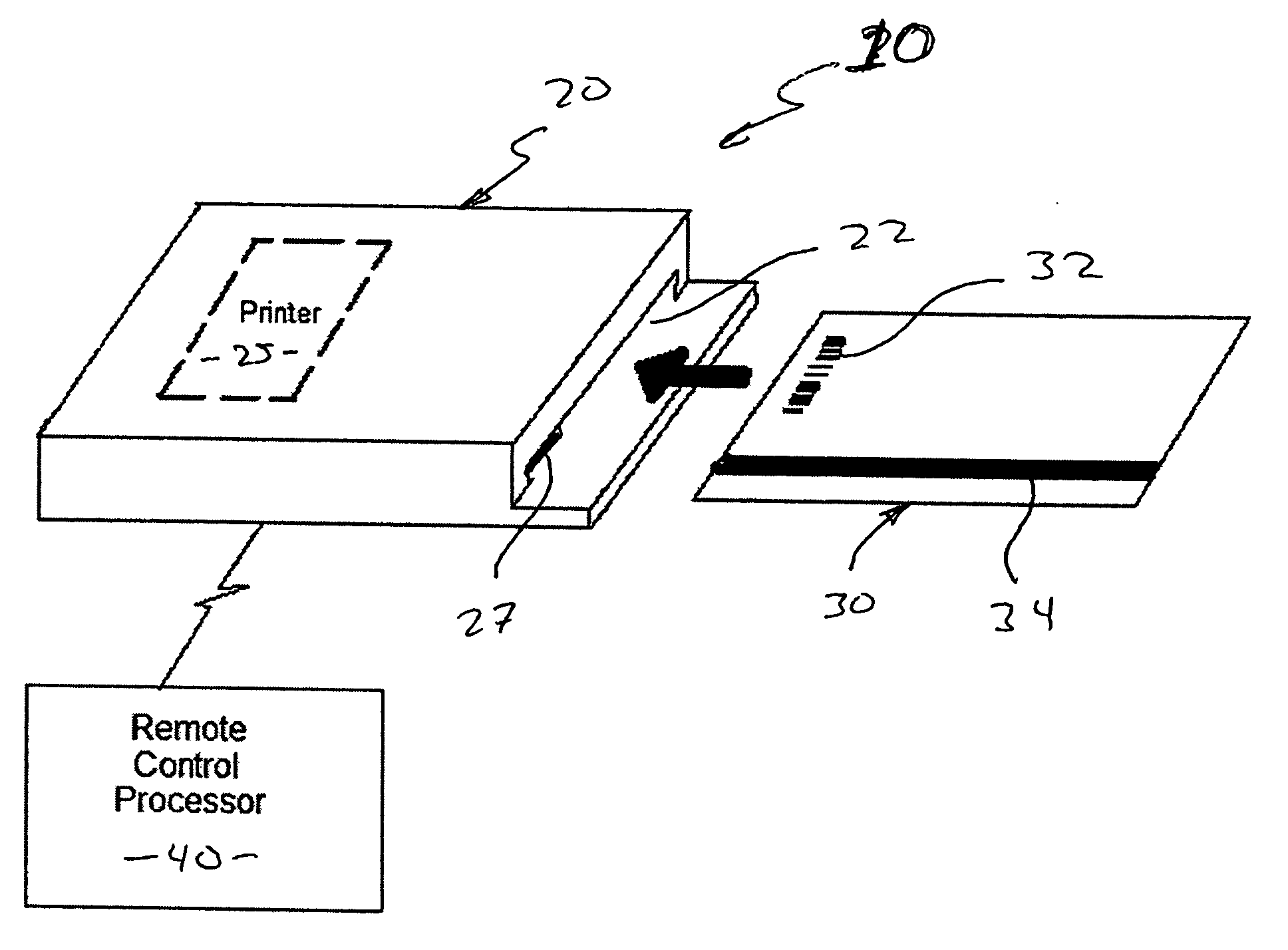
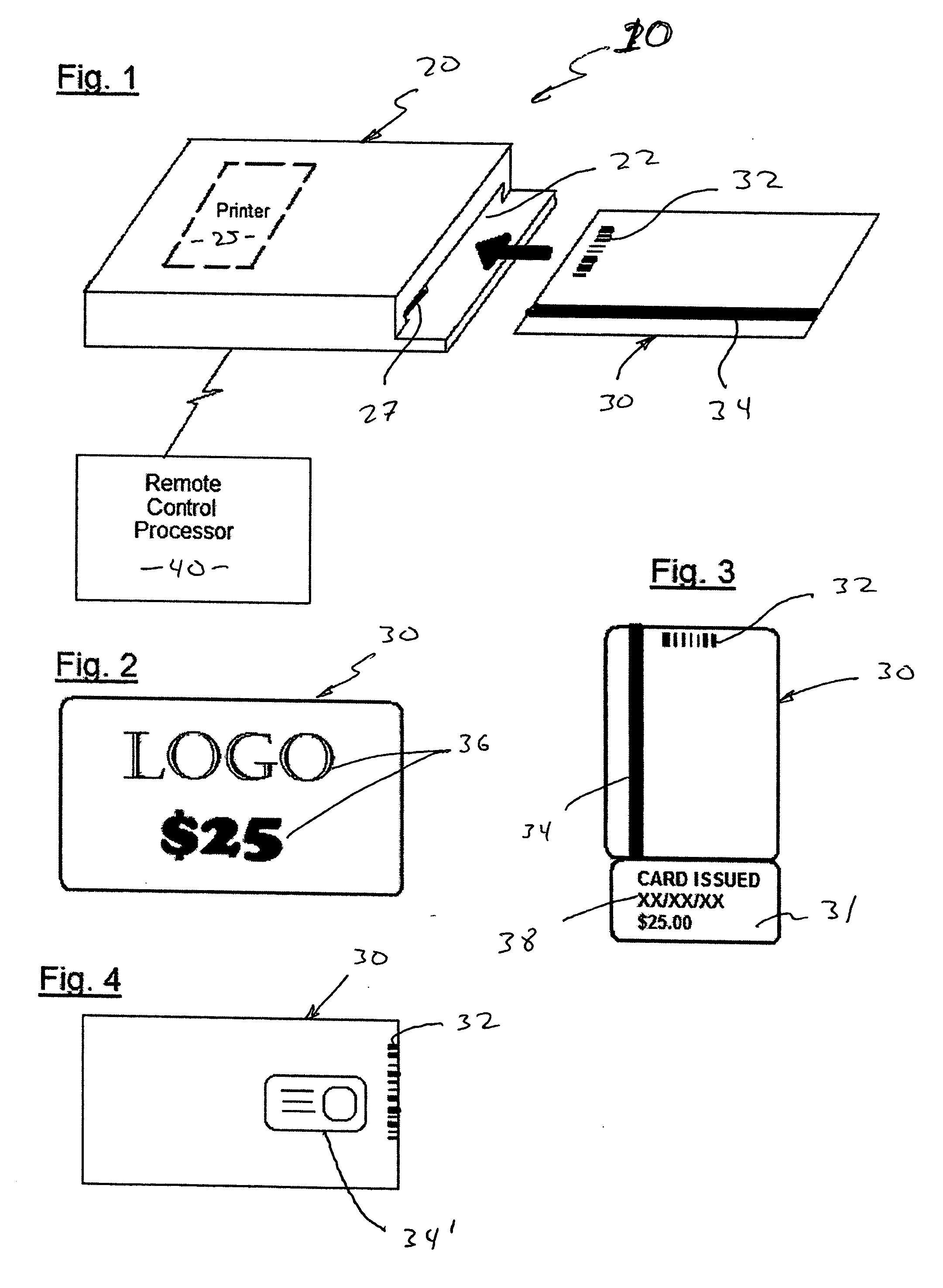
Prepaid card issuing system
InactiveUS20050218216A1Enabling useHighly marketableCo-operative working arrangementsApparatus for meter-controlled dispensingComputer hardwareInformation processing
A prepaid card issuing system that includes a card with identifying indicia associated with a specific entity, such as a store from which products or services can be purchased, and a value such as a financial denomination, disposed thereon. An issuing terminal is also provided and is structured to receive the card, identify the security identifier, and communicate with a remote, control processor that receives the security identifier and defines and communicates to the issuing terminal usage information associated with the security identifier. The issuing terminal is further structured to dispose account information on the card in accordance with said the information so as to permit use of the card for the purchase of products or services, and to retain the card therein during detection of the security identifier, disposition of the account information on the card and printing of an issuance confirmation on the card.
Owner:ARIAS LUS
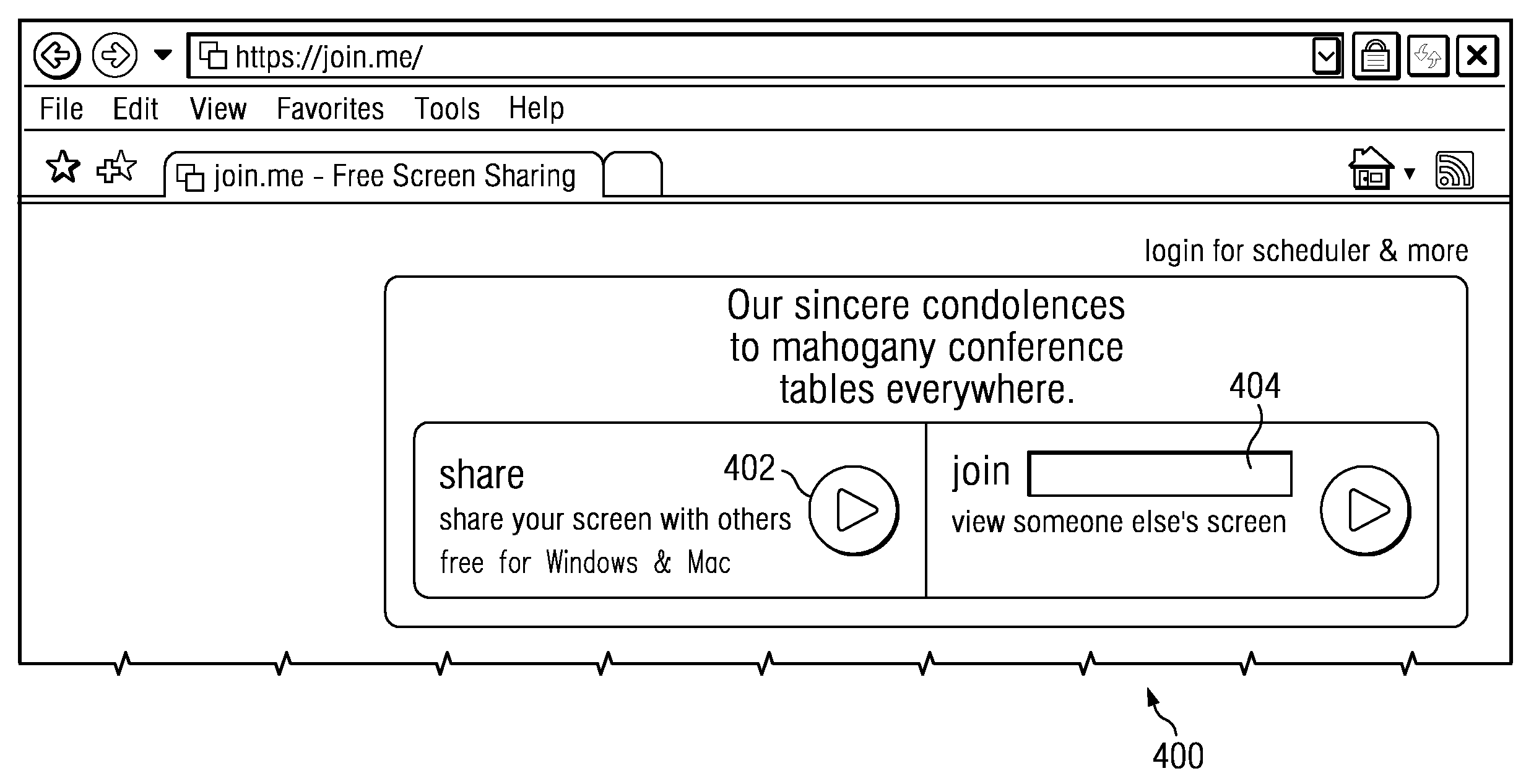
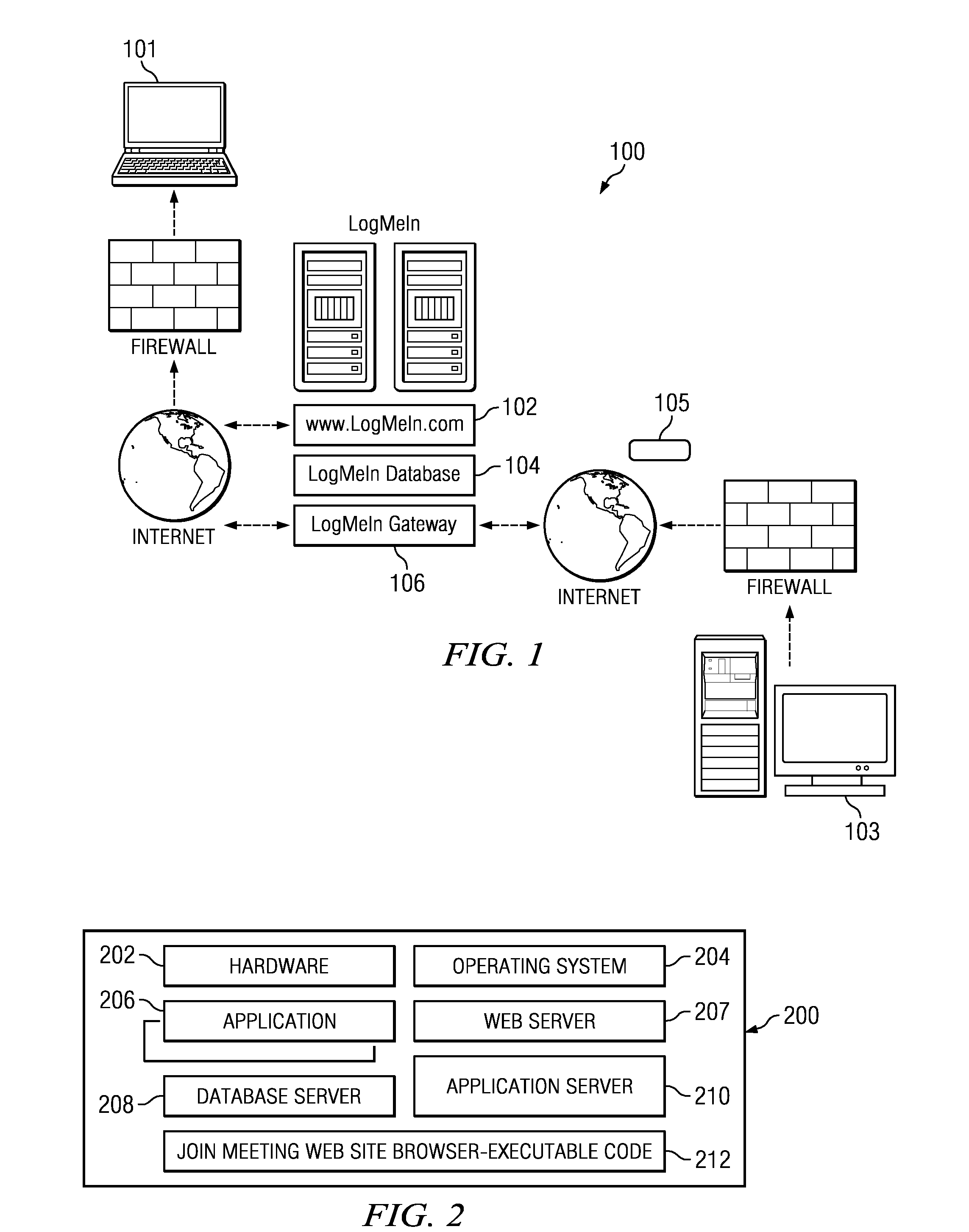
Network-based quick connect meeting service
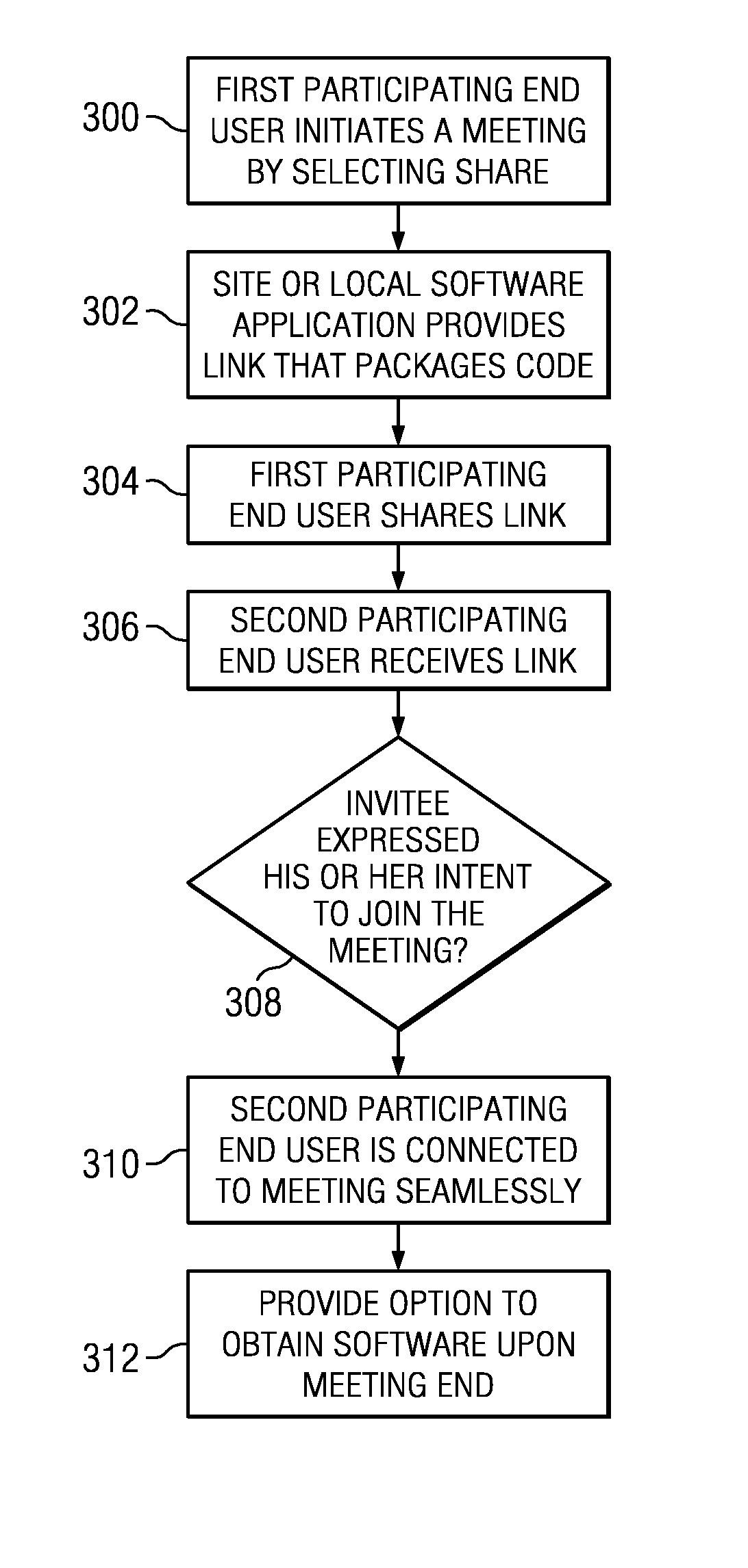
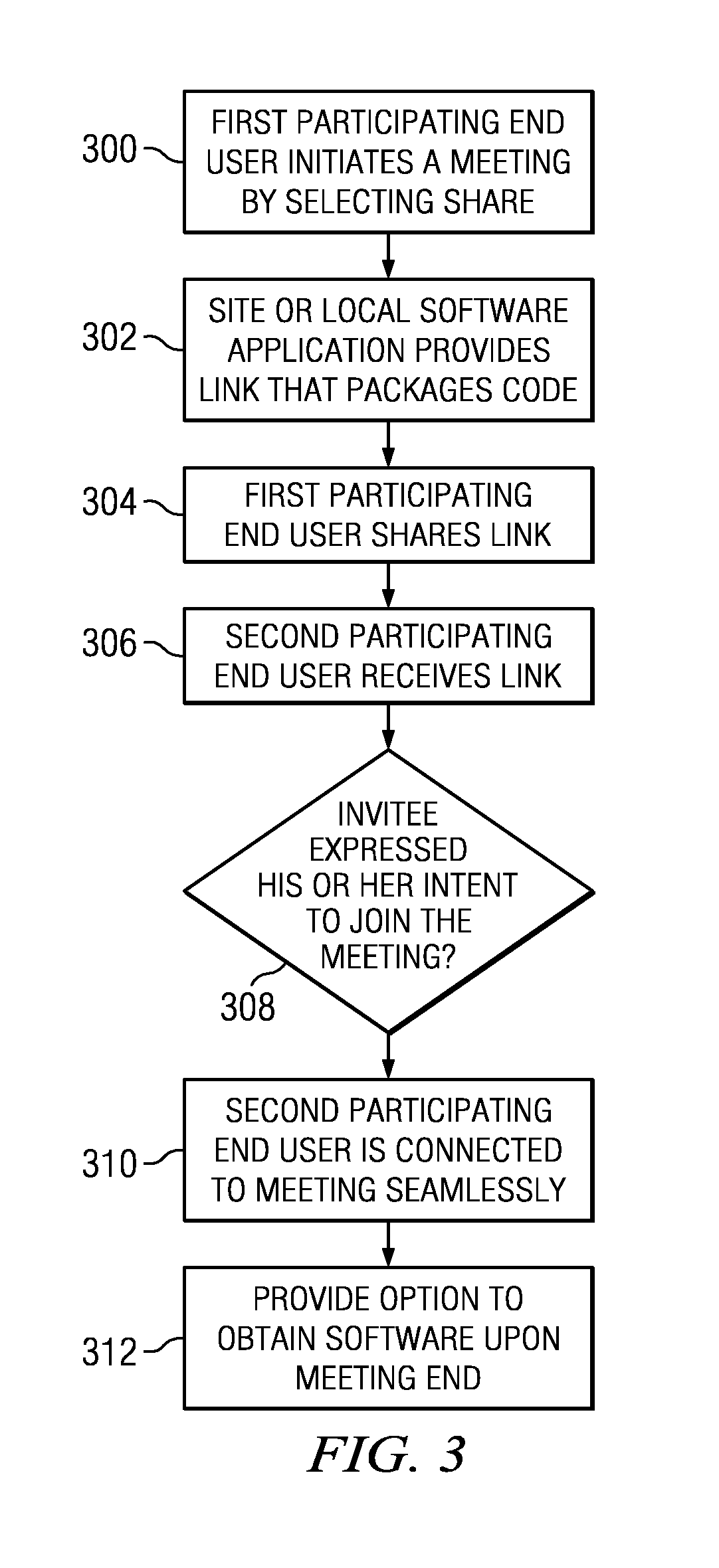
ActiveUS20120117156A1Easy to useHighly-available, scalable “joinData processing applicationsWeb data indexingWi-FiWeb site
A network-accessible service enables participating end users to collaborate with one another over a network. End users have computing devices (e.g., computers, mobile phone, tablet devices, or the like) that include hardware and software to enable the device to access a network, such as the public Internet, a Wi-Fi network connected to the Internet, a 3G or higher wireless network connected to the Internet, a private network, or the like. The network-accessible service provides a publicly-available site (such as a Web site) or a local software application from which a first participating end user initiates a “meeting,” e.g., by selecting a “share” button. In response, the site or software application provides an HTTP link that includes a “meeting” code, which may be a one-time unique code. The first participating end user then shares the link with whomever he or she desires to collaborate. Upon receiving the link (e.g., by e-mail, instant message, SMS, MMS, orally, or the like), a second participating end user joins the meeting “on-the-fly” by simply selecting the link or navigating to the site and entering the “meeting” code (in a “join” field). The service connects the second participating end user to the meeting immediately and without requiring any registration, software download, or the like.
