Patents
Literature
30results about How to "Maintaining secrecy" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
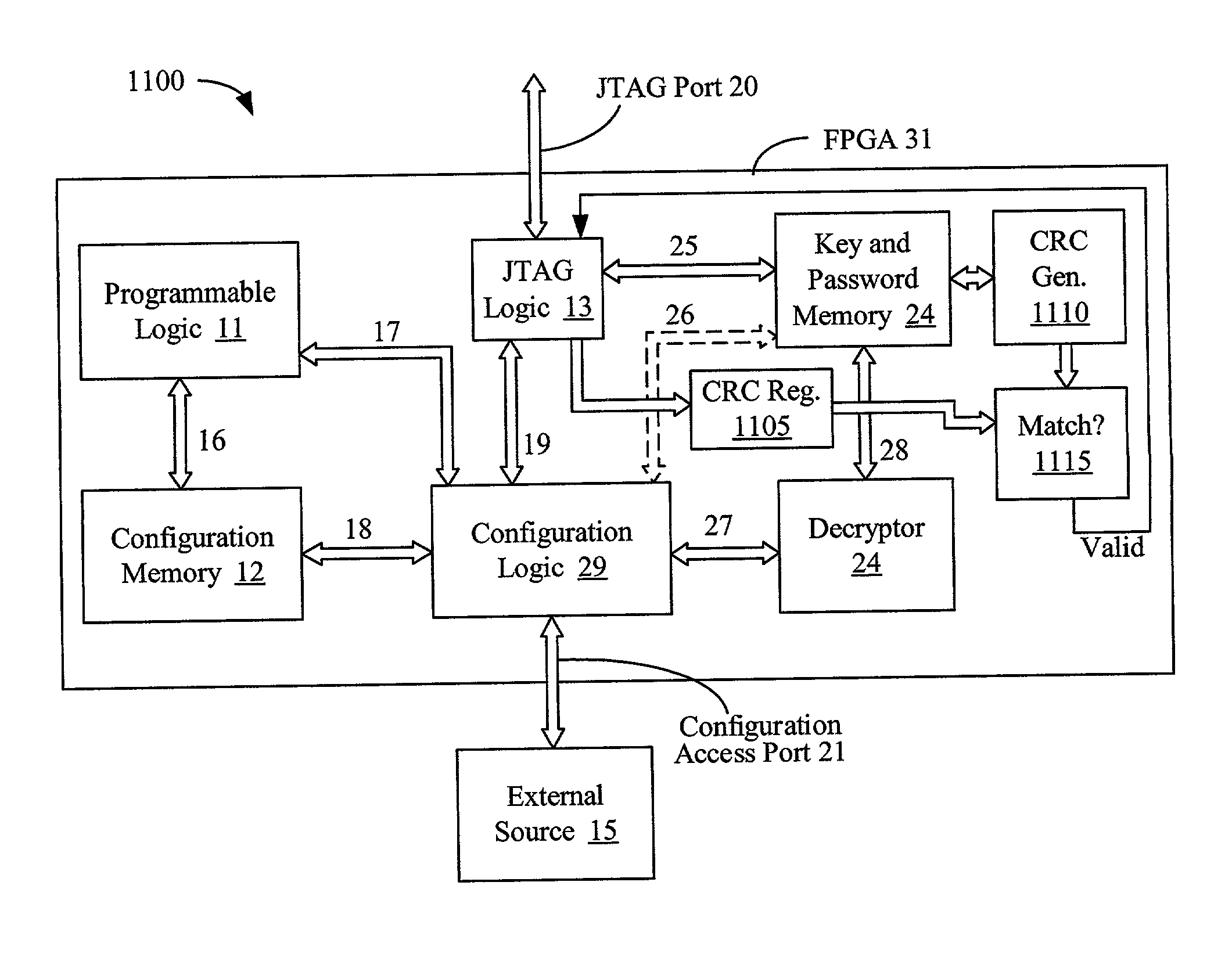
Error-checking and correcting decryption-key memory for programmable logic devices
ActiveUS7200235B1Reduce riskPreventing the overwriting of framesReliability increasing modificationsError preventionError checkingProgrammable logic device
Described are circuits that detect and correct for decryption key errors. In one example, a programmable logic device includes a decryption key memory with a number of decryption-key fields and, for each key field, an associated error-correction-code (ECC) field. The PLD additionally includes error-correction circuitry that receives each key and associated ECC and performs an error correction before conveying the resulting error-corrected key to a decryptor.
Owner:XILINX INC
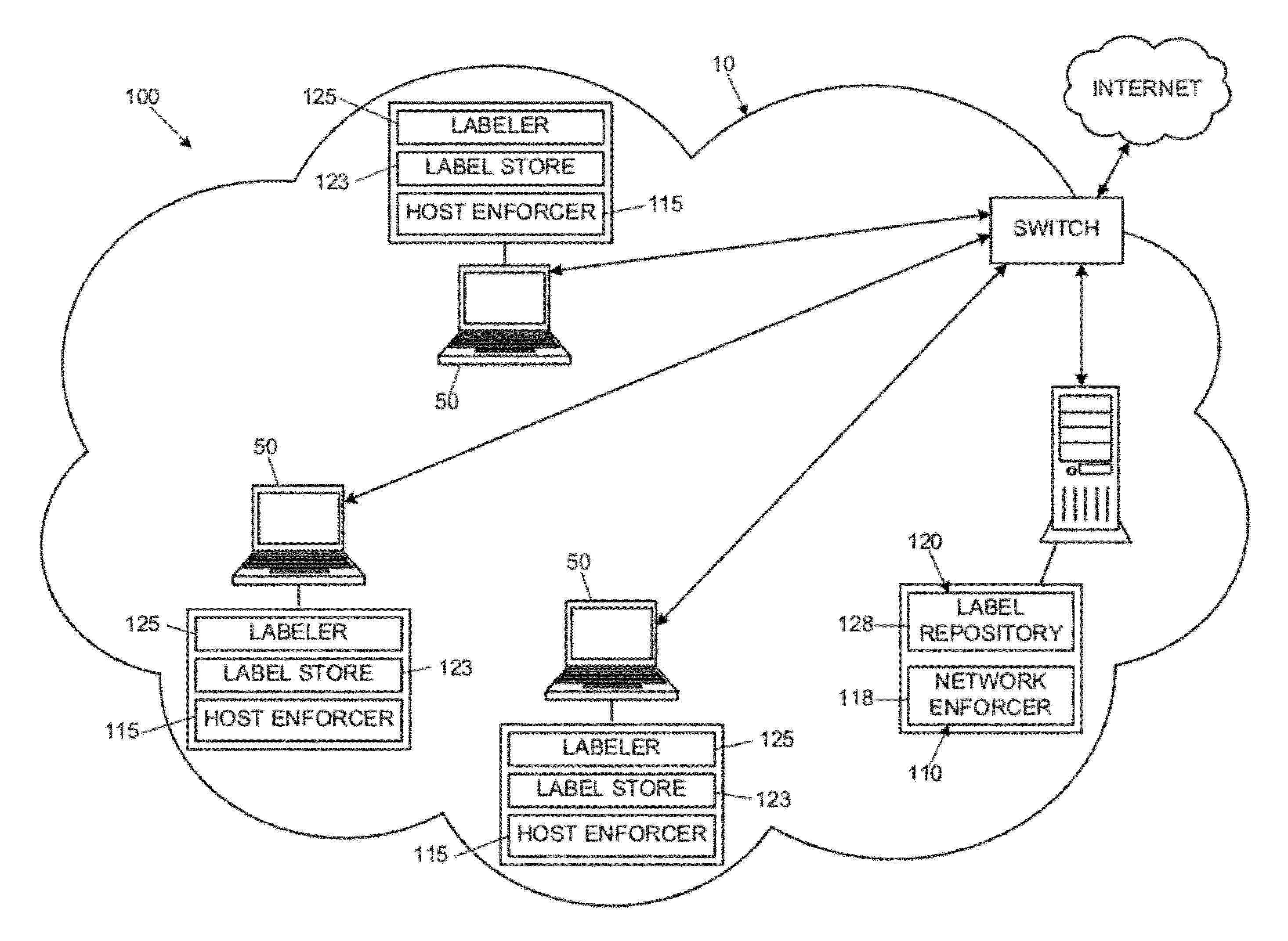
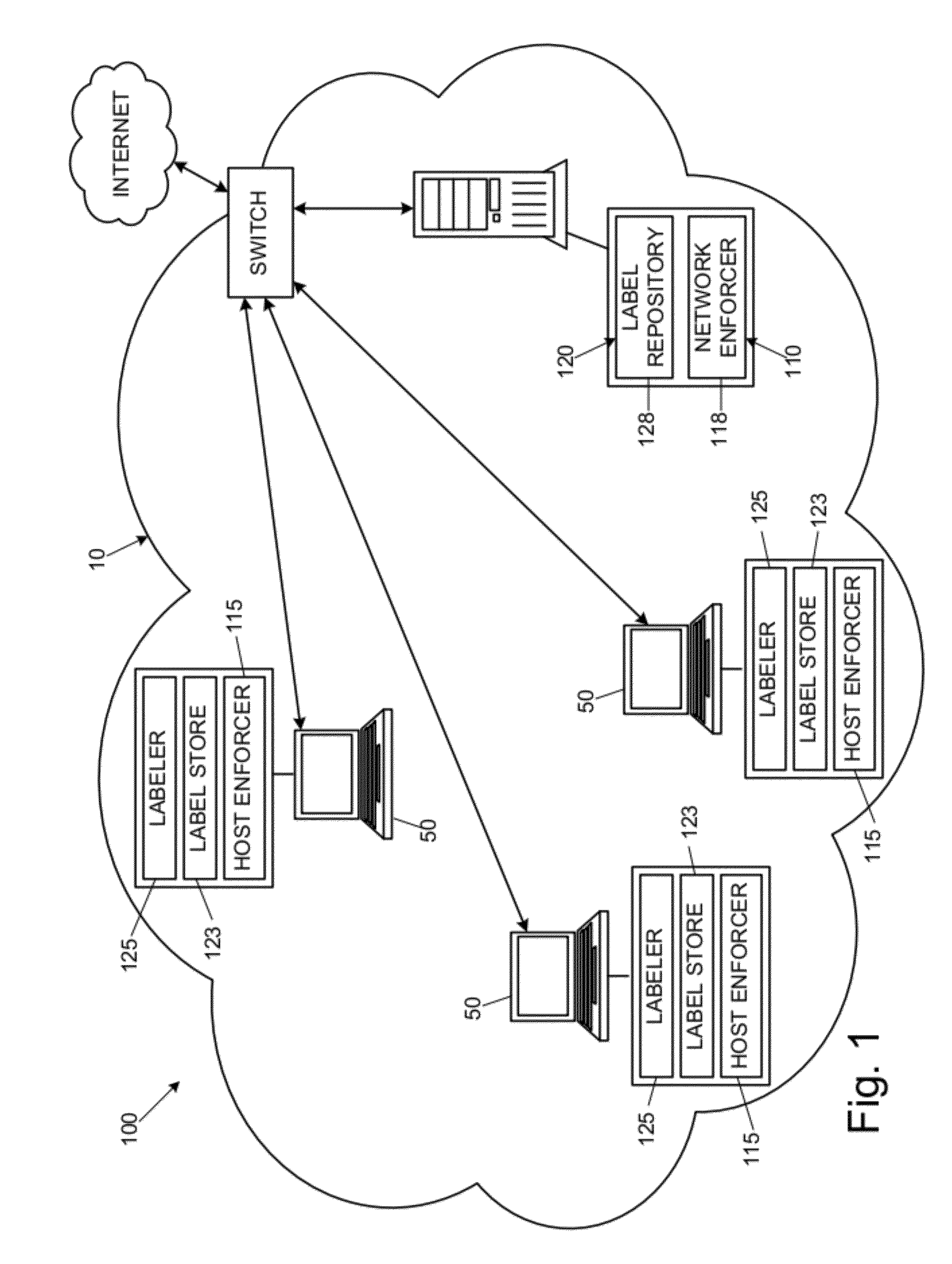
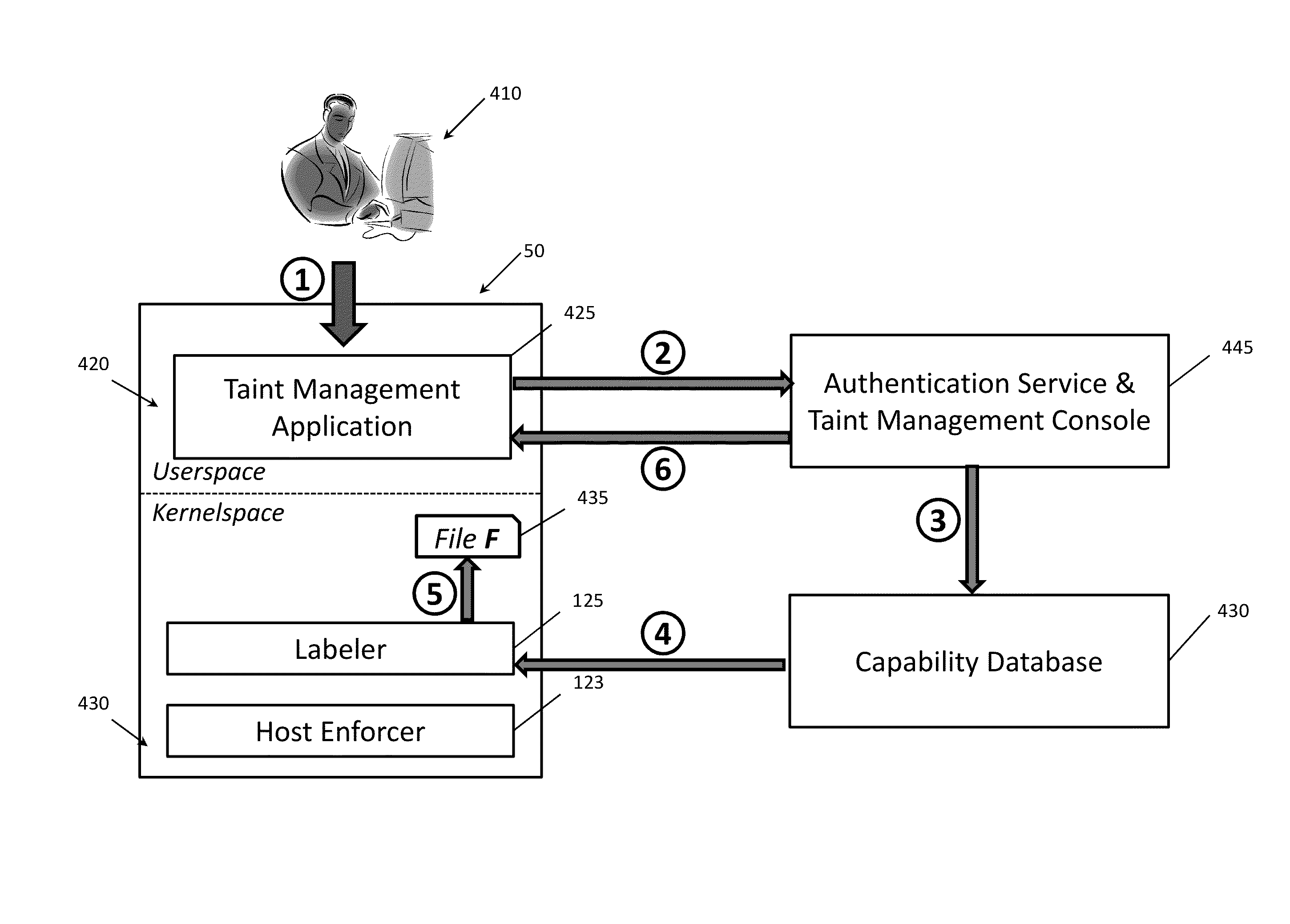
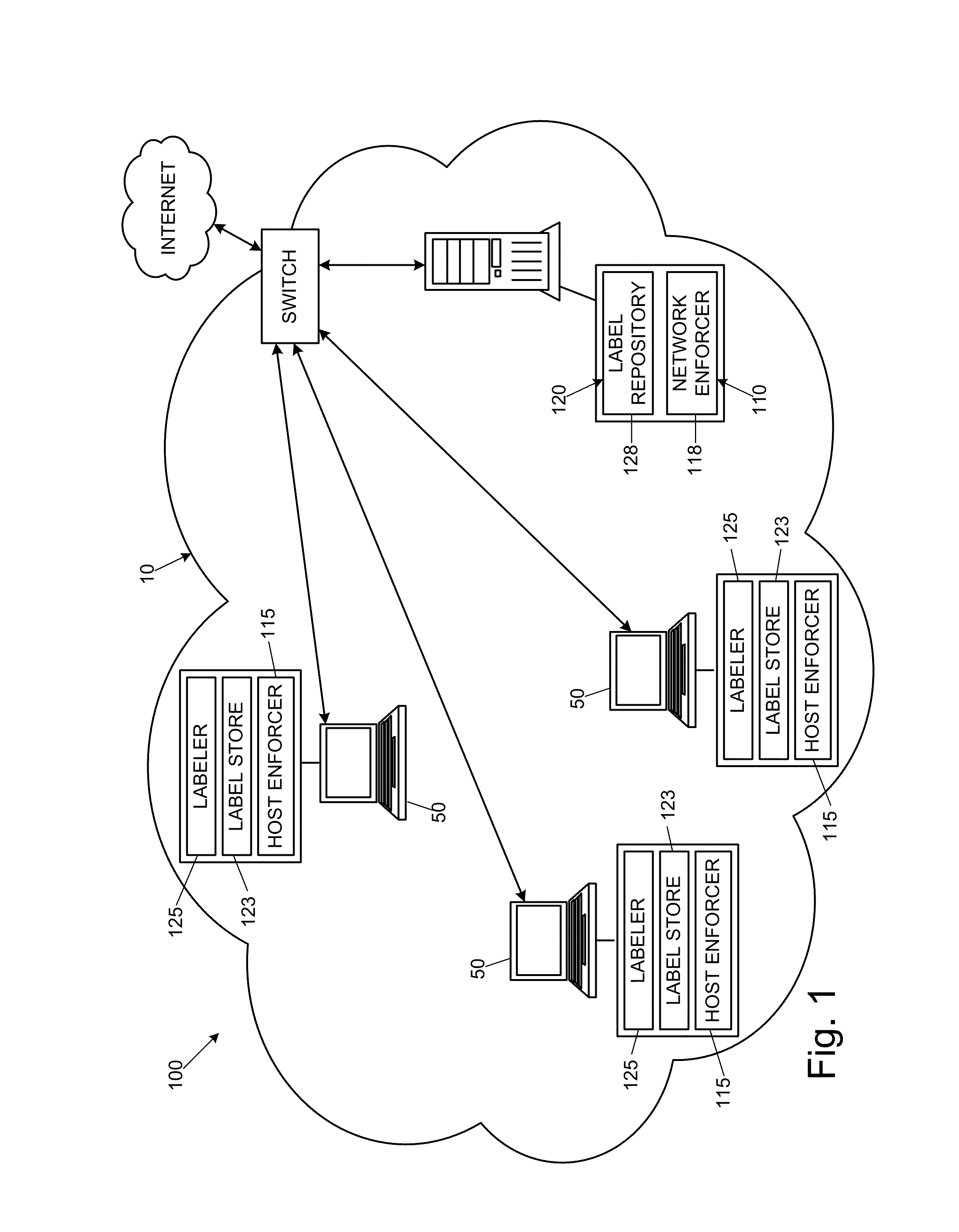
Security systems and methods to reduce data leaks in enterprise networks
InactiveUS20120137375A1Harder to evadeSolve excessive overheadDigital data processing detailsAnalogue secracy/subscription systemsSecurity systemDistributed computing
Disclosed are embodiments of a security system for reducing data leaks by checking information flows between resources of a network. When an information flow is attempted between a sending resource, which can be anywhere in the network, and a receiving resource residing at a specific host within the network, a host labeler can determine whether information is allowed to flow from the sending resource to the receiving resource. The sending resource and the receiving resource can each have an applicable label, and each label can comprise zero, one, or more taints. For each taint having an active secrecy characteristic in a label of the sending resource, the host labeler can require that there be a matching taint with active secrecy characteristic in the receiving resource. If this condition is not met, the security system can block the information flow between the sending and receiving resources.
Owner:GEORGIA TECH RES CORP
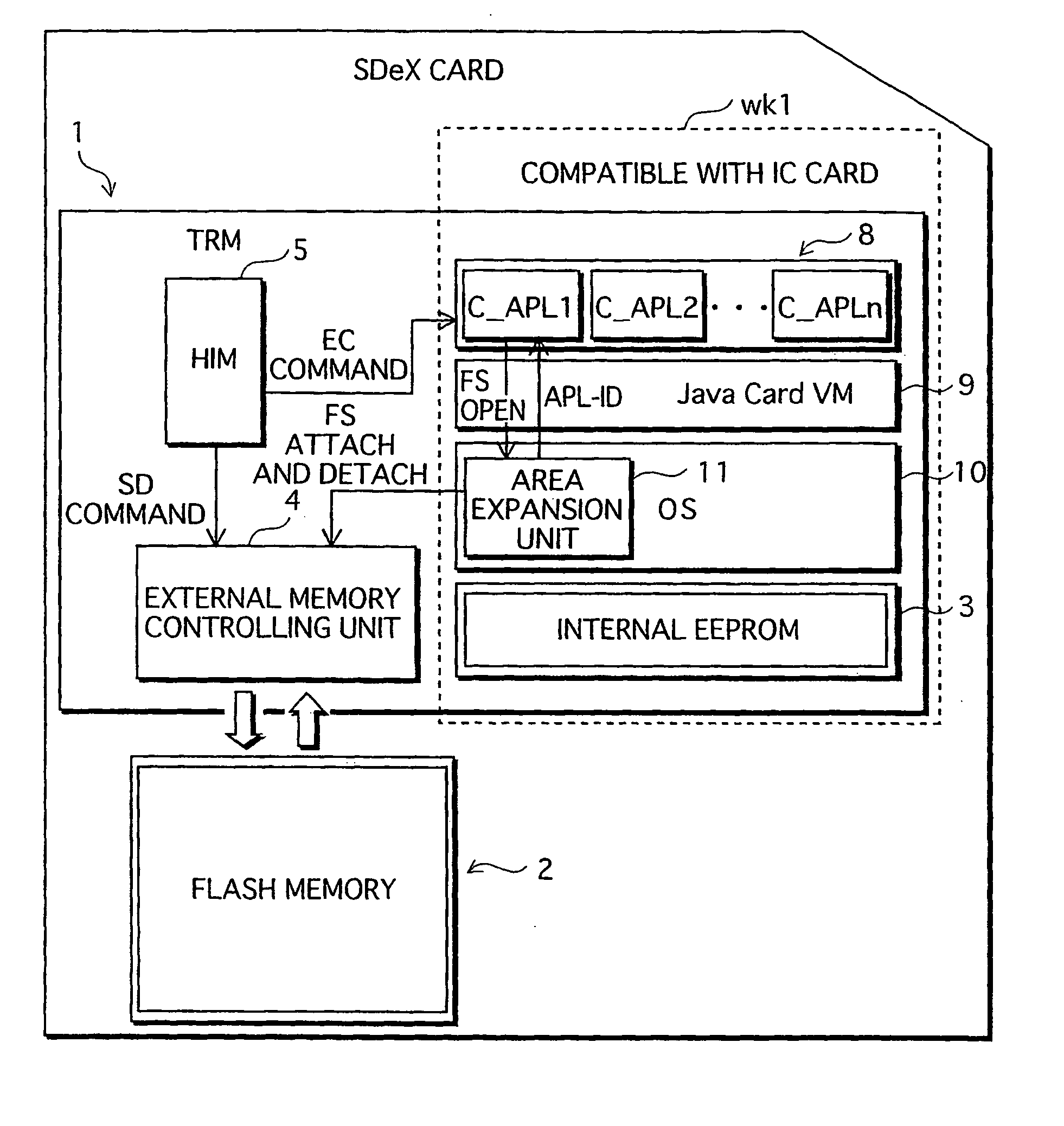
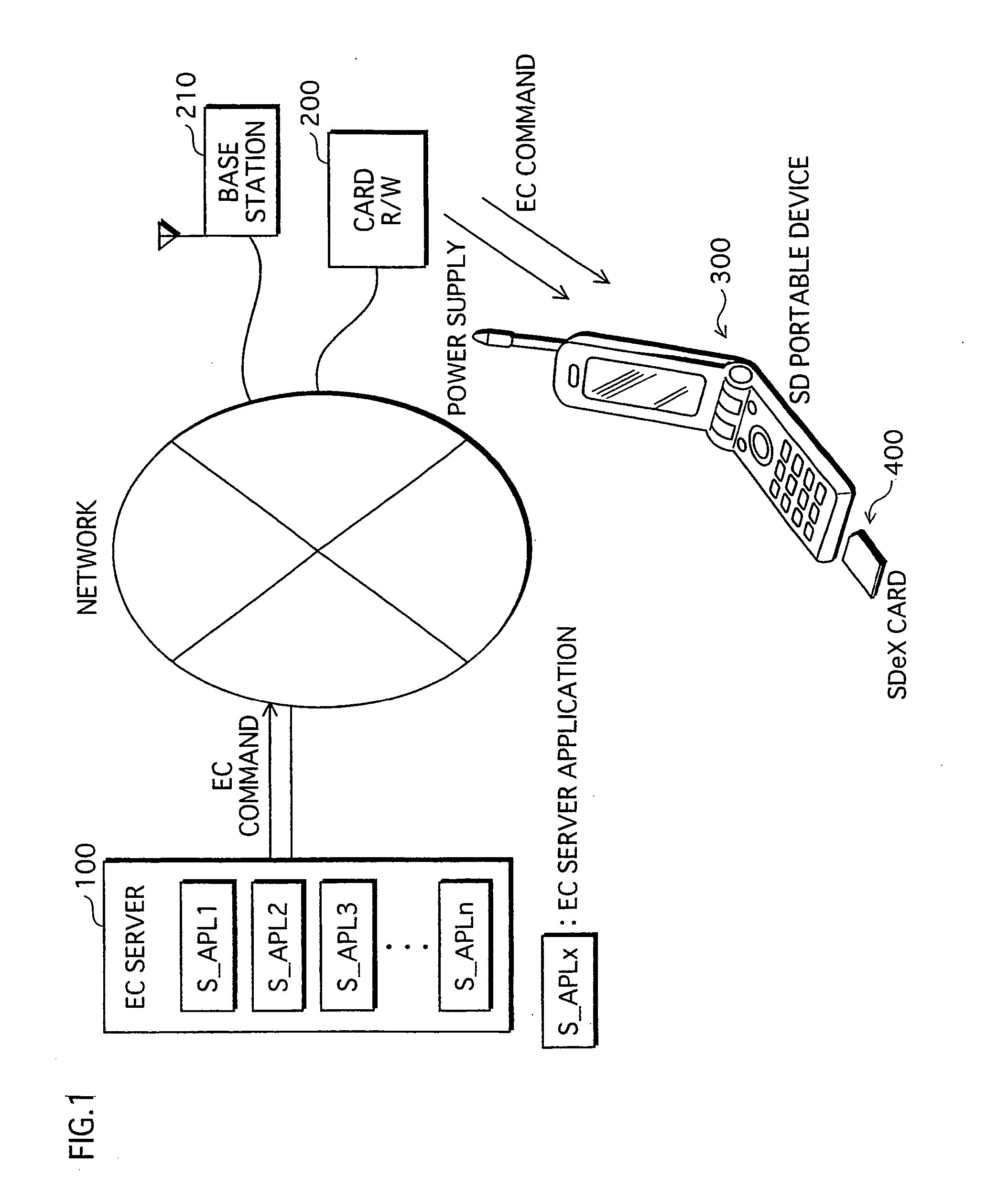
Semiconductor memory card, and program for controlling the same
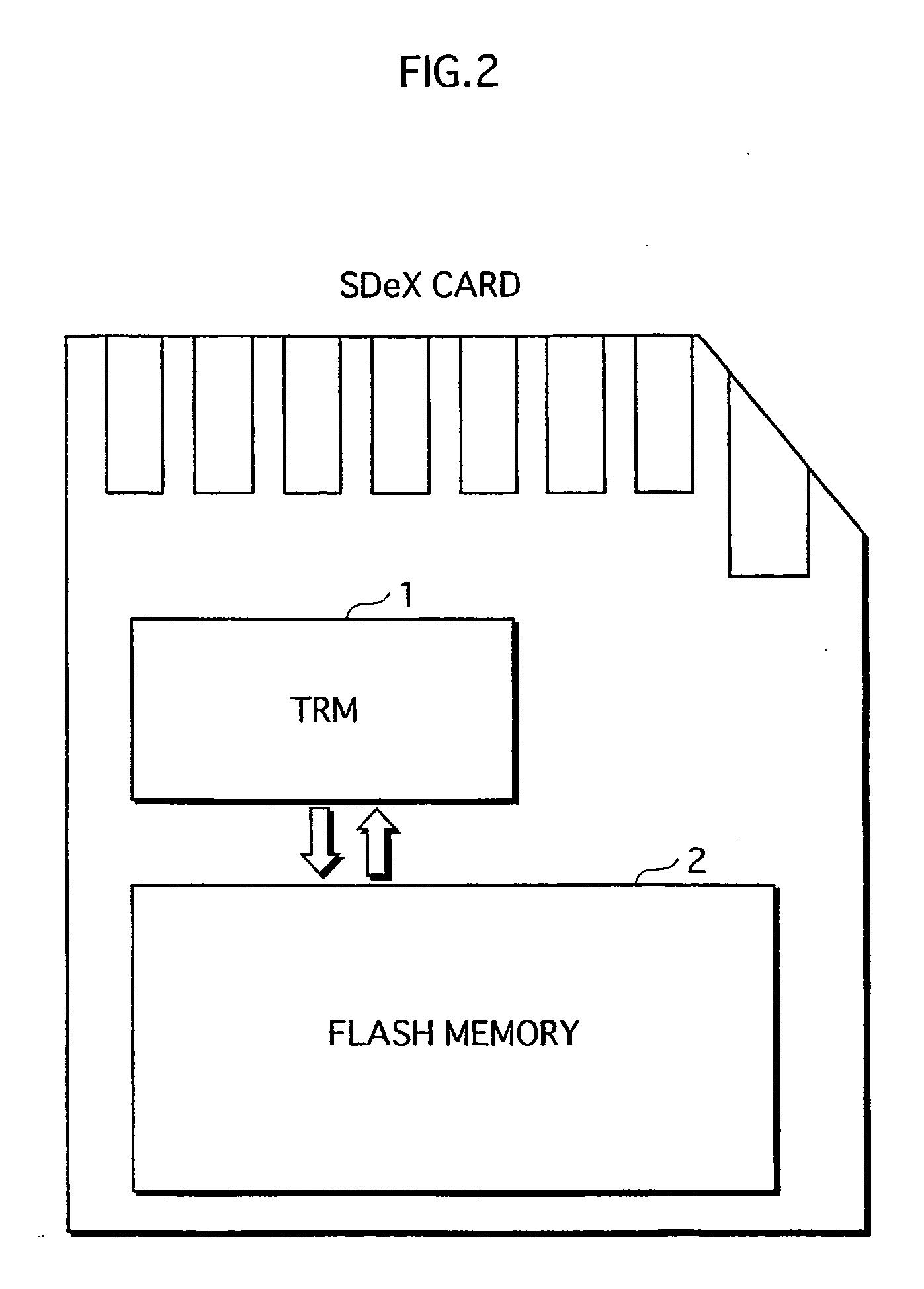
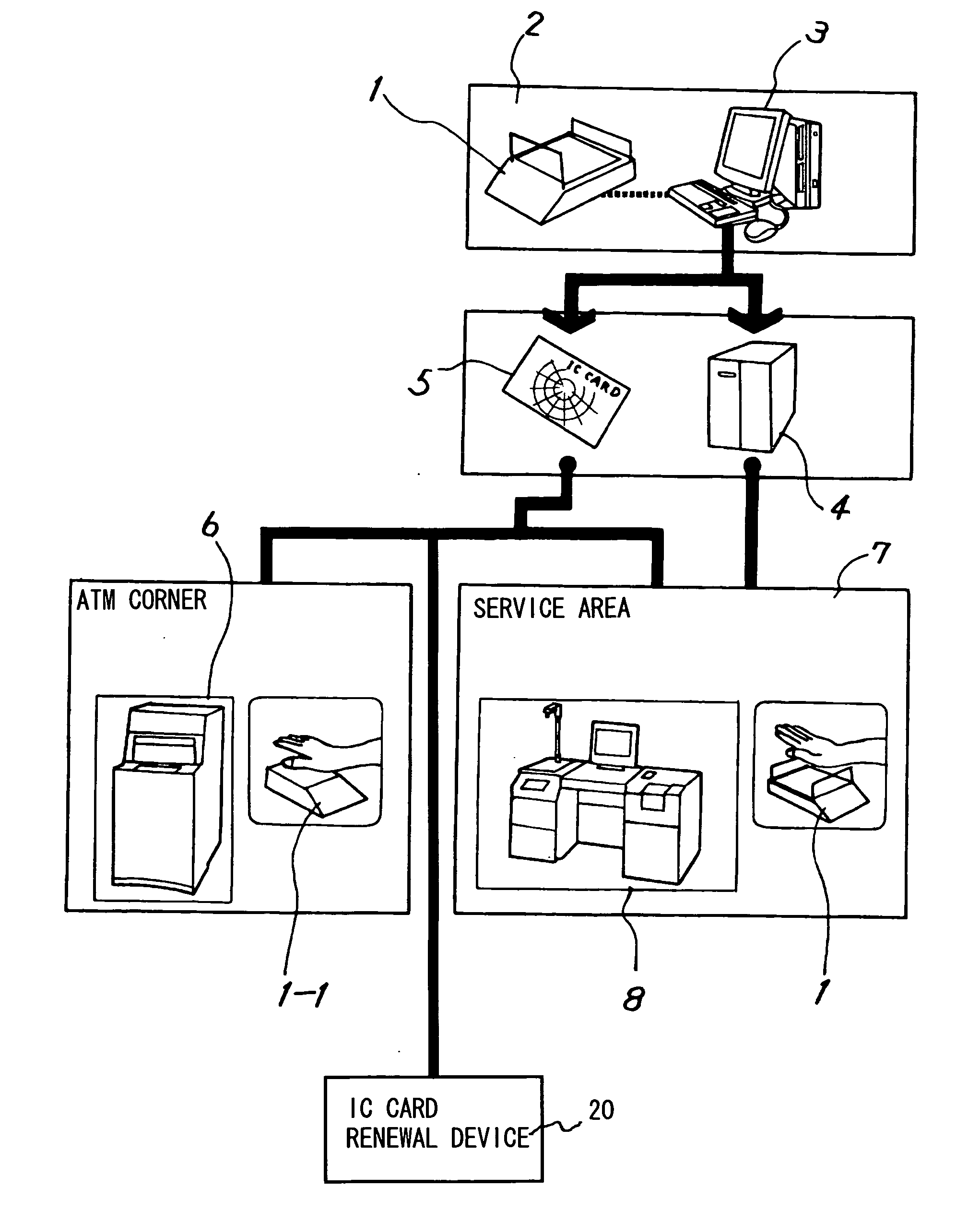
