Patents
Literature
2109results about "Subscription services" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
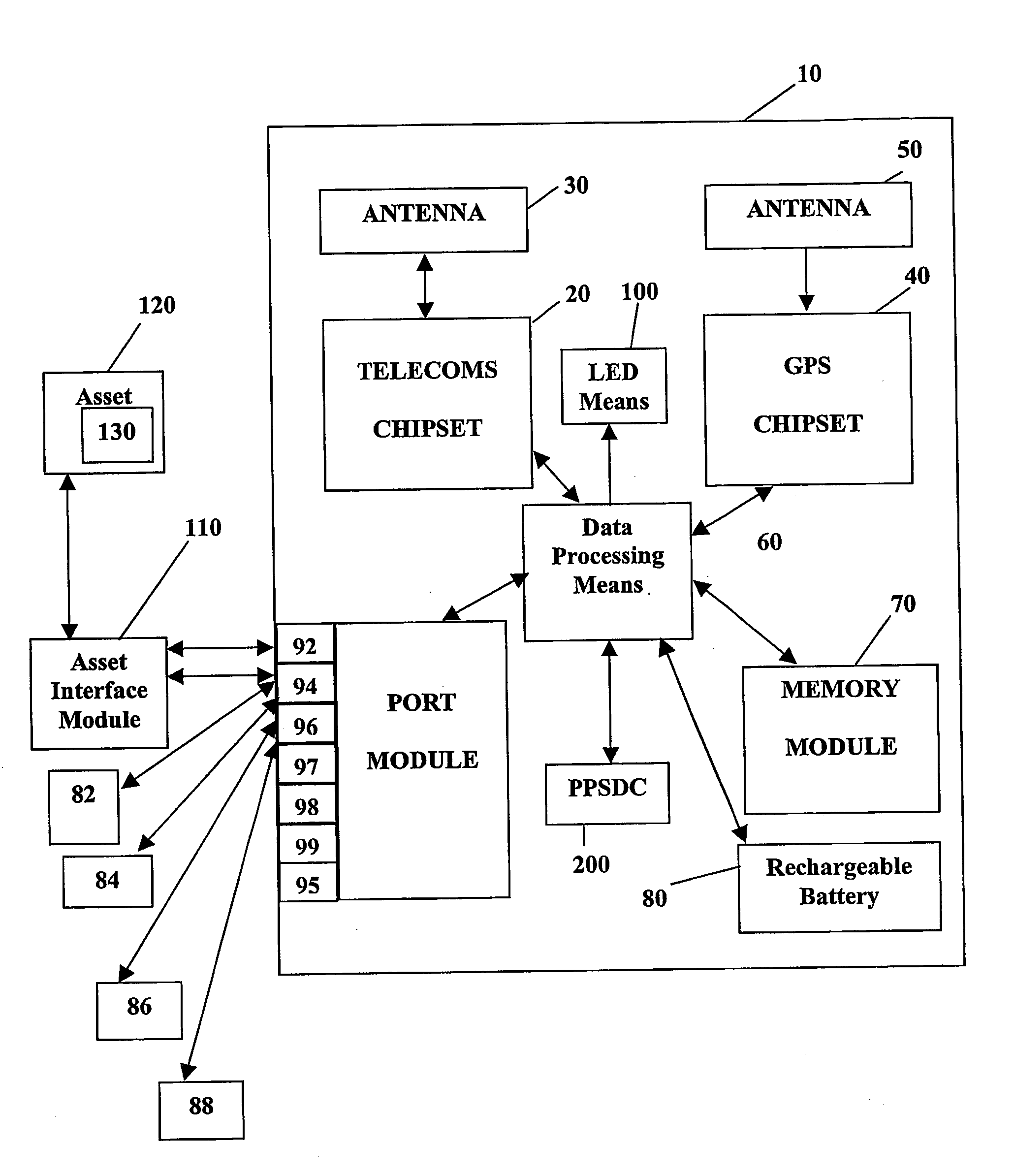
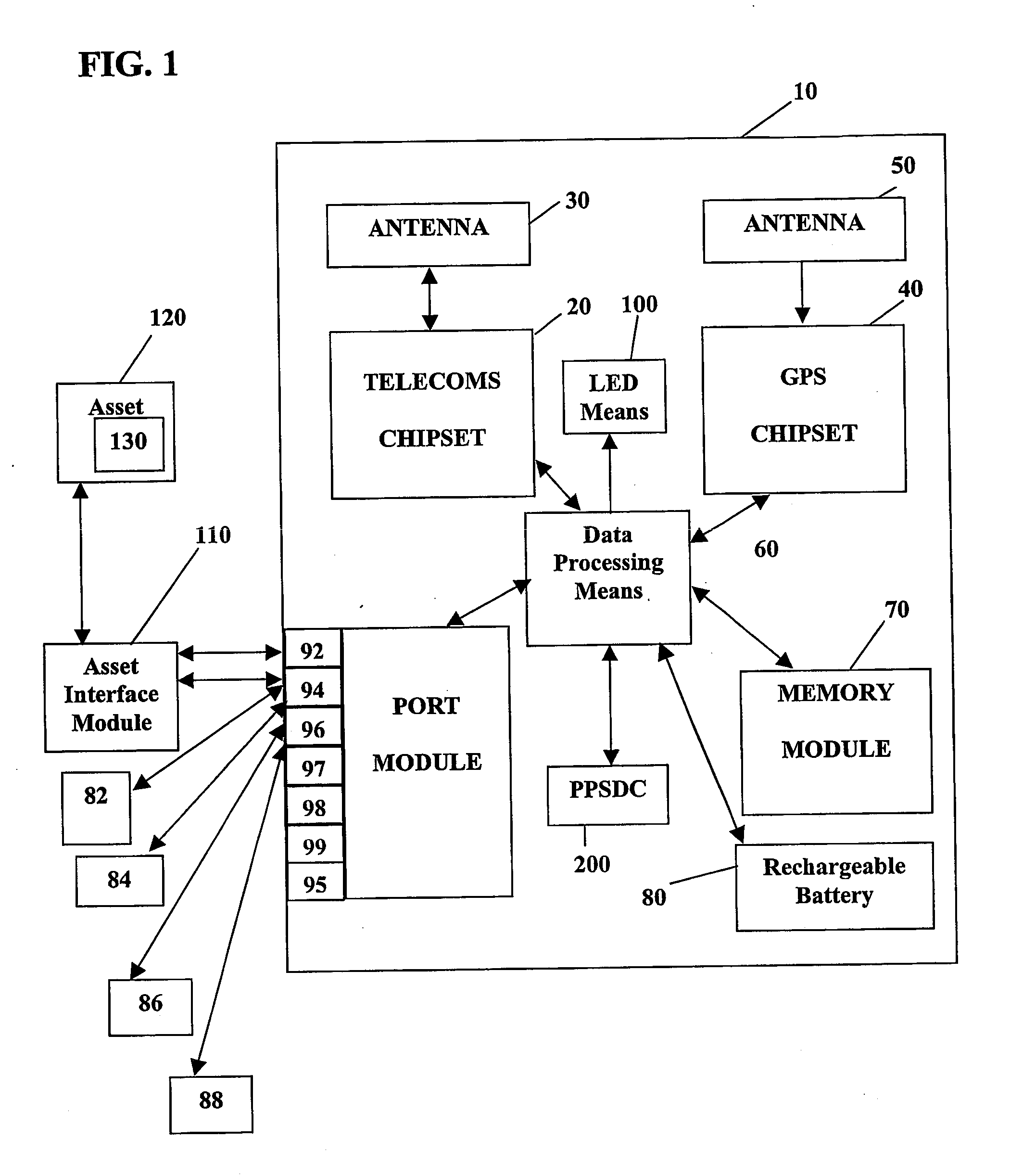
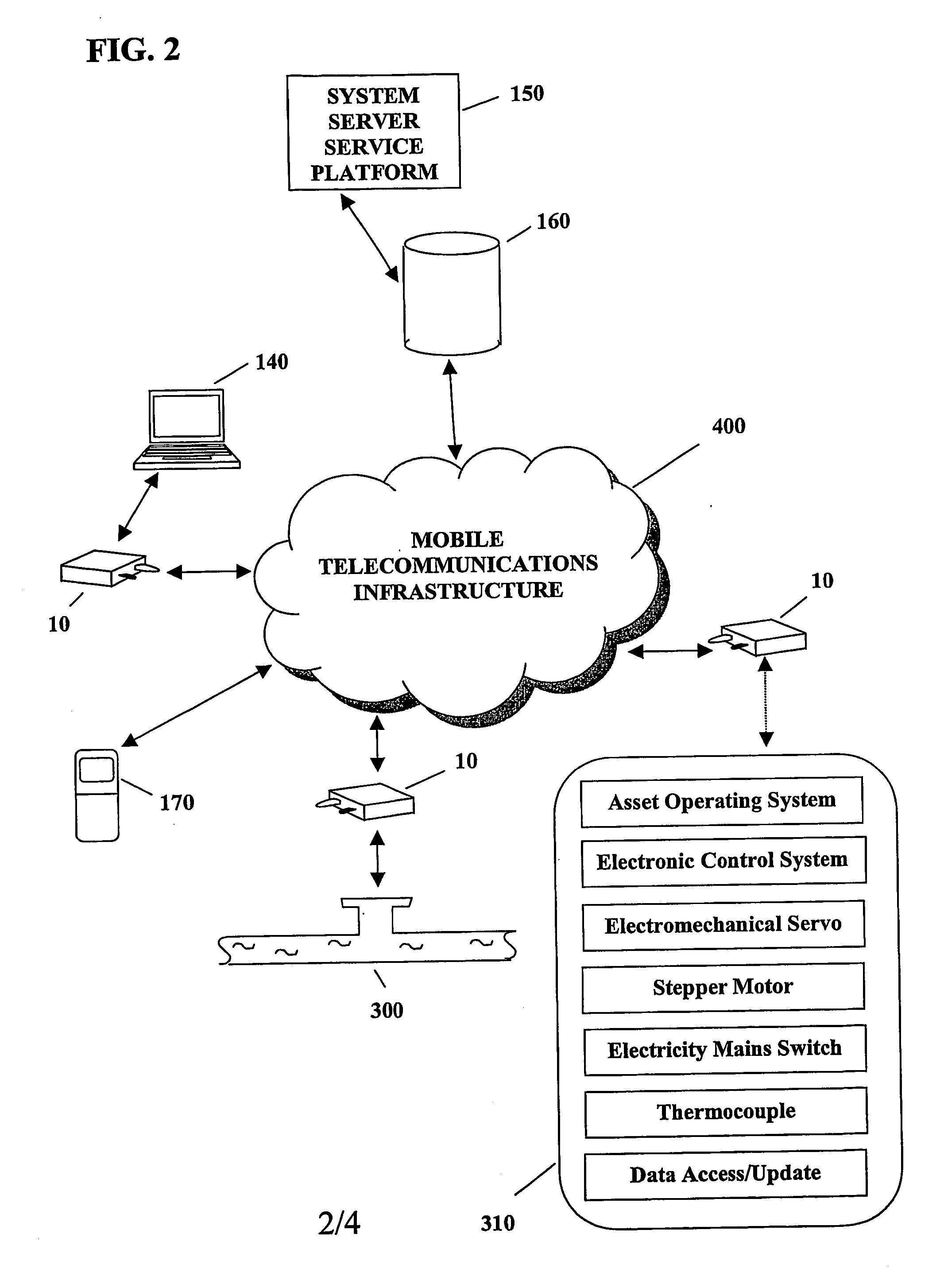
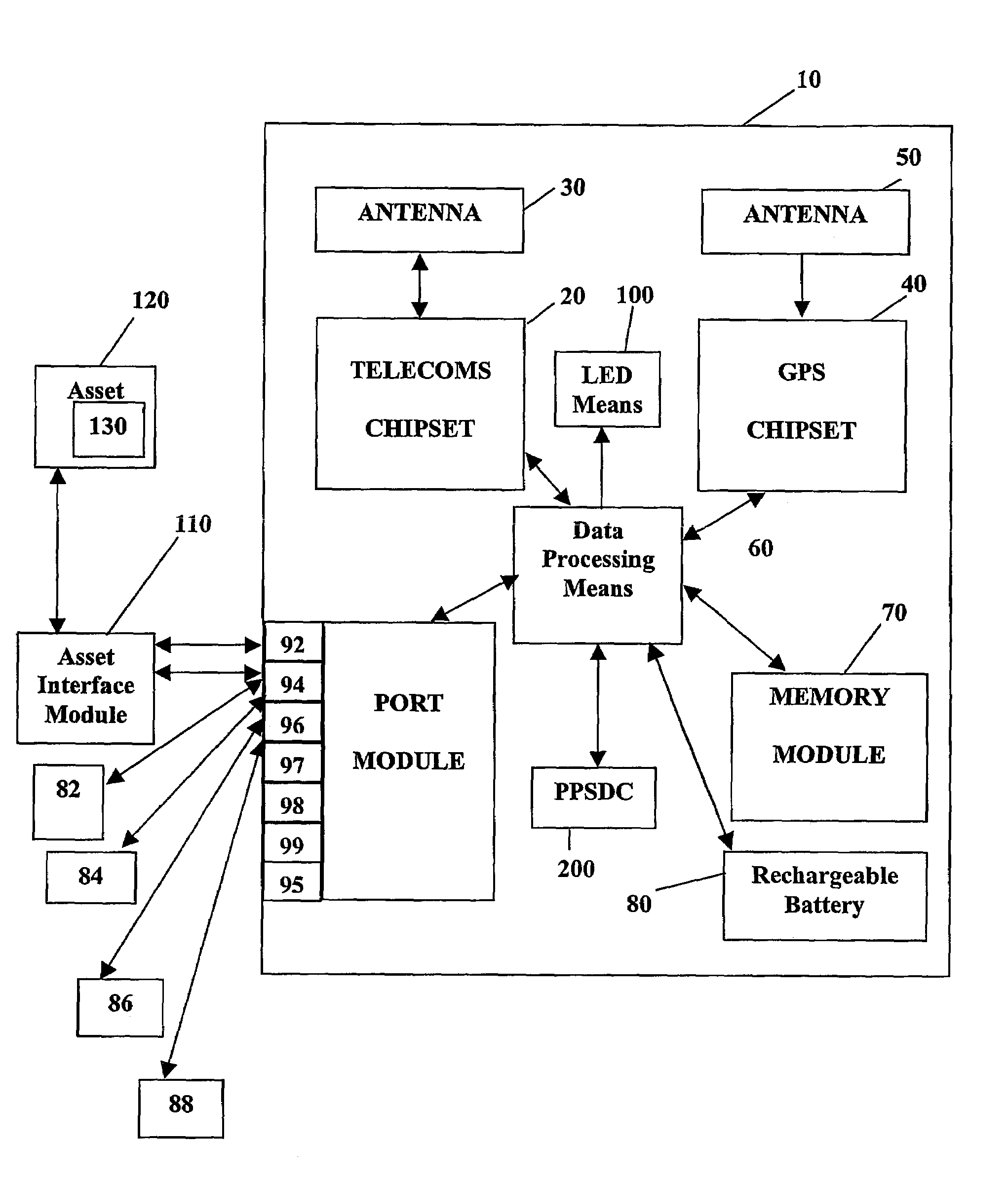
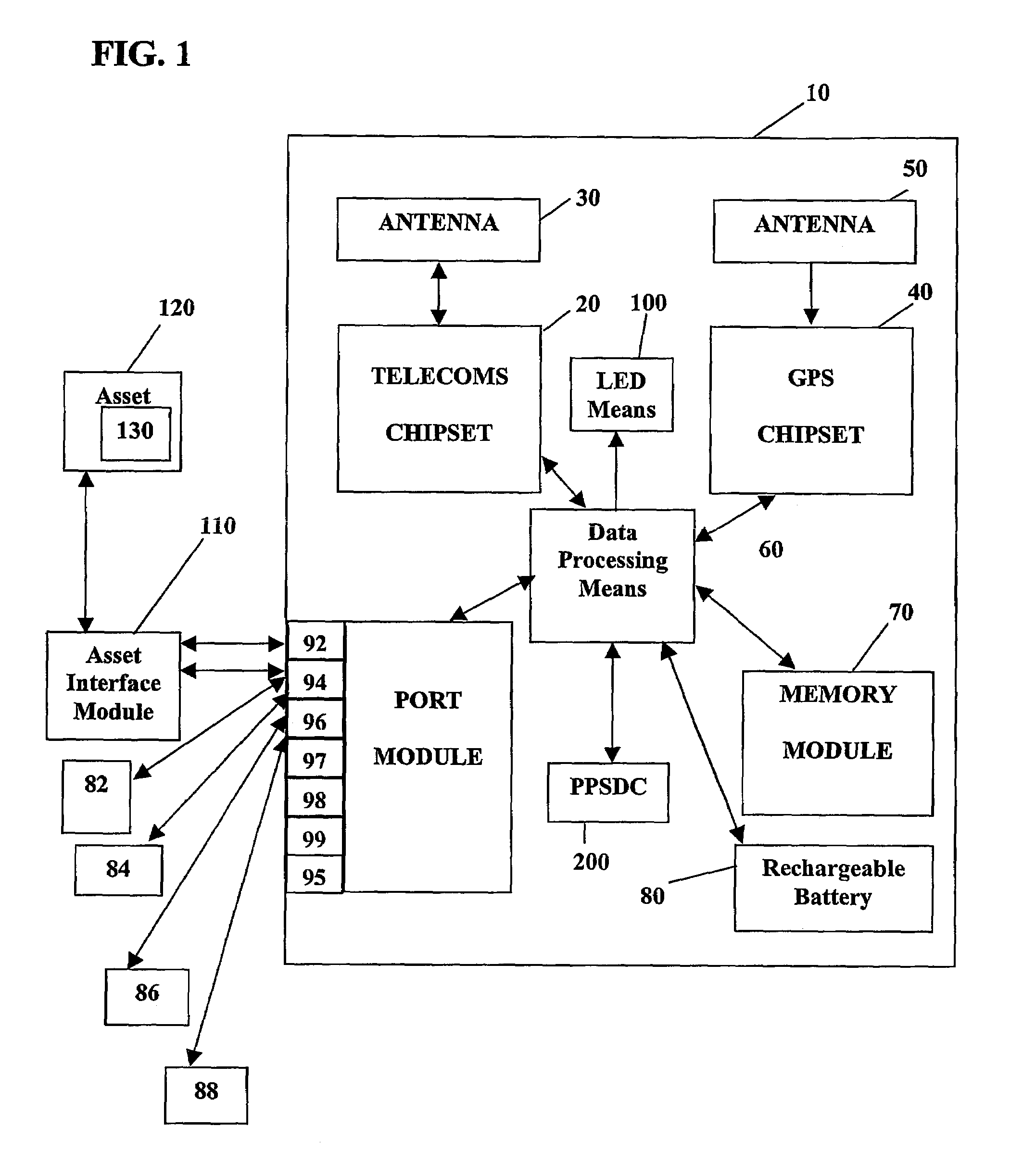
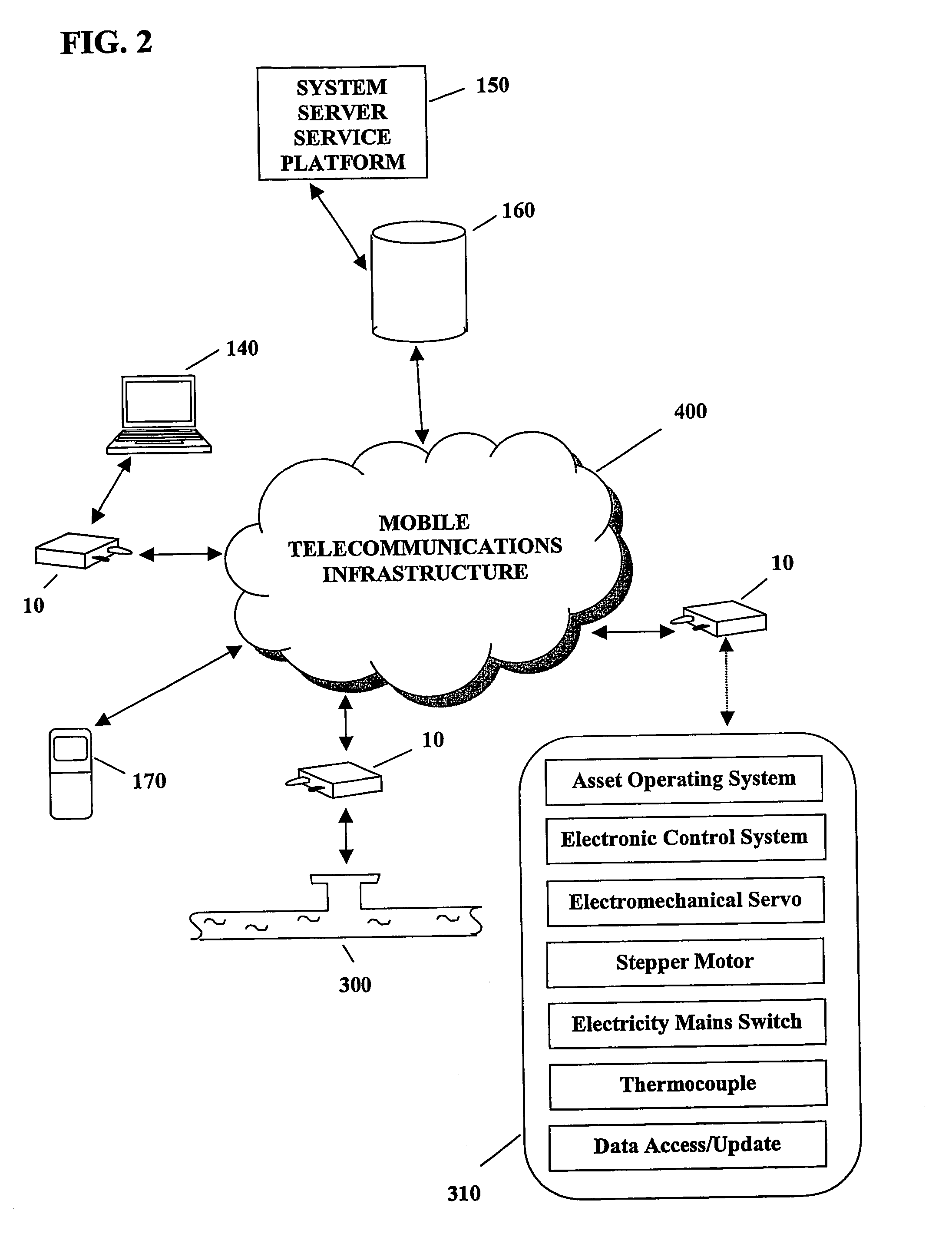
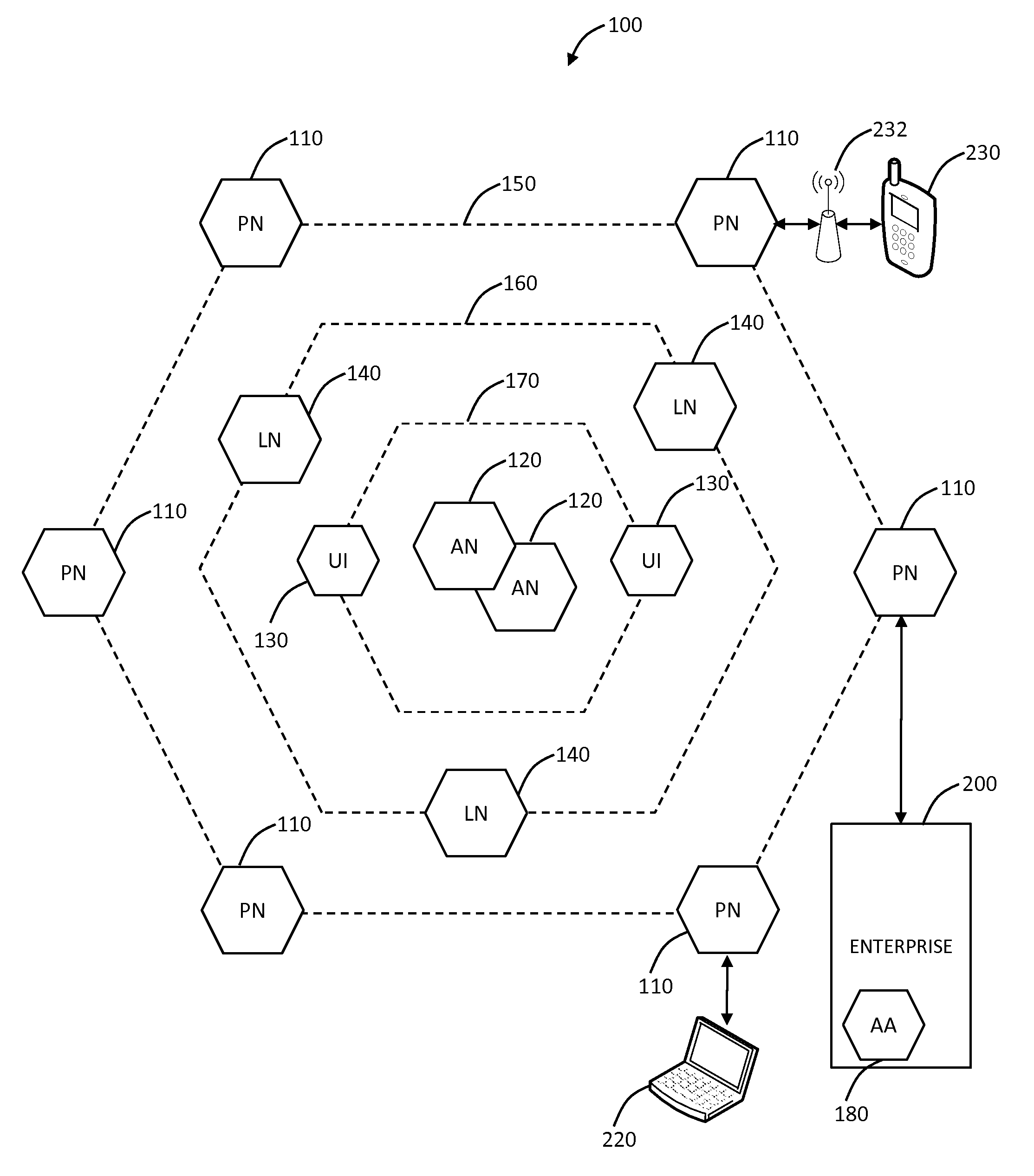
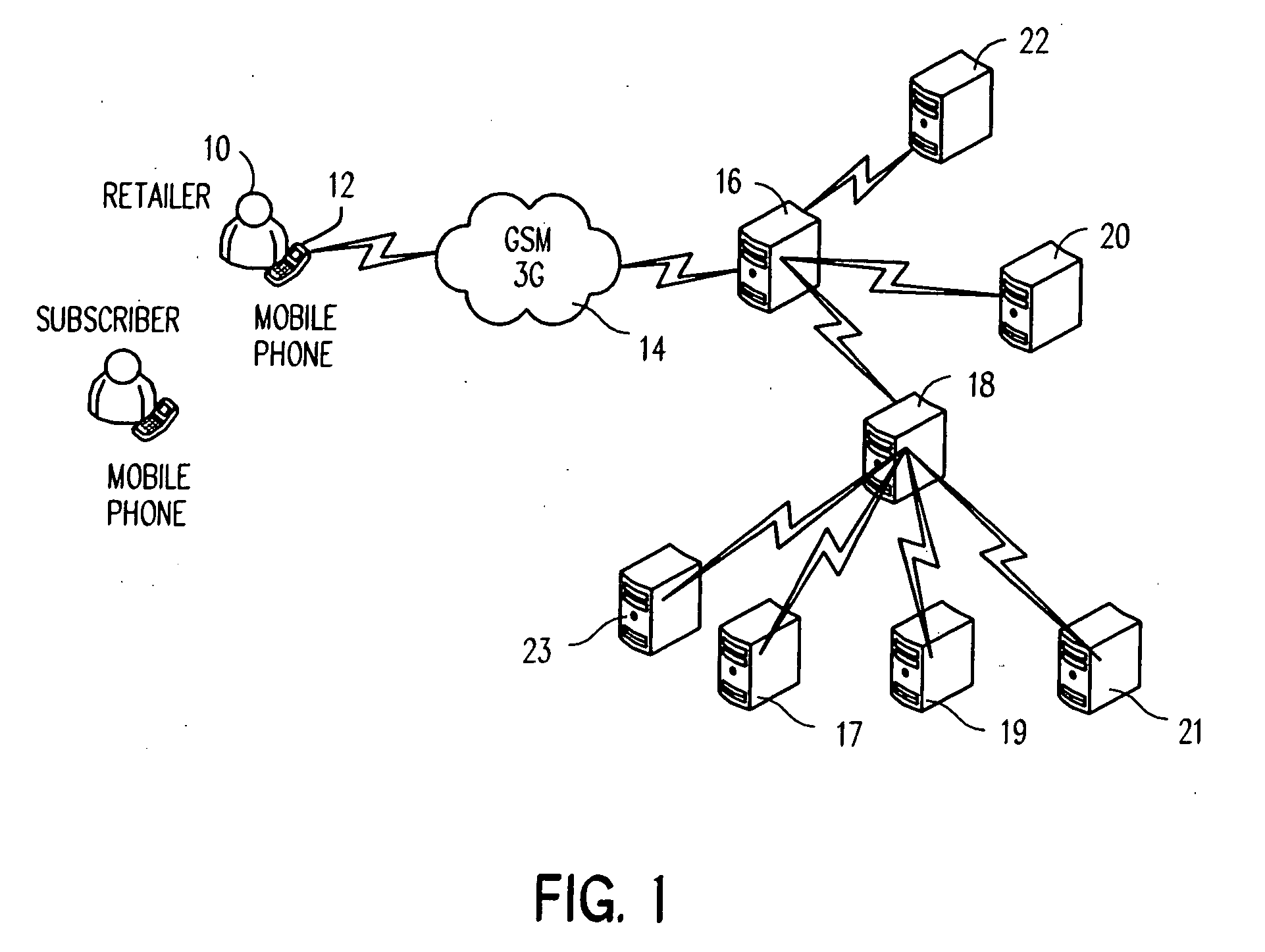
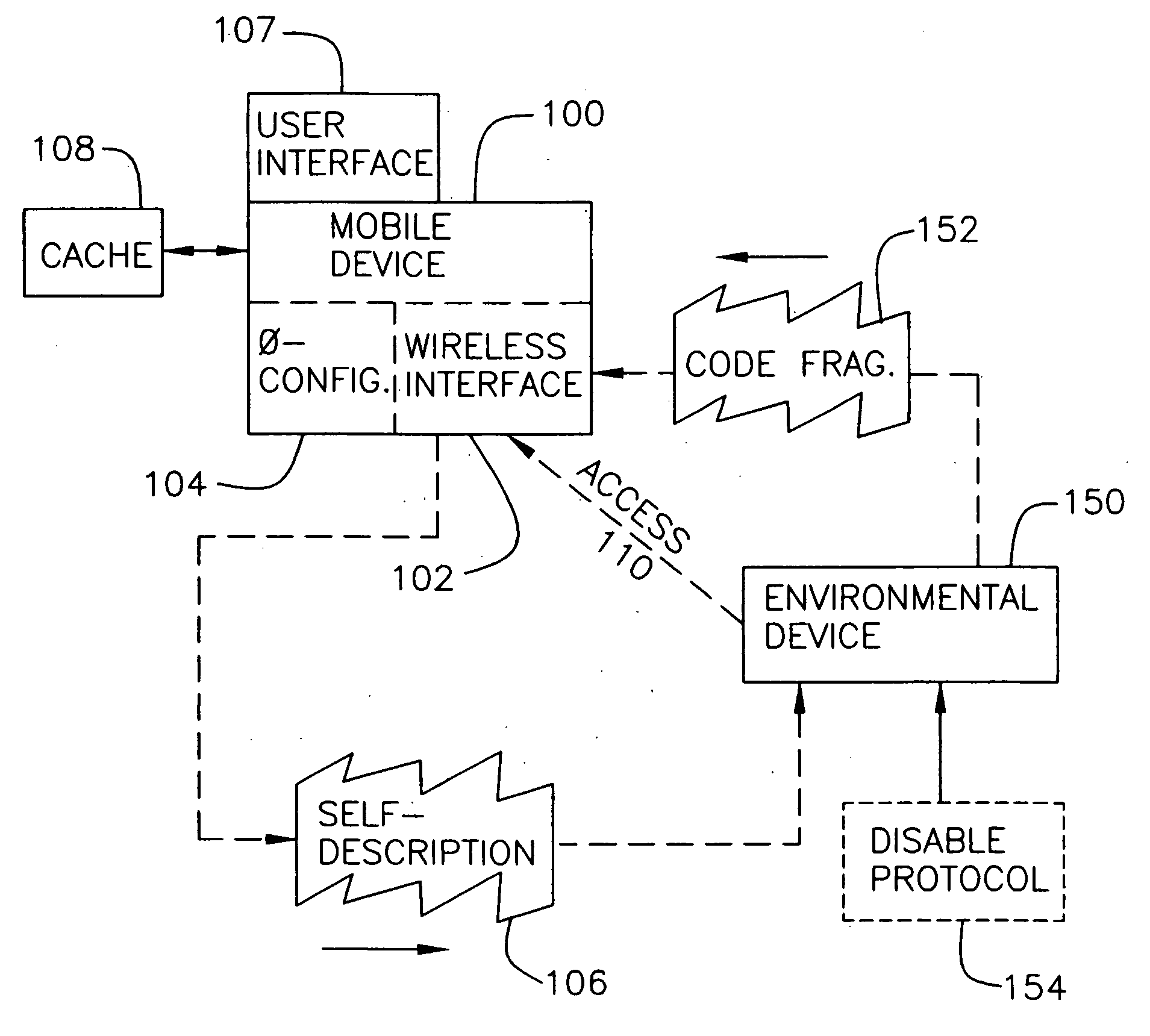
System and method for monitoring and control of wireless modules linked to assets
A system and method for remote asset management is described which can provide the basis for a diverse product group including an improved remote location monitoring system, a means for communicating with and for monitoring the status and or location of a plurality of diverse assets, as well as the means for communicating with said assets for the purpose of modifying the operational status of one or more of said assets according to one or more stored data parameters such as location, use, battery power, and such like. The remote asset management system comprise a wireless module, which is associated with at least one of the plurality of assets and which is interfaced with the operating system of said asset and or with an electromechanical control means, which may control one or more features of the operation of said assets. A supporting network-based, or internet-based service platform controls and manages the status of each of the plurality of assets, either automatically, or in response to received messages from fixed or wireless communication devices, and which is capable of selectively communicating data to said assets for changing the operational status of said assets according to pre-programmed conditions.
