Key management method and network equipment
A technology for network equipment and key management, which is applied in the field of key management methods and network equipment, and can solve problems such as increasing the workload of administrators, unfavorable large-scale deployment and management of routing equipment, manual configuration and update, and the inability to replace keys.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
application example 1
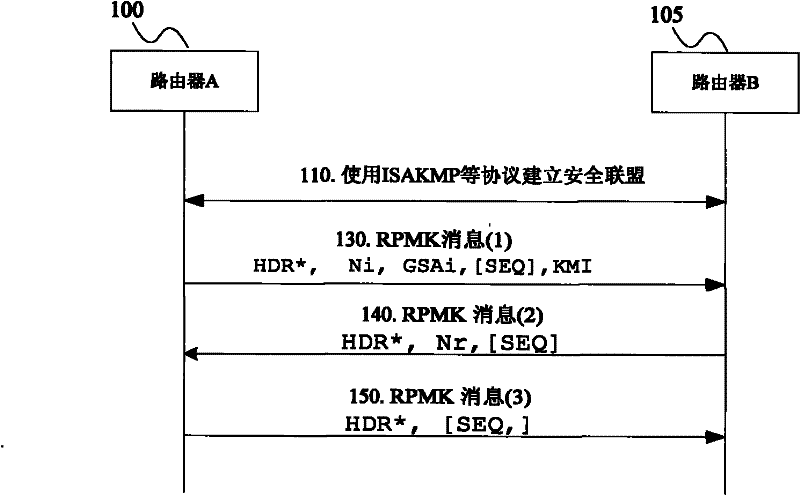
[0431] figure 1 It is a schematic diagram of the automatic negotiation of the routing protocol group key based on GDOI for application example 1 of the present invention, which includes the following steps:
[0432] Step S110: A security association is established between routing device A and routing device B using protocols such as ISAKMP.
[0433] Step S130: routing device A sends an RPMK I message to routing device B, which contains group security association information parameters, and the group security association information parameters include GDOI message header (HDR), random number (NONCE) N, group security association (GSA) payload, serial number (SEQ), and key material information (KMI), etc. Wherein, the Domain of Interpretation (DOI) field of the security association payload of the GDOI is set to 2, indicating that the DOI is a GDOI, that is, the DOI of the group security association is negotiated. The setting of group security association is as above.
[0434]...
application example 2
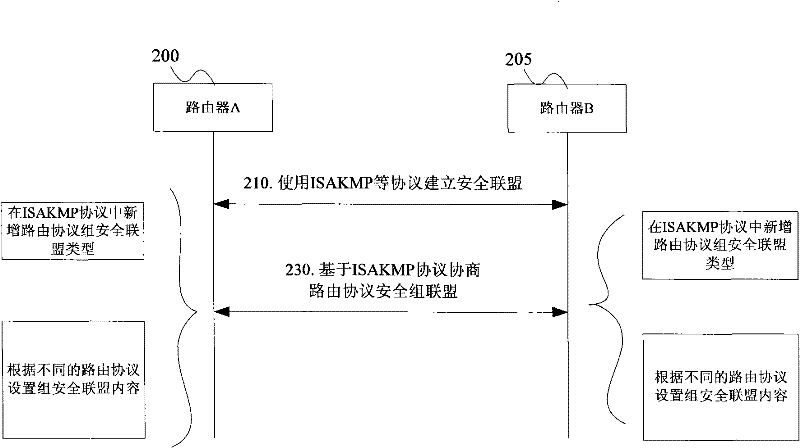
[0438] figure 2 The second schematic diagram of the method for automatic negotiation of routing protocol group keys based on ISAKMP for application example 2 of the present invention, which includes the following steps:
[0439] Step S210: A security association is established between routing device A and routing device B using protocols such as ISAKMP.
[0440] Step S230: routing device A and routing device B use ISAKMP to carry out the negotiation of the group security association of the routing protocol, wherein in the ISAKMP, the group security association load (that is, for example, defined as Group SA (GSA)) is added, and the group security association load in the group security association The Domain of Interpretation (DOI) type is 3, and 3 indicates that the type of the negotiated group security association is a group security association of a specific routing protocol (such as the group security association of OSPFv2), and a new group security association is added. ...
application example 3
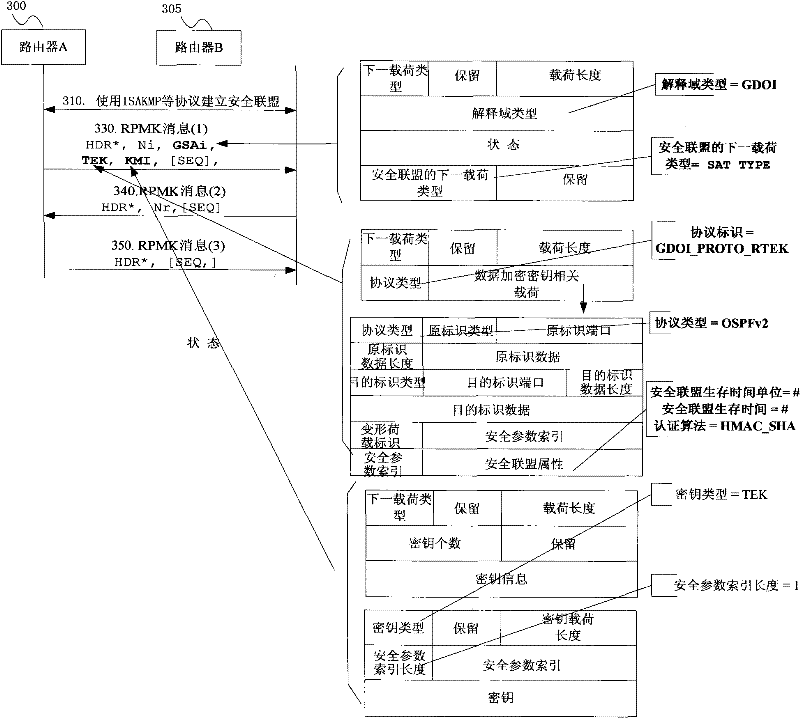
[0443] image 3 It is a schematic diagram of a GDOI-based OSPFv2 routing protocol group security association negotiation mode 1 for application example 3 of the present invention, which includes the following steps:
[0444] Step S310: A security association is established between routing device A and routing device B using protocols such as ISAKMP.
[0445] Step S330: routing device B sends an RPMK message to routing device A; the RPMK message includes group security association information parameters, and the group security association information parameters include GDOI message header (HDR), random number (NONCE), and group security association ( GSA) load, etc.
[0446] Wherein, setting the Domain of Interpretation (DOI) field of the security association payload of the GDOI to 2 indicates that the DOI is the GDOI, that is, the DOI of the group security association. The SA Next Payload field in the SA payload is set to the TEK payload type, indicating that the payload typ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com