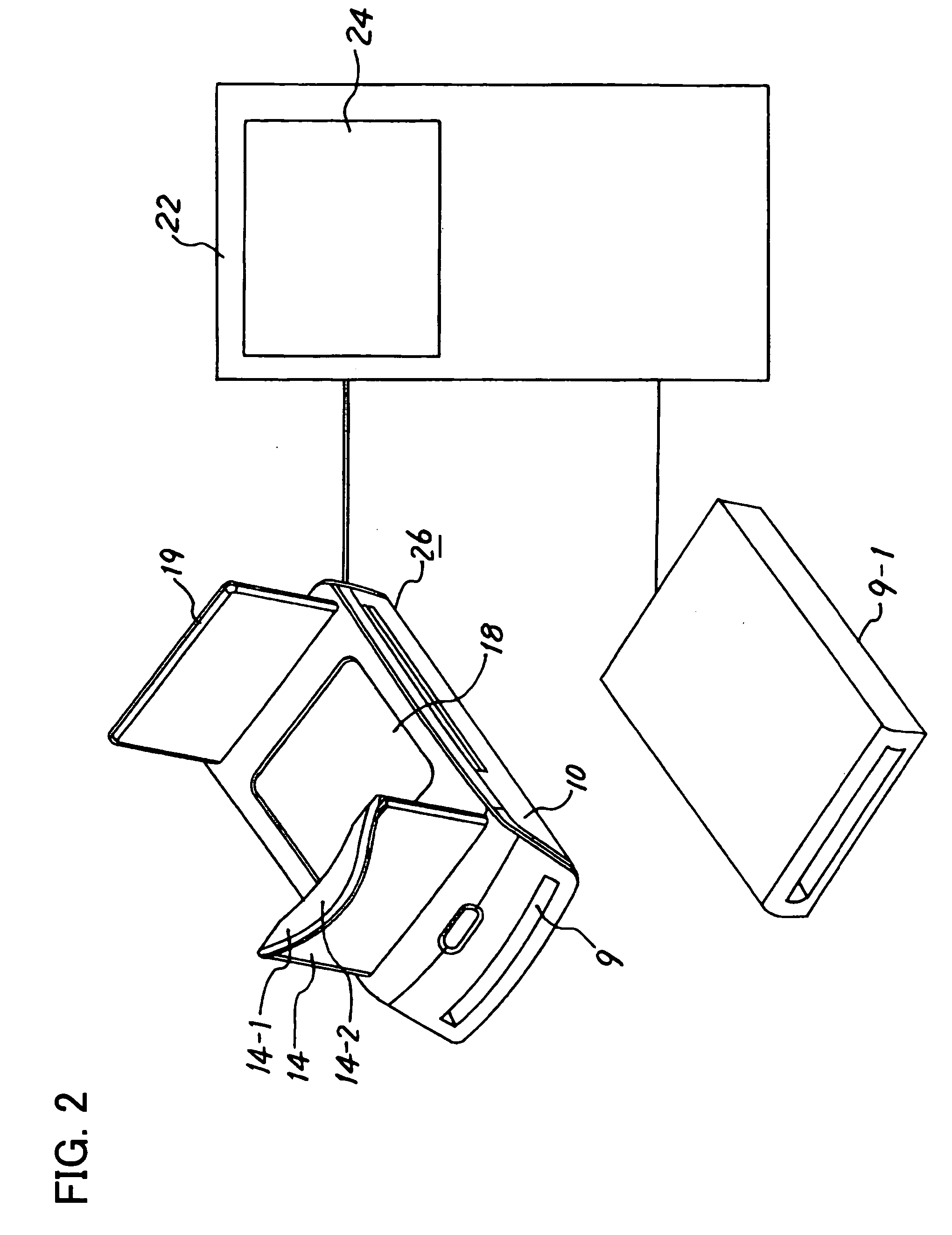
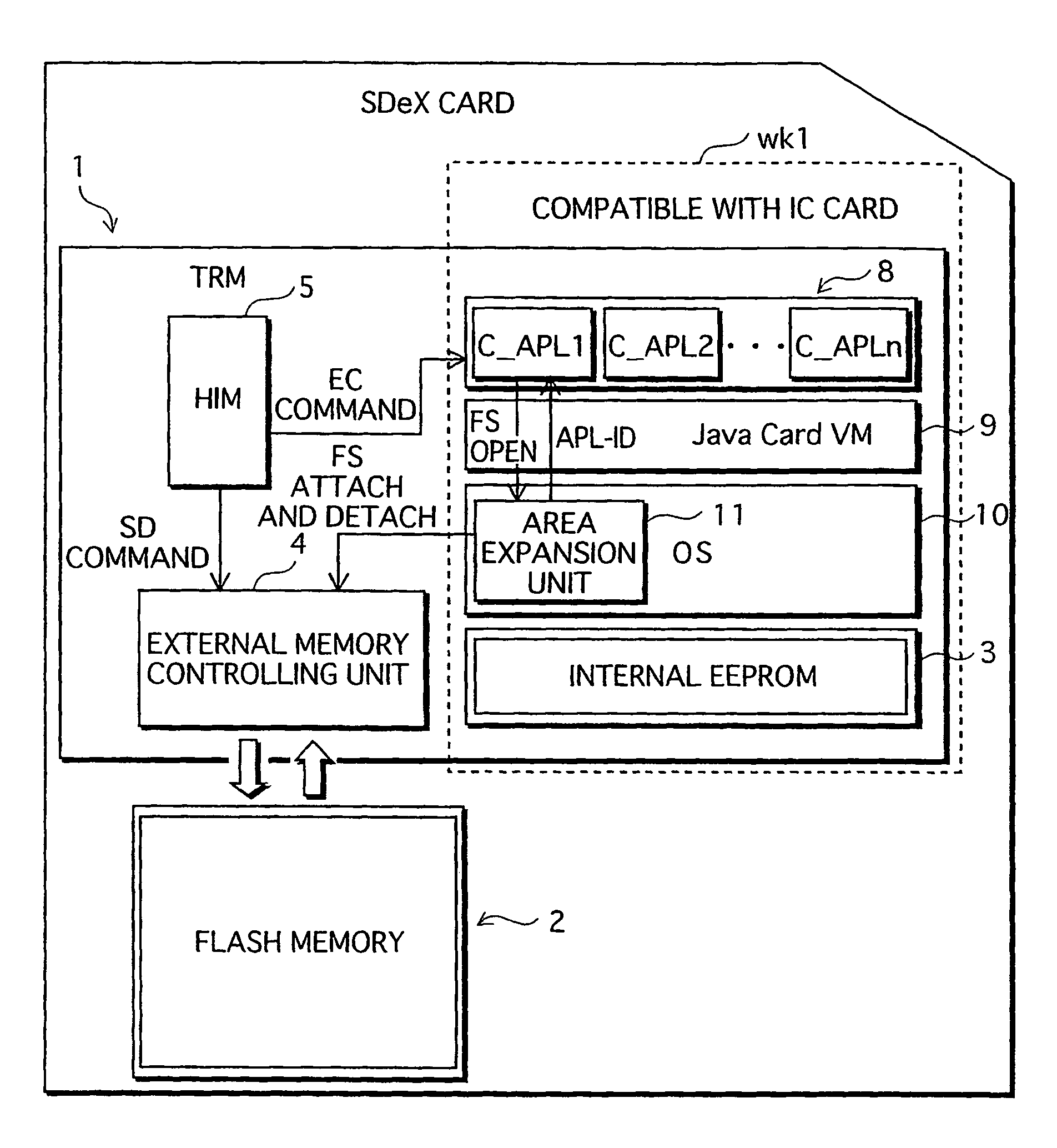
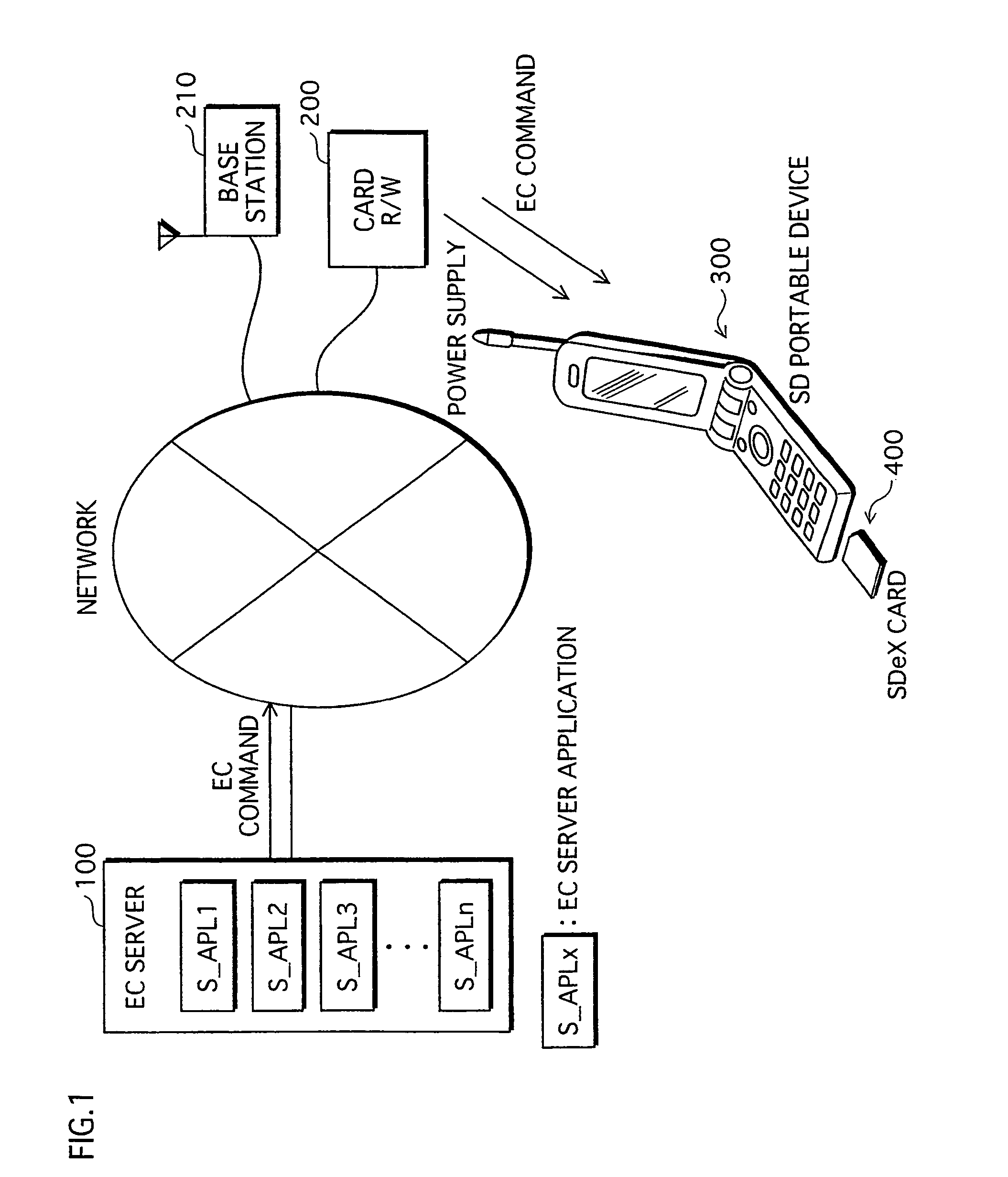
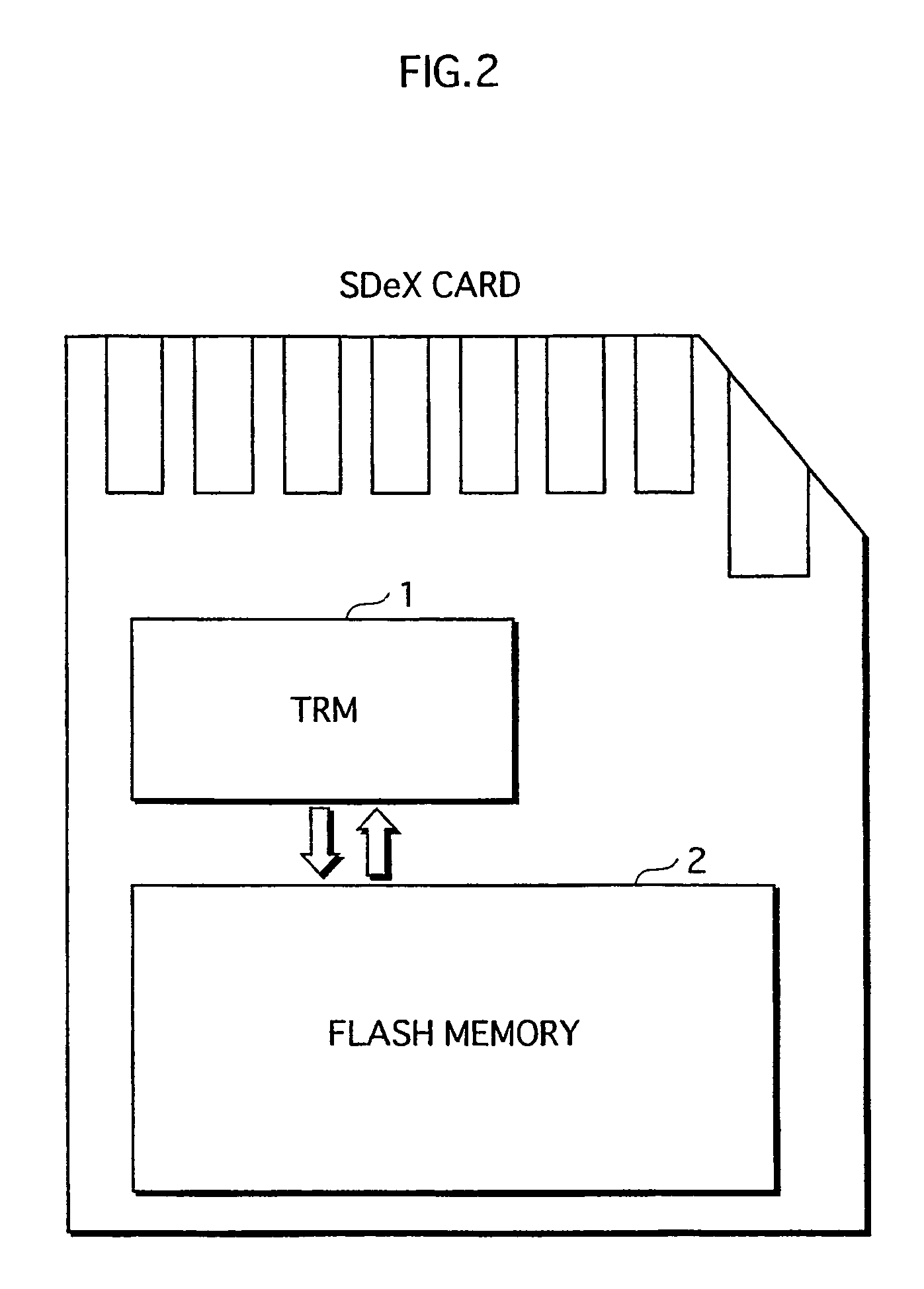
ActiveUS20060026338A1Maintaining secrecyLower security levelUnauthorized memory use protectionDigital data protectionTamper resistanceE-commerce
A semiconductor memory card that has a sufficient storage capacity when an electronic commerce (EC) application writes data to a storage is provided. A usage area for the EC application in EEPROM 3 in a tamper resistant module (TRM) 1 is expanded. The expansion is such that a partition generated in a flash memory 2 outside the TRM 1 is assigned to the EC application while a partition table is allocated in the internal EEPROM 3. Because the partition table is in the TRM 1, only a CPU 7 in the TRM 1 is able to access the generated partition table. Secrecy of stored contents increases because the access to the expanded area is limited to the CPU in the TRM 1.
Owner:PANASONIC CORP
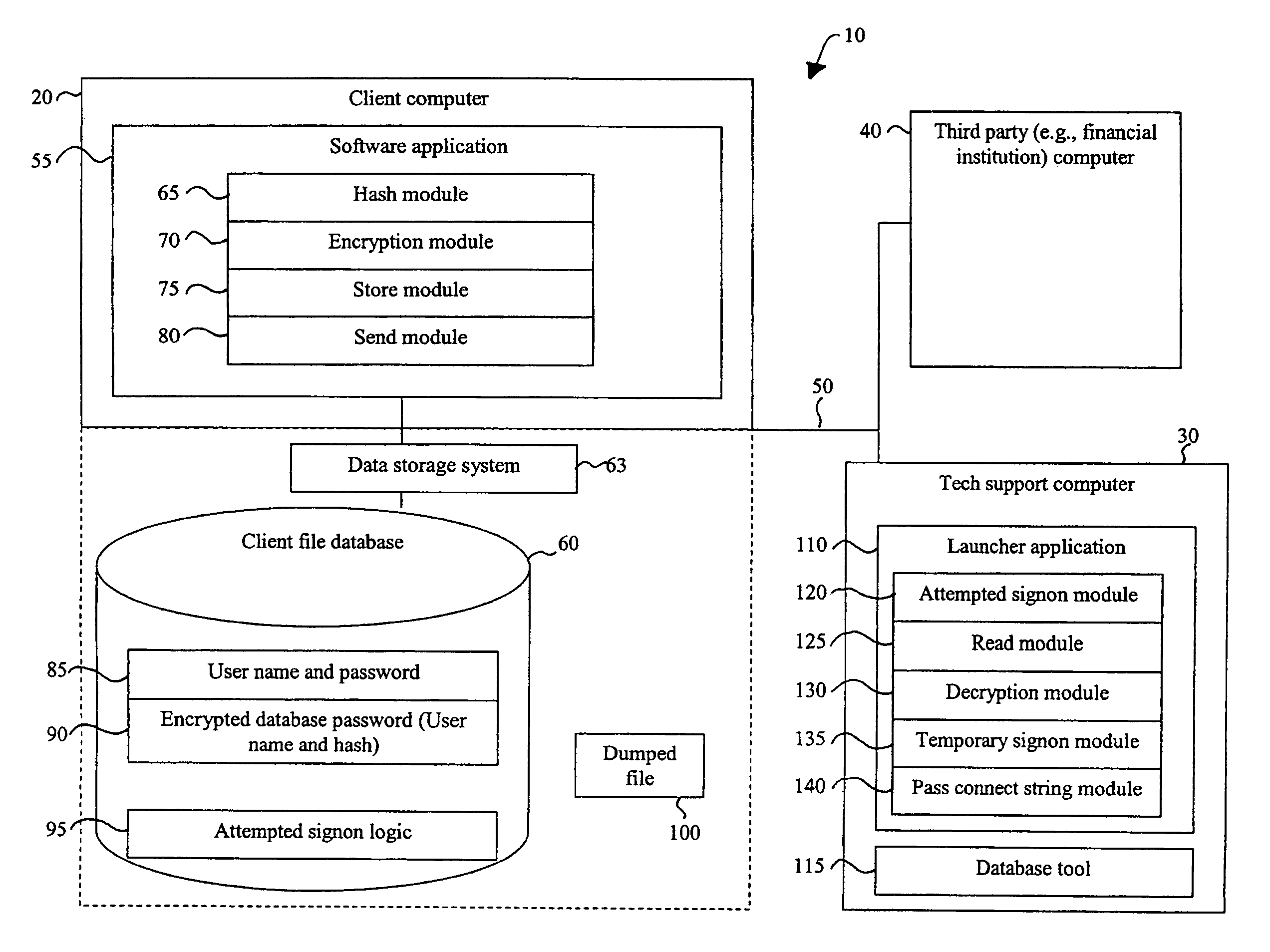
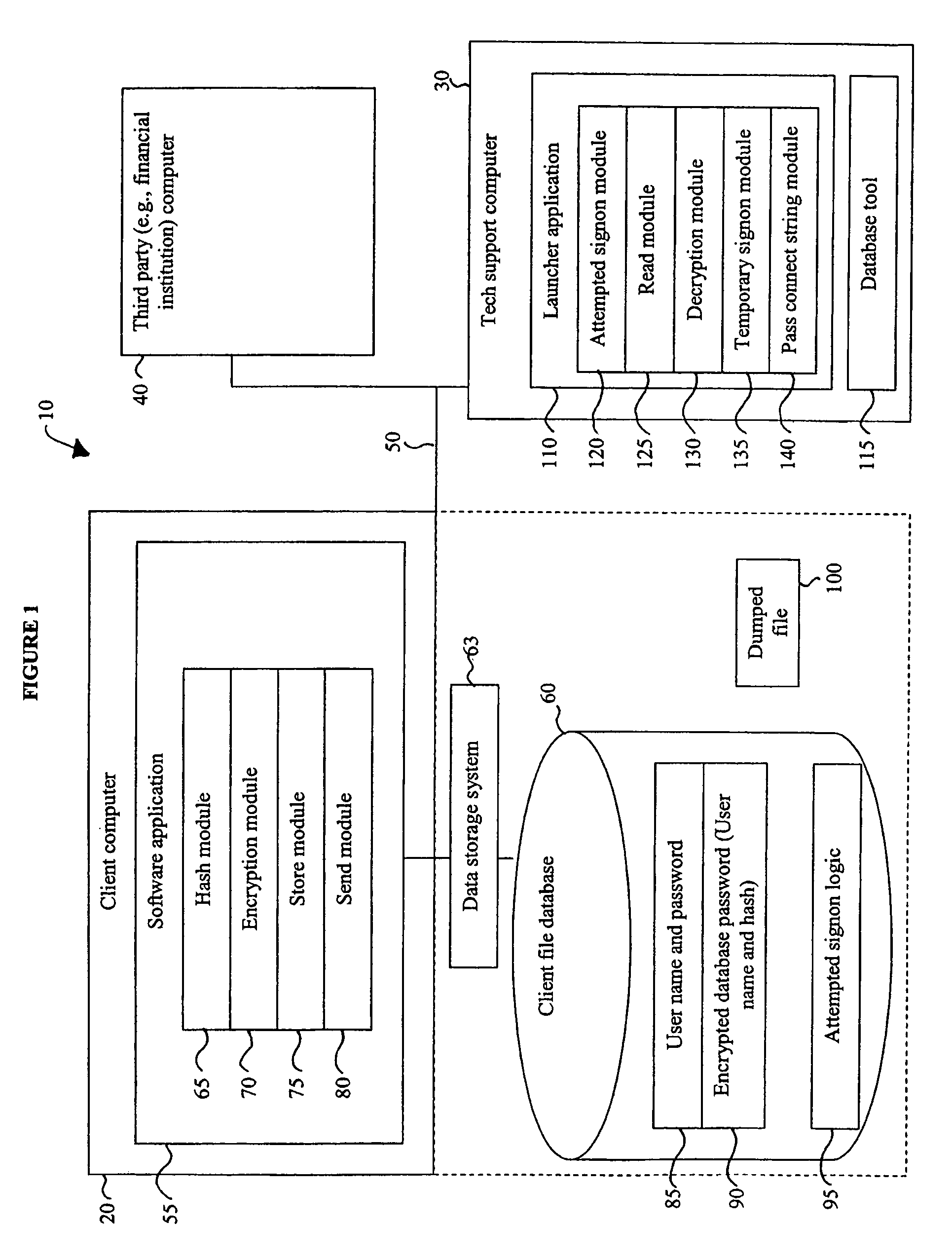
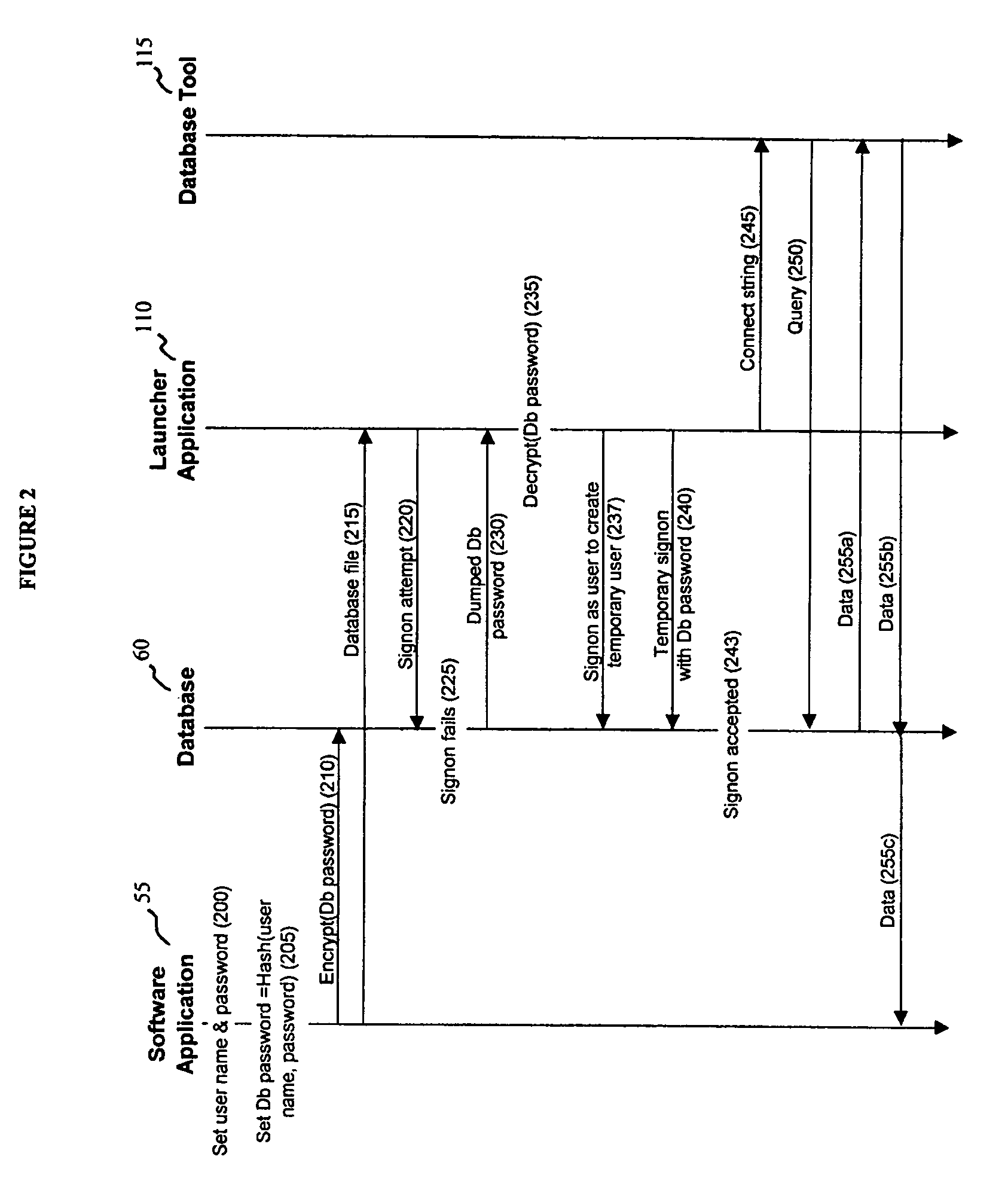
Recovery access to secure data
ActiveUS7644285B1Improve securityImprove user securityKey distribution for secure communicationDigital data processing detailsInternet privacyPassword
A security mechanism affords data recovery engineers the ability to access and recover secure data from user files without knowledge of the user's password. The mechanism uses a launcher application to access the database by establishing a temporary, restricted user session. The launcher application also passes a handle to an industry standard database tool, allowing the data recovery engineer to recover the user file data. The recovered data then can be accessed by the software application.
Owner:INTUIT INC
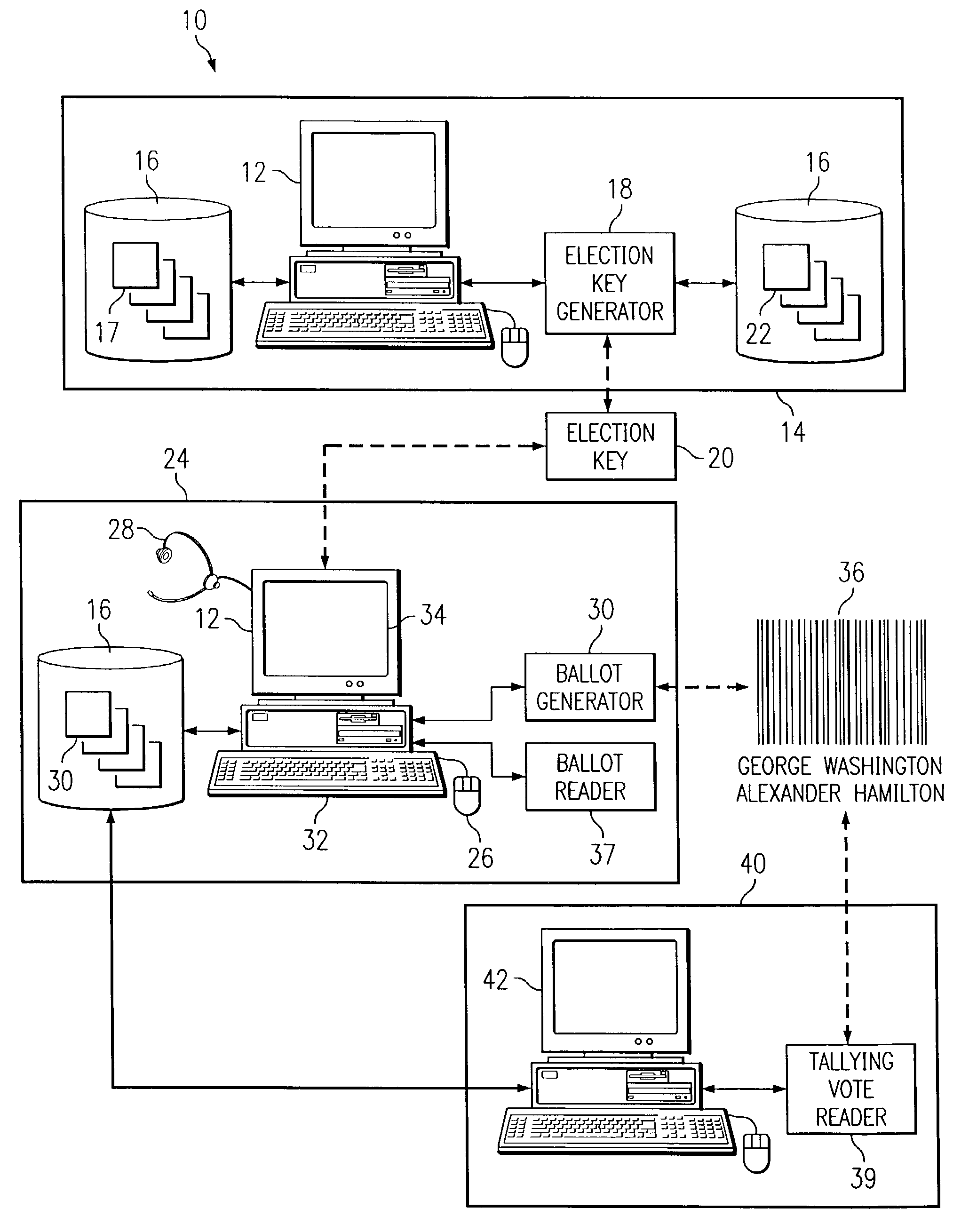
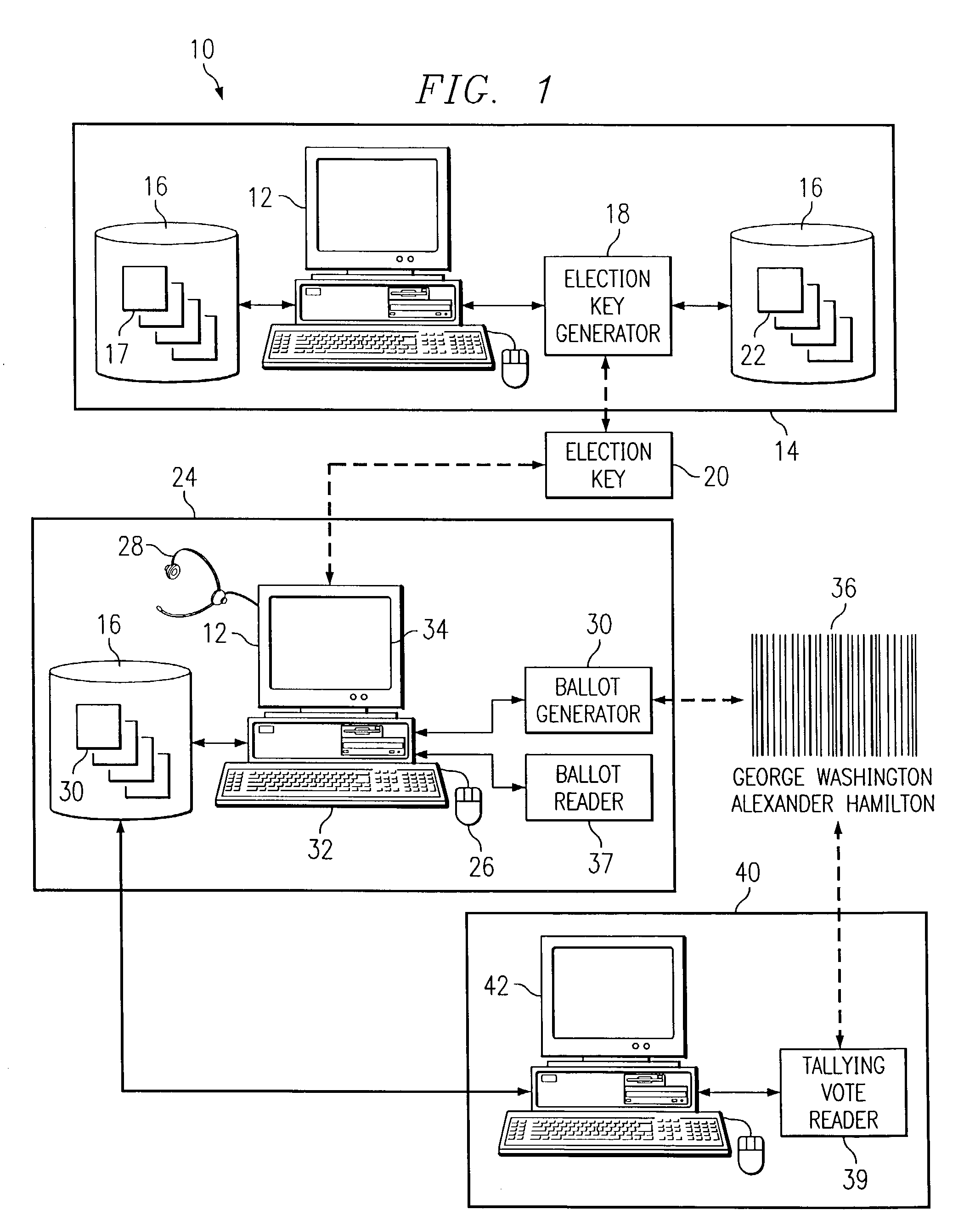
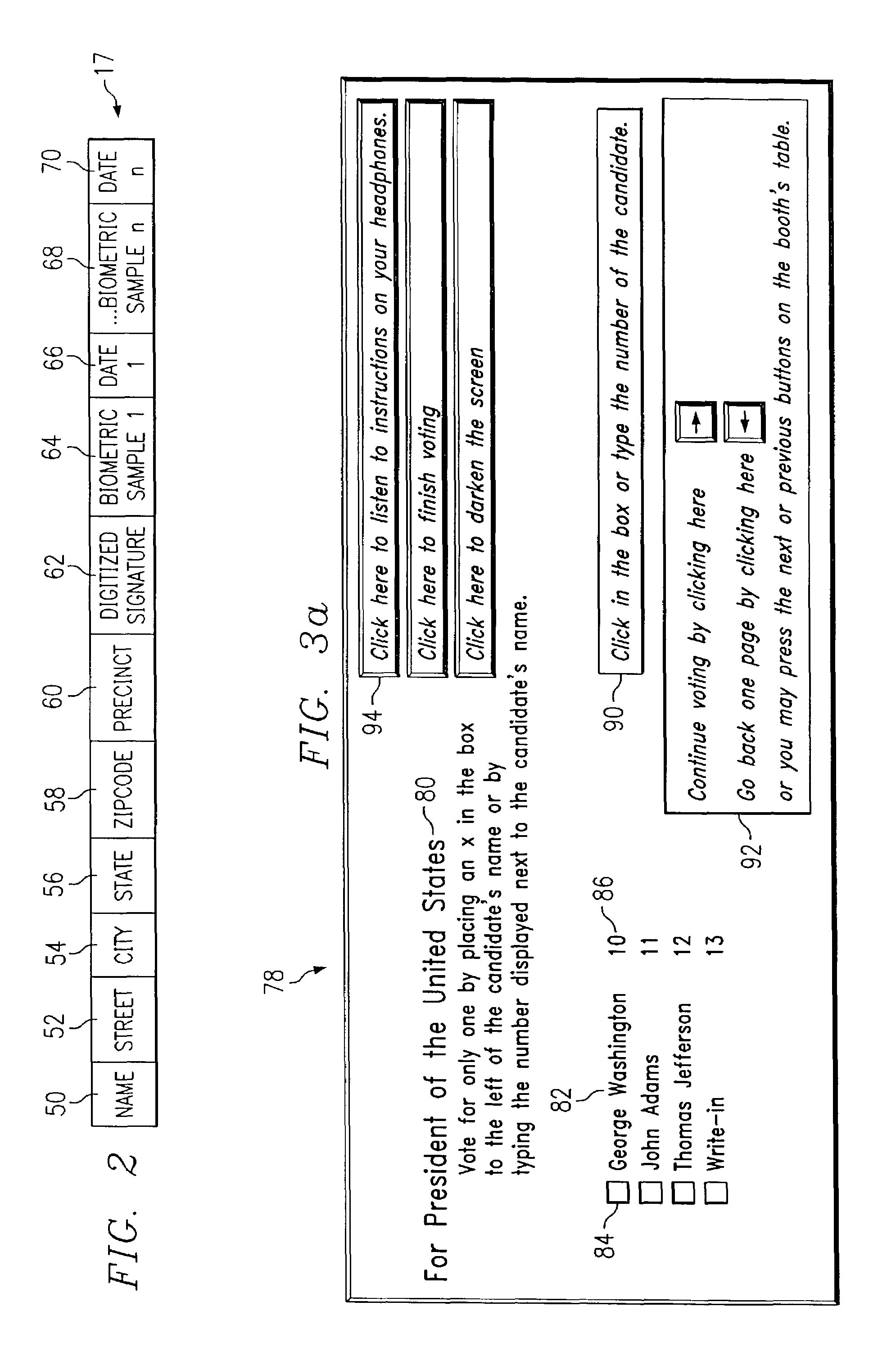
Advanced voting system and method
InactiveUS7306148B1Disadvantages and and reduced eliminatedMethods and reduced eliminatedVoting apparatusCo-operative working arrangementsMultimedia
According to one embodiment of the present invention, an advanced voting system includes one or more computing devices. The one or more computing devices display ballot questions to the voter and receive interactive voter selections from the voter. A ballot generator generates encoded ballots encoded with the voter selections.