Owner:M2M SOLUTIONS
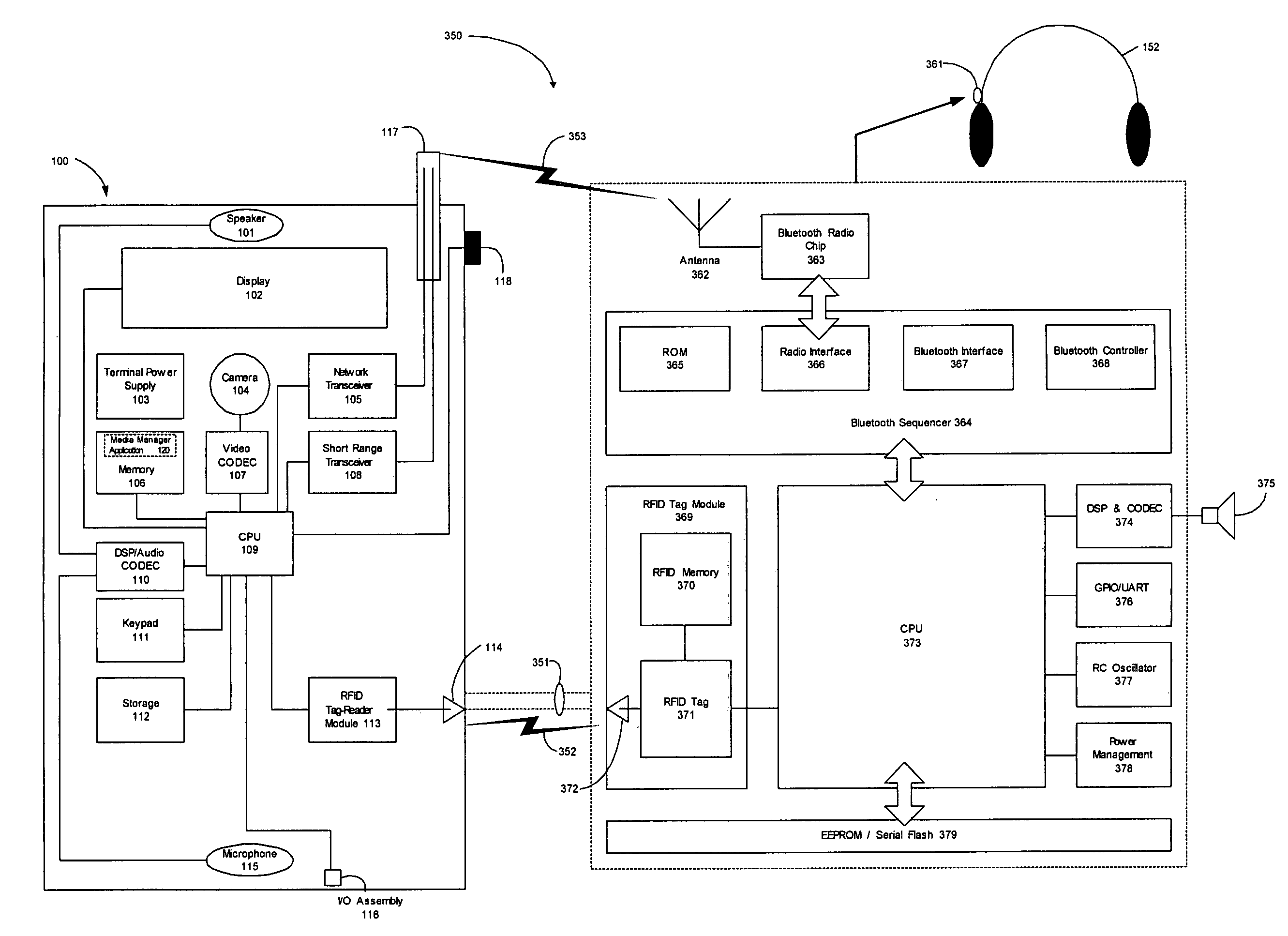
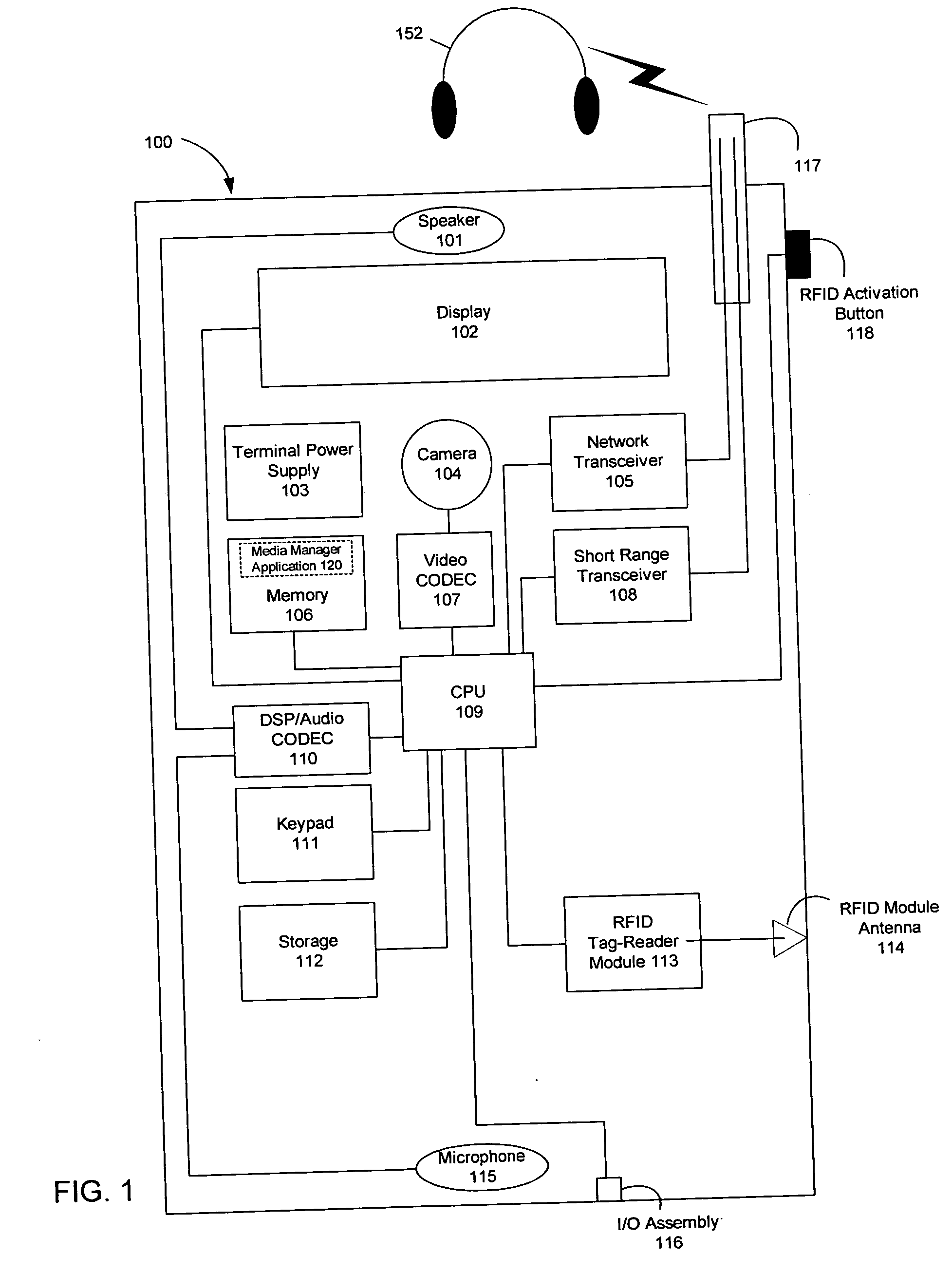
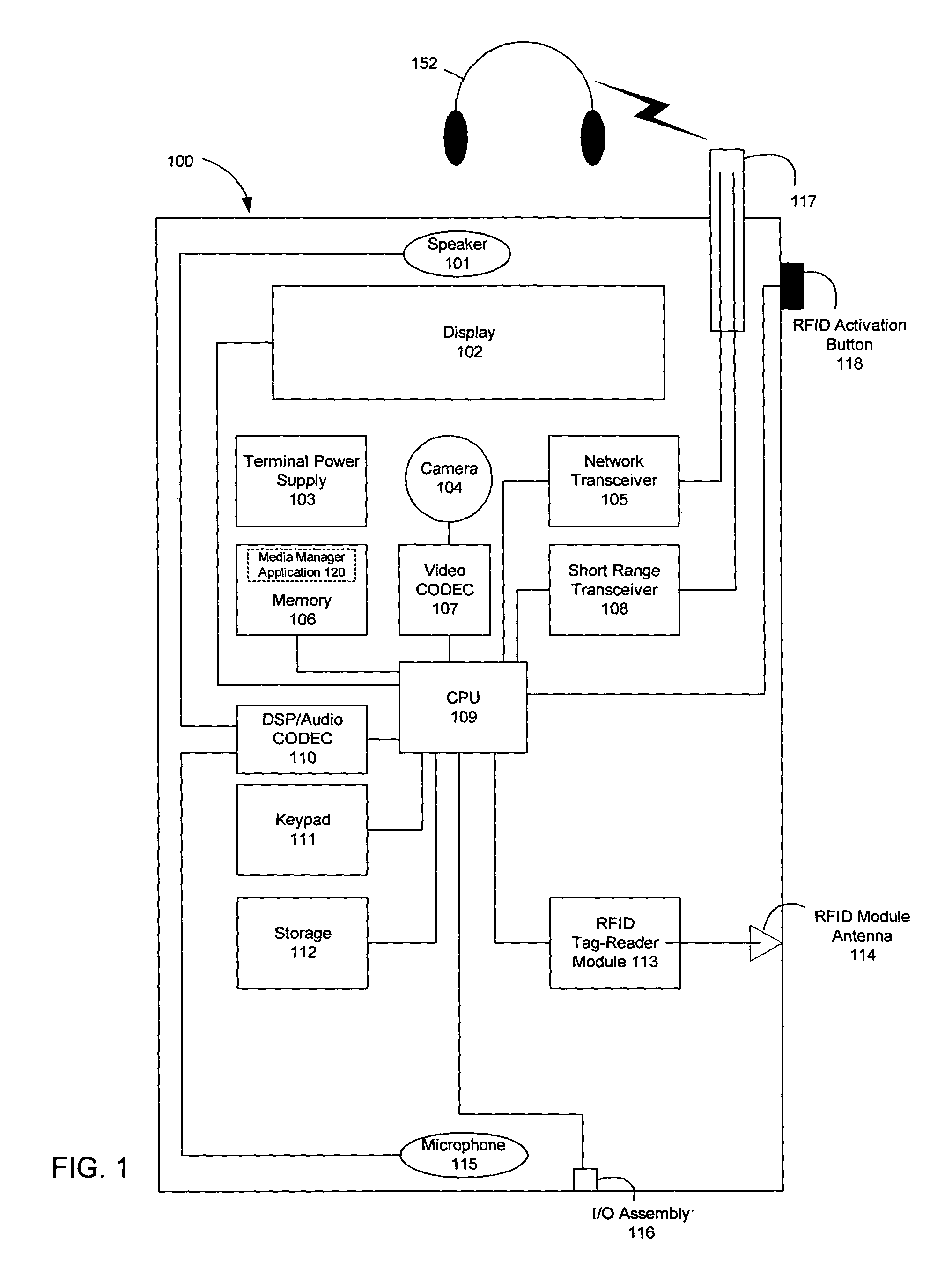
Wireless media system and player and method of operation
ActiveUS20060258289A1Easy to useMultimedia data browsing/visualisationPayment architectureUltra-widebandSecure communication
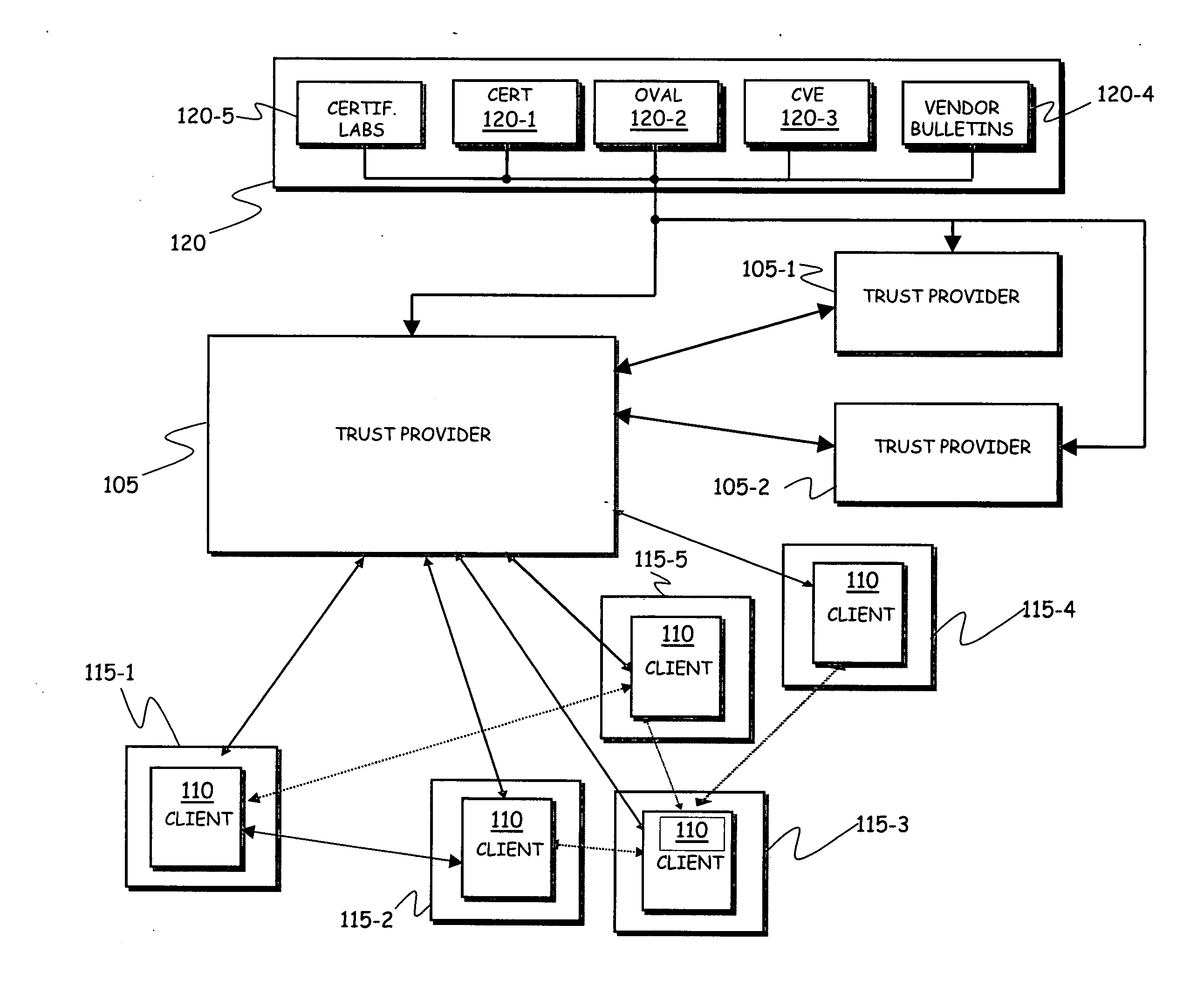
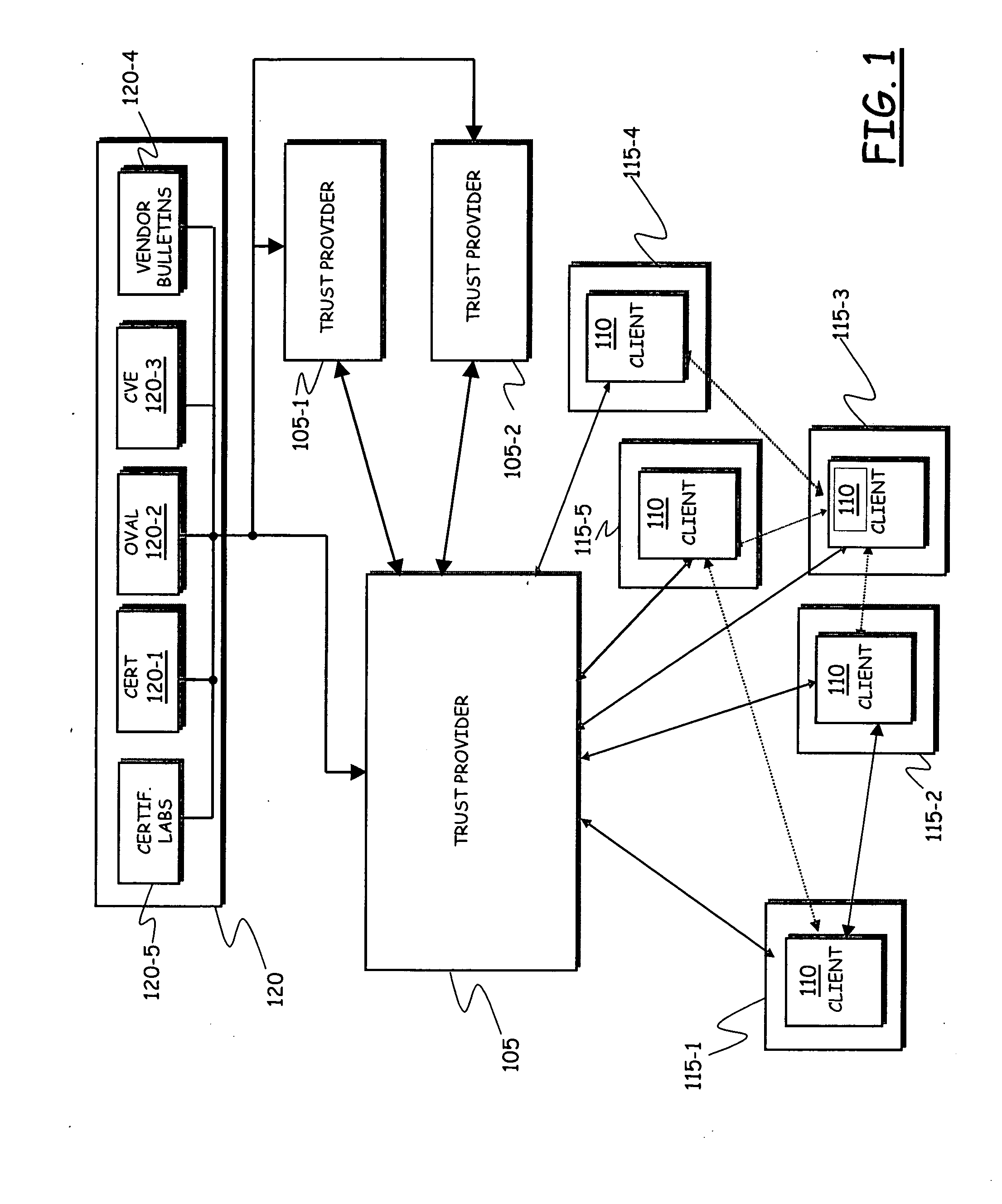
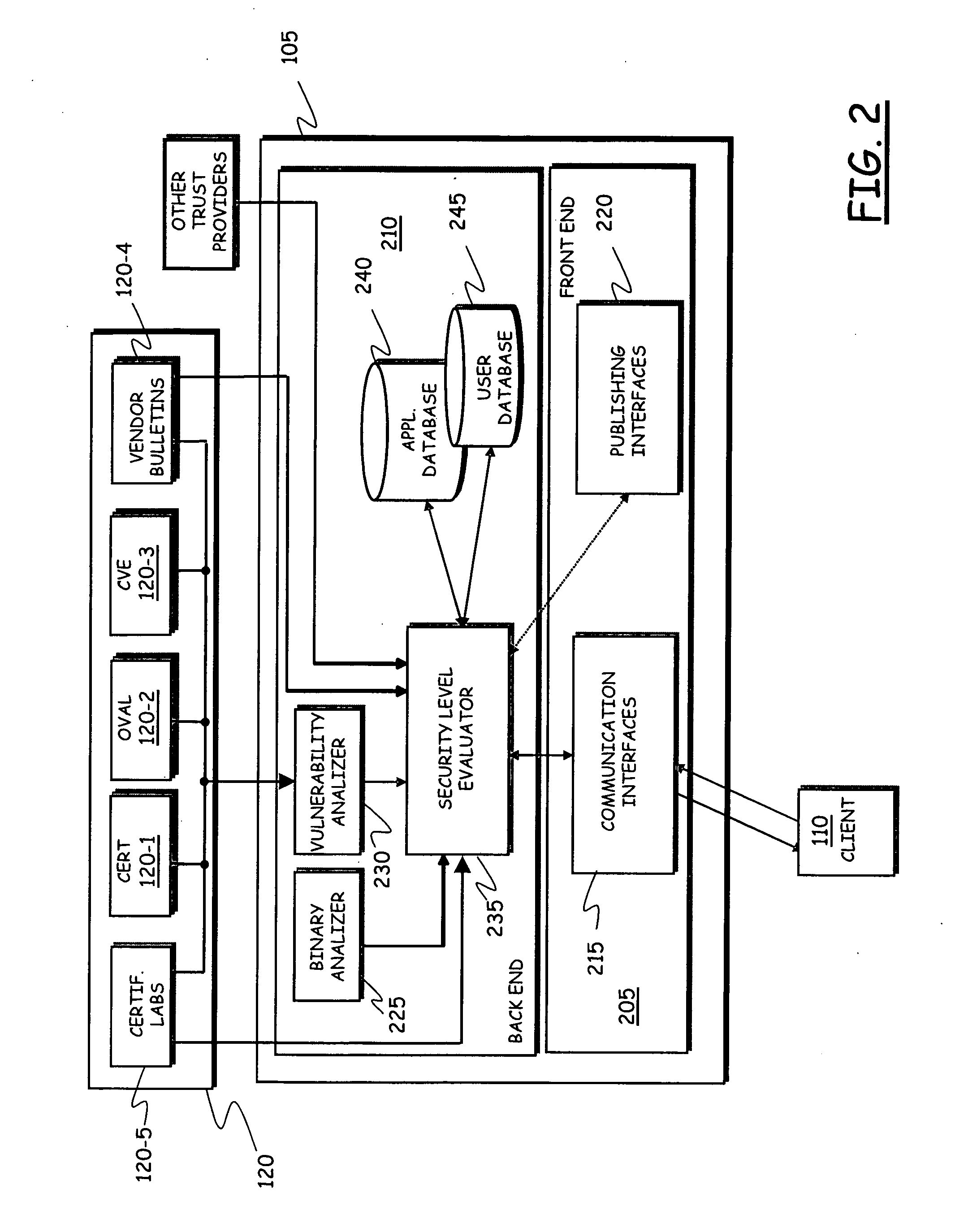
A wireless media player and a related system and methodology are disclosed. One aspect of the wireless media player system pertains to a virtual connector system, apparatus, and method for the automatic establishment of wireless connectivity with other electronic devices. In one embodiment, the media player device employs the use of integrated Radio Frequency Identification (RFID) technology to exchange communication settings, media capability, and other parameters with an external device that also has integrated RFID technology. The automatic exchange of settings and other information via a proximity-based RFID data exchange allows a media player to quickly establish a secure communication link with another device via a commonly supported wireless protocol such as Ultra Wideband (UWB) or Bluetooth. Another aspect of the media player system pertains to a method of using the captured media capability of the connecting device to customize certain menu options and software parameters in the media player.
Owner:SYNDEFENSE
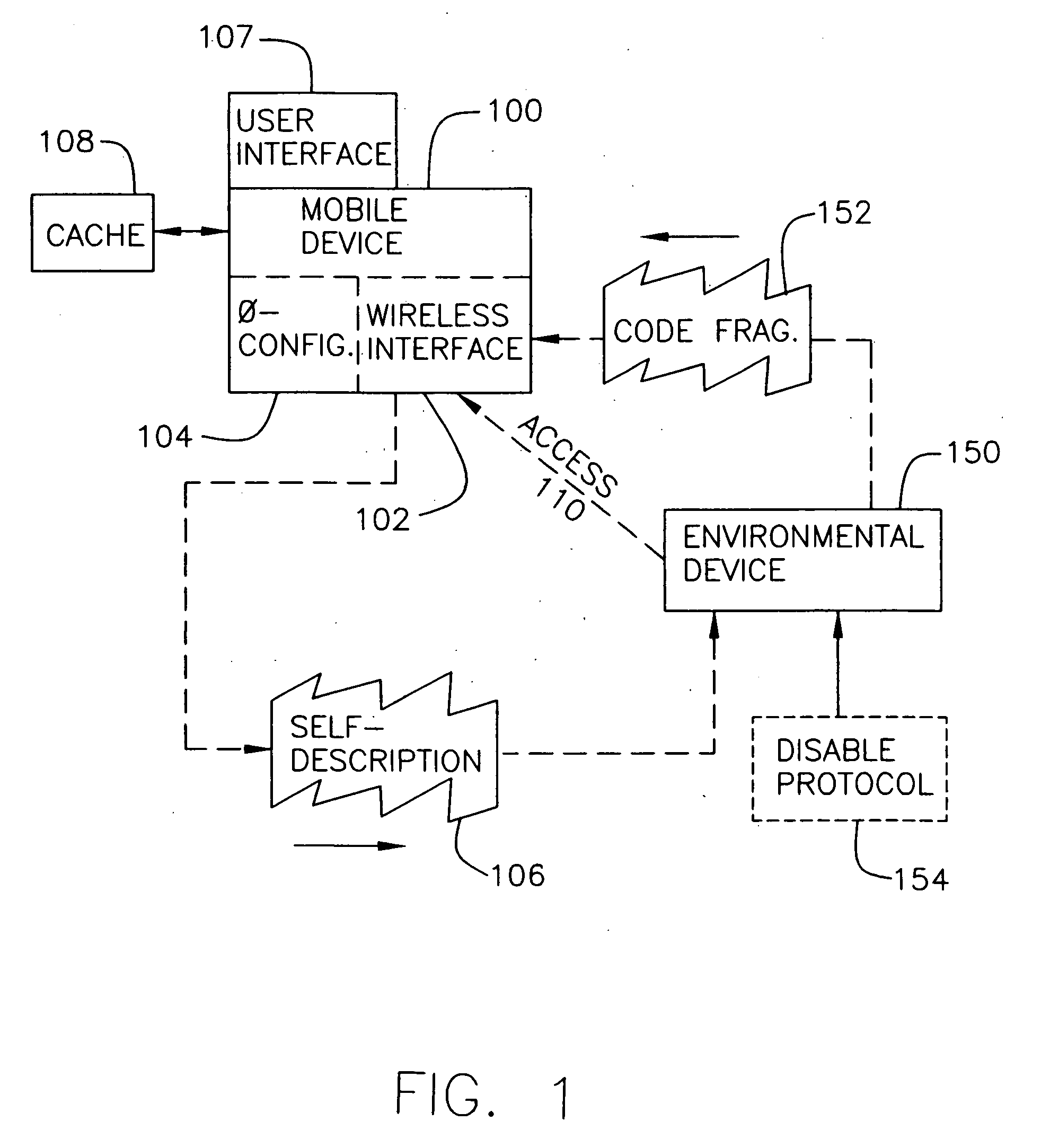
System and method for monitoring and control of wireless modules linked to assets
InactiveUS7027808B2Wireless commuication servicesElectric/magnetic detectionOperational systemComputer module
A system and method for remote asset management is described which can provide the basis for a diverse product group including an improved remote location monitoring system, a means for communicating with and for monitoring the status and or location of a plurality of diverse assets, as well as the means for communicating with said assets for the purpose of modifying the operational status of one or more of said assets according to one or more stored data parameters such as location, use, battery power, and such like. The remote asset management system comprises a wireless module, which is associated with at least one of the plurality of asset and which is interfaced with the operating system of said assert and or with an electromechanical control means, which may control one or more features of the operation of said assets. A supporting network-based, or internet-based service platform, controls and manages the status of each of the plurality of assets, either automatically, or in response to received messages from fixed or wireless communication devices, and which is capable of selectively communicating data to said assets for changing the operational status of said assets according to pre-programmed conditions.