Owner:GOTO GRP INC
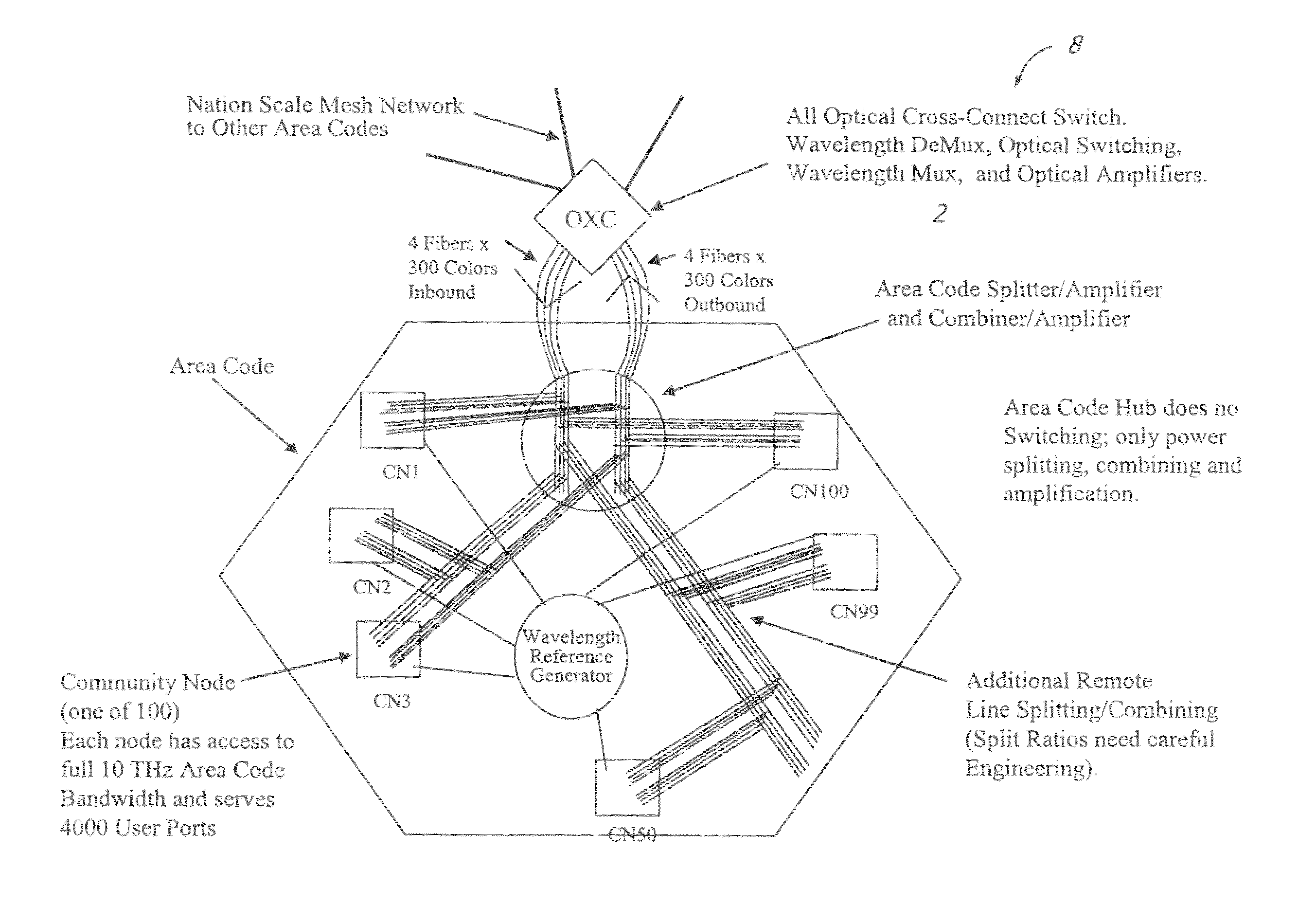
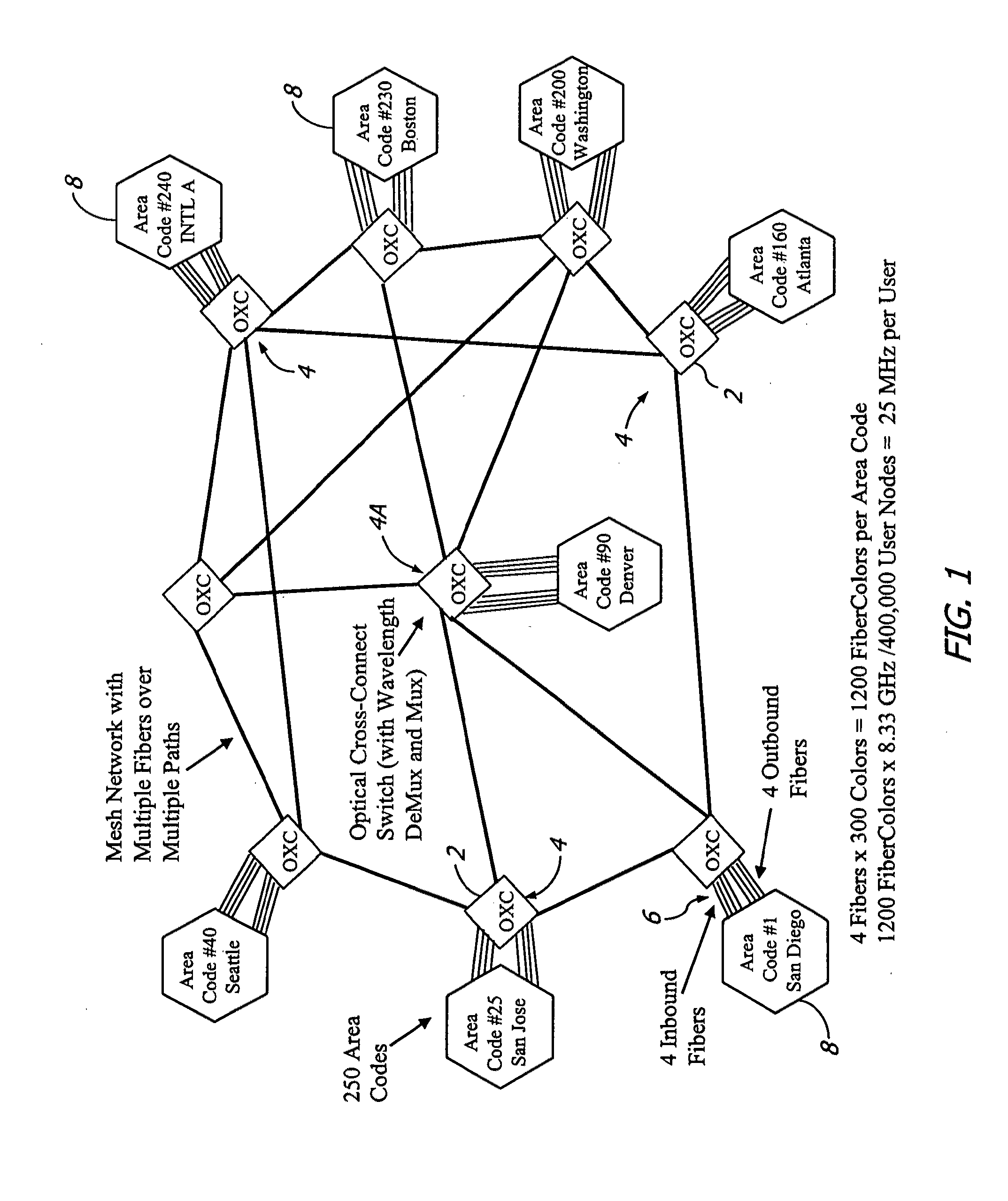
Optically switched communication network
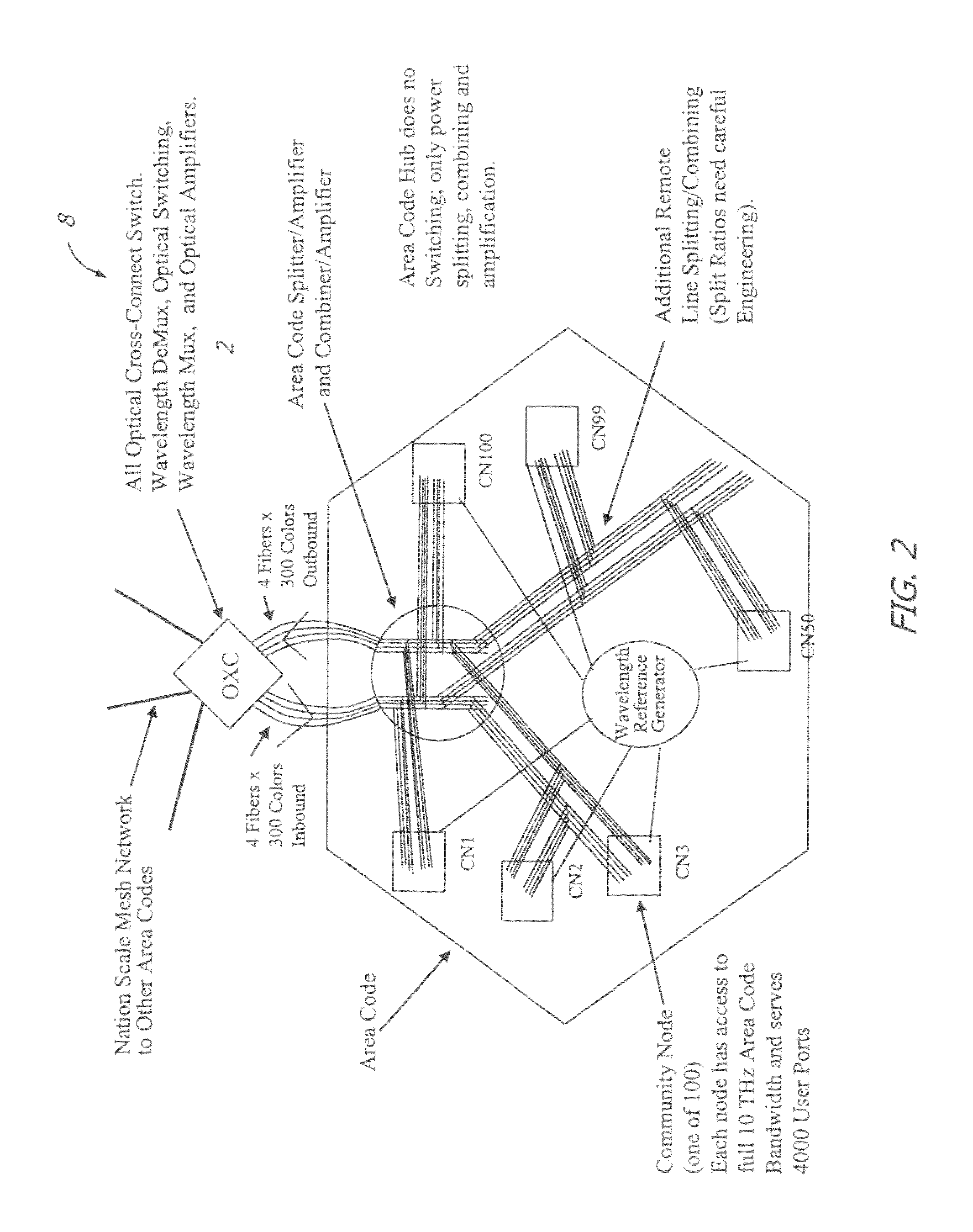
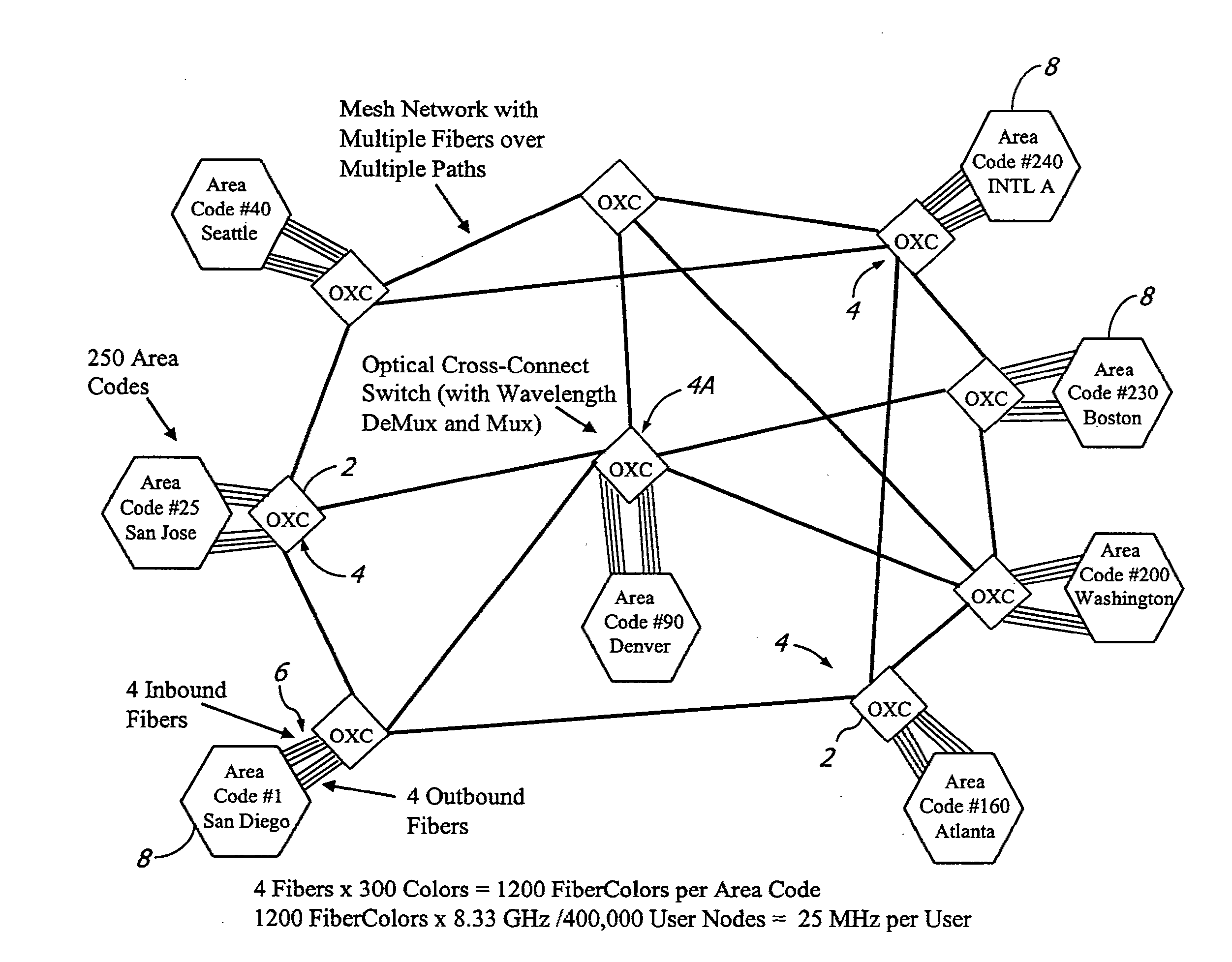
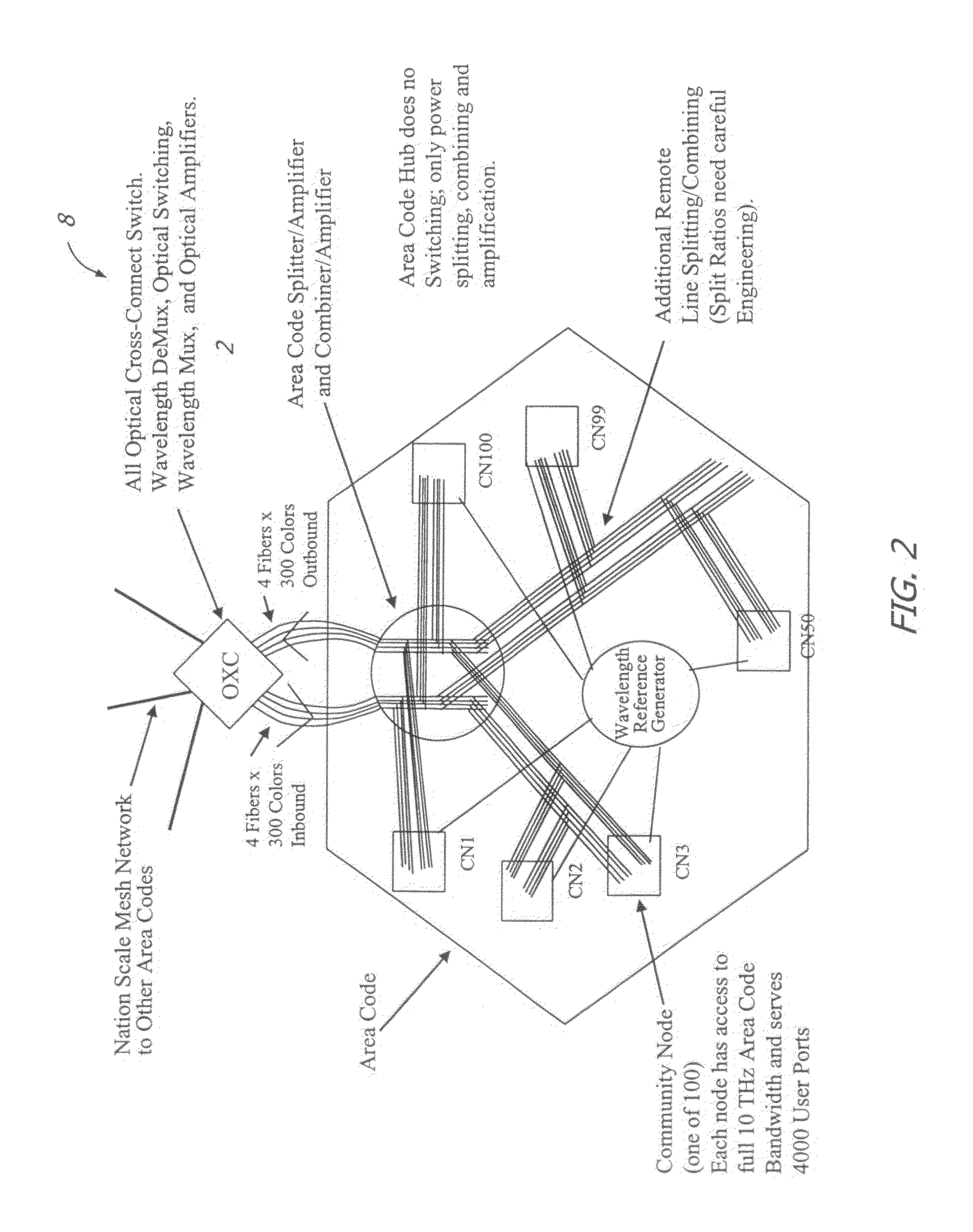
InactiveUS8401385B2Improve scalabilityHighly secureMultiplex system selection arrangementsWavelength-division multiplex systemsTelecommunications linkCarrier signal
A large communication network suitable for nationwide or worldwide utilization. The present invention overthrows the conventional packet switching technologies with an all-optical network. The invention uses tunable laser sources to generate large number of highly stable narrow-band optical signals, each serving as a communication channel. With packet processing replaced by all-optical channels, the network become highly secure and scalable while harnessing the virtually unlimited capacity of fiber-optic. A large number of nodes (called area code nodes) are connected with all-fiber-optic links with all-optical switches. A routing algorithm provides one or more communication links from each area code node to every other area code node so that information never has to change carrier wavelength as it travels the network. Each area code node contains circuits that are provided to connect individual users to the network.
Owner:TREX ENTERPRISES CORP
Secure diamond smart cards and exchange systems therefor
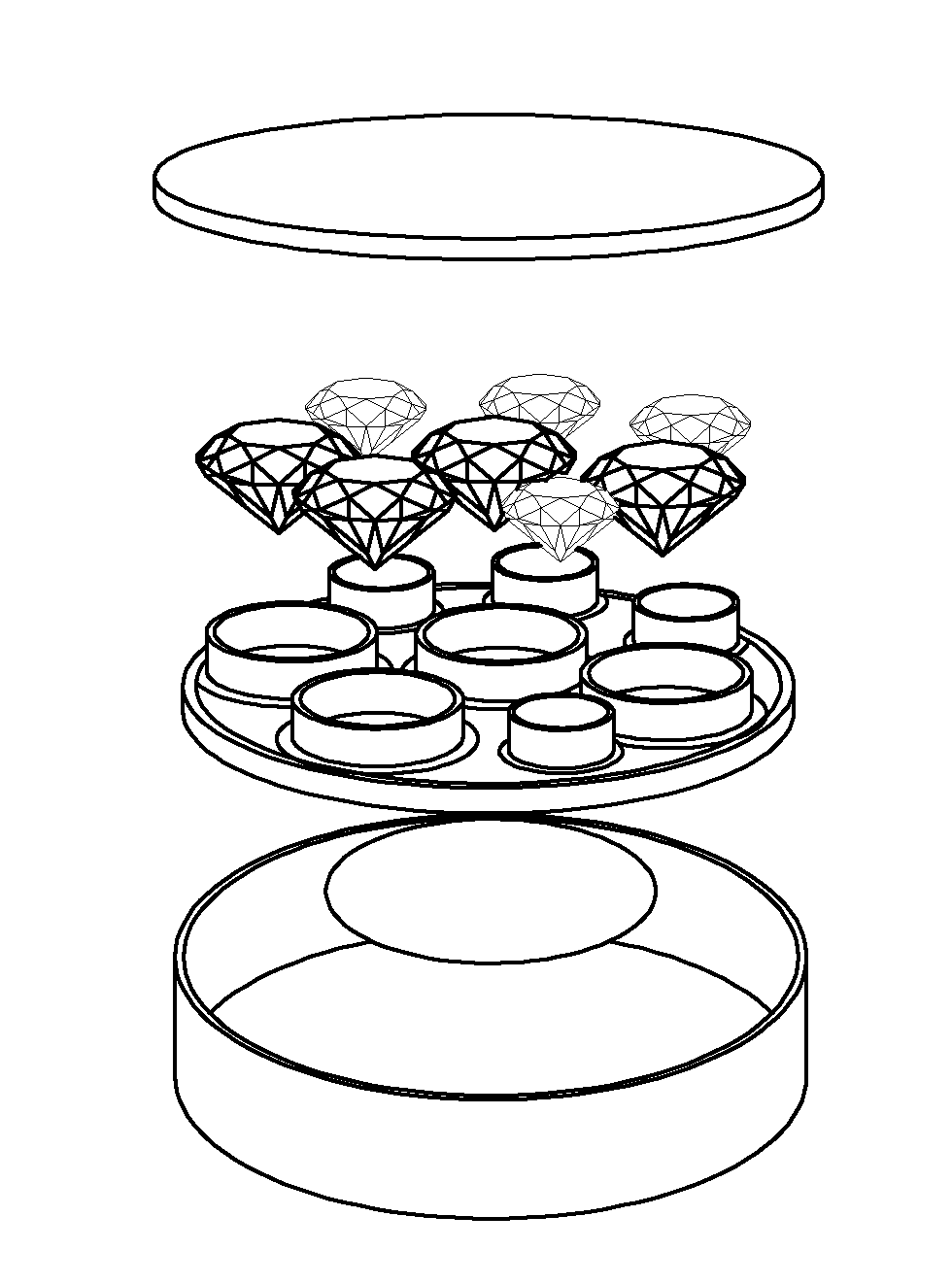
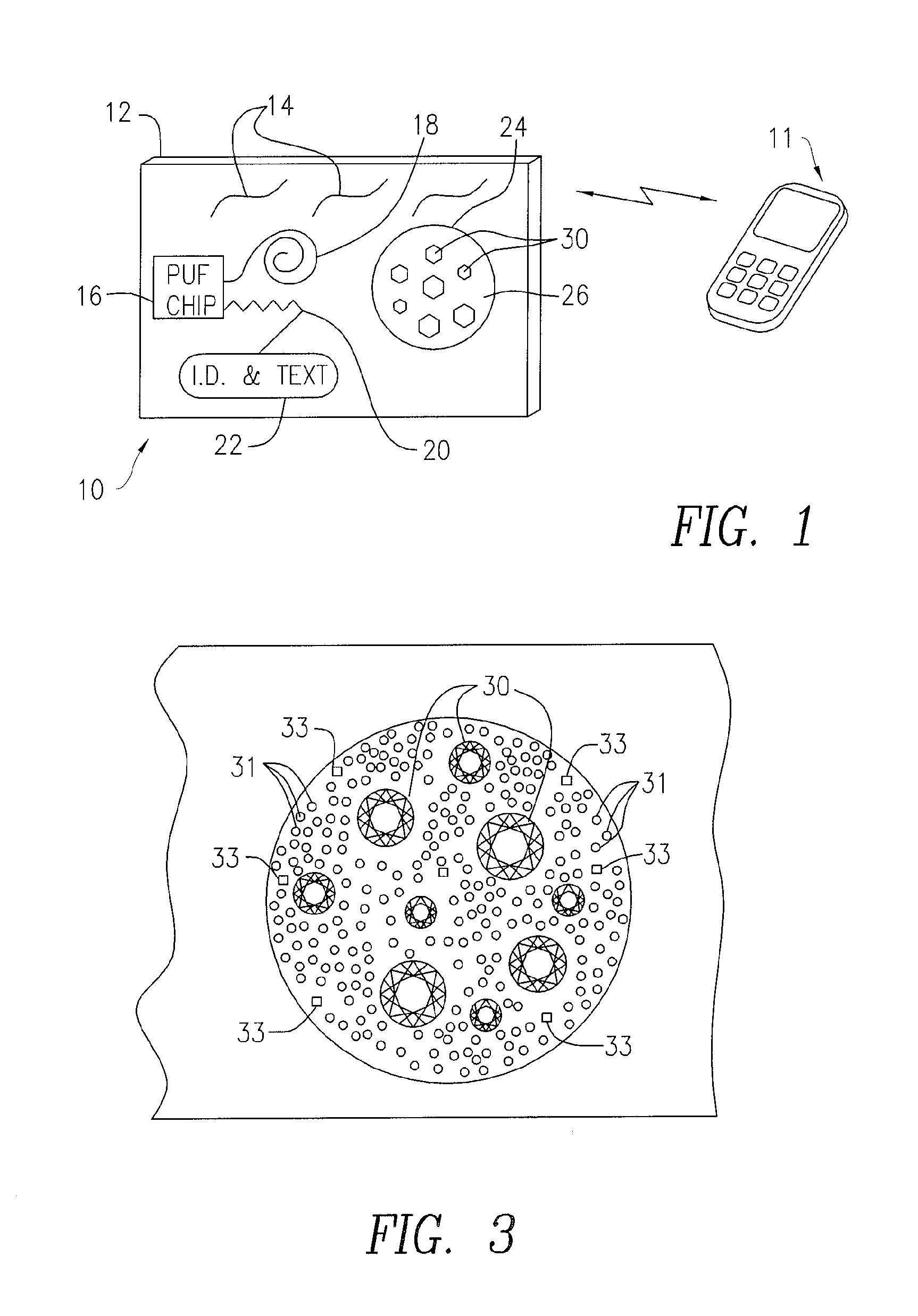
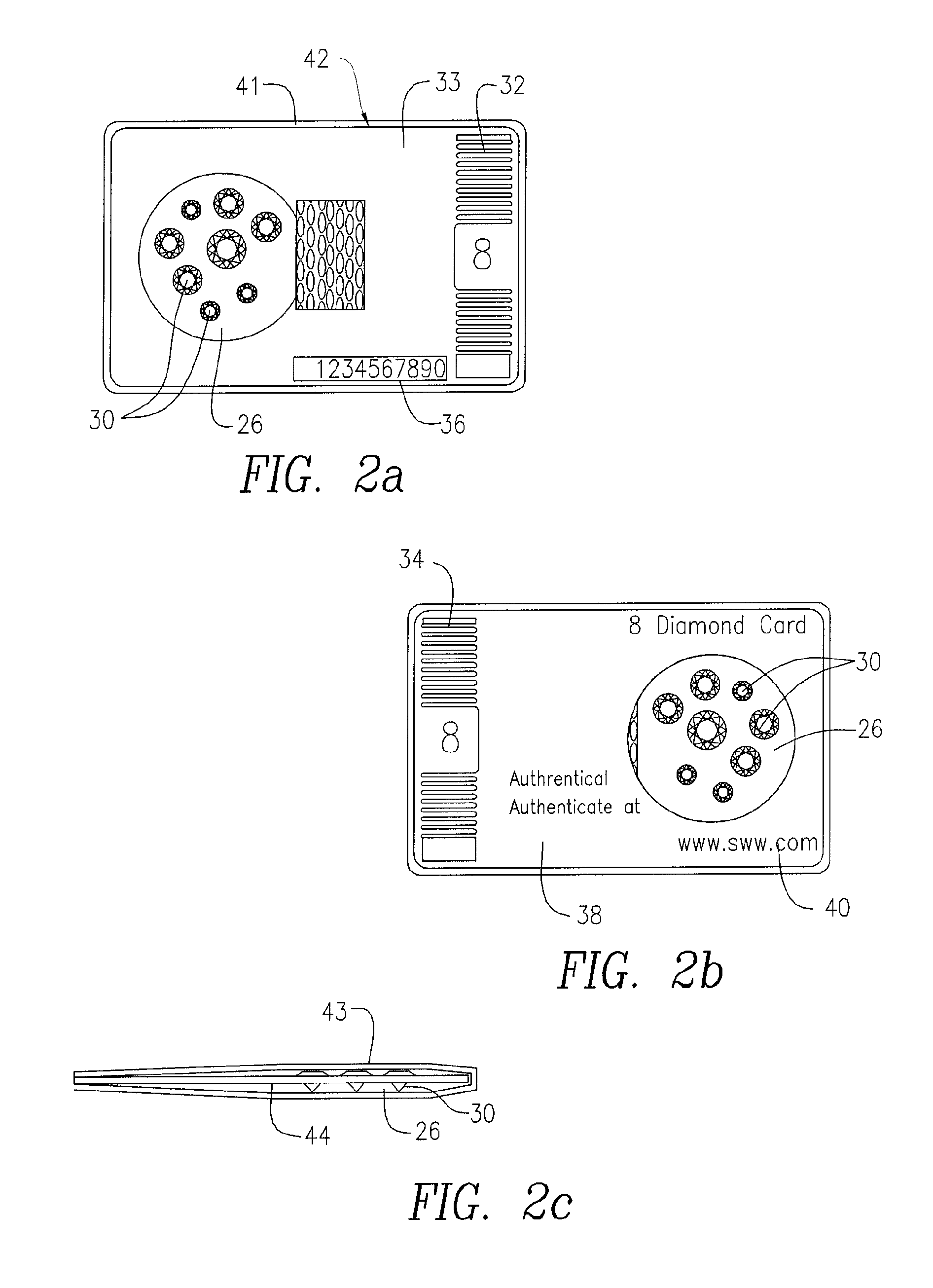
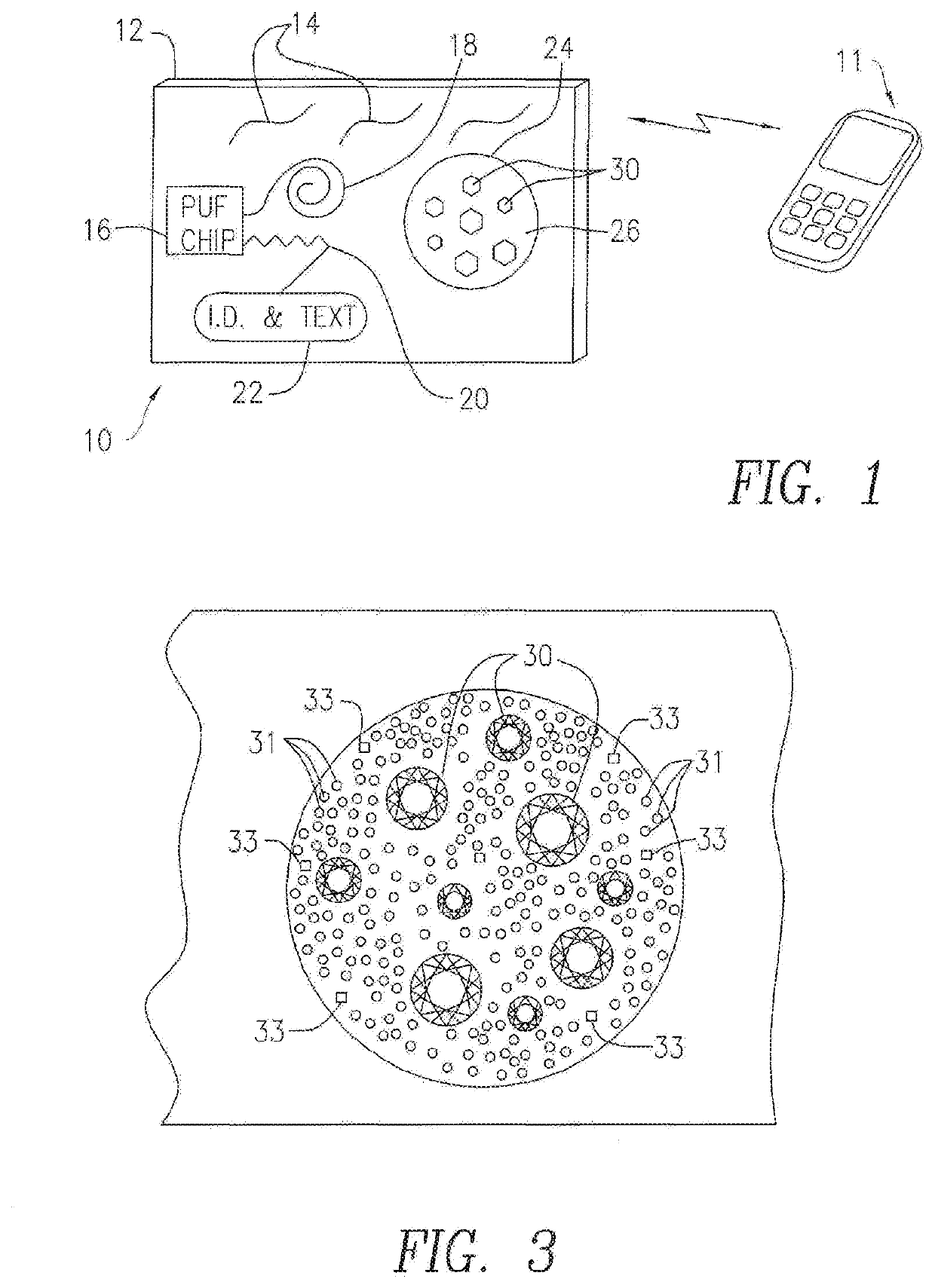
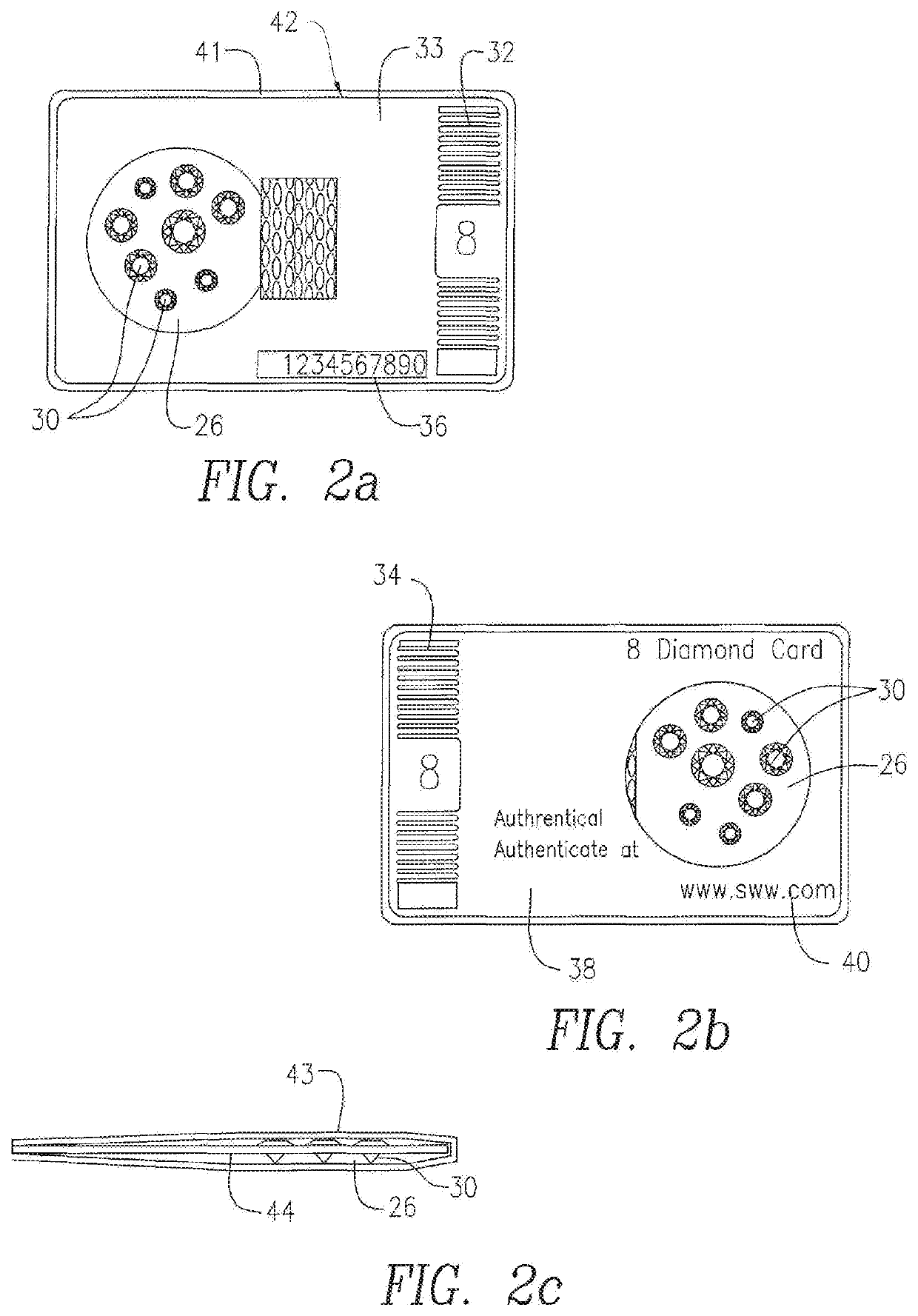
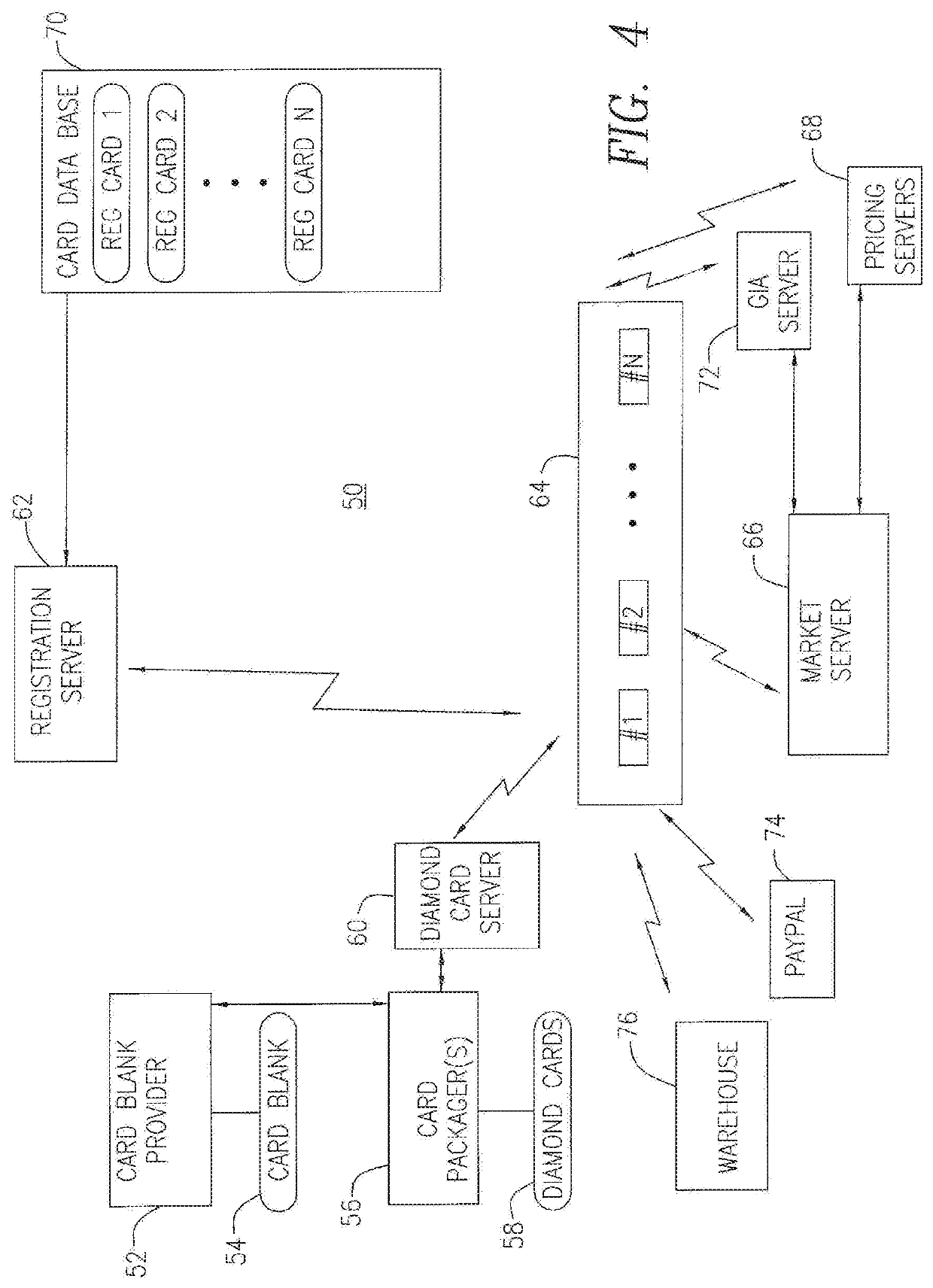
InactiveUS20150223580A1Improve reliabilityHighly secureDigital data authenticationBuying/selling/leasing transactionsCredit cardSmart card
A tamperproof diamond package comprises a package body; at least one chip embedded in the package body and at least one antenna configured to enable communication with the chip; anti-counterfeiting visual impressions on the package body; a diamond pouch formed at a predetermined section within the package body; andone or more diamonds located inside the diamond pouch and an outer covering encasing the package body and configured to reveal any tampering with the one or more diamonds located in the diamond pouch. The diamond package can be credit card shaped and also contains serial number and website information and be provided in nominal dollar values. An associated diamond exchange system utilizes the diamond packages and provides a registration server which stores unique identifying information that enable interrogating the individual diamond packages and checking their authenticity with the registration server.
