Detection method, system and apparatus of zombie network
A botnet and detection method technology, applied in the transmission system, digital transmission system, data exchange network, etc., can solve the problem of not being able to detect the communication messages of the botnet in real time, and not being able to quickly and accurately locate the botnet and its operators and other issues to achieve the effect of network communication security and avoiding harm
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
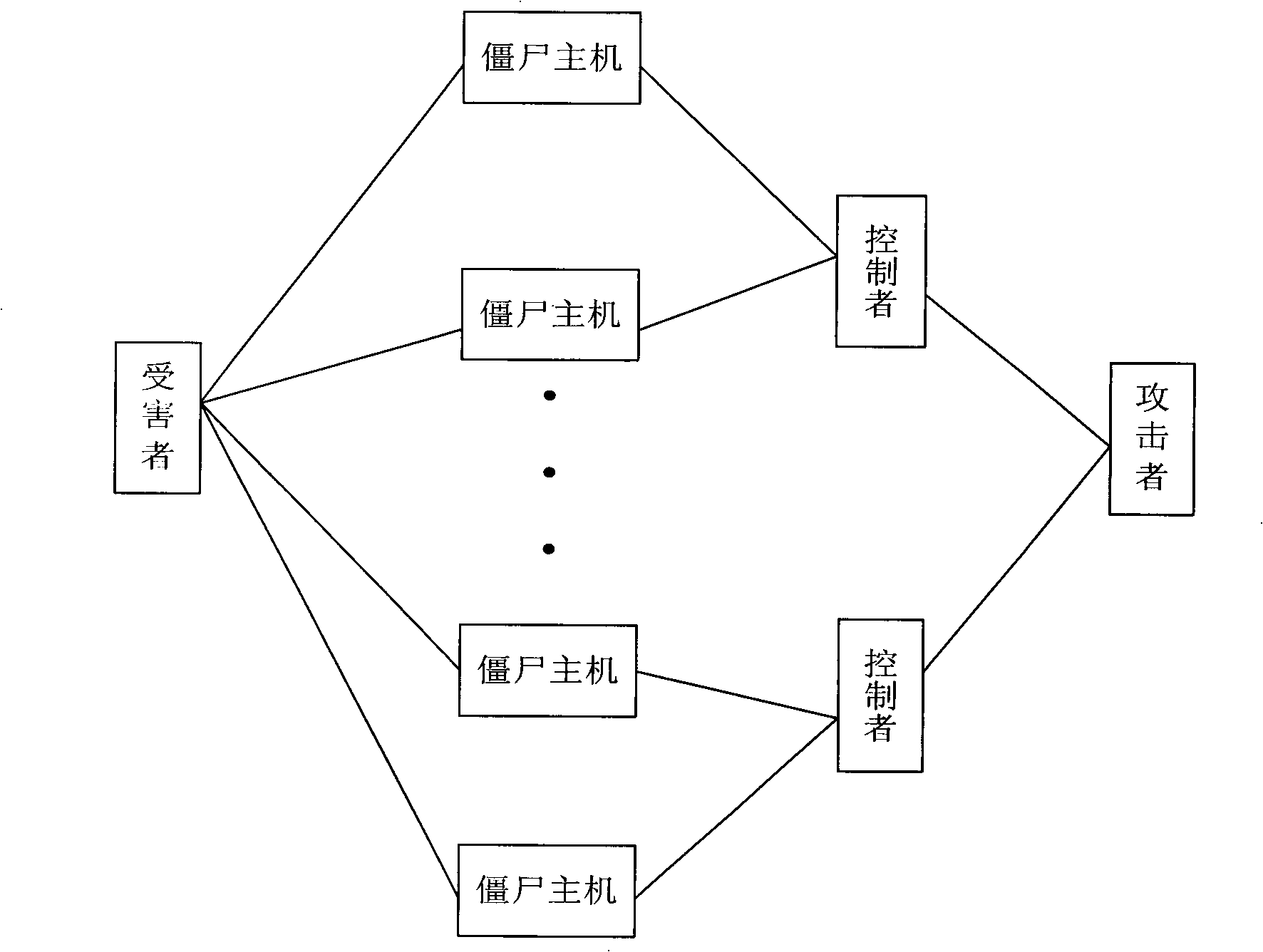
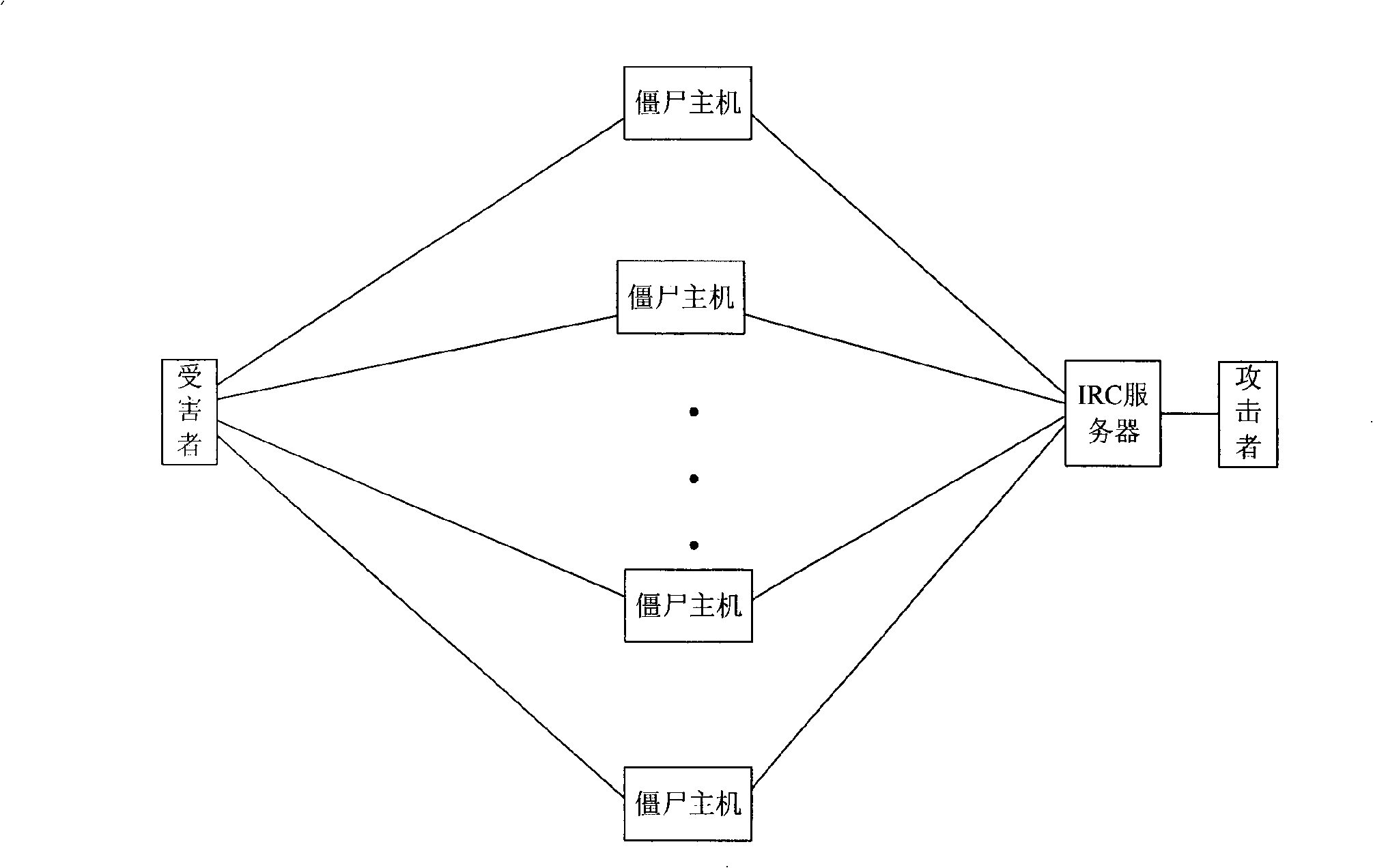
[0042]The embodiment of the present invention provides a method for detecting a botnet. The method identifies the botnet message through rule matching between the communication message and the rules stored in the rule base, thereby realizing the detection of the botnet.
[0043] Before the botnet detection system performs detection, a rule base has been formed and stored in the database. Among them, the specific steps of the rule base formation process are:
[0044] Step A: The botnet detection system analyzes the communication messages between the bot host and the controller in the detected or existing botnet, extracts the characteristics of the bot messages from the communication messages, and forms a feature library;
[0045] Wherein, the characteristics of the zombie message extracted from the communication message are specifically the name of the zombie tool, the type of the protocol, the type of the botnet, and the like.
[0046] Step B: converting the feature library i...