Owner:M2M SOLUTIONS
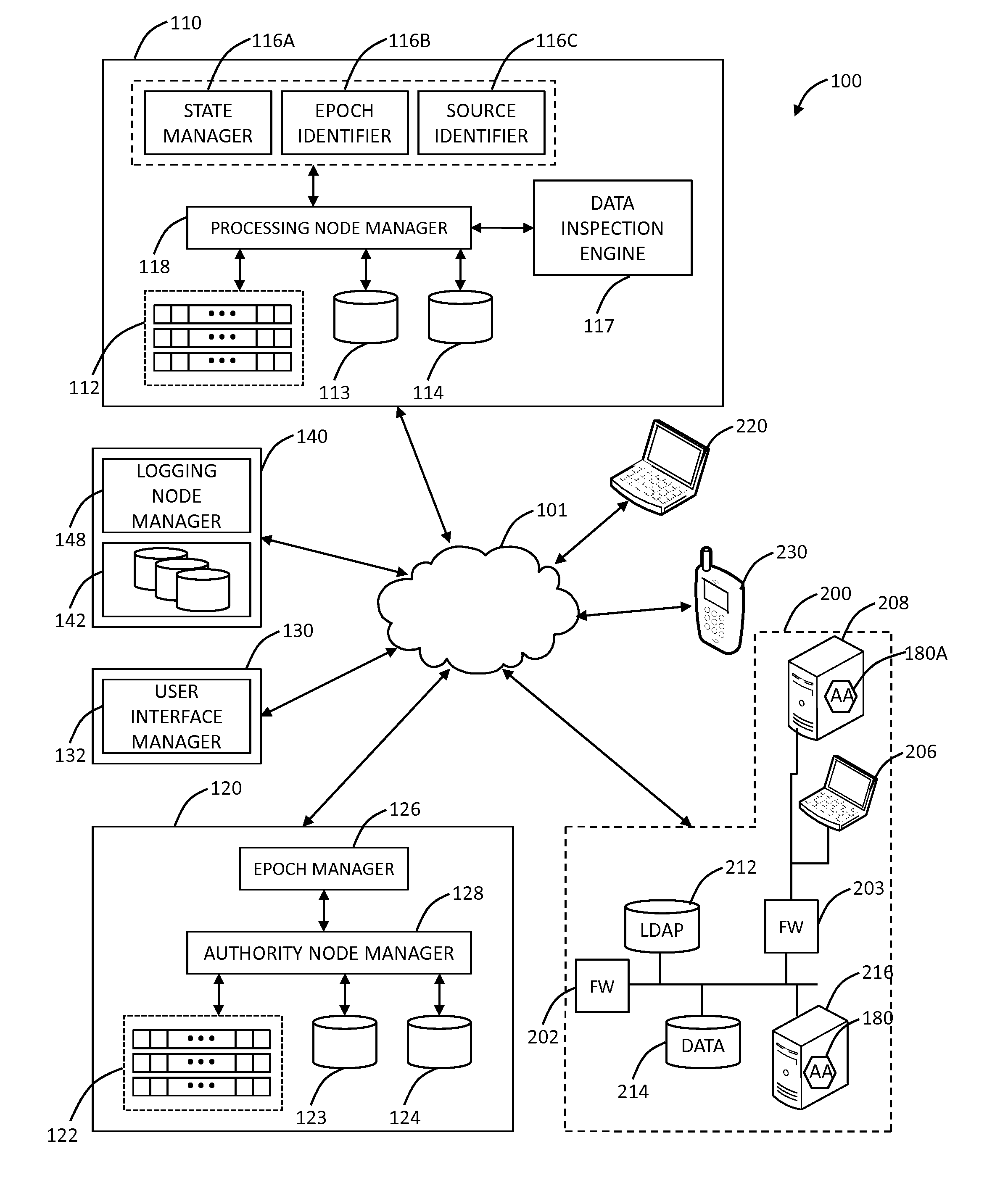
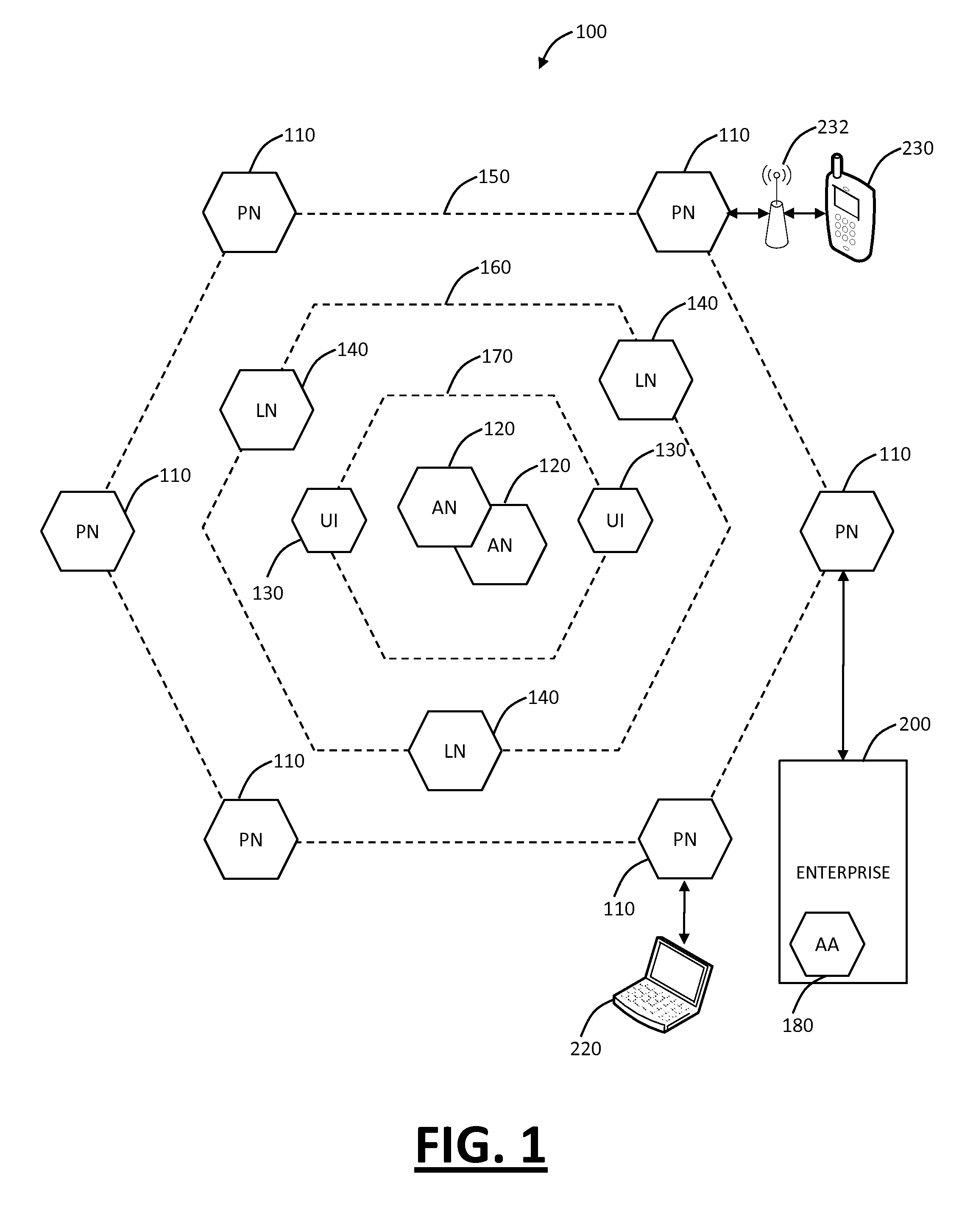
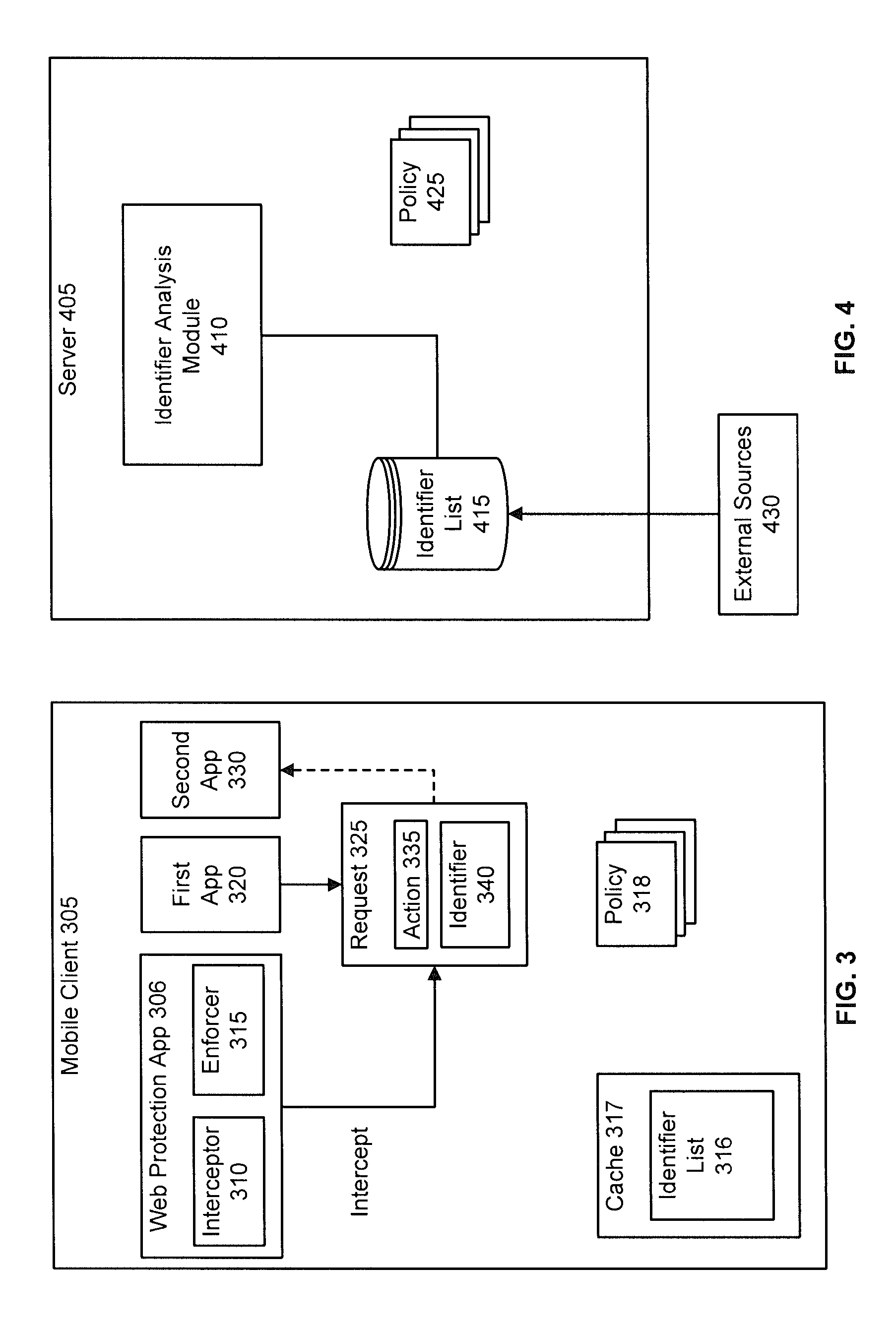
Cloud based mobile device security and policy enforcement
ActiveUS20120240183A1Computer security arrangementsMobile application execution environmentsTablet computerOperational system
The present disclosure relates to cloud based mobile device security and policy systems and methods to use the “cloud” to pervasively enforce security and policy on mobile devices. The cloud based mobile device security and policy systems and methods provide uniformity in securing mobile devices for small to large organizations. The cloud based mobile device security and policy systems and methods may enforce one or more policies for users wherever and whenever the users are connected across a plurality of different devices including mobile devices. This solution ensures protection across different types, brands, operating systems, etc. for smartphones, tablets, netbooks, mobile computers, and the like.
Owner:ZSCALER INC
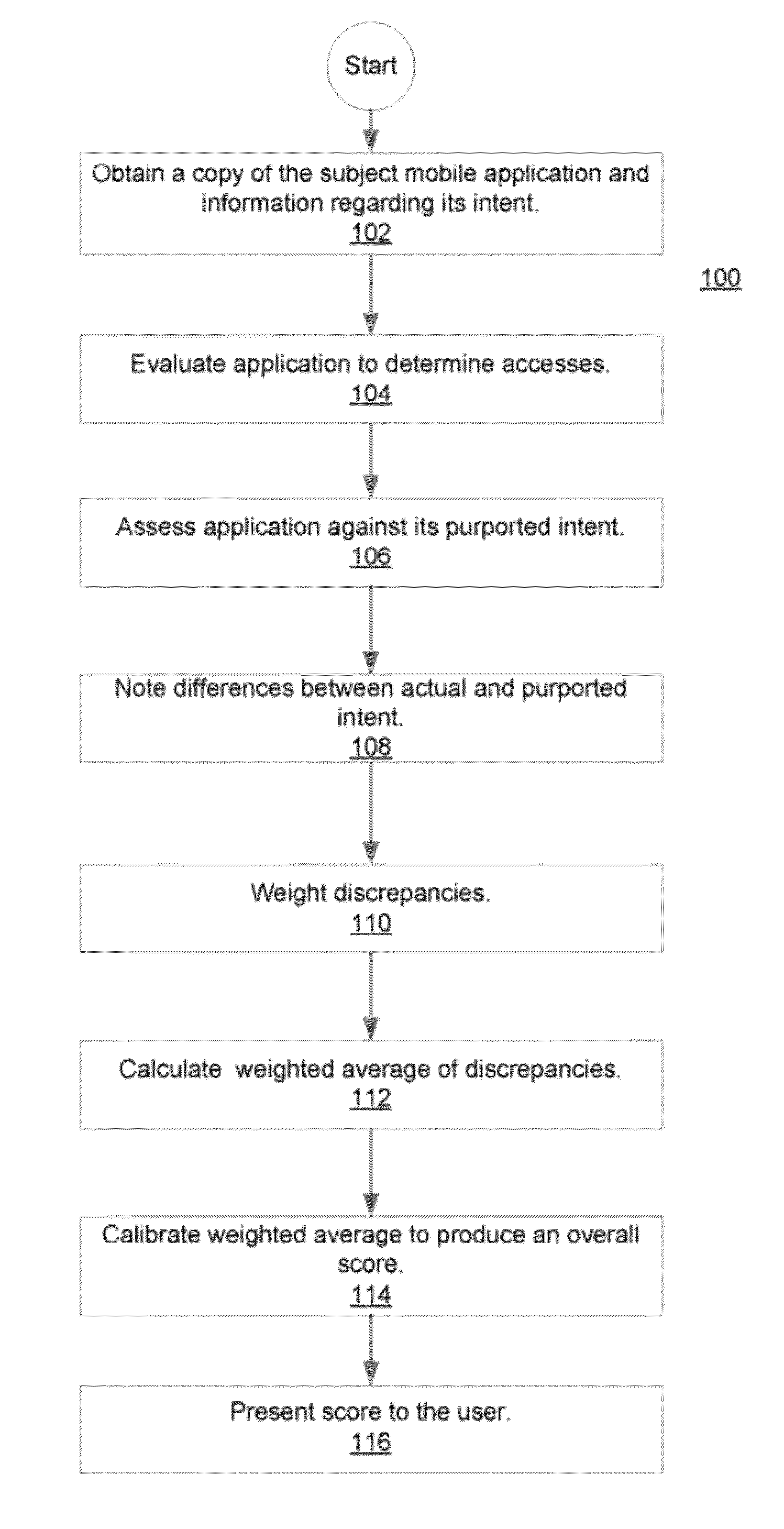
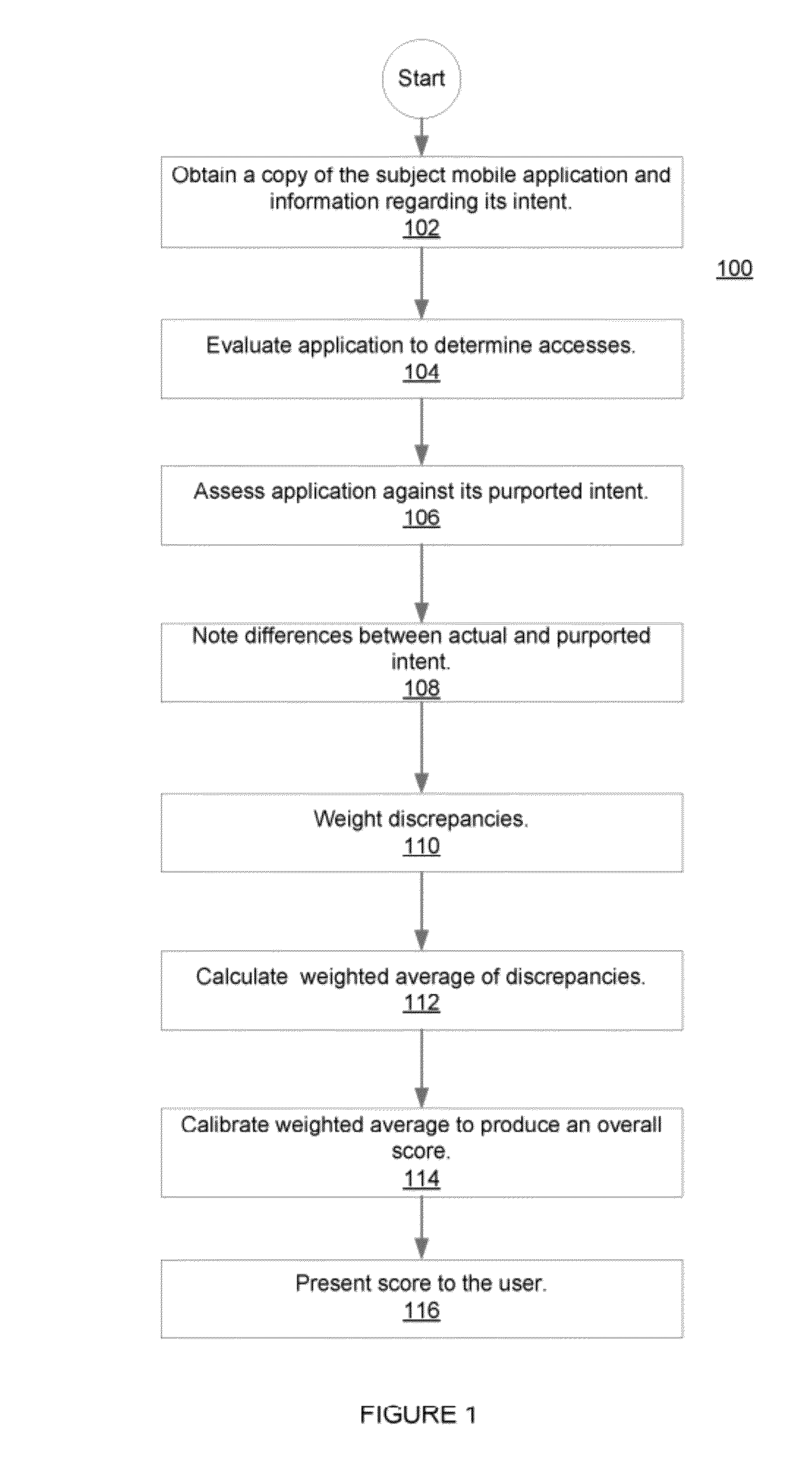
Methods and systems for rating privacy risk of applications for smart phones and other mobile platforms
InactiveUS20120110674A1Better-informed decisionService provisioningMemory loss protectionInternet privacyUser privacy
Methods and systems for evaluating and rating privacy risks posed by applications intended for deployment on mobile platforms. Validating the “intent” of a mobile platform application vis-à-vis its impact on user privacy, as viewed from an end-user's perspective allows those end-users to make better-informed decisions concerning the downloading, installation and / or operation of mobile platform applications. In making such assessments user preferences can be taken into account. Privacy scores are provided through sales channels for the applications, thereby affording potential users the opportunity to assess whether they wish to incur the associated privacy risk, before purchasing a subject application.
Owner:NCC GRP SECURITY SERVICES
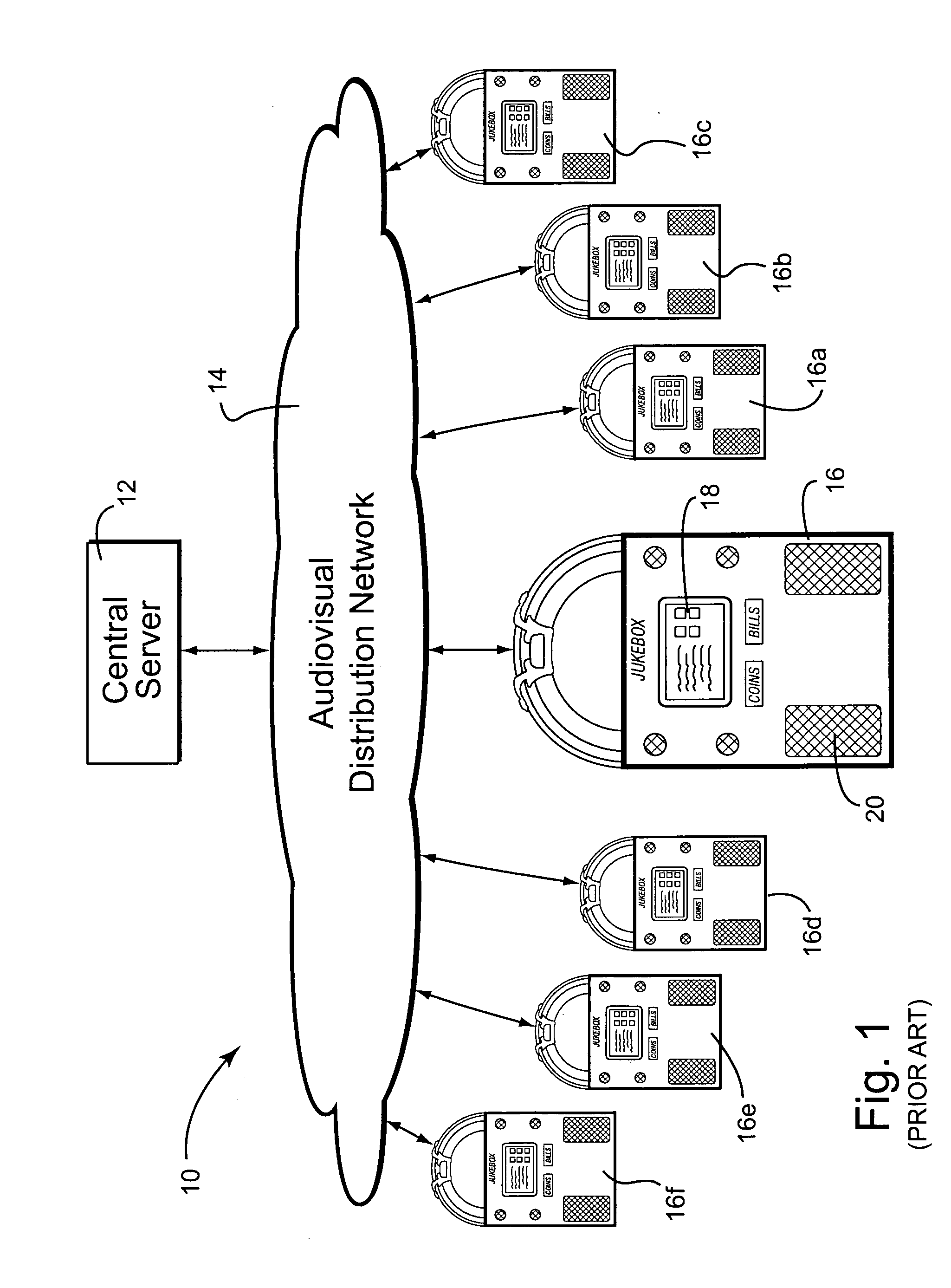
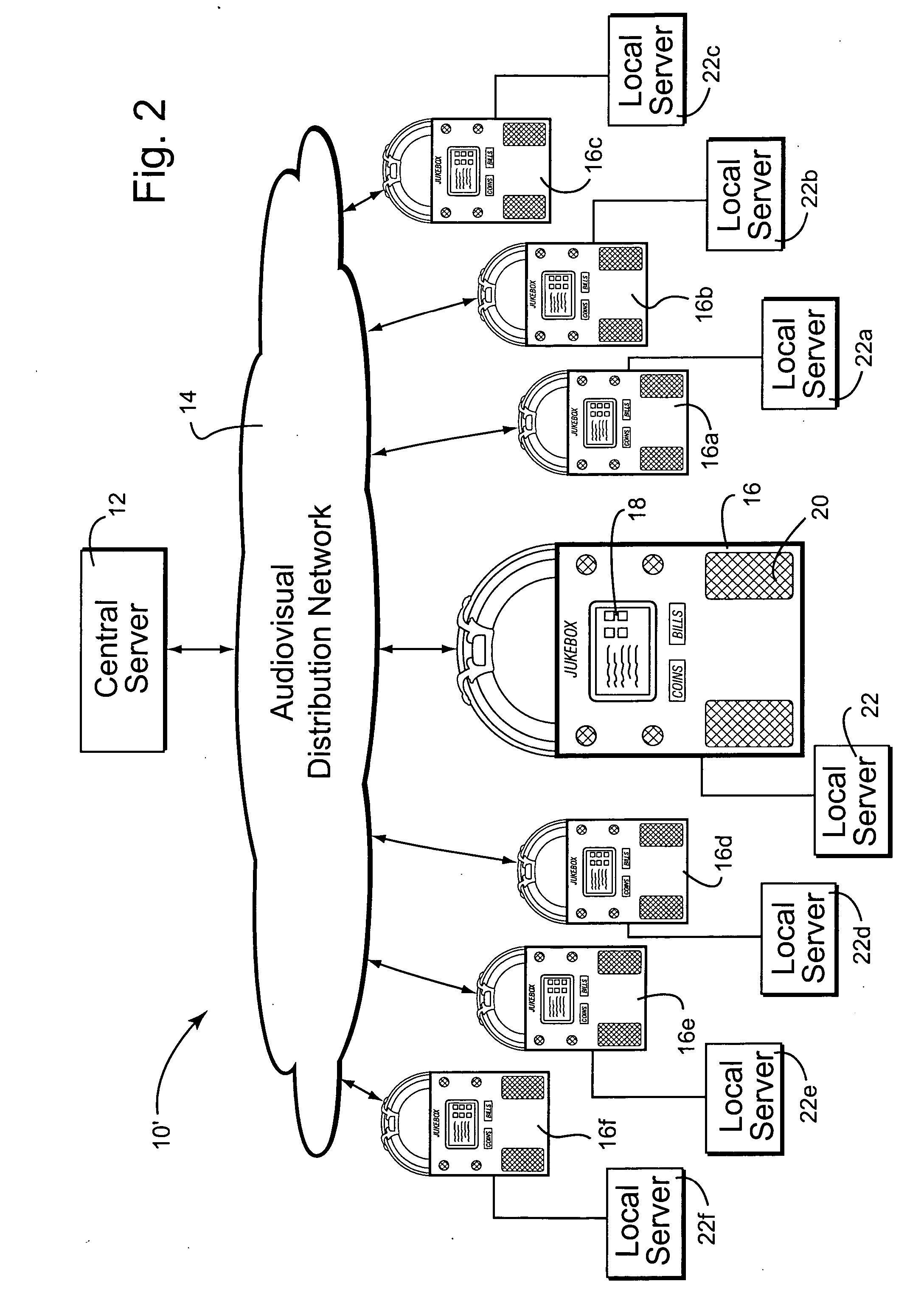
Digital downloading jukebox system with user-tailored music management, communications, and other tools
InactiveUS20060239131A1Accurate and reliable processCreating a sense of ownershipVoting apparatusRecord information storageThe InternetUser interface
A digital downloading jukebox system including a mechanism for delivering custom services to a recognized user, including services for creating playlists, communicating with others, accessing other features, etc. is provided. In some exemplary embodiments, after a user is recognized, the jukebox system allows users to access a special front-end via an Internet-enabled device or on an actual jukebox. Then, the user may, for example, create playlists, share songs with friends, send messages to friends, and access other value-added content. Such a system preferably learns about networks of friends, and enables managers to send similar messages to regular customers and / or others known to the system. In some exemplary embodiments, changes via a first user interface on a first device are reflected on second user interface on other properly-configured devices.
Owner:TOUCHTUNES MUSIC CORP
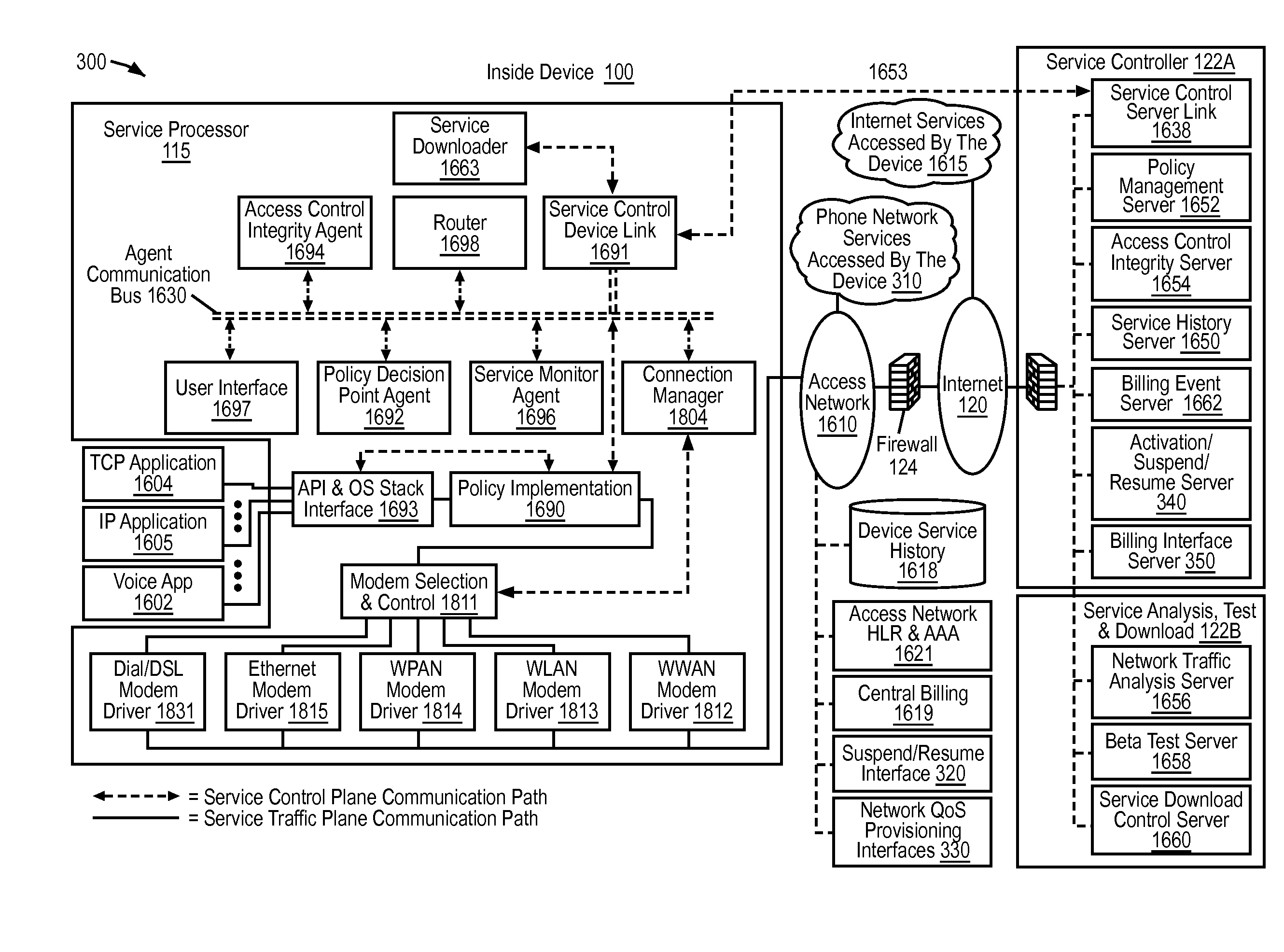
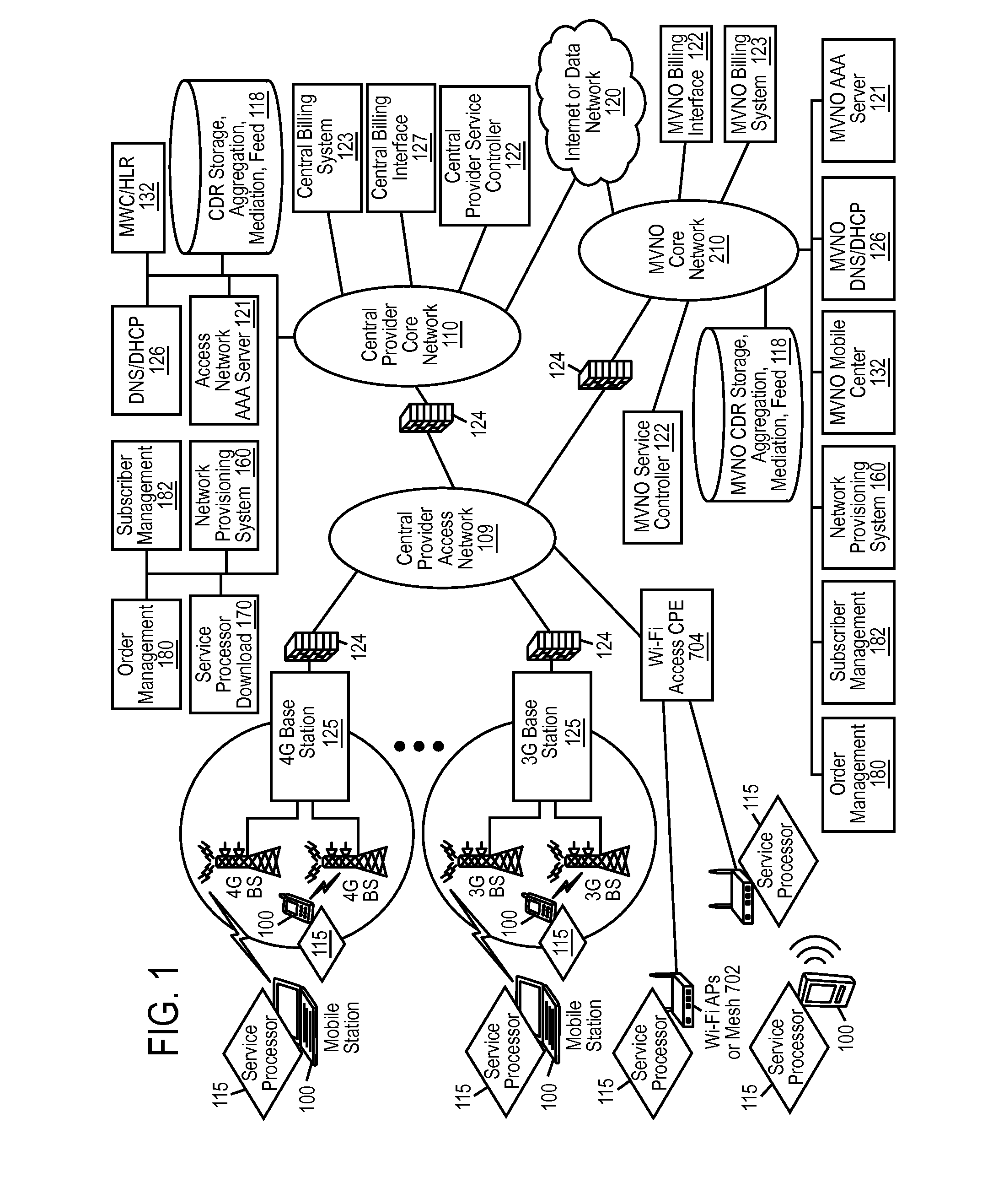
End user device that secures an association of application to service policy with an application certificate check
ActiveUS20120221955A1Input/output for user-computer interactionAccounting/billing servicesTraffic capacityApplication software
Network service provisioning is described. Network service provisioning to a device includes a mechanism for ensuring that network services are available based upon one or more of appropriate traffic control, billing, and notification policies. Ensuring that the policies are properly enforced on a device is a focus of this paper. The enforcement policies can be on the device or in the network.