Owner:DIAMOND STANDARD INC +1
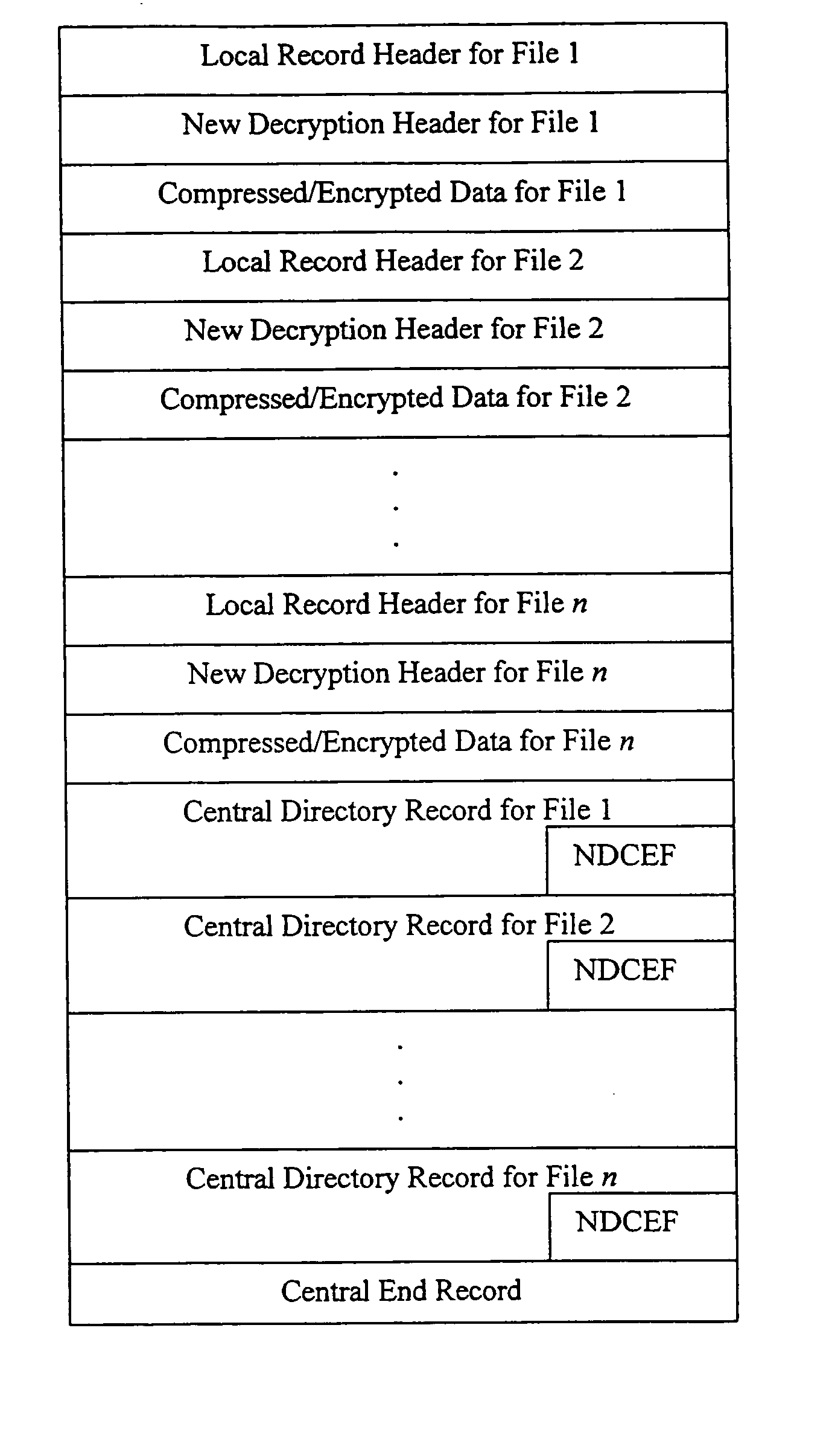
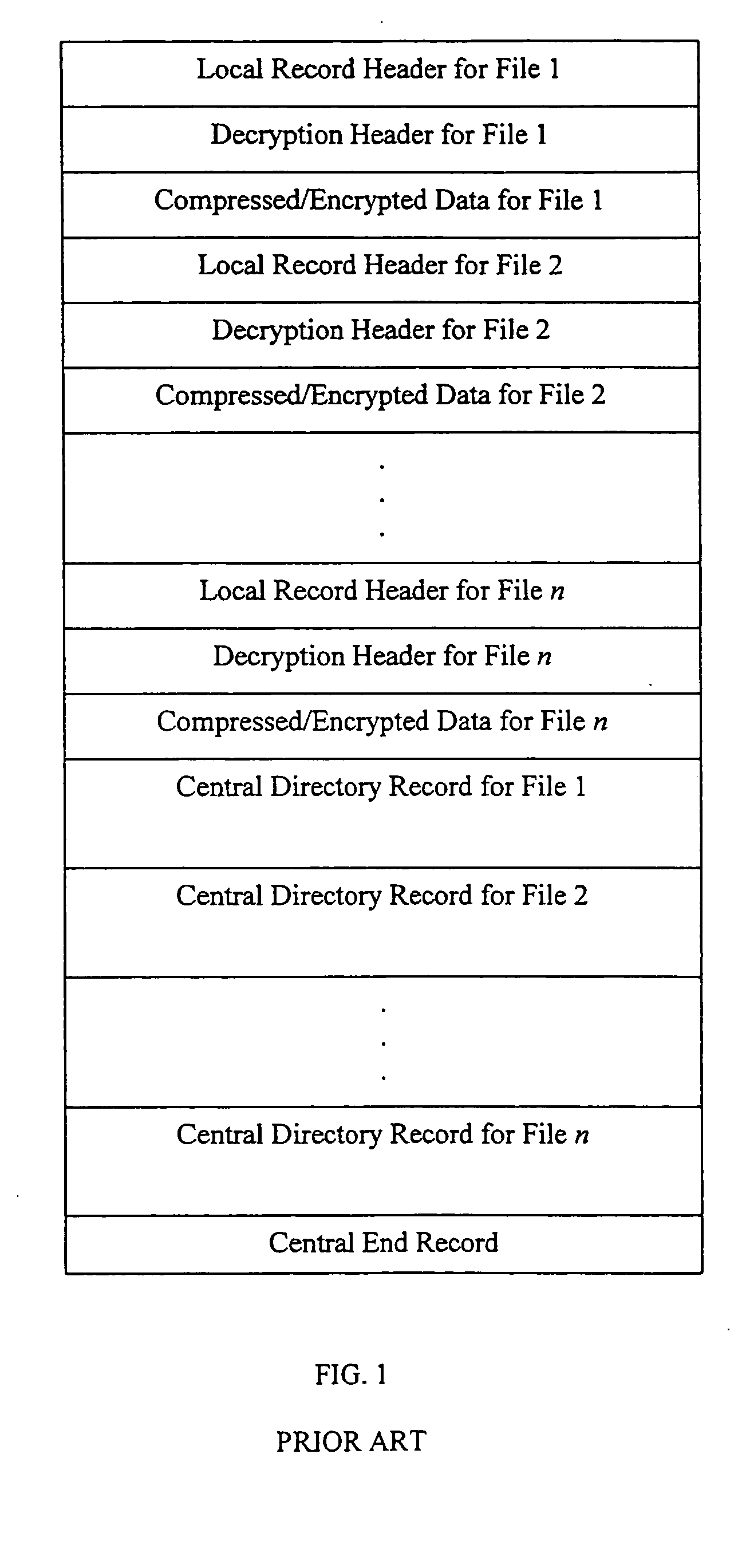
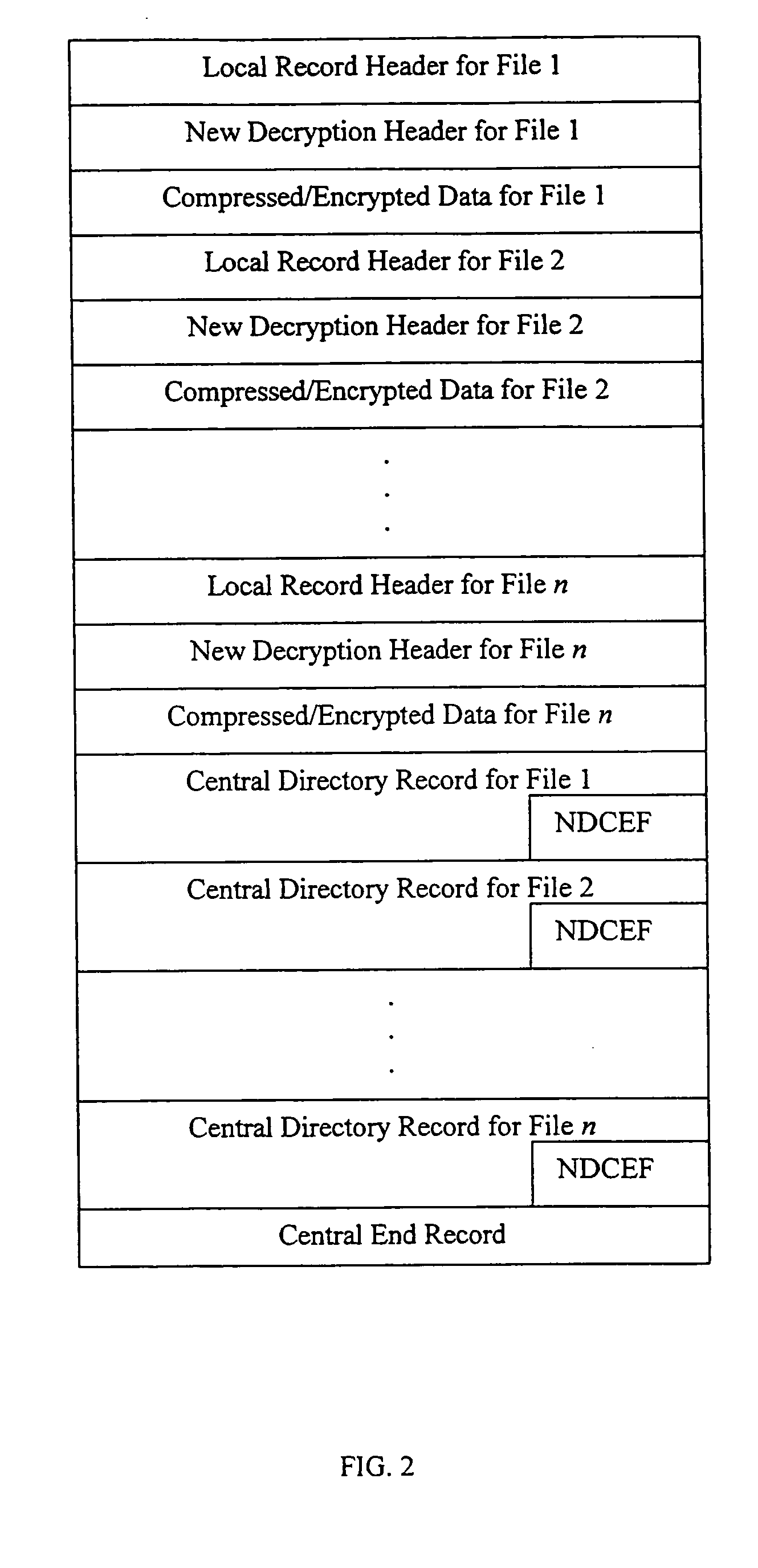
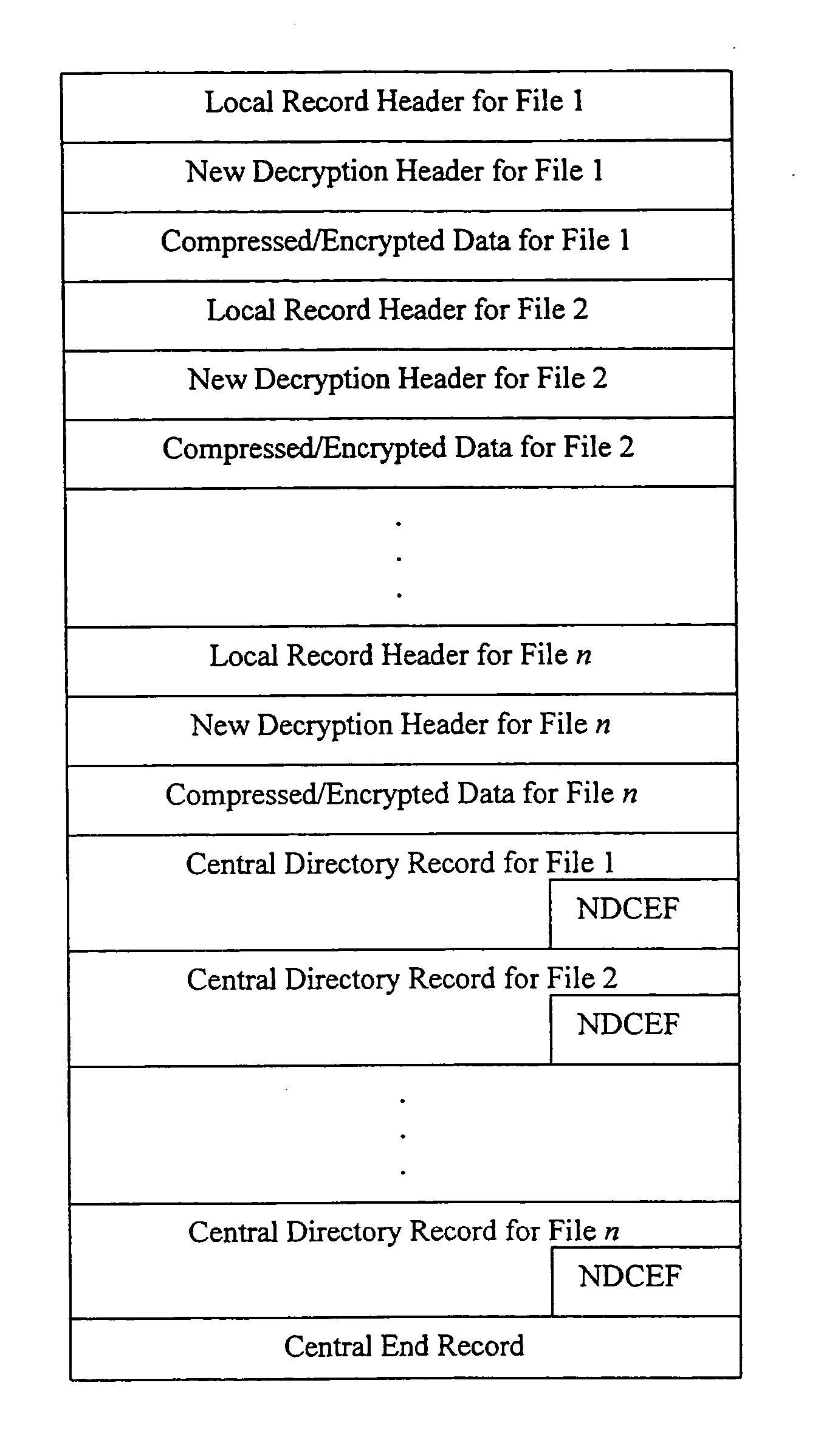
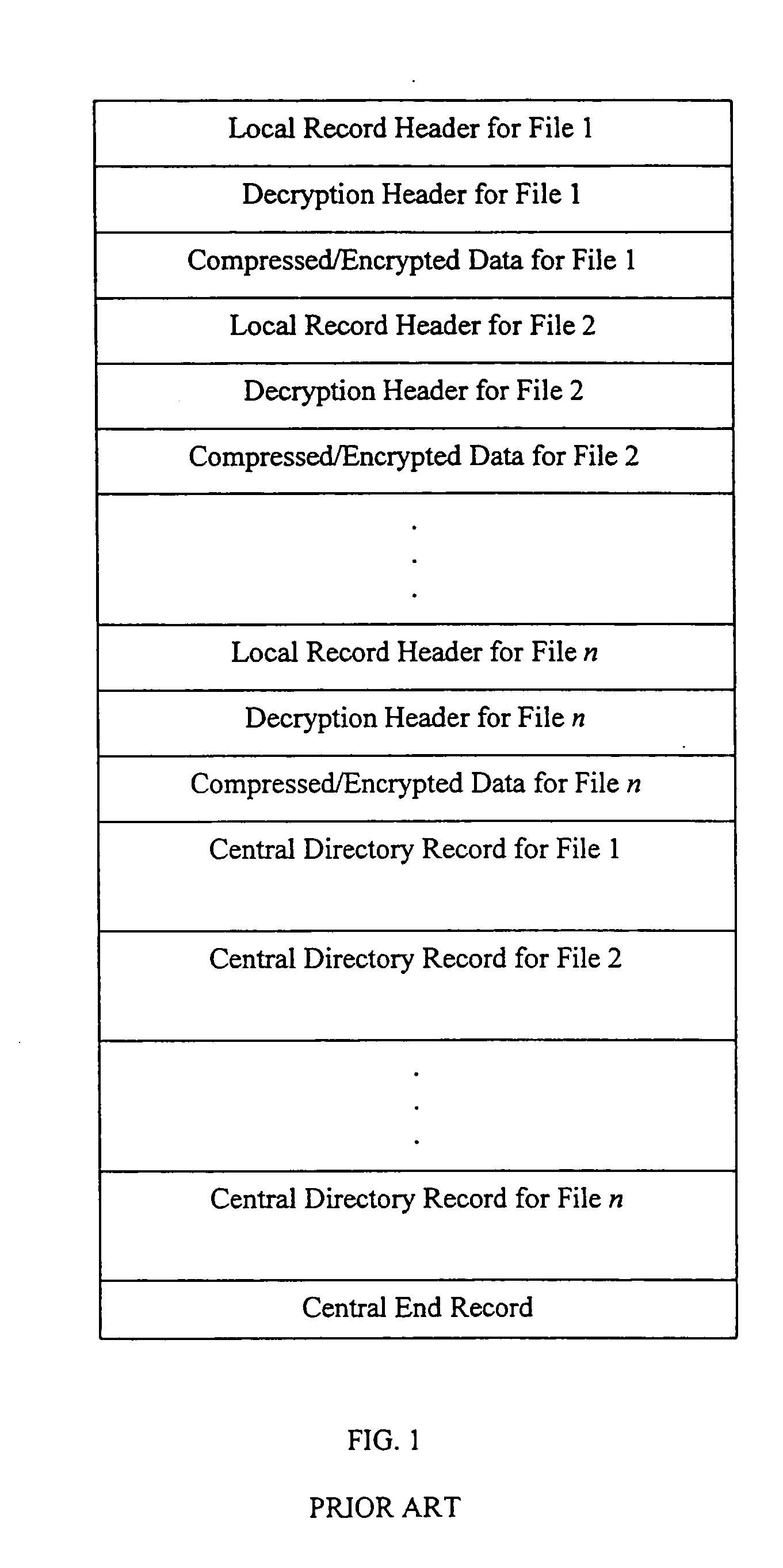
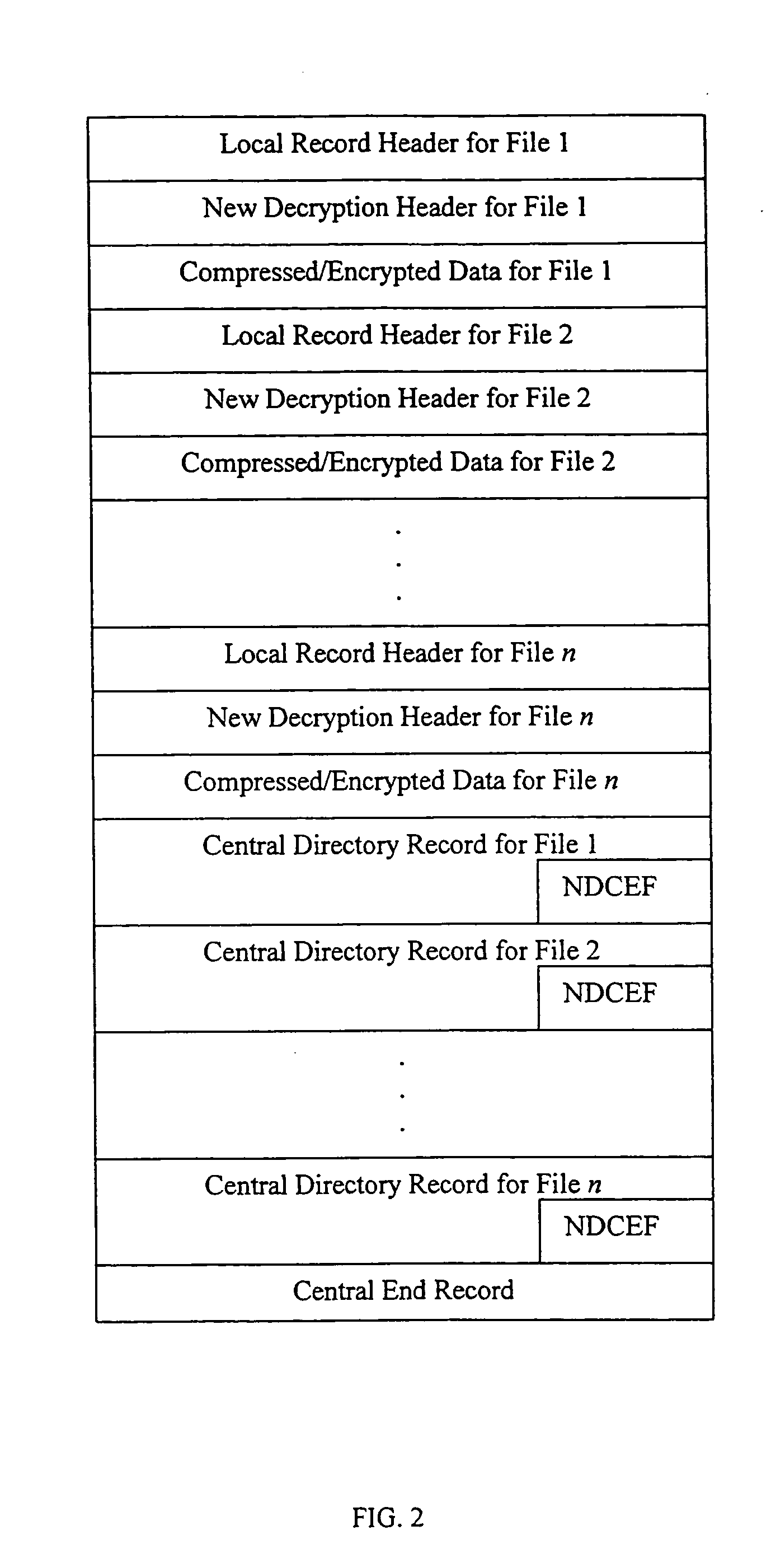
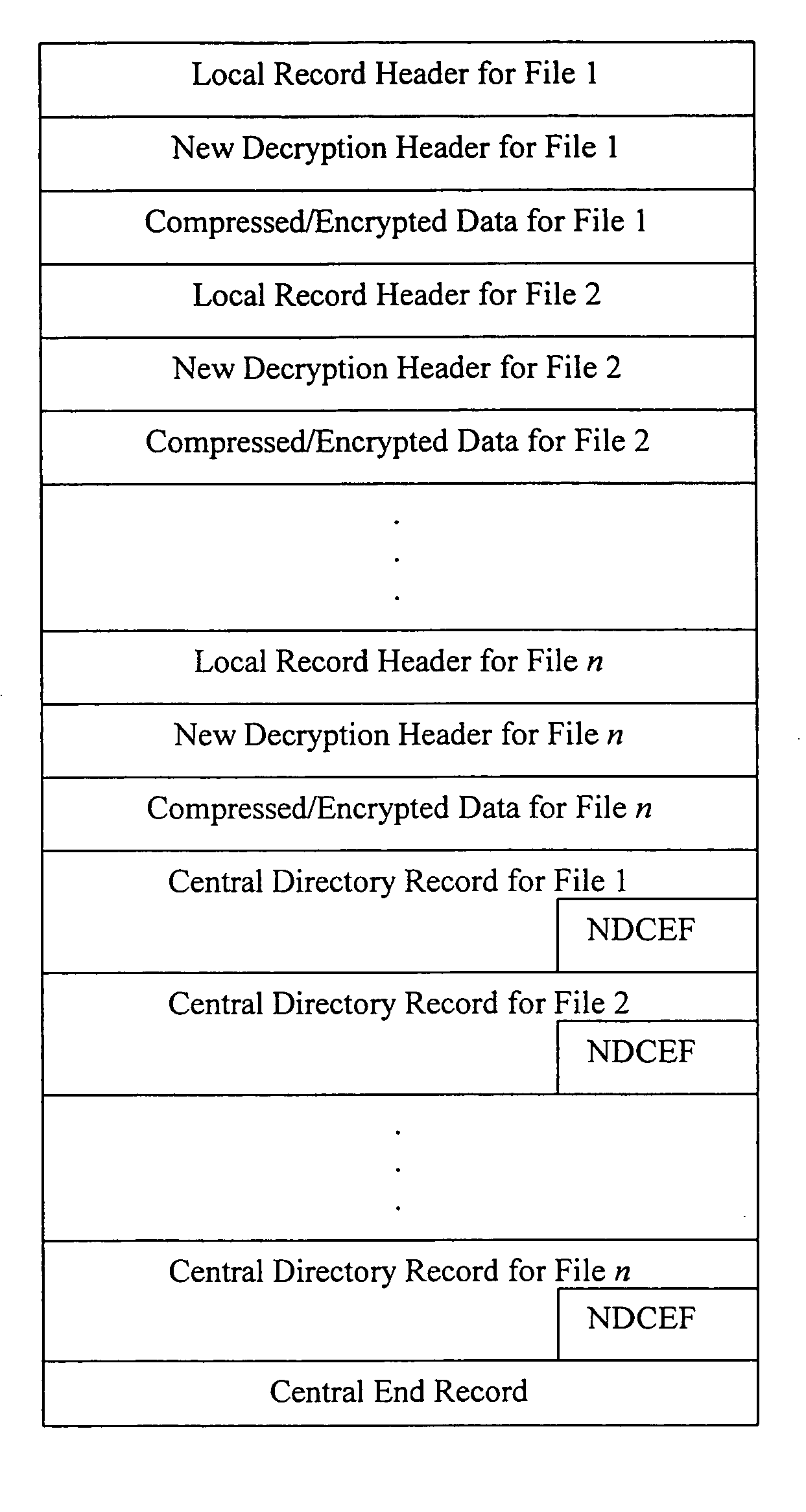
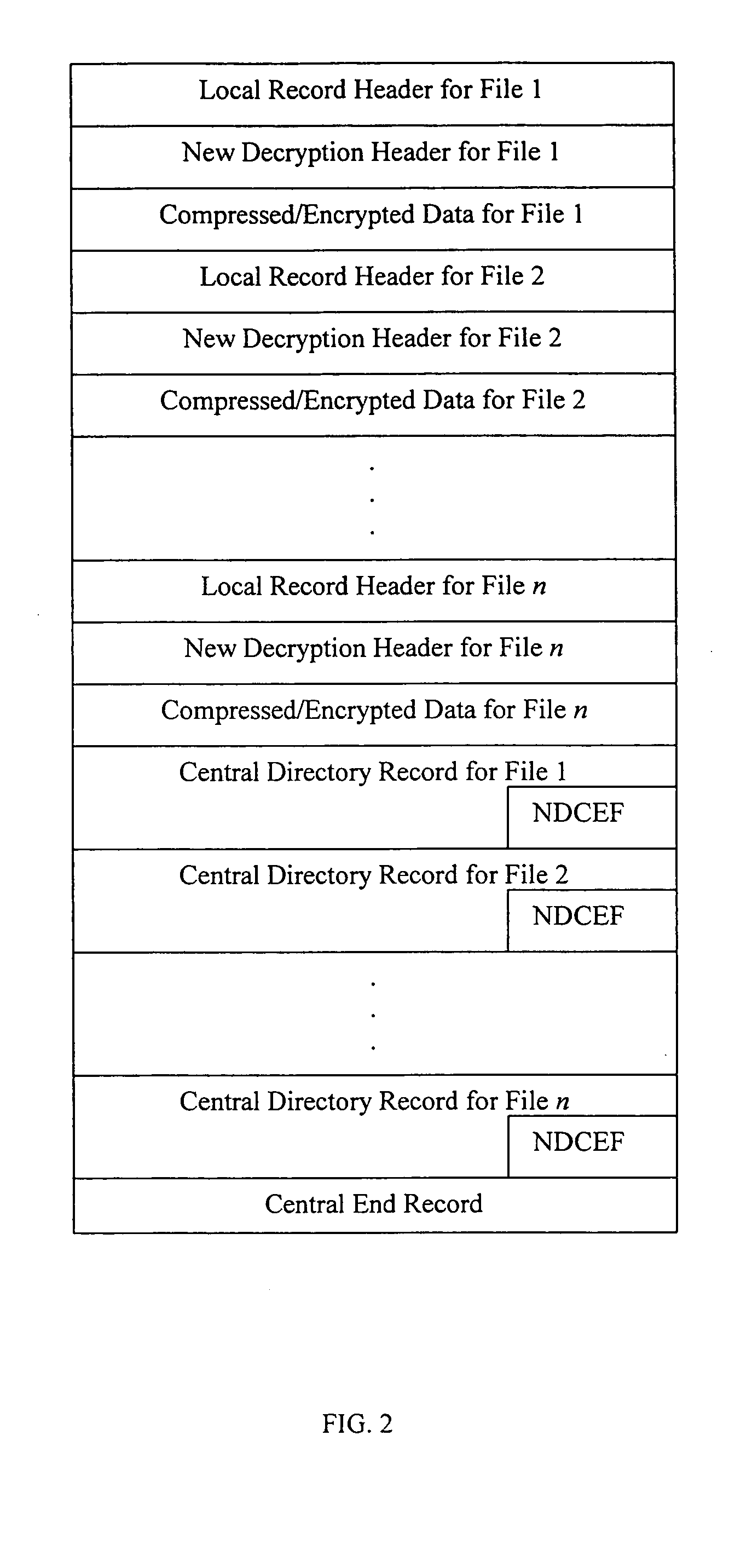
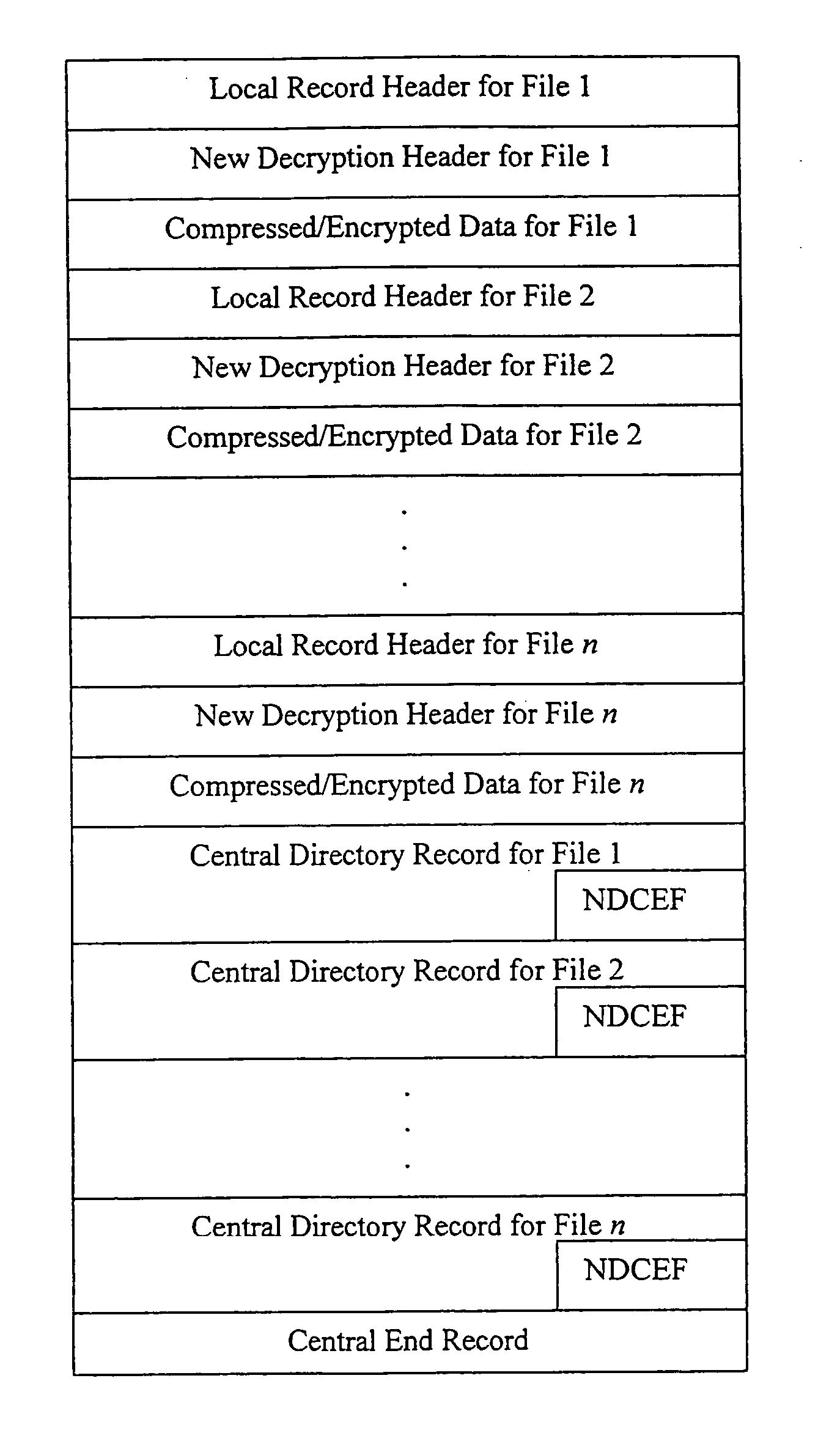
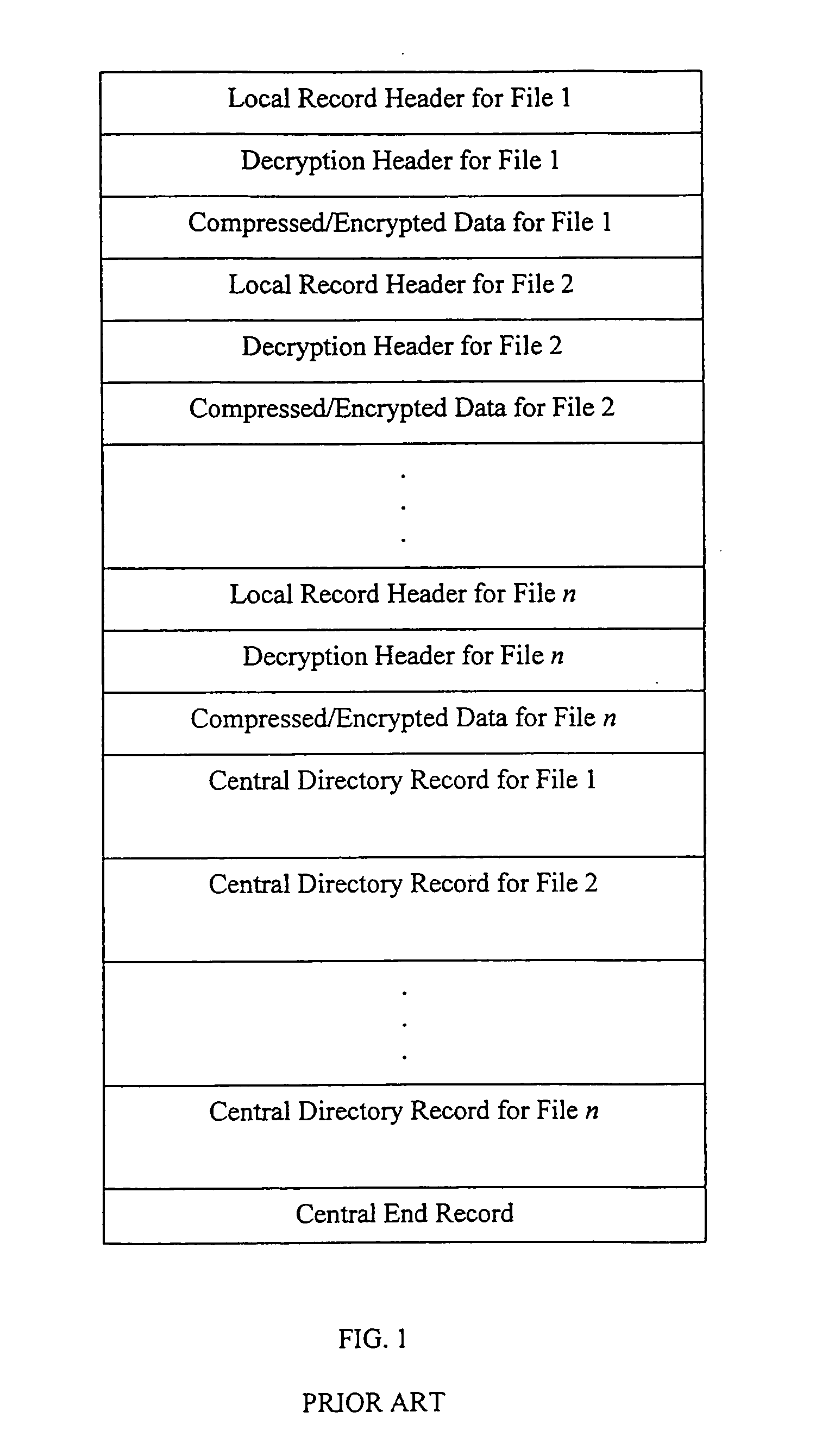
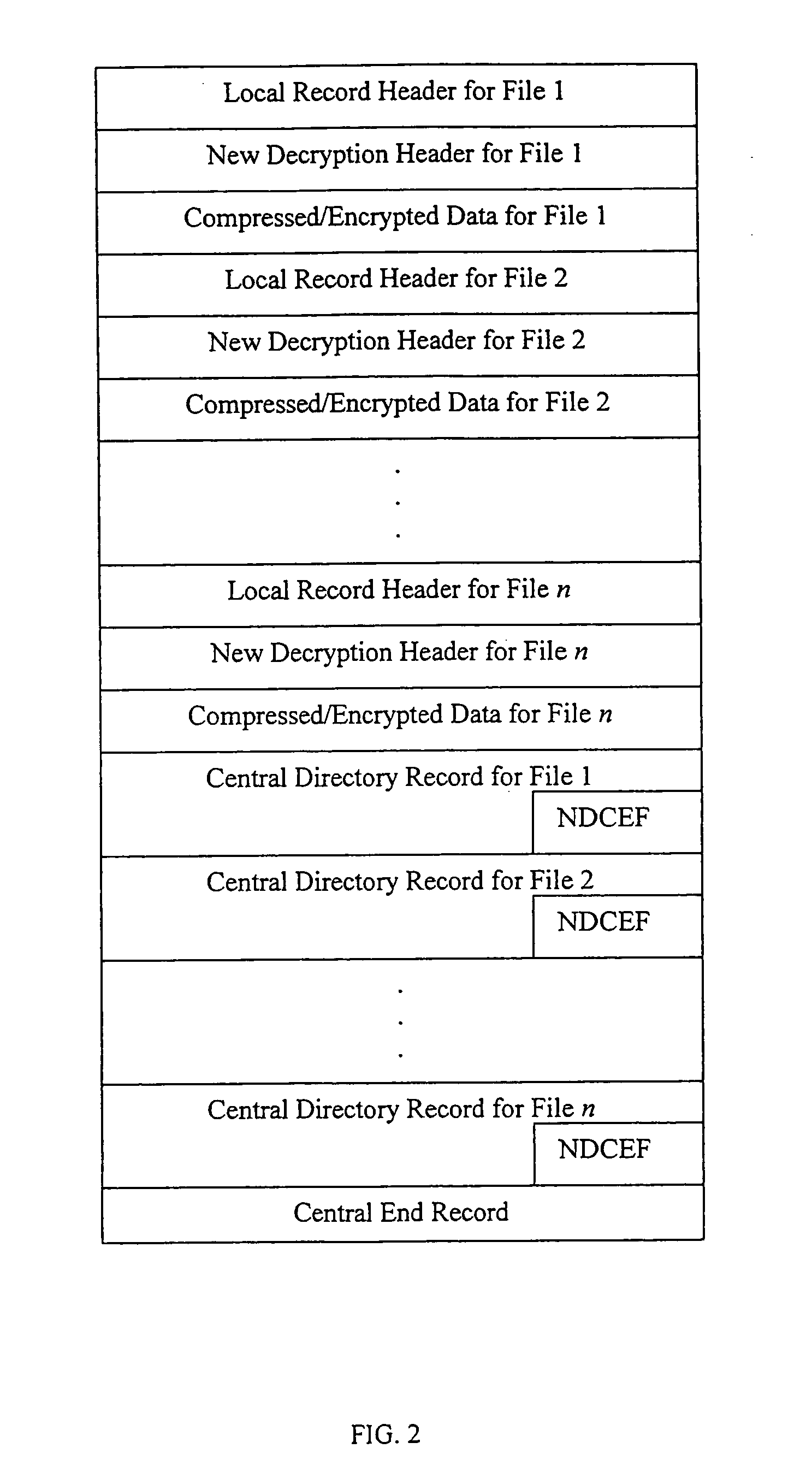
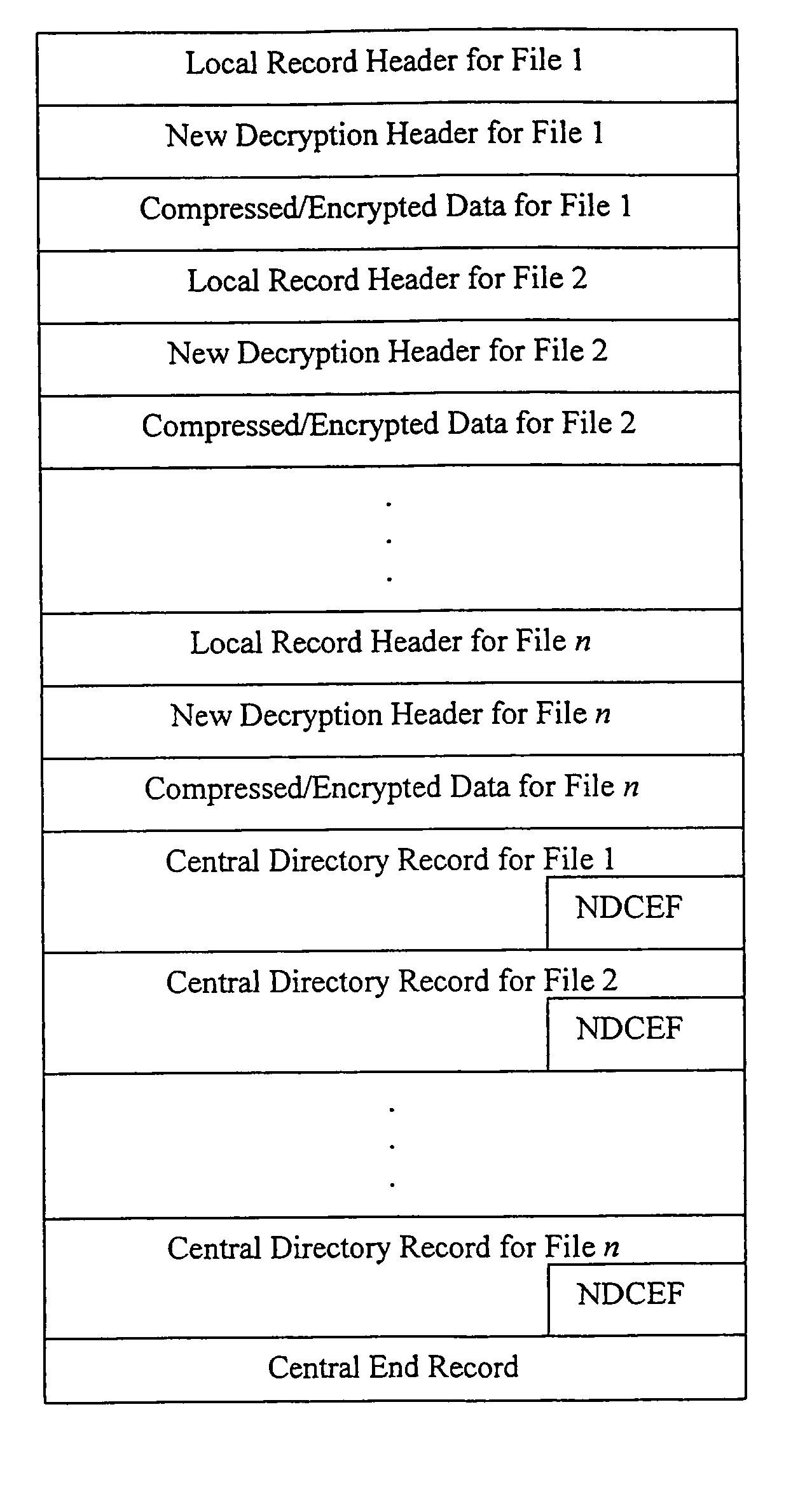
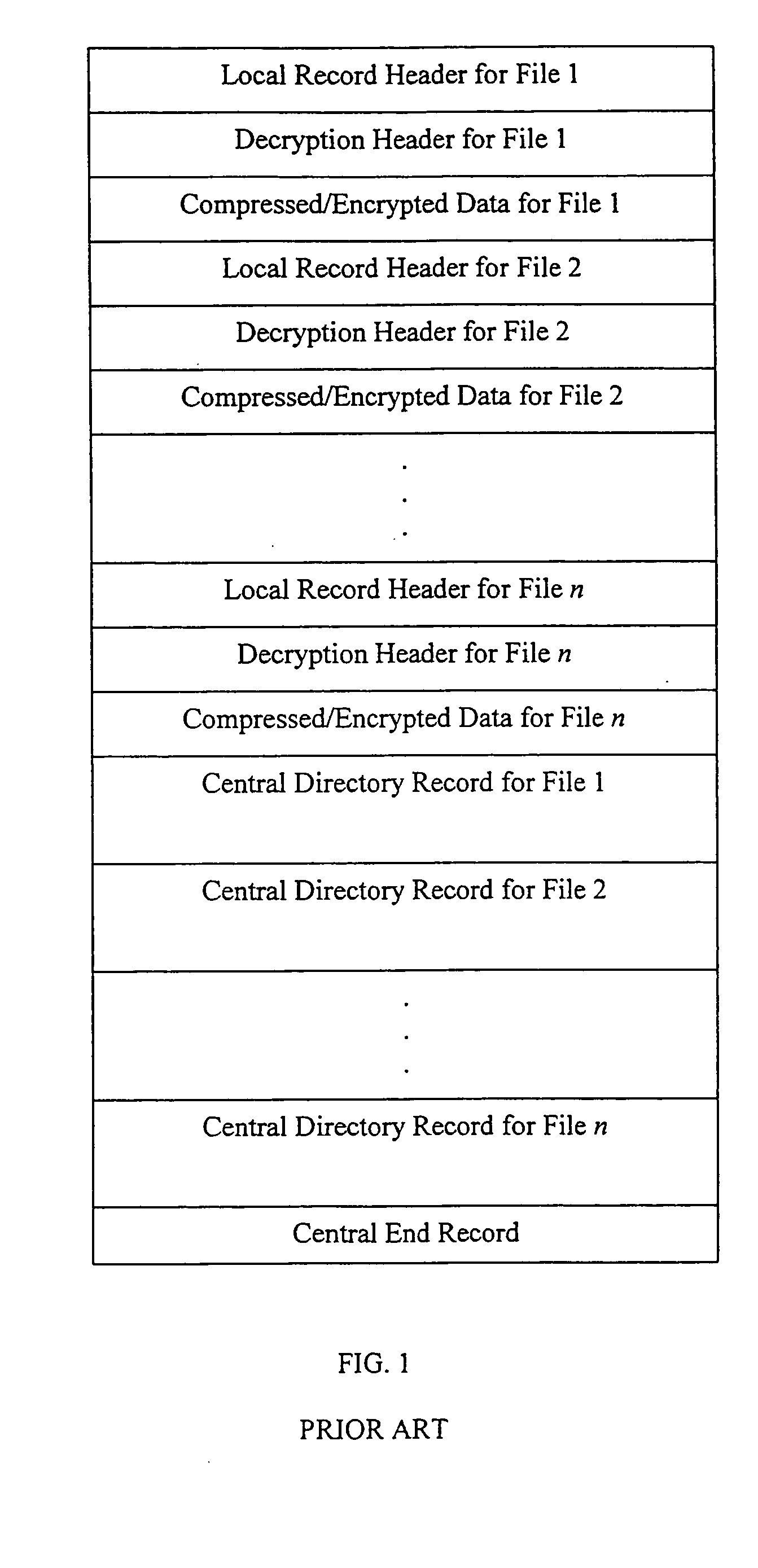
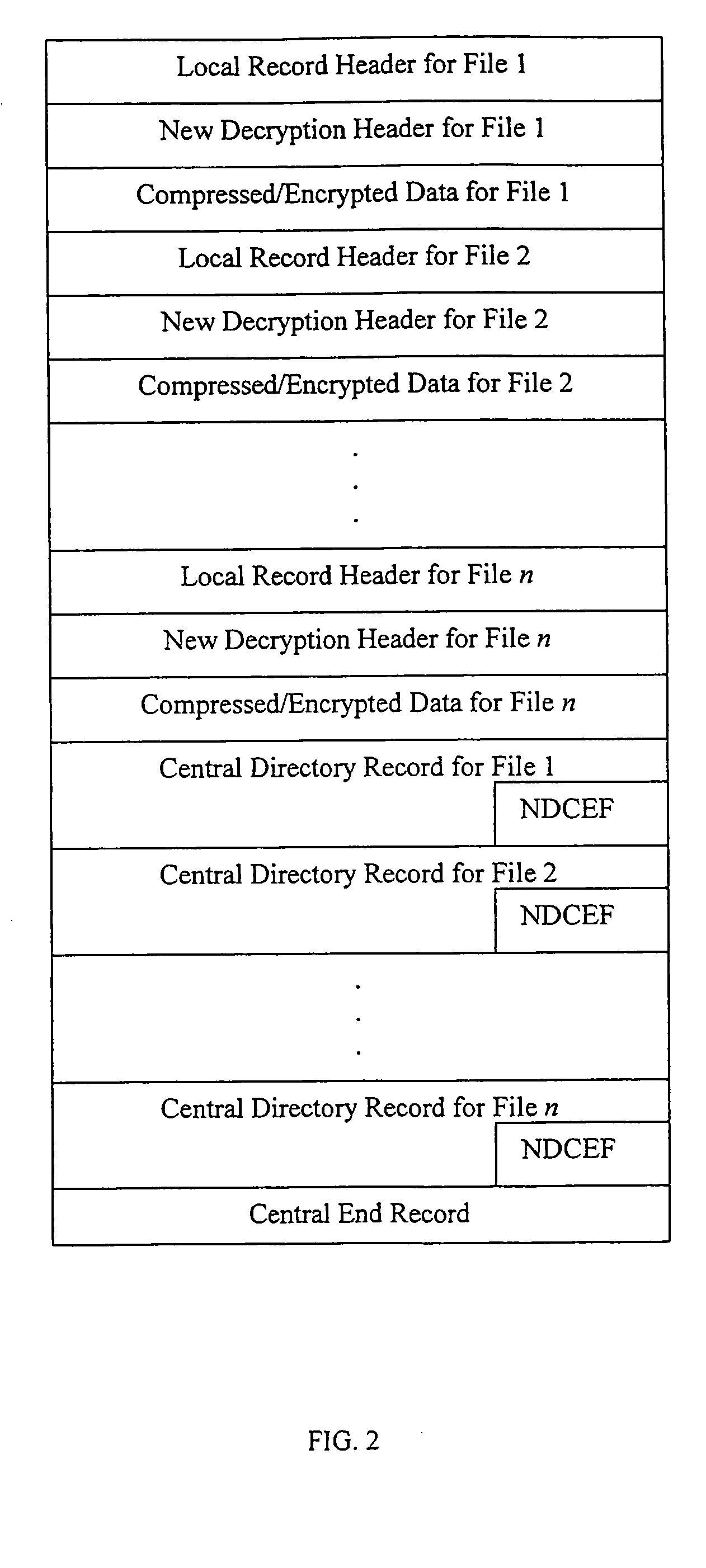
Method and system for decrypting strongly encrypted .ZIP files
InactiveUS20050086196A1Flexible useRaise security concernsEncryption apparatus with shift registers/memoriesDigital data processing detailsMultiple methodsKey management
The present invention provides a method of integrating existing strong encryption methods into the processing of a .ZIP file to provide a highly secure data container which provides flexibility in the use of symmetric and asymmetric encryption technology. The present invention adapts the well established .ZIP file format to support higher levels of security and multiple methods of data encryption and key management, thereby producing a highly secure and flexible digital container for electronically storing and transferring confidential data.
Owner:PKWARE
Method and system for multiple asymmetric encryption of .Zip files
ActiveUS20050081031A1Flexible useRaise security concernsKey distribution for secure communicationEncryption apparatus with shift registers/memoriesMultiple methodsKey management
