Credible data transmission method
A transmission method and data transmission technology, applied in the field of information security, can solve problems such as prolonging the use of expired files, being vulnerable to some attacks, and violating usage policies, etc., to achieve the effect of ensuring security, ensuring privacy, and ensuring security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
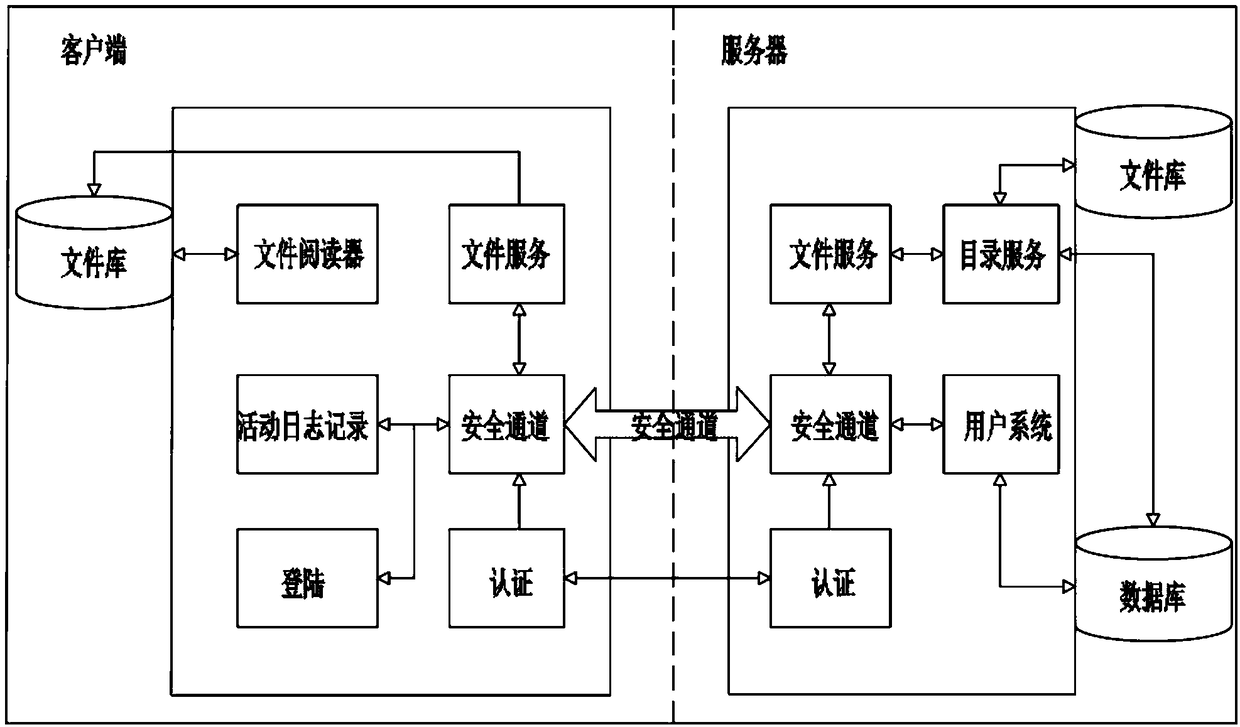
[0040] The invention relates to a trusted data transmission method. The client and server for data transmission are authenticated through SGX, and the client authentication module verifies the legitimacy of the platform and the user to the corresponding server. After the client is authenticated, , a session with the server is established, the client and the server perform a one-time provisioning agreement, and the confidential data of the client application is sealed to the platform where the application is located, among which, a separate security is established between the server and the client Each channel corresponds to a unique client, and the data sent by the server to the client is encrypted during transmission; after the protected file is encrypted in the enclave, it sends a specific file request to the client according to the client's file request. files, which are then distributed to authenticated and authorized app users to view or perform other operations.
[0041]...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com