Patents
Literature
124 results about "Token passing" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
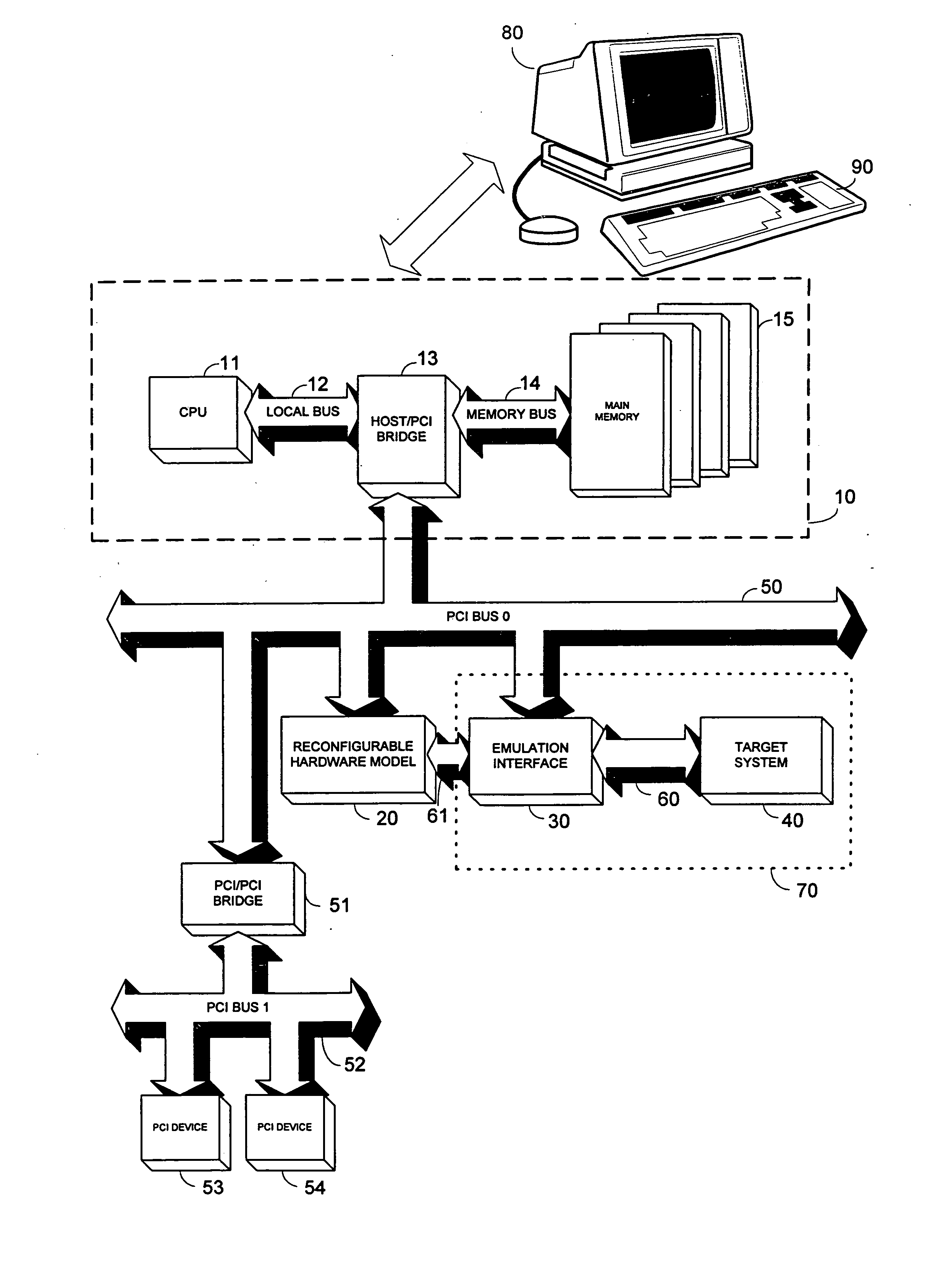
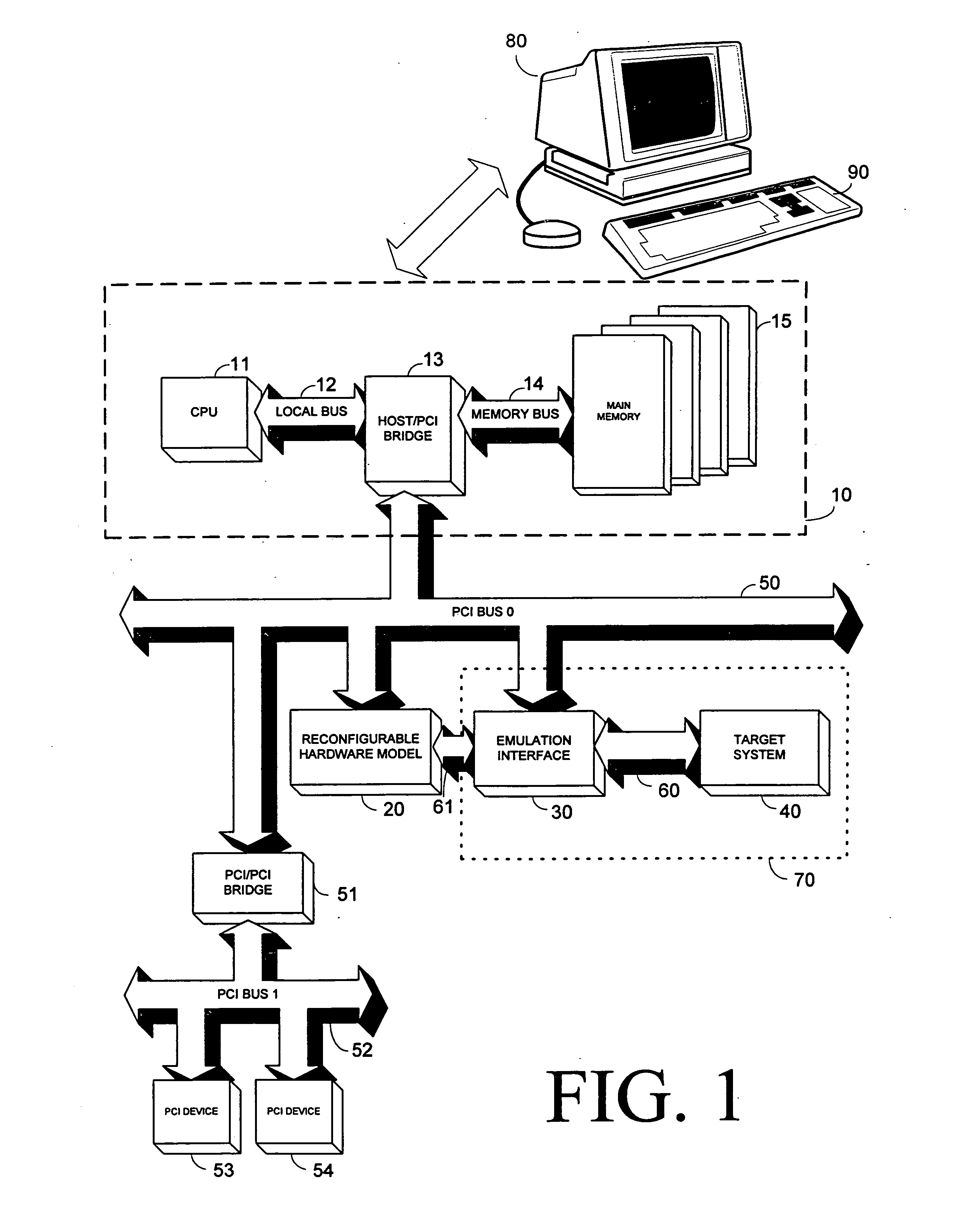
Patent Type
Patent Status
Application Year
Inventor
On a local area network, token passing is a channel access method where a signal called a token is passed between nodes to authorize that node to communicate. In contrast to polling access methods, there is no pre-defined "master" node. The most well-known examples are token ring and ARCNET, but there were a range of others, including FDDI (Fiber Distributed Data Interface), which was popular in the early to mid 1990s.
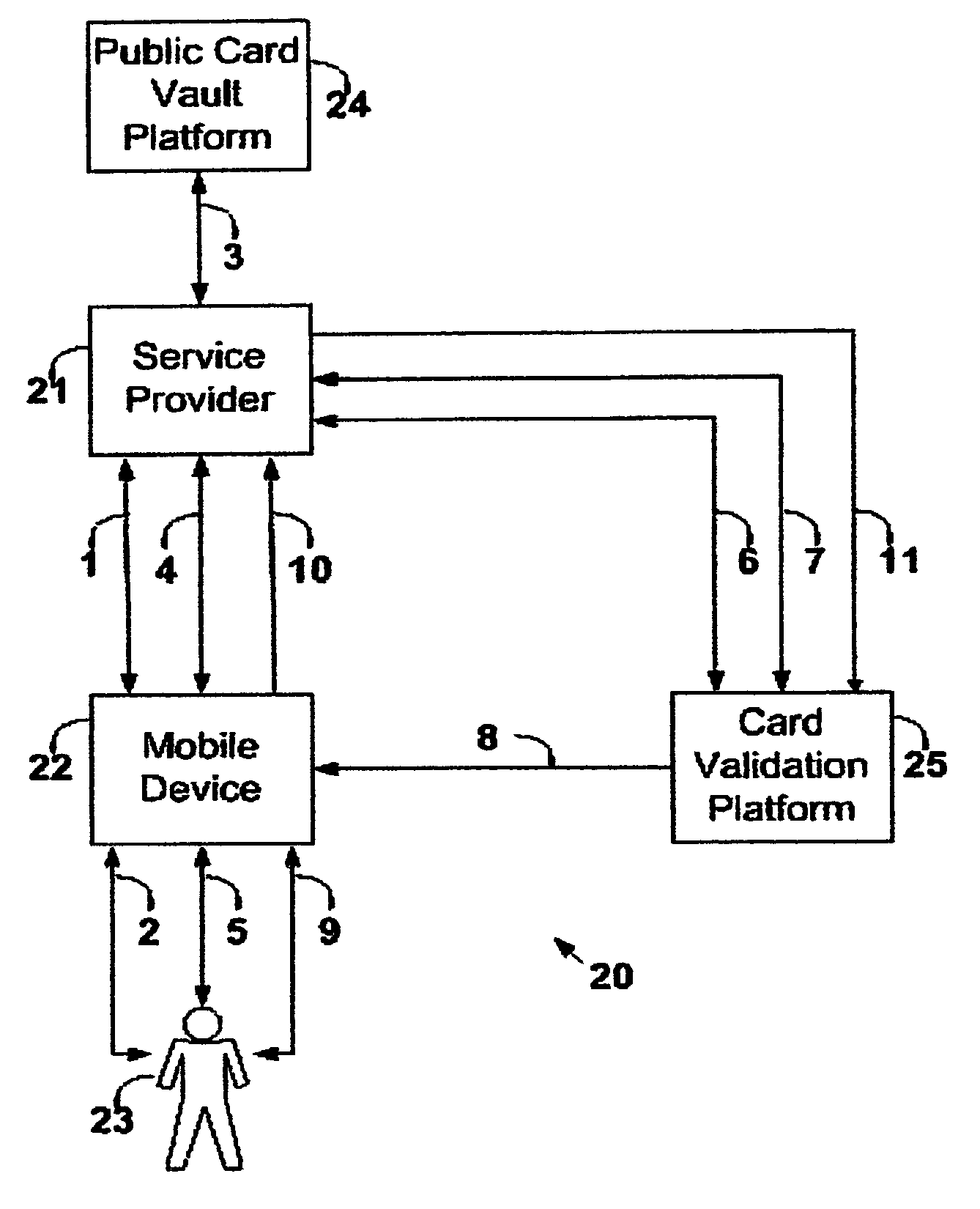
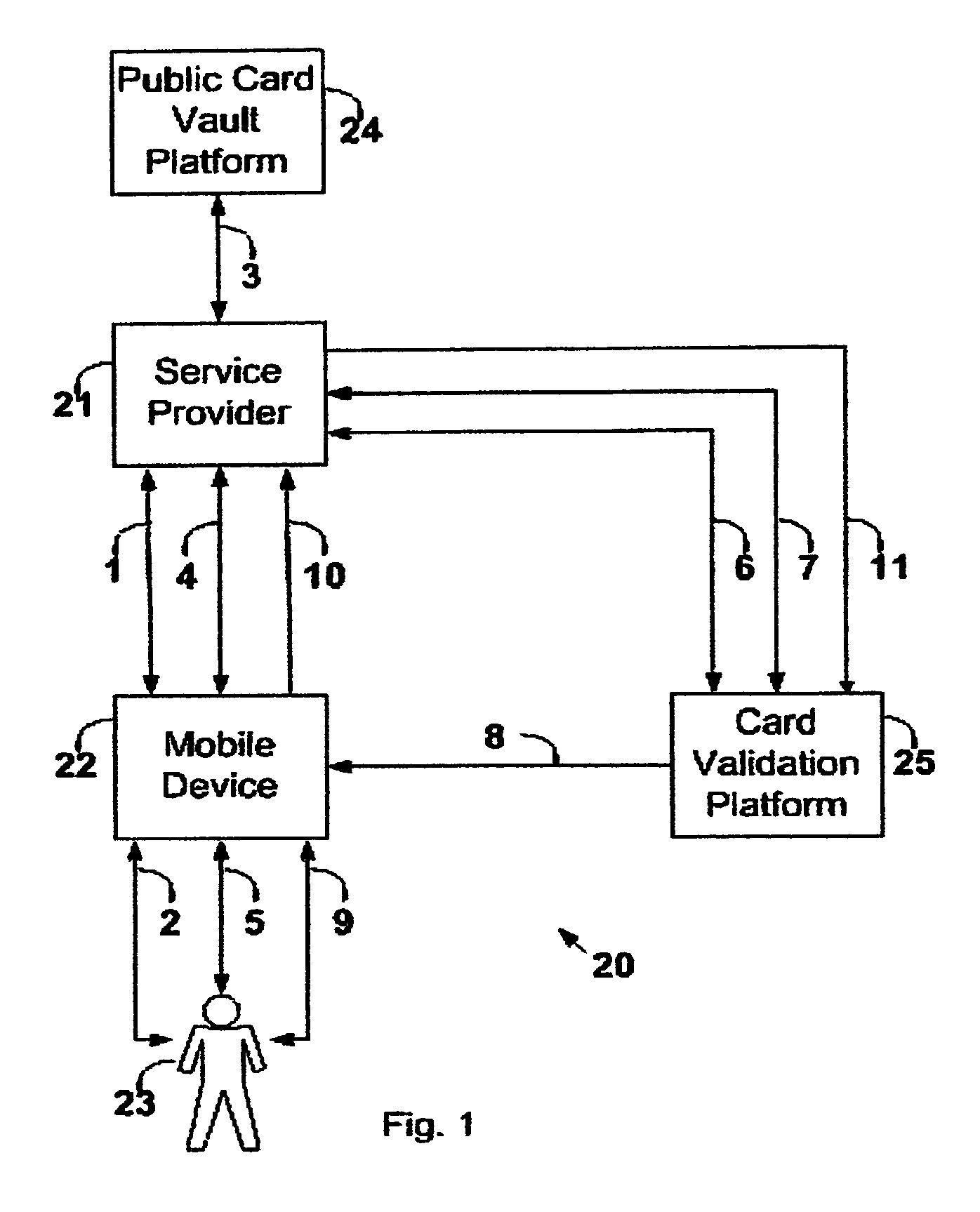
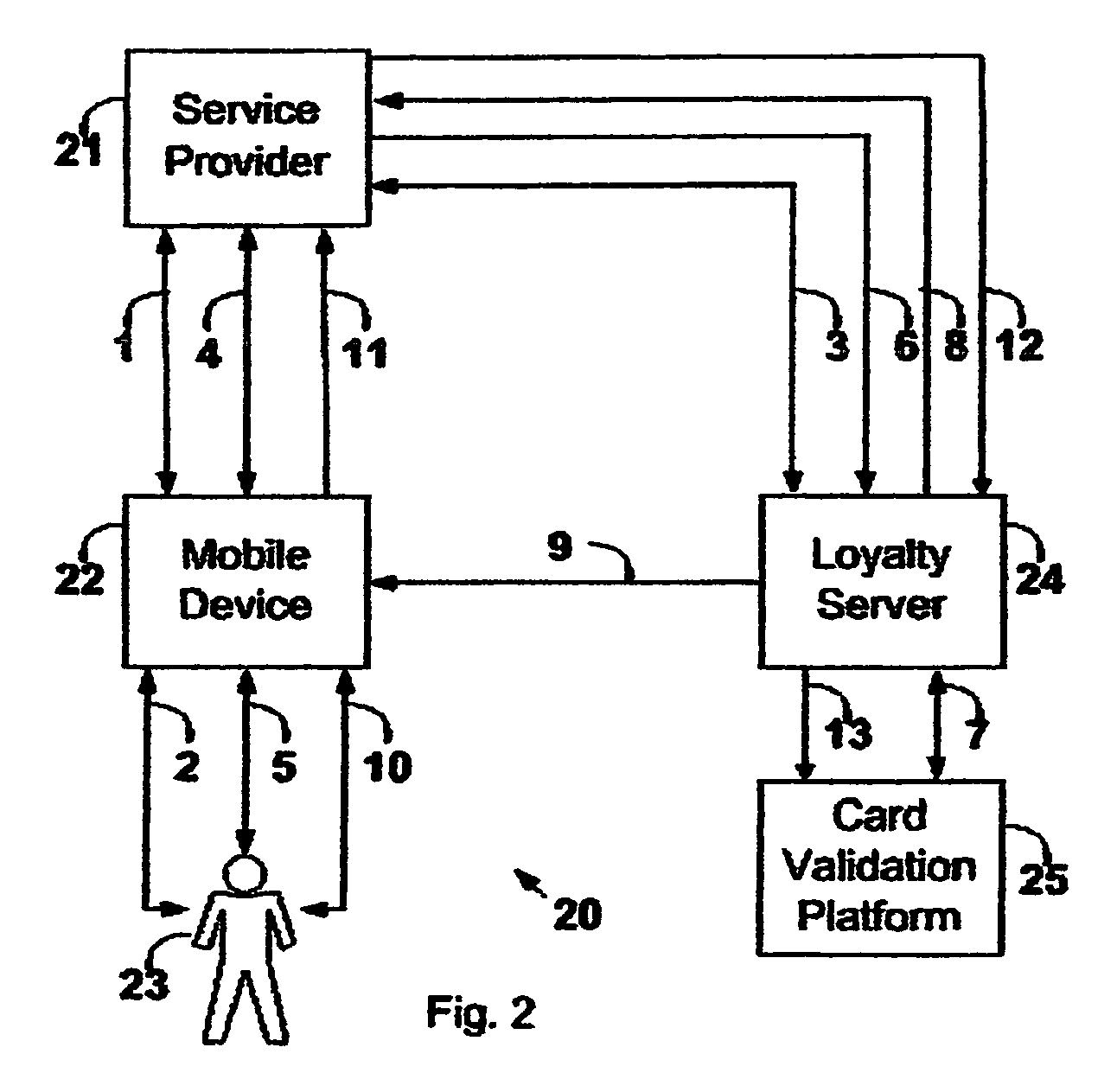
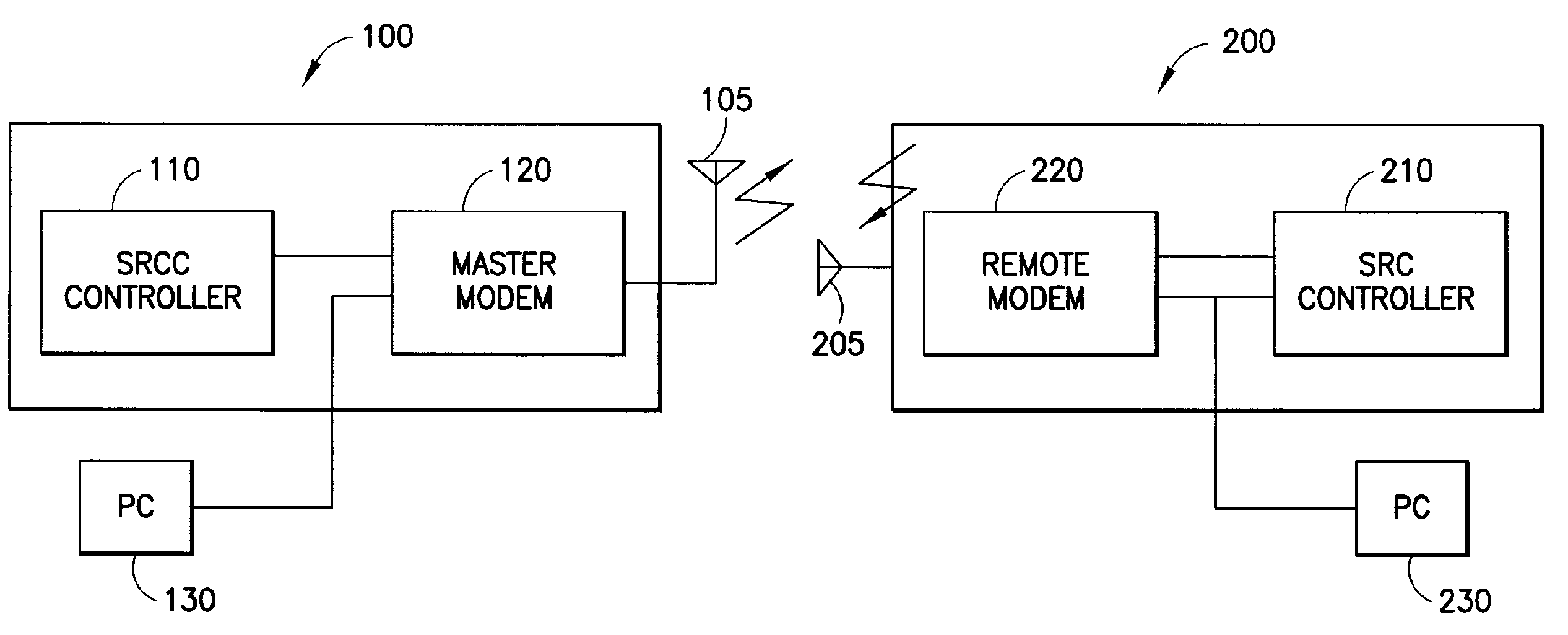
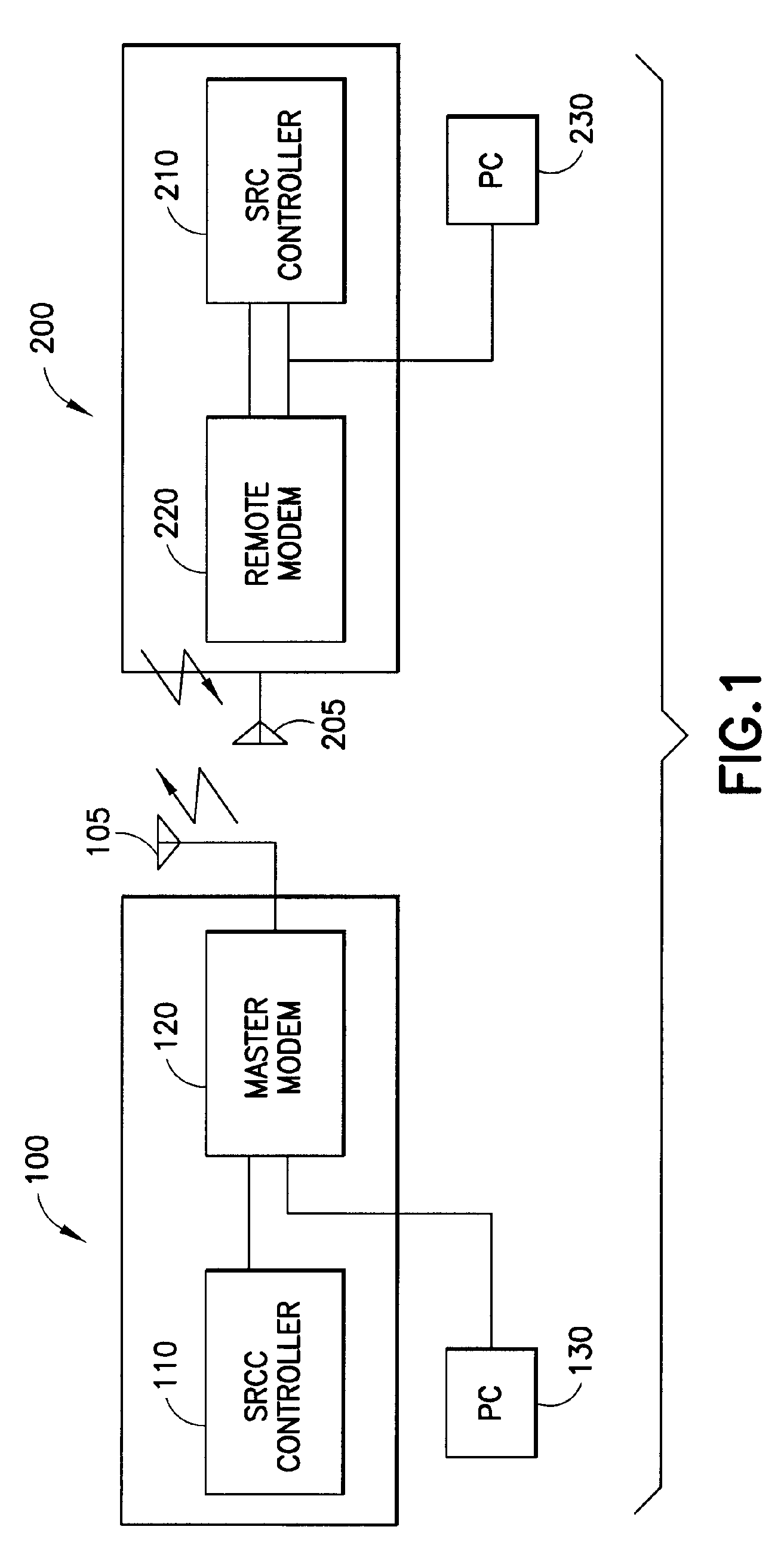
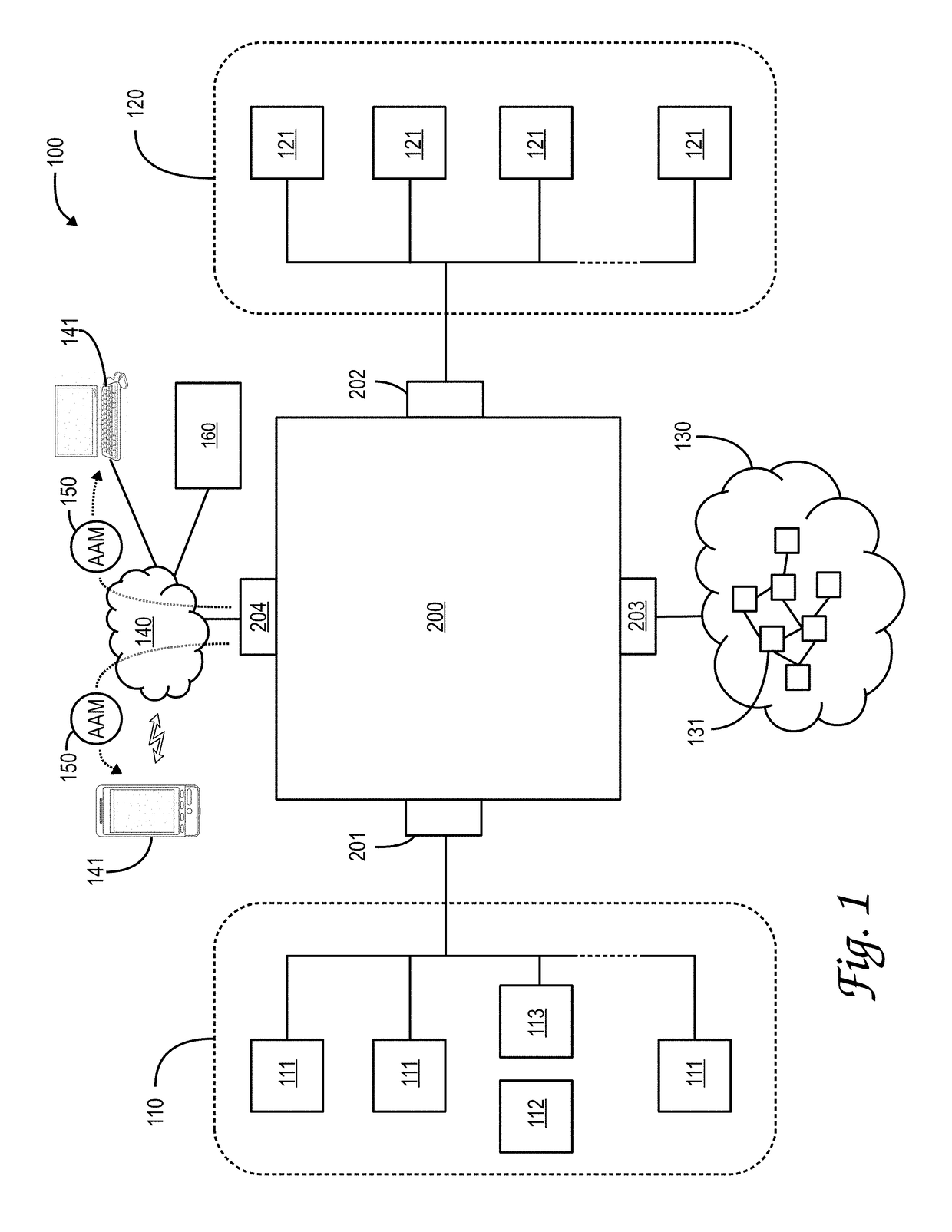
Wireless payment processing system
InactiveUS6988657B1Improve the security environmentImprove securityFinanceElectronic credentialsPrivate networkBluetooth
The transaction method is for secure payment by credit cards or debit cards for goods or services with the use or mobile devices. The payment authorization center delivers a public portion of the authorization token to the service provider via the existing communication channels and the private portion of the authorization token is delivered to the mobile device via SMS or USSD or e-mail short message. The mobile device delivers the private authorization token to the service provider via a private local network based on bluetooth, infrared or other short radio frequency based technology. The credit card or debit card number is never revealed and a temporary card token replaces it.
