Patents
Literature
90 results about "Past history" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
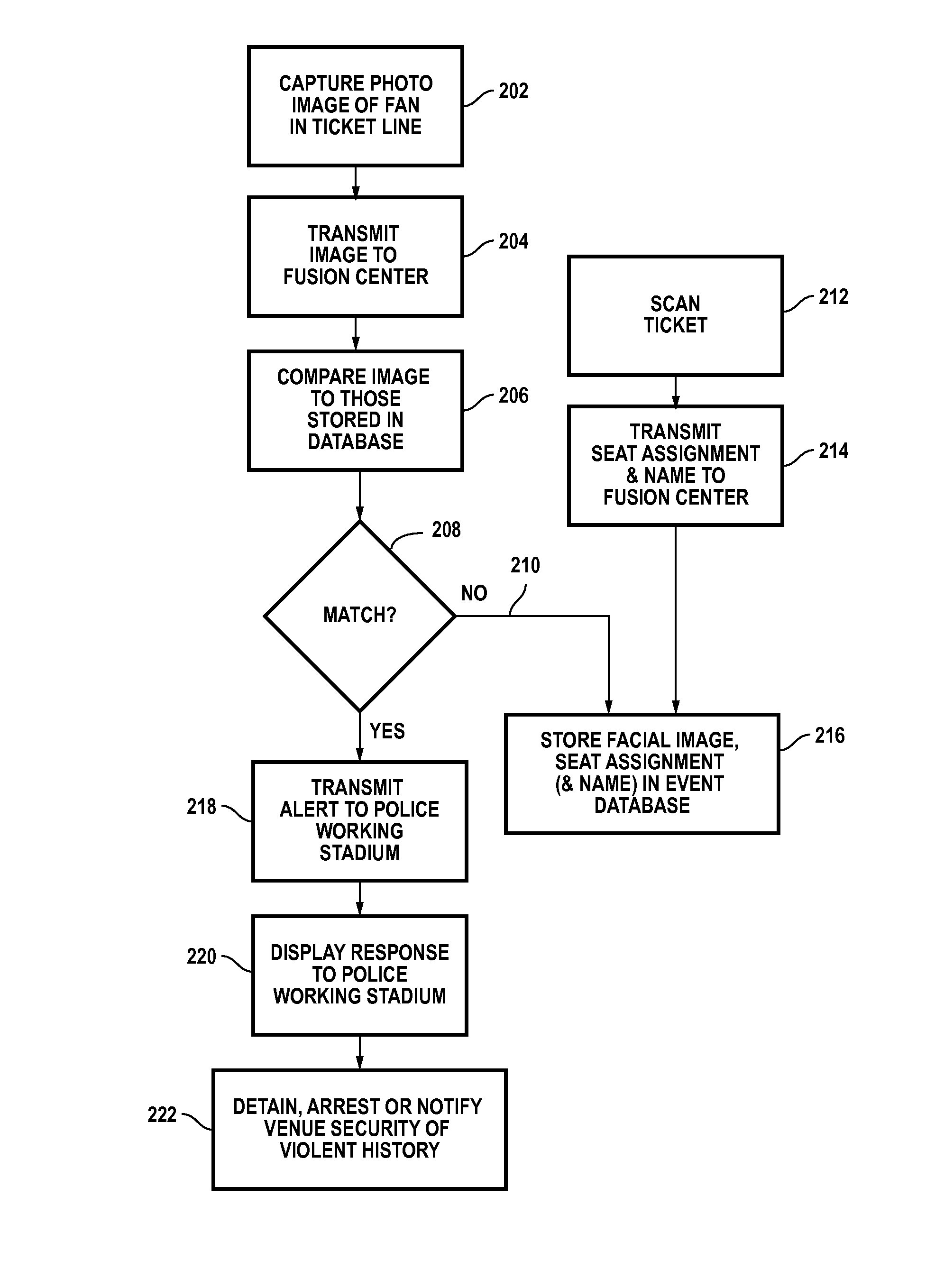
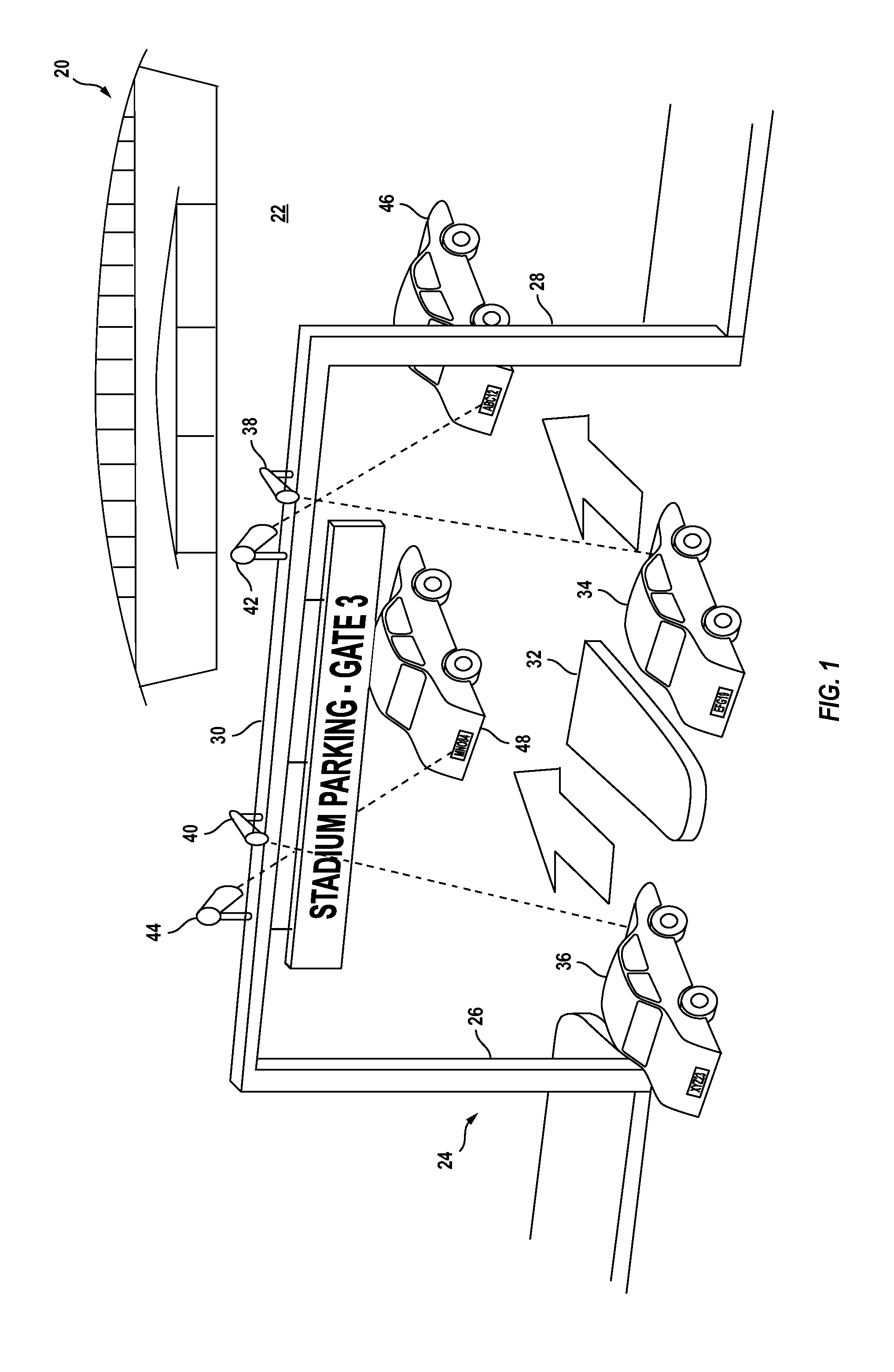
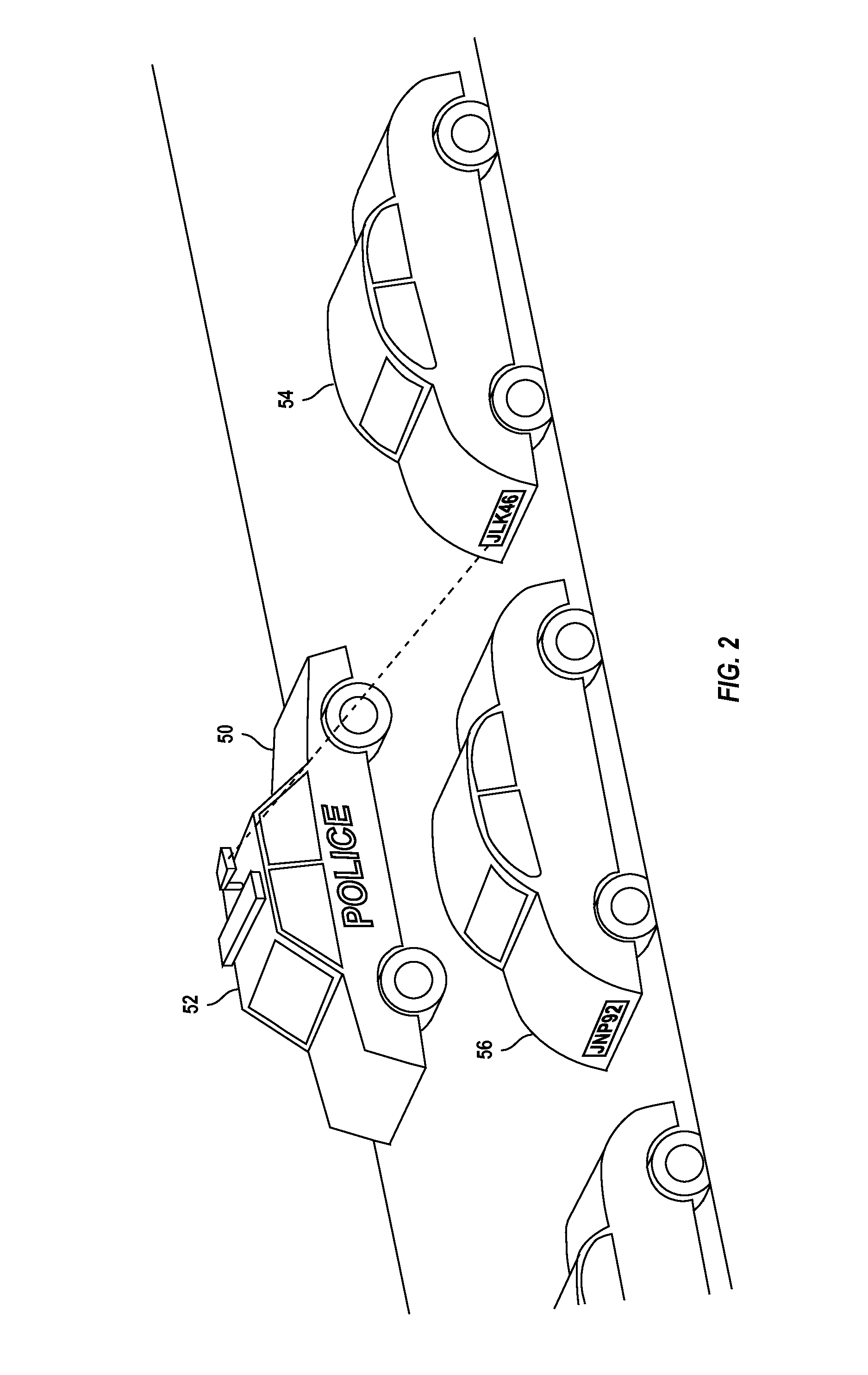
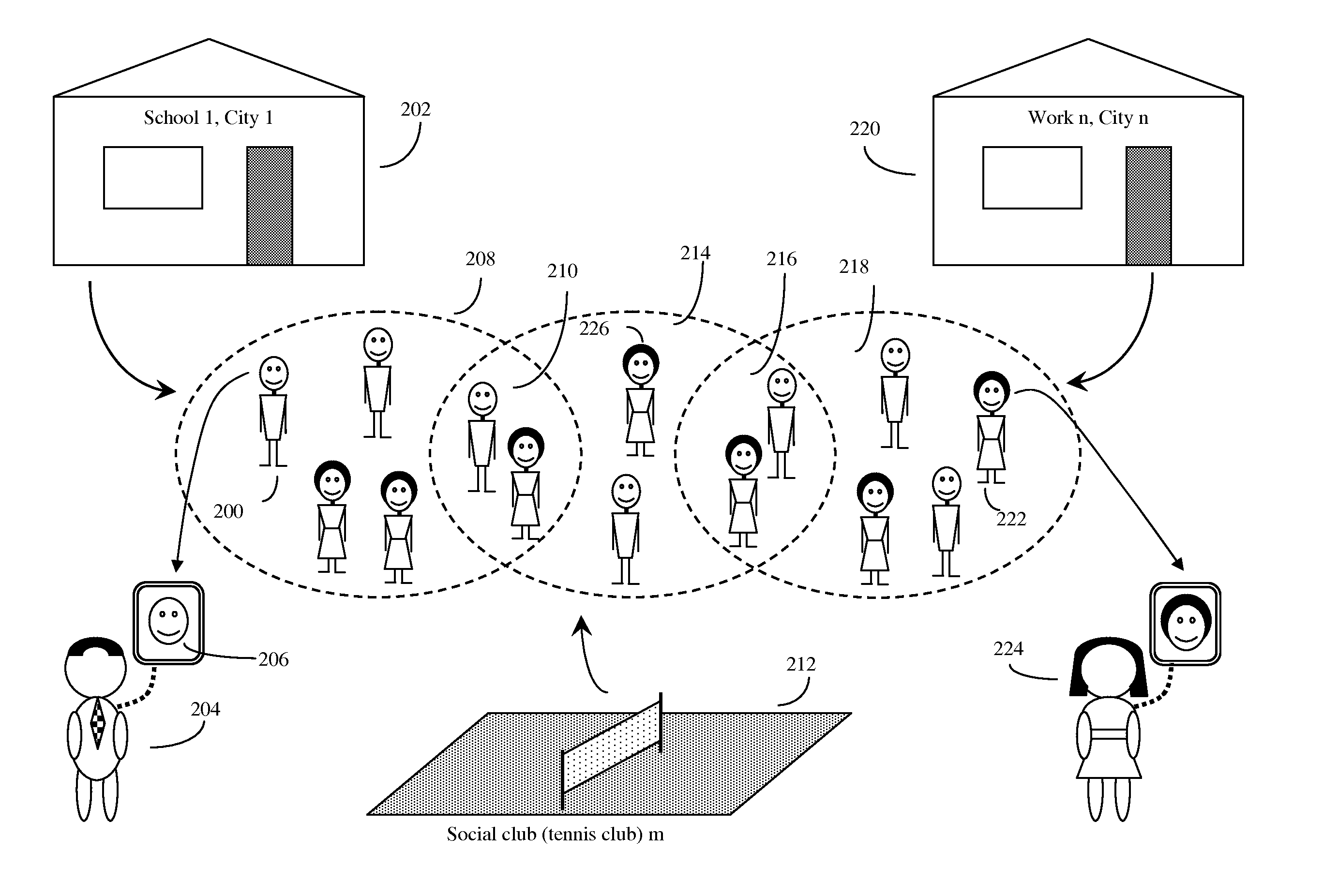
Large venue security method
ActiveUS20130279757A1Reducing violent actEnhance the imageTransportation facility accessReservationsParking areaComputer vision
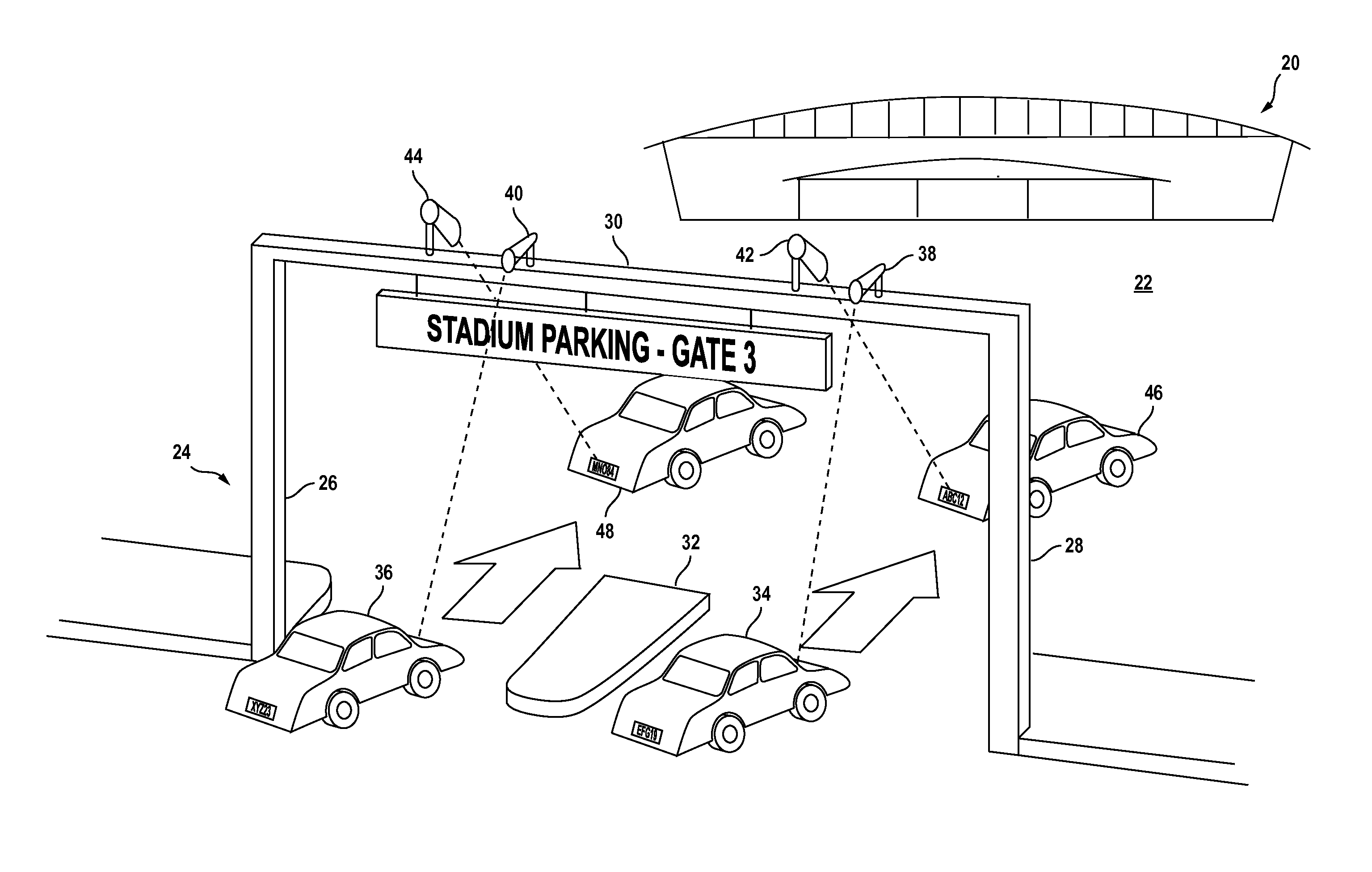
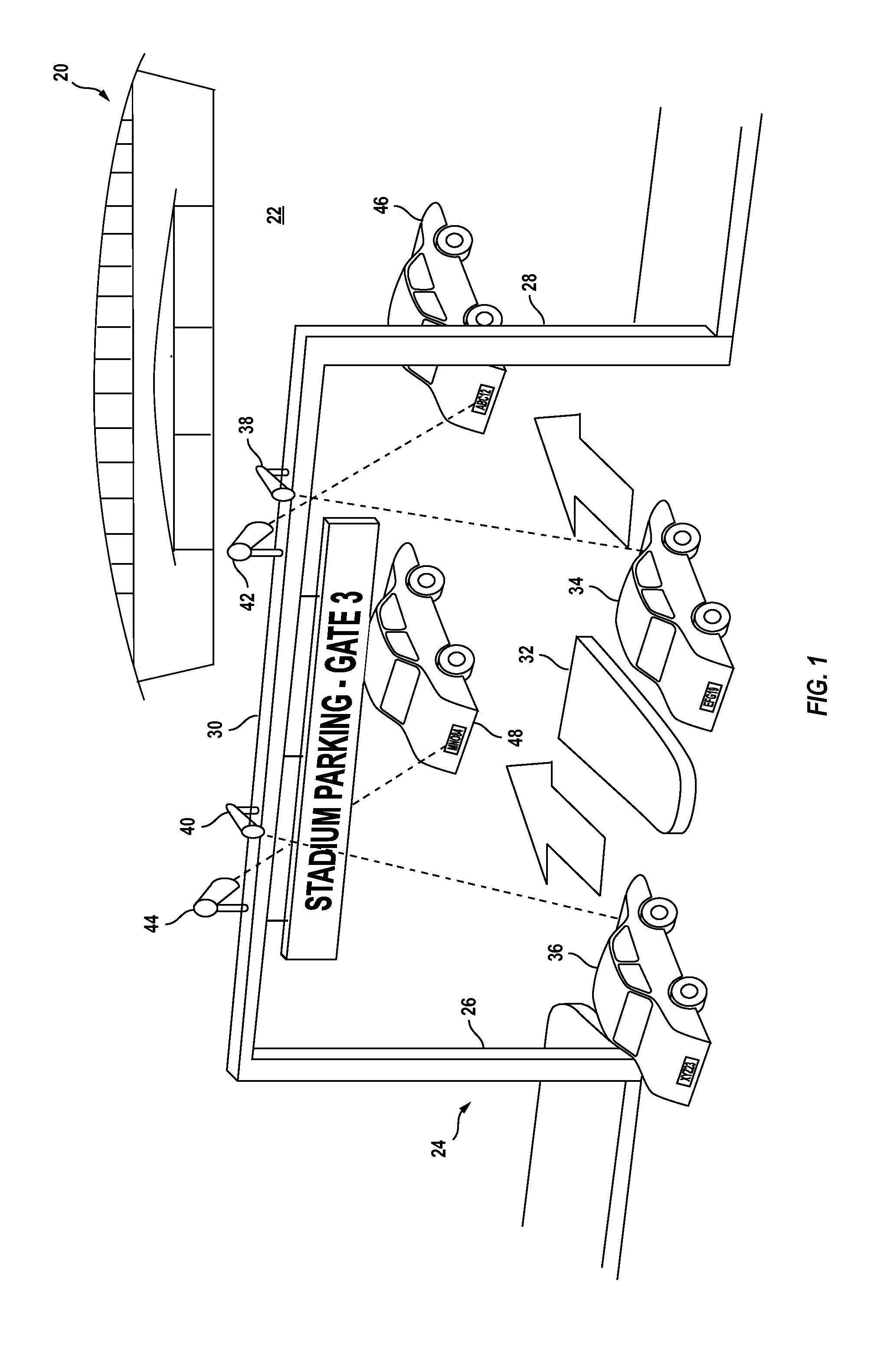
A method for reducing violence within crowded venues includes reading license plates of vehicles passing into entry ports of a parking area, and capturing facial images of persons seeking admission to the venue. A computer compares such license plates to a database of vehicle license plates associated with persons with past histories of violence. A computer also compares captured facial images to a database of facial data for persons with past violent histories. Upon detecting a match, the computer creates an alert presented to law enforcement officers at the venue to facilitate detention of such persons for investigation. Information recorded on entry tickets is scanned and saved together with the facial image of the ticket holder. If a violent act occurs, cameras within the venue capture facial images of participants. The computer matches such participants to stored identifying data to assist in the identification and apprehension of such persons.
