Identifying and tracing system with unique identity and method
An identity identification, unique technology, applied in the field of digital signature authentication and encryption and decryption, can solve the problems of not forming a closed-loop system, unable to achieve anti-counterfeiting, unable to effectively adapt to different industries, etc., to achieve high system security and security management Simple and reliable effects
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0042] In order to further explain the technical means and beneficial effects adopted by the present invention to achieve its purpose, and to implement the present invention according to the detailed introduction of this specification, the specific implementation of the present invention will be described below in conjunction with the accompanying drawings and preferred embodiments of the present invention. The method is described in detail below.
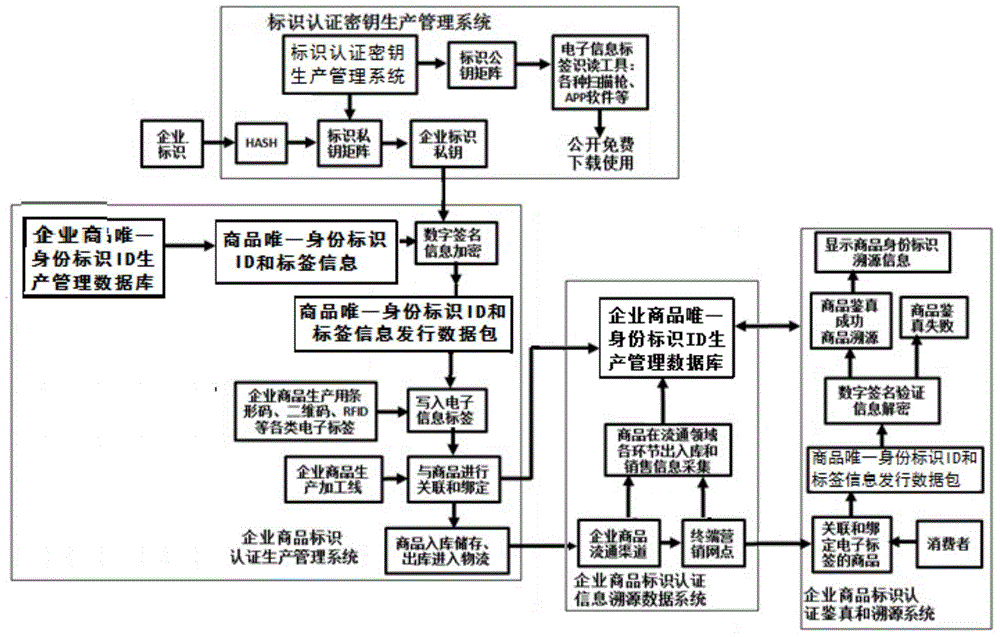
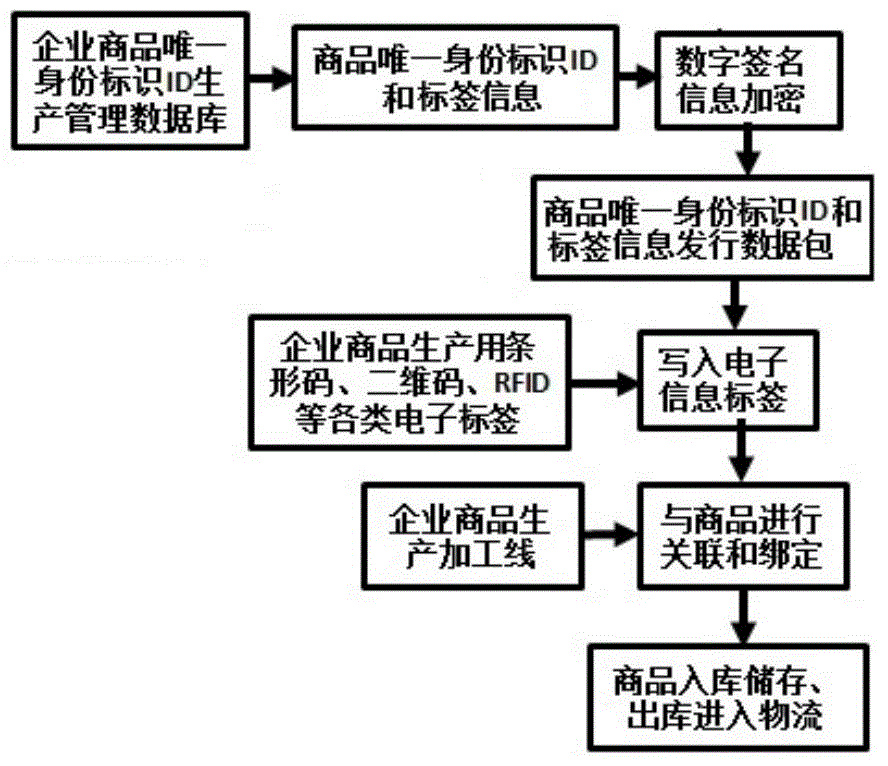
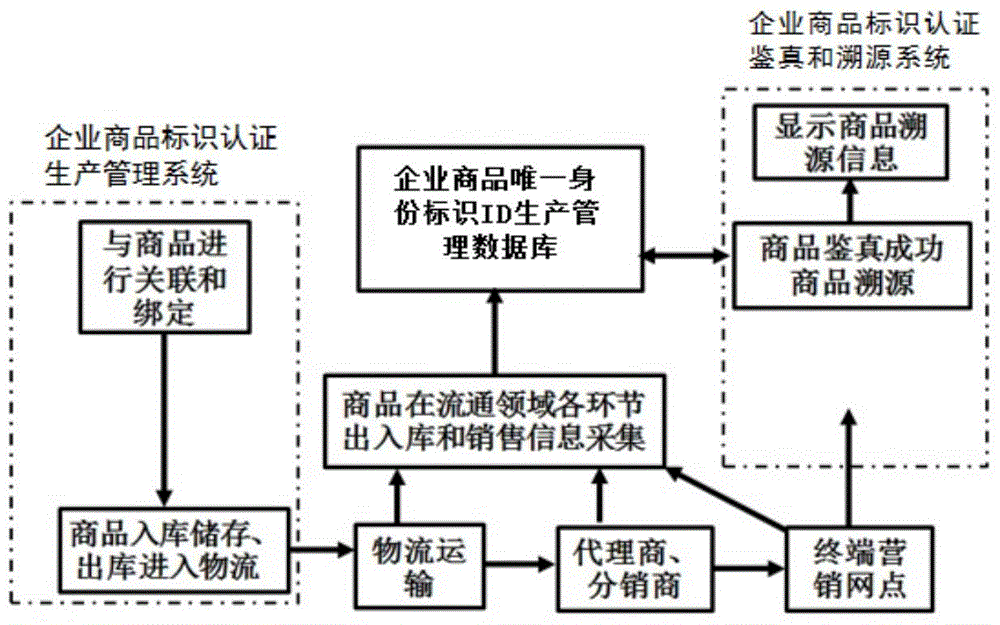
[0043] The present invention discloses a product authenticity and traceability system based on combined public key cryptosystem identification authentication technology, such as figure 1 As shown, the system includes: logo authentication key production management system, enterprise commodity logo authentication production management system, enterprise commodity logo authentication information traceability data system, enterprise commodity logo authentication authenticity and traceability system.
[0044] see figure 1 , the identif...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com