The present invention provides a method of integrating existing strong encryption methods into the processing of a .ZIP file to provide a highly secure data container which provides flexibility in the use of symmetric and asymmetric encryption technology. The present invention adapts the well established .ZIP file format to support higher levels of security and multiple methods of data encryption and key management, thereby producing a highly secure and flexible digital container for electronically storing and transferring confidential data.
Owner:PKWARE
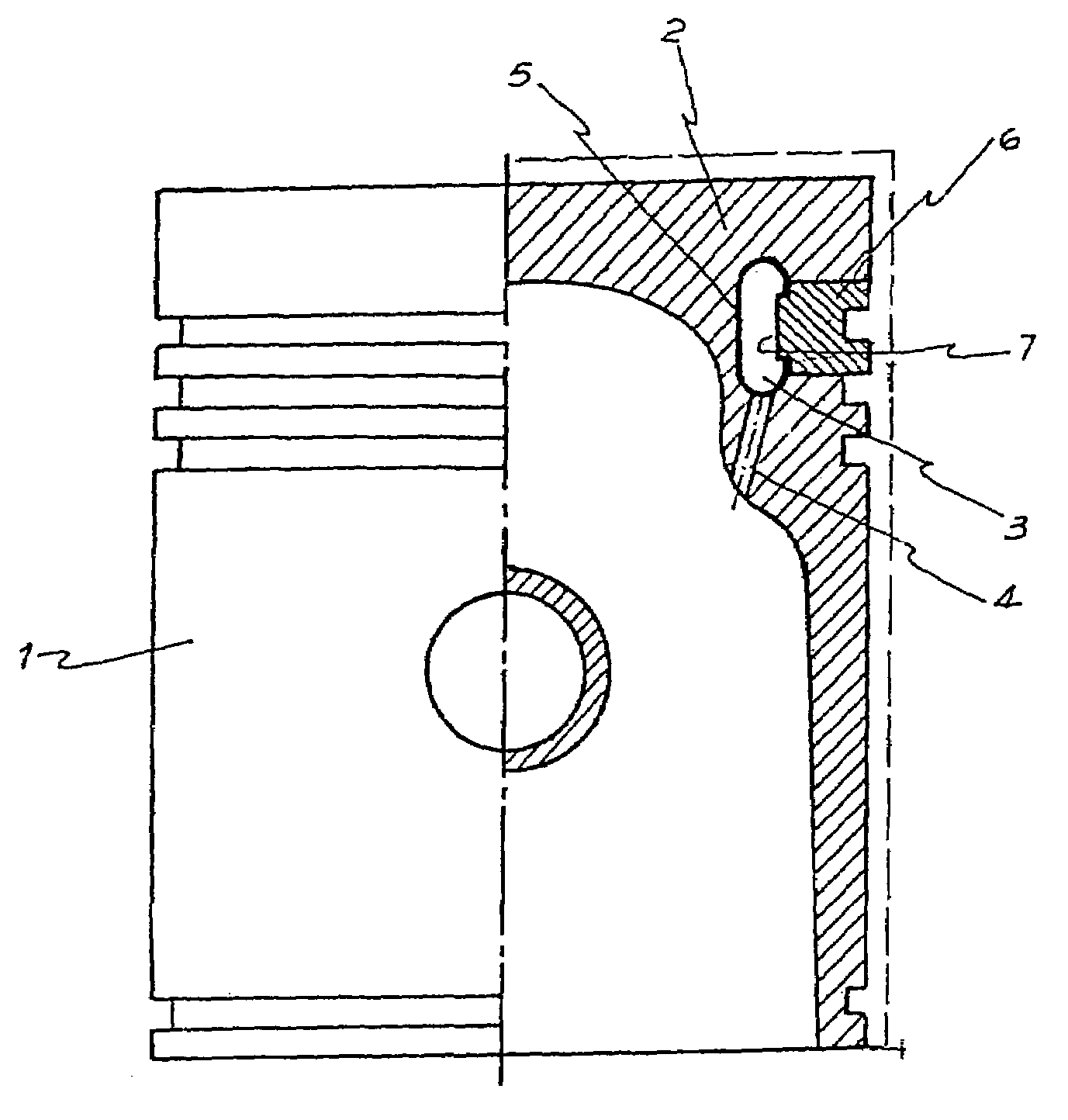
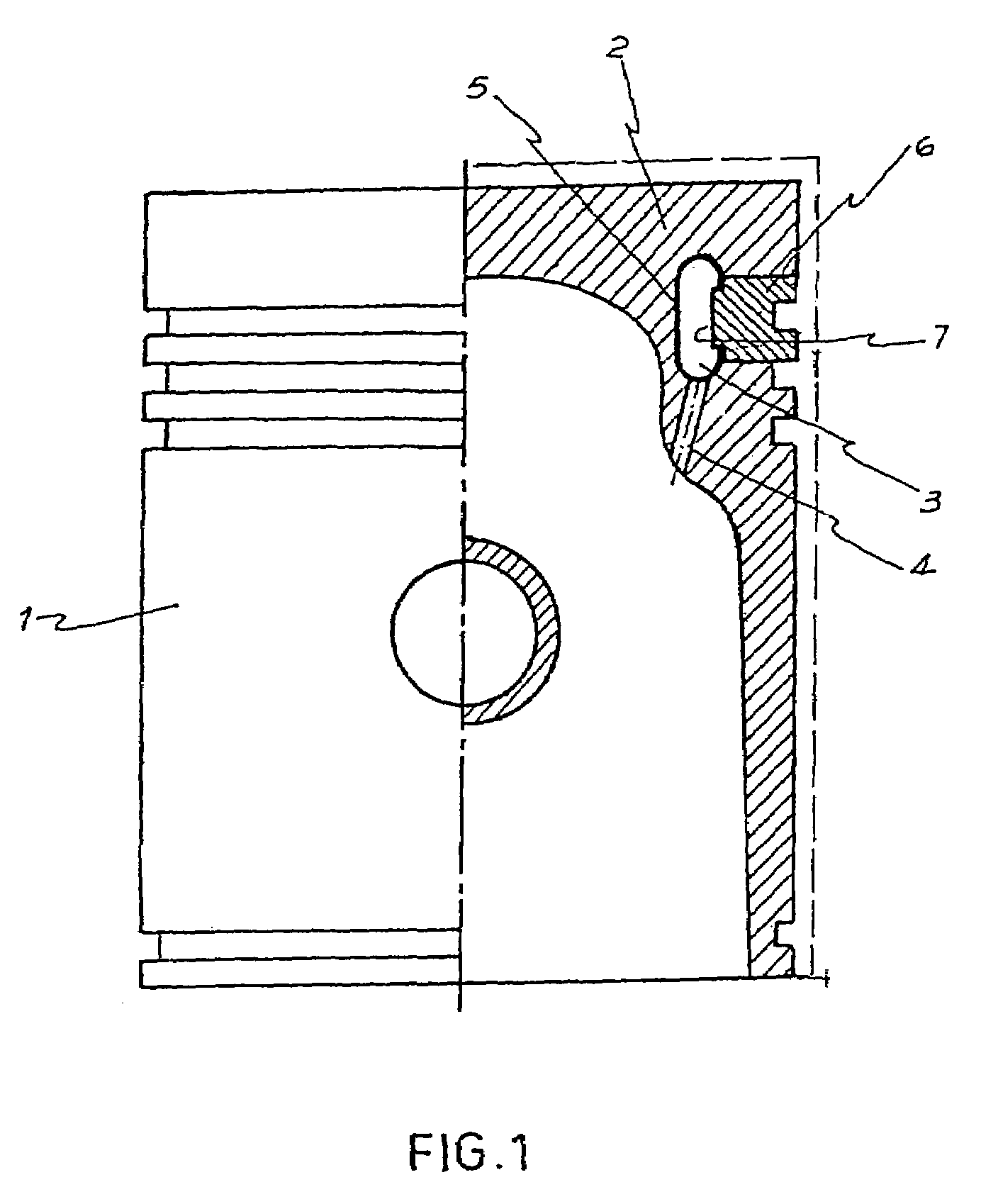
Method of mounting a metal sheet ring assembled and welded in a carrier hoop to conform the annular cooling tube of a piston of internal combustion engine
A metal sheet ring (5) has a web (15) extending between two fins (10) and (11) projecting towards a carrier hoop (6), wherein free ends of the fins rest on and couple to respective annular seats (8) and (9) defined in an internal face of the carrier hoop, the free ends being sealed by respective annular welding beads (14) to form an internal annular cooling tube (3) having an inside surface constituted by the metal sheet ring and the inside surface (7) of the carrier hoop. For the support and coupling of the ring (5) on the carrier hoop, a preform of the ring, formed outside of the carrier hoop, has a preform fin (10′) open at an angle slightly greater than the angle of the other preform fin (11) and with a free end of smaller diameter than the inside surface diameter (7) of the carrier hoop (6), while the other preform fin (11) has a larger diameter than the diameter of the inside surface (7) of the carrier hoop (6) in a way that a final stamping action, which is the only action performed with the preform in the carrier hoop, gives the final configuration to the fin (10) of the metal sheet ring (5).
