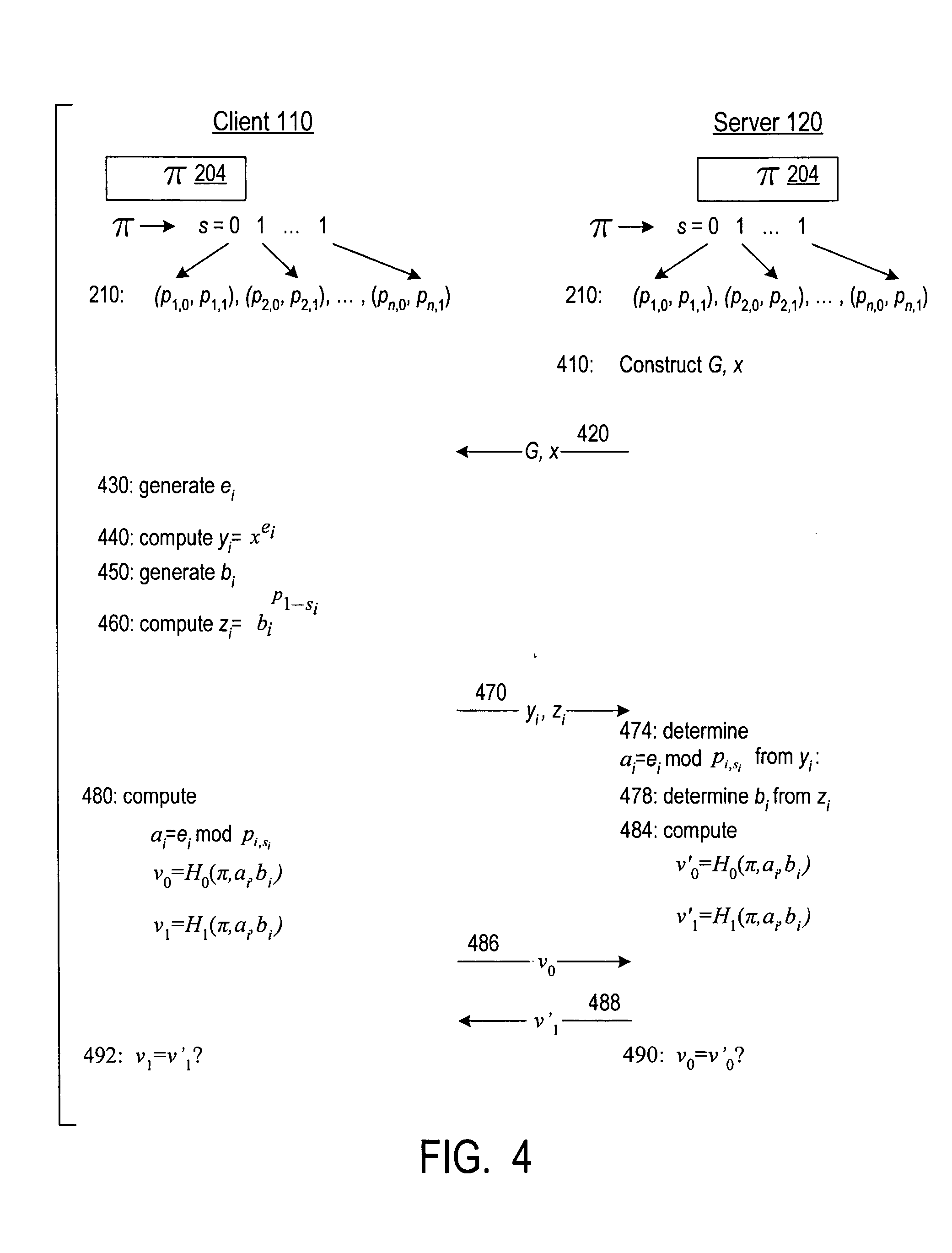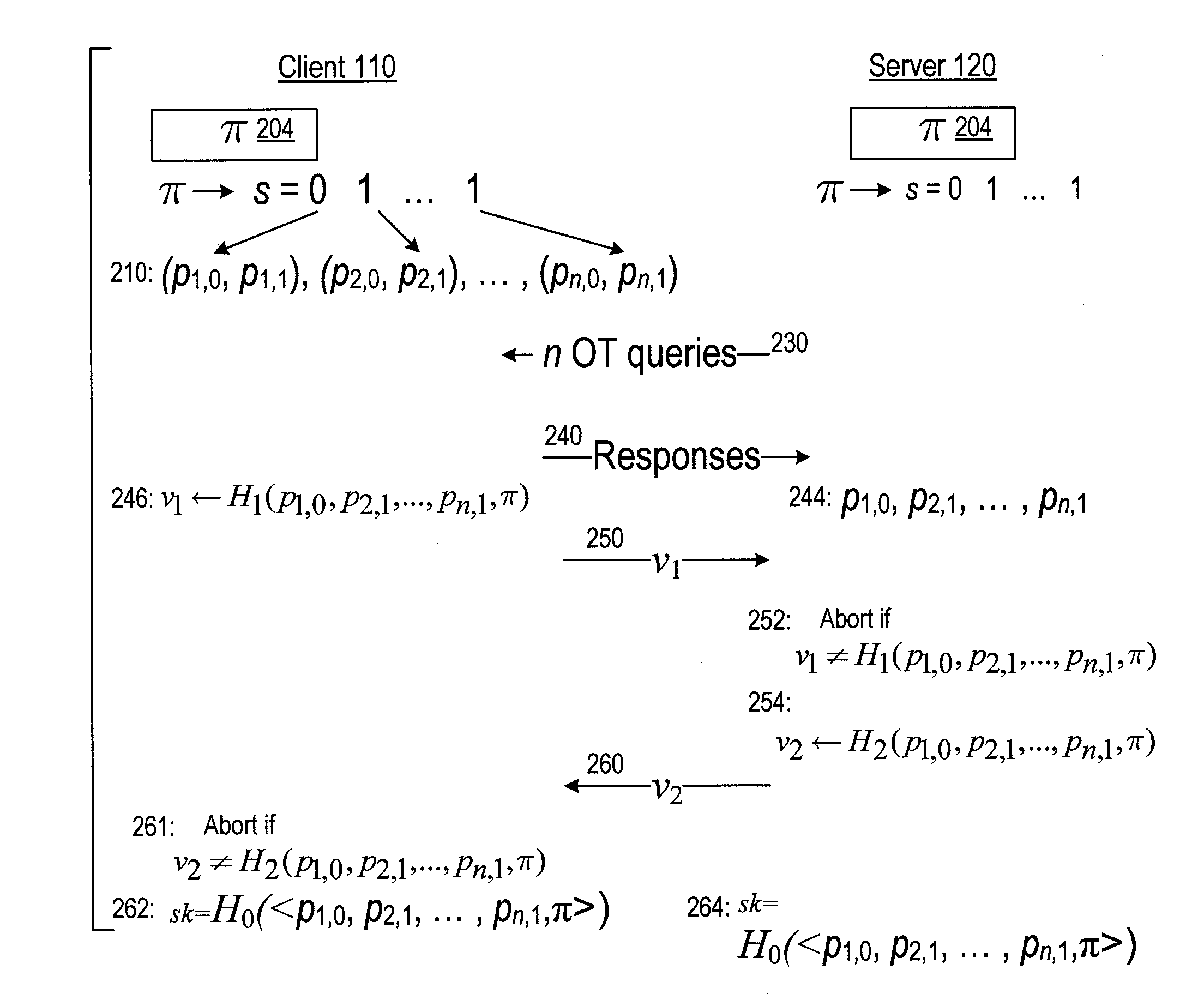Patents
Literature
40results about How to "Small probability" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Addressing in wireless local area networks
InactiveUS7359989B2Small probabilityReduced risk of collisionError prevention/detection by using return channelNetwork topologiesMAC addressReal-time computing
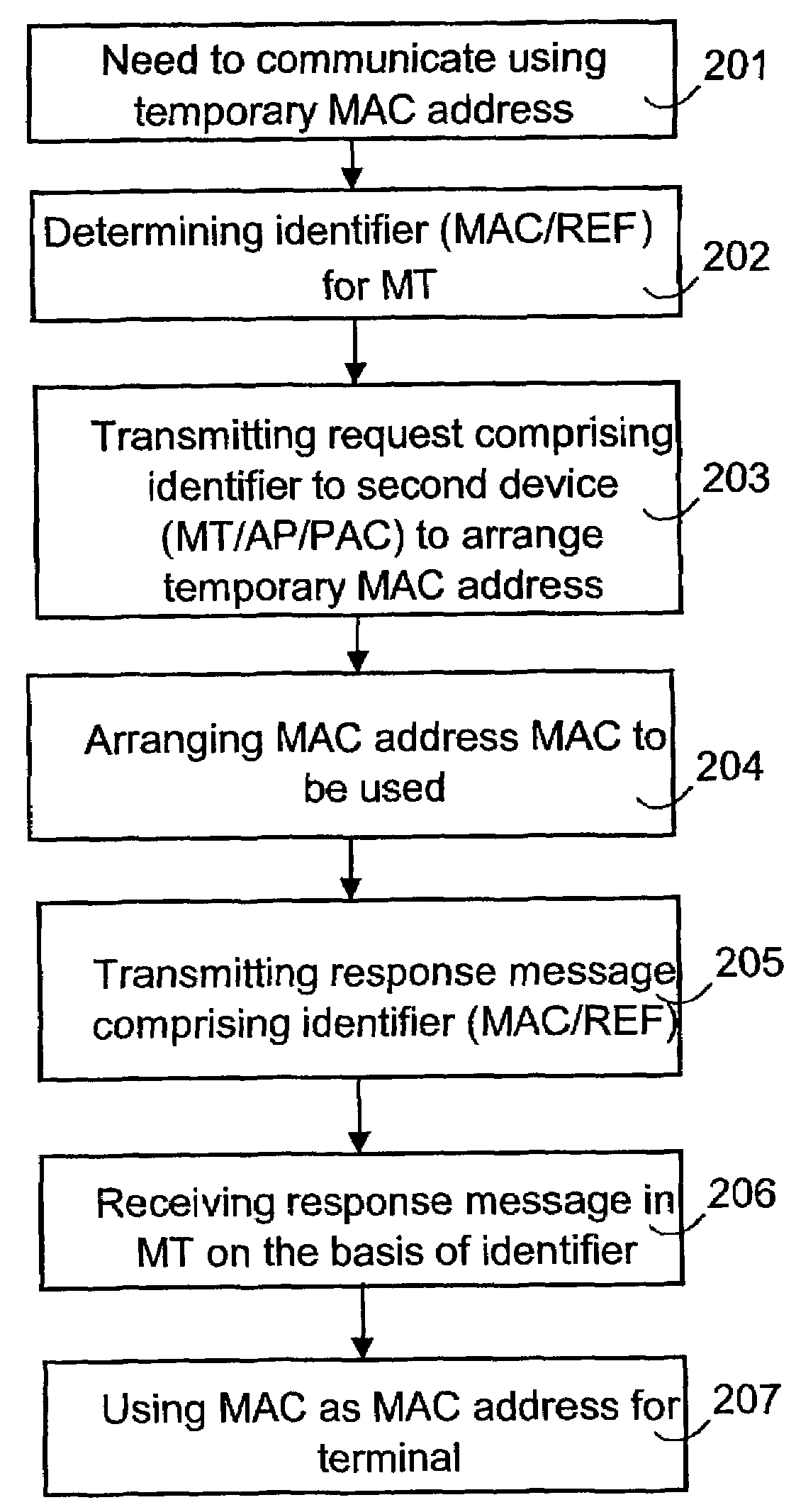
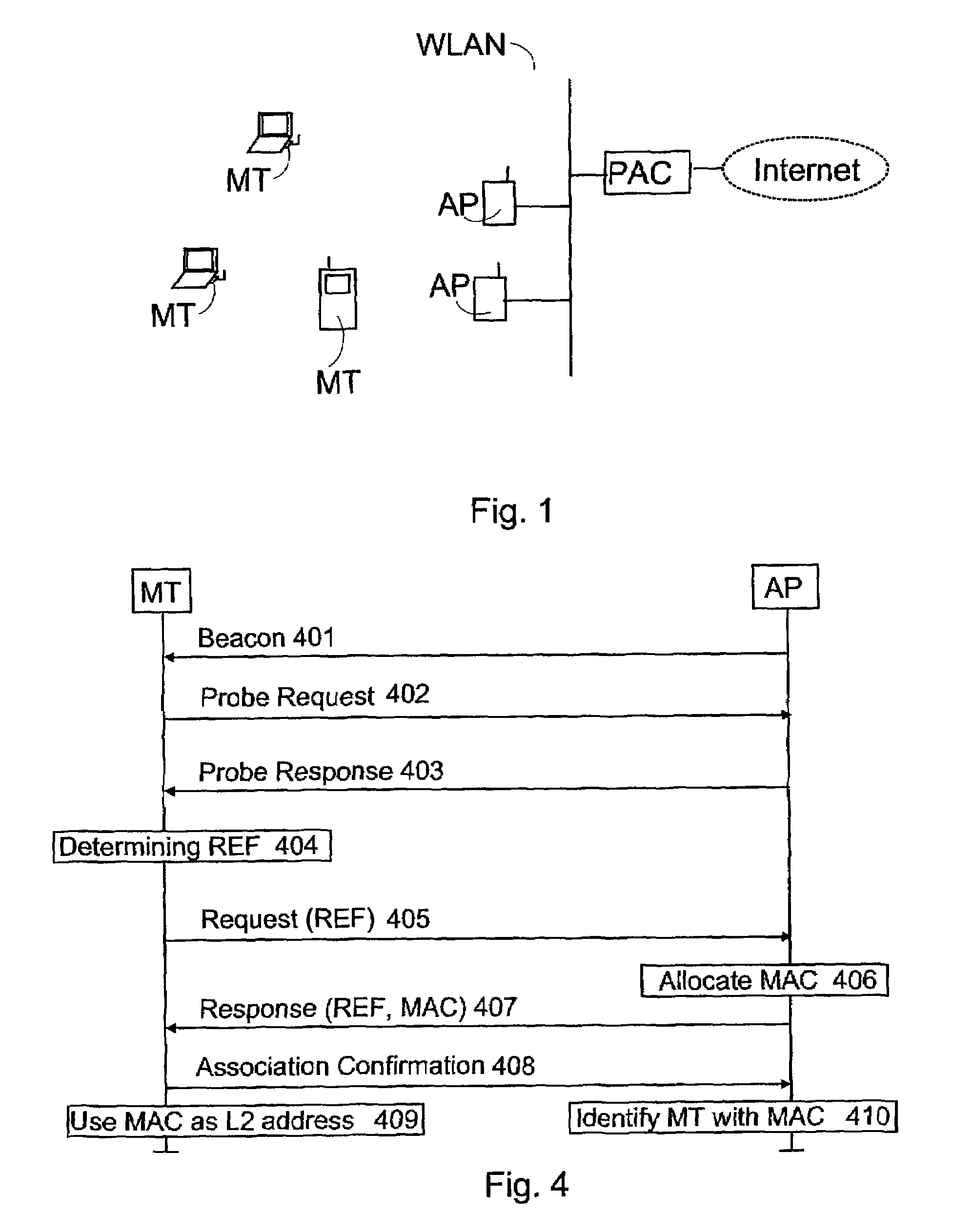
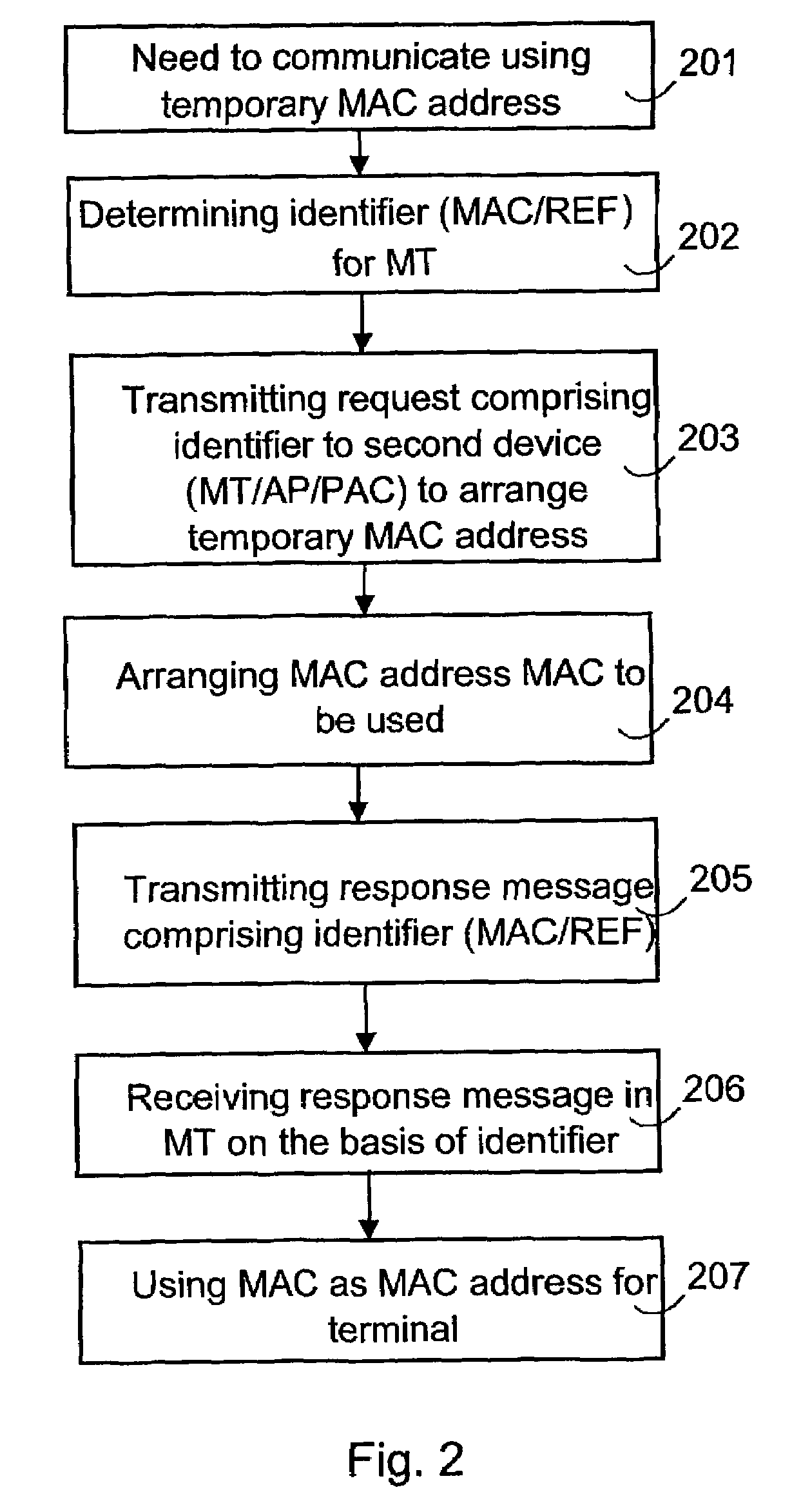
The invention relates to a method of transferring required messages for acquiring a temporary MAC address in a wireless local area network. In a first device in the local area network, a first identifier is determined to identify the first device. A message comprising the first identifier is transmitted from the first device to a second device to arrange a temporary MAC address. A response message relating to the acquisition