Owner:POPULEX CORP
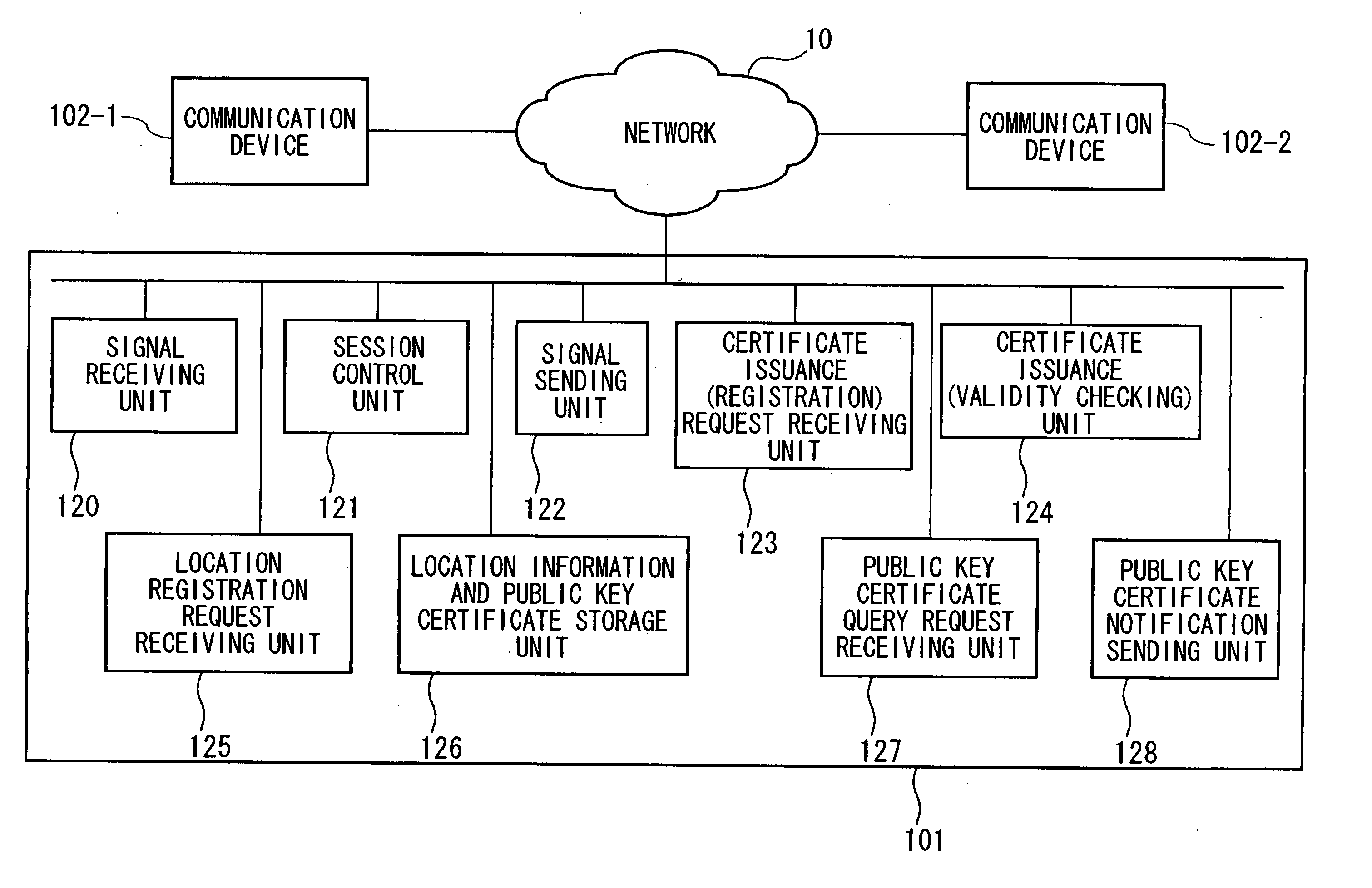
Session control server, communication system
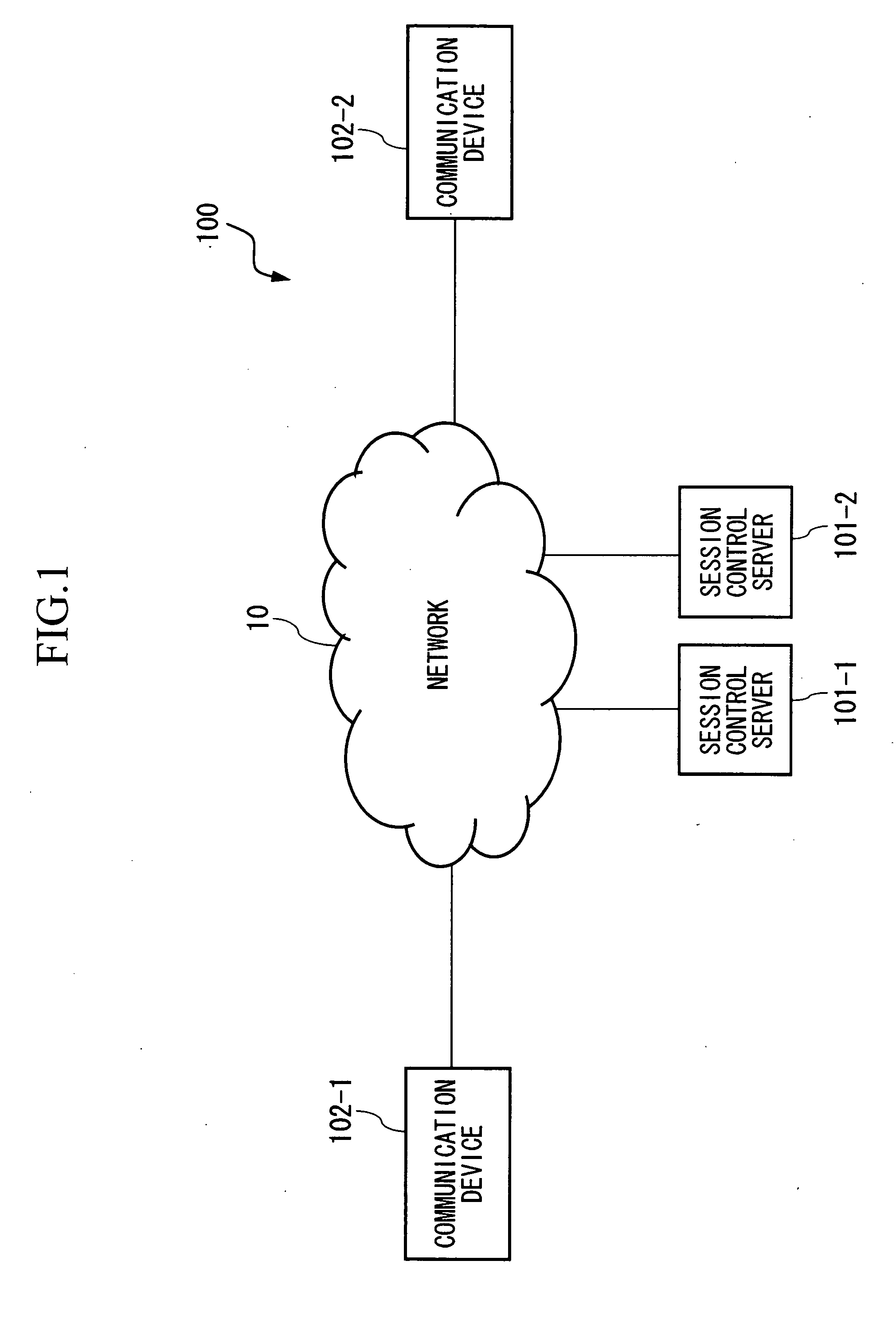
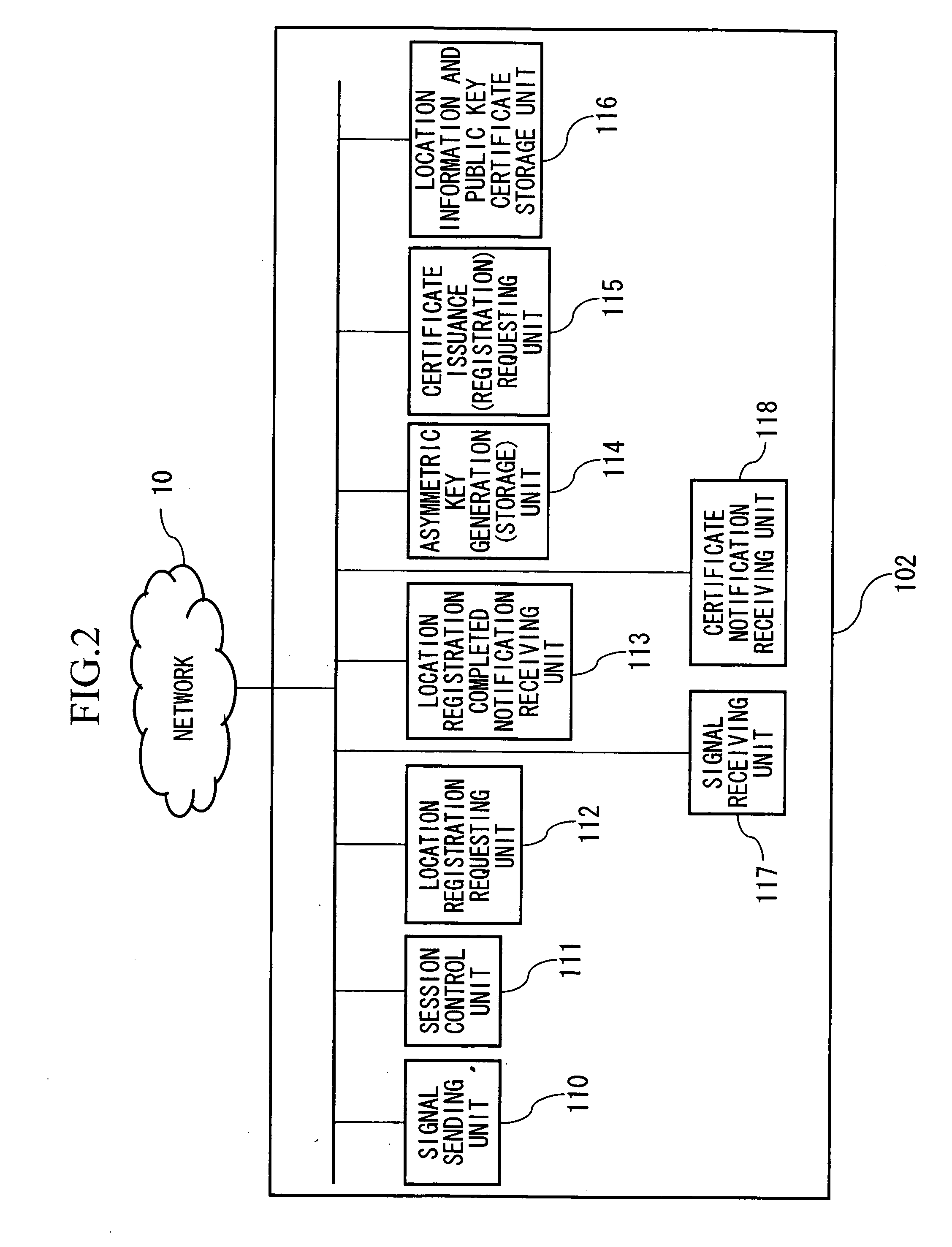
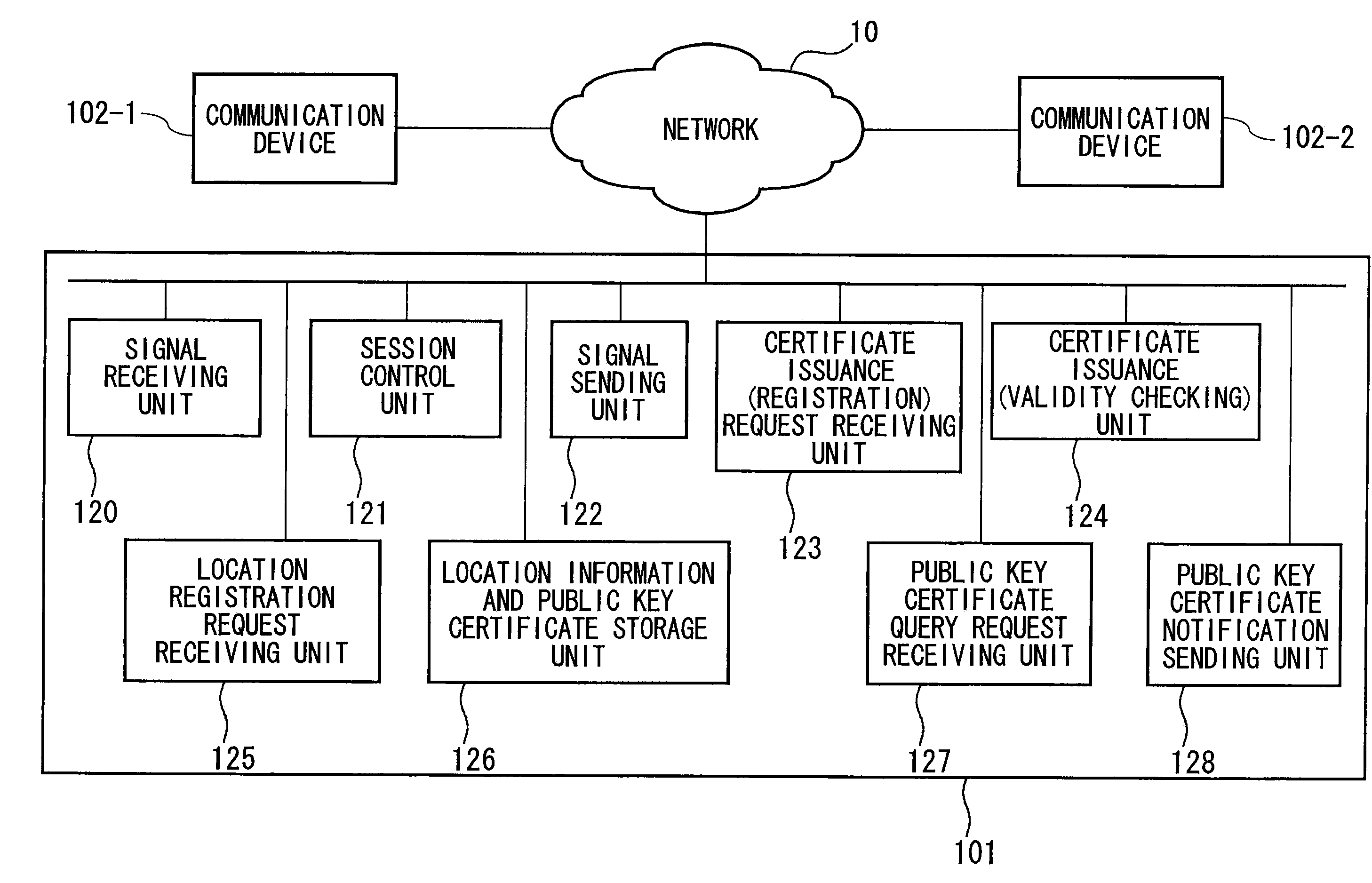
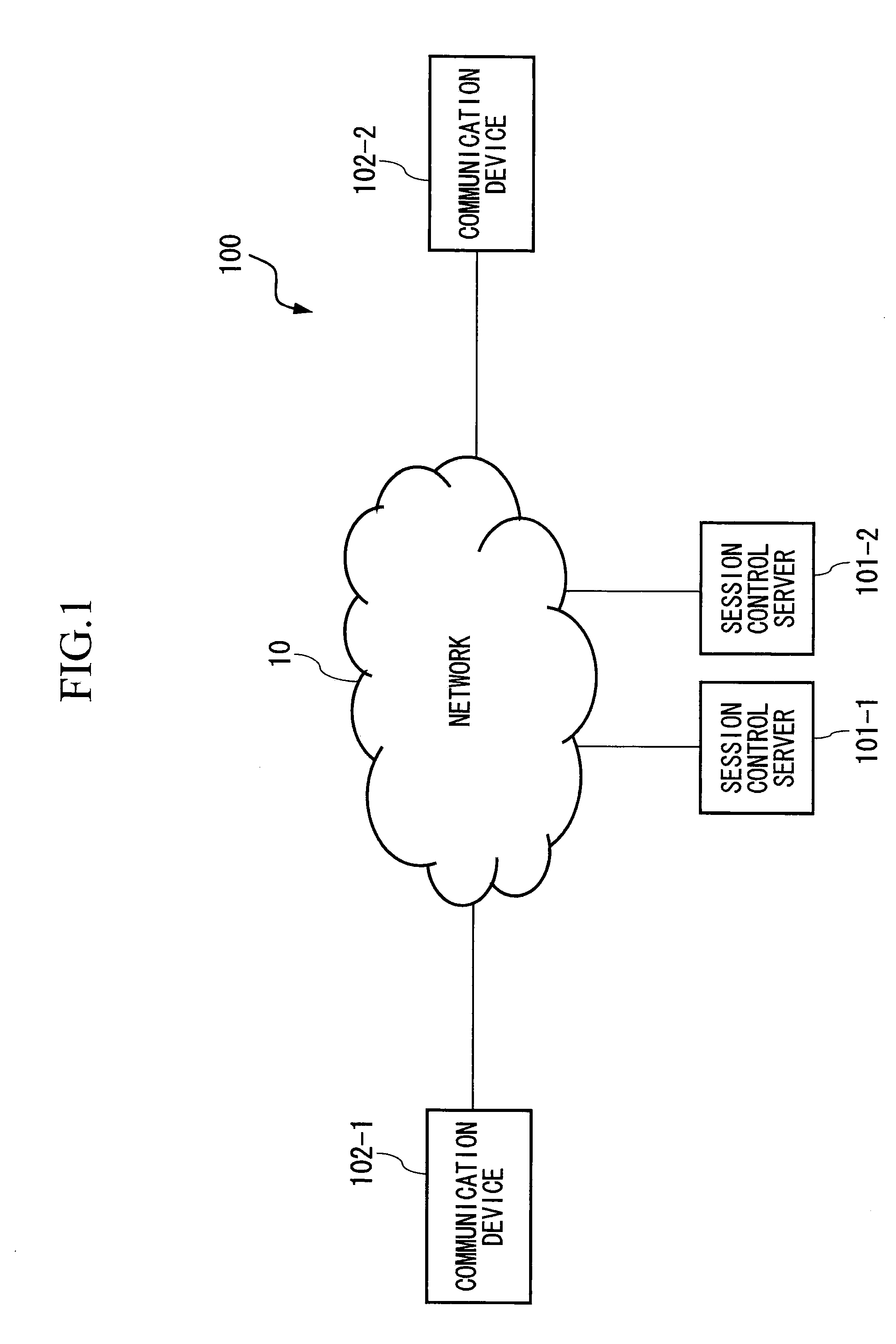
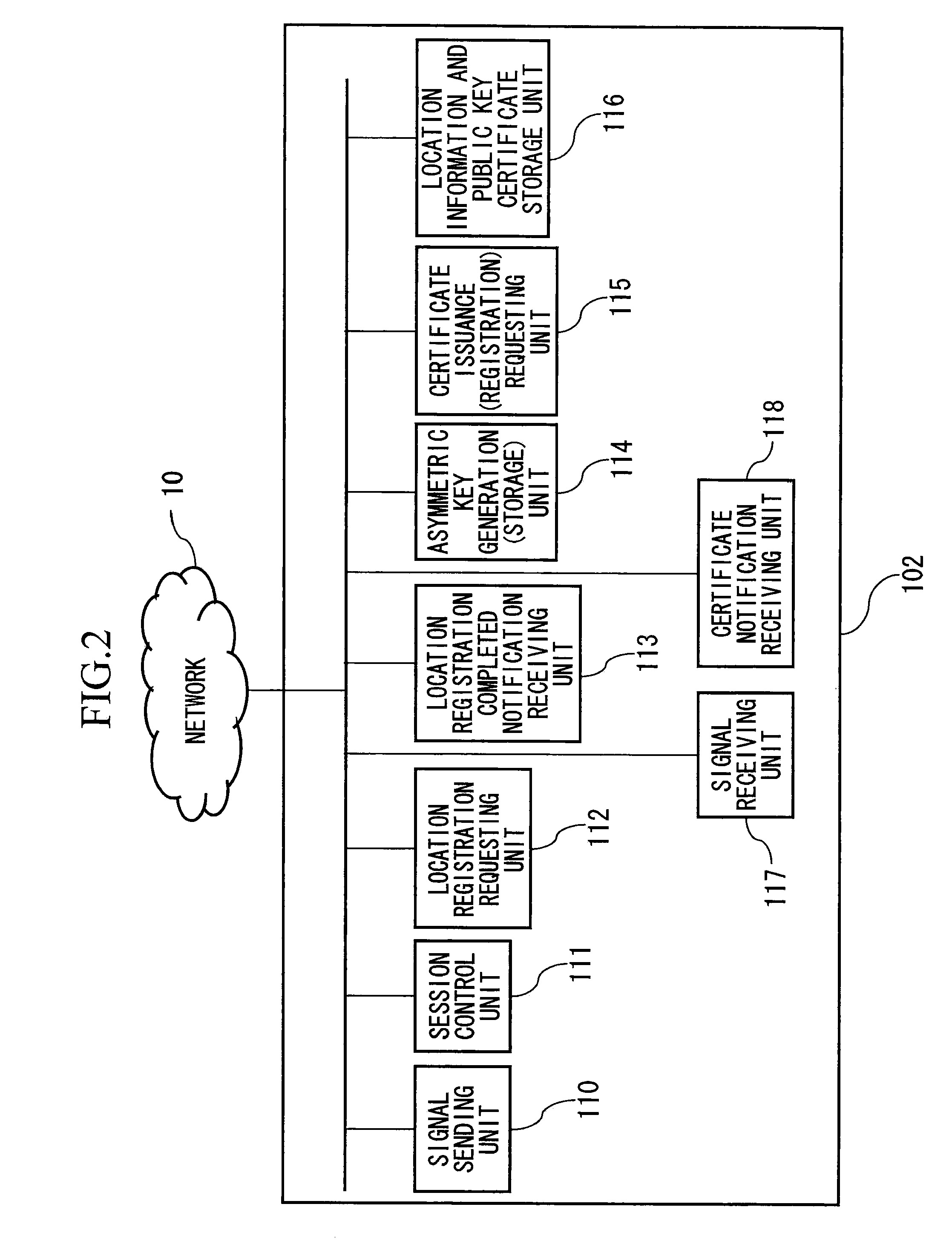
InactiveUS20060047960A1Easy to checkMaintaining secrecyKey distribution for secure communicationUser identity/authority verificationCommunications systemSession control
A communication device, connected via a network so as to be able to communicate with a session control server, and which establishes a session with another communication device by performing signal transmission to and reception from the session control server, includes: a unit which generates an asymmetric key pair; a request unit which requests certificate issuance for a public key in the asymmetric key pair; a receiving unit which receives notification of public key issuance completion from the session control server; a storage unit which stores a public key certificate which has been received; a sending unit which sends a location registration request of a communication device to the session control server; and a receiving unit which receives a location registration completed notification which includes a term of validity from the session control server; and which sends a location registration request and a certificate issuance request as a combined request.
Owner:NIPPON TELEGRAPH & TELEPHONE CORP
Identity-based-encryption system with hidden public key attributes
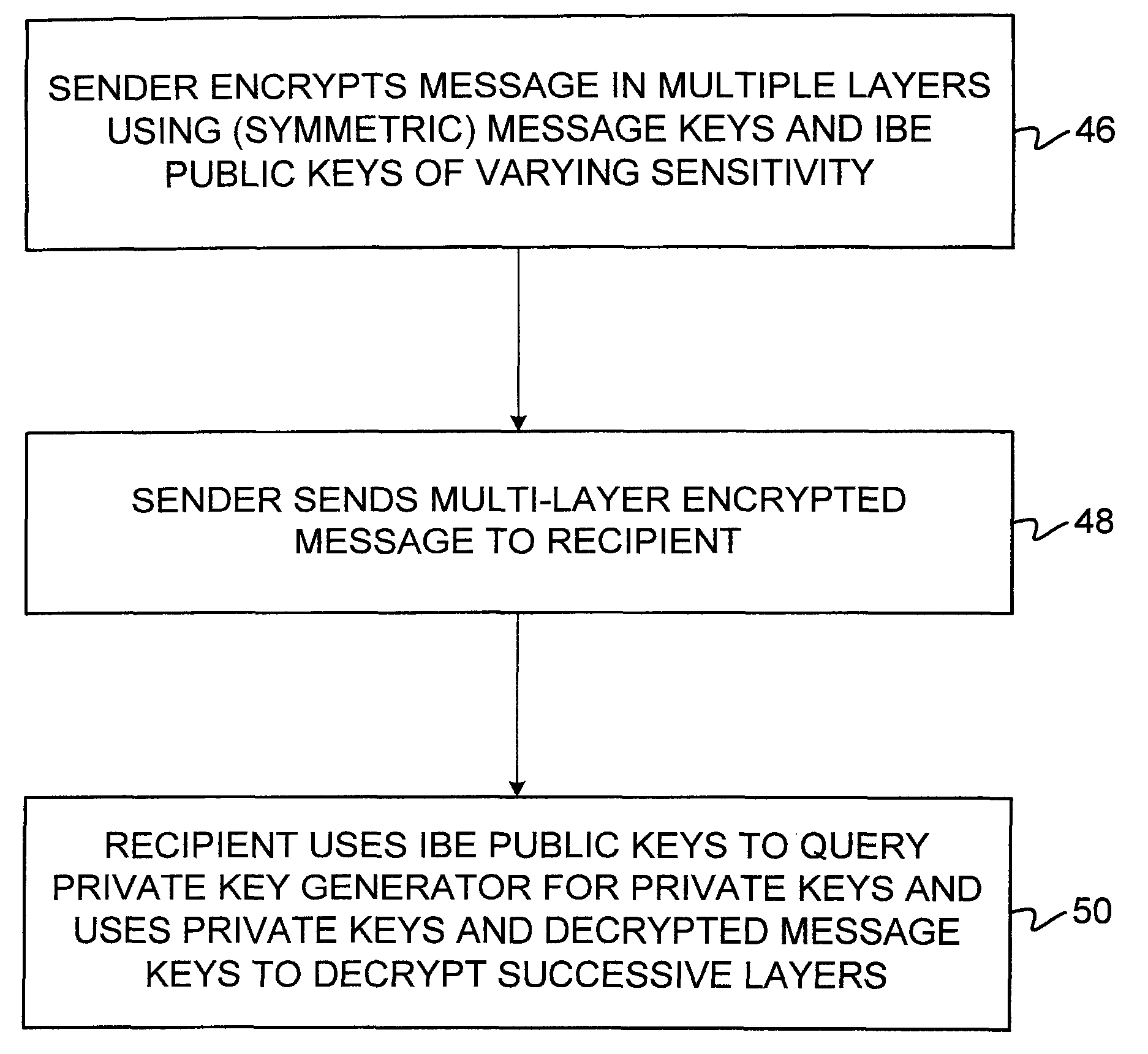
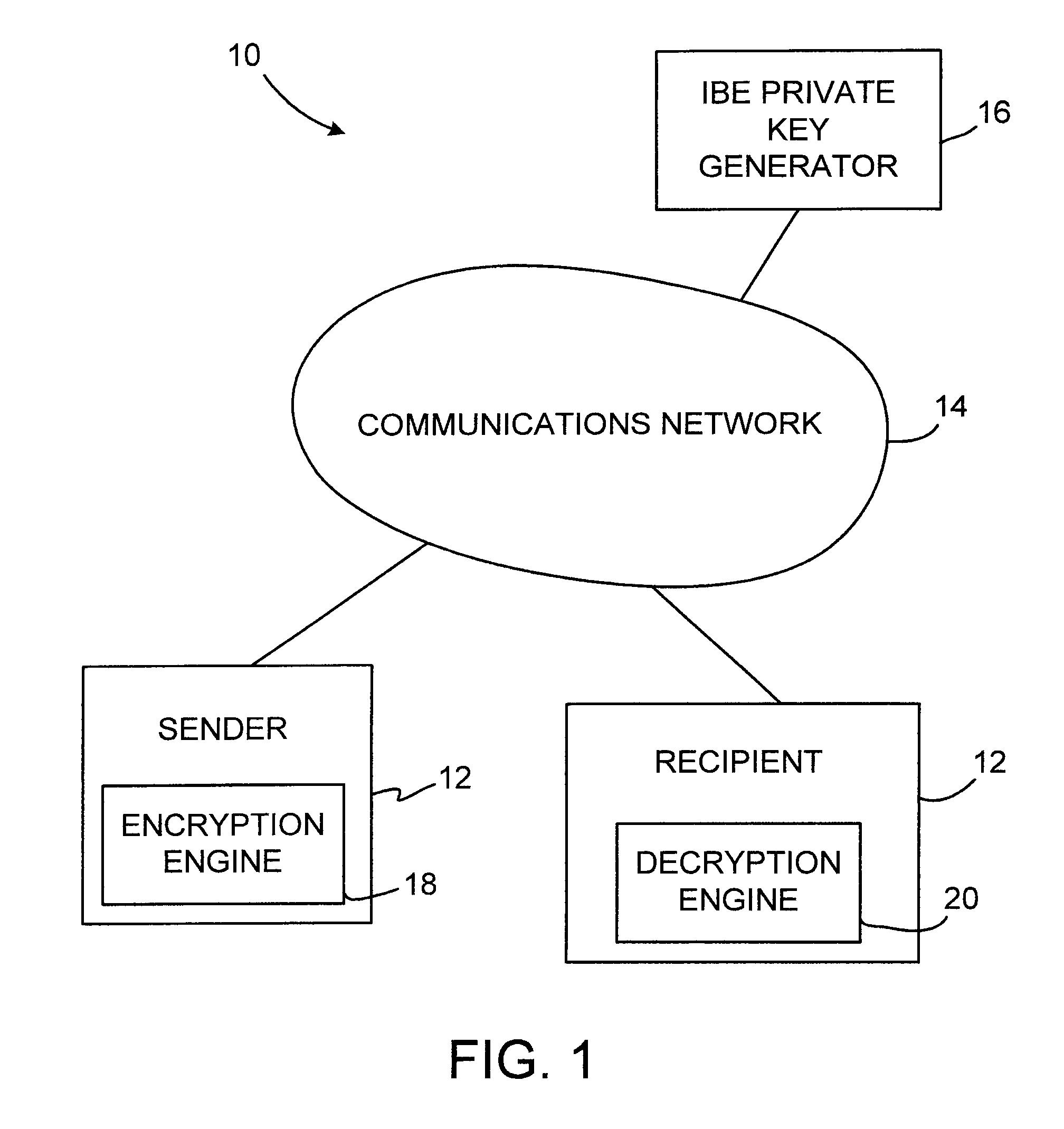
InactiveUS7961879B1Improve efficiencyReduce overheadKey distribution for secure communicationInformation securityEncryption system
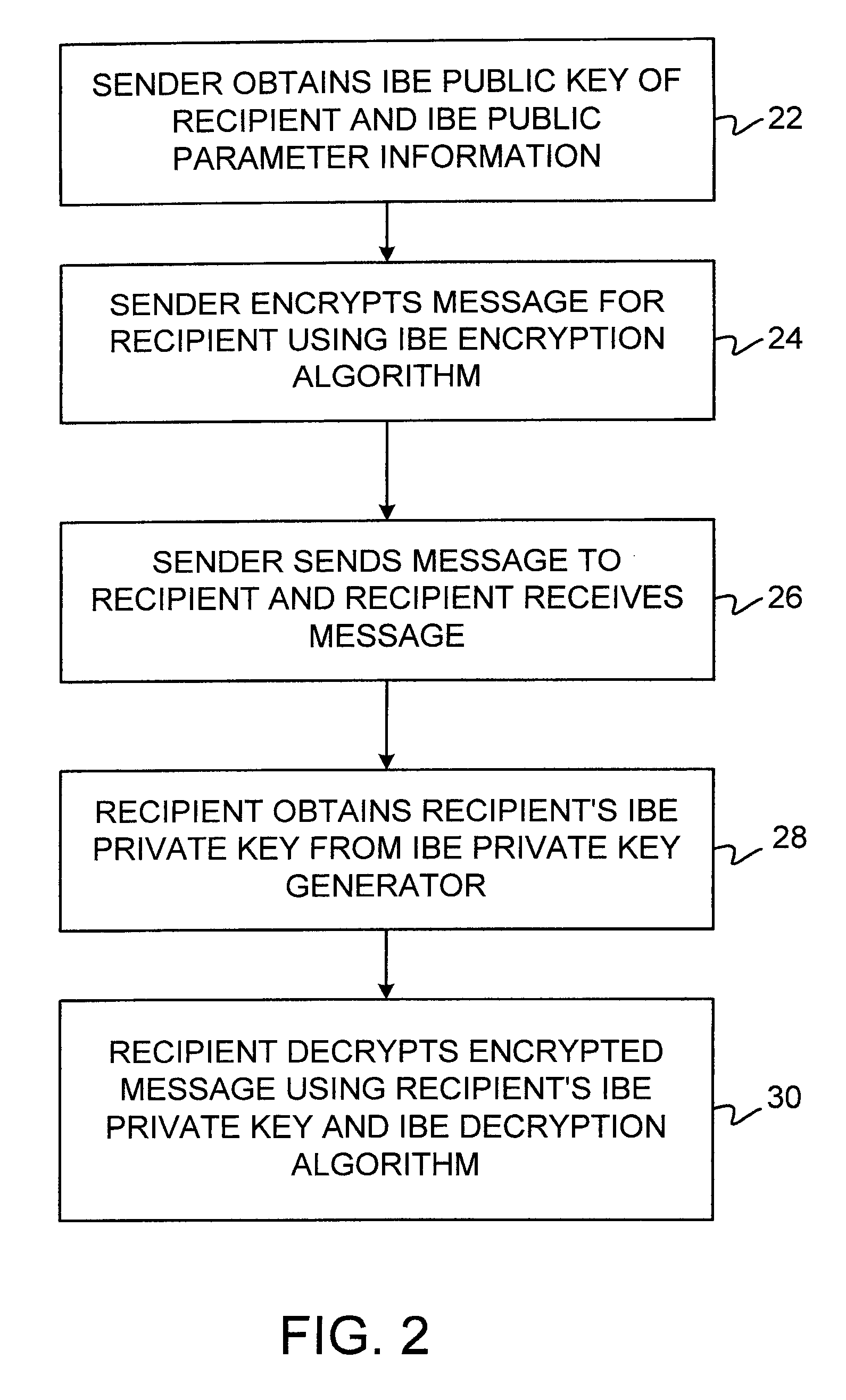
A system is provided that uses identity-based encryption (IBE) to allow a sender to securely convey information in a message to a recipient over a communications network. IBE public key information may be used to encrypt messages and corresponding IBE private key information may be used to decrypt messages. Information on which IBE public key information was used in encrypting a given message may be provided to the message recipient with the message. Multiple IBE public keys may be used to encrypt a single message. A less sensitive IBE public key may be used to encrypt a more sensitive public key, so that the more sensitive public key can remain hidden as it is sent to the recipient.
