Network application encrypted traffic recognition method and device based on protocol attributes
A network application and traffic identification technology, applied in electrical components, transmission systems, etc., can solve the problems of reduced classification and identification accuracy of encrypted network traffic, unsatisfactory application fingerprint differences, and inability to achieve high accuracy, etc. Effects of accuracy and recognition precision, likelihood reduction, low false positive and false positive rates
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
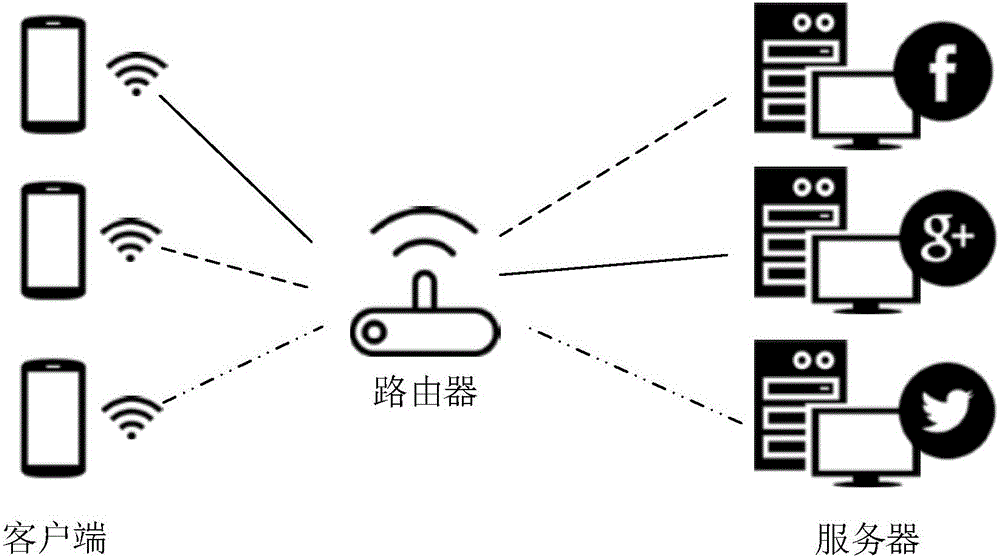
[0060] The principle and structure of the data set acquisition in the "a method for identifying network application encrypted traffic based on protocol attributes" in this embodiment are as follows: figure 1 shown. The communication between the client and the application server is accomplished through continuous addressing, topology and delivery within the Internet through network flows. Deploy a data set acquisition platform based on network packet capture tools such as Wireshark or Tshark on network link nodes such as gateways, monitor and store encrypted network flows passing through this node, and construct offline training data sets. Due to the different configurations of SSL / TLS protocol clients, there are certain differences in the encrypted network flow from the client to the server corresponding to the same behavior operation of the same network service or application, which is not convenient for modeling, and only one-way flow is required for modeling , and does no...
Embodiment 2
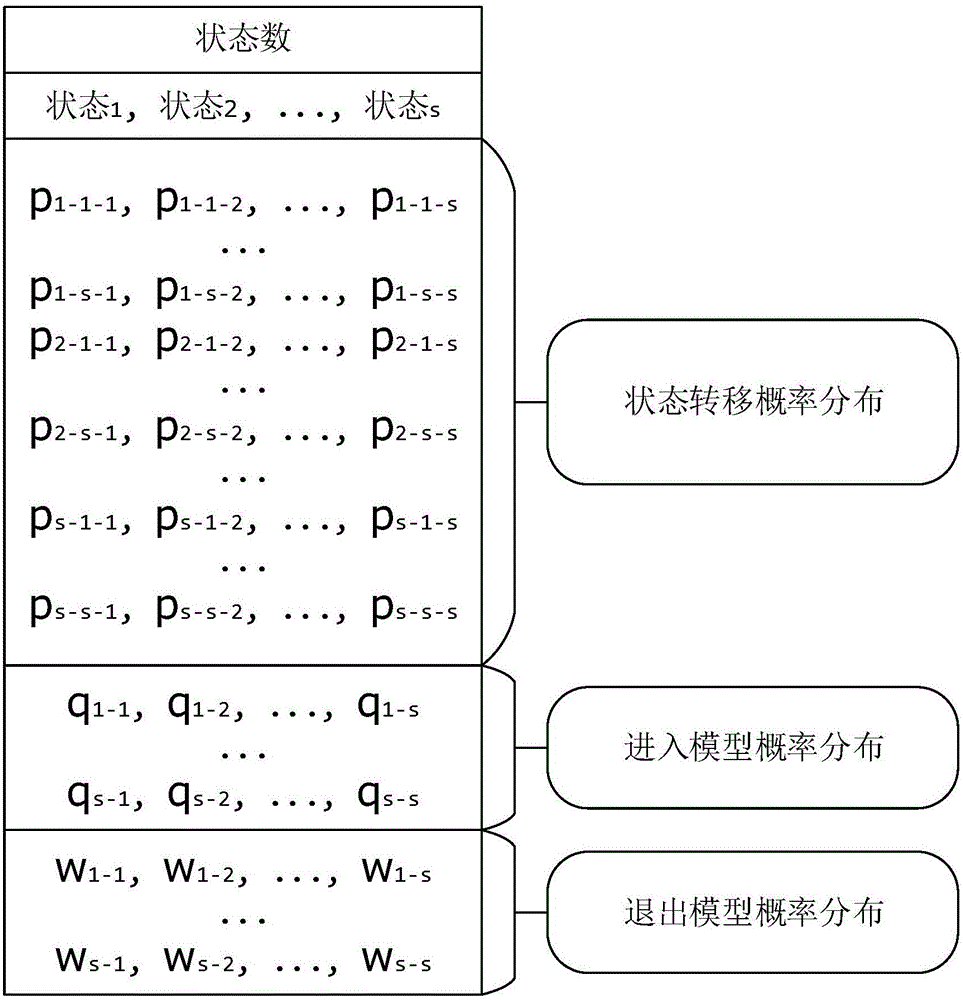
[0067] The process of establishing a message type fingerprint based on a second-order Markov chain in the "A Method for Identifying Network Application Encrypted Traffic Based on Protocol Attributes" in this embodiment is described as follows:
