Method and system for realizing file sharing access control based on protocol proxy
A file sharing and access control technology, applied in transmission systems, electrical components, etc., can solve the problems of cumbersome authorization, no file access log, and helpless enterprise managers, and achieve the effect of eliminating cross-authority access.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
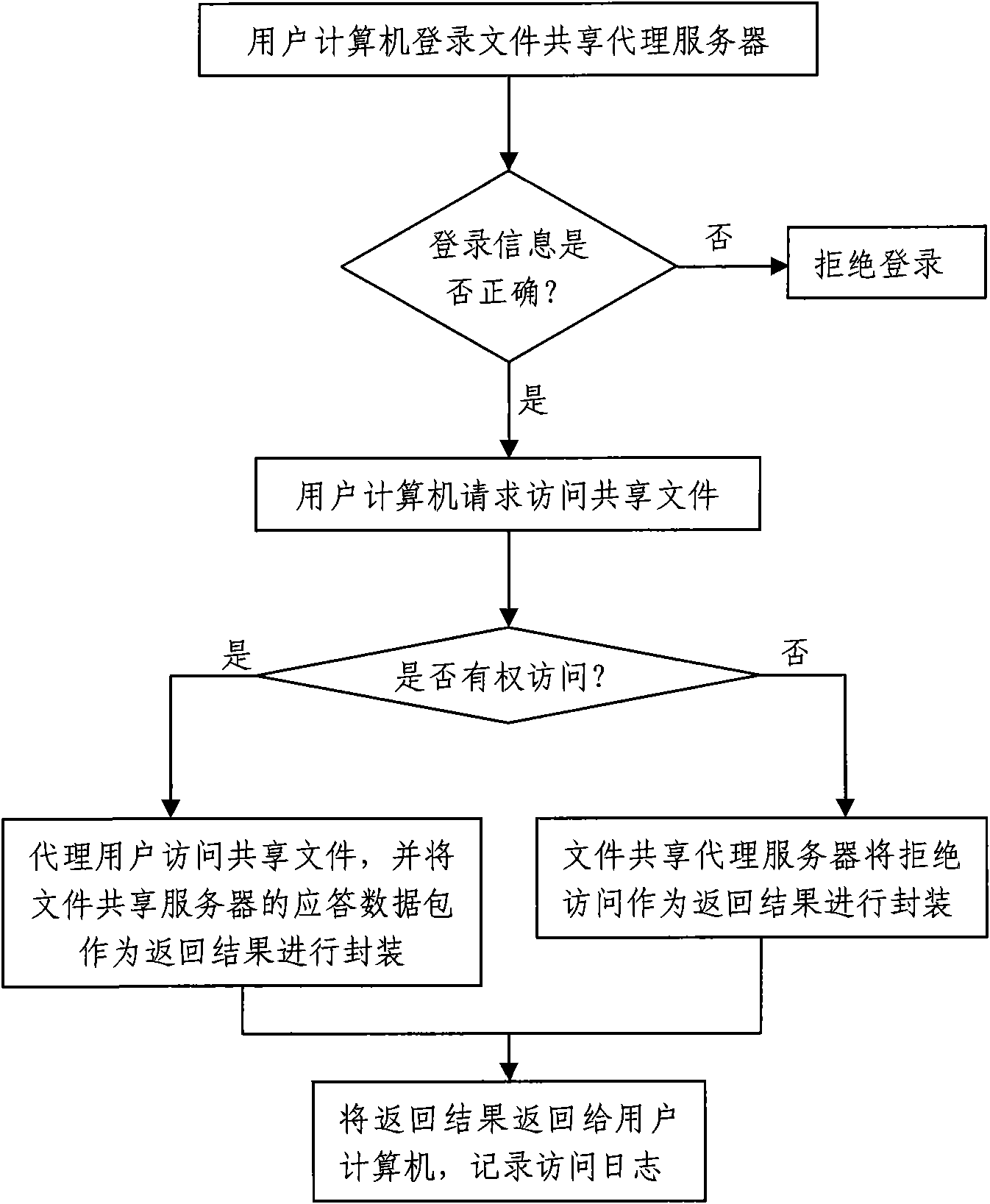
[0056] The protocol proxy-based implementation of the file sharing access control method proposed by the present invention is described as follows in conjunction with the accompanying drawings and embodiments.