Owner:MICRO FOCUS LLC
Wireless communication device, mac address management system, wireless communication method, and program
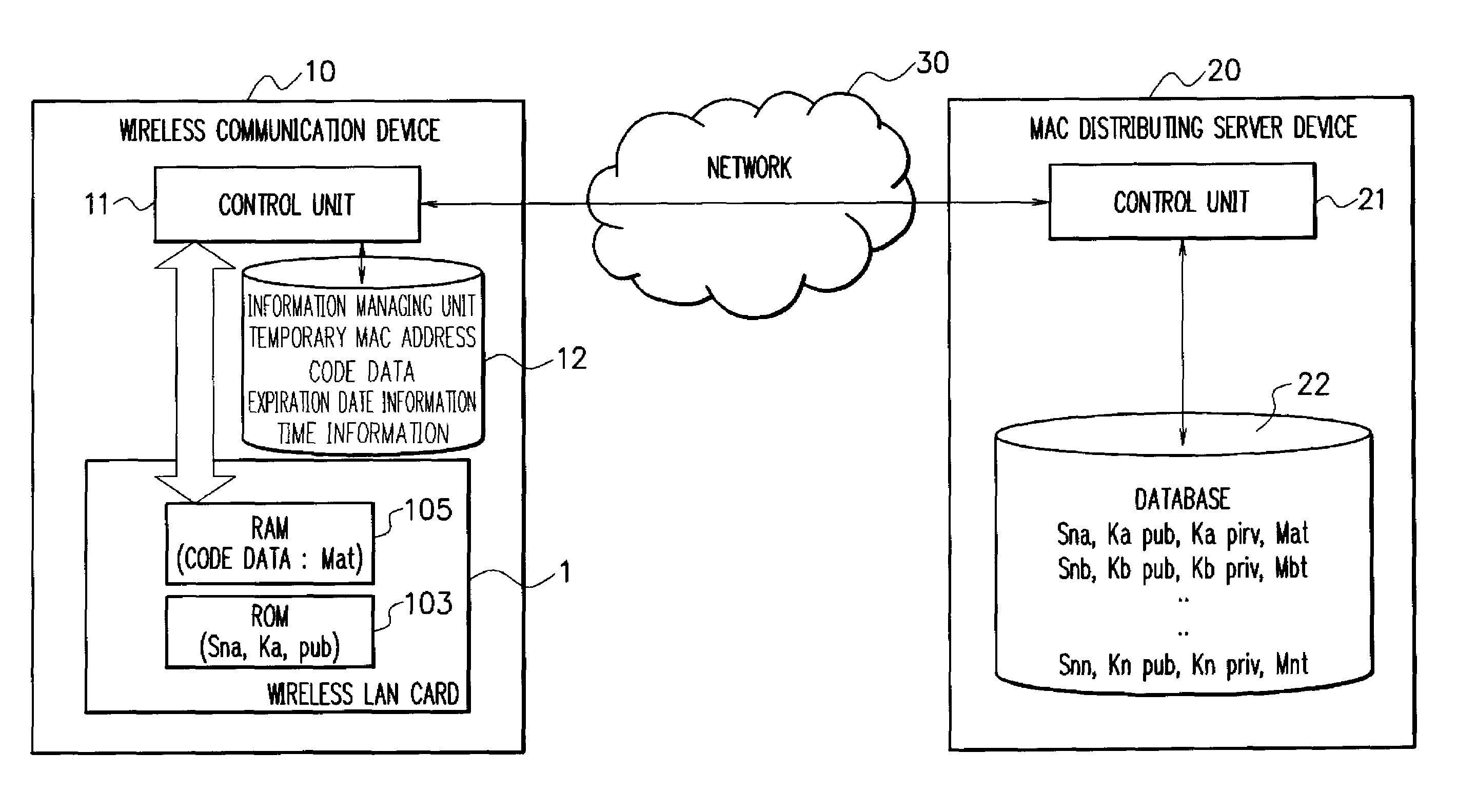
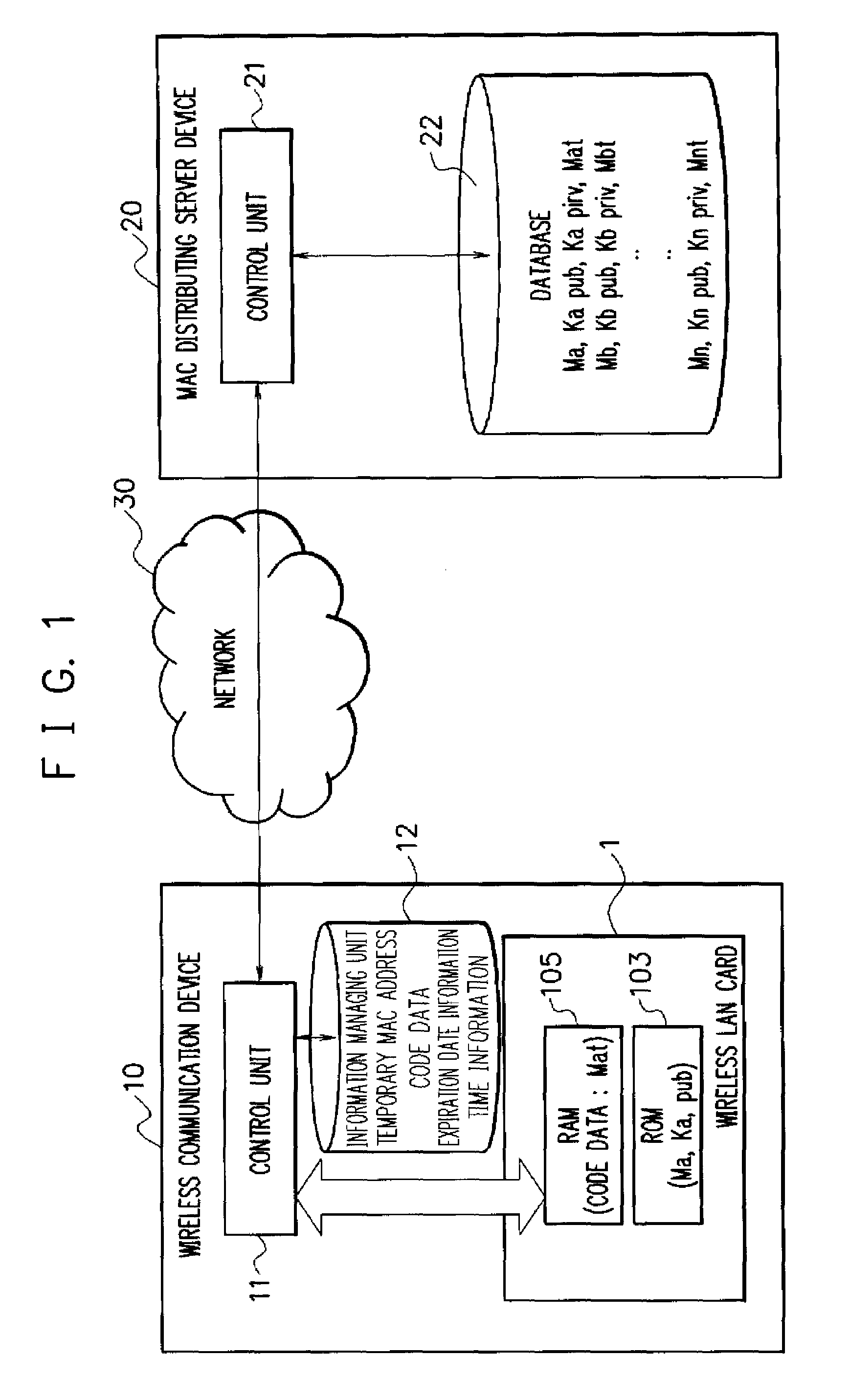
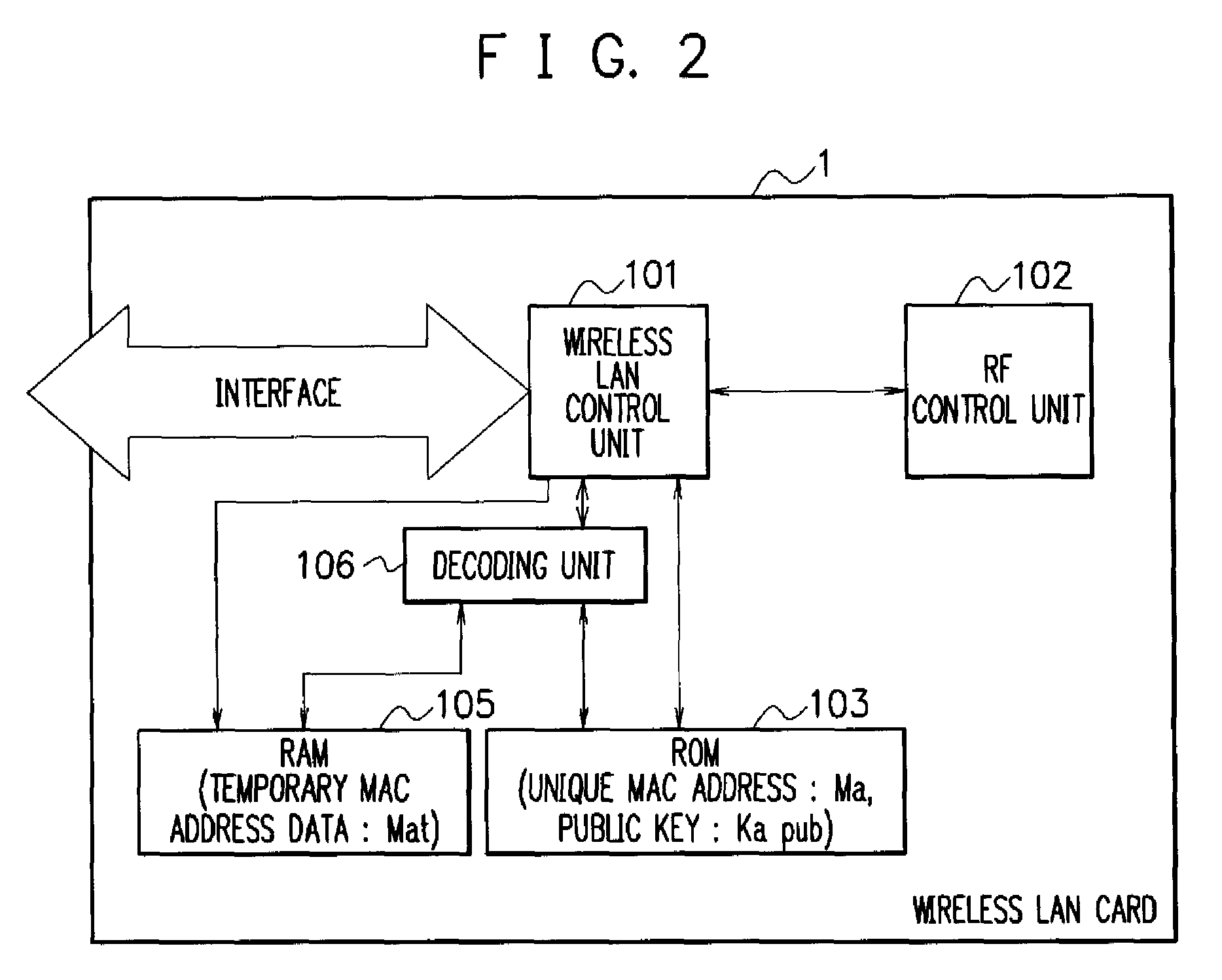
ActiveUS20070211653A1Maintaining secrecyProtect user privacyUnauthorised/fraudulent call preventionEavesdropping prevention circuitsComputer hardwareDistributed servers
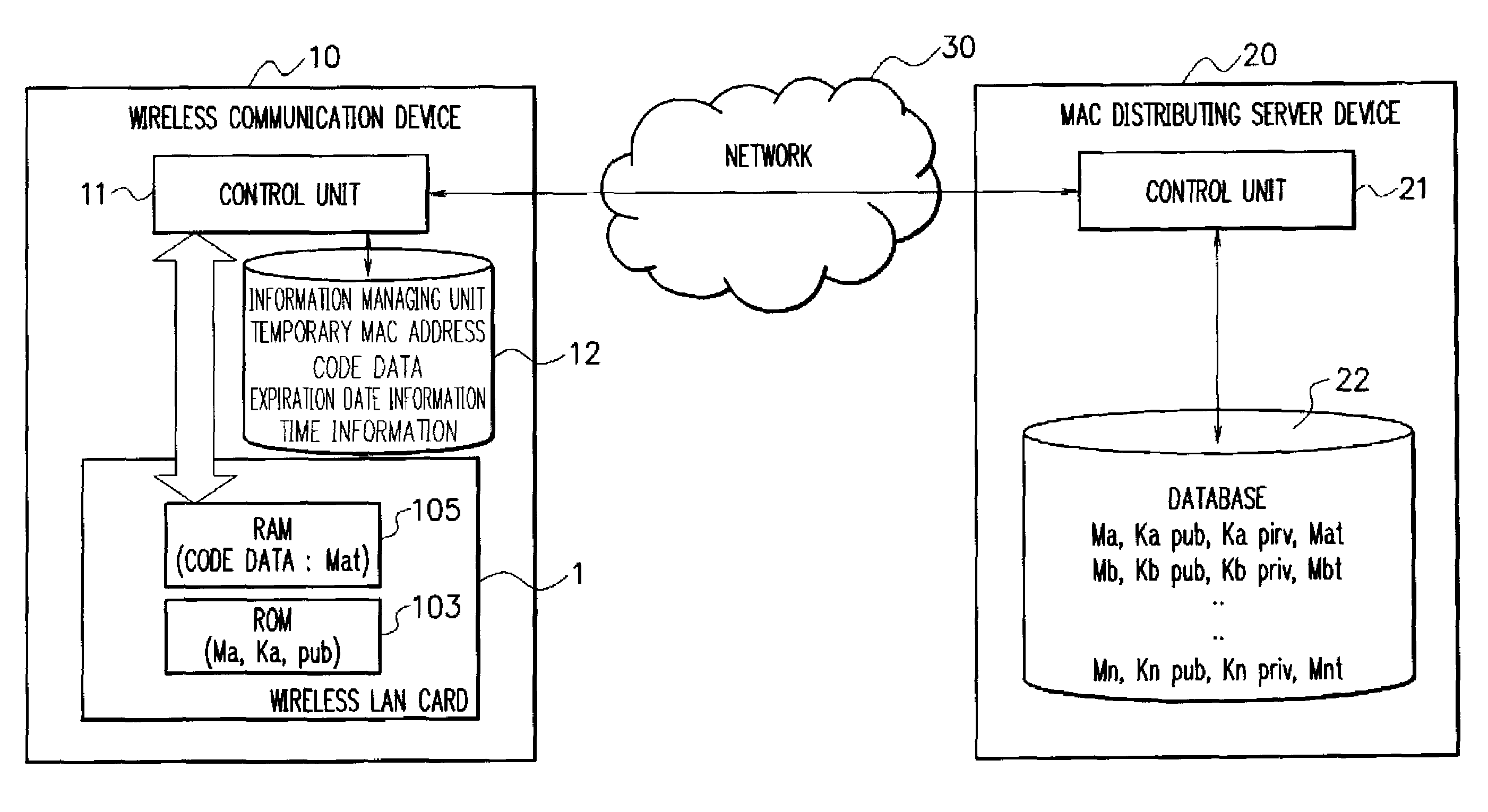
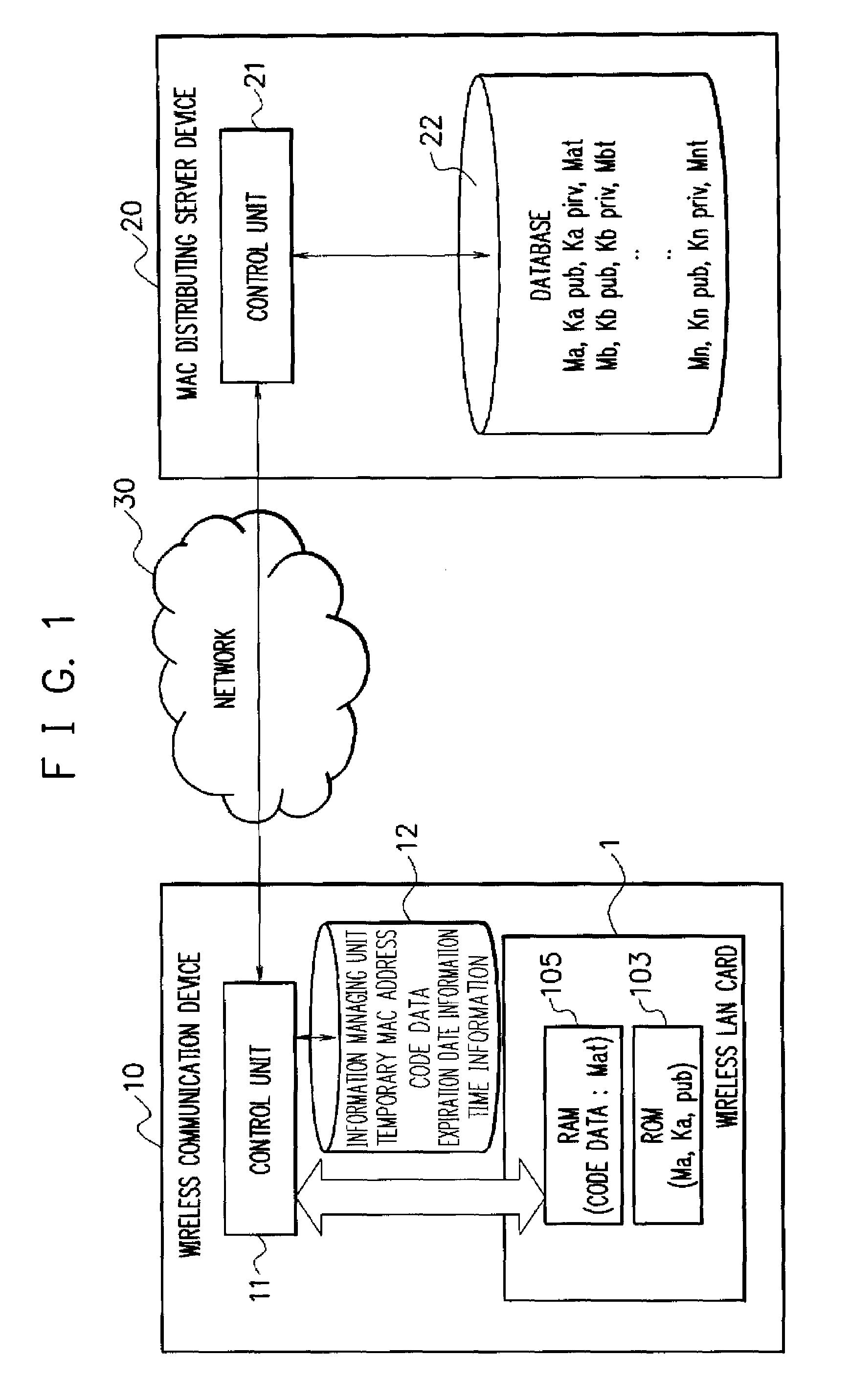
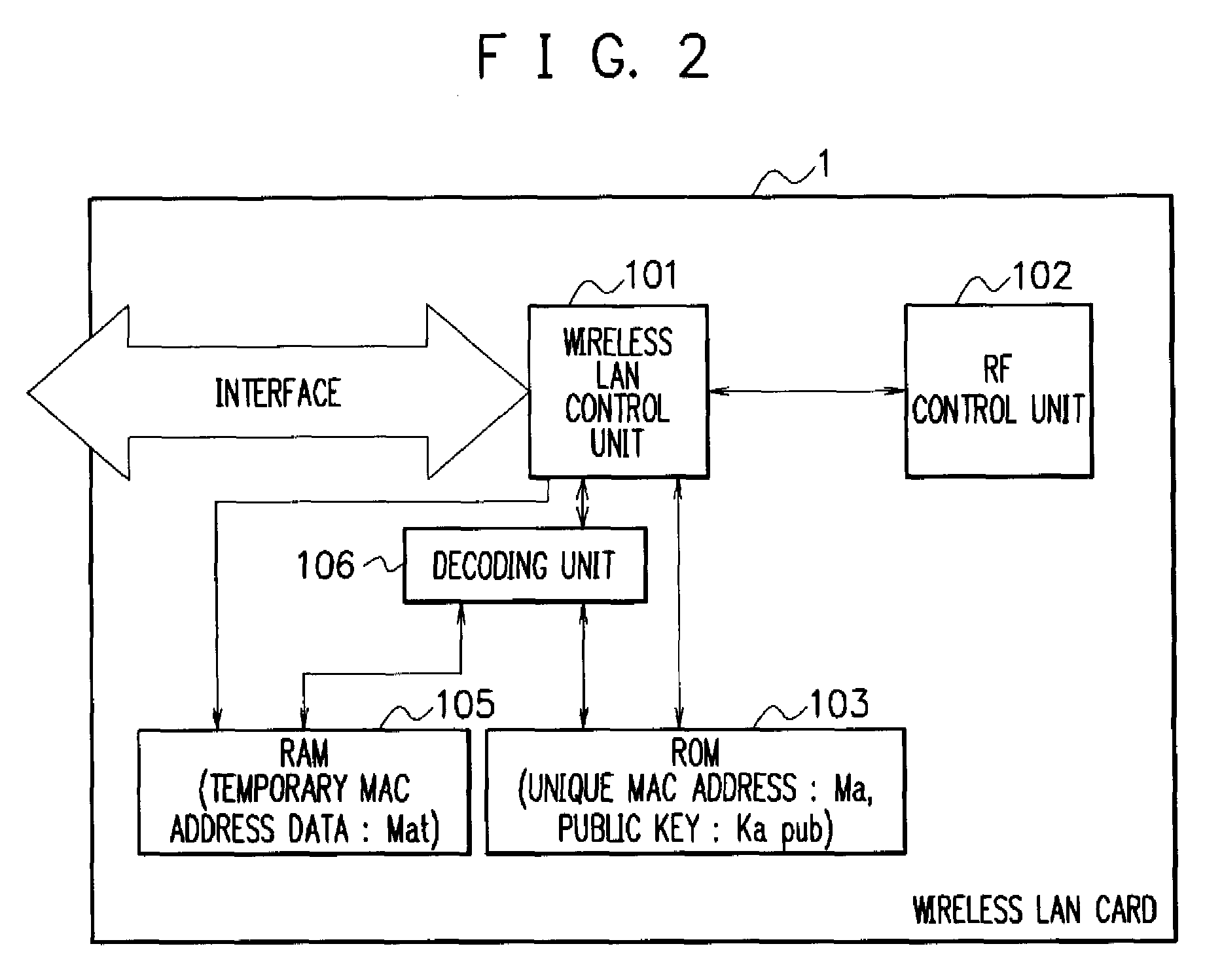
A MAC address management system acquires code data obtained by encoding a temporary MAC address that can be temporarily used and decodes the acquired code data to perform wireless communication. The MAC address management system includes a MAC distributing server device in which a temporary MAC address which can be temporarily used is stored and a wireless communication device that acquires the temporary MAC address from the MAC distributing server device and performs wireless communication by using the acquired temporary MAC address, the wireless communication device acquires code data obtained by encoding the temporary MAC address from the MAC distributing server device, decodes the acquired code data, and performs wireless communication by using the decoded temporary MAC address.
Owner:NEC CORP
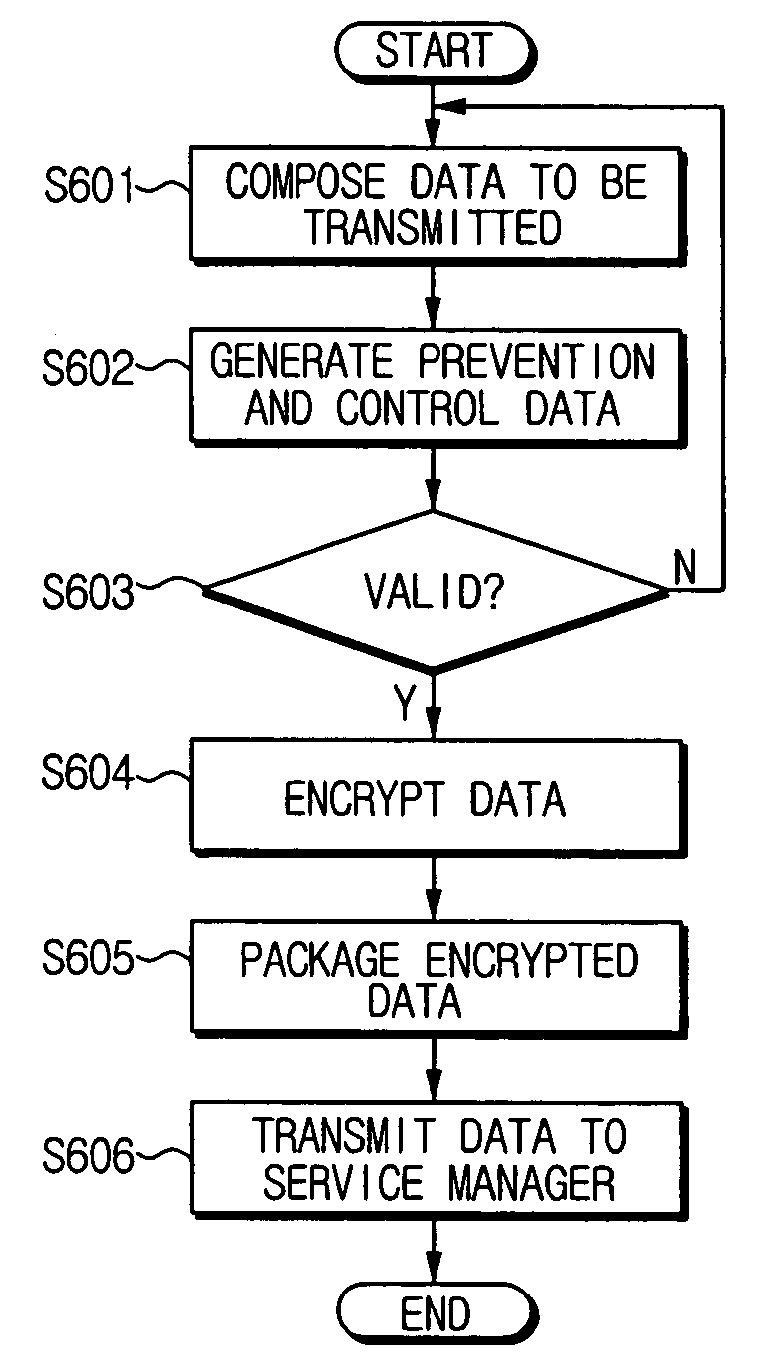
Apparatus and method of generating and detecting prevention and control data for verifying validity of data
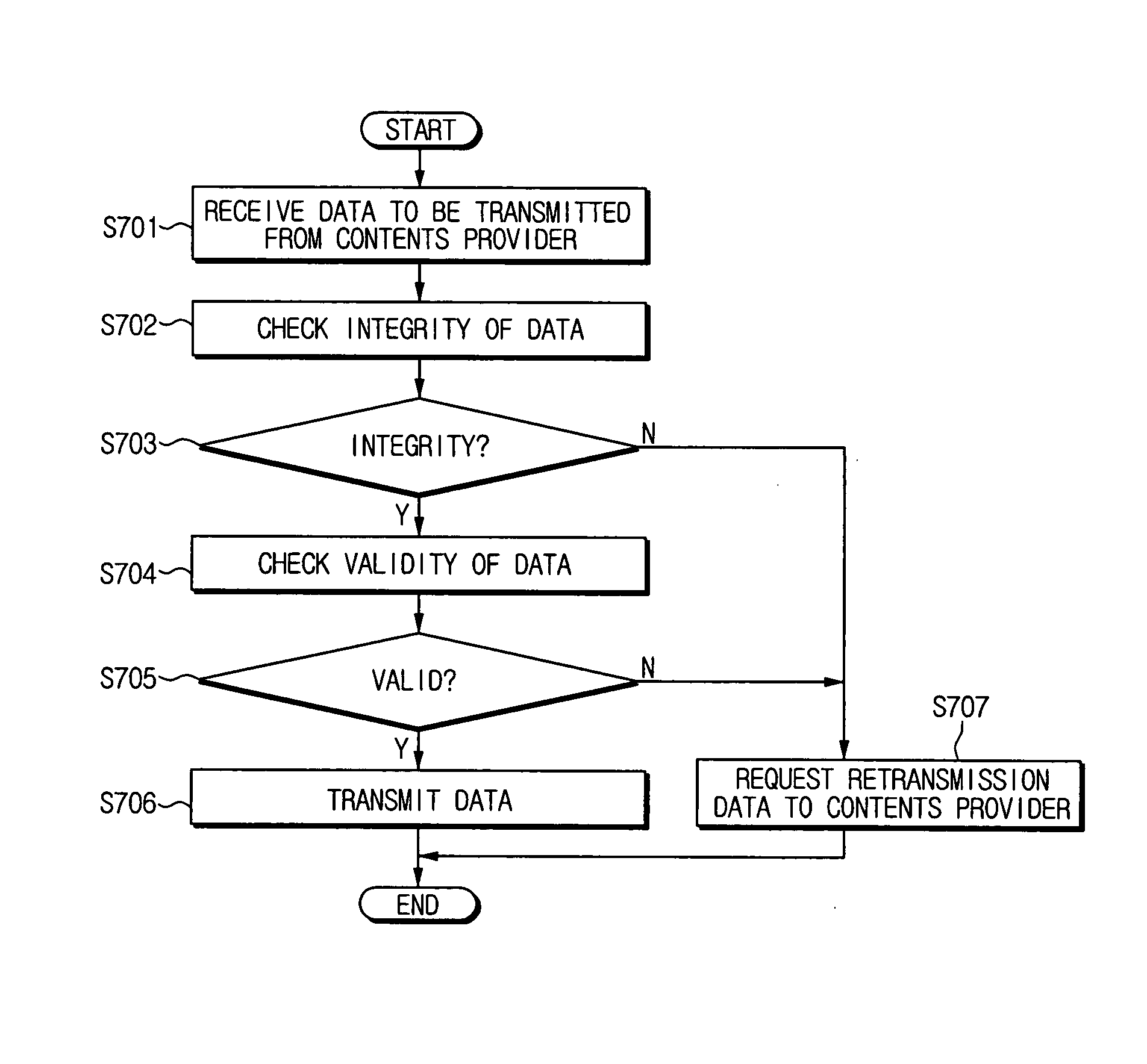
InactiveUS20060137024A1Maintaining secrecyVerify validityKey distribution for secure communicationDigital data processing detailsReal-time computingControl data
A method of generating prevention and control data to verify validity of data to be transmitted, and an apparatus to perform the method, the method including generating the prevention and control data according to composing information of the data to be transmitted, and transmitting the prevention and control data along with the data to be transmitted to verify the validity of the data to be transmitted.