Owner:ROK MONICA LINDA
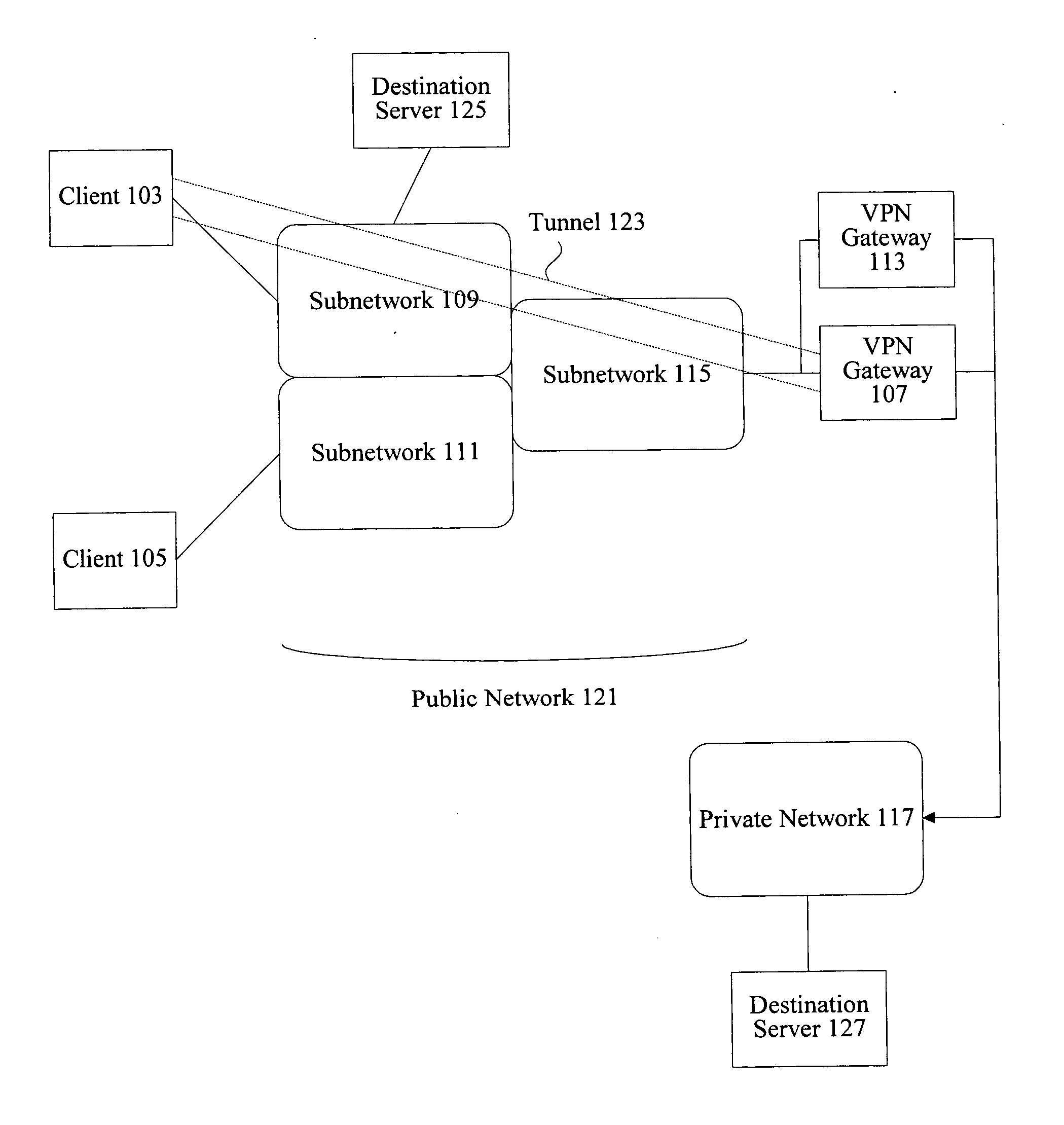
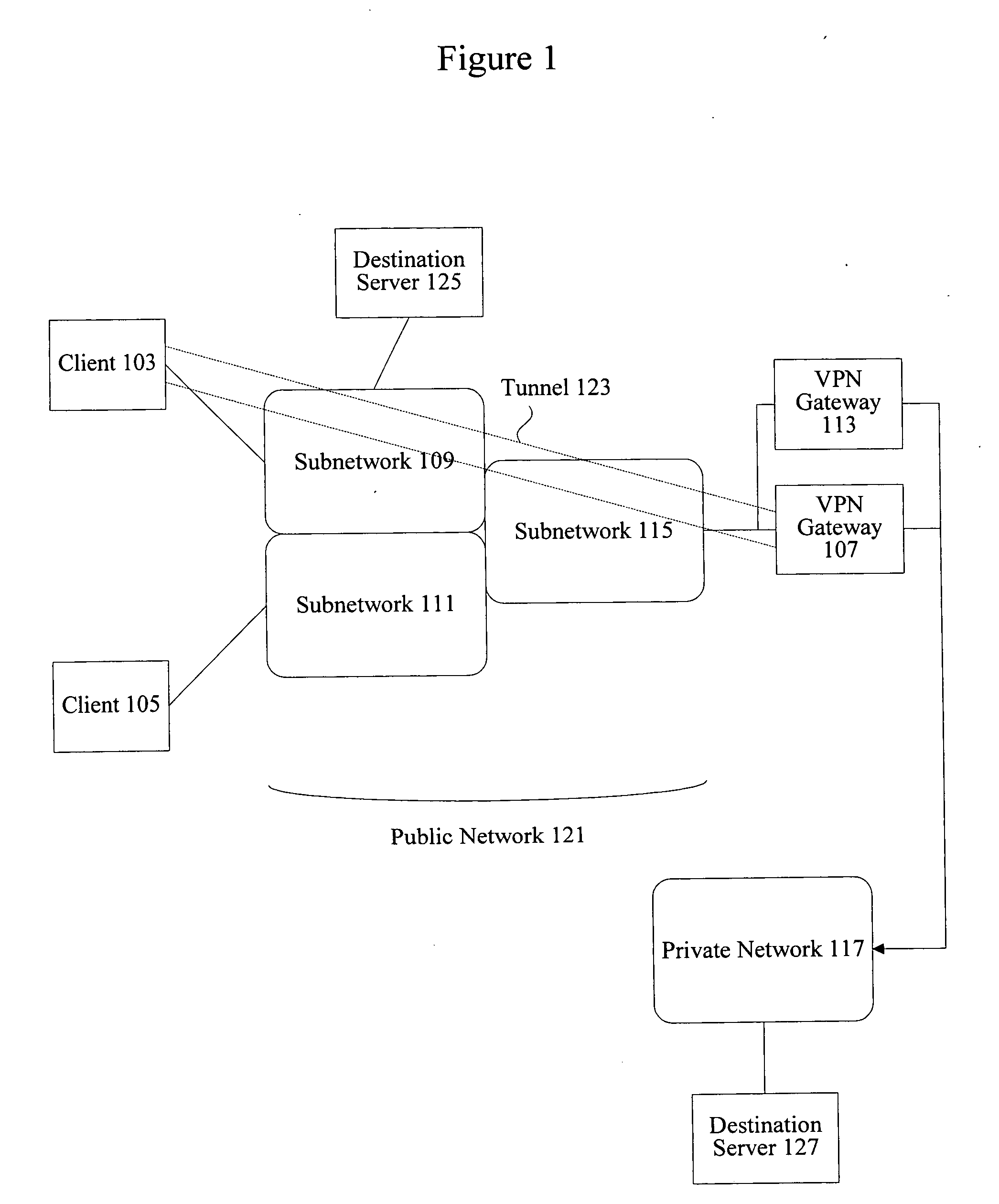
System and method for secure network connectivity
InactiveUS20070101405A1Accurate protectionConnection securityRandom number generatorsMemory loss protectionSecurity checkRemote computer
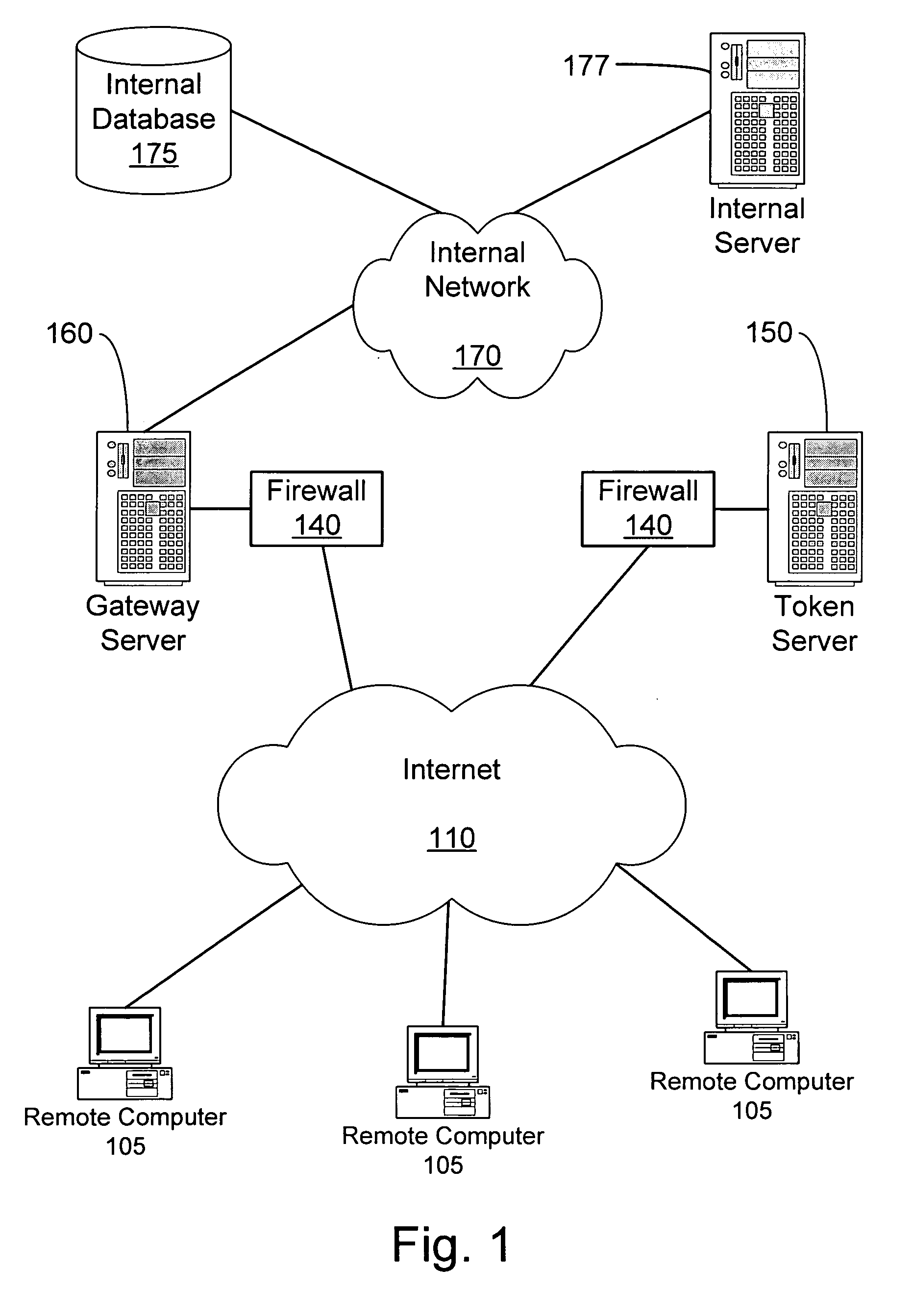
A system and method to ensure that a remote computer making a VPN connection complies with network security policies. Server-driven security checks may be configured to verify compliance with each access level before access is granted at that level. The security checks may be selected based at least according to the information received from the remote computer. After the server determines that the remote computer complies with the security policy for the requested access level, the server may pass a token to the remote computer, or may grant VPN access to the remote computer. If the remote computer does not comply with the security policy associated with the requested access level but is in compliance with a security policy corresponding to a lower access level, the server may grant the remote computer access to the lower access level.
Owner:BARCLAYS CAPITAL INC
Multistandard video decoder and decompression system for processing encoded bit streams including start codes and methods relating thereto
InactiveUS7095783B1Increase flexibilityPicture reproducers using cathode ray tubesPicture reproducers with optical-mechanical scanningComputer hardwareVideo decoder
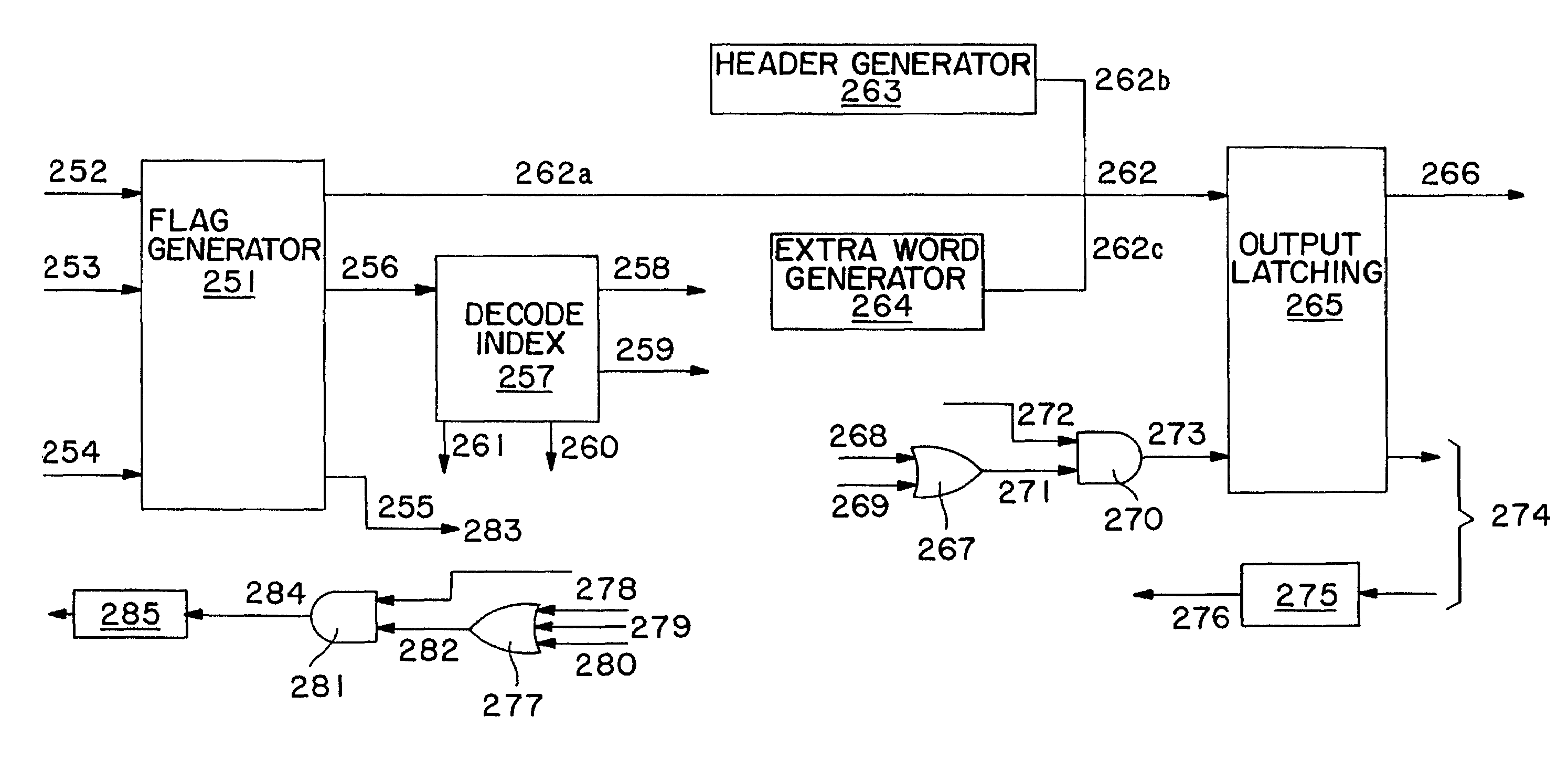
A pipeline video decoder and decompression system handles a plurality of separately encoded bit streams arranged as a single serial bit stream of digital bits and having separately encoded pairs of control codes and corresponding data carried in the serial bit stream. The pipeline system employs a plurality of interconnected stages to decode and decompress the single bit stream, including a start code detector. When in a search mode, the start code detector searches for a specific start code corresponding to one of multiple compression standards. The start code detector responding to the single serial bit stream generates control tokens and data tokens. A respective one of the tokens includes a plurality of data words. Each data word has an extension bit which indicates a presence of additional words therein. The data words are thereby unlimited in number. A token decode circuit positioned in certain of the stages recognizes certain of the tokens as control tokens pertinent to that stage and passes unrecognized control tokens to a succeeding stage. A reconfigurable decode and parser processing means positioned in certain of the stages is responsive to a recognized control token and reconfigures a particular stage to handle an identified data token. Methods relating to the decoder and decompression system include processing steps relating thereto.
Owner:CHARTOLEAUX
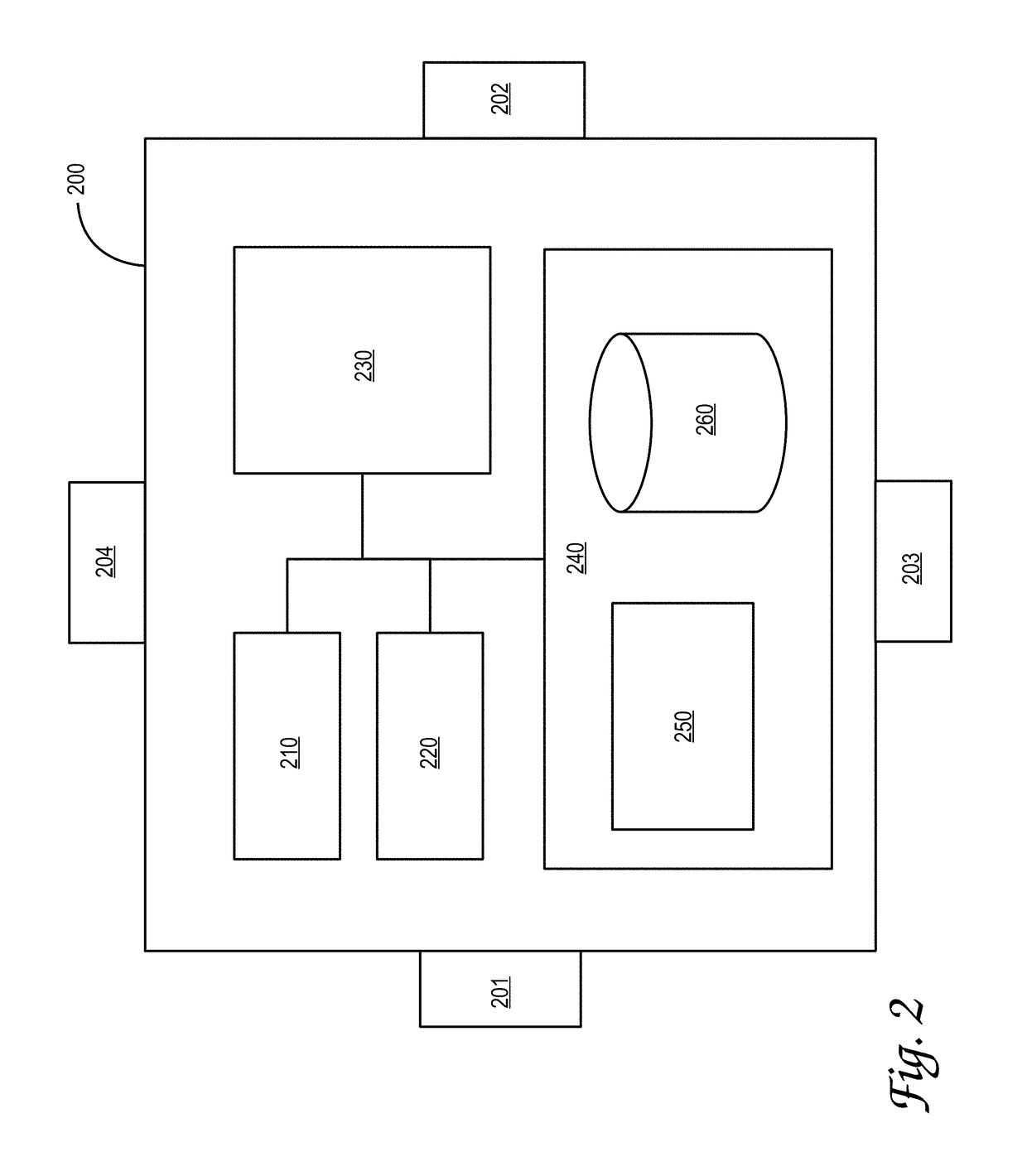
Profile framework for token processing system
ActiveUS20070288745A1Key distribution for secure communicationUser identity/authority verificationHandling systemClient-side
Embodiments of the present invention provide a profile framework for handling enrollment requests. In particular, when a token processing system receives an enrollment request, it selects an applicable profile based on information in the request. The profile may indicate a variety of parameters for fulfilling the enrollment request, such as the locations of the applicable certificate authority, token key service, and the like. The profile may also indicate items, such as the number of keys to generate on a token, a token label, and connection information to securely communicate with other components and the client making the enrollment request.
Owner:RED HAT
Inter-chip communication system
InactiveUS20050102125A1Decrease in performanceMultiple digital computer combinationsCAD circuit designData packCommunications system
Owner:CADENCE DESIGN SYST INC
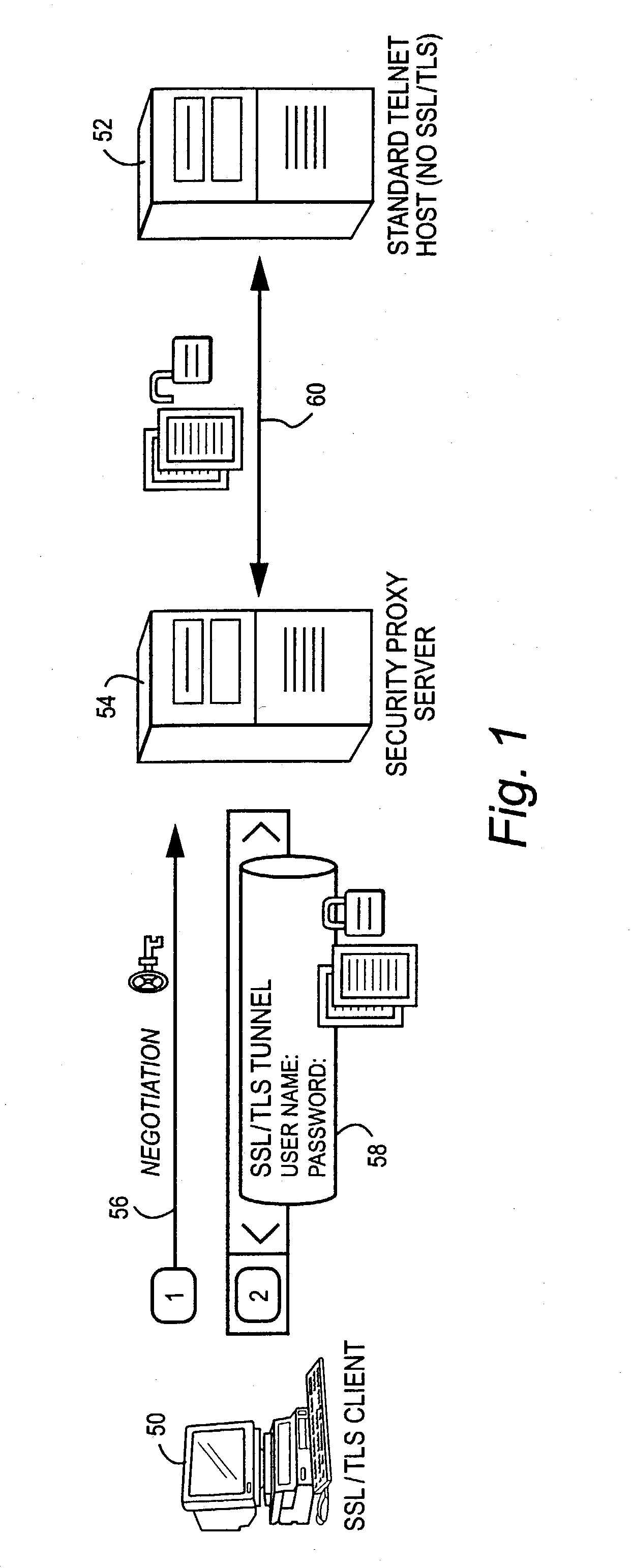
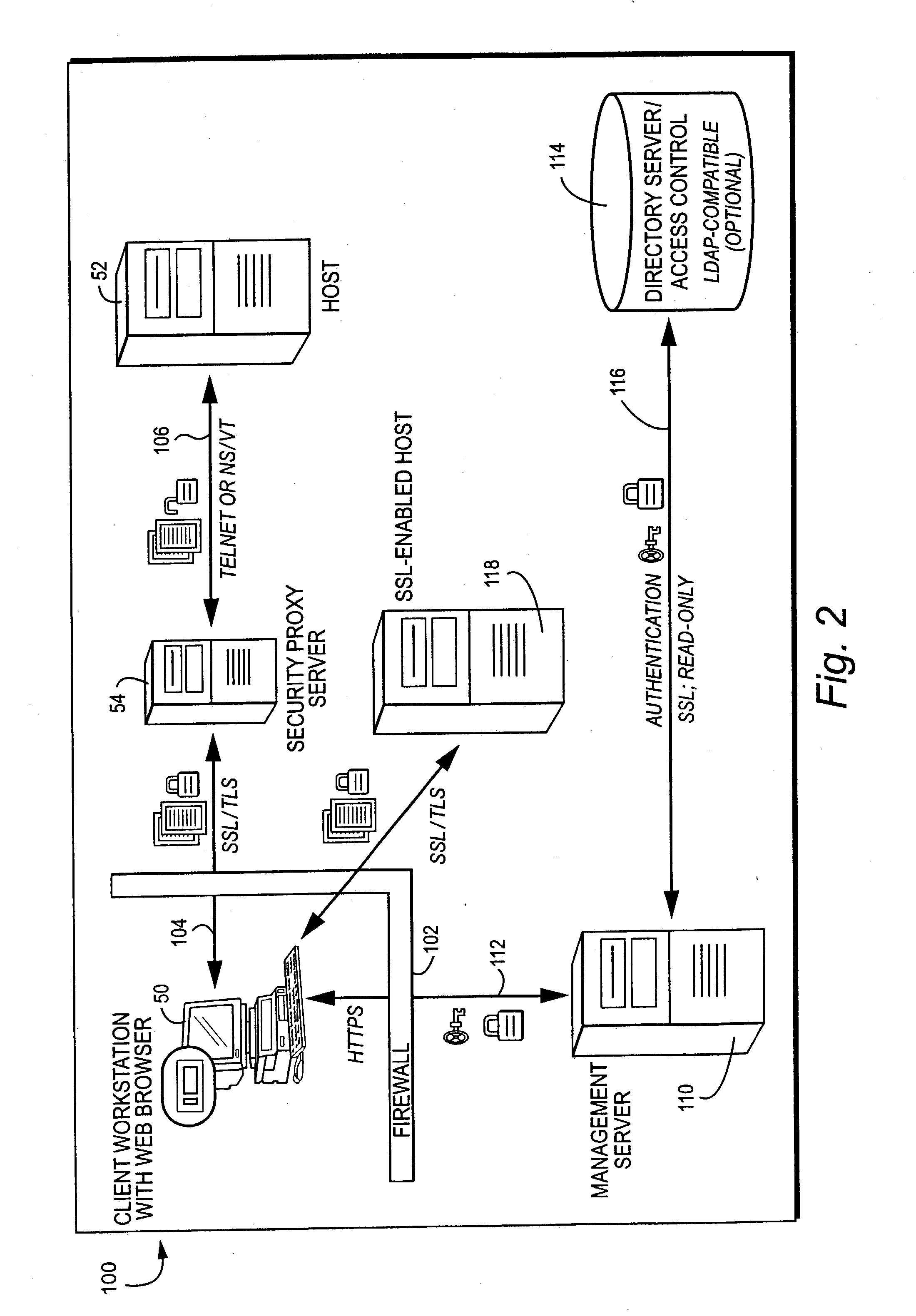
Proxy server security token authorization
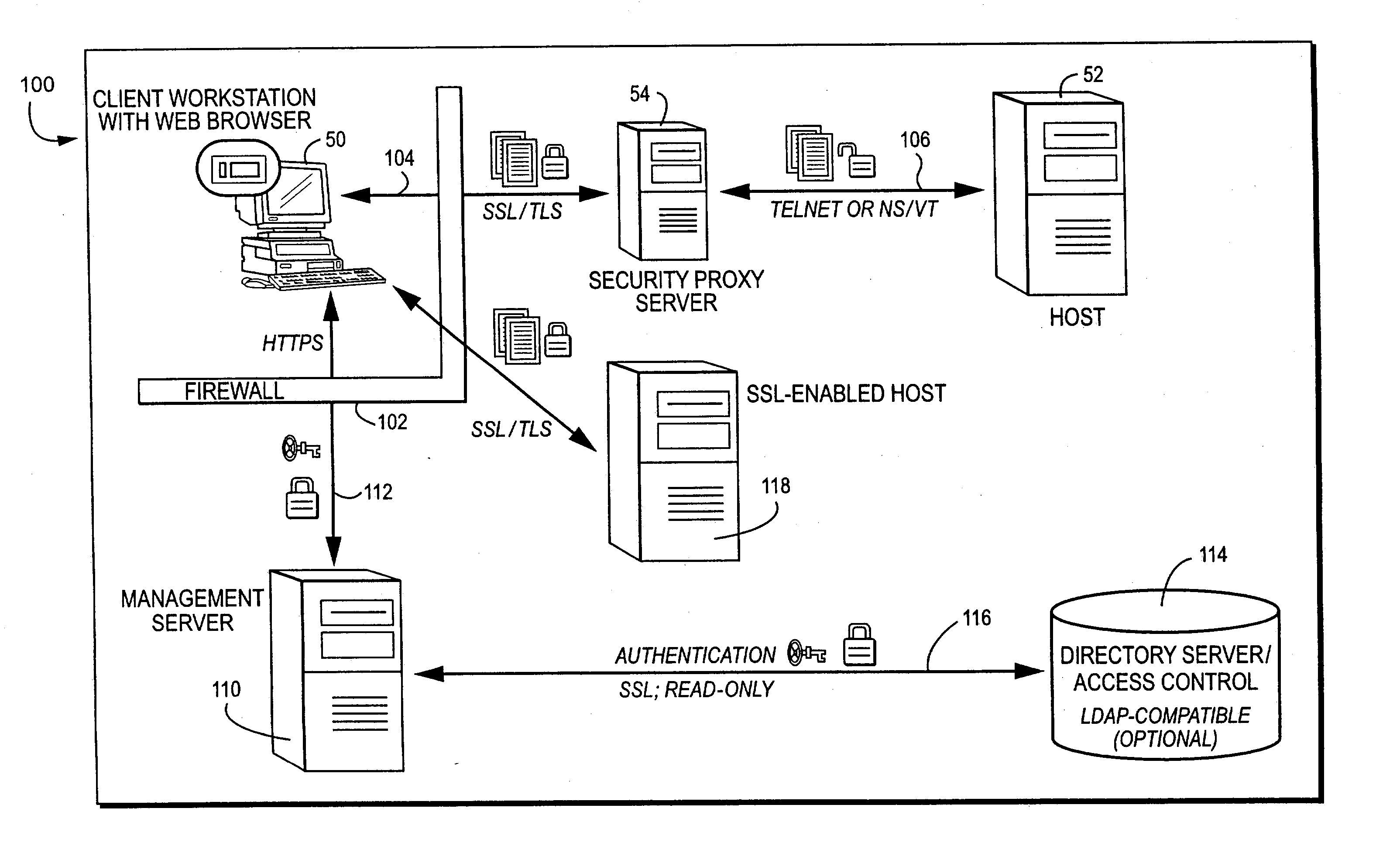
ActiveUS20050005133A1Computing securityDigital data processing detailsComputer security arrangementsSecure communicationDigital signature
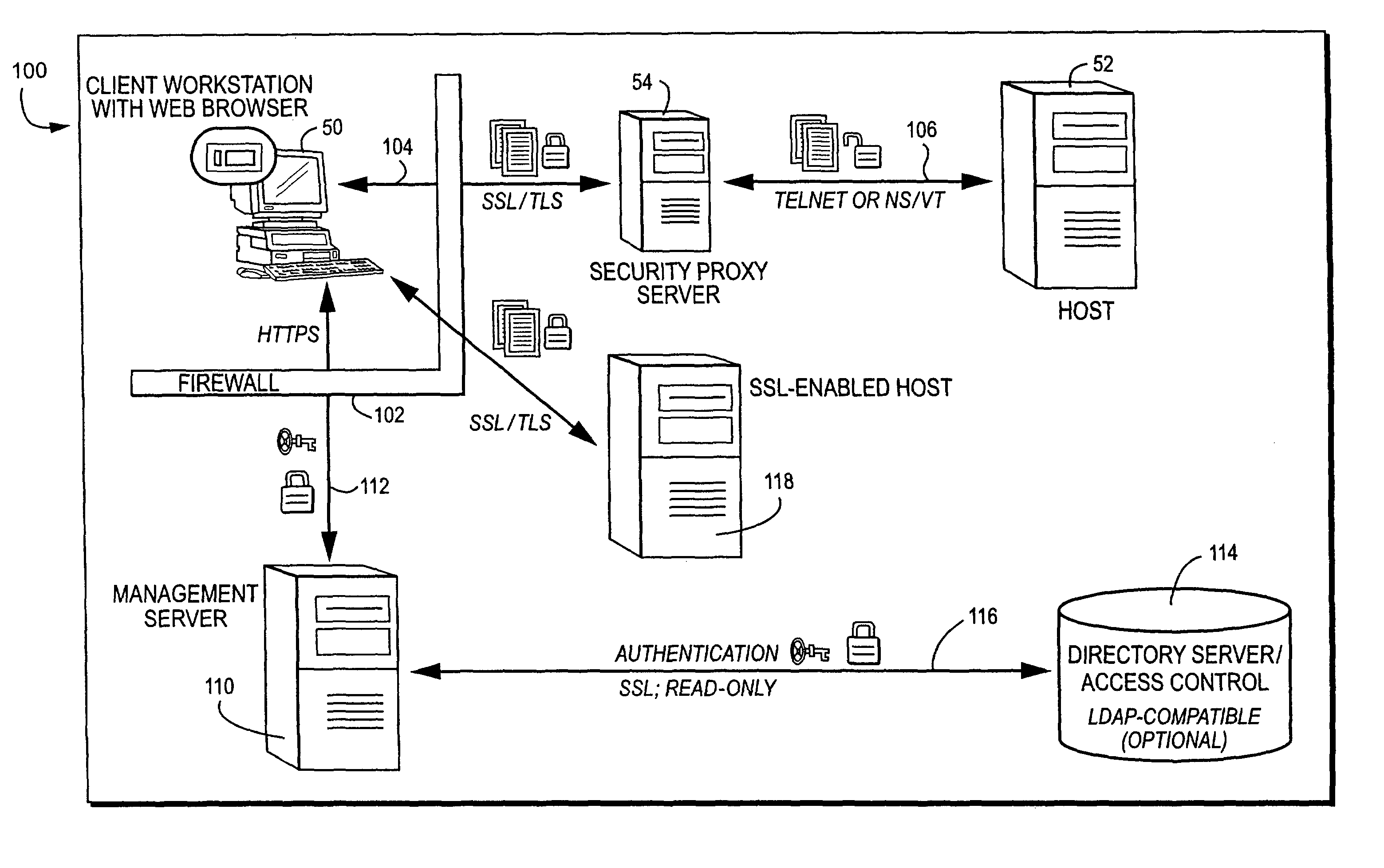
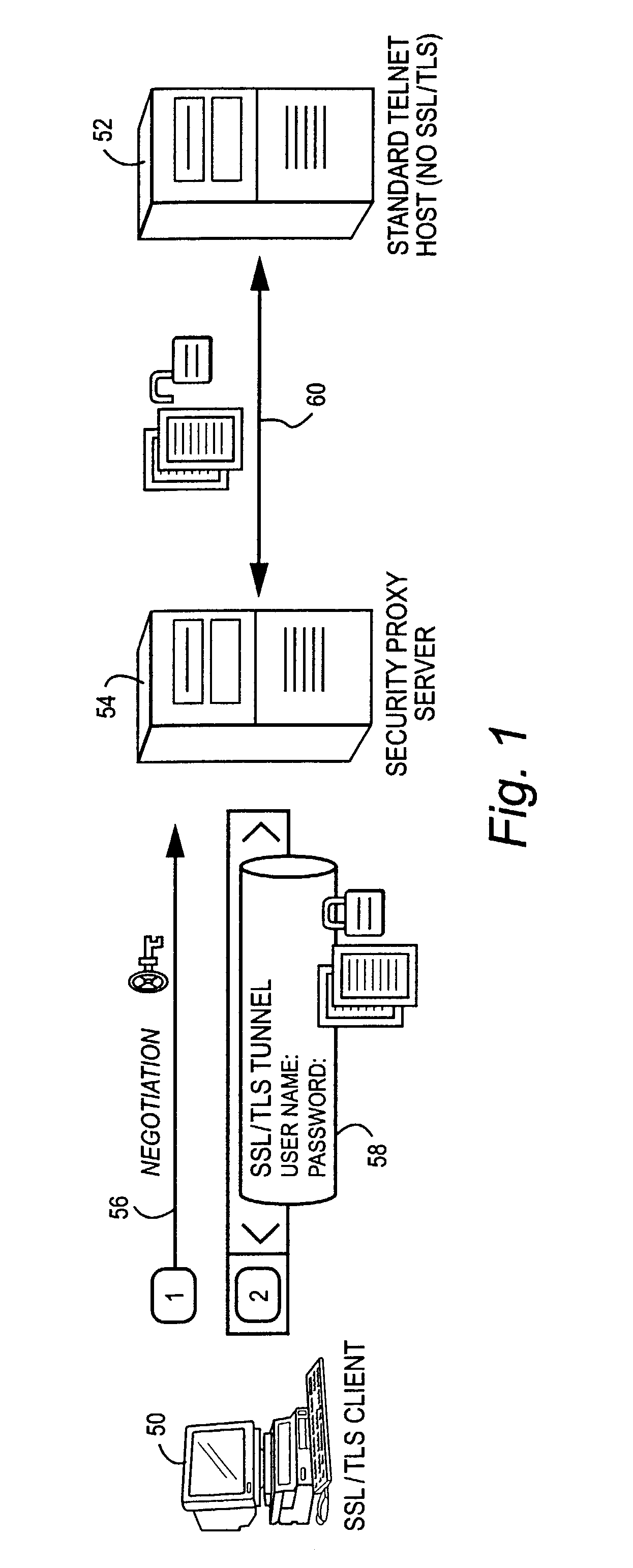
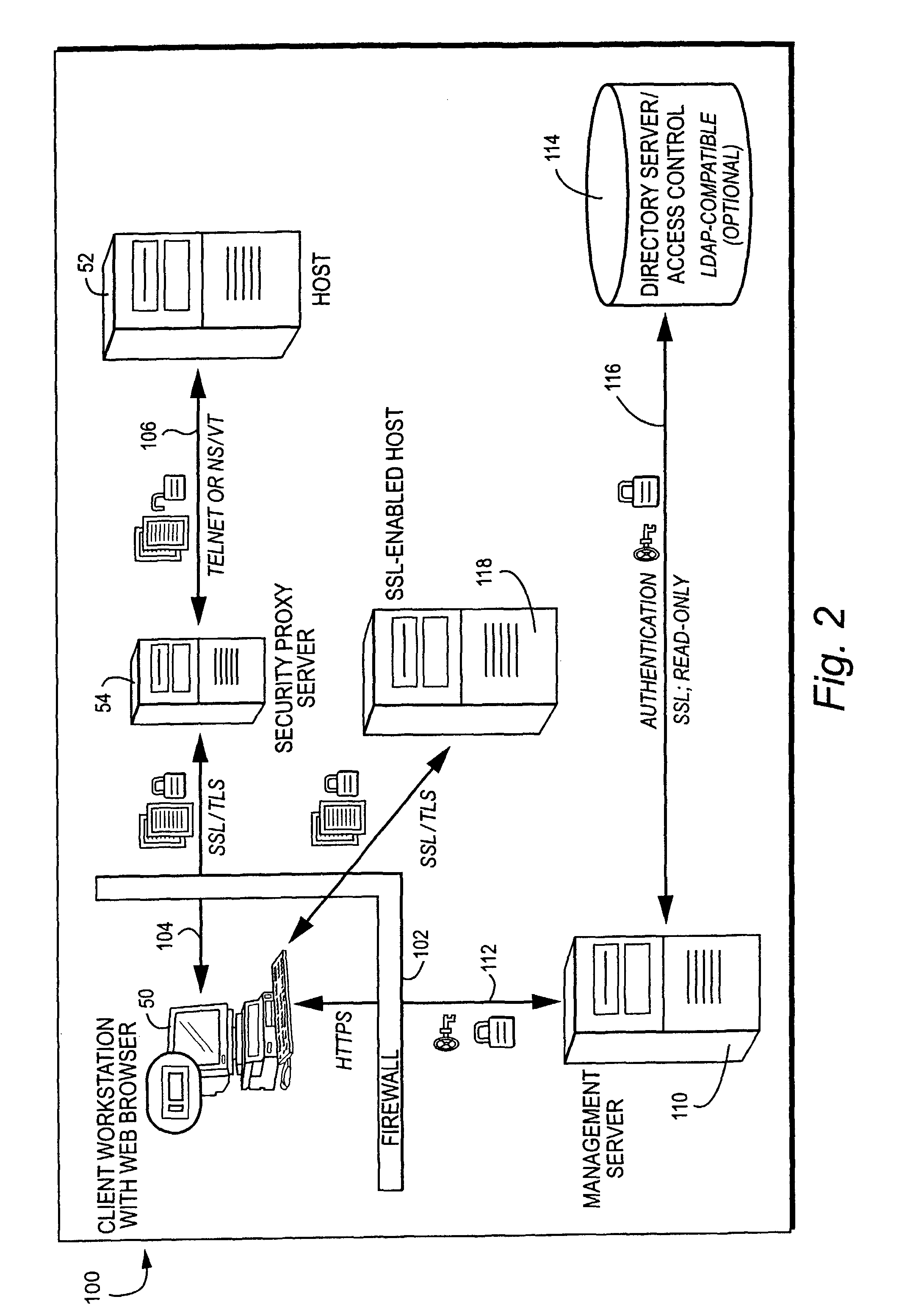
A management server manufactures a secure, tamper-resistant token for a particular user specifying the permissions and authorizations that user possesses. The token may be in the form of a digitally-signed message specifying, for example, a particular computer and associated port number that the user is permitted to access. The management server delivers the token to the user, preferably over a secure communications session. When challenged, the user presents the secure token to the security proxy server. The security proxy server examines the token to be sure it is authentic and has not be tampered with, and then extracts information contained in the token to determine the user's authorization to access a particular computer, particular port number and / or other resource. The security proxy server then establishes authorized communication with the authorized computing resource based on the information contained in the user's token, and thereafter may act in one embodiment as essentially a passthrough or proxy for permitting the user to access and communicate with the resource.
