Patents
Literature
1673results about "Circuit fault indications" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
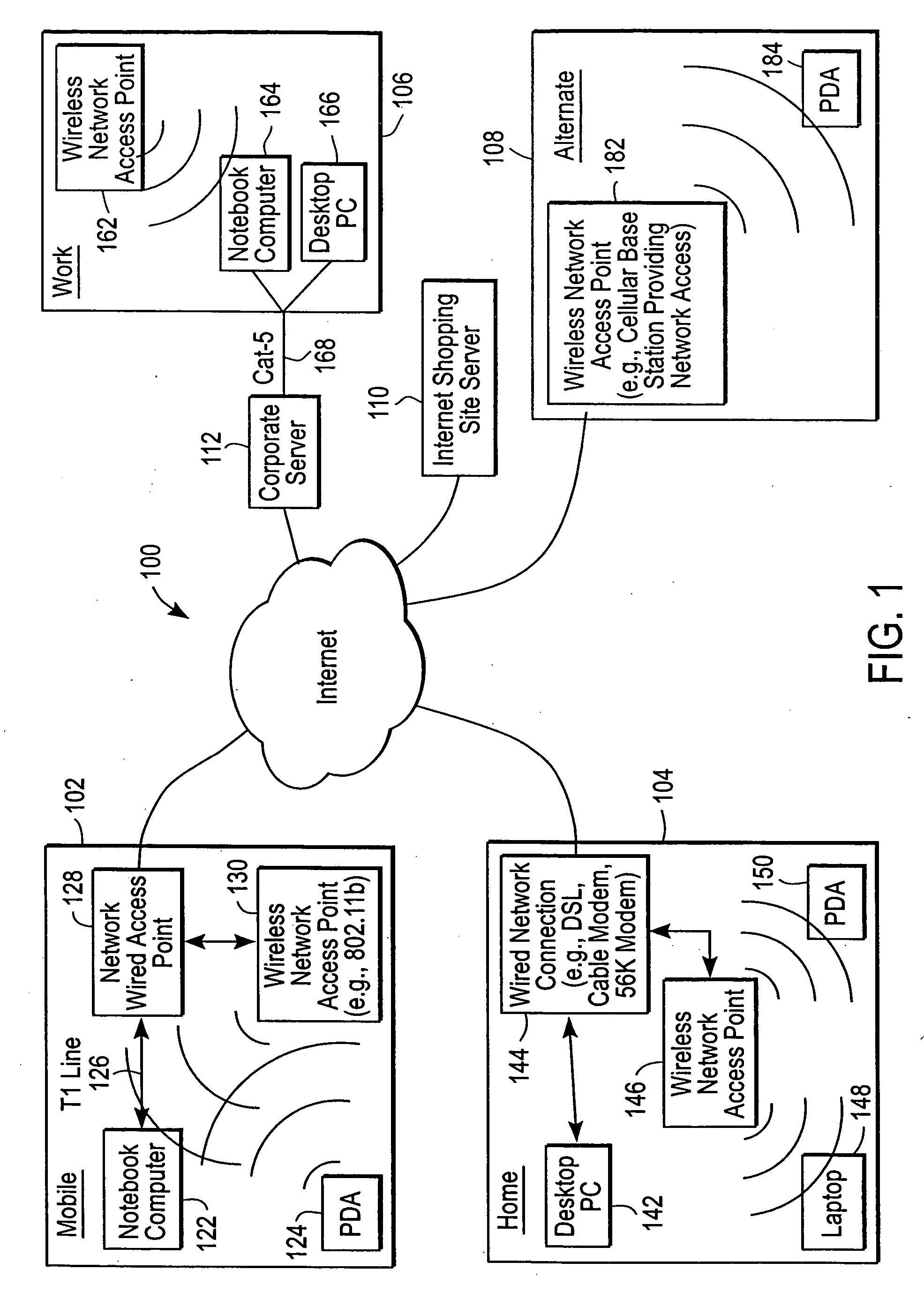
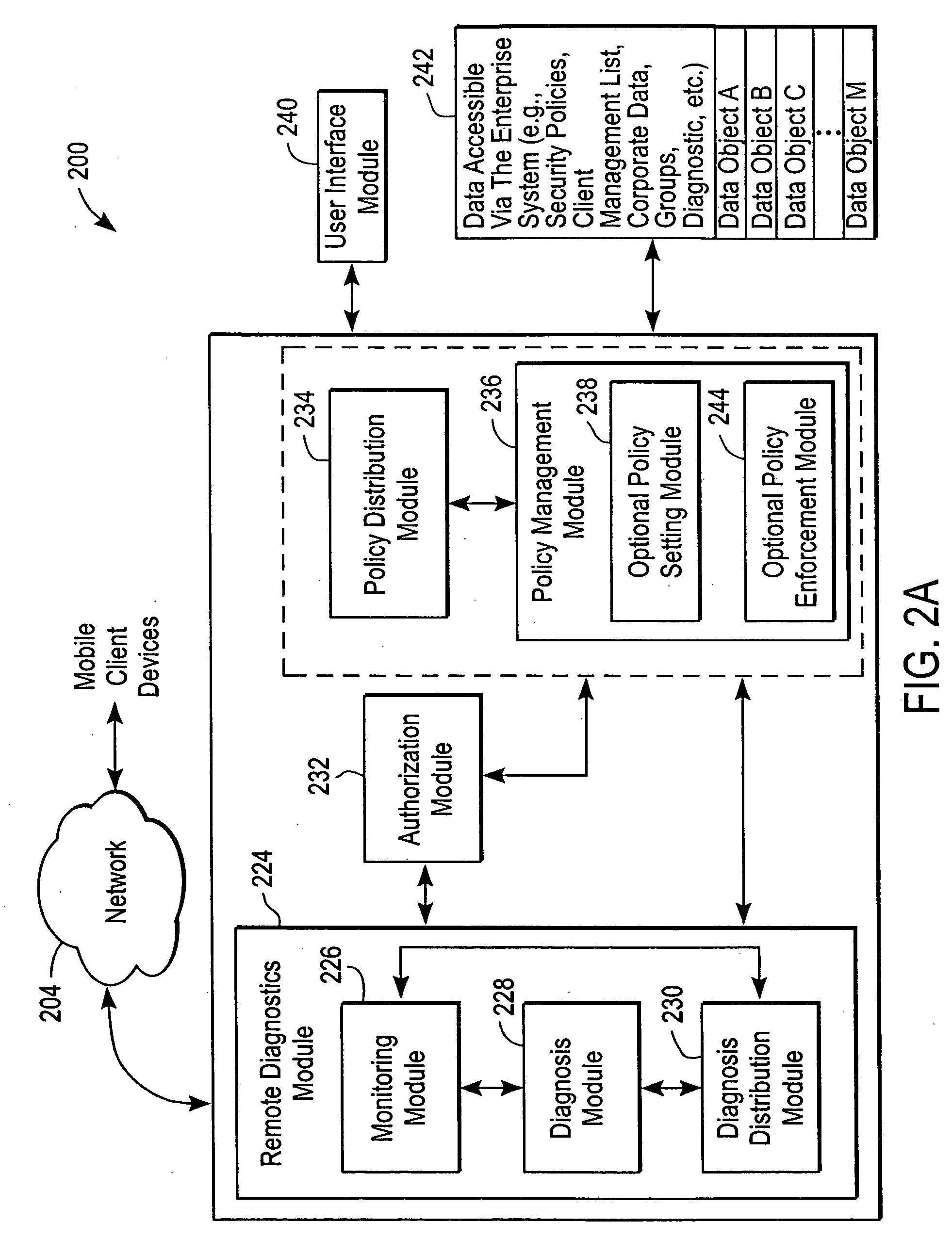
Administration of protection of data accessible by a mobile device
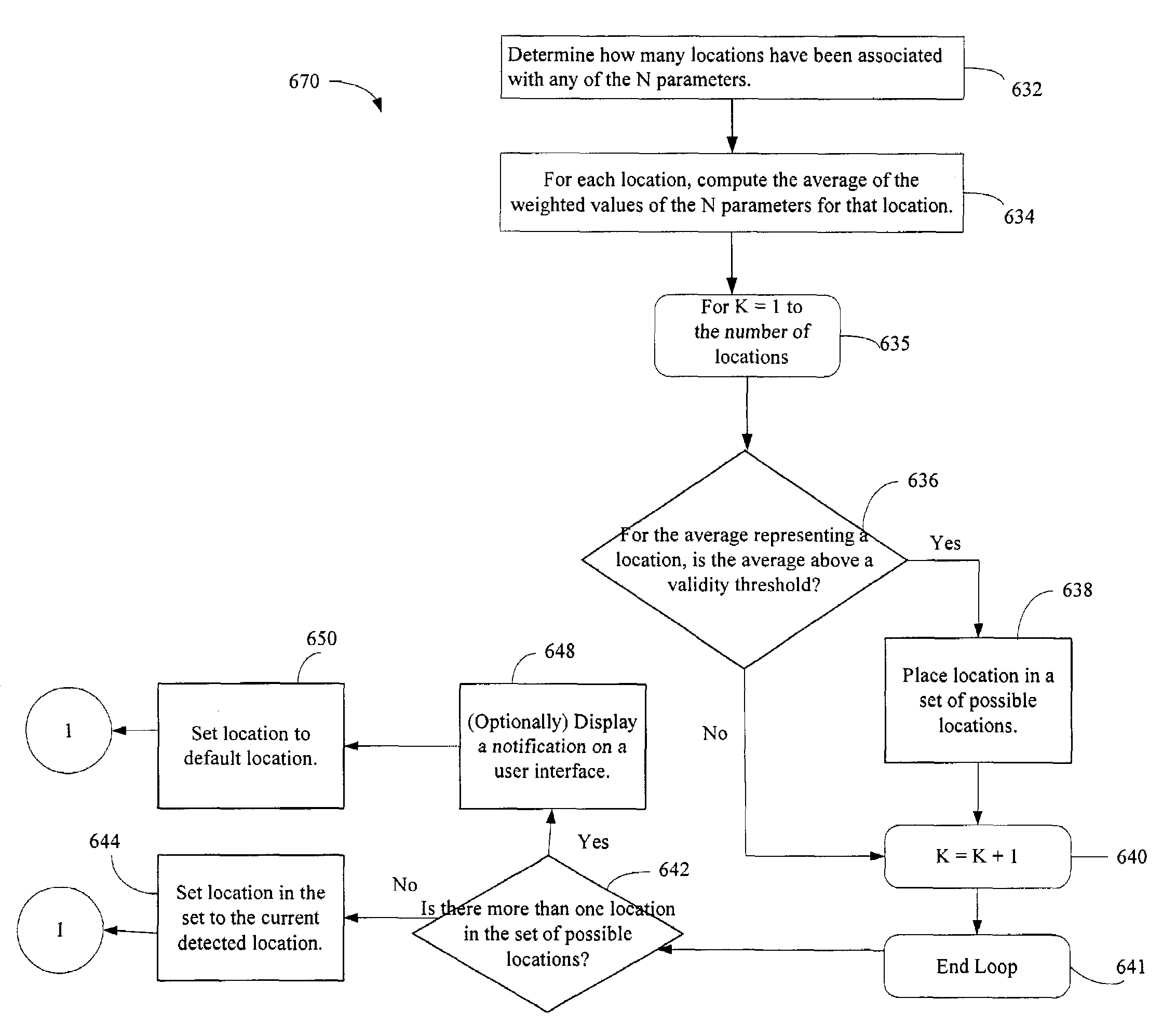
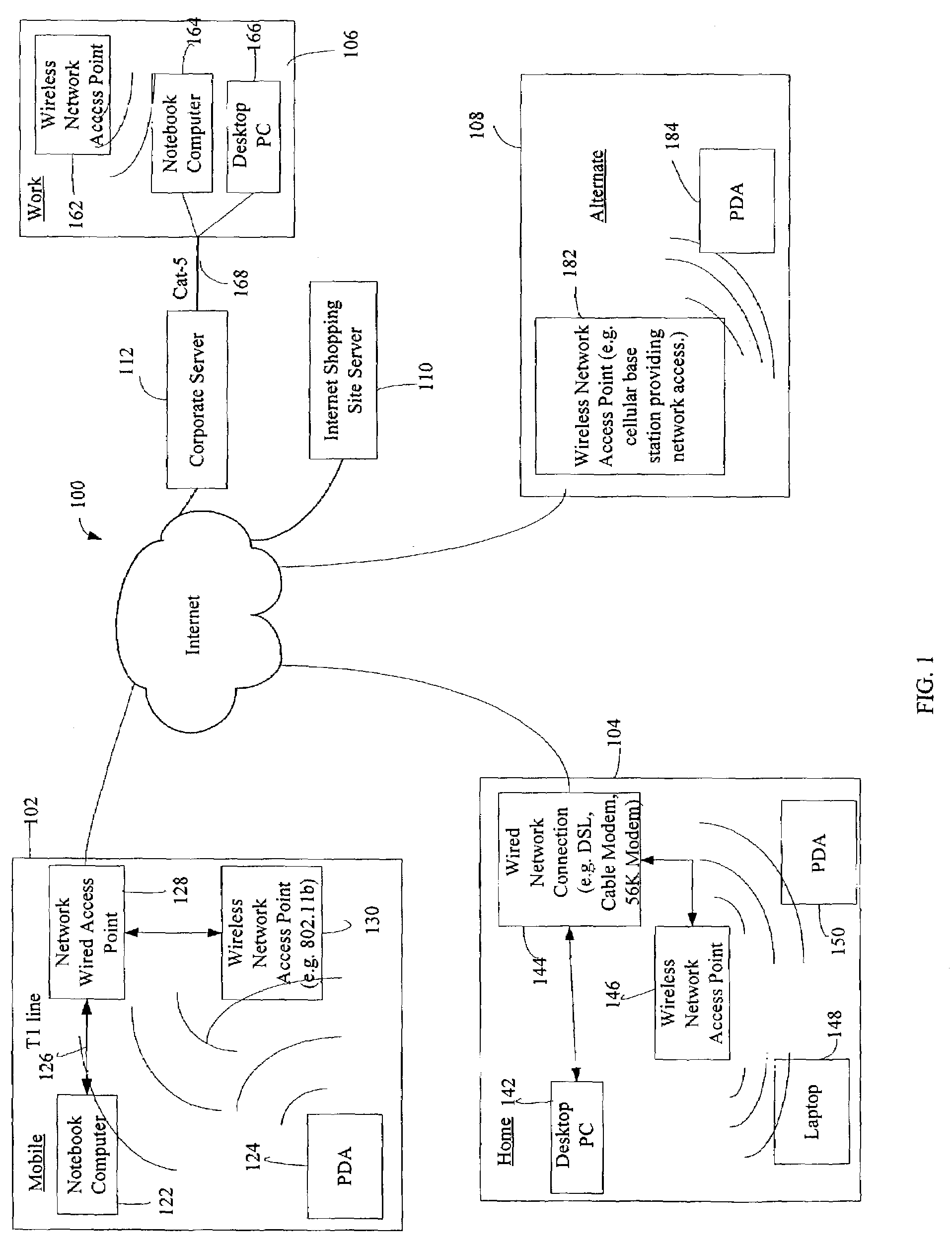
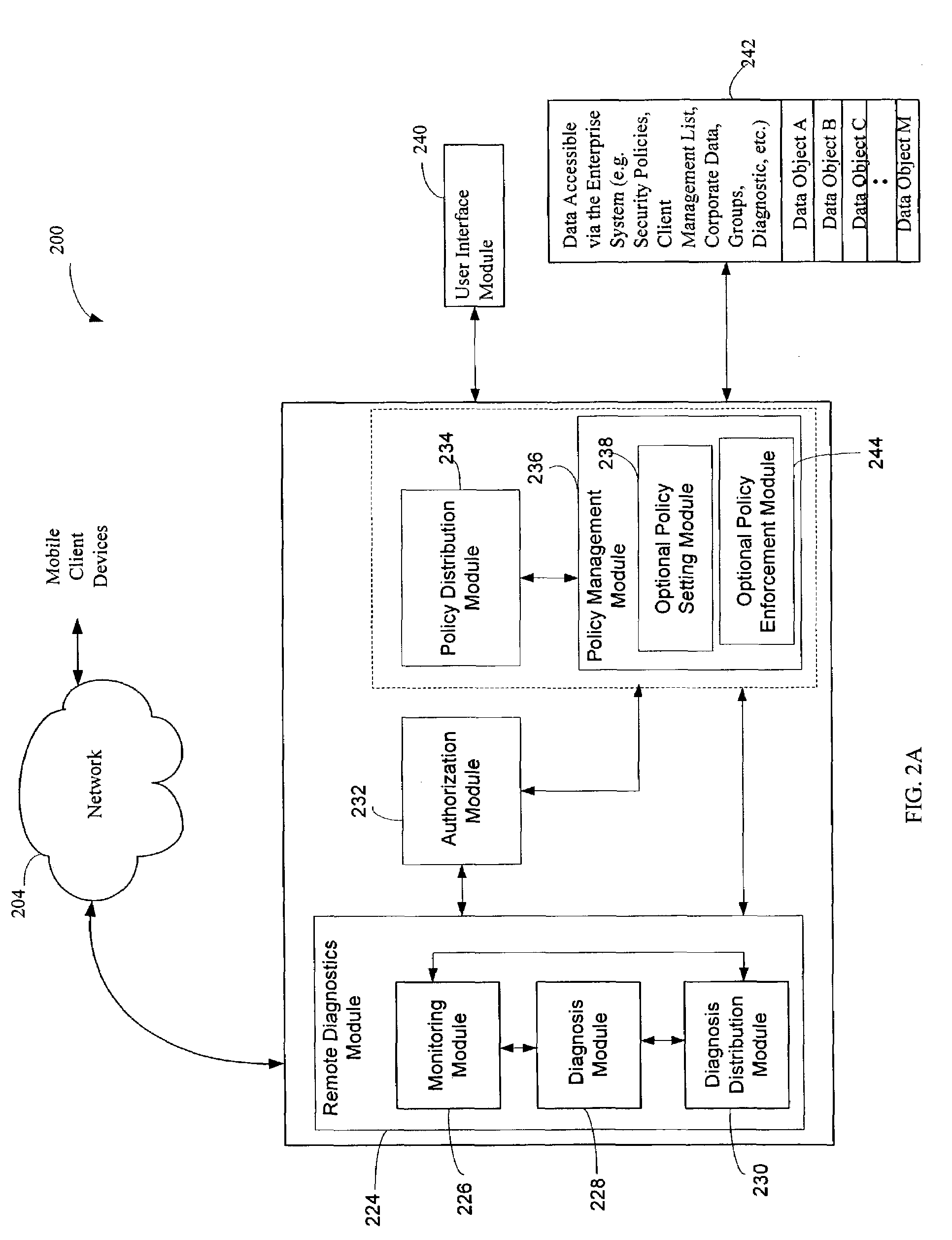
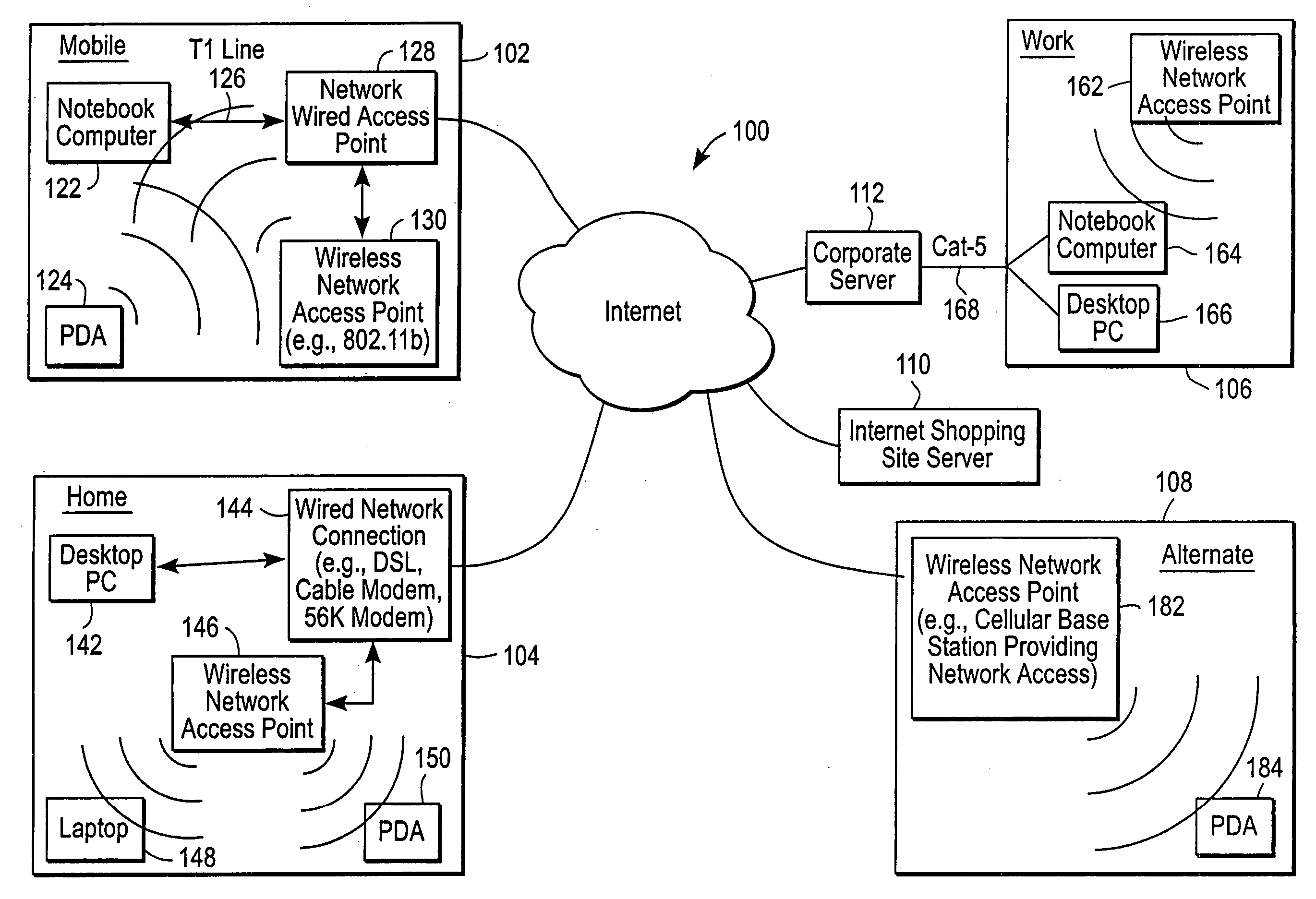
The administration of protection of data on a client mobile computing device by a server computer system such as within an enterprise network or on a separate mobile computing device is described. Security tools are described that provide different security policies to be enforced based on a location associated with a network environment in which a mobile device is operating. Methods for detecting the location of the mobile device are described. Additionally, the security tools may also provide for enforcing different policies based on security features. Examples of security features include the type of connection, wired or wireless, over which data is being transferred, the operation of anti-virus software, or the type of network adapter card. The different security policies provide enforcement mechanisms that may be tailored based upon the detected location and / or active security features associated with the mobile device. Examples of enforcement mechanisms are adaptive port blocking, file hiding and file encryption.
Owner:APPLE INC
Administration of protection of data accessible by a mobile device
ActiveUS20050055578A1Digital data processing detailsMultiple digital computer combinationsAnti virusEnterprise networking
The protection of data on a client mobile computing device by a server computer system such as within an enterprise network or on a separate mobile computing device is described. Security tools are described that provide different security policies to be enforced based on a location associated with a network environment in which a mobile device is operating. Methods for detecting the location of the mobile device are described. Additionally, the security tools may also provide for enforcing different policies based on security features. Examples of security features include the type of connection, wired or wireless, over which data is being transferred, the operation of anti-virus software, or the type of network adapter card. The different security policies provide enforcement mechanisms that may be tailored based upon the detected location and / or active security features associated with the mobile device. Examples of enforcement mechanisms are adaptive port blocking, file hiding and file encryption.
Owner:APPLE INC
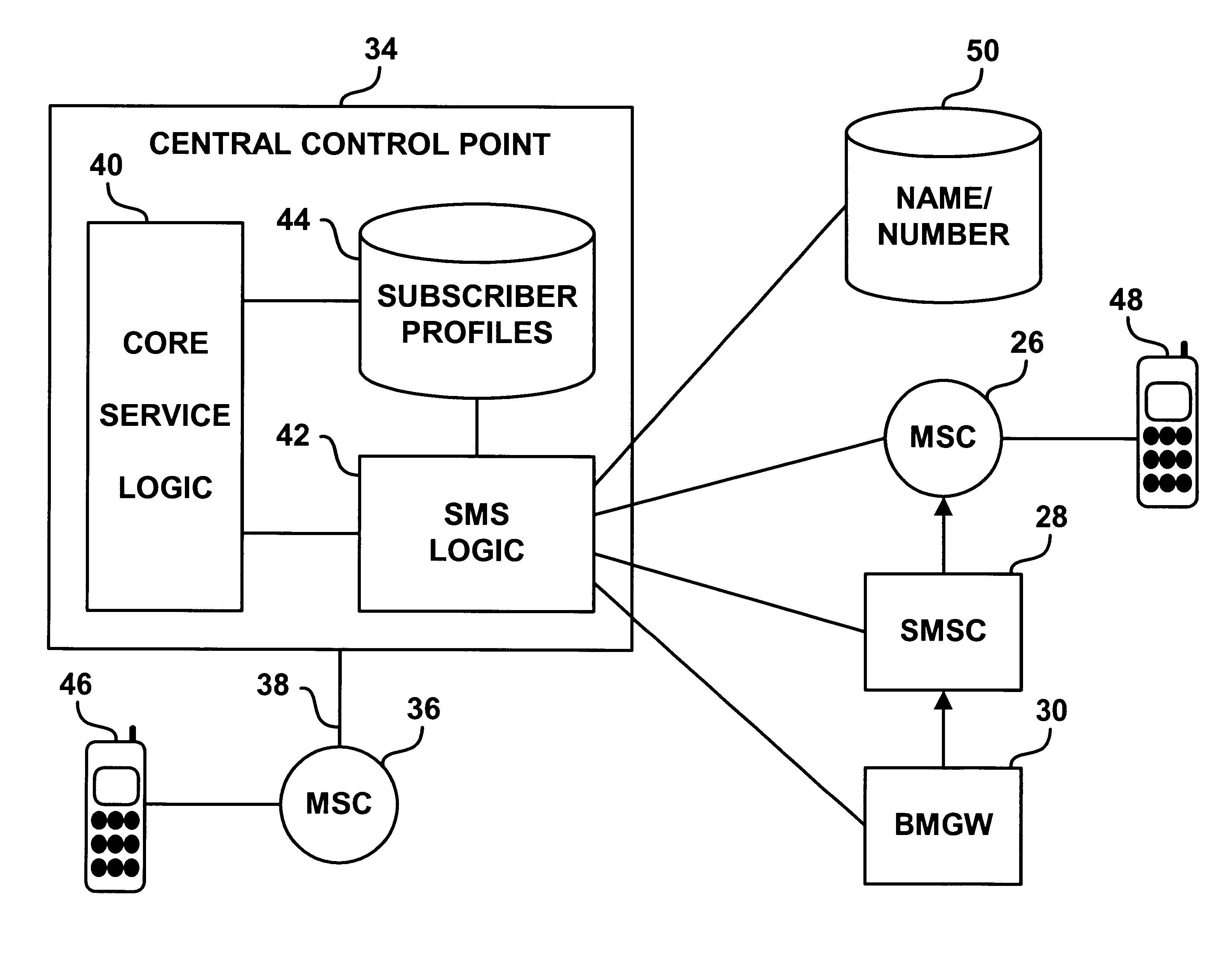
Automatic in-line messaging system
InactiveUS6718178B1Multiplex system selection arrangementsTelephone data network interconnectionsTelecommunications networkFacsimile
An automatic messaging system for a telecommunications network is disclosed. A call processing entity such as a switch or central control point recognizes a call-processing event and responsively generates and sends an informational message to a specified destination. The informational message may be a text description of the event, such as an indication that "calling party just placed a call to called party" or may take other forms, such as a video message, an audio message or a fax message.
Owner:SPRING SPECTRUM LP
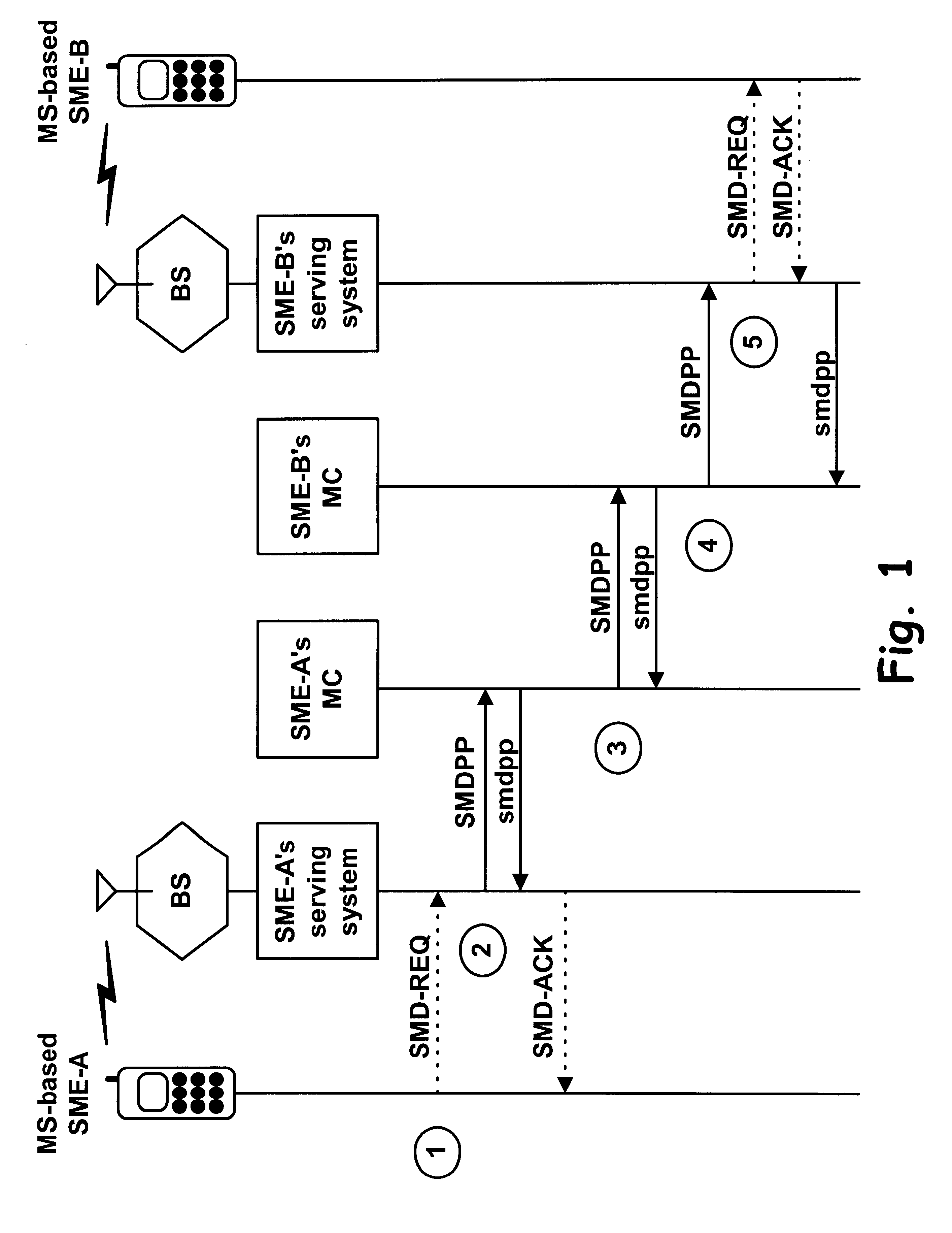
Method and system for comprehensive testing of network connections
InactiveUS20070041554A1Special service for subscribersSupervisory/monitoring/testing arrangementsData setNetwork connection
The present invention is an system and method for comprehensively testing a customer connection to a communications network. A customer is identified from information obtained at a customer interface. A test can be performed on the customer connection. A typical test compares two datasets related to the customer connection to determine a state of the customer connection. The first and second dataset can include historical data. A parameter in the first dataset obtained from a network element can be compared to a parameter in a second dataset obtained from a customer database. The comparison can be made in light of changes recorded in a provisioning database. Relevant network data can be obtained from customer premises equipment (CPE). The customer can be notified of a network issue proactively or upon customer inquiry.
