Host risk evaluation method and device
A risk assessment and host technology, applied in the direction of electrical components, transmission systems, etc., can solve the problems of inability to deeply explore host vulnerabilities, lack of host topology and attack paths, and achieve perfect host risk assessment and ideal results
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
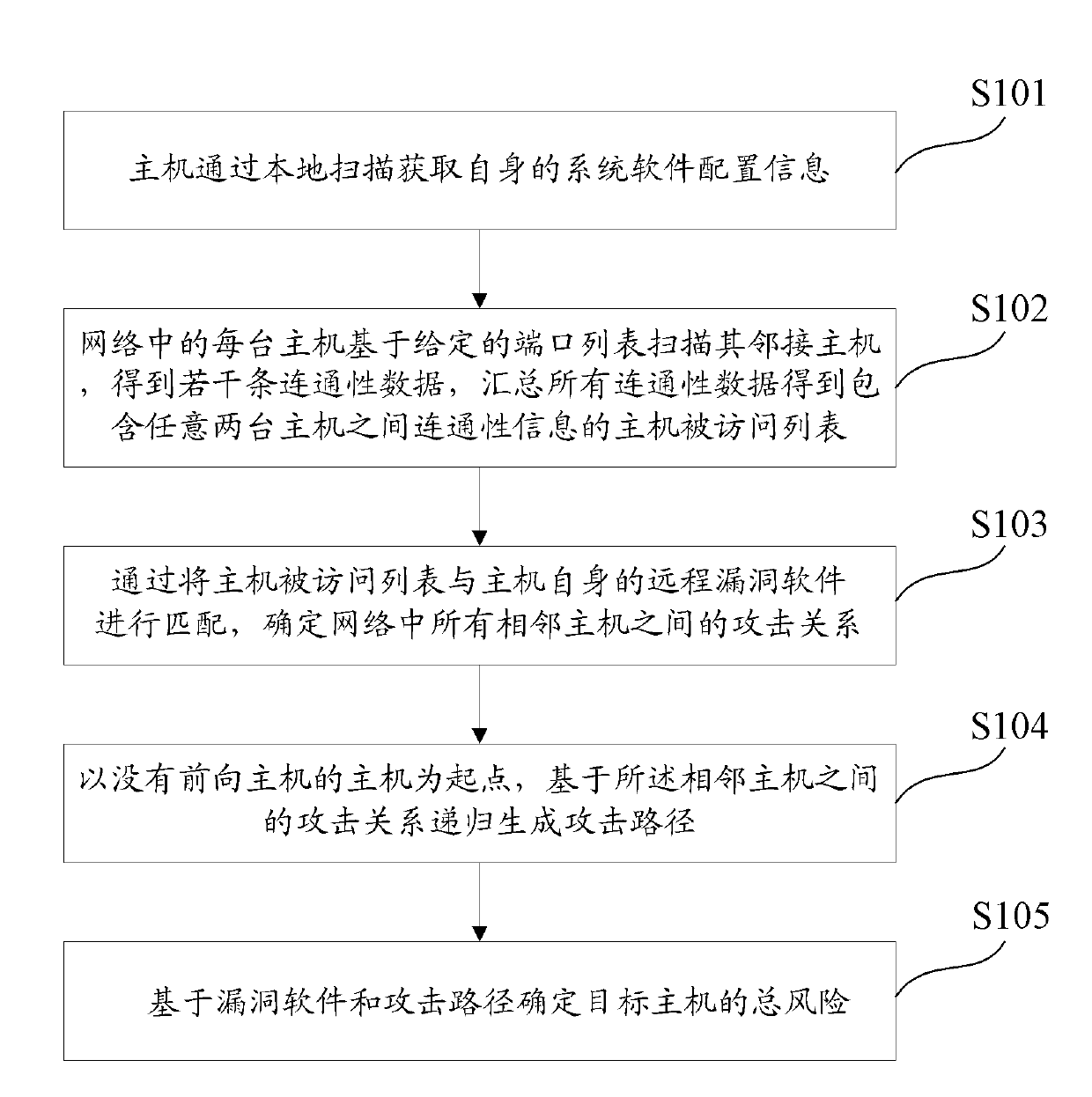
[0044] In the first embodiment of the present invention, a host risk assessment method, such as figure 1 shown, including the following specific steps:
[0045] Step S101 , the host obtains its own system software configuration information through local scanning, and the system software configuration information includes software name, version, patch and so on.
[0046] Comparing the system software configuration information with the vulnerability software database file, the local vulnerability software and remote vulnerability software existing in the host itself are obtained. Wherein, each remote vulnerability software corresponds to a fixed port on the host.