Owner:ATTACHMATE
Inter-chip communication system
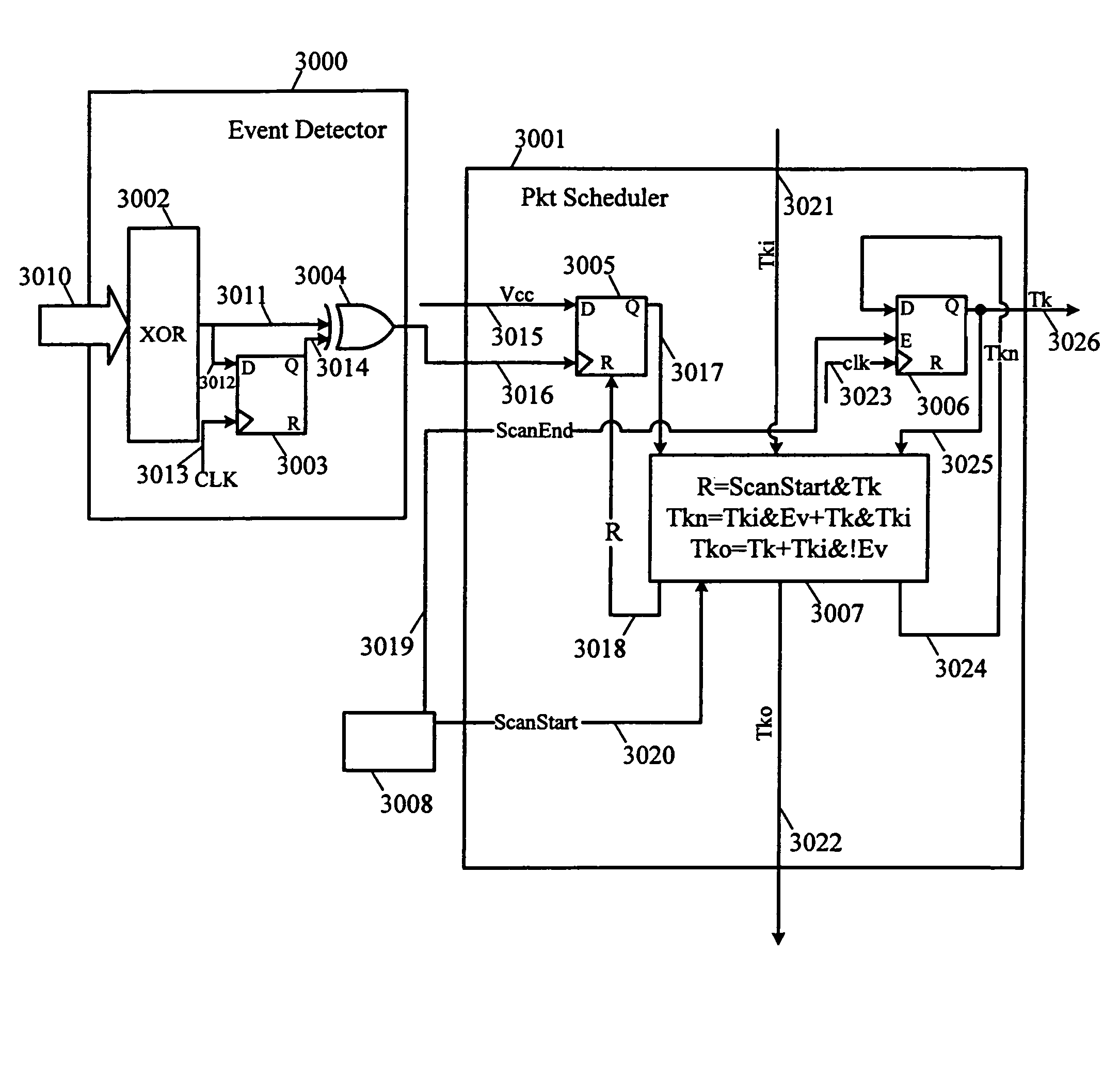
InactiveUS7512728B2Decrease in performanceMultiple digital computer combinationsCAD circuit designCommunications systemPacket scheduling
The complexity of user designs, the limited capacity of FPGA chips, and the limited number of chip pinouts have resulted in the development of inter-chip communication technology that necessitates the transfer of a large amount of data across a limited number of pins in the shortest amount of time. The inter-chip communication system transfers signals across FPGA chip boundaries only when these signals change values. Thus, no cycles are wasted and every event signal has a fair chance of achieving communication across chip boundaries. The inter-chip communication system includes a series of event detectors that detect changes in signal values and packet schedulers which can then schedule the transfer of these changed signal values to another designated chip. Working with a plurality of signal groups that represents signals at the separated connections, the event detector detects events (or changes in signal values). When an event has been detected, the event detector alerts the packet scheduler. The packet scheduler employs a token ring scheme as follows. When the packet scheduler receives a token and detects an event, the packet scheduler “grabs” the token and schedules the transmission of this packet in the next packet cycle. If, however, the packet scheduler receives the token but does not detect an event, it will pass the token to the next packet scheduler. At the end of each packet cycle, the packet scheduler that grabbed the token will pass the token to the next logic associated with another packet.
Owner:CADENCE DESIGN SYST INC
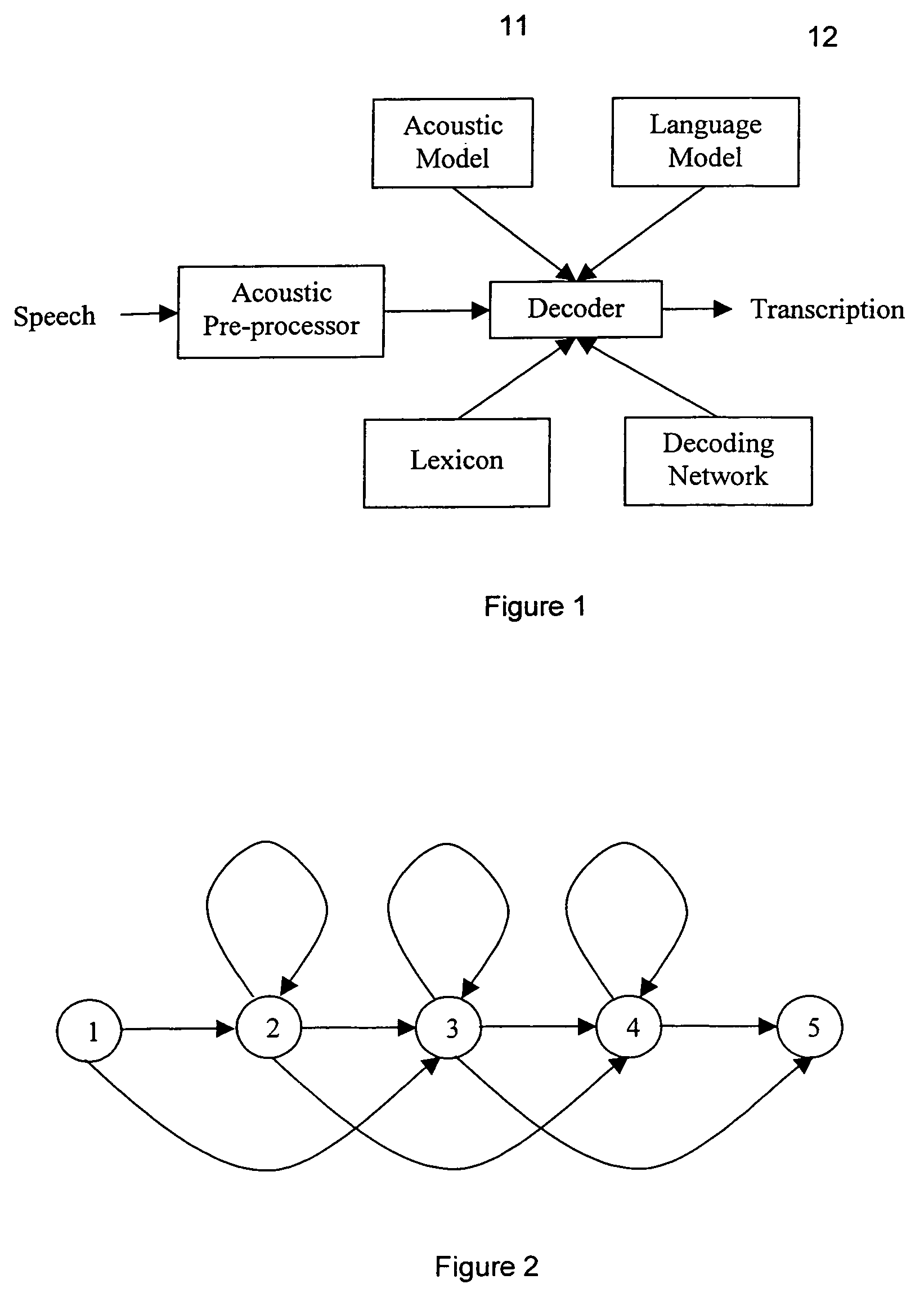
Speech recognition system and technique
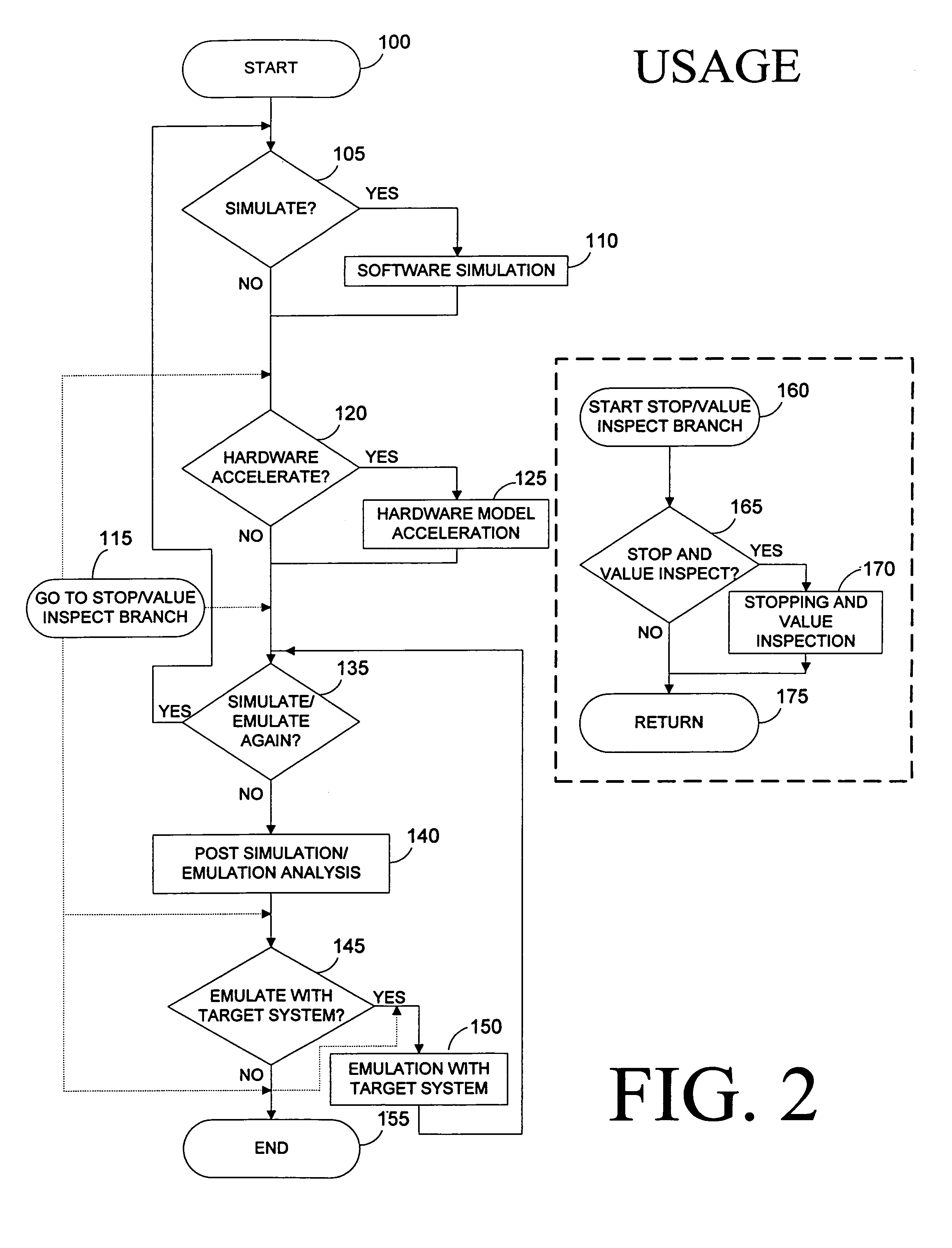
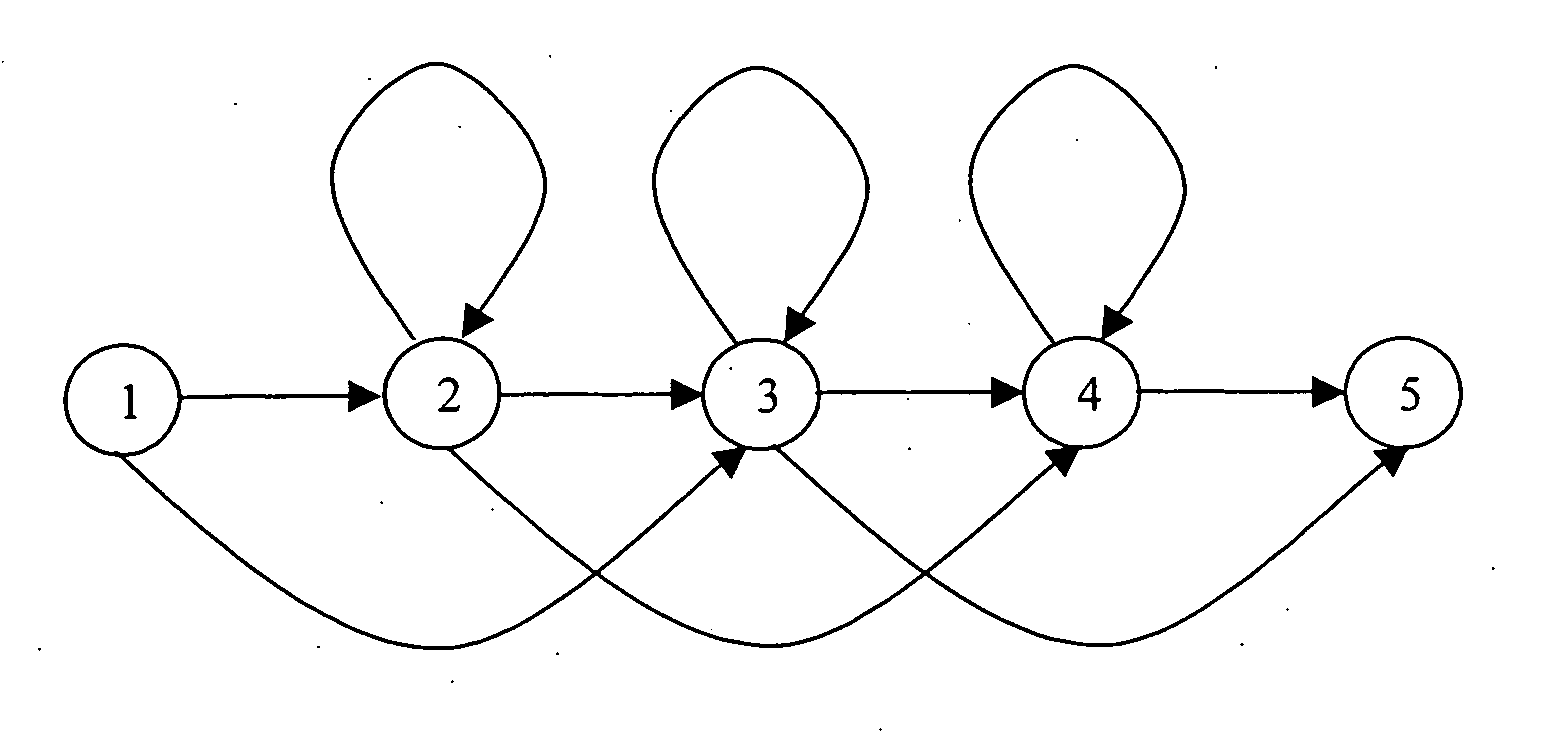
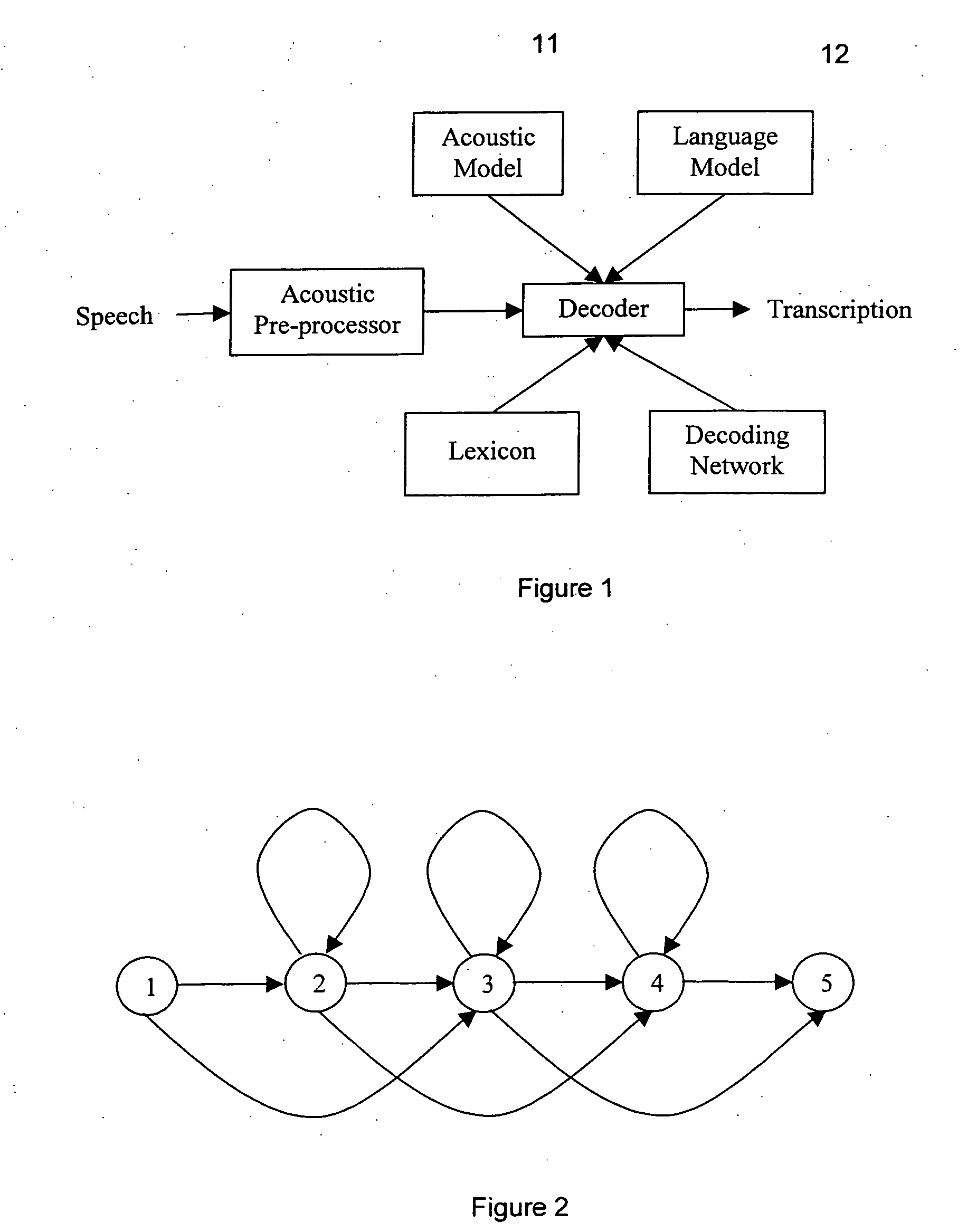
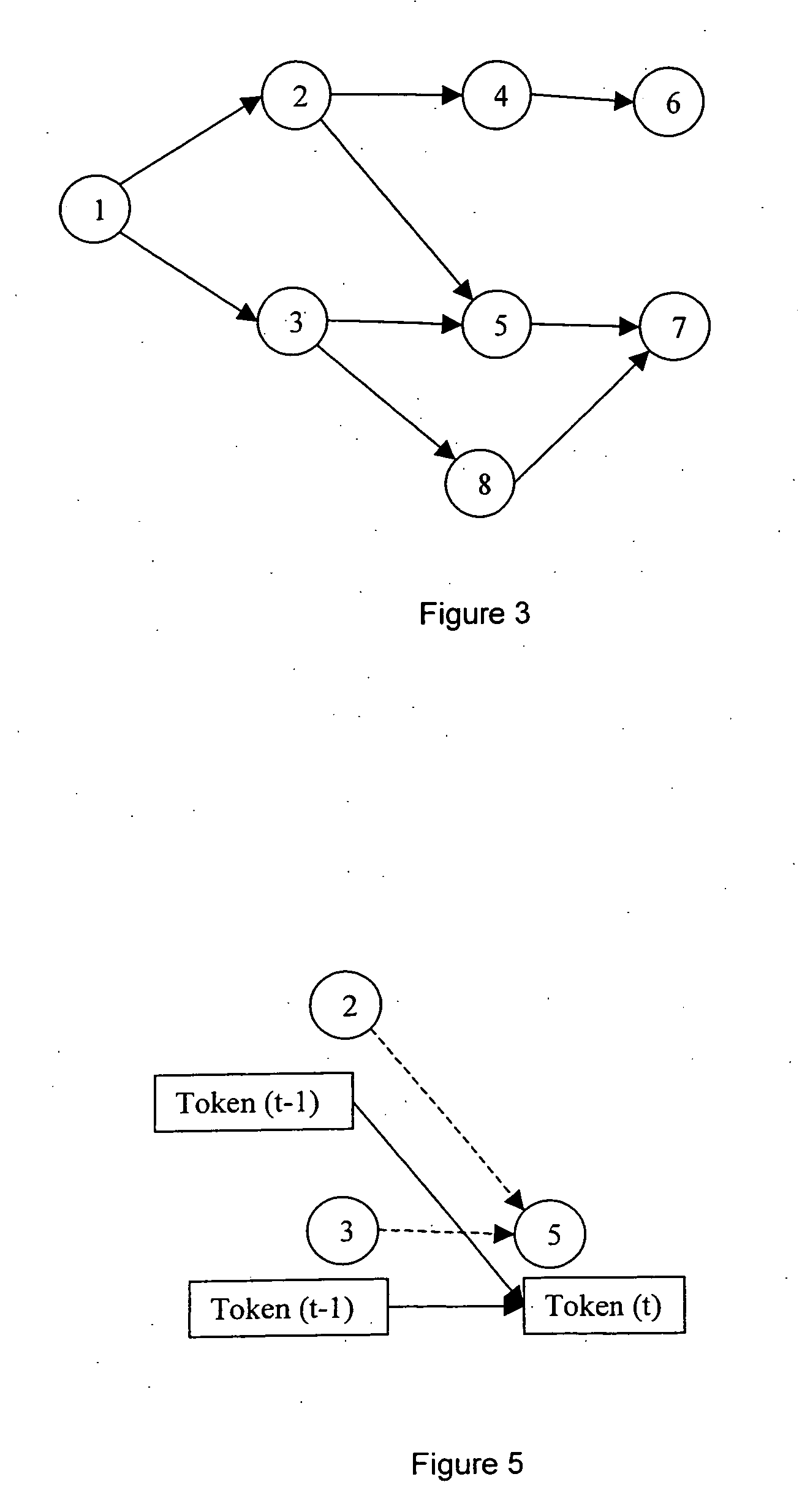
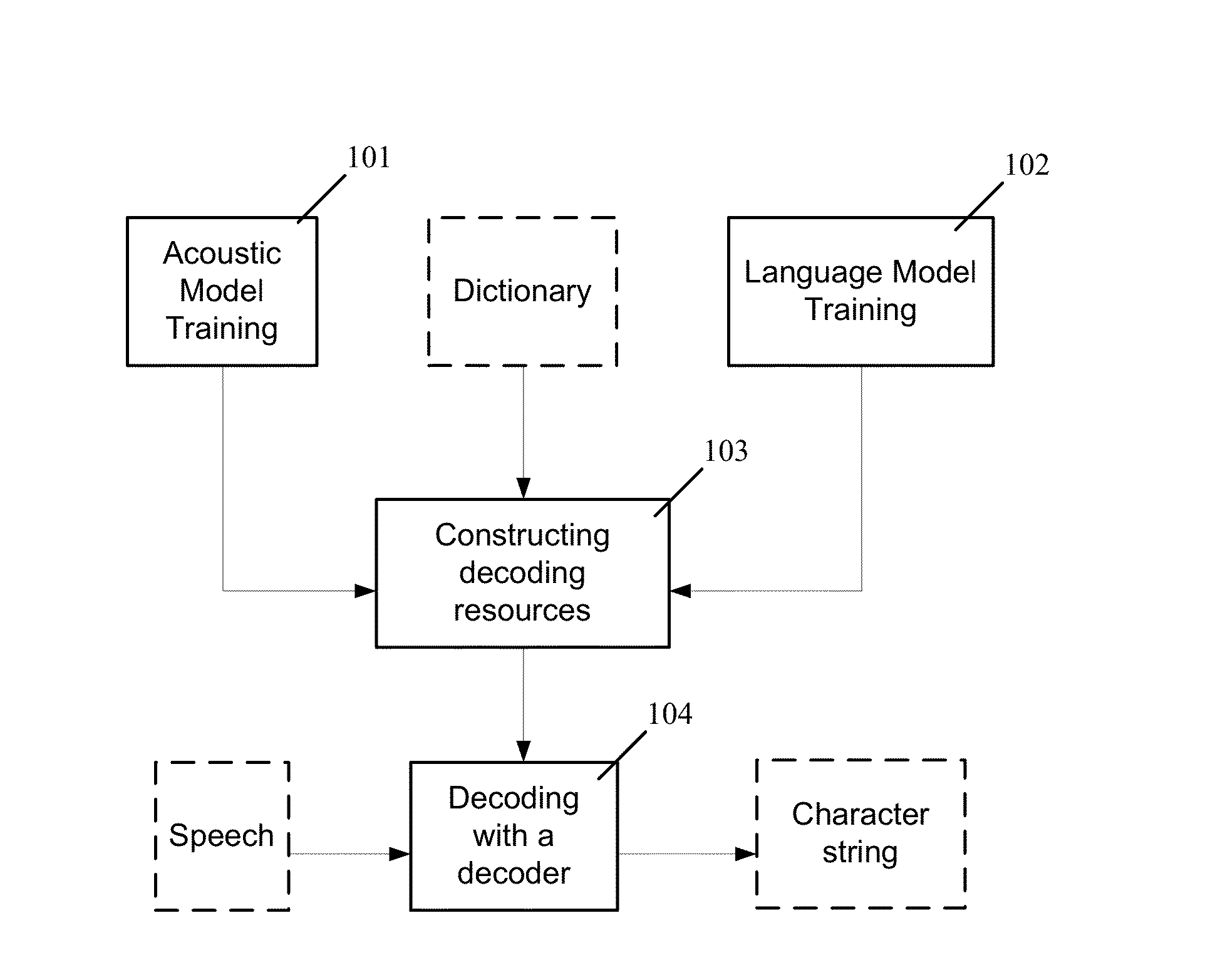
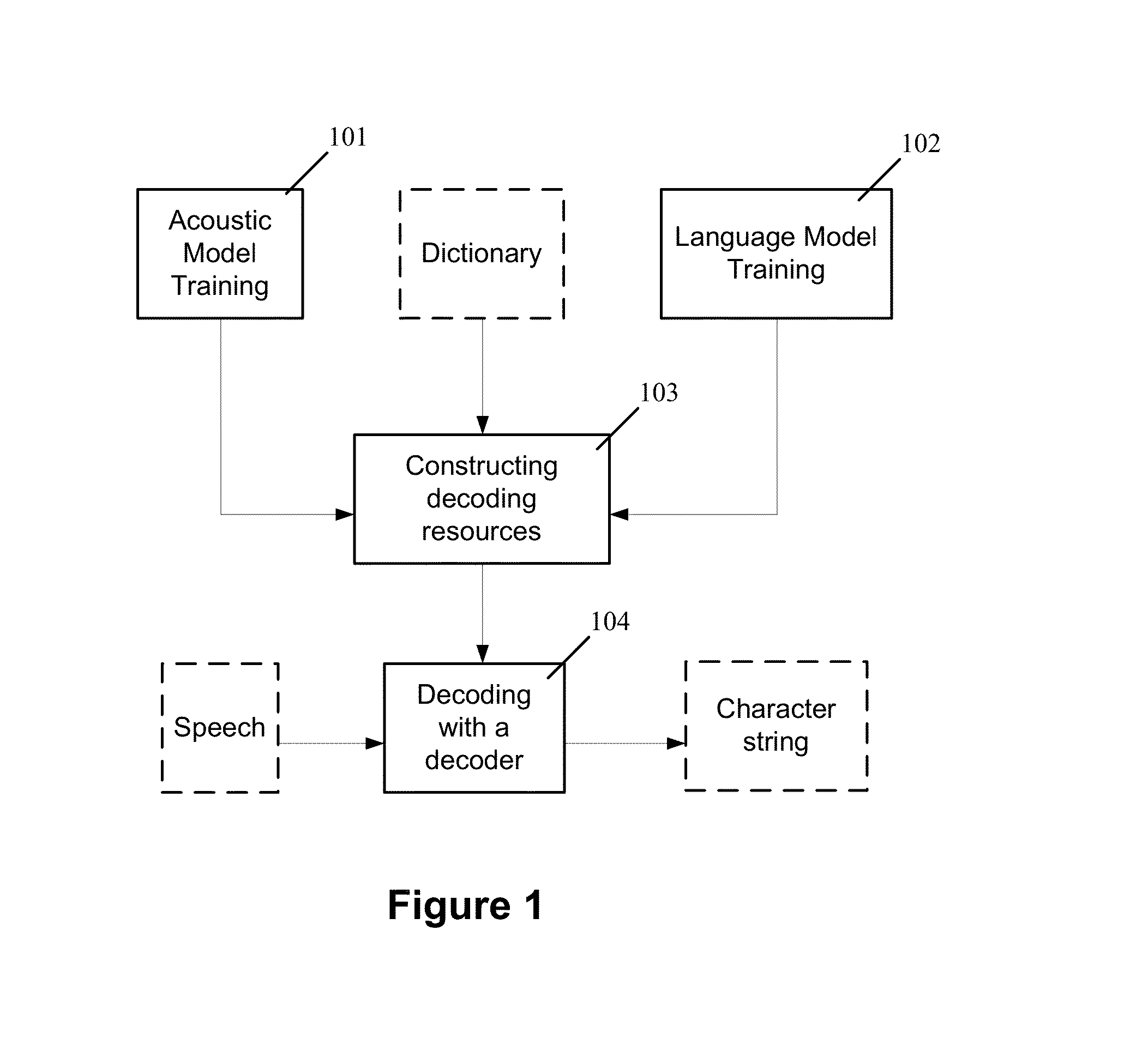
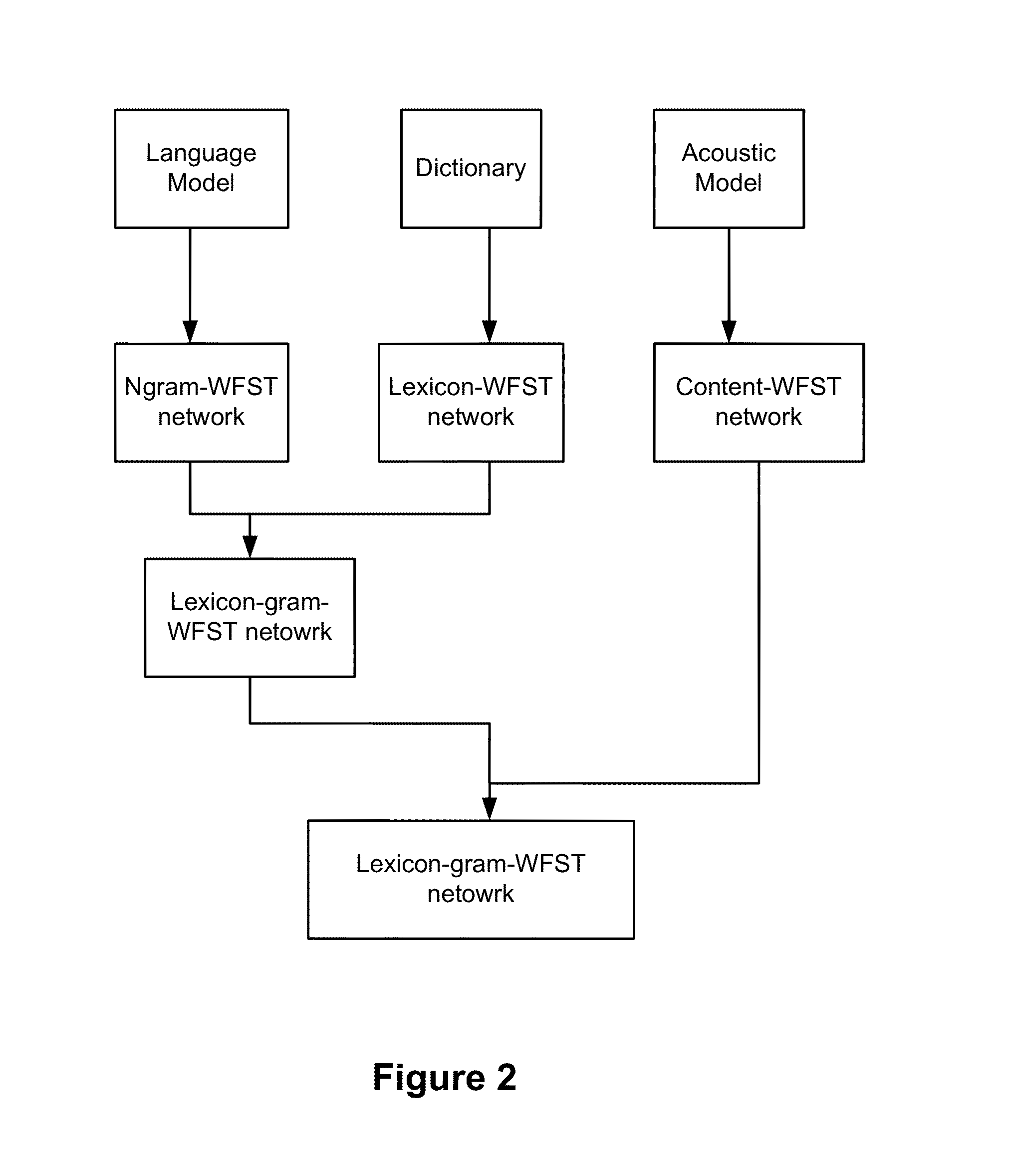
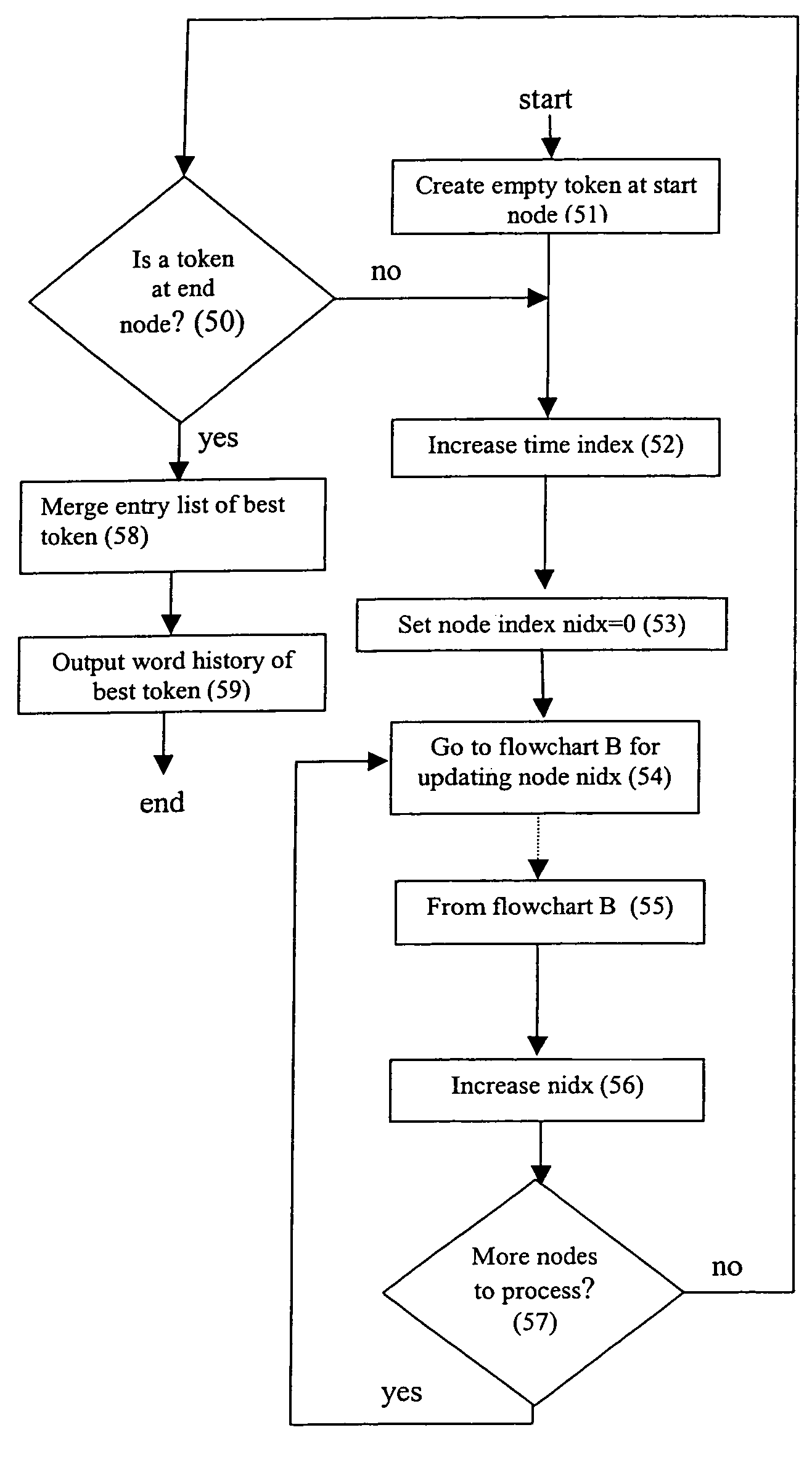
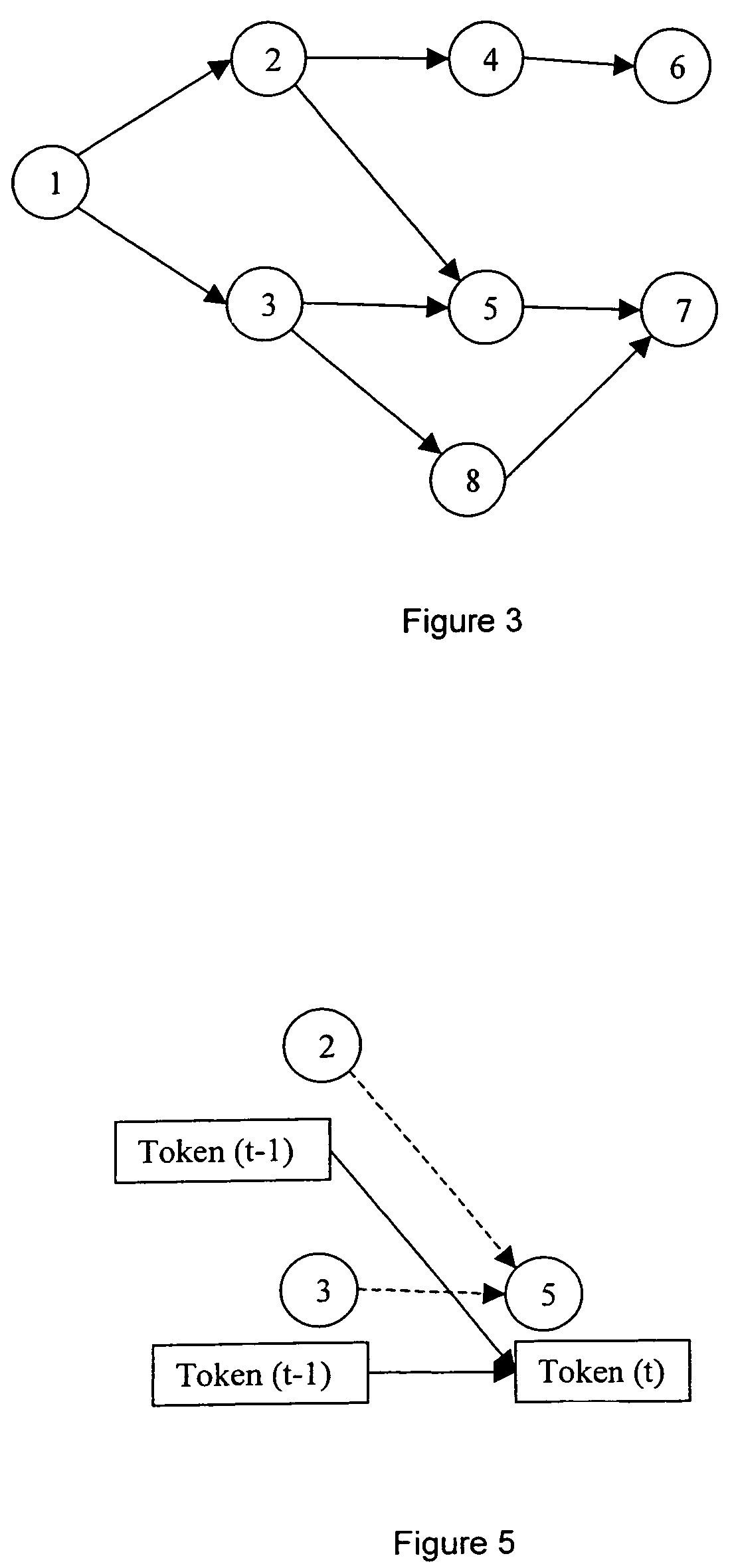
The present invention relates to speech recognition systems, particularly speech-to-text systems and software and decoders for the same. The present invention provides a decoder for an automatic speech recognition system for determining one or more candidate text unit concatenations according to a predetermined criterion and which correspond to a speech segment, the decoder comprising: means for receiving a sequence of feature vectors corresponding to the speech segment; means for mapping with different likelihood values the feature vectors to sequences of nodes in a decoding network, every sequence representing a concatenation of text units; means for determining one or more candidate node sequences in the decoding network corresponding to the candidate text unit concatenations by implementing a dynamic programming token passing algorithm in which each token corresponds to a node and is associated with a number of text unit concatenations and likelihood values for these concatenations, and wherein a token associated with a node in the decoding network is derived from the tokens associated with the previous nodes in the network; wherein tokens from different nodes that are to be passed to a common node are combined to generate a new token corresponding to the common node and associated with an identifier for text unit concatenations and likelihood values associated with the previous tokens of said different nodes. This is combined with means for merging a said token having a said identifier, the text unit concatenations of the said previous tokens being associated with said merged token dependent on their corresponding likelihood values.