Owner:SBC KNOWLEDGE VENTURES LP
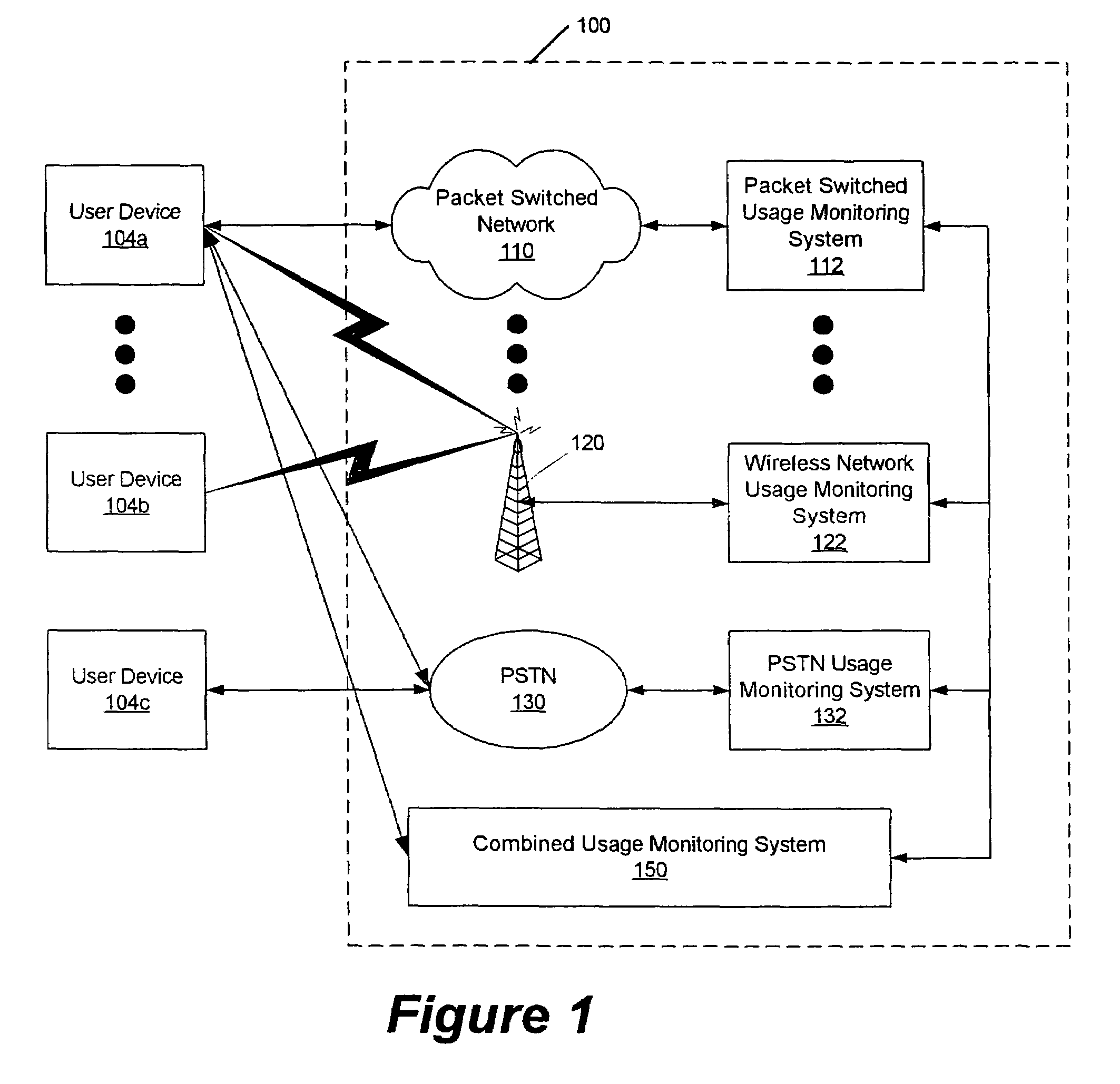
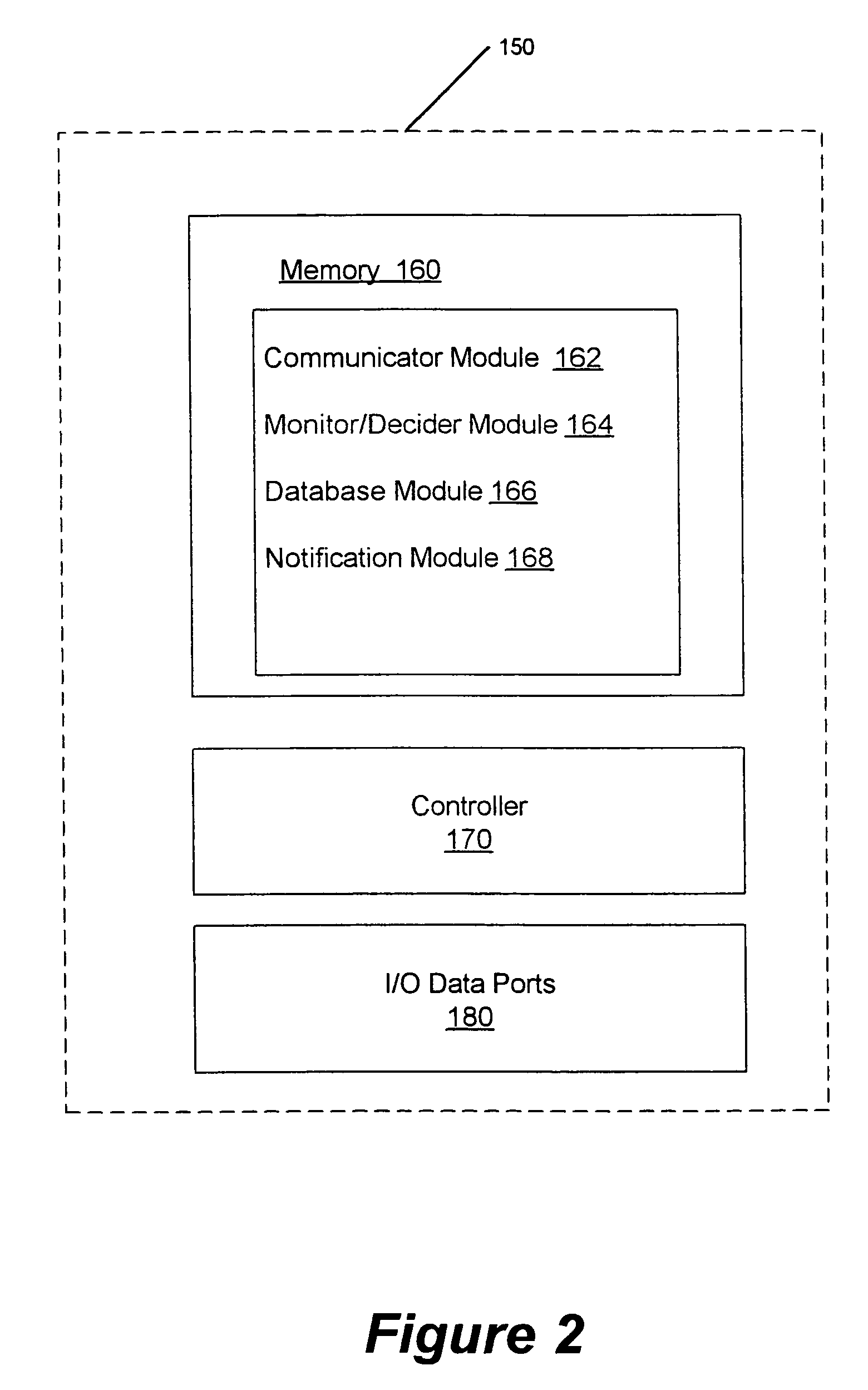
Methods, systems and computer program products for monitoring service usage
InactiveUS7620162B2Metering/charging/biilling arrangementsAccounting/billing servicesCommunications systemUse of services
Monitoring criteria is received that corresponds to a usage quantity for a plurality of services. Each of the plurality of services is provided over ones of a plurality of different communication systems. Actual service usage information is received for the plurality of services. The actual service usage information and the monitoring criteria are compared. An electronic notification message is sent when the monitoring criteria for one or more of the plurality of services is satisfied.
Owner:AT&T INTPROP I LP
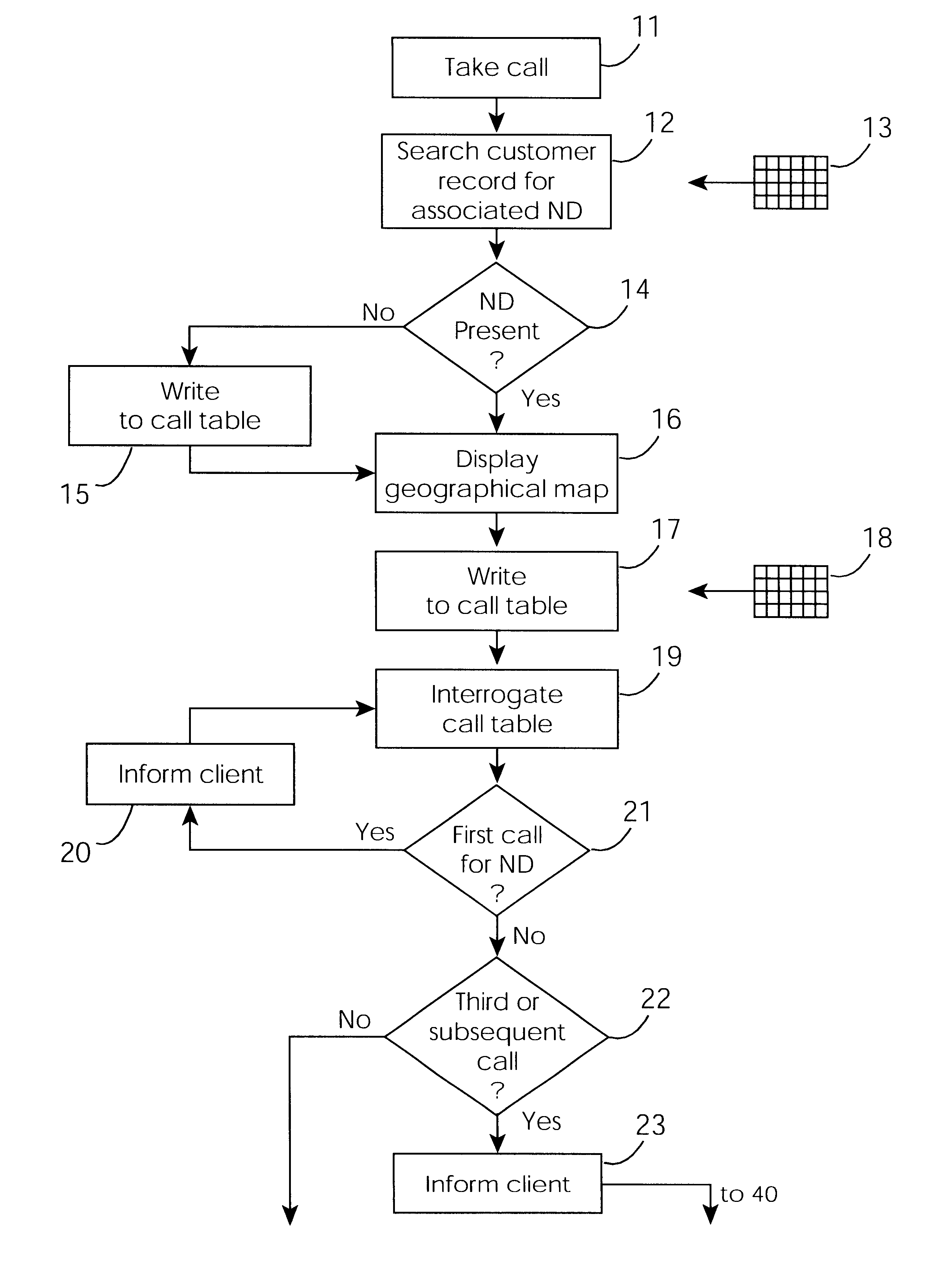
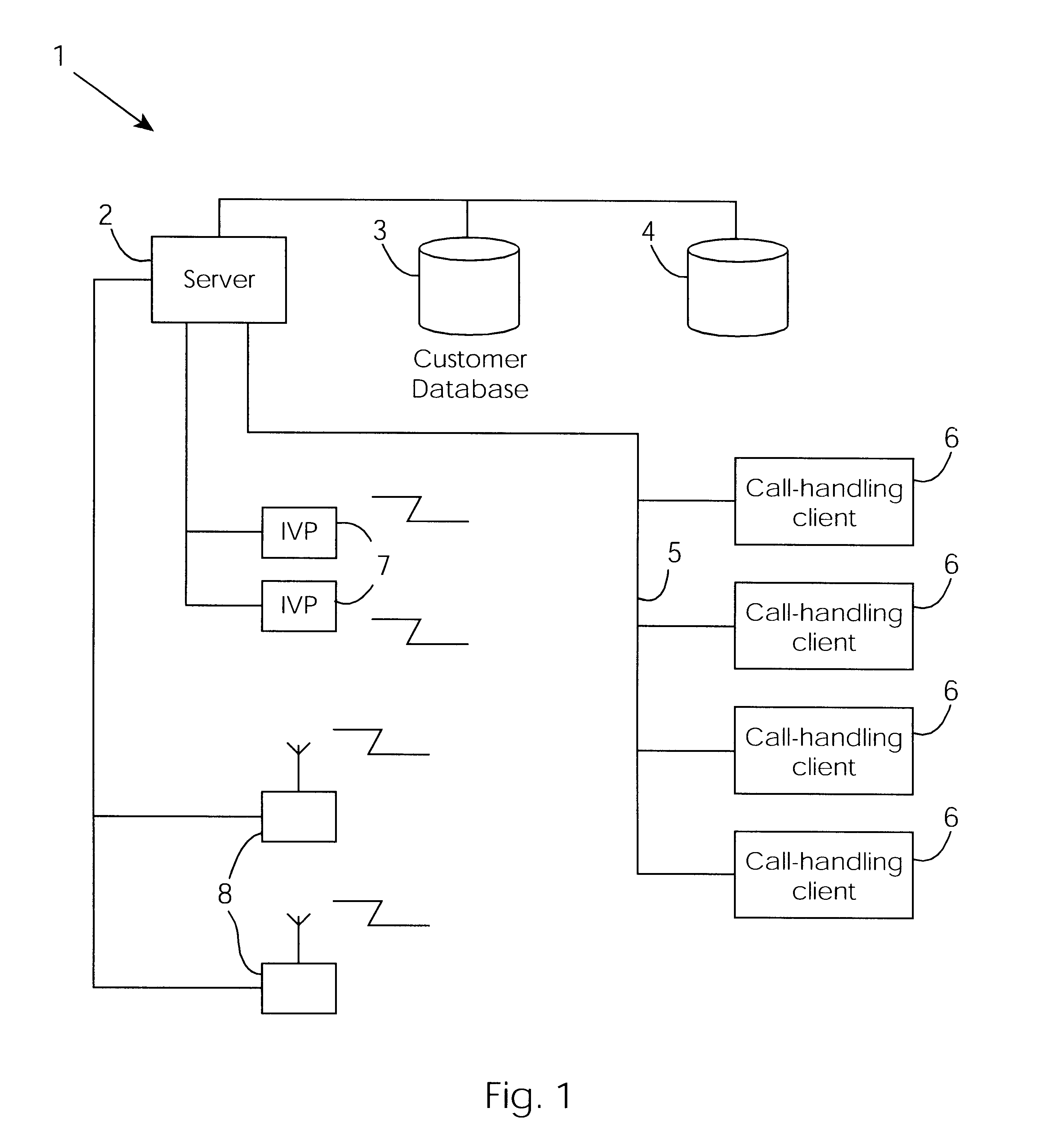
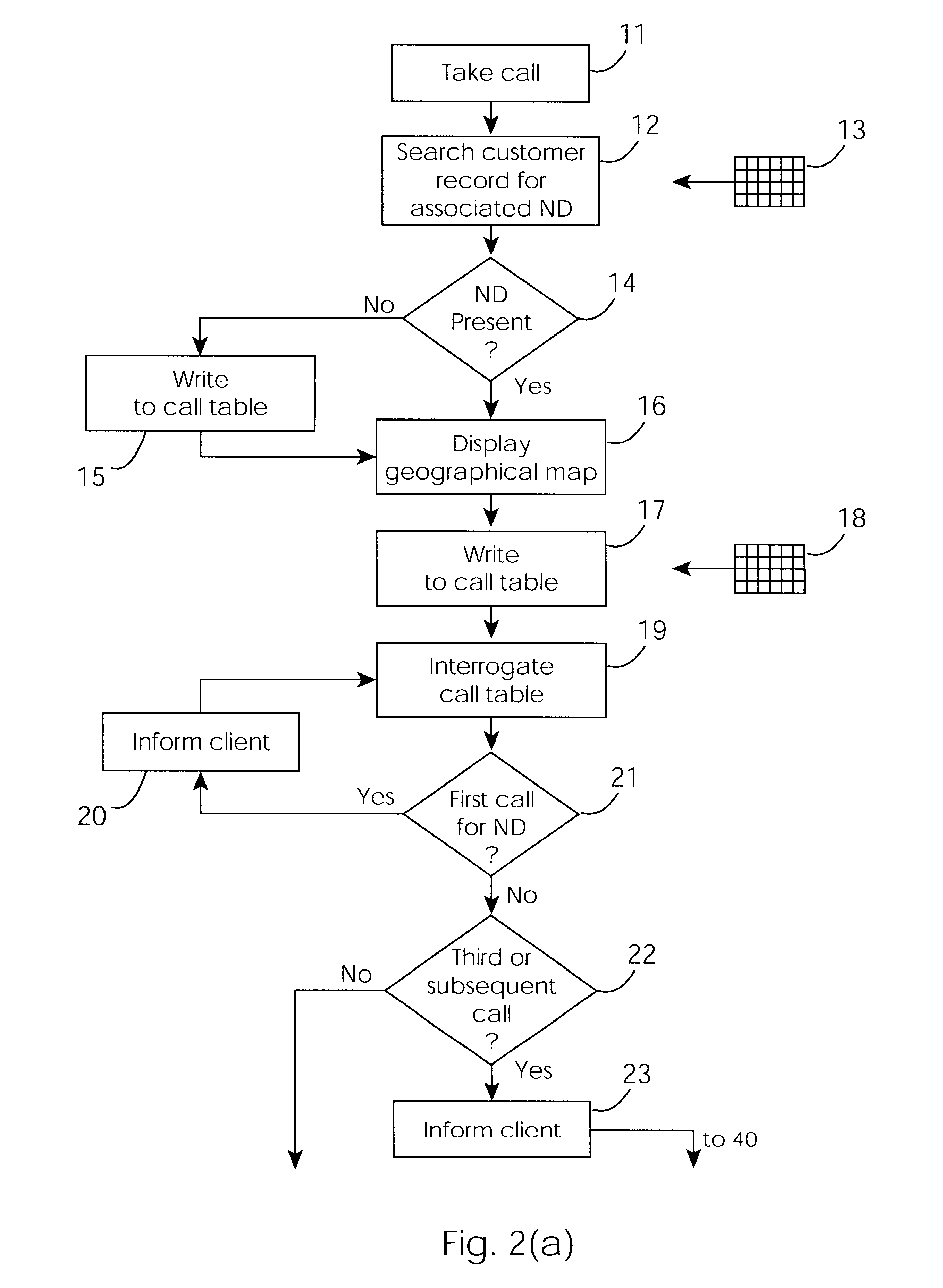
Cable network repair control system
InactiveUS6671824B1Shorten the timeSupervisory/monitoring/testing arrangementsSubstation equipmentControl systemEngineering
A cable network repair control system including a server communicating with multiple call-handling clients in a trouble call center. The databases are used to automatically determine an associated network device for the customer who makes a trouble call. When a second call is received for a particular network device, an inferencing engine automatically operates to identify potential repairs crews and to control communication with them to ensure that optimum use of the repair crew time and quick repair. Various tables are generated dynamically and are used to update management status tables for reviewing of network repair status.
Owner:LAKEFIELD ETECH GROUP
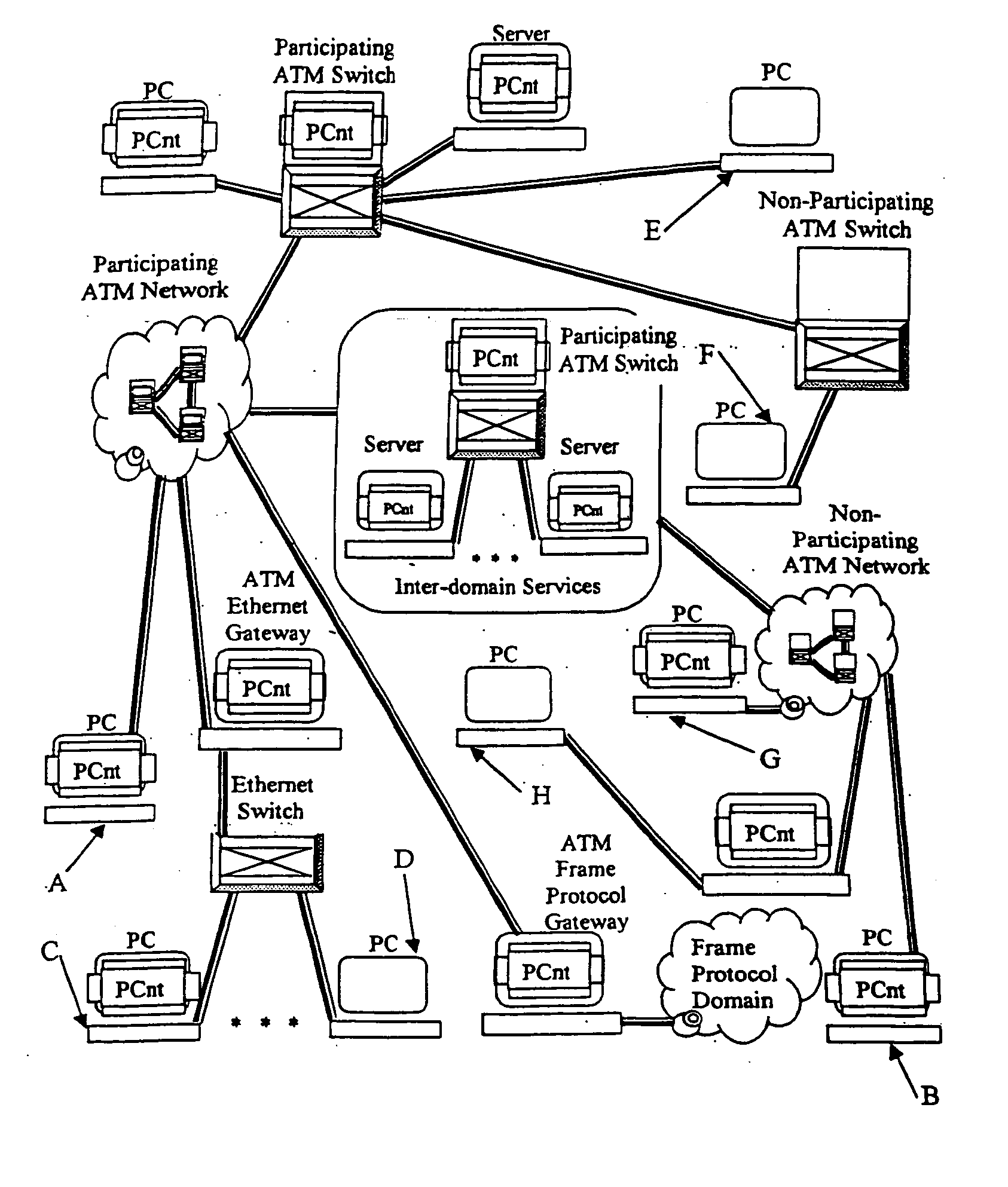
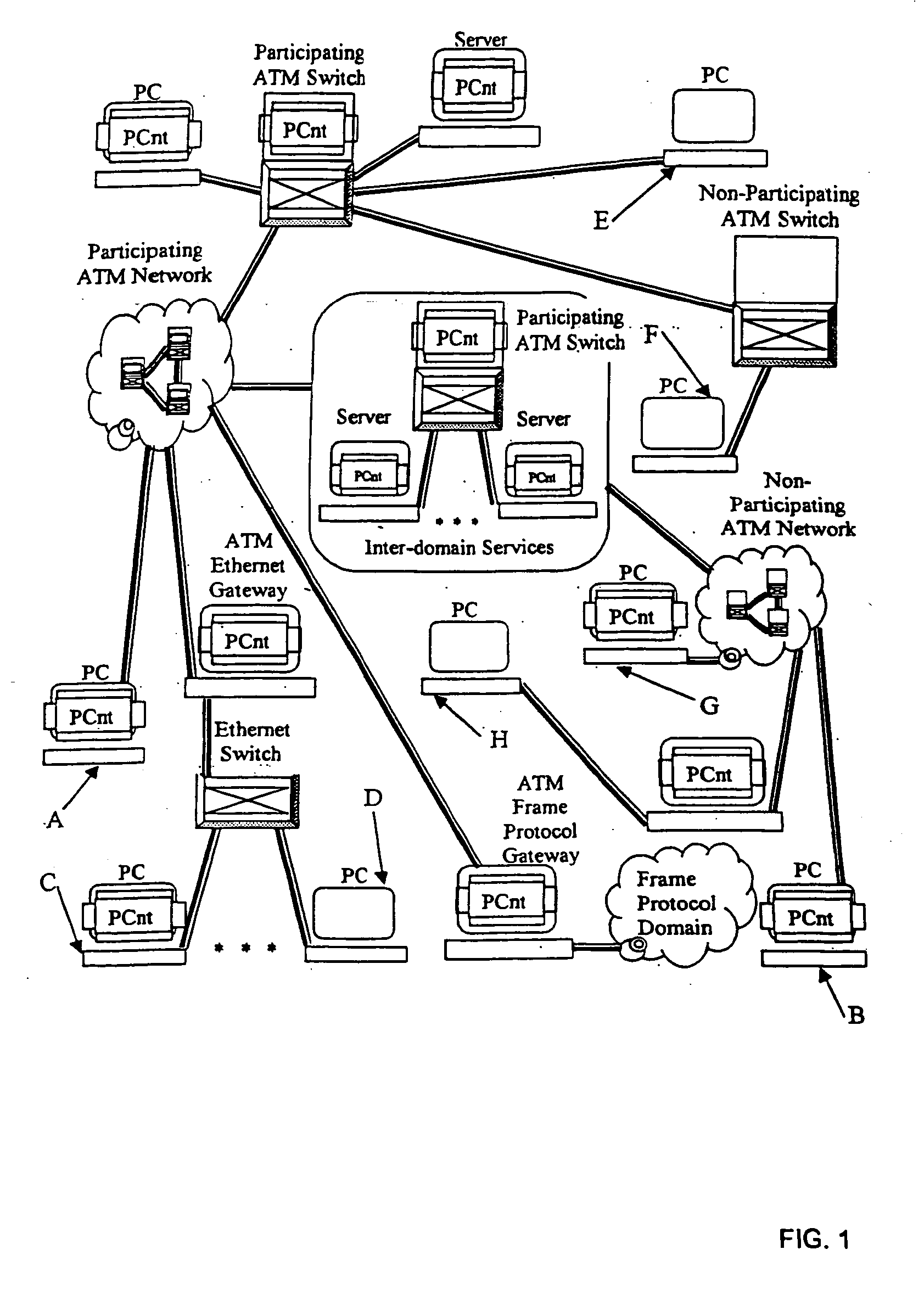
System and method for providing peer-oriented control of telecommunication services
InactiveUS20050027870A1Supporting development and deploymentHybrid switching systemsSupervisory/monitoring/testing arrangementsTelecommunications networkEngineering
In a telecommunications network environment including non-participating elements and participating elements, a method for providing a telecommunications service between a first peer element connected to the telecommunications network environment and a second peer element connected to the telecommunications network. At a first peer element, an indication of the type of telecommunications service to be provided between the first peer element and the second peer element is received. A telecommunications service template in association with the indicated telecommunications service is determined, the telecommunications service template including instructions for configuring the non-participating elements of the telecommunications network environment to provide the indicated telecommunications service and instructions for configuring the participating elements of the telecommunications network environment. Upon establishing a communication channel between the first peer element and the second peer element, the service template is transferred to the second peer element. The second peer element then executes the instructions to configure the participating elements and non-participating elements of the telecommunications network environment to provide the telecommunications service.