Owner:KEPHART CONSULTING LLC +1
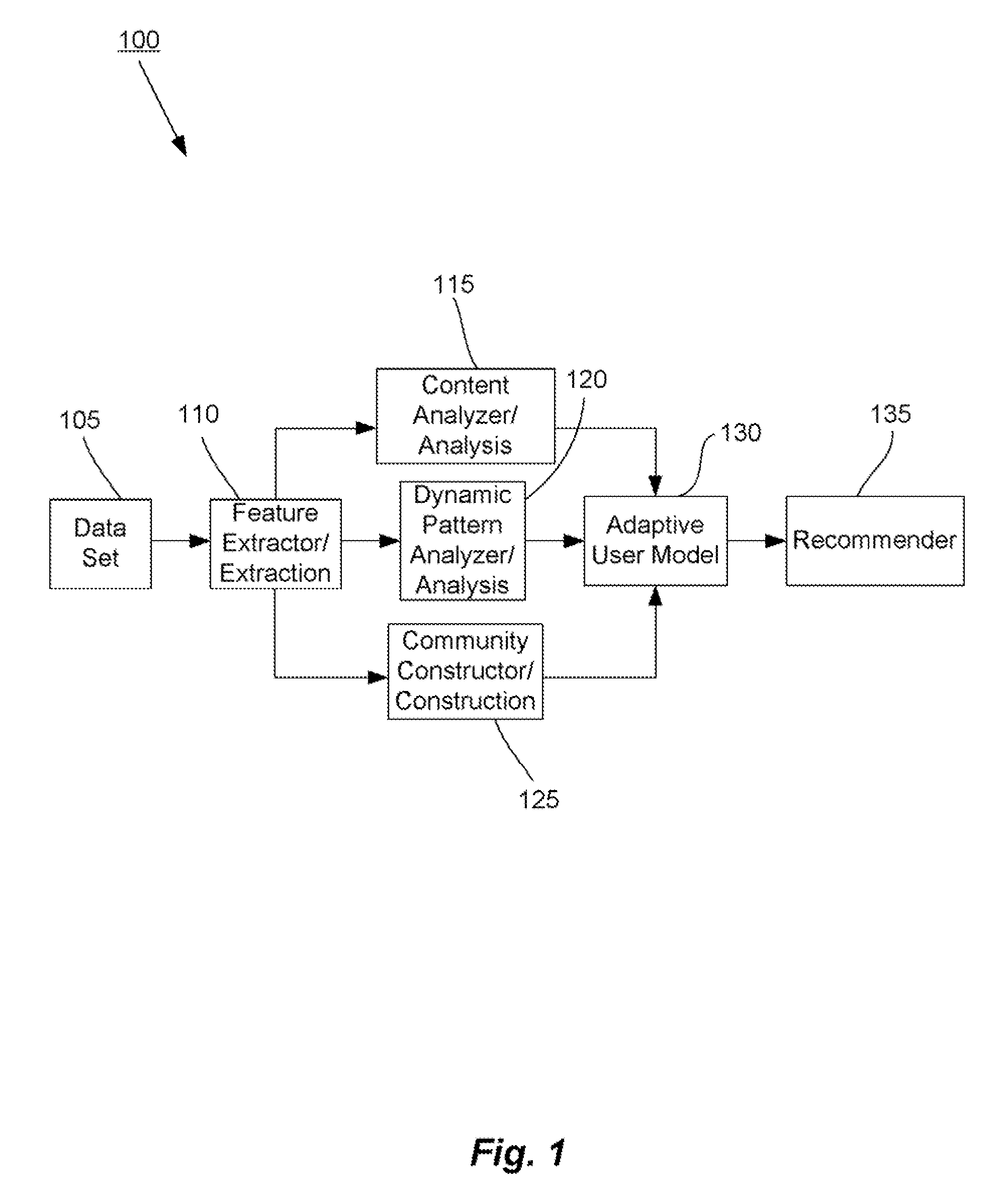
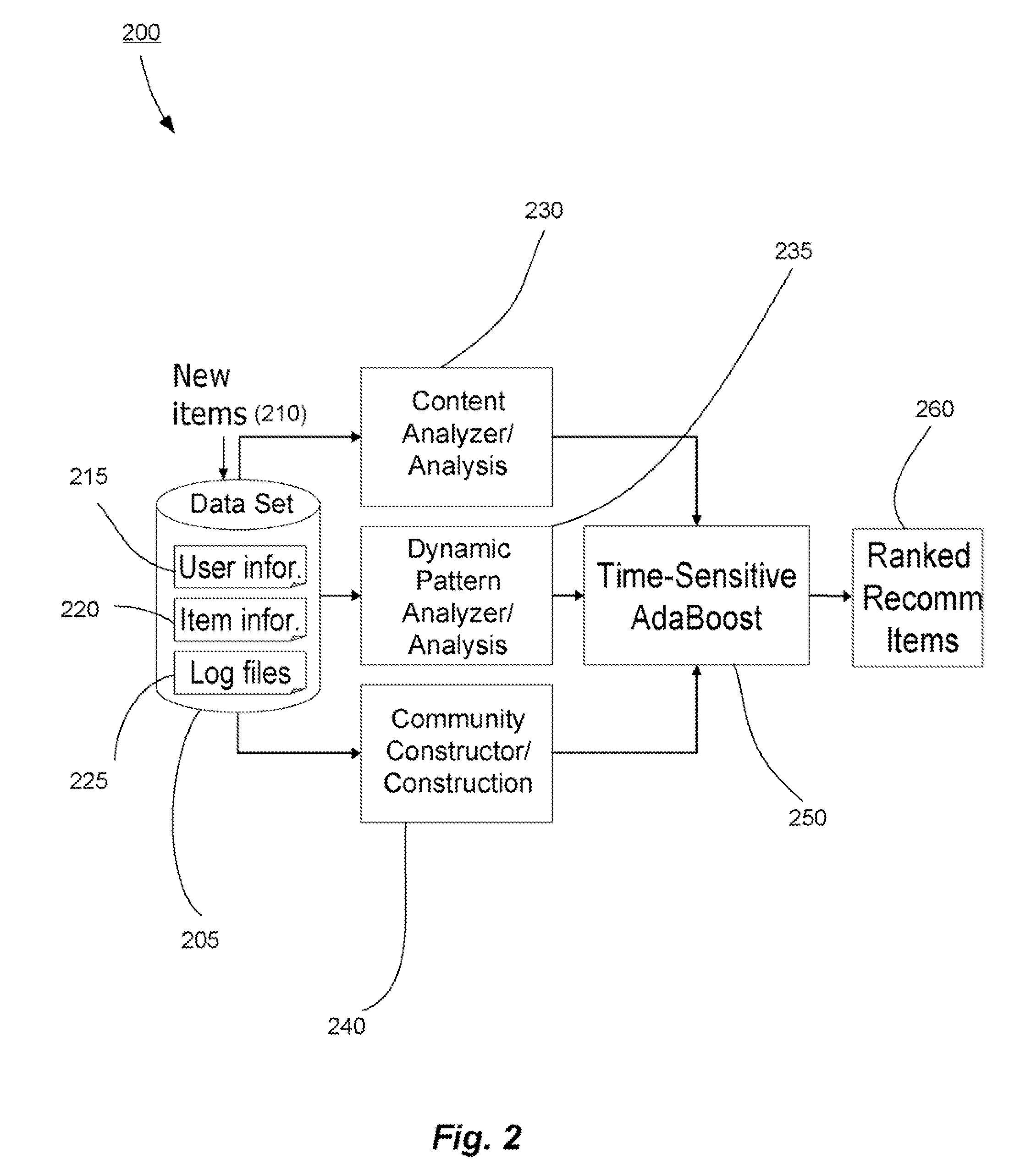
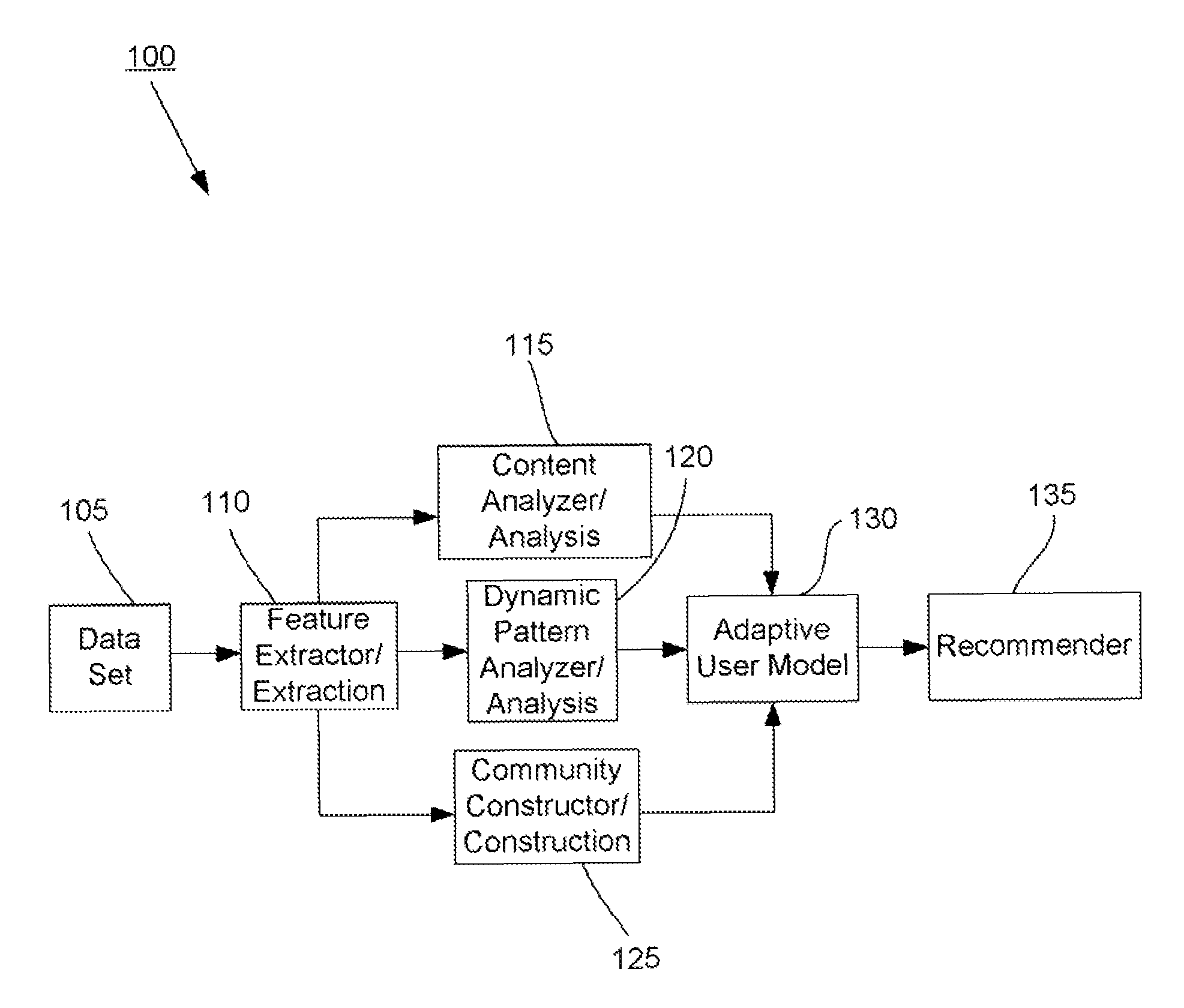
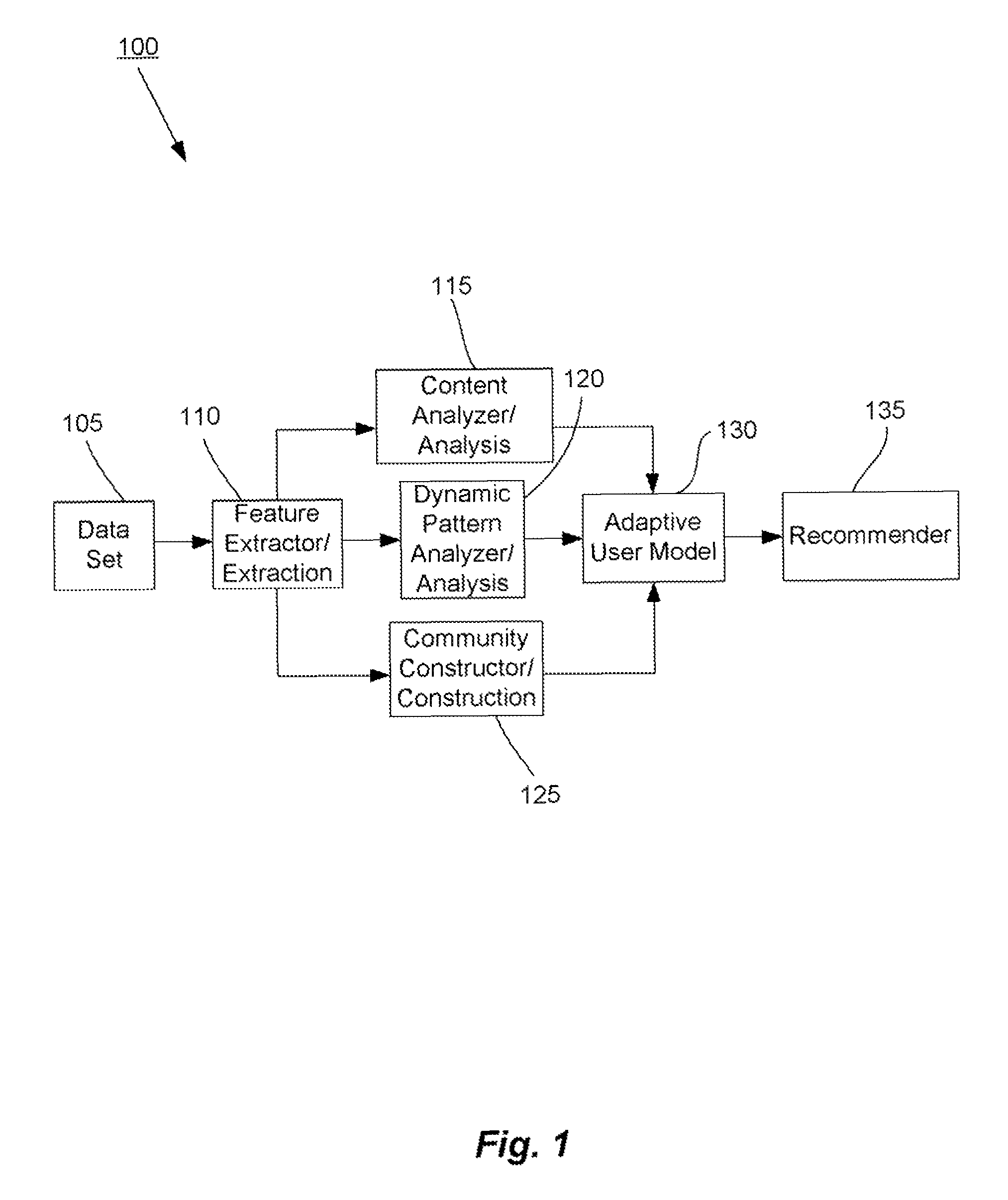
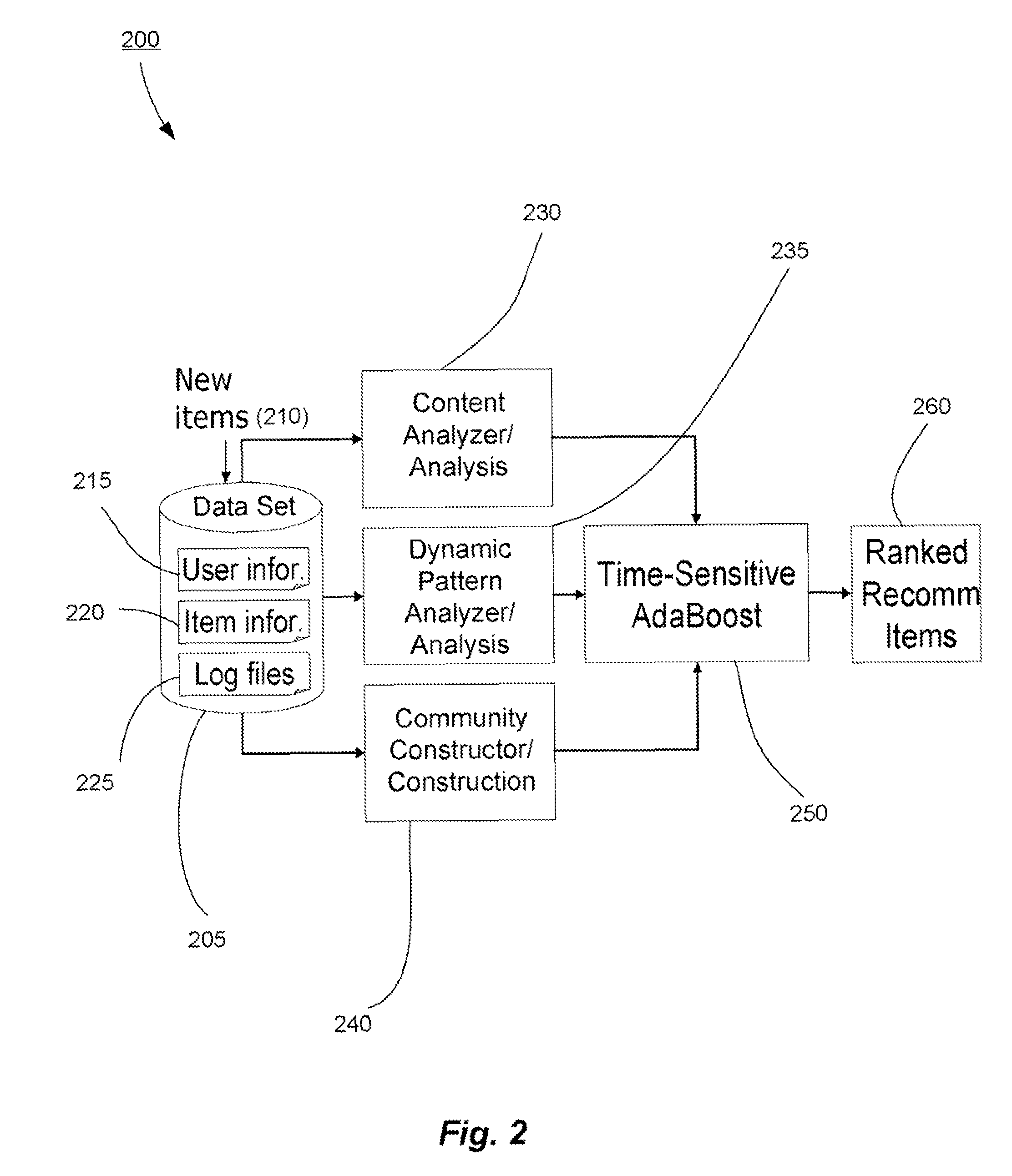
Methods and systems for utilizing content, dynamic patterns, and/or relational information for data analysis
InactiveUS20070118498A1Avoid problemsCommerceSpecial data processing applicationsTemporal changeAnalysis data
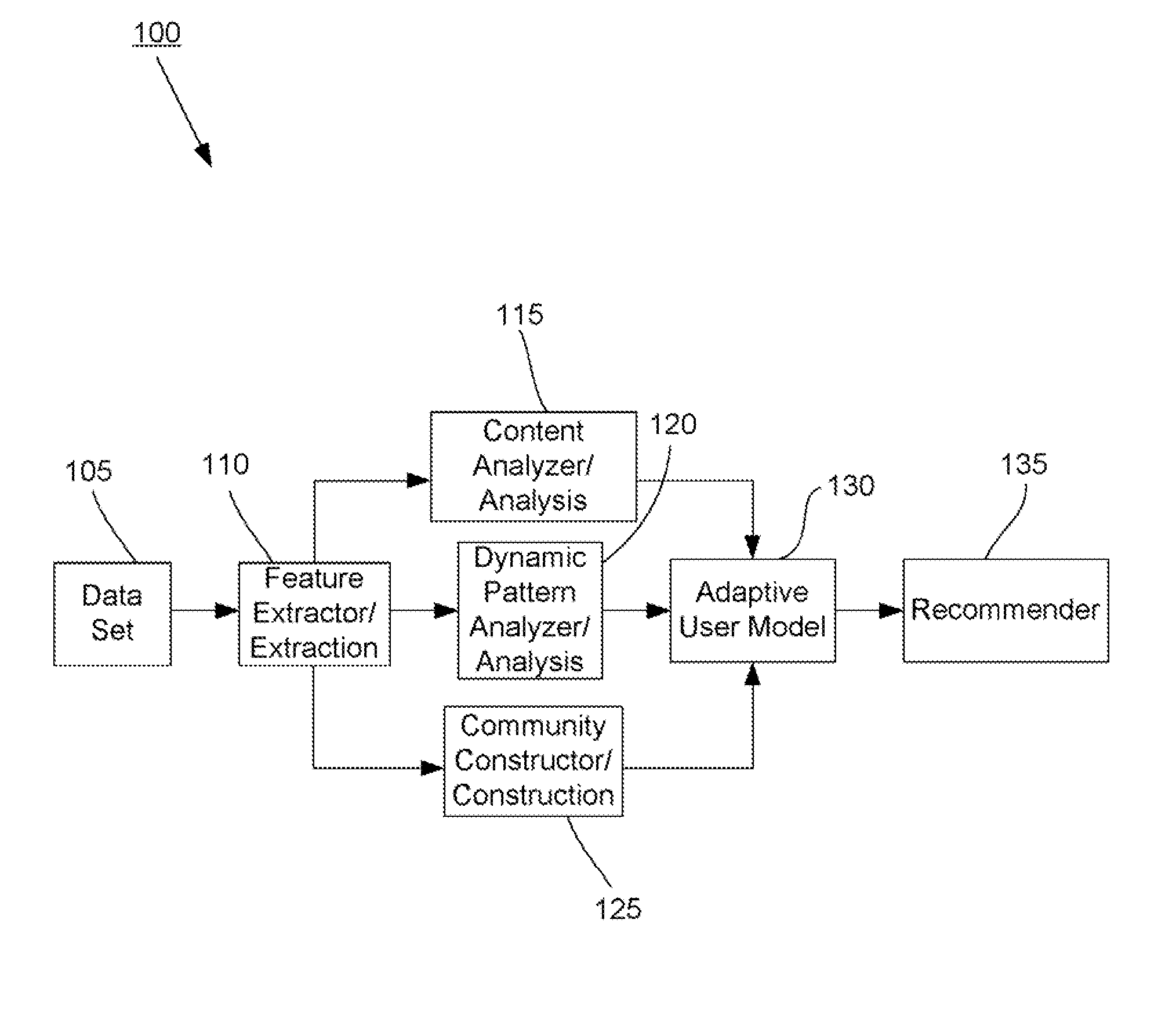
The present invention is directed generally to providing systems and methods for data analysis. More specifically, embodiments may provide system(s) and method(s) including dynamic user modeling techniques to capture the relational and dynamic patterns of information content and / or users' or entities' interests. Various embodiments may include system(s) and method(s) that are based on, for example, the past history of content semantics, temporal changes, and / or user community relationship. Various embodiments may include modeling and / or analysis of the dynamic nature of an item of interest's value to a user(s) / entity(ies) over time. The dynamic factors may be consider in any manner, such as, individually or combined, sequentially or simultaneously, etc. Further, some embodiments may include, for example, system(s) and method(s) relating to analyzing data to capture user / entity interests and / or characteristics, consider content semantics and evolutionary information, and / or using community relationships of users / entities to thereby analyze information and provide dynamic conclusion(s) (e.g., recommendation(s)).
Owner:NEC CORP
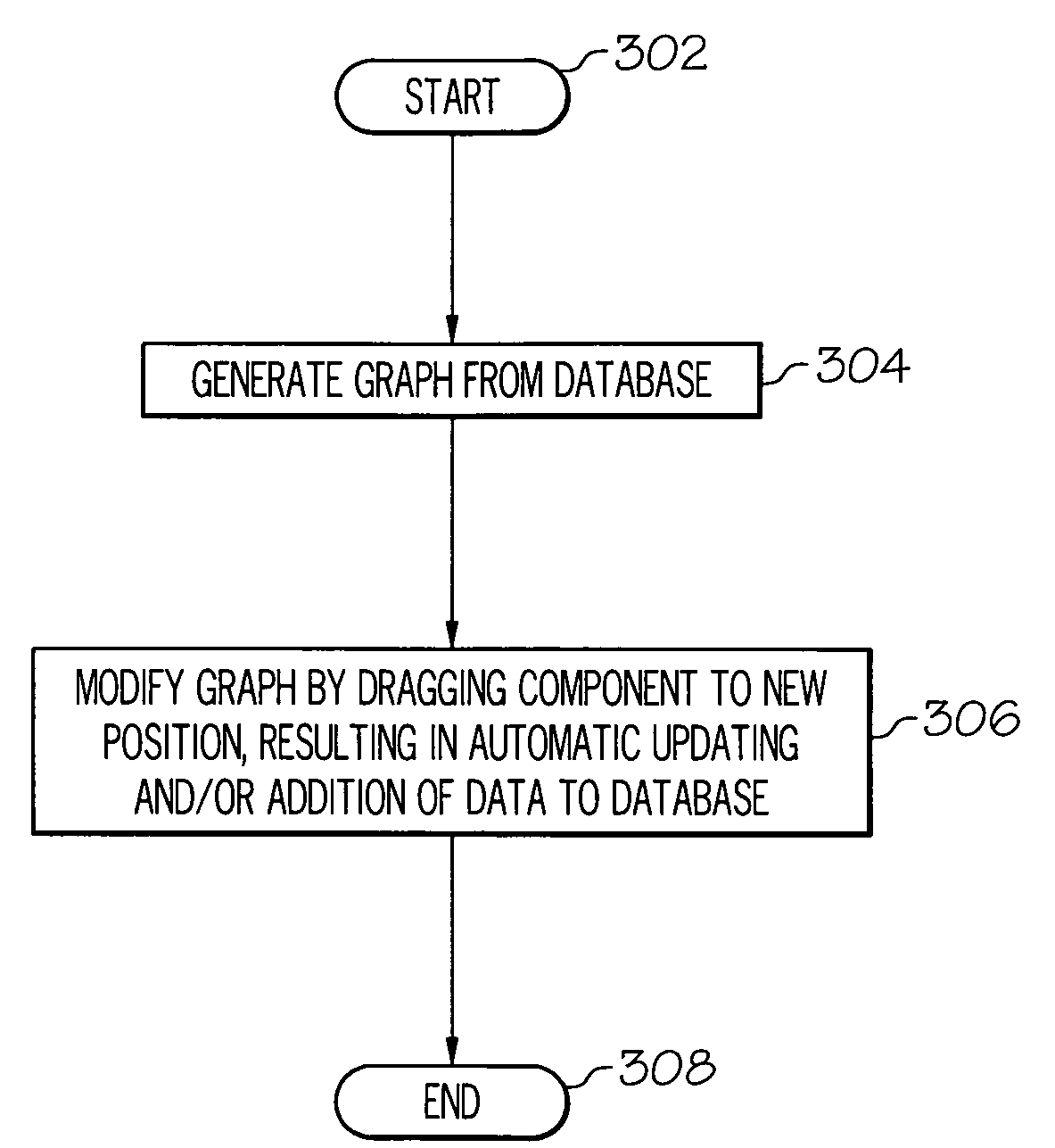
Graphically manipulating a database
InactiveUS20070271285A1Simple methodDigital data processing detailsVisual data miningGraphicsData mining
A method and system for managing a database through a graphical representation is presented. The method the method includes dynamically adjusting data in a database by graphically manipulating a graph that represents the database. In one embodiment, a predictive cone is overlaid onto the graph. The predictive cone is created from a heuristic algorithm that uses past historical data to predict where future real data will track on the graph.
Owner:IBM CORP
Session initiation protocol routing using voice cookies
InactiveUS20020147818A1Determination of addressEasy to understandMultiple digital computer combinationsAutomatic exchangesWeb siteWeb service
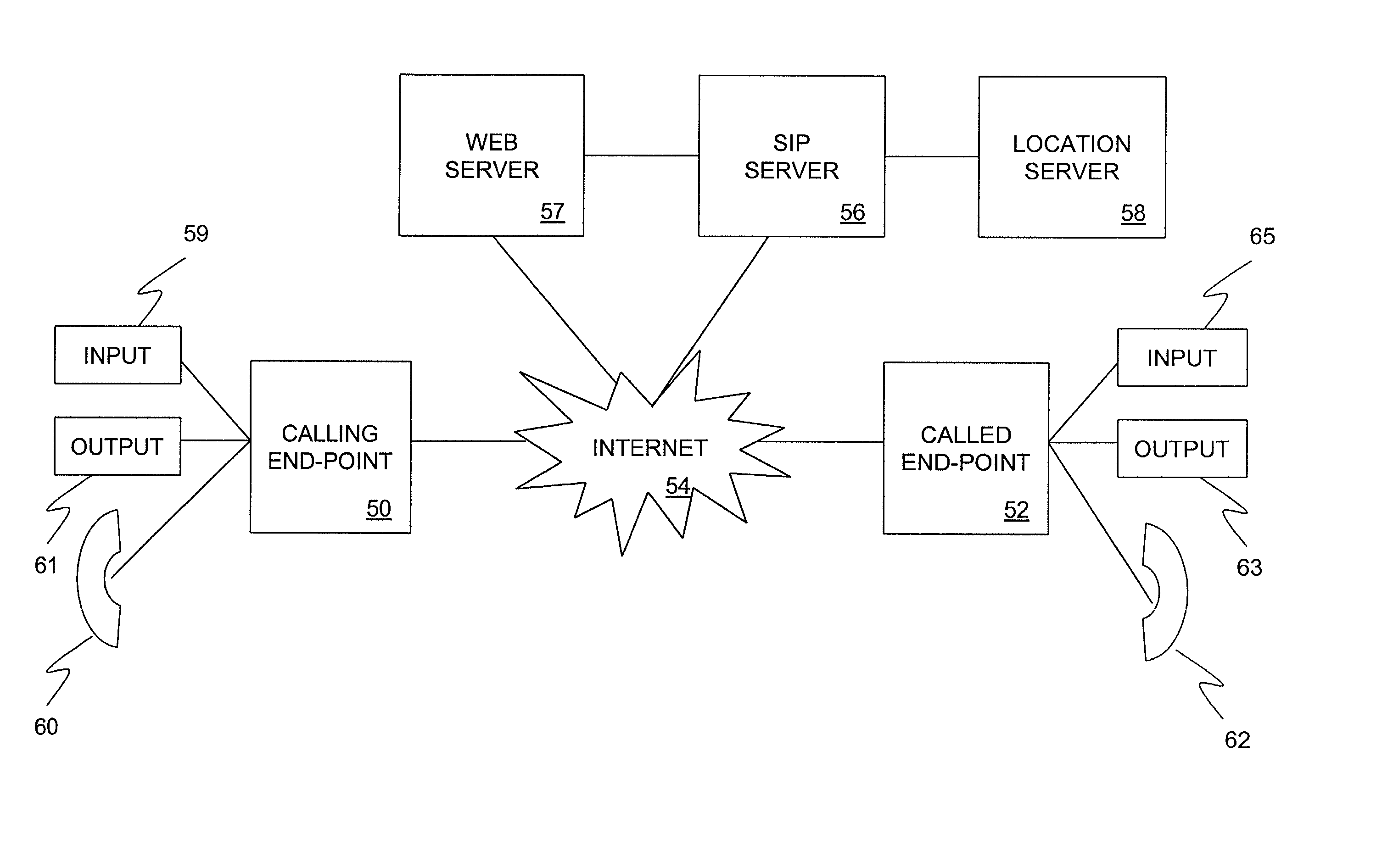
A system and method for establishing a SIP session between calling and called end-points. A SIP server receives a SIP INVITE request for establishing the SIP session. The SIP INVITE request includes standard routing information in its header. The SIP server receives the SIP INVITE request and responds by transmitting to the calling end-point a HTML link associated with a web server. In rendering the contents of the HTML link, the calling end-point transmits an HTTP request to the web server including voice cookie information. The voice cookie information may include information gathered about the caller such as the caller profile information, transaction information, caller intent information, or recent and past history associated with a web site domain. The web server forwards the voice cookies to the SIP server. The SIP server determines an address of the called end-point as a function of the routing information in the SIP INVITE request and the voice cookie information. The call is then routed to the determined address along with the voice cookies or information derived from the voice cookies. New voice cookies may be written to the web server which transmits these to the calling end-point within an HTTP response.