Owner:HEADWATER RES LLC
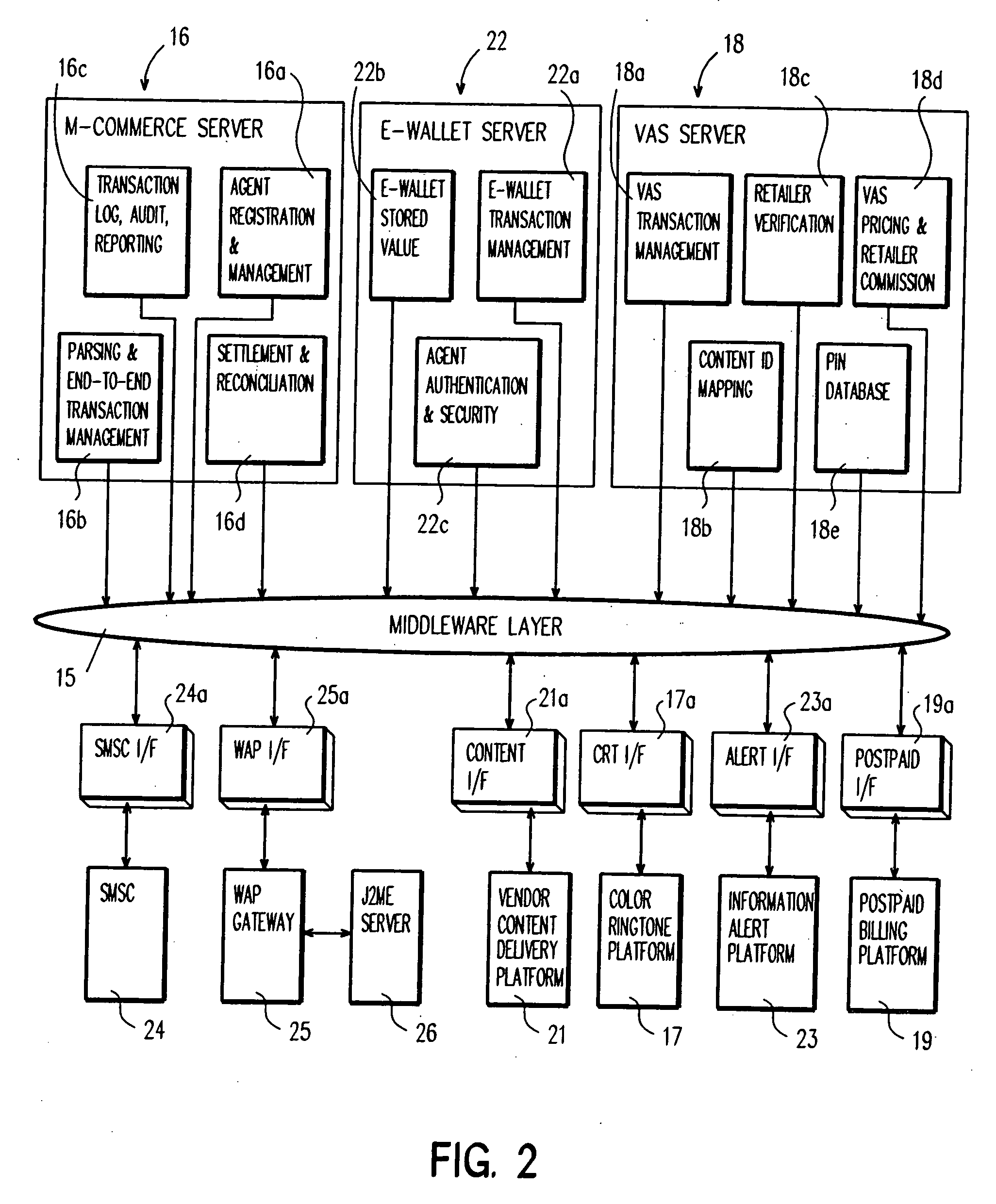
Media delivery platform
InactiveUS20030033214A1Prevent intellectual propertyAccurate methodModulated-carrier systemsPayment architectureCorrection algorithmMediaFLO
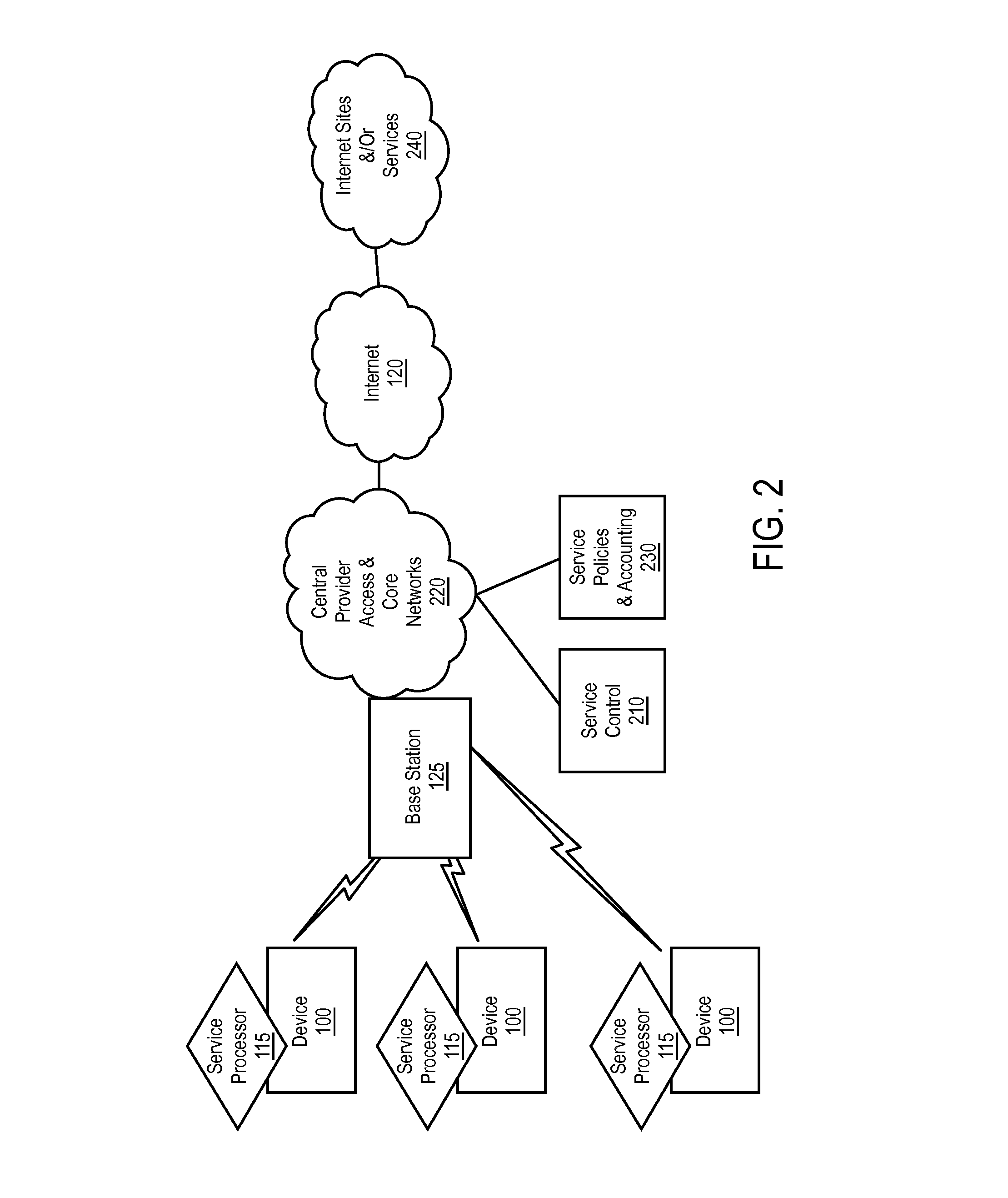
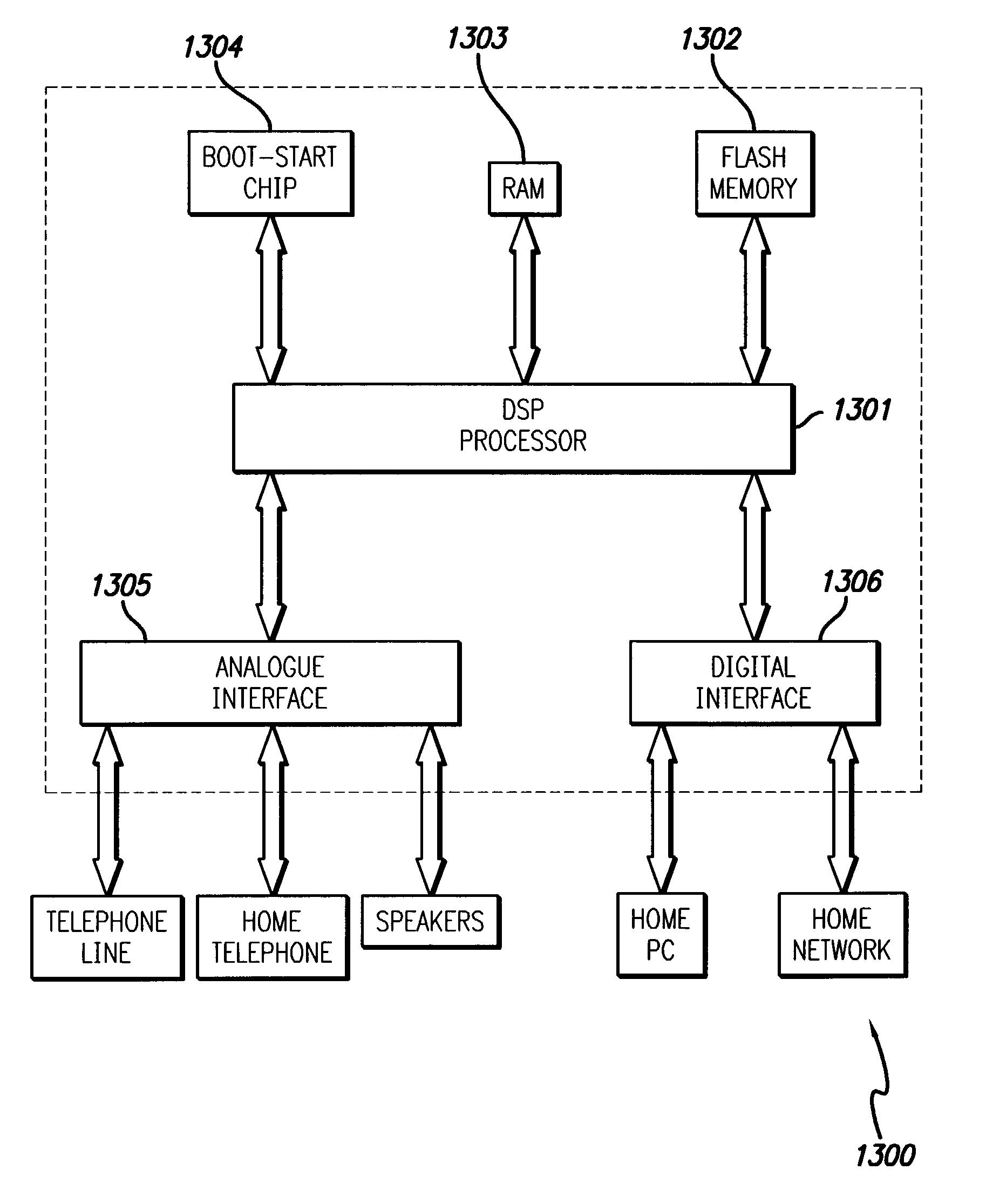
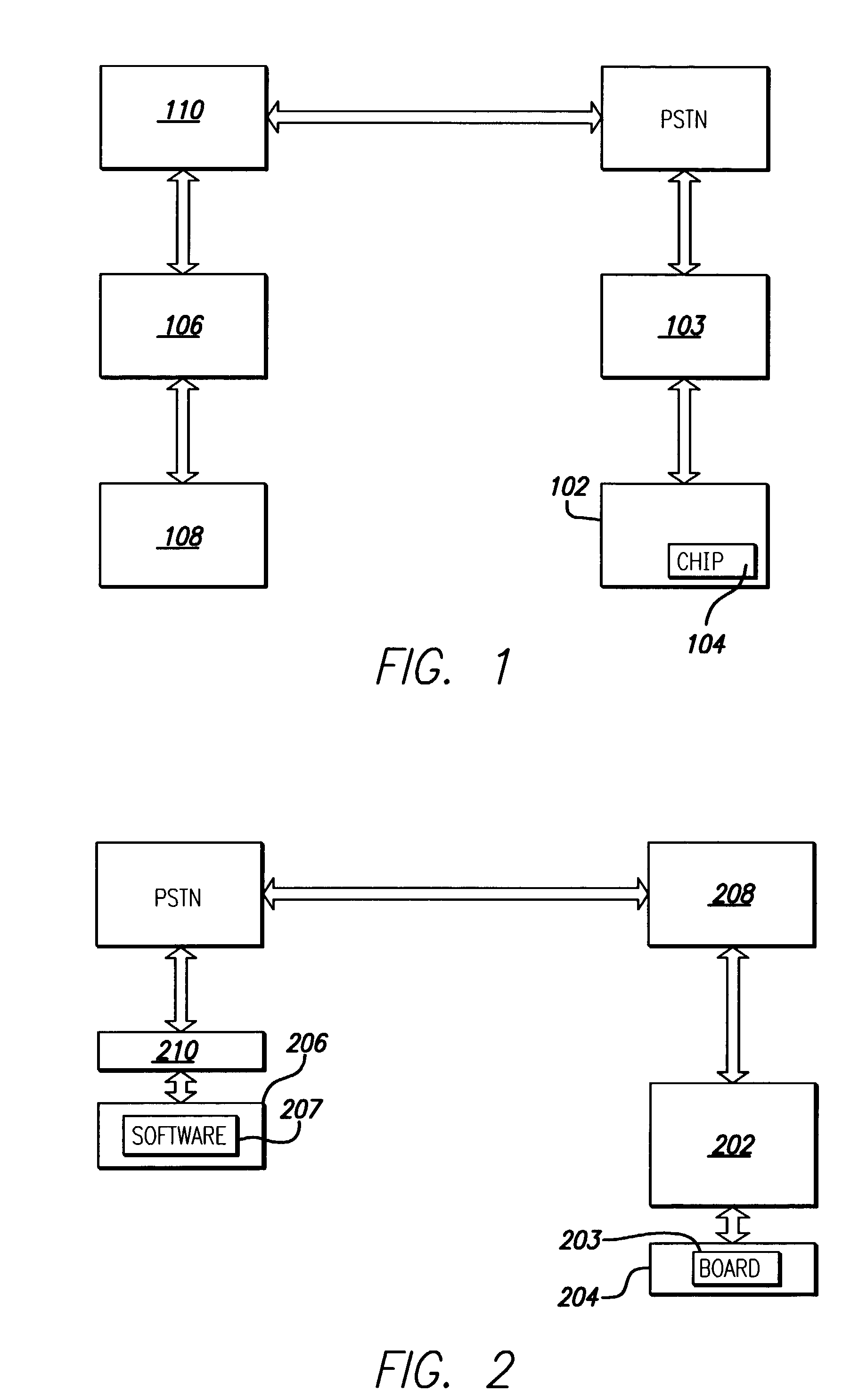
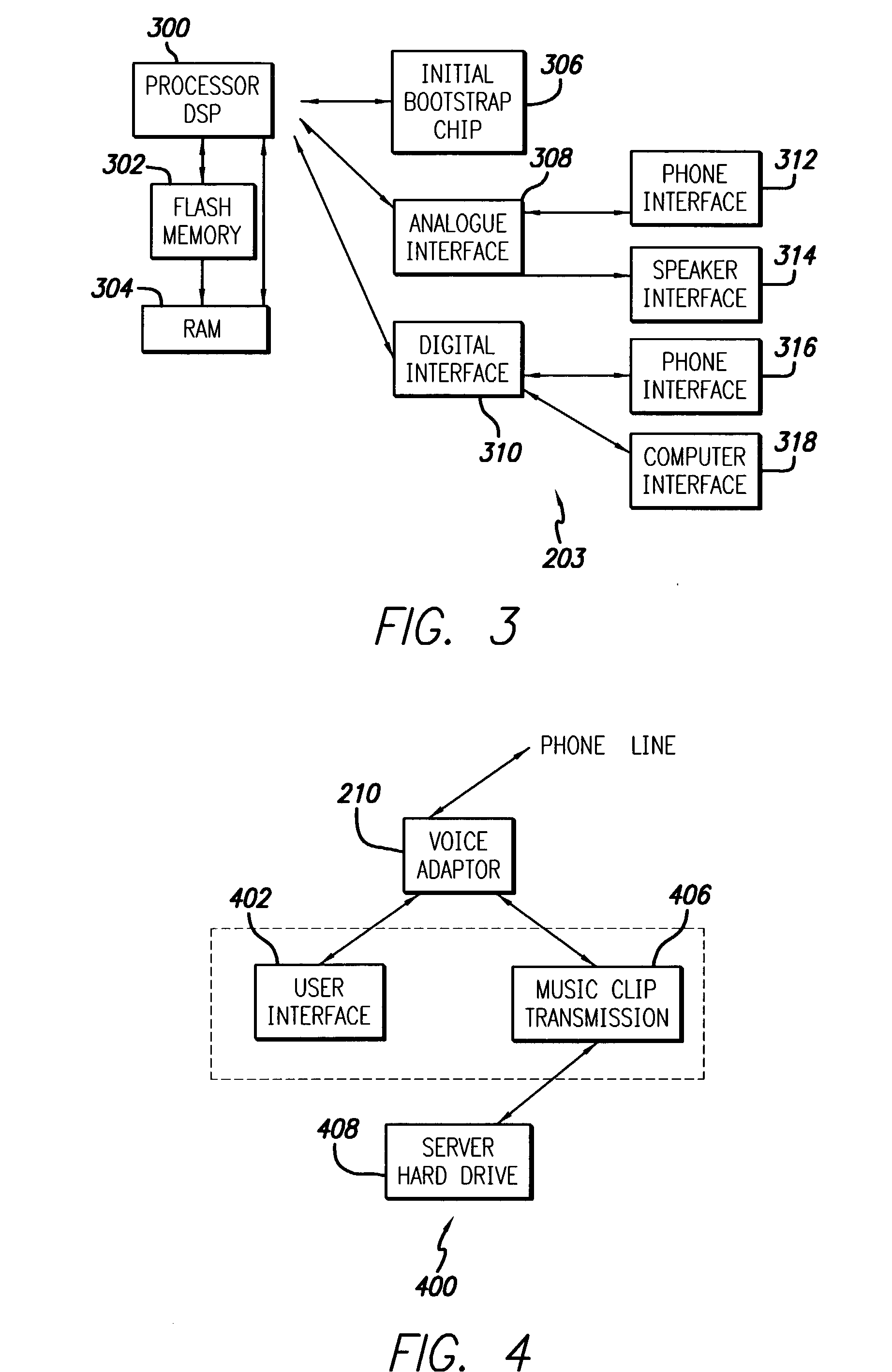
An improved method for delivery and play back of sound and image files is provided. This new method includes the use of sound and / or image clips, which can be snippets or full files, as alerts for a variety of electronic devices or for playing on a handheld device, and for use as a promotion to sell items associated with the files. A collection or library of uniquely selected and / or edited clips may also be provided to the consumer in a manner far more conveniently on conventional telephone equipment than previously available. Algorithms are provided for the delivery, storage and playback of the sound files, including a delivery method algorithm (500), a parametric optimization and compression algorithm (1500), and an error correction algorithm. In contrast to the conventional ring tones or musical chimes used to ring cellular phones currently on the market, the current invention provides a method for ringing cellular phones and landline telephones with real sound recordings including real music, which may be songs lifted from copyright registered CD tracks, and may comprise human voice, various instrument sounds, and other sound effects of a high quality. A software based system for encoding the hardware of existing cellular phones at the time of manufacturing with delivery, storage, and playback capabilities in accordance with the present invention is provided, such that additional hardware is not required.
Owner:SKKY
Systems and methods for mobile application security classification and enforcement
ActiveUS20110167474A1Avoid forwardingMemory loss protectionError detection/correctionUser deviceThe Internet
The present disclosure provides systems and methods for mobile application security classification and enforcement. In particular, the present invention includes a method, a mobile device, and a distributed security system (e.g., a “cloud”) that is utilized to enforce security on mobile devices communicatively coupled to external networks (i.e., the Internet). Advantageously, the present invention is platform independent allowing it to operate with any current or emerging mobile device. Specifically, preventing malicious applications from running on an end user's mobile device is challenging with potentially millions of applications and billions of user devices; the only effective way to enforce application security is through the network that applications use to communicate.
Owner:ZSCALER INC
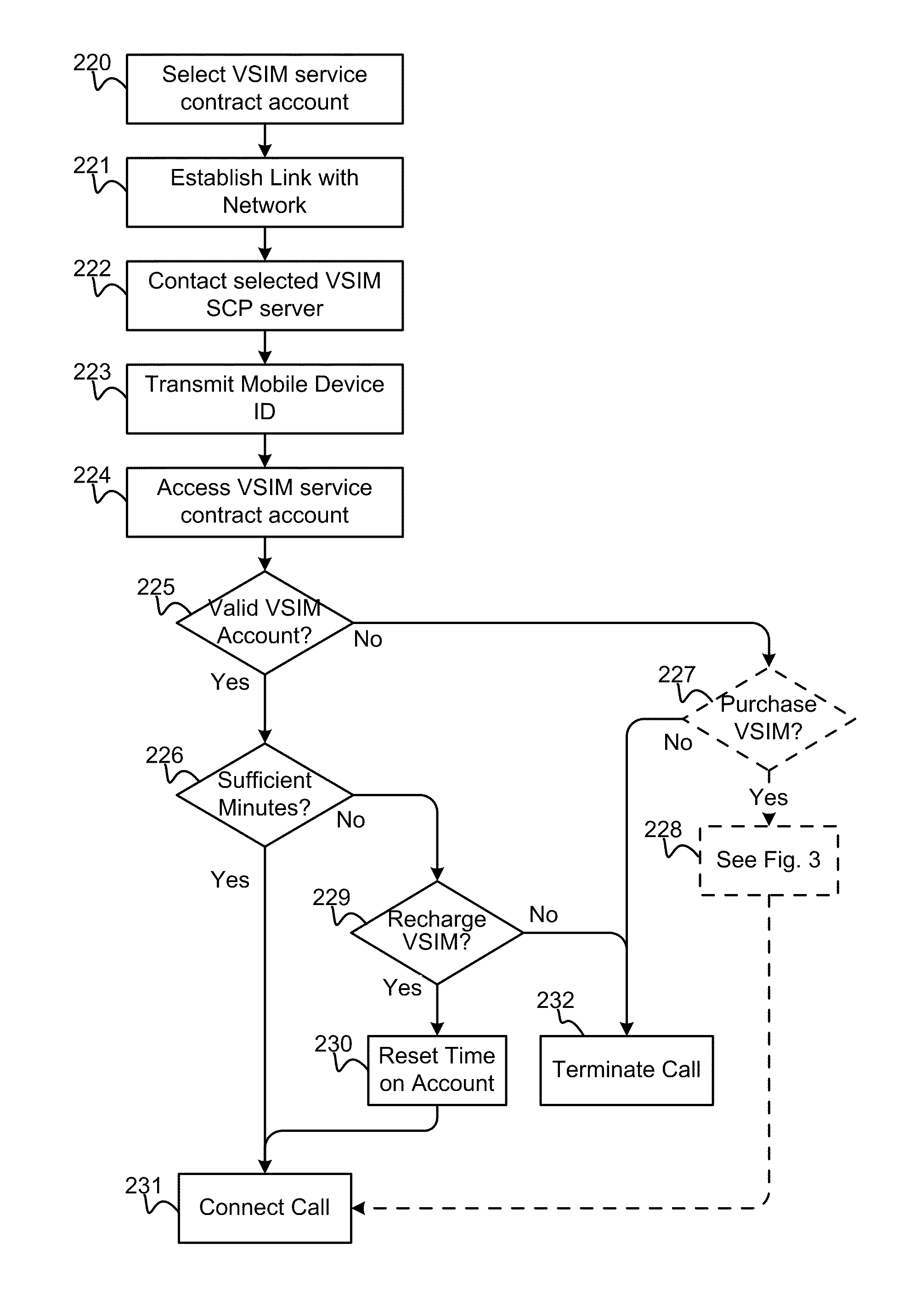
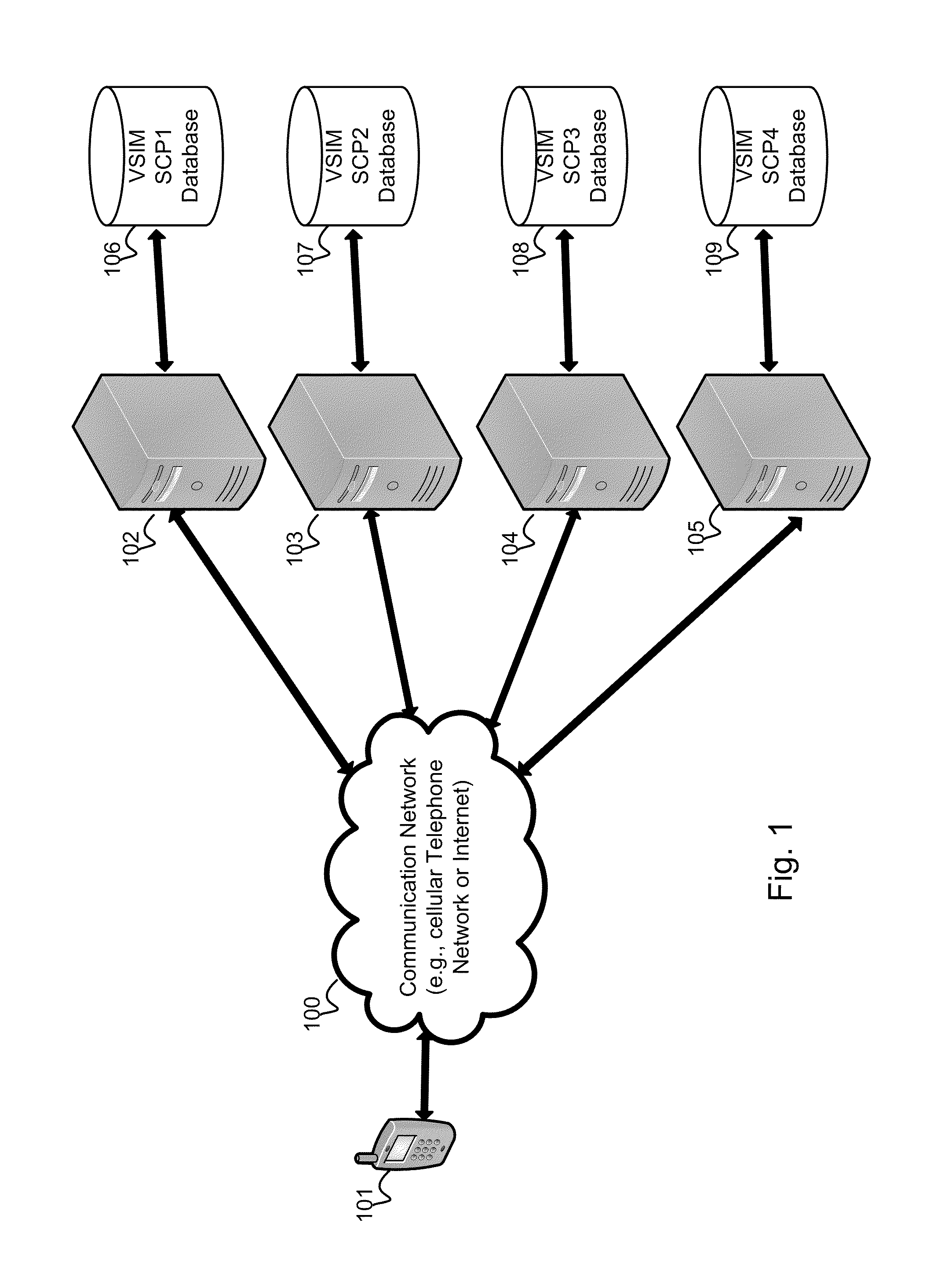
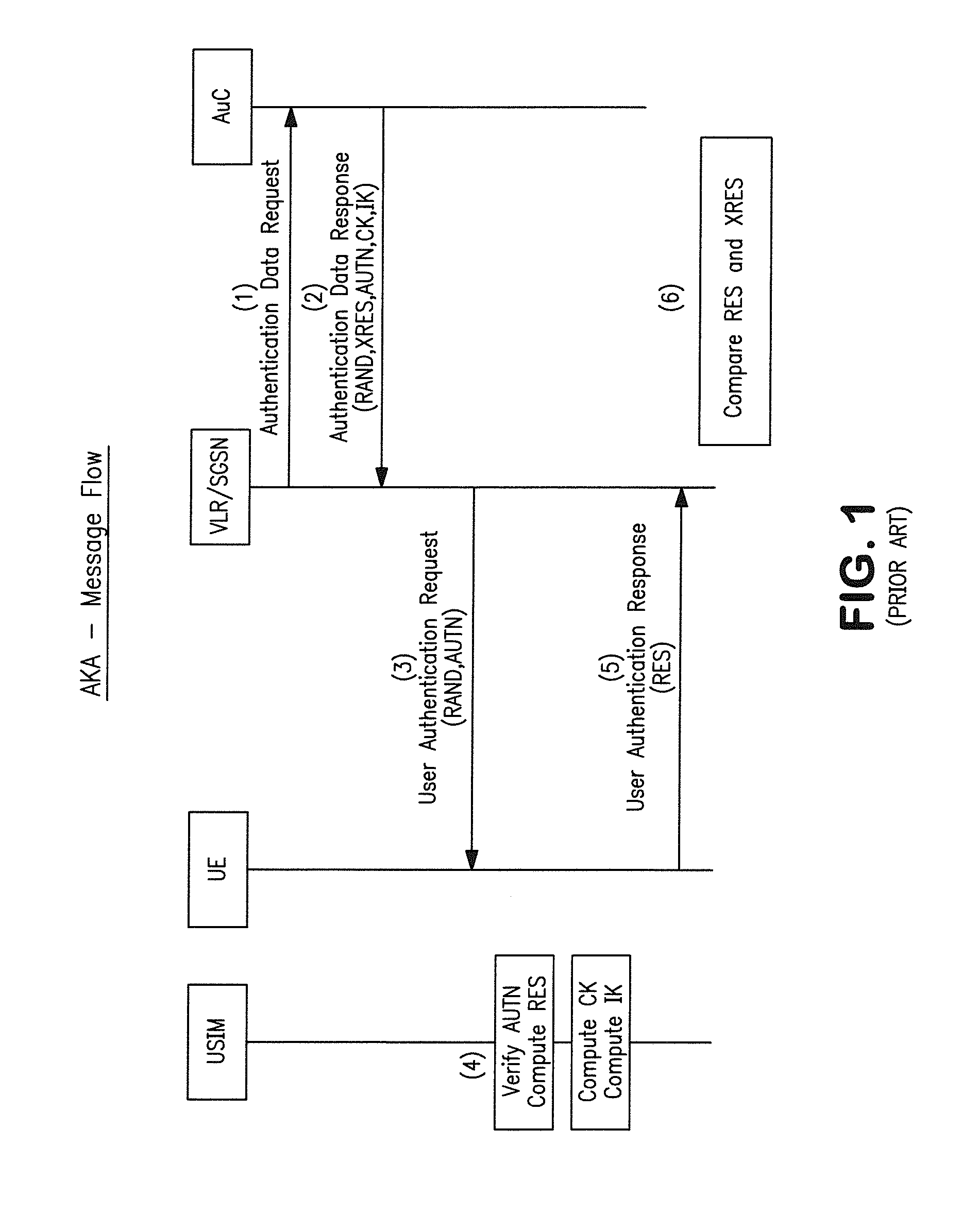
Method and apparatus for performing soft switch of virtual sim service contracts
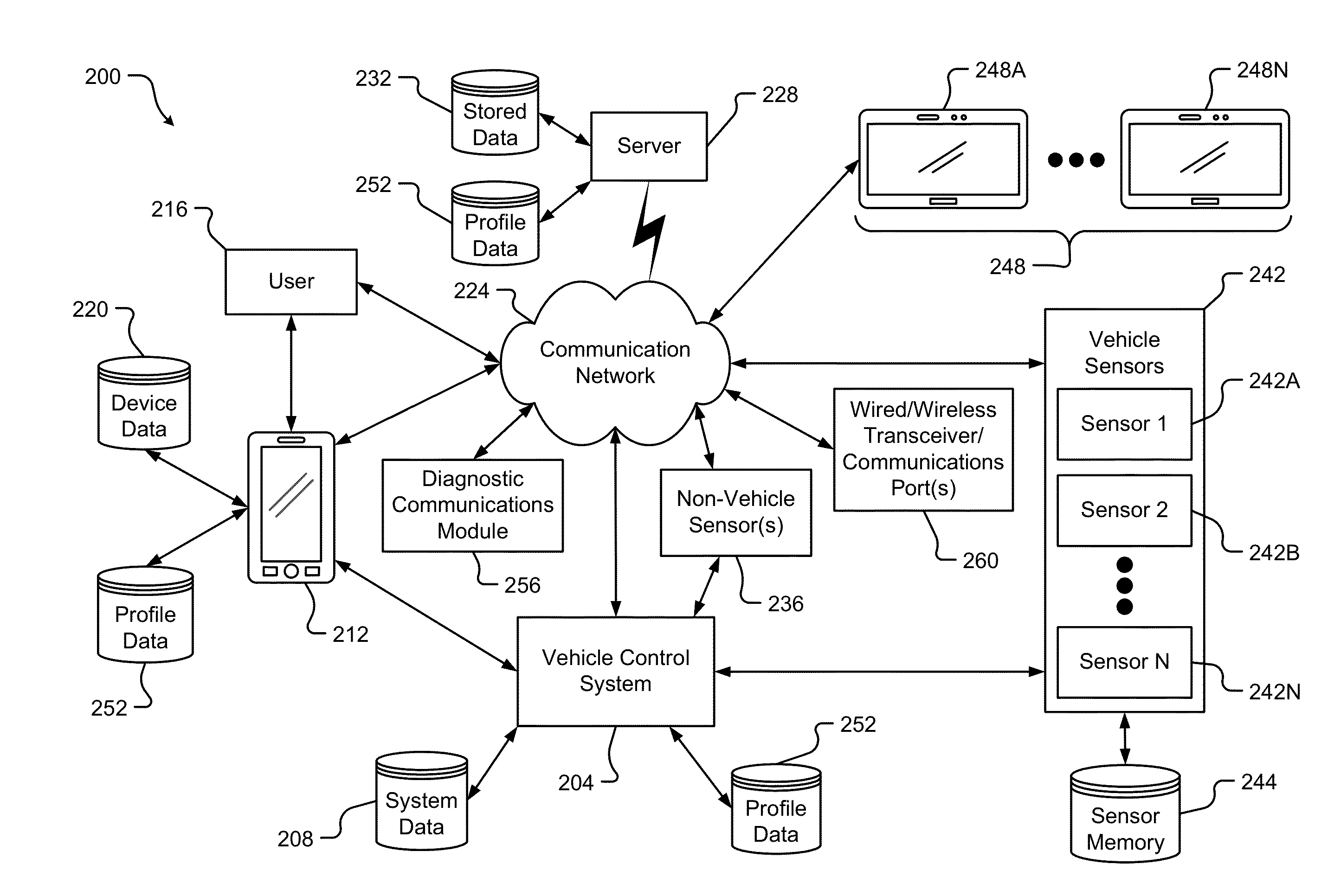
InactiveUS20100311402A1Save battery powerEffective supportService provisioningAssess restrictionInternal memoryService provision
A system and method for providing updated rules governing the switching of enabled provisioning data supporting a wireless service contract. A mobile device may be initially programmed with a profile data table and priority list index data table to automatically enable provisioning data supporting one of the plurality of service providers stored in a VSIM internal memory unit to conduct a wireless communication when certain operational parameter values are satisfied. The profile data table and priority list index data table may be automatically updated in response to a variety of triggers. The profile data table and priority list index data table may be stored remotely. Operational parameters regarding each call request are collected and transmitted to a remote service contract selection server. The selection of an optimal service provider account may be made remotely in the service contract selection server and transmitted back to the mobile device.
