Certifying and key consulting method and its device based on TTP
A key agreement and key material technology, which is applied in the field of TTP-based authentication and key agreement, can solve the problems of the Diffie-Hellman key exchange protocol being irresistible, and achieve the effect of preventing midway interception and leakage, and preventing man-in-the-middle attacks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
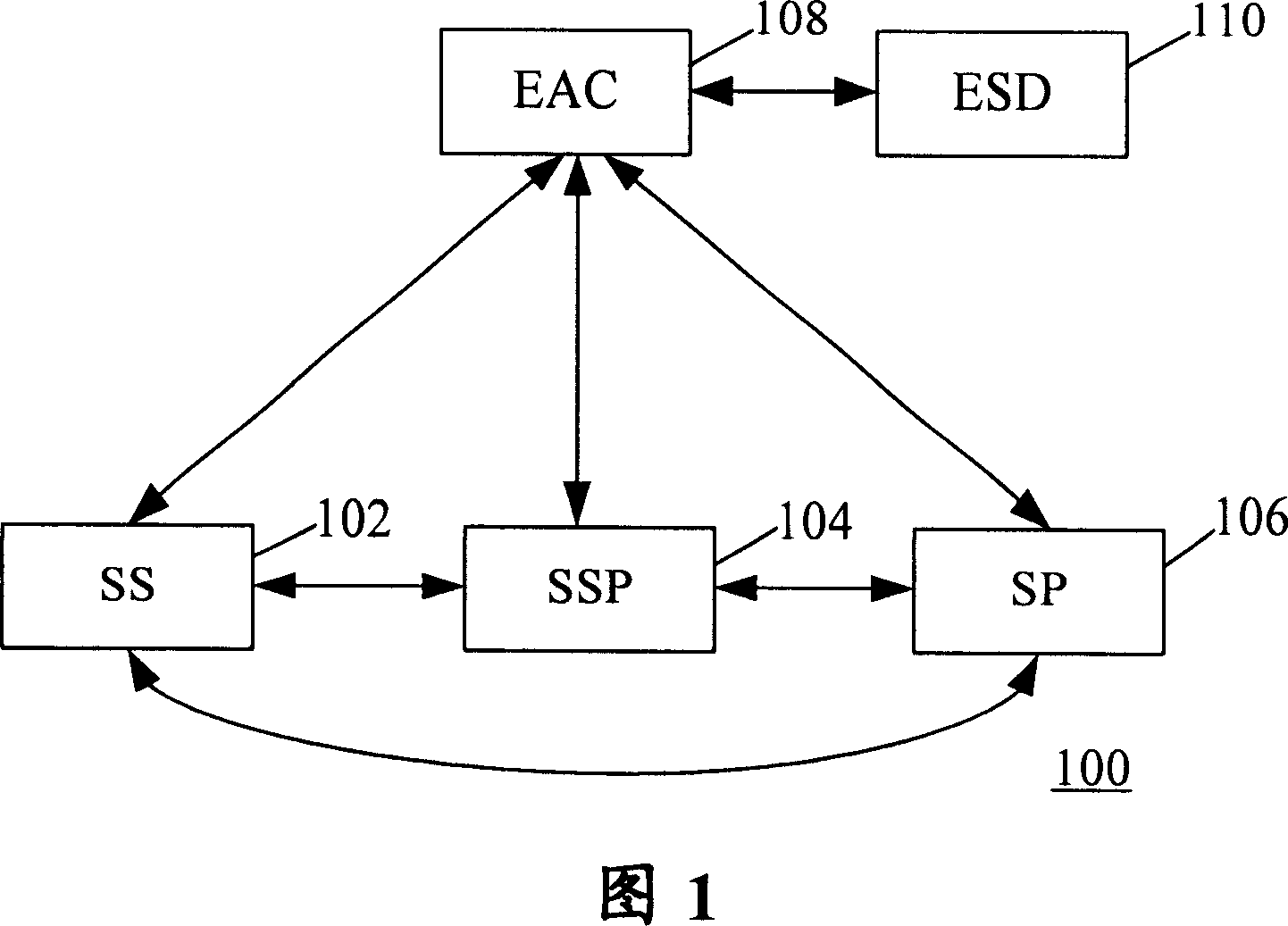
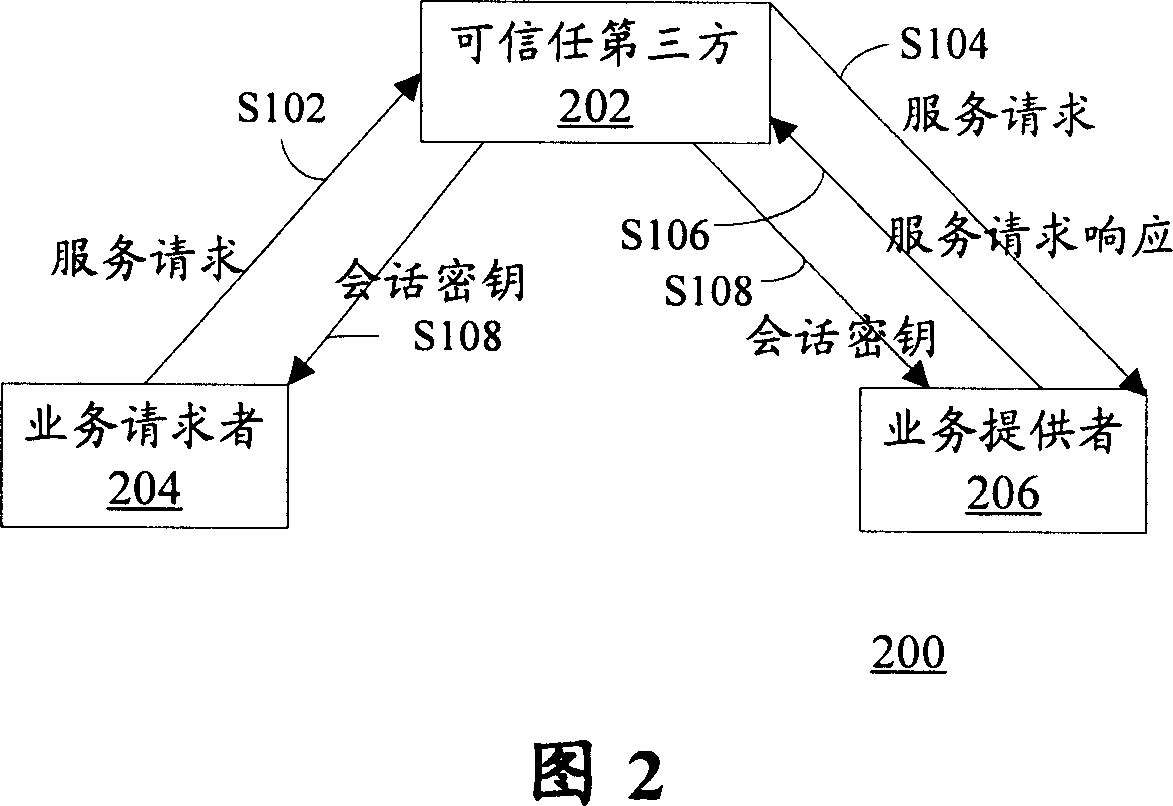