Owner:TREBES HAROLD HERMAN JR
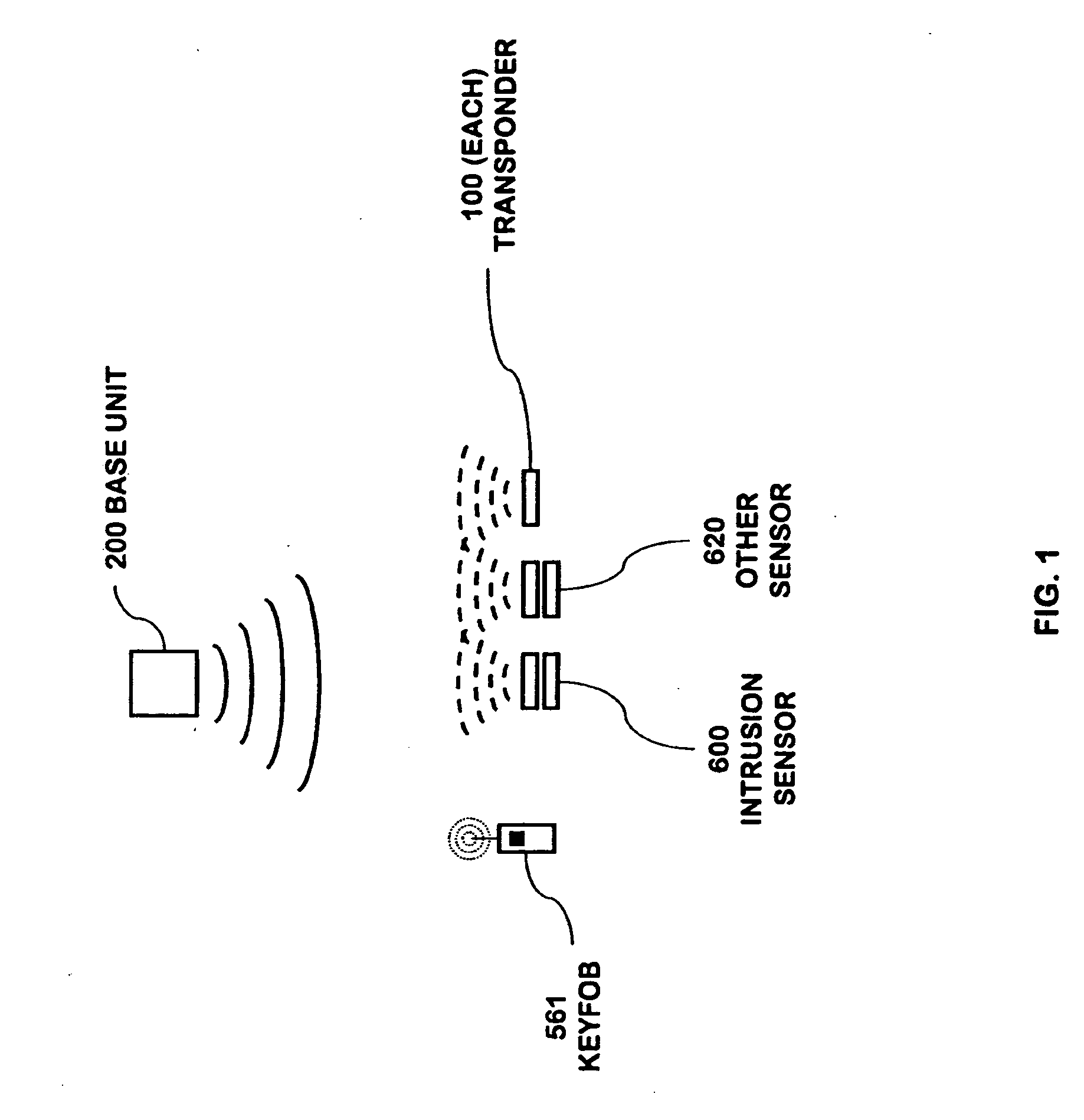
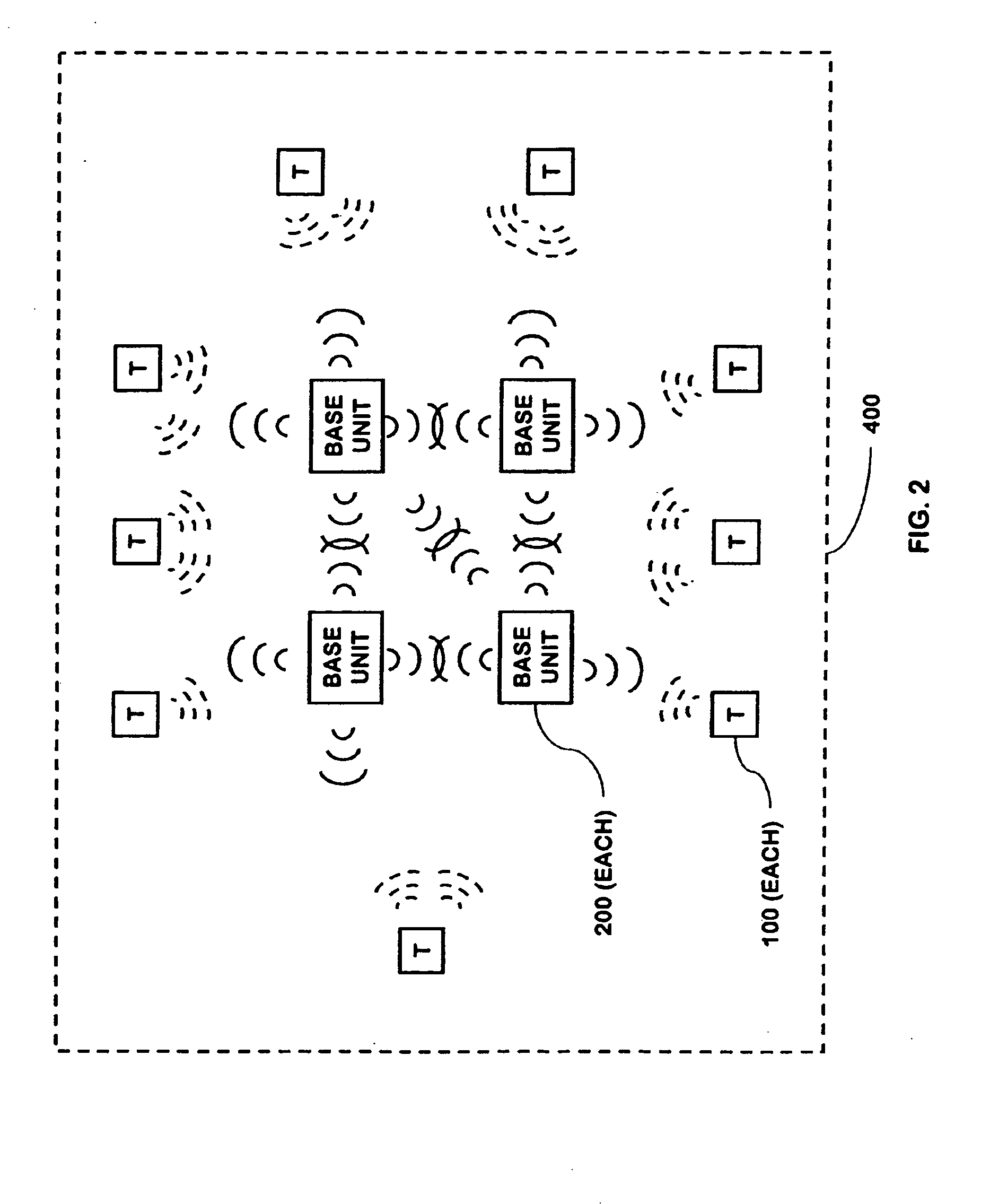
Portable telephone in a security network
InactiveUS20080001734A1Improve reliabilityLow costSafety arrangmentsComputer controlKey pressingNetwork communication
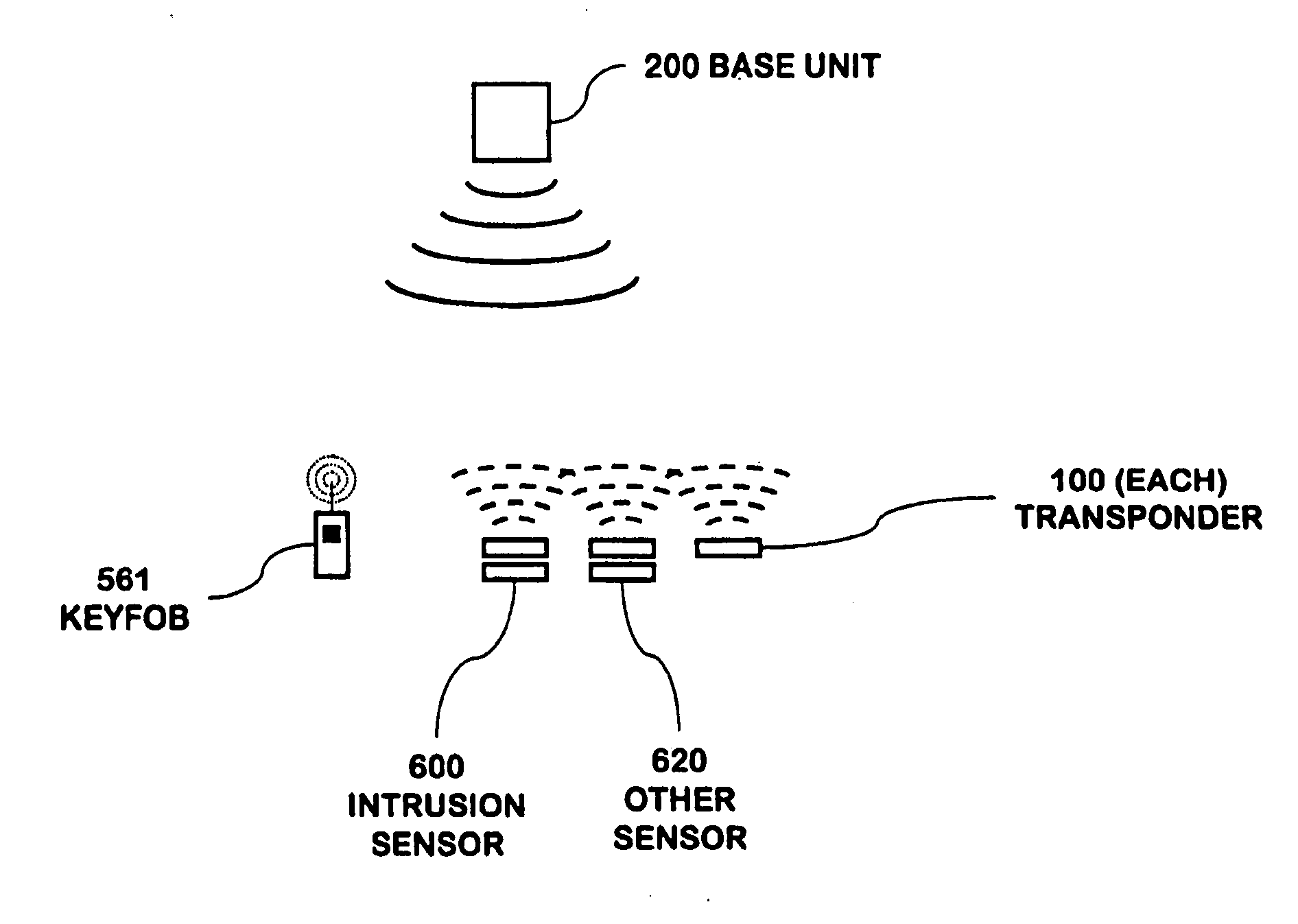
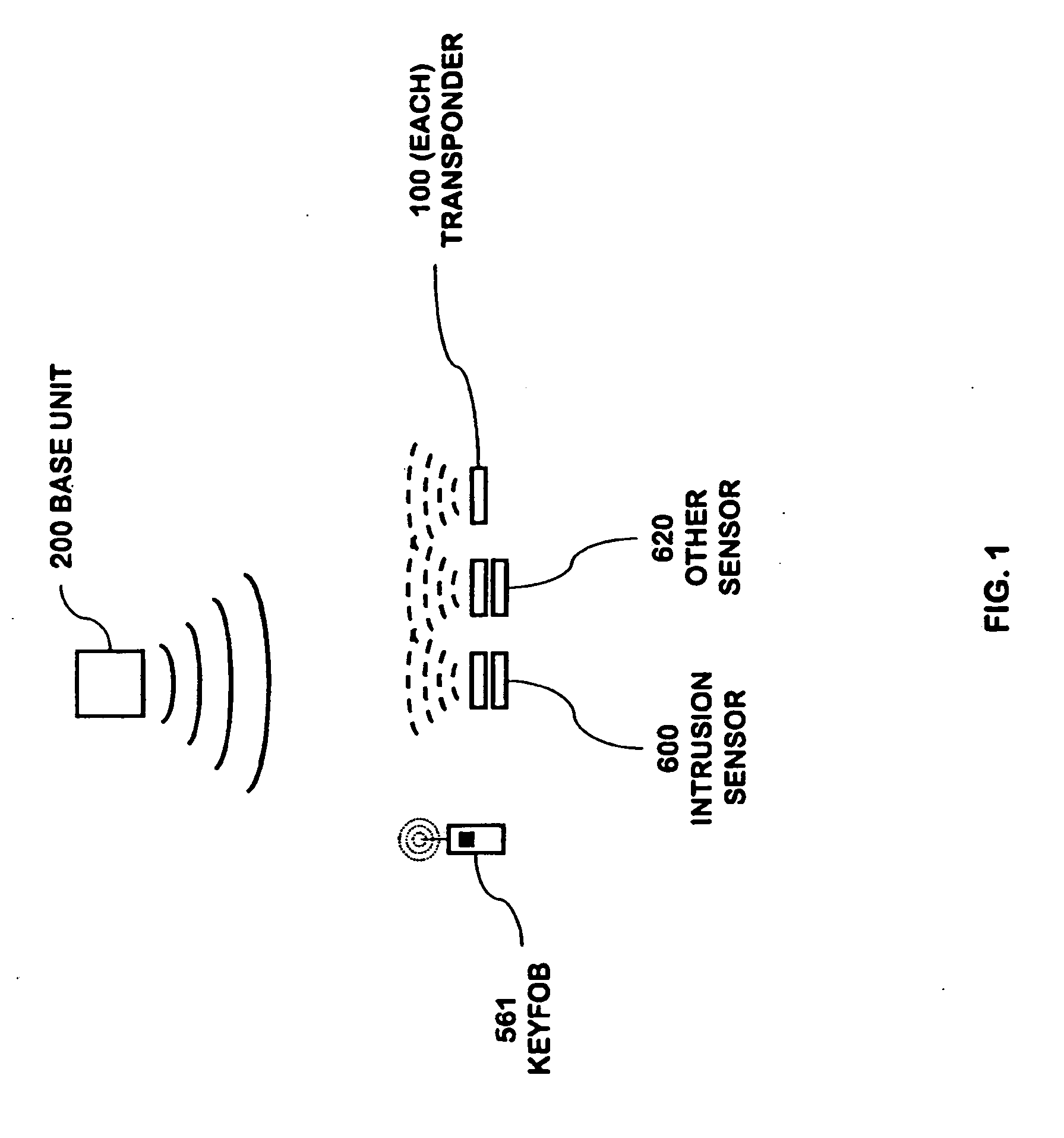
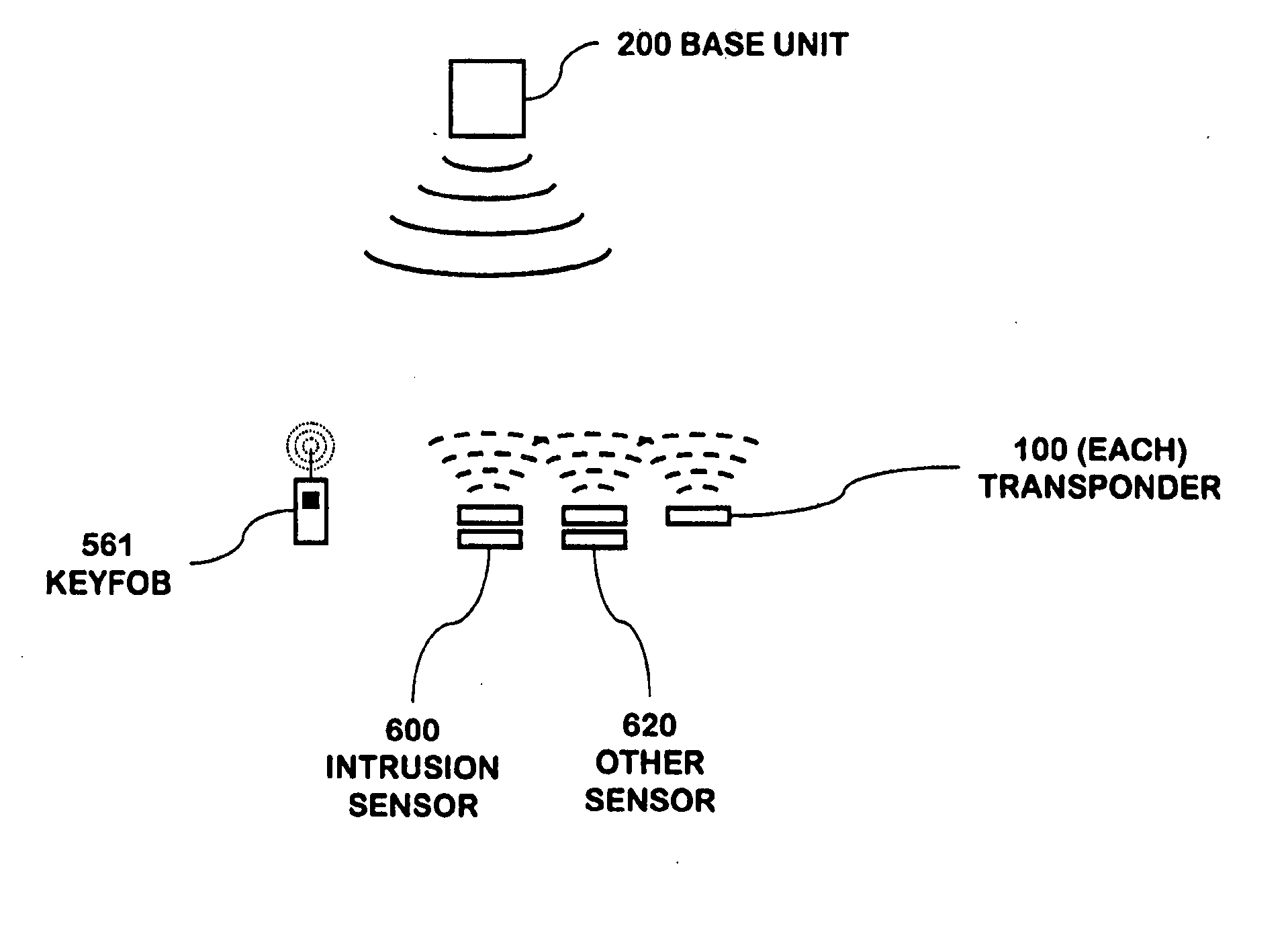
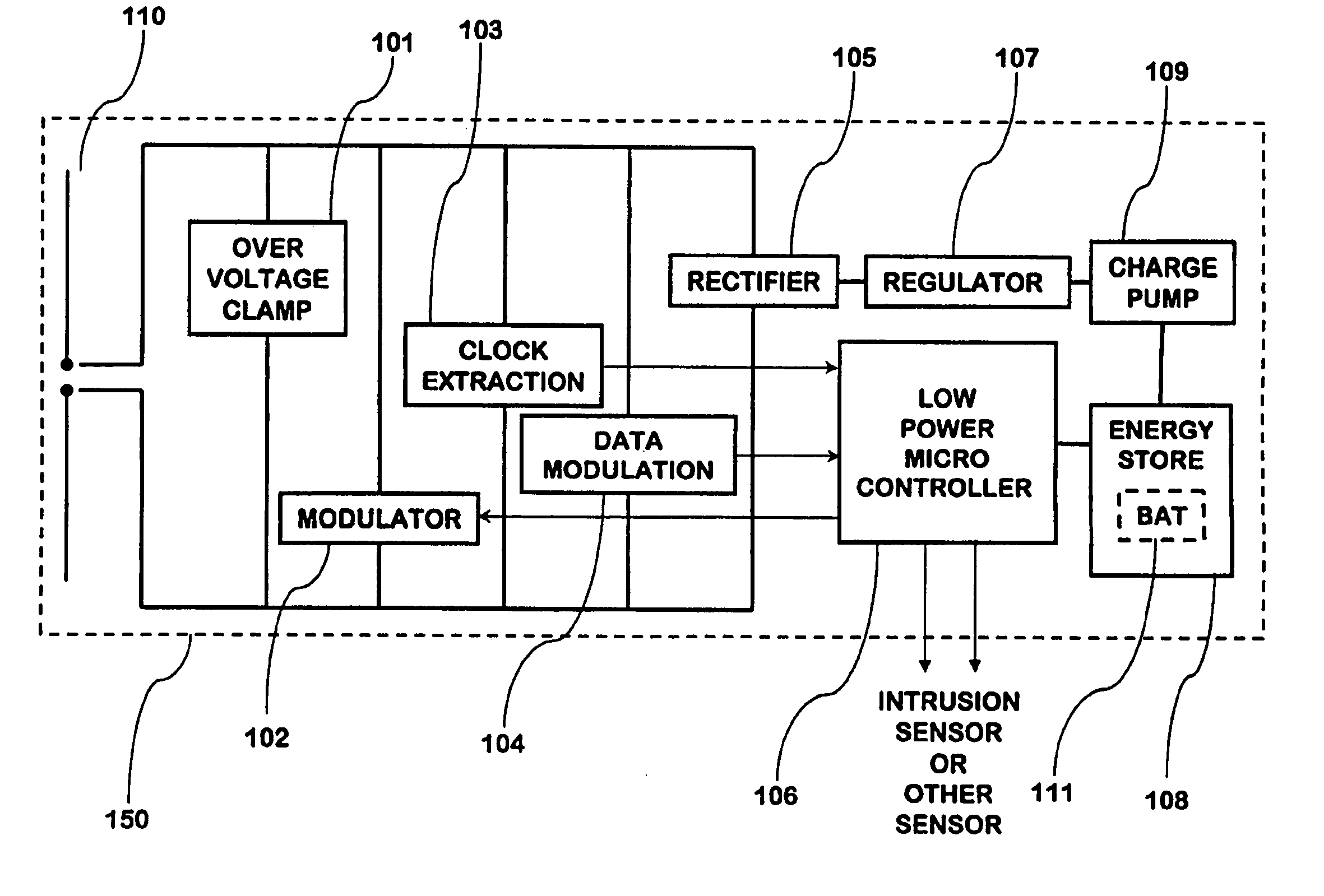
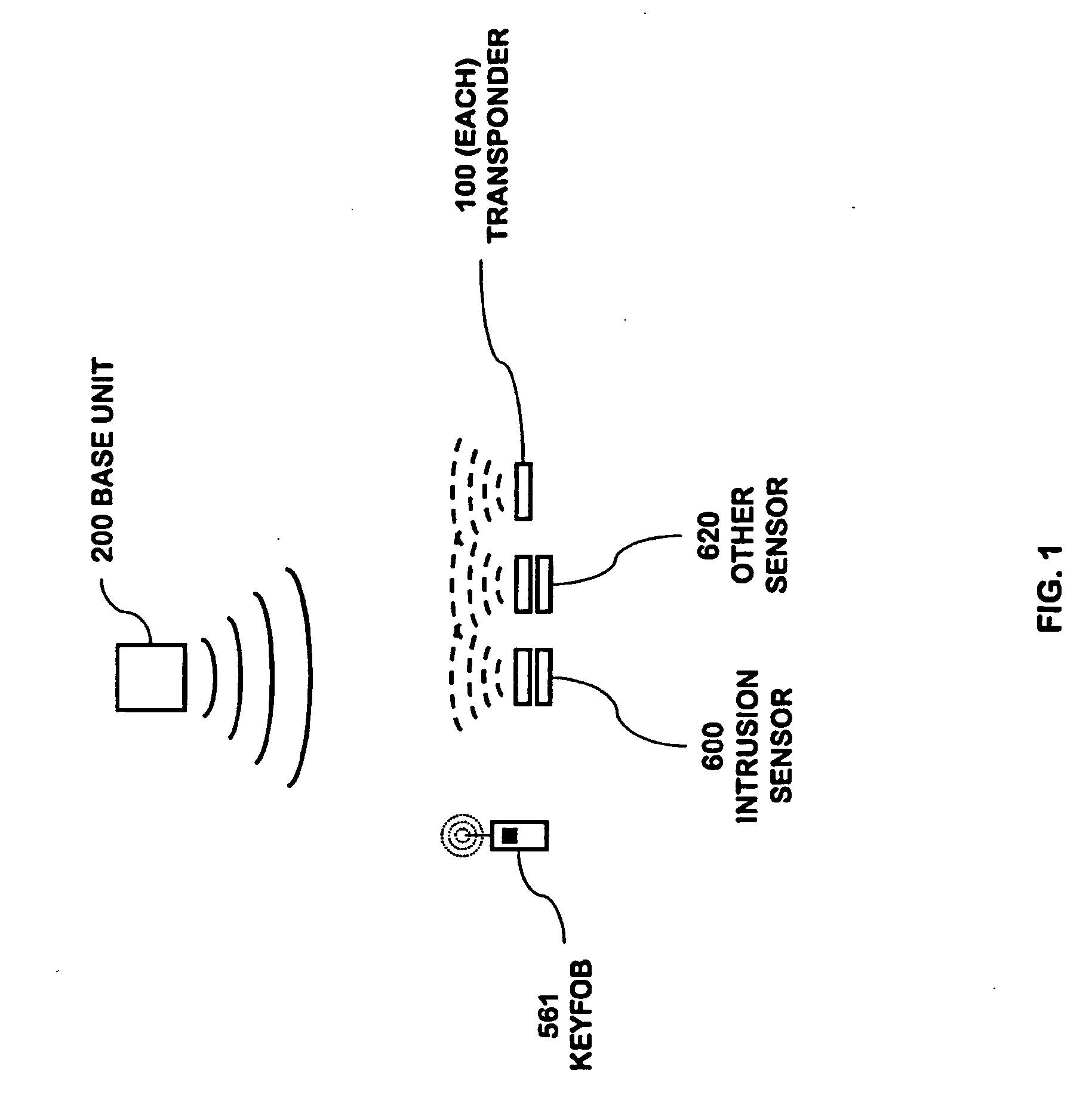
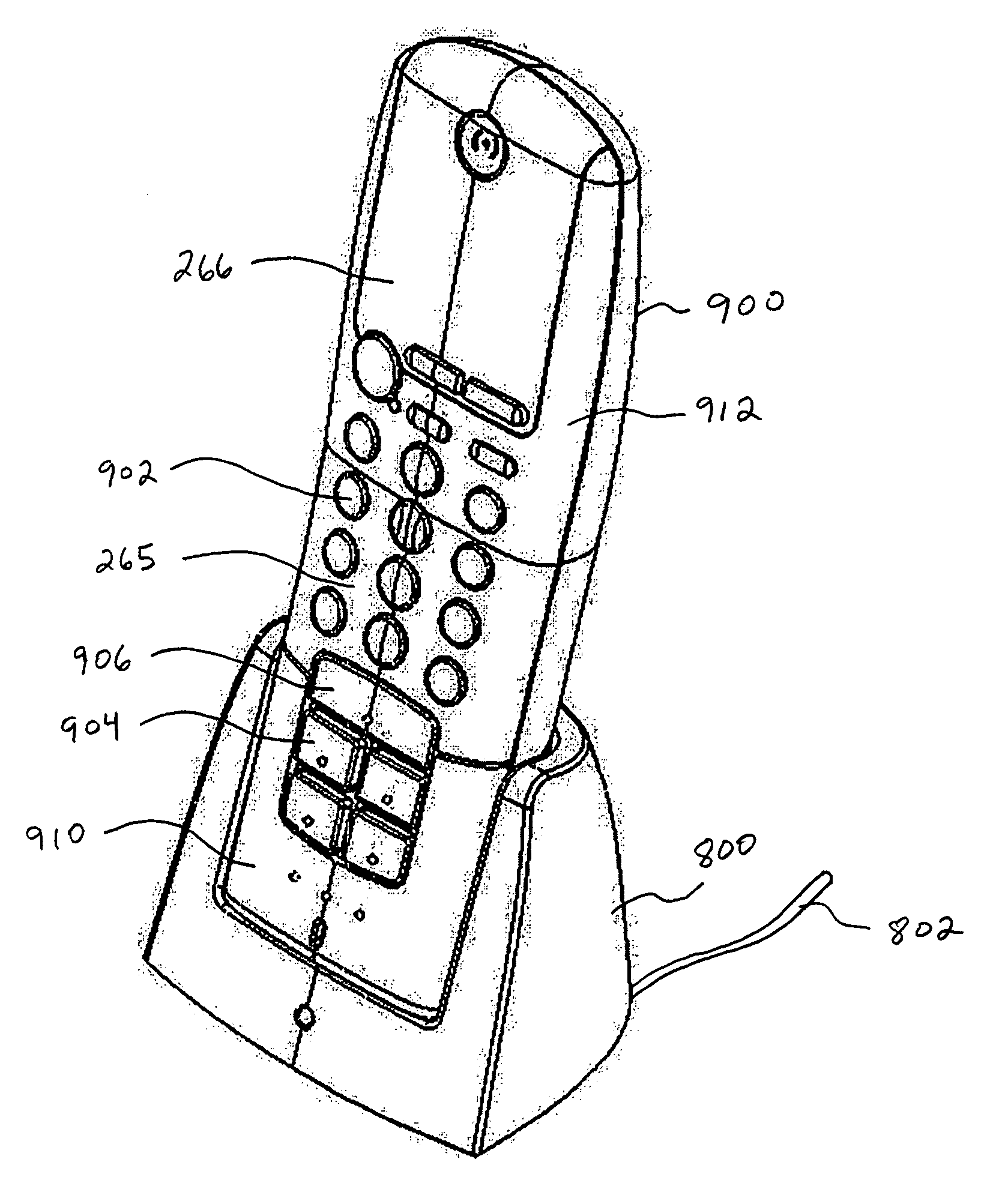
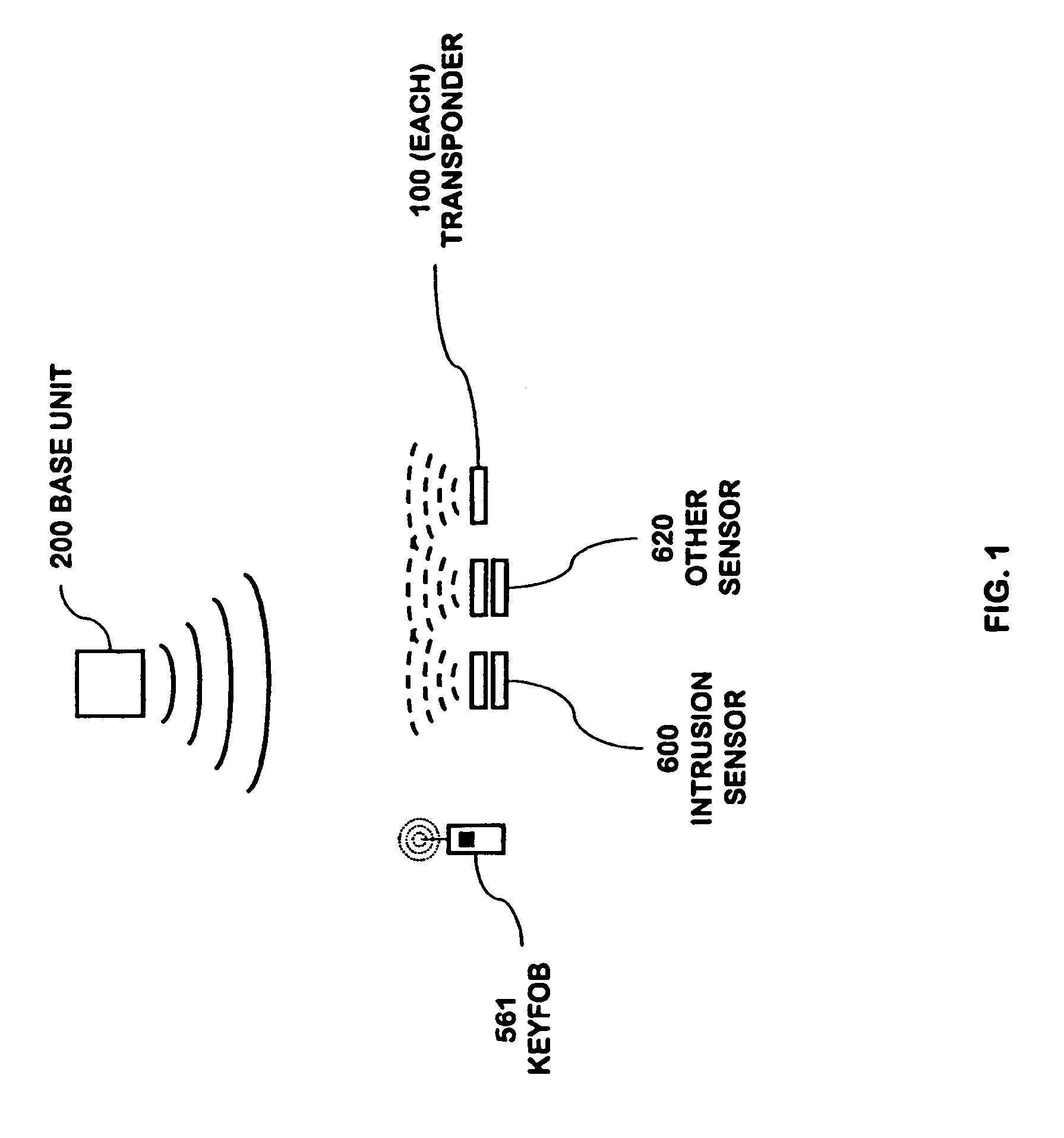
A security network for use in a building with an opening to be monitored for possible intrusion. The network includes an intrusion sensor monitoring the opening; an RFID transponder associated with the sensor; an RFID reader in wireless communication with the transponder; and a portable telephone handset having first keys activating conventional telephone capability and second keys activating interaction with the other security network components. The handset wirelessly communicates with the reader. The reader may take the form of a security cradle for the handset. Alternatively, the reader may take the form of a telephone console. The console has keys enabling a user to dial remote telephone numbers; circuitry adapted to receive wireless communications from the transponder; circuitry in wireless communication with the handset; circuitry in communication with an external network; and a processor executing program code enabling the handset to communicate with the external network via the telephone console.
Owner:ADT US HLDG INC
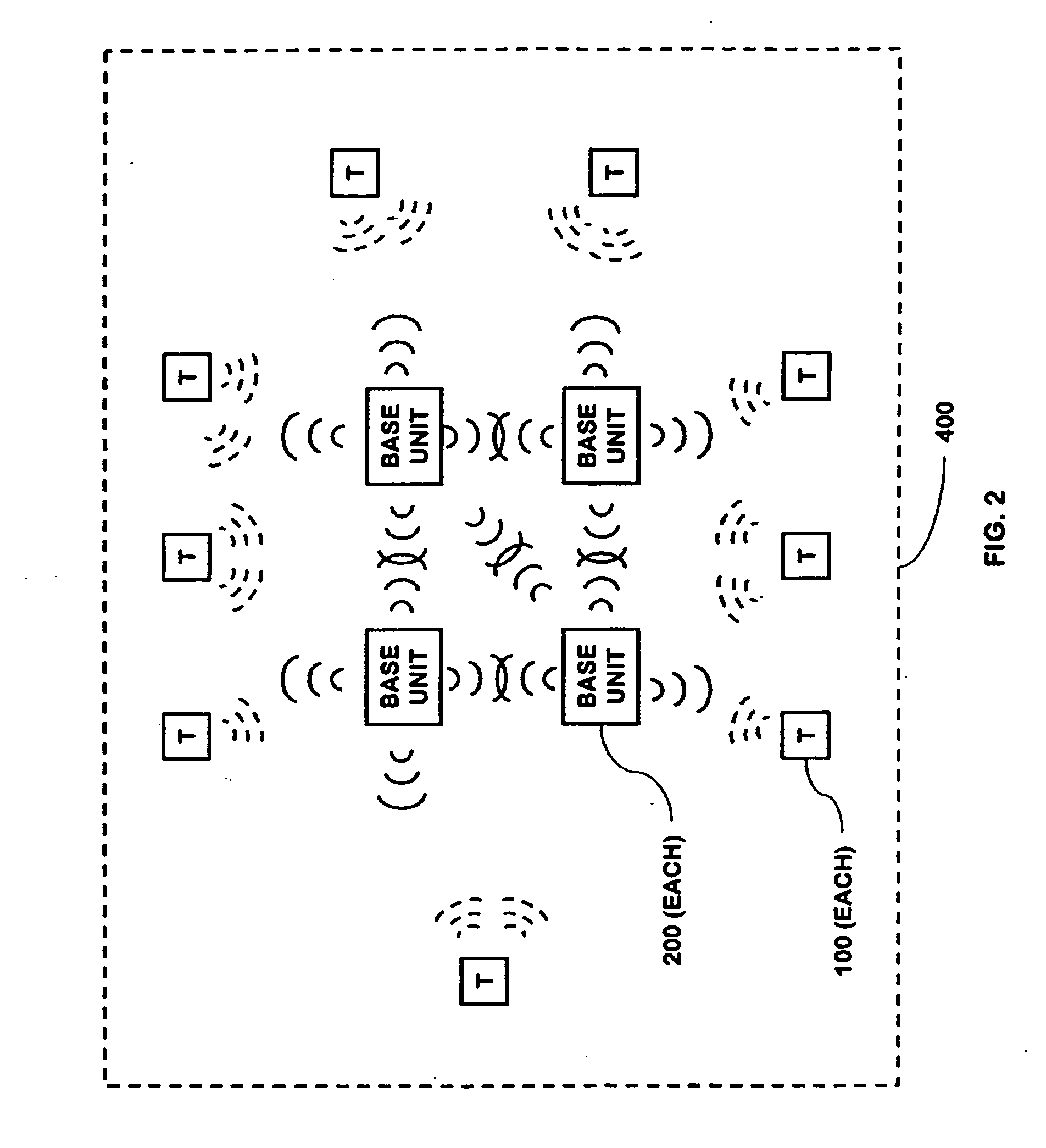
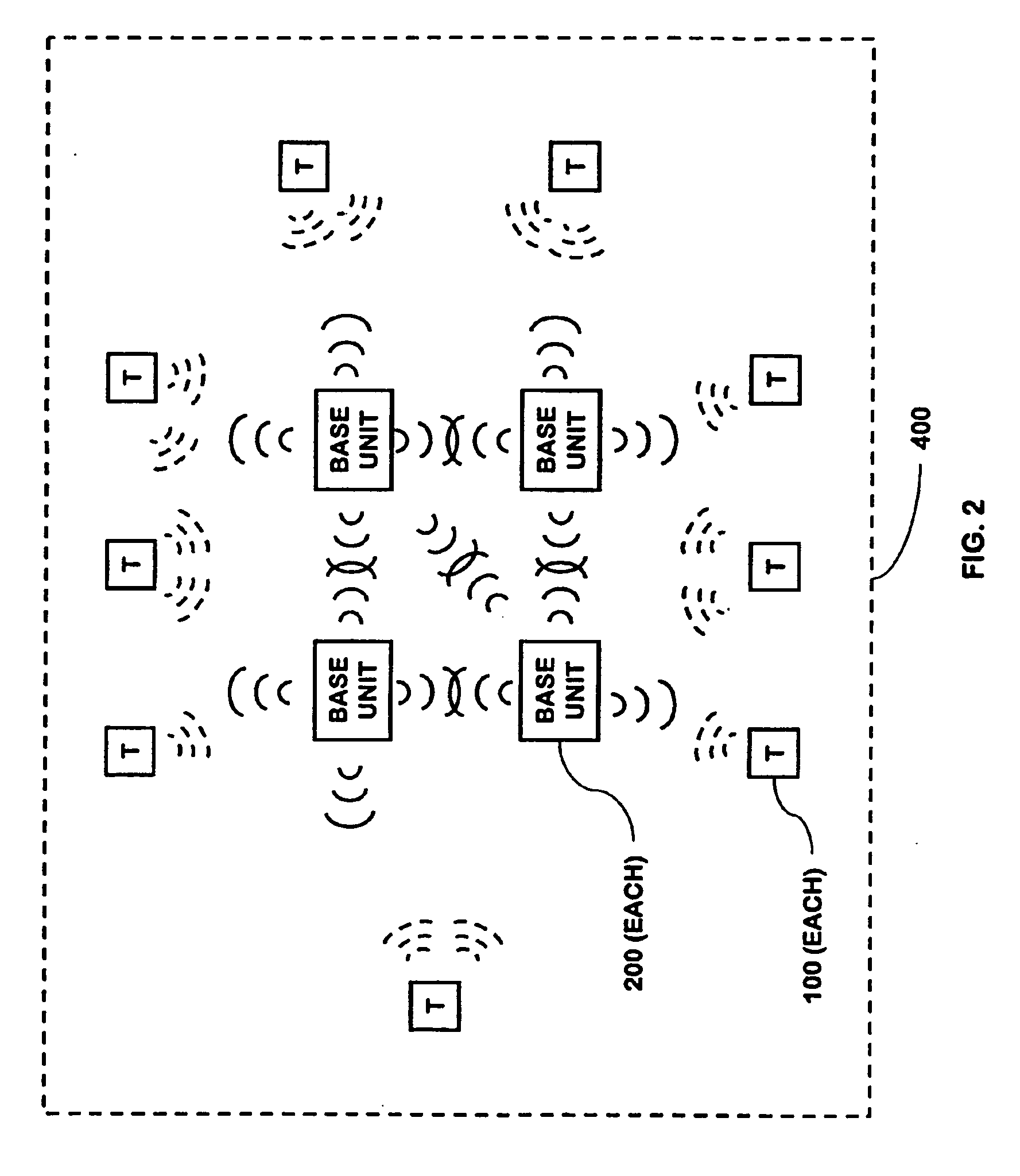
Multi-level meshed security network
InactiveUS20060145842A1Improve reliabilityLow costSafety arrangmentsComputer controlEngineeringSecondary layer
Owner:ADT US HLDG INC
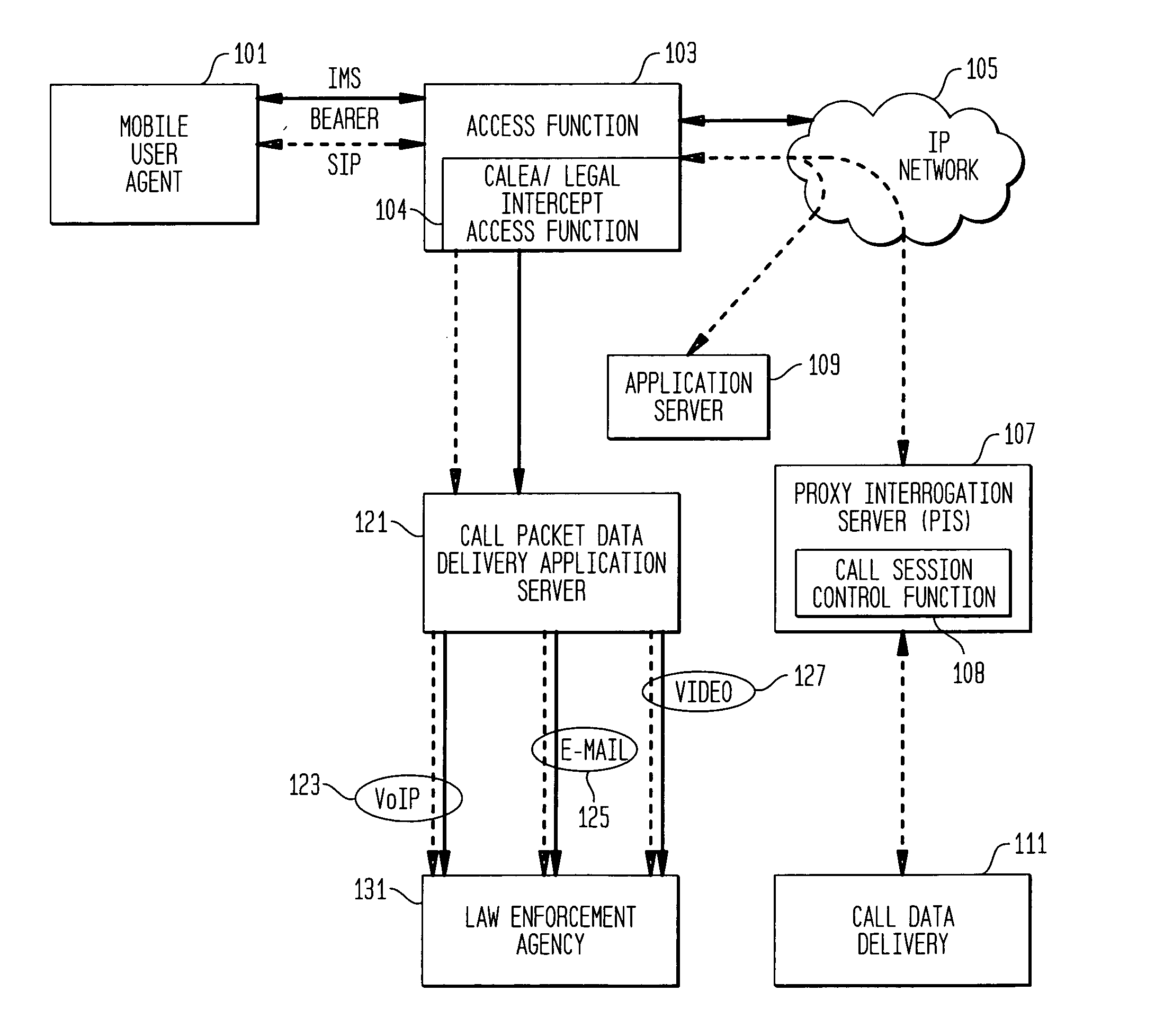
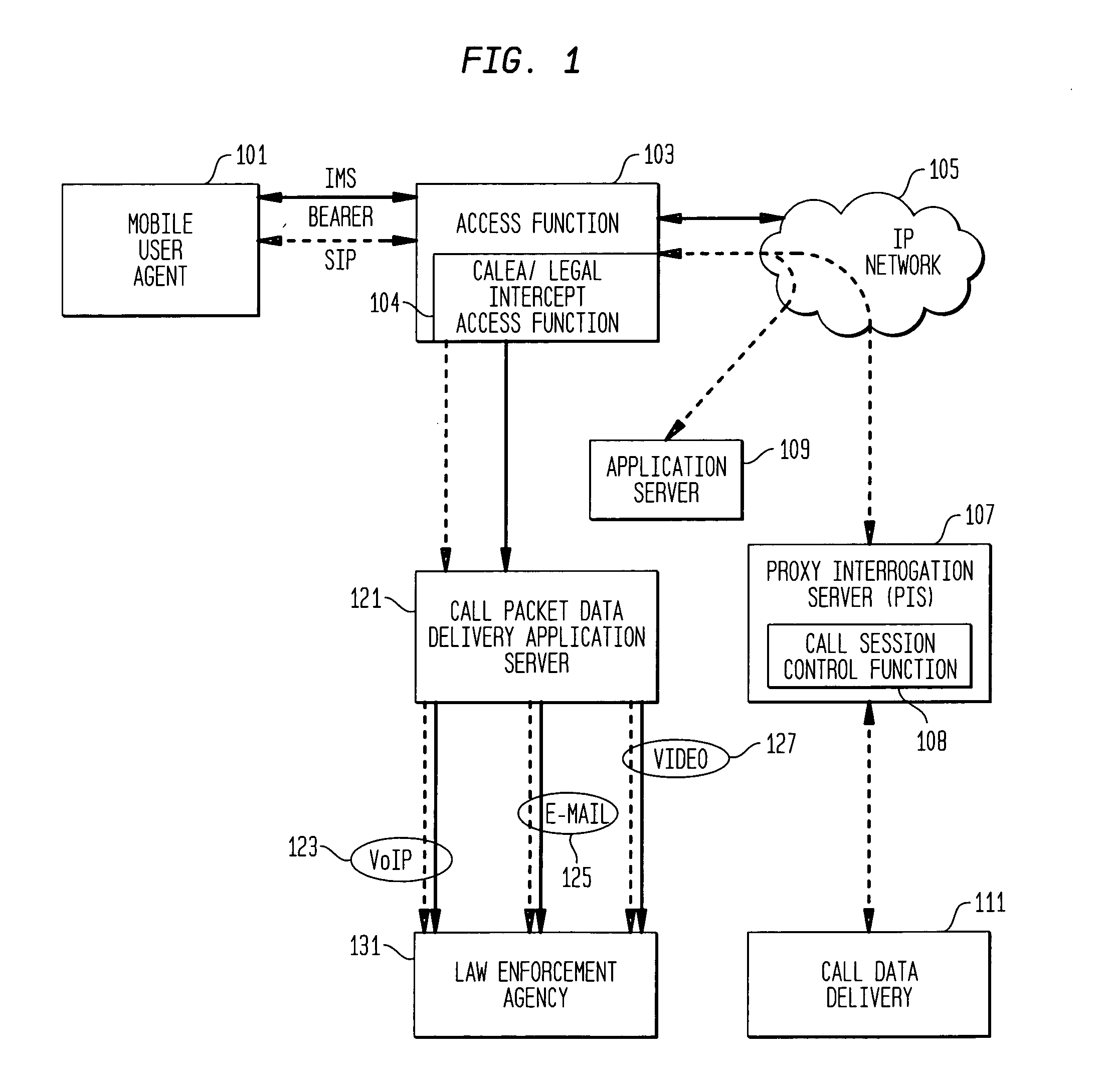
Providing CALEA/LegaI Intercept information to law enforcement agencies for internet protocol multimedia subsystems (IMS)
ActiveUS20060072550A1Supervisory/monitoring/testing arrangementsRadio/inductive link selection arrangementsData connectionApplication server
A method and apparatus for providing useful packet data to a CALEA / Legal Intercept collection function. At an access point to a network such as the Internet, sources and destinations of data connections are examined to determine whether any of the bearer messages should also be routed to a CALEA / Legal Intercept monitoring system. If this condition is recognized, the bearer messages and corresponding signaling control messages are correlated in a call packet delivery application server and then delivered to a CALEA / Legal Intercept monitoring system. Advantageously, the monitoring receives as a bundled message set the bearer message and the control messages used to route and otherwise process these bearer messages.