of the MAC address and comprising the first identifier is transmitted from the second device to the first device. The first device identifies on the basis of the first identifier that the response message is intended for it.
Owner:NOKIA CORP
Cryptographic authentication and/or establishment of shared cryptographic keys, including, but not limited to, password authenticated key exchange (PAKE)
ActiveUS20060291661A1Improve efficiencySmall probabilityUser identity/authority verificationTransmission protocolAlgorithm
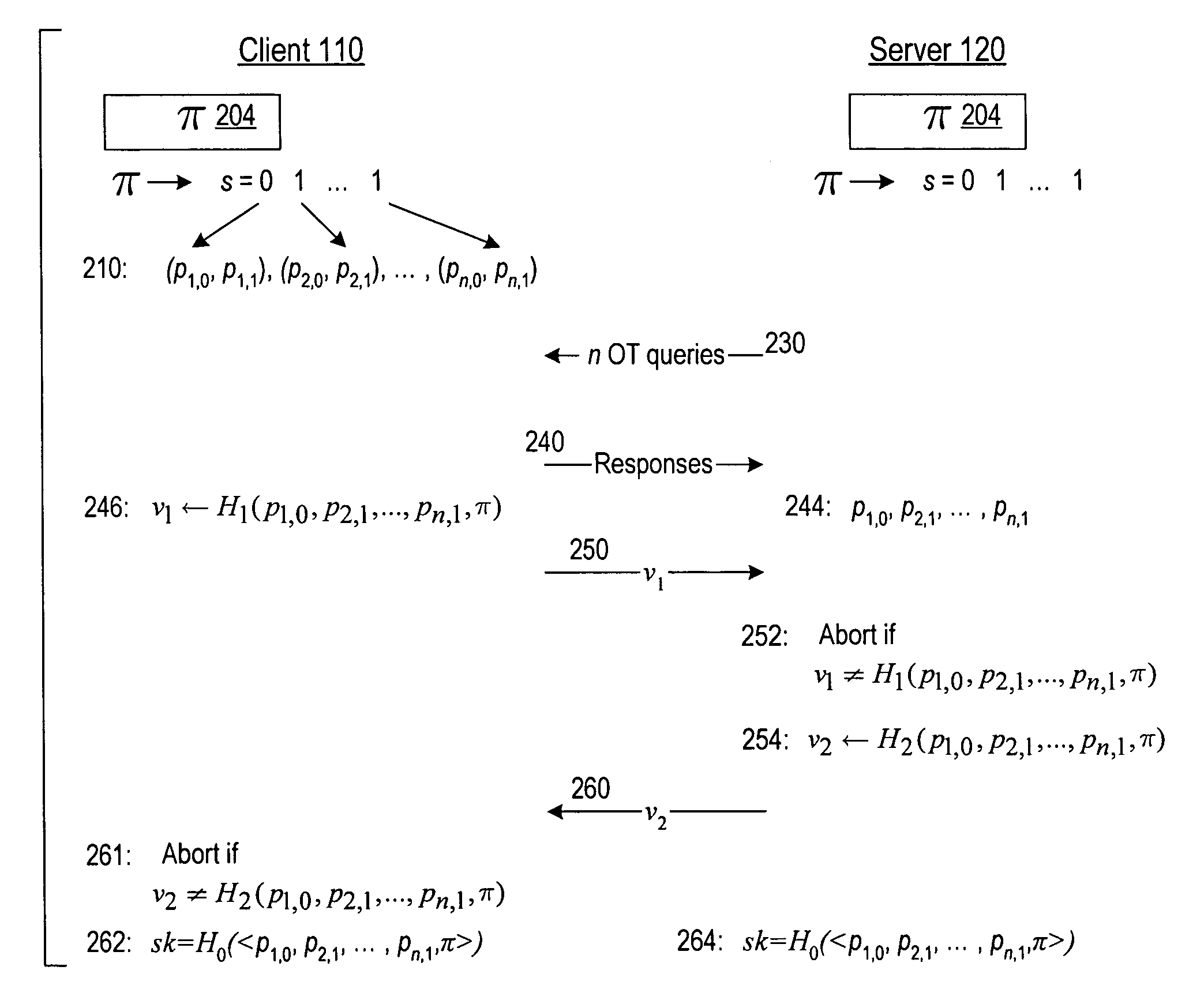
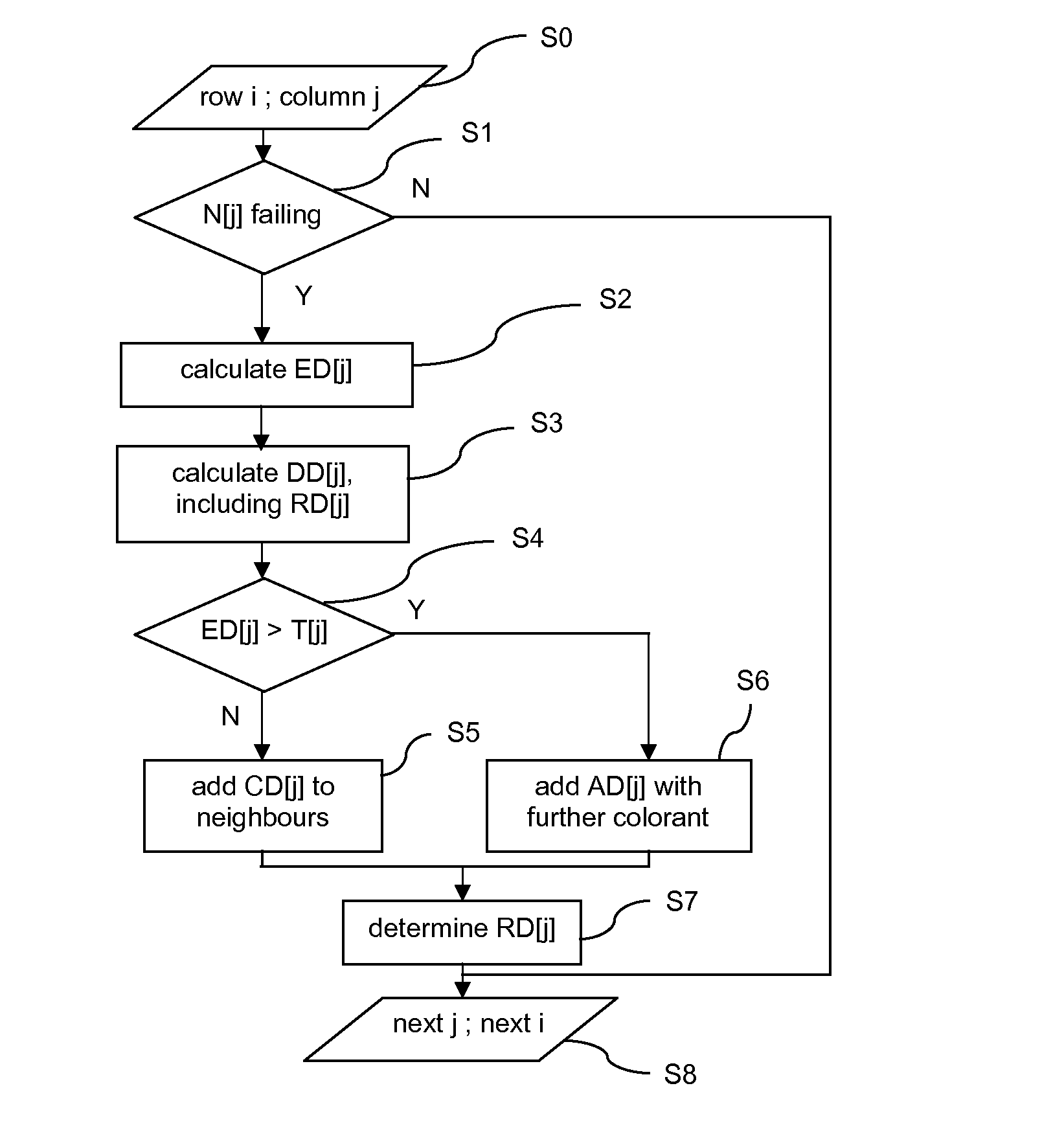
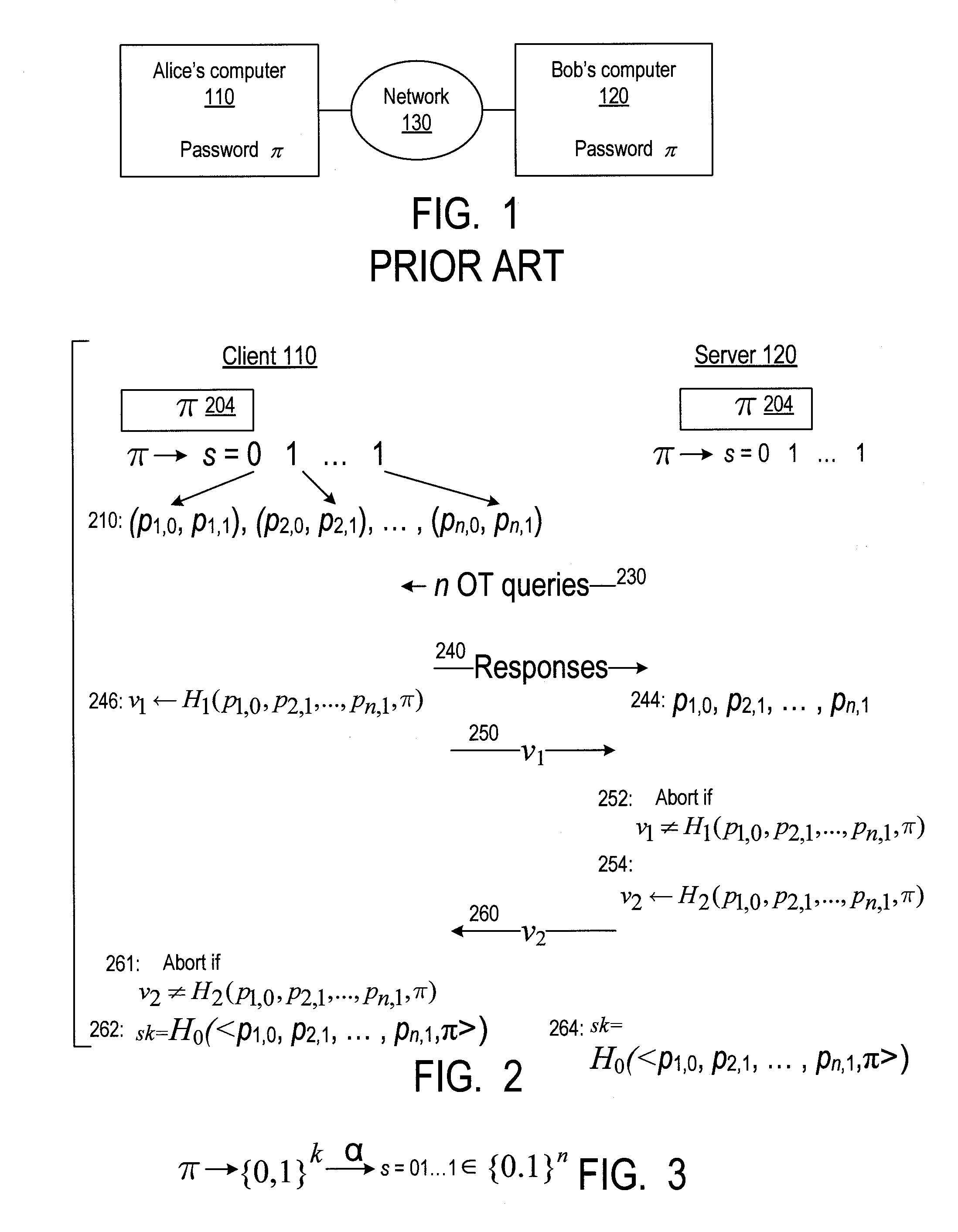
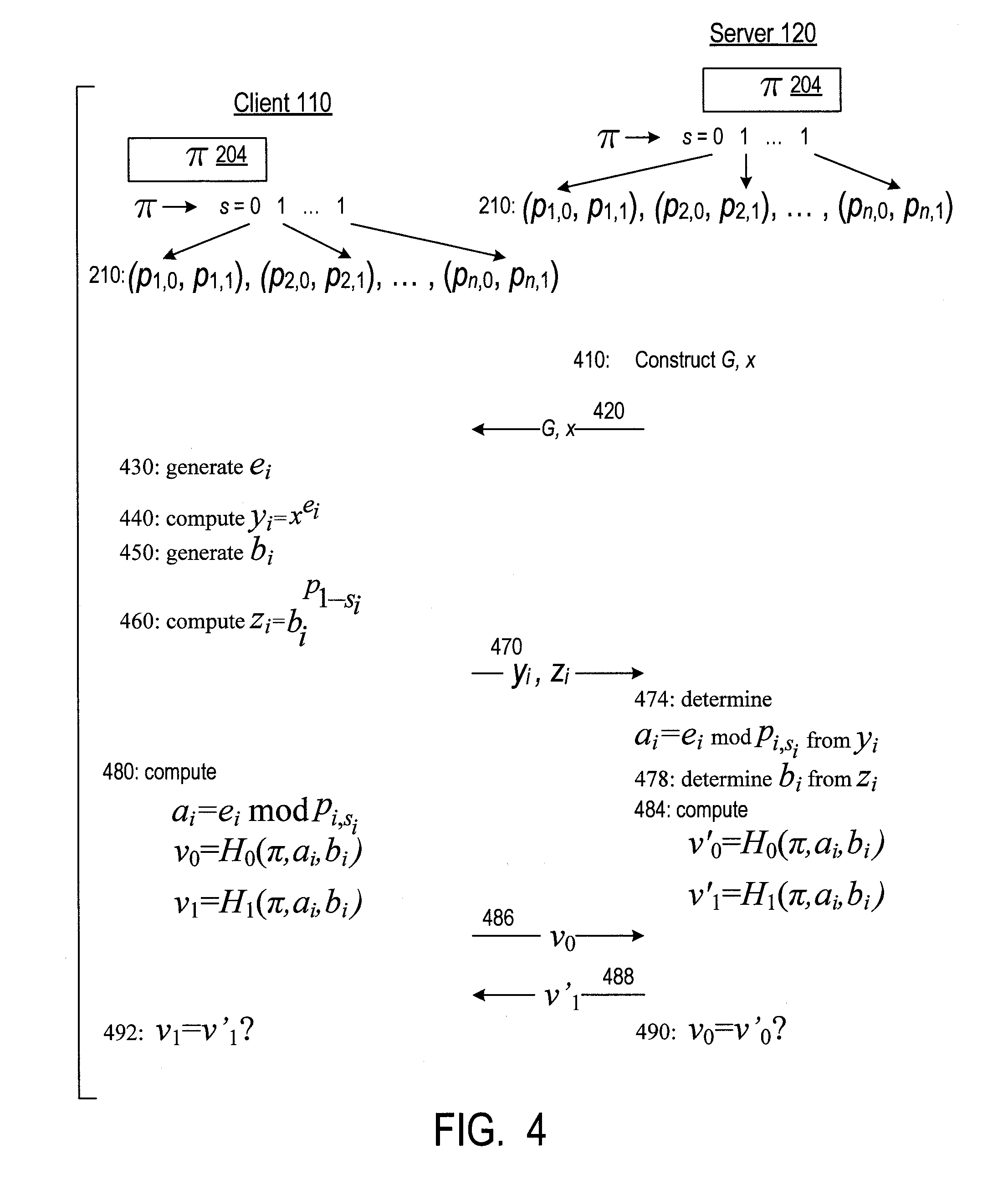
A server (120) uses a password (π) to construct a multiplicative group (ZN*) with a (hidden) smooth order subgroup (<x′>), where the group order (Pπ) depends on the password. The client (110) uses its knowledge of the password to generate a root extraction problem instance (z) in the group and to generate data (y) allowing the server to construct a discrete logarithm problem instance (y′) in the subgroup. The server uses its knowledge of the group order to solve the root extraction problem, and solves the discrete logarithm problem efficiently by leveraging the smoothness of the subgroup. A shared key (sk) can be computed as a function of the solutions to the discrete logarithm and root extraction problem instances. In some embodiments, in an oblivious transfer protocol, the server queries the client (at 230) for data whose position in a database (210) is defined by the password. The client provides (240) such data without knowing the data position associated with the server's query. The client obtains the data position independently from the password. The data positions and / or the respective data are used for authentication and shared secret key generation. Other embodiments are also provided.
