Intrusion detection method for fusion of multiple neutral networks
A technology of network fusion and intrusion detection, applied in the field of intrusion detection of multi-neural network fusion, can solve the problems of the intrusion detection system of the intelligent method of neural network, etc., and achieve the effect of good scalability and good compatibility
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
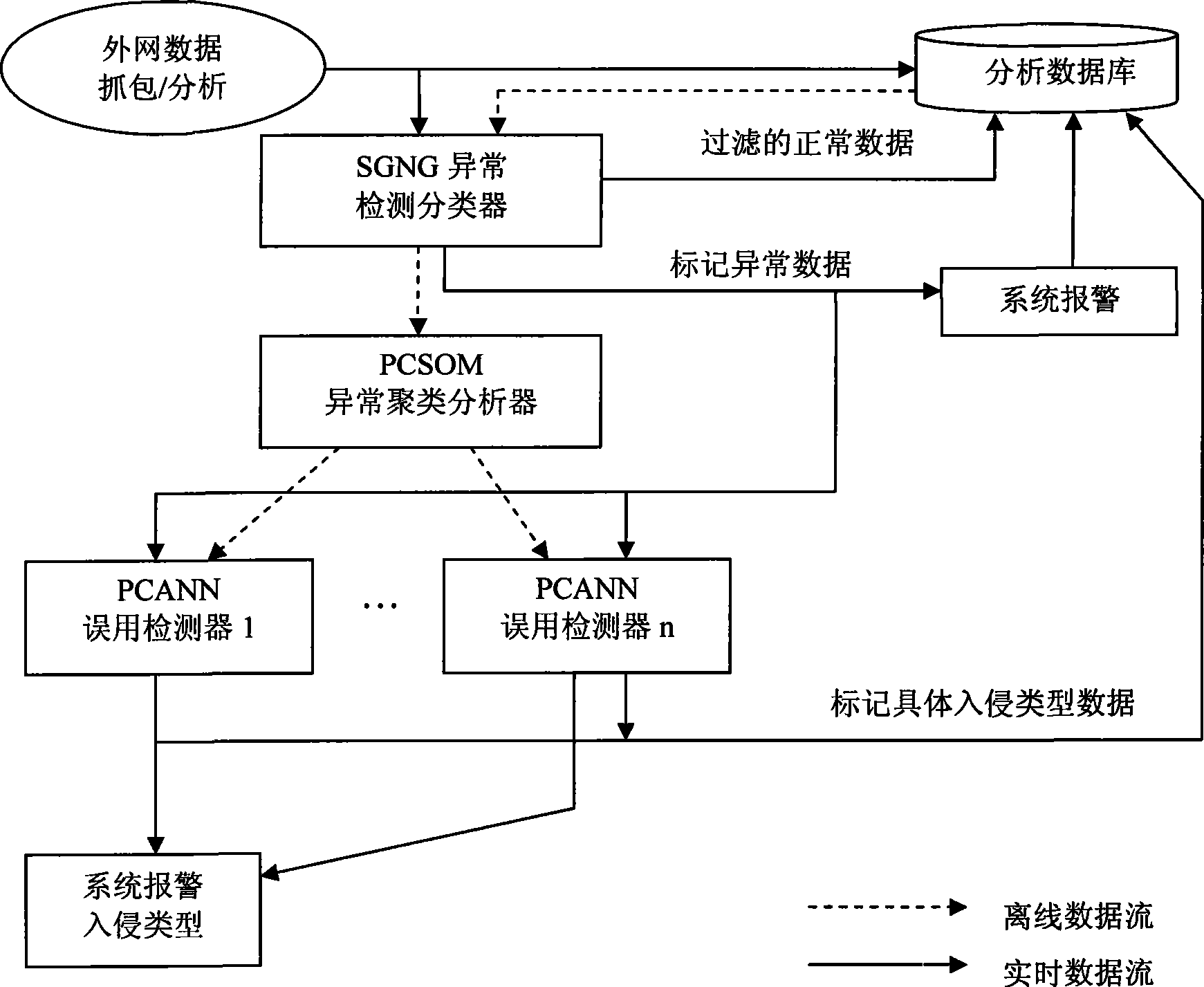
[0035] The present invention will be further described below with reference to the accompanying drawings and embodiments. like figure 1 As shown, the dotted line in the figure represents the offline data flow for training a neural network classifier or cluster analysis, while the solid line represents the online data processing flow.