Owner:ALCATEL-LUCENT USA INC
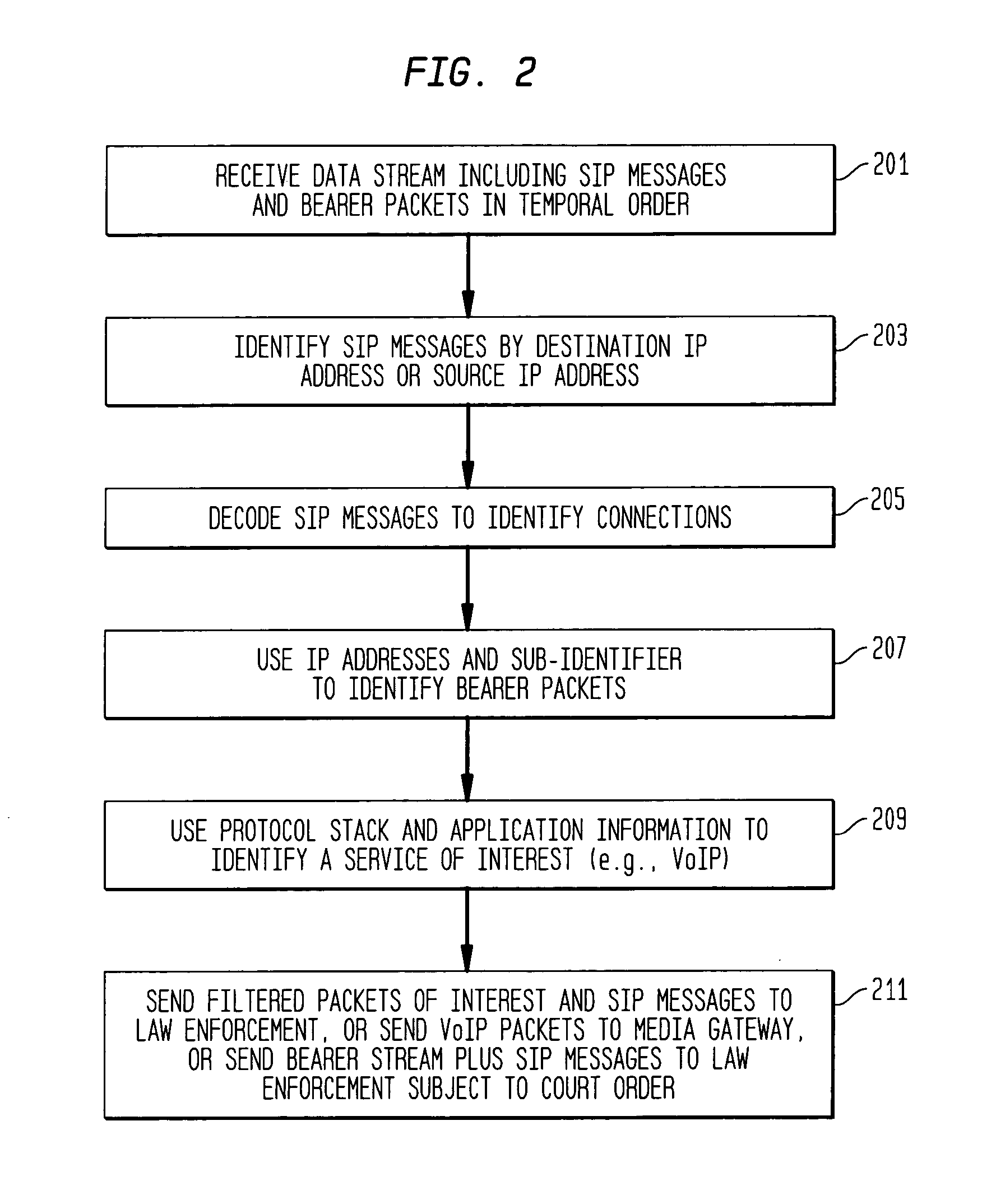
Pressure alarms and reports system module for proactive maintenance application
InactiveUS6771739B1Supervisory/monitoring/testing arrangementsSubstation equipmentFiberNetwork analytics
Methods and systems for proactively maintaining a telephone system local loop. One embodiment includes communicating with a communications network and acquiring information associated with pressure or flow sensors along fiber optic cables. Proactive maintenance of the fiber optic cables is predicted using the information associated with pressure or flow sensors. The embodiment may further include generating and dispatching work order information describing the predicted proactive maintenance. The embodiment may also include predicting proactive maintenance of telephone lines using information from a Dynamic Network Analyzer and using information from a Loop Facilities and Control System. Another embodiment includes a system for predicting proactive maintenance of a telephone system local loop. This embodiment includes a Pressure Alarms and Reports System Module, a database stored in memory, and a processor. The Pressure Alarms and Reports System Module communicates with a communications network and acquires at least one of i) pressure information associated with fiber optic cables and ii) flow information associated with fiber optic cables. The database stores the acquired information. The processor processes information stored in the database and generates predicted proactive maintenance.
Owner:BELLSOUTH INTPROP COR
Power management of transponders and sensors in an RFID security network
InactiveUS20060132302A1Improve reliabilityLow costElectric signal transmission systemsSafety arrangmentsAudio power amplifierOn-off keying
An RFID transponder with an associated sensor used in a security network including at least one RFID reader that transmits signals at a first frequency. The transponder has a processor controlling its other components. Transmitter circuitry coupled to a transmit antenna transmits signals to the reader at a second frequency. A receive antenna receives signals in a frequency band that includes the first frequency. One or more RF diodes obtain the signal from the receive antenna and output a power envelope signal representing the power level of the signal obtained from the receive antenna. An amplifier coupled to the output of the RF diode amplifies the power envelope signal received from the RF diode. The processor receives the amplified power envelope signal and decodes any data that have been encoded using an on-off keyed modulation scheme applied to the signal obtained from the receive antenna.
Owner:INGRID
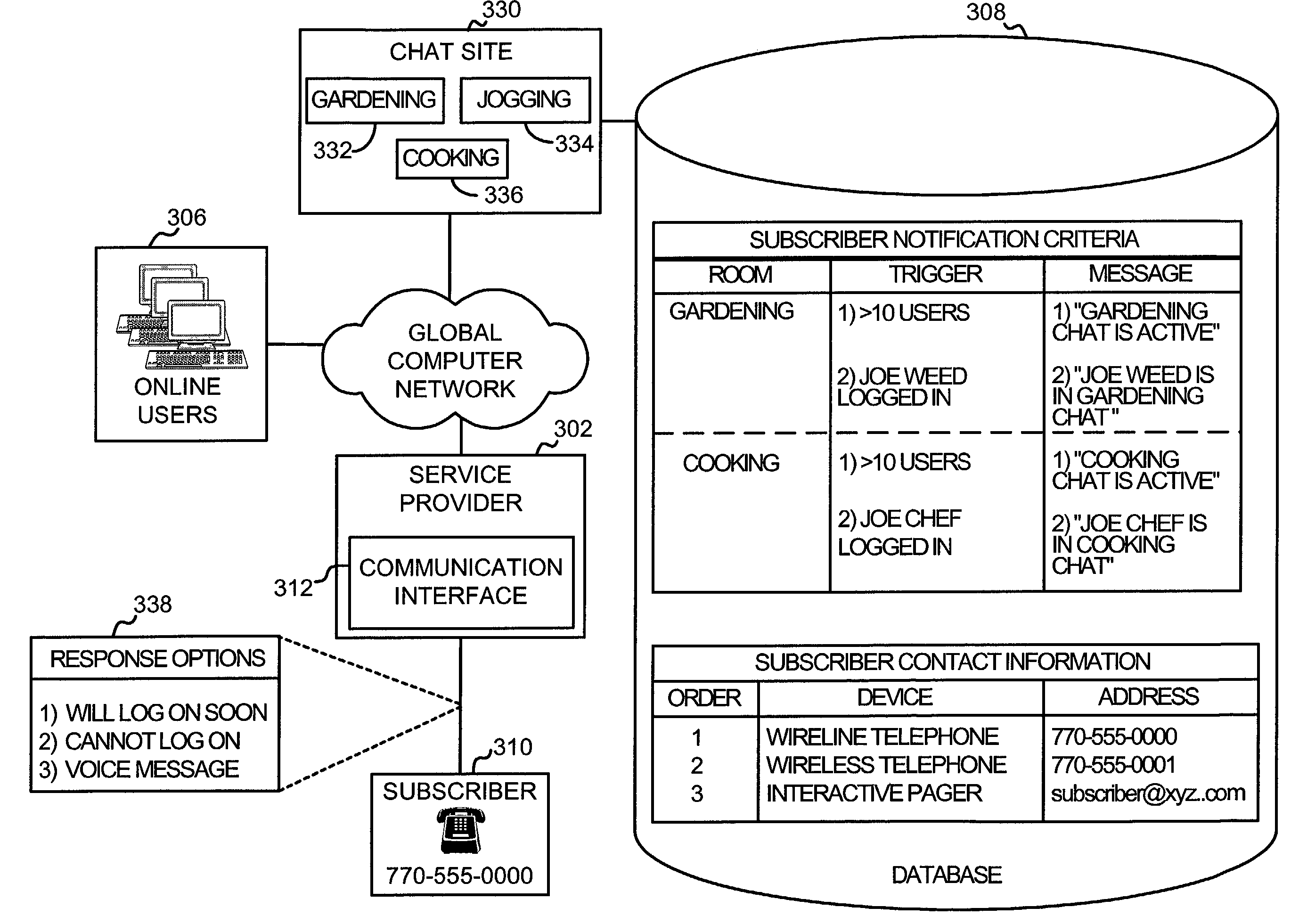
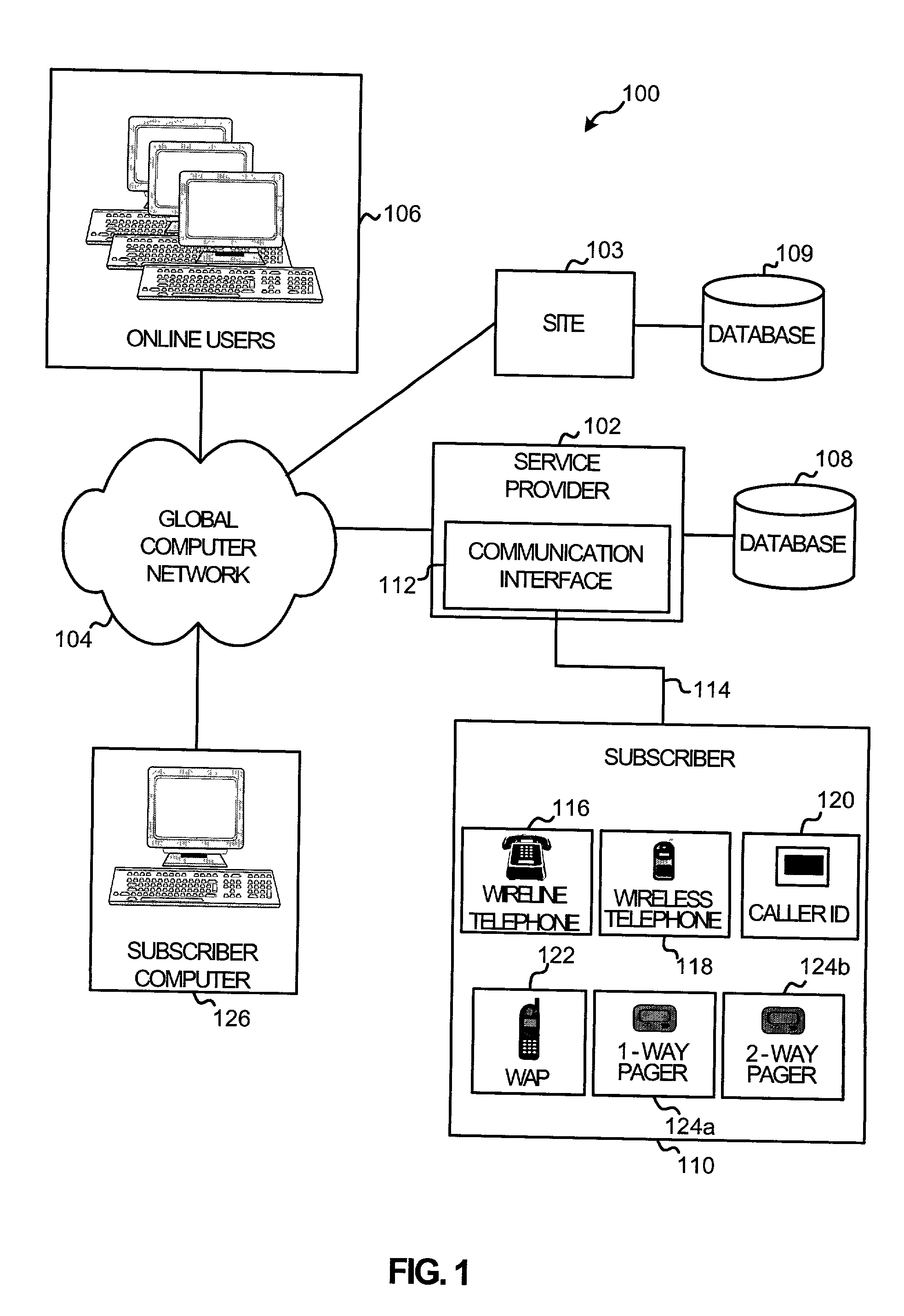
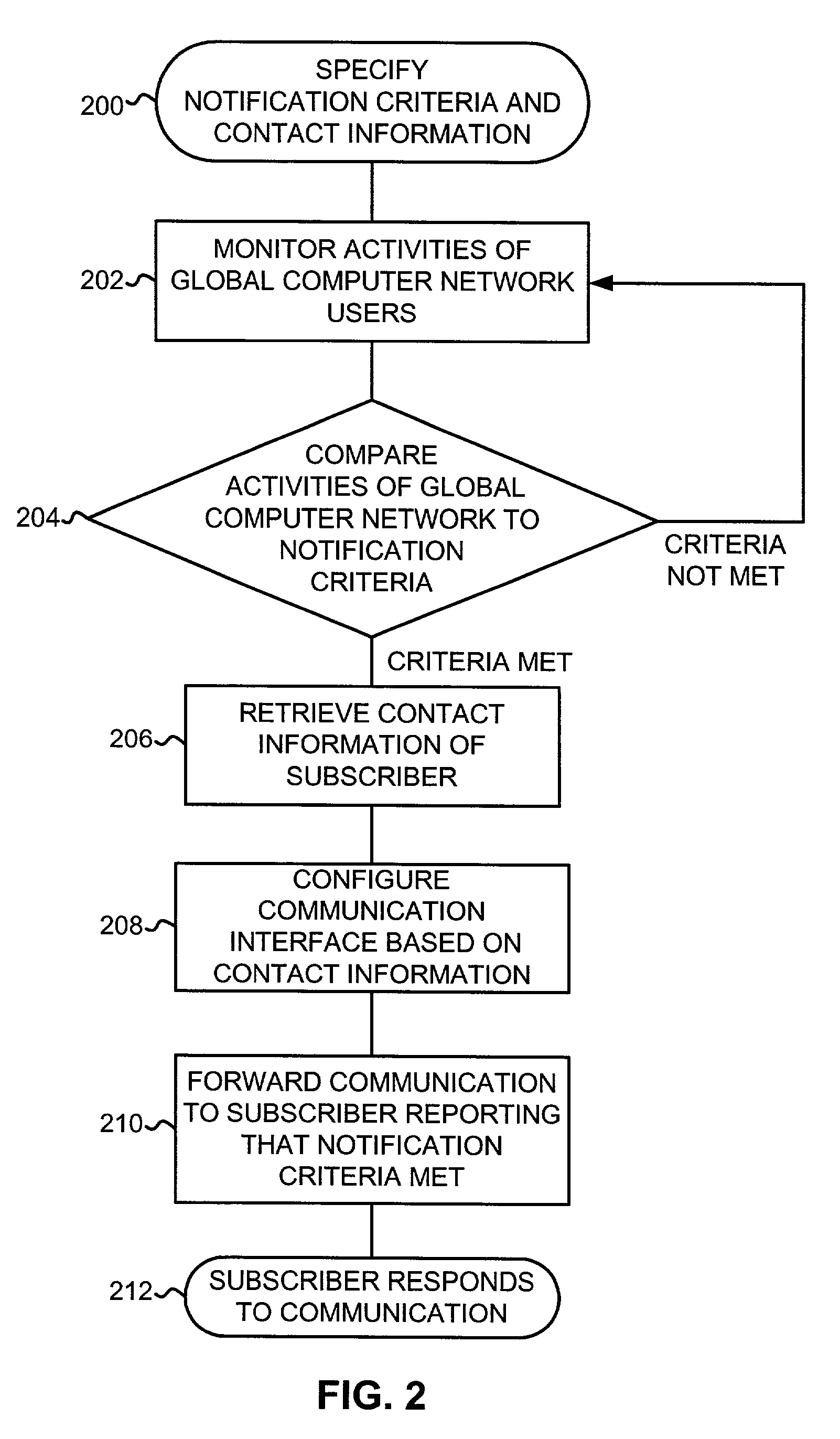
System and method for notifying an offline global computer network user of an online interaction
InactiveUS20050004984A1Easy to placeAvoid difficultySpecial service provision for substationFinanceChat roomPager
A system and method for notifying an offline global computer network user of an online interaction in which the offline user could participate. The system and method specify notification criteria of the offline user, monitor activities occurring on the global computer network, compare the activities to the notification criteria, and, if the activities satisfy the notification criteria, forward an offline communication to the offline user, which notifies the offline user of the online interaction. Examples of the online interactions include chat rooms, game sites, instant messaging services, auctions, and calls made over the global computer network. Examples of the offline communication include calls to a wireline telephone, calls to a wireless telephone, messages to a caller identification device, messages to a wireless access protocol device, messages to a one-way pager, and messages to an interactive pager.
Owner:BELLSOUTH INTPROP COR
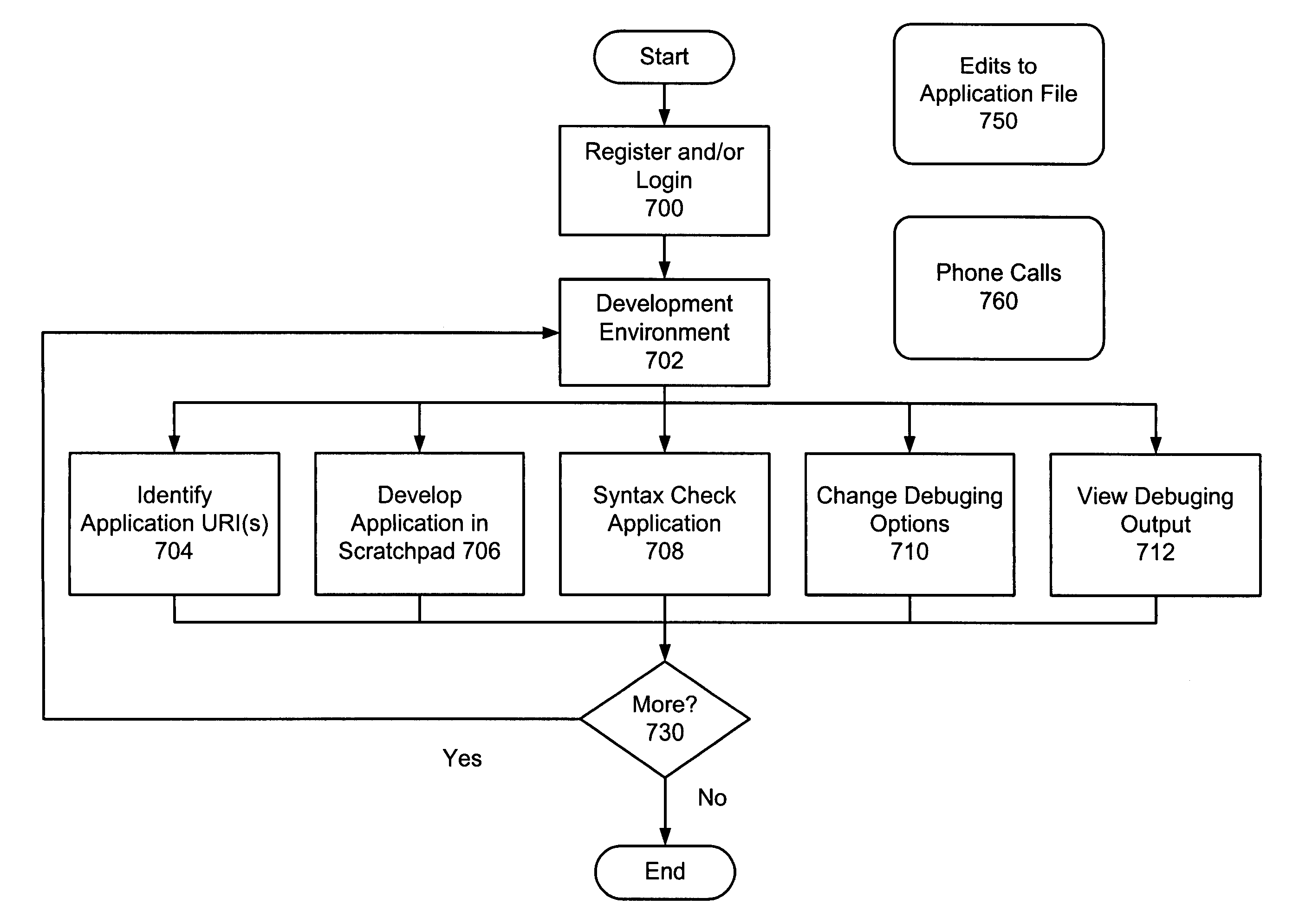
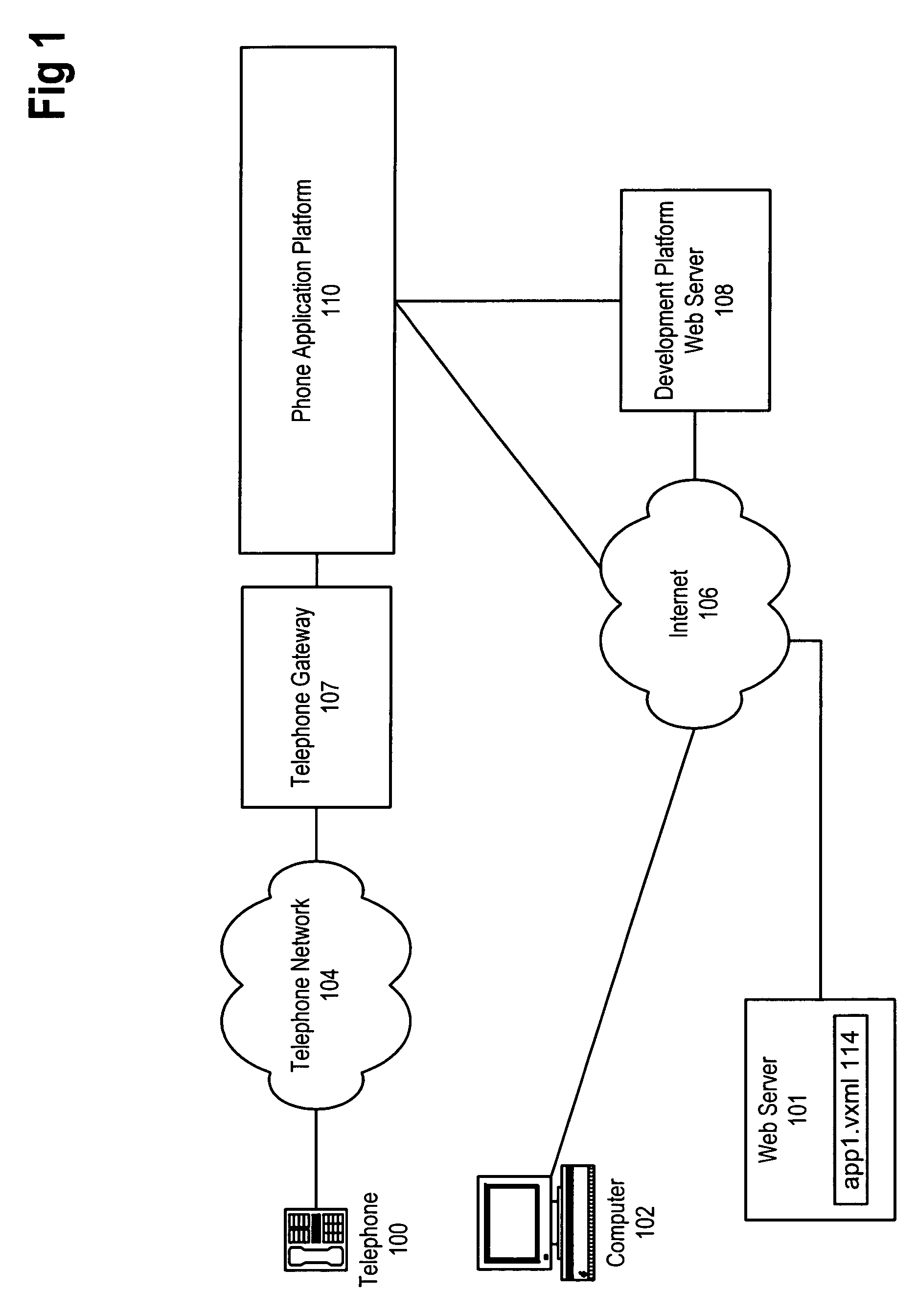
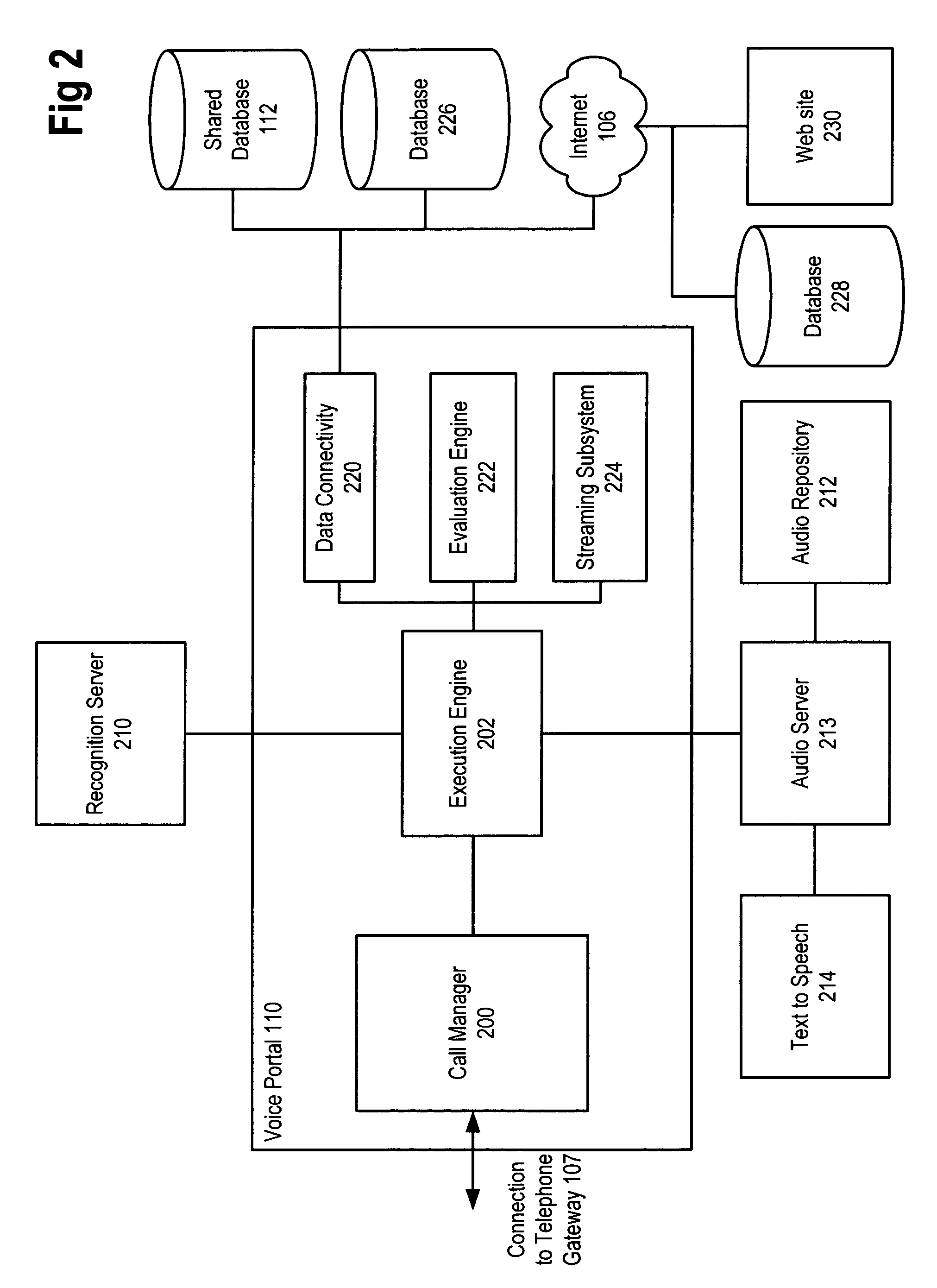
Method and apparatus for zero-footprint phone application development
InactiveUS7140004B1Avoid any surpriseTelephone data network interconnectionsError detection/correctionWeb browserApplication procedure
A zero-footprint remotely hosted phone application development environment is described. The environment allows a developer to use a standard computer without any specialized software (in some embodiments all that is necessary is a web browser and network access) together with a telephone to develop sophisticated phone applications that use speech recognition and / or touch tone inputs to perform tasks, access web-based information, and / or perform commercial transactions. Some embodiments support concurrent call flow tracking that allows a developer to observe, using a web browser, the execution of her / his application. A variety of reusable libraries are provided to enable the developer to leverage well-developed libraries for common playback, input, and computational tasks. Embodiments support rapid application deployment from the development environment to hosted application deployment to the intended audience.