Owner:KK TOSHIBA
Multistandard video decoder and decompression system for processing encoded bit streams including a video formatter and methods relating thereto
InactiveUS7230986B2Picture reproducers using cathode ray tubesPicture reproducers with optical-mechanical scanningComputer hardwareVideo decoder
A pipeline video decoder and decompression system handles a plurality of separately encoded bit streams arranged as a single serial bit stream of digital bits and having separately encoded pairs of control codes and corresponding data carried in the serial bit stream. The pipeline system employs a plurality of interconnected stages to decode and decompress the single bit stream, including a start code detector. When in a search mode, the start code detector searches for a specific start code corresponding to one of multiple compression standards. The start code detector responding to the single serial bit stream generates control tokens and data tokens. A respective one of the tokens includes a plurality of data words. Each data word has an extension bit which indicates a presence of additional words therein. The data words are thereby unlimited in number. A token decode circuit positioned in certain of the stages recognizes certain of the tokens as control tokens pertinent to that stage and passes unrecognized control tokens to a succeeding stage. A reconfigurable decode and parser processing means positioned in certain of the stages is responsive to a recognized control token and reconfigures a particular stage to handle an identified data token. Methods relating to the decoder and decompression system include processing steps relating thereto.
Owner:CHARTOLEAUX
Proxy server security token authorization
ActiveUS7836493B2Digital data processing detailsComputer security arrangementsSecure communicationDigital signature
A management server manufactures a secure, tamper-resistant token for a particular user specifying the permissions and authorizations that user possesses. The token may be in the form of a digitally-signed message specifying, for example, a particular computer and associated port number that the user is permitted to access. The management server delivers the token to the user, preferably over a secure communications session. When challenged, the user presents the secure token to the security proxy server. The security proxy server examines the token to be sure it is authentic and has not be tampered with, and then extracts information contained in the token to determine the user's authorization to access a particular computer, particular port number and / or other resource. The security proxy server then establishes authorized communication with the authorized computing resource based on the information contained in the user's token, and thereafter may act in one embodiment as essentially a passthrough or proxy for permitting the user to access and communicate with the resource.
Owner:ATTACHMATE
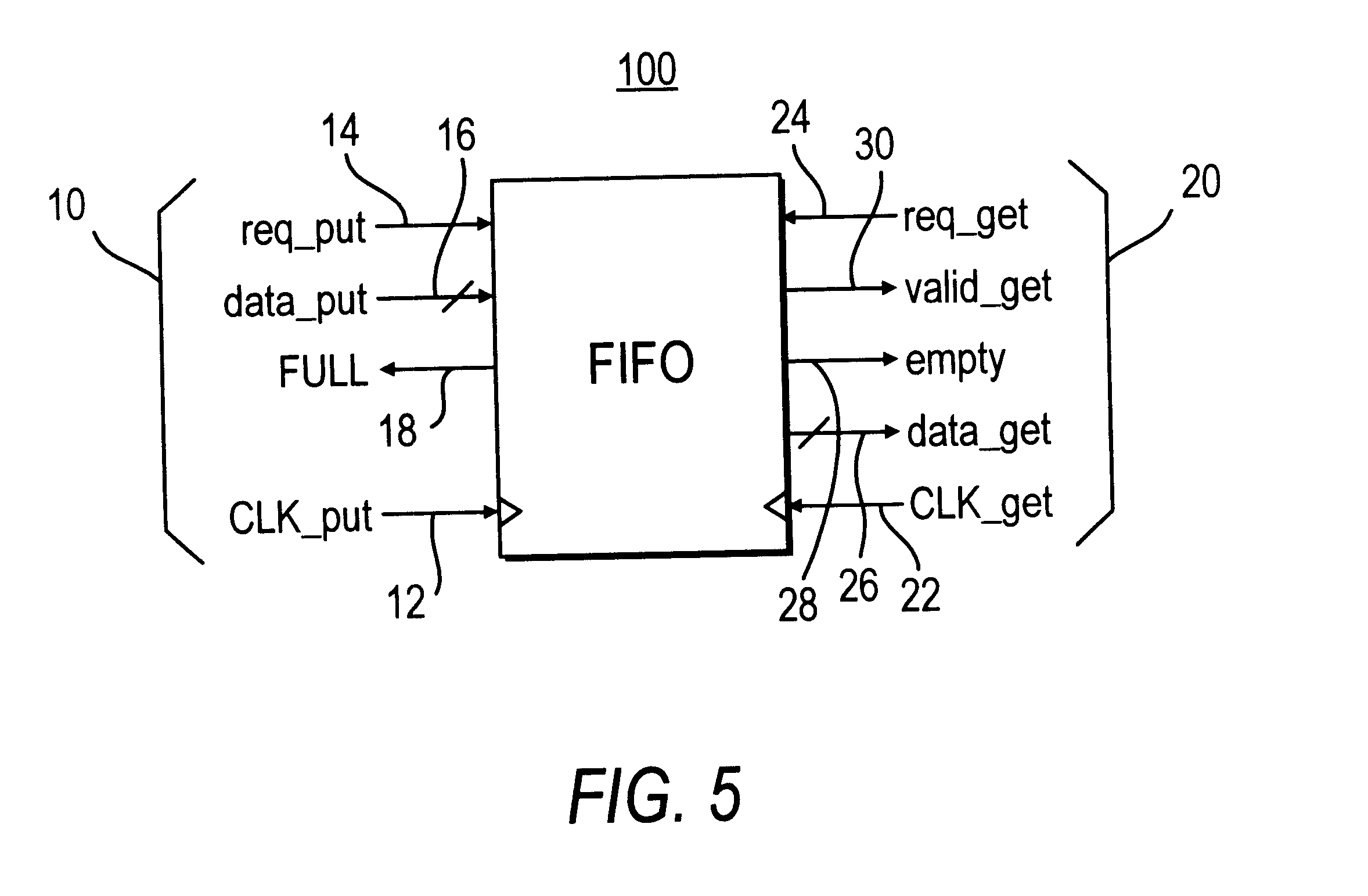
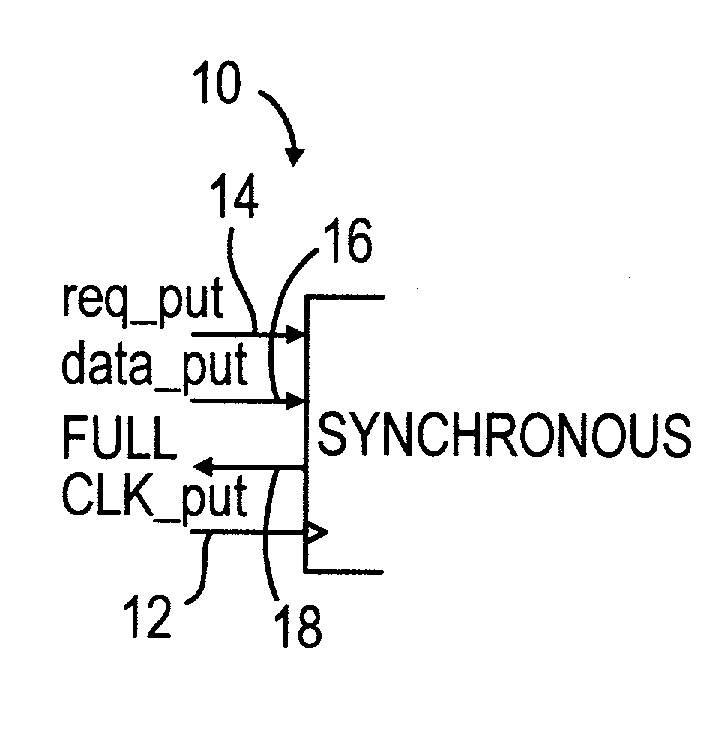
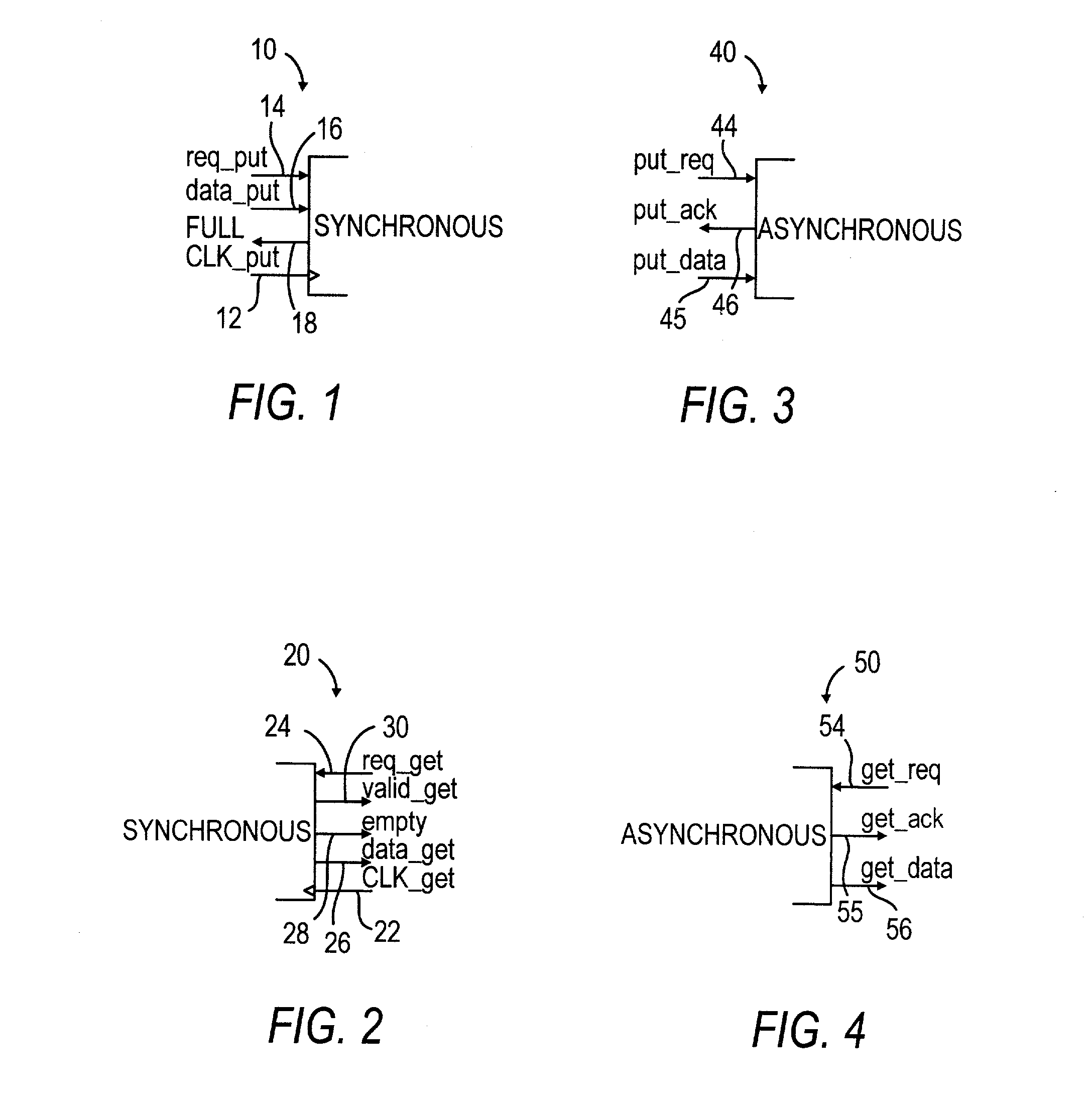