Owner:SAMSUNG ELECTRONICS CO LTD
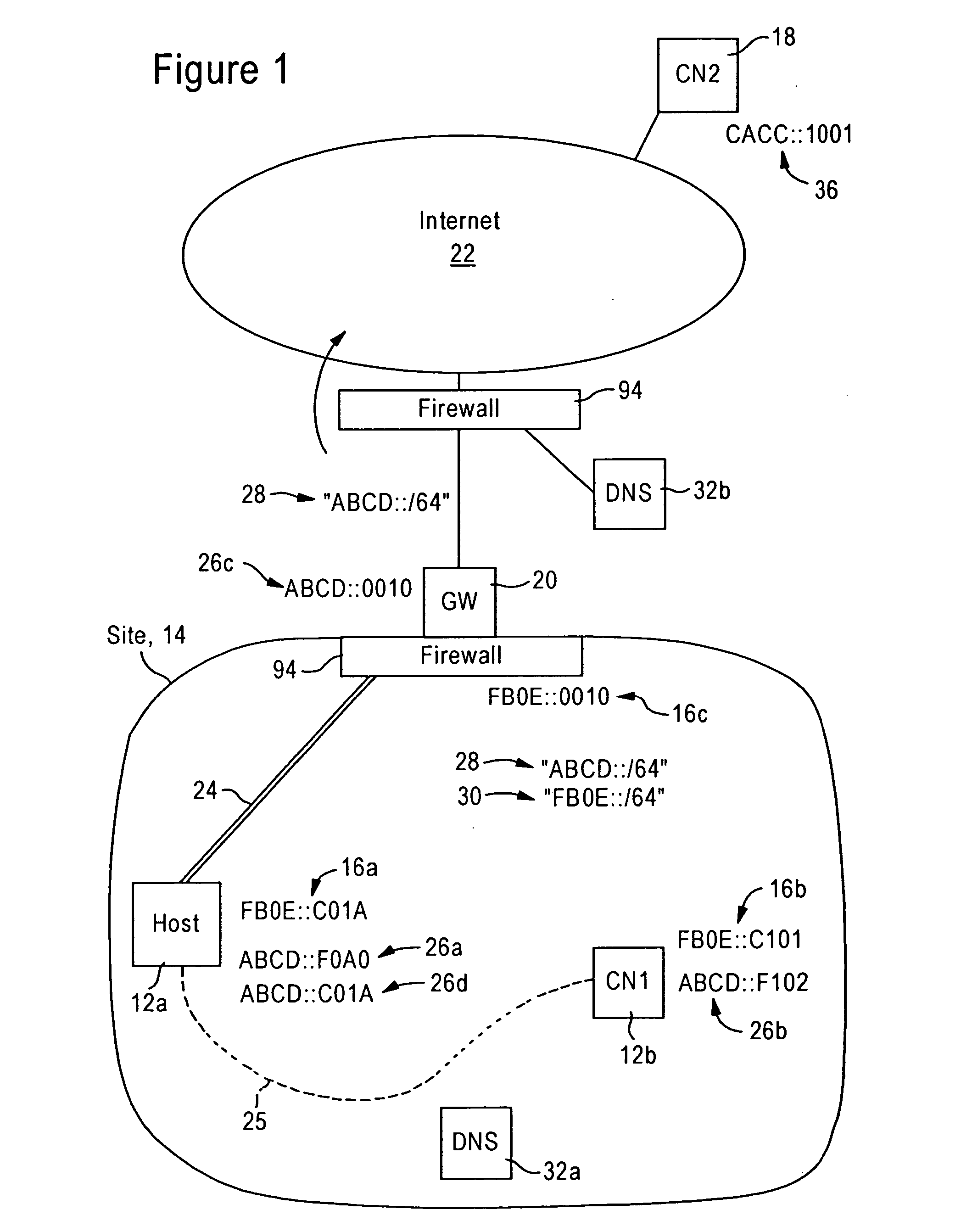
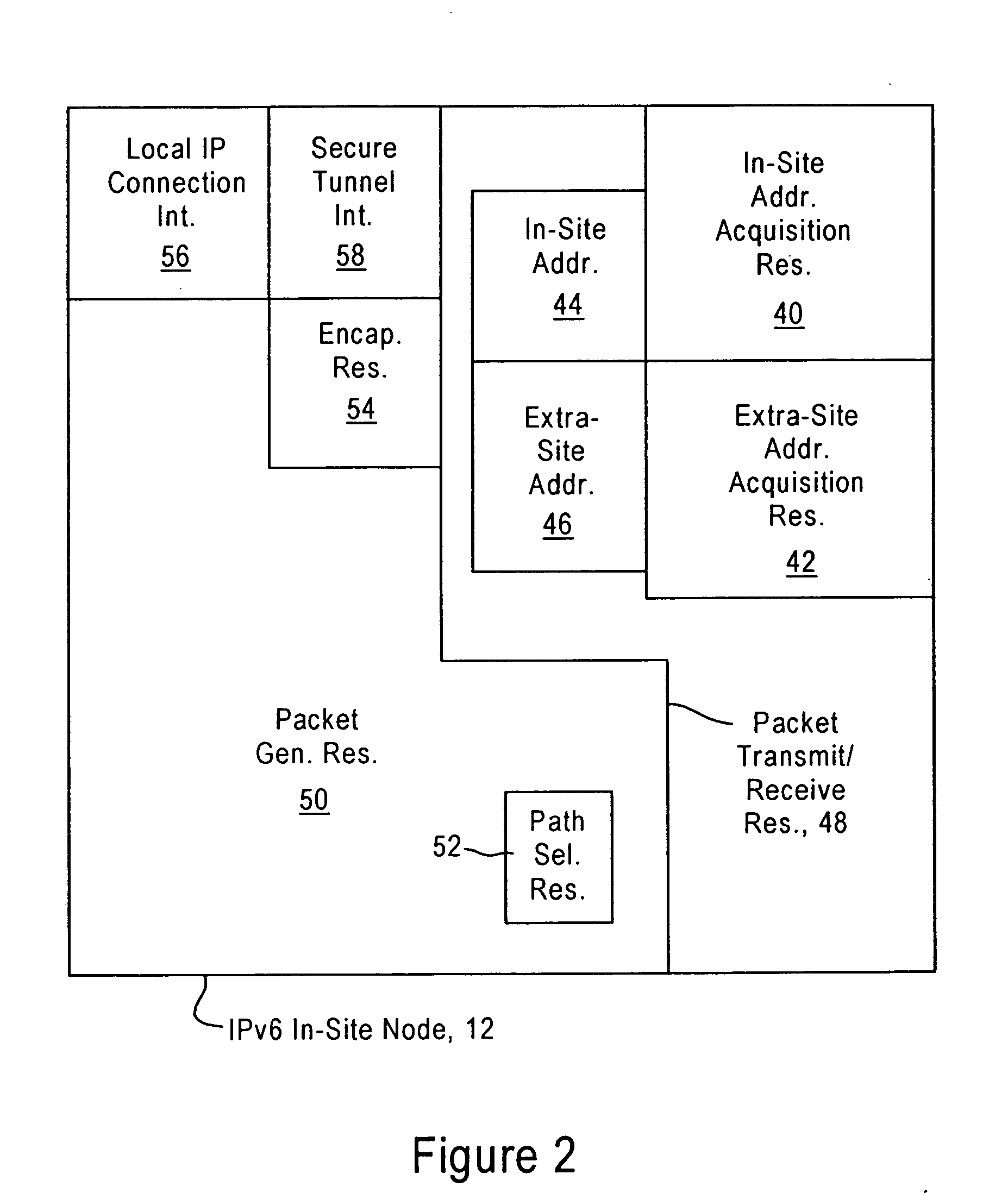
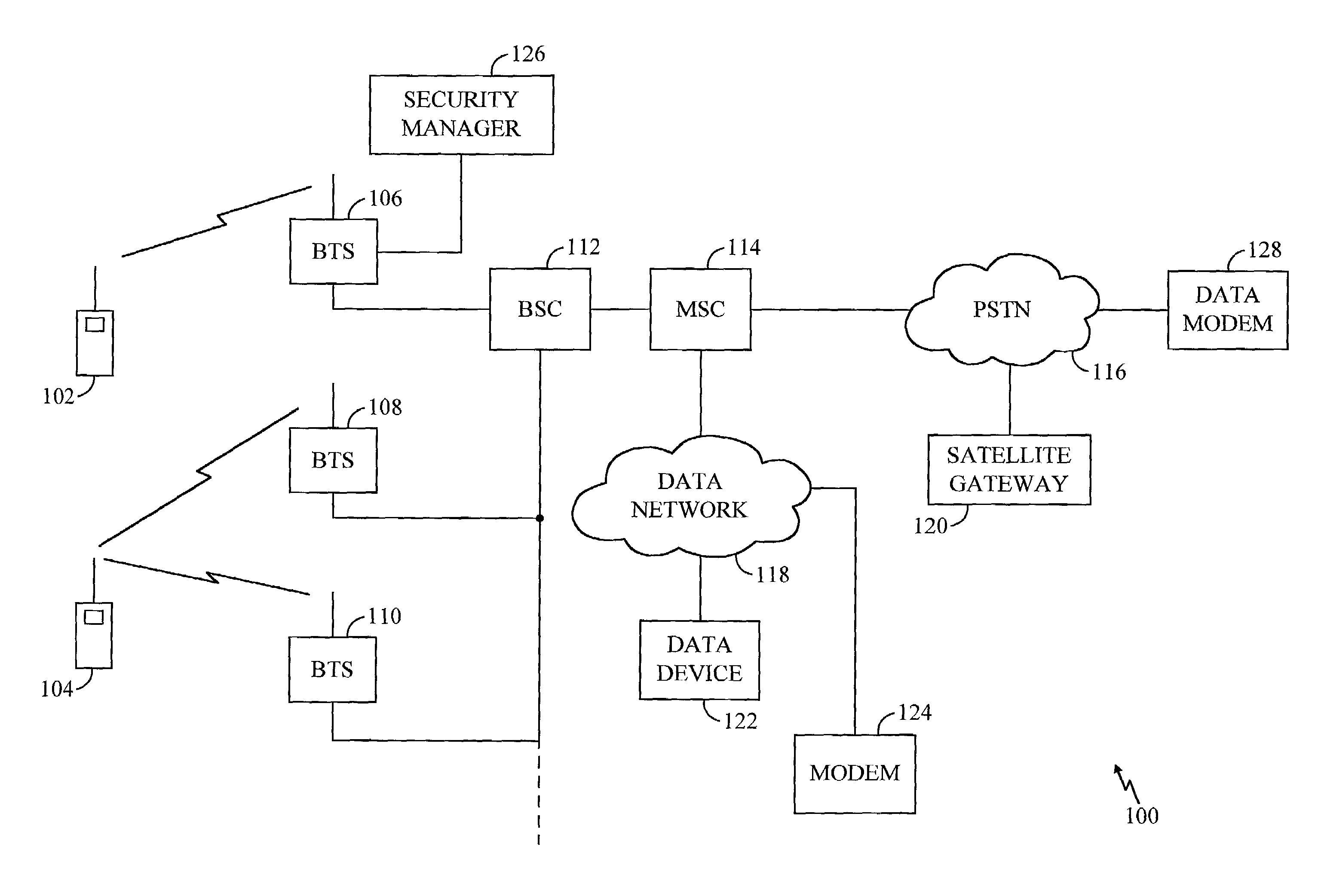
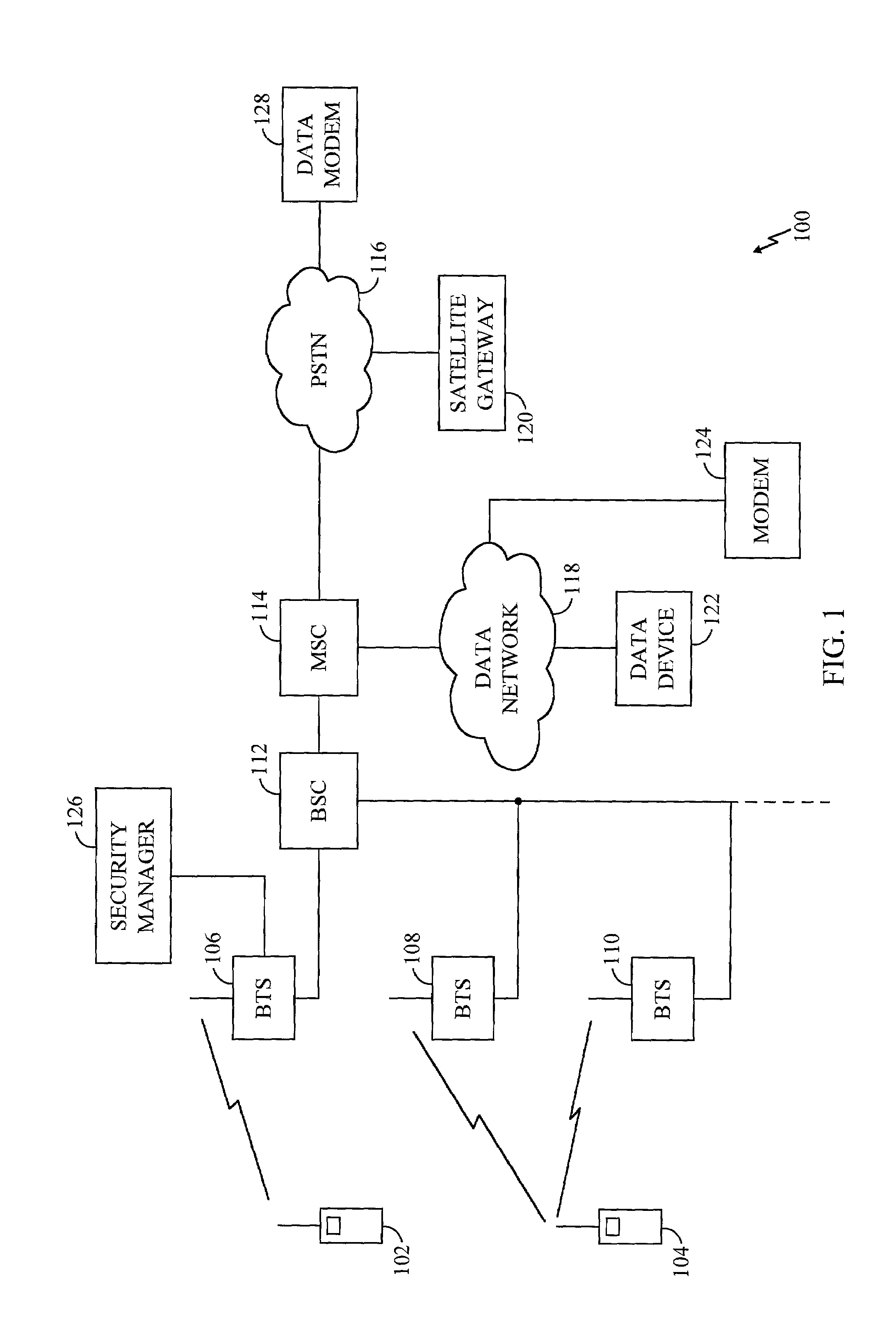
Maintaining secrecy of assigned unique local addresses for IPv6 nodes within a prescribed site during access of a wide area network
ActiveUS20060092949A1Communication securityMaintaining secrecyTime-division multiplexData switching by path configurationUnique local addressConfidentiality
Owner:CISCO TECH INC
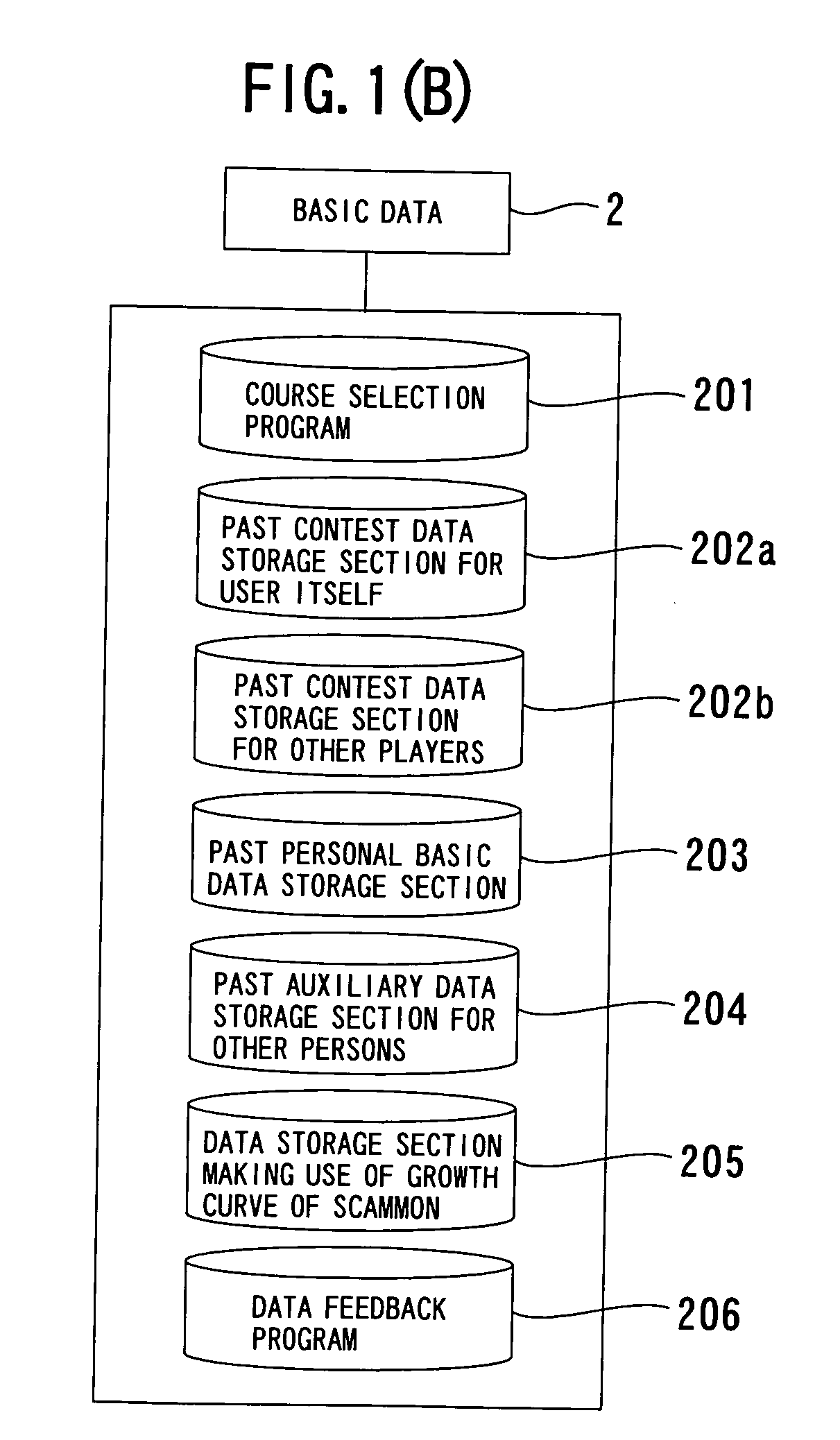
Sports skill evaluation system
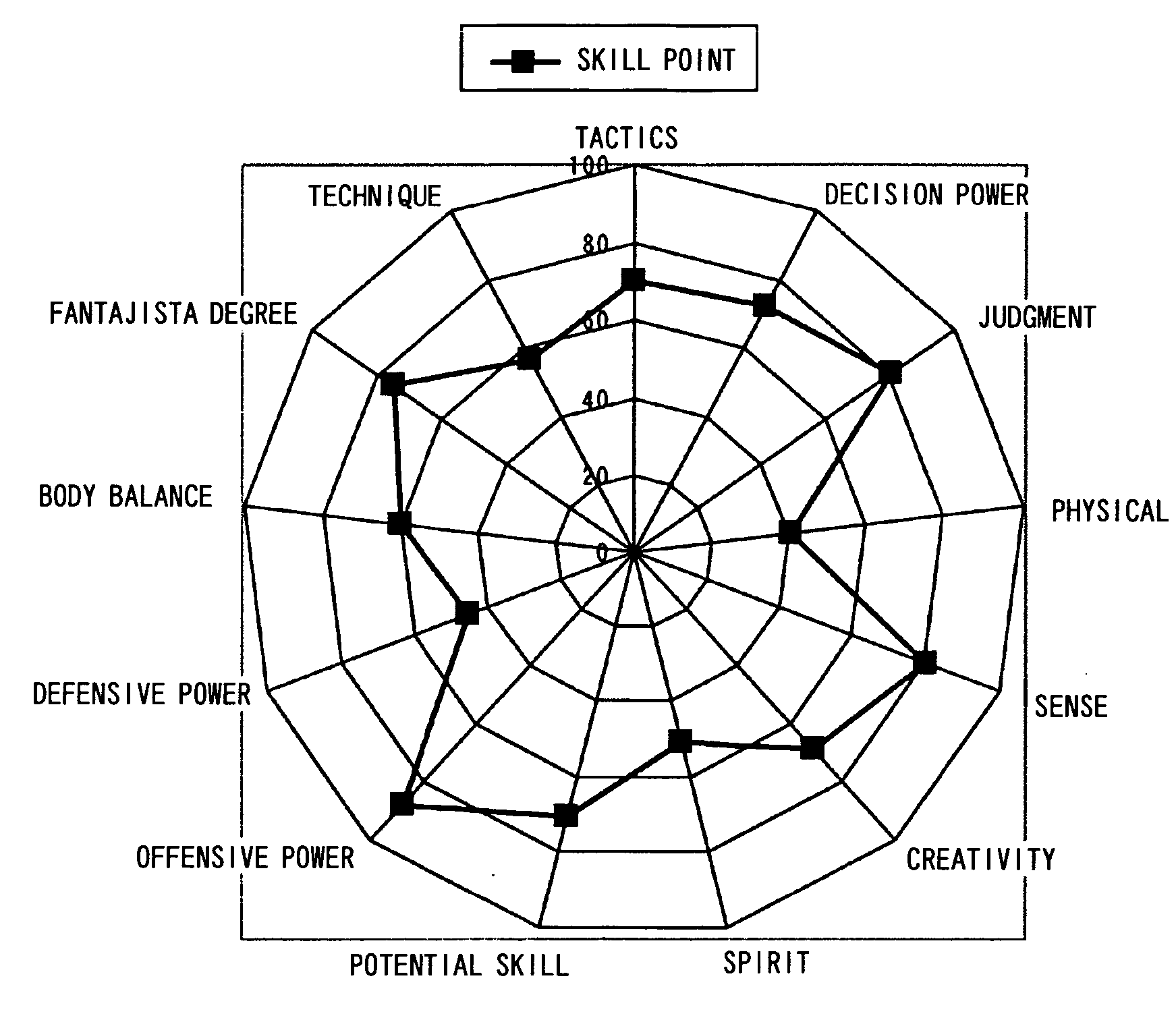
ActiveUS20070166680A1Detailed analysisBroadness in rangeCosmonautic condition simulationsGymnastic exercisingSkill setsEvaluation system
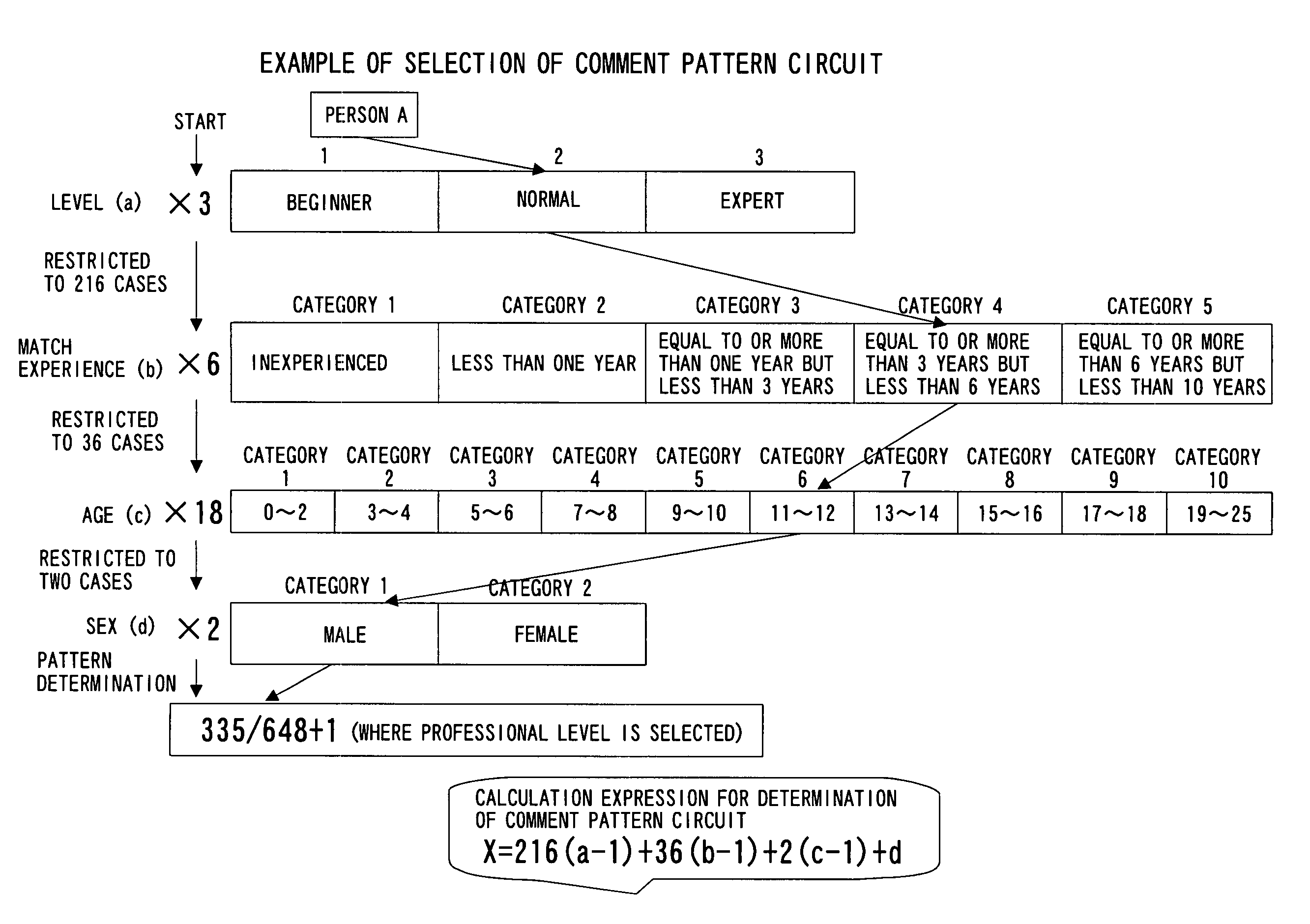
A sports skill evaluation system is provided which can perform a detailed skill analysis based on the level, match experience, age, sex and so forth of a user, careful advice based on a result of the skill analysis, rearing diagnosis in the future, estimation evaluation with the growth in the future taken into consideration and so forth. Individual application coefficients stored in a coefficient table in advance are referred to based on basic user data of the user including the level, match experience, age and sex and a score according to a result of a match to calculate skill item points for individual skills required for the match, and diagnosis graphs for the individual skills are produced from the calculated skill item points for the individual skills. The level, match experience, age and sex of the user are converted into numerical values, and a comment pattern designation value is calculated for each skill item in accordance with a predetermined calculation expression from the numerical values. A comment of a number corresponding to the comment pattern designation value is extracted for each skill item from a comment table.
Owner:SPOTREND
Method and apparatus for providing privacy of user identity and characteristics in a communication system
ActiveUS6983376B2Maintaining secrecyKey distribution for secure communicationData resettingCommunications systemTransceiver
A method and apparatus for providing privacy of user identity and characteristics in a communication system. A public key and a private key is generated, corresponding to a transceiver. The public key is transmitted to a wireless communication device. The wireless communication device encrypts one or more an initial messages using the public key and transmits the one or more encrypted initial messages to the transceiver. The transceiver receives the one or more encrypted initial messages and decrypts it using the private key. The transceiver may then allocate resources to initiate a desired communication between said wireless communication device and a second communication device.
Owner:QUALCOMM INC
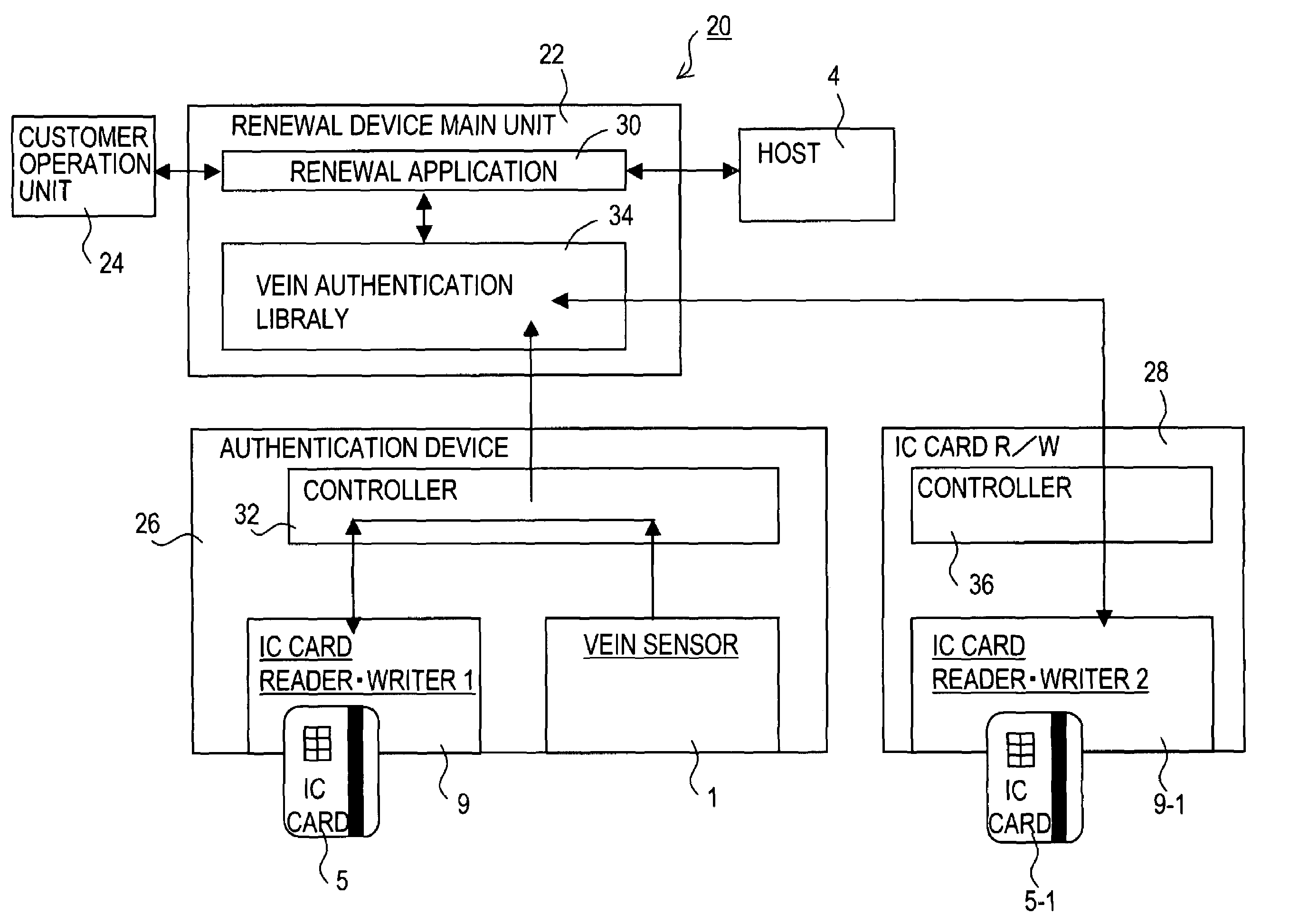
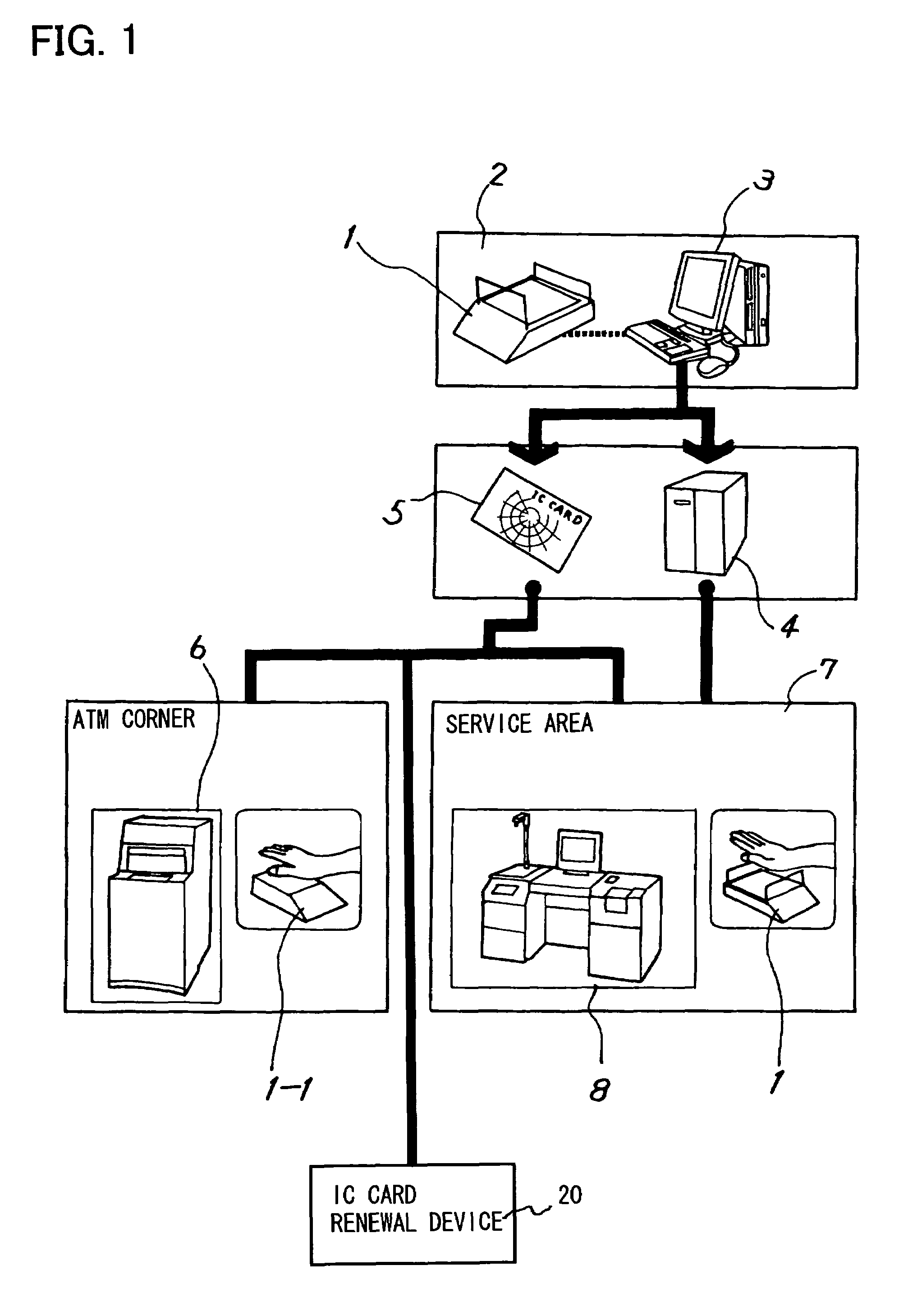
Renewal method and renewal apparatus for an IC card having biometrics authentication functions
InactiveUS20060151599A1Avoid registrationEasy to migrateCo-operative working arrangementsDigital data authenticationComputer hardwareSingle image
A renewal apparatus for an IC card, which utilizes biometrics information to perform individual authentication, prevents the divulgence of biometrics data during renewal, while rigorously confirming the identity of the individual. A control unit confirms the identity of the individual in biometrics authentication by the biometrics authentication functions of an old IC card, and confirmation of the identity of the individual is performed rigorously using the IC card with biometrics authentication functions. If confirmation of the identity of the individual is satisfactory, the biometrics data obtained in the biometrics authentication is registered in a new IC card. The renewal can be performed with only a single image capture operation, and divulgence of biometrics information is prevented.
