Method and apparatus for accessing Web services and URL resources for both primary and shared users over a reverse tunnel mechanism
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
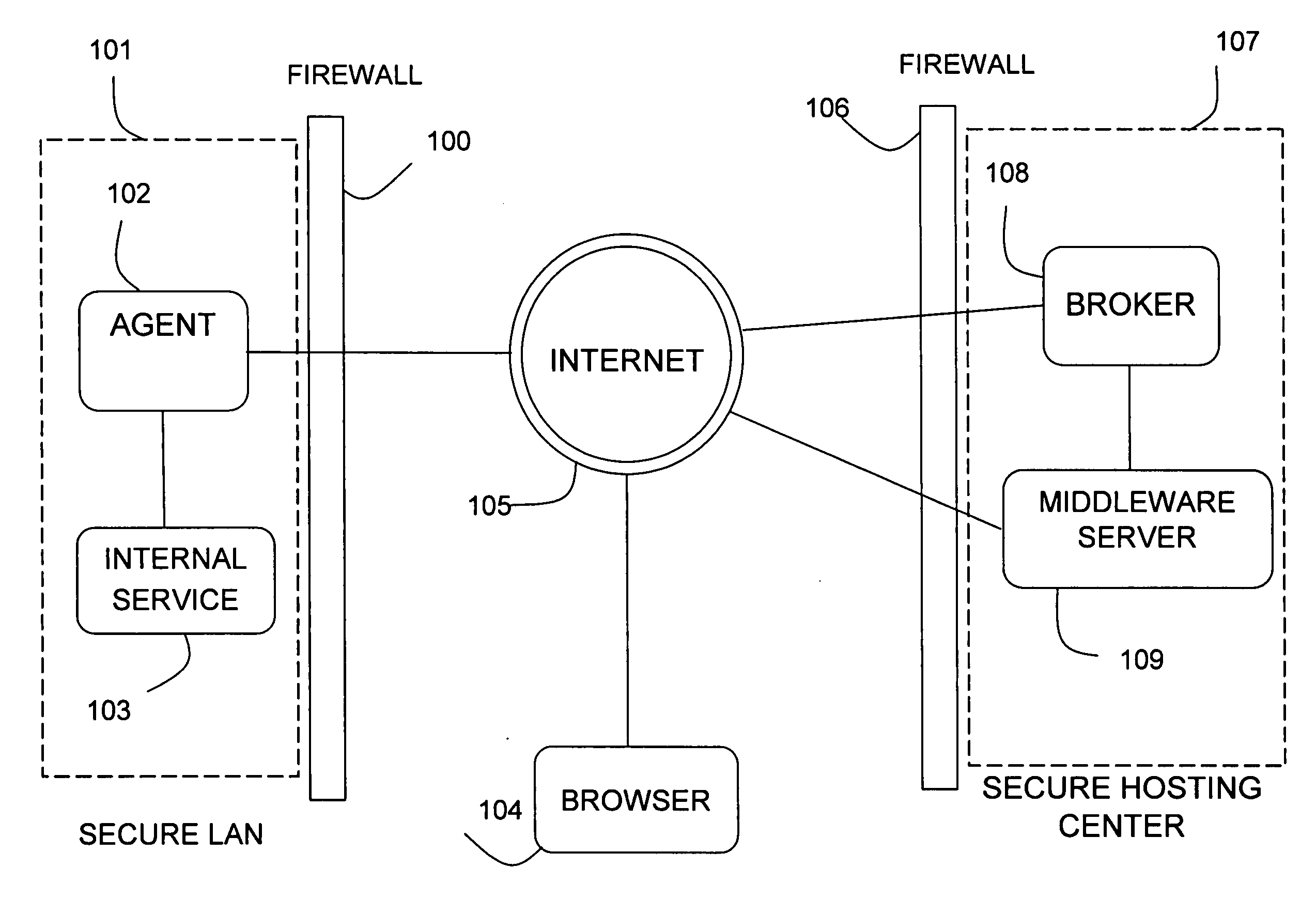
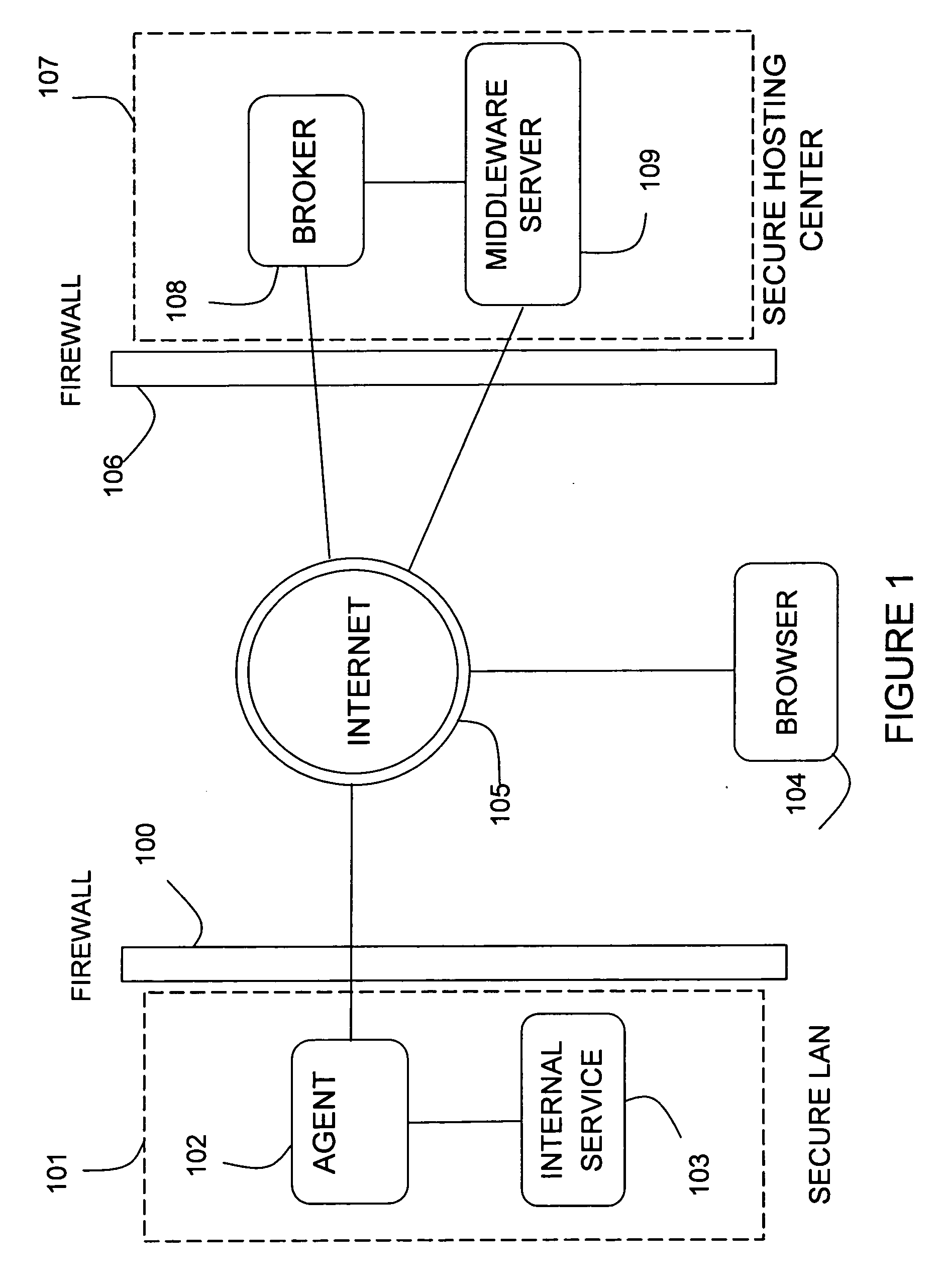
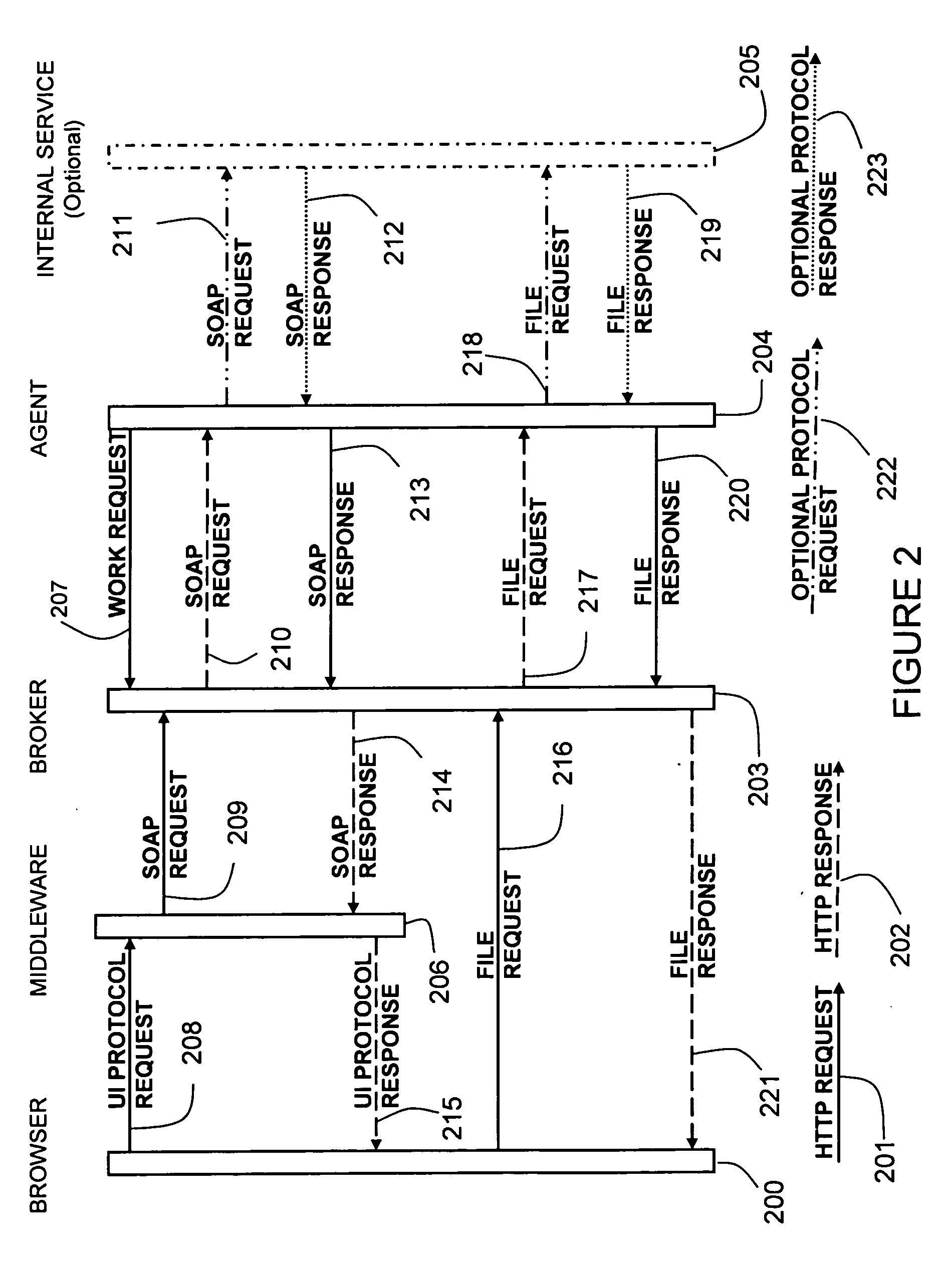
[0024] A method and apparatus for securely accessing Web services and URL resources located within a protected environment, such as a corporate LAN, from outside that environment are described. In the following description of the method and apparatus, many specific details are provided to offer a more thorough explanation of embodiments of the invention. To one skilled in the art, however, it will be clear that the invention may be accomplished without these specific details. In other cases, obvious elements have not been described at length, so as not to render the invention ambiguous.
Terminology
[0025] Throughout the following explanation, mention of a “user” may refer either to a person interacting with a computer interface, to one or more software program elements (such as a user interface), or both. A program element may be any element of a computer program, whether that executes remotely or locally, as that element interacts with an embodiment or embodiments of the invention...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com