Owner:APPO ROBERTO OSCAR
Management and distribution of keys in distributed environments
InactiveUS20200259637A1Highly flexibleHighly secureKey distribution for secure communicationEncryption apparatus with shift registers/memoriesEngineeringDistributed computing
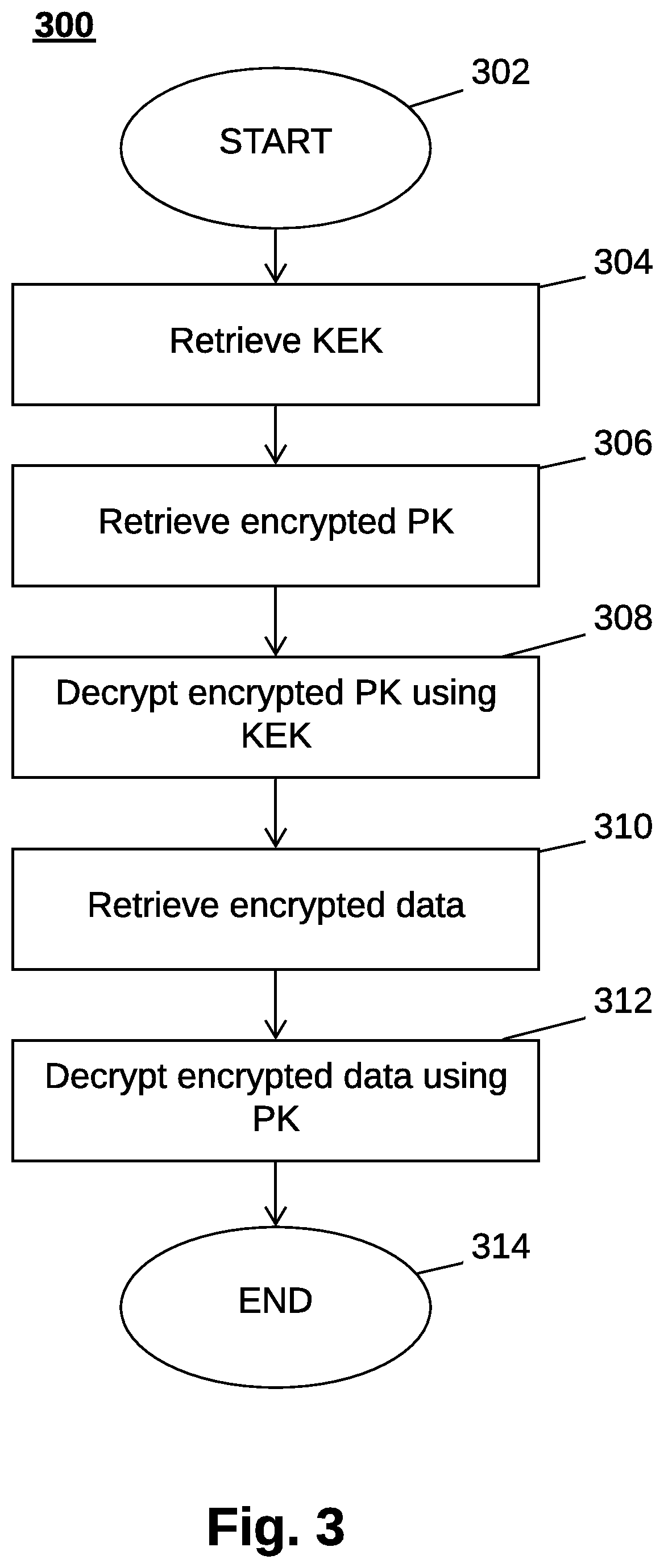
A computer-implemented method for securely retrieving data on a client device in a distributed environment is disclosed. The method comprises retrieving a key encryption key from a local storage, retrieving an encrypted private key associated with the key encryption key from the distributed environment, the encrypted private key being remotely stored in the distributed environment, decrypting the encrypted private key using the key encryption key, thereby generating a private key, retrieving encrypted data from the distributed environment, the encrypted data being remotely stored in the distributed environment, and decrypting the encrypted data using the private key. A respective client device, a method for securely providing data in the distributed environment, and a distributed environment are disclosed.
Owner:TOMES GMBH
Prepaid card issuing system
InactiveUS20060032911A1Highly marketableHighly secureCo-operative working arrangementsApparatus for meter-controlled dispensingComputer hardwareInformation processing
A prepaid card issuing system that includes a card with identifying indicia associated with a specific entity, such as a store from which products or services can be purchased, and a value such as a financial denomination, disposed thereon. An issuing terminal is also provided and is structured to receive the card, identify the security identifier, and communicate with a remote, control processor that receives the security identifier and defines and communicates to the issuing terminal usage information associated with the security identifier. The issuing terminal is further structured to dispose account information on the card in accordance with said the information so as to permit use of the card for the purchase of products or services, and to retain the card therein during detection of the security identifier, disposition of the account information on the card and printing of an issuance confirmation on the card.
Owner:ARIAS LUS
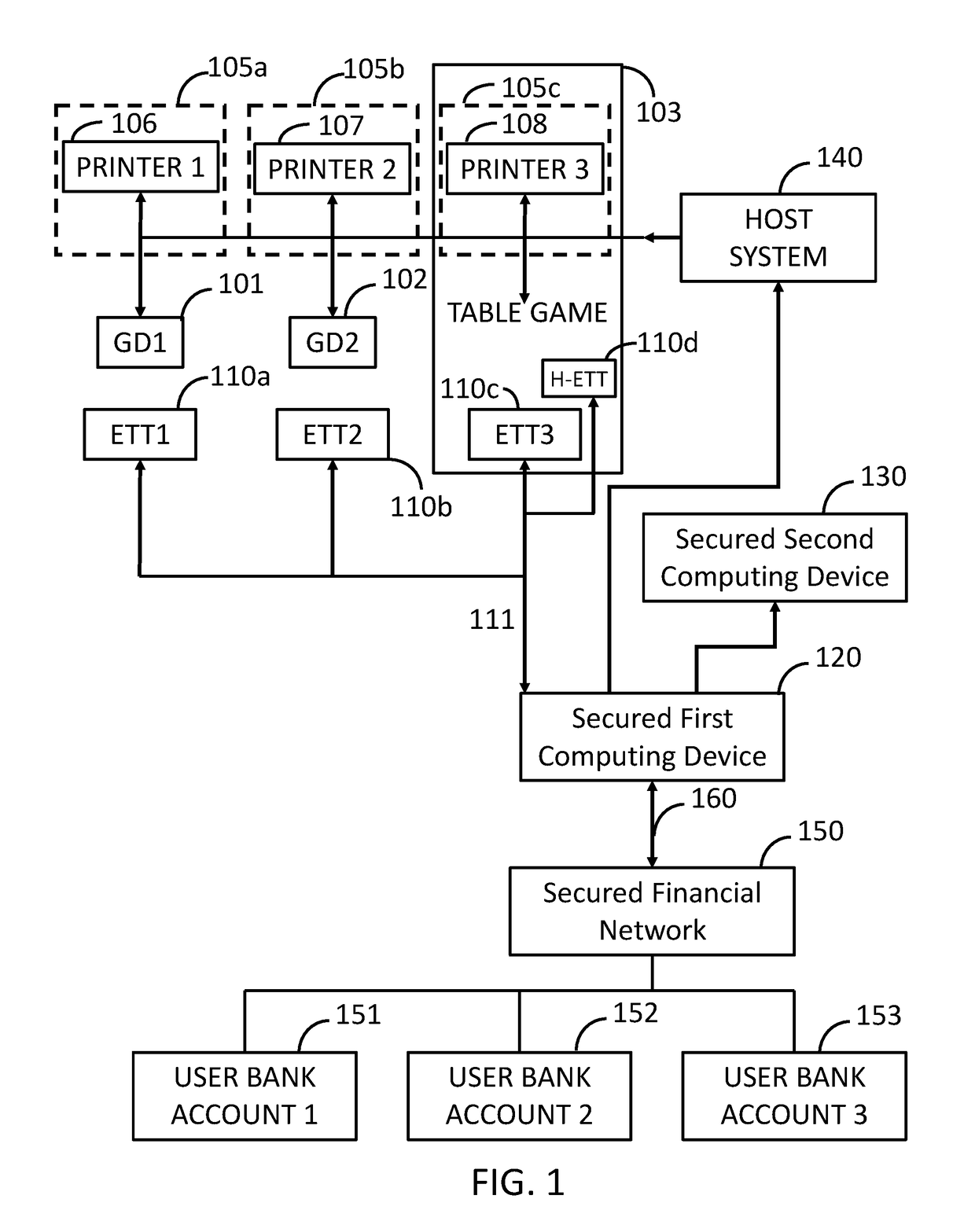
Electronic transaction systems and methods for gaming or amusement credit purchases
ActiveUS10223866B2Efficient retrievalImprove integrityFinanceApparatus for meter-controlled dispensingDisplay deviceDebit card
Systems, and methods are provided for the electronic purchase of gaming or amusement credits using a transaction device at a patron's location to apply funds from a financial account to the purchase of credits for use with an amusement or gaming device, system, or point of other wagering activity. Such credits are provided at the patron's location in the form of a printed ticket or other physical indicia of equivalent value, credits appearing in the credit meter and on the display of a gaming device, credit issued to a player card confirmed at the patron's location, credit issued to a debit card confirmed at the patron's location, and / or cash or other monetary-equivalents. In addition, physical confirmation of the completed electronic transaction from the patron's financial account may be concurrently provided to the patron in the form of a receipt.
Owner:AUTOMATED CASHLESS SYST INC
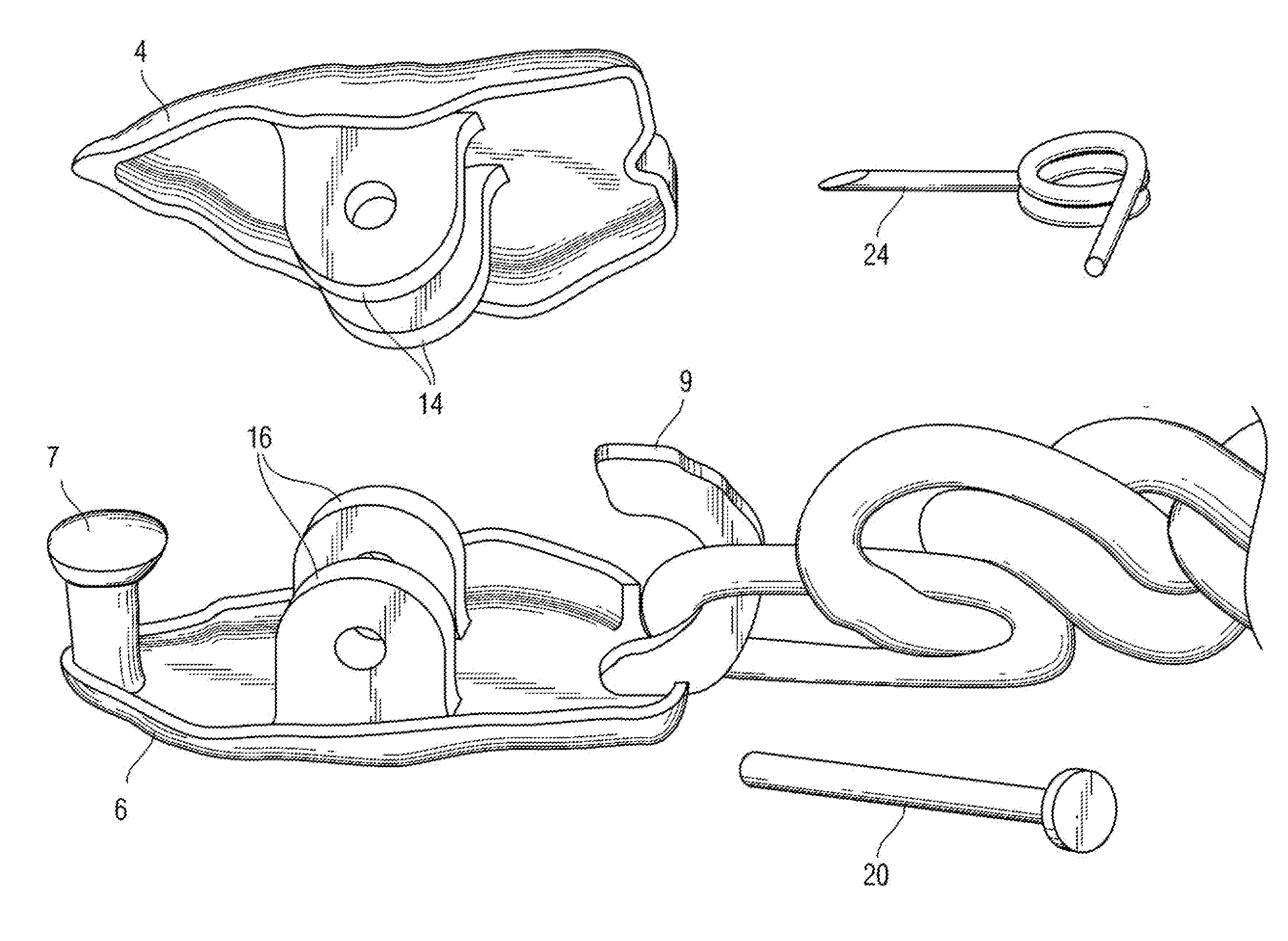
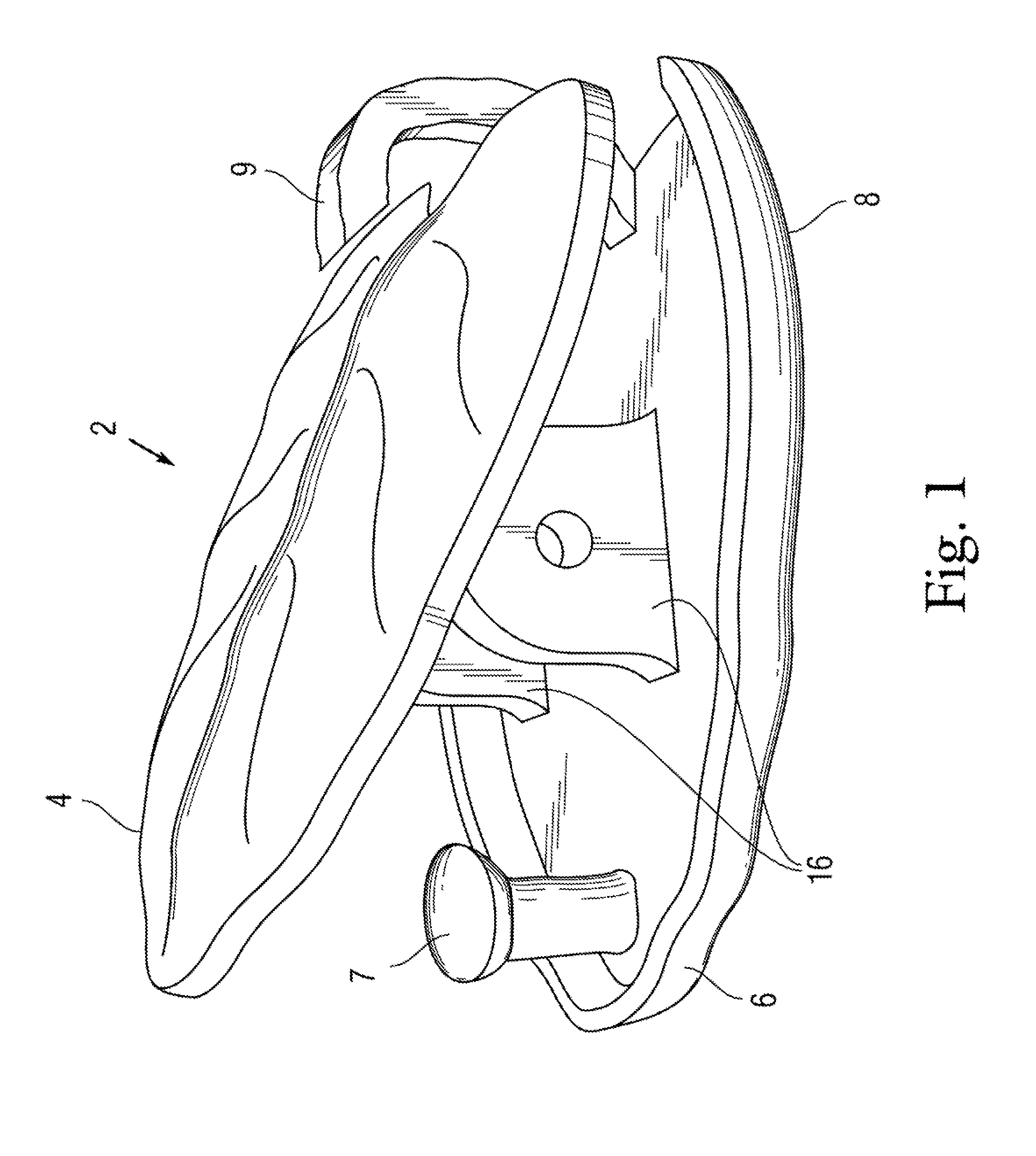
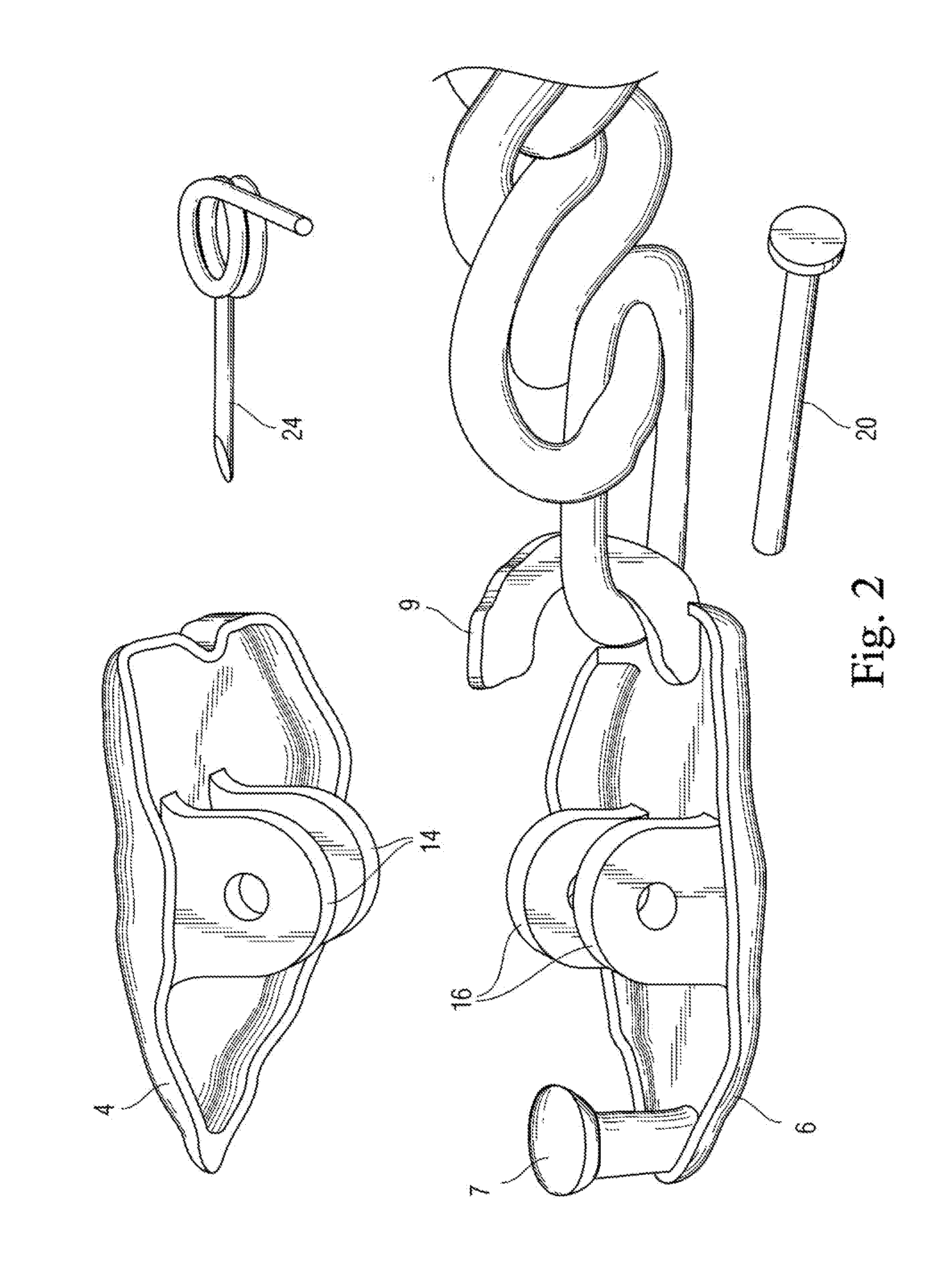
Decorative jewelry double clasp with single spring for bracelets & necklaces
InactiveUS20110185768A1Fine and delicate and ornamental appearanceHighly secureSnap fastenersClothes buttonsEngineeringTorsion spring
A decorative double-sided jewelry clasp for joining two ends of a jewelry chain together. The clasp comprises a rocker plate pivotally mounted to a base plate at a hinge. The hinge is formed by cooperating yokes extending from the center of each of the rocker plate and base plate. With plates facing, the yokes align and a pin is inserted there through to pivotally secure them together. A torsion spring is carried on the pin to bias the rocker plate versus the base plate. Further, the base plate has a short post at one end and a longer hook at the other, the hook looping around to the backside of the rocker plate, and thereby stopping counter-pivoting of the rocker plate. Both hook and post catch and secure the ends of the jewelry chain, with the spring locking the chain at both ends until a user depresses the rocker plate, thereby counter-biasing it open at both ends to release the chain.
Owner:PINCHUK ANNA
Optically switched communication network
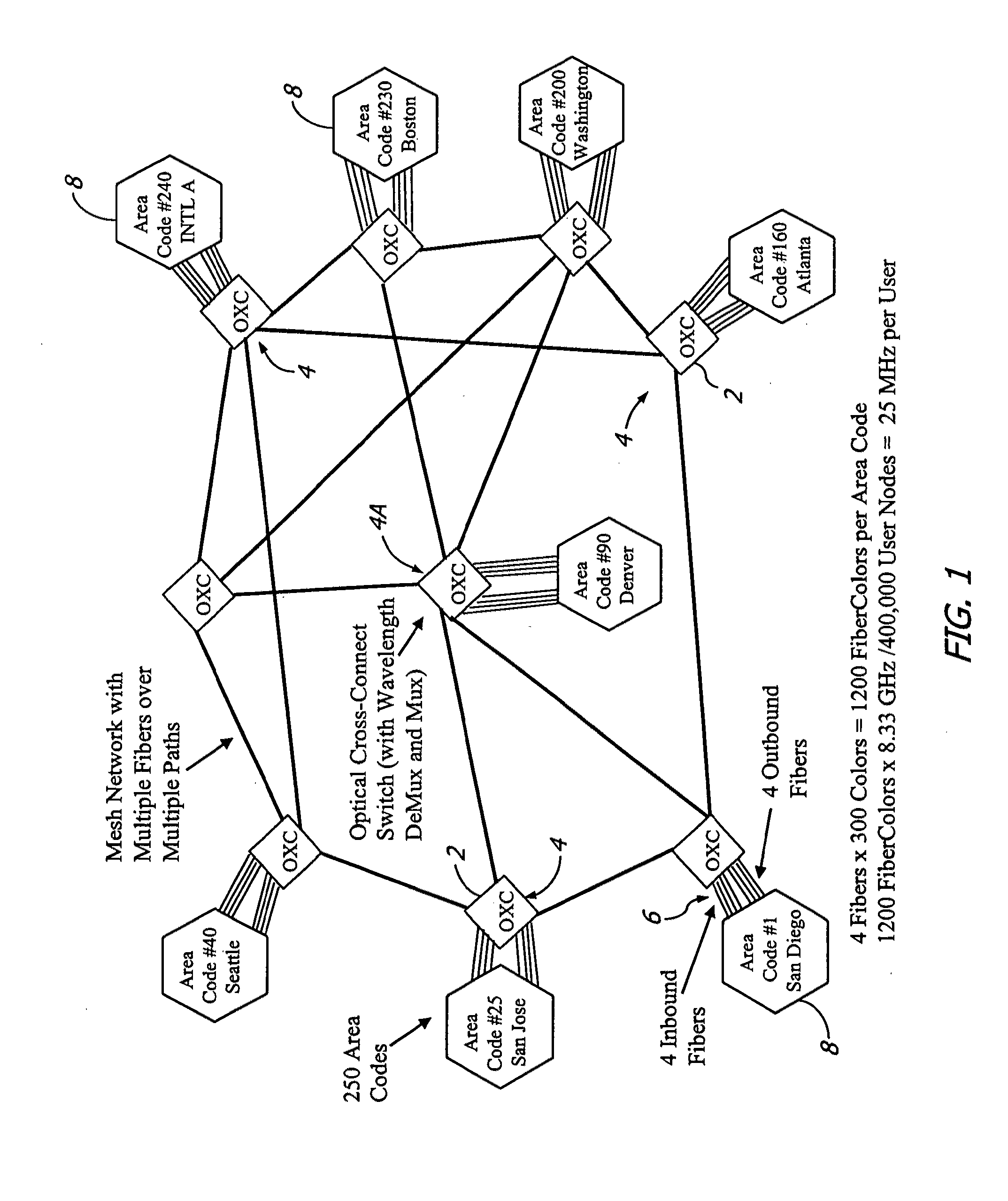
InactiveUS20120237217A1High scale performanceReduce network energy needMultiplex system selection arrangementsWavelength-division multiplex systemsFiberTelecommunications link
A large communication network suitable for nationwide or worldwide utilization. The present invention overthrows the conventional packet switching technologies with an all-optical network. The invention uses tunable laser sources to generate large number of highly stable narrow-band optical signals, each serving as a communication channel. With packet processing replaced by all-optical channels, the network become highly secure and scalable while harnessing the virtually unlimited capacity of fiber-optic. A large number of nodes (called area code nodes) are connected with all-fiber-optic links with all-optical switches. A routing algorithm provides one or more communication links from each area code node to every other area code node so that information never has to change carrier wavelength as it travels the network. Each area code node contains circuits that are provided to connect individual users to the network.