Owner:FUJITSU LTD +1
Semiconductor memory card, and program for controlling the same
ActiveUS7526625B2Large data capacityMaintaining secrecyDigital data protectionPayment architectureSemiconductorEEPROM
A semiconductor memory card that has a sufficient storage capacity when an EC application writes data to a storage is provided. A usage area for the EC application in an EPPROM 3 in a TRM 1 is expanded. The expansion is such that a partition generated in a flash memory 2 outside the TRM 1 is assigned to the EC application while a partition table is allocated in the internal EEPROM 3. Because the partition table is in the TRM 1, only a CPU 7 in the TRM 1 is able to access the generated partition table. Secrecy of stored contents increases because the access to the expanded area is limited to the CPU 7 in the TRM 1.
Owner:PANASONIC CORP
Session control server, communication device, communication system and communication method, and program and recording medium for the same
InactiveUS20090094692A1Easy to checkMaintaining secrecyKey distribution for secure communicationUser identity/authority verificationCommunications systemSession control
A communication device, connected via a network so as to be able to communicate with a session control server, and which establishes a session with another communication device by performing signal transmission to and reception from the session control server, includes: a unit which generates an asymmetric key pair; a request unit which requests certificate issuance for a public key in the asymmetric key pair; a receiving unit which receives notification of public key issuance completion from the session control server; a storage unit which stores a public key certificate which has been received; a sending unit which sends a location registration request of a communication device to the session control server; and a receiving unit which receives a location registration completed notification which includes a term of validity from the session control server; and which sends a location registration request and a certificate issuance request as a combined request.
Owner:NIPPON TELEGRAPH & TELEPHONE CORP
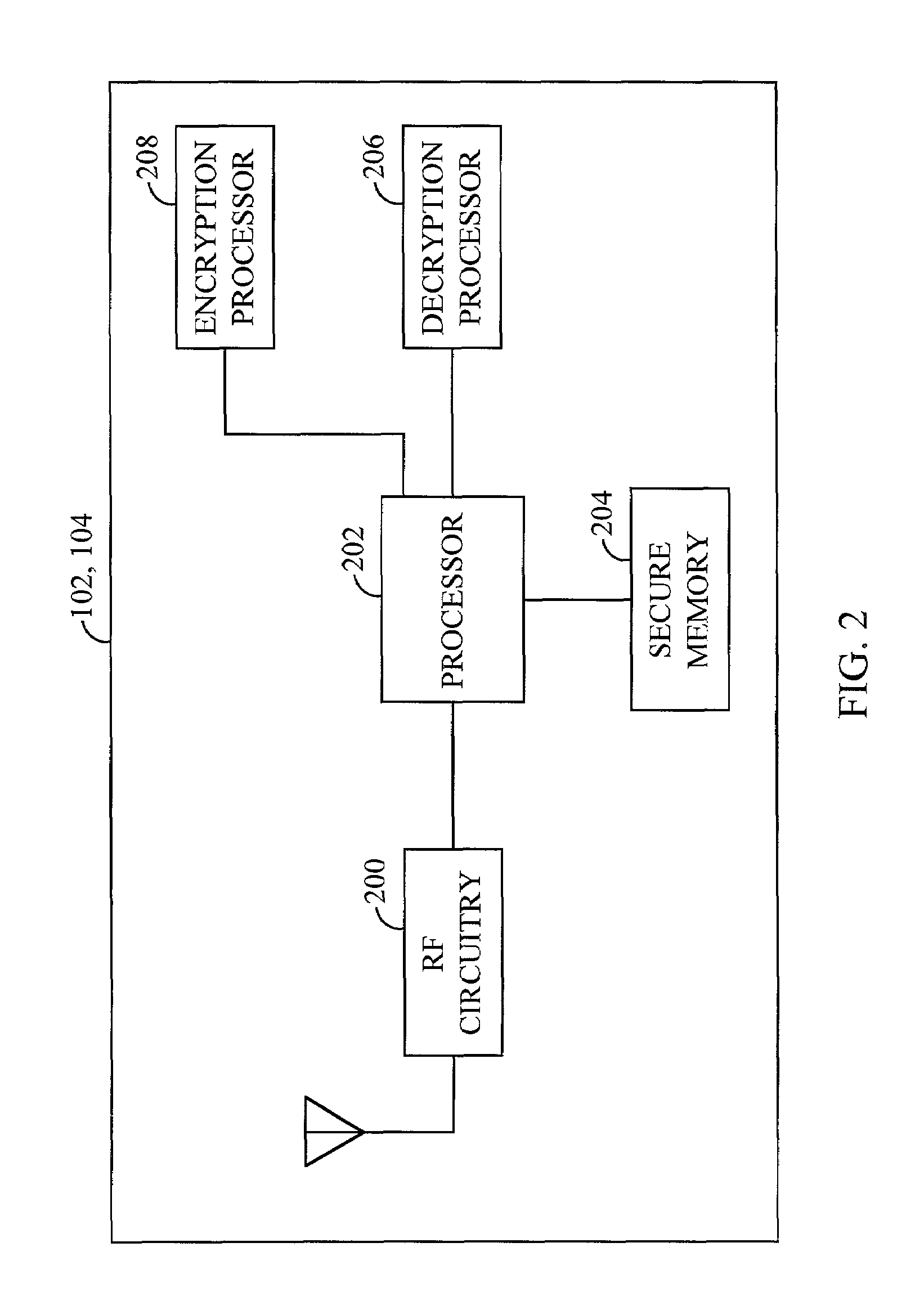
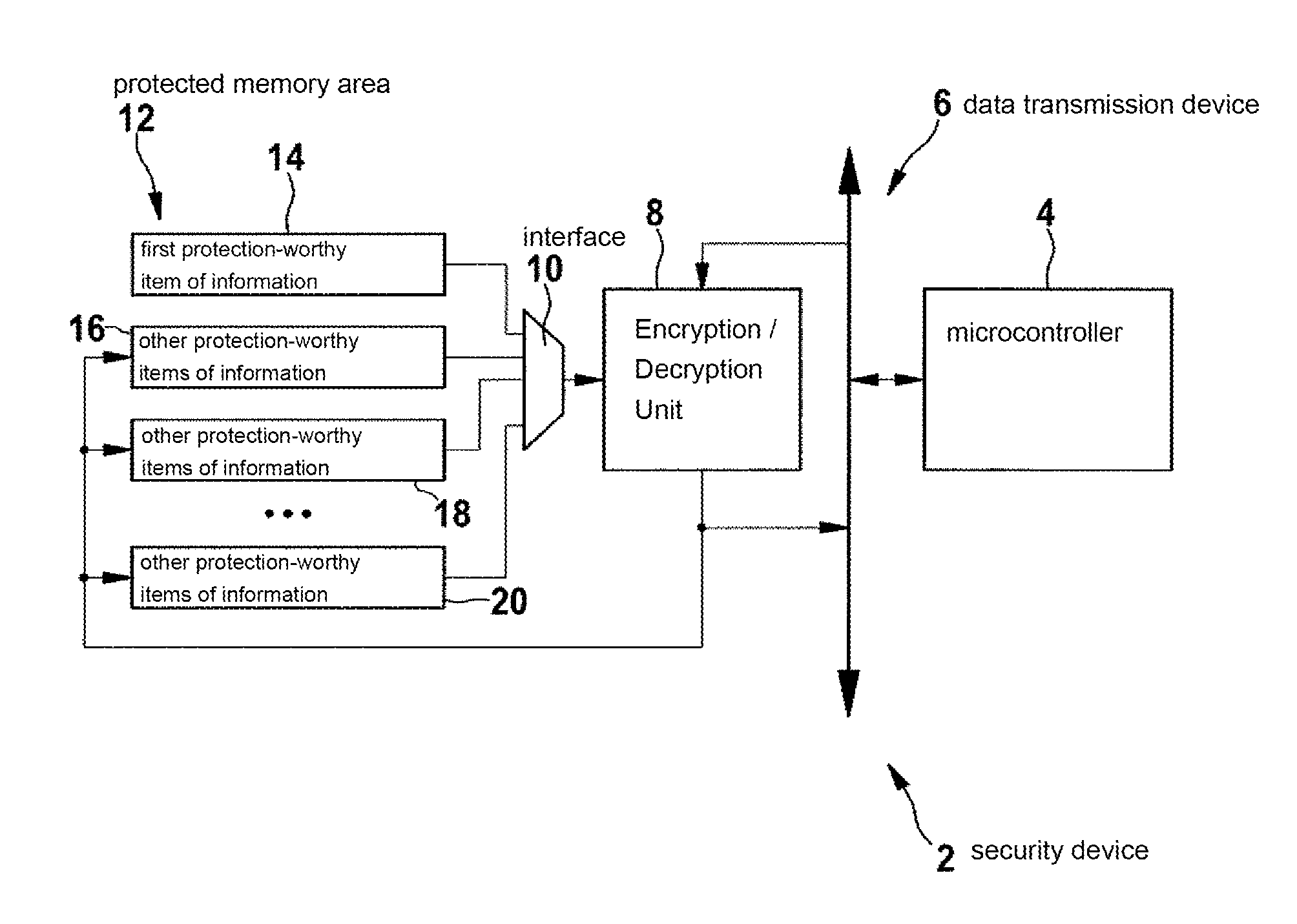
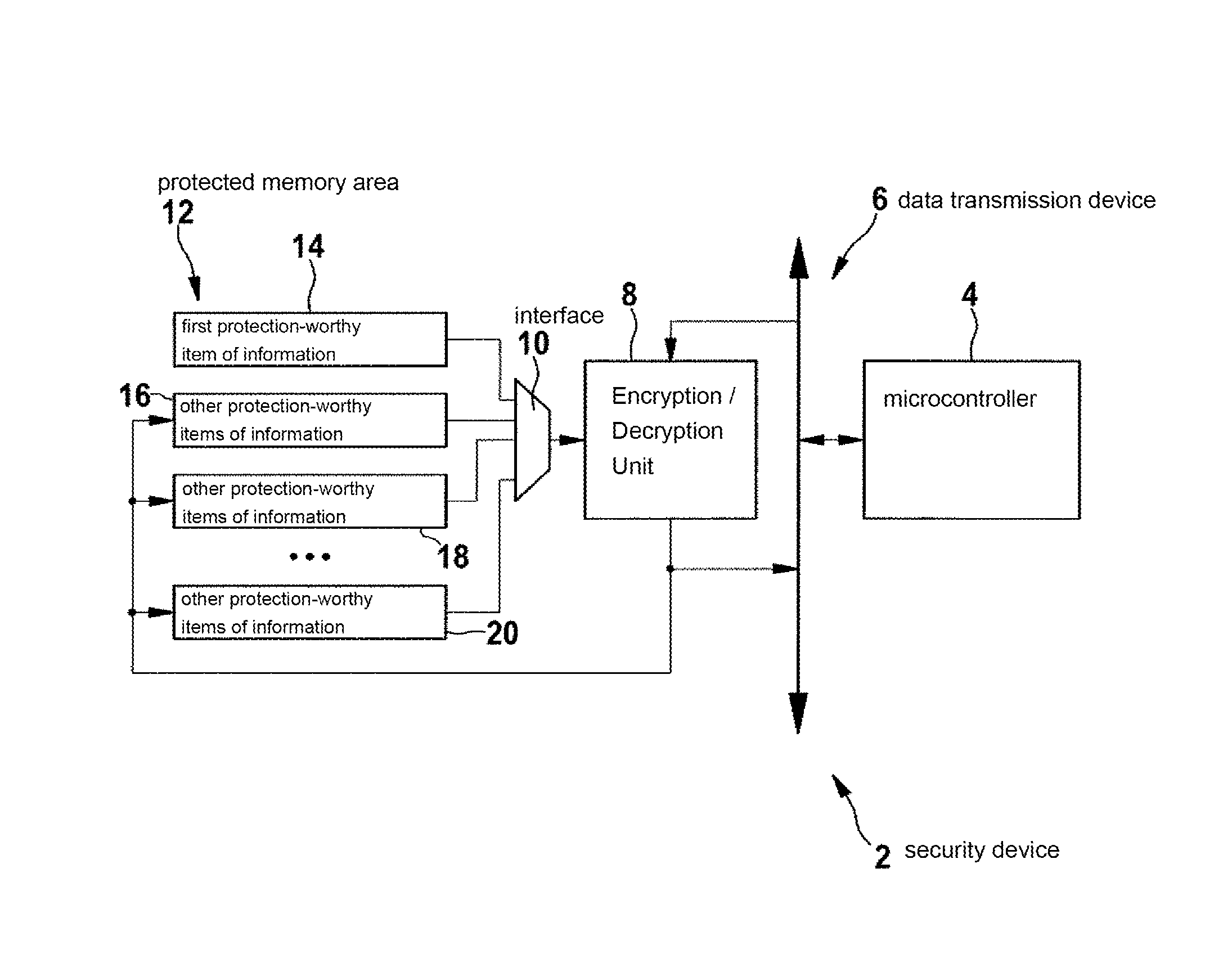
Method for operating a security device
ActiveUS20110145601A1Maintaining secrecyEliminate errorsUnauthorized memory use protectionHardware monitoringMicrocontroller
A method for operating a security device includes a microcontroller, a protected memory area, in which at least one item of protection-worthy information is stored, and a unit, the microcontroller being connected to the protected memory area via the unit, the at least one item of protection-worthy information being accessed by the microcontroller via the unit when the method is carried out.
Owner:ROBERT BOSCH GMBH
Renewal method and renewal apparatus for an IC card having biometrics authentication functions
InactiveUS7471810B2Maintaining secrecyInhibition releaseCo-operative working arrangementsDigital data authenticationComputer hardwareSingle image
A renewal apparatus for an IC card, which utilizes biometrics information to perform individual authentication, prevents the divulgence of biometrics data during renewal, while rigorously confirming the identity of the individual. A control unit confirms the identity of the individual in biometrics authentication by the biometrics authentication functions of an old IC card, and confirmation of the identity of the individual is performed rigorously using the IC card with biometrics authentication functions. If confirmation of the identity of the individual is satisfactory, the biometrics data obtained in the biometrics authentication is registered in a new IC card. The renewal can be performed with only a single image capture operation, and divulgence of biometrics information is prevented.
Owner:FUJITSU LTD +1
Security systems and methods to reduce data leaks in enterprise networks
InactiveUS8893300B2Reduce lossesHarder to evadeMemory loss protectionDigital data processing detailsSecurity systemDistributed computing
Disclosed are embodiments of a security system for reducing data leaks by checking information flows between resources of a network. When an information flow is attempted between a sending resource, which can be anywhere in the network, and a receiving resource residing at a specific host within the network, a host labeler can determine whether information is allowed to flow from the sending resource to the receiving resource. The sending resource and the receiving resource can each have an applicable label, and each label can comprise zero, one, or more taints. For each taint having an active secrecy characteristic in a label of the sending resource, the host labeler can require that there be a matching taint with active secrecy characteristic in the receiving resource. If this condition is not met, the security system can block the information flow between the sending and receiving resources.
Owner:GEORGIA TECH RES CORP
Sports skill evaluation system
ActiveUS7575433B2Detailed analysisBroadness in rangeCosmonautic condition simulationsGymnastic exercisingSkill setsEvaluation system
A sports skill evaluation system is provided which can perform a detailed skill analysis based on the level, match experience, age, sex and so forth of a user, careful advice based on a result of the skill analysis, rearing diagnosis in the future, estimation evaluation with the growth in the future taken into consideration and so forth. Individual application coefficients stored in a coefficient table in advance are referred to based on basic user data of the user including the level, match experience, age and sex and a score according to a result of a match to calculate skill item points for individual skills required for the match, and diagnosis graphs for the individual skills are produced from the calculated skill item points for the individual skills. The level, match experience, age and sex of the user are converted into numerical values, and a comment pattern designation value is calculated for each skill item in accordance with a predetermined calculation expression from the numerical values. A comment of a number corresponding to the comment pattern designation value is extracted for each skill item from a comment table.
Owner:SPOTREND
Method and apparatus for password re-entry
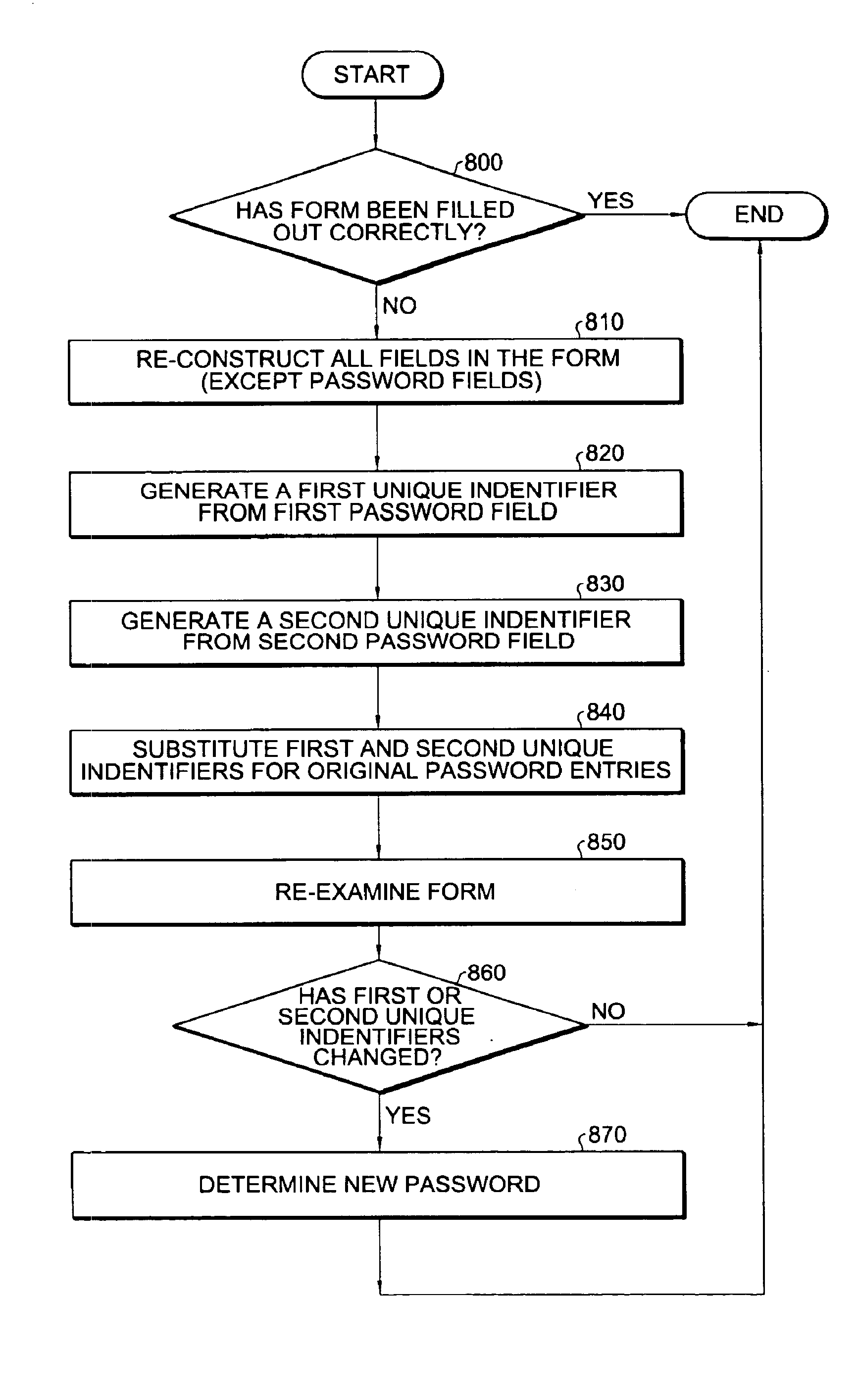
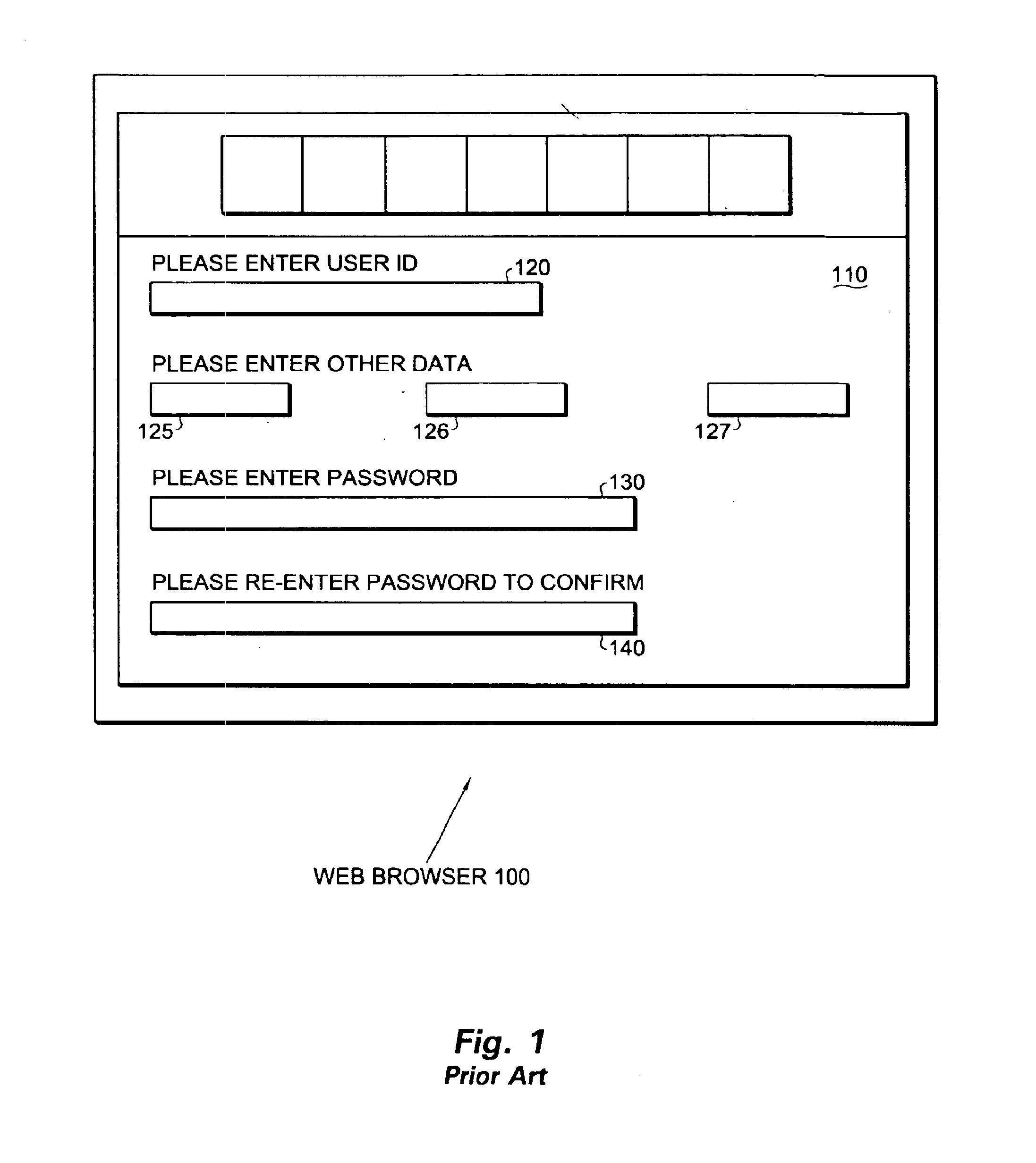
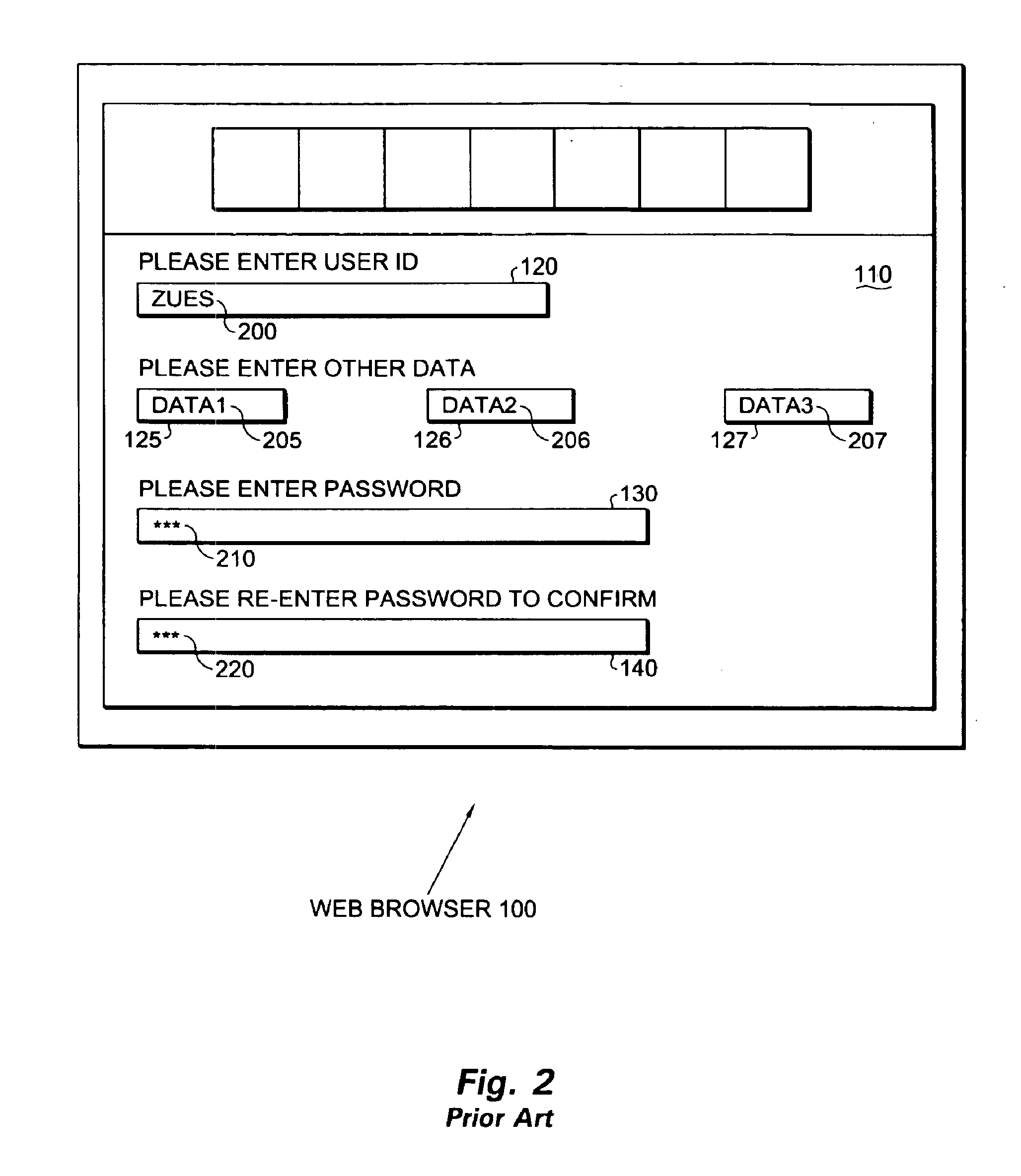
InactiveUS6868499B1Eliminate riskMaintaining secrecyFinanceDigital data processing detailsRe entryWeb browser
The present invention provides a method and apparatus for password re-entry. In one or more embodiments, the invention is in an environment wherein a password and data are input into the same document. In one embodiment, this environment is the Internet where a web browser displays the output of a web server in a form HTML document. When returning a password, the invention generates two unique identifiers that represent the entries in two password fields. Next, the invention reconstructs the form by including previously entered data in the new form and by substituting the two unique identifiers for the password fields. In one embodiment, the user can edit the password by modifying the unique identifier string. The original text of the password remains safely on the server. If the password is edited, the server compares the unique identifier strings re-sent in the encoded web page with the returned web page. In this way, the server detects a modified password while still maintaining the secrecy of the password.