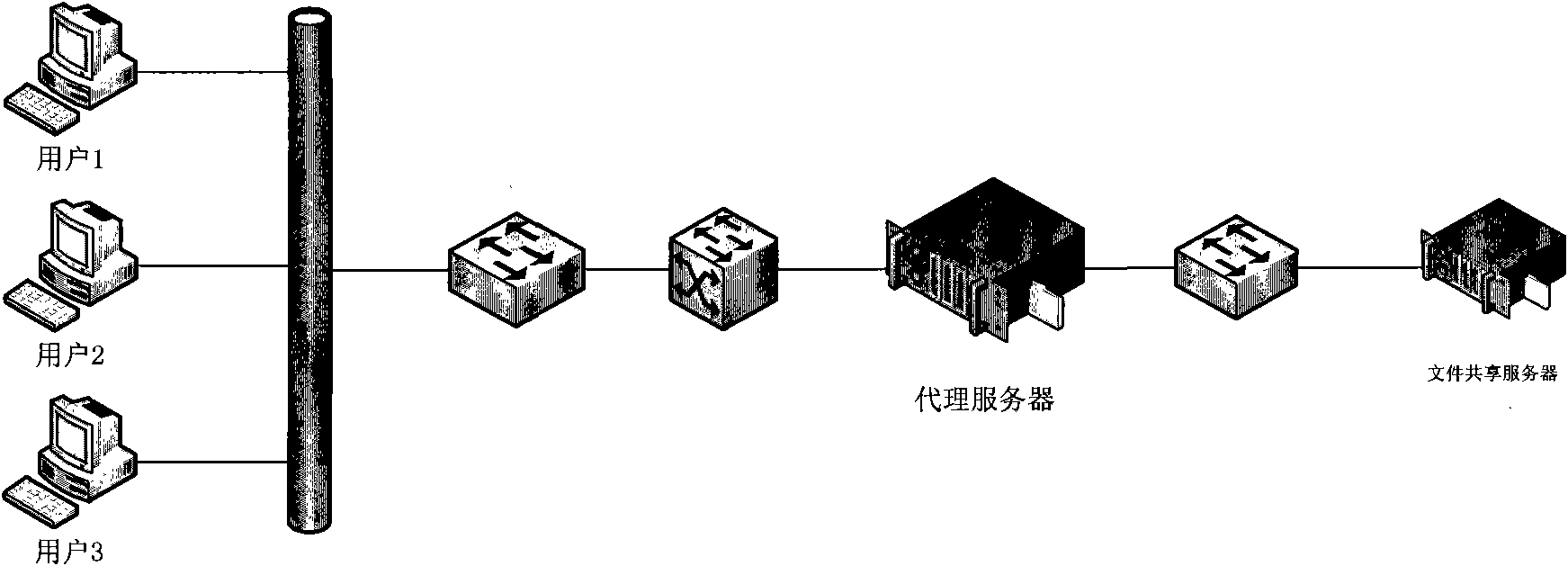
[0057] Such as figure 1 As shown, a file sharing proxy server is added between the original user computer and the file sharing server, figure 1 Among them, three user computers are connected to the file sharing proxy server, and the file sharing proxy server is connected to the file sharing server, and the access control of the user computers to the files in the file sharing server is realized through the file sharing proxy server.