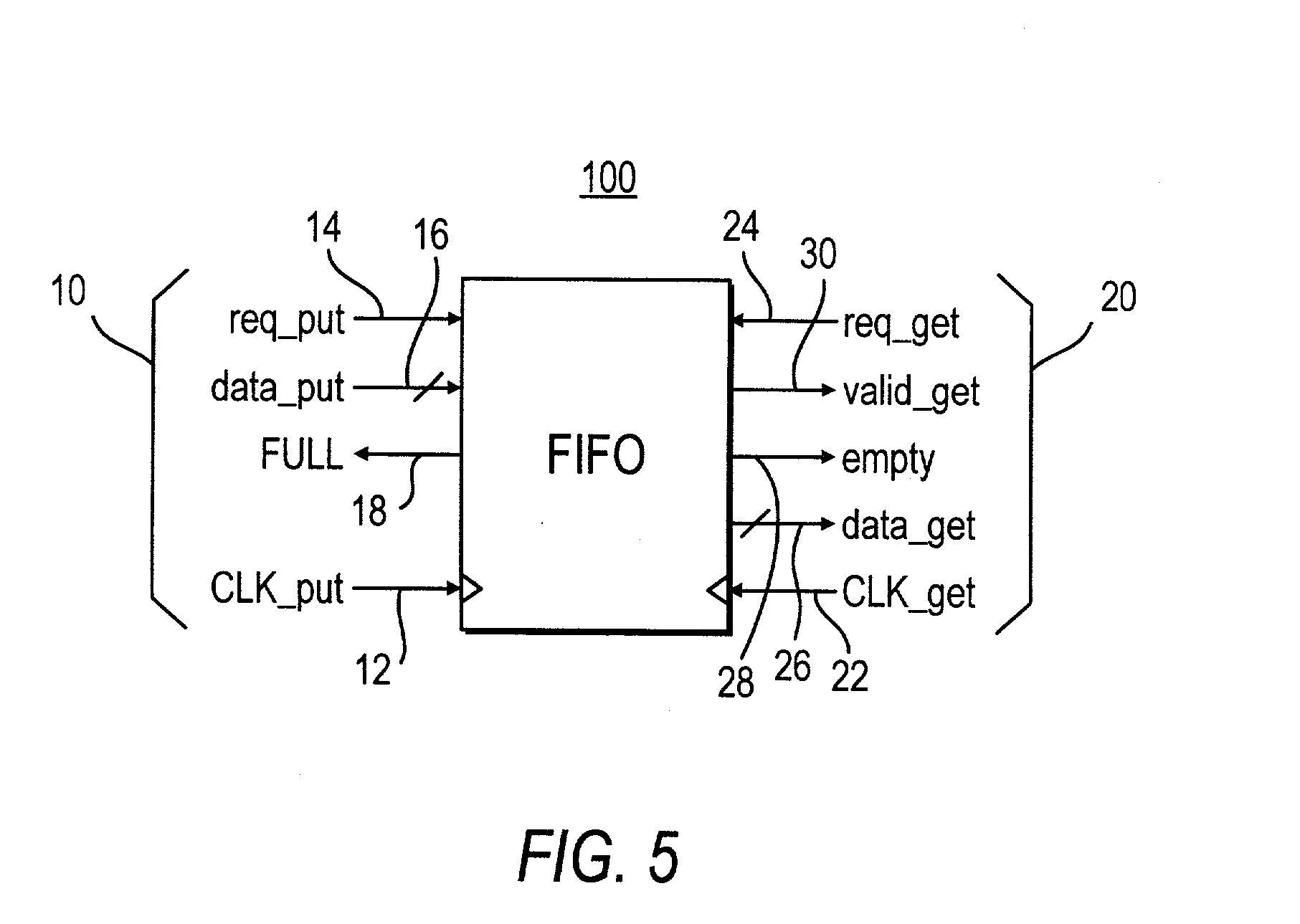
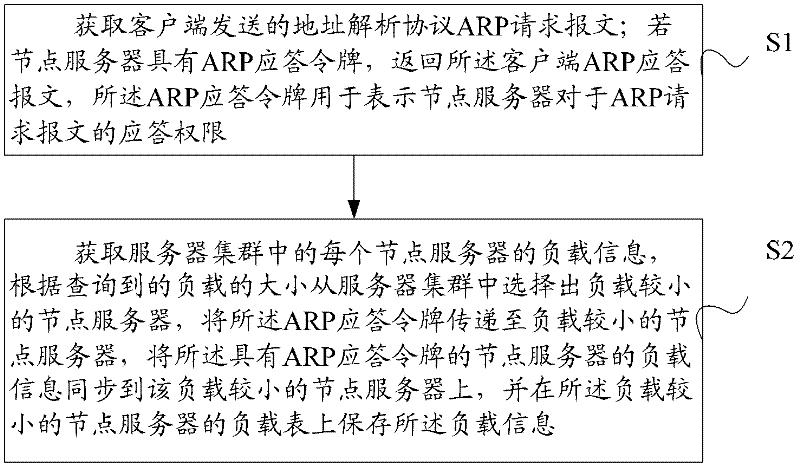
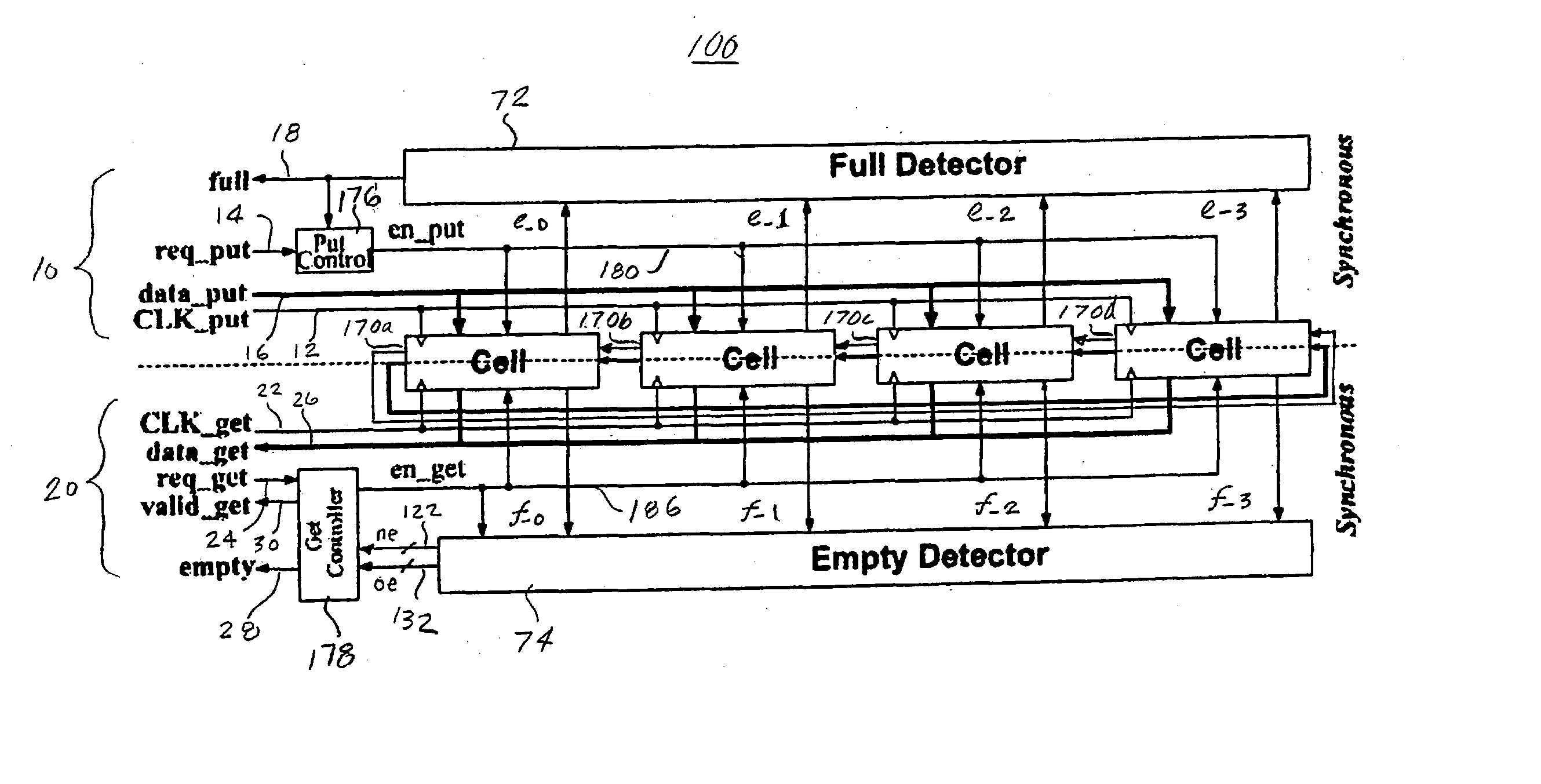
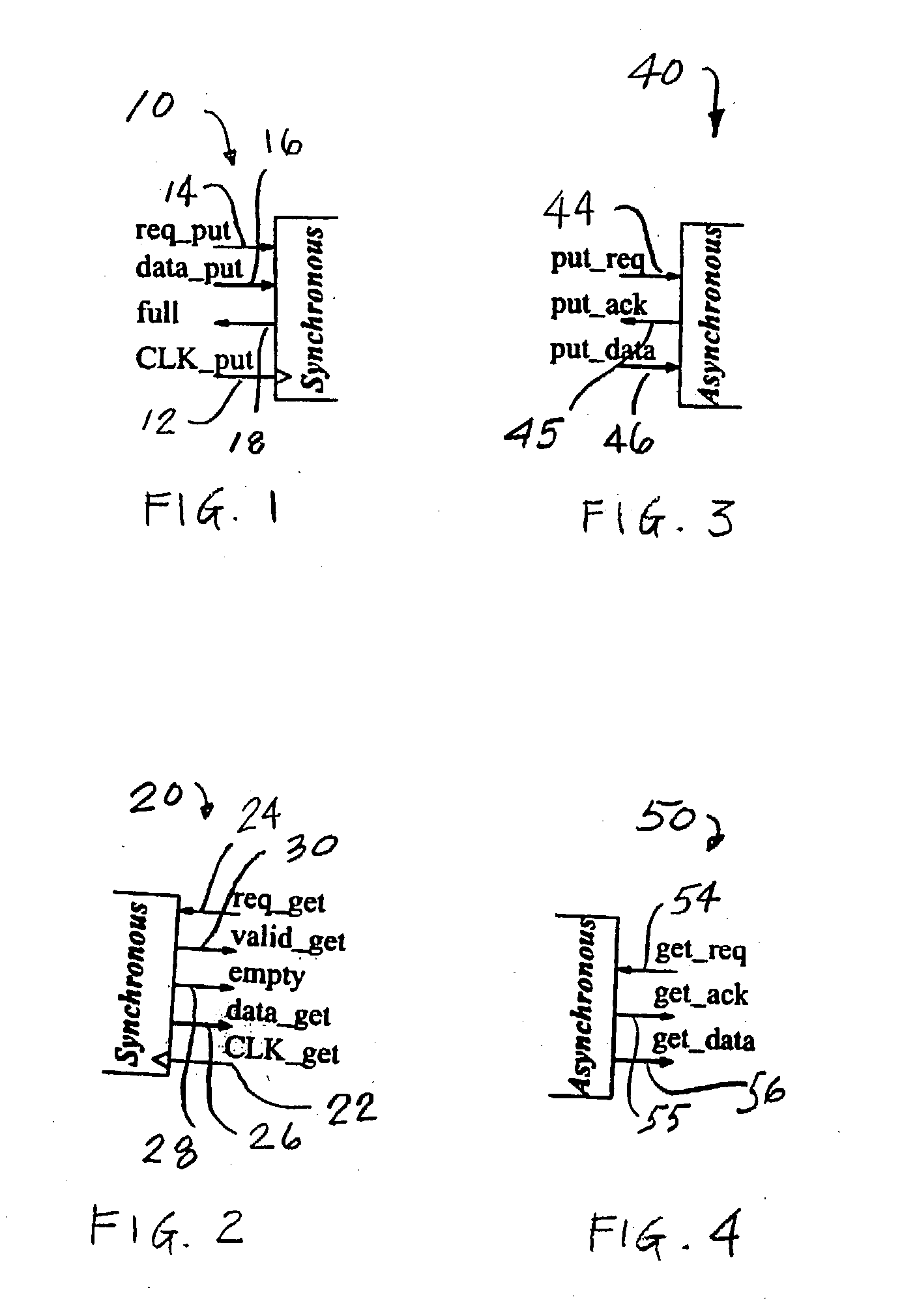
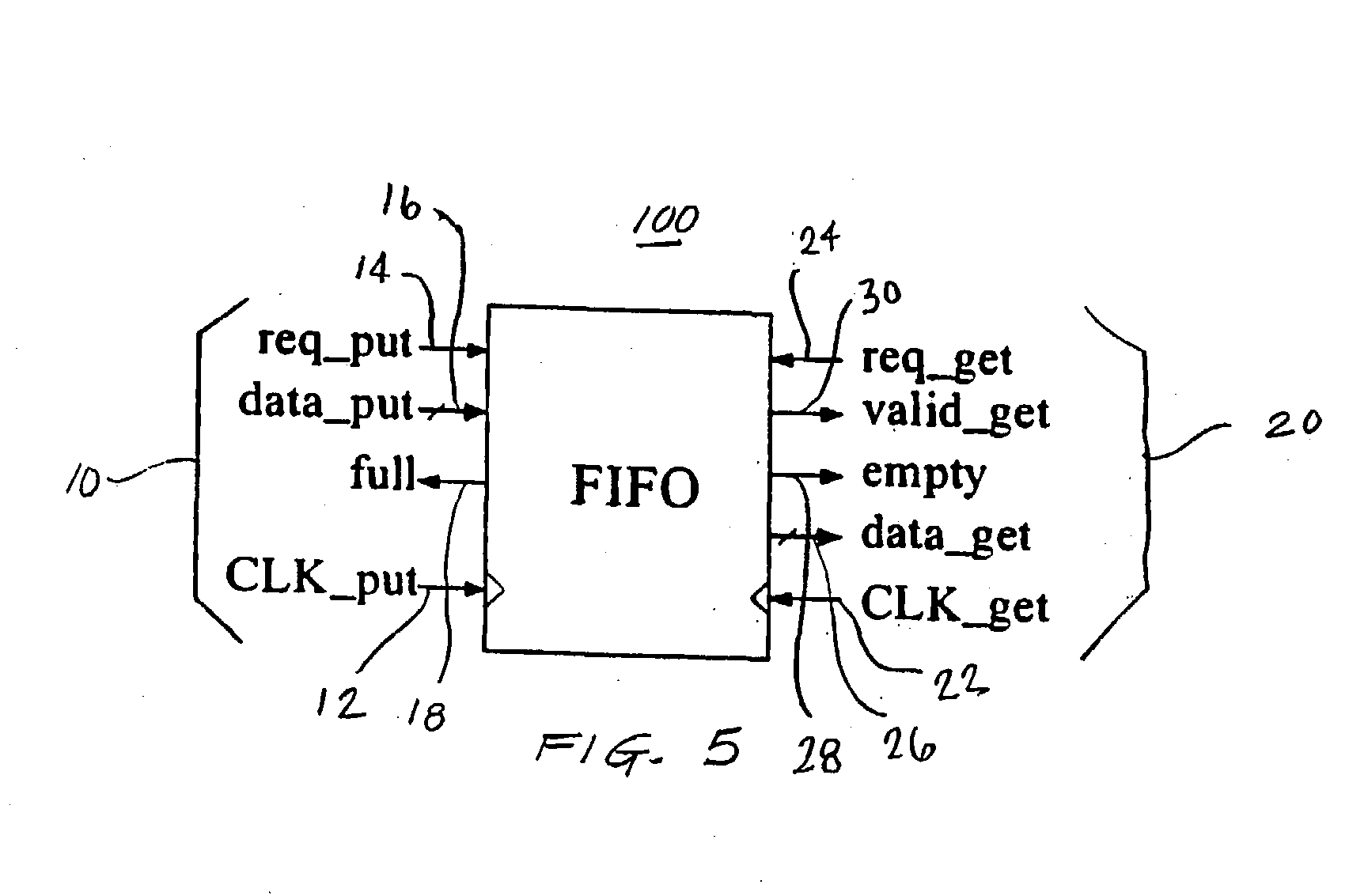
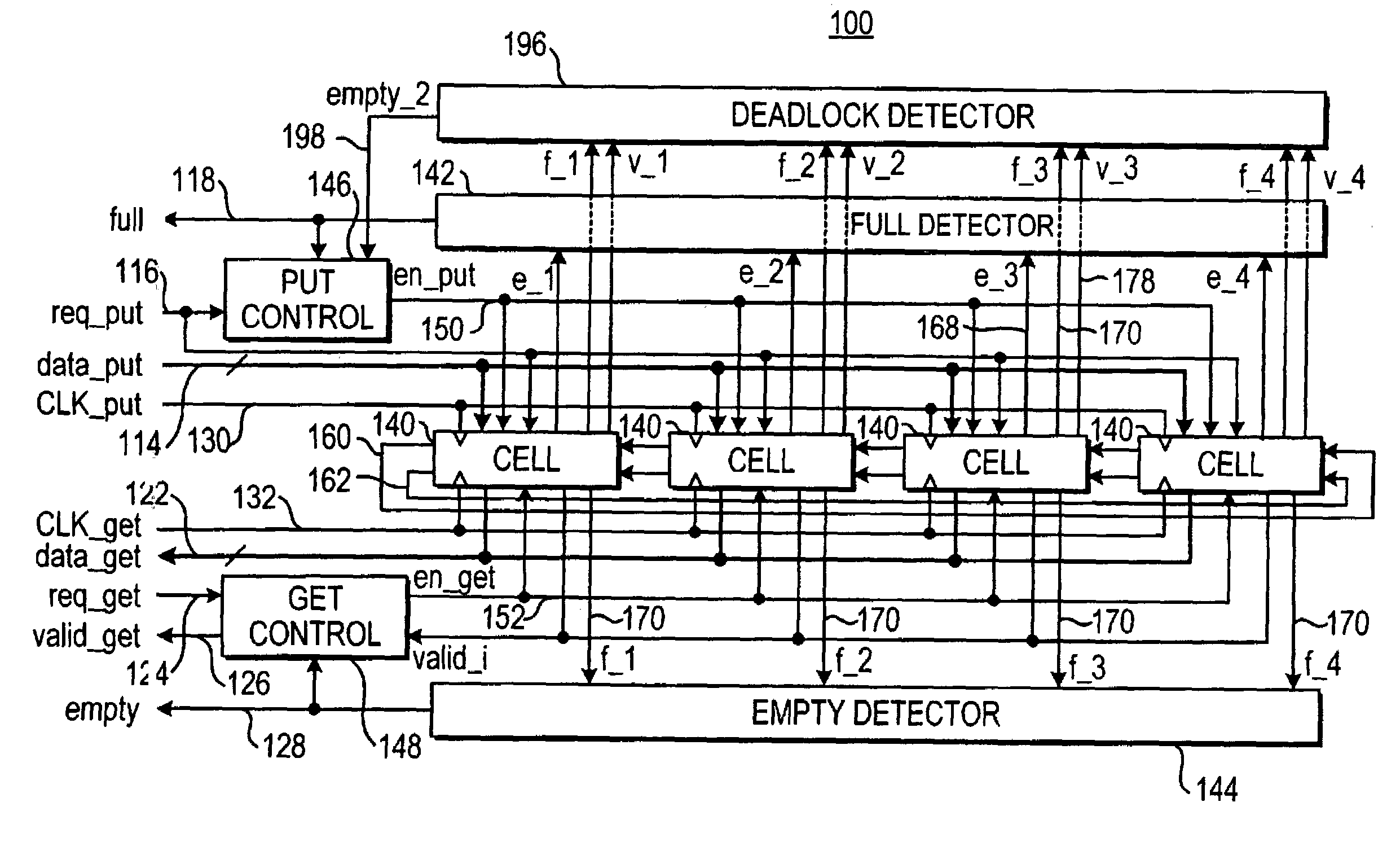
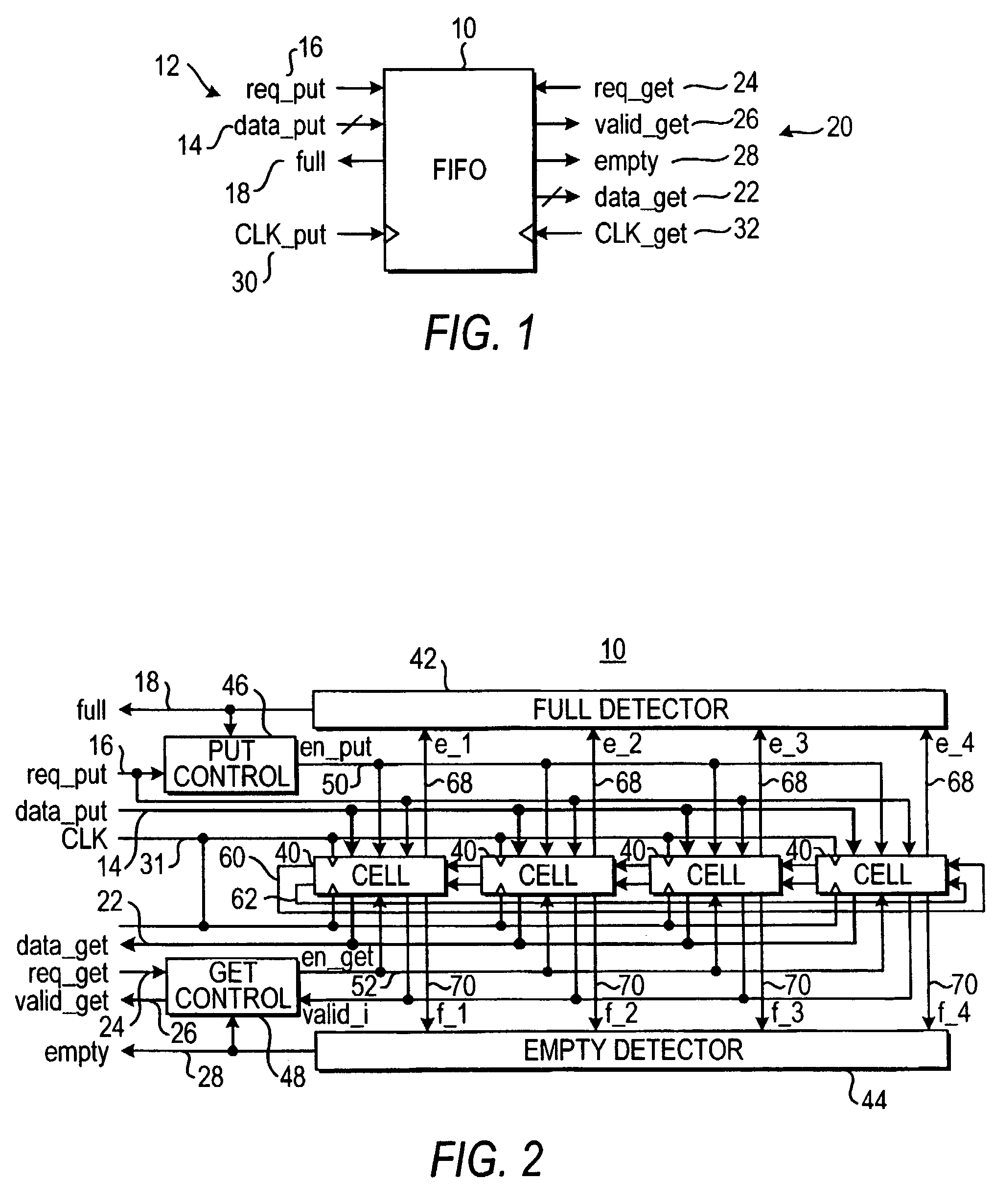
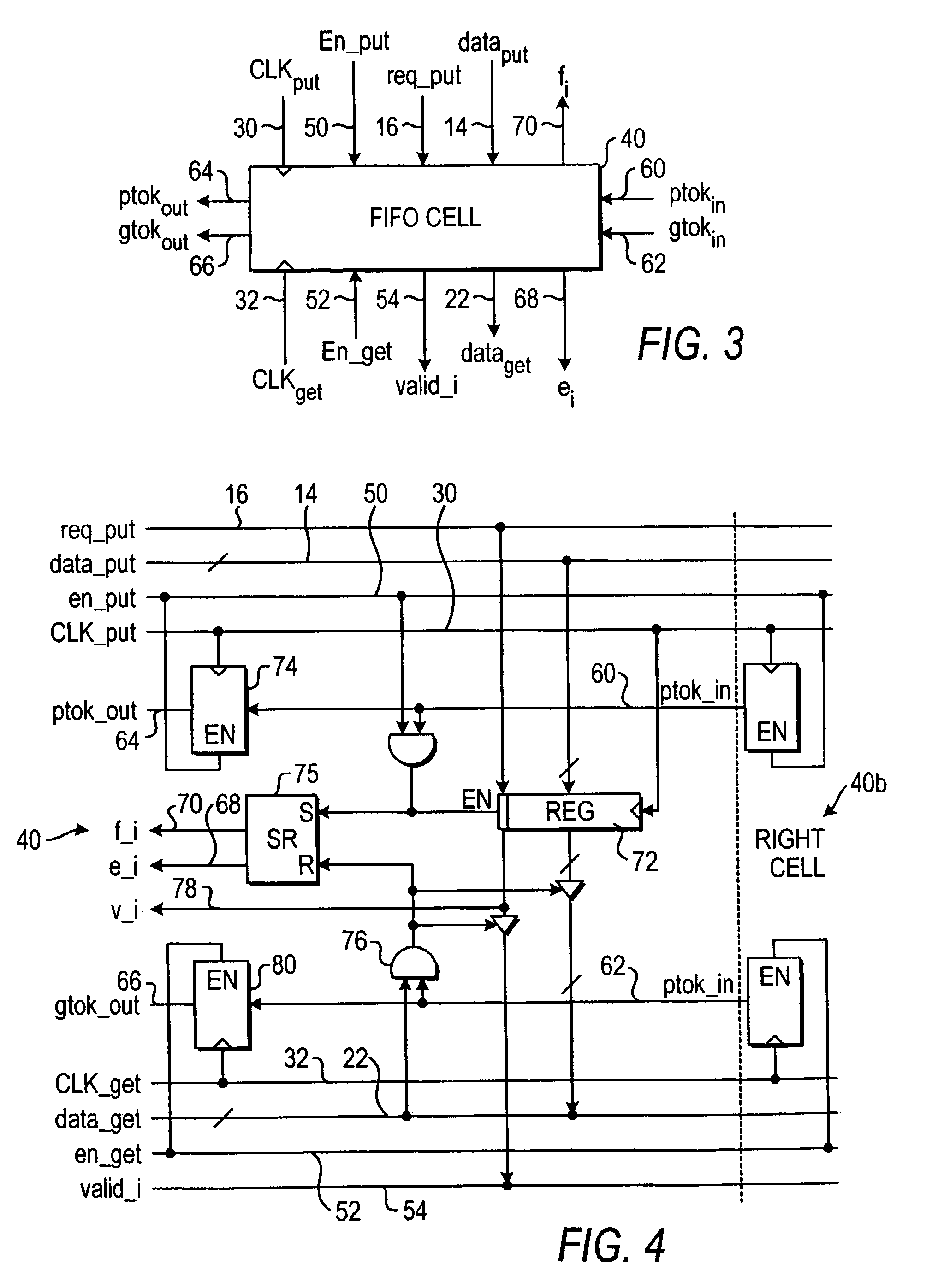
Low latency FIFO circuits for mixed asynchronous and synchronous systems
InactiveUS6850092B2Lower latencyImprove throughputPulse automatic controlDigital storageTime domainProcessor register
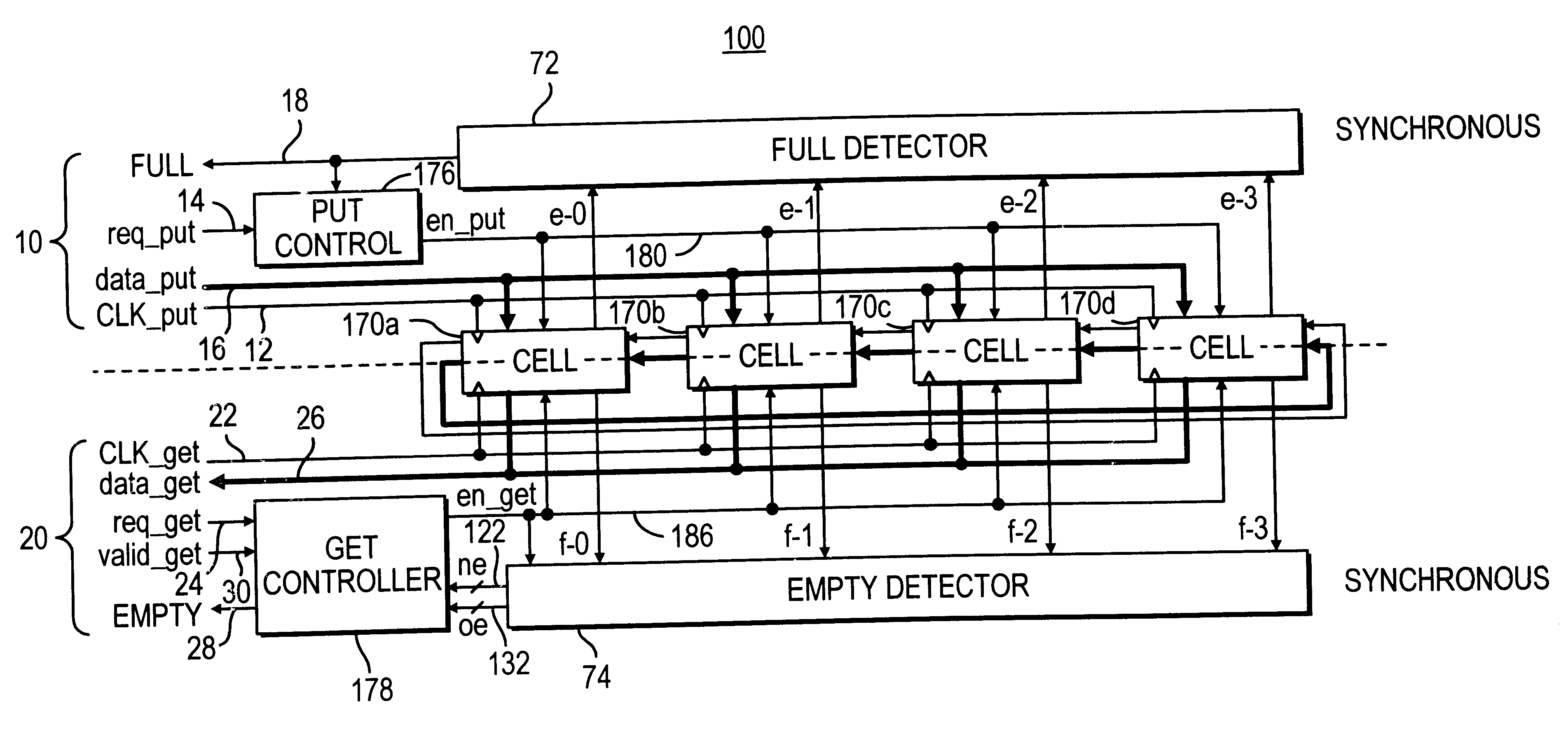
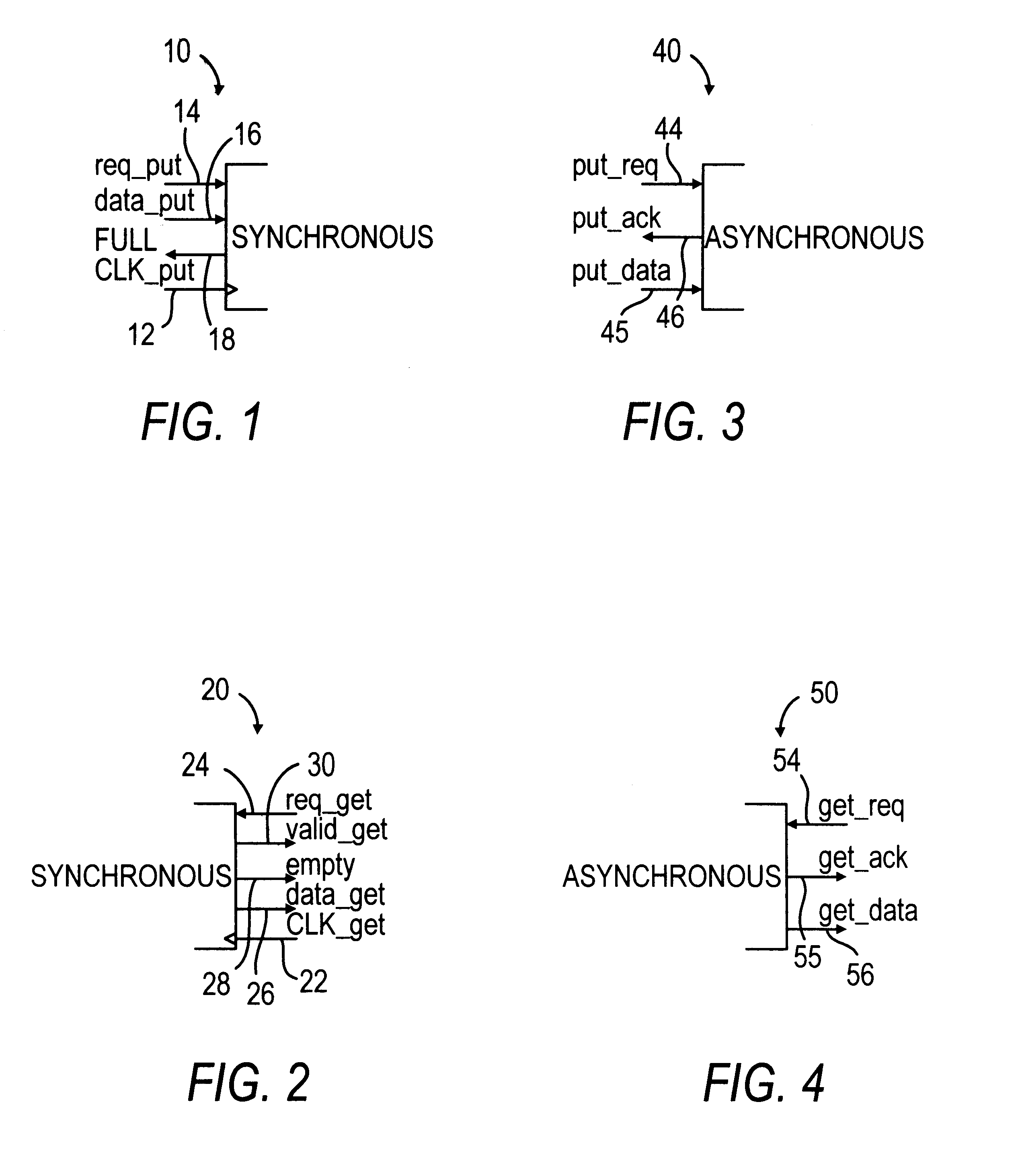
A FIFO design interfaces a sender subsystem and a receiver subsystem operating on different time domains. The sender subsystem and the receiver subsystem may be synchronous or asynchronous. The FIFO circuit includes a put interface configured to operate in accordance with the sender time domain and get interface configured to operate in accordance with the receiver time domain. The FIFO circuit includes an array of cells having a register and state controller indicative of the state of the cell. Each cell also has a put component part configured to operate according to the sender time domain including a put token passing circuit and put controller circuit. Each cell has get component part configured to operate according to the receiver time domain including a get token passing circuit and a get controller circuit. A mixed-clock relay station design interfaces a sender subsystem and a receiver subsystem working at different time domains, and where the latency between sender and receiver is large.
Owner:THE TRUSTEES OF COLUMBIA UNIV IN THE CITY OF NEW YORK
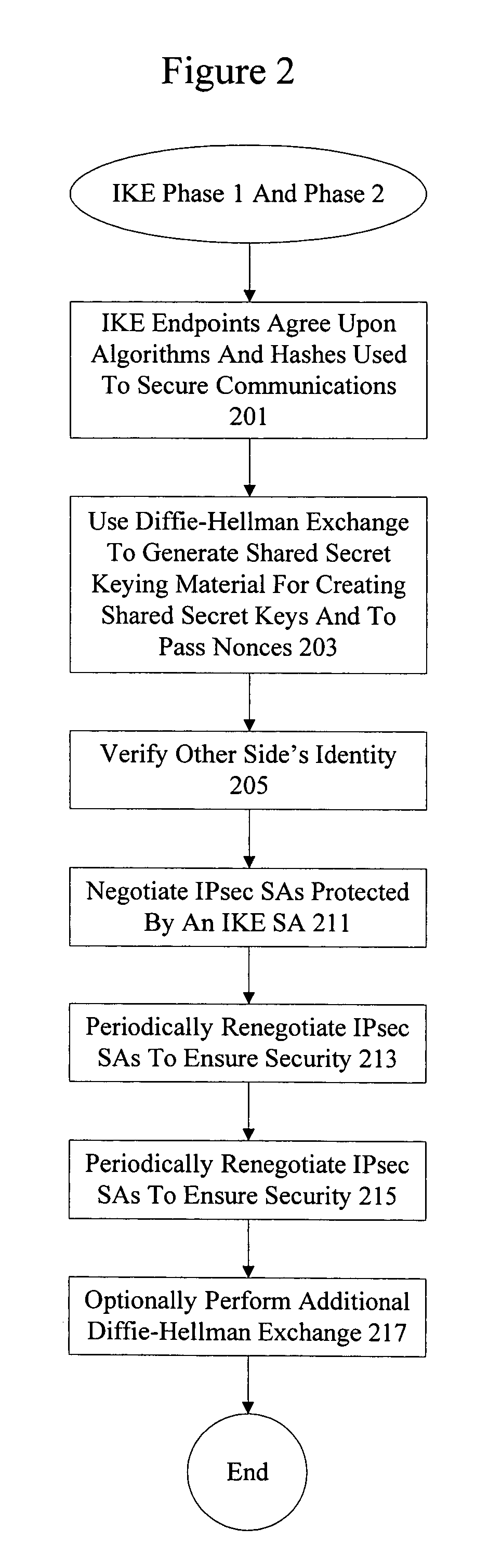
Secure extended authentication bypass
ActiveUS20070192842A1Key distribution for secure communicationDigital data processing detailsKey exchangeInternet Key Exchange
Methods and apparatus are provided to allow Internet Key Exchange (IKE) phase 1 keying materials to be periodically refreshed in a secure manner without requiring user interaction. A client and server perform authentication and key exchange during set up of a secure connection. A token is passed to the client by the server during or after the initial user authentication phase. The token is stored both at the client and at the server. Instead of requiring user credentials, the token can be used to securely prove the identity of the client.
Owner:CISCO TECH INC
System and method for secure network connectivity
InactiveUS20070107061A1Accurate protectionEasy to useRandom number generatorsMemory loss protectionSecurity checkRemote computer
A system and method to ensure that a remote computer making a VPN connection complies with network security policies. Server driven security checks may be configured to verify compliance with each access level before access is granted at that level. The security checks may be selected based at least according to the information received from the remote computer. After the server determines that the remote computer complies with the security policy for the requested access level, the server may pass a token to the remote computer, or may grant VPN access to the remote computer. If the remote computer does not comply with the security policy associated with the requested access level but is in compliance with a security policy corresponding to a lower access level, the server may grant the remote computer access to the lower access level.