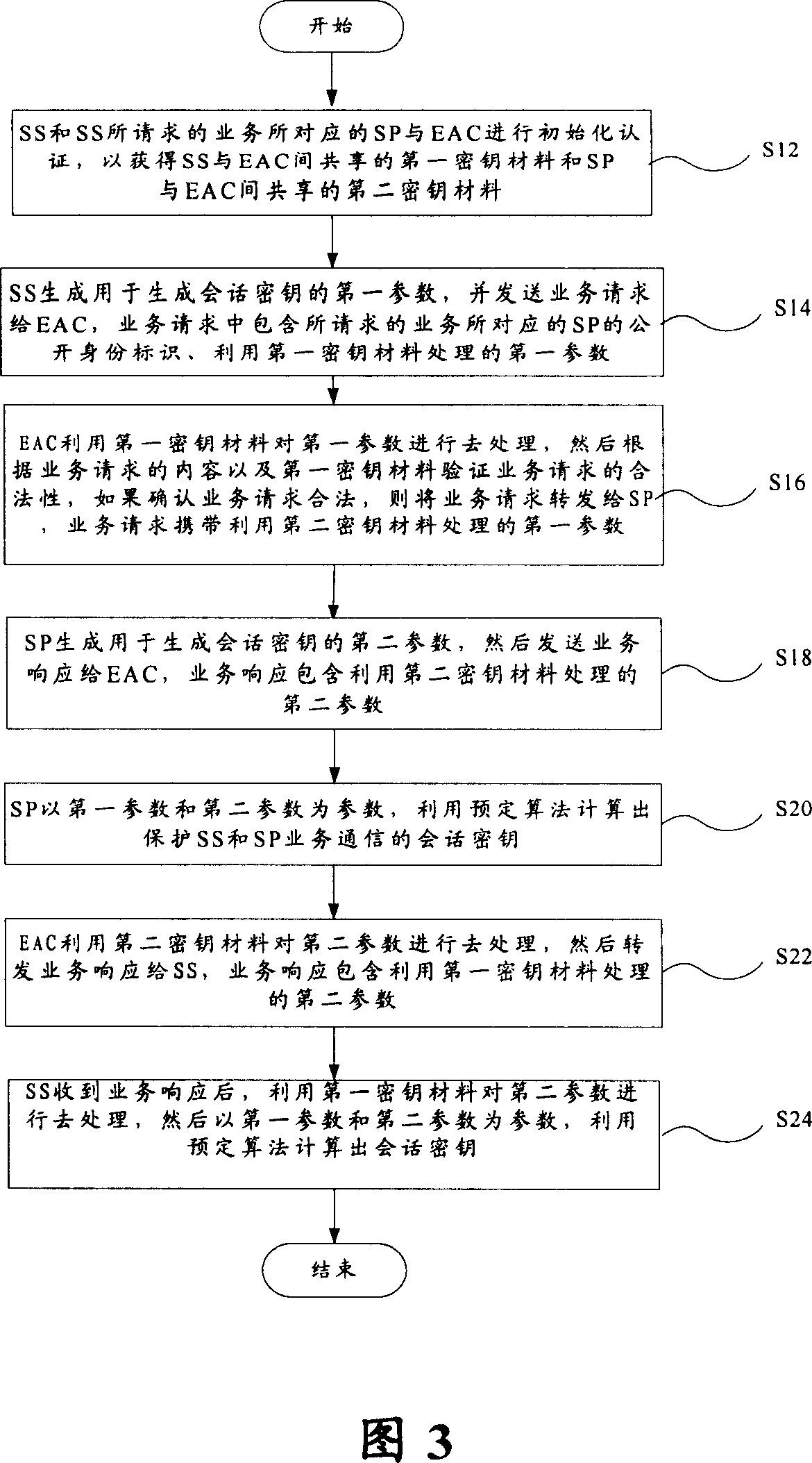
[0066] Hereinafter, the present invention will be described in detail with reference to the accompanying drawings.
[0067] 3 and 4 below illustrate the principle of the present invention.
[0068] It can be seen from the description of related technologies above that the TTP-based authentication and negotiation model can effectively prevent the man-in-the-middle attack in the Diffie-Hellman key exchange protocol by adding TTP to authenticate the identities of the communicating parties. In addition, it can be seen from the above descriptions of related technologies that drawing on the idea of the Diffie-Hellman key exchange protocol can effectively solve the possible Flaws that were intercepted and cracked.
[0069] Therefore, the present invention proposes a solution: the idea of Diffie-Hellman key exchange protocol is adopted in the TTP-based authentication and negotiation model, so that the shared key is directly generated locally by both communication parties without ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com