Owner:TREX ENTERPRISES CORP
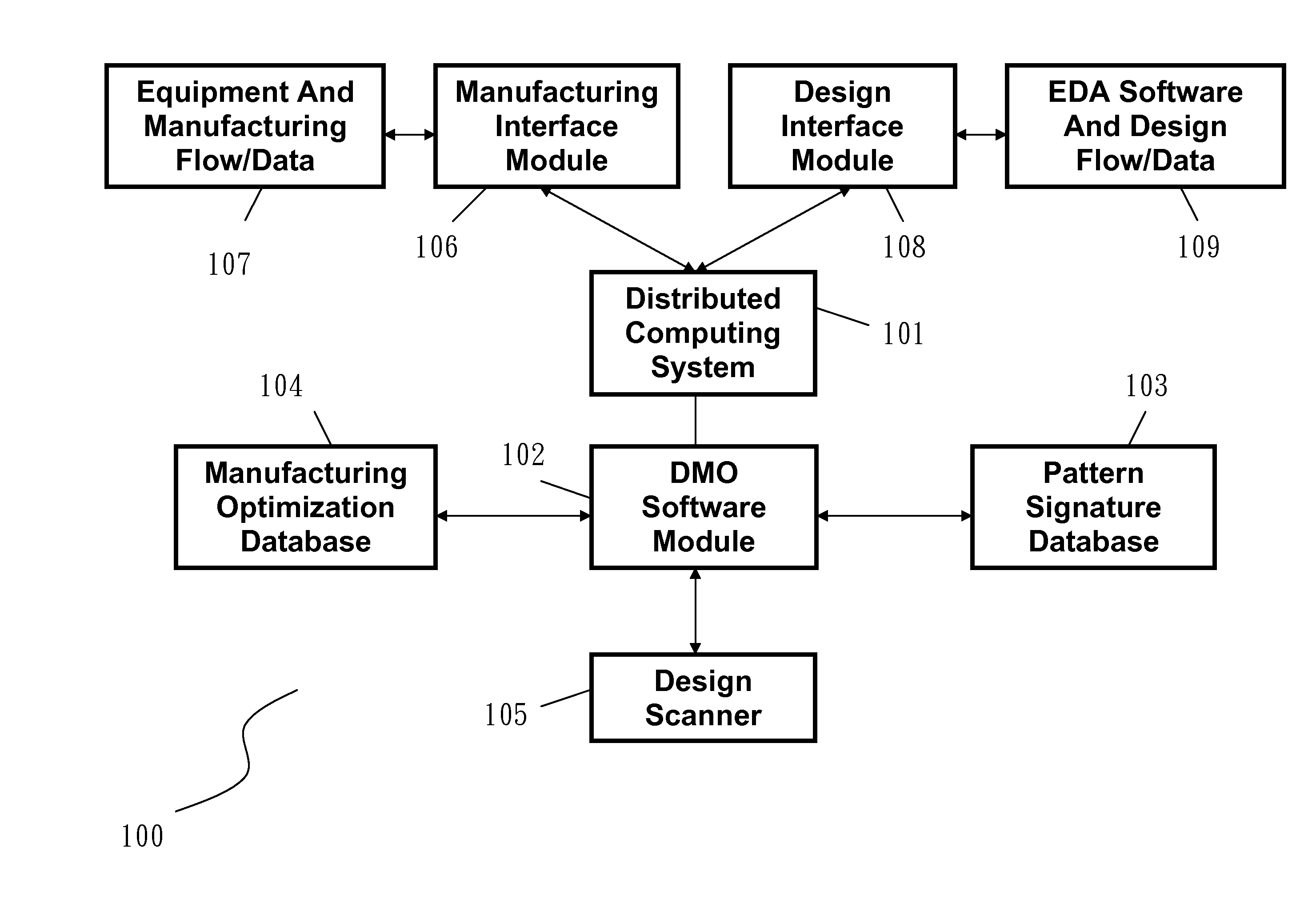
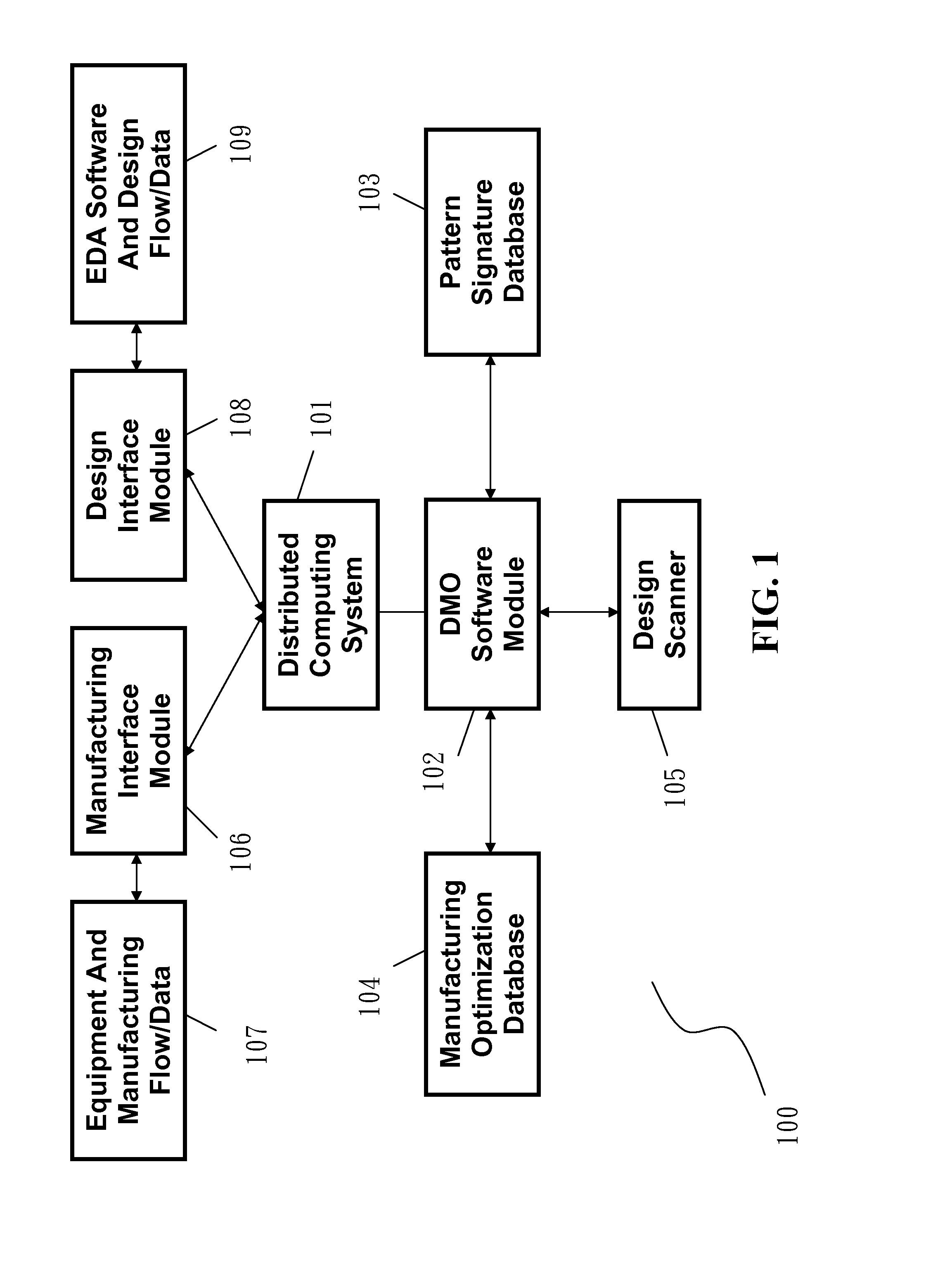
Apparatus For Design-Based Manufacturing Optimization In Semiconductor Fab
InactiveUS20140214192A1Improve scalabilityHighly secureSemiconductor/solid-state device testing/measurementResourcesSemiconductor fabComputing systems
A design-based manufacturing optimization (DMO) server comprises a distributed computing system and a DMO software module incorporating with a design scanner to scan and analyze design data of a semiconductor device for optimizing manufacturing of the semiconductor device. The DMO software module sets up a pattern signature database and a manufacturing optimization database, generates design-based manufacturing recipes, interfaces with manufacturing equipment through a manufacturing interface module, and interfaces with electronic design automation suppliers for the design data through a design interface module. The DMO server executes the design-based manufacturing recipes for manufacturing optimization.
Owner:APPLIED MATERIALS INC
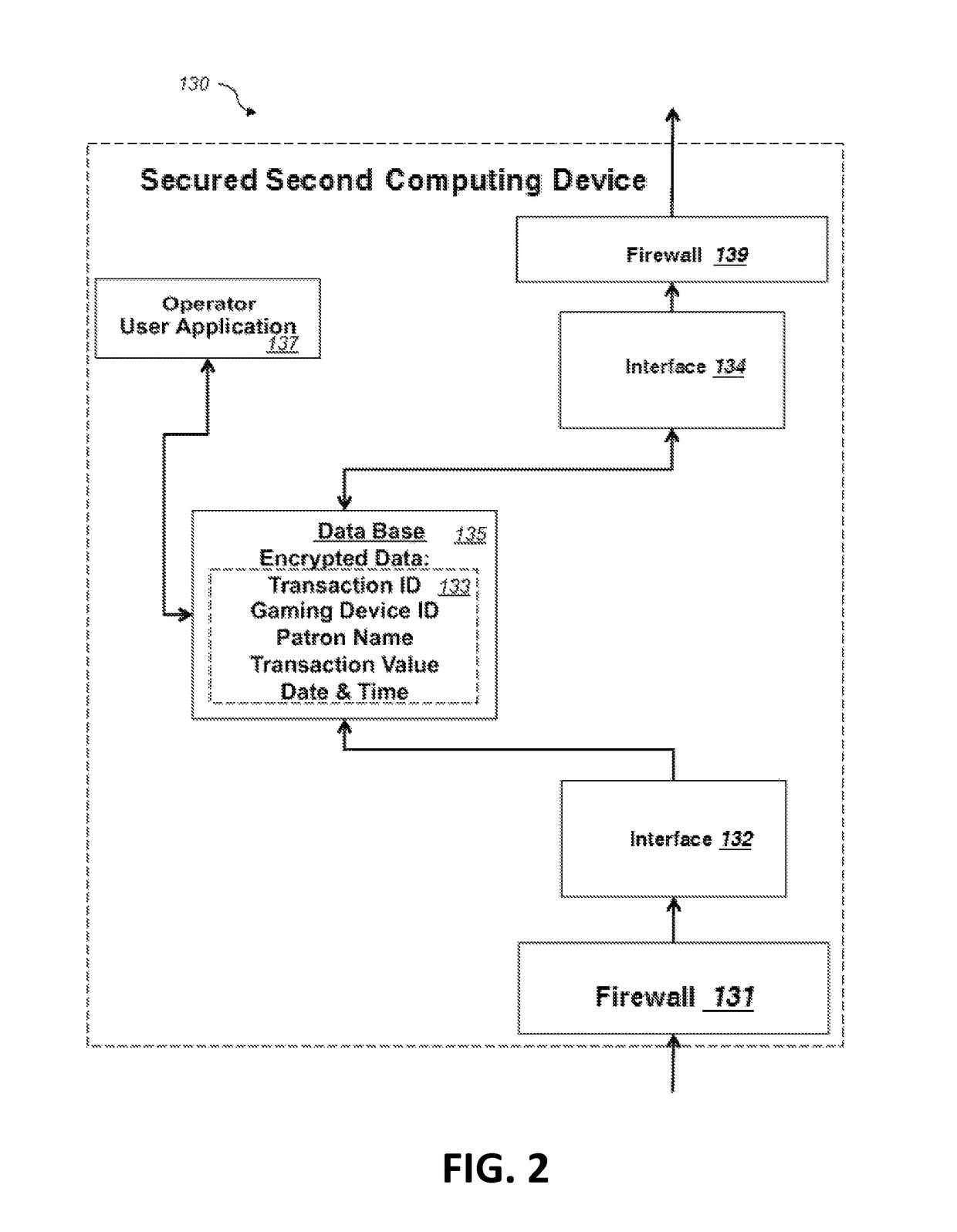
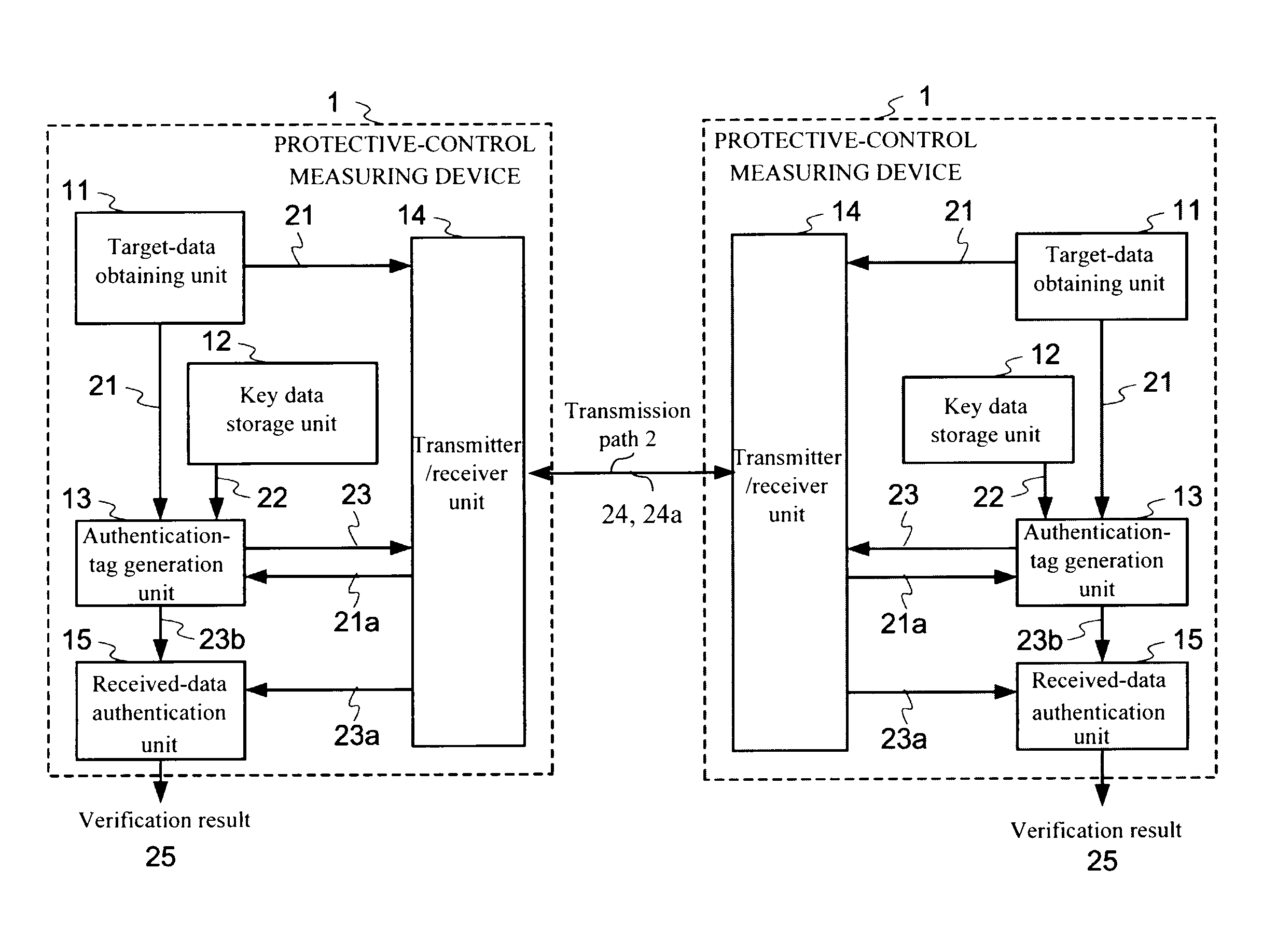
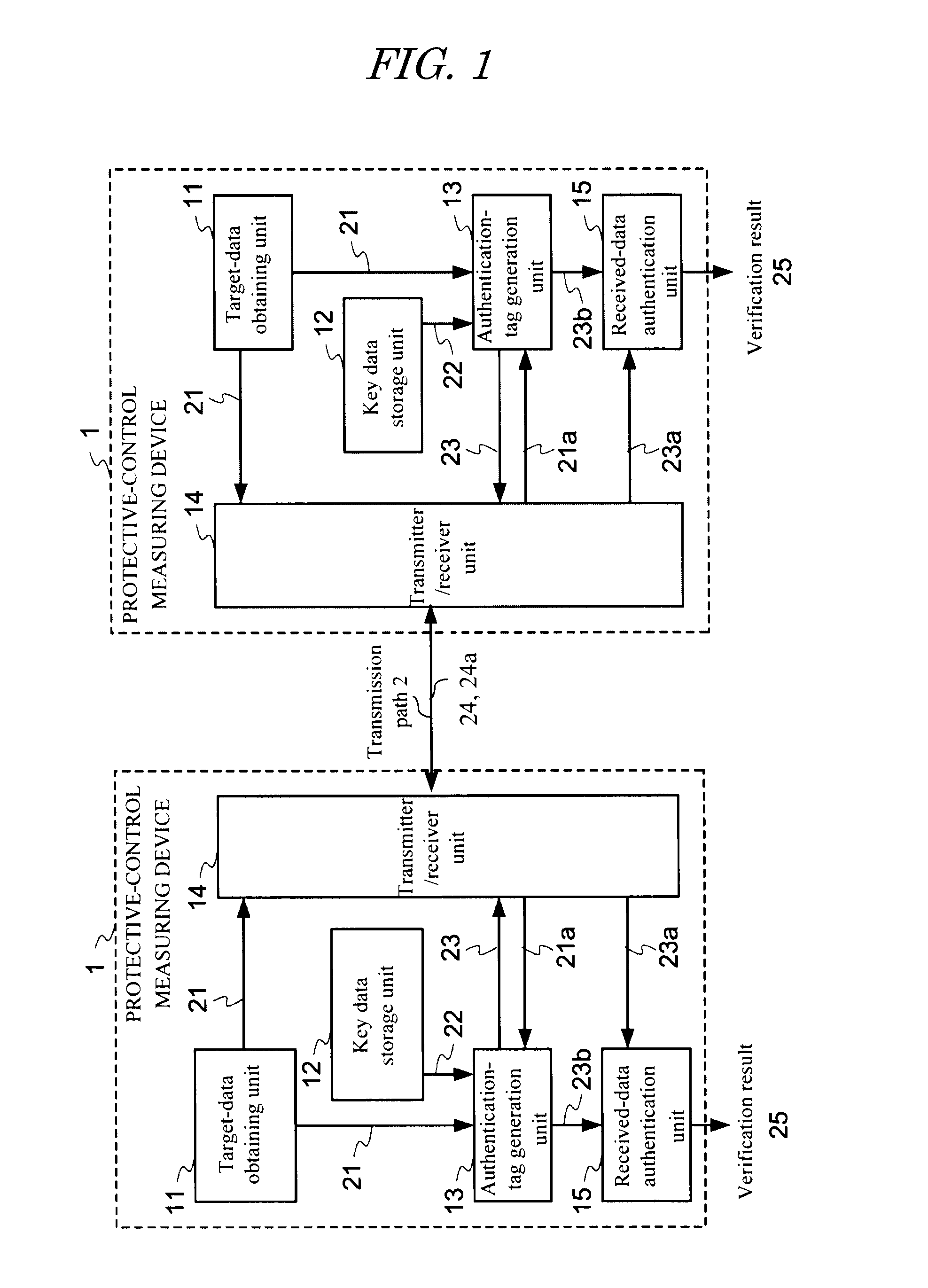
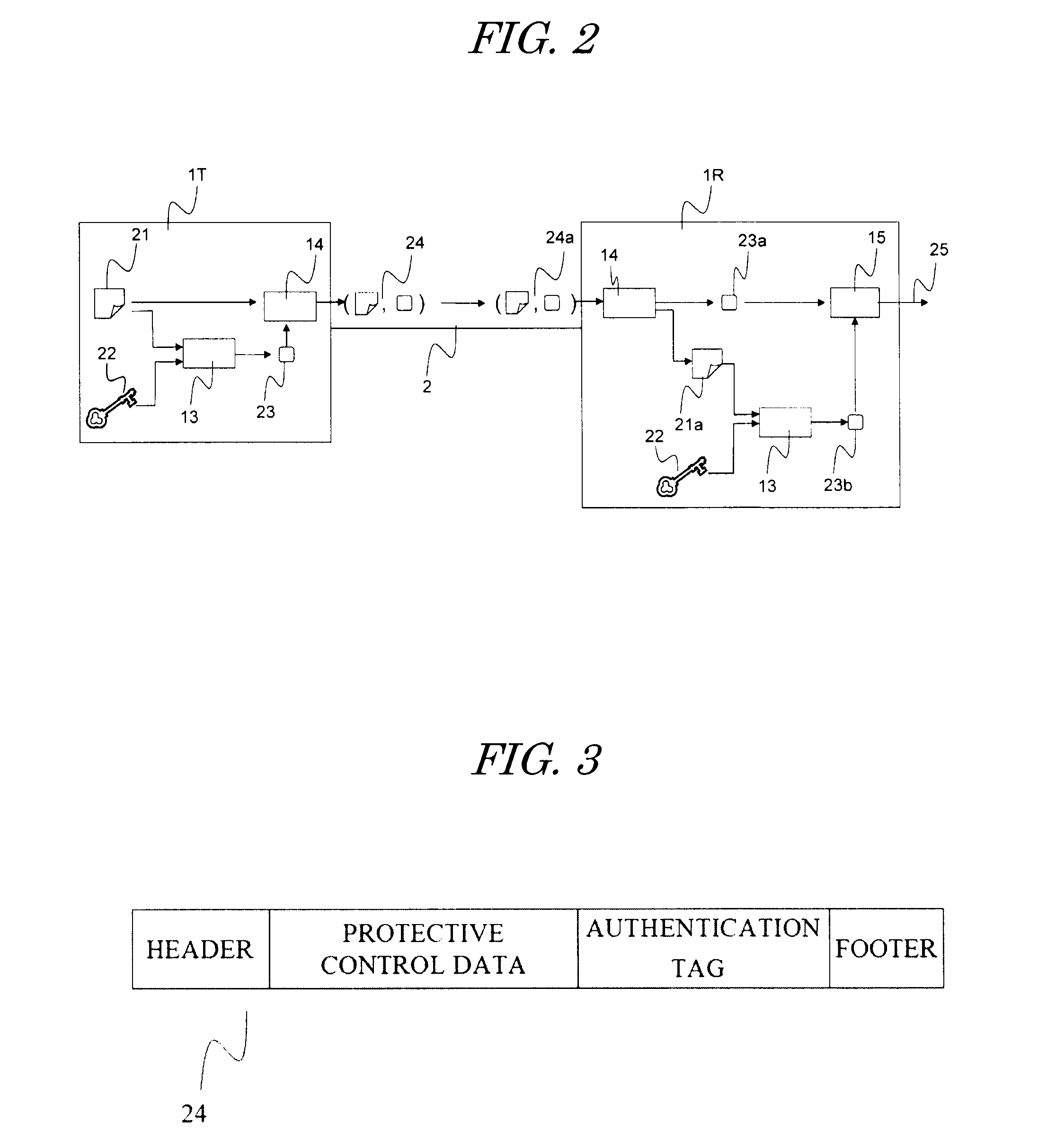
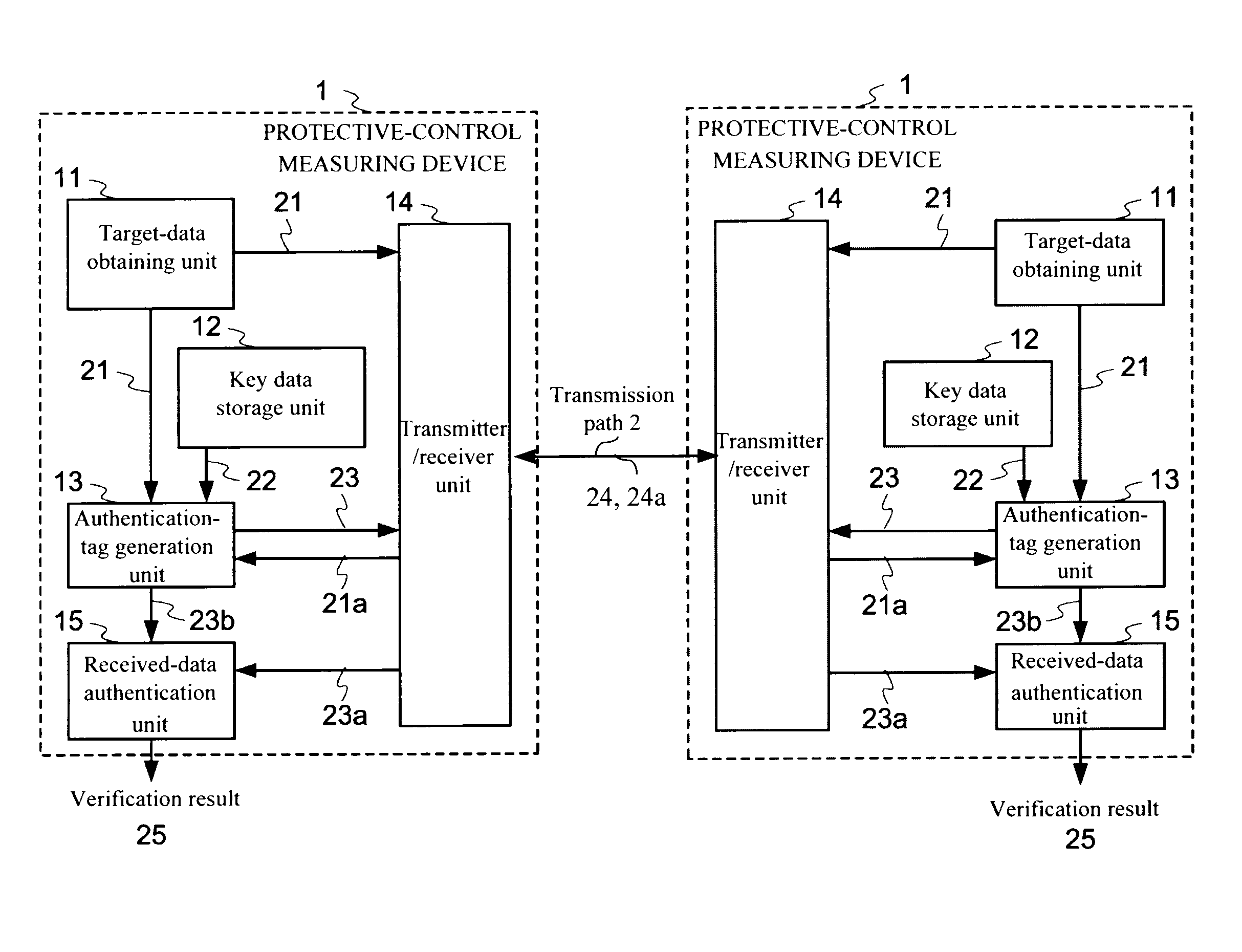
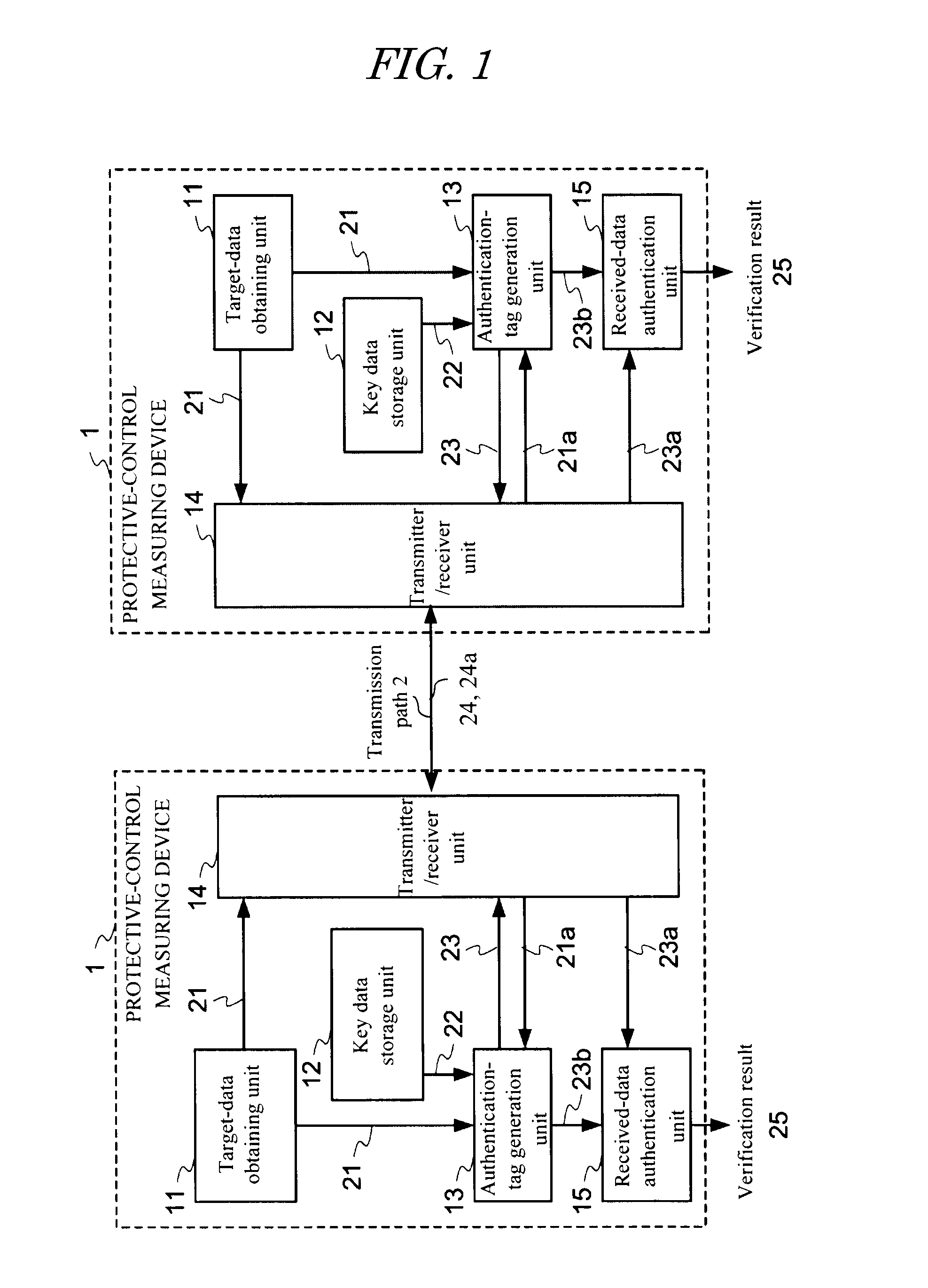
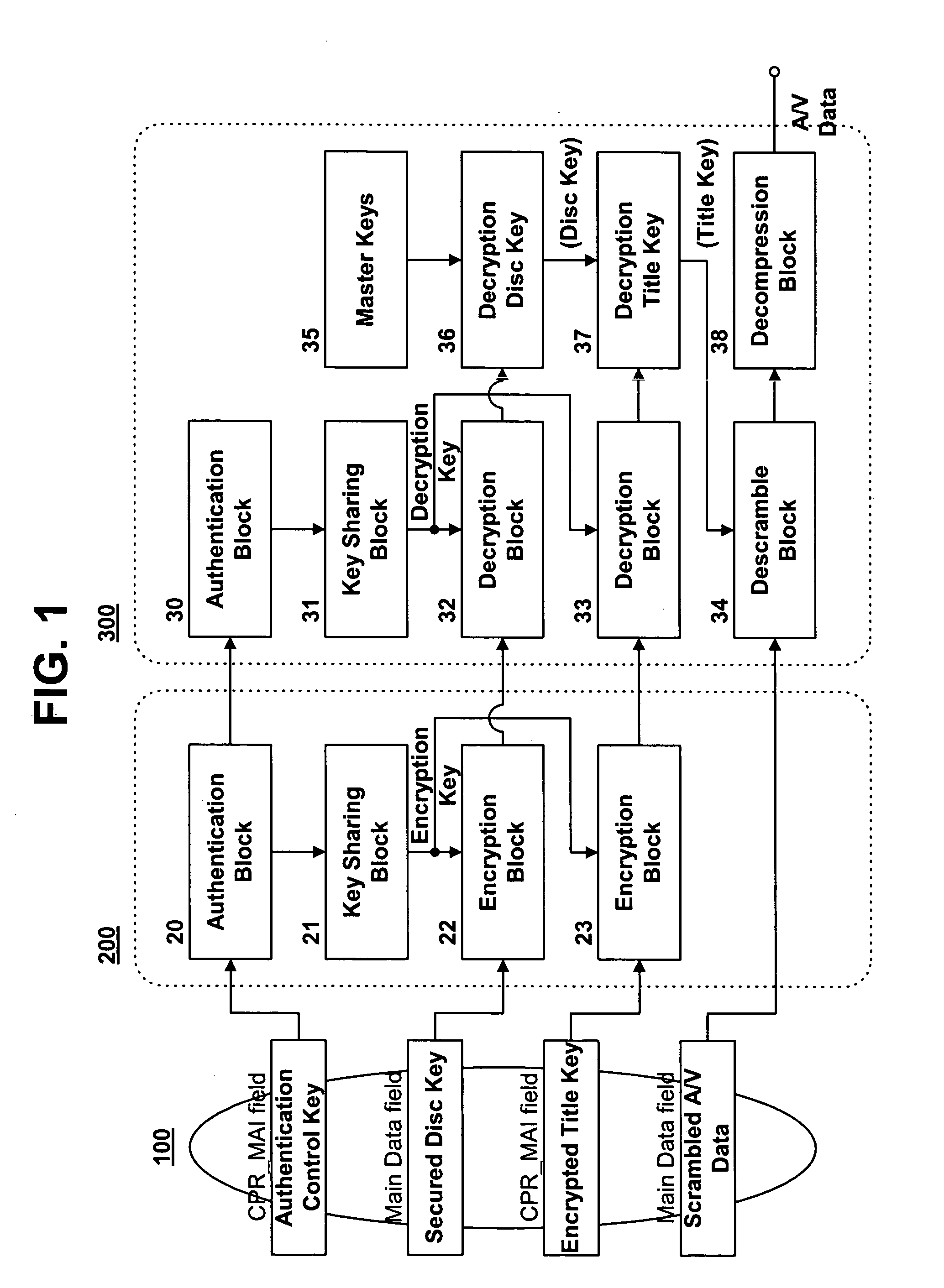
Protective-control measuring system and device and data transmission method
InactiveUS8547201B2Efficient use ofImprove reliabilityElectric signal transmission systemsMultiple keys/algorithms usageComputer hardwareData transmission
Owner:NAT UNIV CORP YOKOHAMA NAT UNIV +1
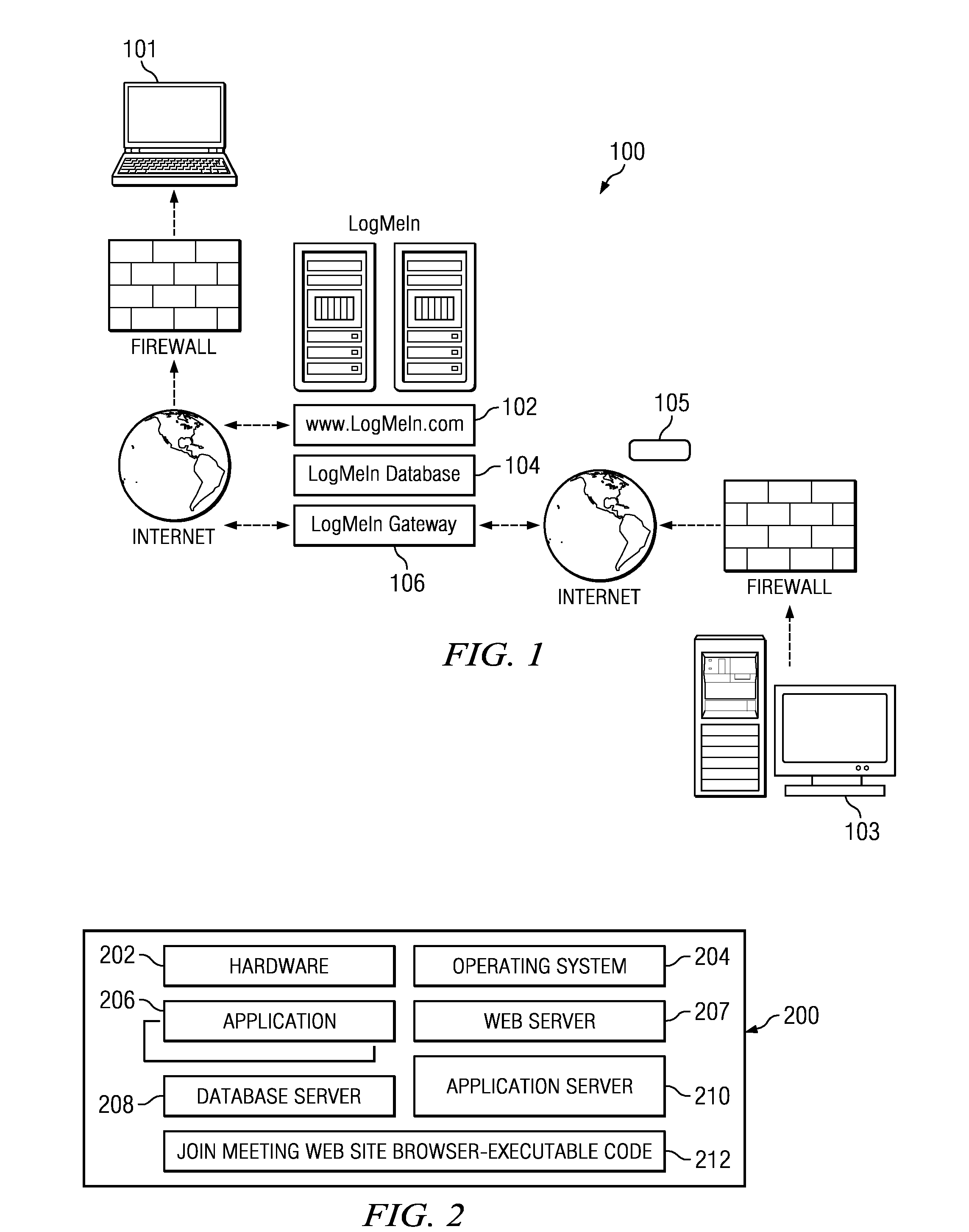
Server apparatus, communication terminal apparatus, delivery system and delivery program
InactiveUS7509488B2Suitable delivery serviceHighly secureDigital data processing detailsUser identity/authority verificationUser identifierAnonymity
There is provided a server apparatus that realizes a suitable delivery service according to requests by performing a highly secure and easy-to-understand authentication while allowing anonymity to be maintained. During connection to the server apparatus, a communication terminal apparatus transmits an appliance type ID and a user ID to the server apparatus according to depression states of authentication buttons. The server apparatus receives the transmitted appliance type ID and user ID, determines the authentication level based on the received appliance type ID and user ID, selects a service content to be provided according to the determined authentication level, and transmits corresponding delivery data to the communication terminal apparatus. As a result, suitable data for requests from the user side can be delivered.