Owner:ORACLE INT CORP
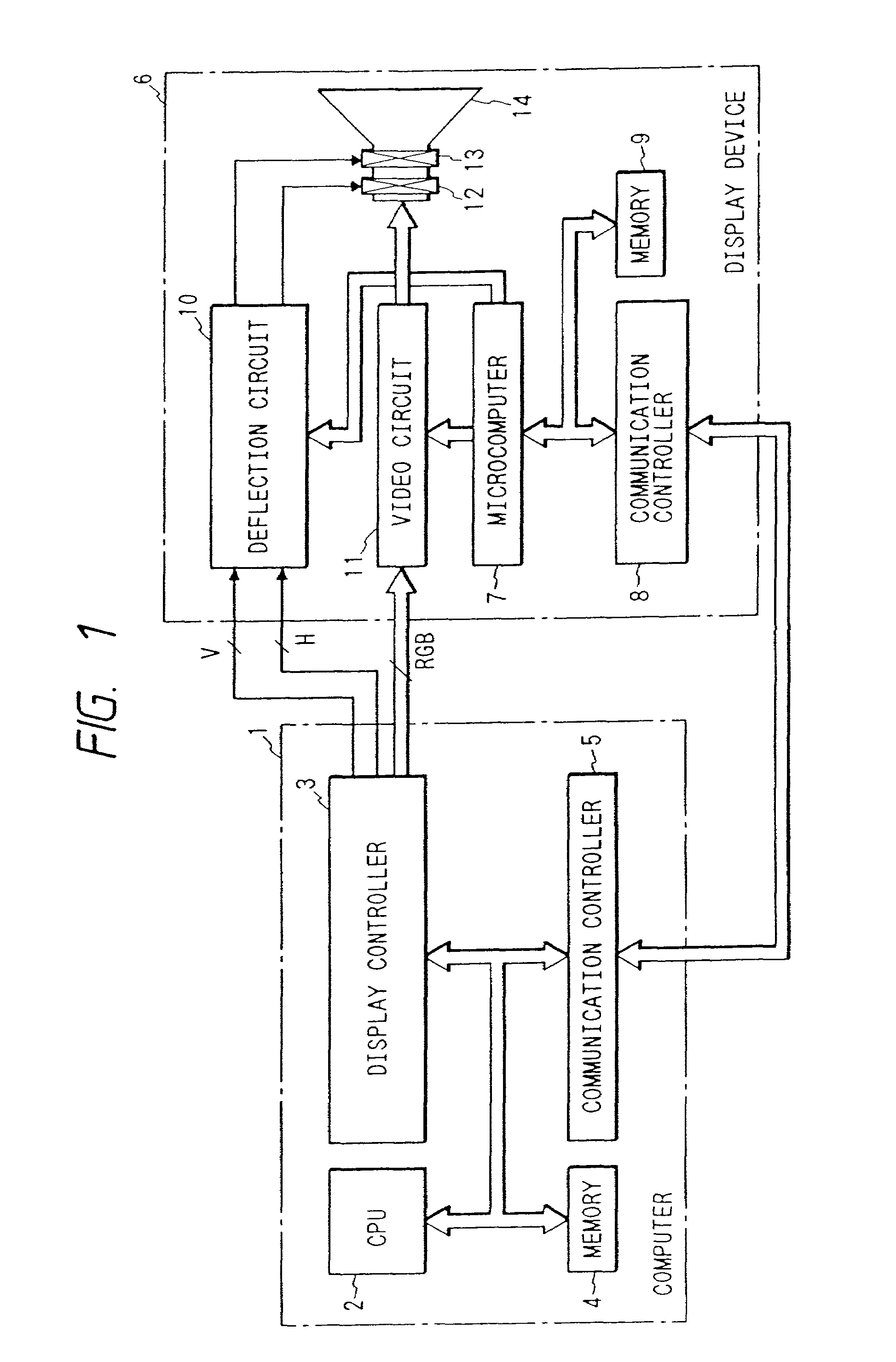
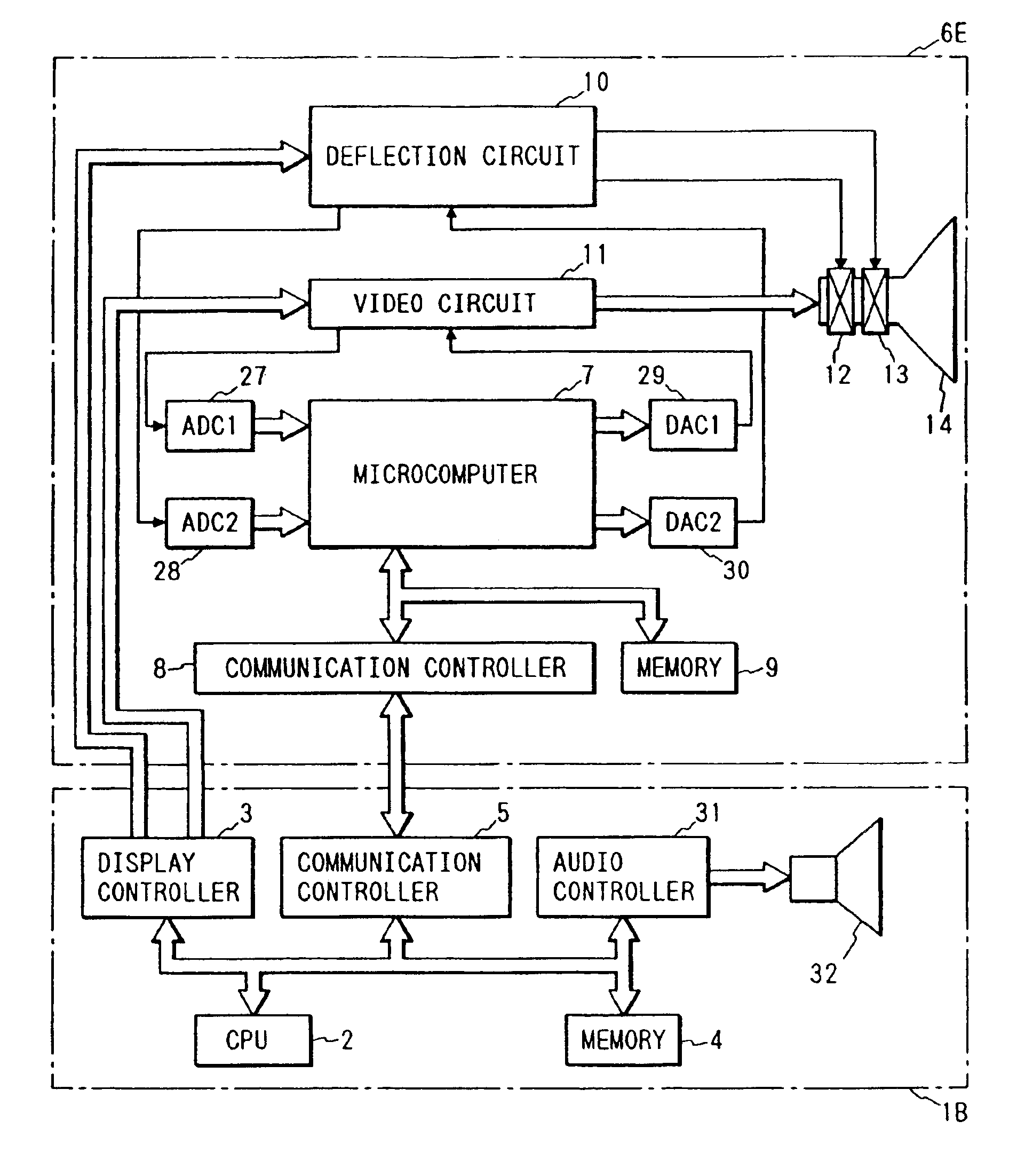
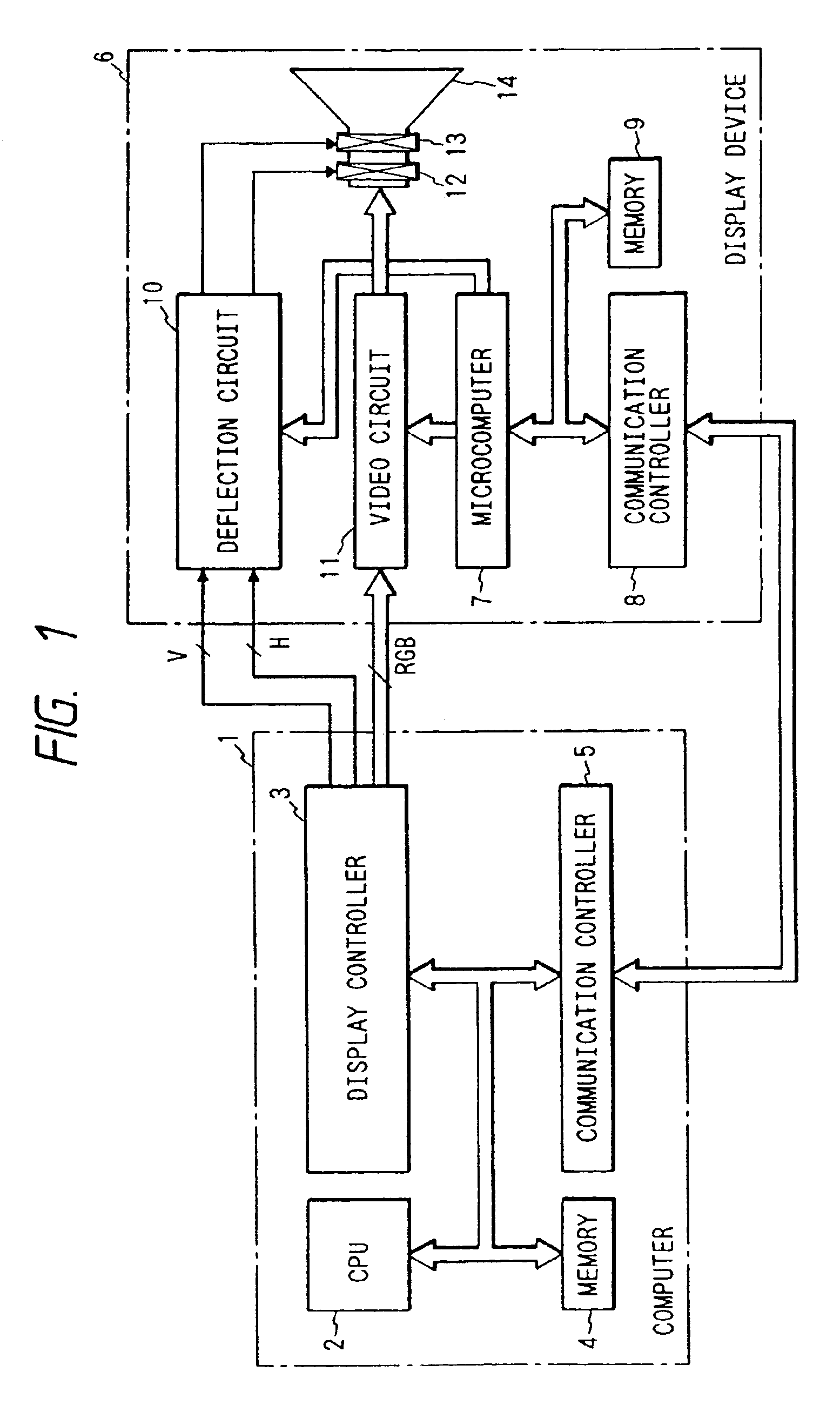
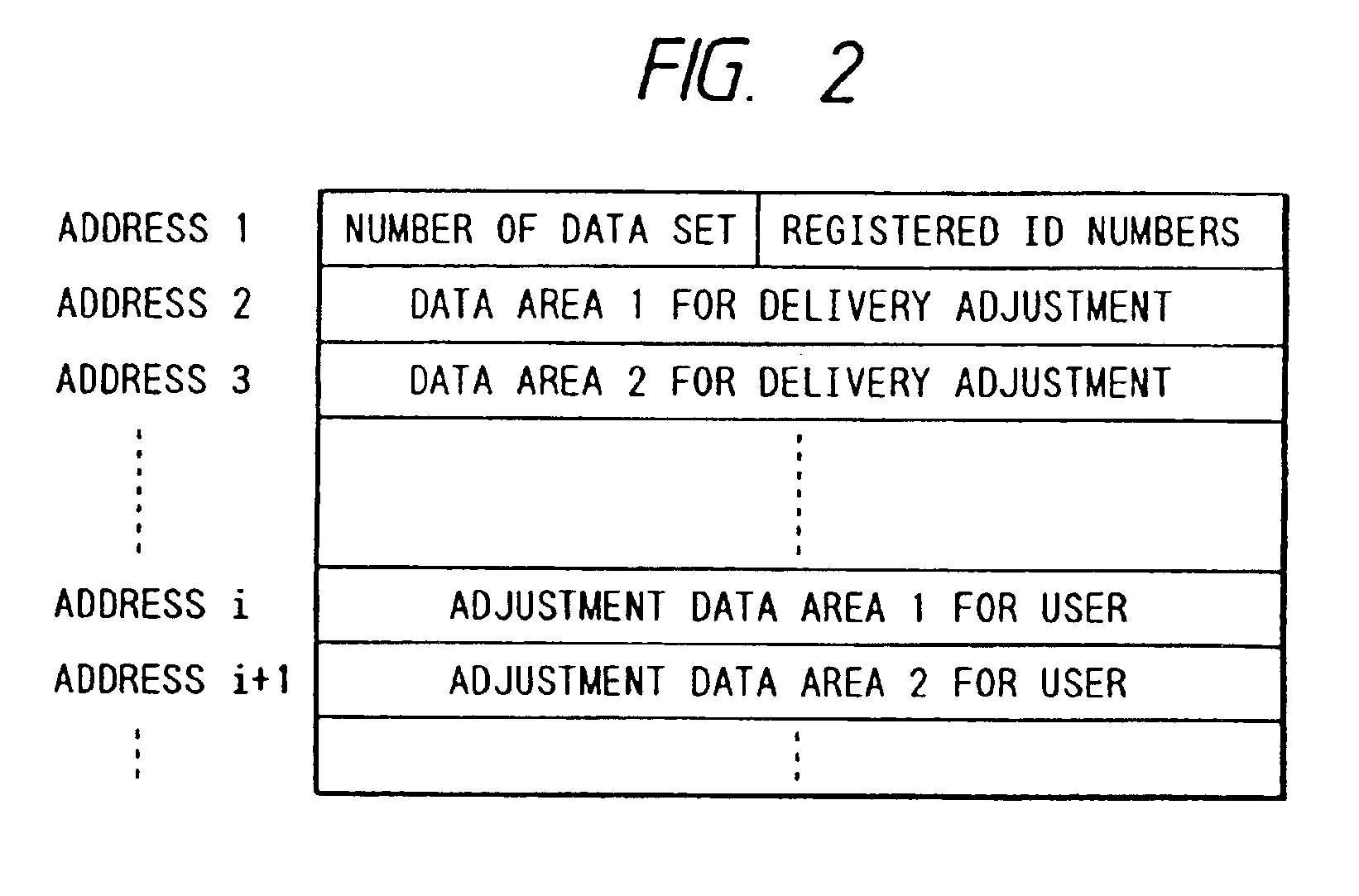
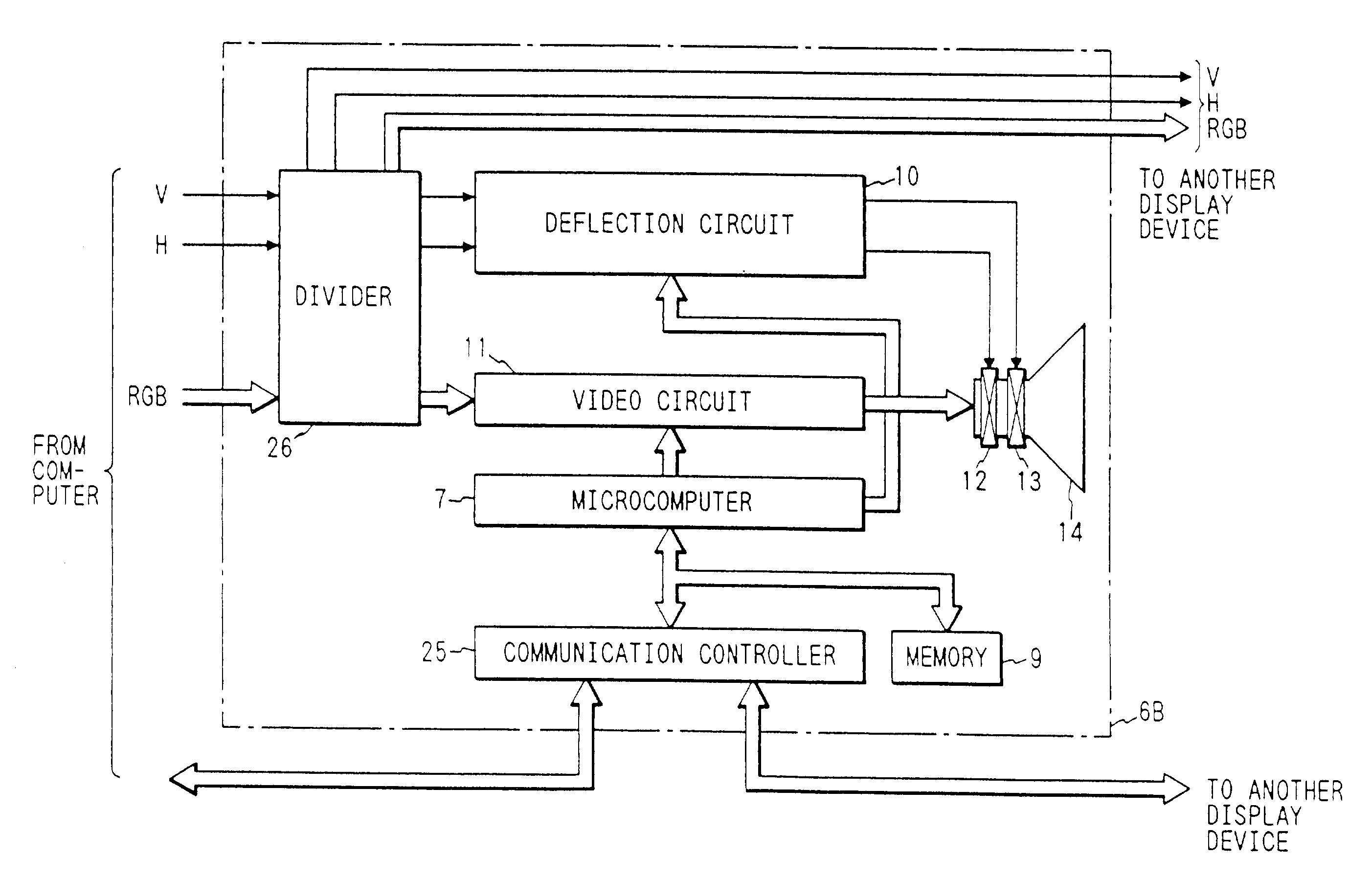
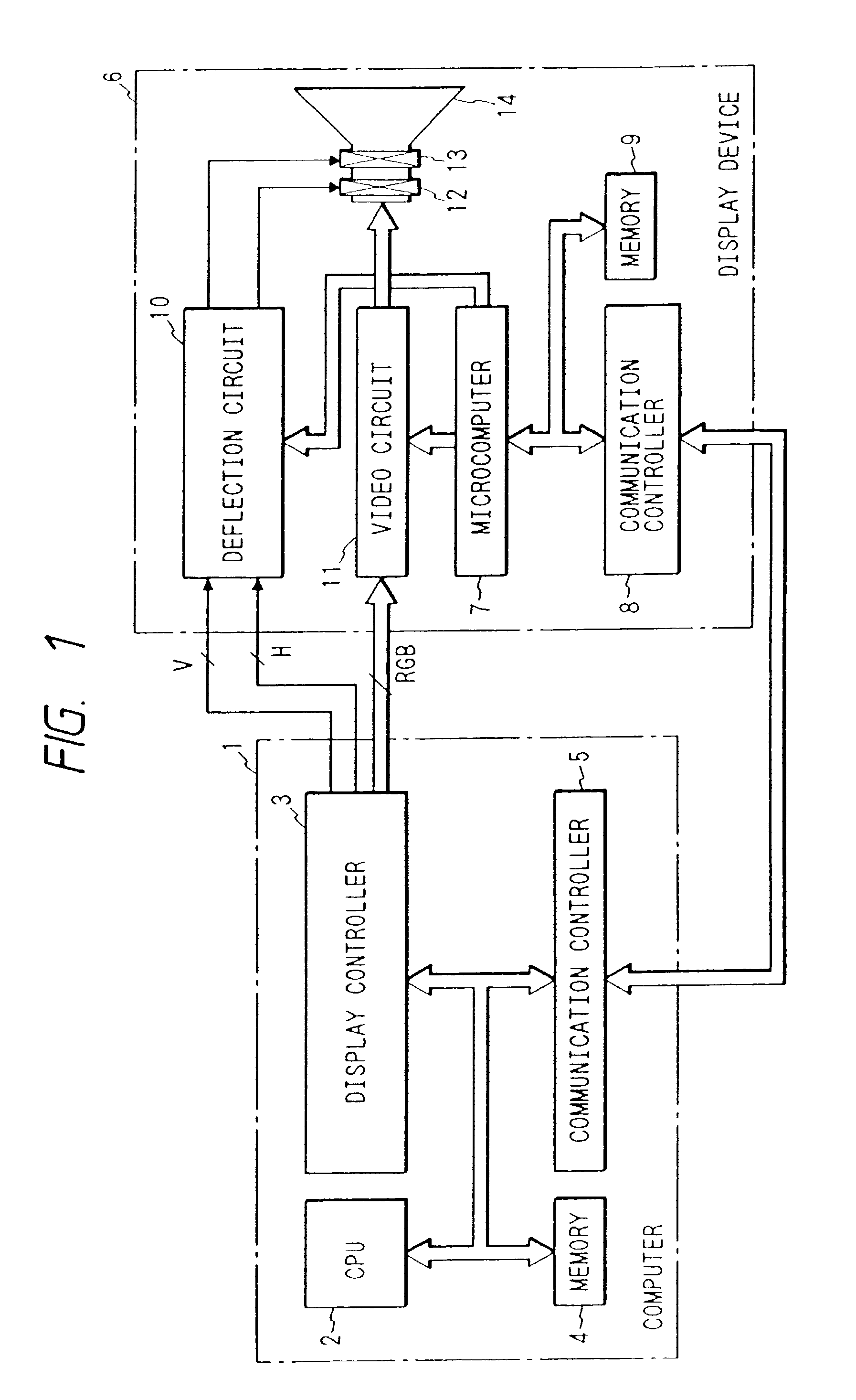
Display unit with communication controller and memory for storing identification number for identifying display unit
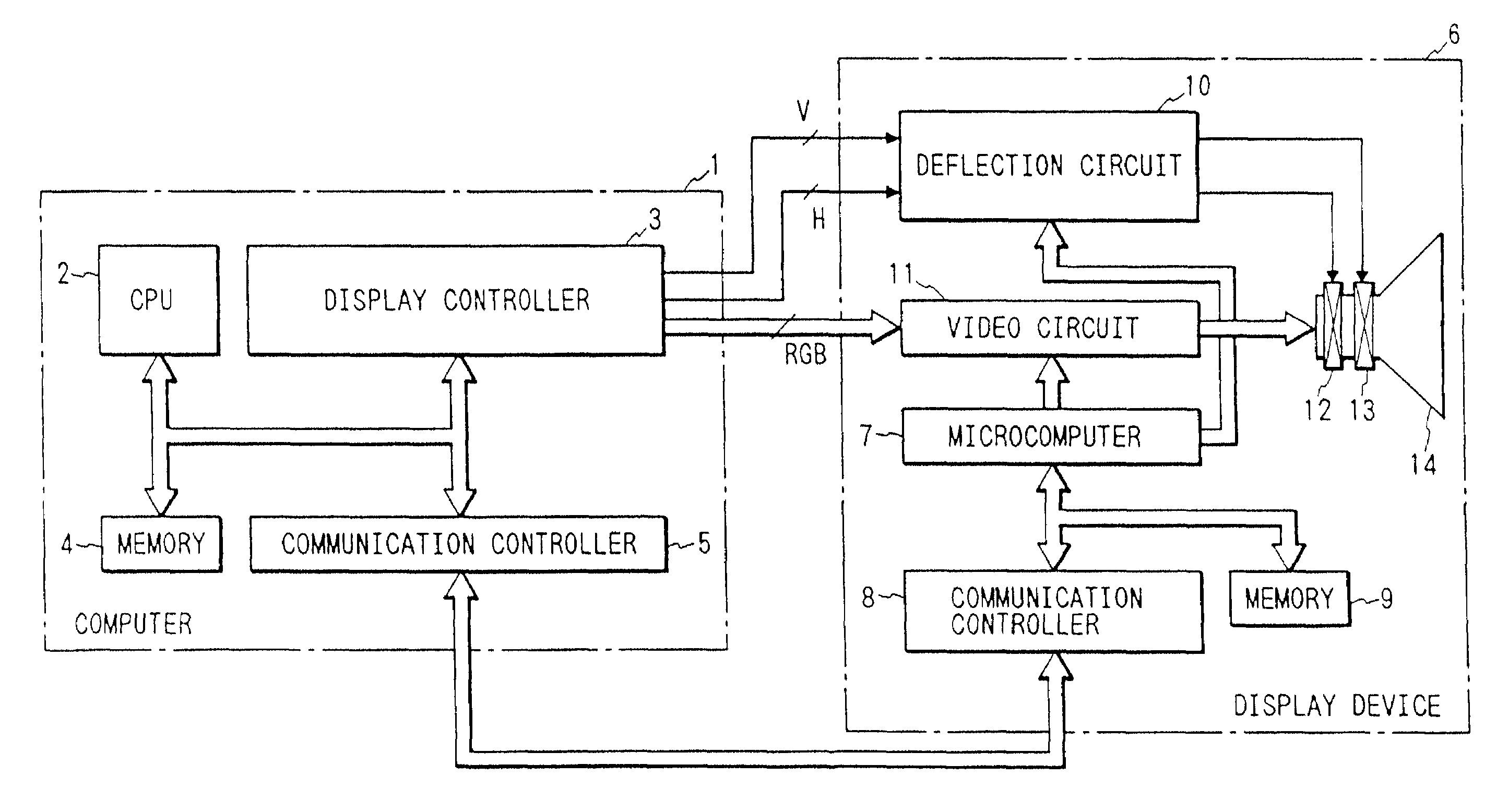
InactiveUS7475180B2Maintaining secrecyAvoid power consumptionCathode-ray tube indicatorsTransmissionCommunication controlExternal connection
A display unit for displaying an image based on video signals and synchronization signals inputted from an externally connected video source, includes a video circuit adapted to display an image based on the video signals sent by the externally connected video source, a memory which stores an identification number for identifying the display unit, and a communication controller which sends the identification number stored in the memory to the video source. The communication controller is capable of bi-directionally communicating with the video source.
Owner:MONDIS TECH
Method enabling display unit to bi-directionally communicate with video source
InactiveUS7089342B2Maintaining secrecyAvoid power consumptionColor television with pulse code modulationColor television with bandwidth reductionVIT signalsMultimedia
A method for a display unit displaying video signals sent by a video source, the method comprising the steps of communicating display unit information stored in a memory of the display unit to the video source, wherein the display information includes identifying information of the display unit; receiving a signal from the video source, wherein the signal is generated based on at least a portion of the display unit information; and wherein the display unit is capable of bi-directionally communicating with the video source.
Owner:MONDIS TECH
Display unit with processor and communication controller which communicates information to the processor
InactiveUS7475181B2Maintaining secrecyAvoid power consumptionCathode-ray tube indicatorsTransmissionTelecommunicationsCommunication control
Owner:MONDIS TECH
Wireless communication device, mac address management system, wireless communication method, and program
ActiveUS8428064B2Maintaining secrecyProtect user privacyUnauthorised/fraudulent call preventionEavesdropping prevention circuitsComputer hardwareDistributed servers
A MAC address management system acquires code data obtained by encoding a temporary MAC address that can be temporarily used and decodes the acquired code data to perform wireless communication. The MAC address management system includes a MAC distributing server device in which a temporary MAC address which can be temporarily used is stored and a wireless communication device that acquires the temporary MAC address from the MAC distributing server device and performs wireless communication by using the acquired temporary MAC address, the wireless communication device acquires code data obtained by encoding the temporary MAC address from the MAC distributing server device, decodes the acquired code data, and performs wireless communication by using the decoded temporary MAC address.