Owner:NTT DOCOMO INC
Method for compensating a failing nozzle
ActiveUS20150314591A1Increase probabilityHigh optical densityOther printing apparatusSpray nozzleEngineering
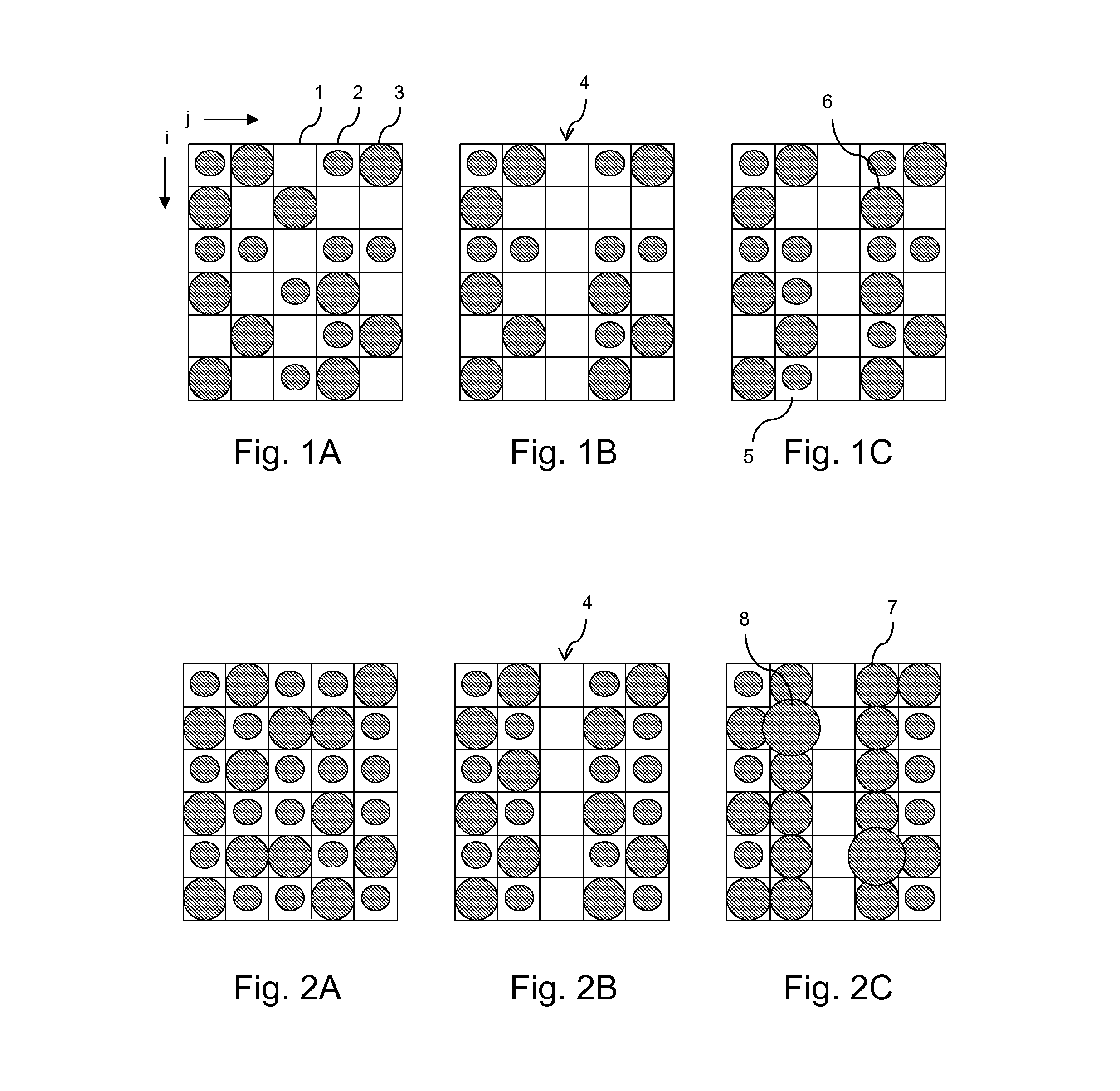
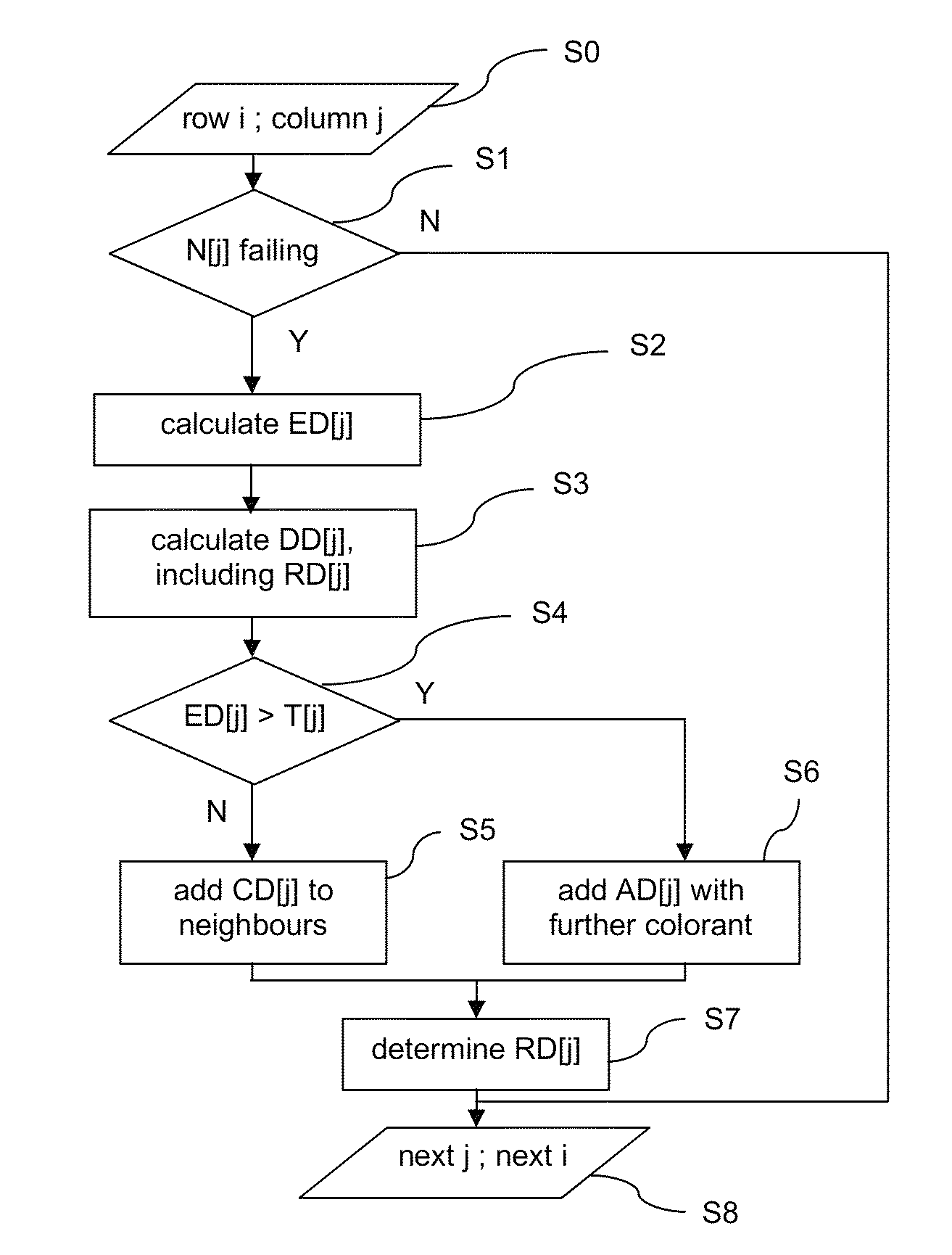
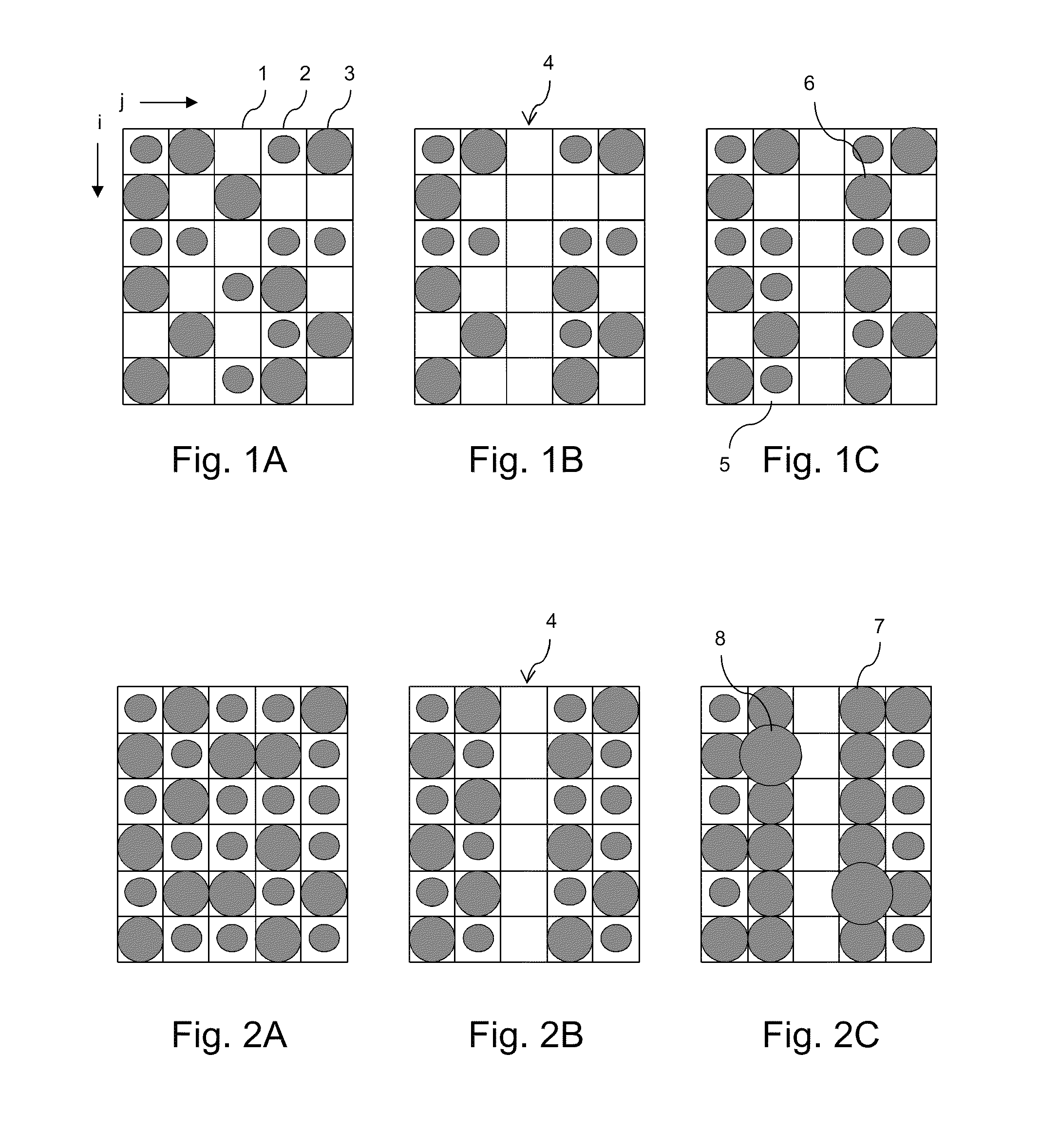
A method is provided for compensating a failing nozzle in a printhead comprising a series of print elements with nozzles for operation in an inkjet printing process in which a colorant is applied for locally changing an optical density, thereby printing an image.The method comprises at least two compensation mechanisms, each providing a different amount of additional optical density in the environment of a missing dot in the printed image. A nozzle is recorded as a failing nozzle if the associated print element does not apply an ink dot within predetermined specifications. An environment density is determined in an environment of a missing dot associated with said failing nozzle. The environment density is compared with a predetermined threshold, and an appropriate compensation mechanism is selected from the at least two compensation mechanisms. The method is applied in an inkjet printing system for balancing under- and overcompensated optical density.
Owner:OCE TECH
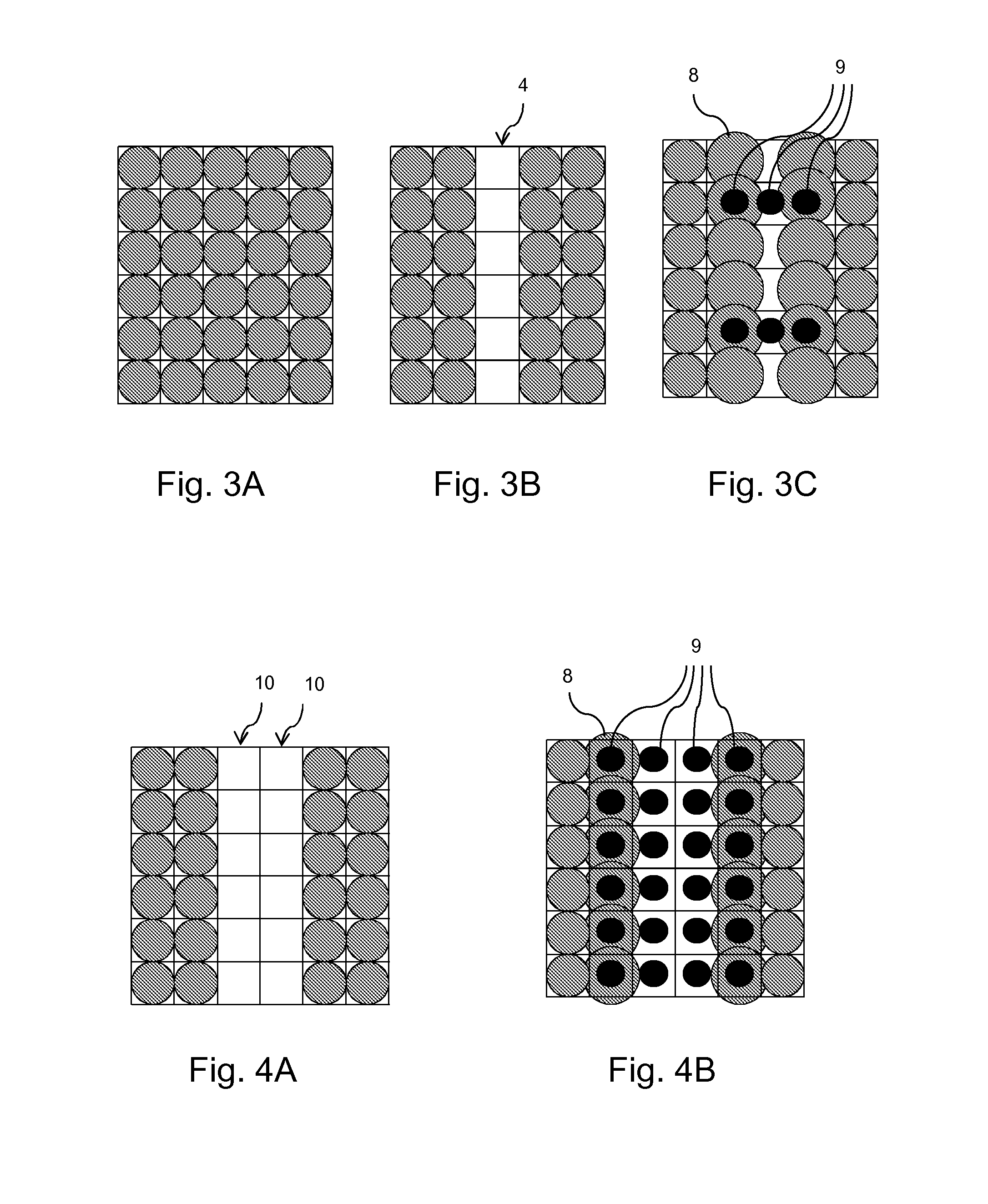
Similarity calculation device and similarity calculation program
InactiveUS20060294060A1Small probabilityShort calculation timeDigital data information retrievalOffice automationDecompositionData mining
There is provided a similarity calculation device for calculating an index for judging technical similarity between technical document groups consisting of technical documents. The similarity calculation device includes: technical document group input means (365) for inputting a first technical document group and a second technical document group to be compared; technical information input means (371) for inputting technical information; cluster analysis means (380) for searching technical documents contained in the first technical document group and the second technical document group and including the technical information which has been input and decomposing the searched technical documents into a cluster for each technical information; similarity calculation means (380) for calculating the ratio of the number of mixed clusters including the technical documents of both of the first technical document group and the second technical document group against the total number of clusters obtained as the cluster decomposition; and output means (365) for outputting the similarity calculated.