Owner:QUALCOMM INC
Systems and methods for mobile application security classification and enforcement
The present disclosure provides systems and methods for mobile application security classification and enforcement. In particular, the present invention includes a method, a mobile device, and a distributed security system (e.g., a “cloud”) that is utilized to enforce security on mobile devices communicatively coupled to external networks (i.e., the Internet). Advantageously, the present invention is platform independent allowing it to operate with any current or emerging mobile device. Specifically, preventing malicious applications from running on an end user's mobile device is challenging with potentially millions of applications and billions of user devices; the only effective way to enforce application security is through the network that applications use to communicate.
Owner:ZSCALER INC
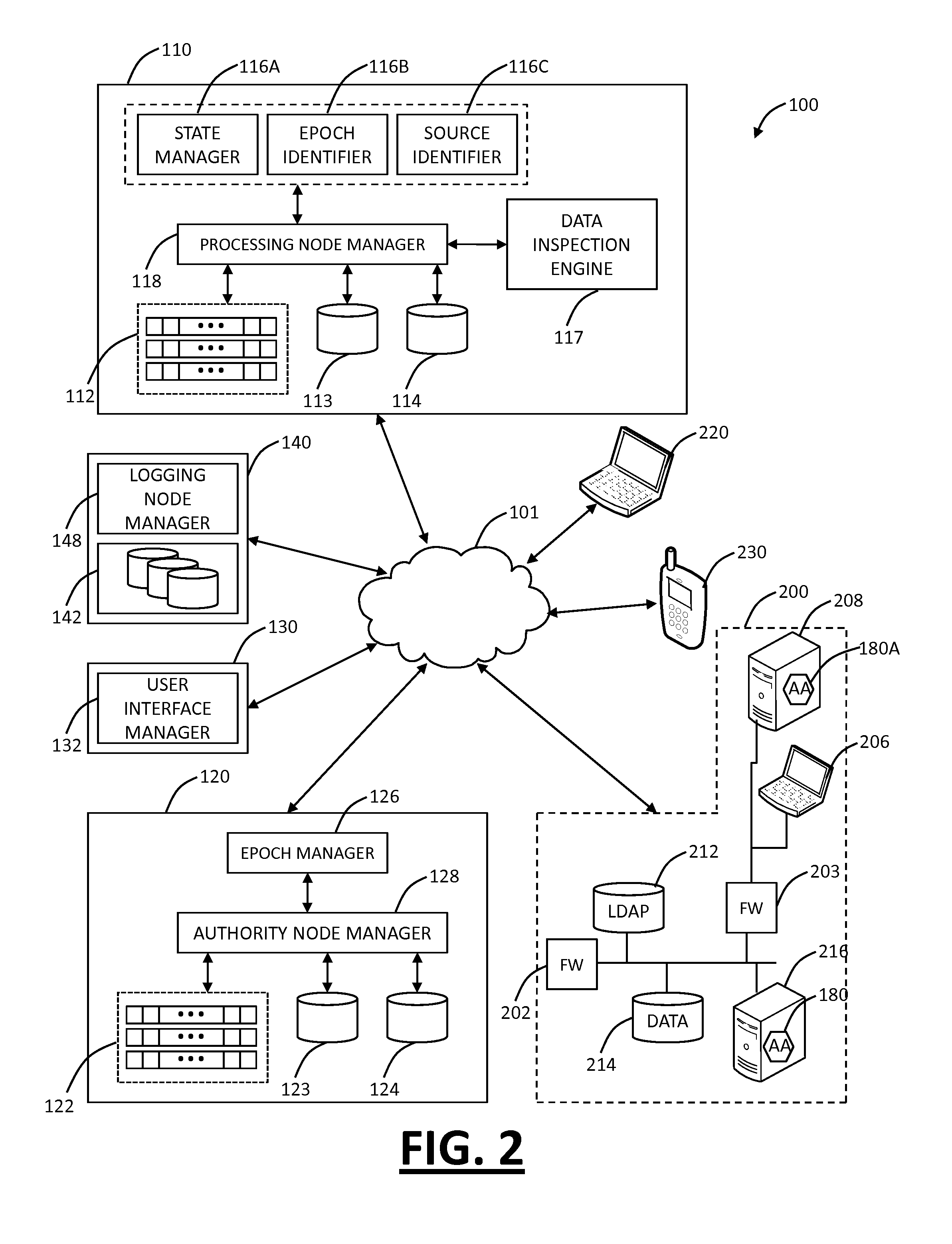
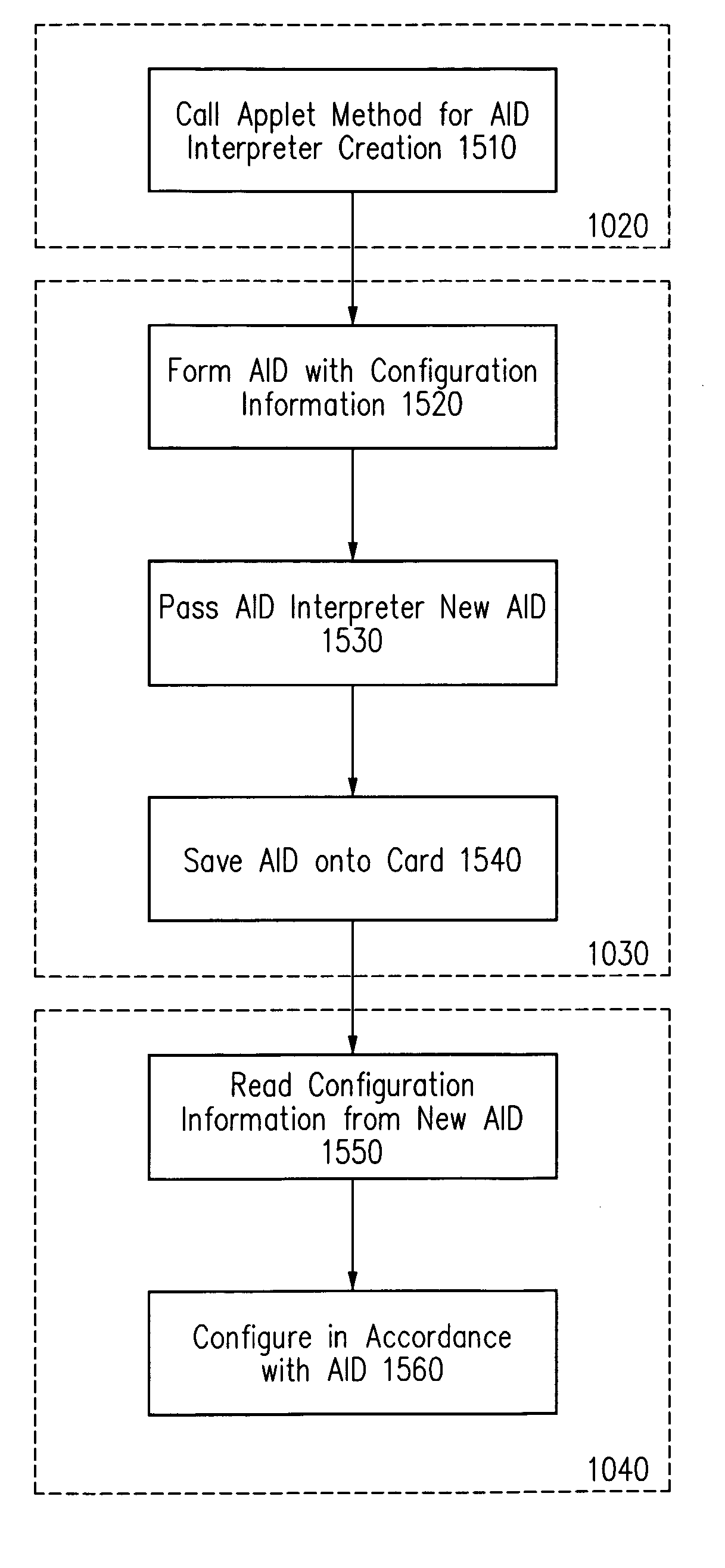
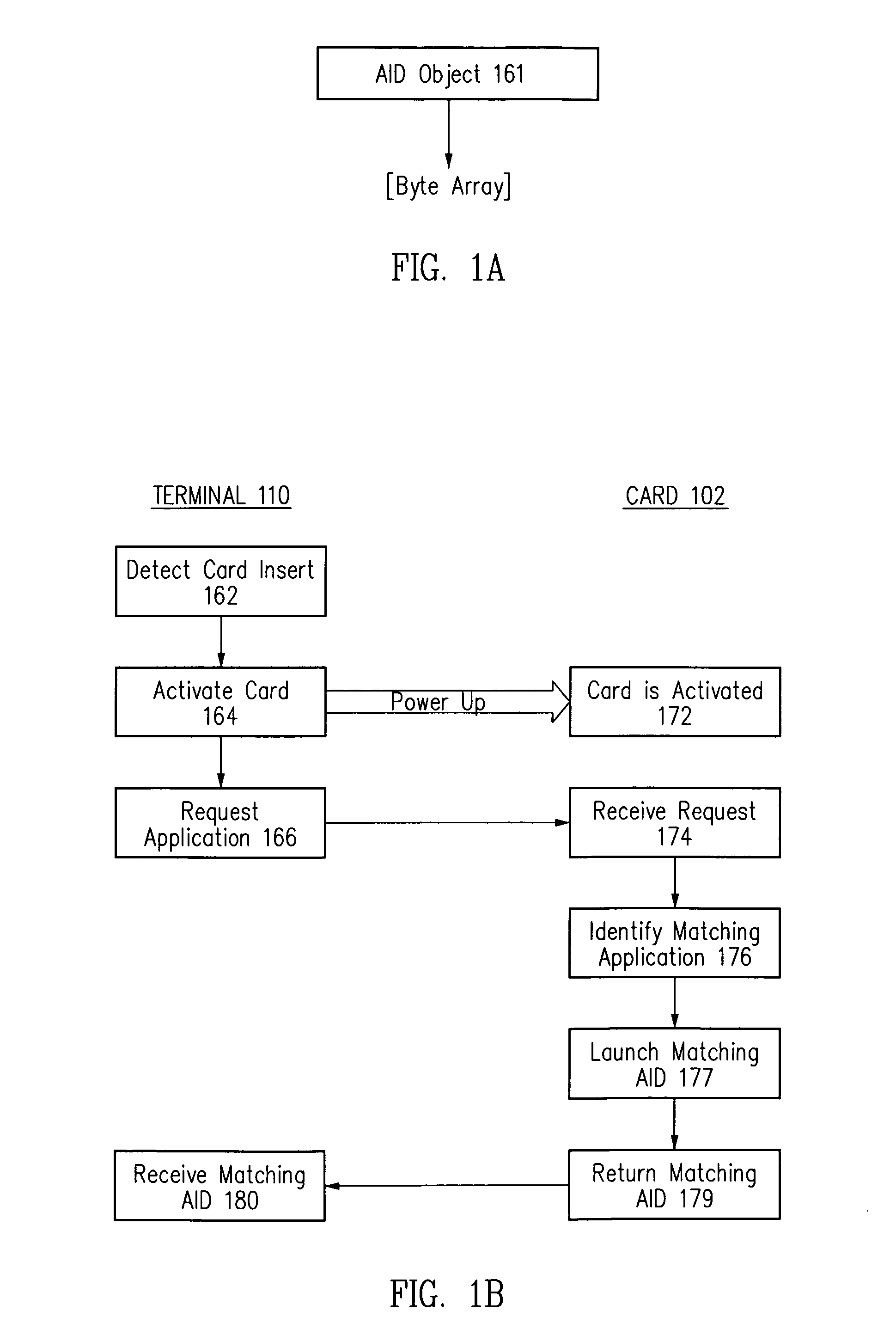
Method and apparatus for installing an application onto a smart card
Owner:ORACLE INT CORP
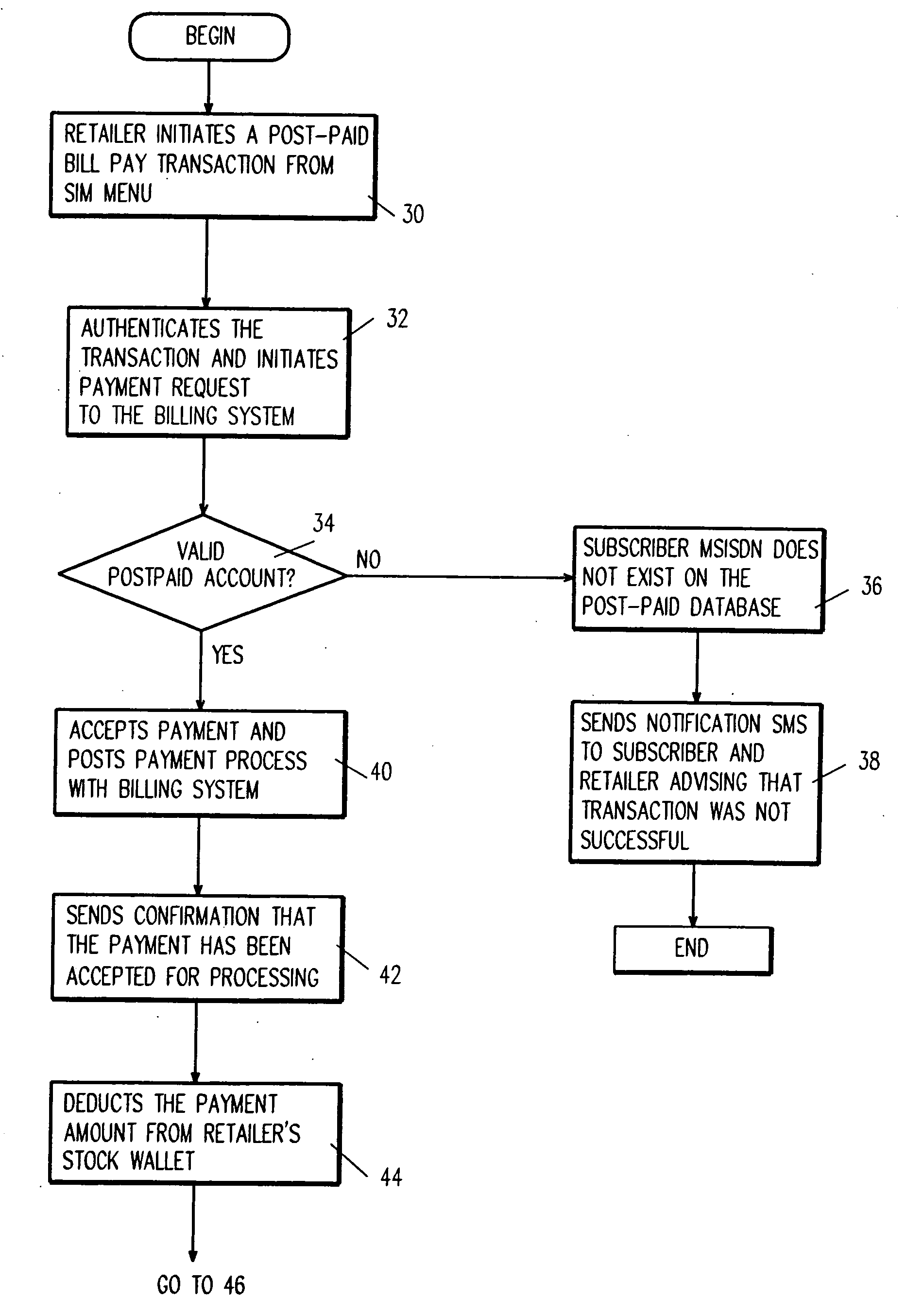
Mobile phone as a point of sale (POS) device
InactiveUS20070106564A1Easy accessAcutation objectsAccounting/billing servicesMobile deviceComputer science
A system and method for provisioning one or more value added services to a postpaid / prepaid mobile account and / or a postpaid / prepaid mobile device using a wireless communication device as a point-of-sale device, is disclosed.
Owner:SHANGHAI RES INST OF PETROCHEMICAL TECH SINOPEC +1
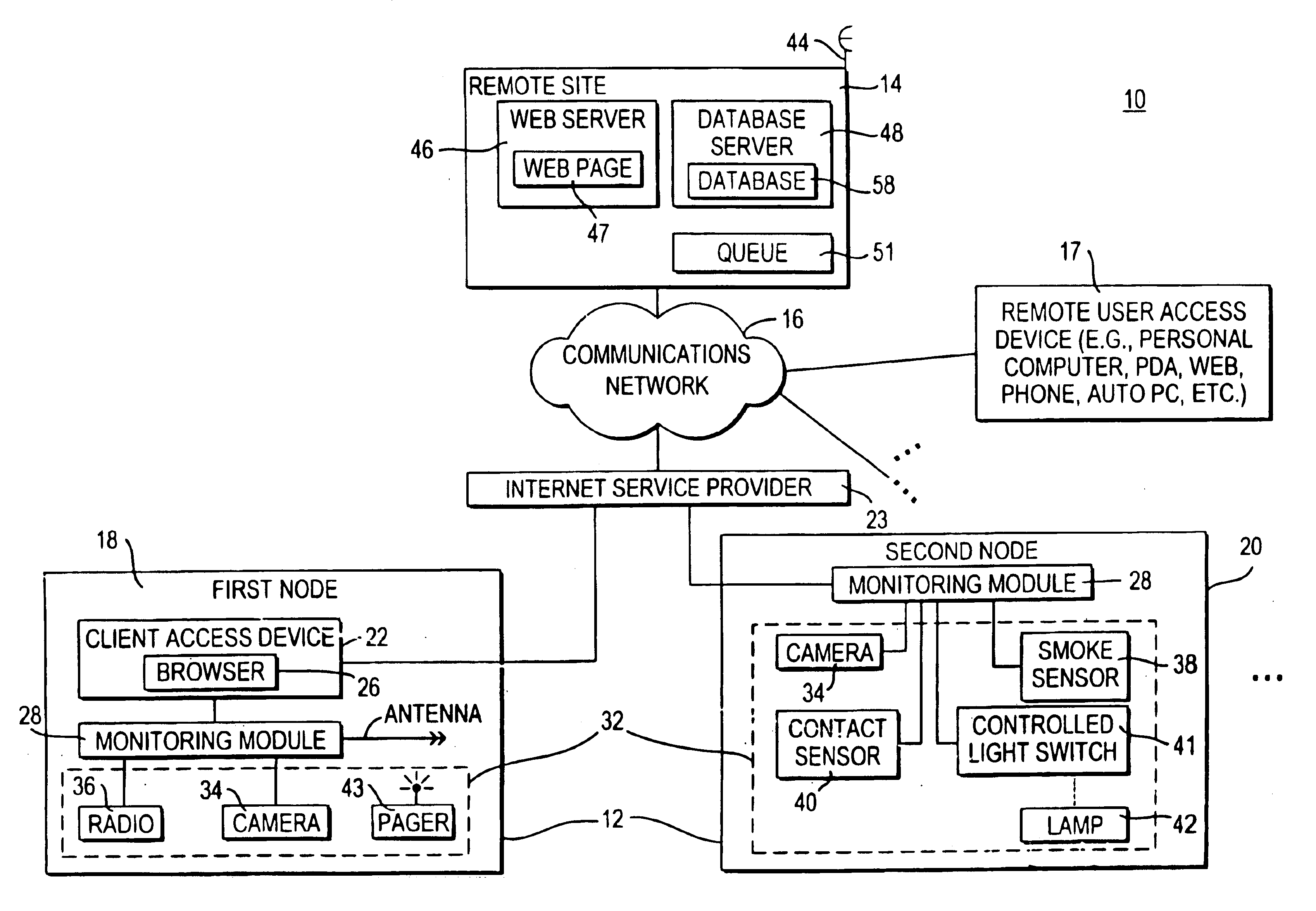
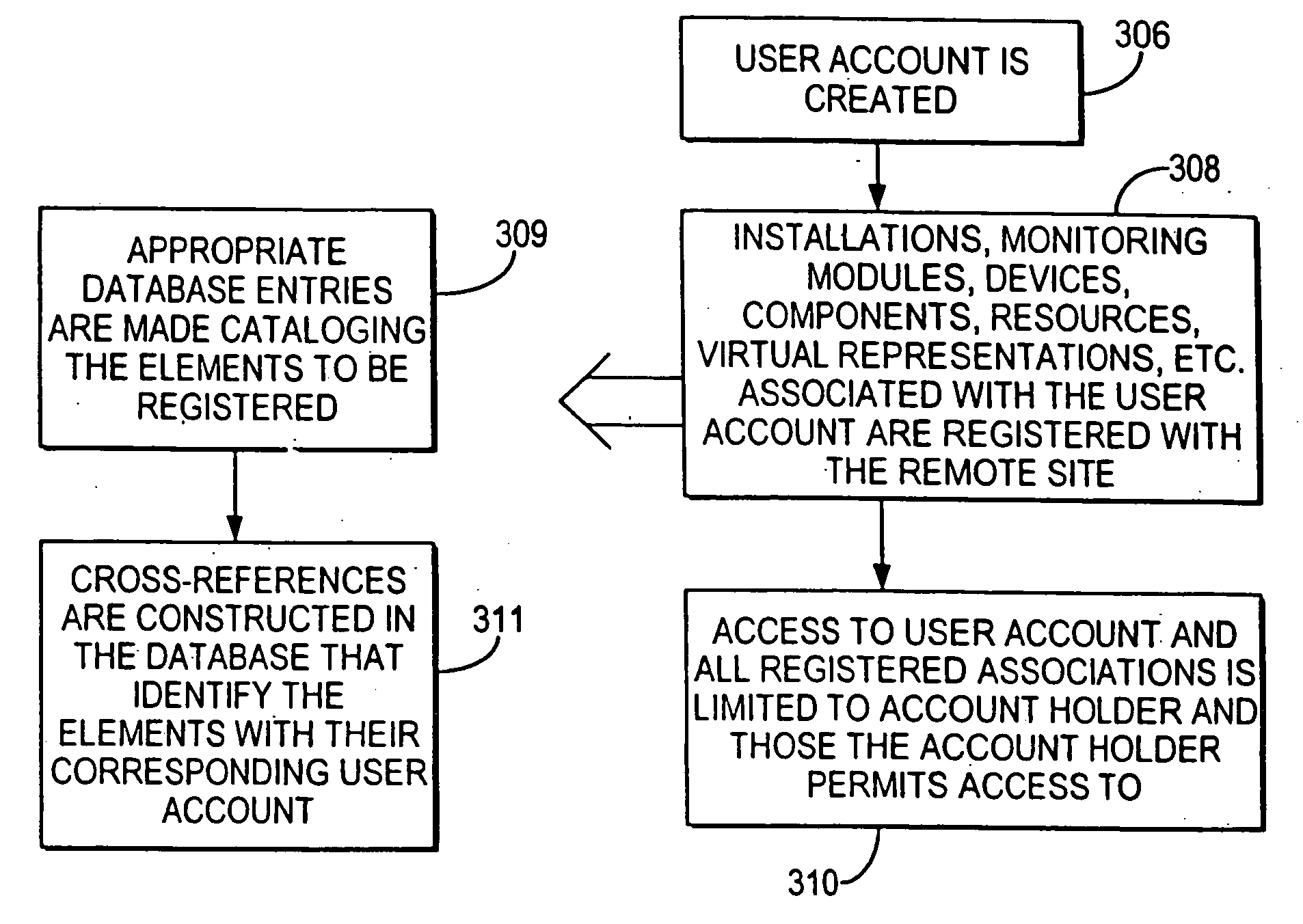
Systems and methods for the automatic registration of devices
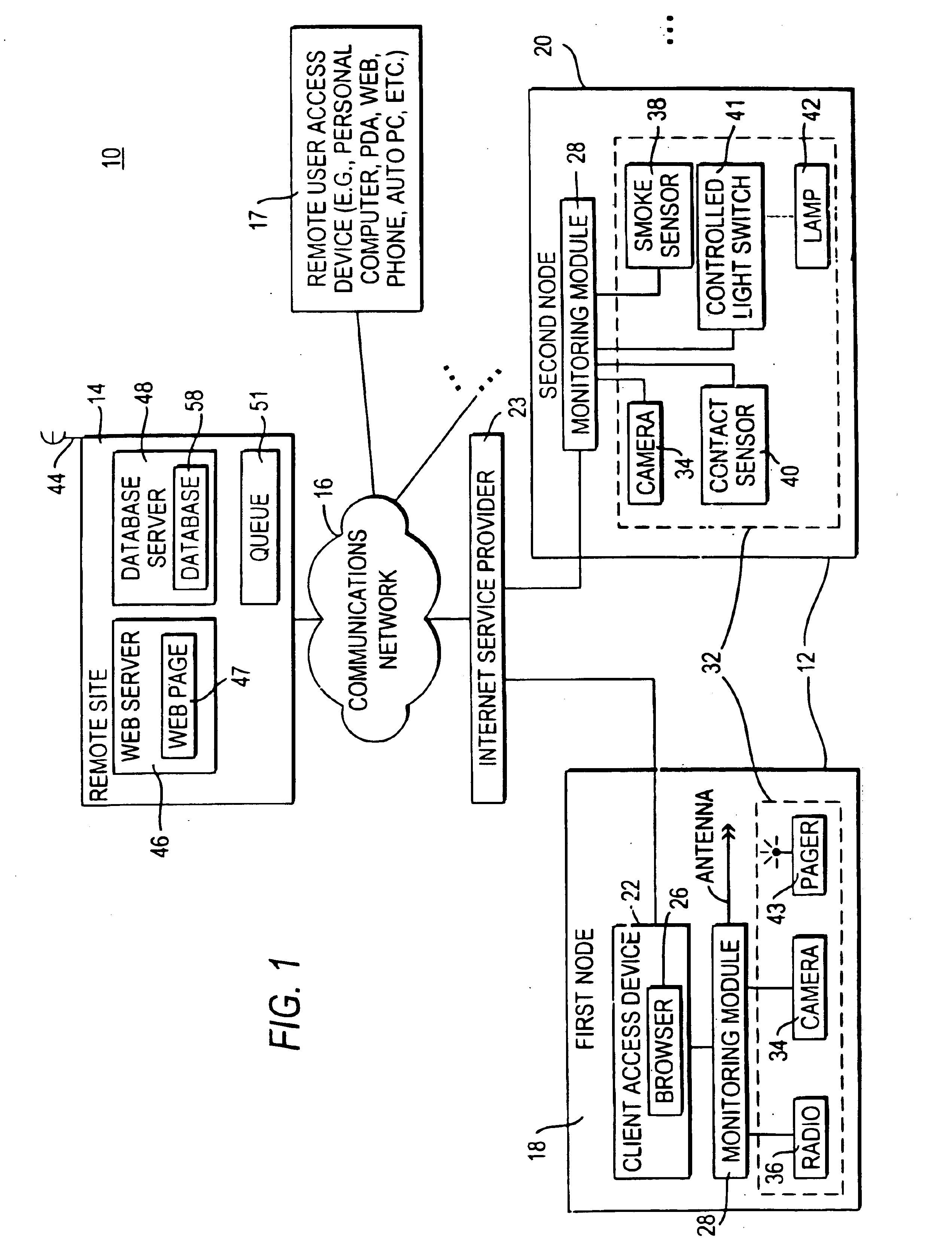
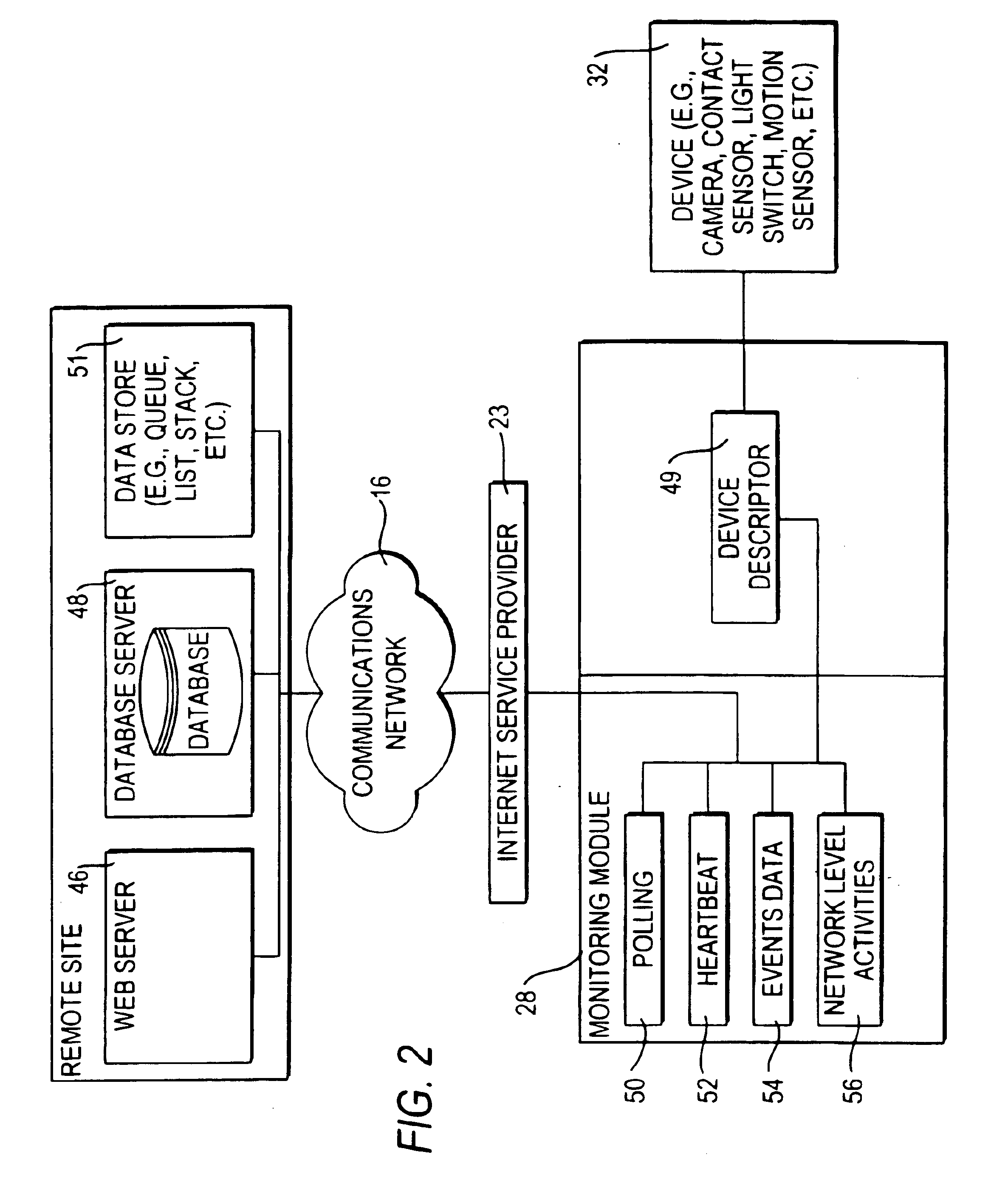
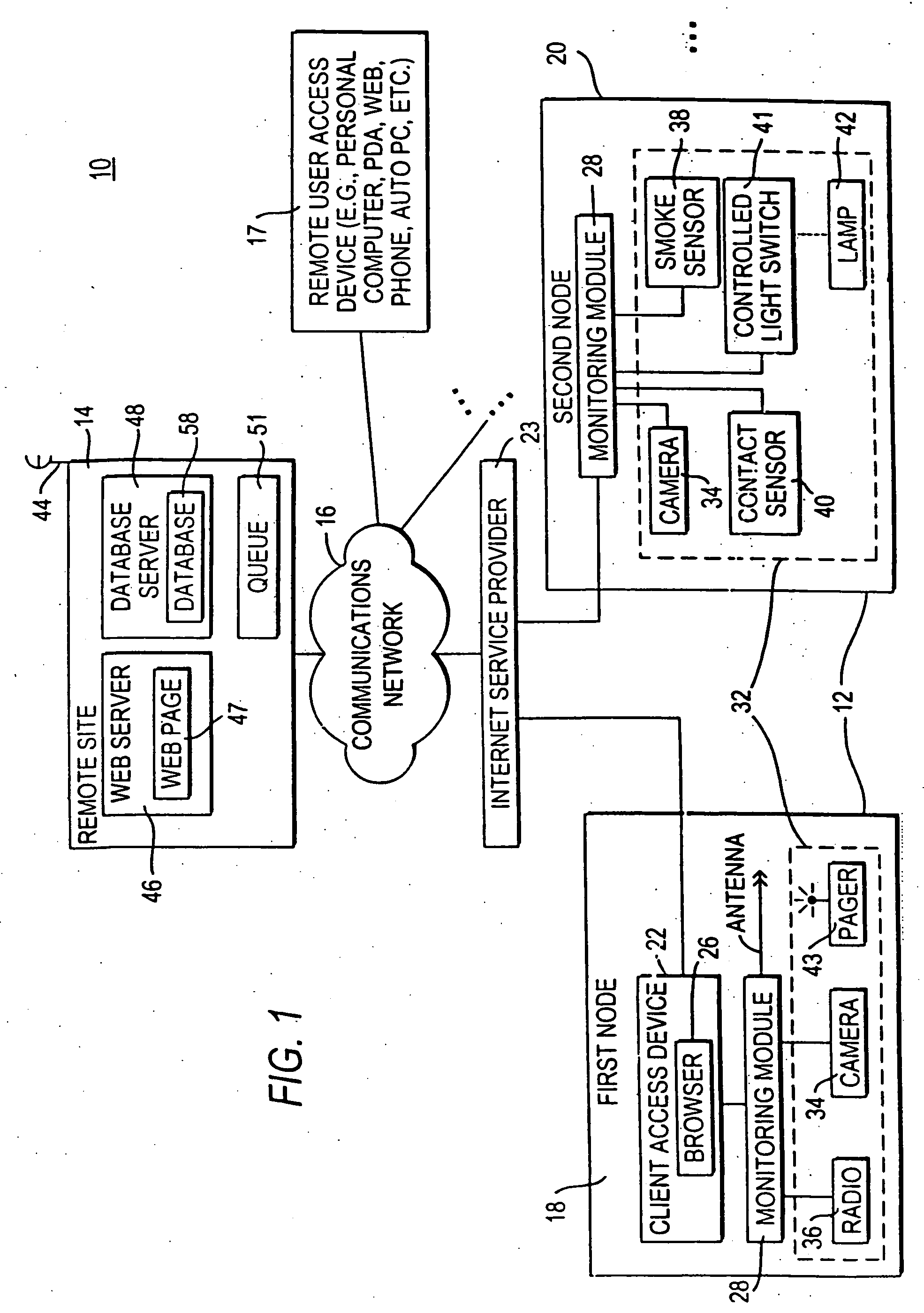
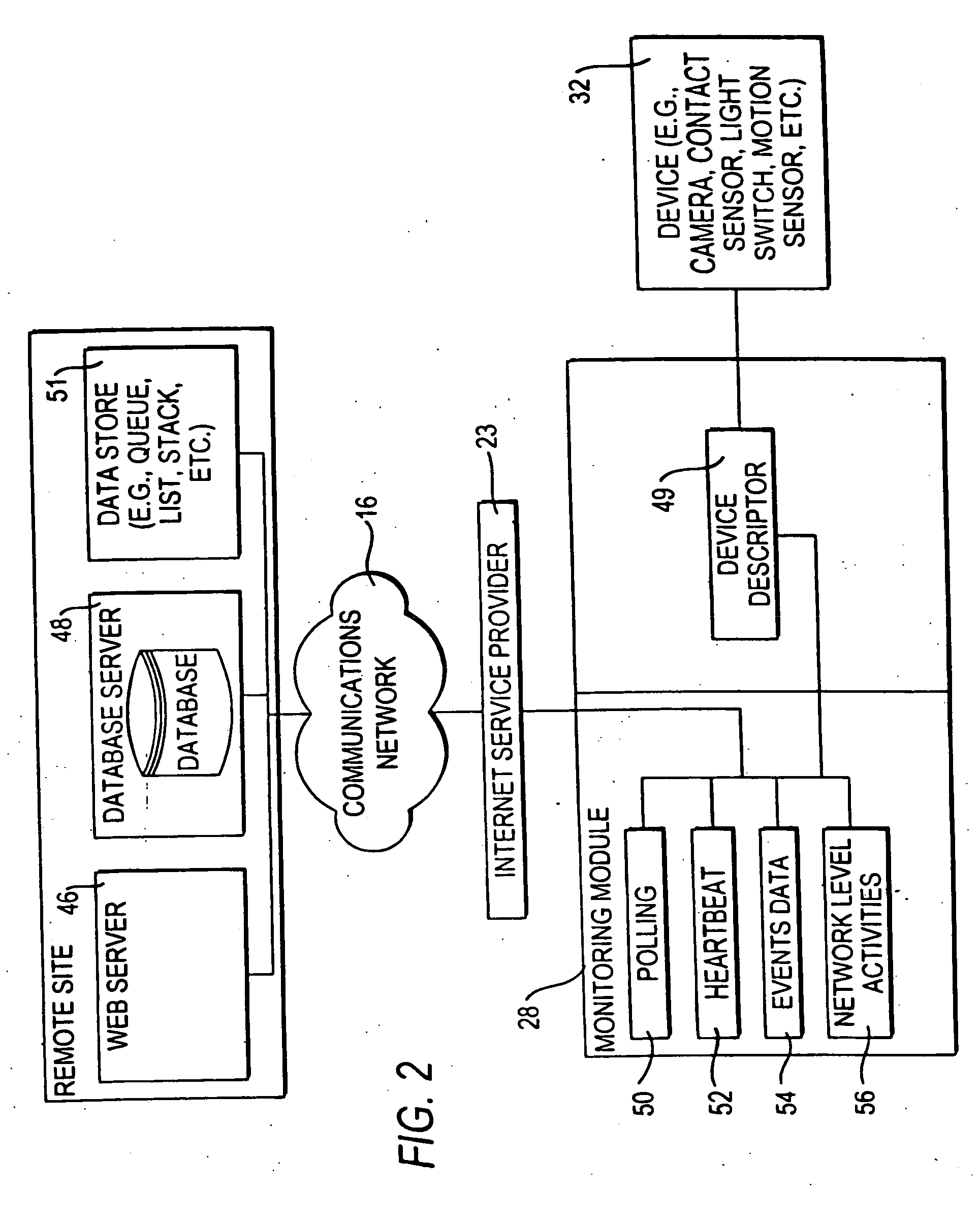
InactiveUS6943681B2Not automaticallyBroadband local area networksElectric testing/monitoringDatabase serverData library
Systems and methods for providing registration at a remote site that may include, for example, a monitoring module that may communicate with a remote site. A registration protocol may be used by the monitoring module and the remote site in generating the messages communicated during the registration process. The monitoring module may gather and generate various identification information to be included in the registration protocol messages. The registration information provided by the monitoring module may be stored at the remote site in a database server having a database. A confirmation message may be communicated from the remote site to the monitoring module that may either acknowledge successful registration or report that an error occurred during the registration process.