Owner:MICROSOFT TECH LICENSING LLC
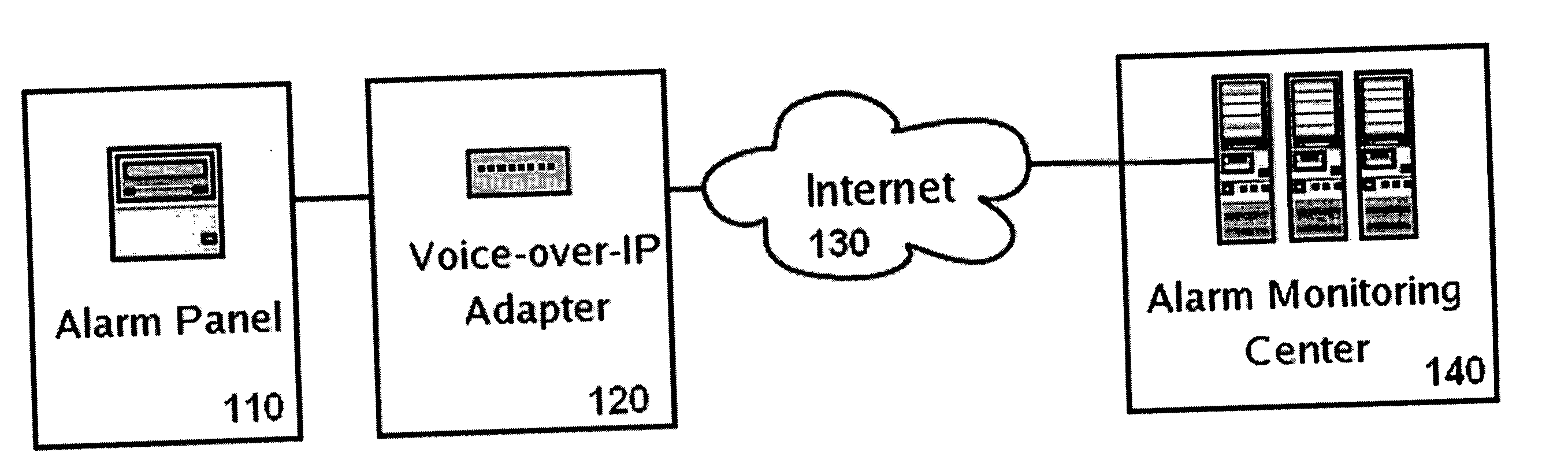
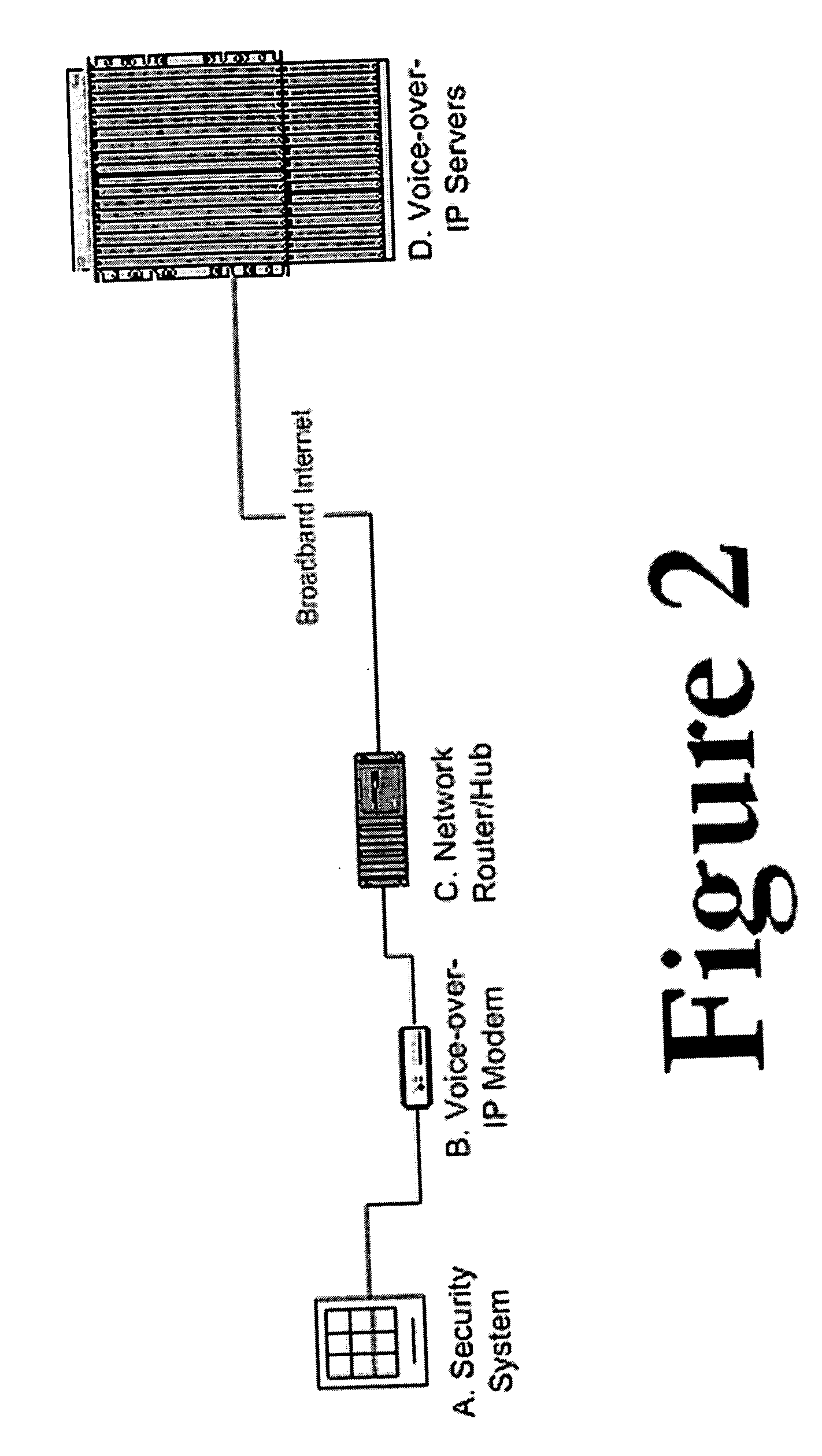
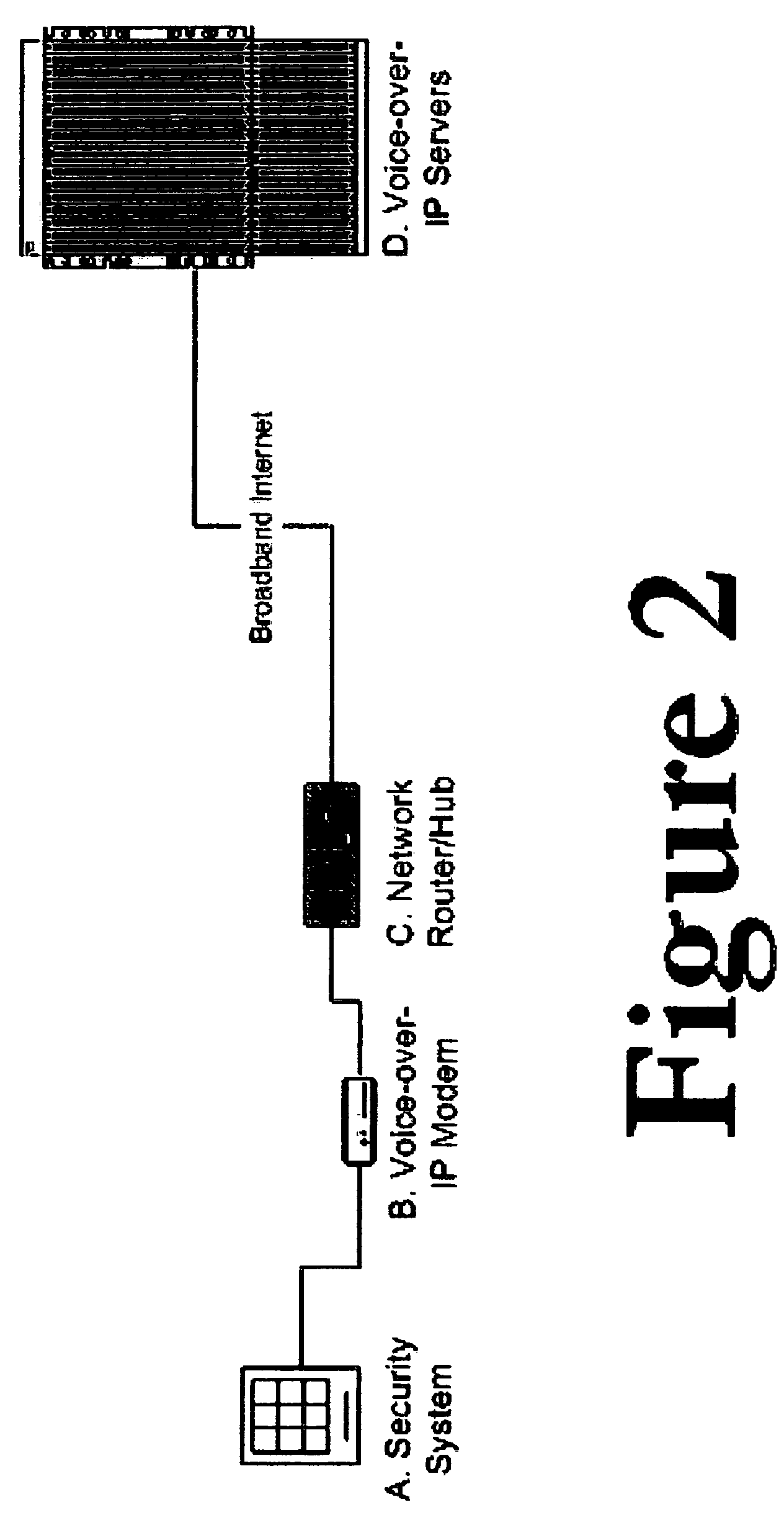
Private VoIP network for security system monitoring
InactiveUS20060067484A1Reduce errorsShort response timeInterconnection arrangementsFrequency-division multiplex detailsCommunications securityPrivate network
Security systems typically communicate with alarm monitoring centers using a telephone connection. Security systems will check in with the alarm monitoring center with a diagnostic signal at a predetermined interval—typically once per day. When a security system is connected to a Voice-over-IP service (using Broadband Internet), rather than a standard telephone line, the opportunity exists to poll in real-time the status of the connection, and alert the owner (or alert the alarm monitoring center) that the customer's connection has been broken. The present invention offers a system and technique for monitoring a security system connected using a Voice-over-IP connection, in real time, and alerting the owner of the security system, or the alarm-monitoring center, when the connection is broken. This alert can be used, for example, to issue a telephone call to the police, informing them of the breach of line integrity and possible compromise of the premise.
Owner:NUMEREX CORP
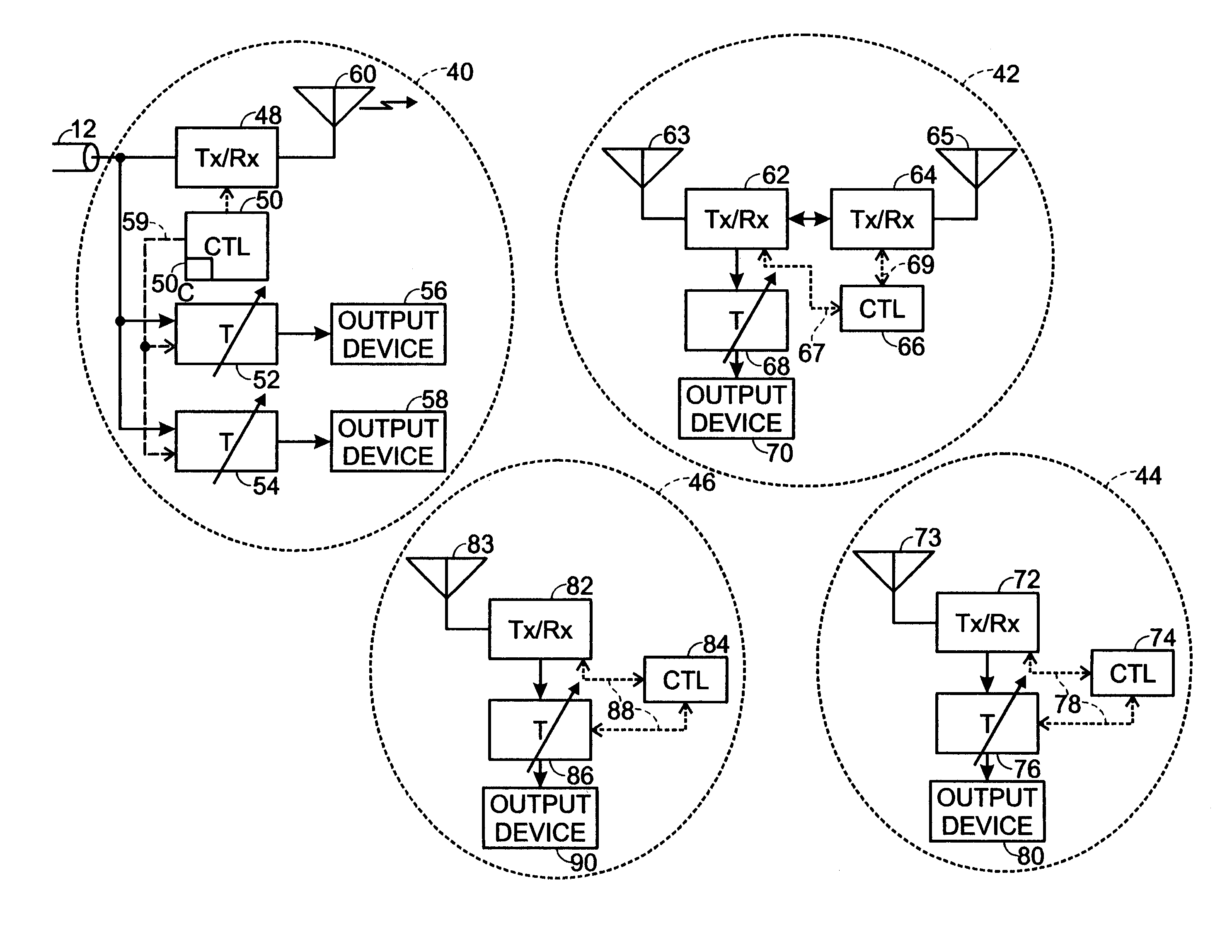
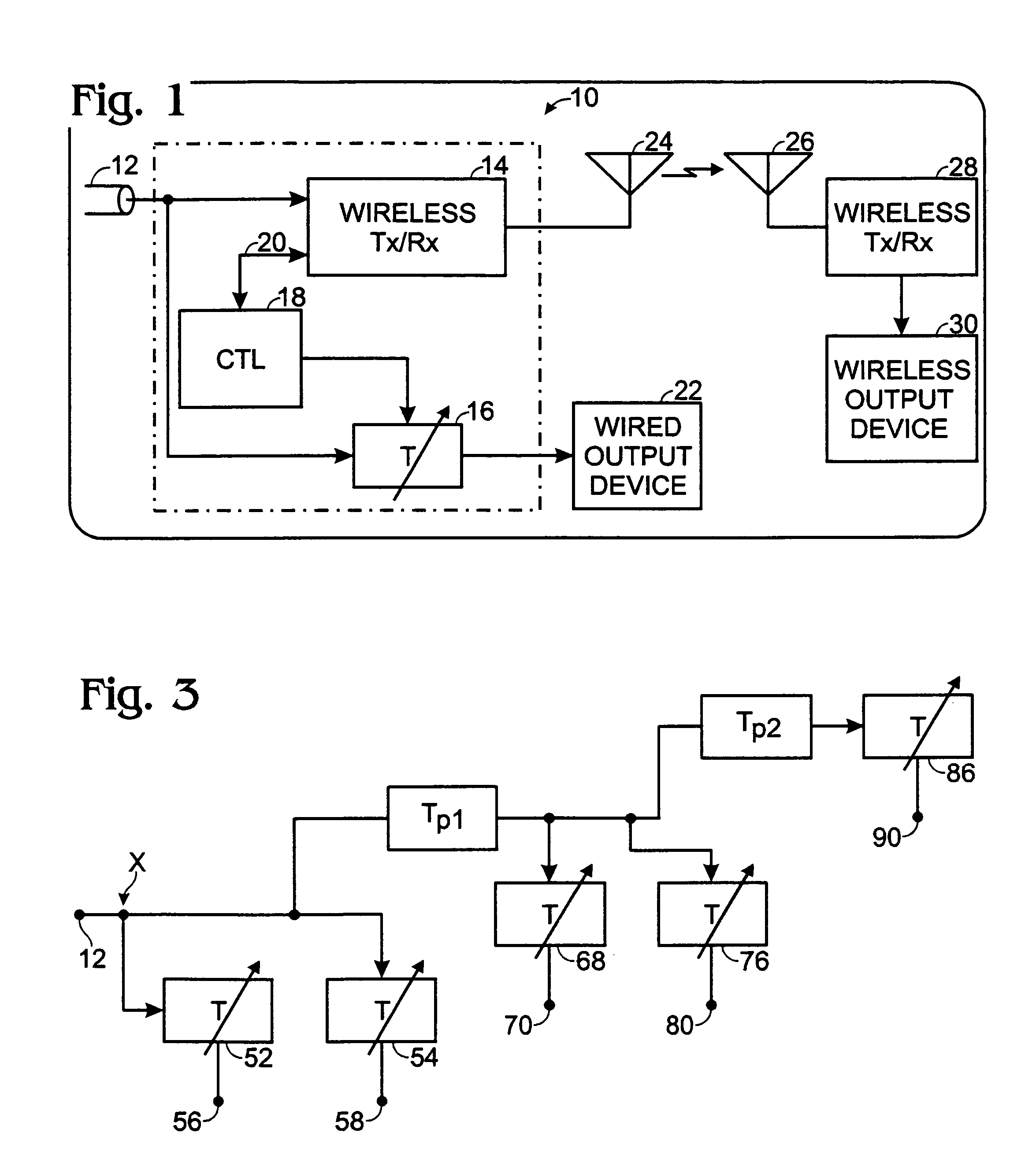
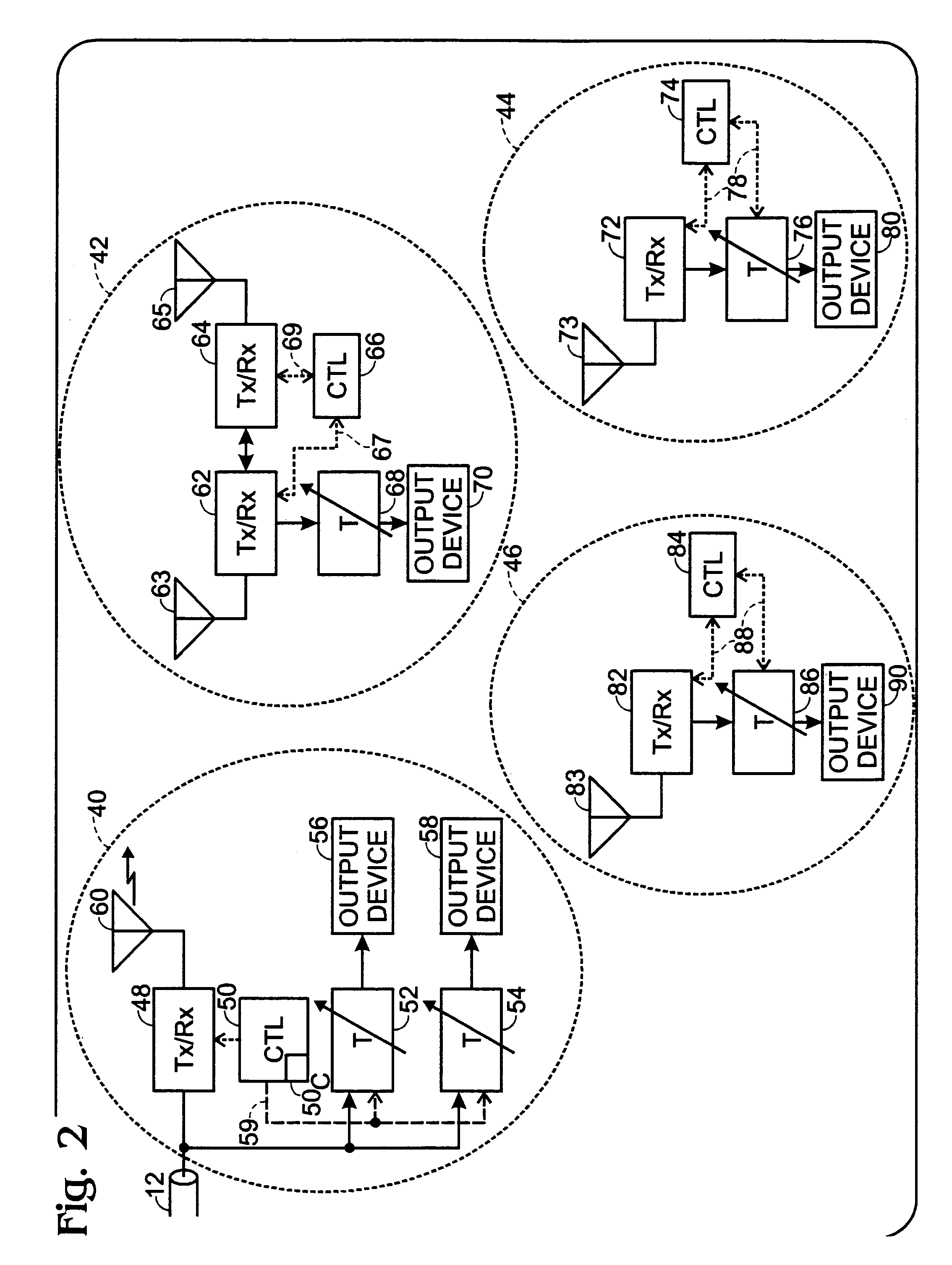
Multimedia wired/wireless content synchronization method
A method of synchronizing a multimedia content stream for output to a plurality of wired and wireless output device in a network having plural realms, wherein each realm includes a CTL, includes buffering the multimedia content stream in a first realm; determining a buffer delay; transmitting the buffer delay to all CTLs in all realms of the network; and transmitting the multimedia content stream to all realms in the network.
Owner:SHARP KK
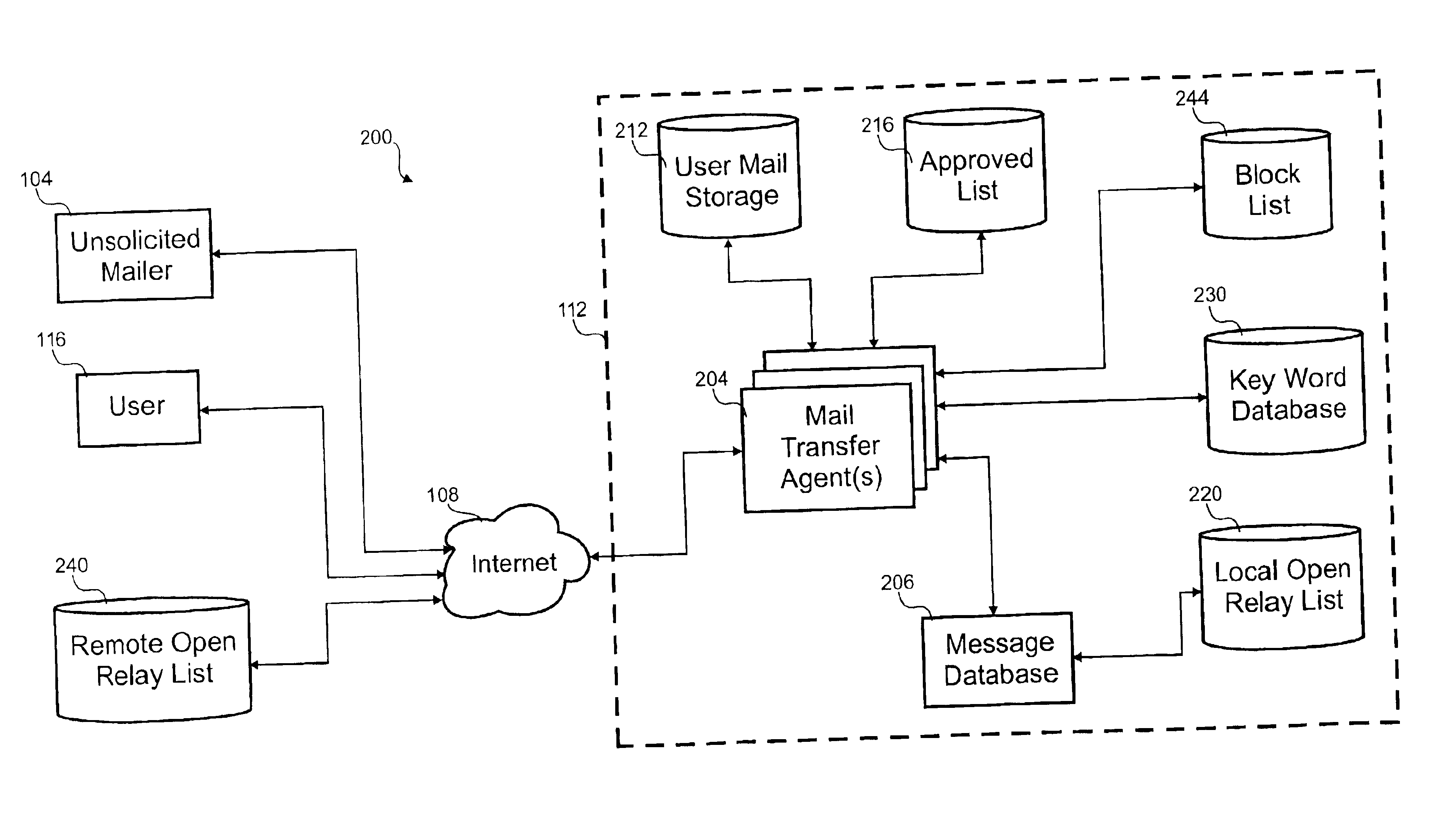
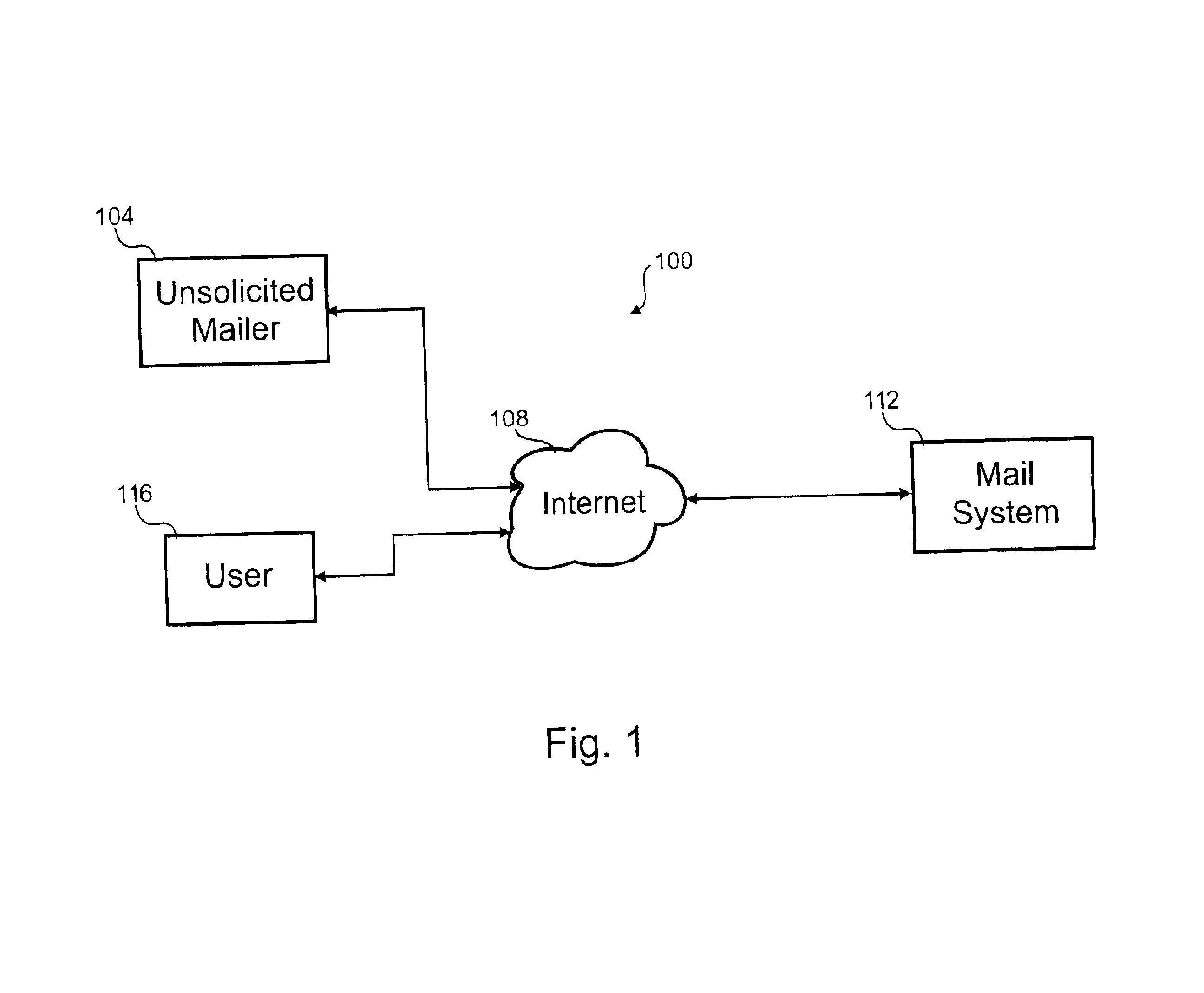
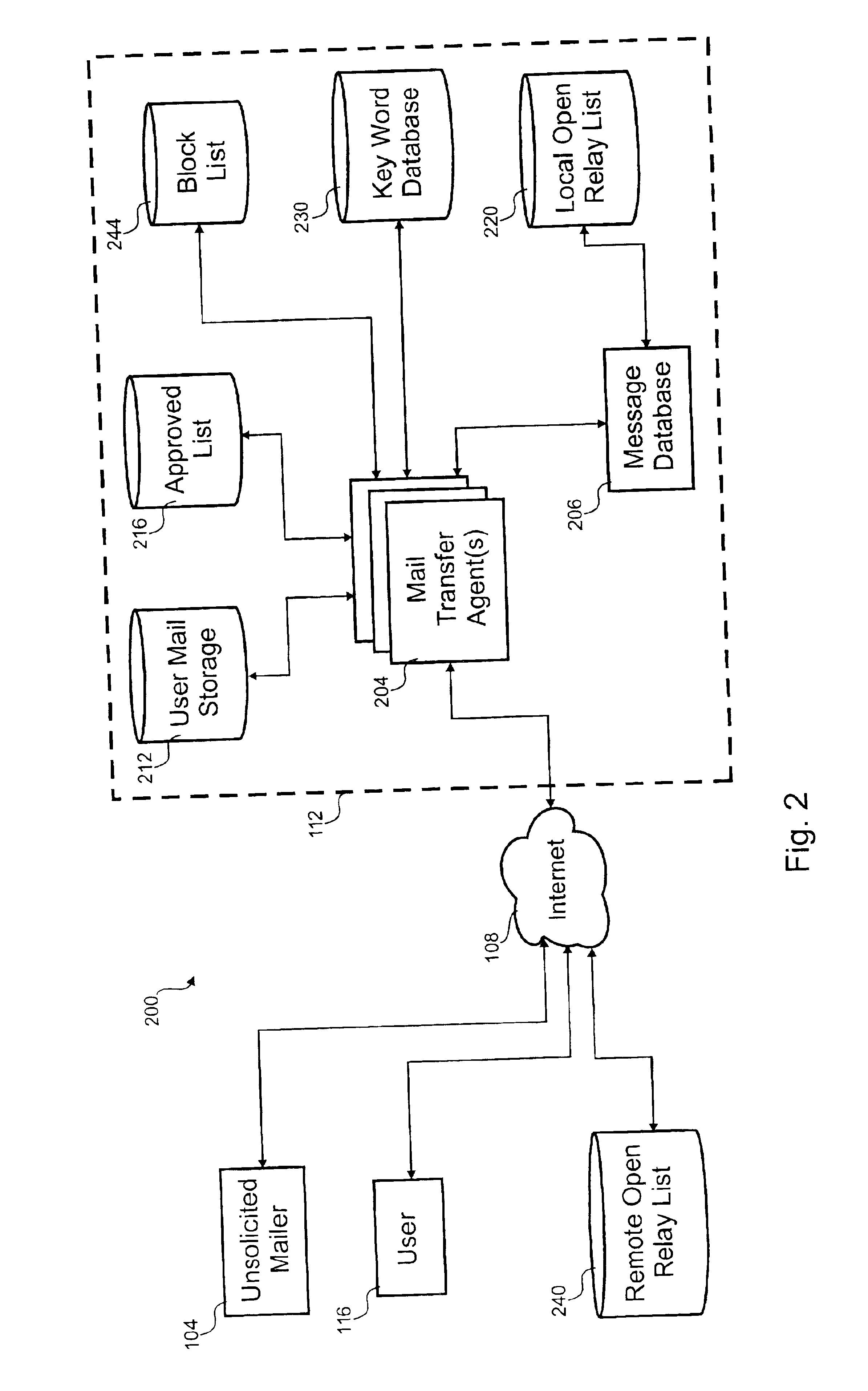
Processing of textual electronic communication distributed in bulk
InactiveUS6842773B1Supervisory/monitoring/testing arrangementsMultiple digital computer combinationsElectronic submissionElectronic communication
The invention relates to processing of electronic text communication distributed in bulk. In one embodiment, a process for blocking electronic text communication distributed in bulk is disclosed. In the process, a first electronic and a second electronic submission are received. A first portion is extracted from the first electronic submission and a second portion is extracted from the second electronic submission. A first code is determined for the first portion and a second code is determined for the second portion. The first code is indicative of the first portion and the second code is indicative of the second portion. After the first code is compared to the second code, the second electronic submission is filtered in response to that comparison.