Owner:NEC CORP
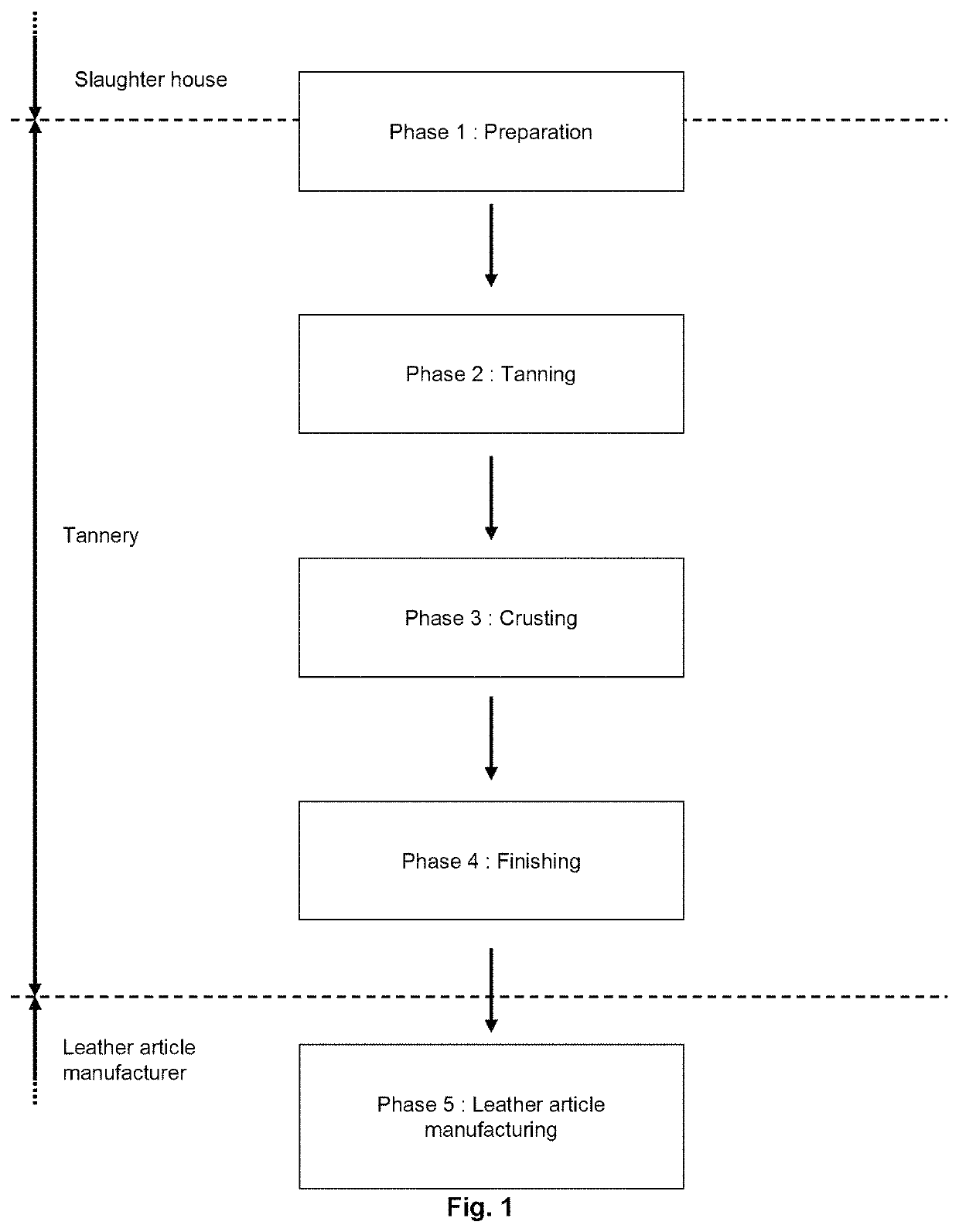
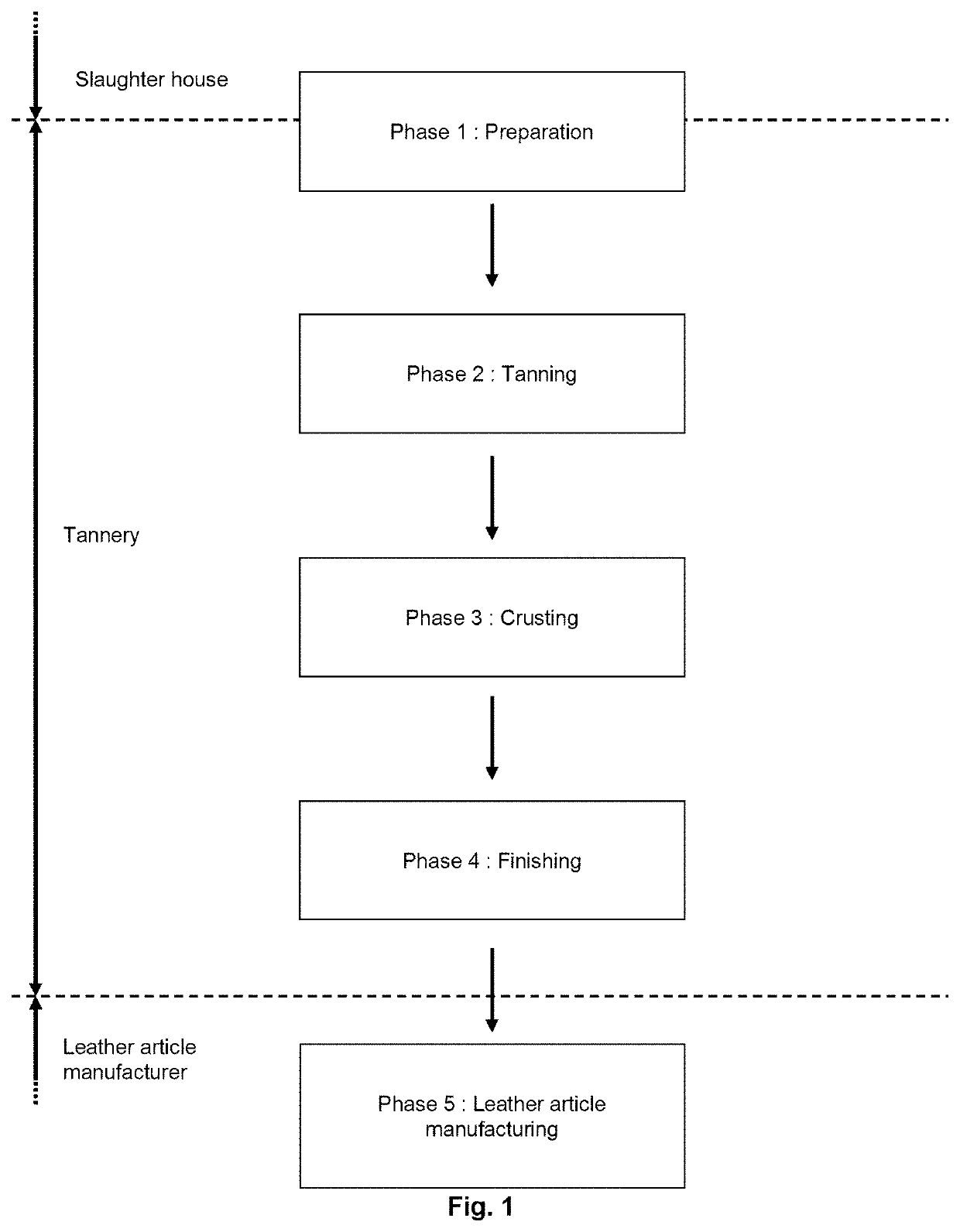
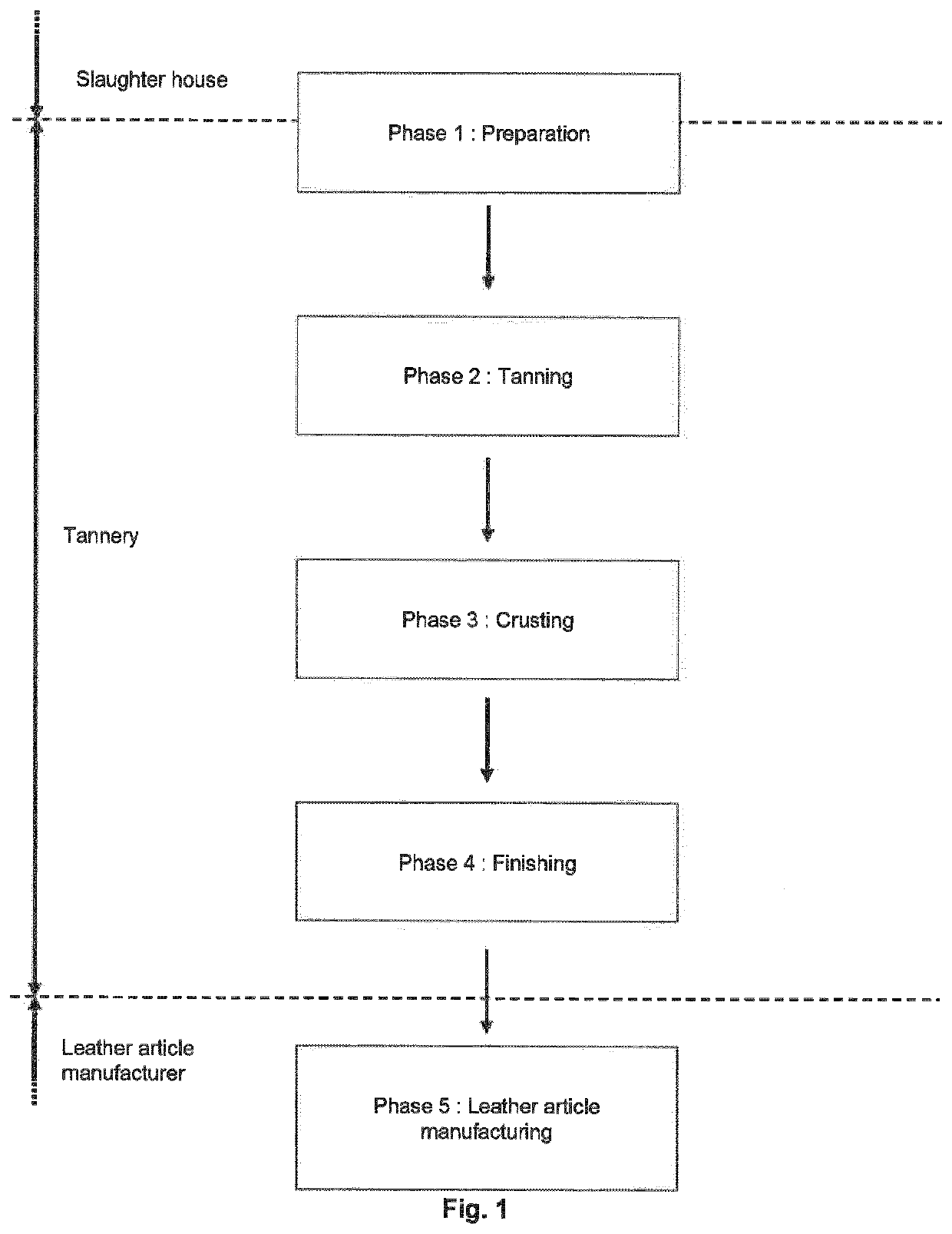
Decorated natural leather
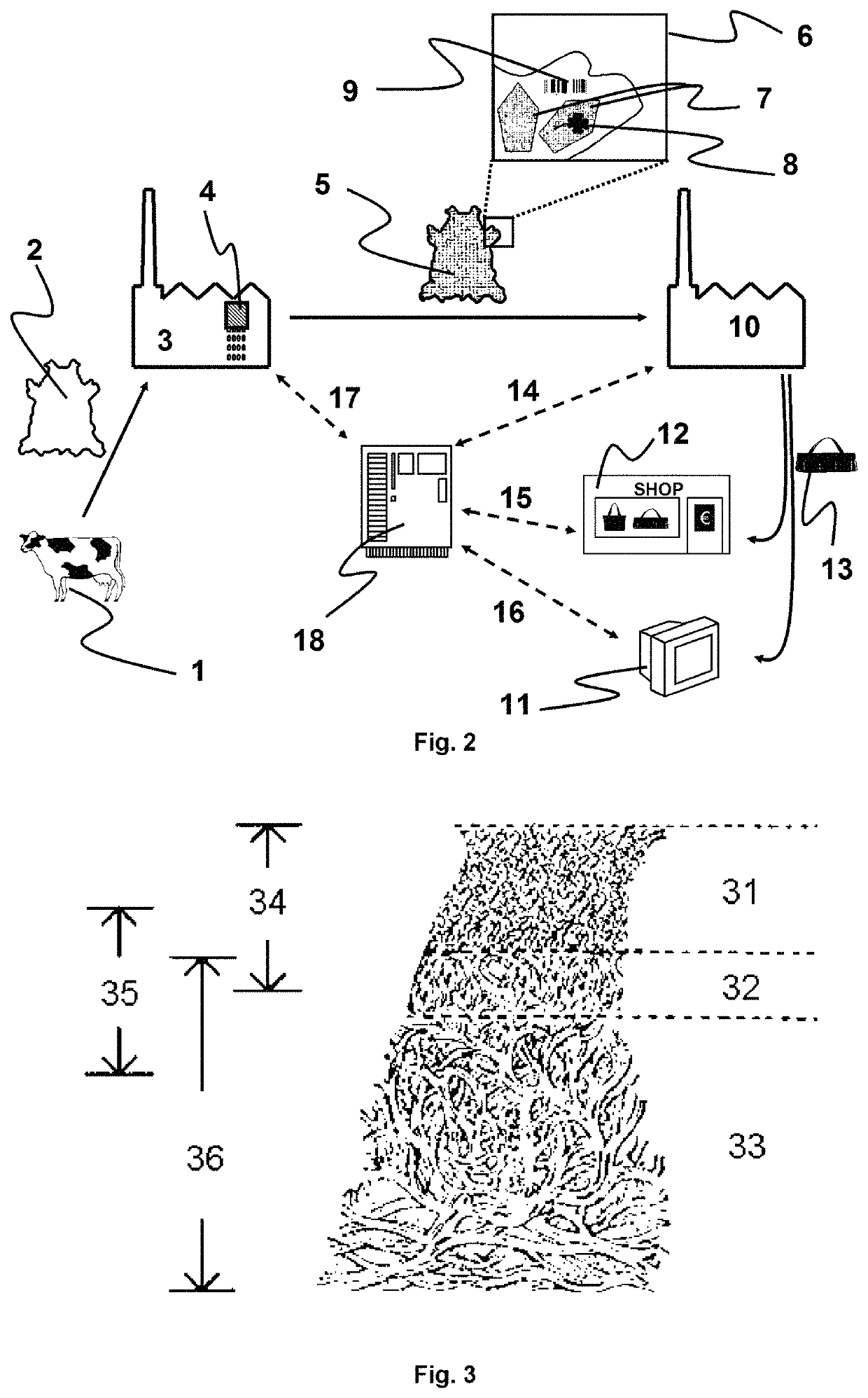
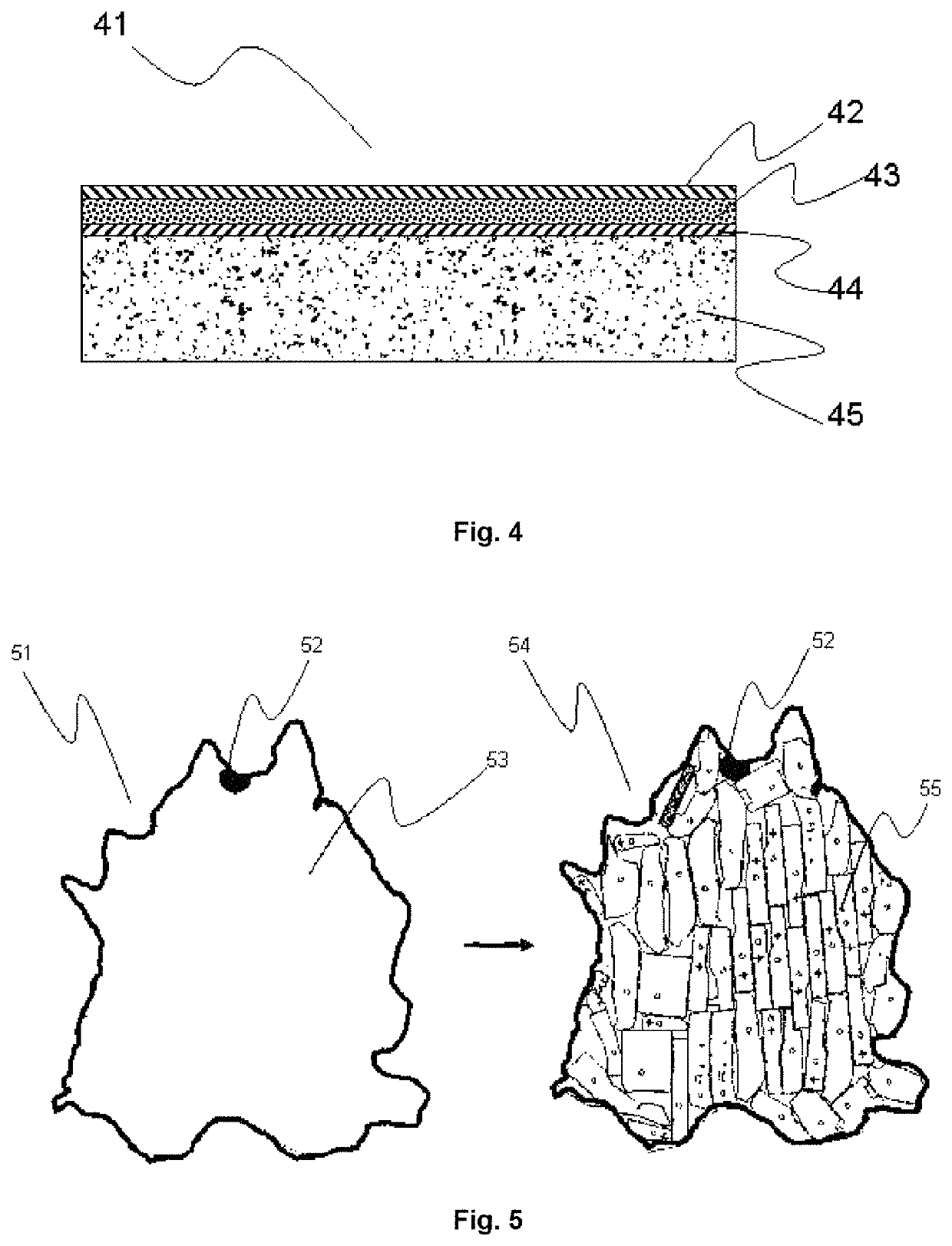
ActiveUS11351805B2Avoid mistakesReduce wastePre-tanning chemical treatmentDuplicating/marking methodsPolymer scienceEngineering
A manufacturing method of decorated natural leather includes applying a base coat on crusted leather, inkjet printing a decorative image on the base coat using one or more pigmented inkjet inks, and applying one or more identification codes.
Owner:AGFA NV
Apparatus and method of generating and detecting prevention and control data for verifying validity of data
InactiveUS8429414B2Maintaining secrecyVerify the validity of the dataKey distribution for secure communicationDigital data processing detailsControl dataReal-time computing
A method of generating prevention and control data to verify validity of data to be transmitted, and an apparatus to perform the method, the method including generating the prevention and control data according to composing information of the data to be transmitted, and transmitting the prevention and control data along with the data to be transmitted to verify the validity of the data to be transmitted.
Owner:SAMSUNG ELECTRONICS CO LTD
Decorated natural leather
ActiveUS20200101783A1Avoid mistakesReduce wastePre-tanning chemical treatmentDuplicating/marking methodsPolymer scienceEngineering
A manufacturing method of decorated natural leather includes applying a base coat on crusted leather, inkjet printing a decorative image on the base coat using one or more pigmented inkjet inks, and applying one or more identification codes.
Owner:AGFA NV
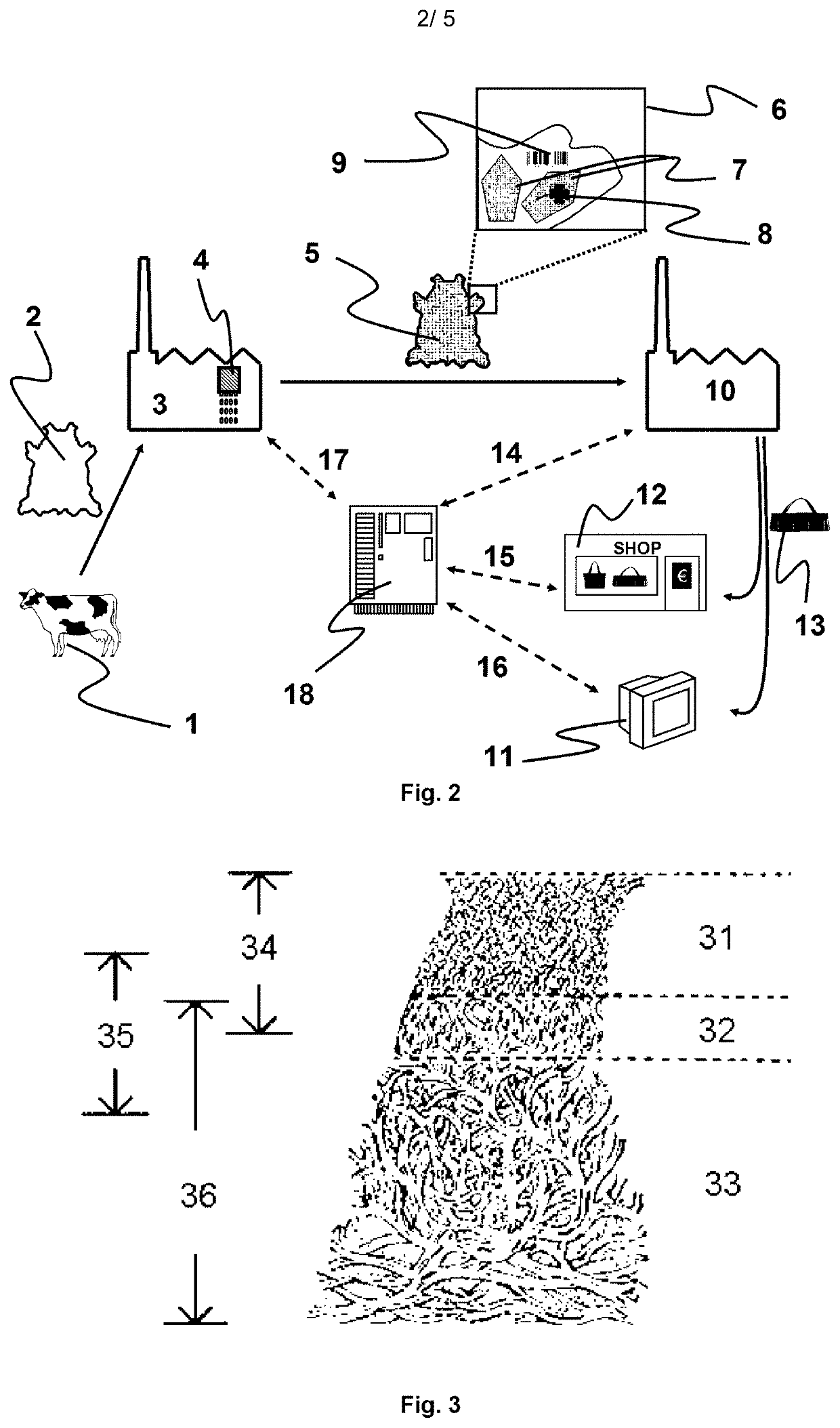
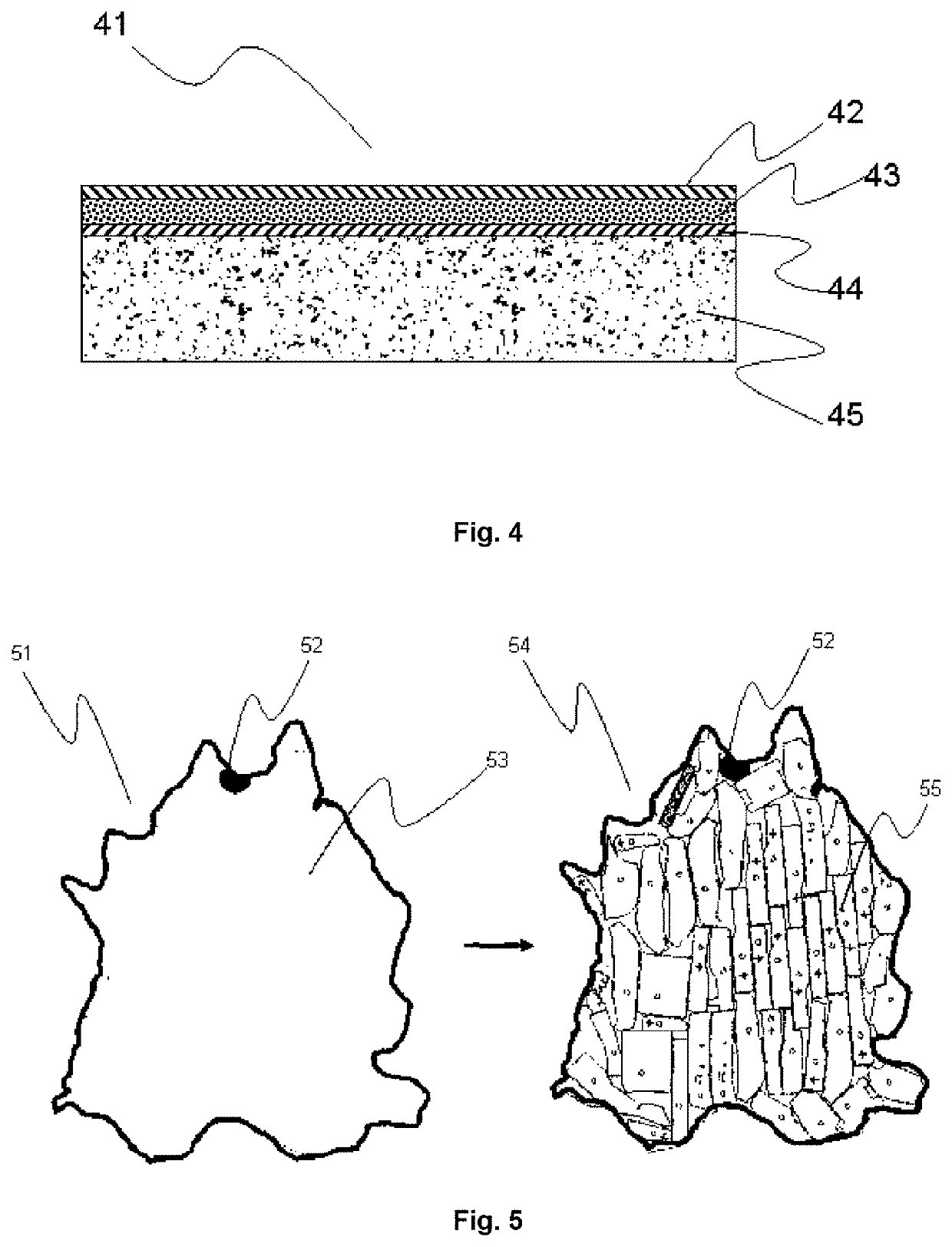
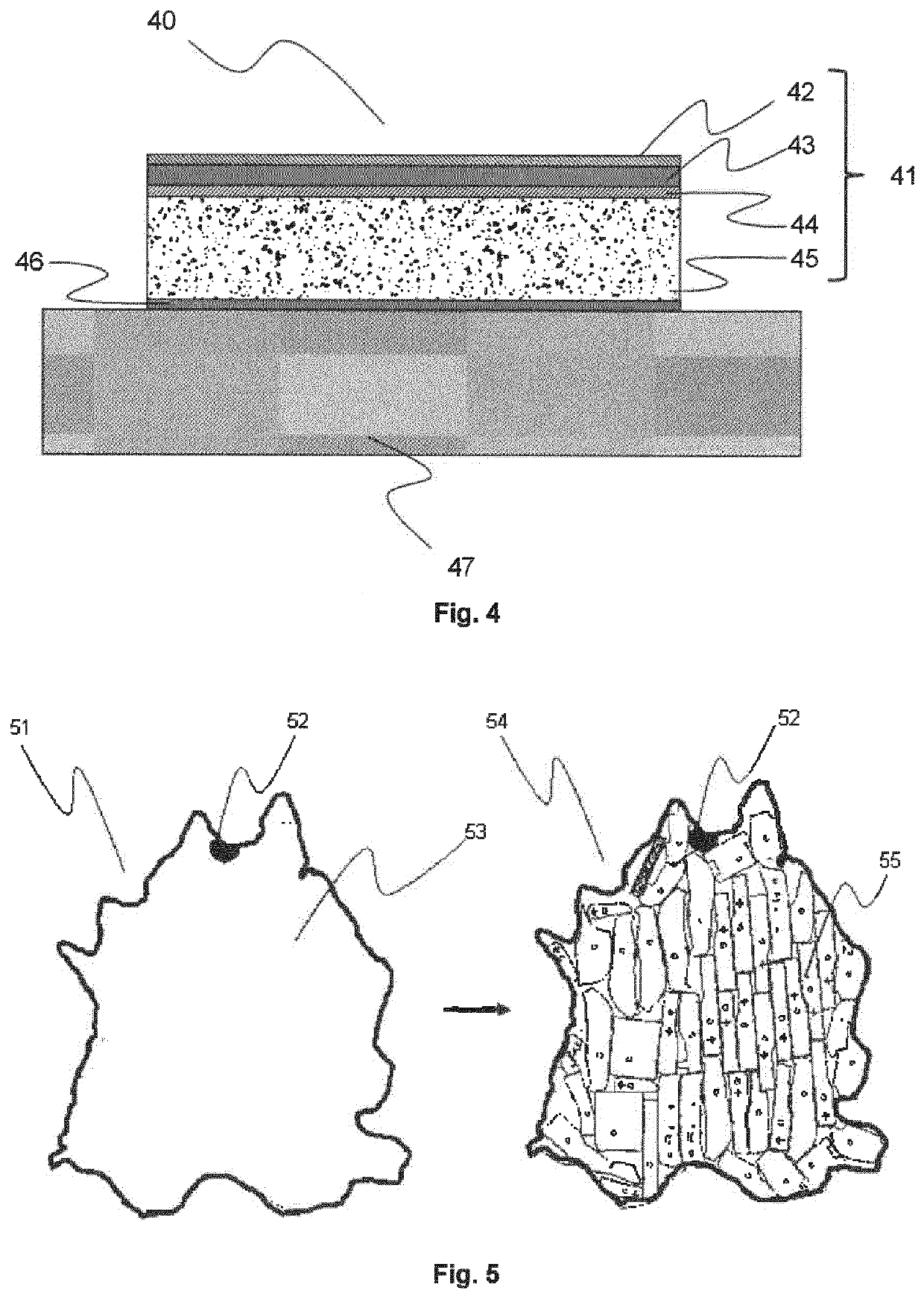
Decorated natural leather
PendingUS20210213768A1Avoid mistakesReduce wasteDuplicating/marking methodsInksPolymer scienceAdhesive
A manufacturing method of decorated natural leather including the steps of: attaching a crusted leather (45) with its corium side by an adhesive (46) to a temporary carrier (47); inkjet printing the crusted leather (45) on its grain side with one or more pigmented inkjet inks; wherein the surface area of the temporary carrier (47) is larger than the surface area of the crusted leather (45).
Owner:AGFA NV
Method for operating a security device
ActiveUS8904193B2Eliminate errorsMaintaining secrecyKey distribution for secure communicationUser identity/authority verificationMicrocontrollerOperation safety
Owner:ROBERT BOSCH GMBH
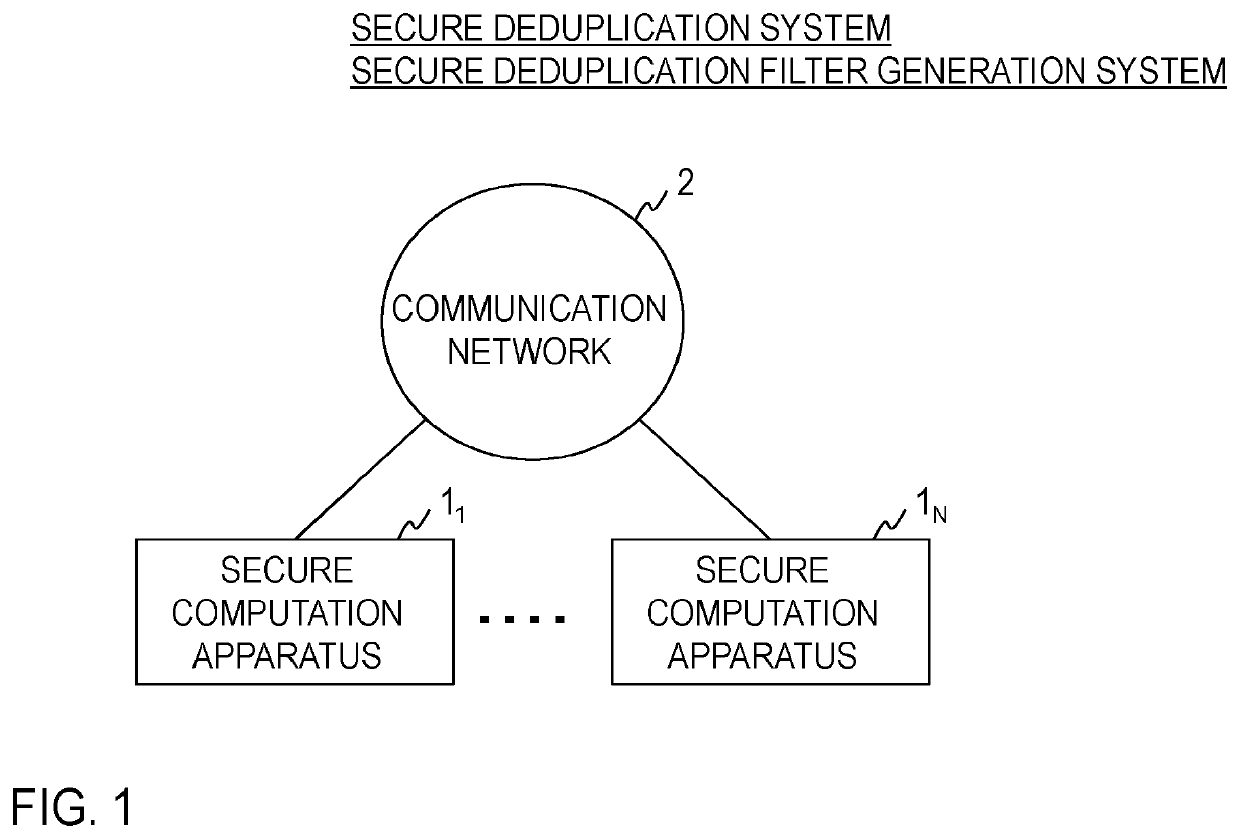
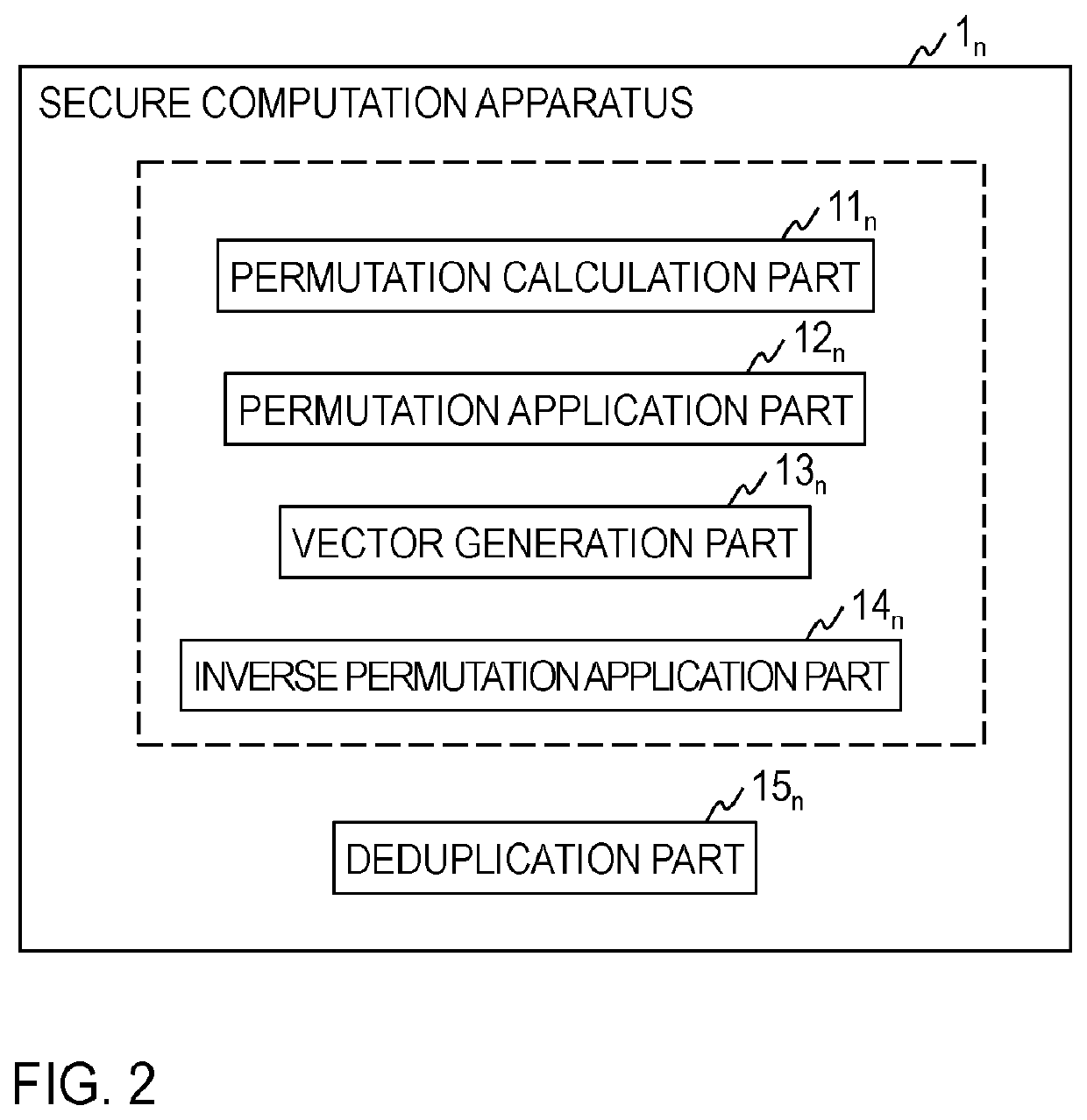
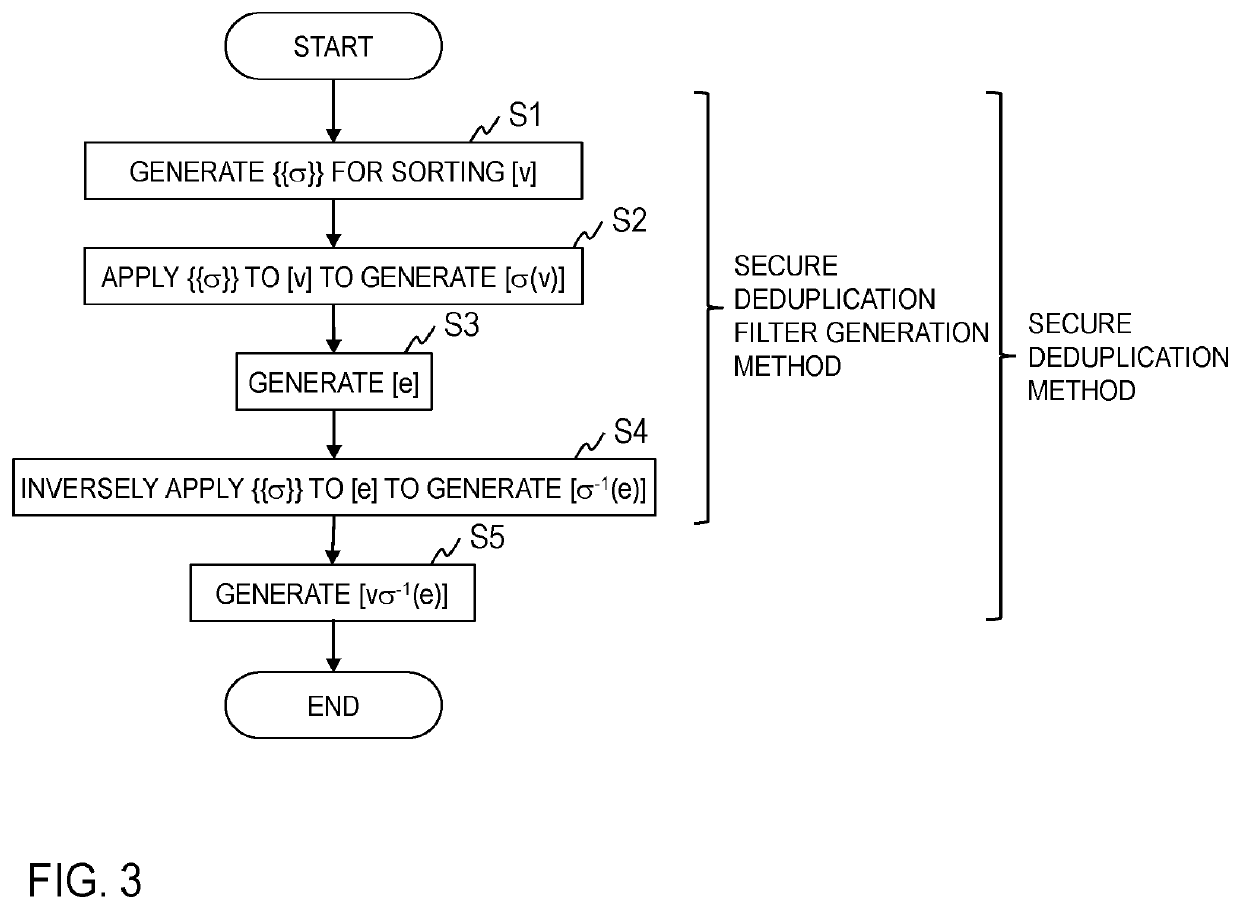
Secret deduplication filter generation system, secret deduplication system, method for these, secret calculation apparatus, and program
ActiveUS20210026812A1Eliminate duplicationMaintaining secrecyDigital data information retrievalMultiple keys/algorithms usageAlgorithmTheoretical computer science
A secure deduplication system, including a plurality of secure computation apparatuses, wherein the plurality of secure computation apparatuses include a plurality of permutation calculation parts 11n for generating a share {{σ}} of a permutation σ that stably sorts a vector v in ascending order, a plurality of permutation application parts 12n for generating a share [σ(v)] of a vector σ(v) obtained by applying the permutation σ to the vector v, a plurality of vector generation parts 13n for generating a share [e] of a vector e that has 1 as an element corresponding to a certain element when the certain element of the vector σ(v) and an element before the certain element are different, and has 0 otherwise, and a plurality of inverse permutation application parts 14n for generating a share [σ−1(e)] of a vector σ−1(e) obtained by applying an inverse permutation σ−1 of the permutation σ to the vector e.
Owner:NIPPON TELEGRAPH & TELEPHONE CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com