Owner:BARCLAYS CAPITAL INC
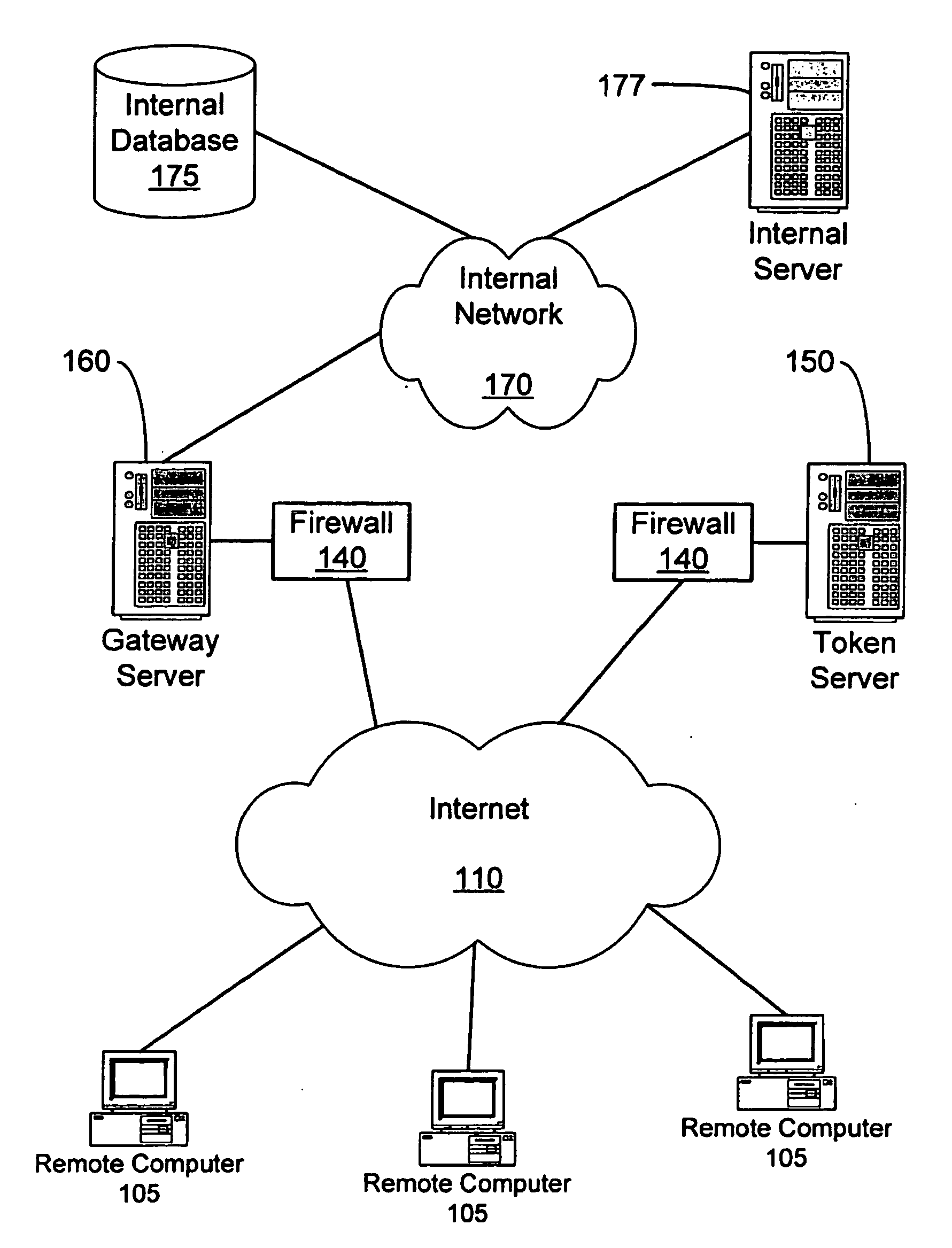
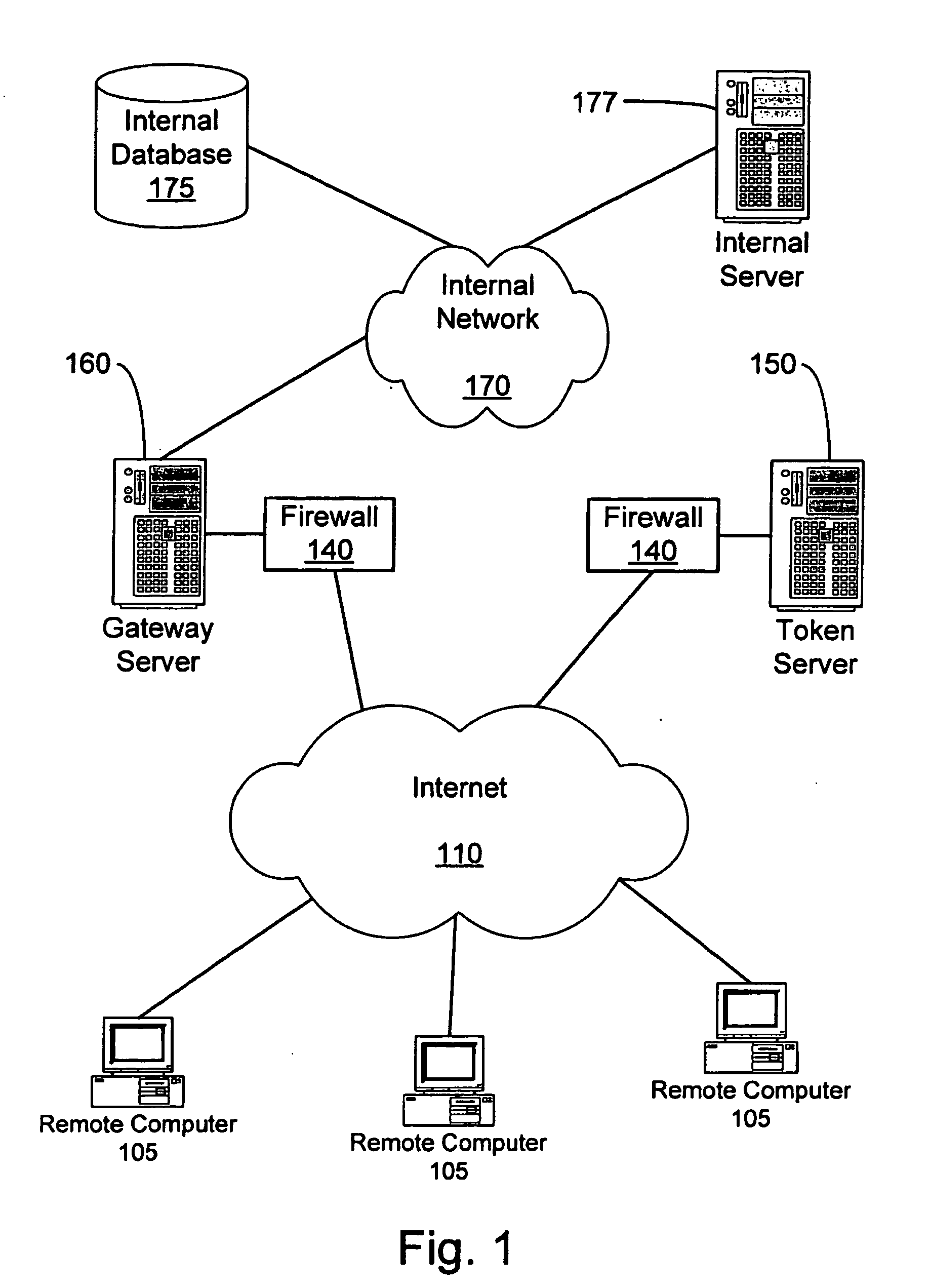
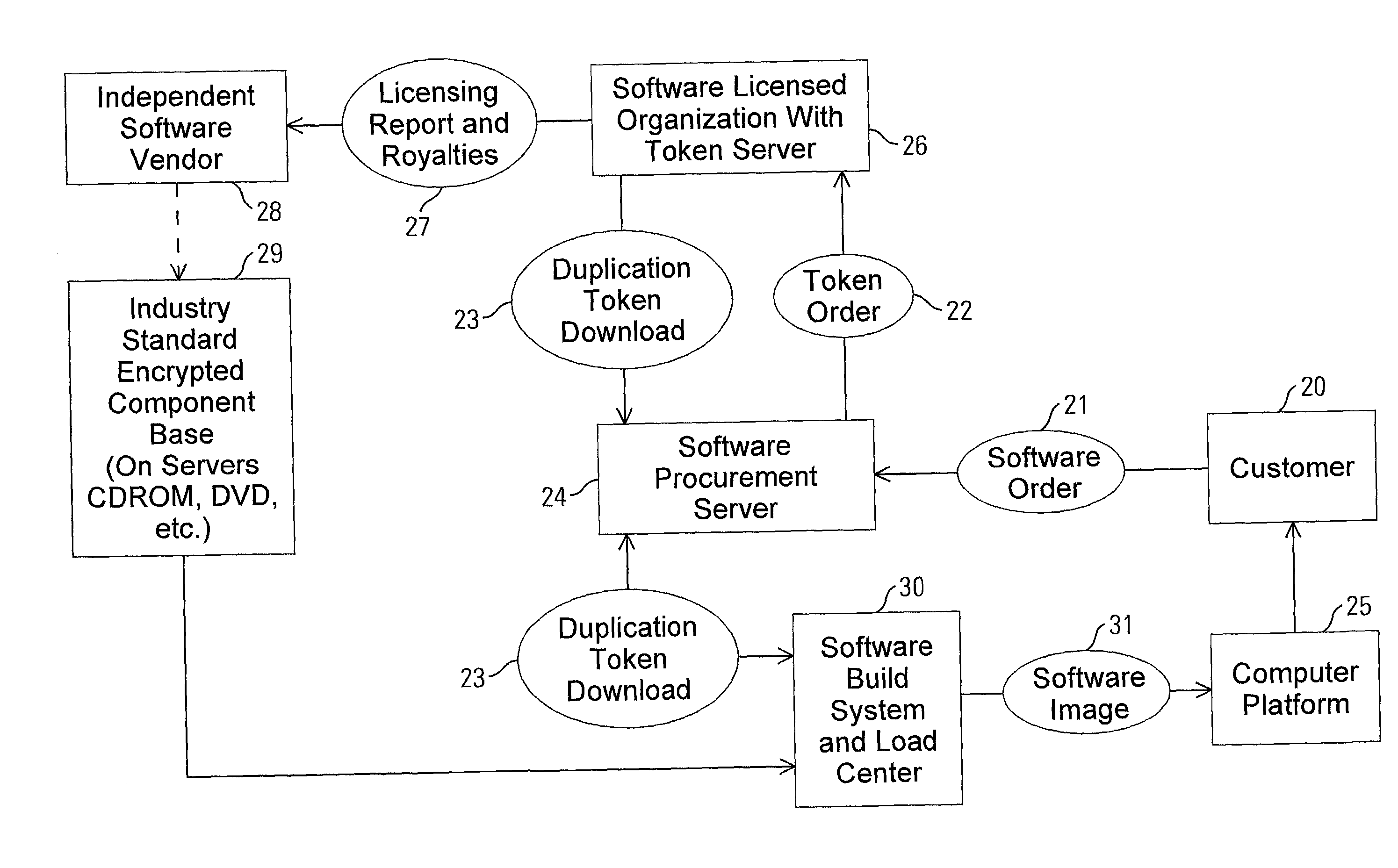
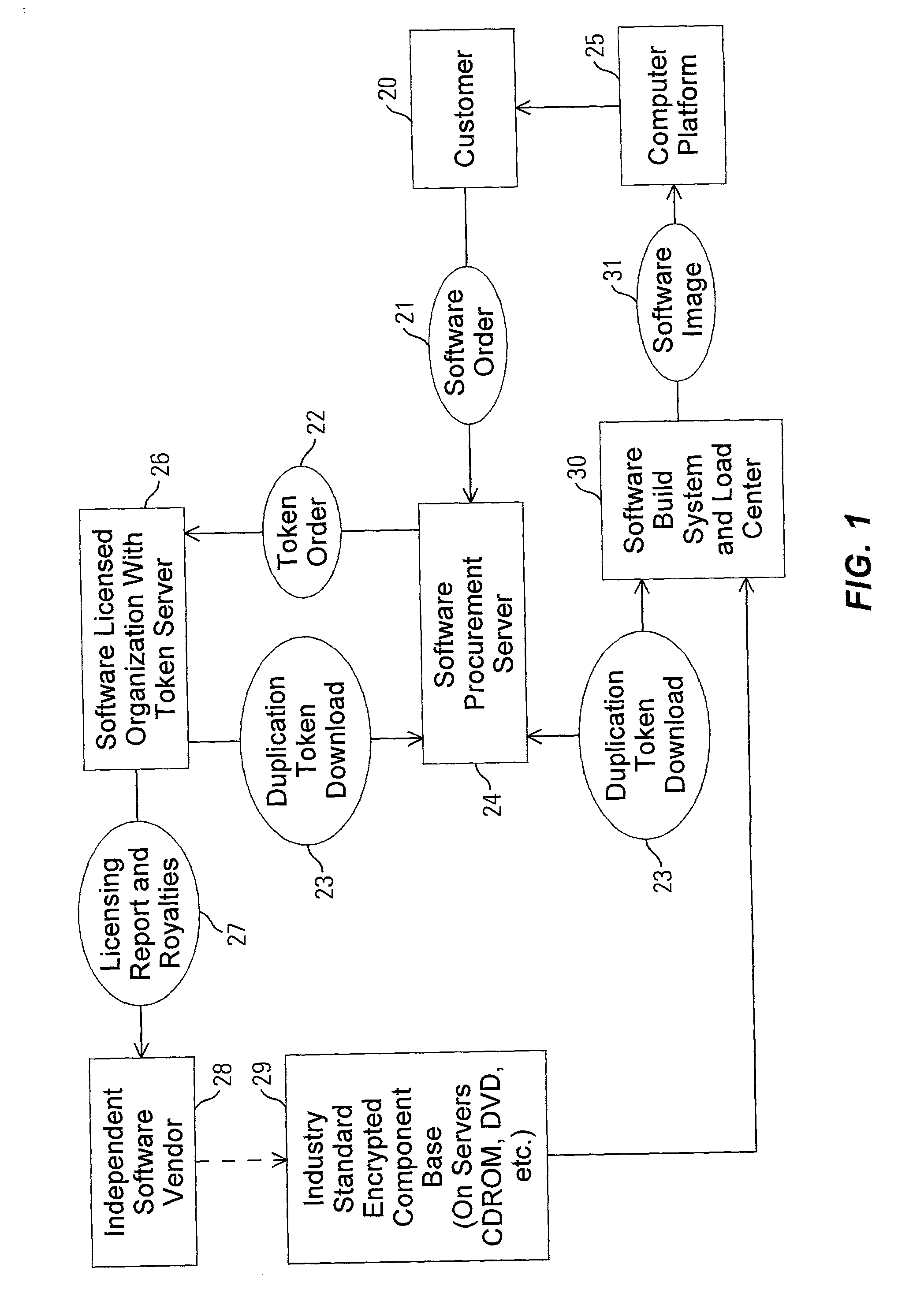
Method and apparatus for uniquely and securely loading software to an individual computer
InactiveUS20020128975A1Increase incomeTurn around timeKey distribution for secure communicationPublic key for secure communicationPersonal computerApplication software
A method and apparatus for uniquely and securely loading software to an individual computer includes requesting download of software components to a hardware platform and delivering a token from a token server responsive to the request. The token server is operated by an entity having rights to grant access to the software components. The token is passed to a system that builds software images. The system is operated by an organization that performs delivery of the software. The software components are assembled and decrypted with the system within an enabled secure process. A software image to be loaded onto the platform is created and bound to the hardware platform by encrypting the software image using an application specific encryption technique.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
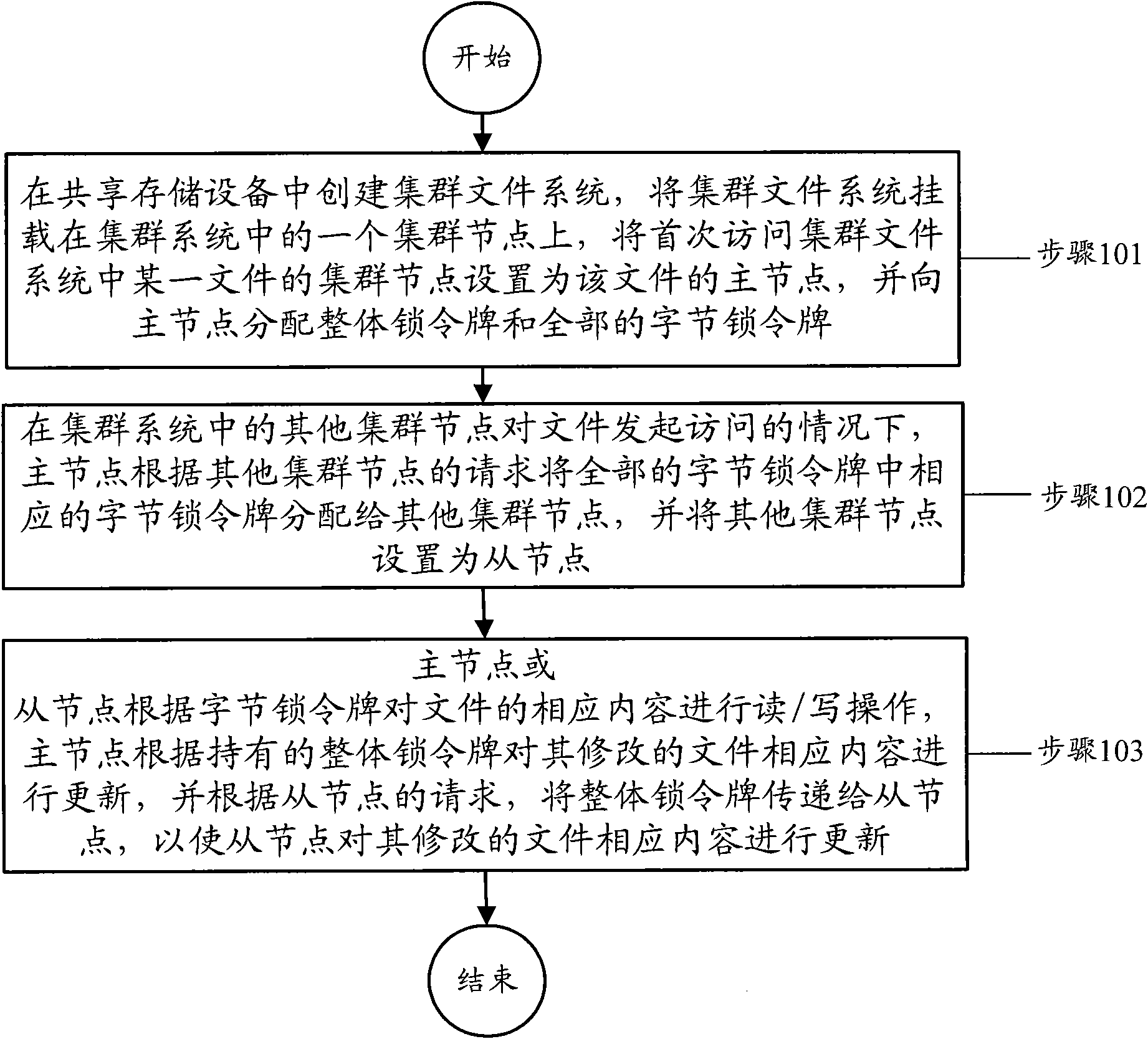
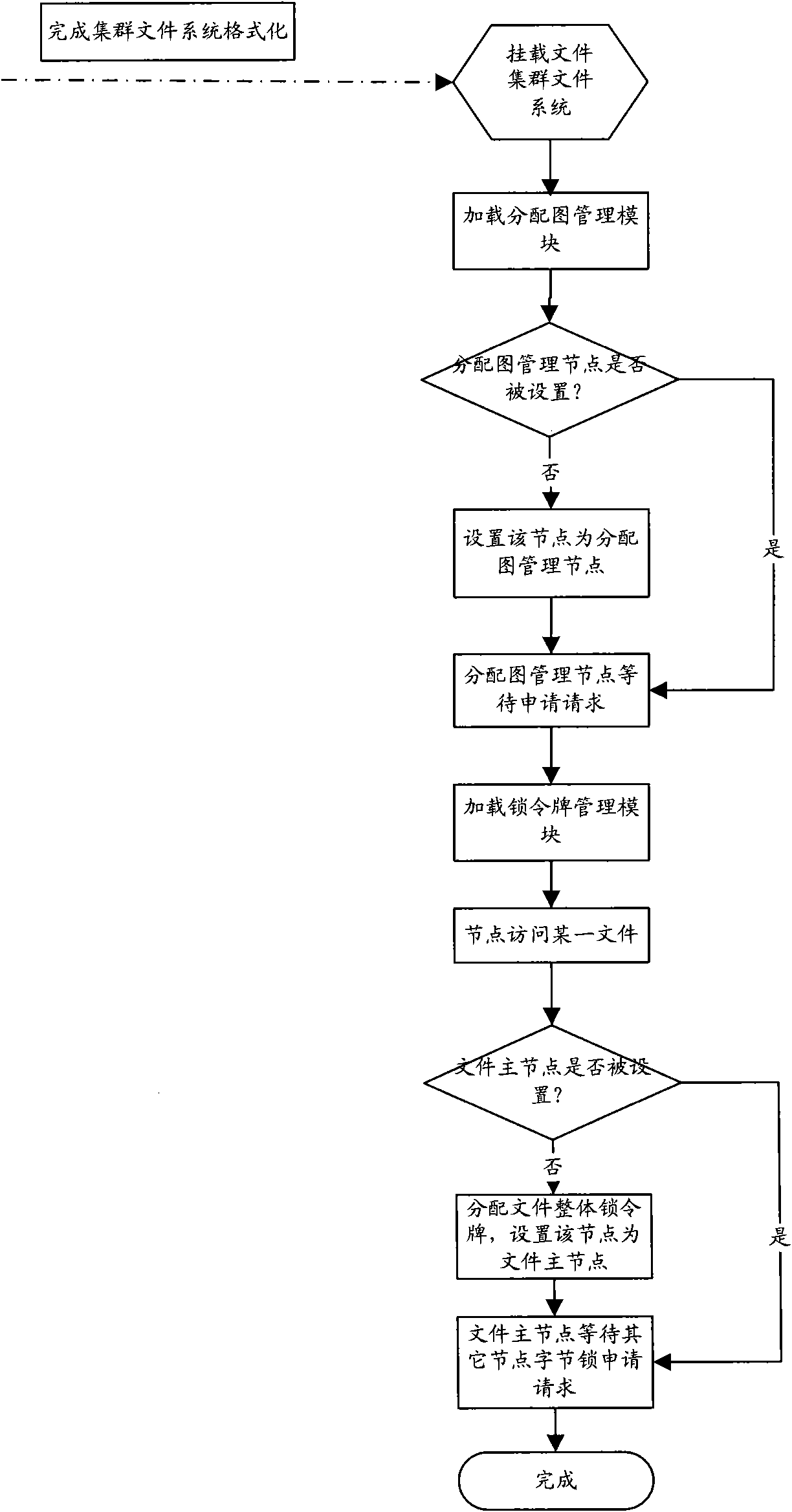
Access control method for cluster file system and cluster node
InactiveCN102339283AImprove access efficiencyMaintain integritySpecial data processing applicationsCluster systemsClustered file system
The invention discloses a control method for a cluster file system access and a cluster node. The method comprises the following steps: a cluster file system is established and mounted on a cluster node in the cluster system, the cluster point of a certain file in the cluster file system which is accessed for the first time is set as a main node of the file, and an integral locking token and a total byte locking token are distributed to the main node; under the condition that other cluster points access the file, the main node distributes the corresponding byte locking token to the other cluster points according to the request of other cluster points and sets the other cluster points as slave nodes; the main nodes or the slave nodes carry out read / write operation on the corresponding contents of the file according to the byte locking token, the main nodes update the corresponding contents of the file modified by the integral locking token according to the holding integral locking token and transmits the integral locking token to the slave nodes according to the request of the slave nodes so that the slave nodes update the corresponding contents of the file modified by the integral locking token.
Owner:ZTE CORP
Method and system for automatic speech recognition
A method of recognizing speech is provided that includes generating a decoding network that includes a primary sub-network and a classification sub-network. The primary sub-network includes a classification node corresponding to the classification sub-network. The classification sub-network corresponds to a group of uncommon words. A speech input is received and decoded by instantiating a token in the primary sub-network and passing the token through the primary network. When the token reaches the classification node, the method includes transferring the token to the classification sub-network and passing the token through the classification sub-network. When the token reaches an accept node of the classification sub-network, the method includes returning a result of the token passing through the classification sub-network to the primary sub-network. The result includes one or more words in the group of uncommon words. A string corresponding to the speech input is output that includes the one or more words.
Owner:TENCENT TECH (SHENZHEN) CO LTD
Bi-directional absolute automated tracking system for material handling
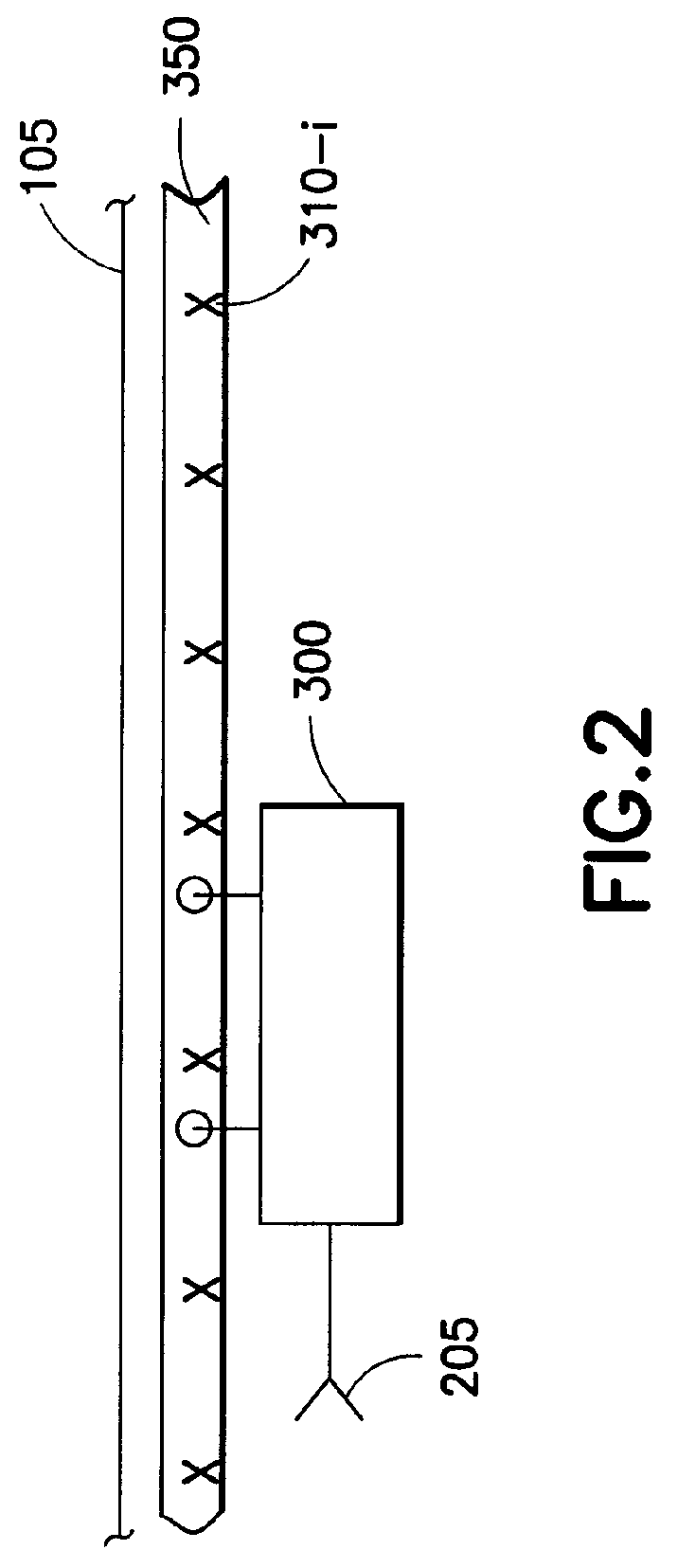
InactiveUS20060069470A1Avoid collisionOptimizationProgramme controlAutomatic initiationsLoop controlControl engineering
Communication between a controller and a set of automated vehicles in a manufacturing facility is improved by use of a closed-loop control system that operates on a real-time interrupt basis in which autonomous carriers report their location, sensed from reference markers along a track, the reference markers being referenced to an absolute grid in space, to a central controller or to one of a set of zone controllers that monitor the location of nearby vehicles that ordinarily use a token-passing system to avoid collisions, but which controllers can intervene to prevent one vehicle from blocking or interfering with another.
Owner:IBM CORP
Low latency FIFO circuits for mixed asynchronous and synchronous systems
A FIFO design interfaces a sender subsystem and a receiver subsystem operating on different time domains. The sender subsystem and the receiver subsystem may be synchronous or asynchronous. The FIFO circuit includes a put interface configured to operate in accordance with the sender time domain and get interface configured to operate in accordance with the receiver time domain. The FIFO circuit includes an array of cells having a register and state controller indicative of the state of the cell. Each cell also has a put component part configured to operate according to the sender time domain including a put token passing circuit and put controller circuit. Each cell has get component part configured to operate according to the receiver time domain including a get token passing circuit and a get controller circuit. A mixed-clock relay station design interfaces a sender subsystem and a receiver subsystem working at different time domains, and where the latency between sender and receiver is large.
Owner:THE TRUSTEES OF COLUMBIA UNIV IN THE CITY OF NEW YORK
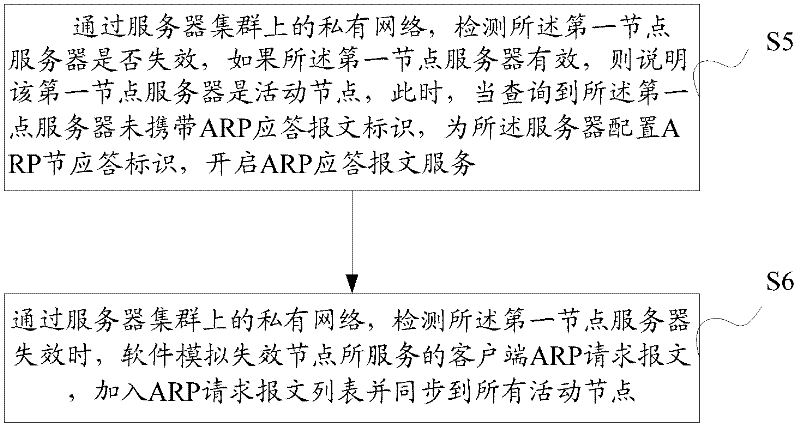
Load balancing method in server cluster, as well as node server and cluster
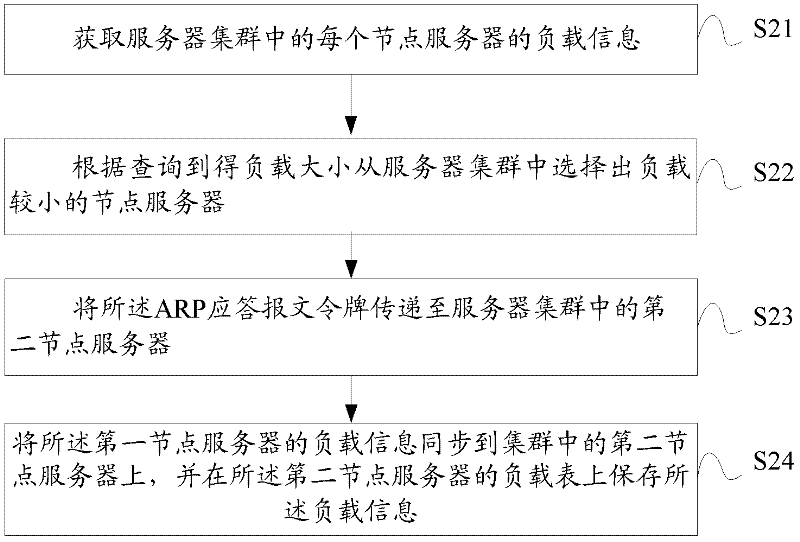
ActiveCN102447624AImprove network bandwidth utilization efficiencyFlexible Load SharingData switching networksAddress Resolution ProtocolName server
The embodiment of the invention discloses a load balancing method in server cluster comprising the following steps: acquiring an address resolution protocol ARP request message sent from a client; if a node server has an ARP response token, returning the client ARP response message, wherein the ARP response token is used for representing the response authority of the node server to the ARP request message; acquiring the load information of each node server in the server cluster, selecting the node server with small load from the server cluster according to the acquired load condition, transmitting the ARP response token to the node server with small load, synchronizing the load information of the node server with the ARP response token to the node server with small load and storing the load information on the load table of the node server with small load. The node server in the embodiment of the invention can flexibly distribute the load according to its own network adapter configuration condition and load condition to improve the server network bandwidth utilization rate, especially to fully utilize all server network adapters and to avoid the performance bottleneck caused by excessive reliance on the load balancing equipment when the server configures multiple network adapters.
Owner:CHENGDU HUAWEI TECH
Low latency fifo circuits for mixed asynchronous and synchronous systems
InactiveUS20040128413A1Input/output processes for data processingData conversionTime domainProcessor register
A FIFO design interfaces a sender subsystem and a receiver subsystem operating on different time domains. The sender subsystem and the receiver subsystem may be synchronous or asynchronous. The FIFO circuit includes a put interface configured to operate in accordance with the sender time domain and get interface configured to operate in accordance with the receiver time domain. The FIFO circuit includes an array of cells having a register and state controller indicative of the state of the cell. Each cell also has a put component part configured to operate according to the sender time domain including a put token passing circuit and put controller circuit. Each cell has get component part configured to operate according to the receiver time domain including a get token passing circuit and a get controller circuit. A mixed-clock relay station design interfaces a sender subsystem and a receiver subsystem working at different time domains, and where the latency between sender and receiver is large.