Owner:YAMAHA CORP
Network-based quick connect meeting service
ActiveUS8539028B2Easy to useHighly-available, scalable “joinData processing applicationsWeb data indexingComputer networkApplication software
A network-accessible service enables participating end users to collaborate with one another over a network. End users have computing devices that include hardware and software to enable the device to access a network. The service provides a publicly-available site or a local software application from which a first participating user initiates a “meeting,” e.g., by selecting a “share” button. In response, the site or software application provides an HTTP link that includes a “meeting” code, which may be a one-time unique code. The first participating user then shares the link with whomever he or she desires to collaborate. Upon receiving the link, a second participating user joins the meeting “on-the-fly” by simply selecting the link or navigating to the site and entering the “meeting” code. The service connects the second participating user to the meeting immediately and without requiring any registration, software download, or the like.
Owner:GOTO GRP INC
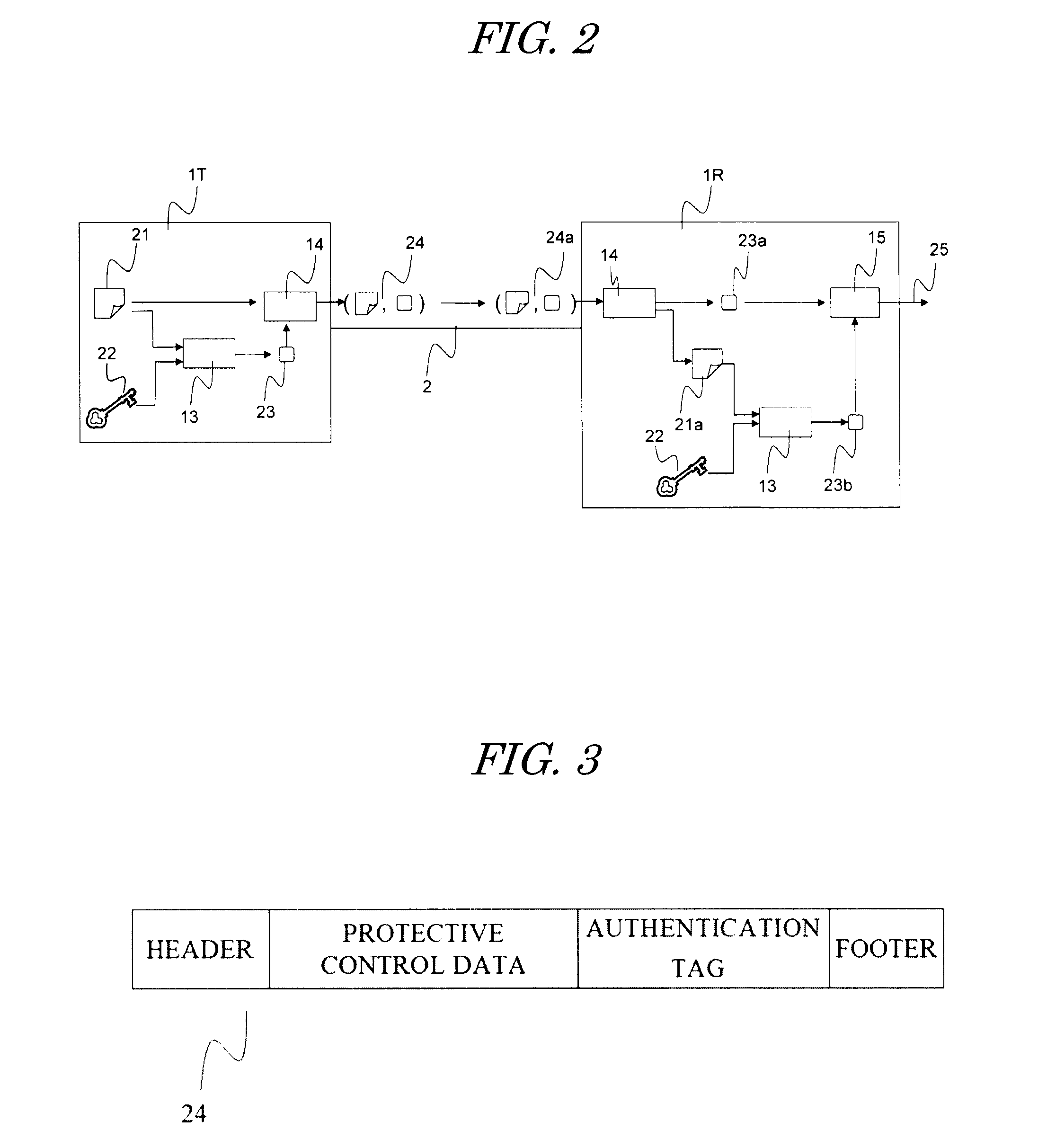
Protective-control measuring system and device and data transmission method
InactiveUS20120019355A1Easily appliedHighly secure and reliableElectric signal transmission systemsMultiple keys/algorithms usageData transmissionControl measure
According to one embodiment, when sending a transmission target main data 21, an authentication-tag generator unit 13 generates an authentication tag 23 by using a main data 21 and a key data 22 stored in a key-data storage unit 12. A transmitter / receiver unit 14 adds the authentication tag 23 to the main data 32 sends as a transmission data. When receiving the received data 24a, the transmitter / receiver unit 14 divides the received data into a main data 21a and an authentication tag 23a. The authentication-tag generator unit 13 generates an authentication tag 23b for comparison. A received-data authentication unit 15 determines whether or not those the received authentication tag 23a and the authentication tag for comparison 23b match with each other. A different key data is used every time upon the authentication-tag generation and use time of each key data during a set period is restricted.
Owner:NAT UNIV CORP YOKOHAMA NAT UNIV +1
Method and system for asymmetrically encrypting .ZIP files
InactiveUS20050081034A1Flexible useRaise security concernsKey distribution for secure communicationEncryption apparatus with shift registers/memoriesMultiple methodsKey management
Owner:PKWARE
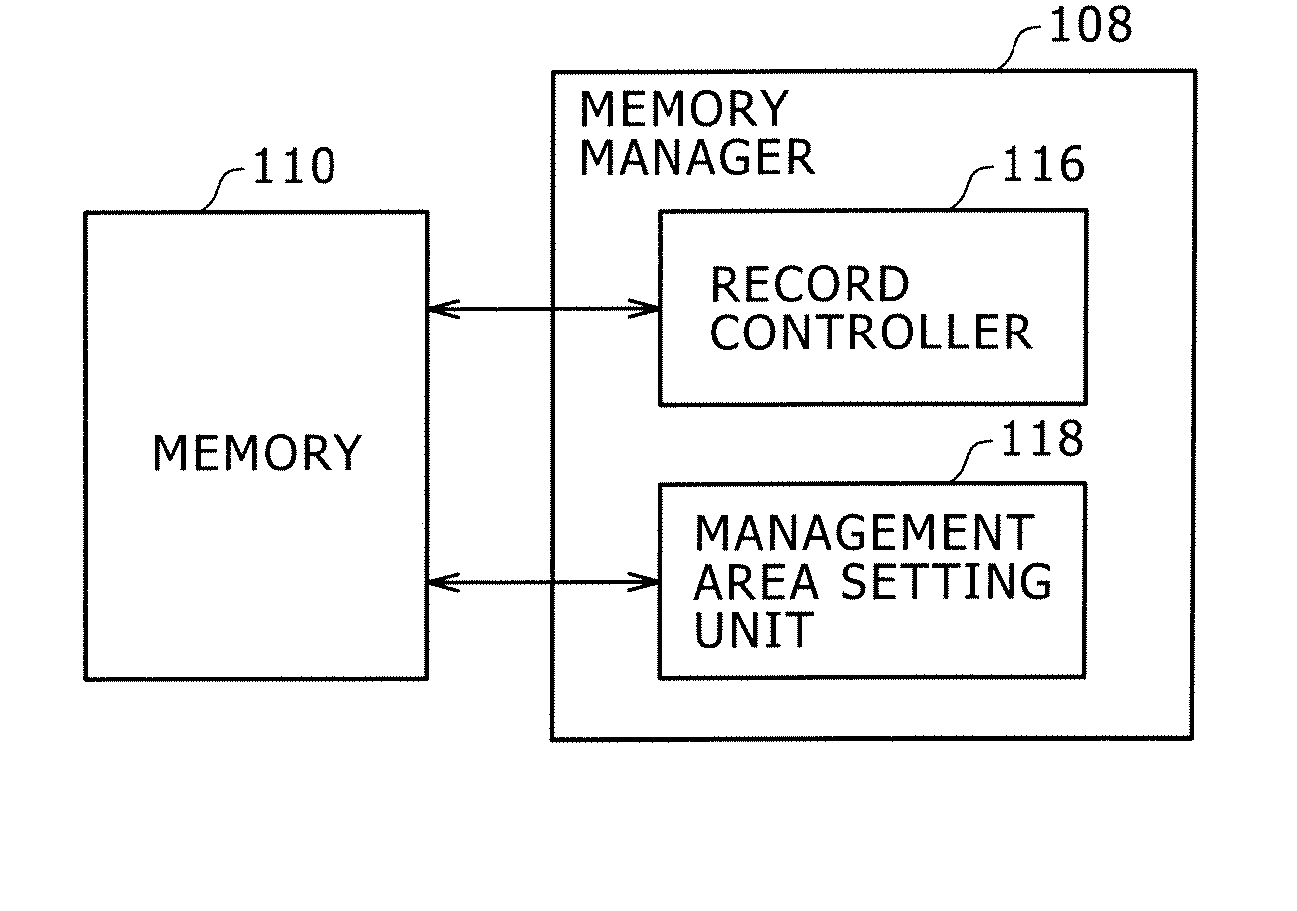
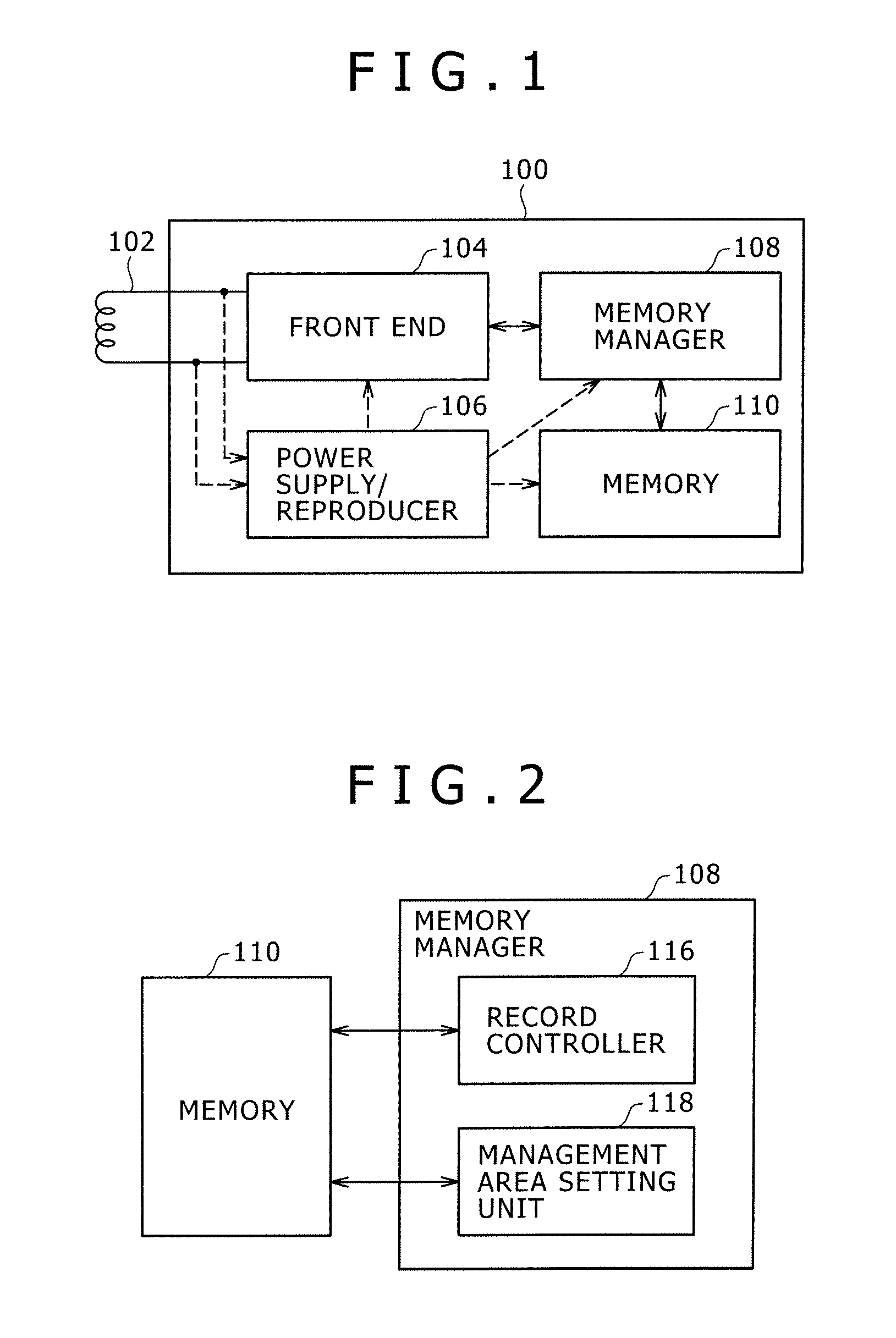
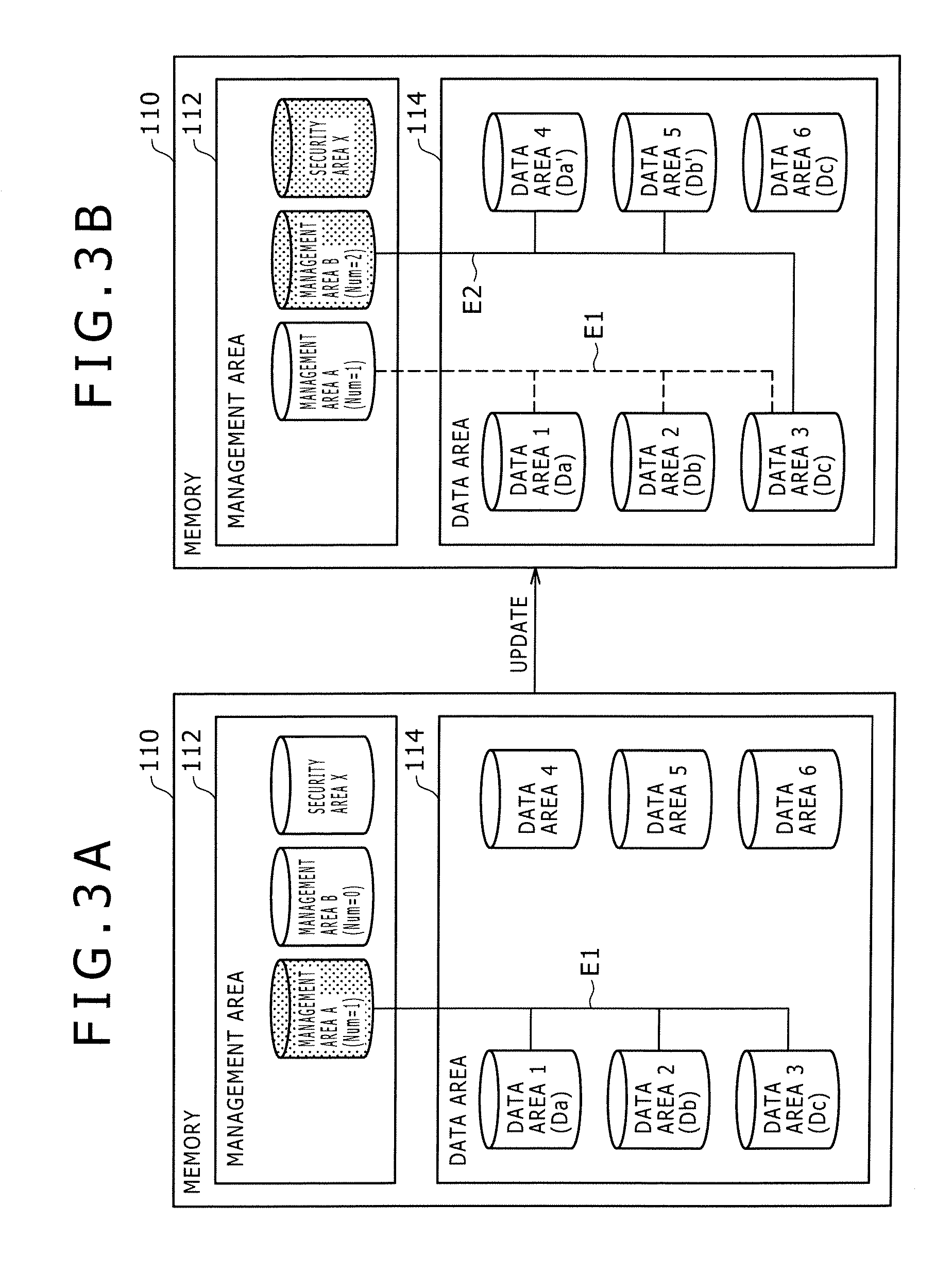
Data Storage Device, Memory Managing Method, and Program
InactiveUS20070274302A1Reliably storing dataReliable updateMultiplex system selection arrangementsError detection/correctionTerm memoryData store
A data storage device includes a memory, a record controller, and a management area setting unit. The method has first and second management areas for recording address information indicative of valid data areas, and a security area for recording information corresponding to address information recorded in either one of the first and second management areas. The record controller rewrites information recorded in the security area after the address information recorded in either one of the first and second management areas has been updated, into information corresponding to the updated address information. The management area setting unit sets either one of the first and second management areas as a valid management area based on the information recorded in the security area.
Owner:FELICA NETWORKS INC
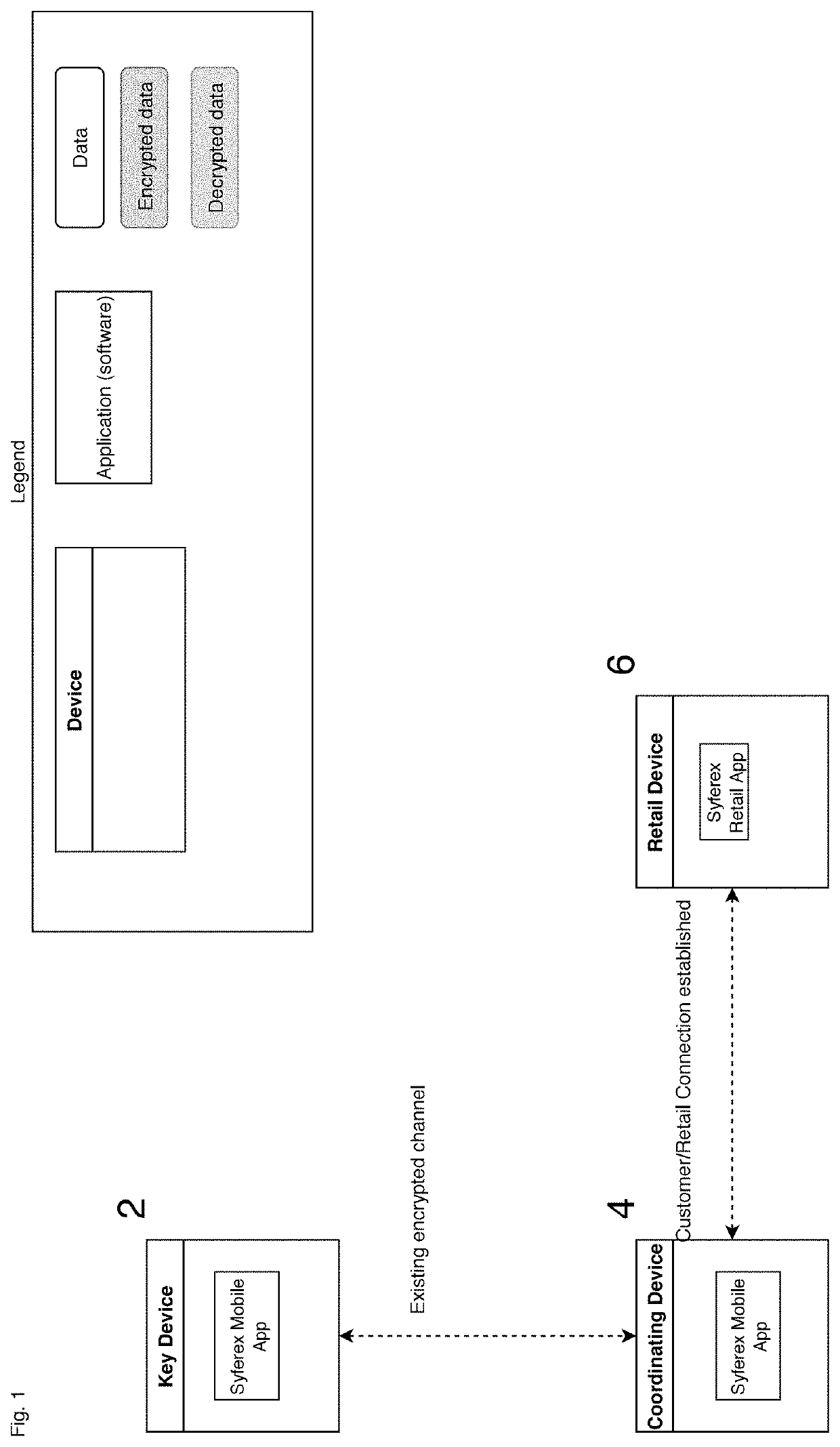
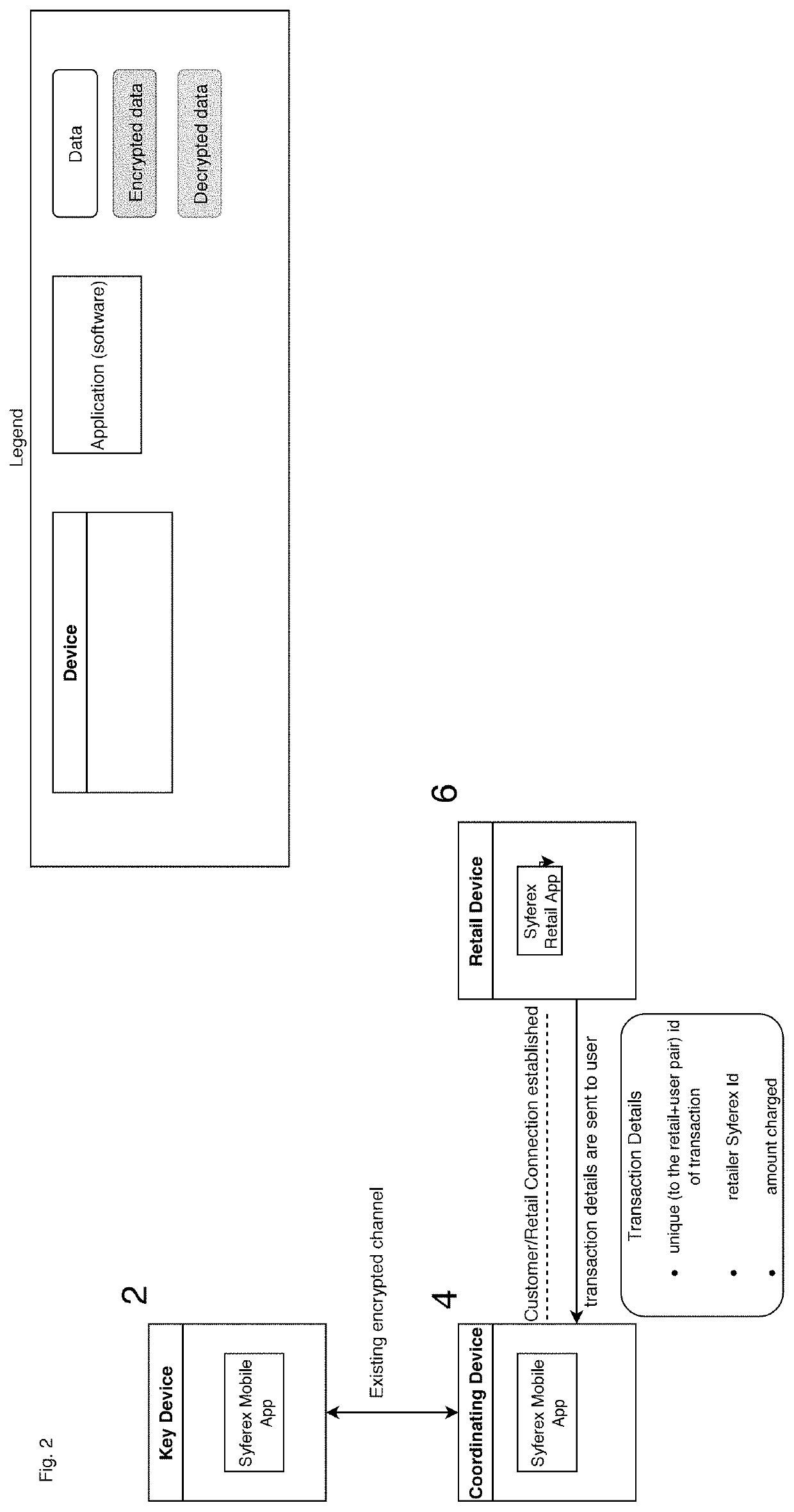
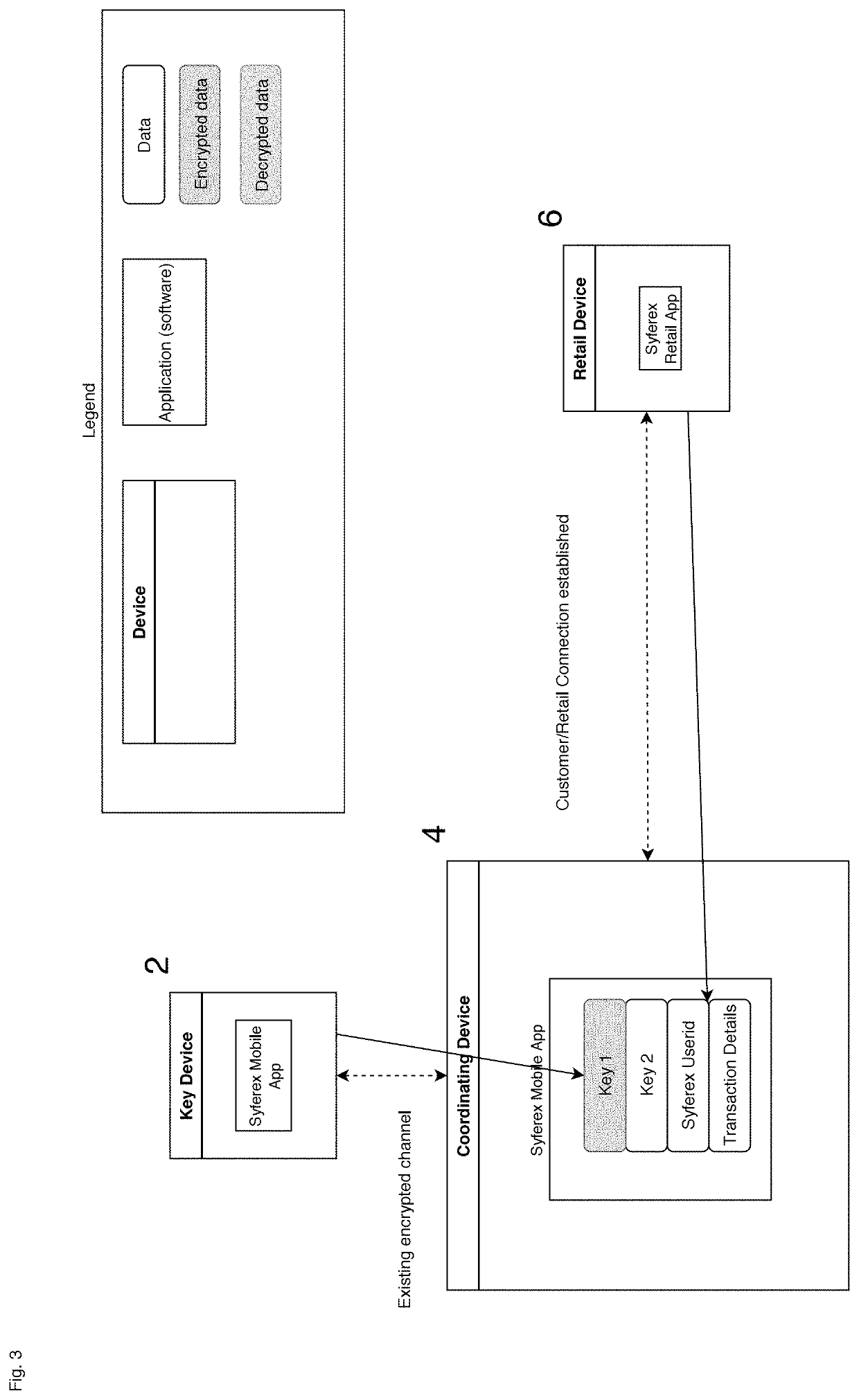
Authentication system using paired, role reversing personal devices
ActiveUS20190349196A1Improve securityImprove simplicityKey distribution for secure communicationMultiple keys/algorithms usageCryptographic key generationAuthentication system
An authentication system is provided for authenticating users in accordance with an encryption / decryption algorithm using first and second separately unique encryption keys that are time variable and are uniquely associated with each user, having a first user controlled computing device under the control of the user for generating said first encryption key using an encryption key generating algorithm. The first user controlled computing device includes a key transmitter for transmitting wirelessly within the immediate vicinity of the user the first encryption key, a second user controlled computing device, operating as a coordinating device under the control of the user, for generating the second encryption key using the encryption key generating algorithm. The second user controlled computing device includes a key receiver for receiving the first encryption key.