Owner:ALCATEL LUCENT SAS
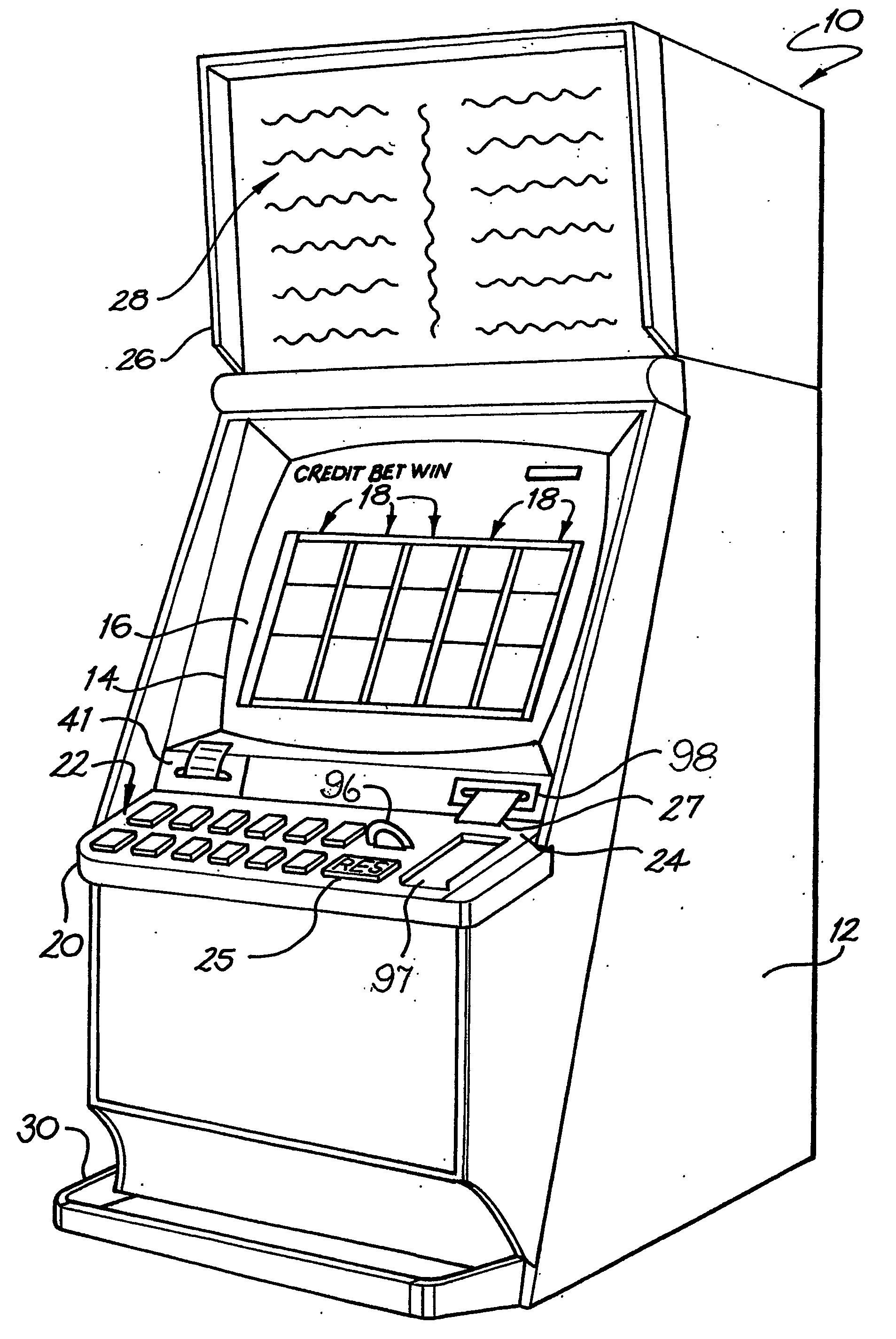
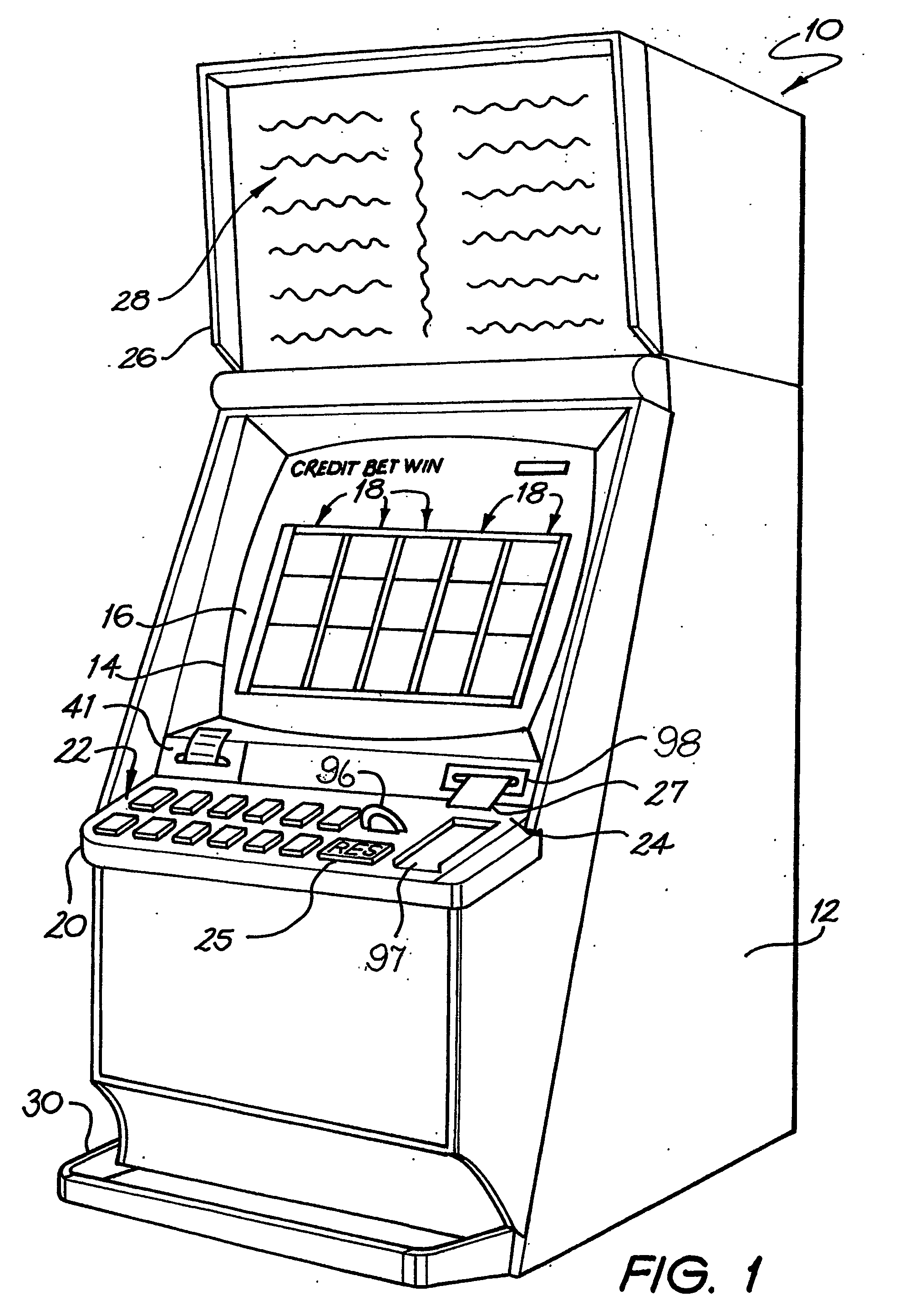
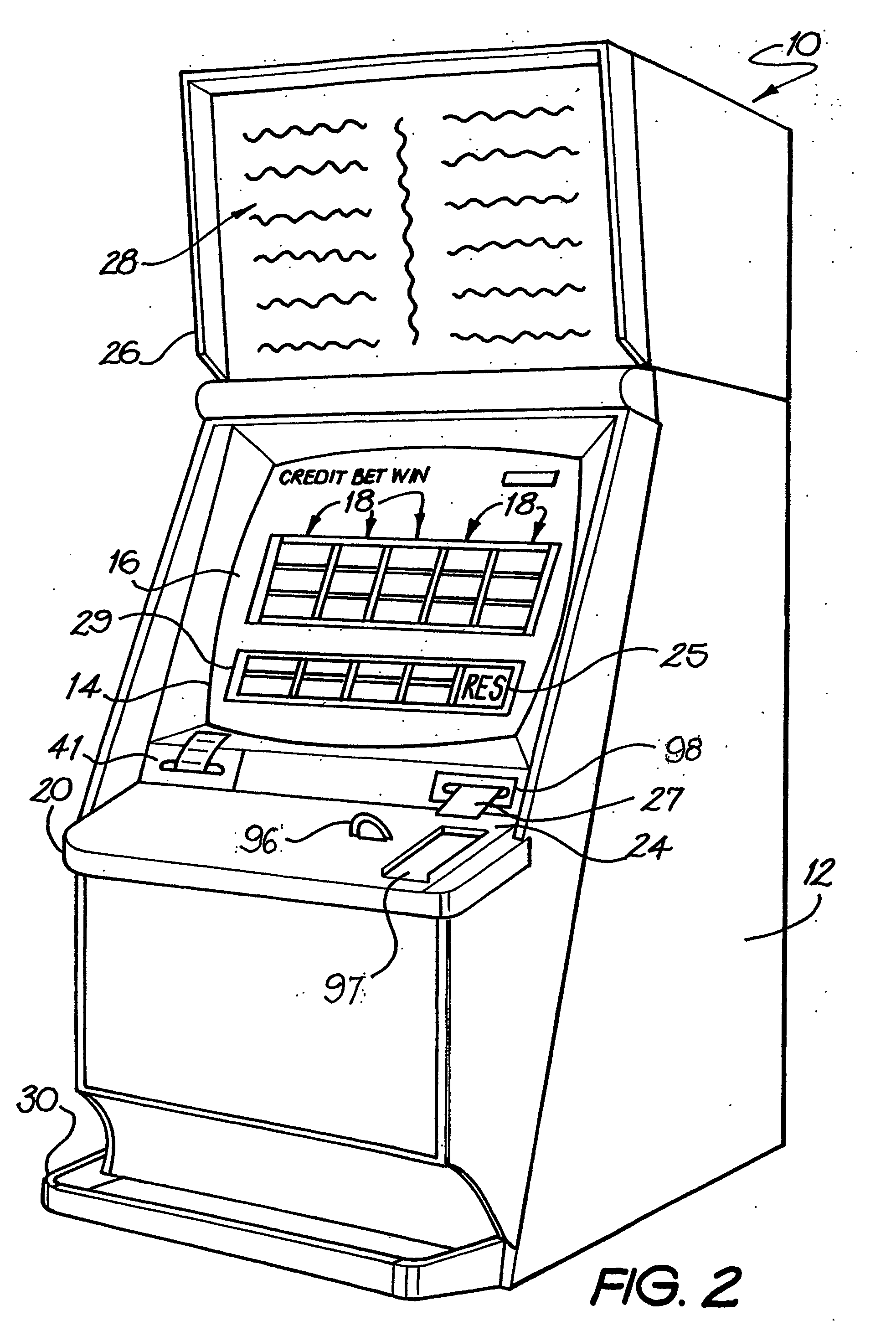
Multigame selection
ActiveUS20070054738A1Apparatus for meter-controlled dispensingOther databases retrievalCommunications systemRanking
A gaming system (100) comprises a gaming server (system controller) (54), a plurality of gaming machines (10), and a communications system (63) connecting each of the plurality of gaming machines (10) to the gaming server (53). The gaming machines (10) each have a display (14), player controls (22), a player tracking device, such as a card reader (24.3) for reading player tracking cards (27), and a game processor (34) which displays sequential game images of a game being played on the respective display (14). Each game processor (34) plays a game initiated by the player, where the game is one of a plurality of games available on the gaming machine (10) and selectable by the player. Each gaming machine (10) includes game selection means (16) which displays a selection of games (211-216 & 311-316) available on the machine for the player to play. The games (211-216 & 311-316) offered for selection are ordered according to a ranking determined as a function of the player's past history of playing games and a history of games played by other players.
Owner:ARISTOCRAT TECH AUSTRALIA PTY LTD
Resource configuration in multi-modal distributed computing systems
InactiveUS7454608B2Digital computer detailsServices signallingBiological activationComputing systems
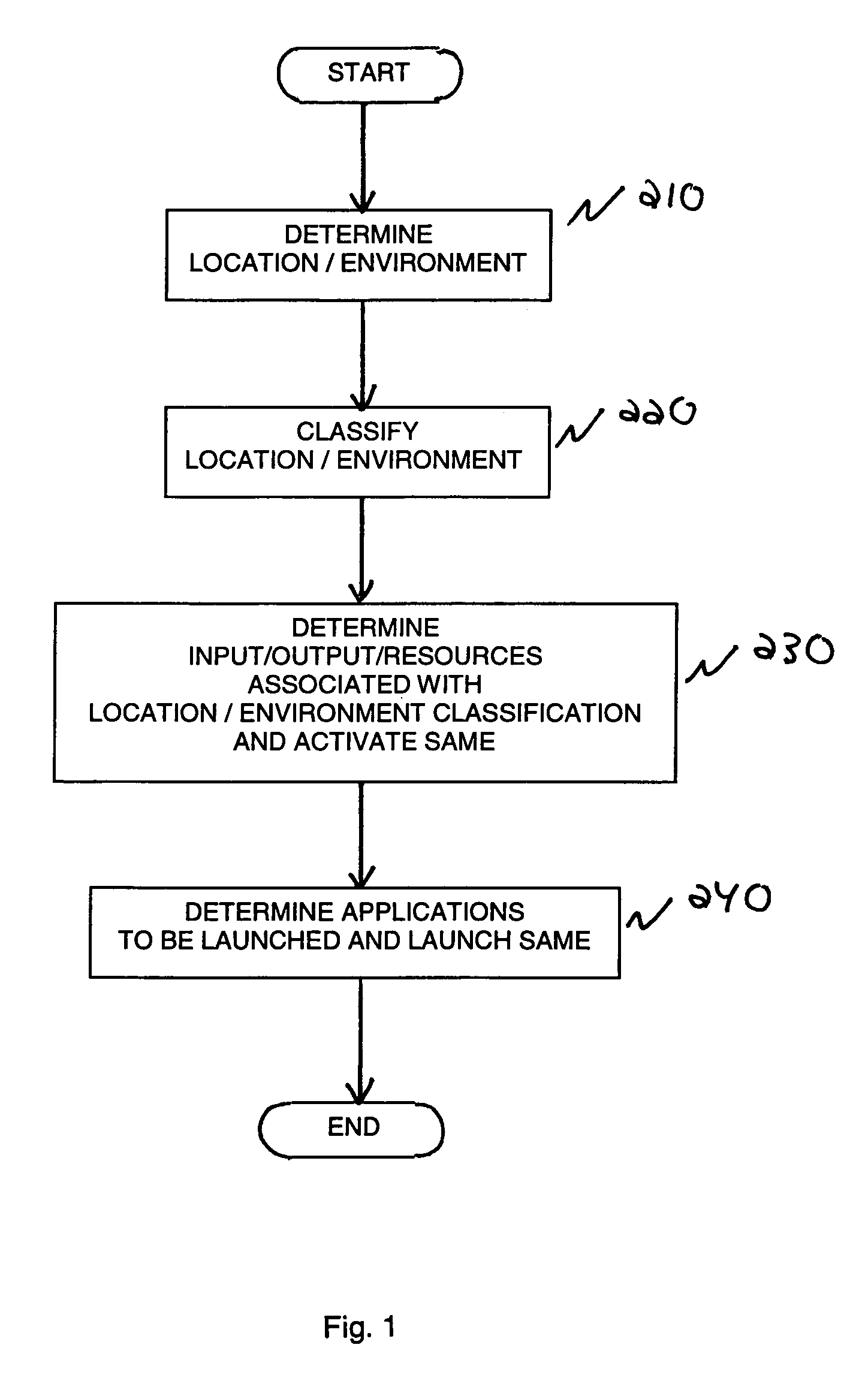
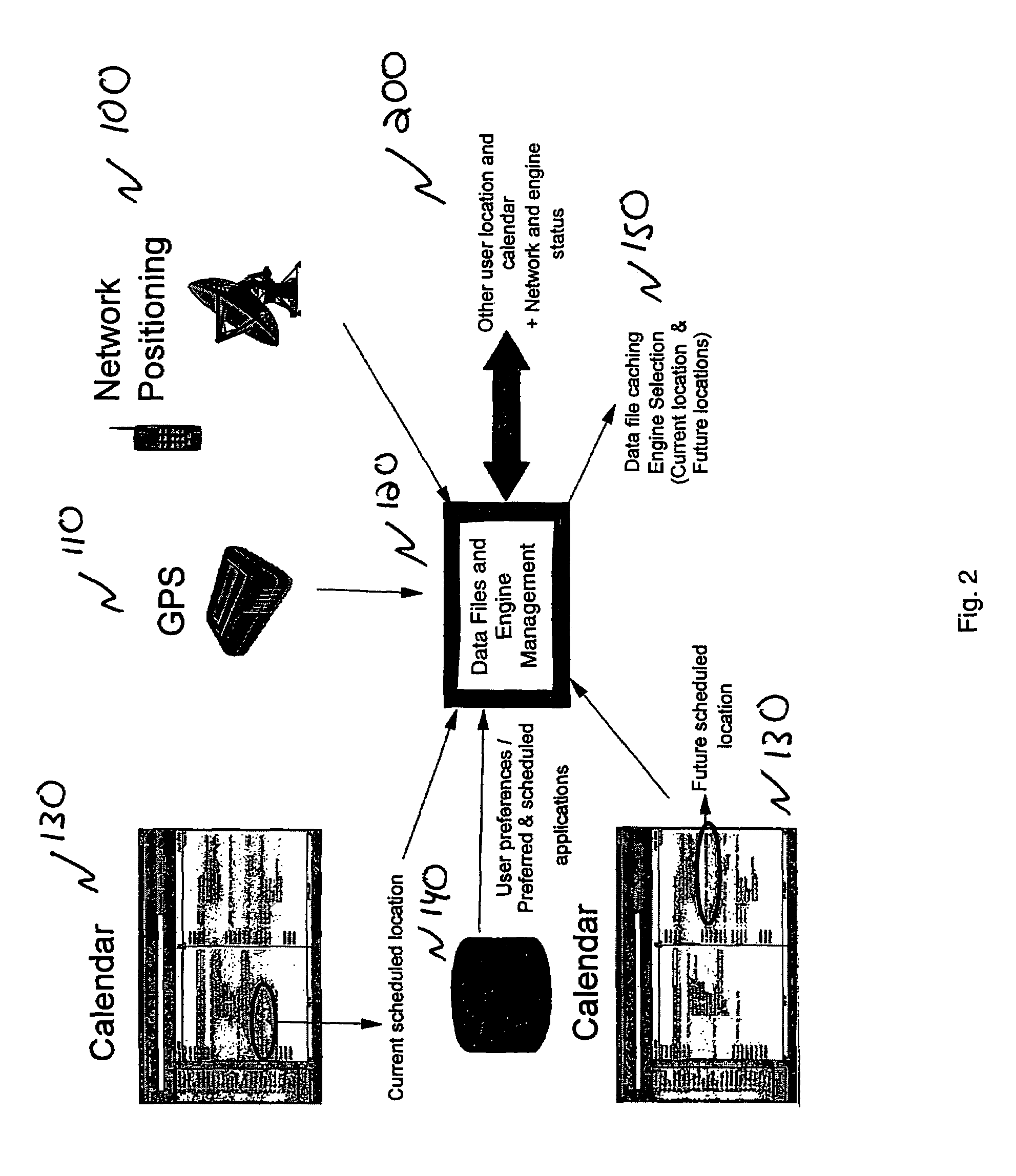
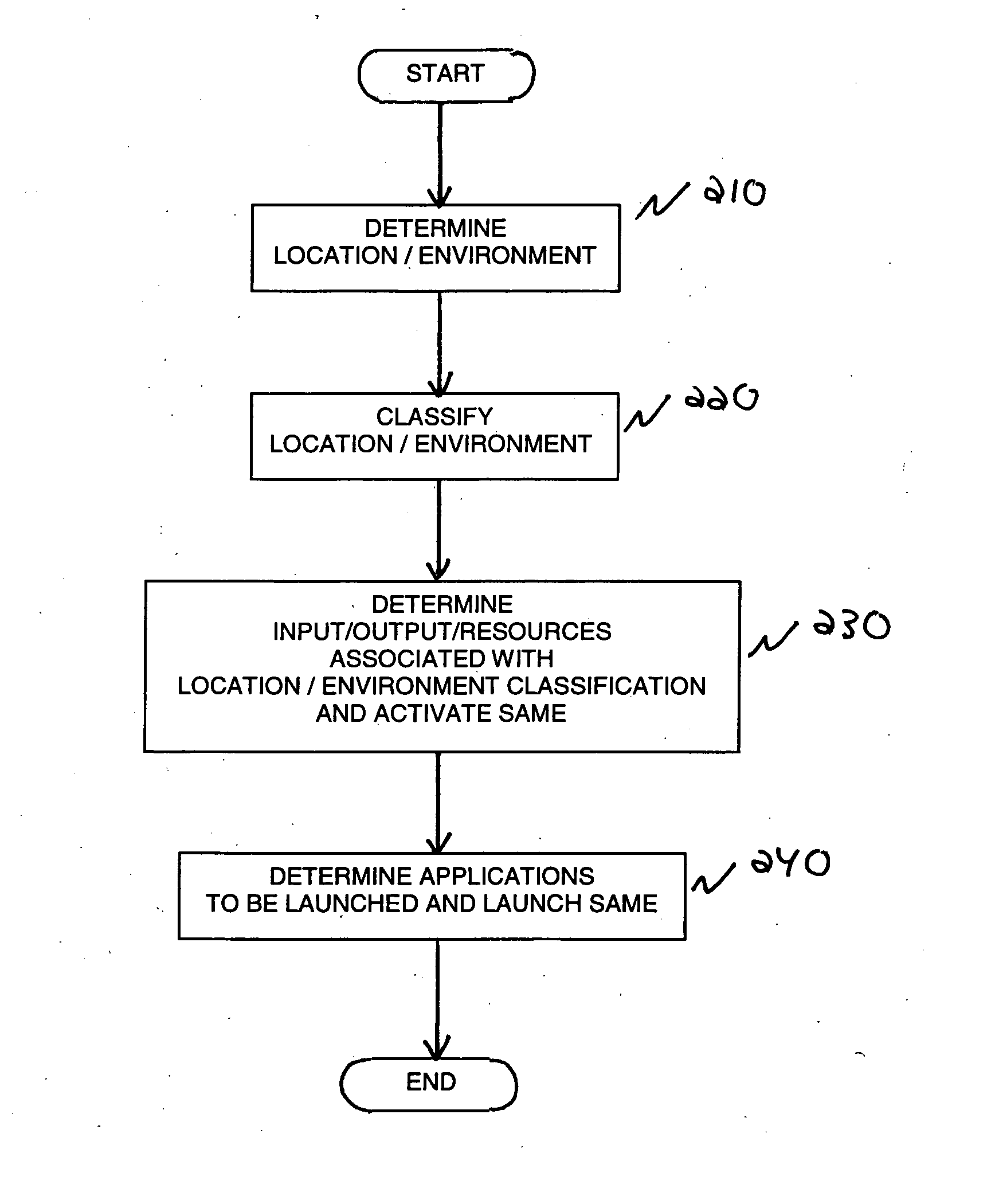
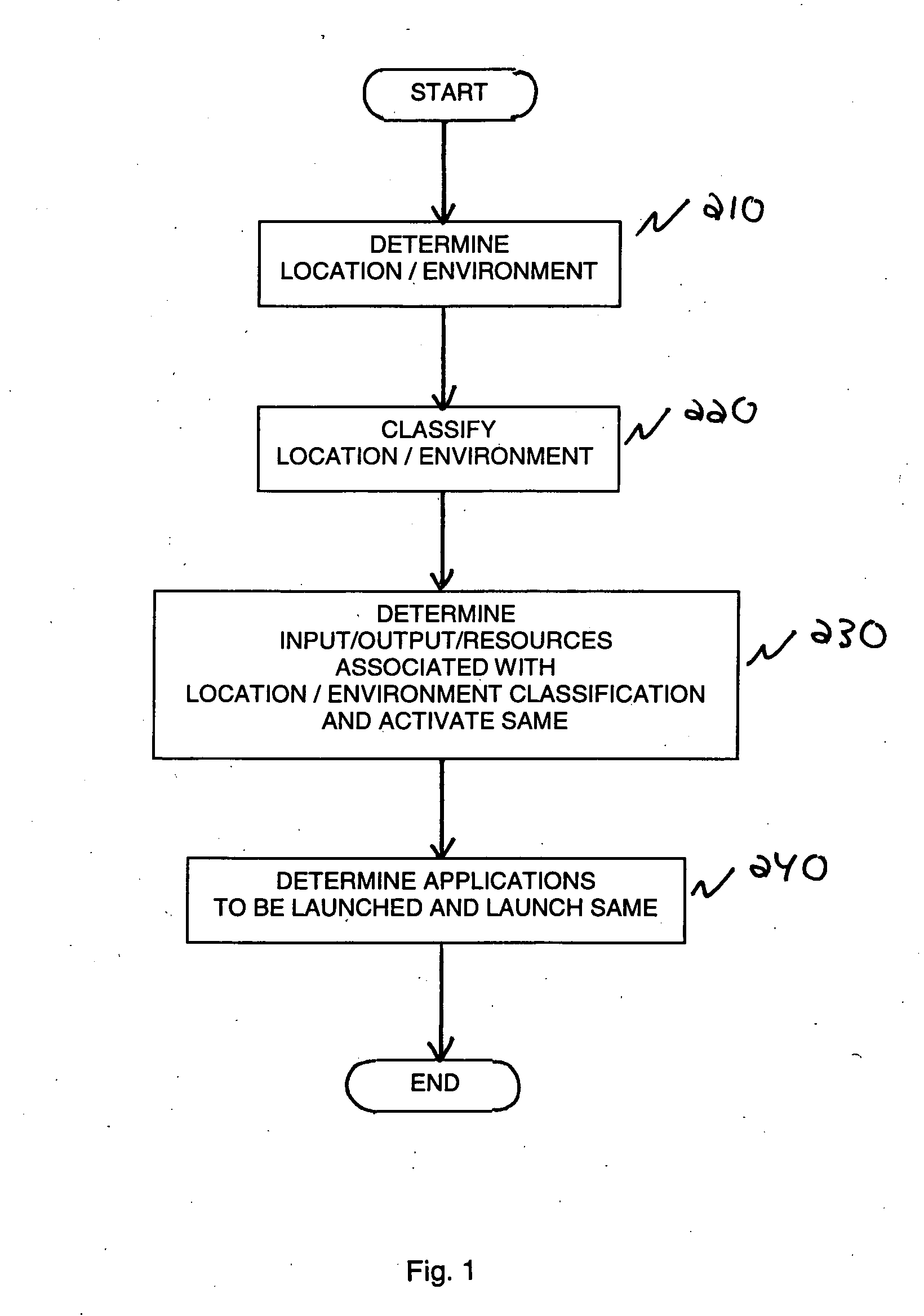
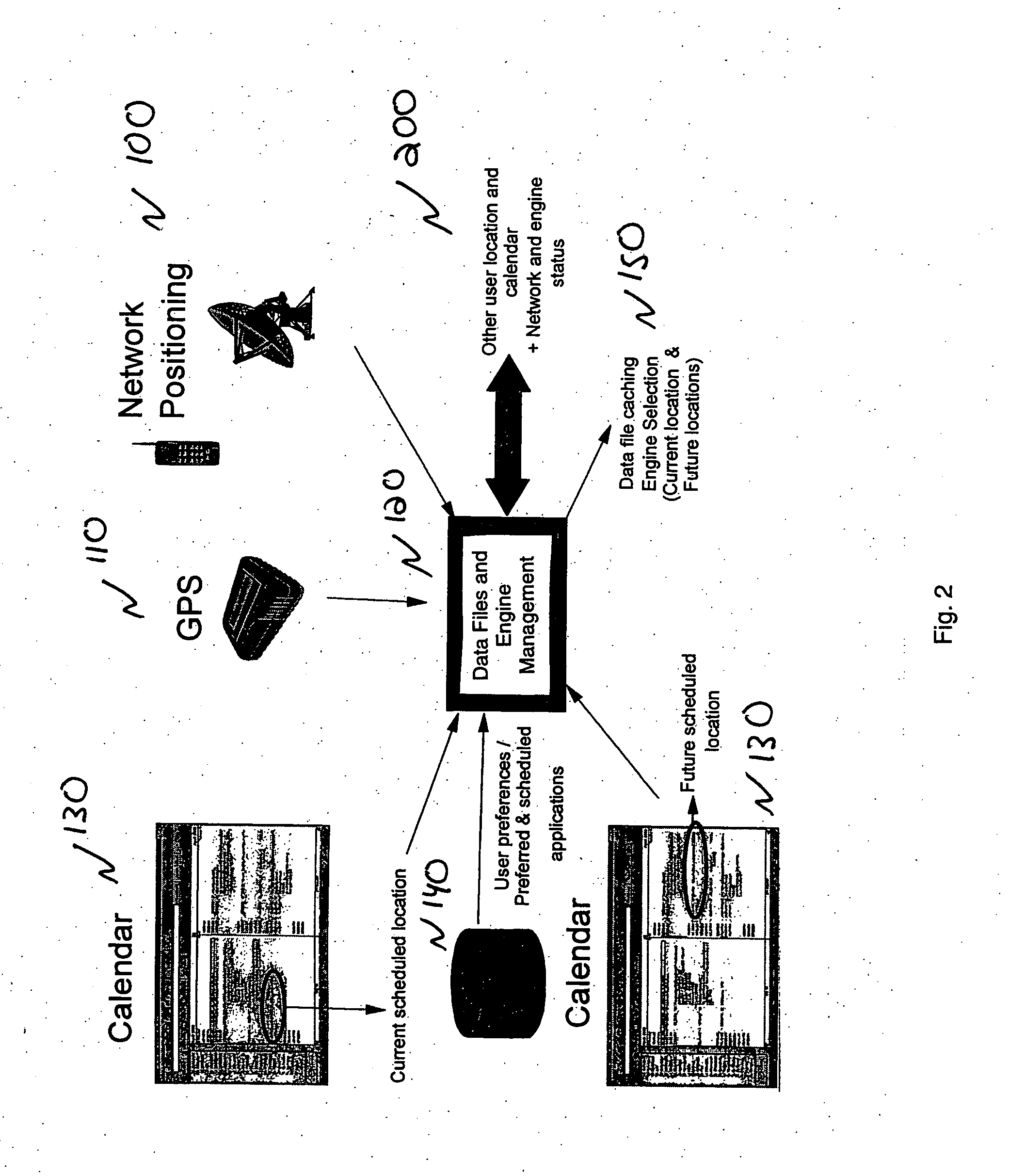
A method and system for configuring available resources in real-time to automatically accommodate the needs of the system user in multi-modal distributed computing system is disclosed. Information about the location or environment of a wireless device is used, preferably in combination with user personal preferences and past history to modify the behavior of the wireless device, including the selection of the most appropriate mode of interaction with the device and the activation of applications thereon as appropriate.
