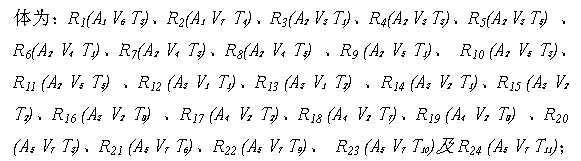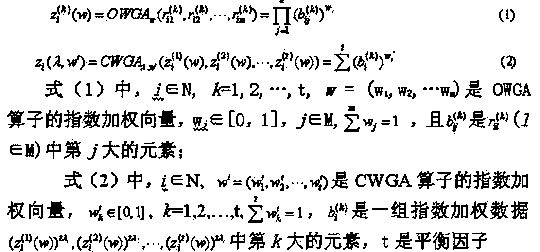Risk assessment algorithm for information system
An information system and risk assessment technology, applied in computing, special data processing applications, instruments, etc., can solve the problems of difficult quantitative operation in risk assessment practice, high subjectivity of assessment algorithms, and impact on the accuracy of results, and achieve a simple index system. , convenient for risk assessment, good use effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0018] Embodiments of the invention: a risk assessment algorithm for an information system,
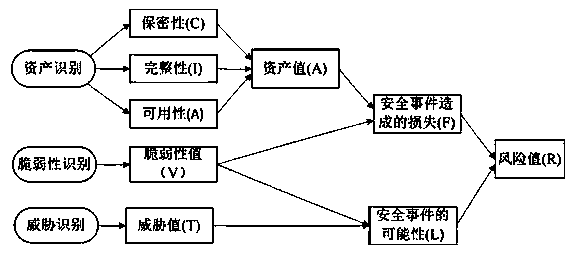
[0019] Step 1: Identify assets. According to the GB / T 20984-2007 standard, a form-based asset classification is shown in Table 1, which is divided into 5 categories. Data mainly includes various data materials on information media; software includes system software, application software, and source programs; hardware includes network equipment, computer equipment, transmission lines, security equipment, security equipment, etc.; services include information services, network services, Office services, etc.; personnel refer to those who have important information and core business.
[0020]
[0021]
[0022] Step 2: Vulnerability identification. In the GB / T 20984-2007 standard, seven categories of vulnerabilities are listed, including technical vulnerabilities and management vulnerabilities, as shown in Table 2. Vulnerability exists in the asset itself. In the actual project imp...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com