Owner:SYFEREX LLC
Method and system for multiple symmetric decryption of .ZIP files
InactiveUS20050086476A1Flexible useRaise security concernsEncryption apparatus with shift registers/memoriesDigital data processing detailsMultiple methodsKey management
The present invention provides a method of integrating existing strong encryption methods into the processing of a .ZIP file to provide a highly secure data container which provides flexibility in the use of symmetric and asymmetric encryption technology. The present invention adapts the well established .ZIP file format to support higher levels of security and multiple methods of data encryption and key management, thereby producing a highly secure and flexible digital container for electronically storing and transferring confidential data.
Owner:PKWARE
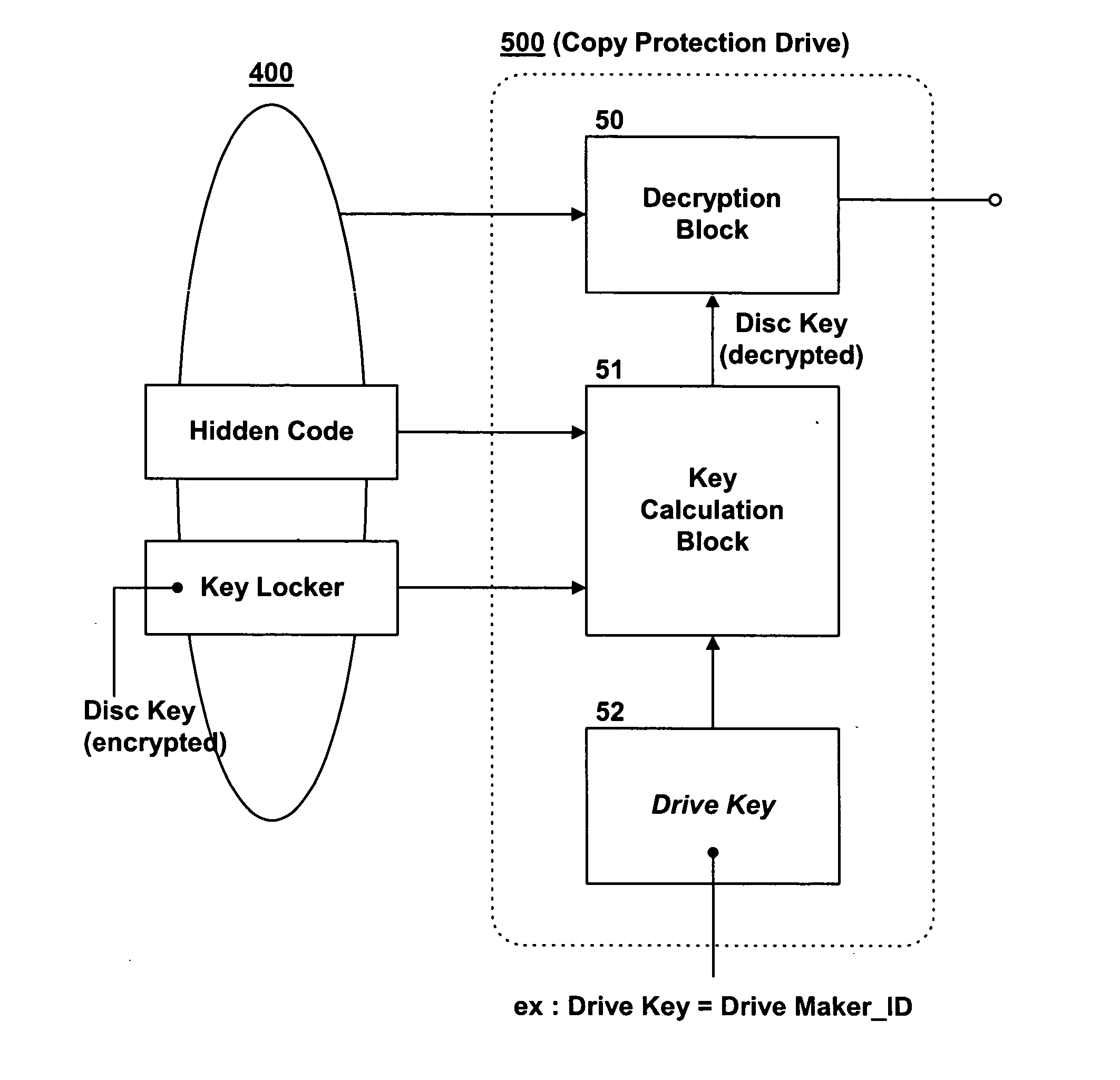
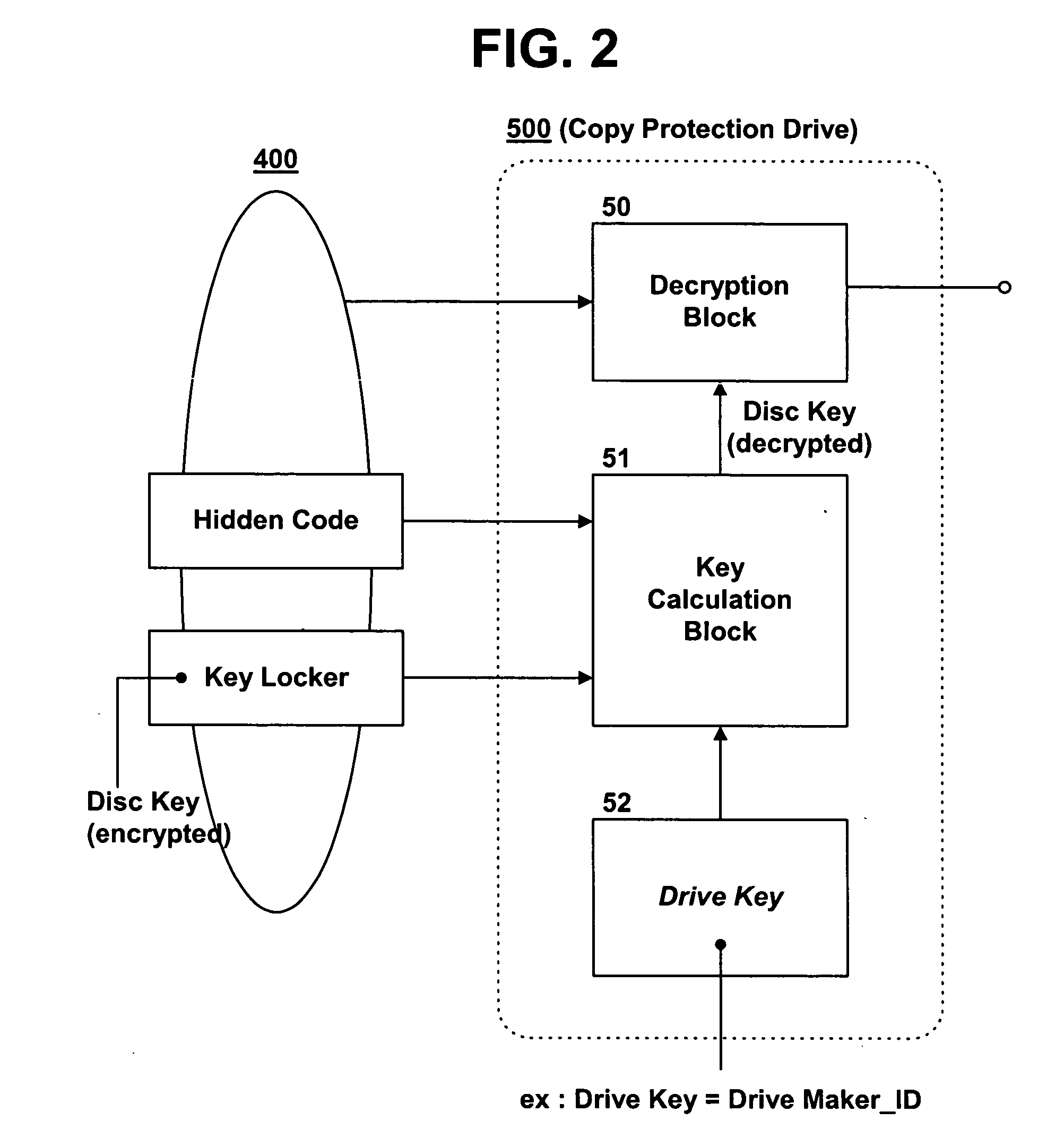
Method for managing copy protection information of recording medium
InactiveUS20040213111A1Reduce risk of exposureImprove reliabilityKey distribution for secure communicationRecord information storageComputer hardwareCopy protection
A method for managing copy protection information of a recording medium is disclosed. Copy protection information for decrypting A / V data encrypted and recorded in a data area of an optical disc such as a CD, a DVD or a BD is recorded in a key locker in the optical disc. A first key value for reading the copy protection information is recorded in a specific area of the optical disc, and a second key value for reading the copy protection information is managed in an optical disc drive or in an application. To reproduce the A / V data in the optical disc, the copy protection information recorded in the key locker is read and decrypted by a combination of a hidden code (having the first key value) recorded in the optical disc and a drive or application key (having the second key value) managed in the optical disc drive or application. This significantly improves the security of the copy protection information.
Owner:LG ELECTRONICS INC
Secure diamond smart cards and exchange systems therefor
InactiveUS20190357648A1Improve reliabilityHighly secureDigital data authenticationBuying/selling/leasing transactionsCredit cardTamper resistance
A tamper-proof diamond package comprises a package body; at least one chip embedded in the package body and at least one antenna configured to enable communication with the chip; anti-counterfeiting visual impressions on the package body; a diamond pouch formed at a predetermined section within the package body; and one or more diamonds located inside the diamond pouch and an outer covering encasing the package body and configured to reveal any tampering with the one or more diamonds located in the diamond pouch. The diamond package can be credit card shaped and also contain serial number and website information and provide nominal dollar values. An associated diamond exchange system utilizes the diamond packages and provides a registration server which stores unique identifying information that enables interrogating the individual diamond packages and checking their authenticity with the registration server.
Owner:GEMSHARES
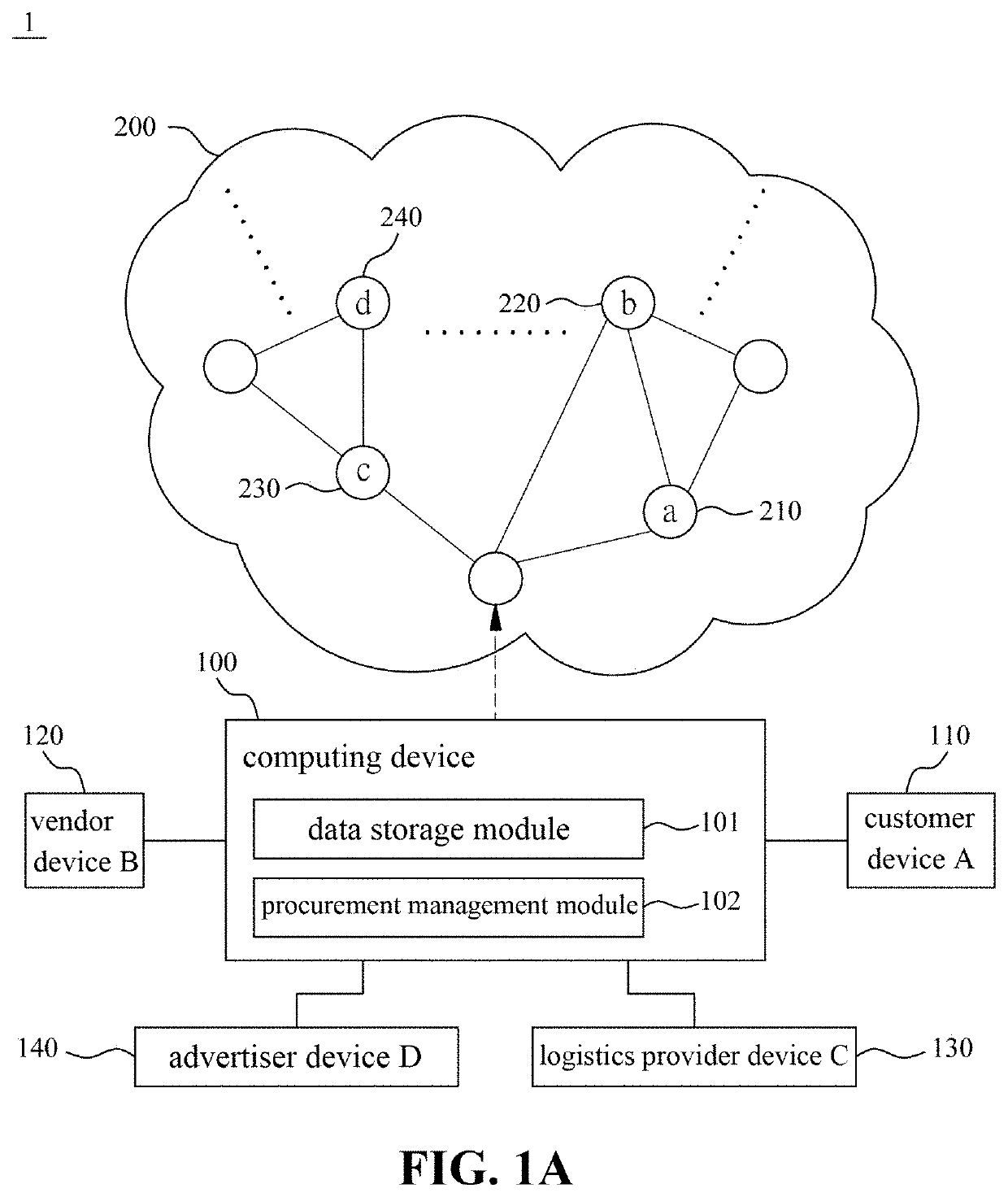
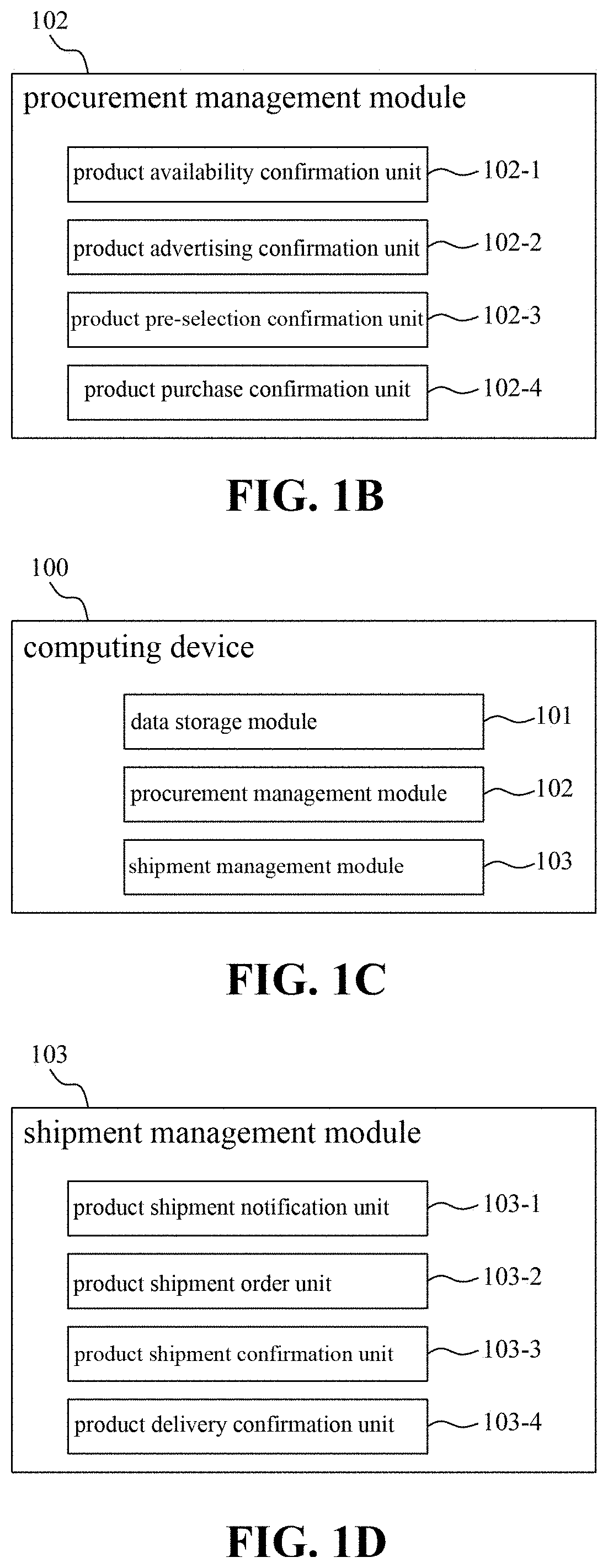
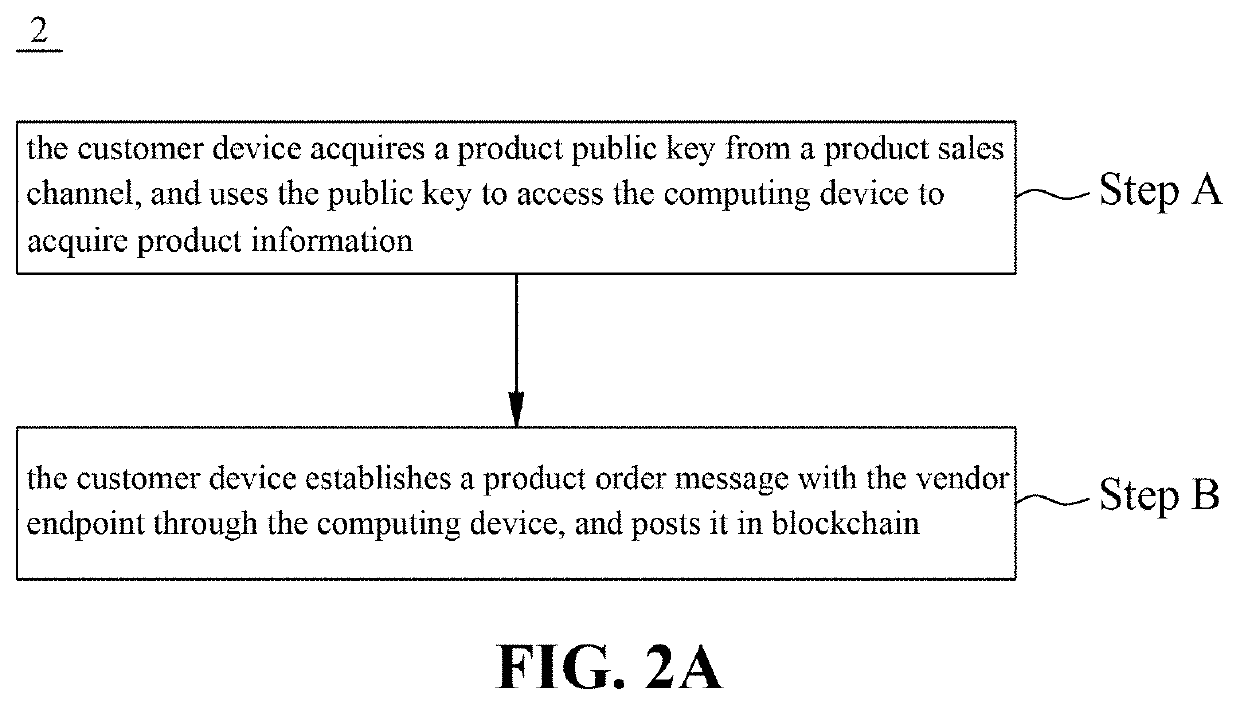
Blockchain-based electronic transaction system free of sales platform and method thereof
InactiveUS20200250665A1Improve reliabilityHighly securePayment protocolsEngineeringPurchasing management
A blockchain-based electronic transaction system free of sales platform comprises a computing device. The blockchain includes a customer endpoint and a vendor endpoint, the customer endpoint and the vendor endpoint corresponding to a customer device and a vendor device, respectively. The computing device comprises a data storage module and a procurement management module. The data storage module stores at least one product sales channel public key and at least one product data. The customer device is connected to the computing device through the blockchain by a product public key of a product sales channel, and acquires the product data from the data storage module. The procurement management module is configured to enable the customer device to establish a product order message with the vendor endpoint, and to broadcast the message in the blockchain. The product order message is encrypted and authenticated by a customer private key.
Owner:ELAND BLOCKCHAIN FINTECH INC
Method and system for mixed symmetric and asymmetric decryption of .ZIP files
InactiveUS20050086475A1Flexible useRaise security concernsEncryption apparatus with shift registers/memoriesPublic key for secure communicationAsymmetryMultiple methods
The present invention provides a method of integrating existing strong encryption methods into the processing of a .ZIP file to provide a highly secure data container which provides flexibility in the use of symmetric and asymmetric encryption technology. The present invention adapts the well established .ZIP file format to support higher levels of security and multiple methods of data encryption and key management, thereby producing a highly secure and flexible digital container for electronically storing and transferring confidential data.
Owner:PKWARE
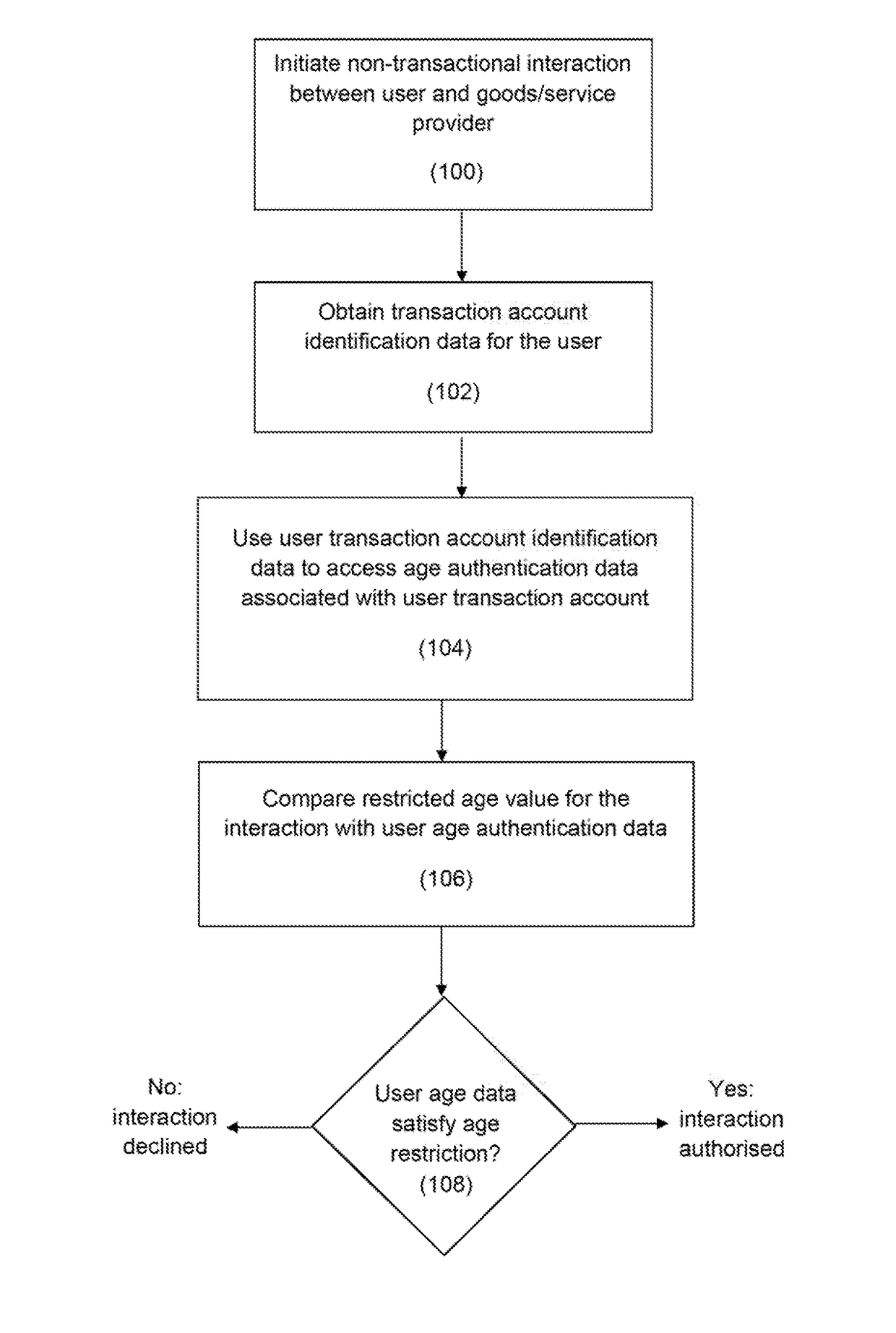
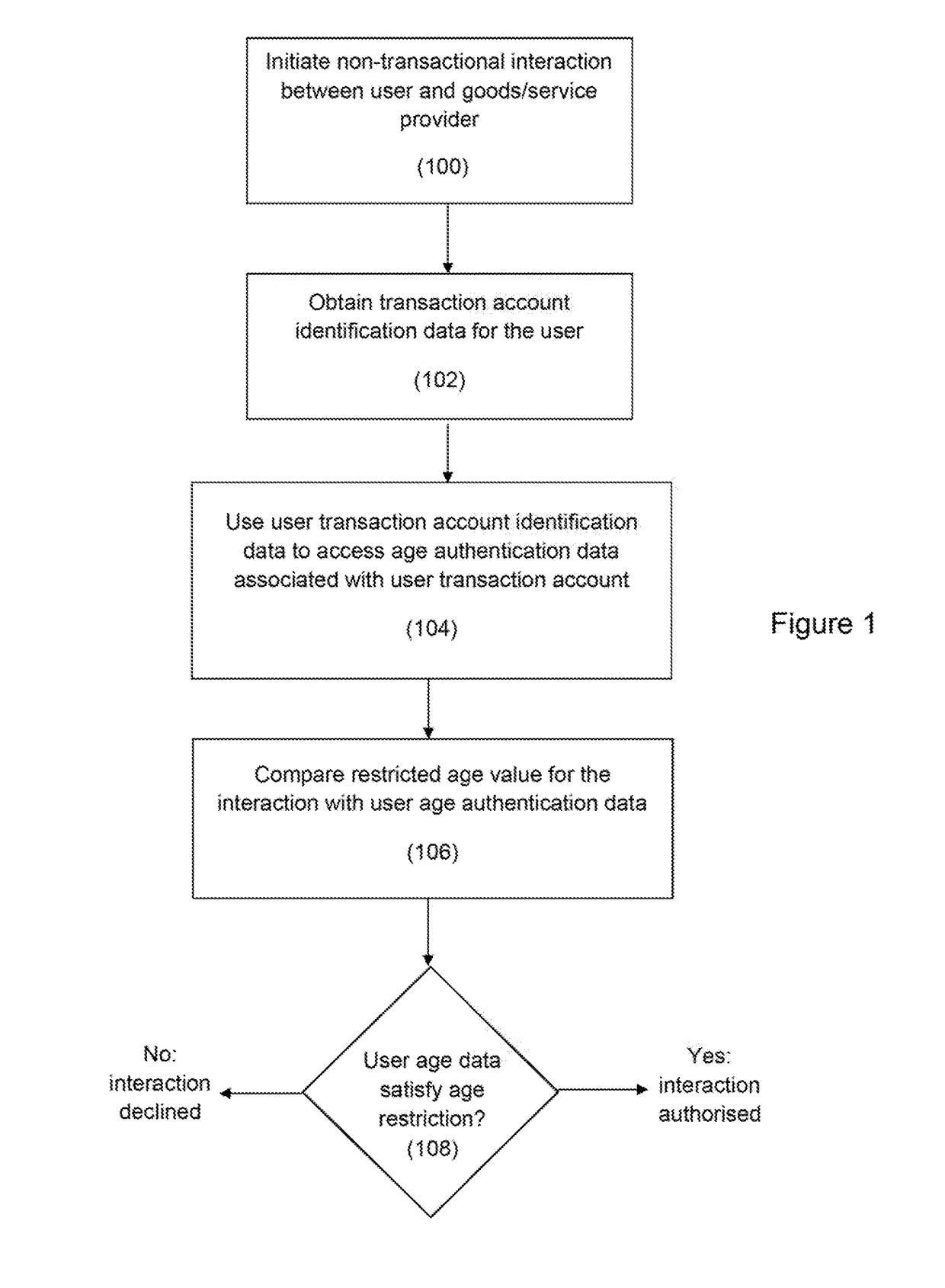
Methods, devices and systems for authorizing an age-restricted interaction
InactiveUS20170124561A1Highly secureSimple methodBuying/selling/leasing transactionsCoin/paper handlersAuthorizationInternet privacy
Methods, a user device and a server system for authorizing an age-restricted non-transactional interaction between a user and a provider are disclosed. Transaction account identification data for the user are obtained. The user transaction account identification data are used to access age authentication data associated with a transaction account of the user, and an authorization for the user is determined by comparing a restricted age value for the interaction with the age authentication data associated with the user transaction account.
Owner:MASTERCARD INT INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com