[0047] Preferably, while obtaining the vulnerable software existing in the host computer, the state of the vulnerable software, including whether it is running and has self-starting characteristics, is further determined by detecting the system process name list, service list and registry.
[0048] Step S102 , each ...
no. 3 example
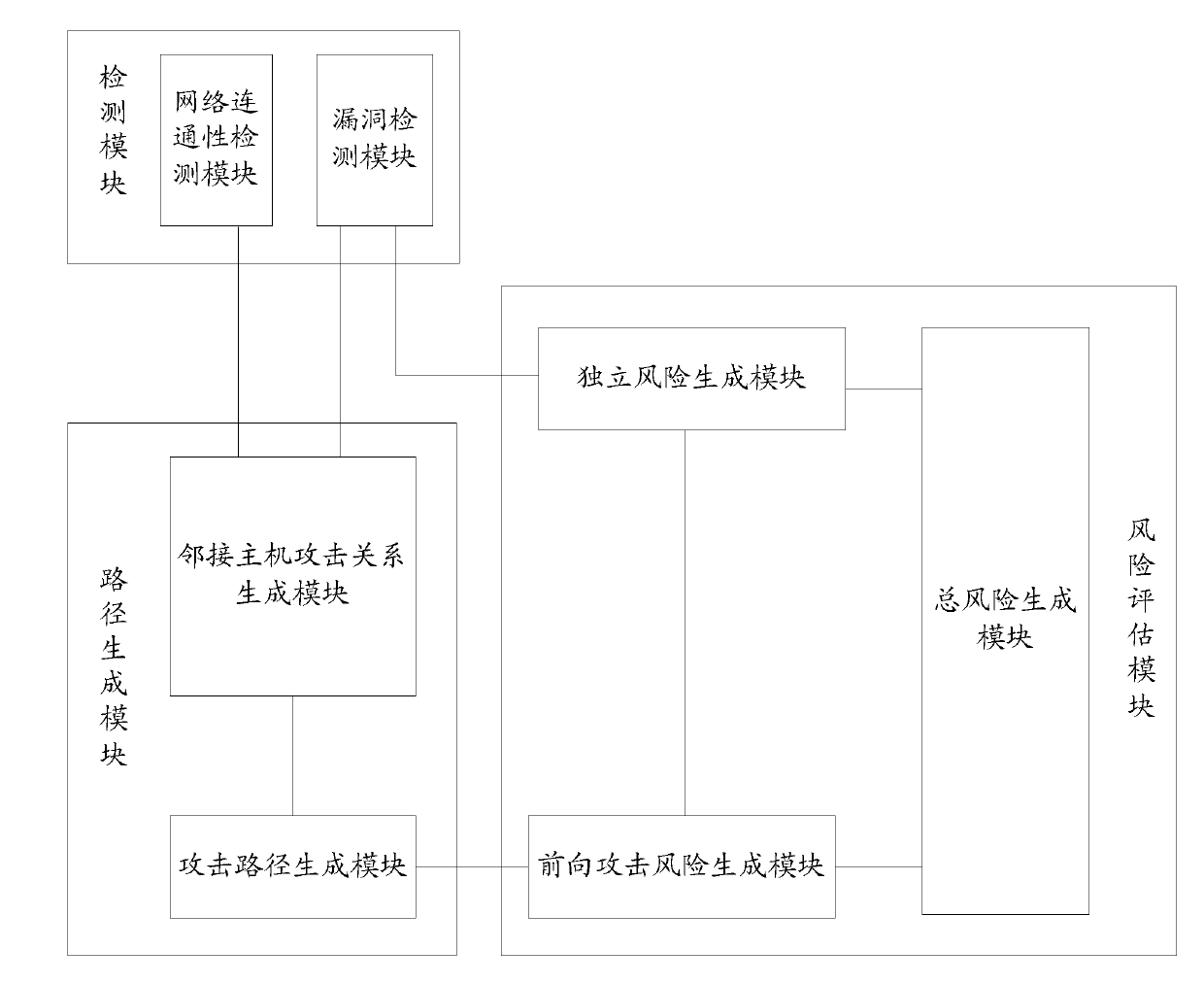
[0063] In the third embodiment of the present invention, a host risk assessment device, such as image 3 As shown, it includes the following components:
[0064] 1) The detection module is deployed in each host in the network, and is used to detect vulnerability information and network connectivity information of all hosts in the network. The detection module specifically includes: a vulnerability detection module and a network connectivity detection module, wherein,
[0065] The vulnerability detection module is used to check the vulnerability information of all hosts in the network. Vulnerability information includes local vulnerable software and remote vulnerable software. Specifically, the system software configuration information of the host is obtained by scanning, and the system software configuration information is compared with the vulnerable software database file to obtain all vulnerable software existing on the host, and each remote vulnerable software correspond...
