Network attack and defense virtual simulation and security evaluation method and system based on virtualization technology
A virtualization technology and security evaluation technology, applied in transmission systems, digital transmission systems, data exchange networks, etc., can solve problems such as inability to evaluate network security, expensive physical simulation platforms, and simulation systems that cannot be visualized in real time. Utilization rate, the effect of avoiding repeated investment in construction
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
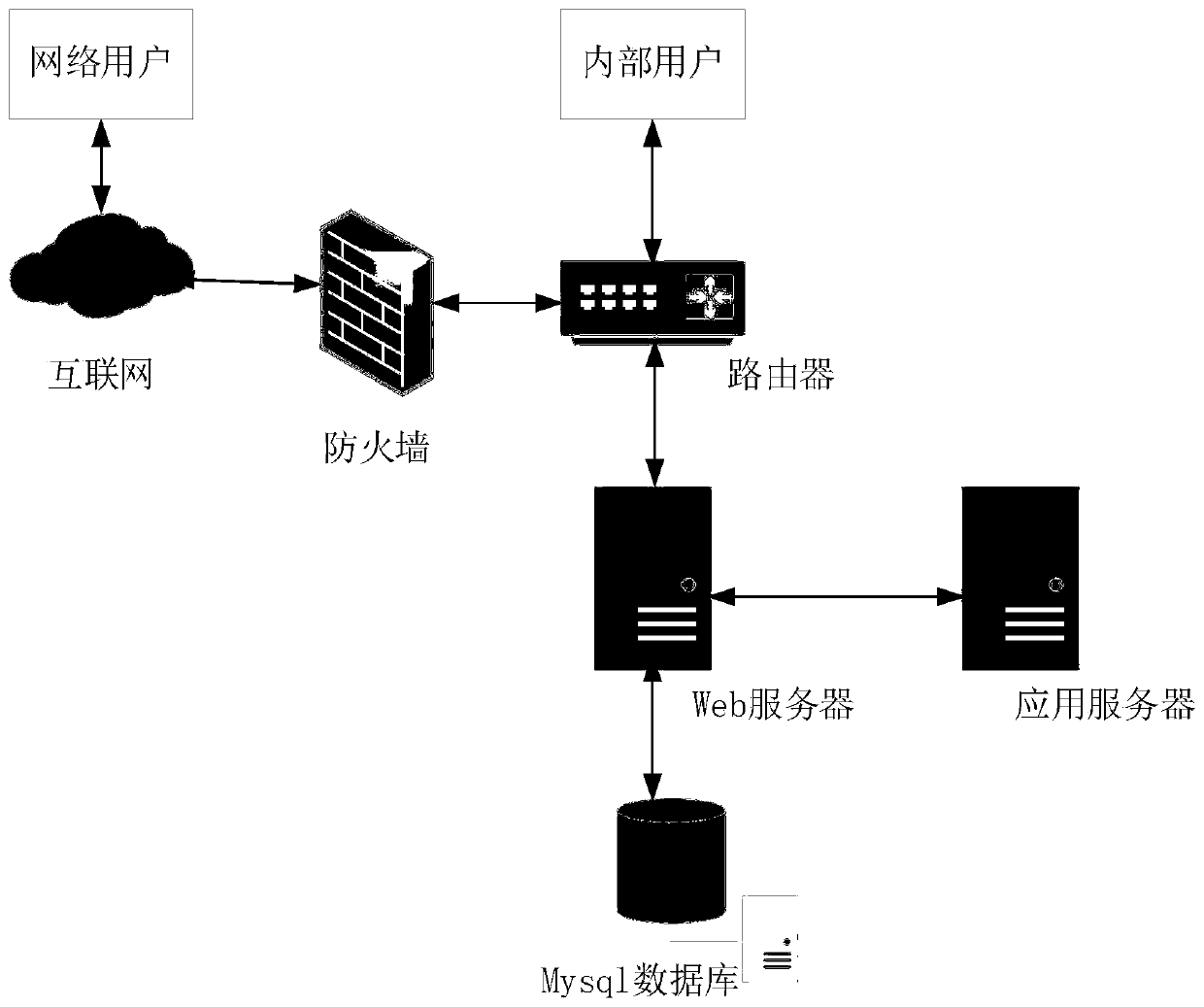
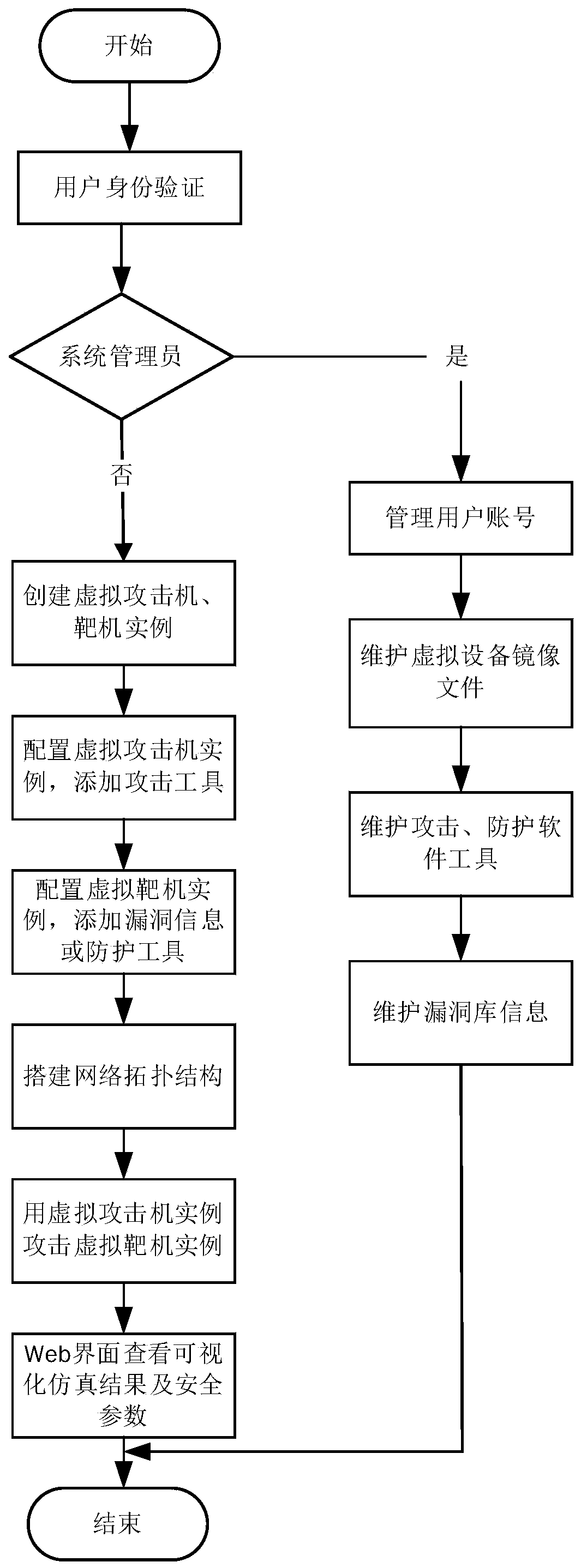
[0034] Attached below figure 1 And attached figure 2 Specific implementations of the present invention are described so that the advantages and features of the present invention can be more easily understood by those skilled in the art, so as to define the protection scope of the present invention more clearly.