[0068] We assume that there exists a discrete random variable X t , where t=t 0 ,t 1 ,...,t n ∈T, T is the time set, representing the time sequence relationship, the random variable X t The corresponding value of i t ∈ {1,...,s}, i t Represents a single message type in an SSL / TLS protocol session or a message type sequence in a TCP segment, and it is assumed to include S message types or sequences in total.
[0069] We assume that X t Represents a second-order Markov chain, that is, when we predict the current state, we need to consider the influence of the first two states. The formal description is as follows:
[0070] P ( ...
Embodiment 3
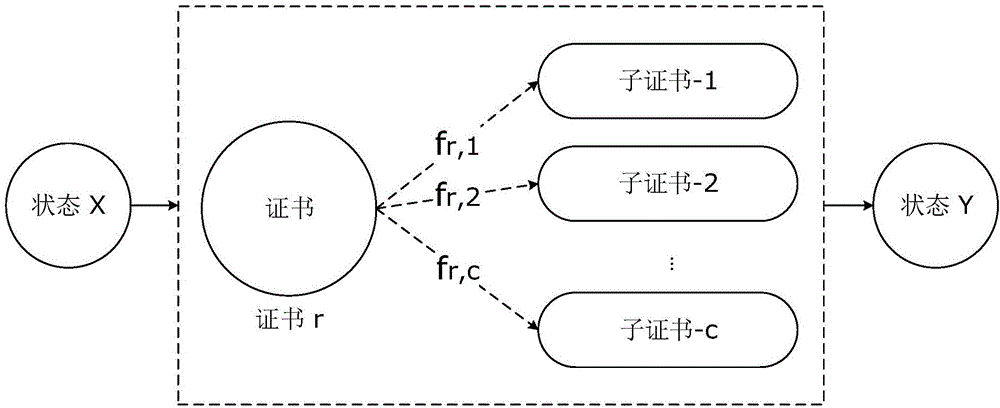
[0084] The process of establishing a message type fingerprint based on certificate length clustering combined with a second-order Markov chain in the "a method for identifying network application encrypted traffic based on protocol attributes" in this embodiment is described as follows. The message type fingerprint modeling based on the second-order Markov chain has been introduced in Embodiment 2, and this embodiment mainly introduces the method of combining certificate length clustering and modeling.
[0085] In fact, we extend the "certificate" message type in the SSL / TLS protocol session. One "certificate" may correspond to multiple "sub-certificates", and a certain Markov chain is from "certificate" to "sub-certificate". The connection path depends on the clustering result of the "certificate" length.
[0086] We cluster the certificate message types of all network services or applications extracted from the offline training set according to their length. Assuming that c ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com