Owner:INTPROP BANK CORP (JP)
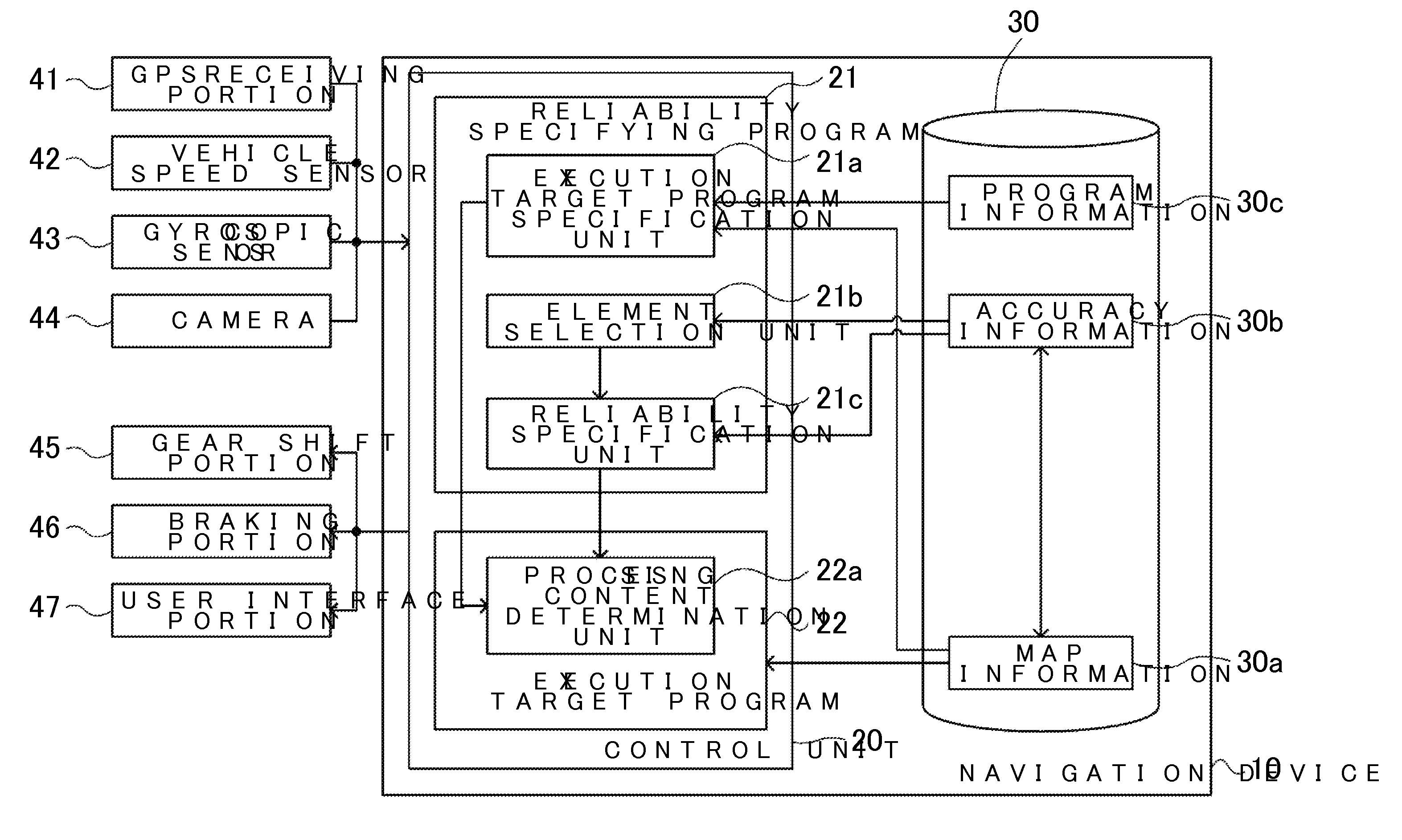
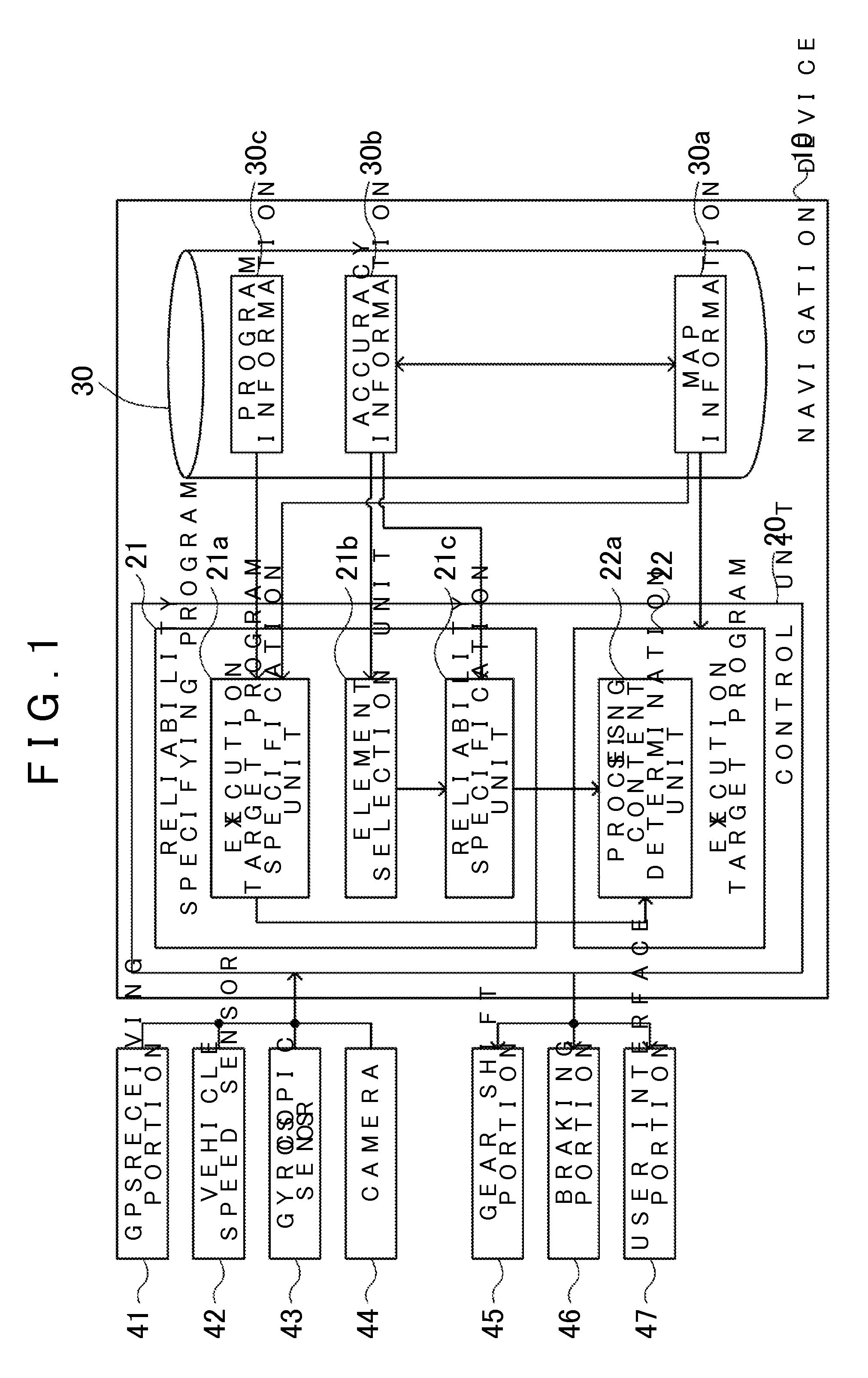
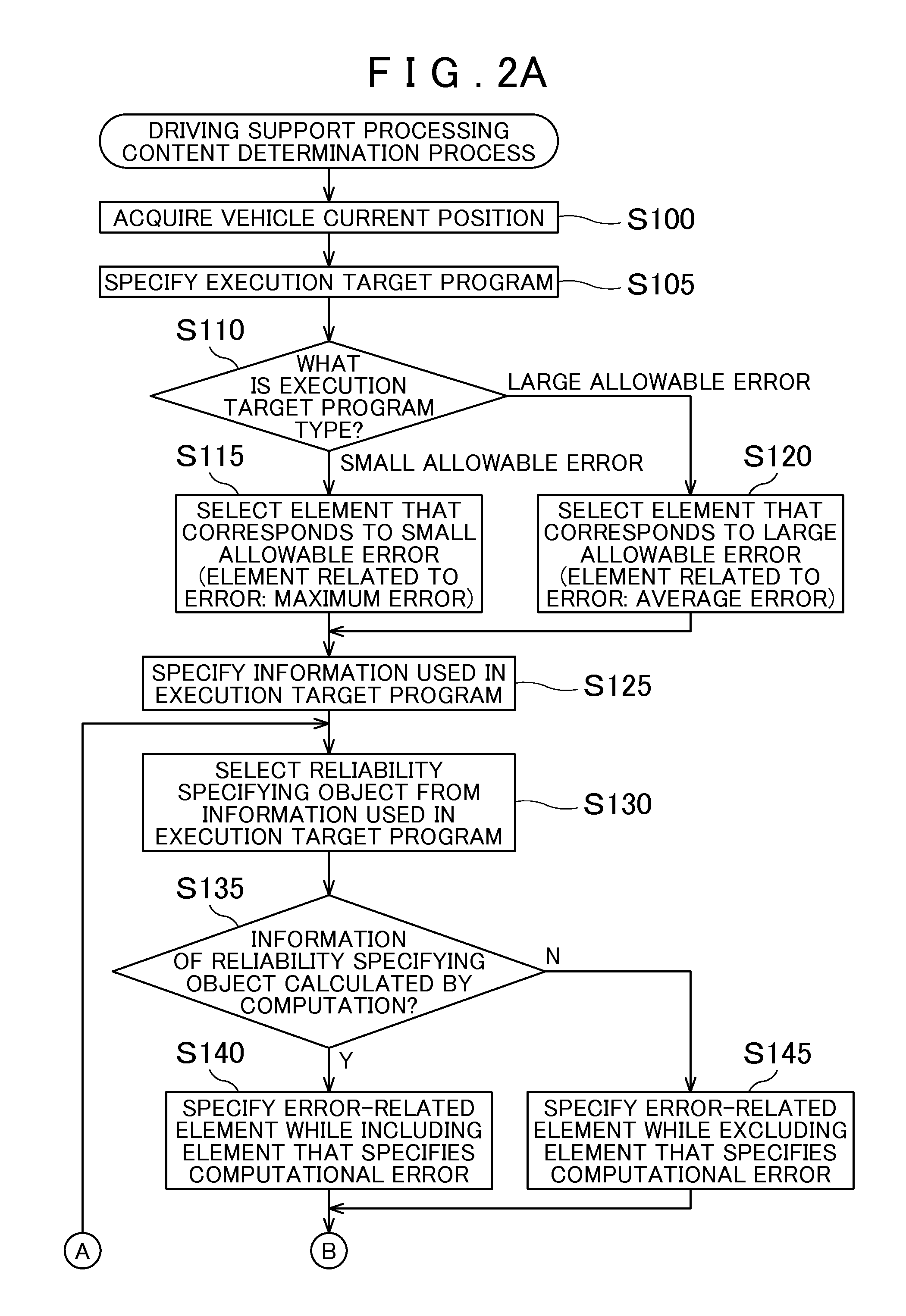
Device, method, and program for specifying reliability of information used in driving support
InactiveUS20110060524A1Eliminate negative effectsEfficient managementInstruments for road network navigationDigital data processing detailsSoftware engineeringProgram specification
Provided is a driving support device and method that specifies the reliability of information used in a driving support device. The driving support device includes a storage medium that stores one or more programs and accuracy information that specifies the reliability of information of various elements used by one of the programs to provide driving support. The driving support device also includes an execution target program specification unit that specifies what program from the one or more programs is to be executed as the execution target program. An element selection unit selects an element that corresponds to the specified execution target program from the various elements. The device also includes a reliability specification unit that specifies the reliability of information used in the target execution program based on the accuracy information of the selected element.