no. 4 example
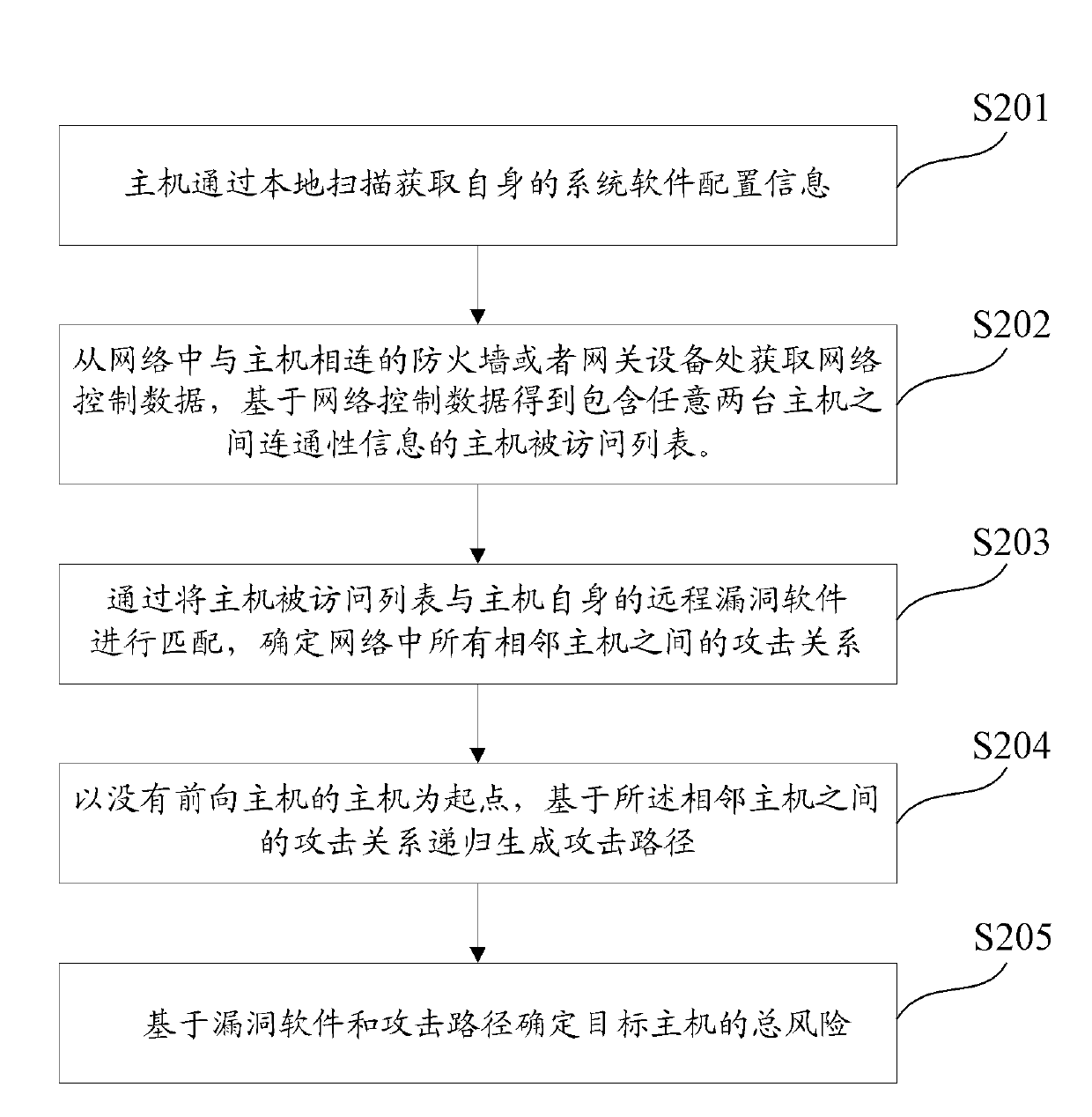
[0083] In the fourth embodiment of the present invention, the following introduces an example of a risk assessment process from the perspective of a device in combination with the above method:
[0084] 1. Control host
[0085] A control host is set independently of all hosts to be assessed for risk in the network, and the control host is mainly responsible for controlling the vulnerability detection module and the network connectivity detection module deployed in each host. The control host includes an adjacent host attack relationship generation module, an attack path generation module and a risk assessment module. The working steps of the control host are as follows:
[0086] Step S1: Send a command. Notify each host to perform its own vulnerability detection and network connectivity detection, and wait for the information to be sent back.
[0087] Step S2: All the information is sent back, and each host is notified that the receiving is completed.
[0088] Step S3: Sub...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com