Embodiment 2
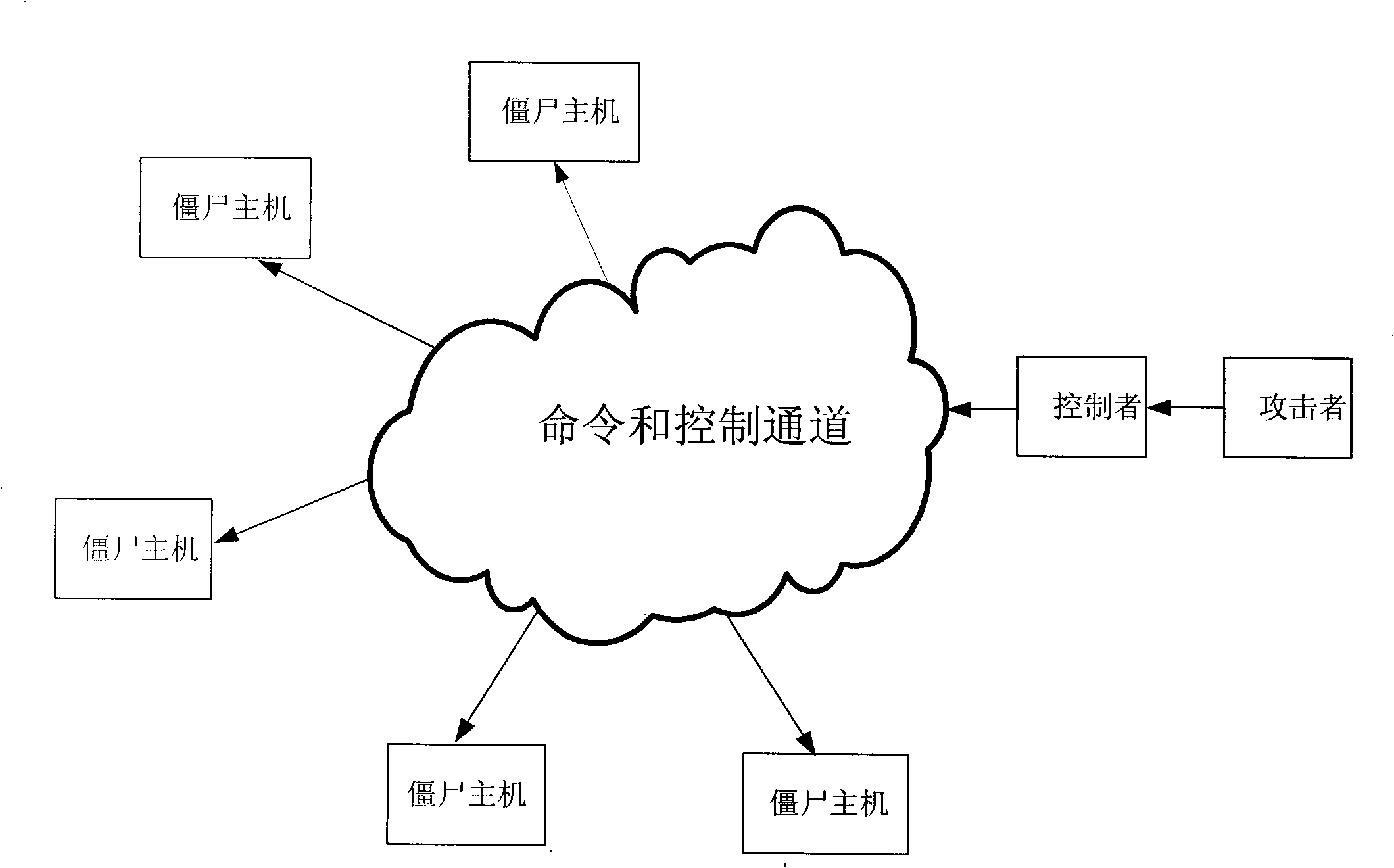
[0089] If the communication message of the botnet is featureless or the feature disappears after encryption, or is a new botnet tool, the embodiment of the present invention provides a botnet detection method for the above situation. The method is to identify the zombie host and the controller according to the difference between the network behavior between the zombie host and the controller and the network behavior between normal users, and save the botnet communication messages between them for use in Manually extract message features to improve the message feature library in Embodiment 1. see Image 6 ,Specific steps are as follows:
[0090] Step 201: the monitoring and analysis center of the botnet detection system receives the IP address list to be detected, and sends the IP address list to the network probe;
[0091]Wherein, the above-mentioned list of IP addresses to be detected is specifically a list of IP addresses that launch attacks or are suspected to be detected...
Embodiment 3
[0104] In order to better grasp the information of the botnet, the embodiment of the present invention also provides two auxiliary means: active detection and remote packet capture, which are used to confirm the information of the botnet; The specific implementation steps of using these two methods to detect botnets are described in detail below.
[0105] (1) see Figure 7 , the specific steps of active detection are as follows:
[0106] Step 301: the botnet detection system simulates a botnet host to send a botnet communication message to the IP suspected of being the controller;
[0107] Among them, the botnet communication message provided by the botnet detection system is the detection message, which has the detection option that the content is blocked, and in some cases, the user is allowed to construct the detection message by himself, so that the user has greater freedom;
[0108] The specific behavioral characteristics of the suspected controller are: regular communi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com