Owner:AISIN AW CO LTD
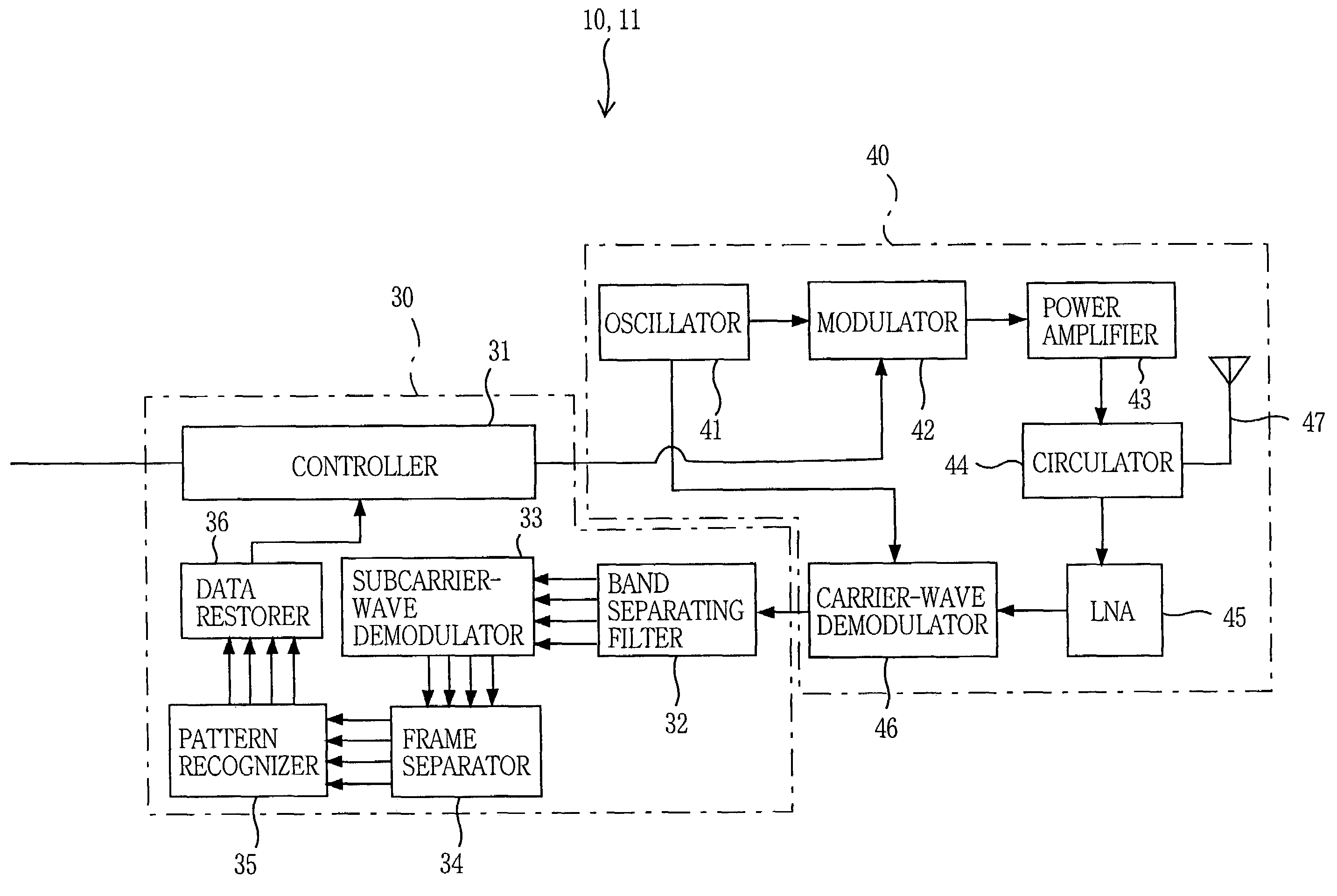
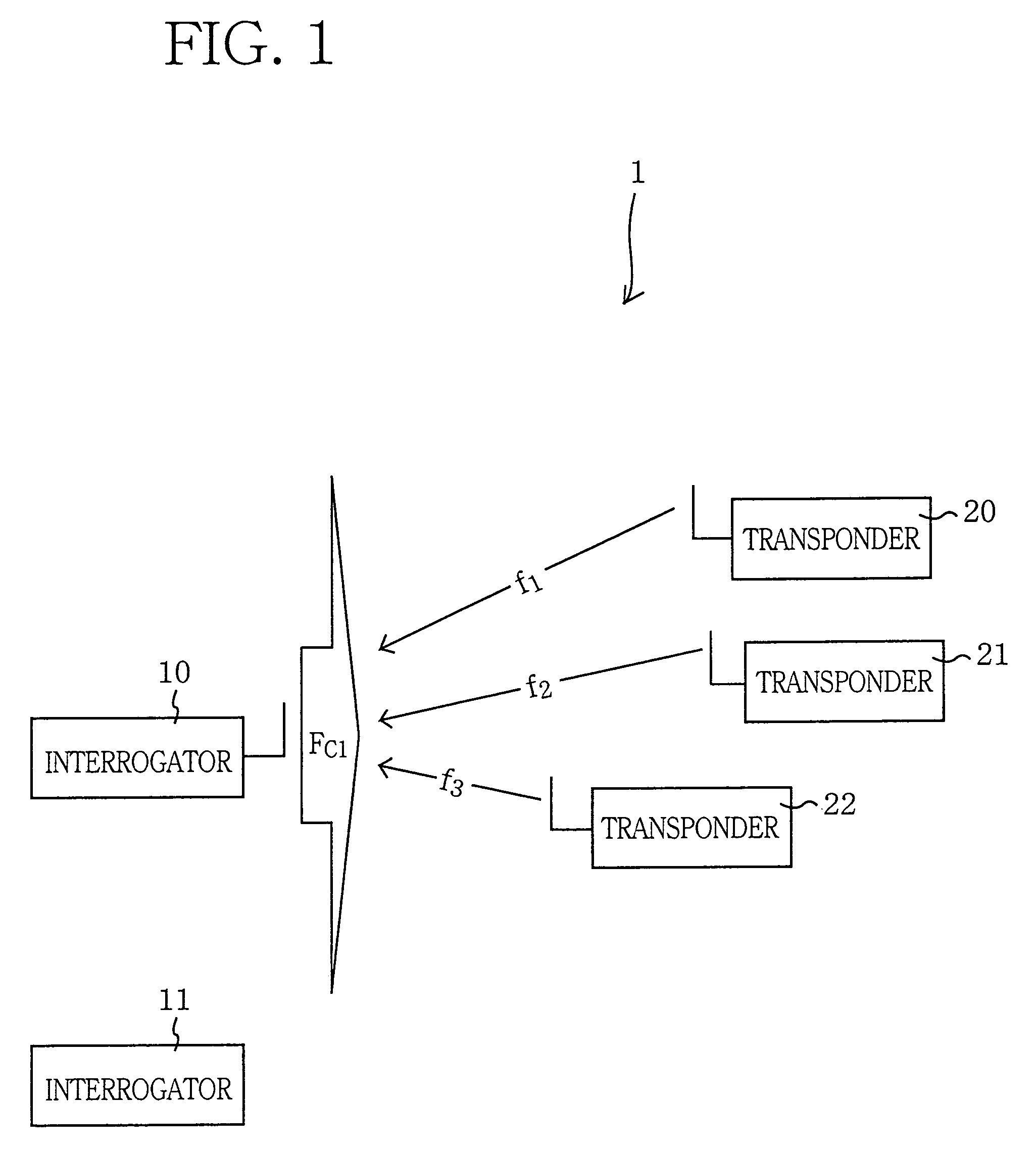
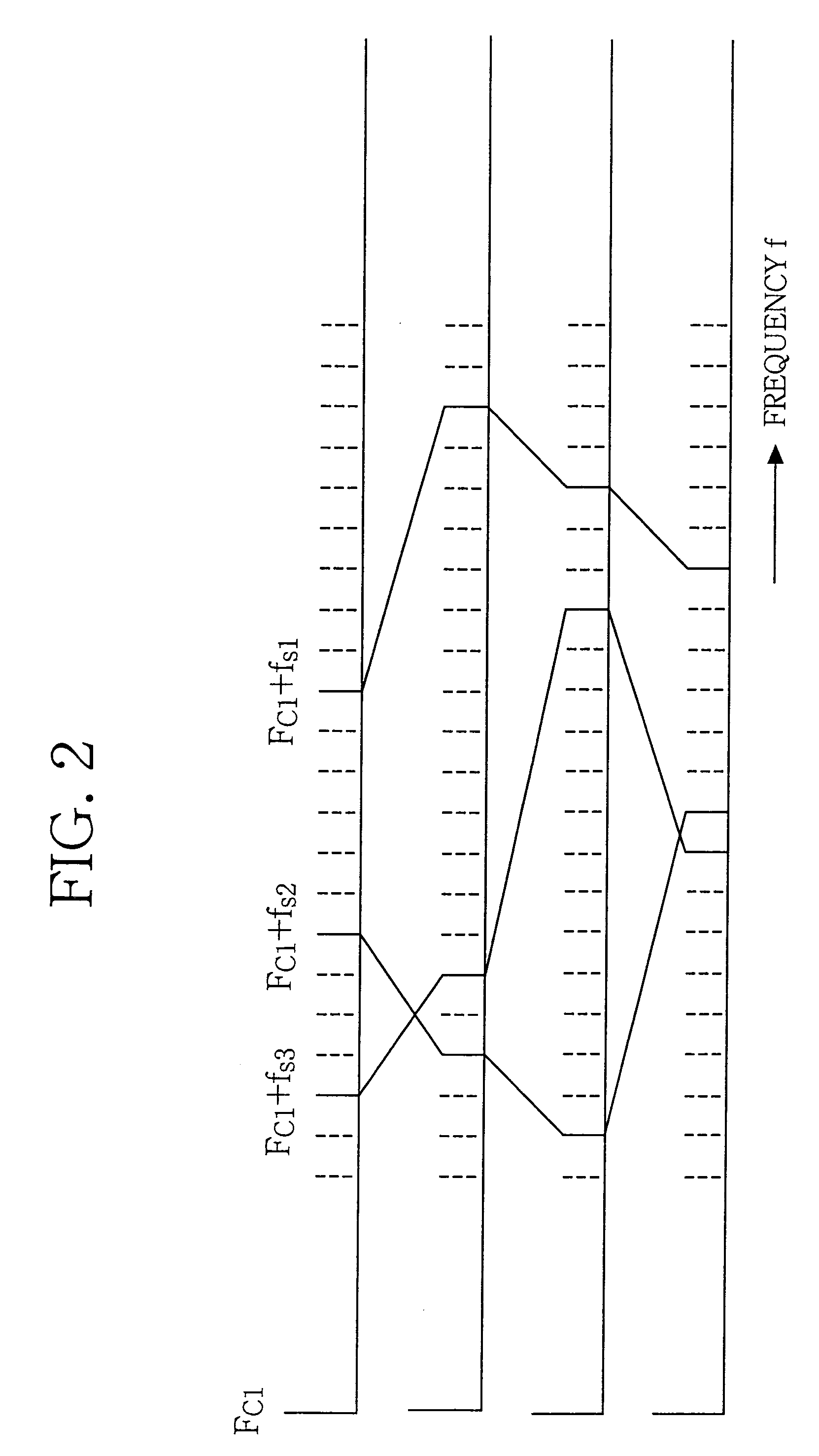
Transponder, interrogator, and communication system
ActiveUS7109844B2Reliably distinguishEasily correct possible error of dataRadio/inductive link selection arrangementsSubscribers indirect connectionCarrier signalSubcarrier
A communication system 1 includes interrogators 10, 11 and transponders 20, 21, 22. The interrogator 10 transmits a carrier wave, FC1, to the transponders 20, 21, 22, and the transponders 20, 21, 22 return respective reflected waves, f1, f2, and f3, to the interrogator 10. The transponders 20, 21, 22 modulate the received carrier waves FC1 using respective subcarrier waves that have been modulated using respective information signals, and return the thus modulated carrier waves as the reflected waves f1, f2, and f3 to the interrogator 10. The transponders 20, 21, 22 hop the frequencies of the subcarrier waves according to respective different hopping patterns, such that an initial hopping frequency with which each of the frequency hopping patterns begins represents right-hand two bit values of a four-bit identification code of a corresponding one of the transponders 20, 21, 22, and respective hopping frequencies of the each frequency hopping pattern represent respective bit values of four-bit transmission data transmitted from the corresponding transponder 20, 21, 22 to the interrogator 10.
