A trusted authentication system and method based on block chain
An identity verification method and identity verification technology, applied in the direction of instruments, electrical digital data processing, digital data protection, etc., can solve problems such as being vulnerable to attack and tampering, user identity being easily used fraudulently, and passwords being easily intercepted in the middle, to achieve Guaranteeing security and reliability, effective management and information protection, and the effect of large-scale interaction
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
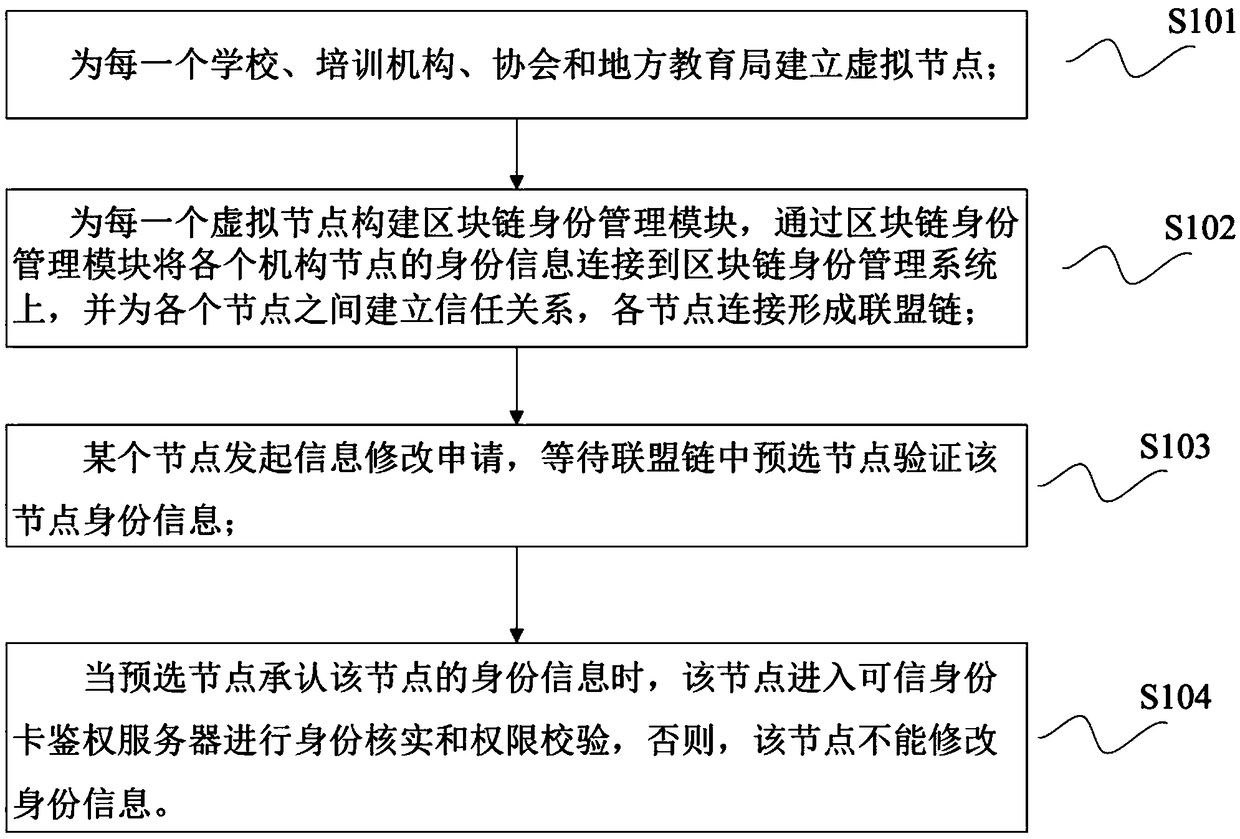
[0035] Such as figure 1 Shown, a kind of trusted identity verification method based on block chain of the present invention, it comprises the following steps:
[0036] S101. Establish a virtual node for each school, training institution, association and local education bureau;
[0037] S102. Build a blockchain identity management module for each virtual node that stores trusted identity information of users, connect the identity information of each organization node to the blockchain identity management system through the blockchain identity management module, and provide Establish a trust relationship between nodes, and each node connects to form an alliance chain;
[0038] S103. A node initiates an information modification application, and waits for the pre-selected node selected within the alliance chain to verify the identity information of the node;
[0039] S104. When the pre-selected node recognizes the node's identity information, the node enters the trusted identity...
Embodiment 2
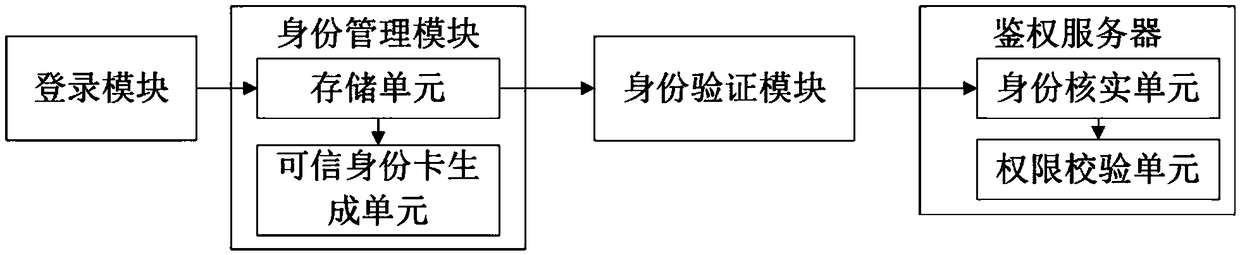
[0046] Such as figure 2 As shown, a trusted identity verification system based on blockchain of the present invention includes a login module, an identity management module, an identity verification module and an authentication server;
[0047] The identity management module stores the user's initial identity information, uses an encryption algorithm to protect the user's identity information, and automatically updates the user's identity information on a regular basis. The identity management module includes: a storage unit and a trusted identity card generation unit; the storage unit stores the user's identity information; the trusted identity card generation unit automatically generates a trusted identity card according to the user's identity information. The storage unit is signally connected with the trusted identity card generation unit and the identity verification module respectively.
[0048] The identity verification module verifies the user's identity information ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com