Owner:GOOGLE LLC
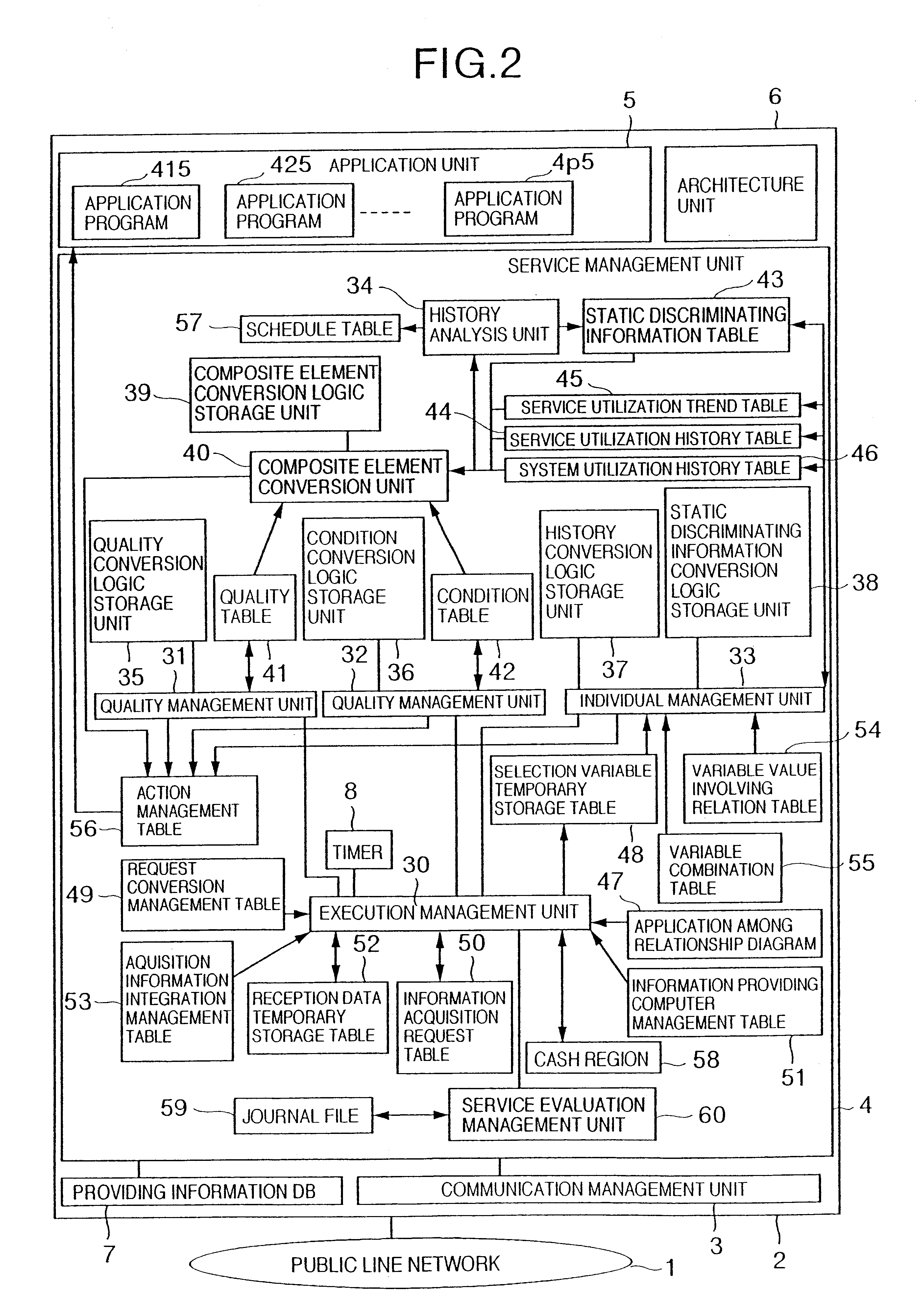
Service providing system and method which divides a request into plural service requests and provides an integrated service based on service utilization history information in response to the request
InactiveUS6847988B2Efficient use ofMultiple digital computer combinationsBuying/selling/leasing transactionsService provisionInformation gain
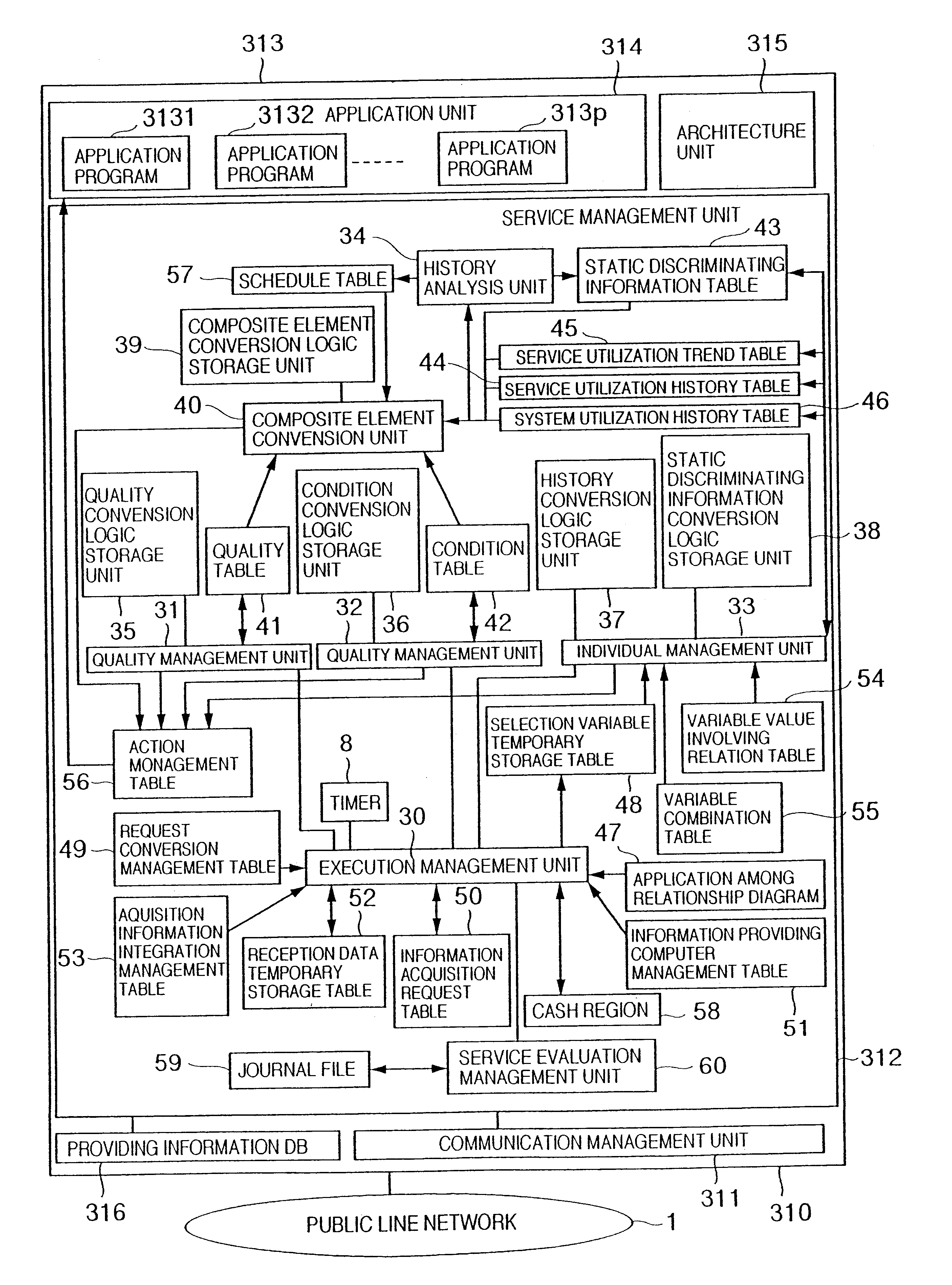
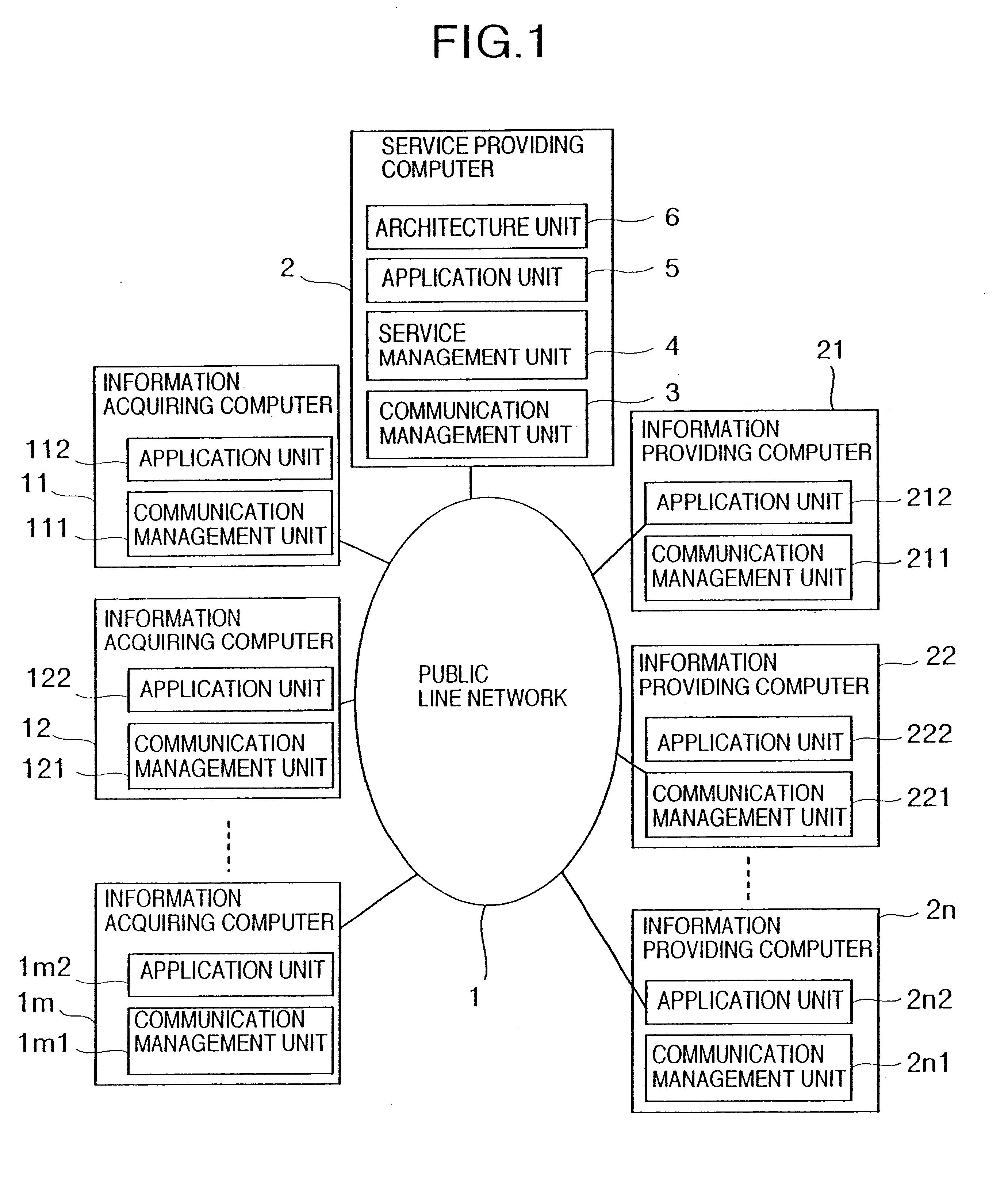
In a service providing system, a plurality of information acquiring computers for acquiring informations are connected via a network to a plurality of information providing computers for providing information. A service providing computer for executing an information providing service with respect to apparatuses for acquiring information is interposed between a plurality of in information acquiring apparatuses and a plurality of information providing apparatuses. The service providing computer receives a content of a request of the information acquiring computer, and determines a sort of information to be provided with a user based upon a quality of this request content, individual information and past historical information of the user, and also various sorts of conditions when the request is received. The service providing computer requests at least one of these information providing computers to provide the information. The information obtained from the request result is integrated by the service providing computer to be transmitted to the information acquiring computer.
Owner:HITACHI LTD
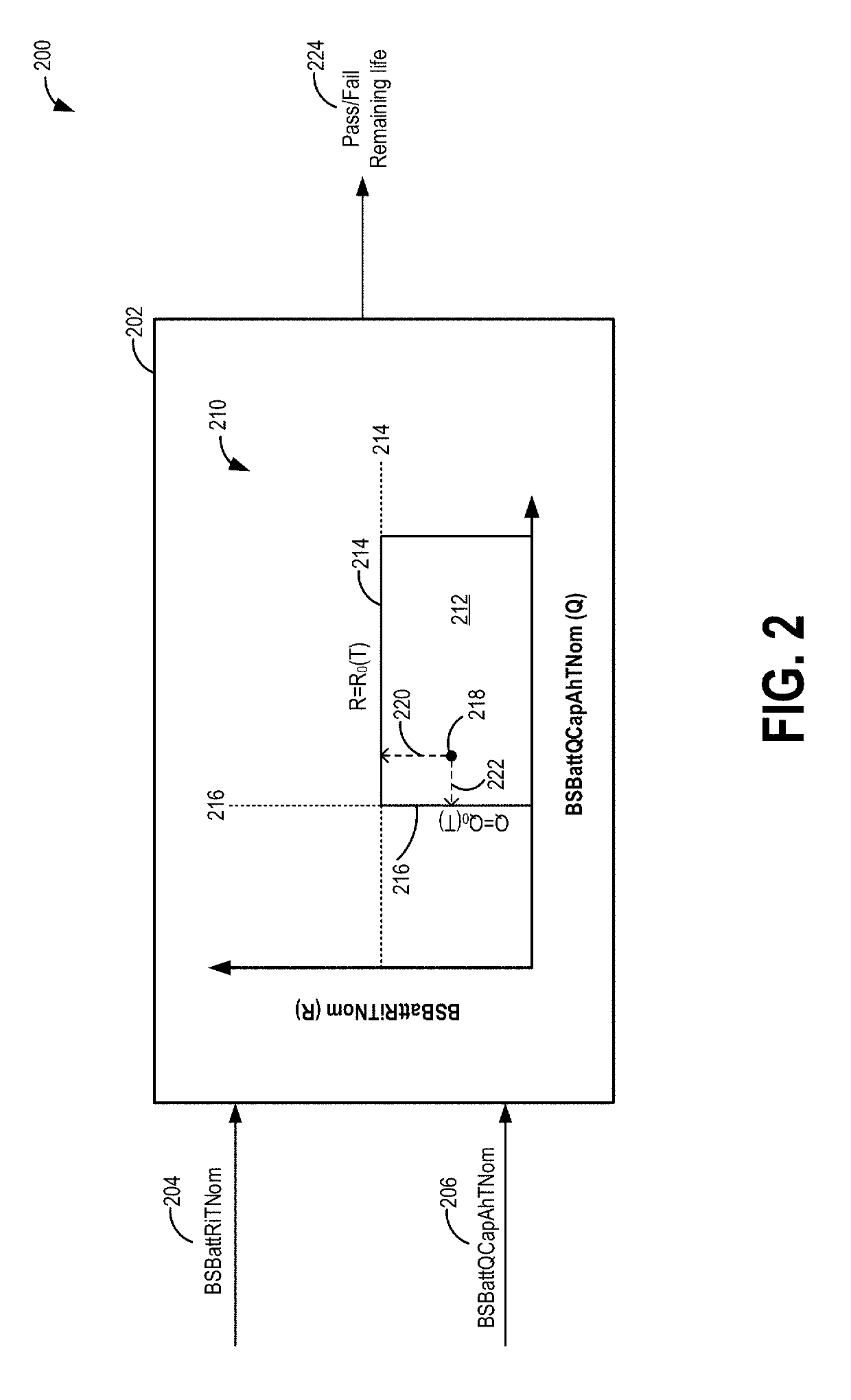
Method for predicting battery life
ActiveUS20190176639A1Increase capacitanceInternal resistance be goodElectric devicesRegistering/indicating working of vehiclesEngineeringLife time
Methods and systems are provided for reliably providing a prognosis of the life-expectancy of a vehicle battery. A state of degradation of the battery is predicted based on a rate of convergence of a metric, that is derived from a sensed vehicle operating parameter, towards a defined threshold, determined based on past history of the metric. The predicted state of degradation is then converted into an estimate of time or distance remaining before the component needs to serviced, and displayed to the vehicle operator. Vehicle control and communication strategies may be defined with respect to the predicted state of degradation.
Owner:FORD GLOBAL TECH LLC
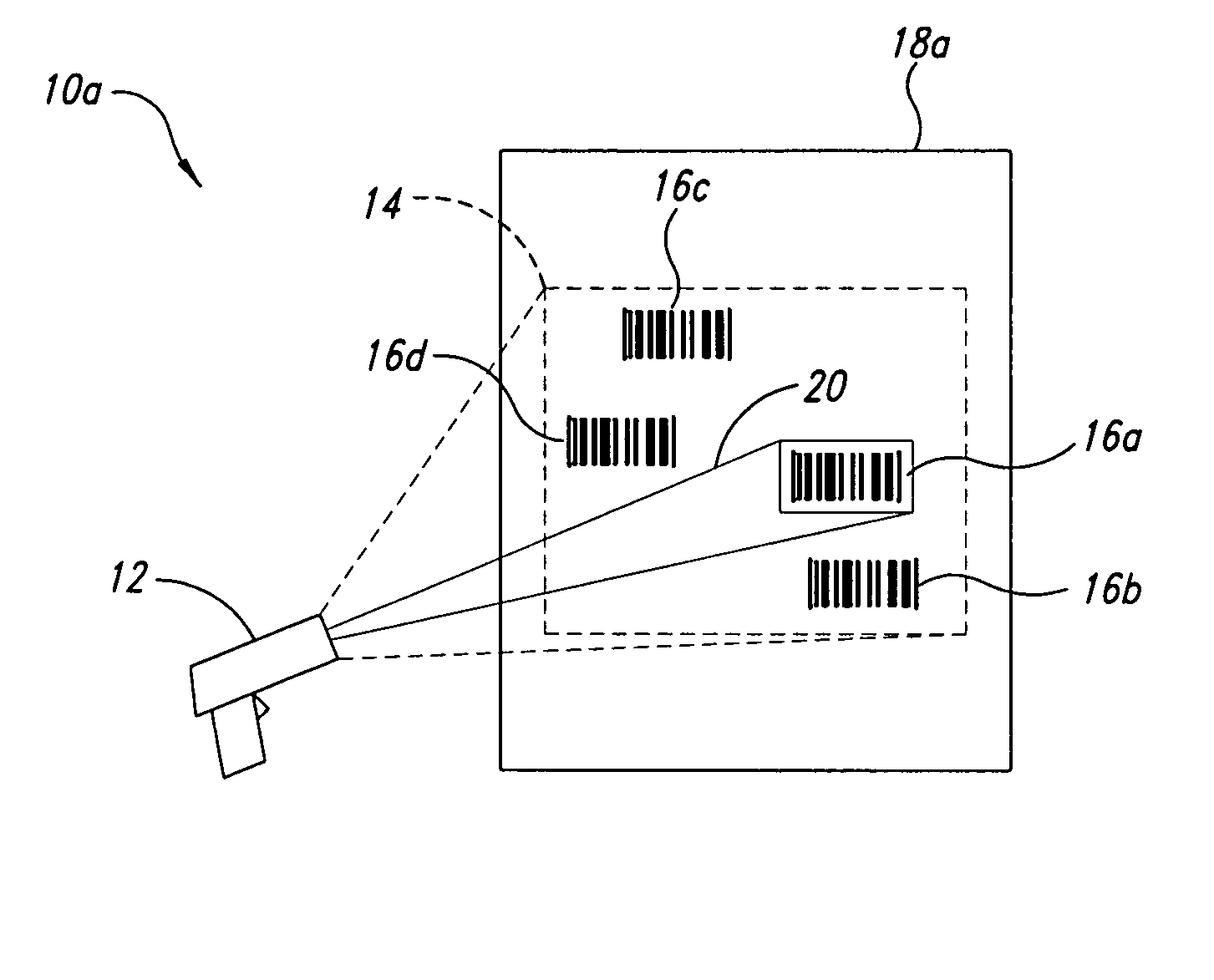
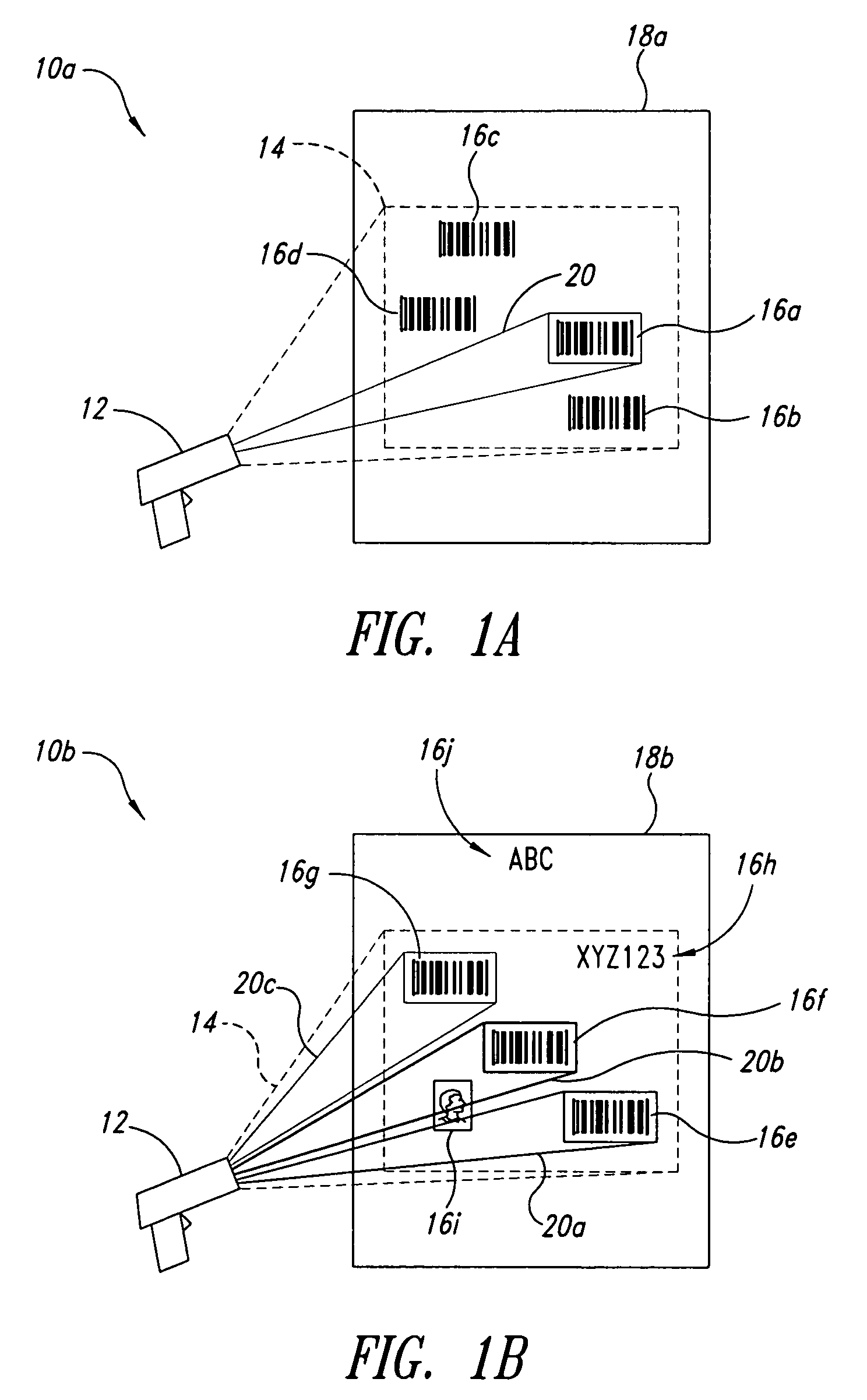
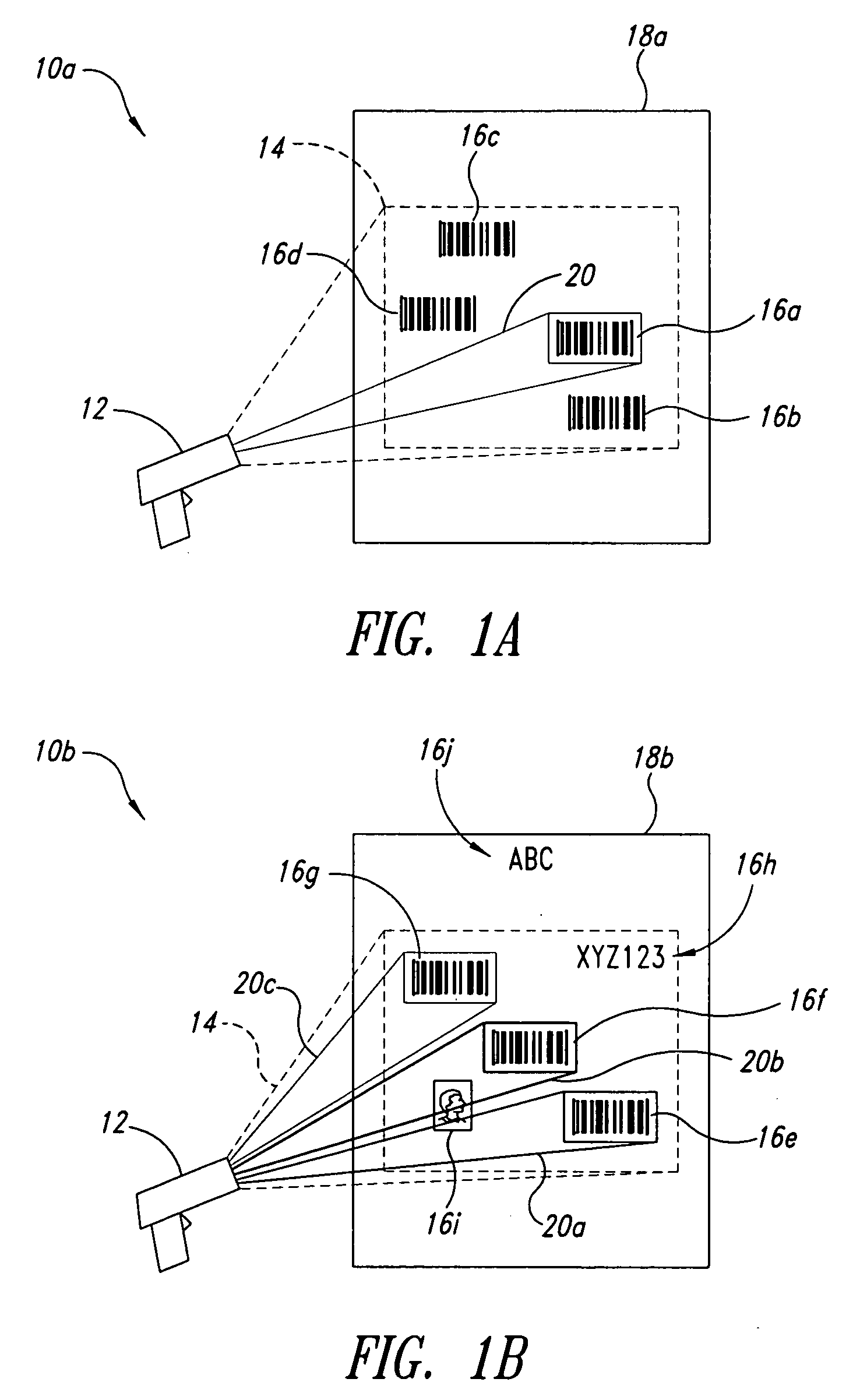
Methods, apparatuses and articles for automatic data collection devices, for example barcode readers, in cluttered environments
ActiveUS7392951B2Enhance the imageCharacter and pattern recognitionRecord carriers used with machinesSymbolic SystemsBarcode reader
Owner:INTERMEC IP CORP
Graphically manipulating a database
A method and system for managing a database through a graphical representation is presented. The method the method includes dynamically adjusting data in a database by graphically manipulating a graph that represents the database. In one embodiment, a predictive cone is overlaid onto the graph. The predictive cone is created from a heuristic algorithm that uses past historical data to predict where future real data will track on the graph.
