Trusted traceability method and system, and storage medium
A blockchain and credible technology, applied in the field of H04L digital information transmission, can solve problems such as inability to effectively open, source data leakage, leakage, etc., to achieve the quality and efficiency of defense, strengthen data security, and break data islands Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
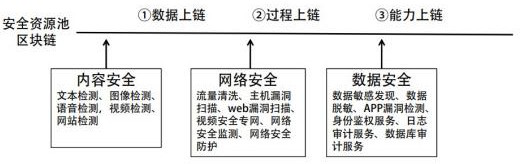
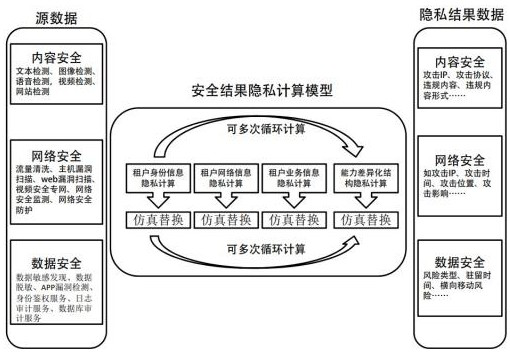
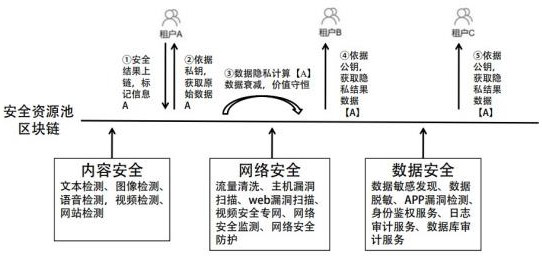
[0039] Based on the issues of security information protection mentioned in the above background, the present invention is based on the block chain, and simultaneously builds a security capability resource pool and a security information chain, that is, using block The process and corresponding data are traceable, all data are kept in the security capacity resource pool in the local area network, the privacy calculation is performed on the authorized data, the data is desensitized, and the diversity of source data is enhanced, so that a single source data can be obtained from one point Protection, upgrade to line protection, further increase authorized source data, and simultaneously upgrade the capability of the security information chain, so that the source data in the security capability resource pool is further upgraded from line protection to surface protection, thereby further realizing information sharing in the security capability resource pool , making the data in the s...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com