Owner:ENERGETIC POWER INVESTMENT
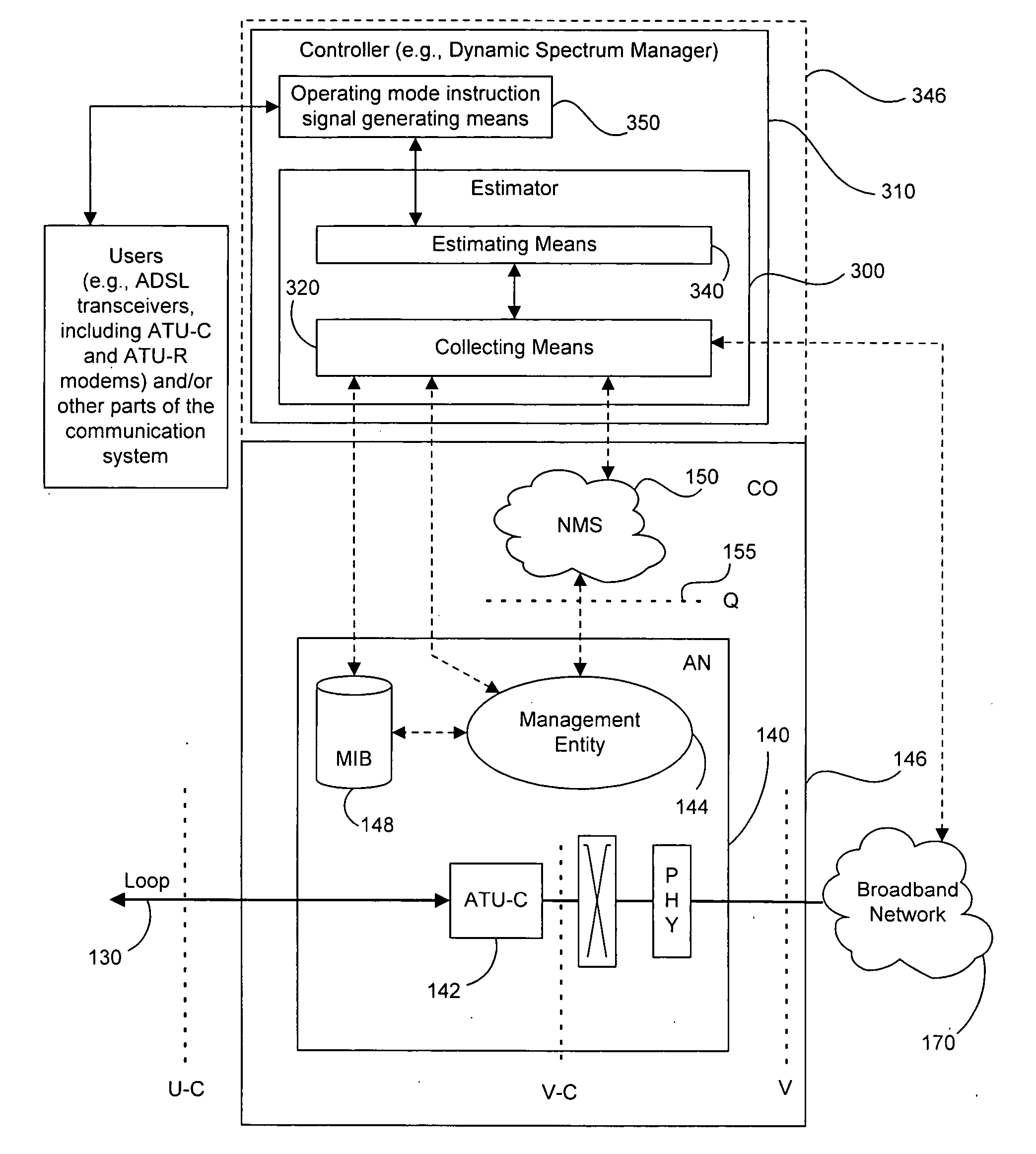
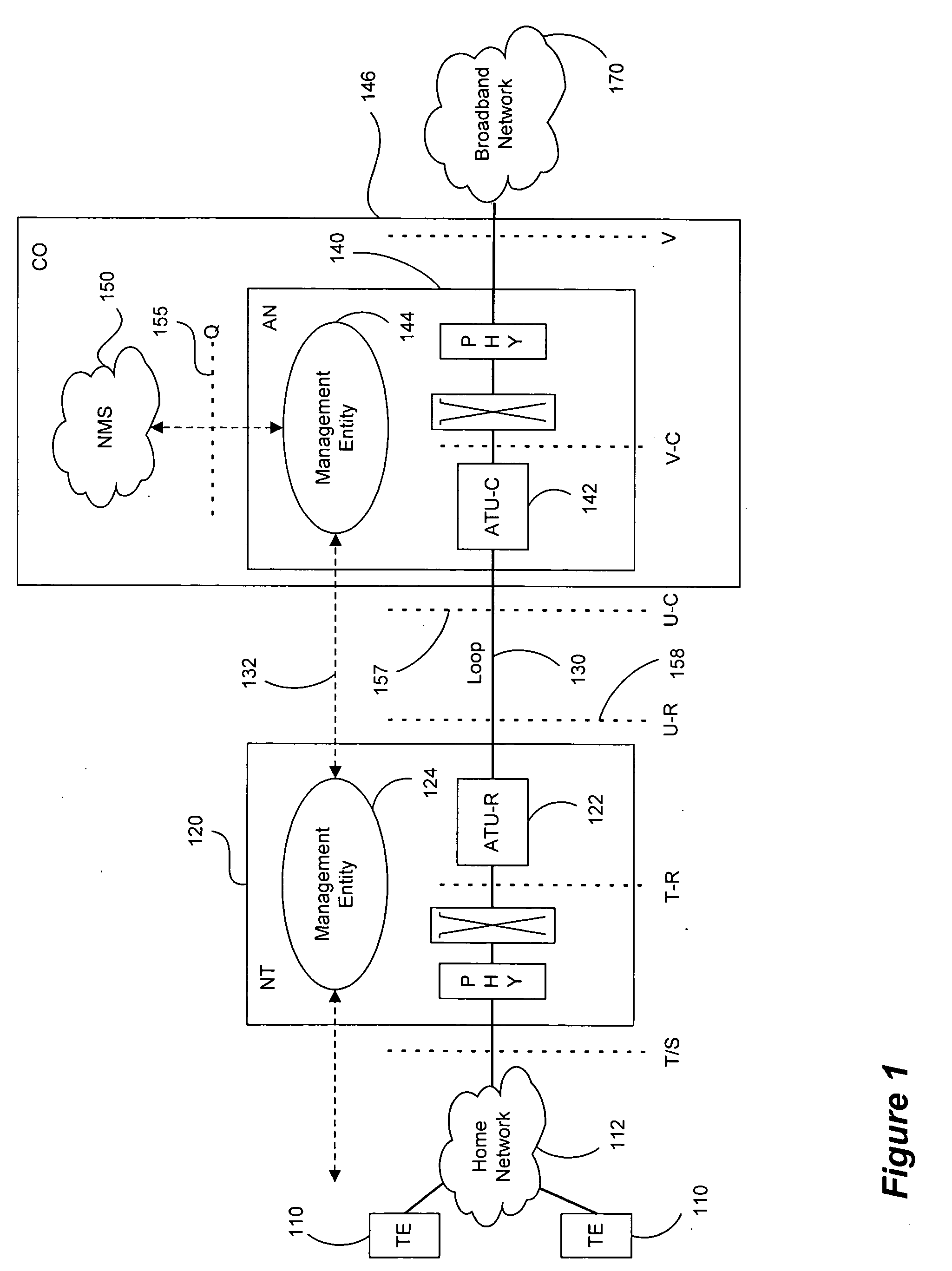
DSL system estimation and parameter recommendation
ActiveUS20050123027A1Improve performanceError preventionModulated-carrier systemsCarrier signalEngineering
Estimates of a communication system configuration, such as a DSL system, are based on operational data collected from a network element management system, protocol, users and / or the like. The operational data collected from the system can include performance-characterizing operational data that typically is available in an ADSL system via element-management-system protocols. Generated estimates and / or approximations can be used in evaluating system performance and directly or indirectly dictating / requiring changes or recommending improvements in operation by transmitters and / or other parts of the communication system. Data and / or other information may be collected using “internal” means or may be obtained from system elements and components via email and / or other “external” means. The likelihood of a model's accuracy can be based on various data, information and / or indicators of system performance, such as observed normal operational data, test data and / or prompted operational data that shows operating performance based on stimulation signals. One example of such prompted data uses frequency carrier masks to approximate the Hlog of a given channel, including information regarding bridged taps, attenuation, etc.
Owner:ASSIA SPE LLC CO THE CORP TRUST CO
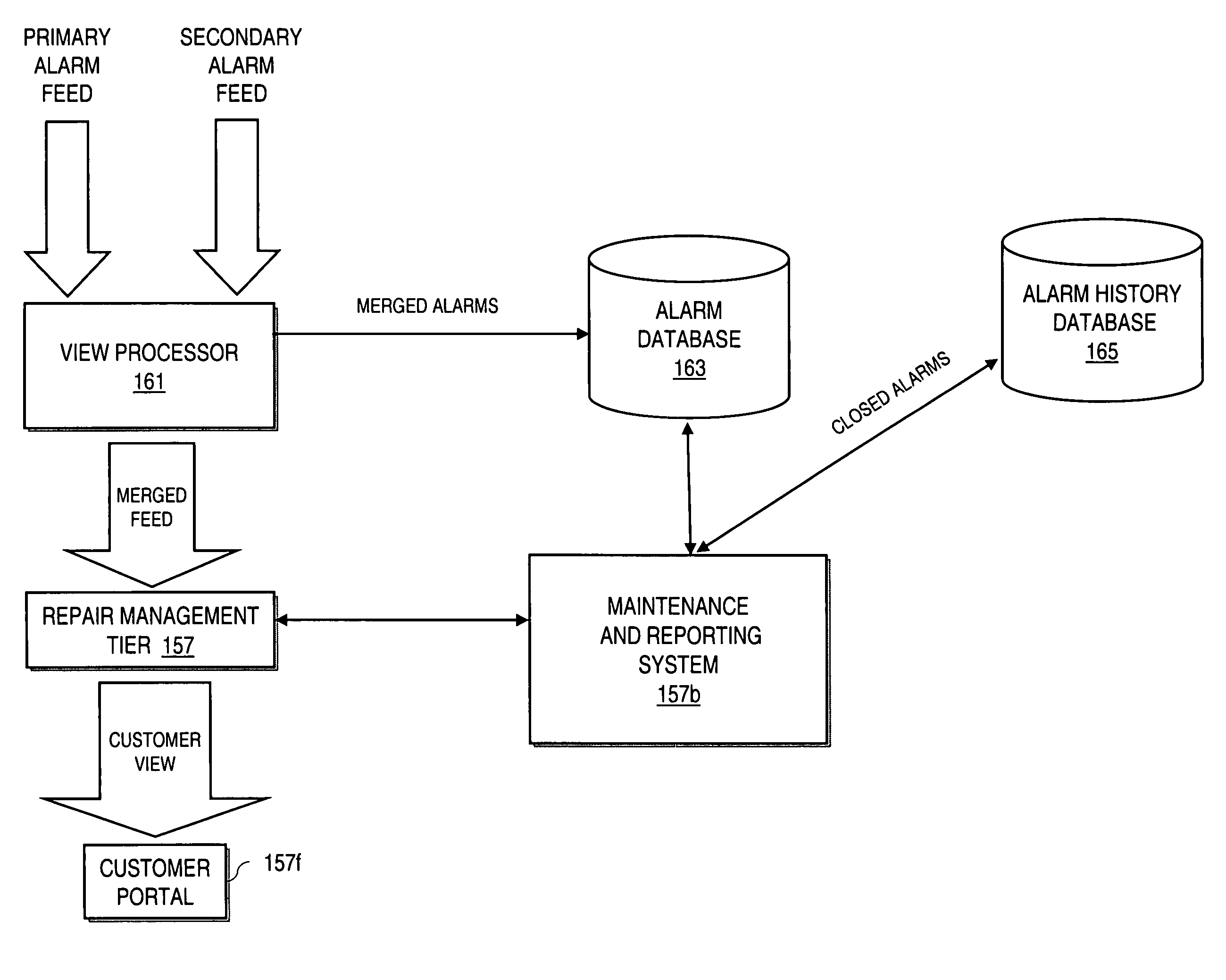
Method and system for providing alarm reporting in a managed network services environment
InactiveUS7525422B2Electric controllersSupervisory/monitoring/testing arrangementsNetwork serviceReal-time computing
An approach for alarm reporting is provided. An alarm from a first alarm feed and an alarm from a second alarm feed are received. A merged alarm is generated to provide a consistent view of an event corresponding to the alarm from the first alarm feed and the alarm from the second alarm feed. The merged alarm is stored for retrieval by a reporting system.
Owner:ATLASSIAN US INC
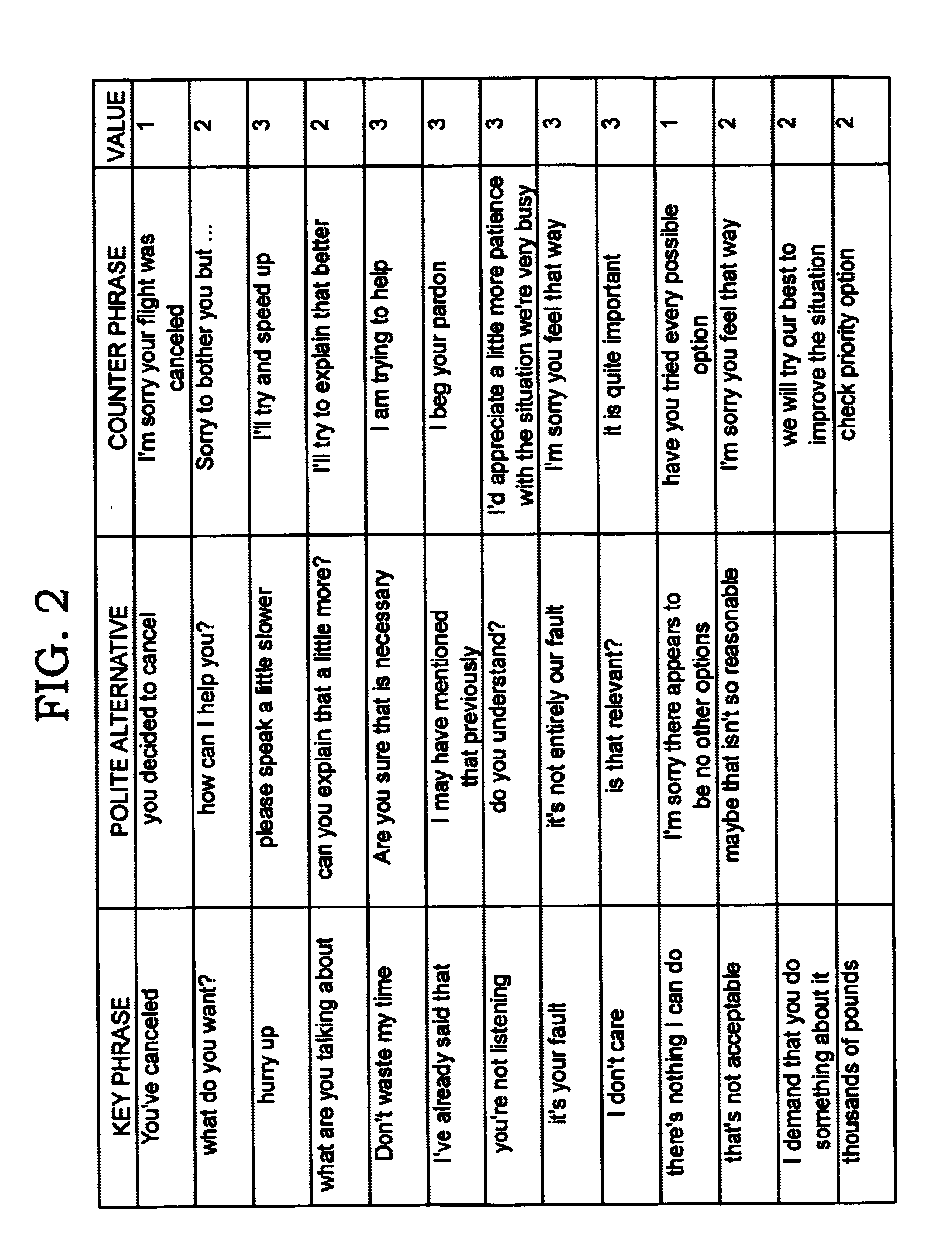
Call centre agent automated assistance
InactiveUS6721416B1The method is simple and fastSpecial service for subscribersSupervisory/monitoring/testing arrangementsHuman–computer interactionSpeech sound
This invention relates to the automated assistance of a telephony call center agent comprising a method and system for providing dialogue suggestions to an agent during an agent caller interaction. A prior art solution provides data based on analyzed text from one or other of the conversations but does not offer any useful information based on the performance of the agent or on the state of the interaction. A method of interaction in a voice response application comprising: receiving a voice signal in a call center; identifying whether the caller or a call center agent is the originator of the voice signal; converting the voice signal into computer readable text; identifying a key word such as a confrontational phrase e.g. 'what are you talking about' in the converted computer readable text; and providing a different suggestion depending on whether the originator is the call agent or the caller. For instance, a suggestion if the agent made the confrontational phrase would be to use a less confrontational phrase next time such as 'can you explain that again'. A suggestion if the caller made the confrontational phrase would be to counter with a 'I'll try to explain that better'.
Owner:IBM CORP
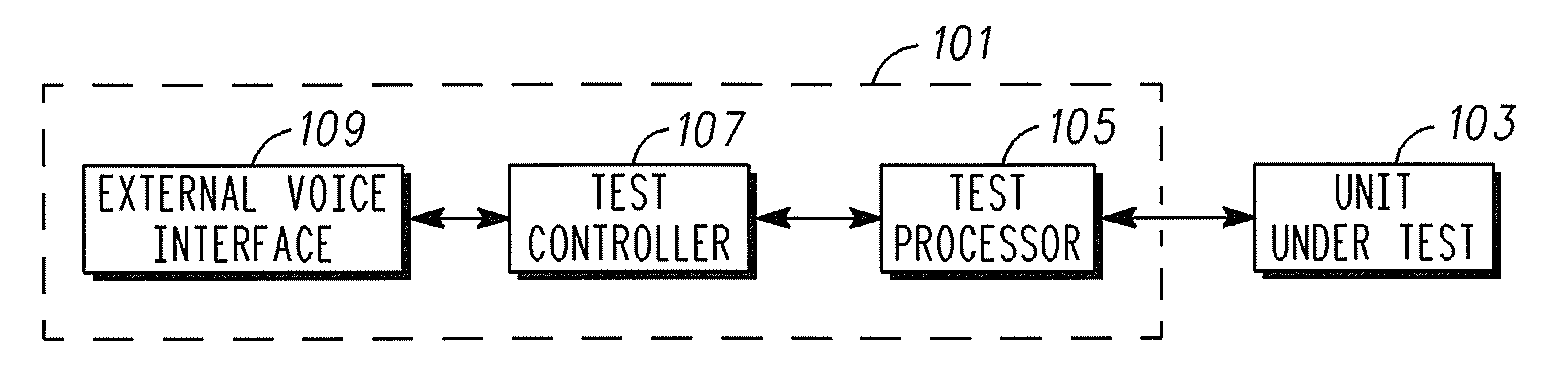
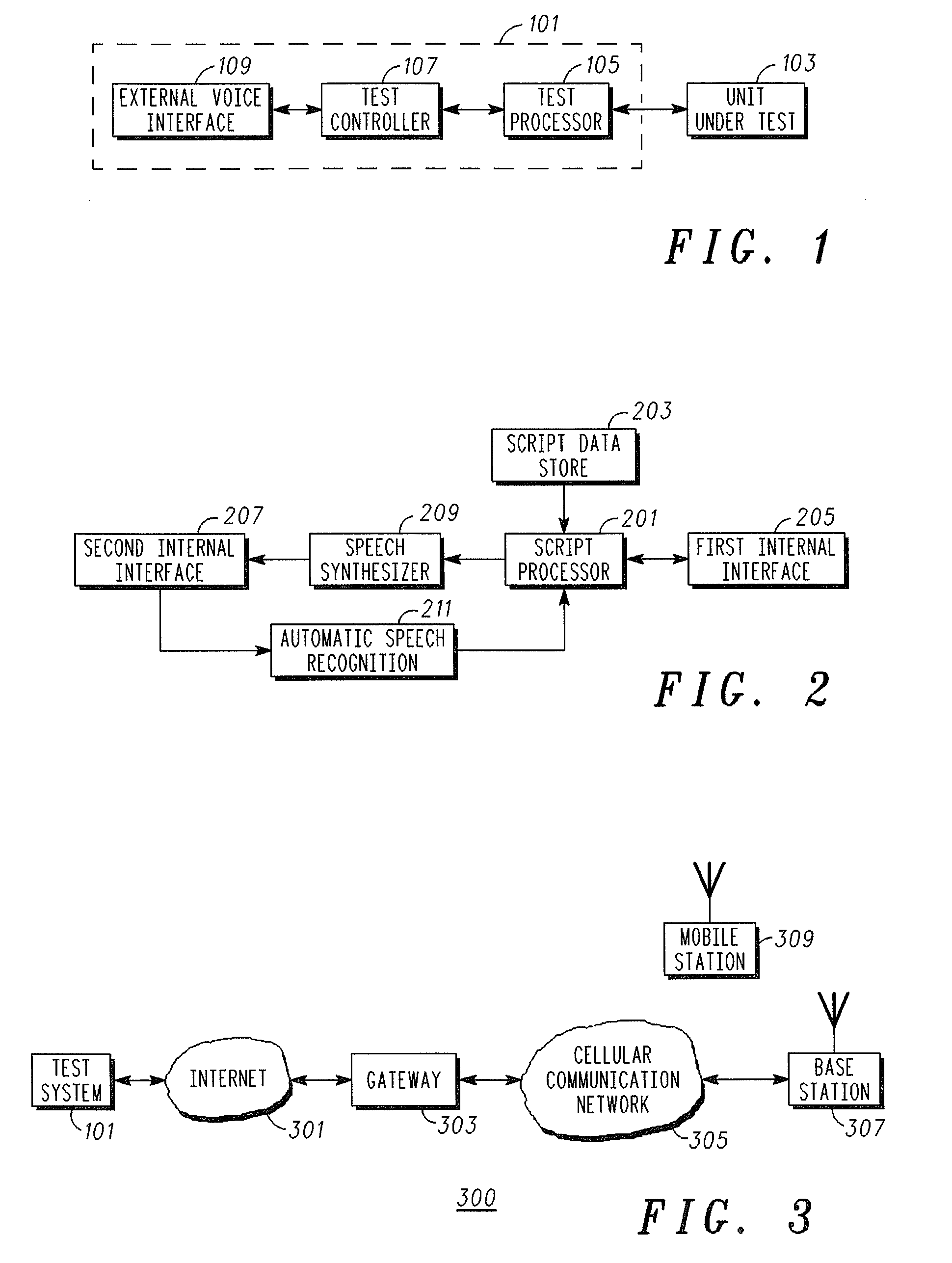
A Test System and method of Operation
InactiveUS20070291905A1Remote control is implementedGood user interfaceDevices with voice recognitionSupervisory/monitoring/testing arrangementsScripting languageComputer hardware
A test system comprises a test processor which is arranged to perform hardware level tests on a unit under test. A voice interface interfaces to an external voice communication link coupled to a remote voice communication unit. A test controller is coupled to the test processor and the voice interface and comprises a script processor for executing a test control script. The test control script is in accordance with a voice scripting language standard, such as the Voice extensible Markup Language, VXML, standard. The script processor comprises a first interface for interfacing with the test processor in response to the test control script and a second interface for interfacing with the voice interface in response to the test control script. The invention may allow a user friendly speech interface to a hardware level test system.
Owner:EMERSON NETWORK POWER EMBEDDED COMPUTING
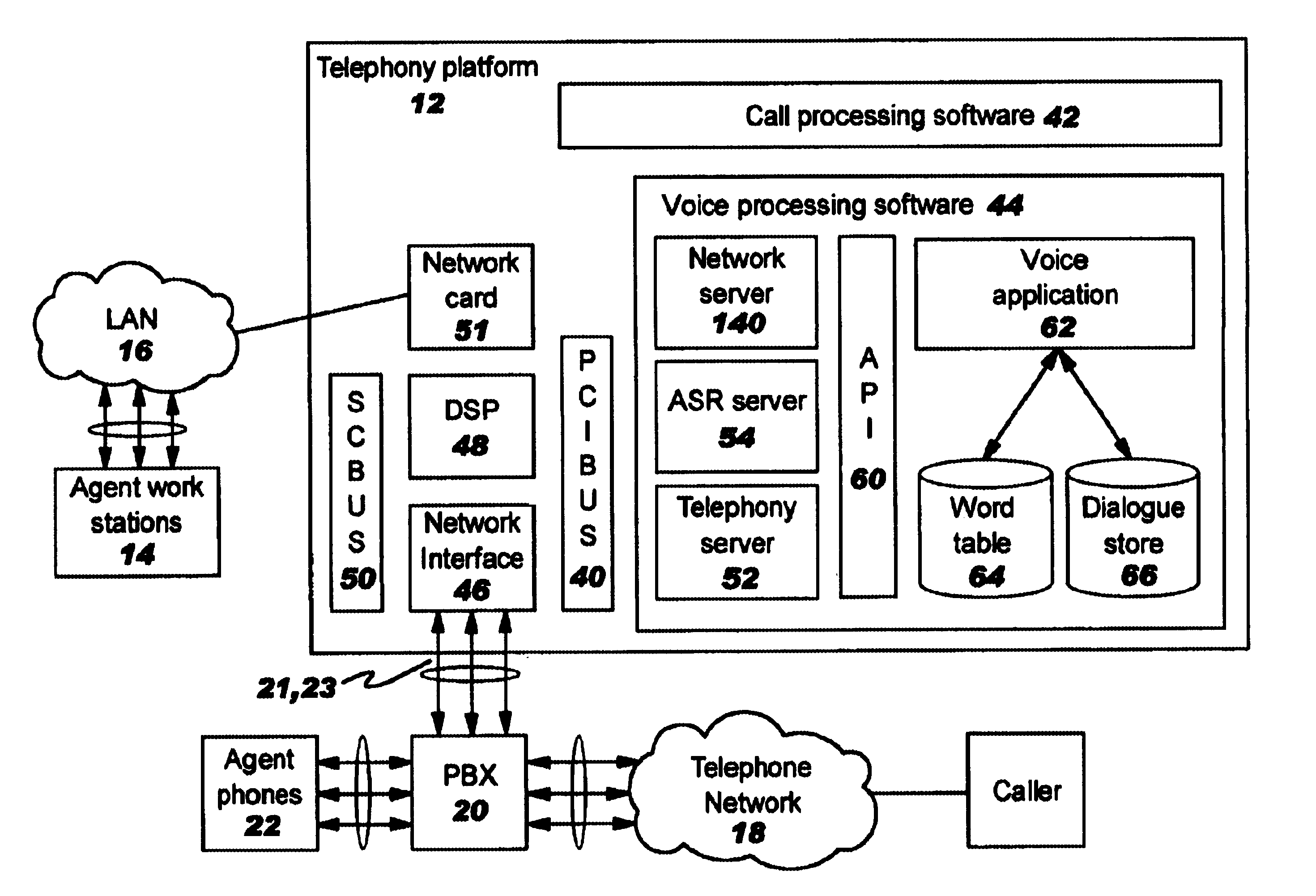
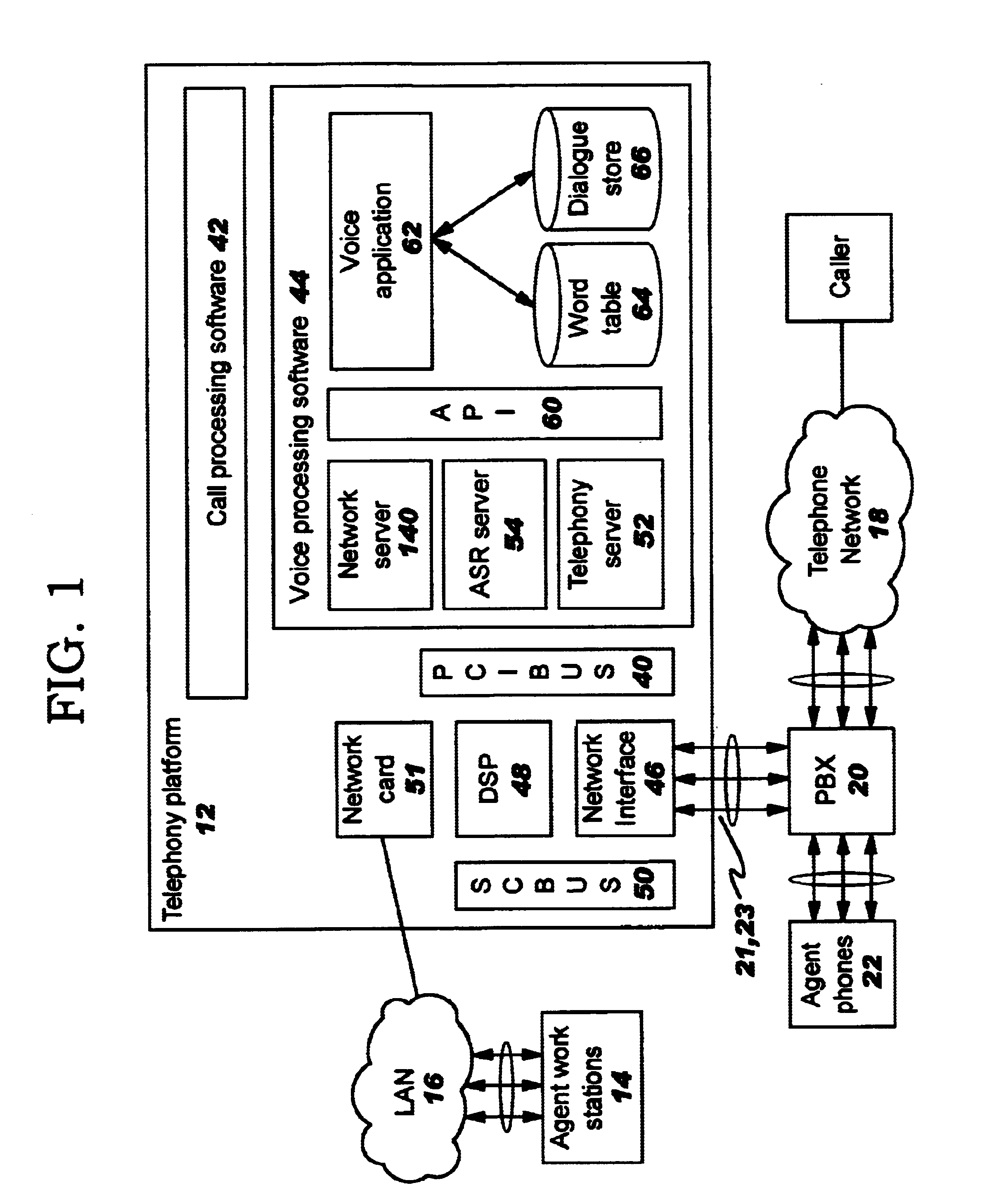
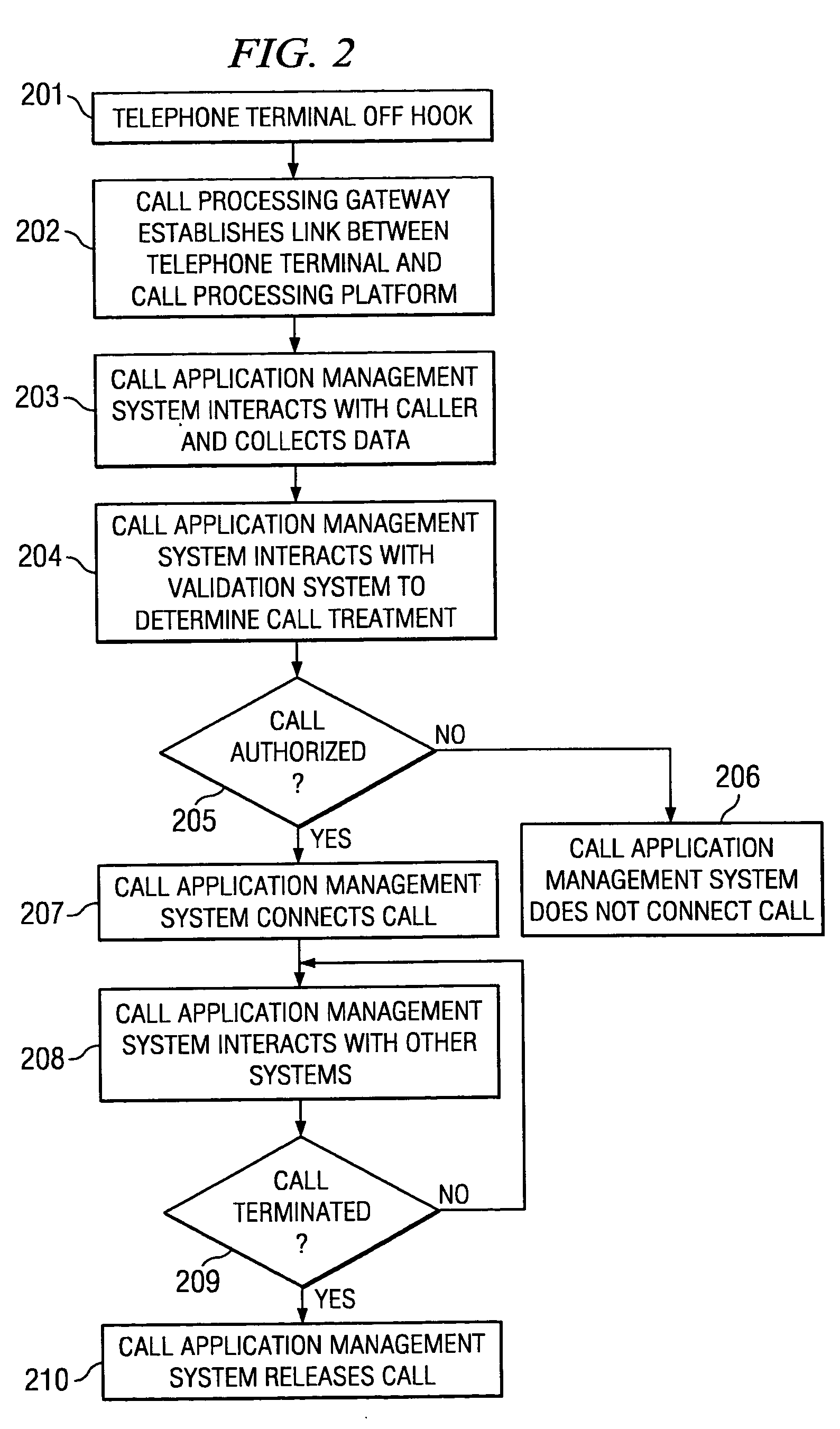
Centralized call processing
InactiveUS7899167B1Reduce data communicationLower connection costsSpecial service provision for substationMultiplex system selection arrangementsData sharingCall routing
Disclosed are systems and methods which provide a centralized architecture for call processing. Embodiments utilize voice over Internet protocols (VoIP) to carry calls from a location at which calling services are provided to a centralized call processing platform providing call processing functionality, such as calling party identification, call validation, call routing, and connection to the public switched telephone network (PSTN). Call processing gateways may be utilized to provide plain old telephone service (POTS) analog line interfaces for use with a plurality of telephone sets disposed for use at a location and at least one wide area network (WAN) interface for providing high speed data communication to a centralized call processing platform. PSTN interfacing by a call processing platform may be provided as a VoIP connection to the PSTN and / or as POTS trunking. Call processing platforms may provide for data sharing, aggregation, and / or analysis across multiple facilities served.