Owner:IBM CORP
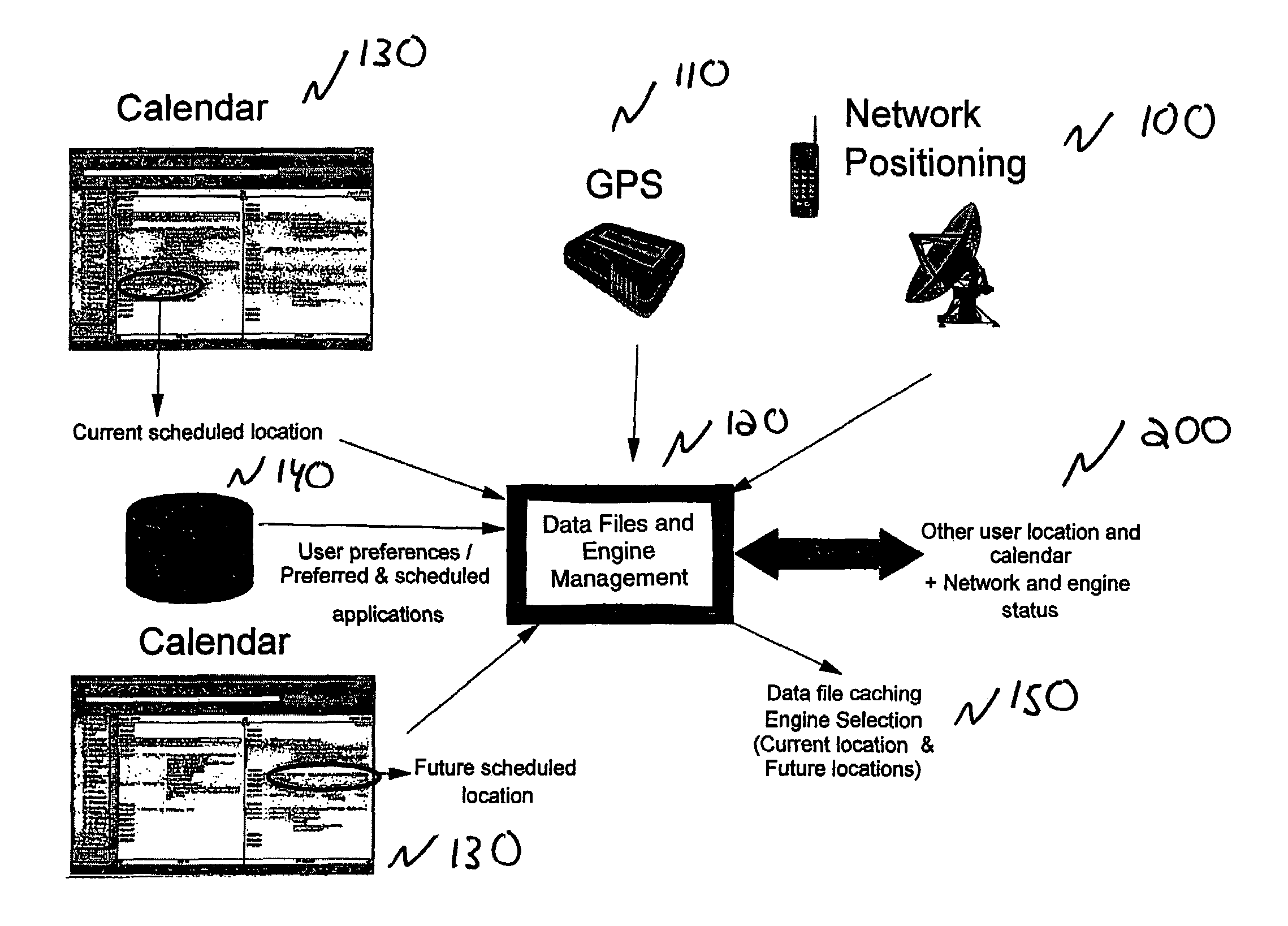
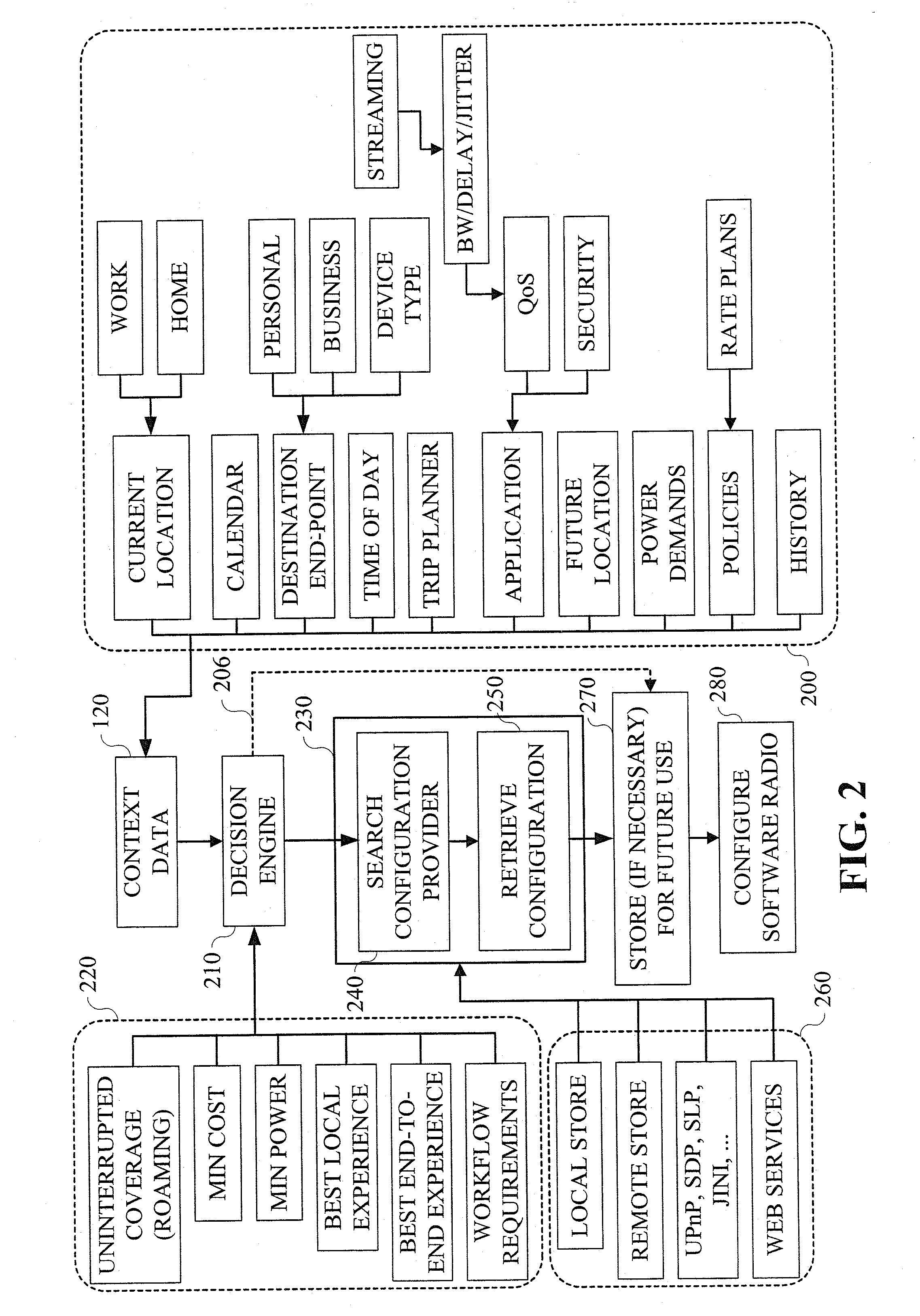
Method and apparatus for preconditioning mobile devices for network and other operations
ActiveUS20050130653A1Radio/inductive link selection arrangementsSubstation equipmentComputer hardwareQuality of service
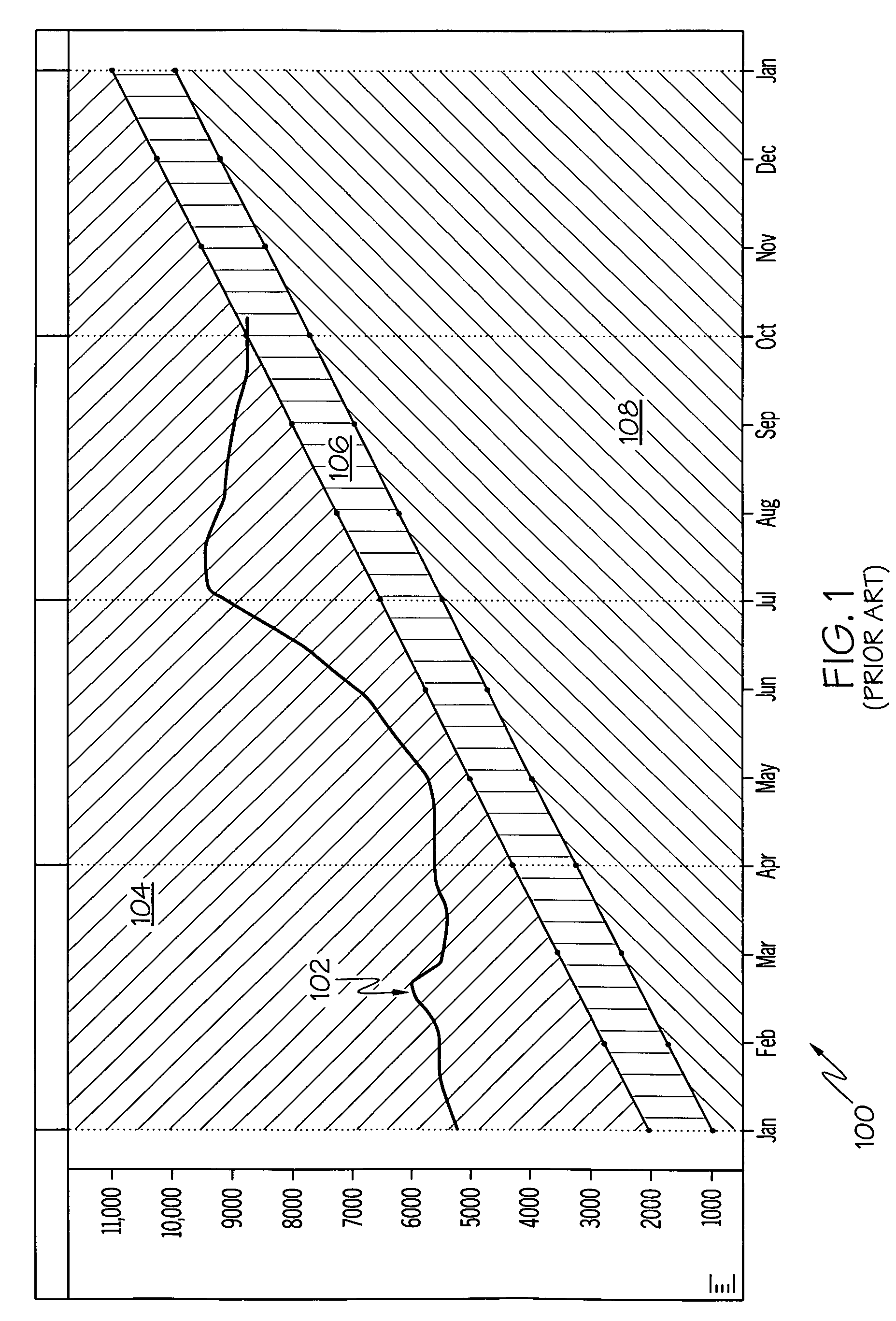
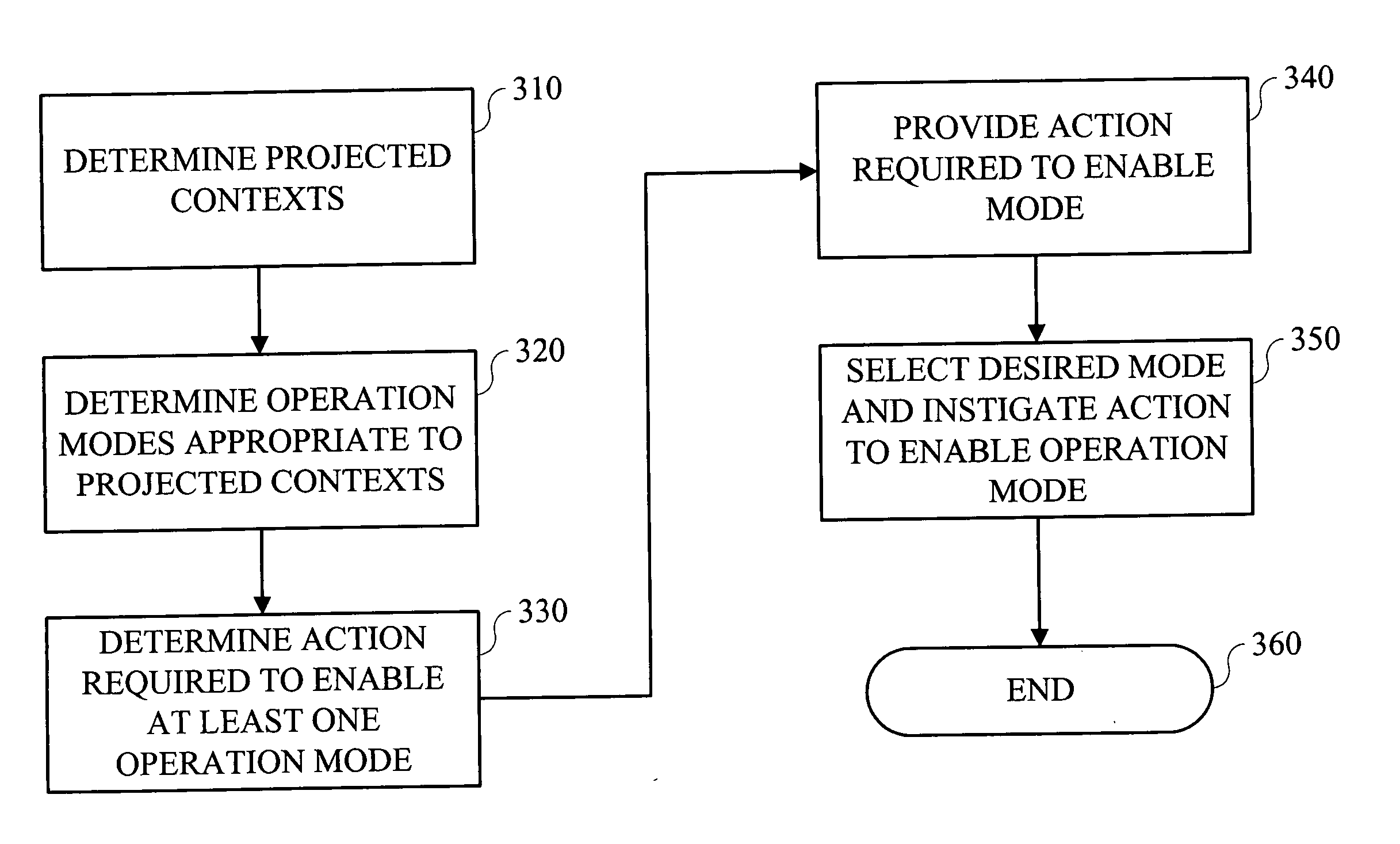
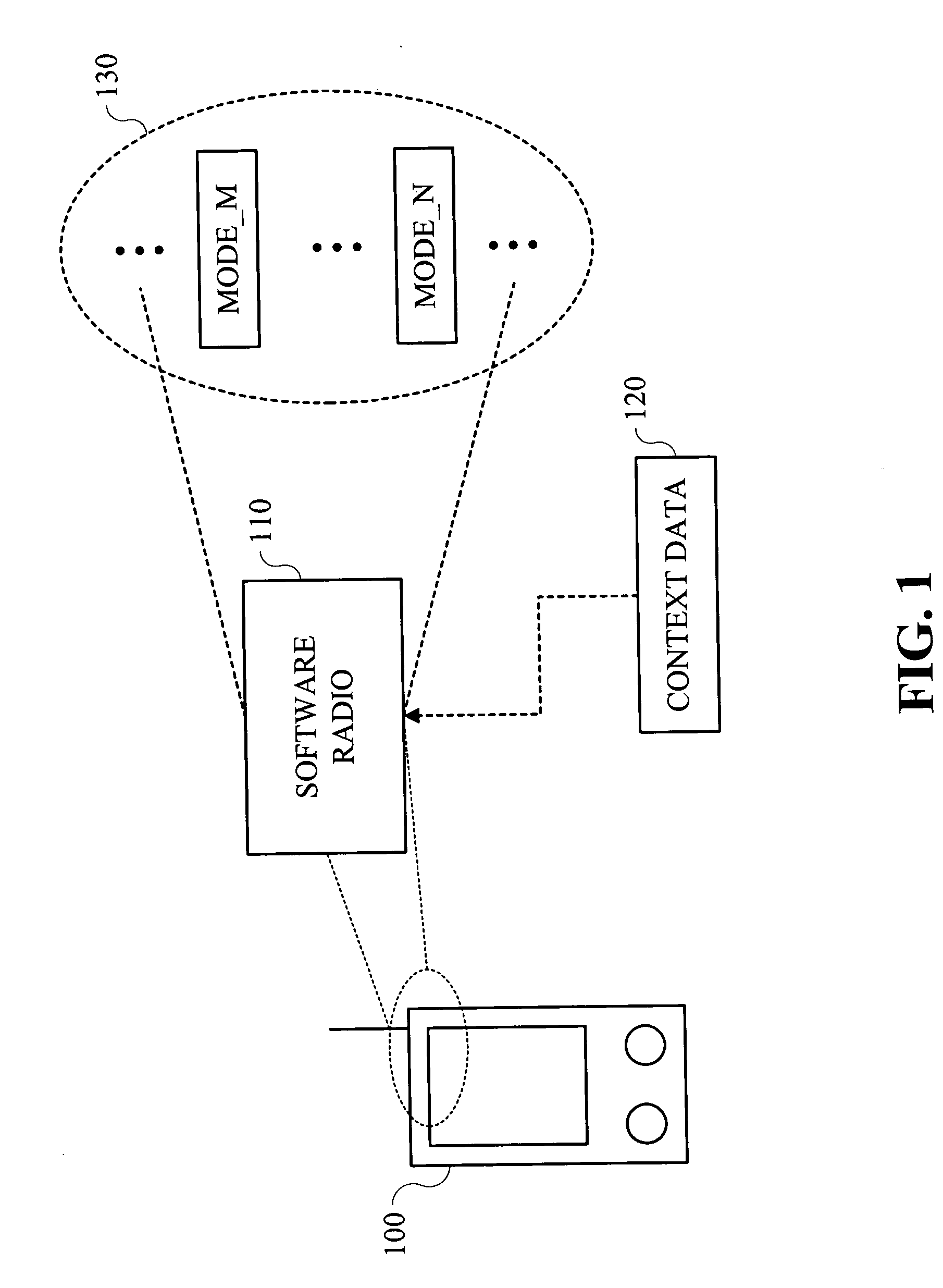
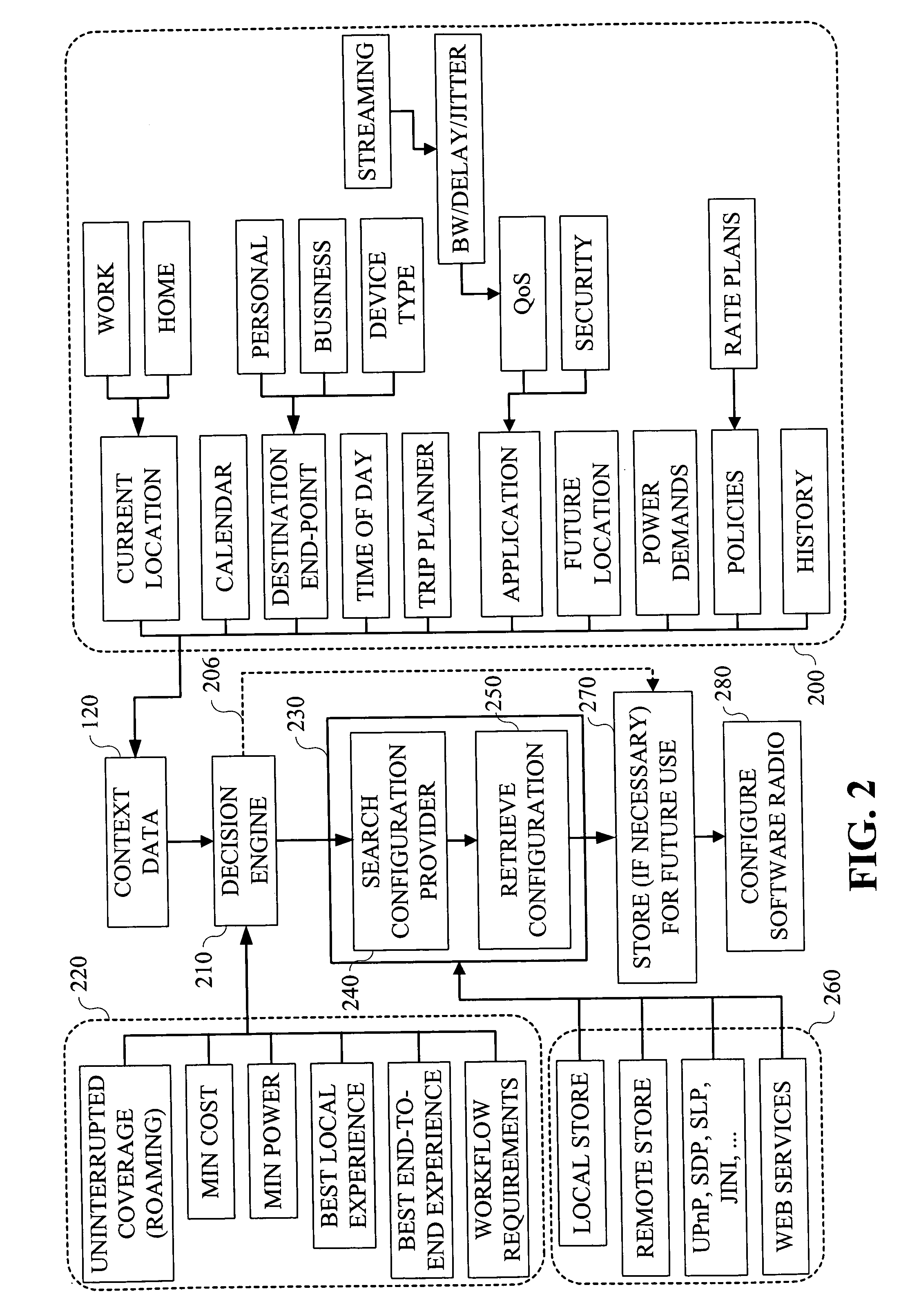
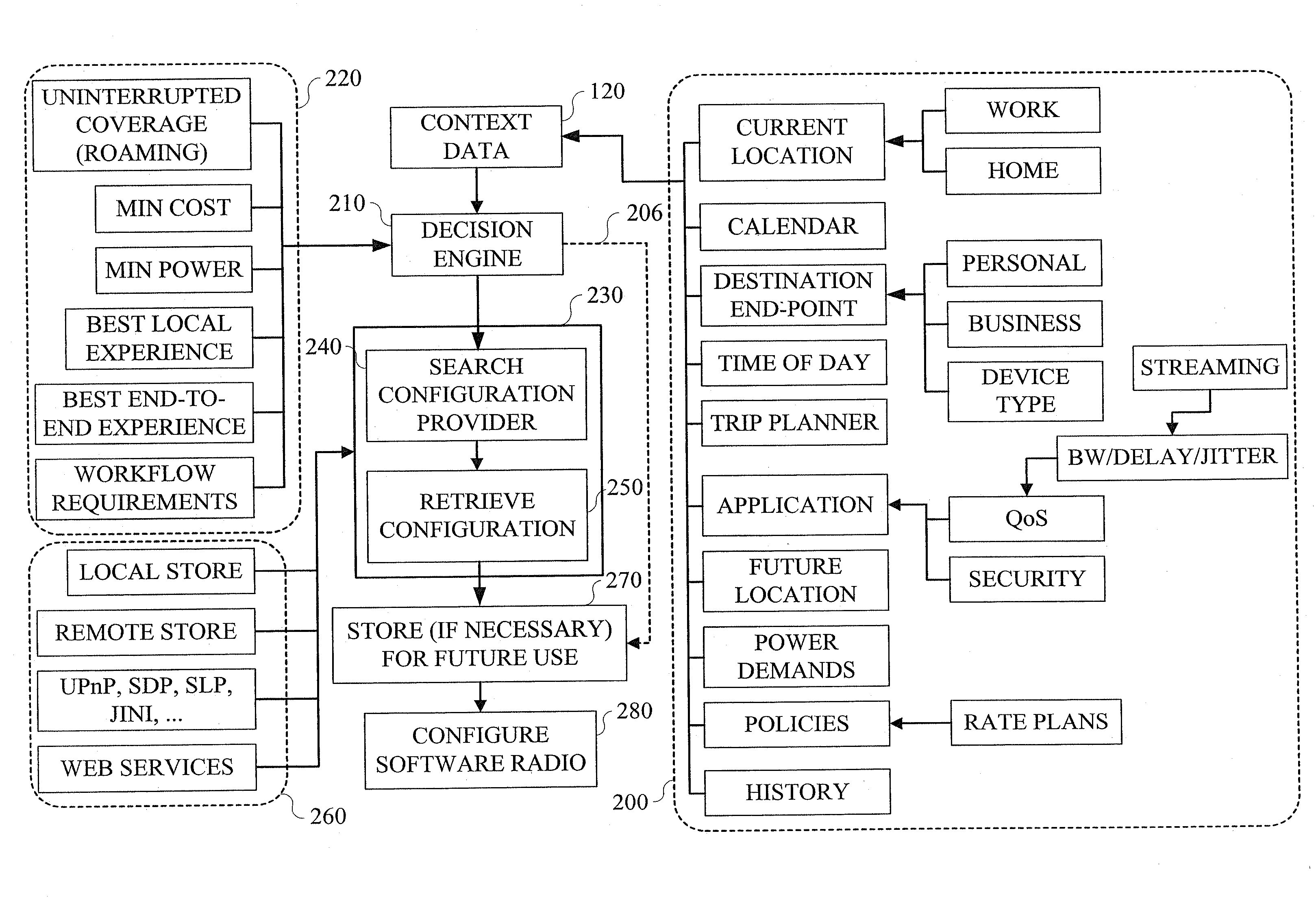
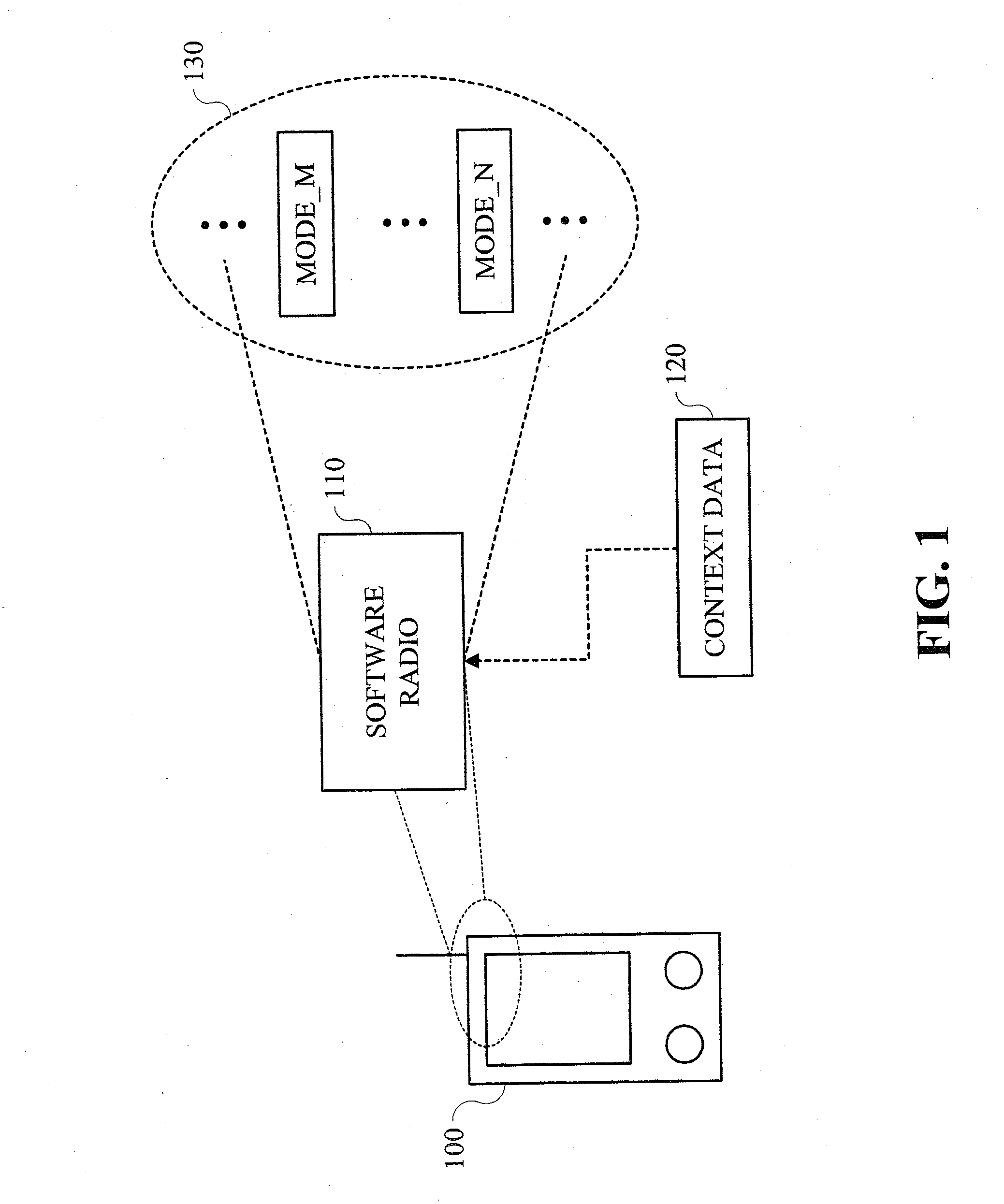
Techniques are provided for providing automated configuration of computing devices. More particularly, principles of the invention may use anticipated context to precondition a device whose operational mode is alterable via computer controllable operations. Anticipated context may be affected by any number of parameters including, but not limited to, current location, time of day, destination end-point, e.g., phone number to be called, past history, subscription rate plans, power requirements of device, application demands with respect to quality-of-service (QoS), security, calendar information, and so on. Further, principles of the invention may use locally derived knowledge about the intended use of a device and dynamically enable it in a desirable mode of operation using locally reachable configuration parameters stored in advance based on the anticipated context for the operation of the device. Still further, principles of the invention may dynamically locate necessary configuration parameters via a service discovery process.
Owner:DAEDALUS GRP LLC
System and process for providing an interactive, computer network-based, virtual team worksite
InactiveUS20060101022A1Chance is facilitatedEasy to implementOffice automationSpecial data processing applicationsWorkstationData store
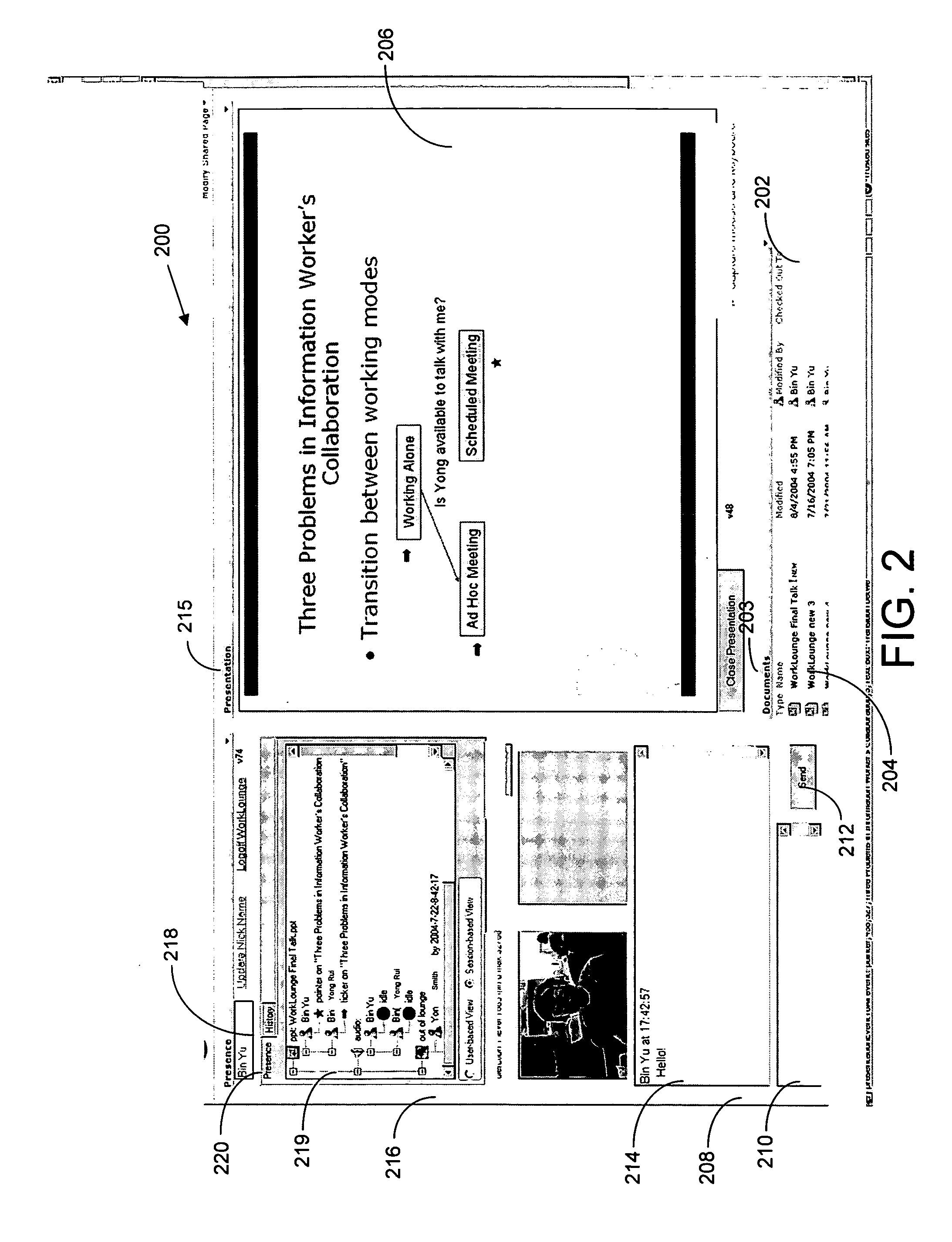
A system and process for providing an interactive computer network-based virtual team worksite that combines data storage, team members' presence information, interaction tools and a past history log into one virtual complex is presented. Generally, this is accomplished by integrating a shared data module, a unique presence module and various conferencing tools such as a collaborative presentation module and chat module into a single worksite assessable over a distributed computer network. Thus, everything a team would need related to a project is available in this integrated place. A team member who logs onto the worksite can input data and commands using the worksite window sectors to interface with other team members also logged on to the worksite and to interact with the displayed data in the collaborative presentation sector.
