Network-operating-system-oriented trusted virtual operating platform
An operating system and operating platform technology, applied in transmission systems, public keys for secure communications, user identity/authority verification, etc., can solve problems such as tampering and counterfeiting, replay attacks, and malicious hardware modifications
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0077] The technology of this patent needs to pay attention to the following matters during the specific implementation:
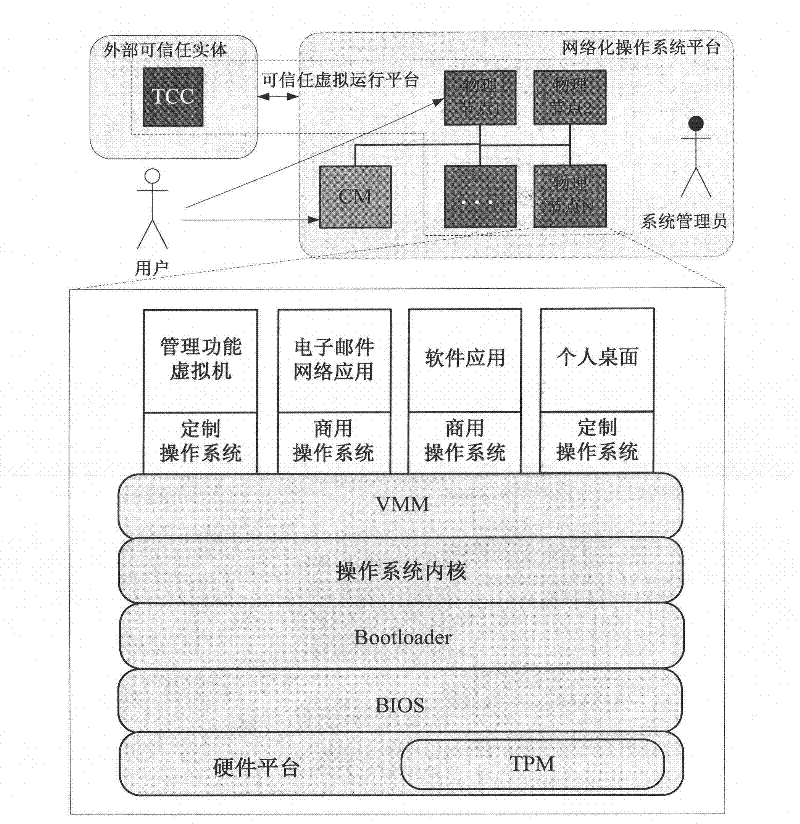
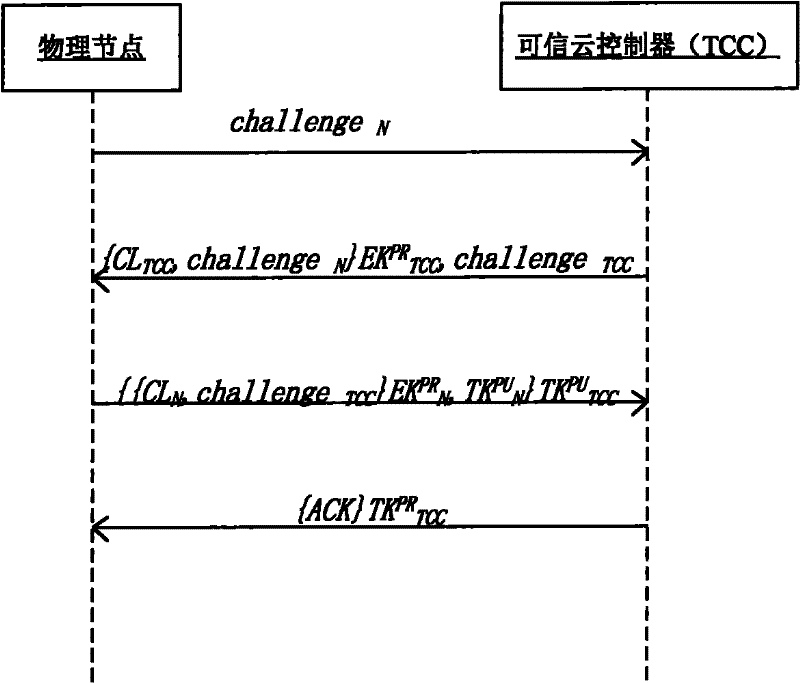
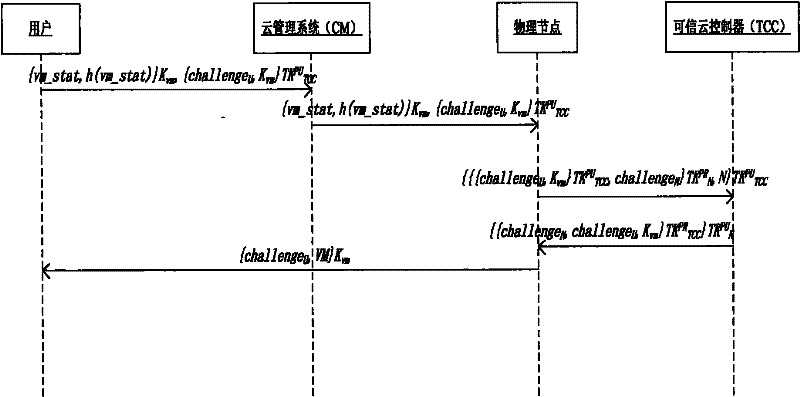
[0078] 1) An external trusted entity provides a trusted cloud manager to verify the networked operating system platform. TCC manages a directory locally, which stores the signed public key EK of the trusted physical node in the networked operating system PU N , public key TK PU N and the configuration list CL N In addition, it is also responsible for publishing its own signature public key EK through a secure channel. PU TCC , public key TK PU TCCand the expected TCC configuration list CL TCC .
[0079] 2) This patent also assumes that the following conditions are established:
[0080] a) The trustworthiness of external trusted entities does not need to be verified;
[0081] b) TCC's signed public key, public key and expected configuration list, physical node's signed public key and expected configuration list are published before the system run...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com