Multi-dimensional software security risk assessment method based on CVSS
A risk assessment and software security technology, applied in the computer field, can solve the problems of lack of vulnerability type and vulnerability exploitation time assessment, lack of vulnerability type and vulnerability utilization time factors, and inaccurate assessment of influencing factors in the combination of dynamic and static features. Achieve the effects of increasing external time factors, diversifying risk assessment scores, and improving diversity
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
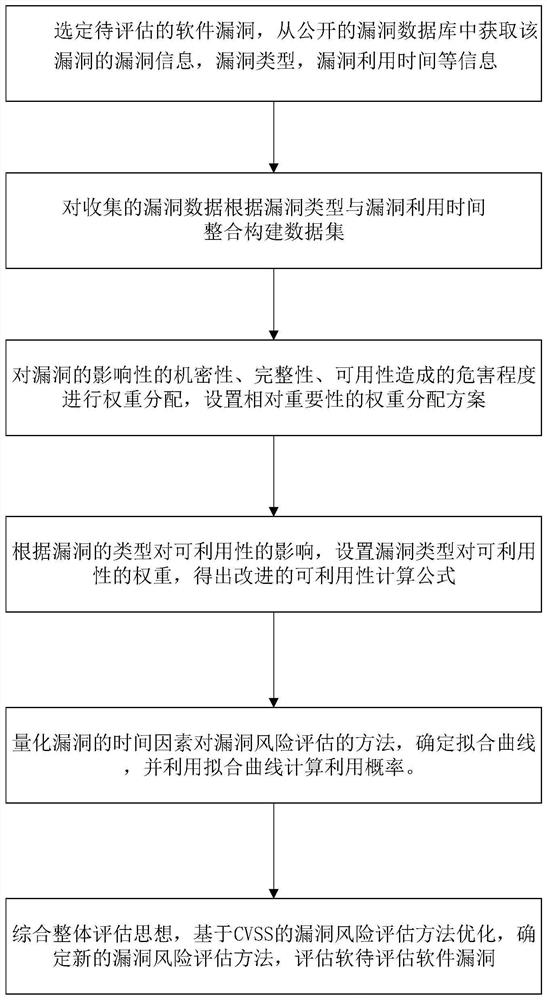
[0031] The application of software is becoming more and more extensive, the scale of software is also increasing, and the demand for software in scientific research and various industries is also increasing. The daily life of modern people is inseparable from the support of software. However, the production and operation of software At the same time, there will inevitably be loopholes. How to make a reasonable assessment of the loopholes and quantify the risk of software loopholes can not only increase users' attention to software loopholes, but also improve the availability of software loopholes, thereby reducing a large number of security incidents. The probability of occurrence, to speed up the time to repair the vulnerability. The safe operation of software is inseparable from a reasonable assessment of vulnerabilities.
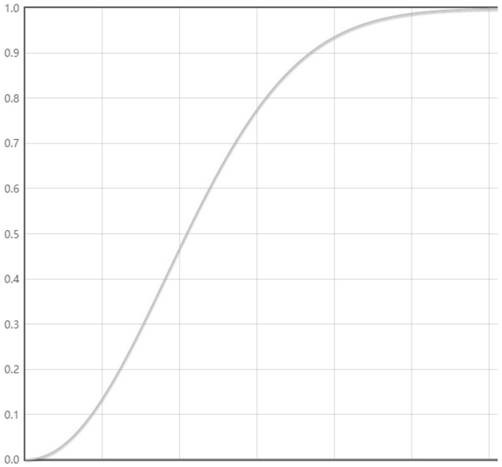
[0032]At present, the commonly used CVSS vulnerability risk assessment method is to set two scoring metrics in the risk score, referred to as metrics, wh...
Embodiment 2
[0055] A CVSS-based multi-dimensional software security risk assessment method is the same as that in Embodiment 1, step 4 in which the weight of the relative importance metric index in the impact metric is reset.
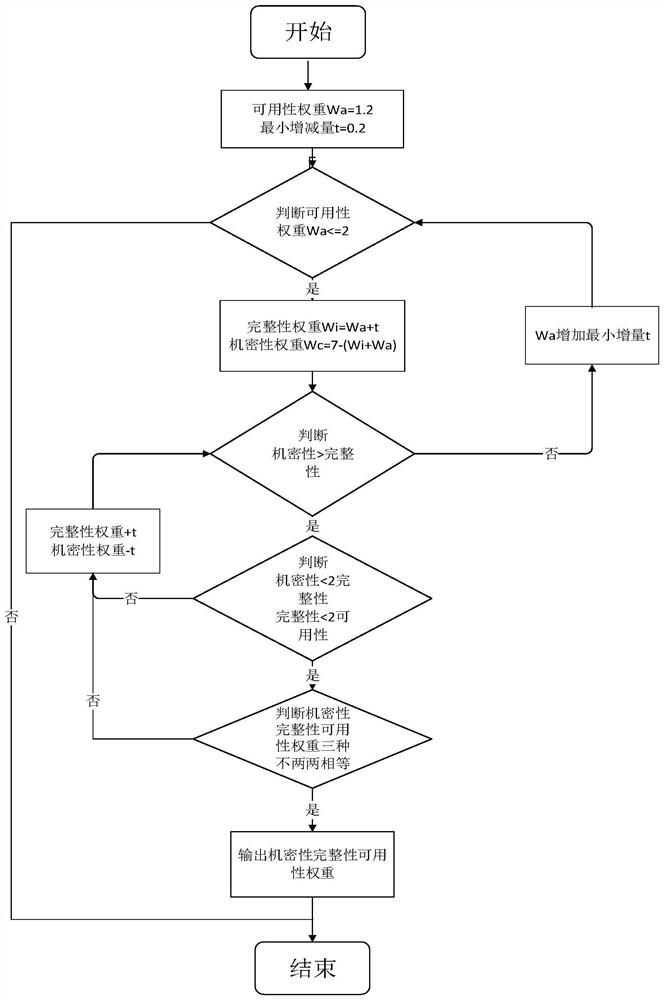
[0056] The traditional CVSS risk assessment method sets the same weight for the confidentiality, integrity and availability measures in impact, which limits the diversity of scores. According to the difference in the degree of harm of the measurement indicators in the impact of vulnerabilities, the present invention designs a relative importance weight distribution scheme, and obtains the weight of the relative importance measurement indicators of each measurement indicator in the impact measurement. Compared with the CVSS evaluation method, it has a more accurate score Standards, more diverse risk assessment methods.
[0057] Step 4.1) Determine the principle of the weight distribution scheme, and obtain a variety of weight distribution schemes: the confidentialit...
Embodiment 3
[0063] A CVSS-based multi-dimensional software security risk assessment method is the same as that in Embodiment 1-2, the vulnerability type measurement index is added in the exploitability measurement described in step 5, and the corresponding weight of each type of vulnerability type measurement index is calculated, Including the following steps:
[0064] Step 5.1) Build a standard weight decision matrix data table: select the vulnerability type data set data, and divide it according to the availability and difficulty standards to obtain four levels: difficult to use B1, relatively difficult to use B2, usable B3, and easy to use B4. A variety of vulnerability types are distributed in each class. Divide each type of vulnerability at the same level by the sum of the levels, thereby constructing initial data tables of different levels, as shown in Table 3, which is a data table for constructing a decision matrix for standard weights in the present invention.
[0065] Step 5.2)...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com