Owner:MICROSOFT TECH LICENSING LLC
Predictive blacklisting using implicit recommendation
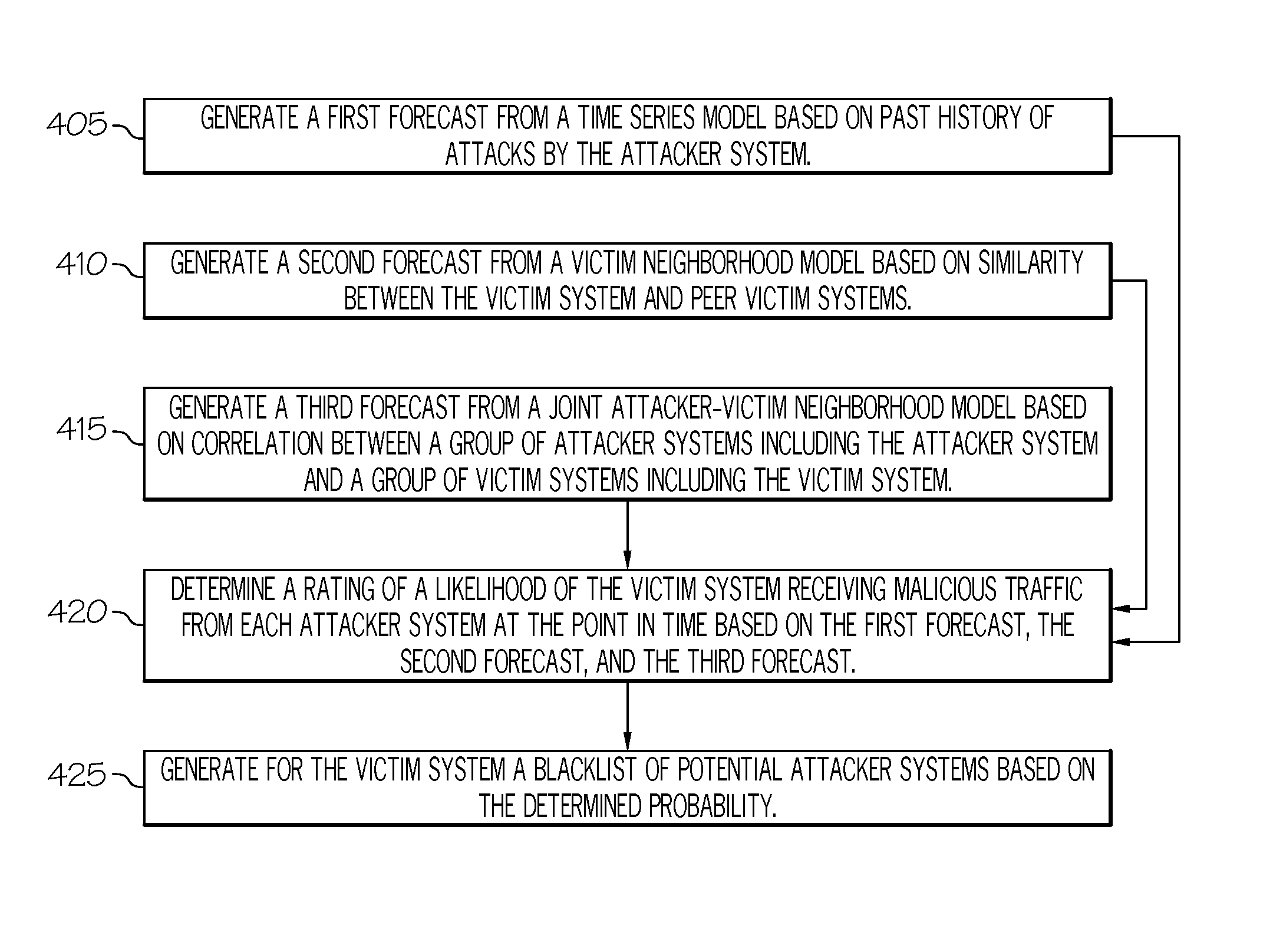
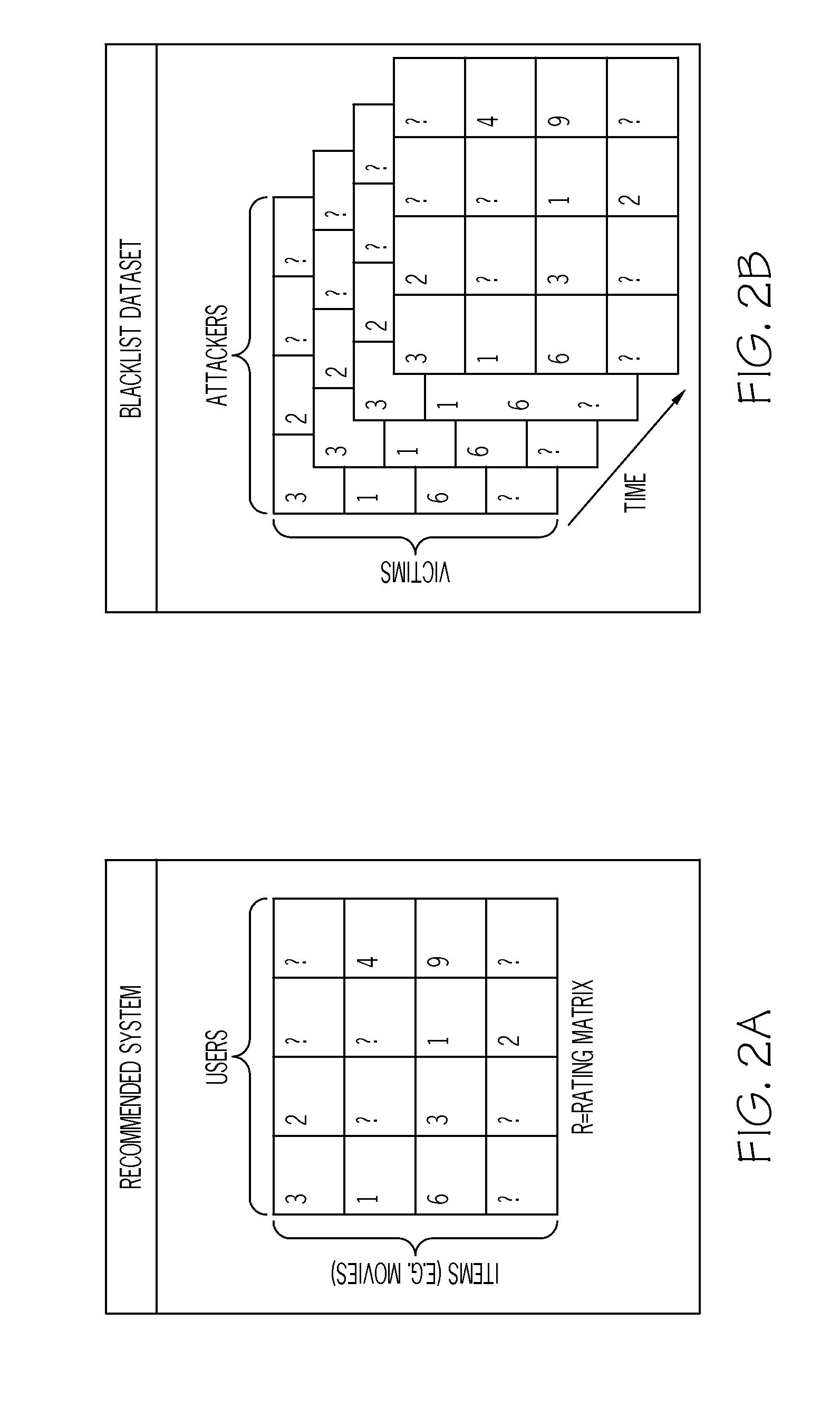
A method is provided for determining a rating of a likelihood of a victim system receiving malicious traffic from an attacker system at a point in time. The method comprises: generating a first forecast from a time series model based on past history of attacks by the attacker system; generating a second forecast from a victim neighborhood model based on similarity between the victim system and peer victim systems; generating a third forecast from a joint attacker-victim neighborhood model based on correlation between a group of attacker systems including the attacker system and a group of victim systems including the victim system; and determining the rating of the likelihood of the victim system receiving malicious traffic from the attacker system at the point in time based on the first forecast, the second forecast, and the third forecast.
Owner:RGT UNIV OF CALIFORNIA
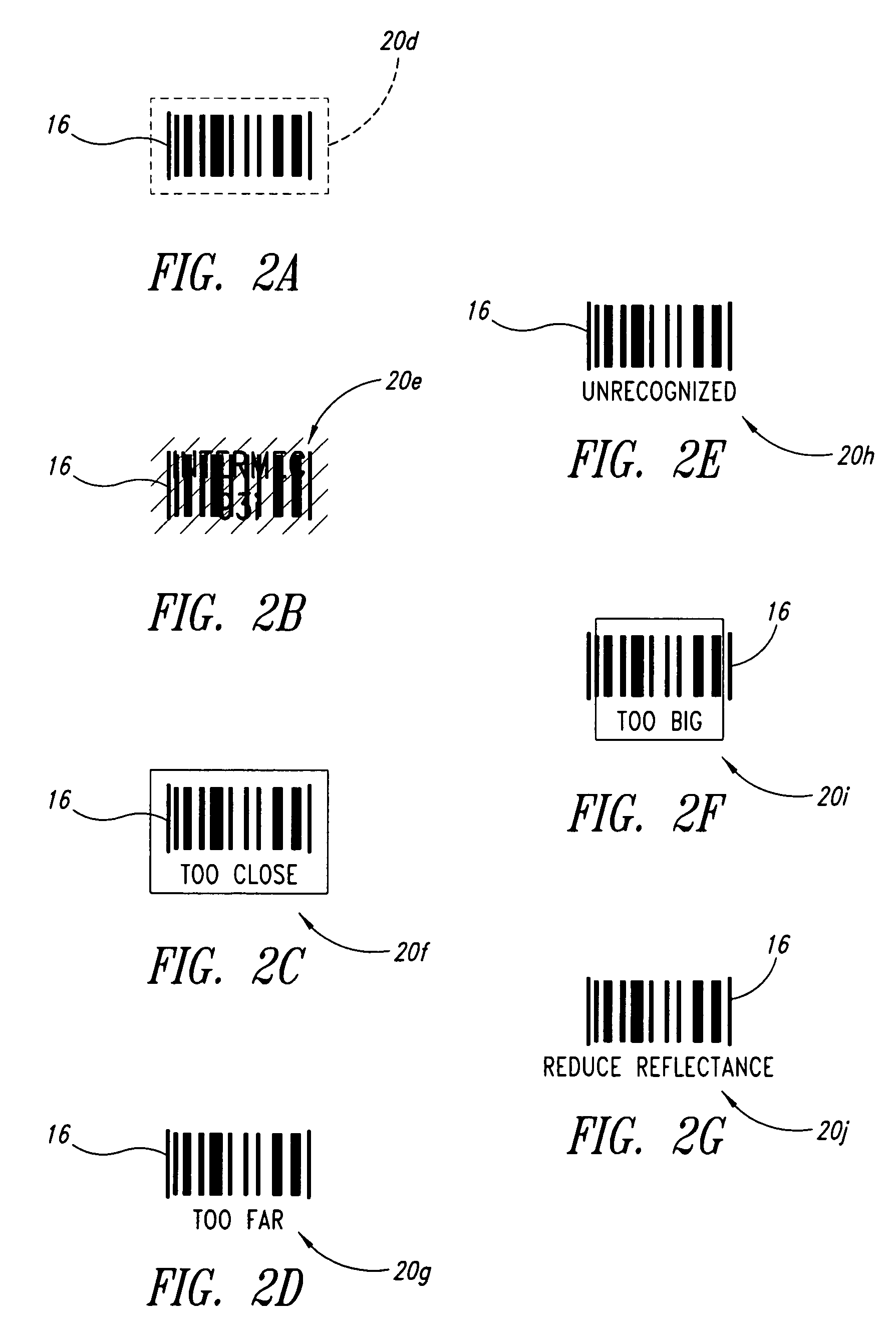
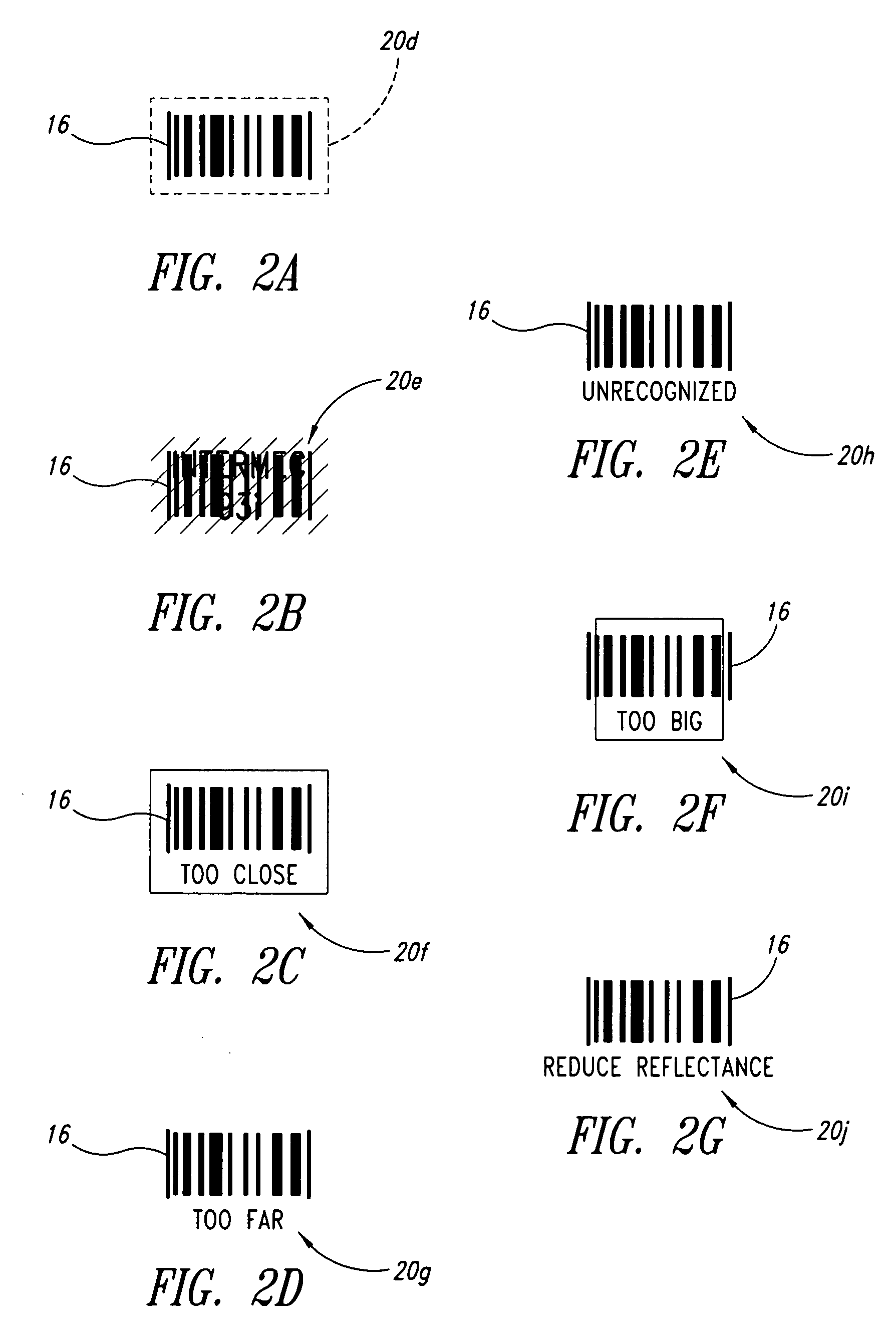
Methods, apparatuses and articles for automatic data collection devices, for example barcode readers, in cluttered environments
ActiveUS20060261167A1Convenient lightingEnhance resulting imageCharacter and pattern recognitionRecord carriers used with machinesSymbolic SystemsBarcode reader
A reader such as a barcode reader identifies at least one potential target such as a barcode symbol in its field-of-view, and projects or transmits an indicator toward or proximate the potential target containing information about the respective potential target. Such information may include which target is currently active, the symbology in which the target is encoded, the relative position of the reader with respect to the target, the ability of the reader to decode the target, and / or ranked or sorted order information regarding the target and neighboring targets. The reader may rank, sort, prioritize or otherwise determine order based on various parameters, including symbology, position in field-of-view, size, etc., and may base such on past history of the reader and / or user, and may weight such.
Owner:INTERMEC IP
Methods and systems for utilizing content, dynamic patterns, and/or relational information for data analysis
The present invention is directed generally to providing systems and methods for data analysis. More specifically, embodiments may provide system(s) and method(s) including dynamic user modeling techniques to capture the relational and dynamic patterns of information content and / or users' or entities' interests. Various embodiments may include system(s) and method(s) that are based on, for example, the past history of content semantics, temporal changes, and / or user community relationship. Various embodiments may include modeling and / or analysis of the dynamic nature of an item of interest's value to a user(s) / entity(ies) over time. The dynamic factors may be consider in any manner, such as, individually or combined, sequentially or simultaneously, etc. Further, some embodiments may include, for example, system(s) and method(s) relating to analyzing data to capture user / entity interests and / or characteristics, consider content semantics and evolutionary information, and / or using community relationships of users / entities to thereby analyze information and provide dynamic conclusion(s) (e.g., recommendation(s)).
Owner:NEC CORP
Large venue security method
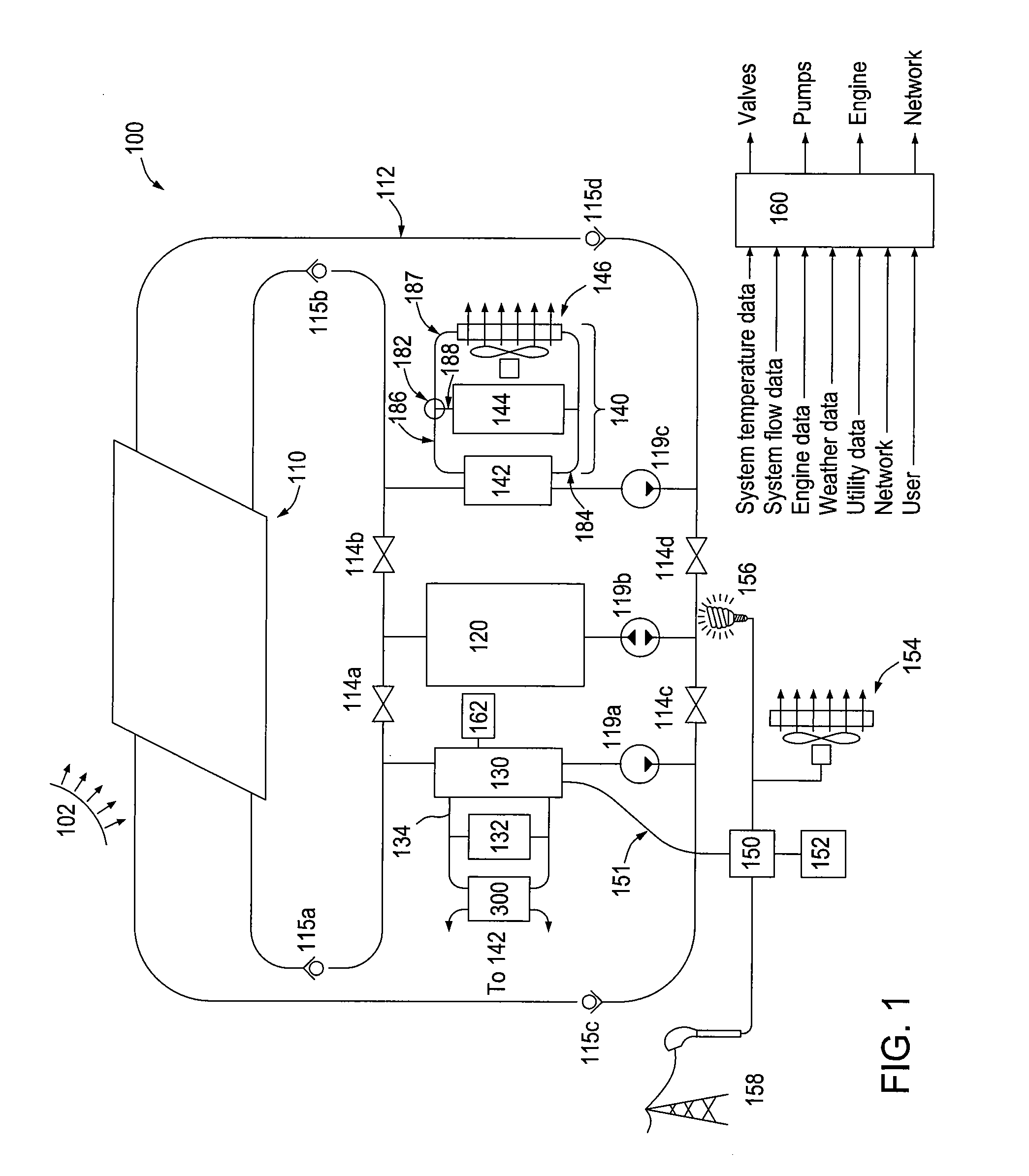
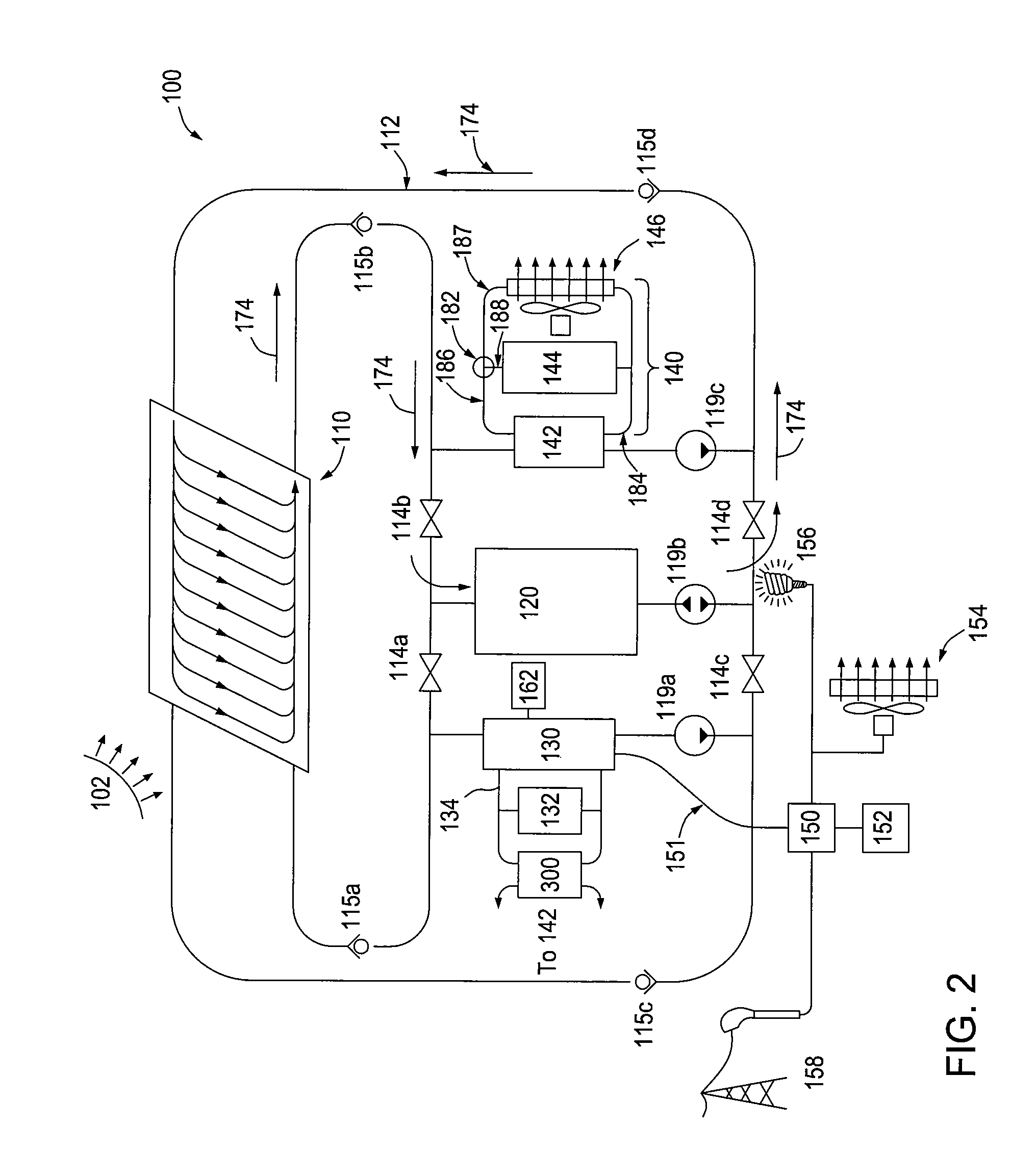
ActiveUS8792677B2Enhance the imageReducing violent actsElectric signal transmission systemsImage analysisParking areaComputer vision
A method for reducing violence within crowded venues includes reading license plates of vehicles passing into entry ports of a parking area, and capturing facial images of persons seeking admission to the venue. A computer compares such license plates to a database of vehicle license plates associated with persons with past histories of violence. A computer also compares captured facial images to a database of facial data for persons with past violent histories. Upon detecting a match, the computer creates an alert presented to law enforcement officers at the venue to facilitate detention of such persons for investigation. Information recorded on entry tickets is scanned and saved together with the facial image of the ticket holder. If a violent act occurs, cameras within the venue capture facial images of participants. The computer matches such participants to stored identifying data to assist in the identification and apprehension of such persons.