Owner:GOOGLE LLC
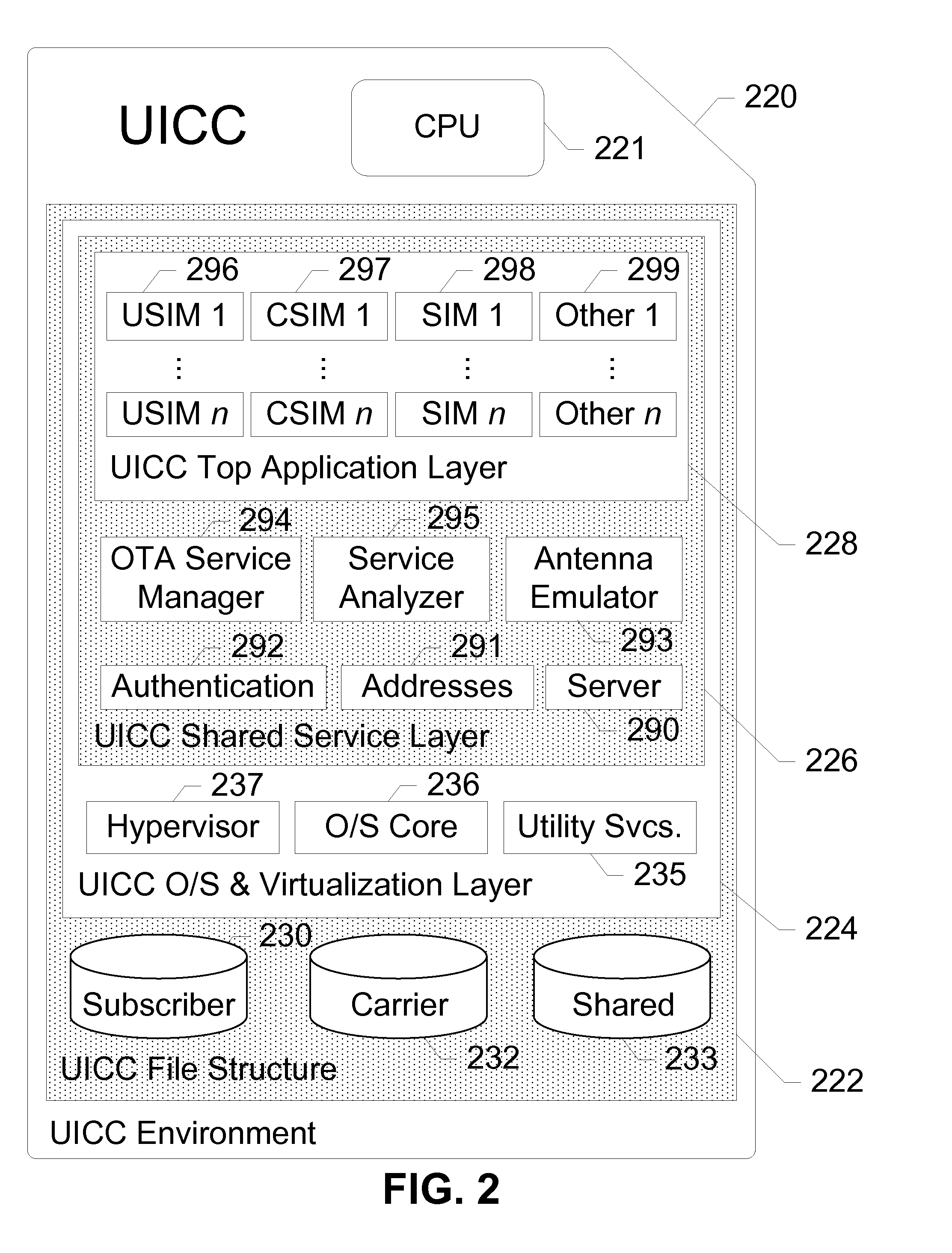
UICC Carrier Switching Via Over-The-Air Technology
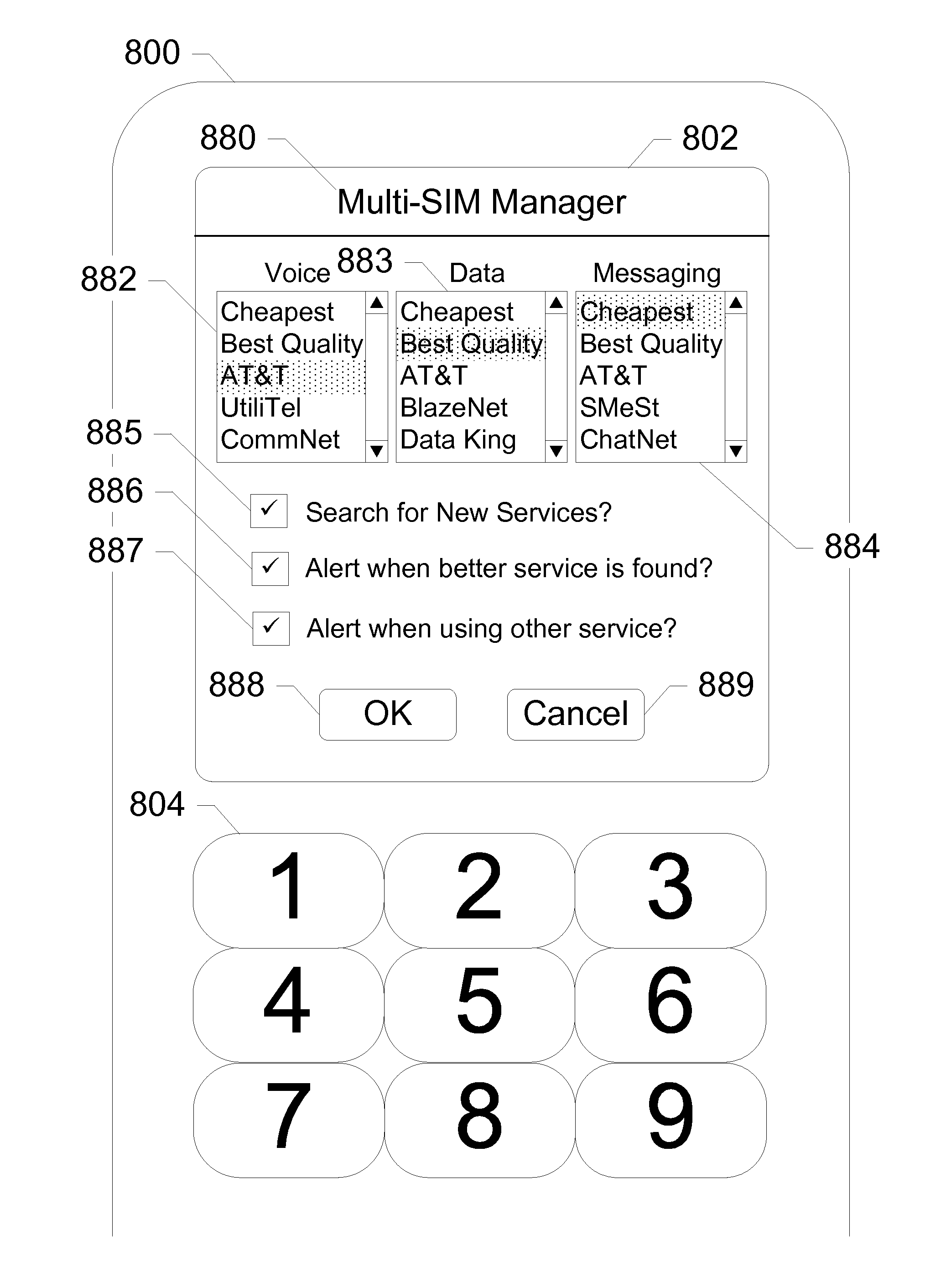
ActiveUS20130023235A1Eliminate needService provisioningUnauthorised/fraudulent call preventionVirtual userCarrier signal
Devices, systems, and methods are disclosed which relate to provisioning a universal integrated circuit card (UICC) with multiple services. The UICC enables a wireless communication device to communicate through multiple carriers by using a unique virtual subscriber identity module (SIM) to register with each carrier. The unique virtual SIM is one of a plurality of virtual SIMs stored on and managed by the UICC. A carrier network includes a server for provisioning a new virtual SIM on a UICC over-the-air (OTA) when a new customer requests a service such as voice, data, or other type of service. These UICCs may also include logic to automatically select the best carrier for a voice call depending on the user settings.
Owner:AT&T INTPROP I L P
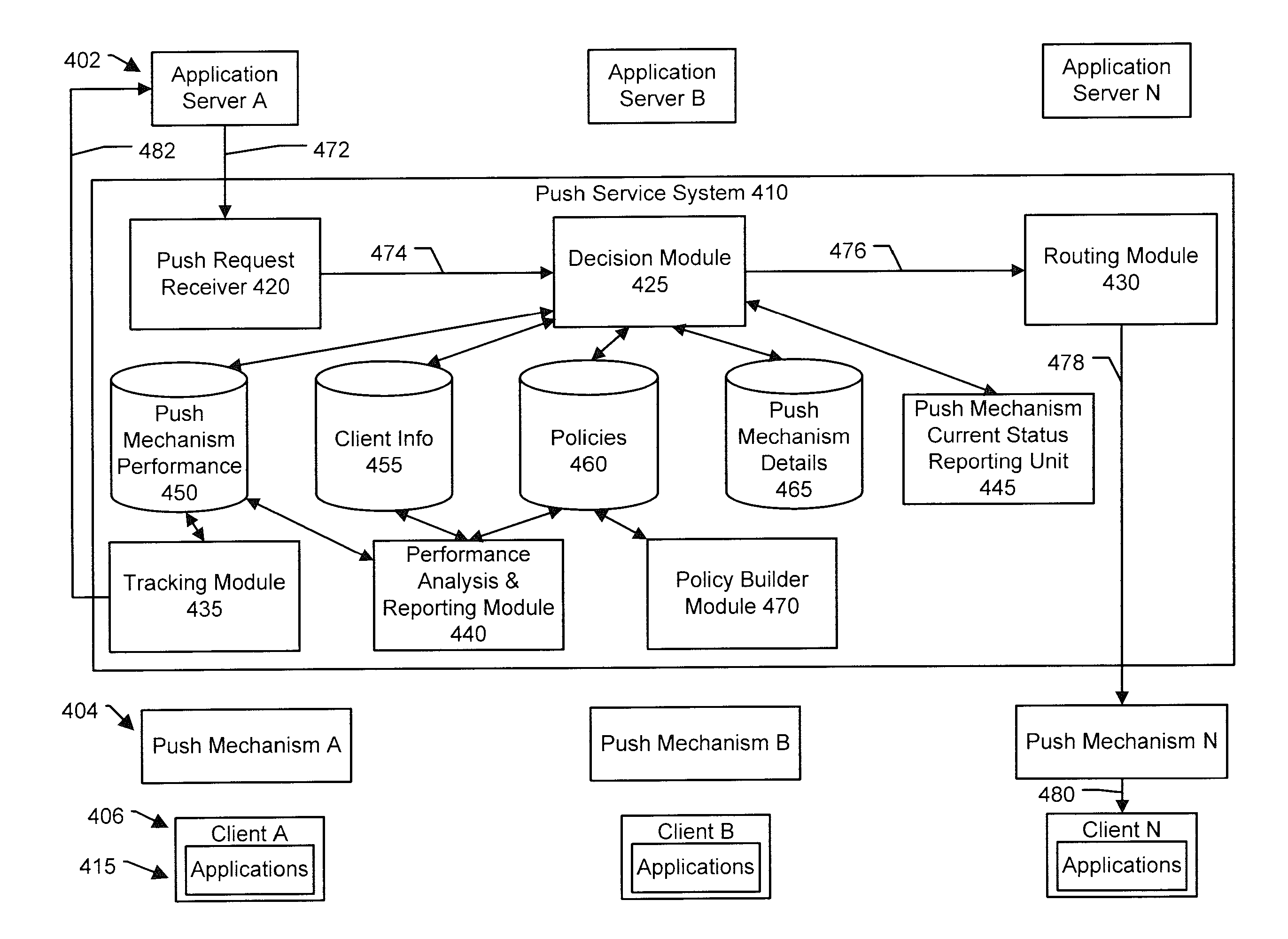
System and method for mobile device push communications
ActiveUS20130047034A1Multiple digital computer combinationsPayment architectureComputer networkMobile device
Pushing data to mobile devices can be problematic because mobile platforms may support a number push services, each of which have different cost and reliability characteristics. The problem of being able to push data to multiple different types of mobile devices from a single server is solved by a push service aggregator supporting multiple push services. Upon receiving a push request, one or more push services are selected for pushing data to a client. The selection may be based on a delivery profile included with the push request, information about the client, past performance of the push services, current status of the push services, or combinations of these. The status of the push may be tracked and monitored so as to retry in the case of non-delivery.
Owner:LOOKOUT MOBILE SECURITY
Method and system for localized data retrieval
ActiveUS9877138B1Easy programmingQuick SetupNetwork topologiesConnection managementData retrievalMobile device
A system and method for localized data retrieval to disseminate data about points of interest at a display venue, based on a local area network established with a series of commonly named wireless access points operatively connected to a main router. The system is connected to a user's mobile device through an application they are directed to download. Each WAP has a common name and is located about the display venue in close enough proximity to other WAPs so as to constitute an uninterrupted communication platform with the main LDRS computer from which data about the points of interest is polled. Interspersed about the display venue is a series of tracking devices causing nearby mobile devices to self report their location to the LDRS computer.
Owner:FRANKLIN WARREN LEE
Methods and apparatus for storage and execution of access control clients
ActiveUS20120108205A1Service provisioningUnauthorised/fraudulent call preventionPersonalizationThird party
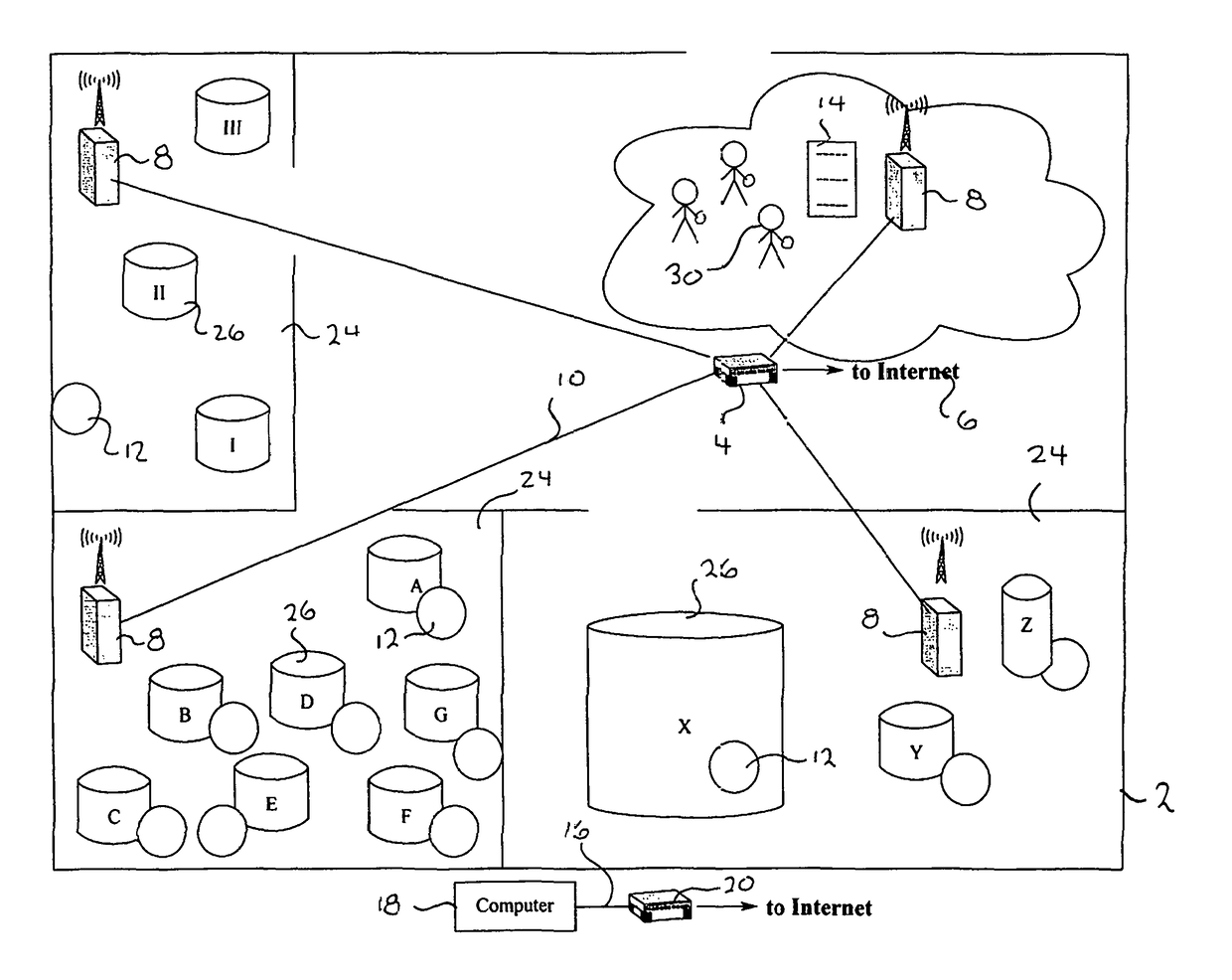
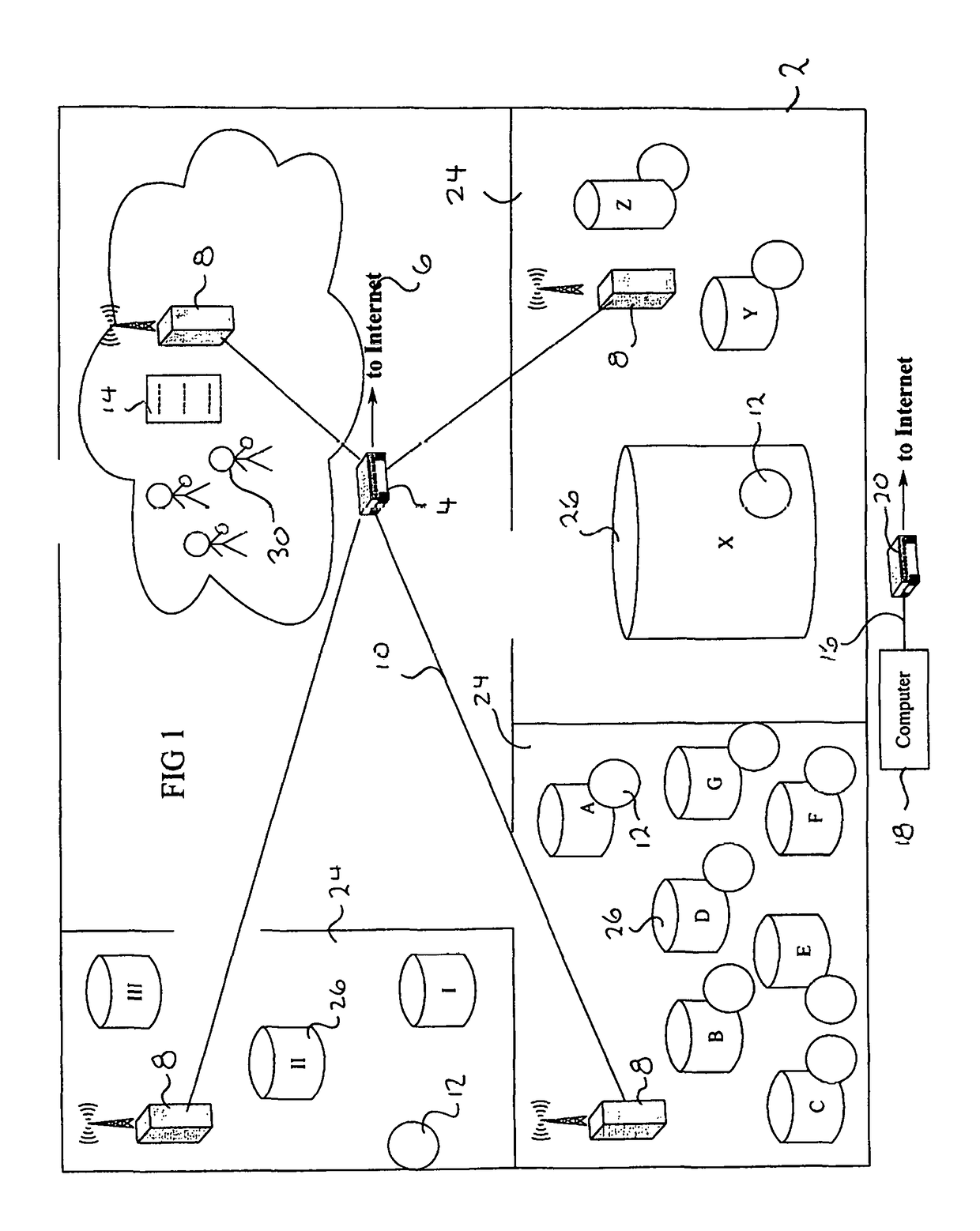
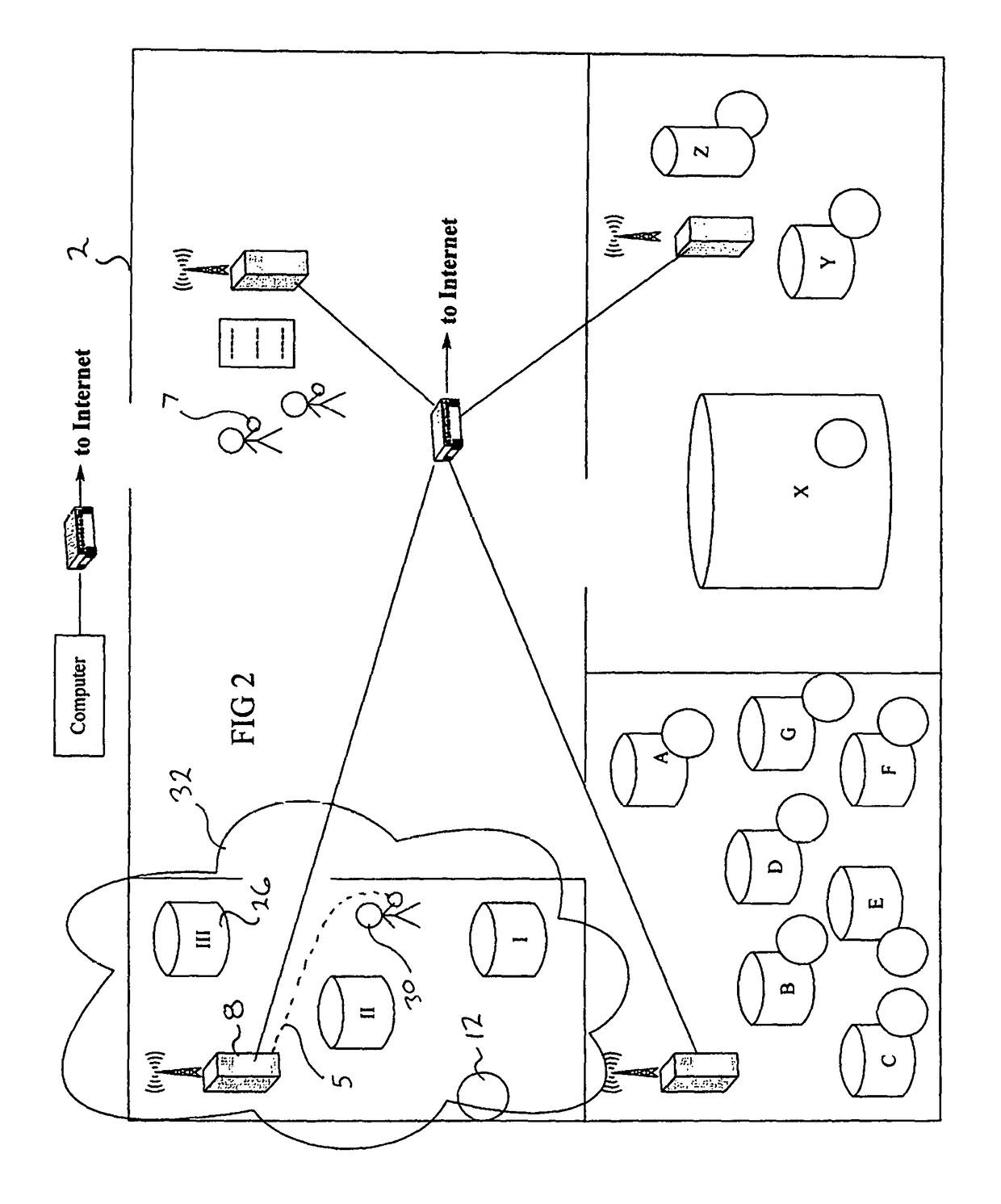
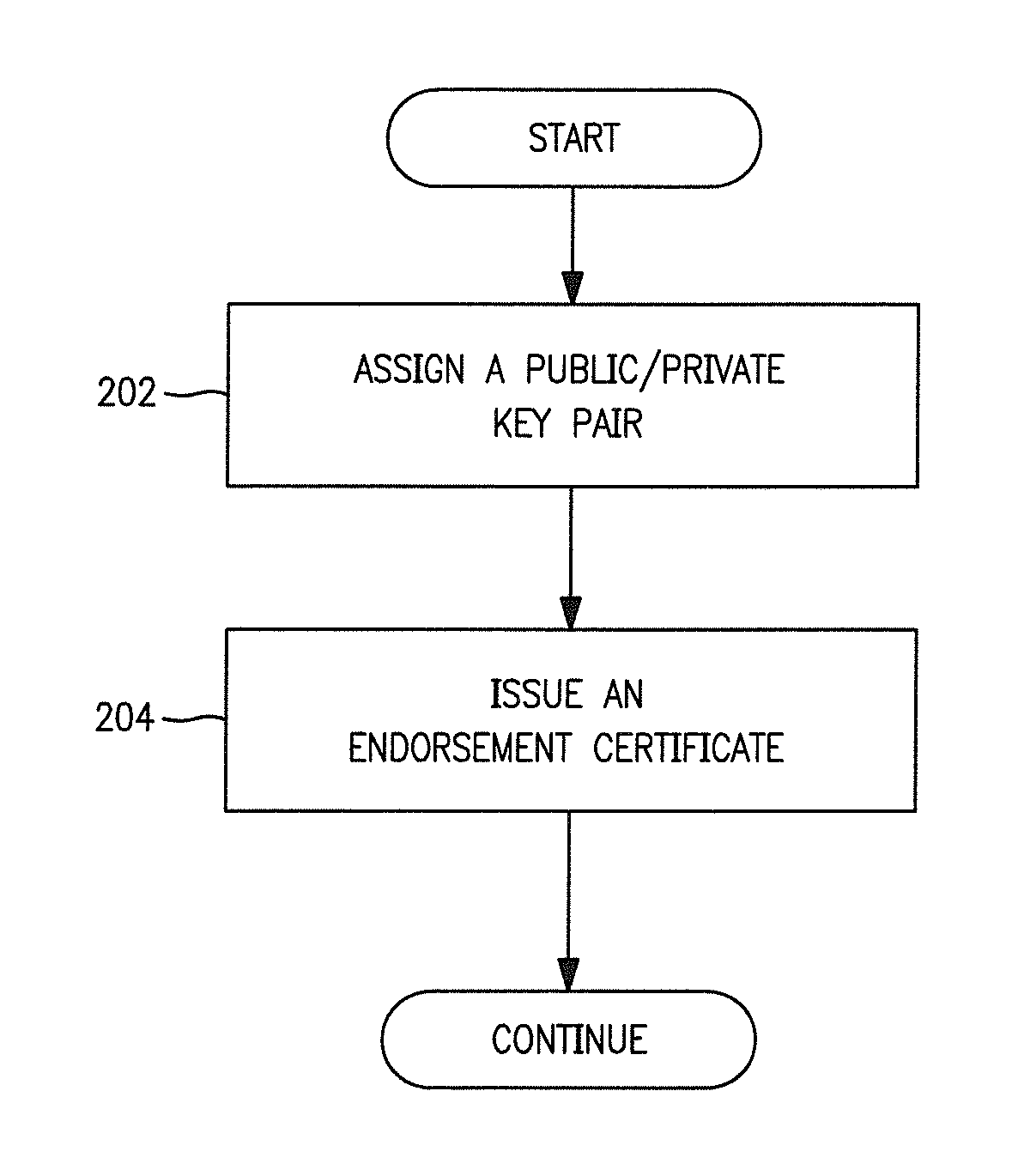
Methods and apparatus for secure provision of access control entities (such as electronic or virtual Subscriber Identity Module (eSIM) components) post-deployment of the host device on which the access control entity will be used. In one embodiment, wireless (e.g., cellular) user equipment is given a unique device key and endorsement certificate which can be used to provide updates or new eSIMs to the user equipment in the “field”. The user equipment can trust eSIM material delivered by an unknown third-party eSIM vendor, based on a secure certificate transmission with the device key. In another aspect, an operating system (OS) is partitioned into various portions or “sandboxes”. During operation, the user device can activate and execute the operating system in the sandbox corresponding to the current wireless network. Personalization packages received while connected to the network only apply to that sandbox. Similarly, when loading an eSIM, the OS need only load the list of software necessary for the current run-time environment. Unused software can be subsequently activated.