Owner:THE TRUSTEES OF COLUMBIA UNIV IN THE CITY OF NEW YORK
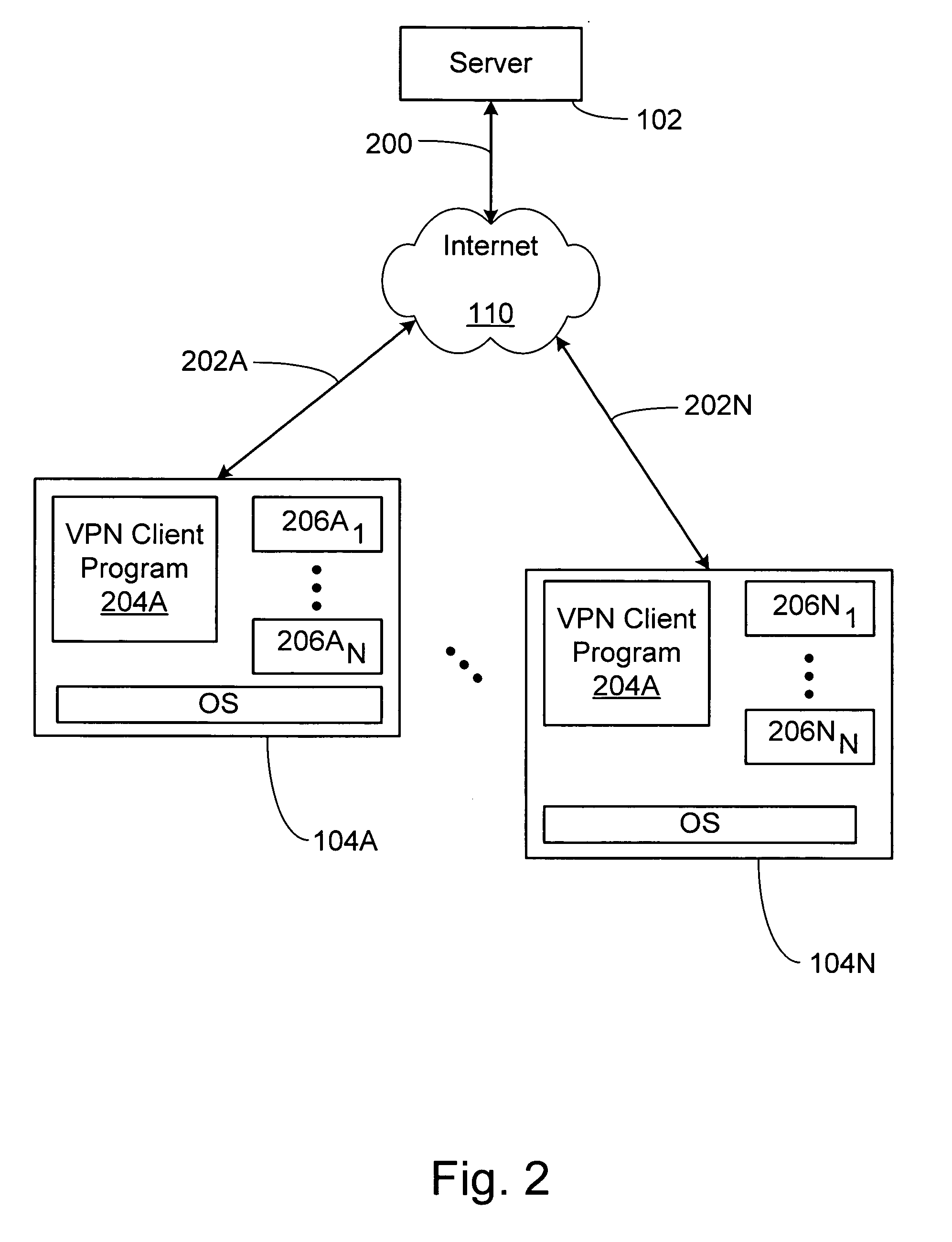
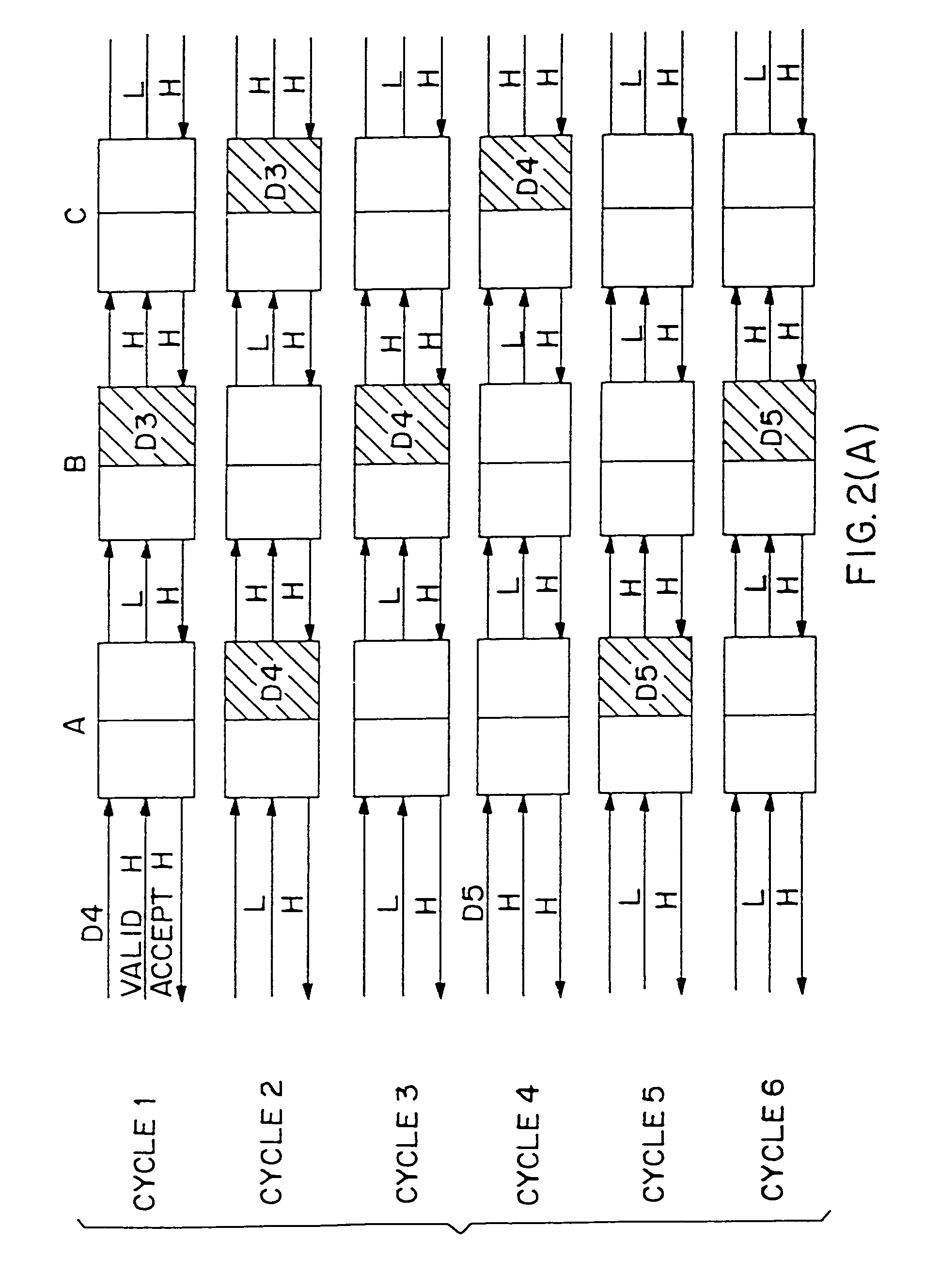
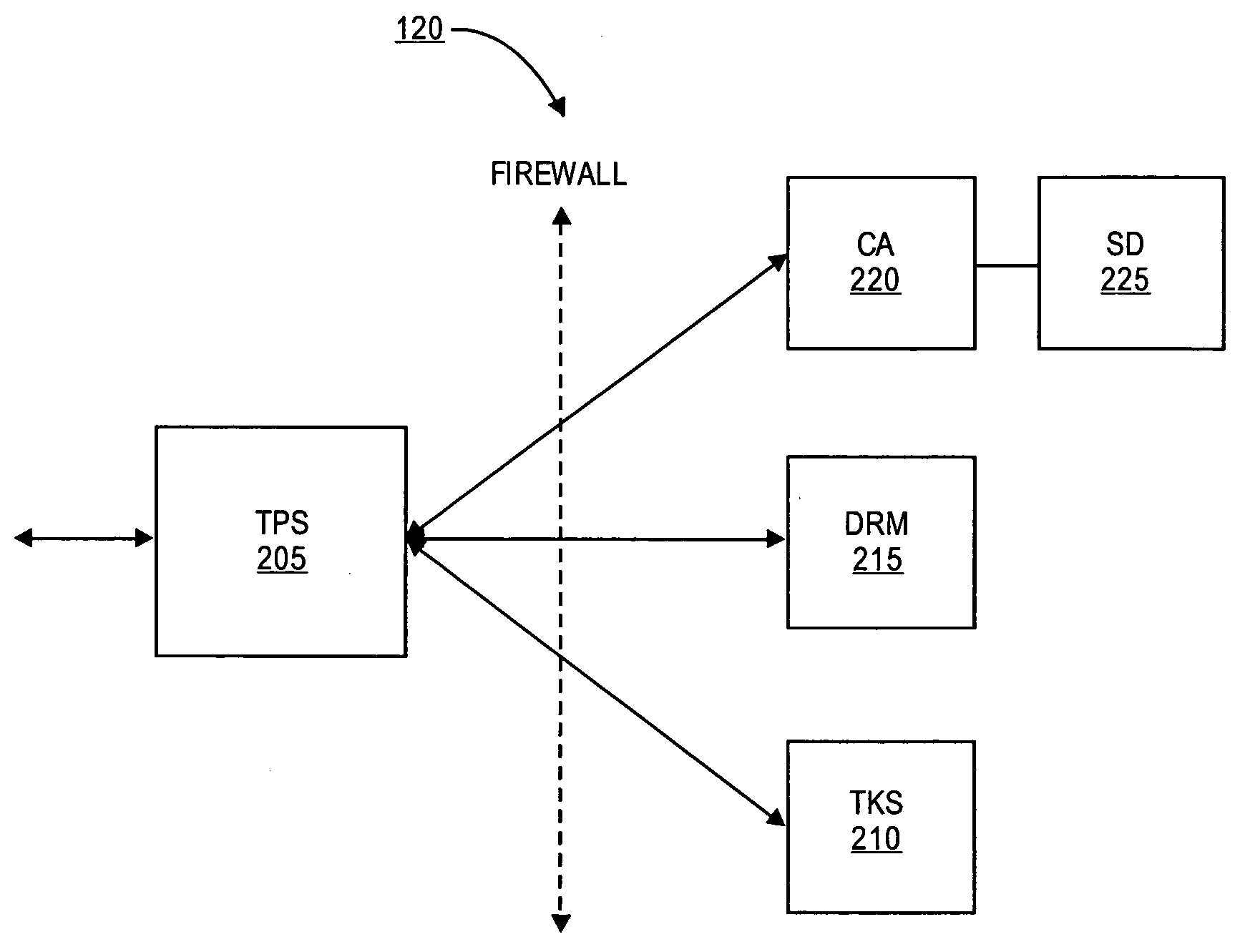
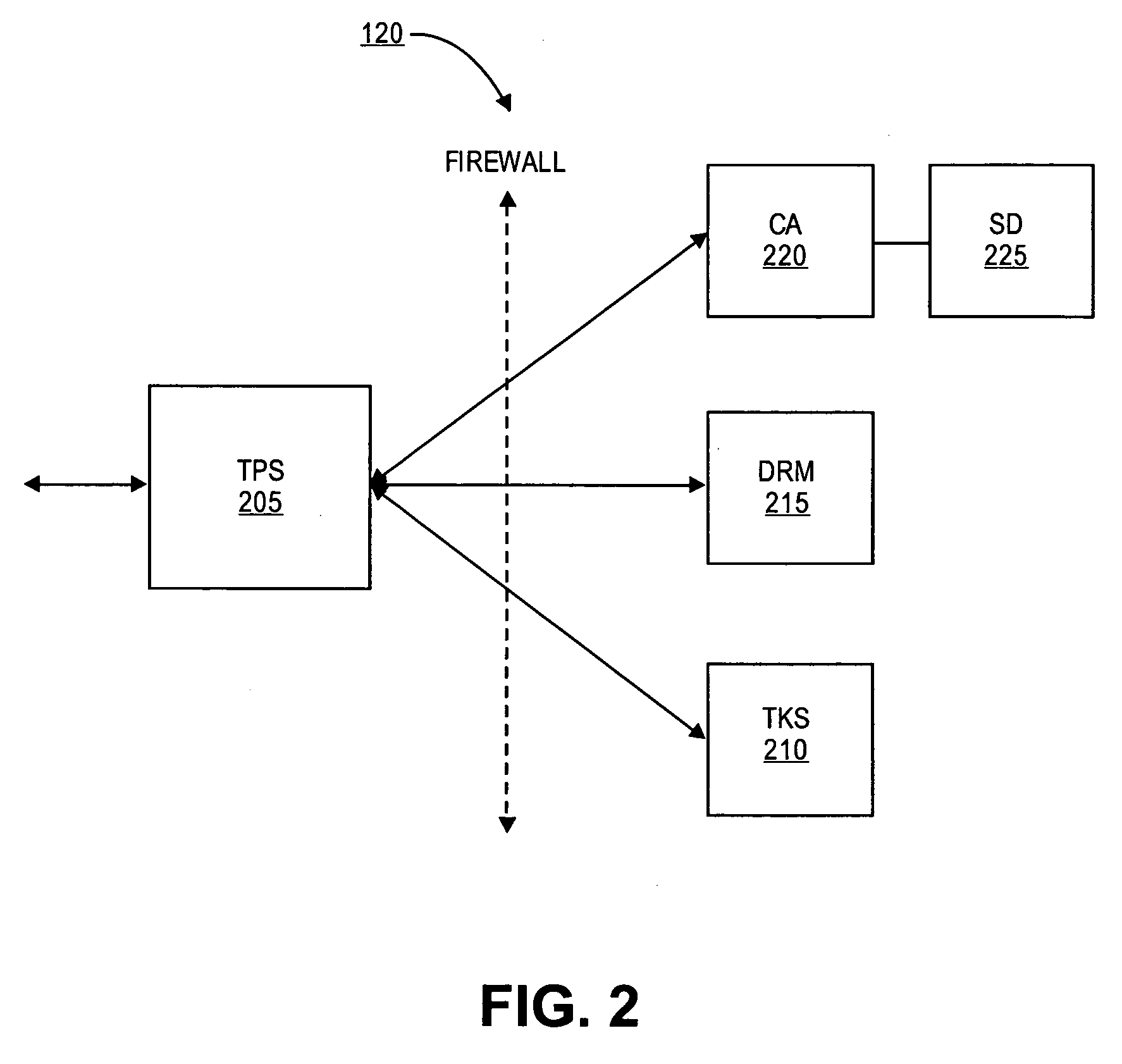
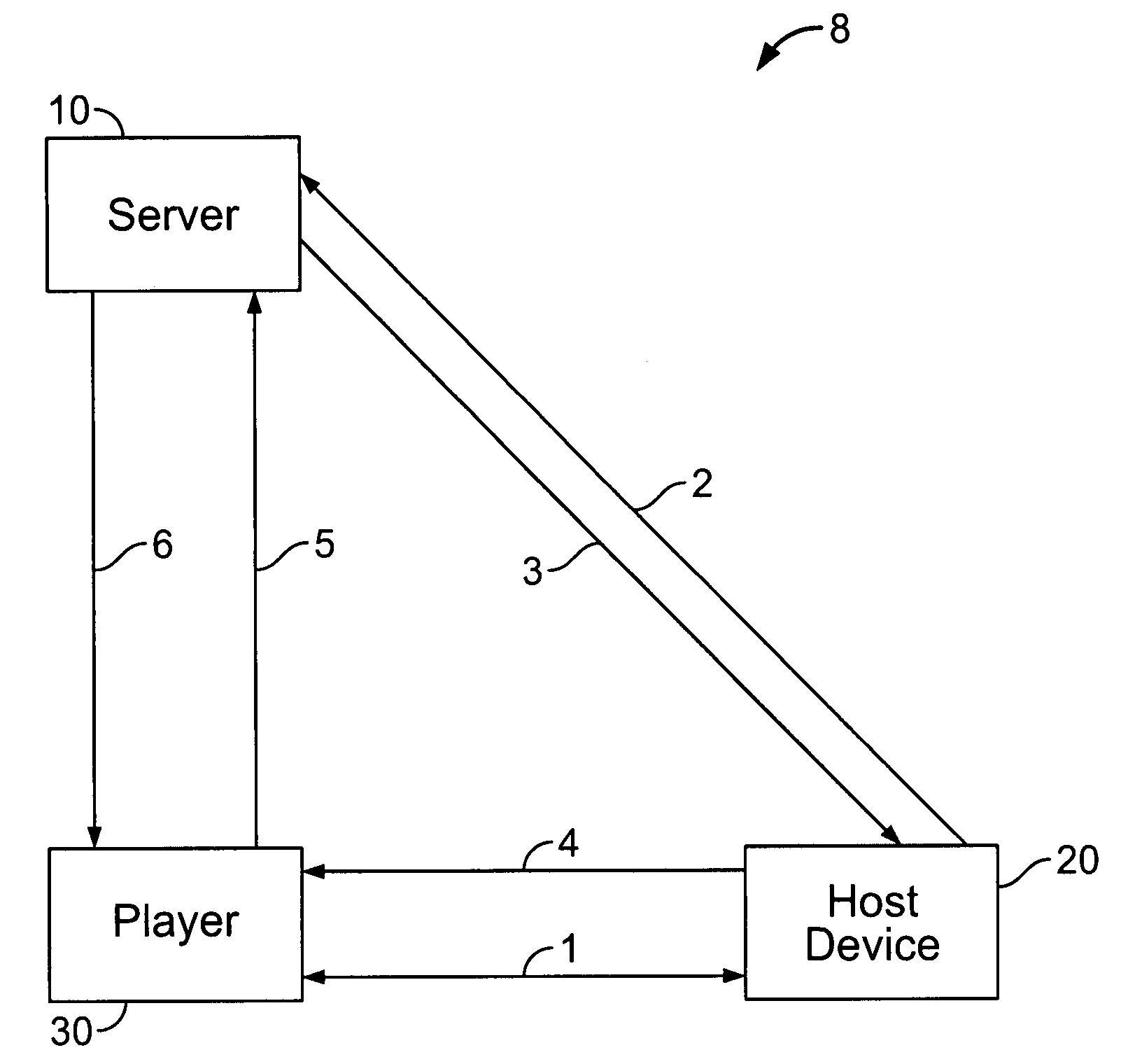
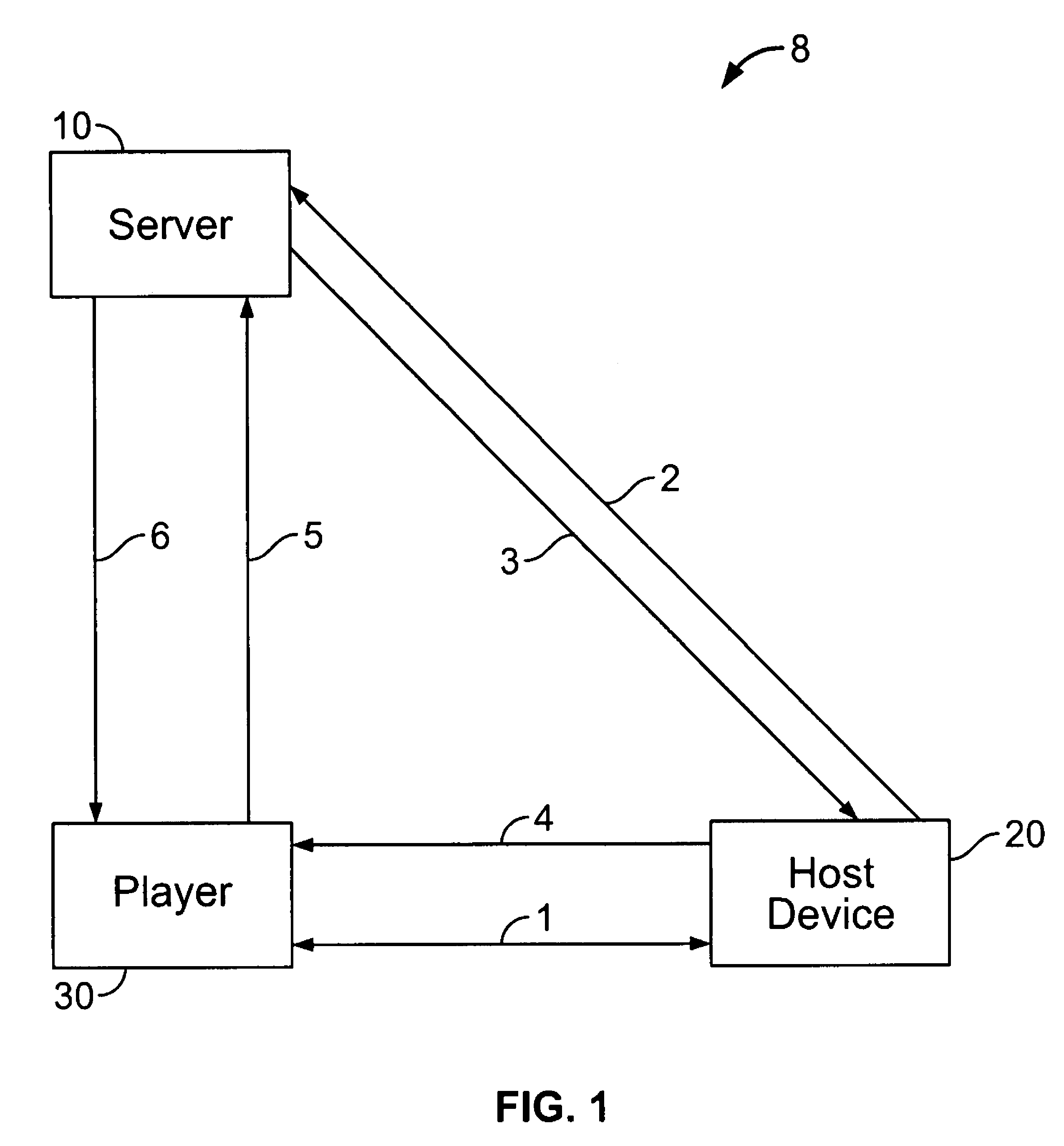
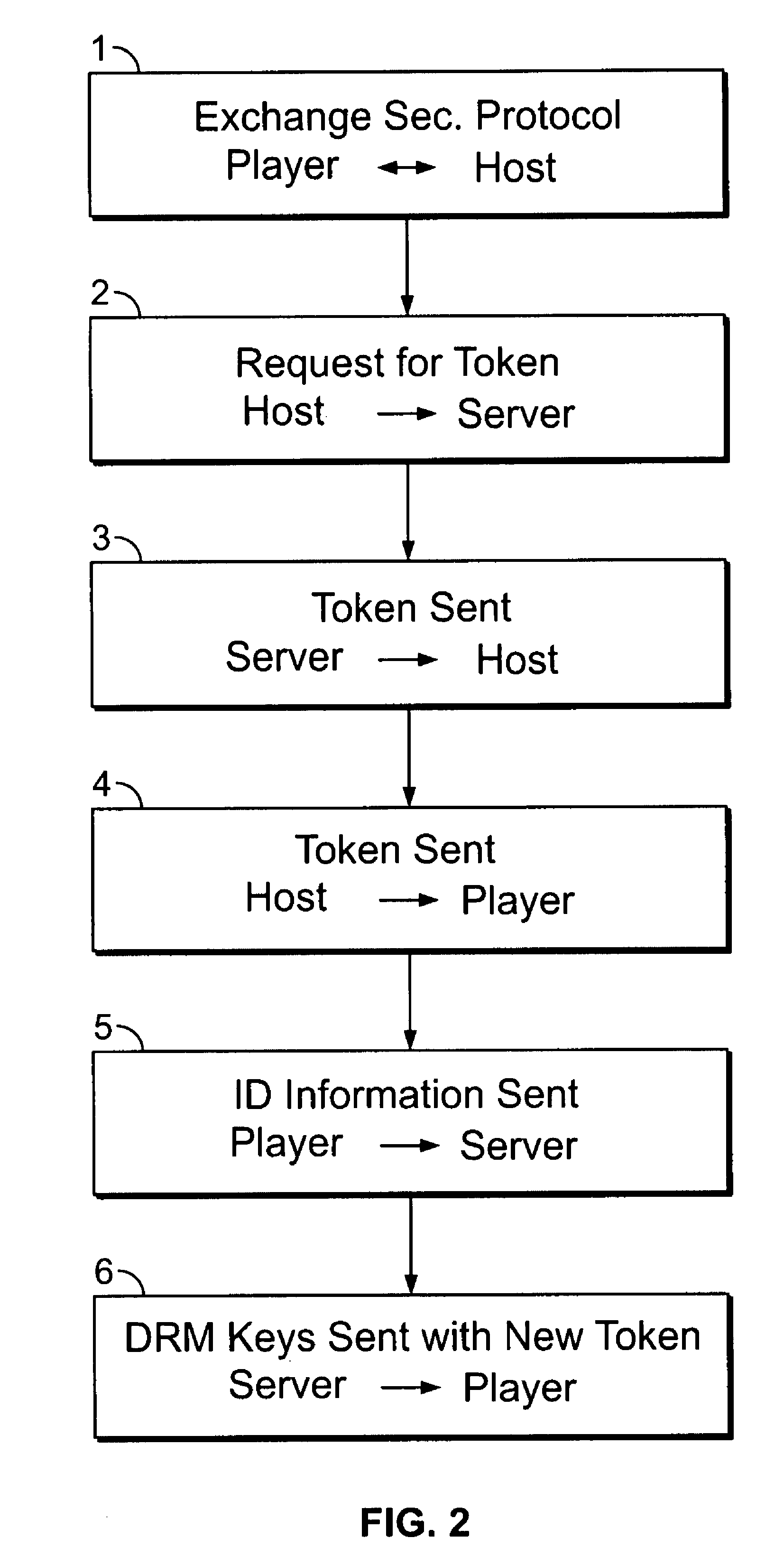
Token passing technique for media playback devices
InactiveUS7975312B2Preventing playing of contentImprove convenienceSynchronising transmission/receiving encryption devicesDigital data processing detailsRelevant informationDigital content
A digital rights management (DRM) system for distribution of digital content such as audio or video uses a token passing scheme to enhance security of the content from unauthorized access and use, including access by unauthorized players. The token is requested from the central content or DRM server by a host device such as a user's computer, using security related information. The token is then passed to a media player associated with the host device, the token being encrypted using a key special to that particular player. Upon receipt of the token, the player transmits back to the server certain related security information confirming receipt of the token and in return receives keys for decryption of the associated digital content. In the absence of proper passing of the token, player access to the content, or further access to other content, is denied. This also allows the player to communicate directly with the server for obtaining the keys.
Owner:APPLE INC
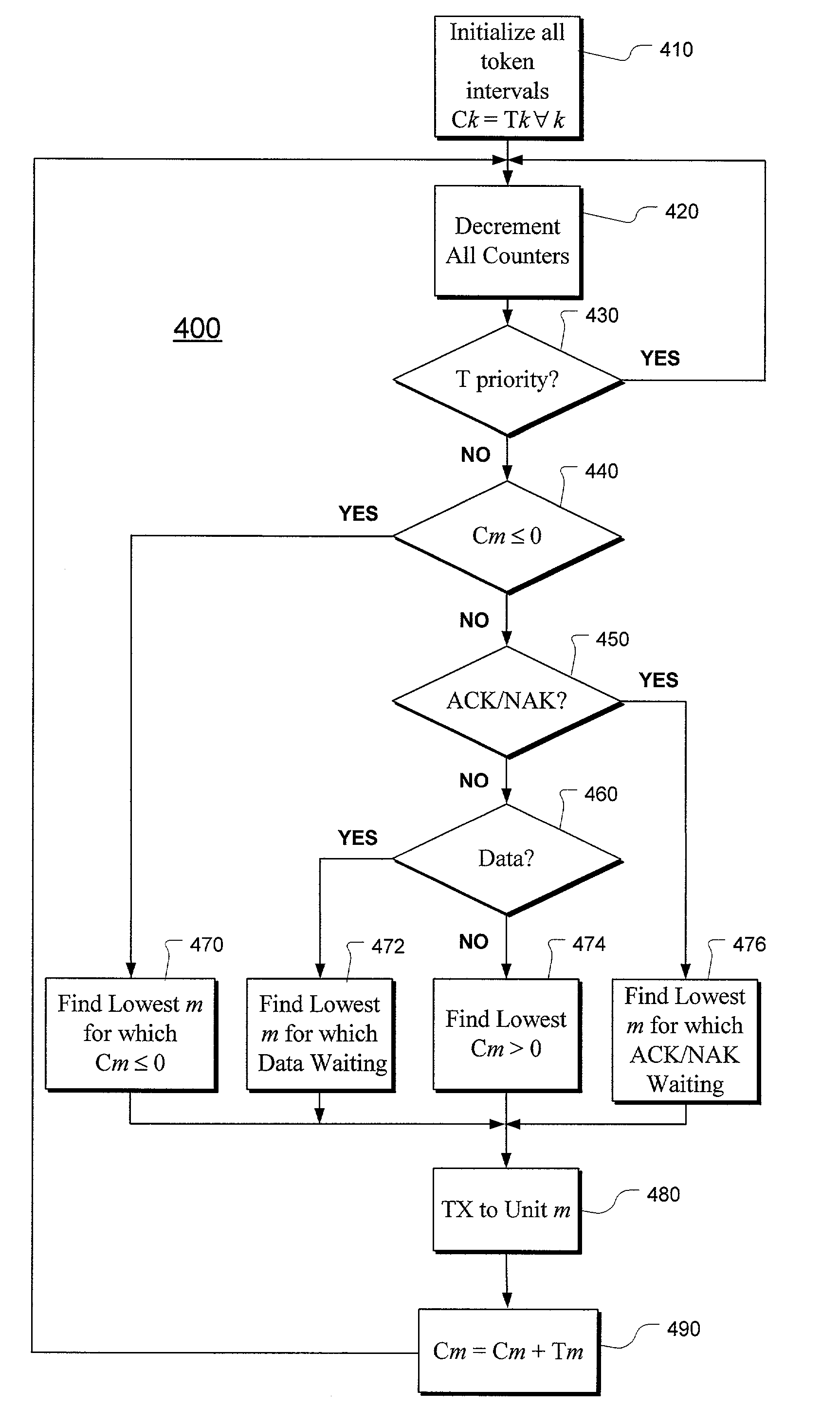
Method and apparatus for token distribution
InactiveUS6965933B2Multiplex communicationDigital computer detailsInterval valuedDistributed computing
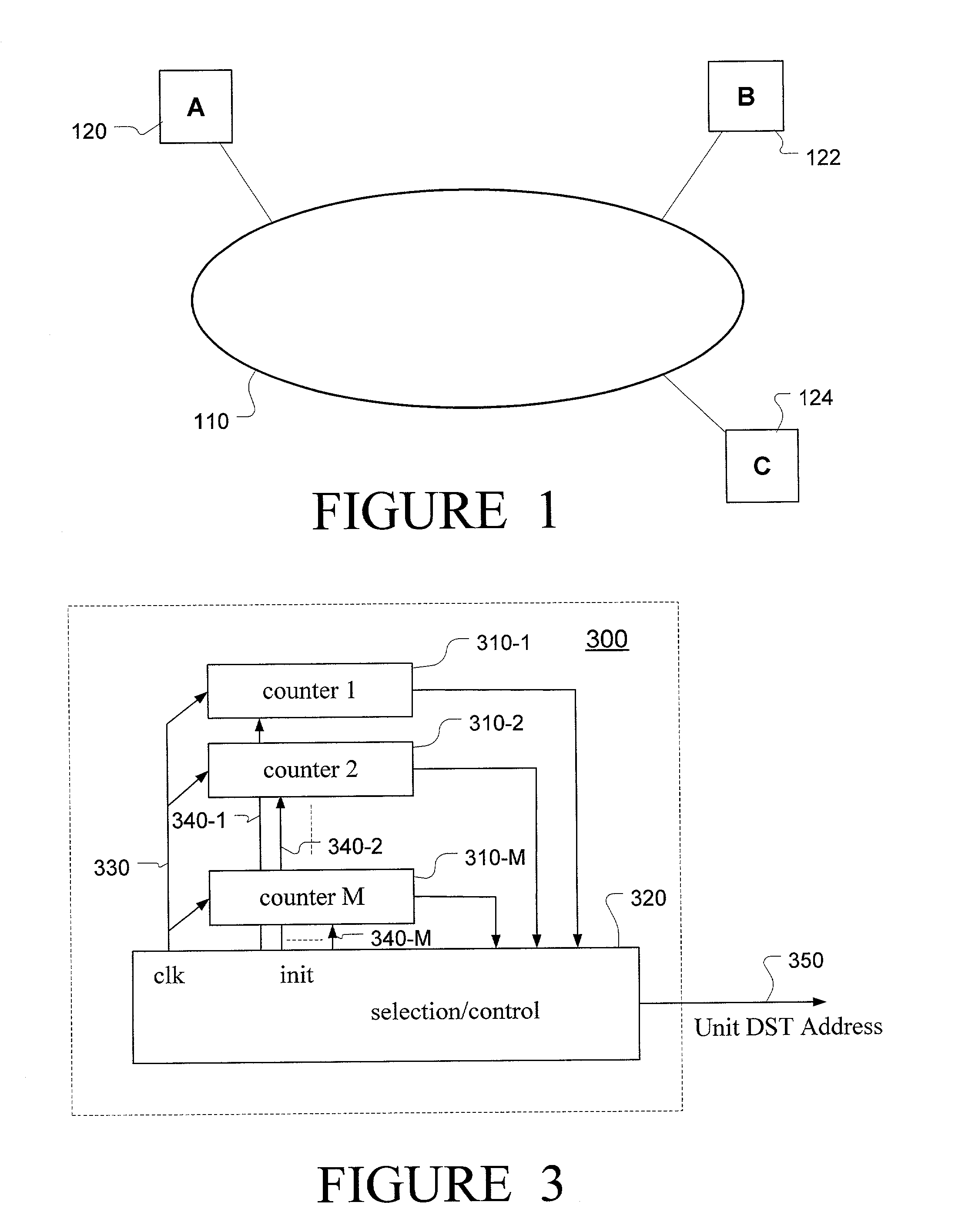
A method and apparatus for token distribution include providing one or more nodes of a plurality of network nodes with a token machine that includes counters associated with each of other network nodes having a token machine. Each time a token possessing network node implicitly or explicitly passes the token to another network node having a token machine, counter values of each of the counters associated with each node having a token machine are adjusted. When a token is passed, the counter value of the receiving node is adjusted based, at least in part, on an initial token interval value, and counter values associated with other nodes are adjusted toward a threshold value. The decision as to where the token is passed may be based, at least in part, on the value of a counter and / or an assigned counter priority level. The system or method also may include priority slots in which the token is unconditionally passed to a node assigned the priority slot, and an ARQ scheme for acknowledgment of transferred information.