Owner:KEPHART CONSULTING LLC
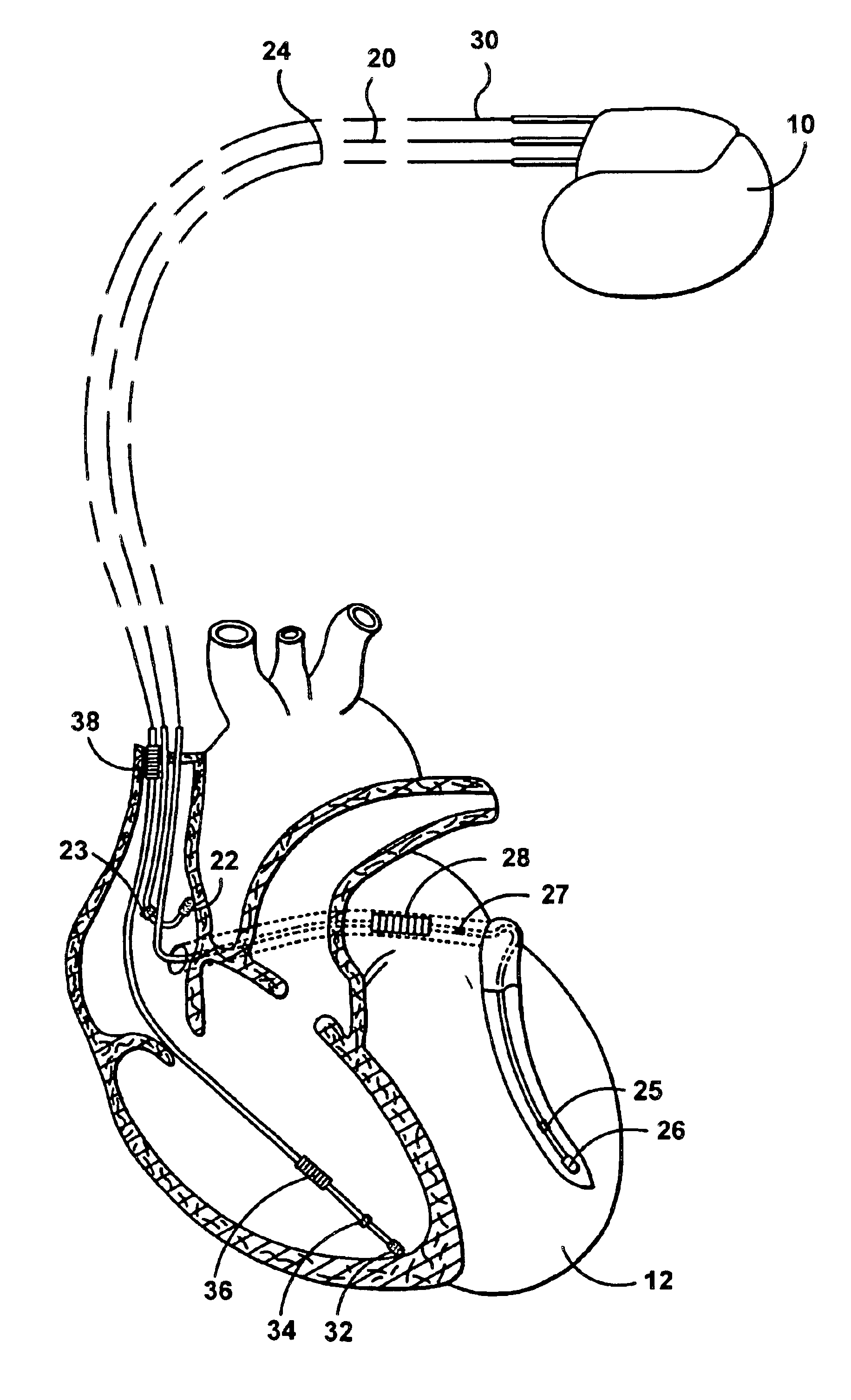
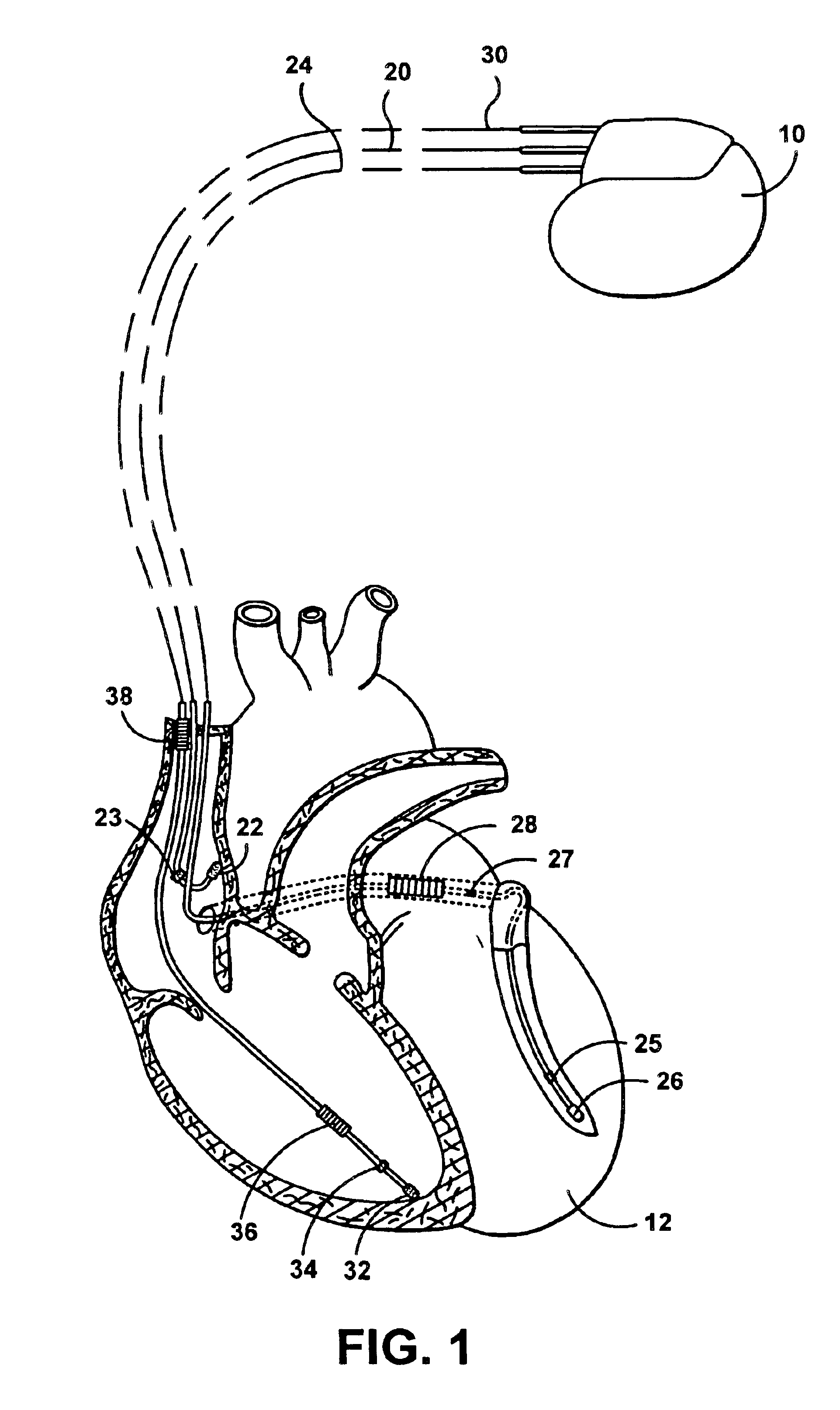
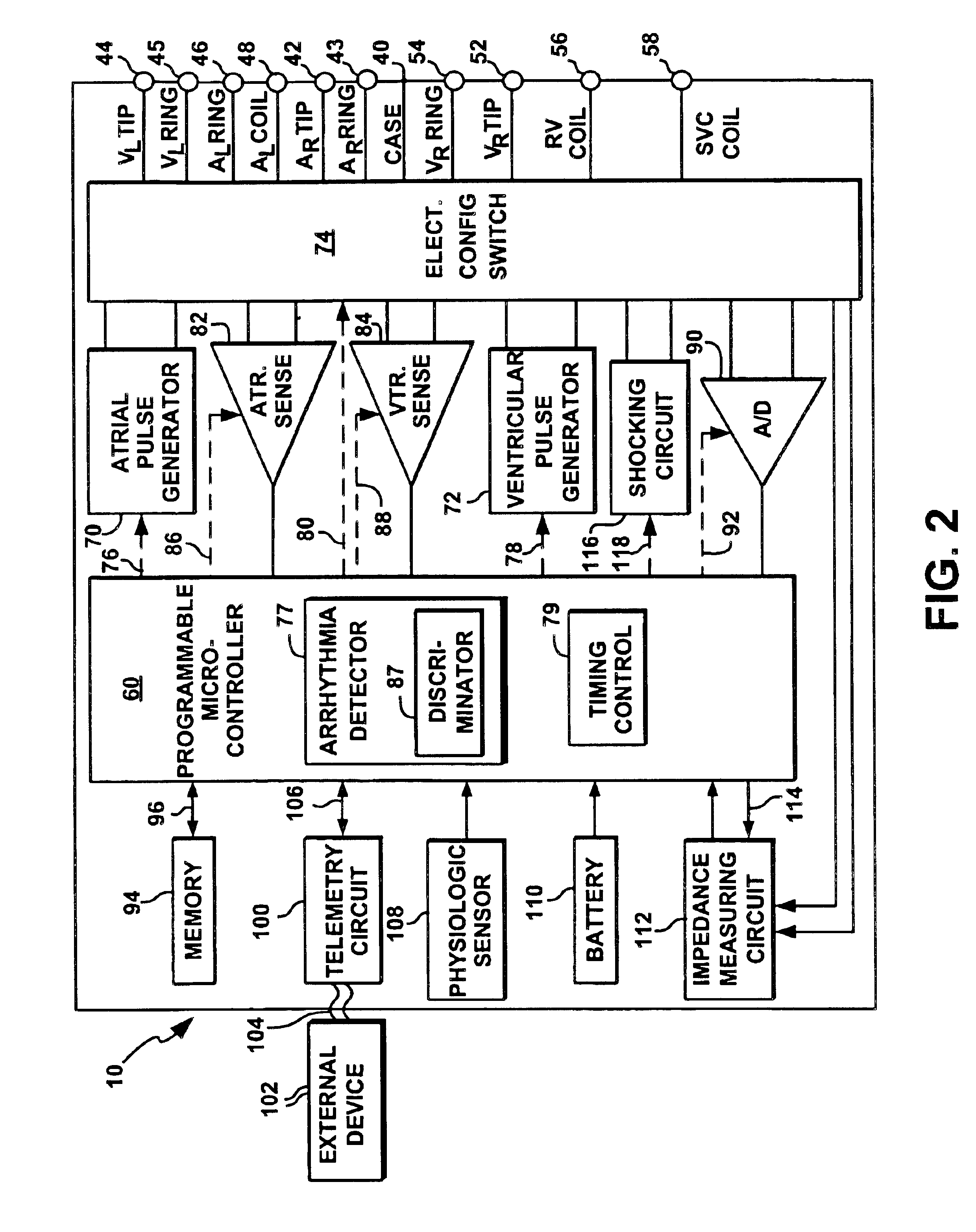
Apparatus and method for automatically sensing threshold histogram with differentiation of sinus from ectopic beats
An implantable programmable cardiac stimulation device and associated method for differentiating between normal sinus events and ectopic beats. The stimulation device monitors the sensing thresholds of sinus and non-sinus cardiac events, and stores a history of these sensing thresholds along with temporal data for accurate event detection. The stimulation device further provides accurate and appropriate detection of sensed events including P-waves, non-conducted PACs, and conducted PACs and thus verifies correct detection of PVCs and R-waves. Furthermore, the present invention provides a history record of ectopic events, distinguished by sensing thresholds and timing intervals, giving a valuable diagnostic tool to the physician in optimizing rhythm management therapy. In addition, the stimulation device allows the sensitivity threshold to be set based on a single cardiac cycle and past history.
Owner:PACESETTER INC
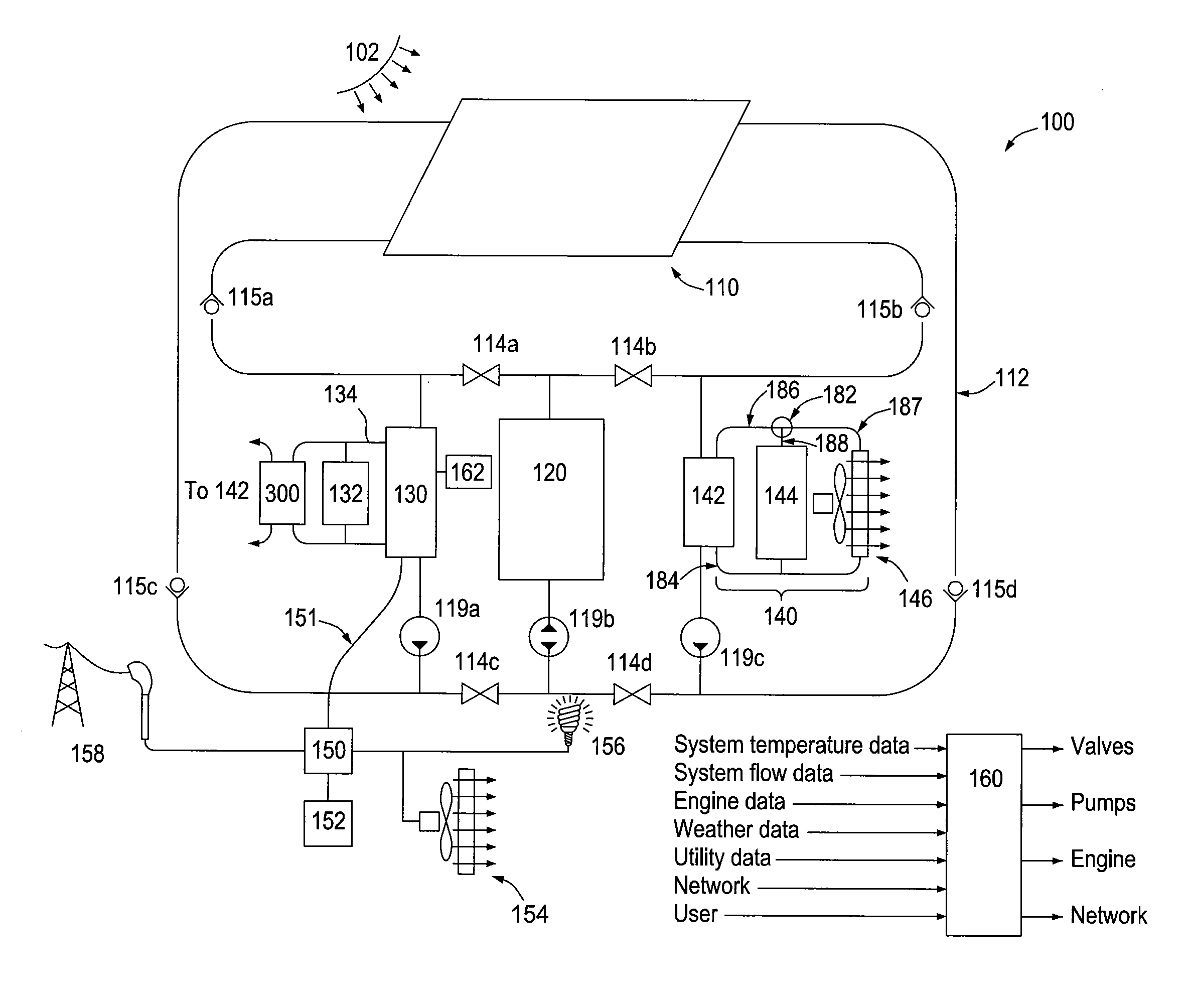
Control of power generation system having thermal energy and thermodynamic engine components
ActiveUS20110030753A1More cost-effectiveMore efficientSolar heating energyThermoelectric device with peltier/seeback effectThermal energyOperation mode
A thermal source provides heat to a heat engine and or one or more thermal demands, including space and water heating and heat storage. Additionally the output of the heat engine may be used for local in situ electricity needs, or directed out over the grid. A system controller monitors conditions of the components of the system, and operates that system in modes that maximize a particular benefit, such as a total accrued desired benefit obtained such as reduced electricity cost, reduced fossil fuel use, maximized return on investment and other factors. The controller may use past history of use of the system to optimize the next mode of operation, or both past and future events such as predicted solar insolation.
Owner:COOL ENERGY
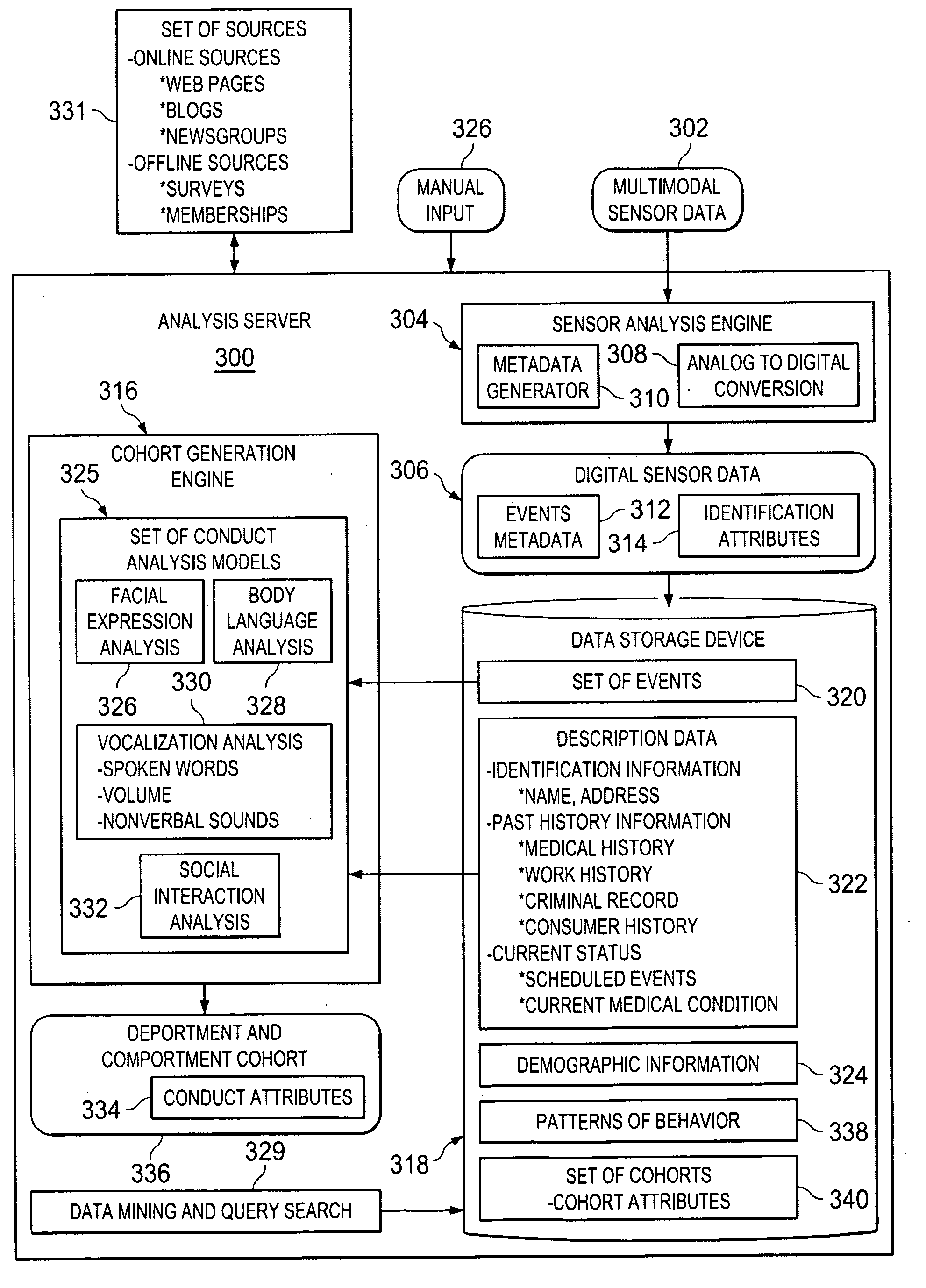
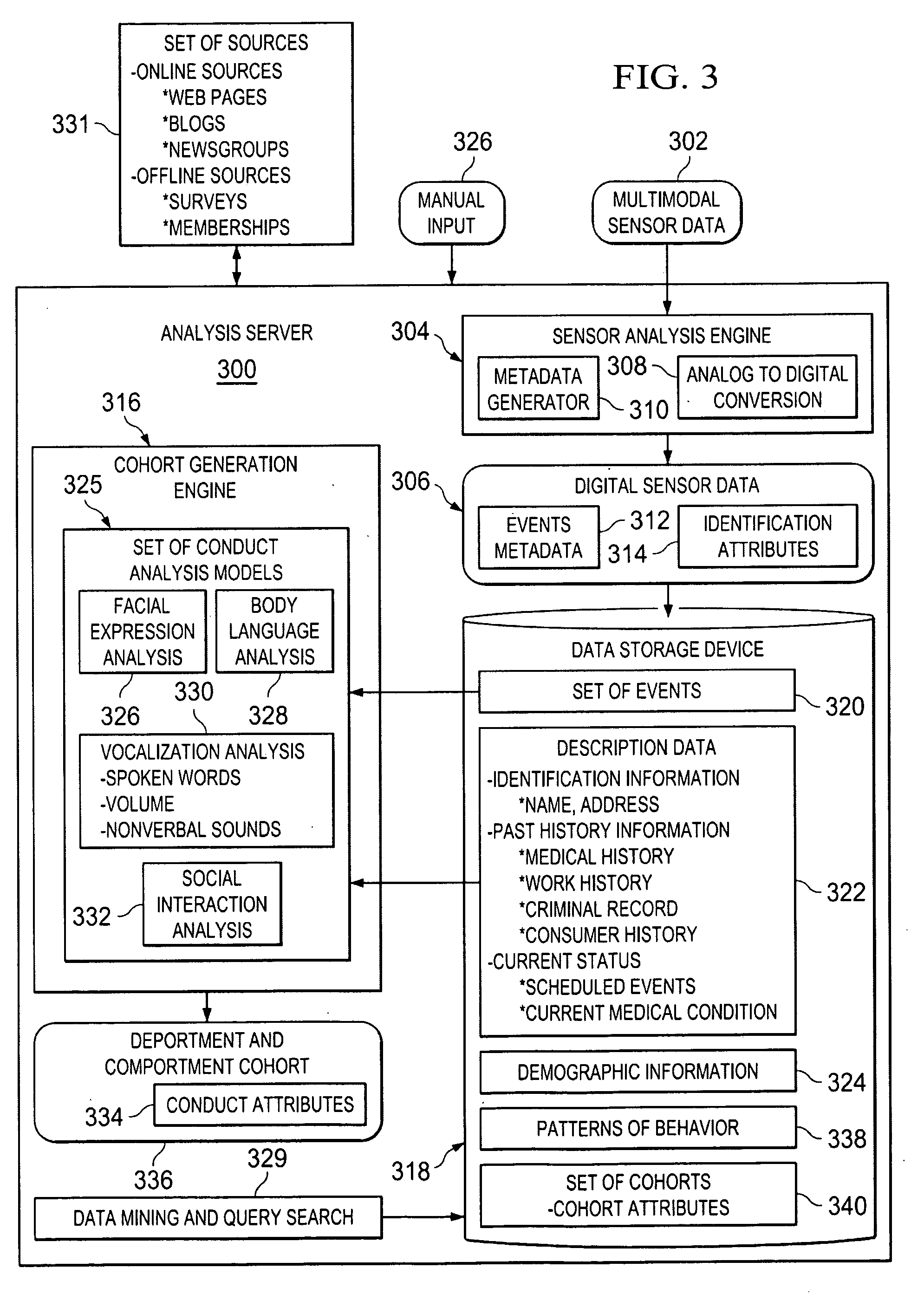
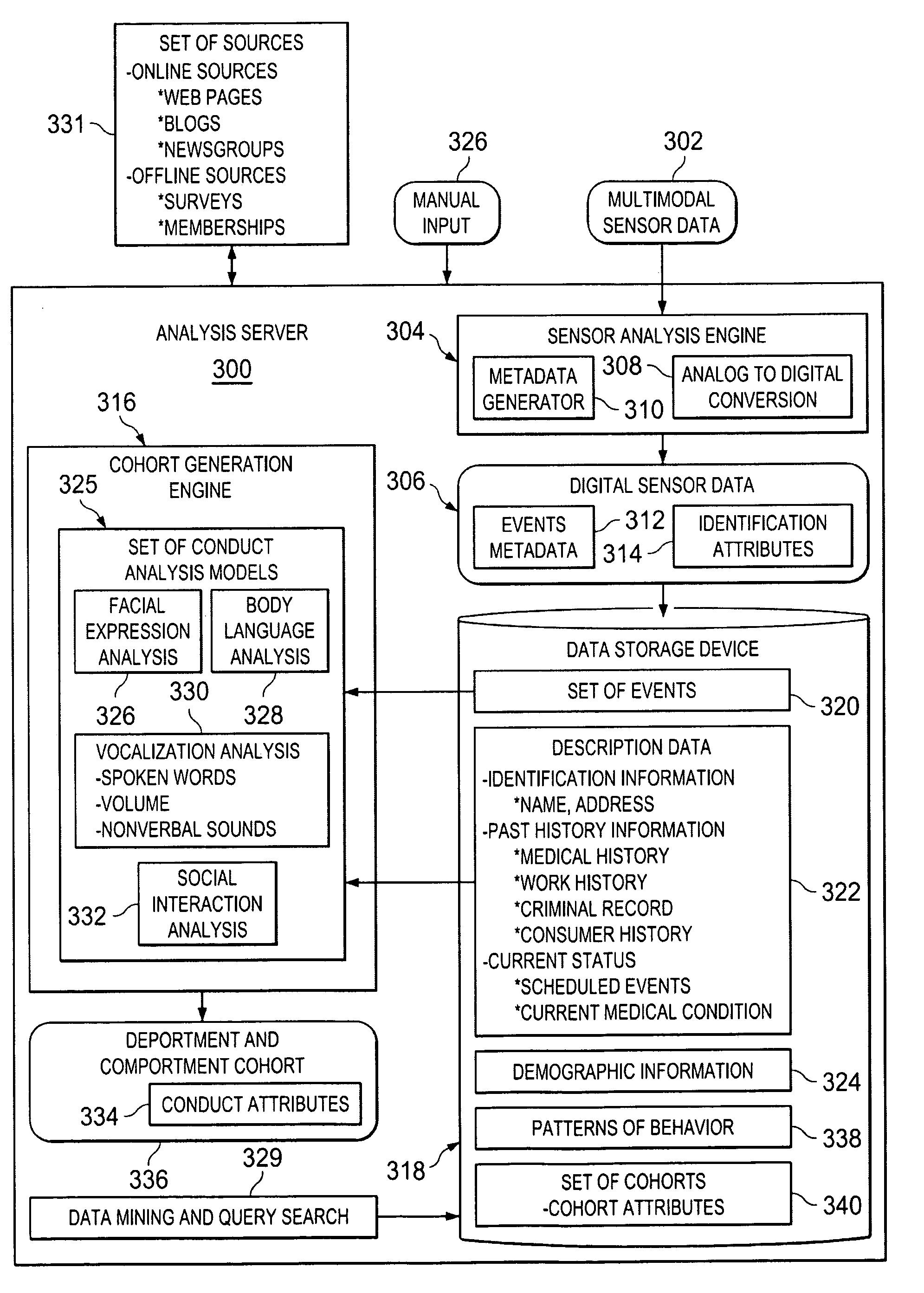
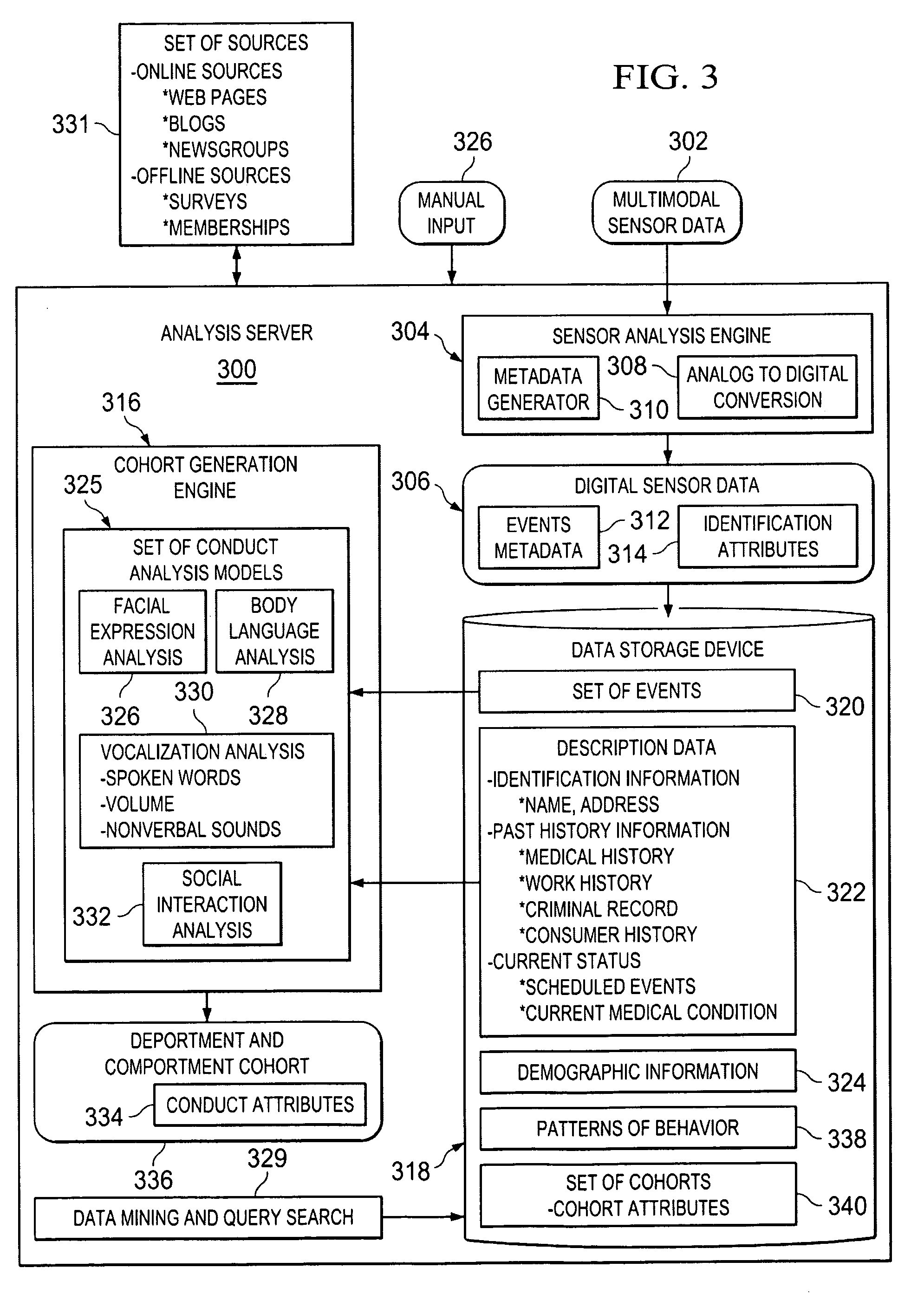
Generating Deportment and Comportment Cohorts
ActiveUS20100148970A1Digital data processing detailsComputer-assisted medical data acquisitionFacial expressionDigital sensors
A computer implemented method, apparatus, and computer program product for generating deportment and comportment cohorts. Digital sensor data associated with an individual is received. The digital sensor data comprises event metadata describing a set of events associated with the individual. The set of events comprises at least one of body language, facial expressions, vocalizations, and social interactions of the individual. In response to determining description data for the individual is available, the description data is retrieved. The description data comprises at least one of identification information, past history information, and current status information for the individual. A set of conduct analysis models based on the event metadata and the available description data is selected. The set of conduct analysis models process the event metadata describing the set of events associated with the individual to identify and interpret the set of events. The event metadata and the description data is analyzed in the set of conduct analysis models to form a deportment and comportment cohort. The deportment and comportment cohort comprises attributes identifying a demeanor and manner of the individual.
Owner:IBM CORP
Generating deportment and comportment cohorts
ActiveUS8493216B2Digital data processing detailsComputer-assisted medical data acquisitionFacial expressionDigital sensors
A computer implemented method, apparatus, and computer program product for generating deportment and comportment cohorts. Digital sensor data associated with an individual is received. The digital sensor data comprises event metadata describing a set of events associated with the individual. The set of events comprises at least one of body language, facial expressions, vocalizations, and social interactions of the individual. In response to determining description data for the individual is available, the description data is retrieved. The description data comprises at least one of identification information, past history information, and current status information for the individual. A set of conduct analysis models based on the event metadata and the available description data is selected. The set of conduct analysis models process the event metadata describing the set of events associated with the individual to identify and interpret the set of events. The event metadata and the description data is analyzed in the set of conduct analysis models to form a deportment and comportment cohort. The deportment and comportment cohort comprises attributes identifying a demeanor and manner of the individual.
Owner:INT BUSINESS MASCH CORP
Resource configuration in multi-modal distributed computing systems
A method and system for configuring available resources in real-time to automatically accommodate the needs of the system user in multi-modal distributed computing system is disclosed. Information about the location or environment of a wireless device is used, preferably in combination with user personal preferences and past history to modify the behavior of the wireless device, including the selection of the most appropriate mode of interaction with the device and the activation of applications thereon as appropriate.
