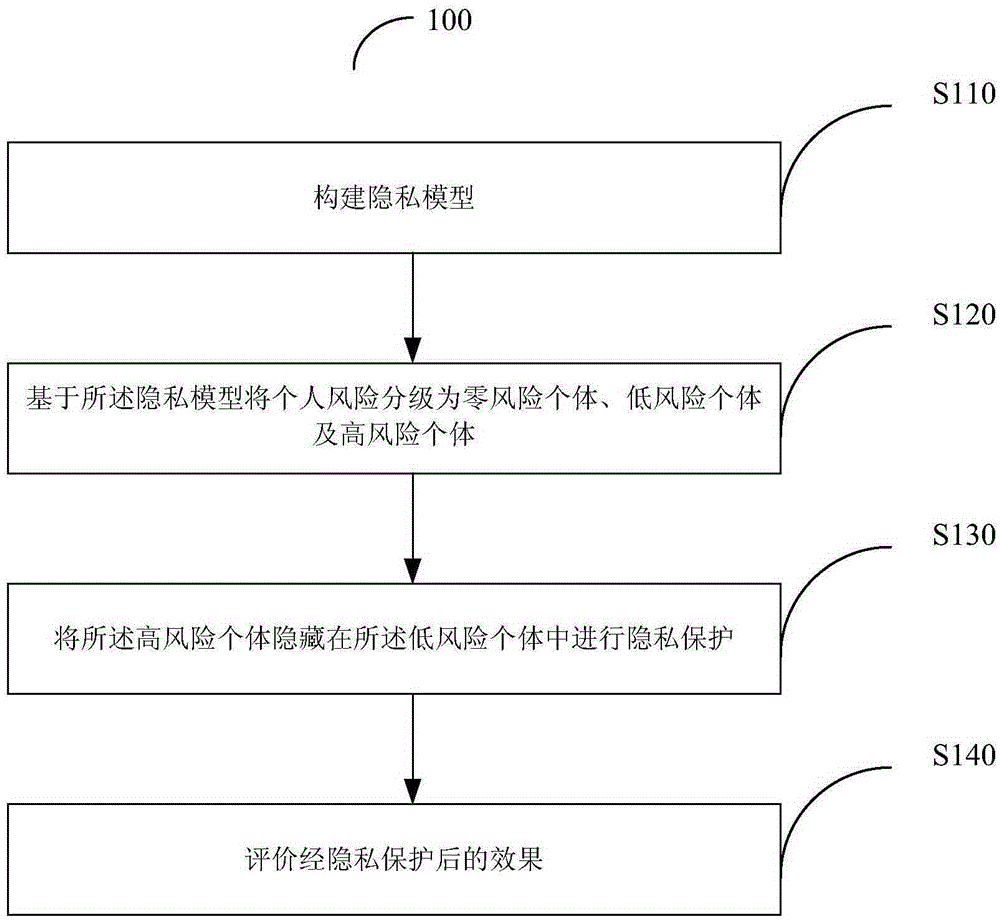
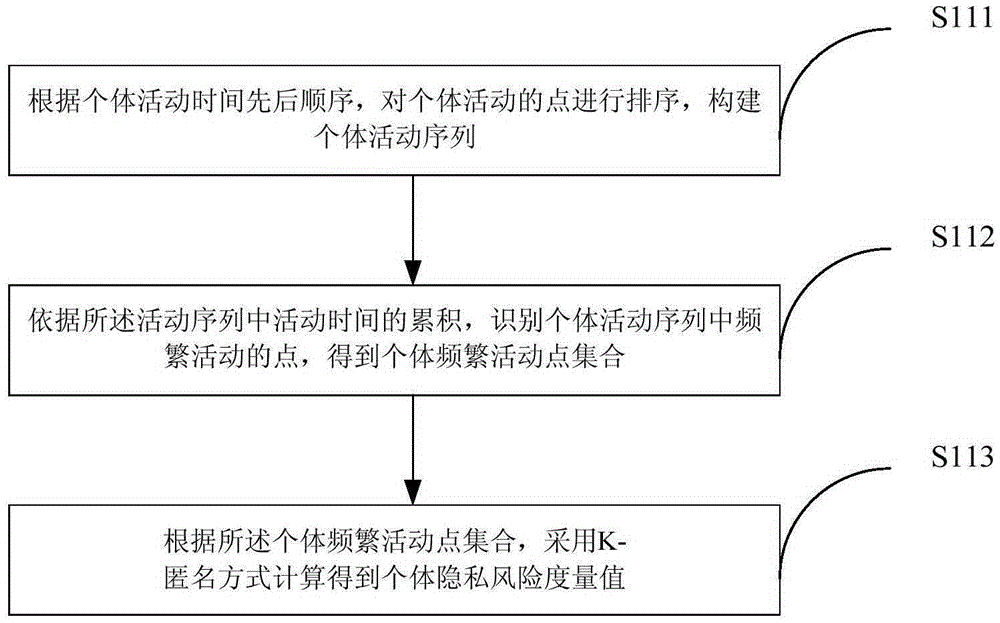
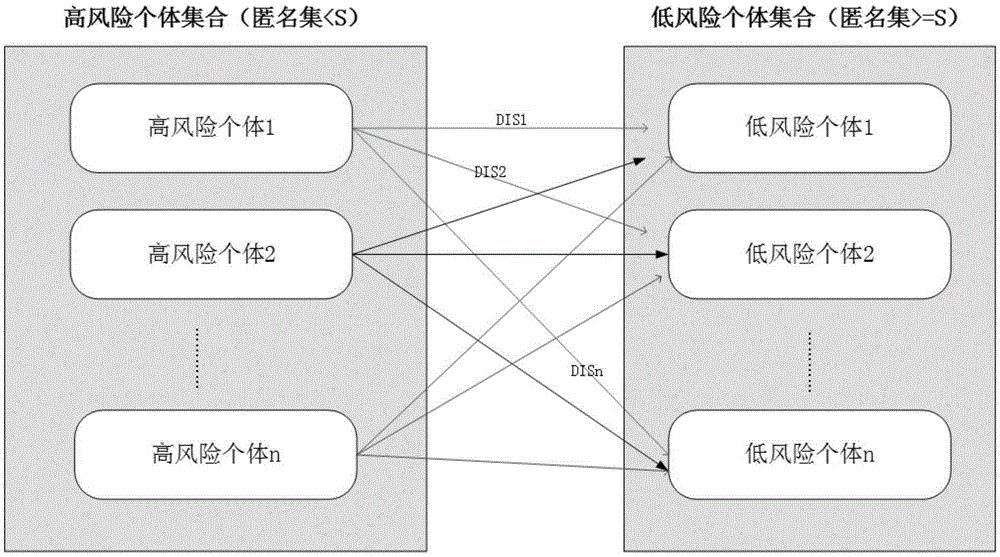
Privacy protection method and system based on high-risk frequent active point replacement policy
A privacy protection and replacement strategy technology, applied in the field of data security, can solve problems such as high computational complexity, difficulty in coping with large amounts of spatial data, resource and time consumption, and achieve low computational complexity and clear protection purposes
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
[0078] This method selects Shenzhen as the research area, and uses the mobile phone call data (CDR) of the research area in 2011 as the research data source. Adopt the method of the present invention to process data.
[0079] Table 1 Partial call records of mobile phone users whose user anonymous identification is "0000****50"
[0080] Anonymous identification of mobile phone users
The time when events such as making / receiving calls occurred
dimension coordinates
longitude coordinates
area code
0000****50
2011 / 5 / 1 4:39
22.550833
114.125833
0
0755
0000****50
2011 / 5 / 1 5:45
22.542534
114.11719
0
0755
0000****50
2011 / 5 / 1 6:03
22.542534
114.11719
1
0755
0000****50
2011 / 5 / 1 9:42
22.542534
114.11719
1
0755
0000****50
2011 / 5 / 1 10:27
22.542534
114.11719
0
0755
[0081] 0000****50
2011 / 5 / 1 15:38...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com