Owner:SECURUS TECH LLC
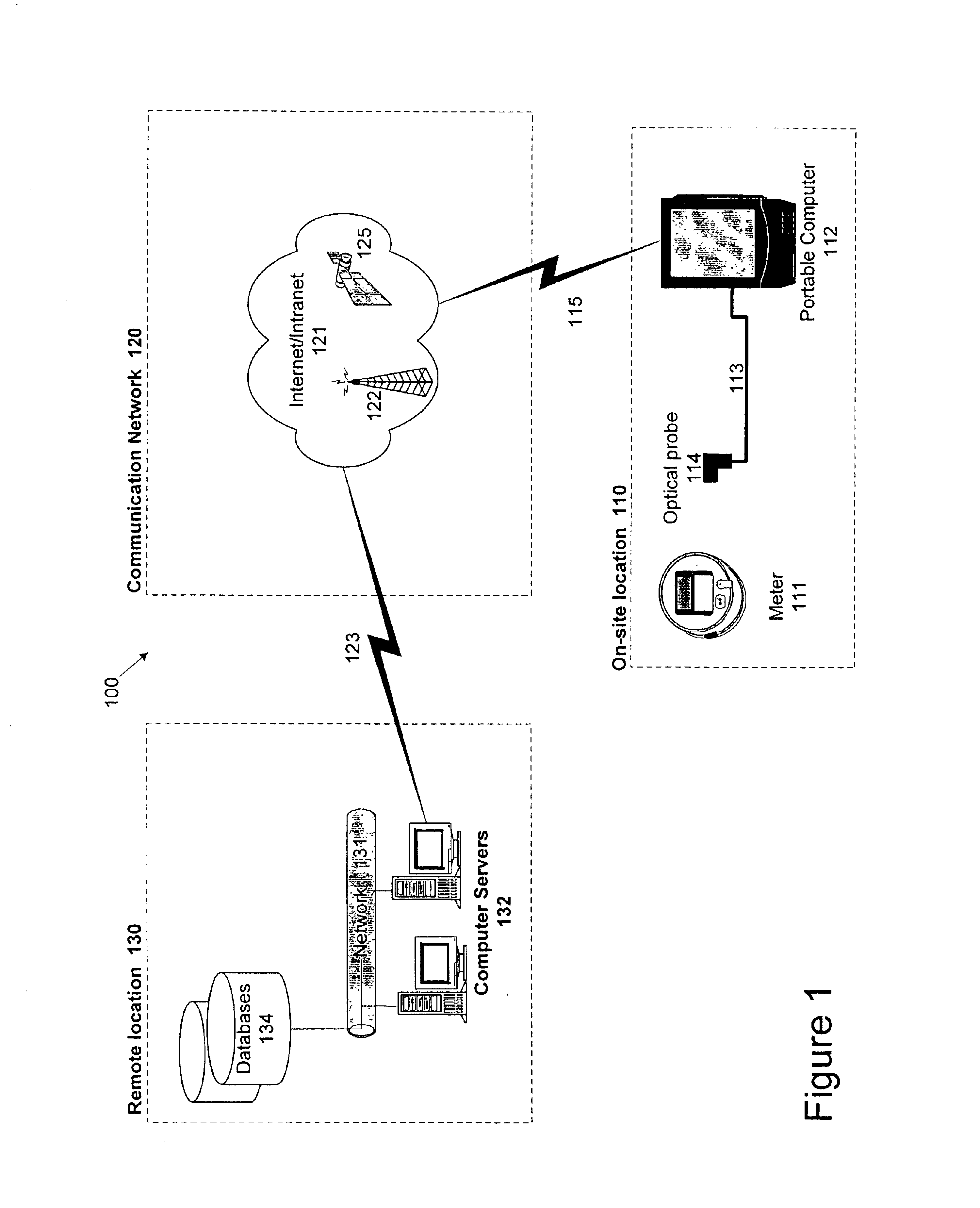
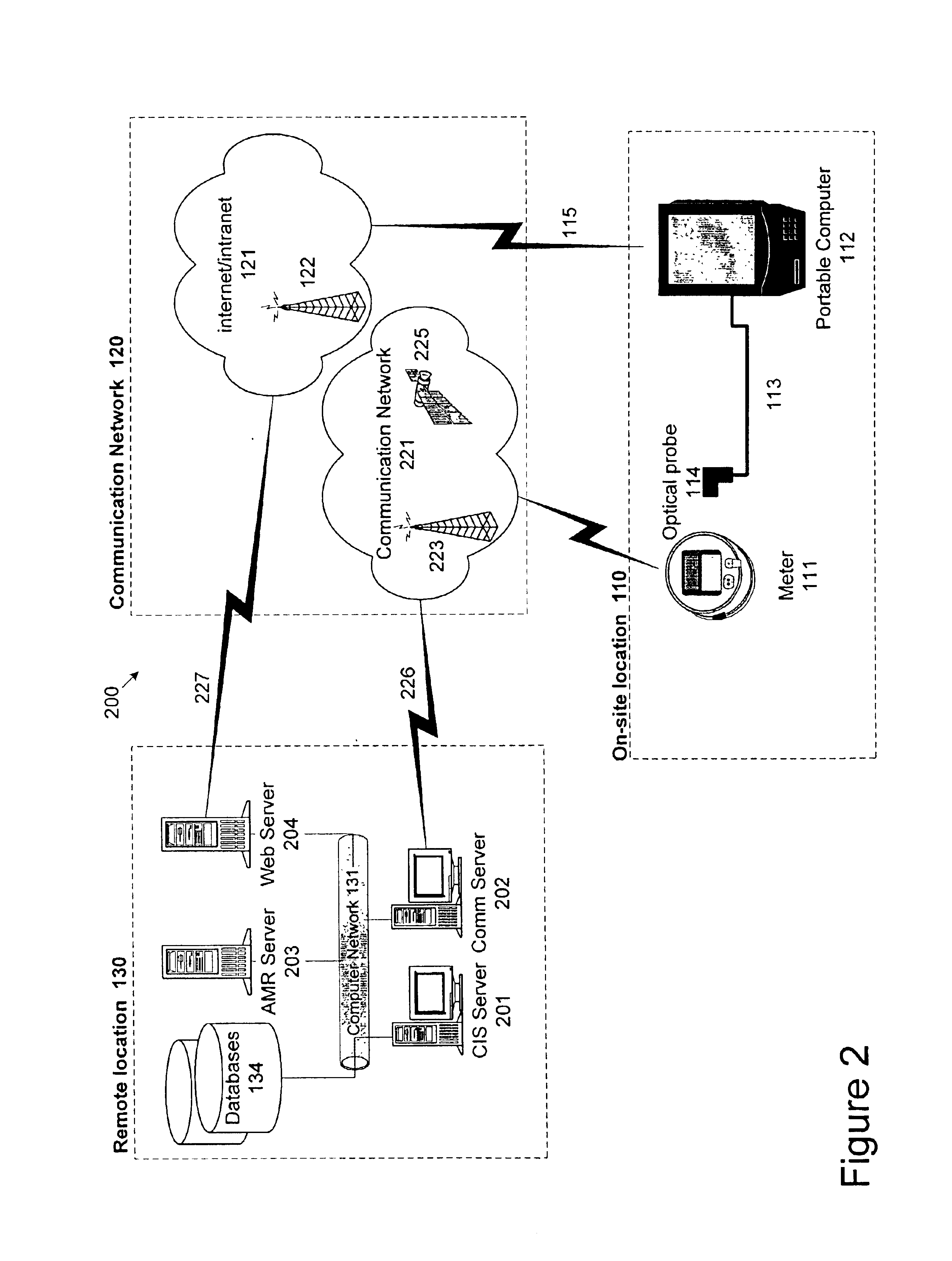
Automated on-site meter registration confirmation using a portable, wireless computing device
InactiveUS6867707B1Electric signal transmission systemsLevel controlWireless computingComputer science
The invention is directed to a method and system for verifying an installation of an meter, for example, an electric power meter. The inventive method includes identifying the electric power meter to a central computer using a mobile computing device. The electric power meter receives computer-executable instructions from the central computer via the mobile computing device, and transmits meter information (e.g., power consumption readings, meter identification information, and meter location) to the central computer. The meter information received from the central computer is compared with meter information available at the electric power meter. The comparison may be accomplished visually by reading the meter and comparing the readings with the information received on the mobile computing device. Also, the comparison may be accomplished automatically by the mobile computing device based on the information it receives from the central computer and the information it receives from the electric power meter.
Owner:ELSTER ELECTRICTY LLC
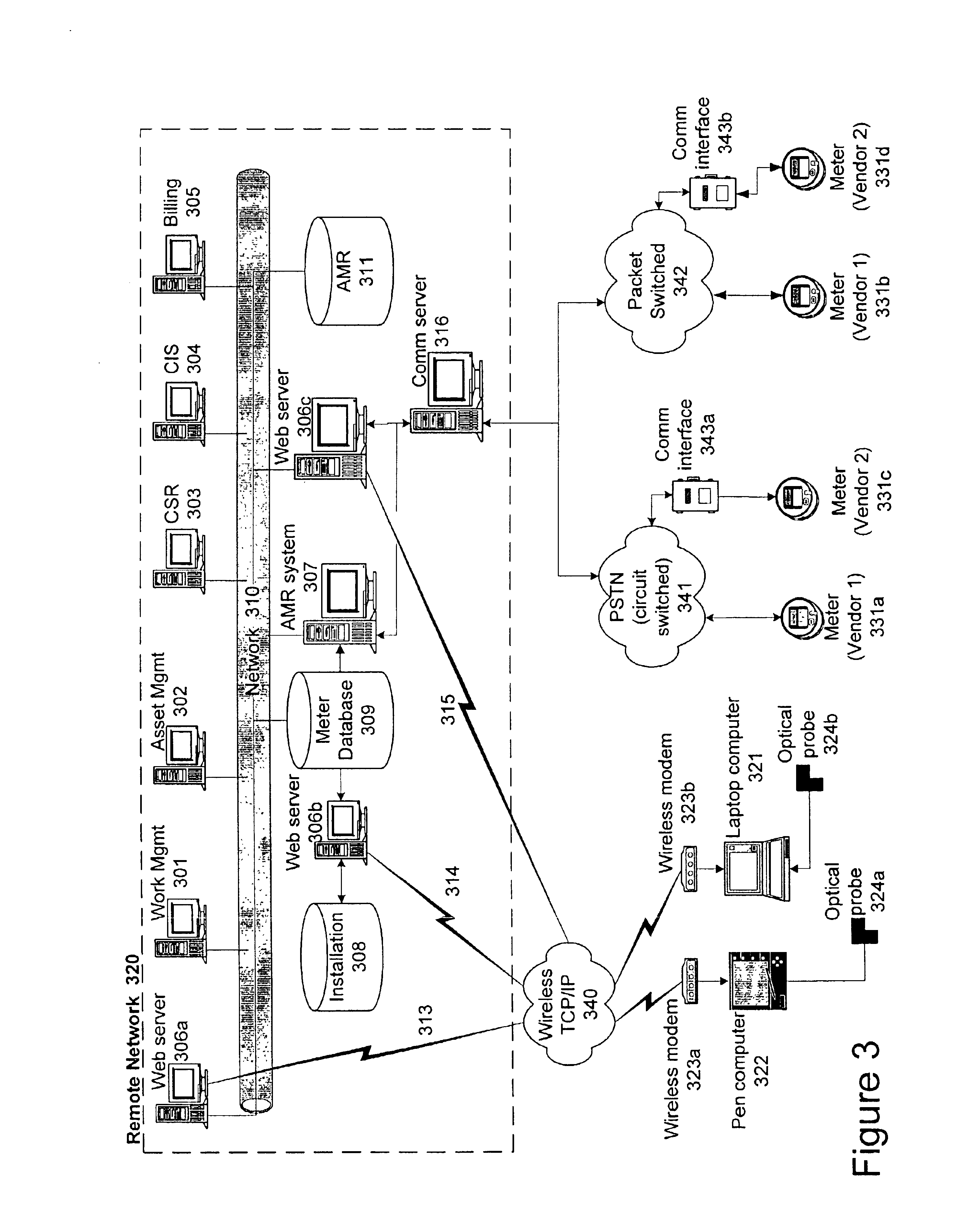
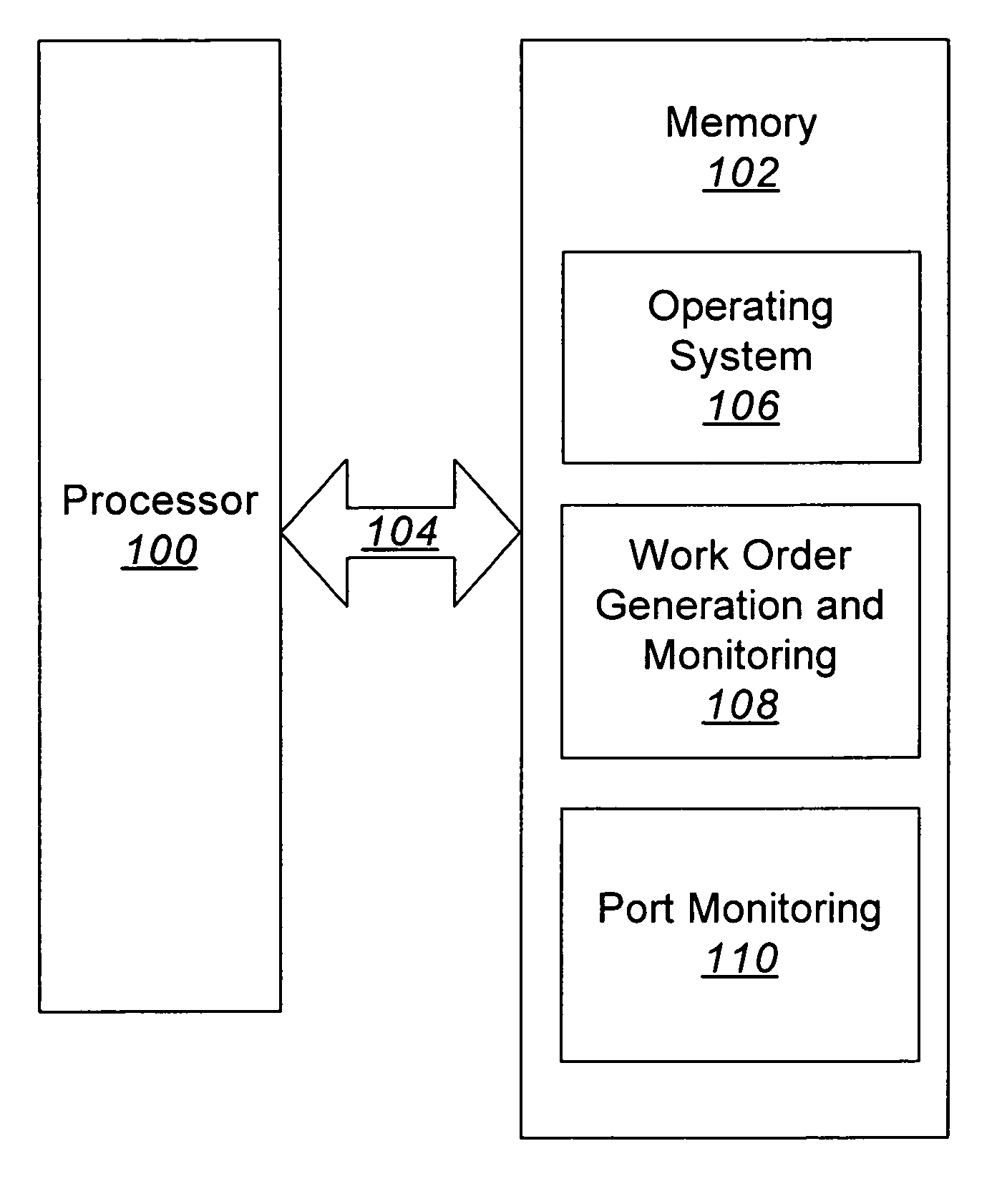
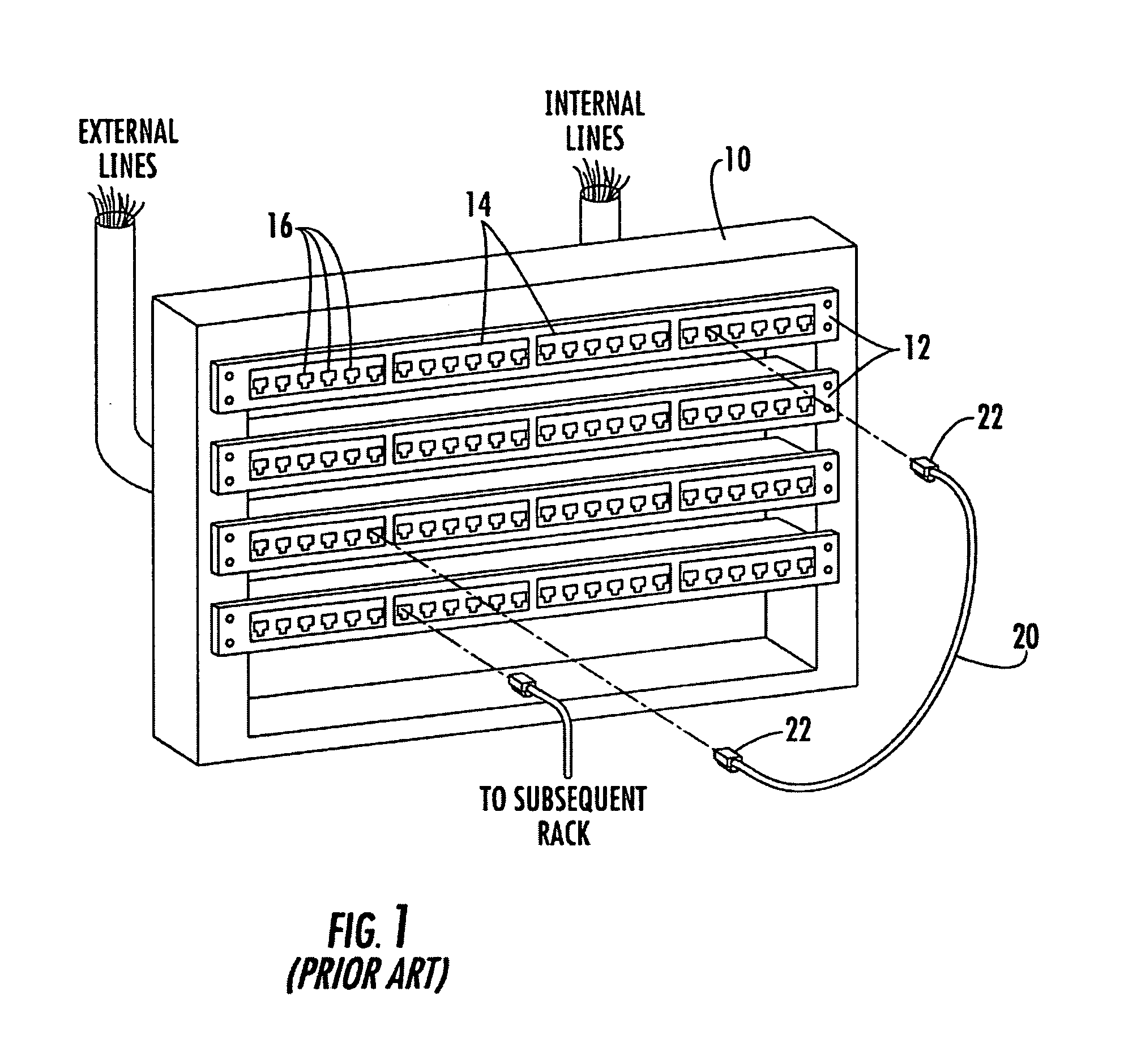
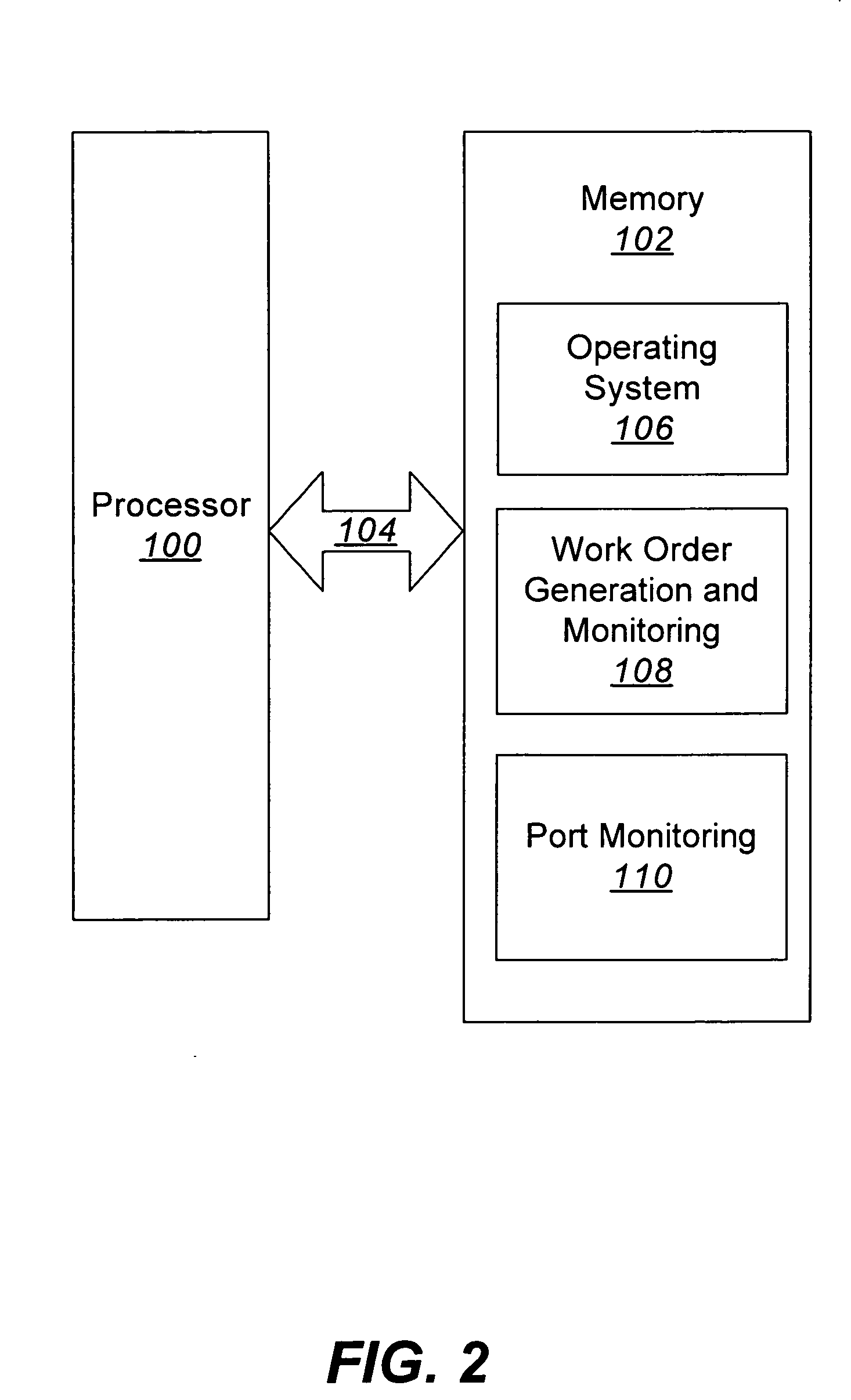
Methods, systems and computer program products for connecting and monitoring network equipment in a telecommunications system
InactiveUS20060160395A1Coupling device detailsSupervisory/monitoring/testing arrangementsPatch panelTime segment
Methods, systems and computer program products for interconnecting network equipment with a telecommunications system includes identifying a patch panel connector port to be connected to a network equipment port, generating a work order for connecting the identified patch panel connector port to the network equipment port via a patch cord, monitoring the identified patch panel connector port to detect whether a patch cord connector has been inserted therein within a predetermined period of time, and monitoring the network equipment port for communications activity within a predetermined period of time. If a patch cord connector has not been inserted within the identified patch panel connector port within the predetermined period of time and / or if communications activity has not been detected at the network equipment port within the predetermined period of time, a technician is notified. Network equipment ports and patch panel ports are monitored for authorized and unauthorized connections.
Owner:COMMSCOPE INC
Two-way voice and voice over IP receivers for alarm systems
ActiveUS7734020B2Reduce errorsShort response timeInterconnection arrangementsSupervisory/monitoring/testing arrangementsVoice communicationVoice over IP
Security systems typically communicate with alarm monitoring centers using a telephone connection. The present invention offers a system and technique for monitoring a security system connected using a Voice-over-IP connection, in real time, and alerting the owner of the security system, or the alarm-monitoring center, when the connection is broken. This alert can be used, for example, to issue a telephone call to the police, informing them of the breach of line integrity and possible compromise of the premise. In addition, the present invention allows for one-way or two-way voice communication between the alarm panel and an alarm operator and / or a 3rd party. Such voice communication helps the alarm operator and / or 3rd party to determine whether an alarm is a real alarm or a possible false alarm.
Owner:SIERRA WIRELESS AMERICA
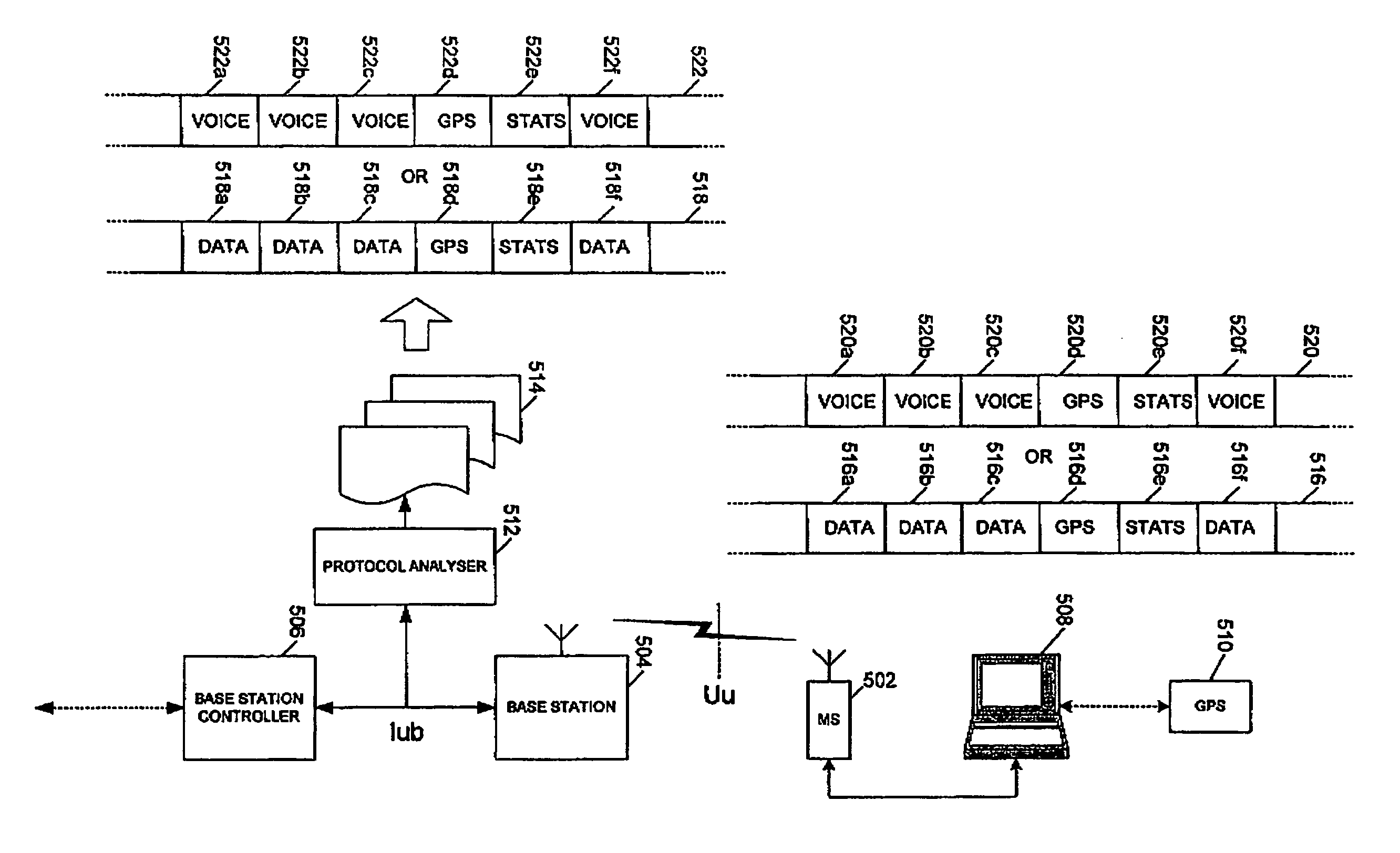
Network testing and monitoring systems
InactiveUS7224968B2Simplify the data collection processNetwork topologiesSupervisory/monitoring/testing arrangementsData streamThird generation
A method of testing a digital mobile phone network such as a GPRS or 3G network comprises either using real traffic or creating test traffic using test mobile phone coupled to a computer, and using the computer to measure a parameter associated with the network's response to the traffic. The measurements made by the computer are themselves sent as traffic to create one or more data streams within the mobile phone network comprising the traffic, measurements relating to the traffic, and signalling relating to the traffic, whereby this data stream or these streams can be captured at interface points within the network and analyzed to investigate the functioning of the network dynamically as the network is exercised with the traffic. Software and test equipment for performing the method are also described.