Owner:APPLE INC
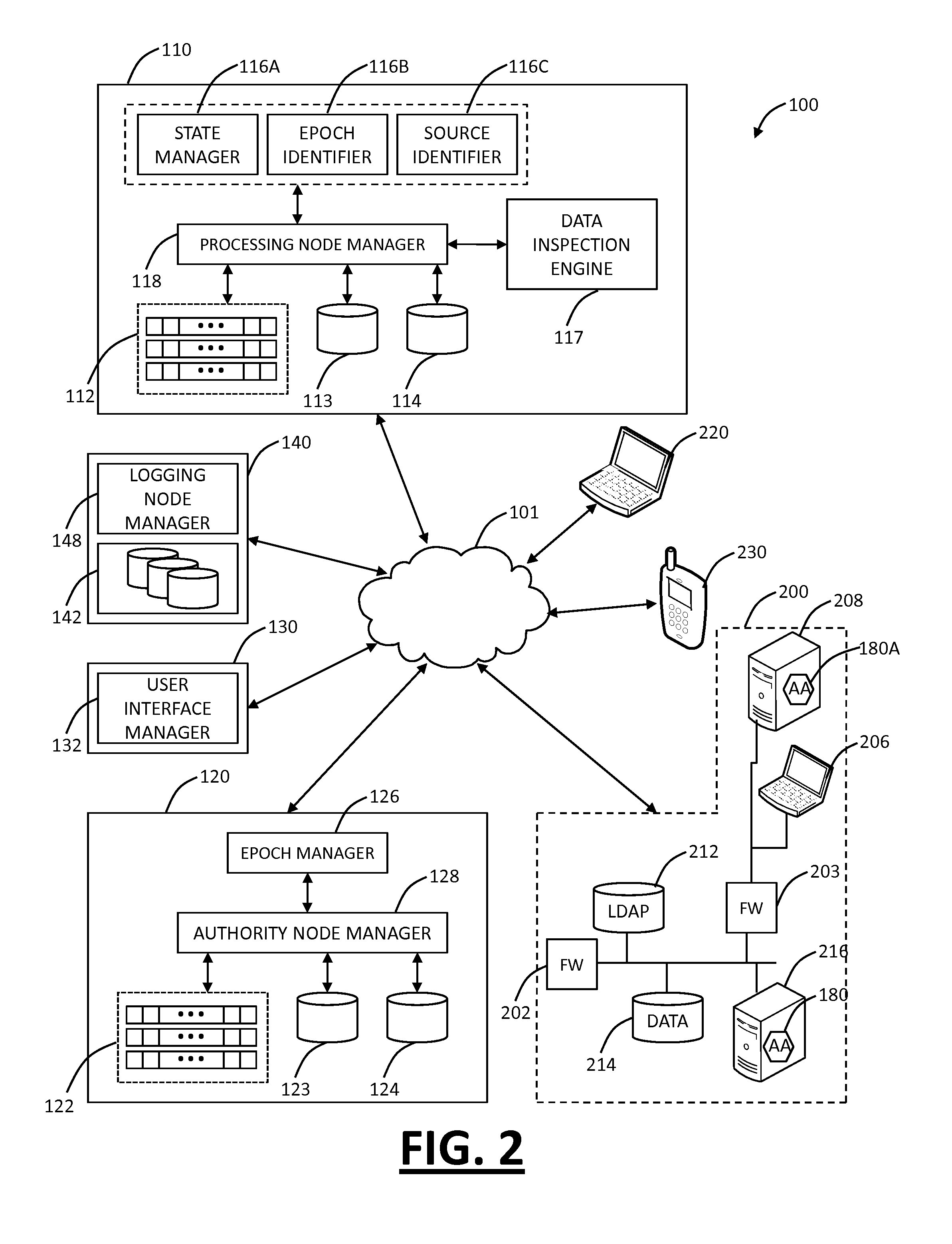
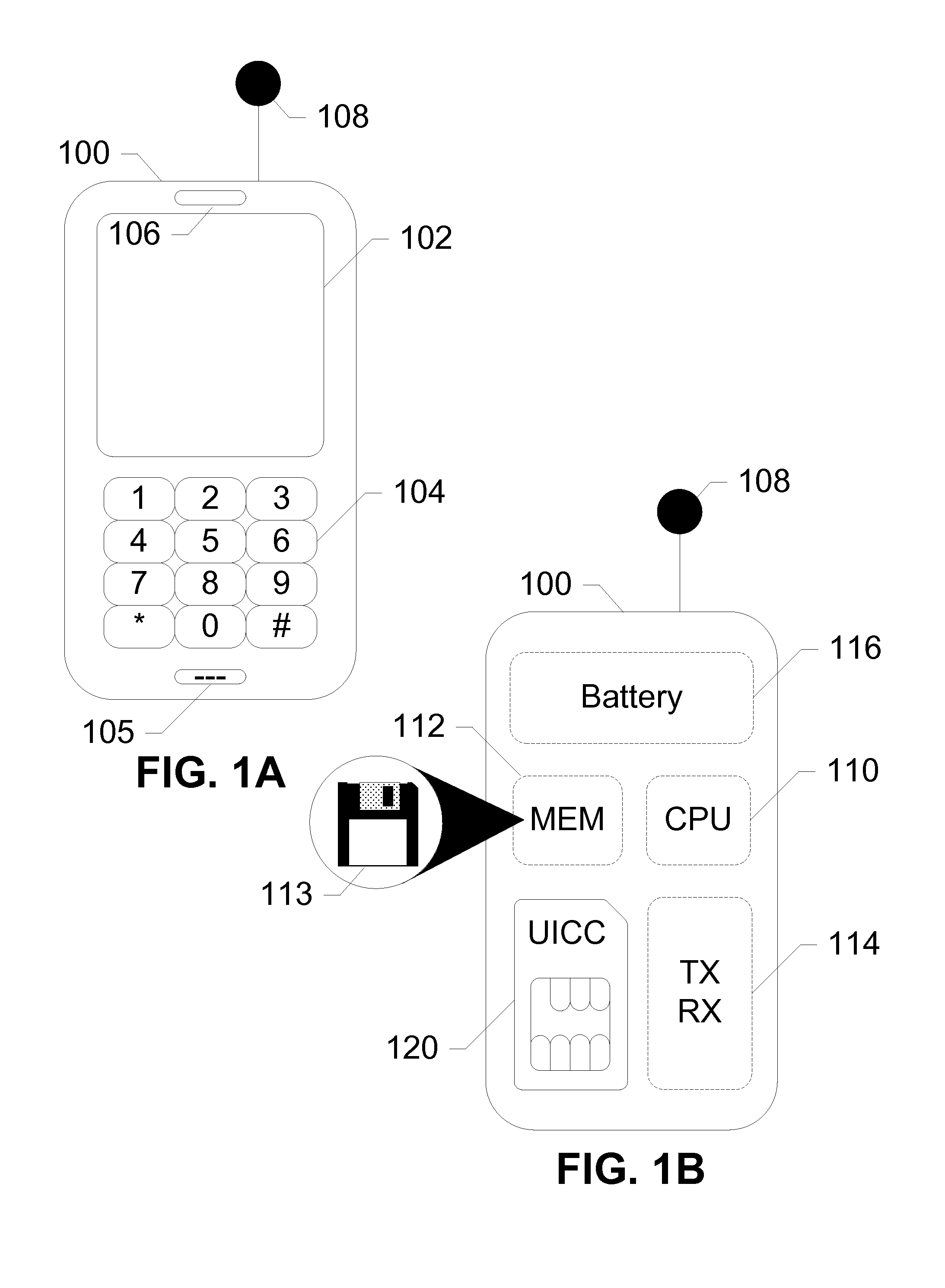
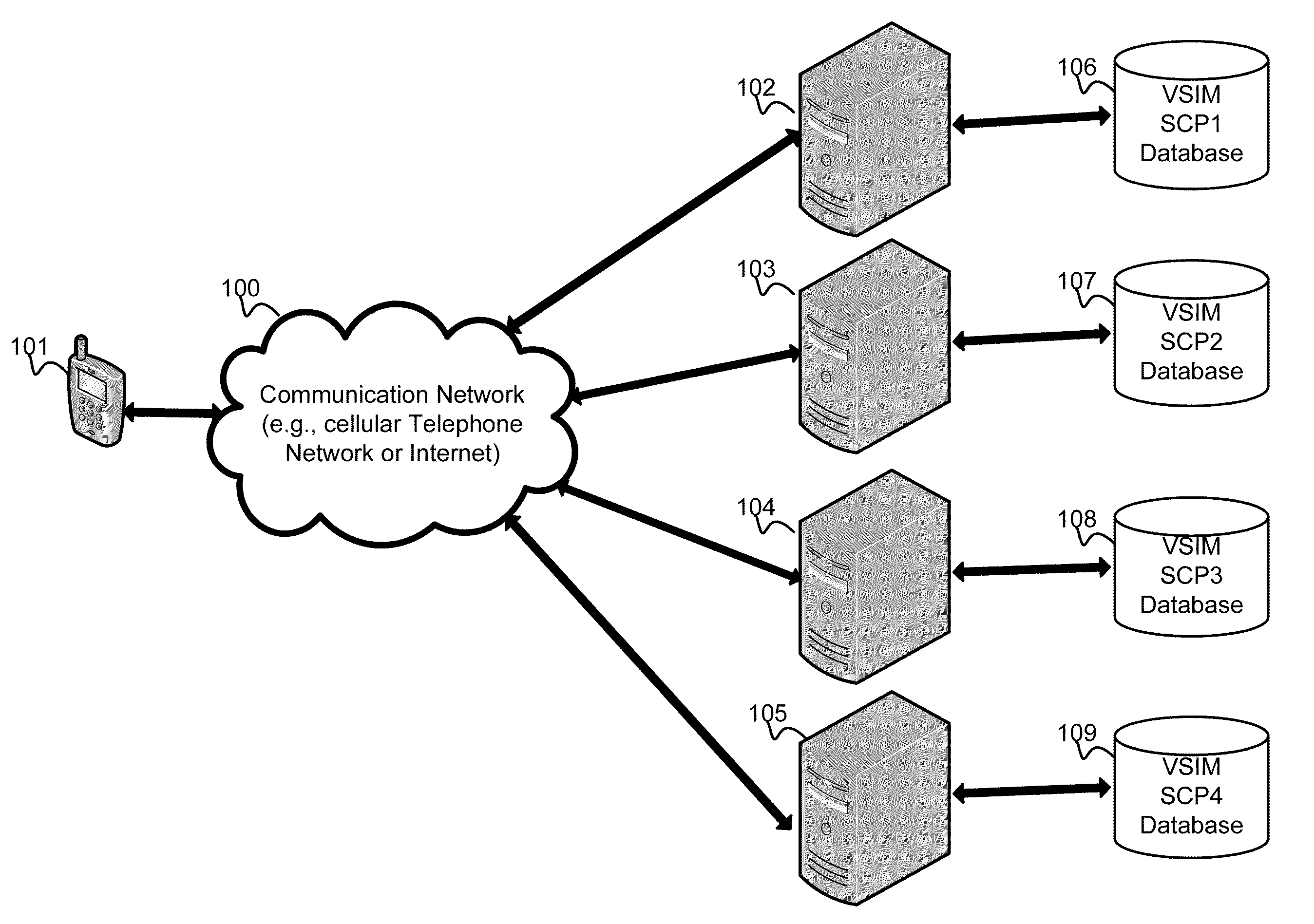
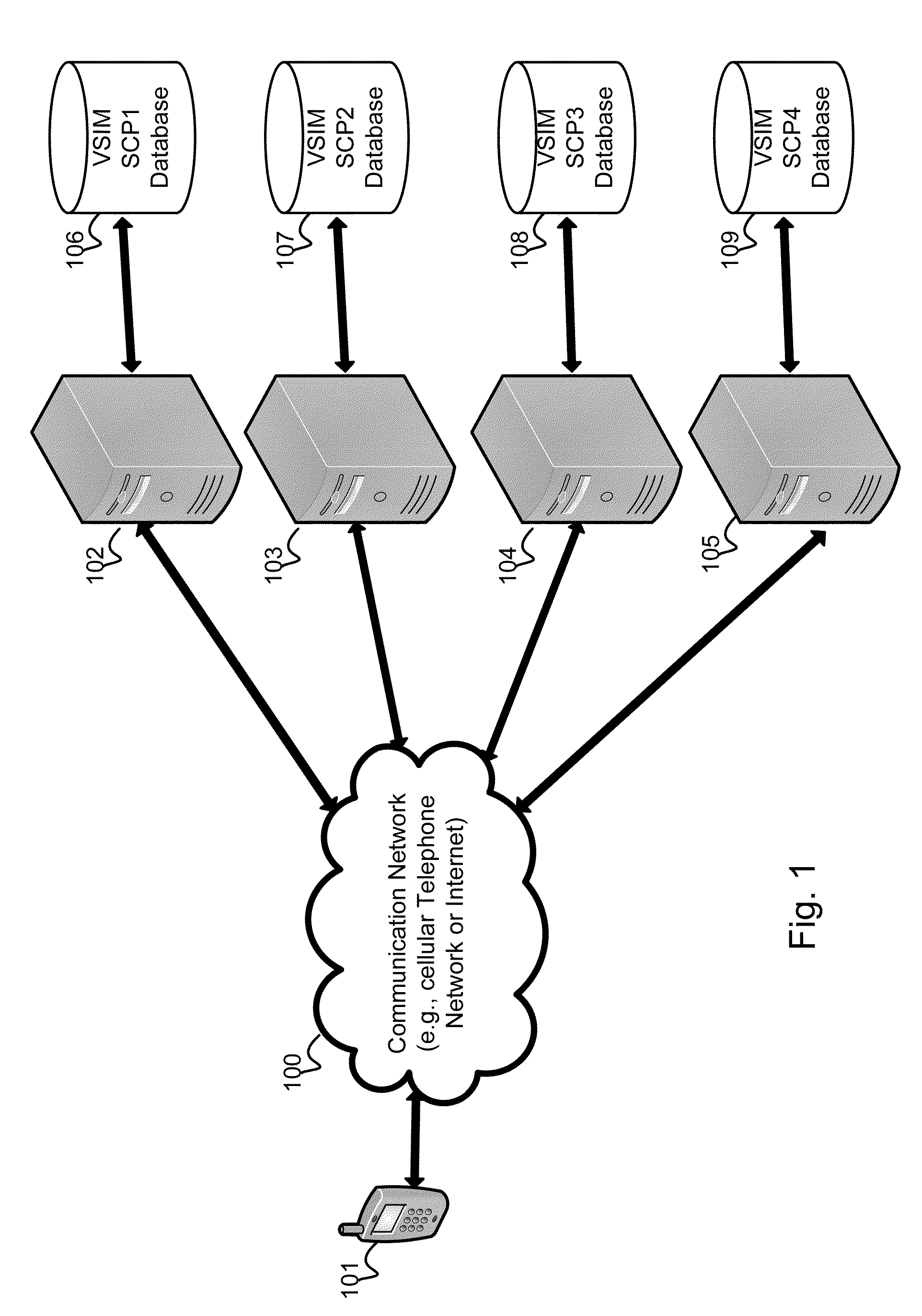
Virtual sim card for mobile handsets
A system and method store provisioning data supporting a plurality of service providers in a VSIM internal memory unit of a mobile device. A user may selectively enable provisioning data supporting one of the plurality of service providers stored in the VSIM internal memory unit to conduct a wireless communication. An embodiment permits backing up, retrieving and restoring personal data in the VSIM internal memory unit using a remote database. Another embodiment allows a mobile device to select an optimal service provider to conduct a wireless communication. The optimal service provider may be determined based upon mobile device location, communication usage request and / or time and date.
Owner:QUALCOMM INC
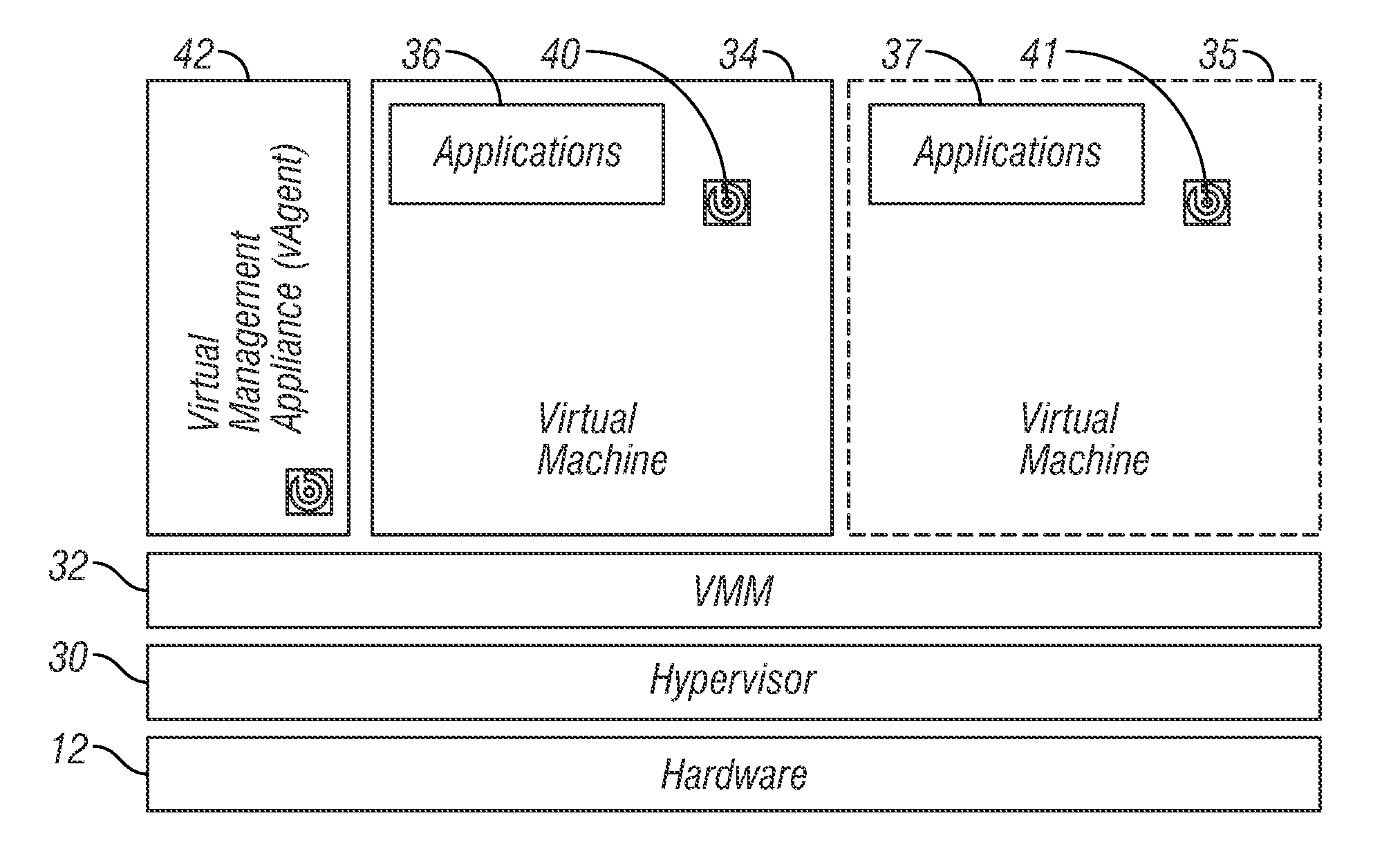
Endpoint-Hosted Hypervisor Management
InactiveUS20110107331A1New of controlNew levelService provisioningMobile application execution environmentsOperational systemClient-side
A client hypervisor comprises a virtual agent that runs outside of a system OS and that allows device management independent of the OS and user. The virtual agent is tied to a device and not a specific instance of the OS. Such client hypervisors expose new functionality to ease managing systems. Some of these capabilities come from the persistence and privileges outside the OS. In some embodiments of the invention, this new management functionality is exposed to allow device management via new virtualization concepts, such as multiple VMs per system, VM replacement, snapshot / rollback, etc.
Owner:IBM CORP
Systems and methods for the automatic registration of devices
InactiveUS20060010078A1Broadband local area networksPayment architectureDatabase serverComputer science
Systems and methods for providing registration at a remote site that may include, for example, a monitoring module that may communicate with a remote site. A registration protocol may be used by the monitoring module and the remote site in generating the messages communicated during the registration process. The monitoring module may gather and generate various identification information to be included in the registration protocol messages. The registration information provided by the monitoring module may be stored at the remote site in a database server having a database. A confirmation message may be communicated from the remote site to the monitoring module that may either acknowledge successful registration or report that an error occurred during the registration process.
Owner:GOOGLE LLC
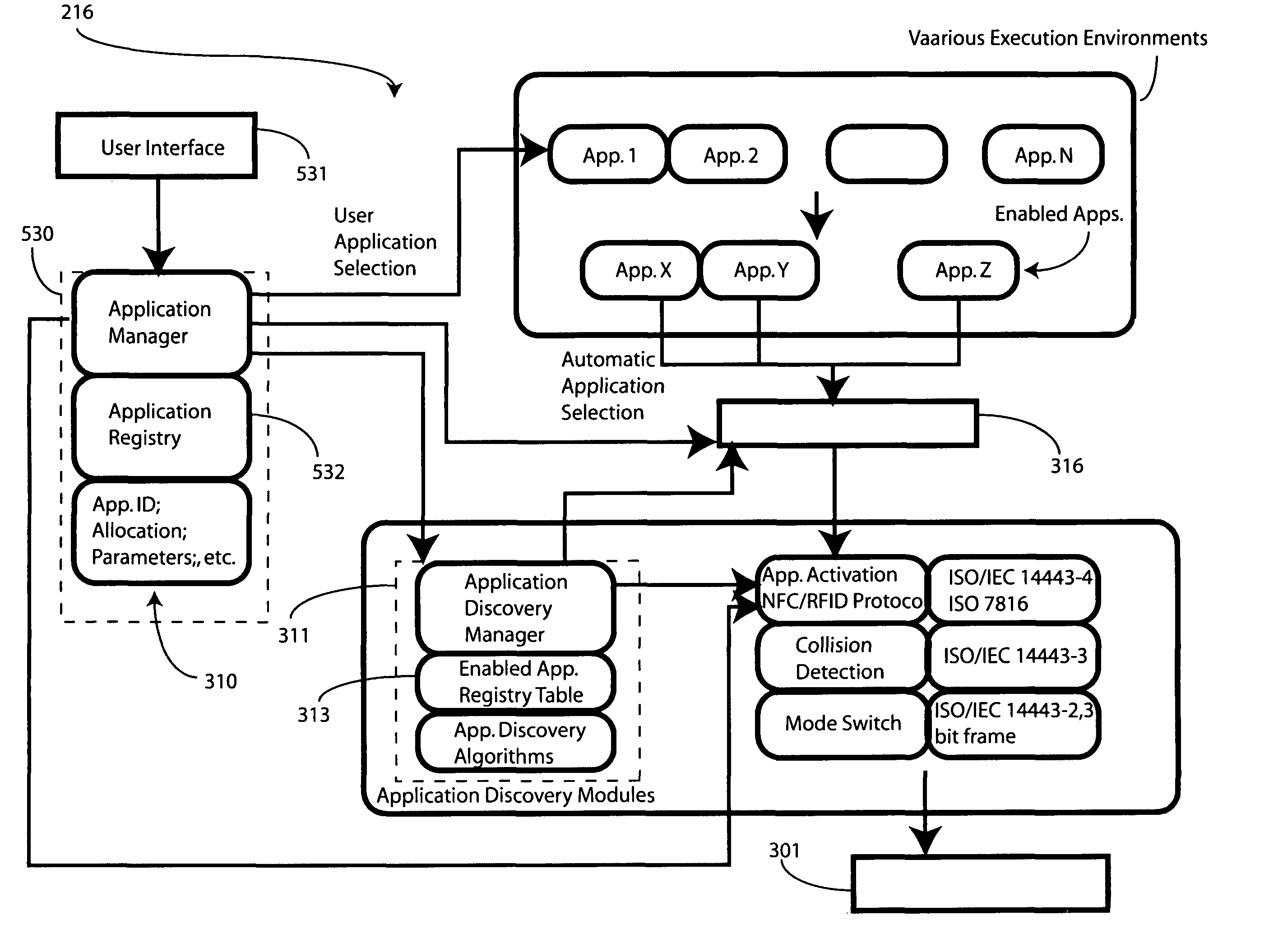
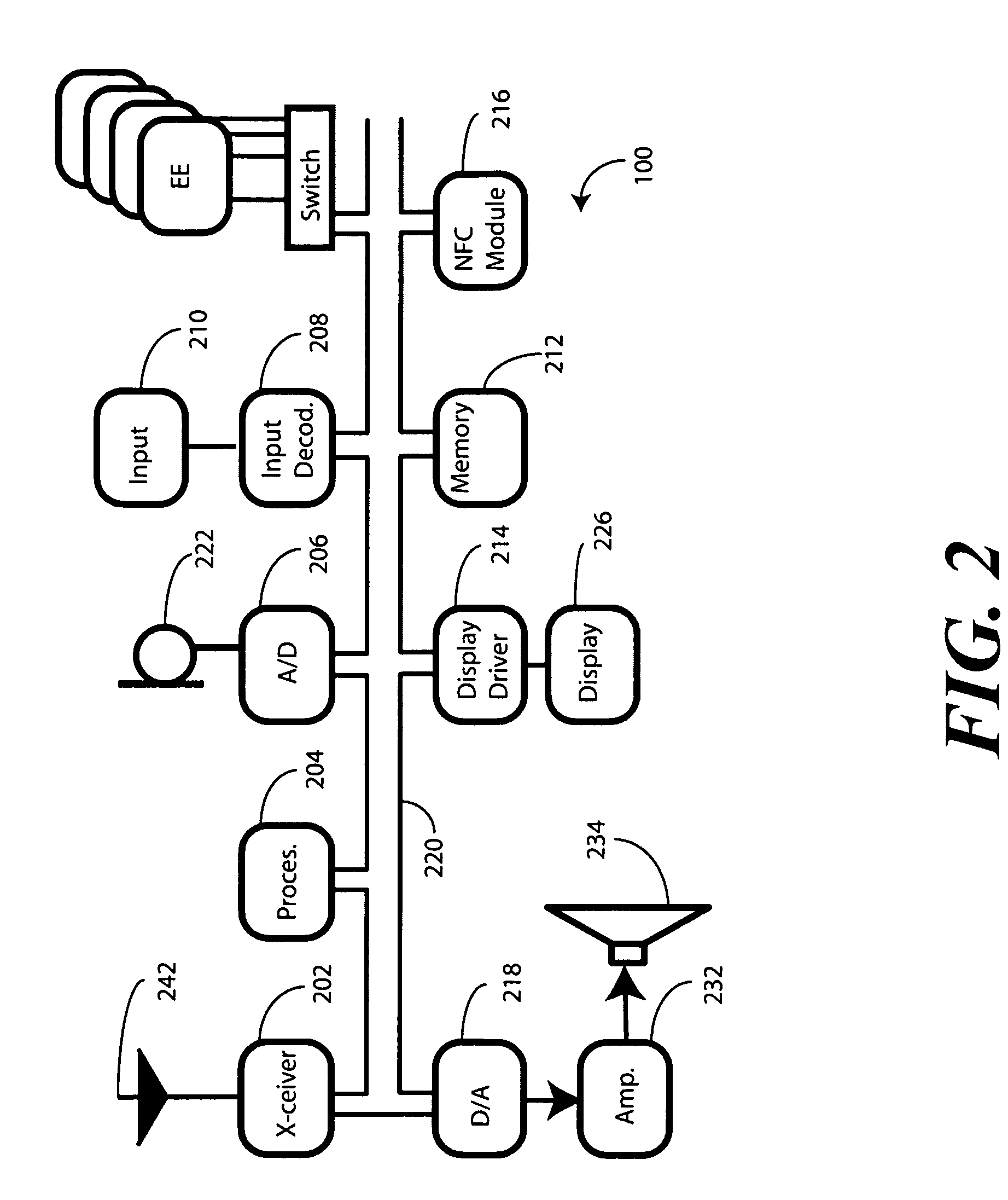
Method and apparatus for automatic near field communication application selection in an electronic device
In a portable electronic device (100) having a plurality of near field communication applications stored within a plurality of execution environments, an application discovery manager (311) is configured to automatically select and launch one or more of the near field communication applications. A near field communication circuit (300) receives a near field communication request from an external near field communication device (700). The application discovery manager (311) identifies a near field communication technology, a protocol, and an application identifier and then references a registry table (313) to determine identification parameters corresponding with the identified information. The application discovery manager (311) then selects a near field communication application and launches it. The application discovery manager (311) further configures a routing switch (316) to direct data between the near field communication circuit controller (301) and the appropriate execution environment.