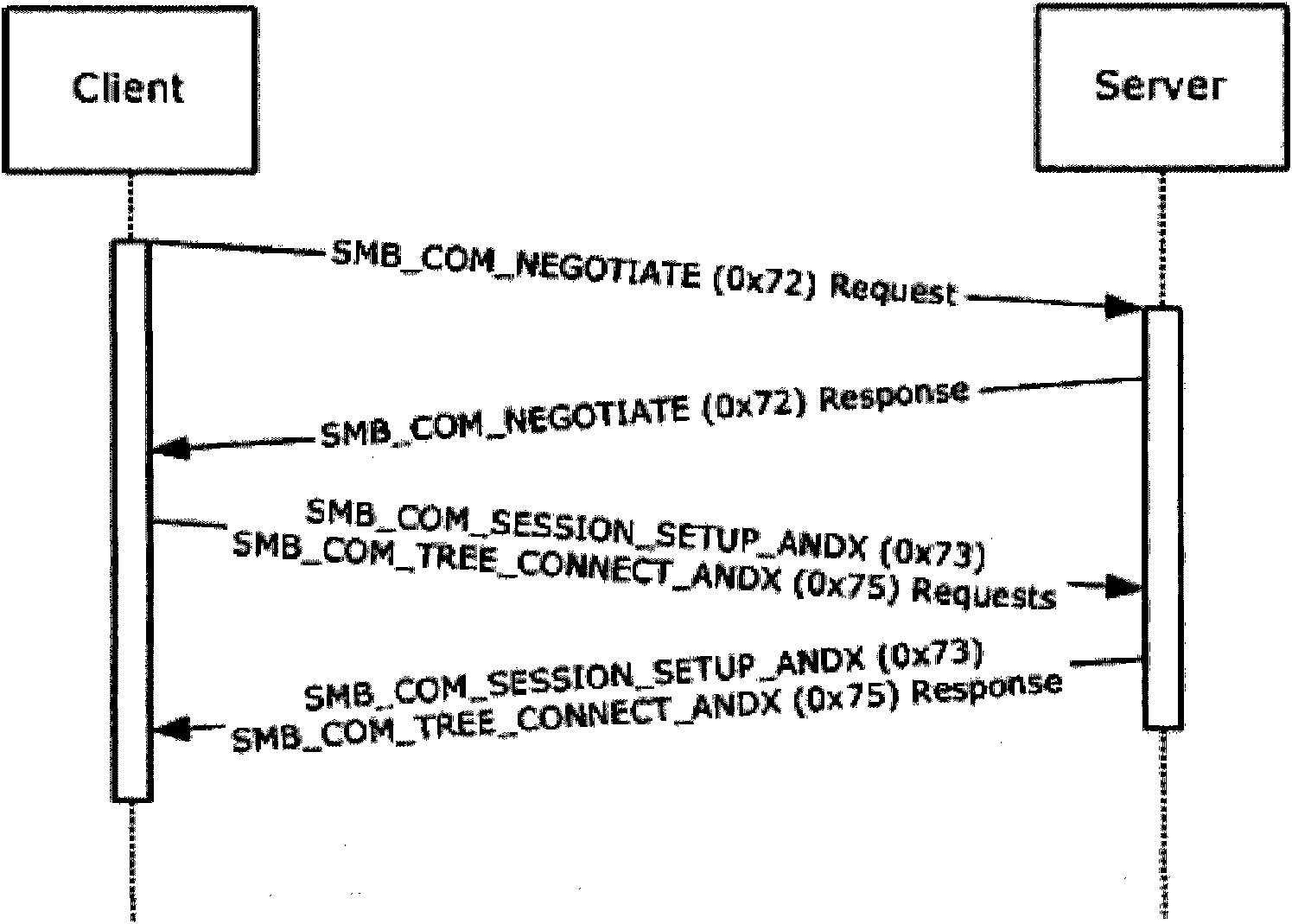
[0058] Before the user computer accesses the shared files, it is necessary to set the IP address of the proxied file sharing server and the login information of the user computer, including the login ID and password; then establish a file sharing proxy server by establishing a connection between the client and the server in the CIFS prot...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com