Owner:ACTIX
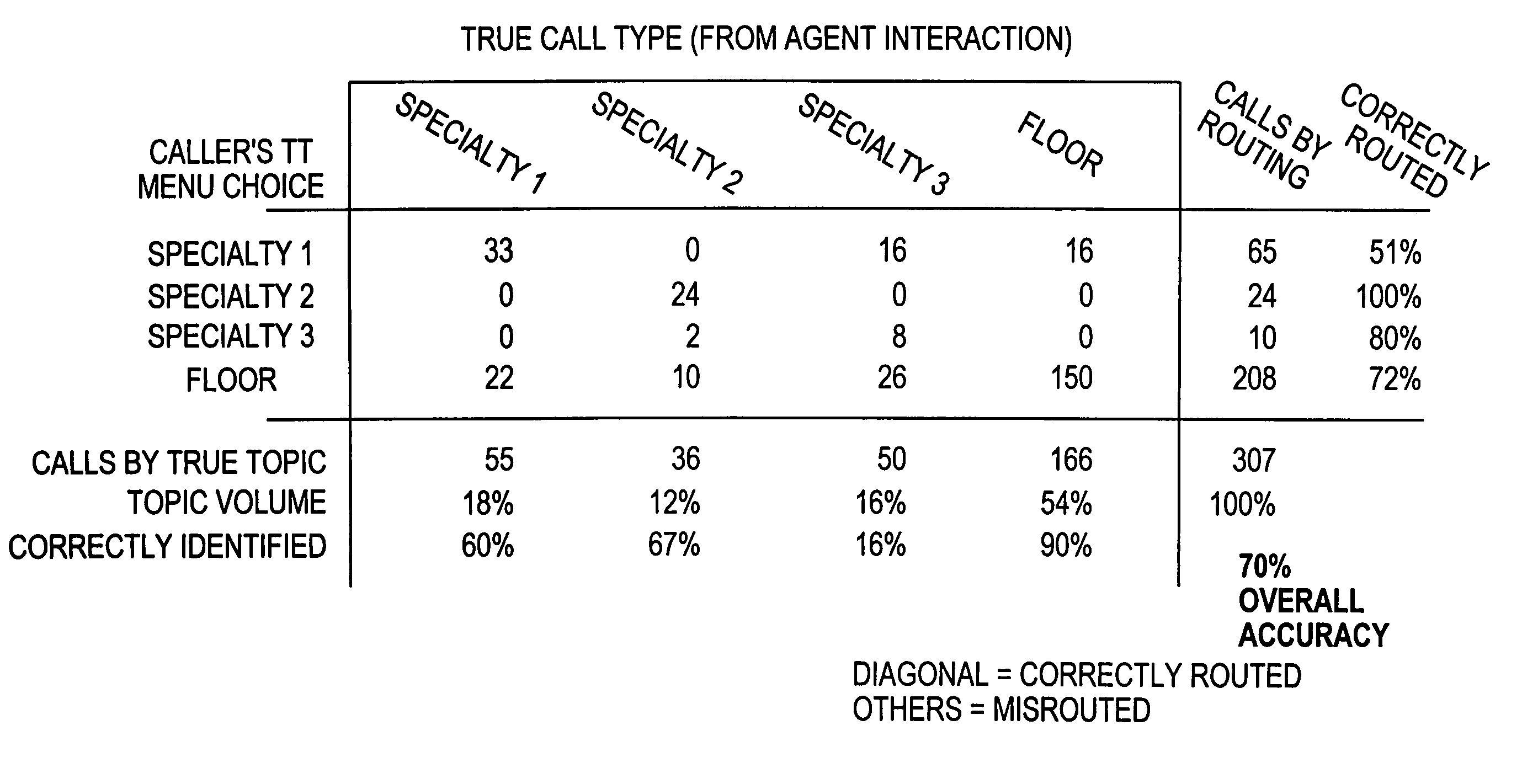
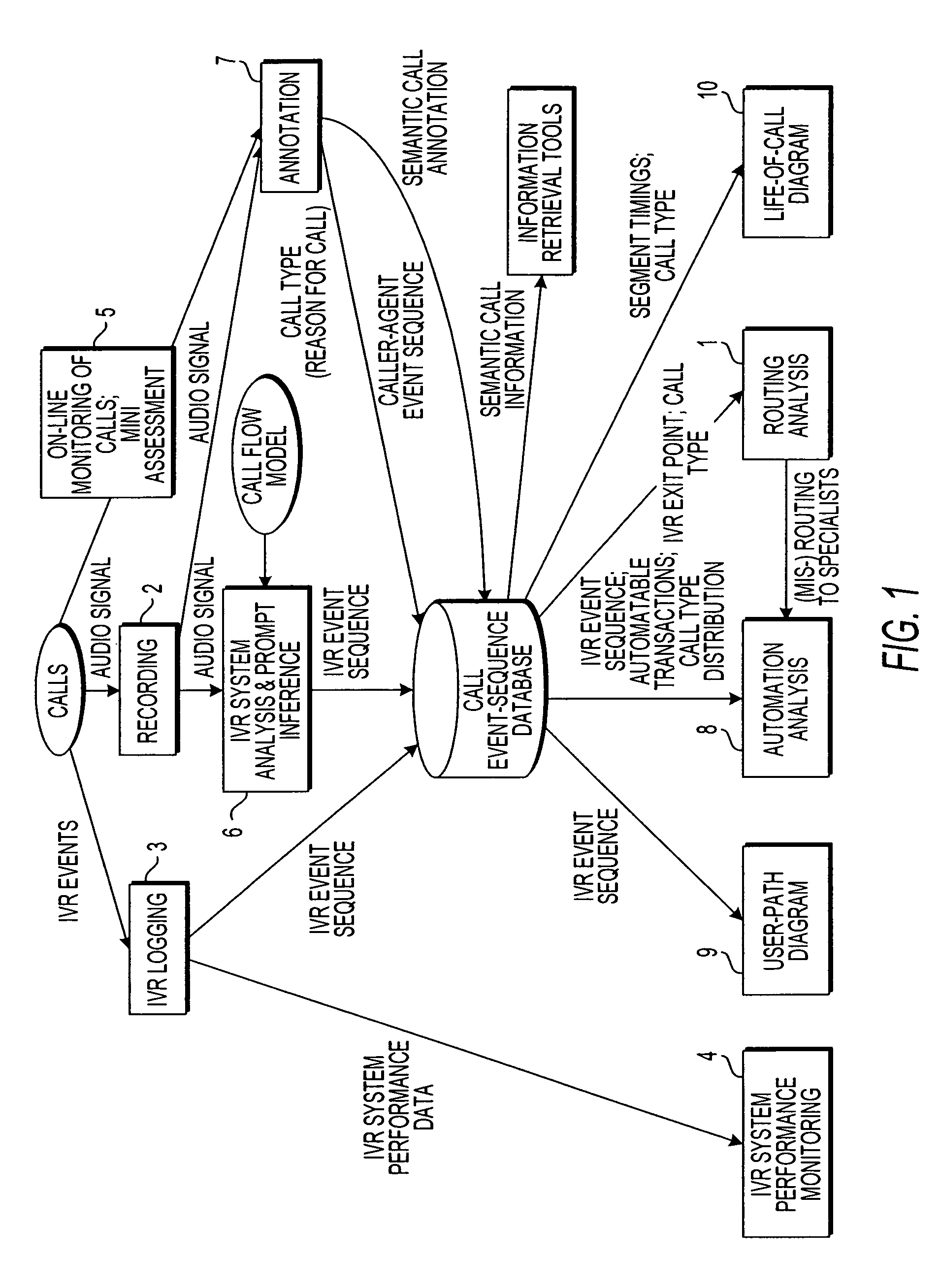
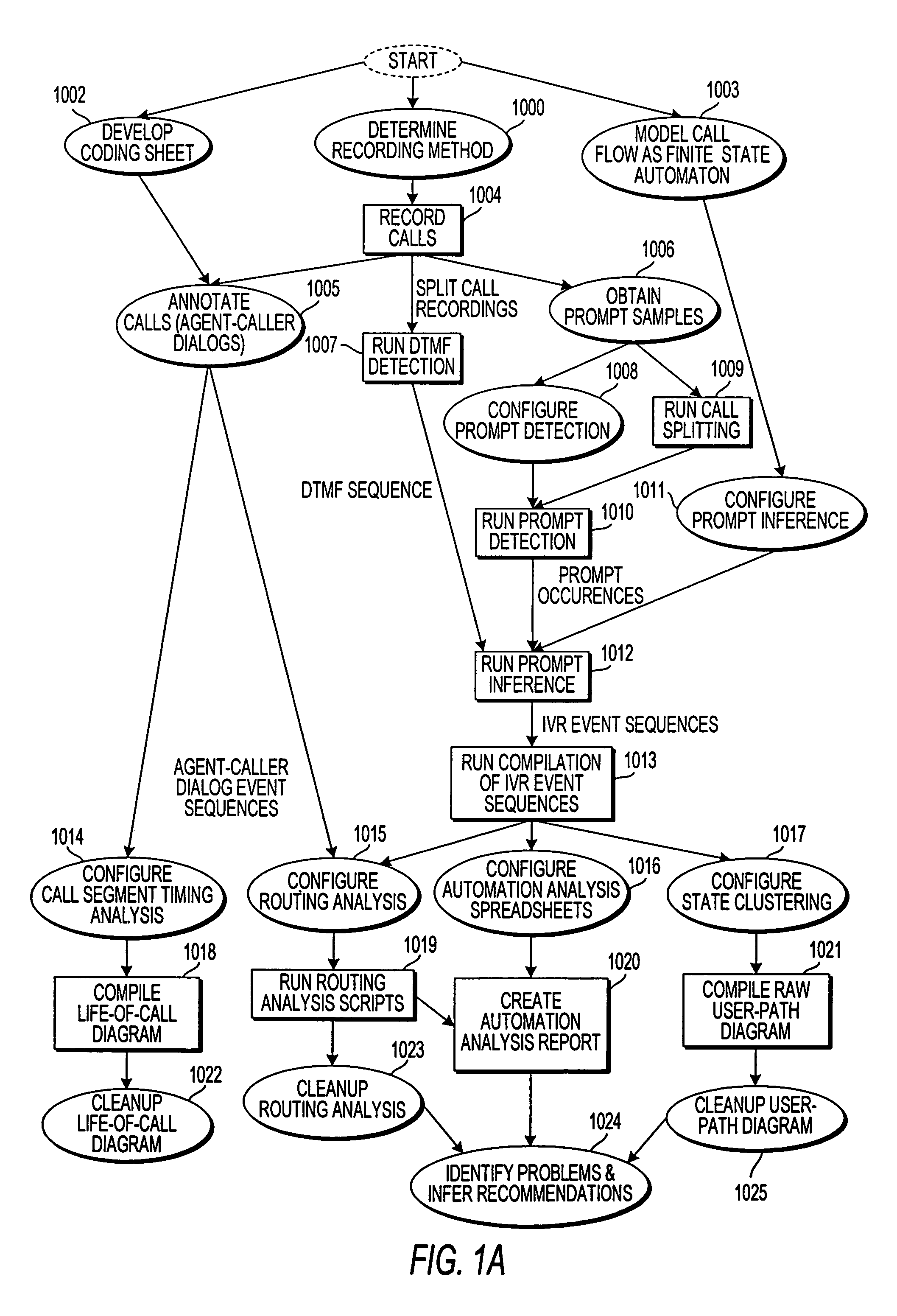
Apparatus and method for monitoring performance of an automated response system
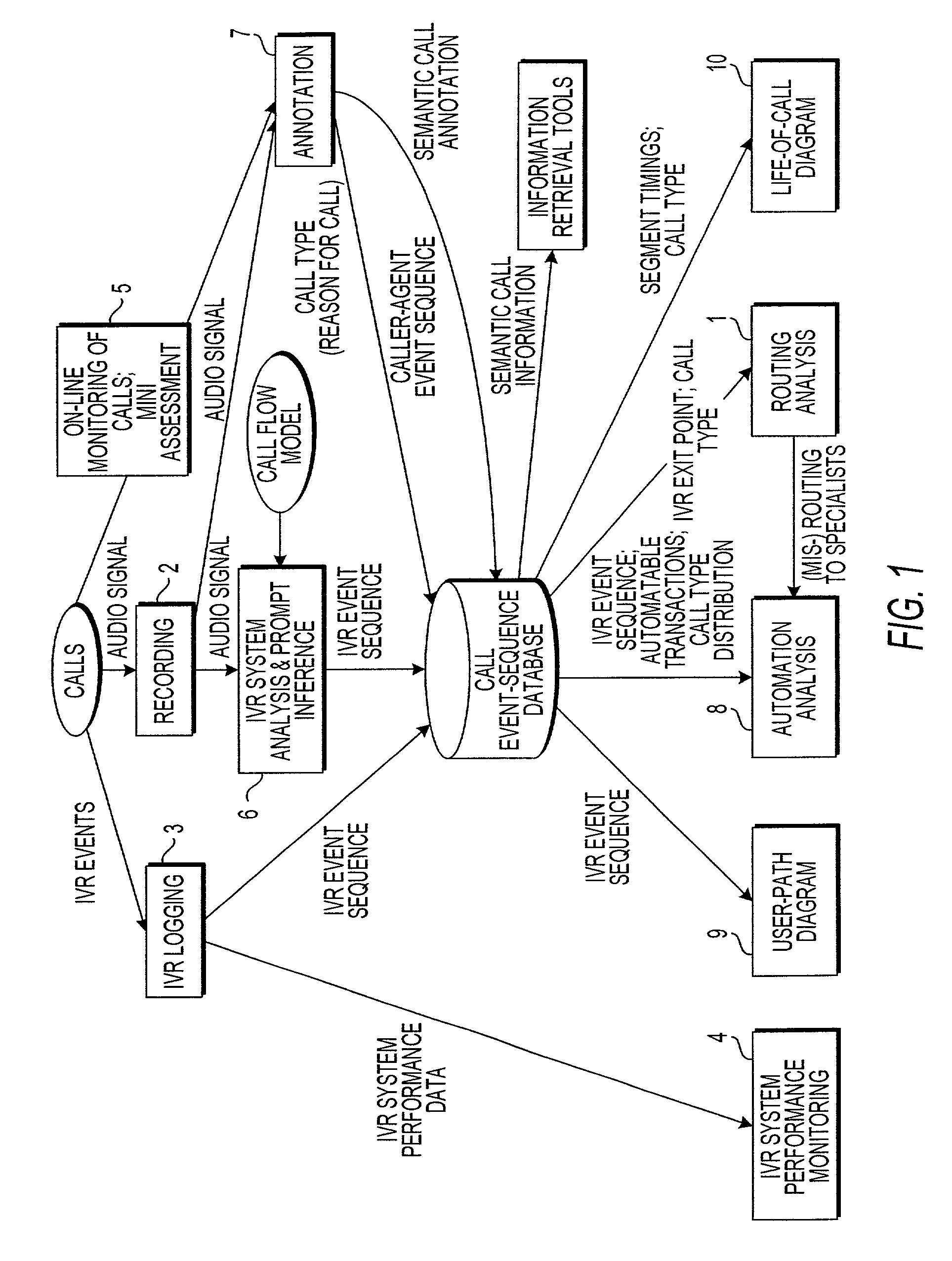
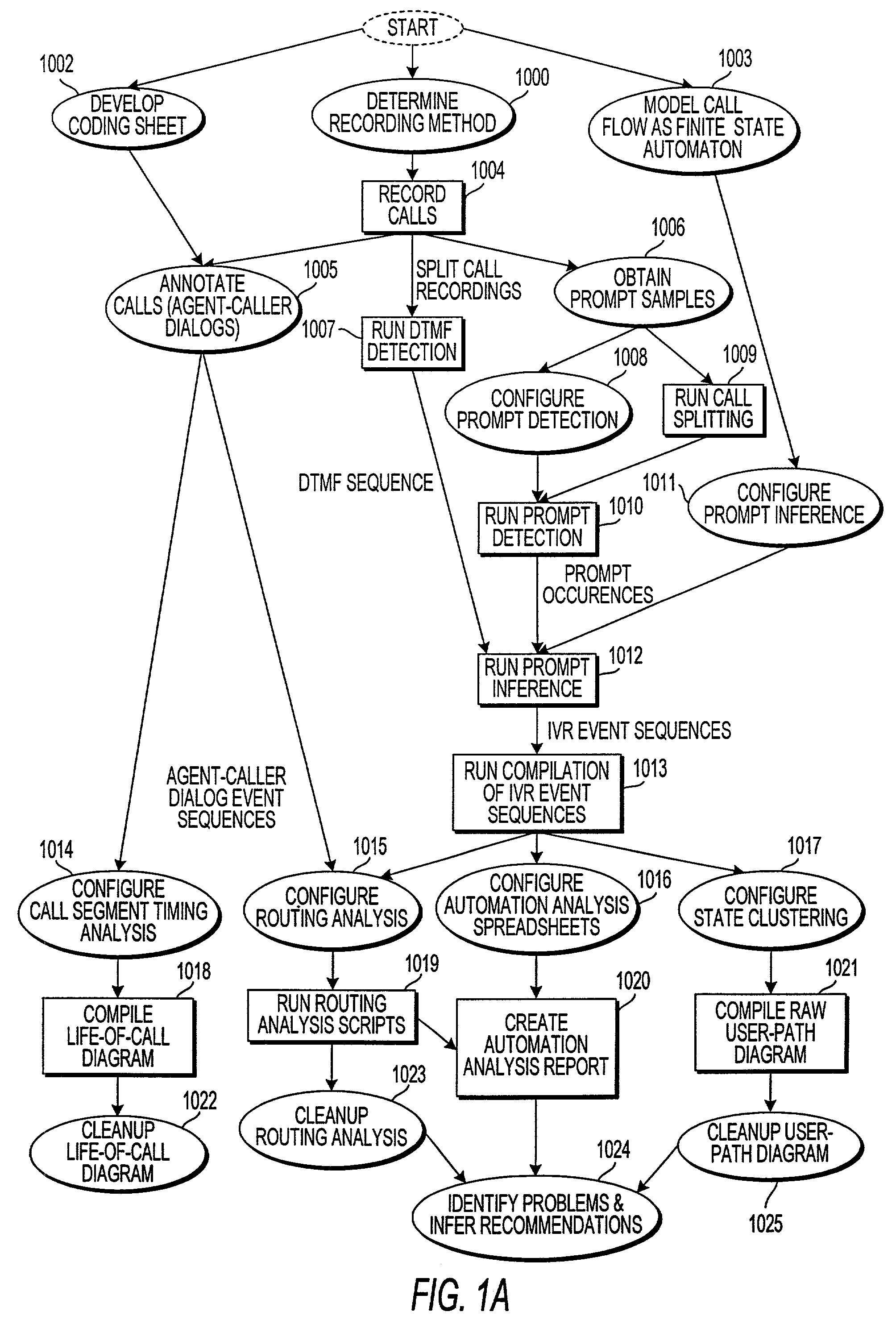
ActiveUS7003079B1Overcome deficienciesSupervisory/monitoring/testing arrangementsManual exchangesCall routingSpeech sound
An apparatus and method for monitoring the performance of an interactive voice response (IVR) system used by an automated call processing center generates logs of call activity, determines routing information from the logs, notes predetermined significant activity in agent-caller dialog portions of calls routed to an agent in the logs, and determines at least one quantity correlated to a true intention of callers. A performance model of the IVR system is generated from the logs. The logs, the routing information, the quantity correlated to the true intention of the callers, and the performance model are analyzed to determine a performance value of the IVR system, which is used to monitor the IVR system.
Owner:VERIZON PATENT & LICENSING INC +1
Portable telephone in a security network
InactiveUS7511614B2Improve reliabilityLow costSafety arrangmentsComputer controlCard readerProgram code
A security network for use in a building with an opening to be monitored for possible intrusion. The network includes an intrusion sensor monitoring the opening; an RFID transponder associated with the sensor; an RFID reader in wireless communication with the transponder; and a portable telephone handset having first keys activating conventional telephone capability and second keys activating interaction with the other security network components. The handset wirelessly communicates with the reader. The reader may take the form of a security cradle for the handset. Alternatively, the reader may take the form of a telephone console. The console has keys enabling a user to dial remote telephone numbers; circuitry adapted to receive wireless communications from the transponder; circuitry in wireless communication with the handset; circuitry in communication with an external network; and a processor executing program code enabling the handset to communicate with the external network via the telephone console.
Owner:ADT US HLDG INC
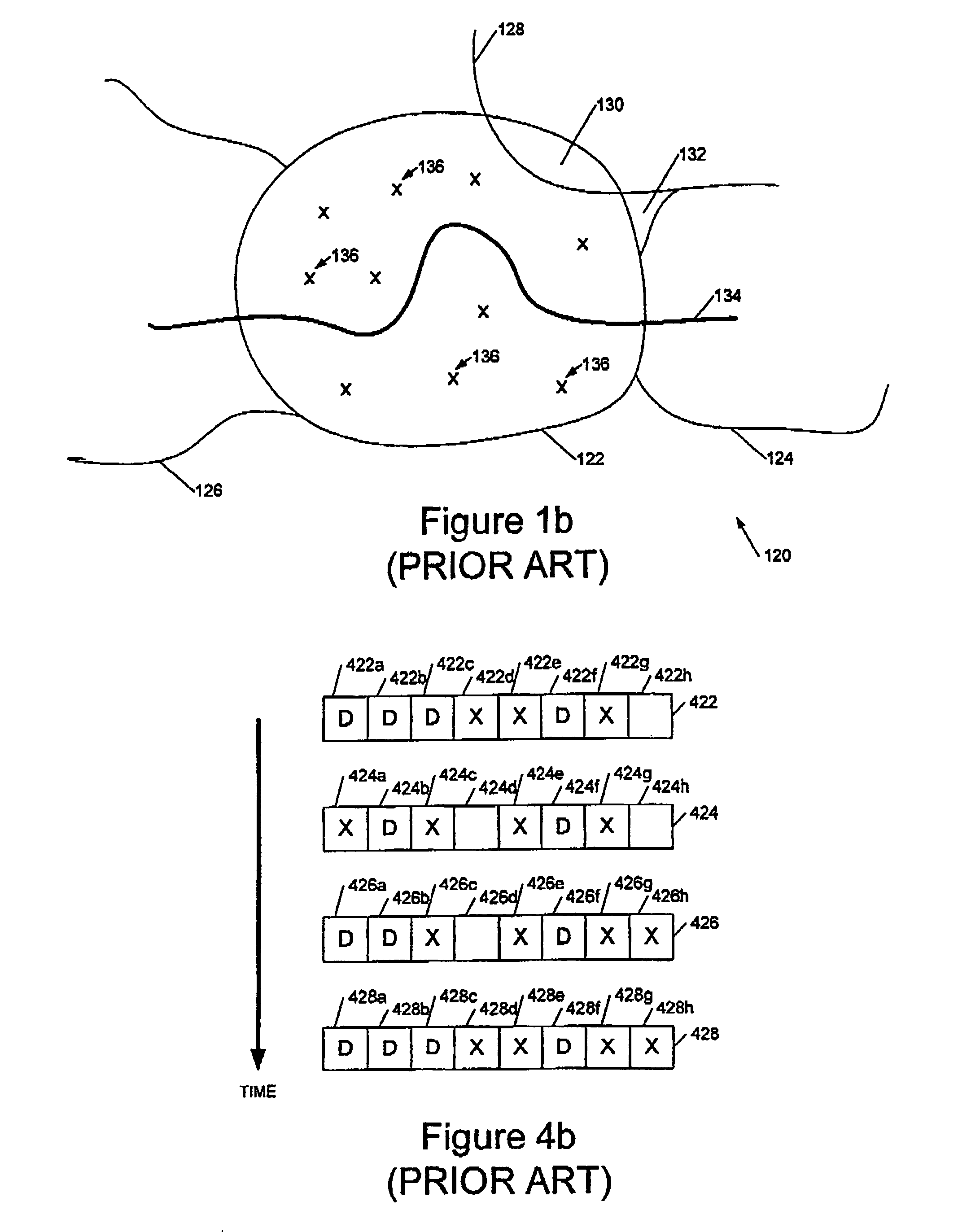
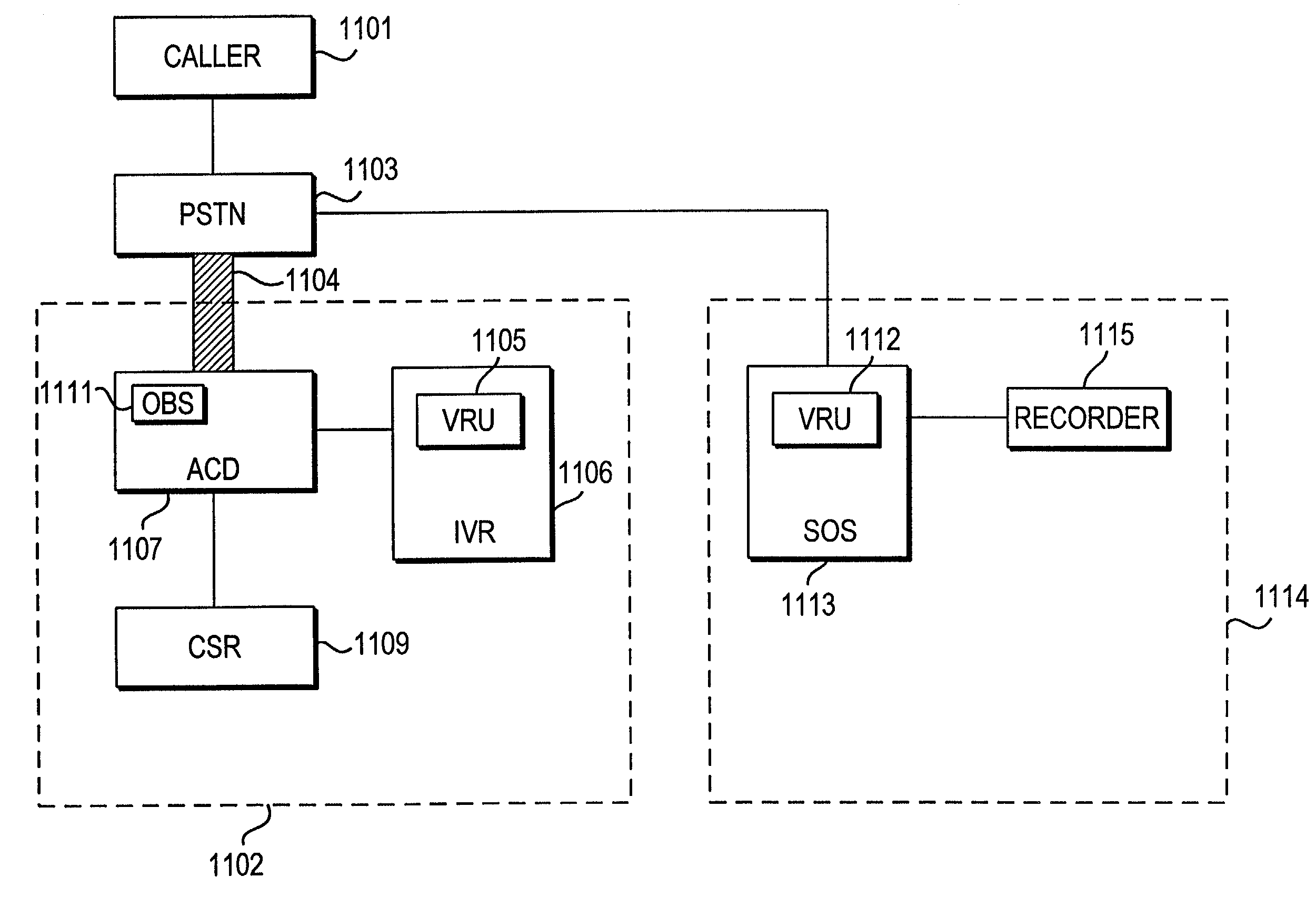
System and method for observing calls to a call center
ActiveUS6970554B1Overcome deficienciesSpecial service for subscribersSupervisory/monitoring/testing arrangementsObservation systemSpeech sound
An observation system for observation calls to a call center includes an automatic call director (ACD) unit, an interactive voice response (IVR) unit, and a recorder unit. The ACD receives incoming calls to the call center and also queues and switches the calls to various lines of the call center. The IVR unit is connected to the ACD unit and interacts with a caller via an interactive computer program in which the caller enters a response to a prompt and the response causes the interactive program to provide the caller with information or another prompt. The recorder unit records calls to the call center from beginning to end, including prompts made by the IVR unit, callers responses to the prompts, and information provided by the IVR unit to the callers.
Owner:CX360 INC +1
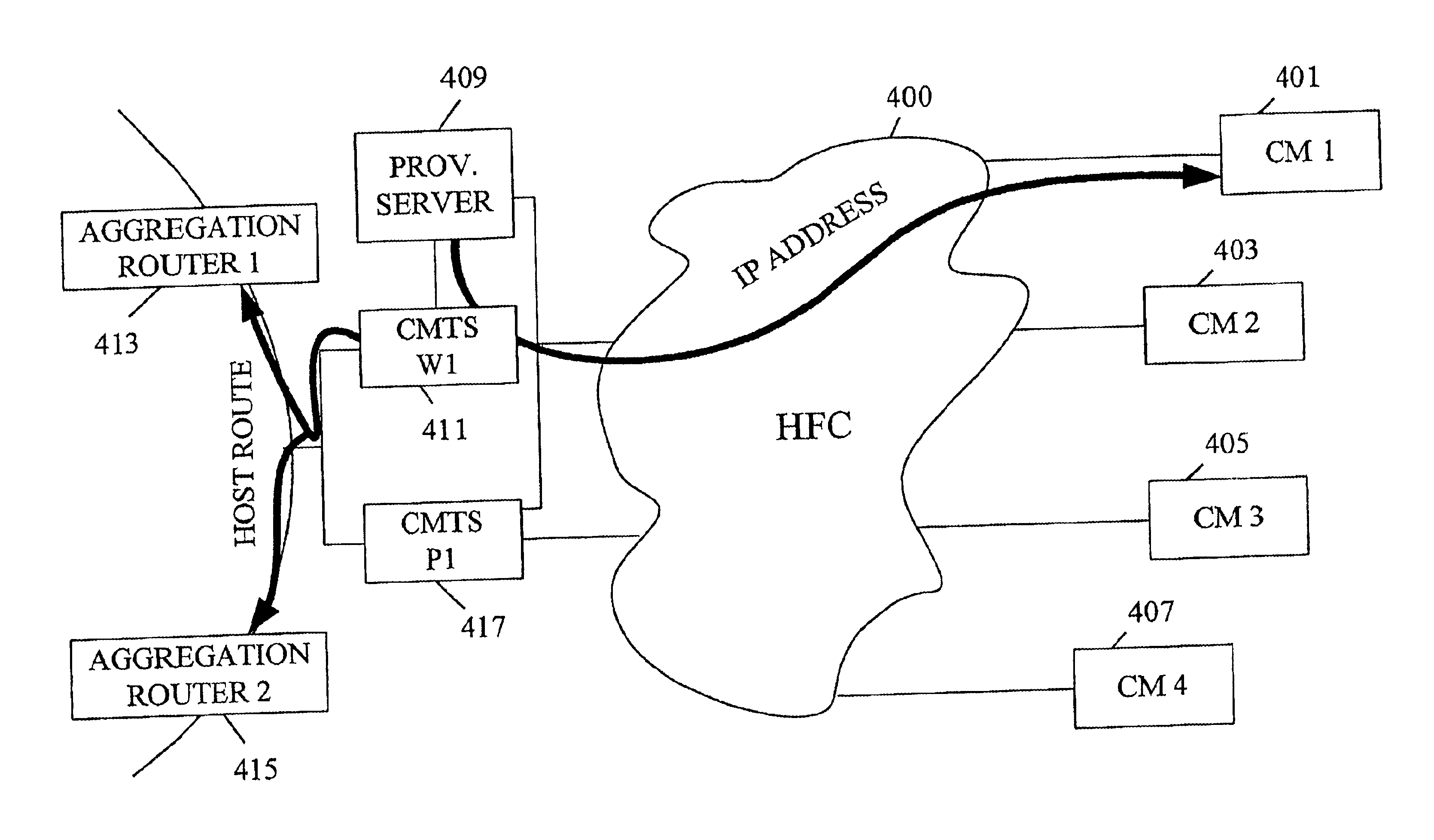
Routing protocol based redundancy design for shared-access networks
InactiveUS6839829B1Reduce delaysFew significant disruptionError preventionBroadband local area networksAccess networkModem device
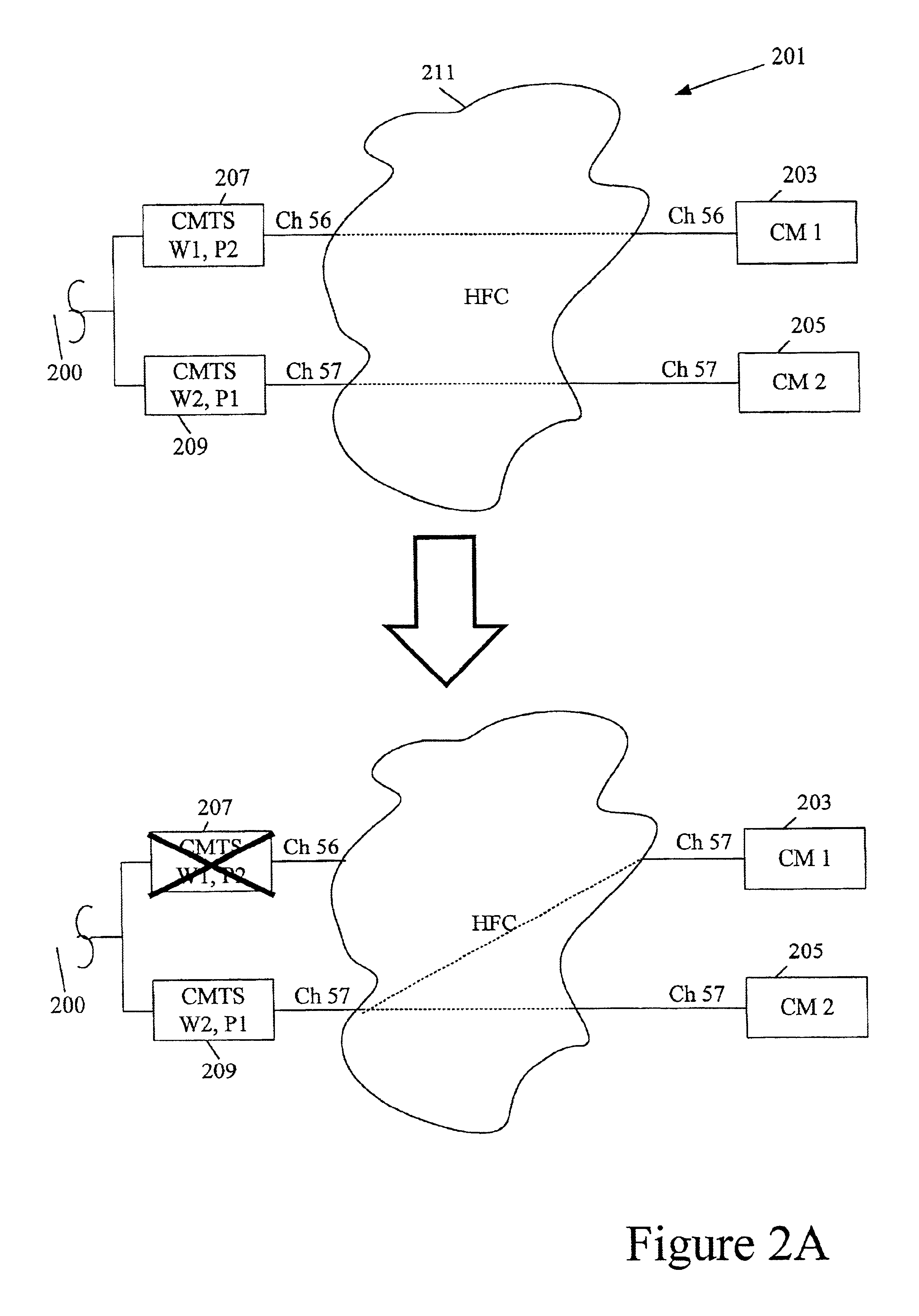
A protection CMTS is available to immediately service a cable modem should that modem's service from a working CMTS fail for any reason. To speed the service transfer (cutover) from the working CMTS to the protection CMTS, the cable modem may preregister with the protection CMTS well before the cutover becomes necessary. The cable modem's registration with both the working CMTS and the protection CMTS preferably employs a single IP address, so that the cable modem need not obtain a new IP address during cutover. While the cable modem may register with both the working CMTS and the protection CMTS, the devices are designed or configured so that only the working CMTS injects a host route for the cable modem into the appropriate routing protocol. Only after cutover to the protection CMTS does the protection CMTS inject its host route.
Owner:CISCO TECH INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com