Owner:GOOGLE TECH HLDG LLC
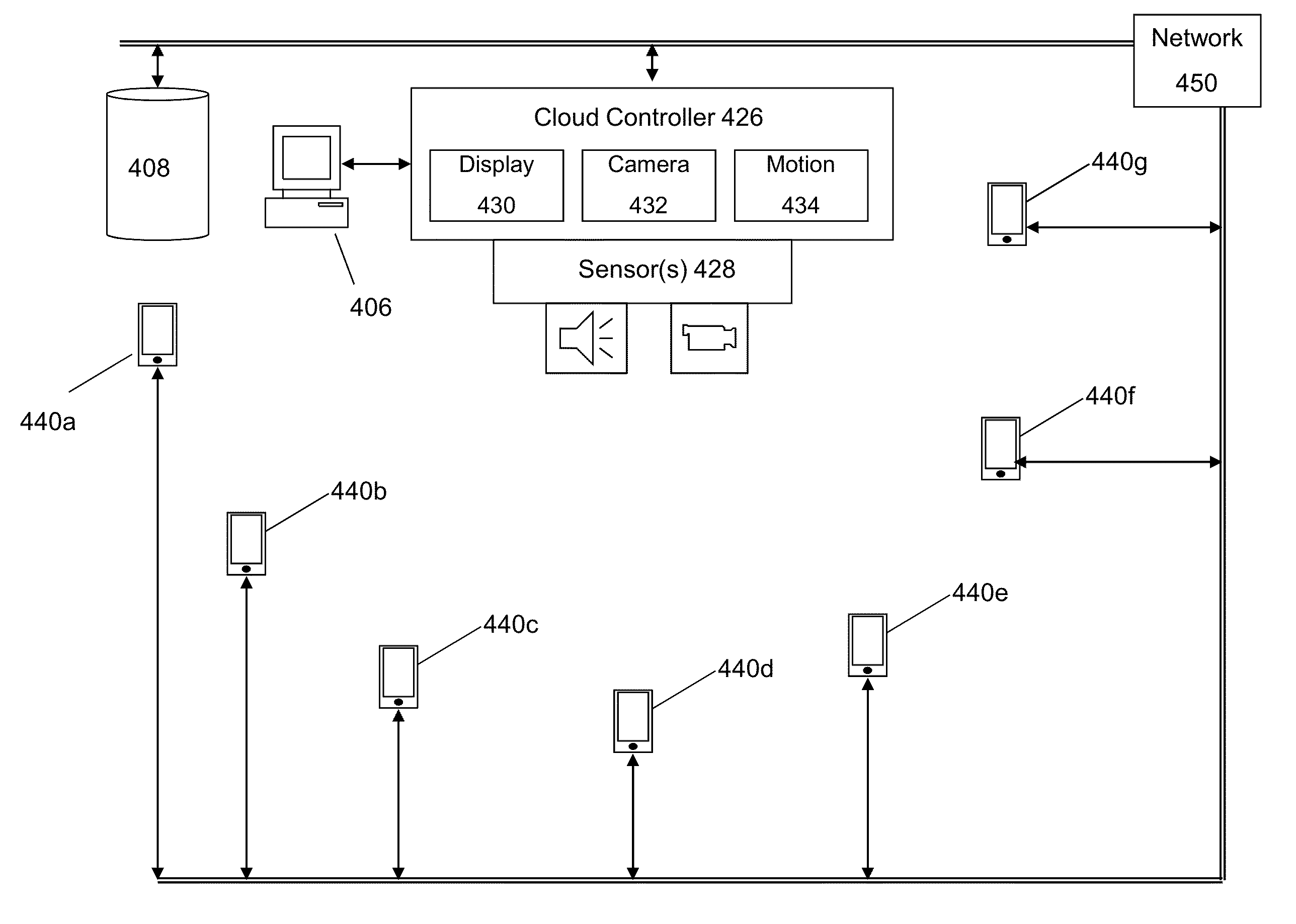
Method and mechanism for performing cloud image display and capture with mobile devices
ActiveUS8499038B1Television system detailsServices signallingHuman–computer interactionMobile device
Disclosed is an improved approach for implementing participatory interaction at events using mobile devices. One approach is to utilize distributed display screens for the mobile devices in an audience to display a much larger collective image. Another approach is to utilize the distributed cameras of mobile devices in an audience to form a massive capture device from the different locations and perspectives of the audience members. Yet another approach is directed to the use of mobile devices in the audience to capture motion events among the audience, which are then used to synthesize new media items and types for the event.
Owner:ENCONCERT
Context-aware code provisioning for mobile devices
ActiveUS20080045172A1Specialized client software is greatly simplifiedSimple processTransmissionLocation information based serviceClient-sideMobile device
A simplification of the process of deploying public services for mobile users Particular refinements in this vein involve the dynamic configuration of client software using available context information and the optimization of software provisioning based on historical usage information, which includes services accessed together with the location and time of access.
Owner:IBM CORP +2
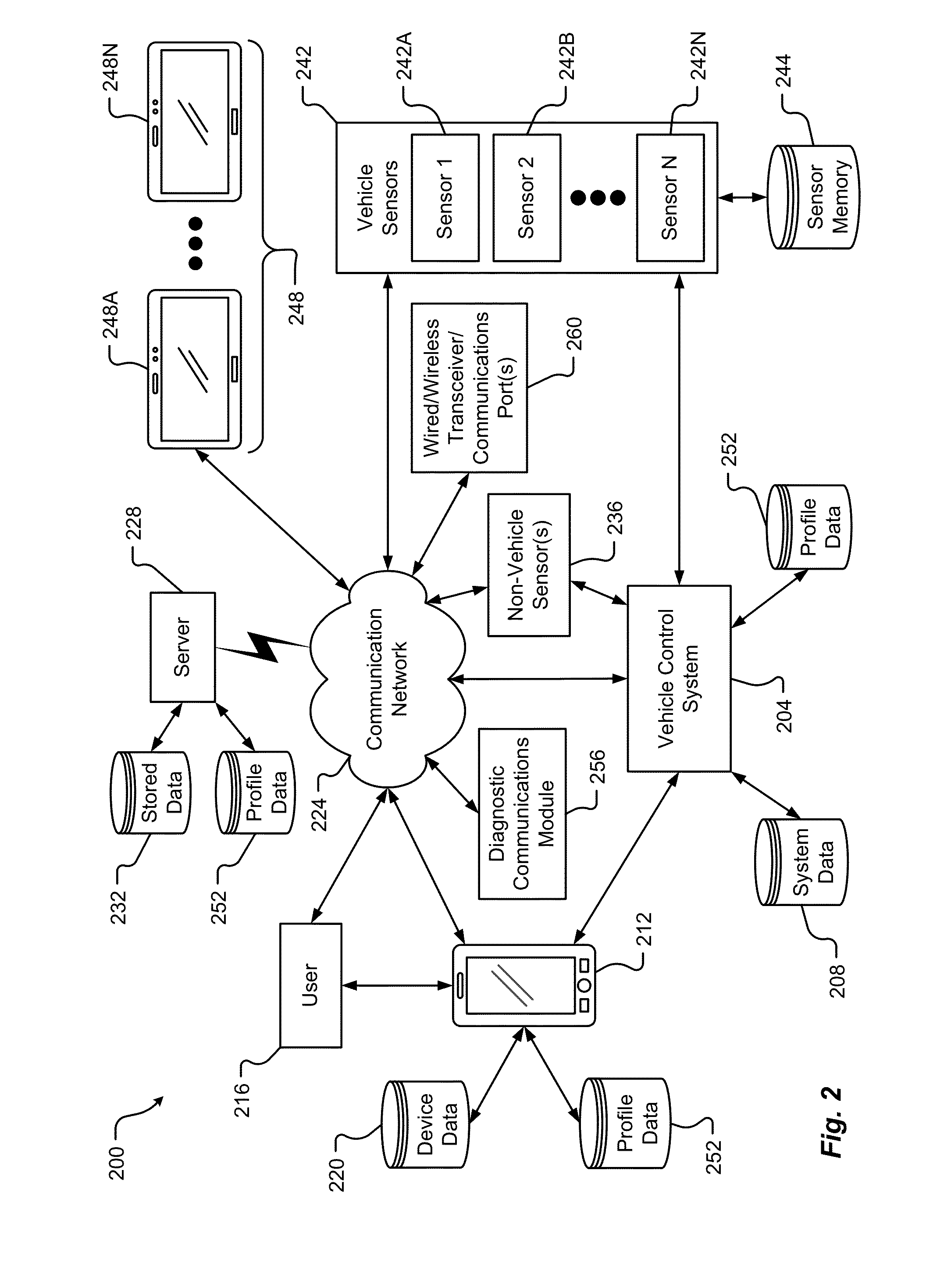
Vehicle-based multimode discovery
ActiveUS20150232065A1Improve reliabilityUnnecessary removalControlling traffic signalsVehicle seatsTelecommunicationsOn board
Methods and systems for a device discovery daemon that bases access of a communication device to an on board vehicle network on device location are provided.
Owner:AUTOCONNECT HLDG
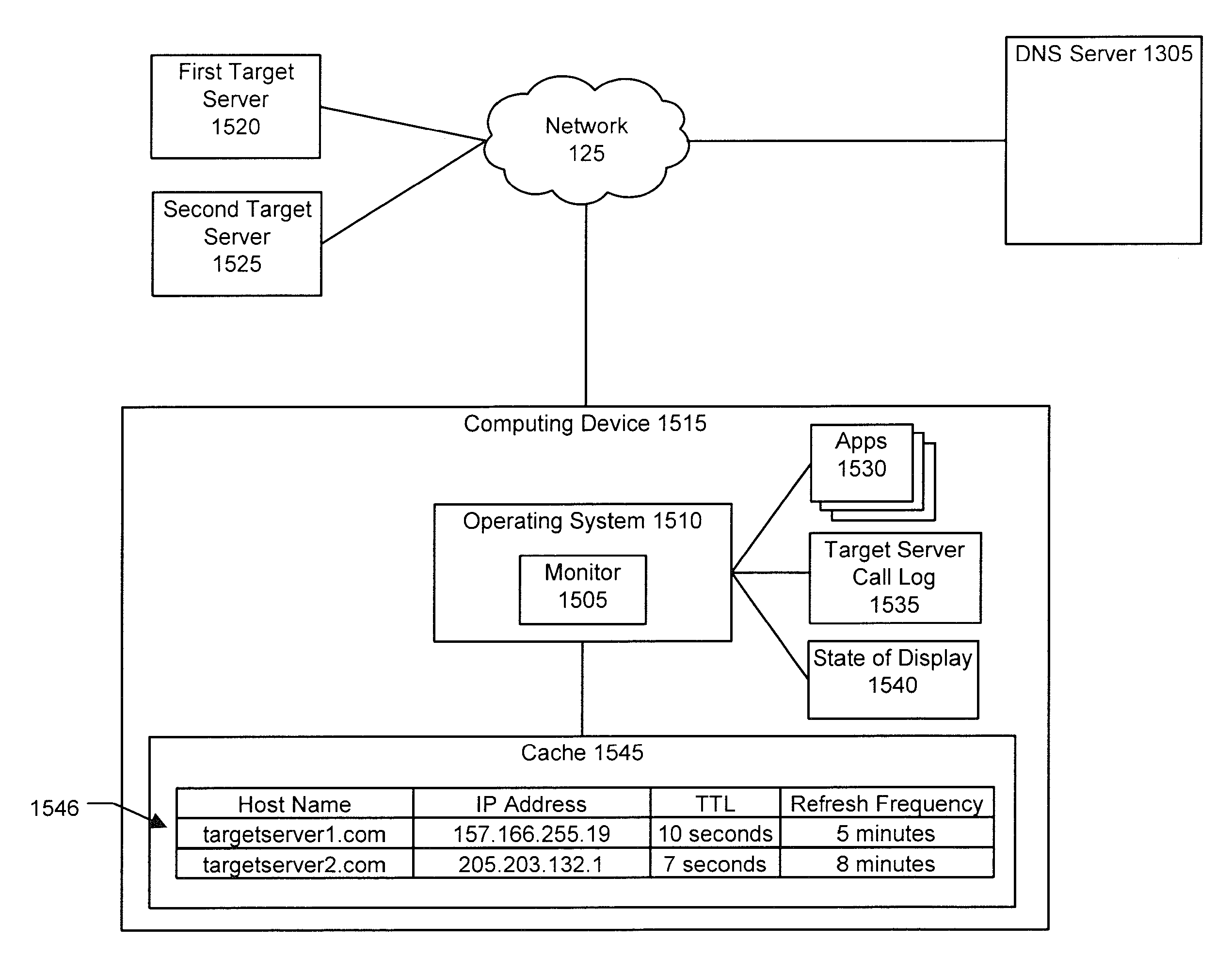
Mobile device DNS optimization
When a mobile device interacts with a network service, synchronous DNS resolution can significantly impact user experience due to lossy or moderate-high latency conditions. Network services that rely on low-TTL DNS records for failover require a client to frequently resolve the service's host name. It is undesirable to block on these frequent resolutions. In an implementation, user activity on a mobile device is monitored to determine whether the user is engaged in an activity that would contact a server. If such an activity is in progress, then DNS requests to resolve the server's host name are periodically generated to make sure the server's IP address is cached. In an implementation, if a request to communicate with a server fails, the DNS cache expires the entry for that server so that a new DNS request can resolve the server's IP address in case the server's IP address has changed.
Owner:LOOKOUT MOBILE SECURITY
System for implementing security on telecommunications terminals
ActiveUS20090254993A1Improve securityOvercome problemsUnauthorised/fraudulent call preventionEavesdropping prevention circuitsTelecommunications linkComputer terminal
A system includes at least one telecommunications terminal having data processing capabilities, the telecommunications terminal being susceptible of having installed thereon software applications, wherein each software application has associated therewith a respective indicator adapted to indicate a level of security of the software application, the level of security being susceptible of varying in time; a software agent executed by the at least one telecommunications terminal, the software agent being adapted to conditionally allow the installation of software applications on the telecommunications terminal based on the respective level of security; a server in communications relationship with the software agent, the server being adapted to dynamically calculate the level of security of the software applications, and to communicate to the software agent the calculated level of security of the software applications to be installed on the telecommunications terminal.
Owner:TELECOM ITALIA SPA
Wireless inter-device data processing configured through inter-device transmitted data
ActiveUS8244179B2Near-field for read/write/interrrogation/identification systemsBroadcast services for monitoring/identification/recognitionUltra-widebandComputer hardware
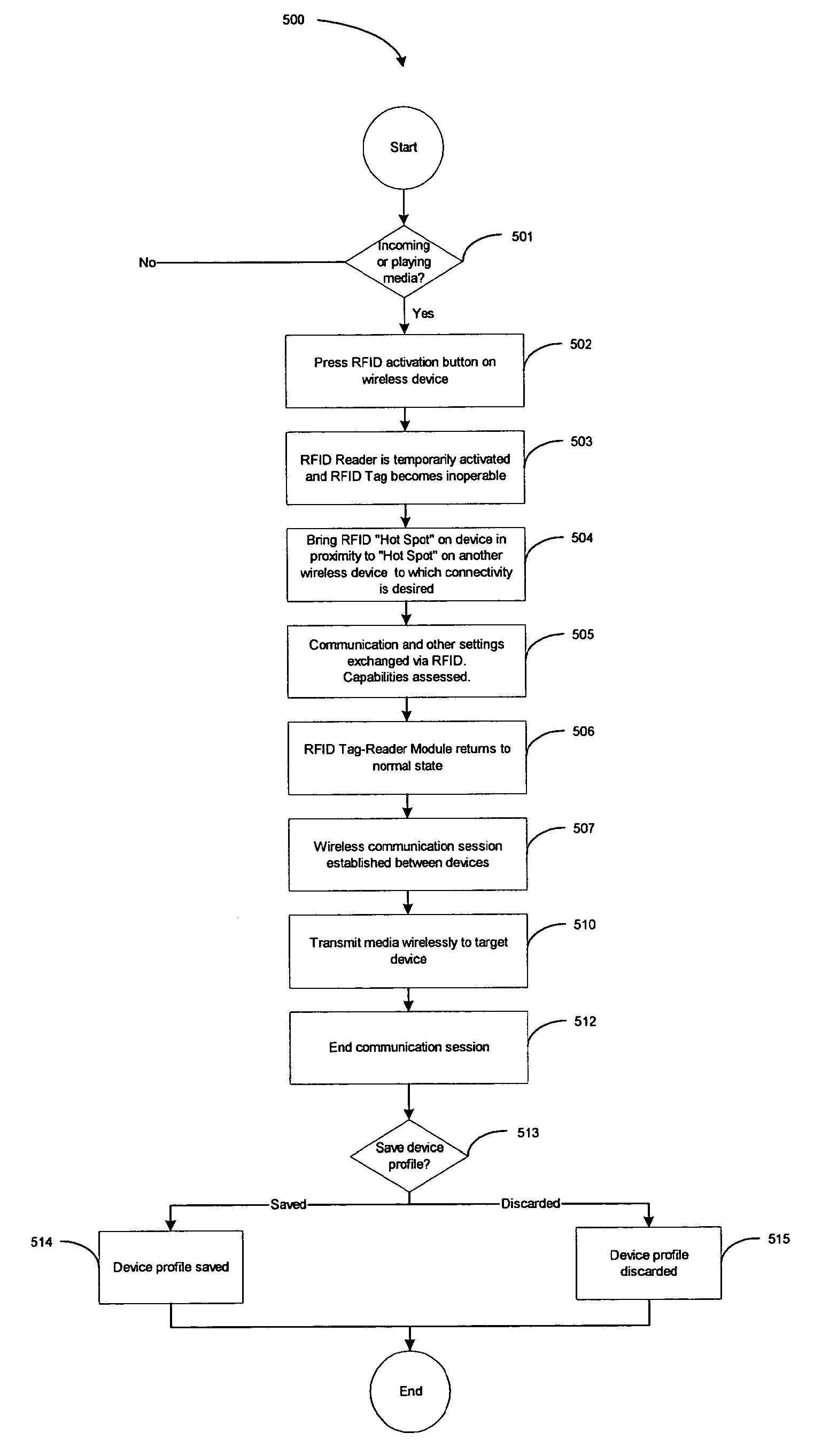
A wireless media player and a related system and methodology are disclosed. One aspect of the wireless media player system pertains to a virtual connector system, apparatus, and method for the automatic establishment of wireless connectivity with other electronic devices. In one embodiment, the media player device employs the use of integrated Radio Frequency Identification (RFID) technology to exchange communication settings, media capability, and other parameters with an external device that also has integrated RFID technology. The automatic exchange of settings and other information via a proximity-based RFID data exchange allows a media player to quickly establish a secure communication link with another device via a commonly supported wireless protocol such as Ultra Wideband (UWB) or Bluetooth. Another aspect of the media player system pertains to a method of using the captured media capability of the connecting device to customize certain menu options and software parameters in the media player.
Owner:SYNDEFENSE
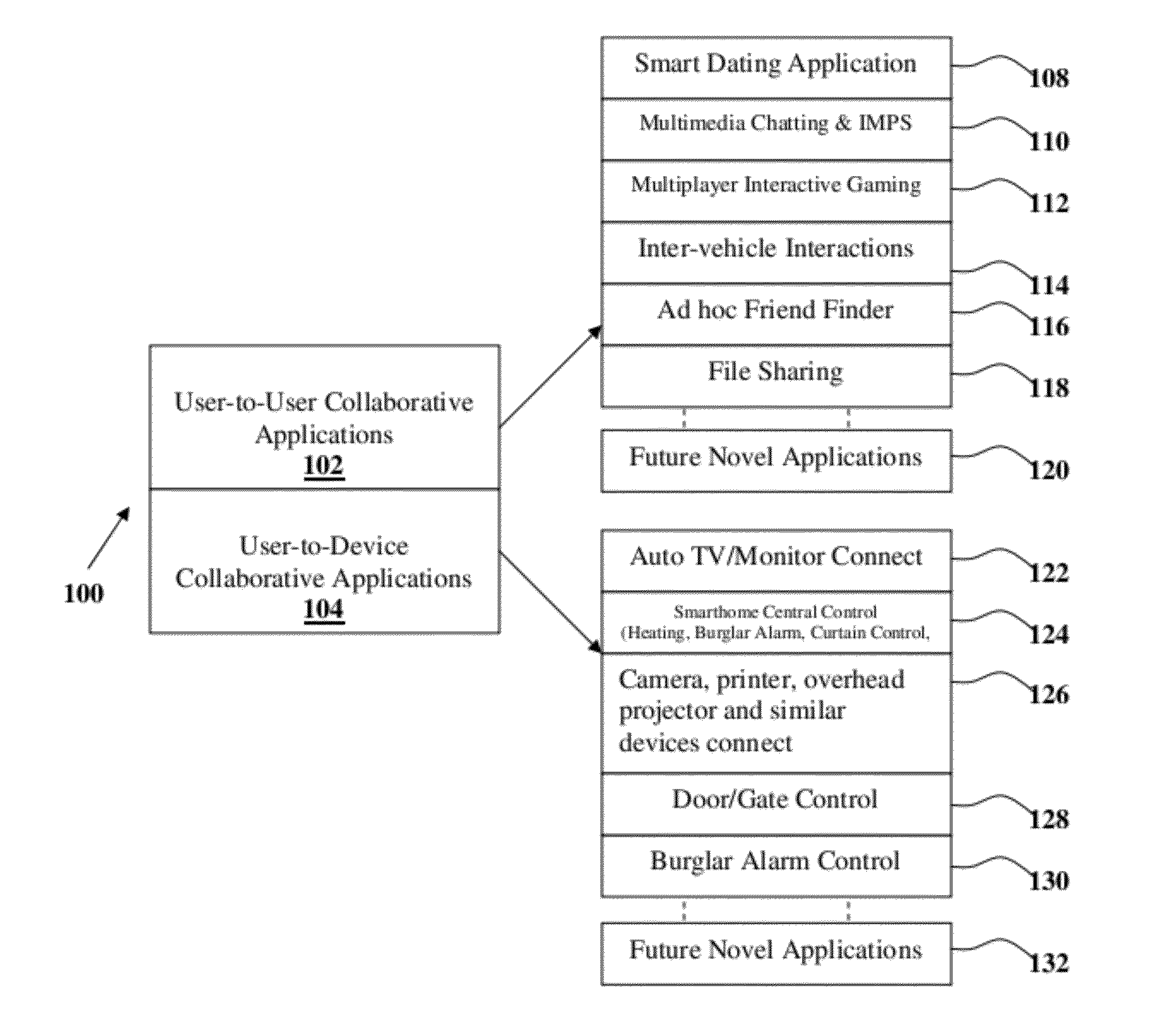
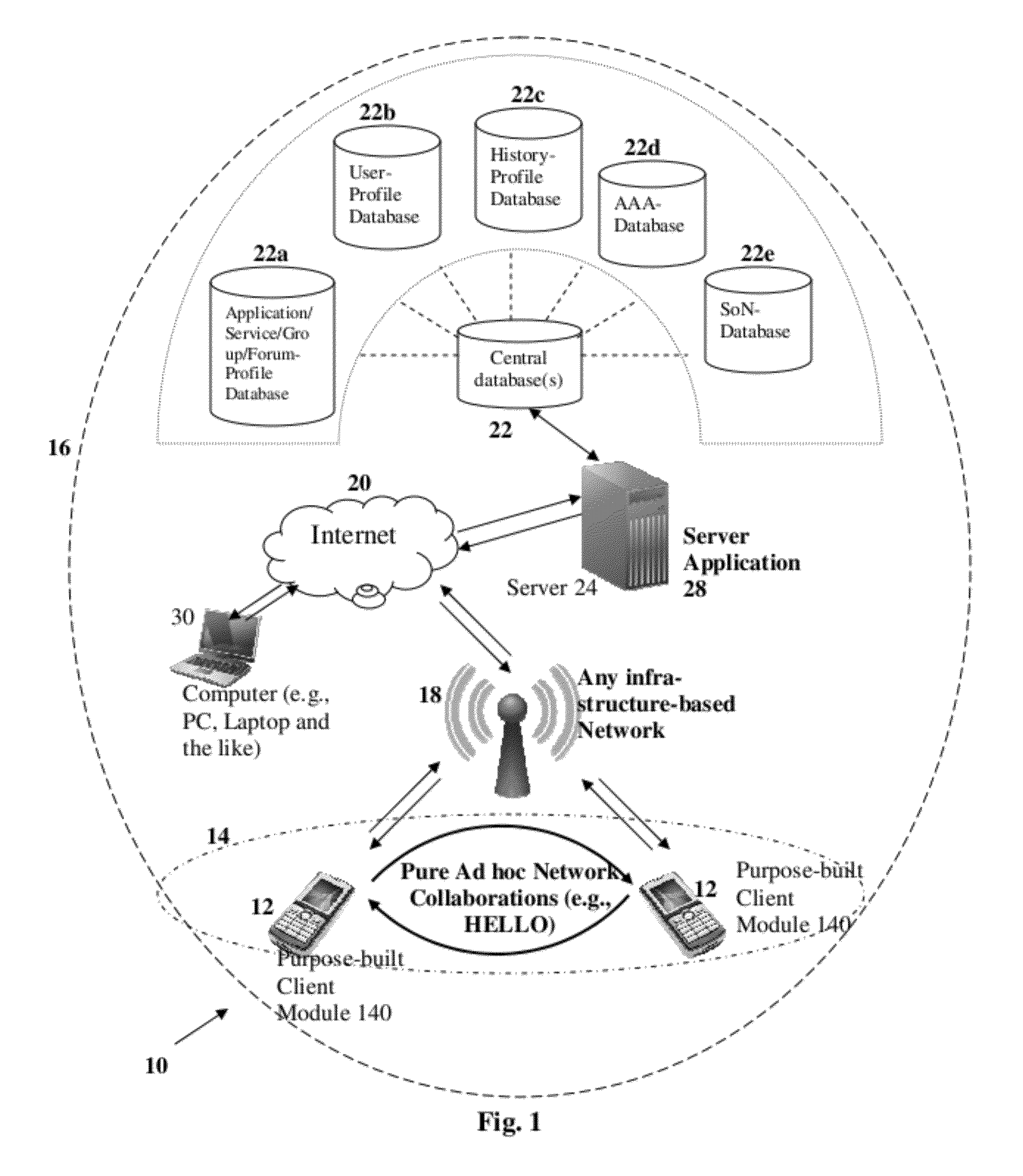
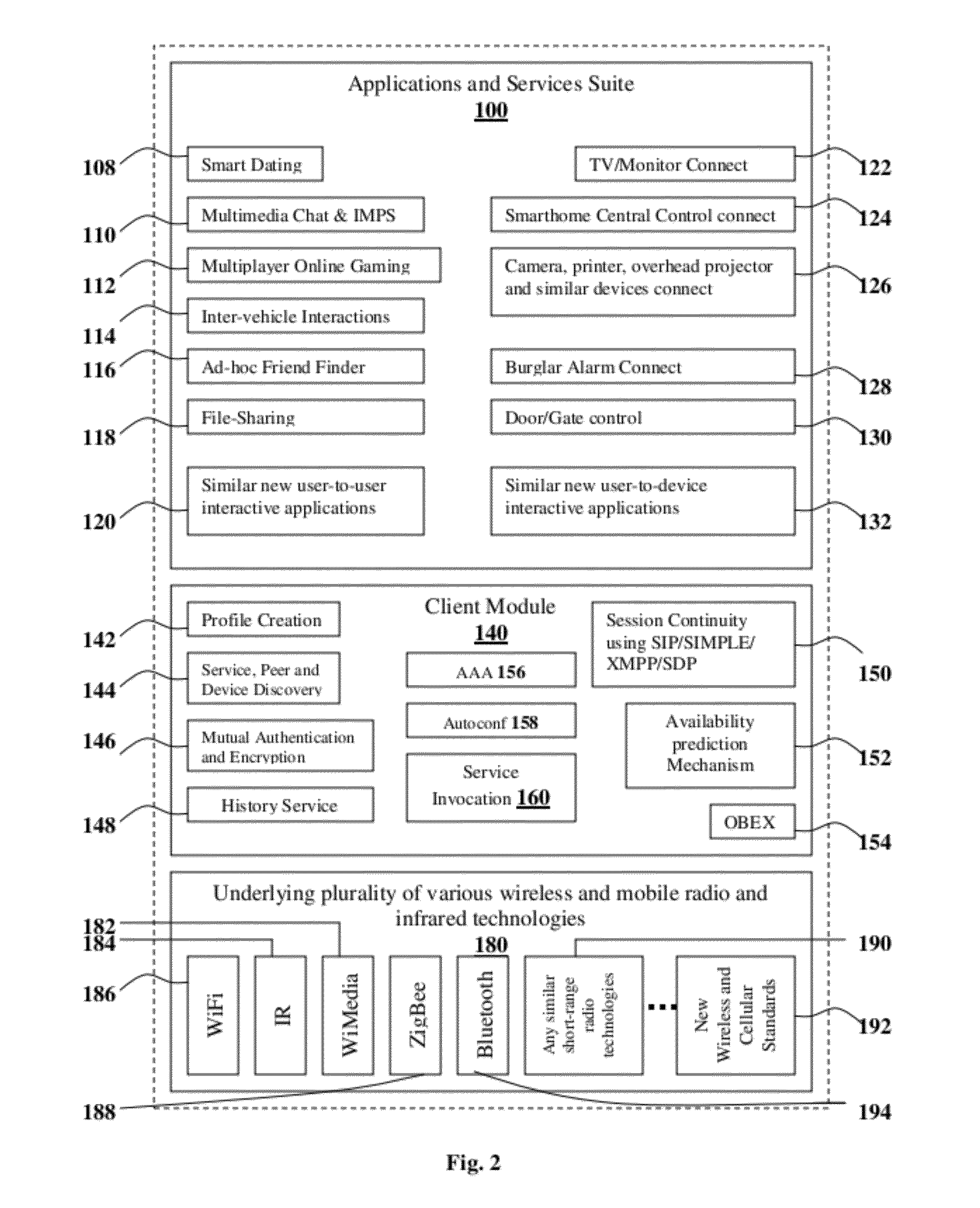
Scalable Secure Wireless Interaction enabling Methods, System and Framework
InactiveUS20120084364A1Avoiding self-configuringConnection securityNetwork topologiesMultiple digital computer combinationsNetwork conditionsOperation mode
The present invention proposes methodologies, a system and a secure spontaneous collaboration framework along with a suitable application and services suite for enabling new paradigm of social networking among users of handheld devices by bridging gab between infra-structure-based networks and mobile ad hoc networks. While supporting three different operating modes for the spontaneous collaboration that suits the user preference and network conditions, the proposed solutions hide the complexity of finding the right peer / device for spontaneous collaboration, self-organising the network to be formed on-demand, mitigating the security threat, being aware of user mobility for service continuity across wide variety of networks. Binding a given user to user's handheld device and specifying the number of applications / services enabling spontaneous collaborations that a given user is interested in are possible through user-profile creations. By taking a holistic view, the proposed solutions enable very practical, scalable, secure and economical spontaneous collaborations.
Owner:SIVAVAKEESAR SIVAPATHALINGHAM
Method and system for electronic content storage and retrieval with galois fields on cloud computing networks
InactiveUS20120278622A1Web data indexingDigital data processing detailsCloud storageCloud communications
A method and system for electronic content storage and retrieval with Galois Fields on cloud computing networks. The electronic content is divided into plural portions and stored in plural cloud storage objects. Storage locations for the plural cloud storage objects are selected using a Galois field and the plural cloud storage objects are distributed across the cloud network. When the electronic content is requested, the plural portions are retrieved and transparently combined back into the original electronic content. No server network devices or target network devices can individually determine locations of all portions of the electronic content on the cloud communications network, thereby providing layers of security and privacy for the electronic content on the cloud communications network.
Owner:LESAVICH STEPHEN +1
Popular searches
Broadcast service distribution Data switching networks Special data processing applications Security arrangement Information technology support system Subscription services Network data management Short range communication service Machine-to-machine/machine-type communication service Near-field in RFID
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com