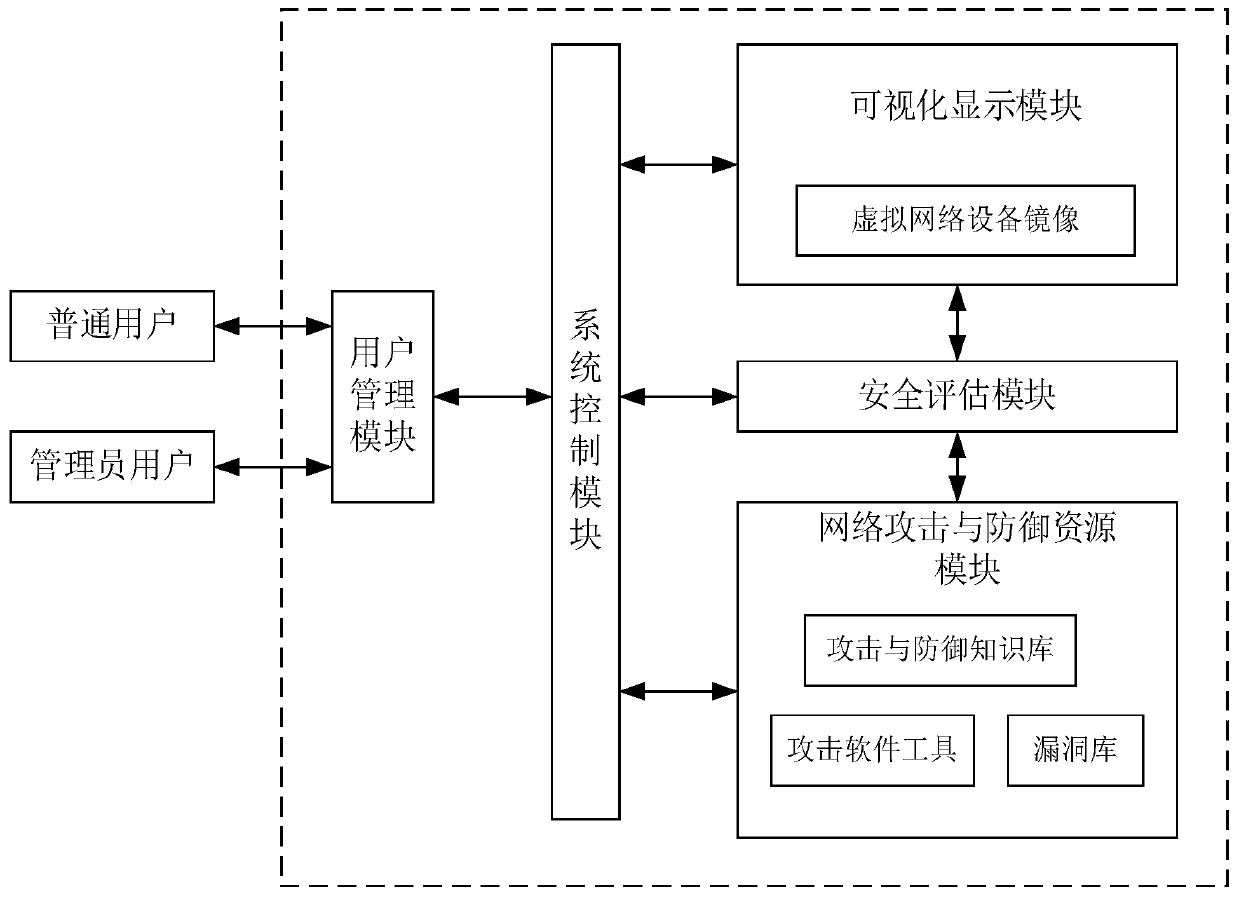
[0035]The network attack and defense virtual simulation and security assessment system based on virtualization technology includes: user management module, system control module, visual display module, security assessment module, network attack and defense resource library module. The user management module is responsible for authenticating and managing user identities. This module manages account information in the system, including user names, initial passwords, user groups, and possible types of network attack and defense operations. The administrator account can also maintain the virtual machine image of the system, maintain and add network attack and defense in...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com