Owner:TELEFON AB LM ERICSSON (PUBL)
Method and apparatus for an ad-hoc wireless communications system
InactiveUS20130070715A1Wireless commuication servicesData switching networksCommunications systemLatency (engineering)
An IBSS that allows token passing for round-robin service of QoS flows is disclosed (an RRBSS). The RRBSS permits low-latency, reduced contention, distributed scheduling useful in any ad hoc network, but particularly suitable for high data rates. Distributed scheduled access is provided for flows through a round-robin token passing service discipline. STAs follow a round-robin order, or list, and are able to communicate with round-robin transmit opportunities during a defined period. Each STA in the list transmits a respective token to transfer access to the shared medium to the next STA in the RR List. Techniques are disclosed to add and remove STAs to the sequence, establish connectivity lists (receive and forward), and maintain other sequence parameters such as bandwidth management and TXOP duration. Various other aspects are also disclosed.
Owner:QUALCOMM INC
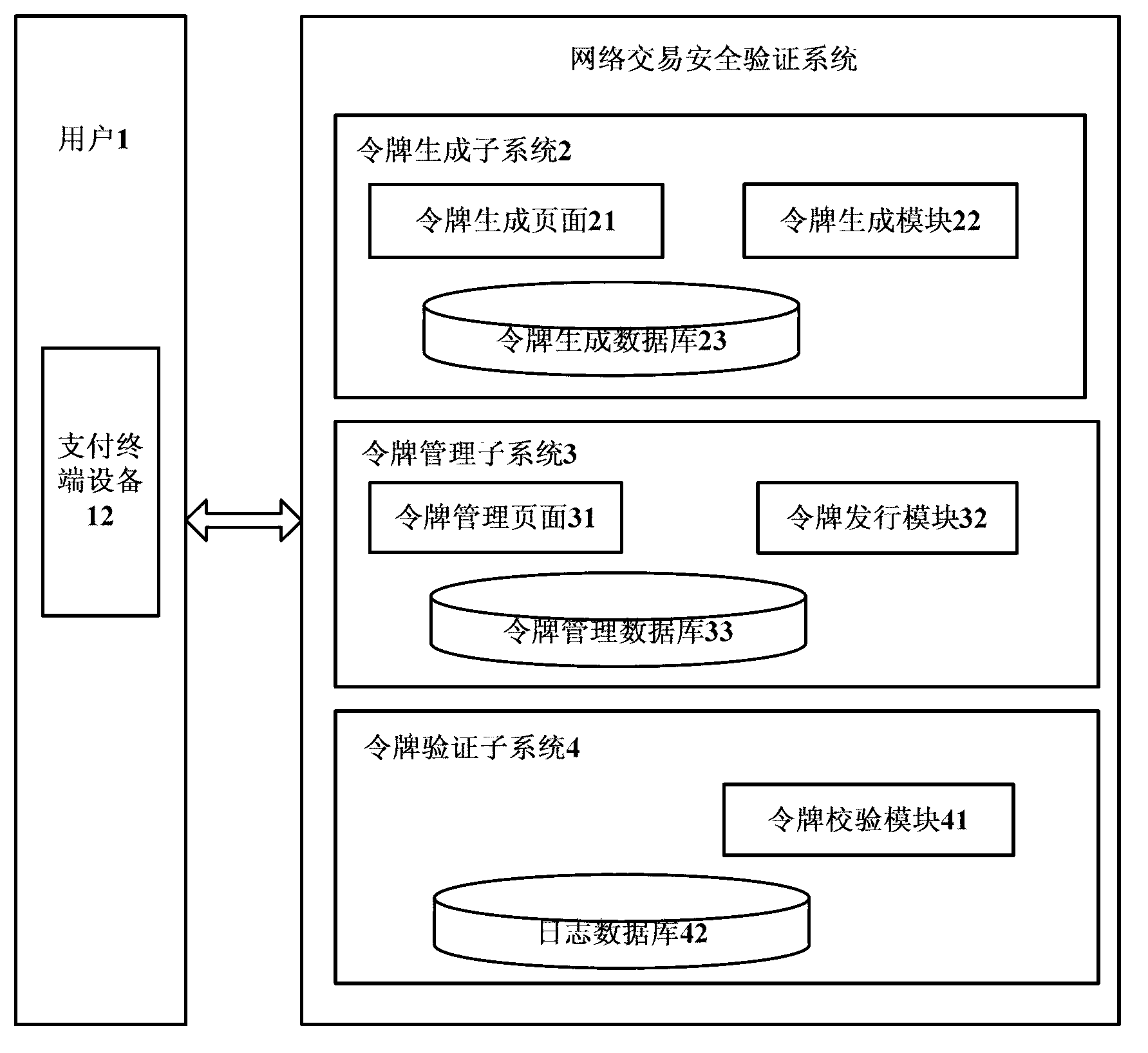
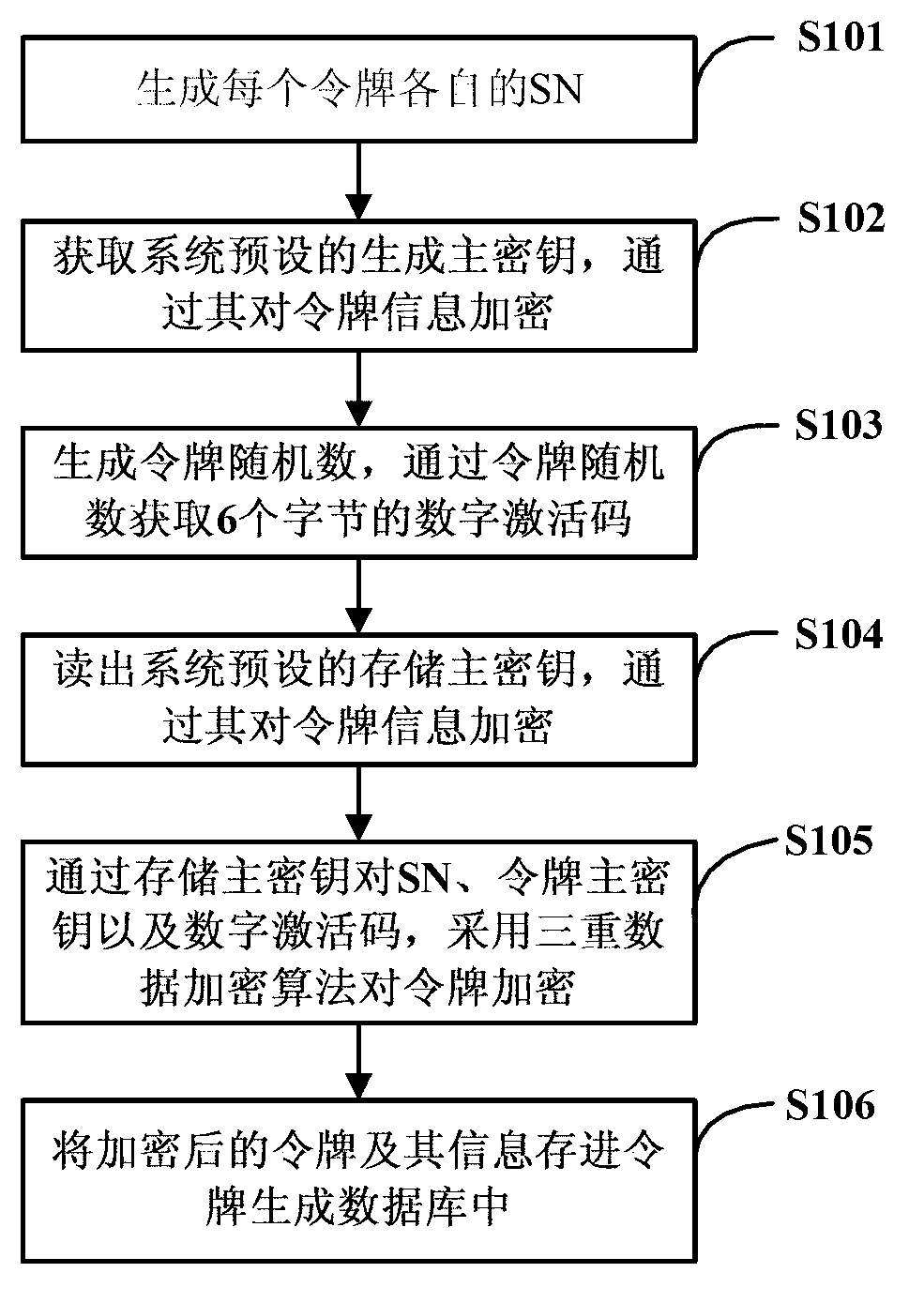
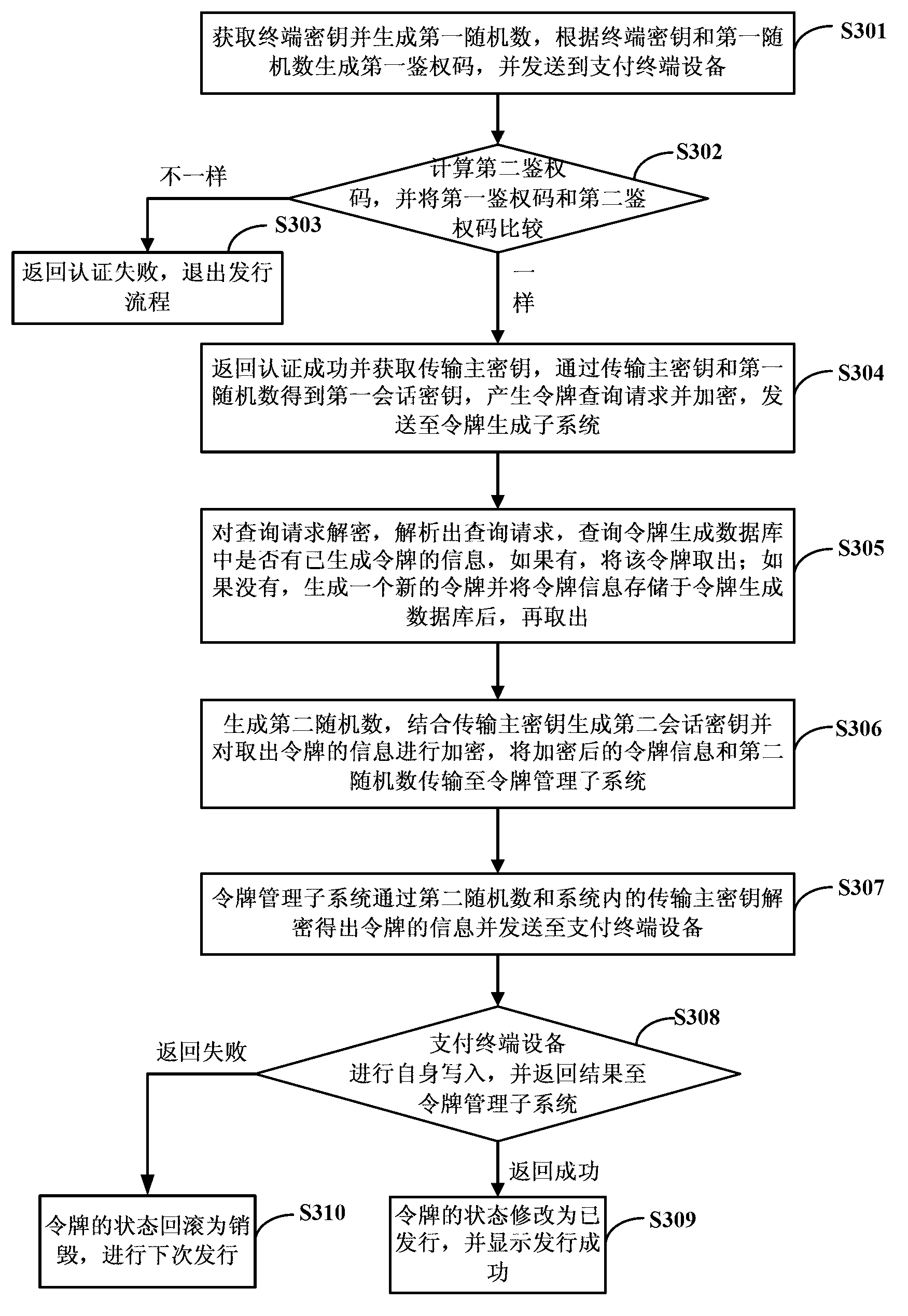
Security verification system based on distributed network transaction
ActiveCN103023657APrevent unauthorized use of certificate storage media for signature operationsEnsure safetyUser identity/authority verificationCommerceDistributed structureMaterial resources
The invention provides a security verification system based on distributed network transaction and relates to the field of network transaction security of financial institutions. The security verification system is in remote connection with a payment terminal device of a user and comprises a token generation subsystem, a token management subsystem and a token verification subsystem. The token generation subsystem is used for generating encrypted tokens, and information of each token comprises a serial number, a token key and a digital activation code. The token management subsystem is used for managing token issuing, toke loss reporting or token destroying. The token verification subsystem is used for verifying the payment terminal device of the user. The three subsystems are disposed in a distributed manner, the three subsystems are provided with a same transmission main key inside, remote communication is applied among the different subsystems, and information of the communicated token each time is re-encrypted. By the security verification system, operations such as signature by theft on certificate storage medium by computer Trojan online can be prevented effectively, and security of an online transaction system is guaranteed. In addition, by the use of the distributed structure, expandability is high, and manpower and material resources costs are reduced.
Owner:WUHAN TIANYU INFORMATION IND
Wireless channel access control method based on virtual token
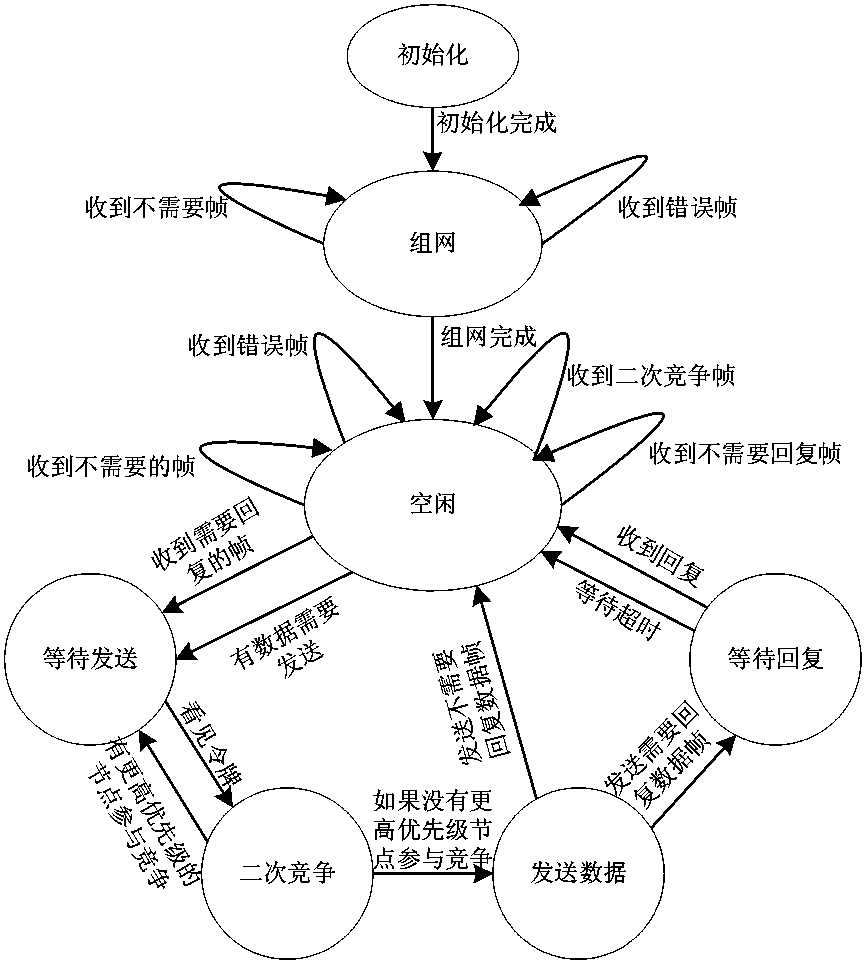
A wireless channel access control method based on a virtual token comprises the following steps of: A, a plurality of nodes are selected, one node is designated as a center node, the other nodes are called as wireless nodes, B, the center node generates a token, some wireless node is designated to hold the token, C, if the center node can monitor that the wireless node of some address uses the token, token passing succeeds, D, if monitoring fails, the token is re-passed for designated times or a data frame is broadcast, another node is designated to hold the token, E, the number of the nodes is updated, F, when the token is lost, the center node generates a token again, G, the nodes are monitored, the token is abandoned, the center node generates a token again, and H, Steps A-G are repeated. The method has the benefits that a secondary competitive mechanism is introduced, with the adoption of a node priority strategy, transmission requirements of emergency messages are met, the high reliability and timeliness of a network are guaranteed, and the effective utilization rate of the network is increased by data frame fusion.
Owner:CHINA SHIP DEV & DESIGN CENT
Multistandard video decoder and decompression system for processing encoded bit streams including a decoder with token generator and methods relating thereto
InactiveUS20030182544A1Digital data processing detailsMemory adressing/allocation/relocationComputer hardwareVideo decoder
A pipeline video decoder and decompression system handles a plurality of separately encoded bit streams arranged as a single serial bit stream of digital bits and having separately encoded pairs of control codes and corresponding data carried in the serial bit stream. The pipeline system employs a plurality of interconnected stages to decode and decompress the single bit stream, including a start code detector. When in a search mode, the start code detector searches for a specific start code corresponding to one of multiple compression standards. The start code detector responding to the single serial bit stream generates control tokens and data tokens. A respective one of the tokens includes a plurality of data words. Each data word has an extension bit which indicates a presence of additional words therein. The data words are thereby unlimited in number. A token decode circuit positioned in certain of the stages recognizes certain of the tokens as control tokens pertinent to that stage and passes unrecognized control tokens to a succeeding stage. A reconfigurable decode and parser processing means positioned in certain of the stages is responsive to a recognized control token and reconfigures a particular stage to handle an identified data token. Methods relating to the decoder and decompression system include processing steps relating thereto
Owner:COASES INVESTMENTS BROS L L C
Low latency FIFO circuit for mixed clock systems
InactiveUS7197582B2Avoid procrastinationDigital storageInput/output processes for data processingTime domainProcessor register
A FIFO design interfaces a sender subsystem and a receiver subsystem operating on different time domains. The sender subsystem and the receiver subsystem may be synchronous or asynchronous. The FIFO circuit includes a put interface configured to operate in accordance with the sender time domain and get interface configured to operate in accordance with the receiver time domain. The FIFO circuit includes an array of cells having a register and state controller indicative of the state of the cell. Each cell also has a put component part configured to operate according to the sender time domain including a put token passing circuit and put controller circuit. Each cell has get component part configured to operate according to the receiver time domain including a get token passing circuit and a get controller circuit. A mixed-clock relay station design interfaces a sender subsystem and a receiver subsystem working at different time domains, and where the latency between sender and receiver is large.
Owner:THE TRUSTEES OF COLUMBIA UNIV IN THE CITY OF NEW YORK
System and method to assist building automation system end user based on alarm parameters
ActiveUS20180061212A1Particular environment based servicesAlarmsNetwork Communication ProtocolsSystem parameters
Disclosed are systems and methods for operating a Building Automation System (BAS) that communicates with end devices via a master-slave token passing network (MSTP), e.g., BACNet, a local operating network (LON), or any other suitable communications protocol to receive alarm messages. The BAC enables a user to rapidly and effectively respond to an alarm by providing an alarm assistance message that provides the user with detailed remediation procedures concerning the current alarm. The nature and content of the alarm assistance message and / or the attachments is determined based upon on a combination of alarm and system parameters, and may be tailored by an administrator to meet local requirements. The alarm assistance message may include one or more remedial or diagnostic attachments, such as a troubleshooting guide, user manual, a video, graphics, or a firmware update, and may include links to external media or cloud-hosted documents.
Owner:TRANE INT INC
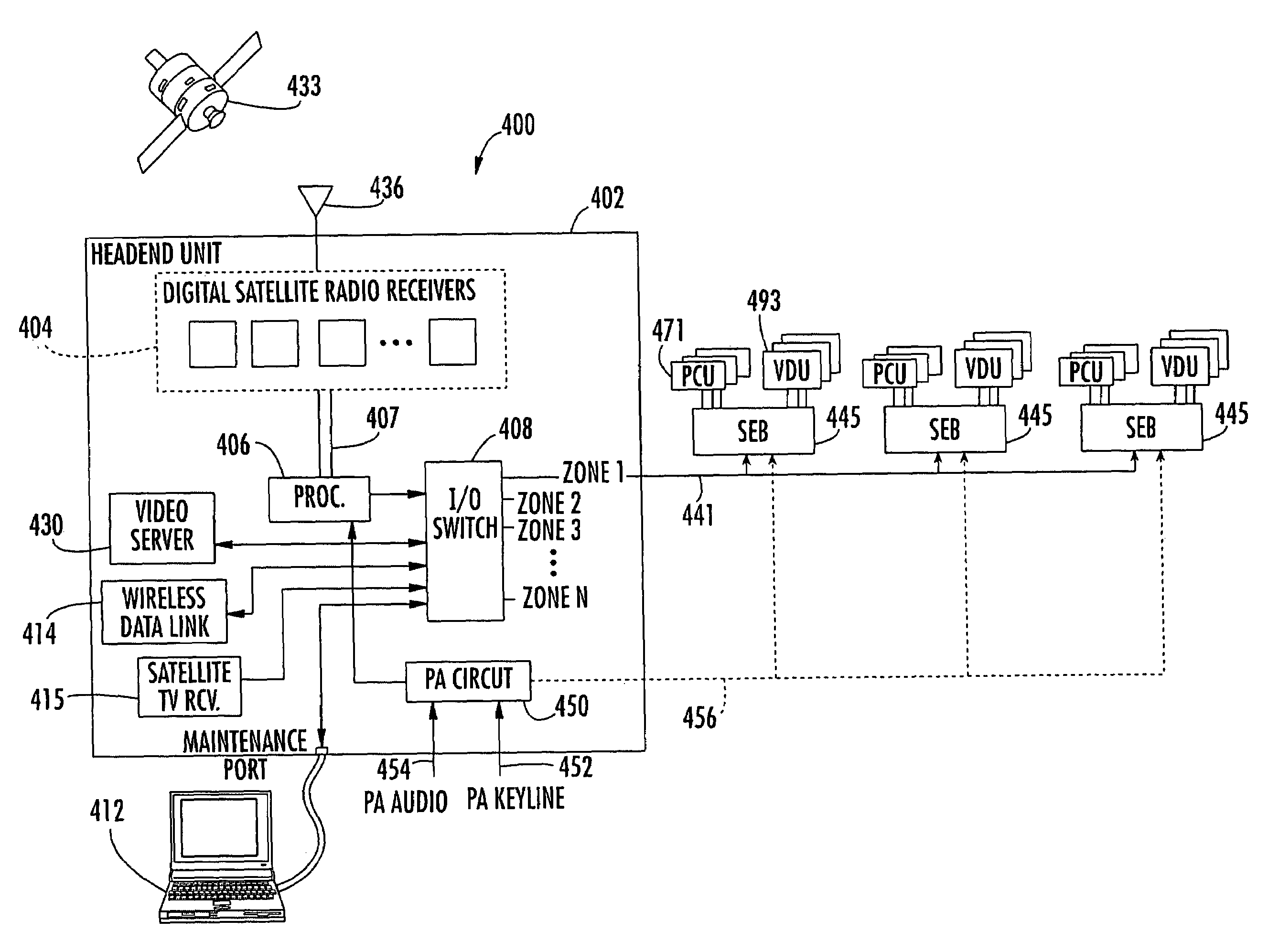
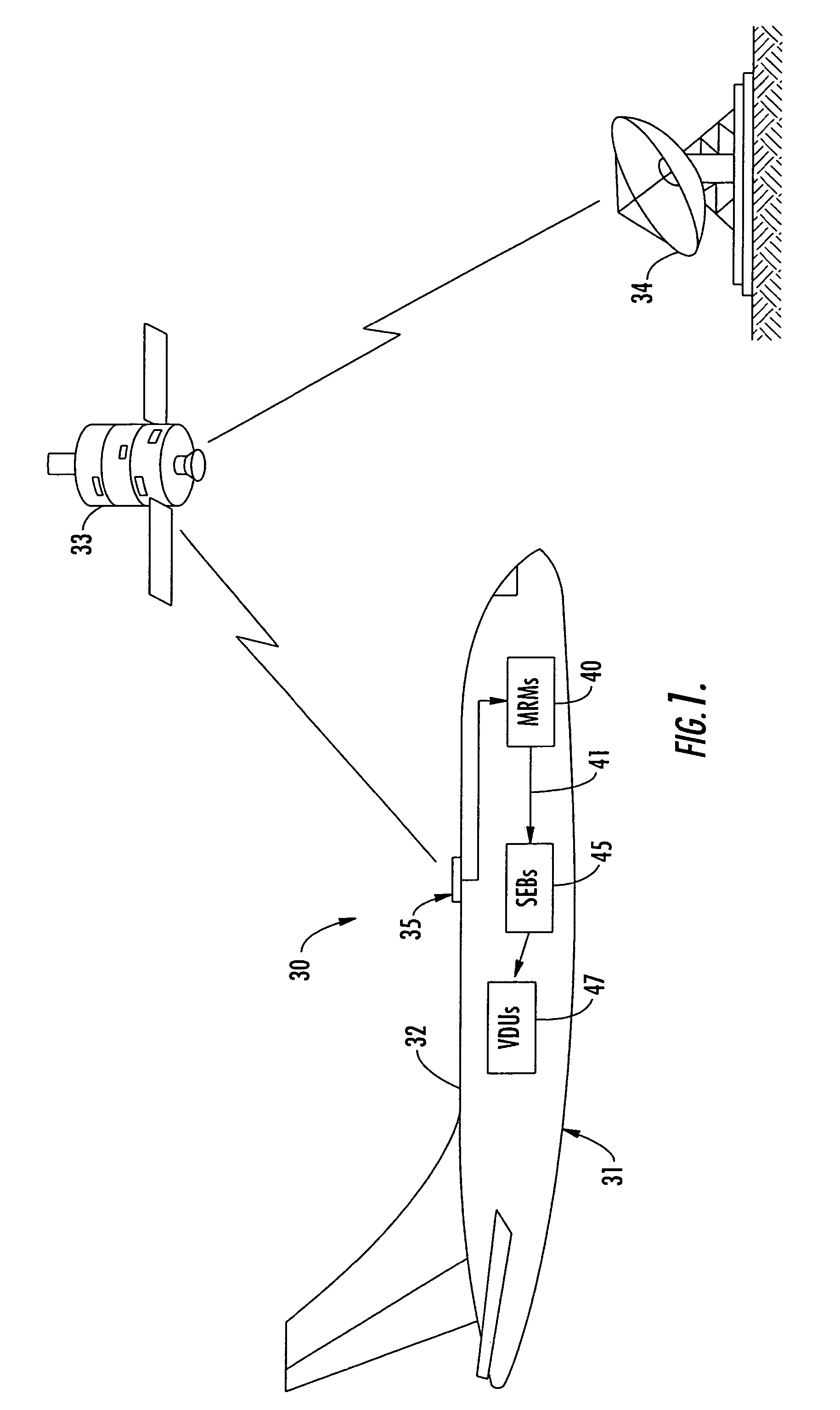
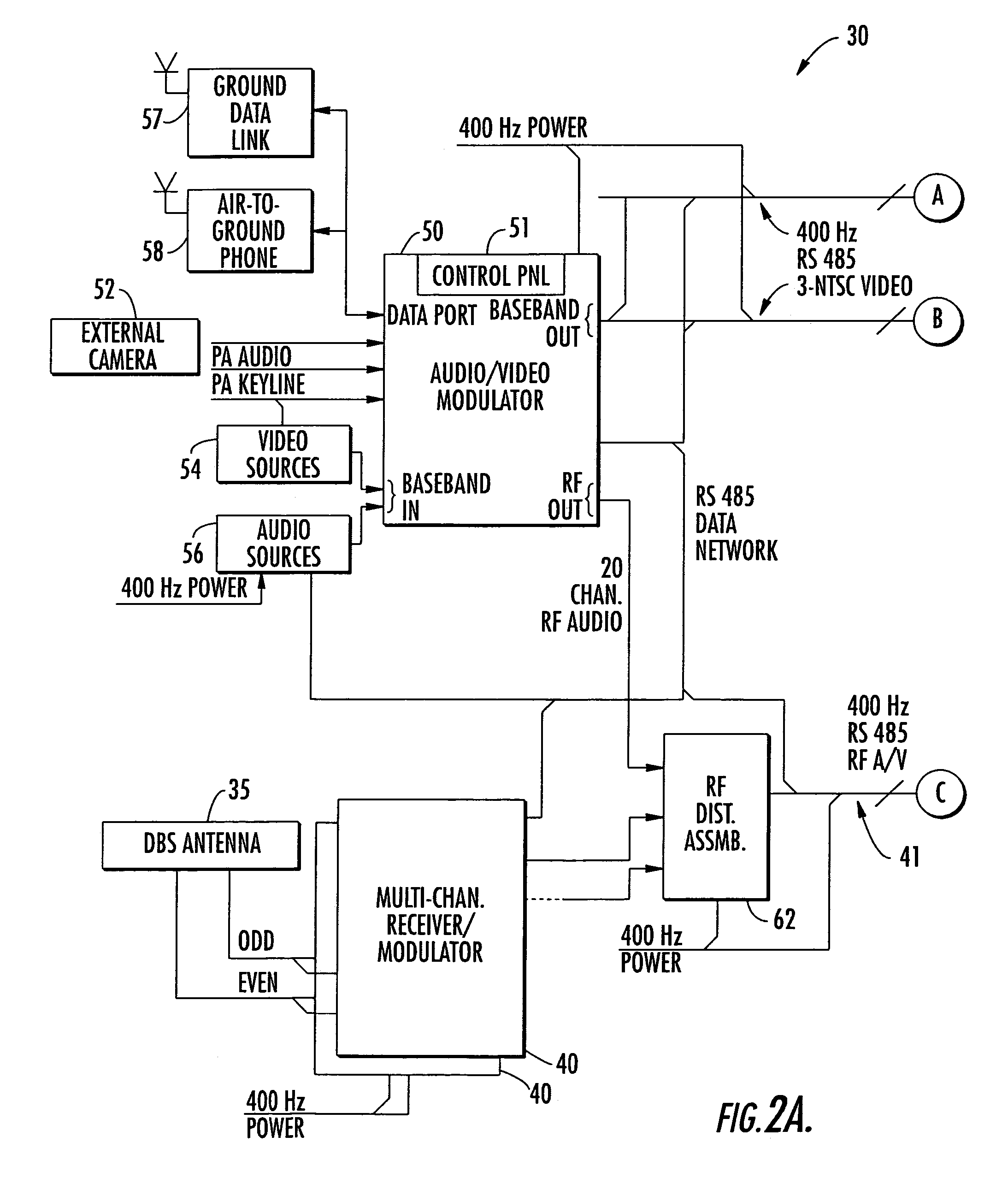
Aircraft in-flight entertainment system including a registration feature and associated methods
ActiveUS7587734B2Shorten the timeImprove availability and reliabilityDigital computer detailsClosed circuit television systemsComputer scienceAirplane
An aircraft in-flight entertainment system includes a plurality of seat electronic boxes (SEBs) spaced throughout the aircraft. Each SEB is configurable for passing a registration token along to an adjacent SEB. Cabling connects the SEBs together in a daisy chain configuration. Registration circuitry is connected to the cabling for identifying a location of each SEB based upon passing of the registration token among the plurality of SEBs.
Owner:LIVETV
Speech recognition system and technique
Owner:KK TOSHIBA
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com