Owner:GOOGLE LLC
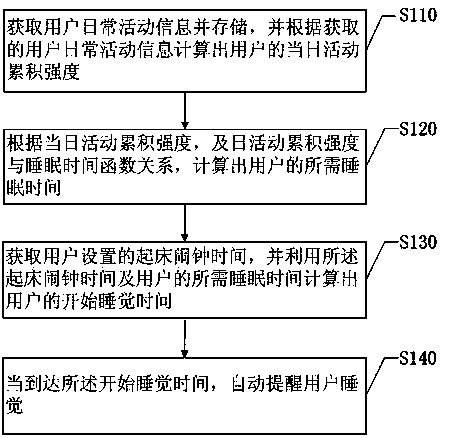
Method and system for automatically reminding users to go to bed and wearable device
Owner:北京神州互联科技股份有限公司
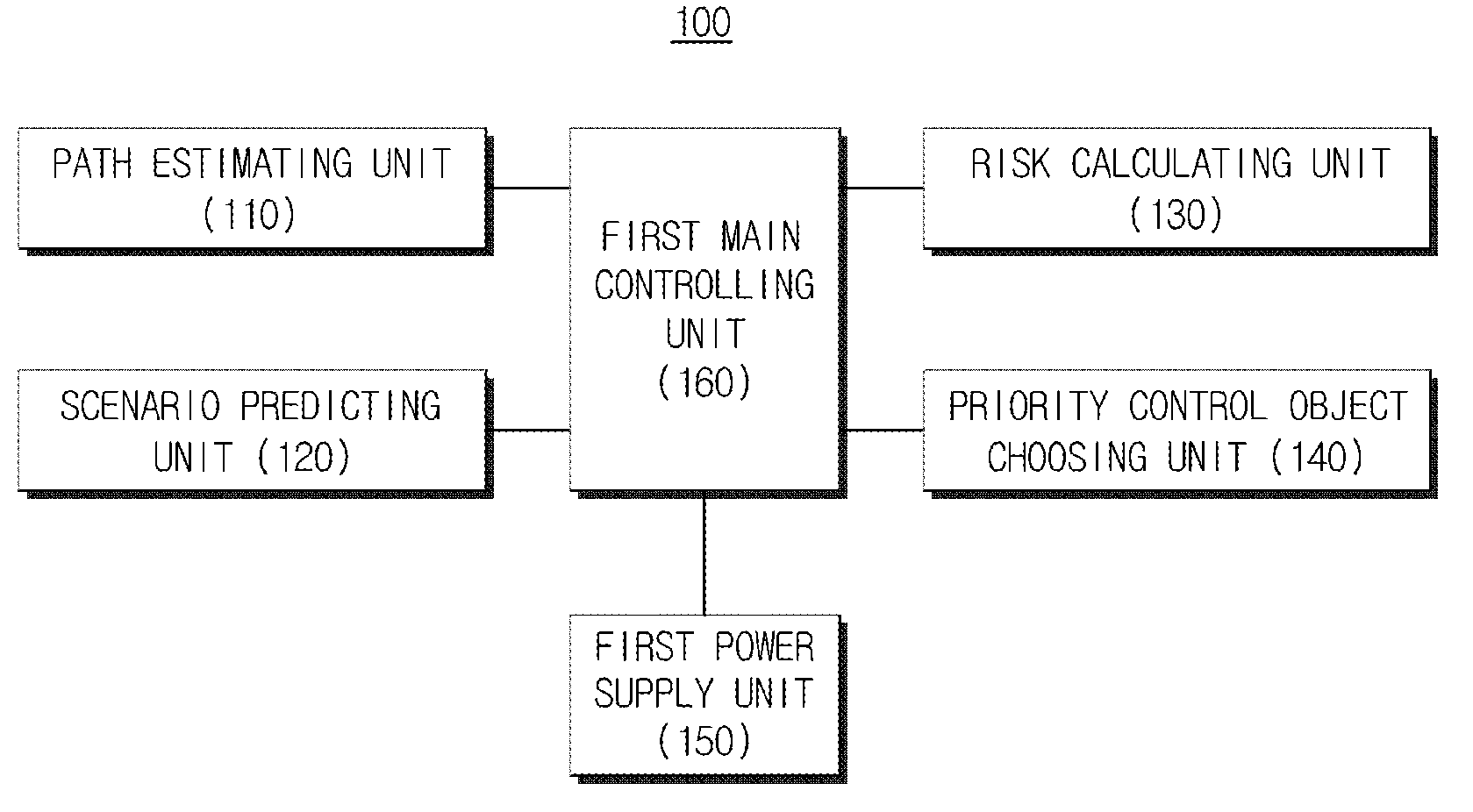
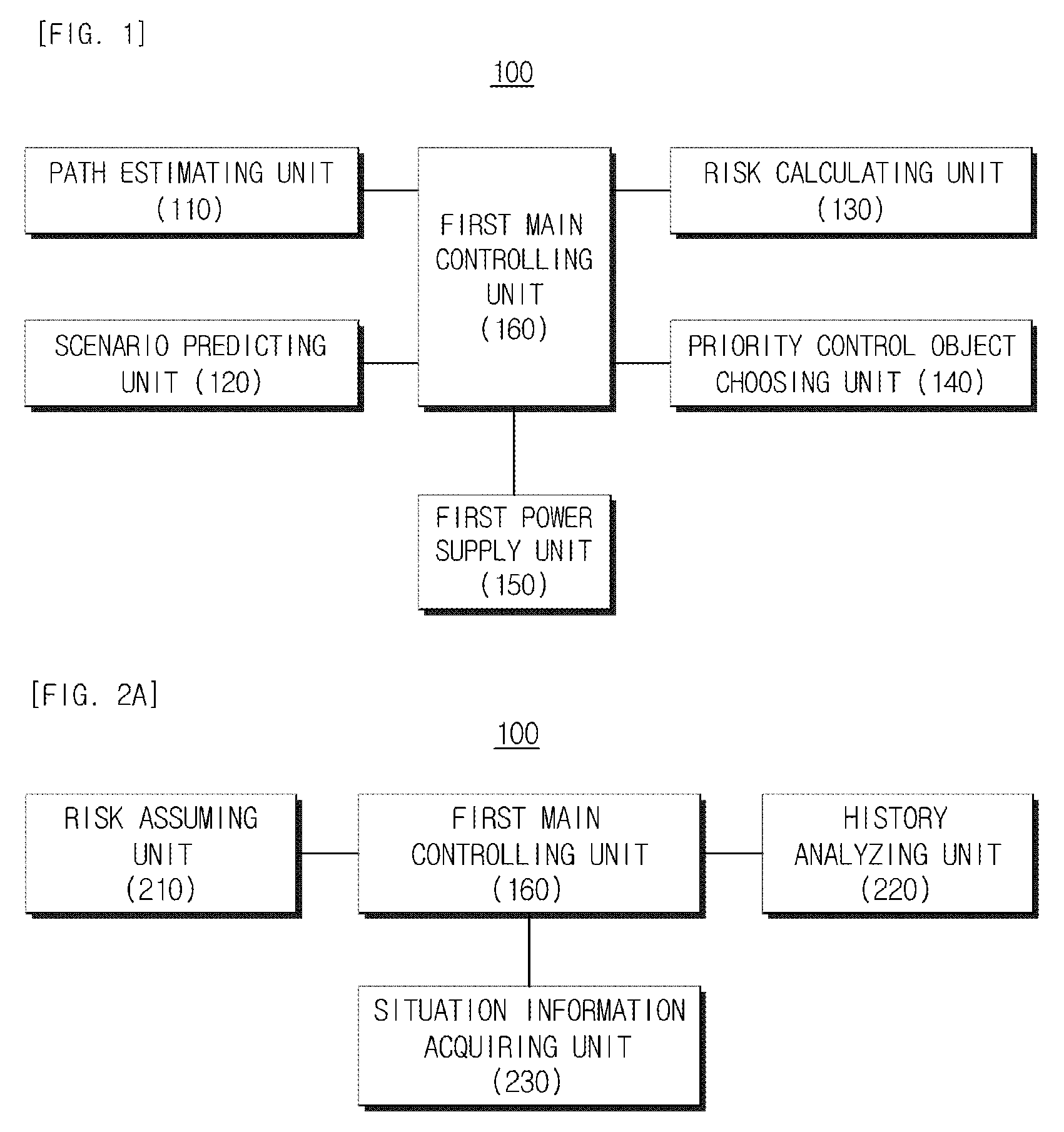
Apparatus and method for choosing priority control object, and apparatus for controlling object
ActiveUS20120271538A1Easy to controlAvoid accidentsAnalogue computers for vehiclesAnalogue computers for trafficEngineeringTime trajectory
Provided are an apparatus and a method that chooses an object to be preferentially controlled based on an accident risk degree and hazard and controls the chosen object. In the present invention, it is possible to choose and control a ship having high hazard calculated with trajectory prediction, current operation state information, and past history information under a traffic situation in which the ships are concentrated, by priority. The ship having high hazard is chosen by calculating and applying various history information including an accident record, an entry history of an operator, an aging degree history of the ship, and a steering feature history by using a collision risk on a real-time trajectory collision risk and past history information and different warnings are given during a control for each level.
Owner:ELECTRONICS & TELECOMM RES INST
Attached personal information device
InactiveUS20060059013A1Data processing applicationsPatient personal data managementHuman bodyTransceiver
An information storage device may be semi-permanently attached to a wearer. The device can include an outer casing configured to be compatible with long term contact with a human body. A data storage component may store information of the wearer and a transceiver may wirelessly communicate information from the data storage component. The stored information can be, for example, the complete medical history of the wearer, “emergency” medical information, prescriptions, medical warnings (e.g., past history of coronary problems), financial information, social security numbers, or other useful information.
Owner:LOWE JOHN C
Method of controlling avatars
ActiveUS20120131478A1Increase probabilityEnhanced interactionData processing applicationsInput/output processes for data processingViewpointsVirtual world
A method of controlling the position and orientation of user controlled computer generated avatars in computer generated virtual world in a manner that tends to bias the user controlled avatar positions and orientations in a way that sends useful non-verbal social cues to outside observers. These non-verbal cues can include cues such as “this conversation is open to outside participants” and “this conversation is private”. The methods can also convey “stage presence” to that can somewhat bias the position and orientation of the user controlled avatars in a manner that takes the viewpoint of an outside observer into account. These effects can be modulated up or down as desired, and may be further modulated by the degree of social connections or past history of virtual world interactions between various users.
Owner:PLAYSTUDIOS US LLC
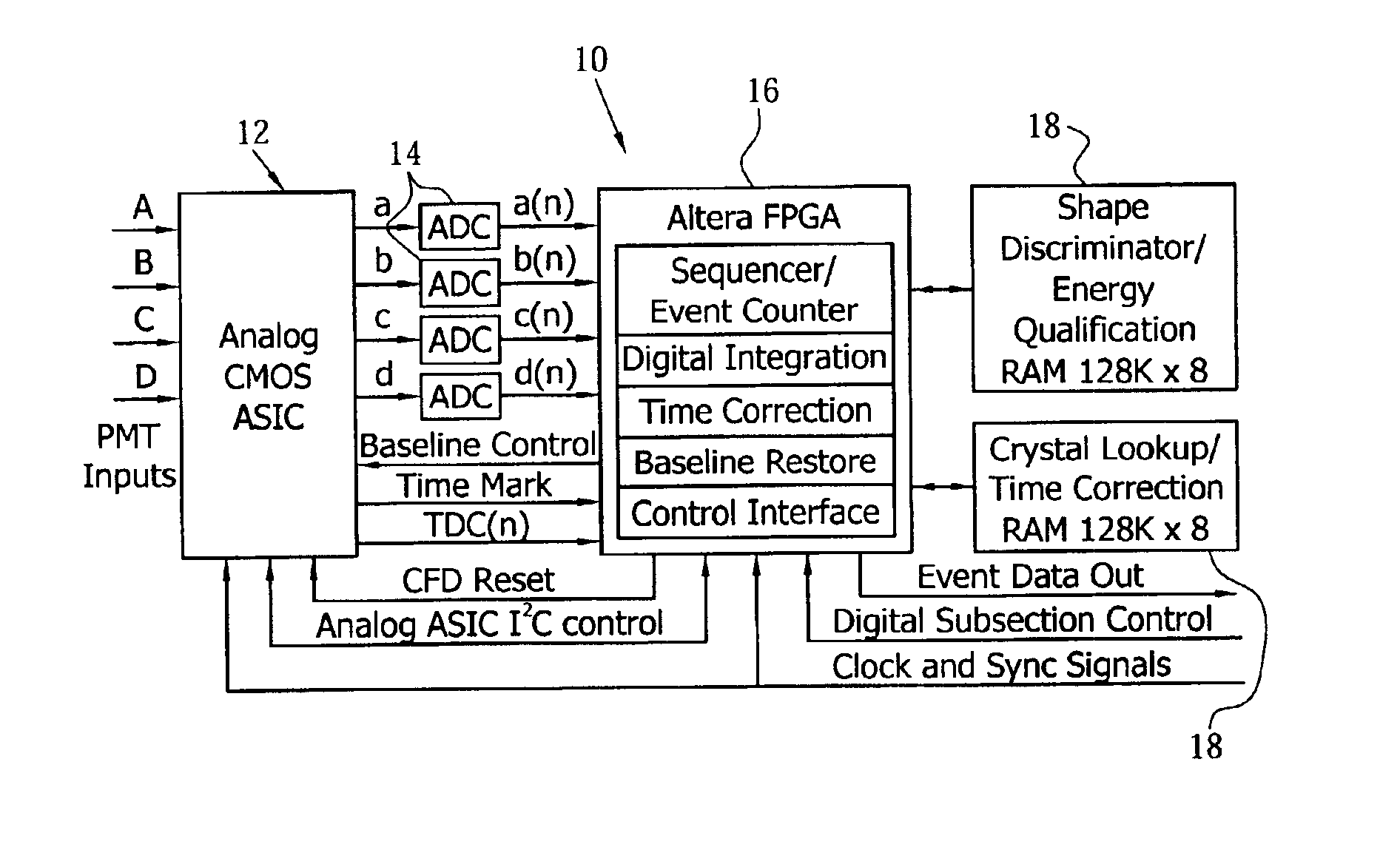
Baseline correction in PET utilizing continuous sampling ADCs to compensate for DC and count rate errors
ActiveUS6903344B2Low costImprove performanceMaterial analysis by optical meansTomographyCounting rateNegative feedback
A method and apparatus for determining and correcting the baseline of a continuously sampled signal for use in positron emission tomography. The method employs continuous signal sampling to determine the signal level at time t(0) so that an accurate determination of an integrated signal may be calculated, resulting in an accurate energy estimate for an ac-coupled, continuously-sampled signal at various count rates. The device includes a front-end electronics processing channel including primarily an analog CMOS ASIC, a bank of ADCs, an FPGA-based digital sequencer, and two RAMs. The processing electronics perform continuous digital integration of PMT signals to obtain normalized position and energy. Continuous baseline restoration (BLR) is used, wherein the baseline of the signal pulses are placed at mid-scale by continuously sampling the ADC, thus always making available the past history. A correction signal is generated for use in negative feedback control of the baseline.
Owner:SIEMENS MEDICAL SOLUTIONS USA INC
Method and Apparatus for Preconditioning Mobile Devices for Network and Other Operations
Techniques are provided for providing automated configuration of computing devices. More particularly, principles of the invention may use anticipated context to precondition a device whose operational mode is alterable via computer controllable operations. Anticipated context may be affected by any number of parameters including, but not limited to, current location, time of day, destination end-point, e.g., phone number to be called, past history, subscription rate plans, power requirements of device, application demands with respect to quality-of-service (QoS), security, calendar information, and so on. Further, principles of the invention may use locally derived knowledge about the intended use of a device and dynamically enable it in a desirable mode of operation using locally reachable configuration parameters stored in advance based on the anticipated context for the operation of the device. Still further, principles of the invention may dynamically locate necessary configuration parameters via a service discovery process.
Owner:INT BUSINESS MASCH CORP
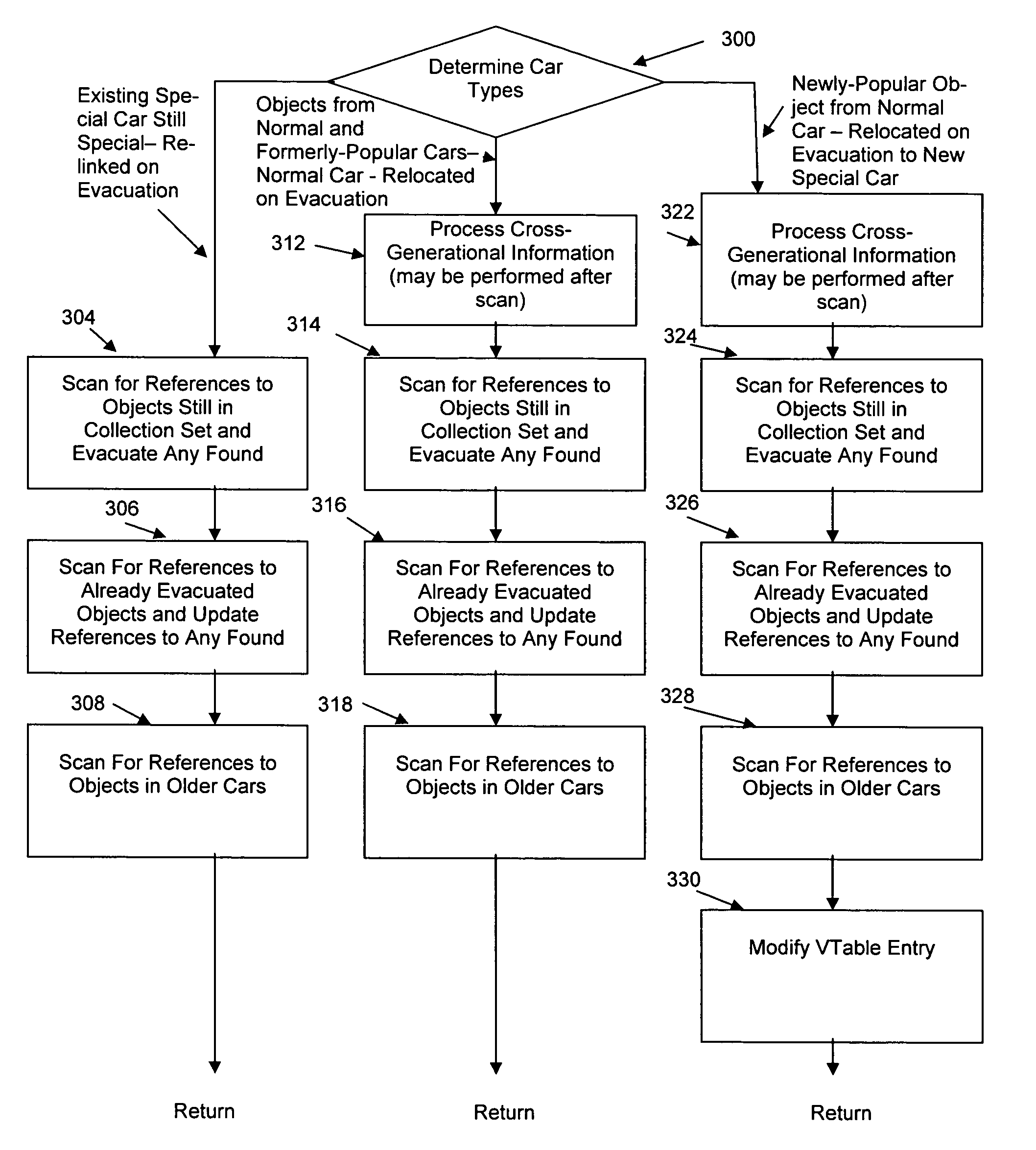
Scanning of evacuated objects in a generation managed by the train algorithm
ActiveUS7676801B1Improve scanning efficiencyImprove recording efficiencyComputer security arrangementsSpecific program execution arrangementsCombined useWaste collection
In computer systems including memory which execute programs of instructions, vtables associated with objects contain pointers which invoke operations to be performed by the program which are related to the objects. The operation invoked may include the step of modifying the pointer such that upon a subsequent reference to the vtable a different operation is invoked. In one embodiment, such vtables are utilized in conjunction with garbage collection methodologies such as those that invoke the train algorithm, such that operations such as reference processing, insertion and scanning during garbage collection may be invoked by pointers in vtables associated with cars or objects in the cars, and the vtables may invoke differing versions of the said operations depending on the characteristics and past history of the car or object, and upon an operation being executed the operation may change the pointer so that a different version of the operation is performed upon a subsequent reference to the vtable associated with the car or object.
Owner:ORACLE INT CORP
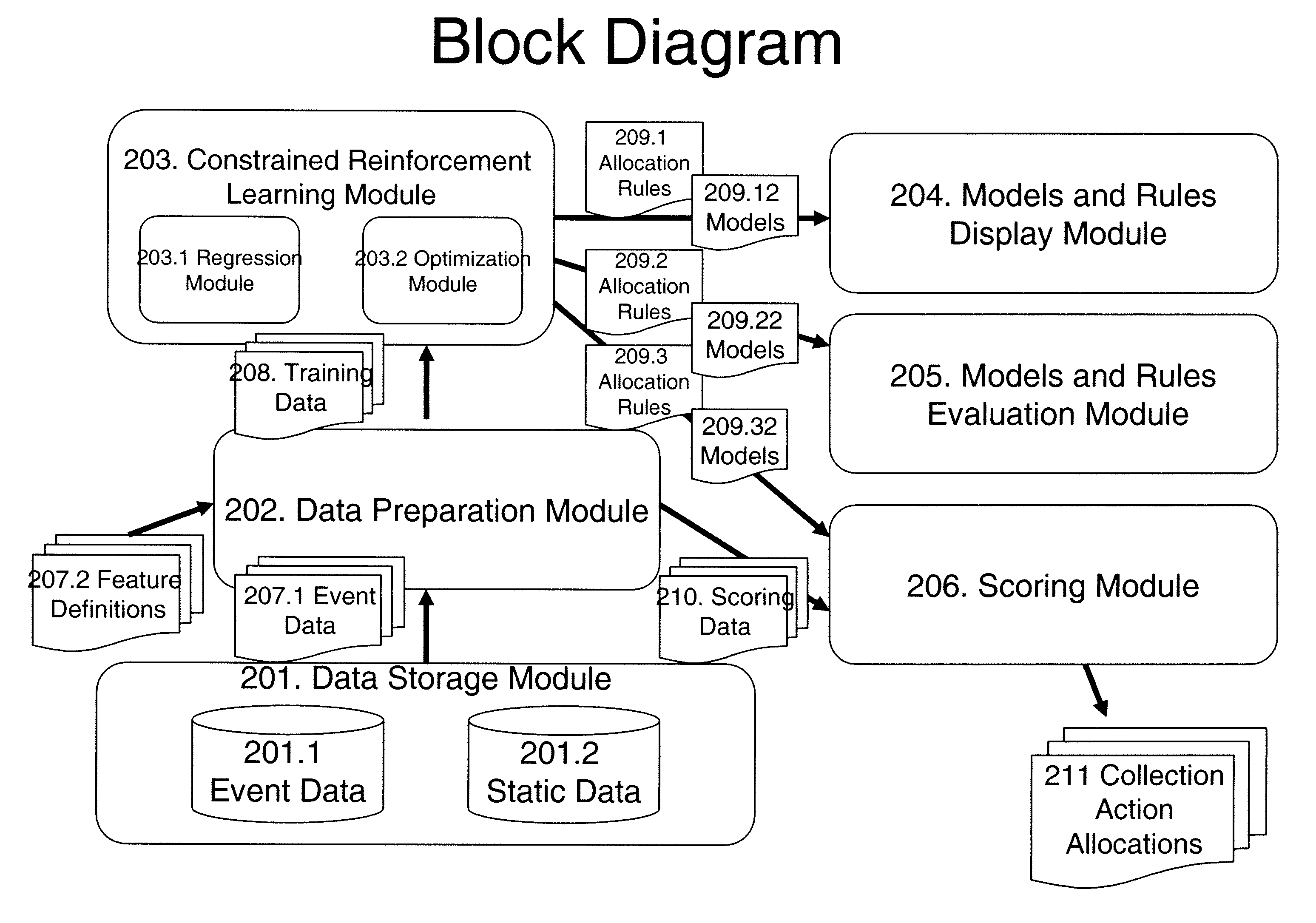
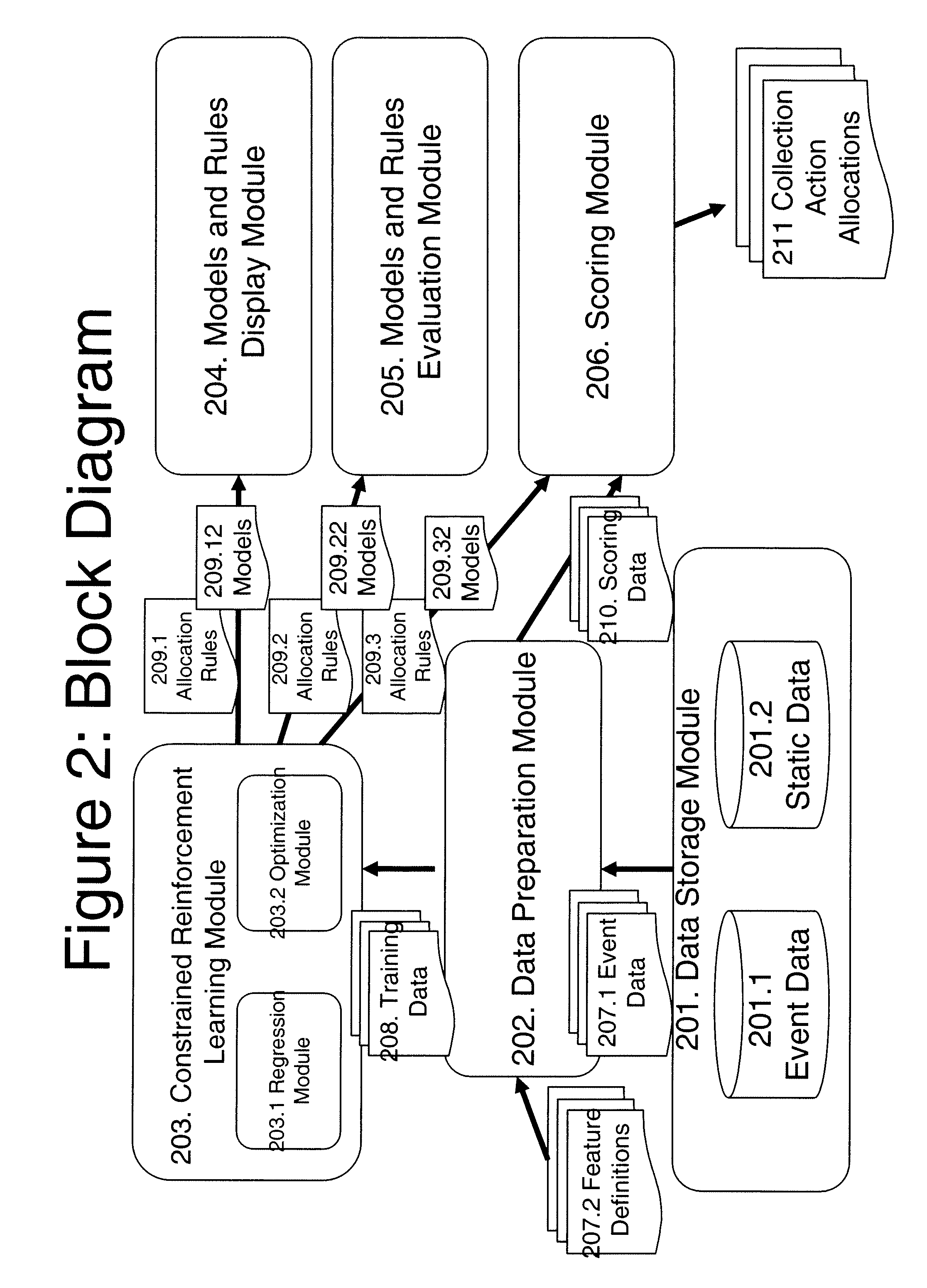
Method and system for debt collection optimization
InactiveUS7519553B2Maximize long-term expected returnsMaximize long-term expected returnComplete banking machinesFinanceData processing systemData modeling
The present invention employs data processing systems to handle debt collection by formulation the collections process as a Markov Decision Process with constrained resources, thus making it possible automatically to generate an optimal collections policy with respect to maximizing long-term expected return throughout the course of a collections process, subject to constraints on the available resources possibly in multiple organizations. This is accomplished by coupling data modeling and resource optimization within the constrained Markov Decision Process formulation and generating optimized rules based on constrained reinforcement learning process comprising applied on the basis of past historical data.
Owner:IBM CORP
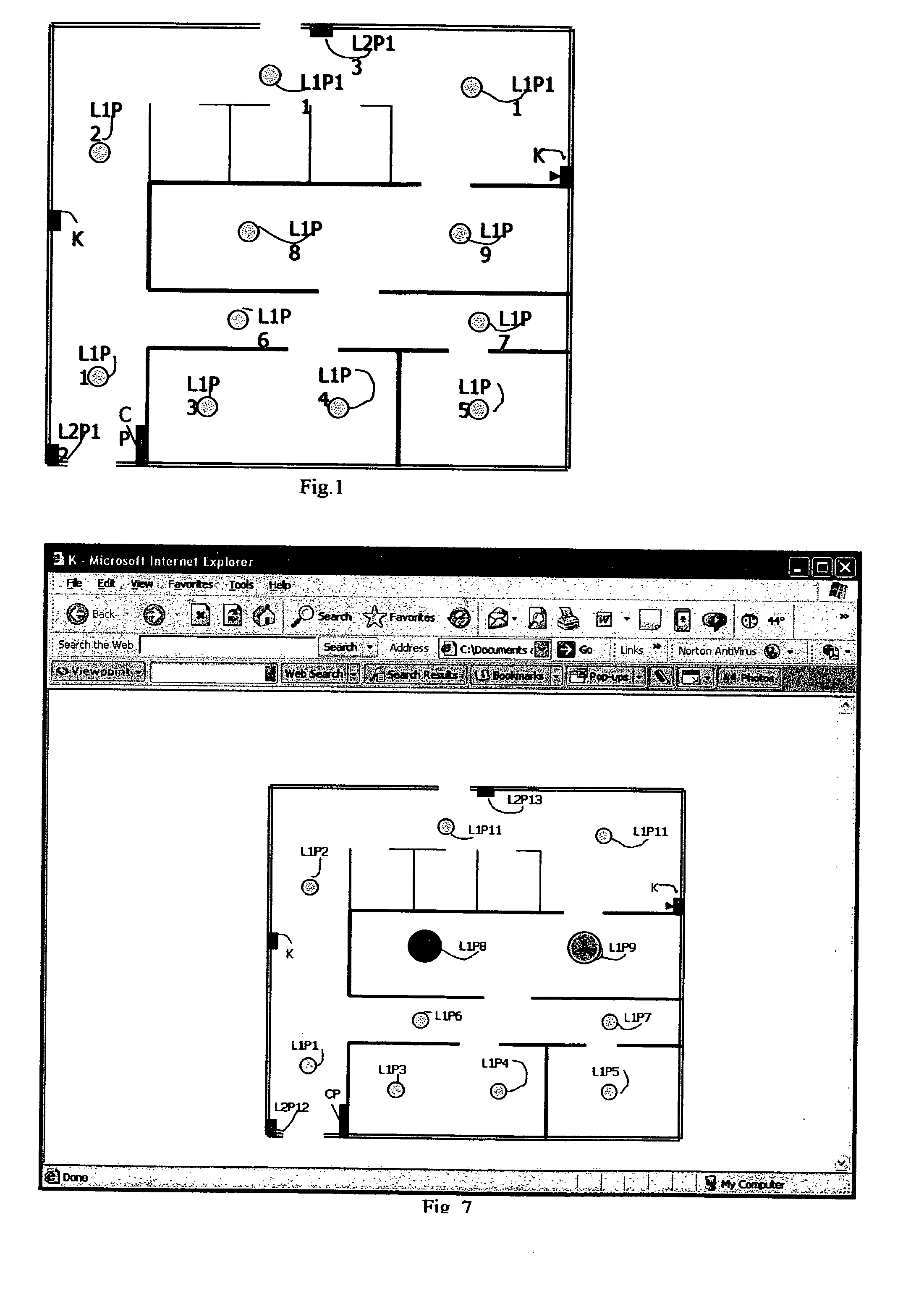
Communication system for a fire alarm or security system
A communications system for an alarm or security system. A plurality of sensors are installed in a facility detect an alarm condition together with a control unit interconnected with the sensors and to which an alarm indication is sent by a sensor going into alarm. A communications path is established by which an alarm signal is transmitted from the control unit to an alarm processing station. A central database, remote from the facility, is accessible from the alarm processing station and includes up-to-date, pertinent information relating to the facility including its address and description, information about the sensor that triggered the alarm, a past history of other alarms, and special instructions regarding how responders should respond in the event hazardous materials are located in an area of the facility where the sensor is located. The system further includes a communications capability for providing this information to responders in route to the facility, including text and graphic information.
Owner:VES
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com