Owner:BROTHER KOGYO KK
Surveillance system using pulse-coded rays
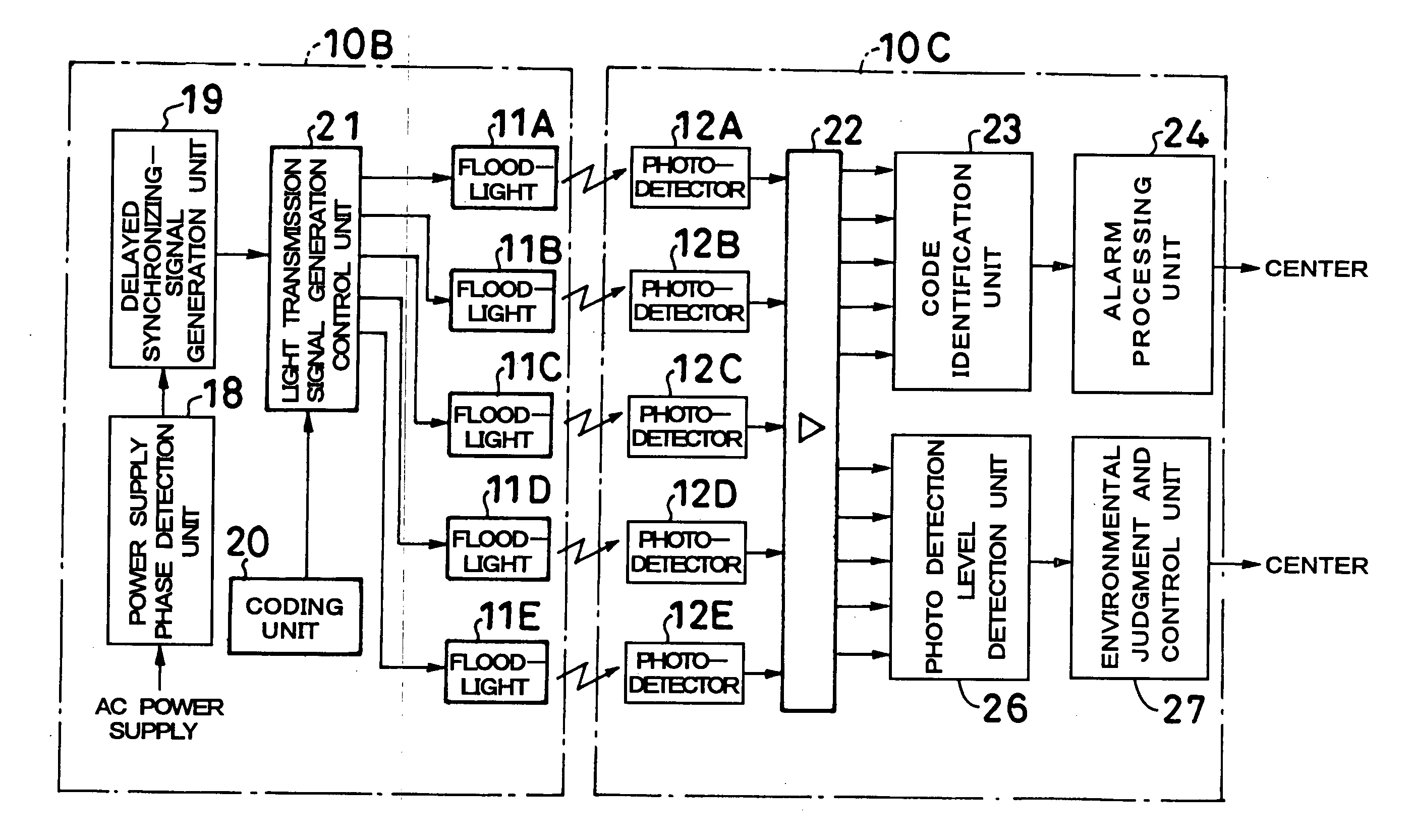
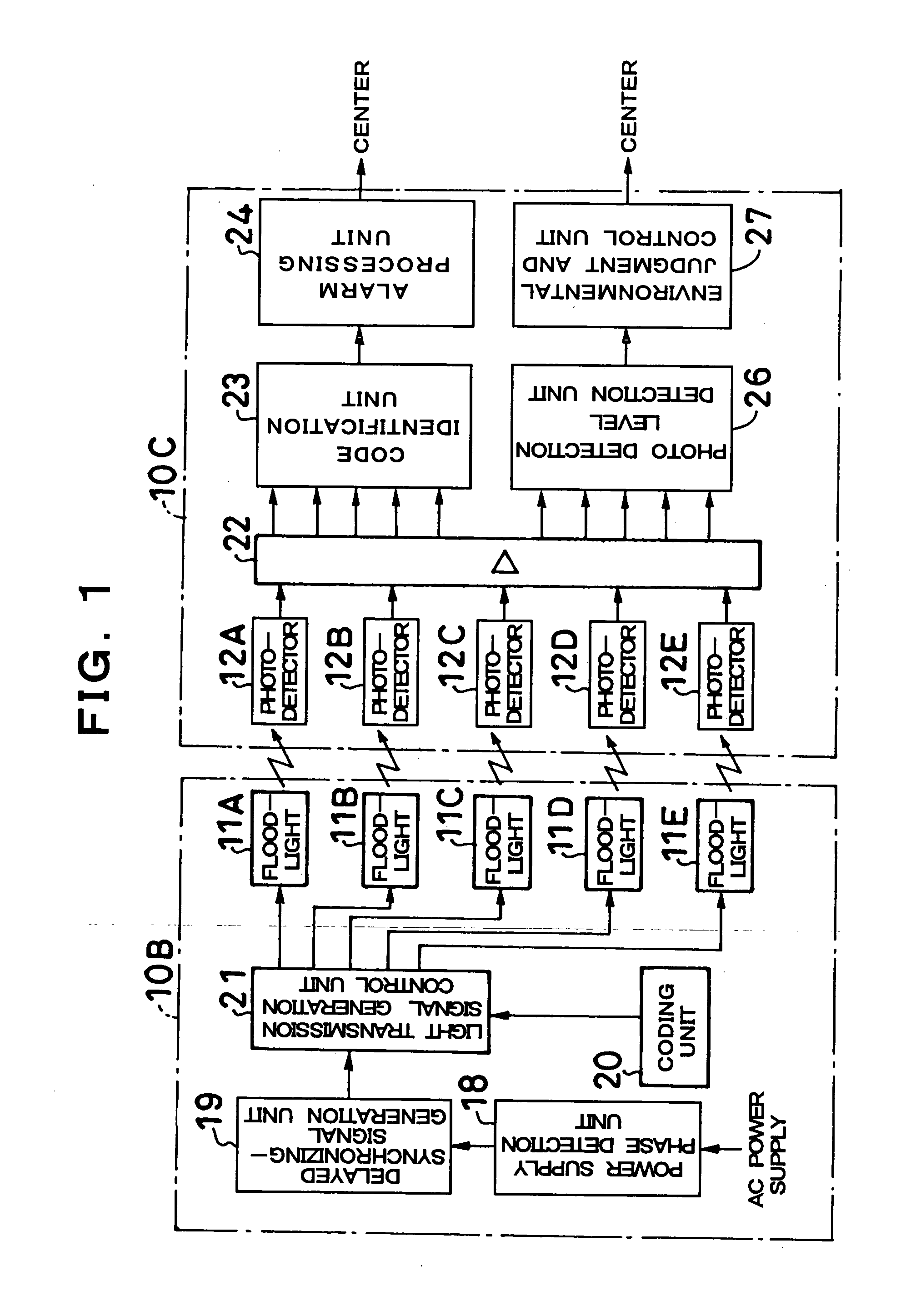
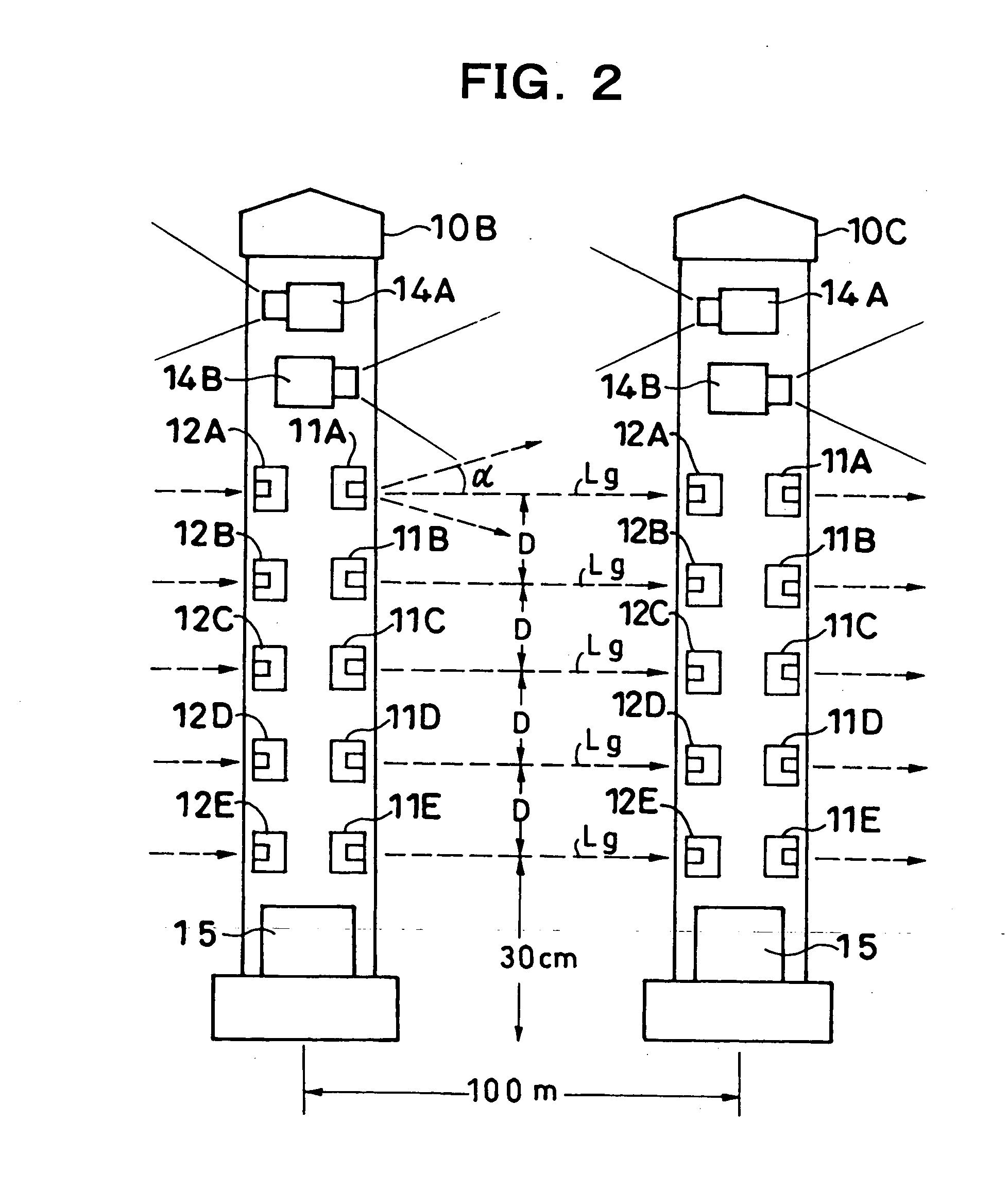
InactiveUS20060072012A1Avoid interferenceSmall probabilityColor television detailsClosed circuit television systemsPhysicsSignal Width
Five infrared sensors are located in different height positions between respective main bodies 10A to 10H, and all of these infrared sensors transmit and receive 35 infrared rays pulse-coded in conformity with a start-stop system. In addition, these pulse-coded infrared rays have the signal width of, for example, 450 μs, and are serially transmitted with a predetermined delay time in a period of 20 ms by a delayed synchronizing-signal. Intrusion surveillance is performed by identifying the pulse codes of these infrared rays. According to this, since not only interference among a plurality of infrared sensors is prevented, but also infrared rays are outputted in a short time, the occurrence of false alarms etc. decreases remarkably.