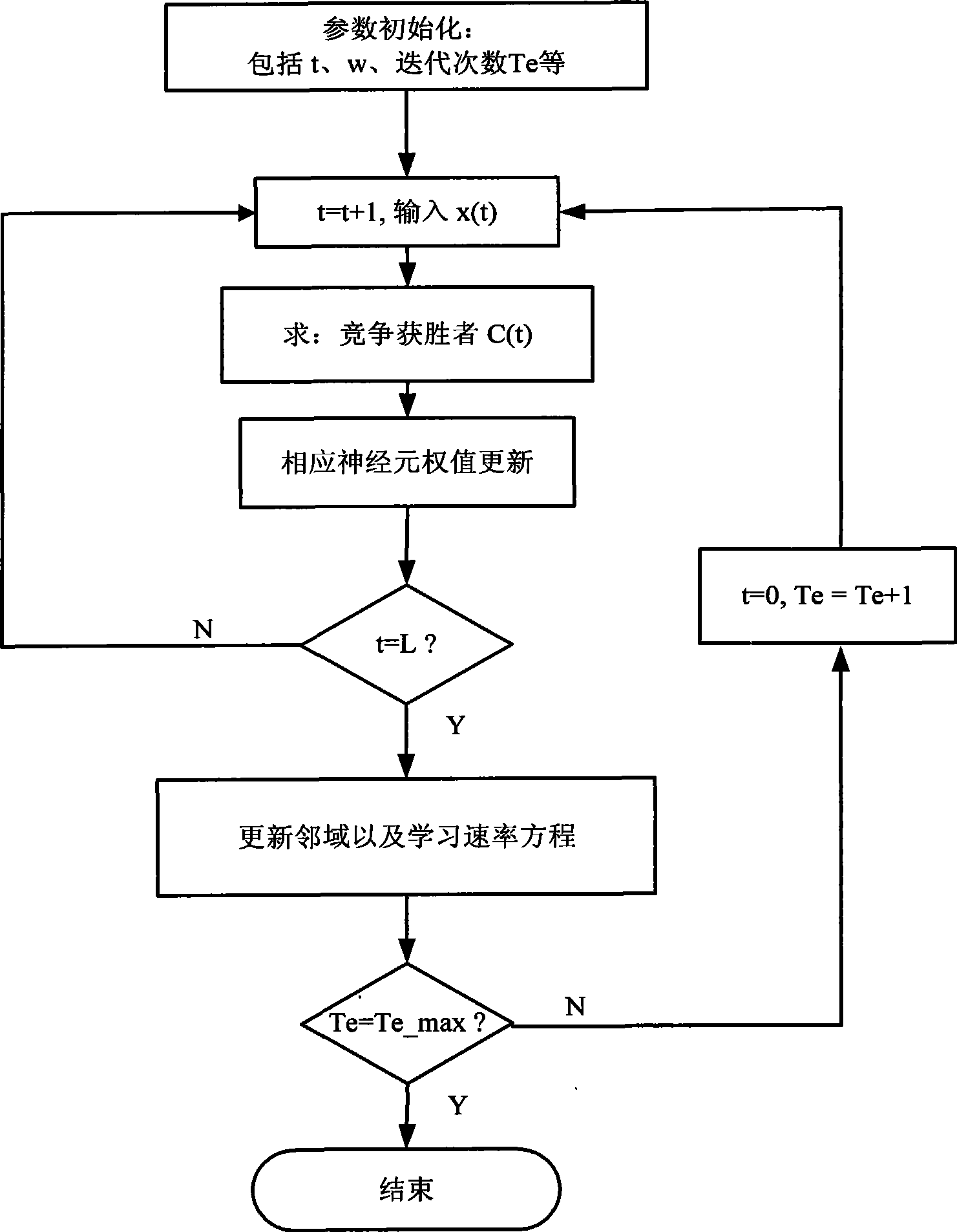
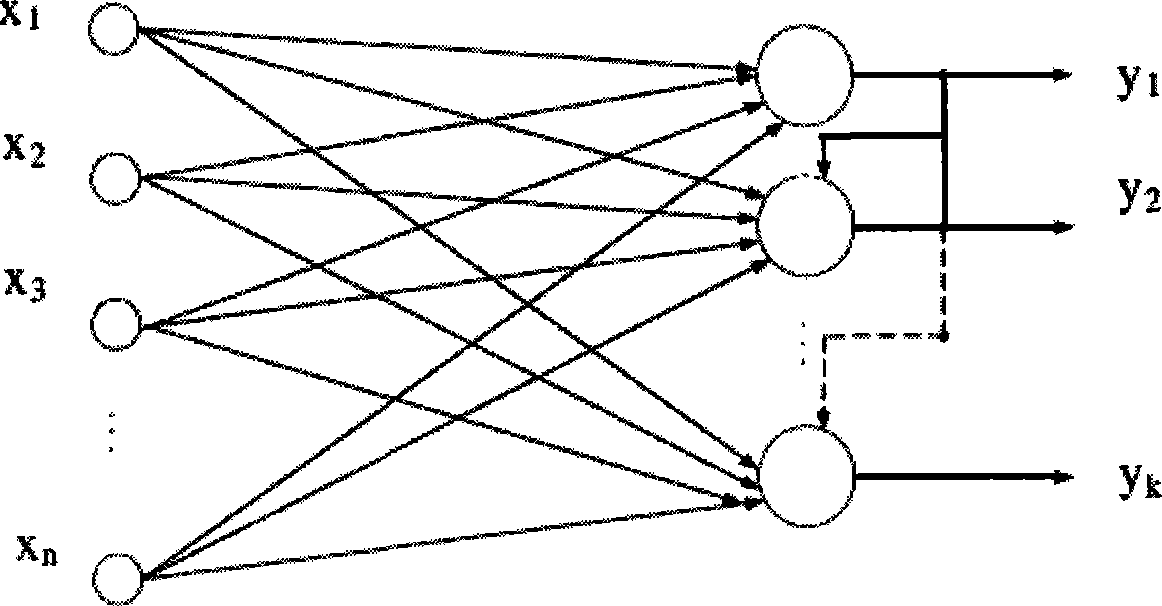
[0036] Among them, the SGNG anomaly detection classifier uses the data collection of the closed network as training data to obtain the normal pattern of network data and behavior, and the training process is supervised training, which performs real-time detection on the open network data collected in real time; the purpose of the SGNG anomaly detection classifier It divides the input network connection data into two categories: normal data and abnormal data. refer to Figure 4 , SGNG anomaly detection classifier is a self-growing neural network model, and the traditional SOM self-organizing network mapping mechanism in different dimensional sp...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com