Owner:UNTERHALTUNGSSOFTWARE SELBSTKONTROLLE
Game service provision device and method
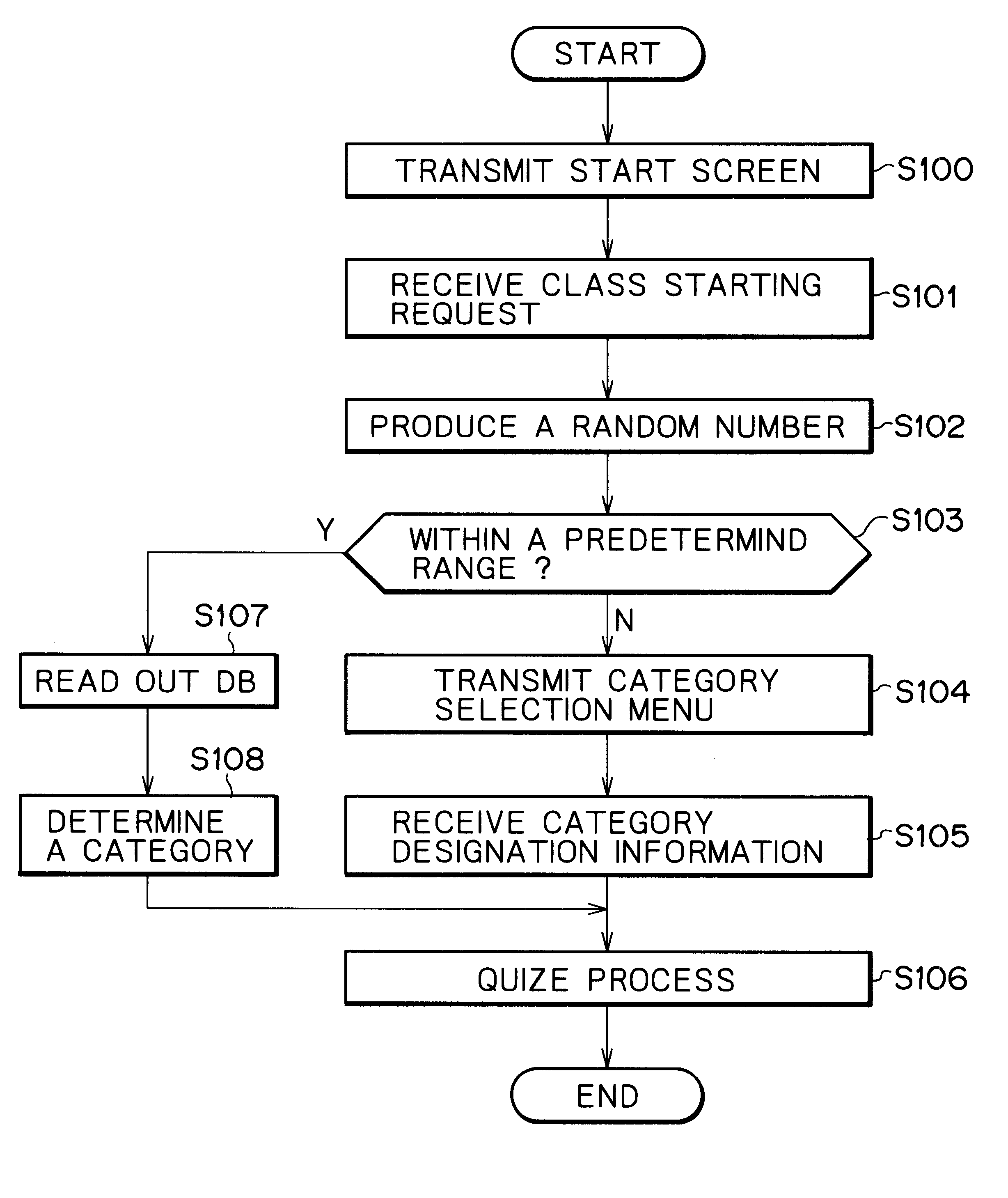
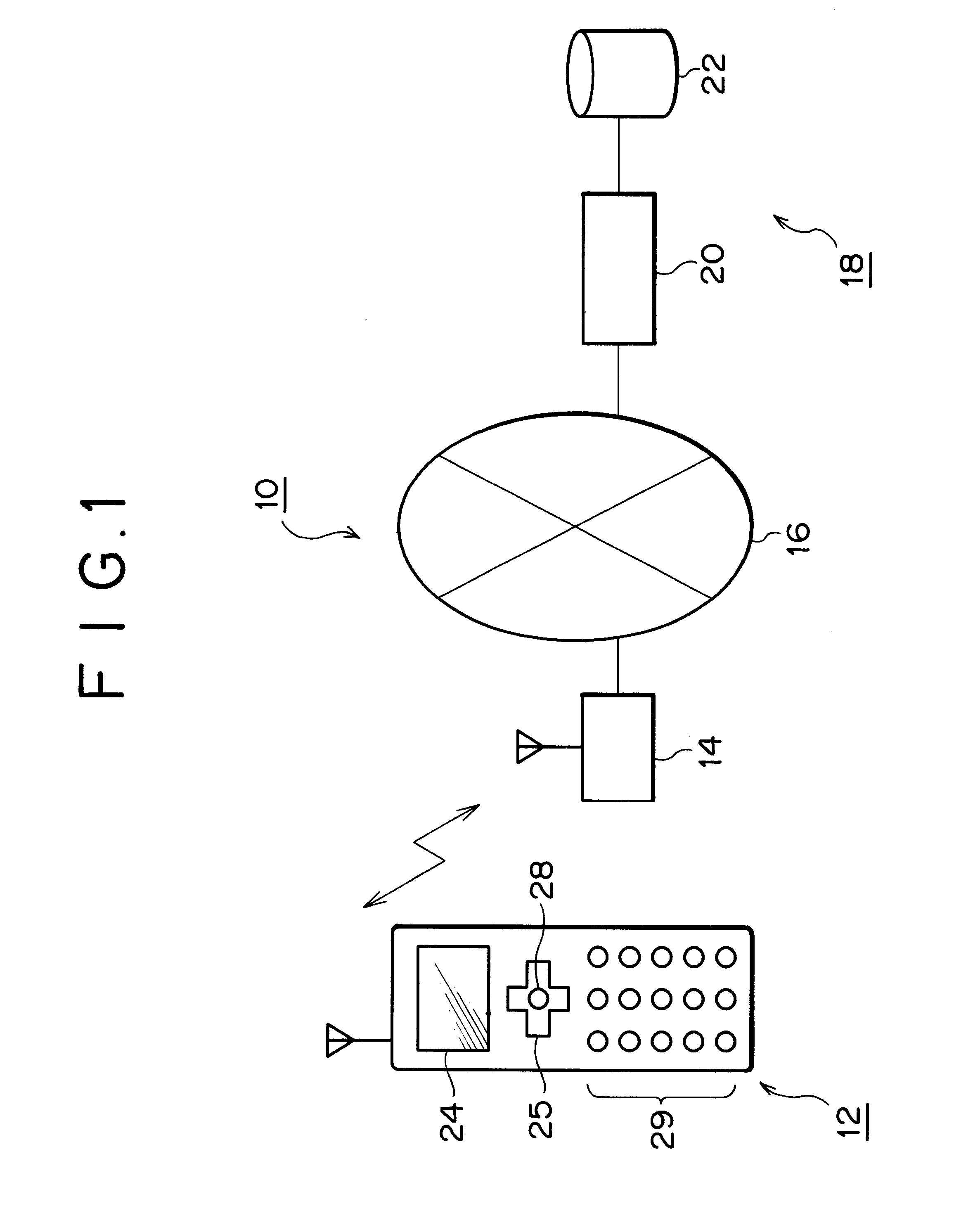
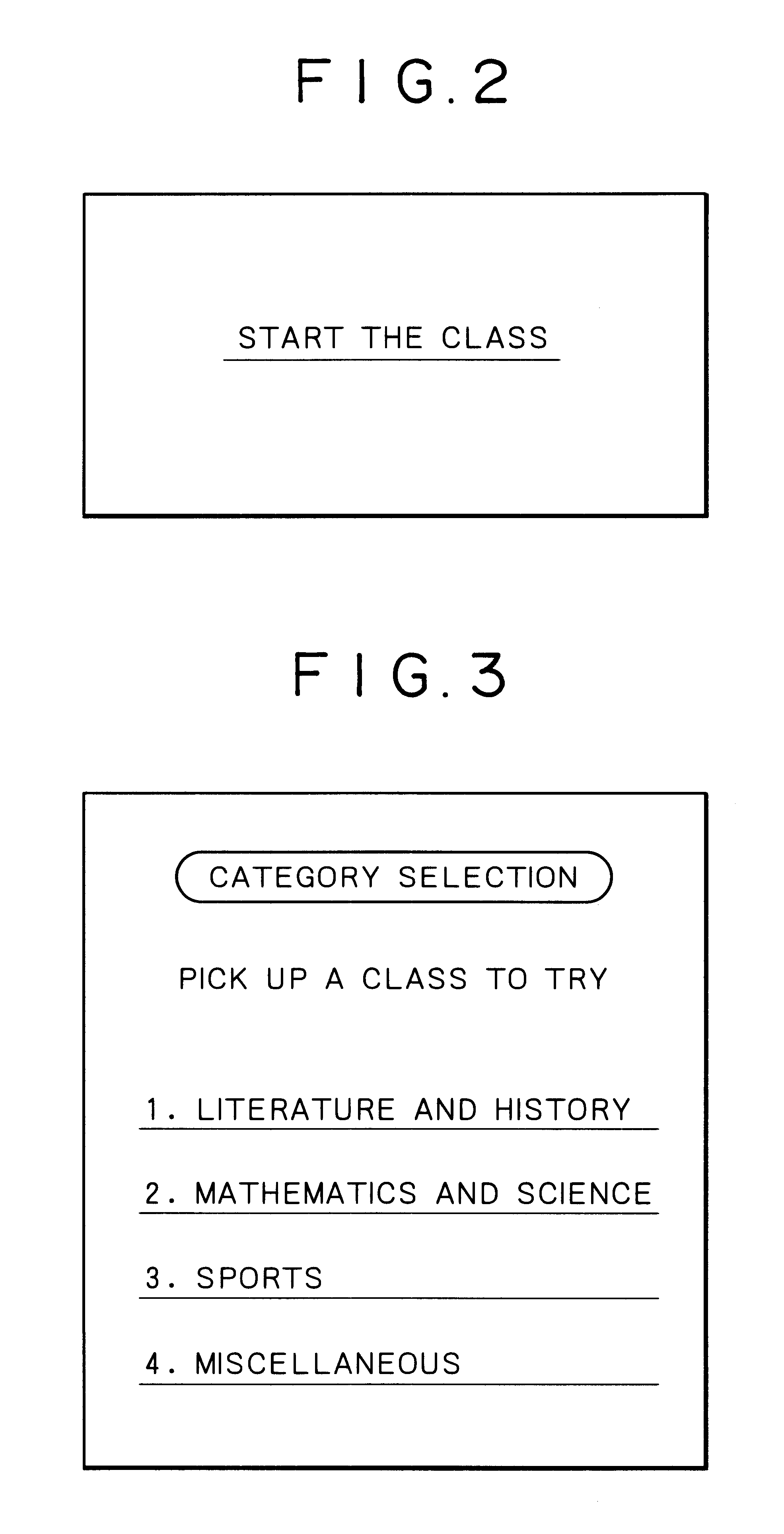
InactiveUS6565437B2Increase excitementSmall probabilityVideo gamesSpecial data processing applicationsService provisionMultimedia
In addition to an optional game service in accordance with a designation made by a player, a compulsory game service not directly related to the designation by the player can be provided. A game service provision device is configured so as to perform the steps of receiving a game service request from a player (S101), transmitting a game service designation request to said player in response to said game service request (S104), receiving a game service designation transmitted from said player in response to said game service designation request for designating at least one of a plurality of game services (S105), transmitting the game service designated by said game service designation to said player as an optional game service (S106), and transmitting to said player a compulsory game service selected from said plurality of game services based on predetermined basic information associated with said player at a predetermined probability instead of said game service designation request when said game service request is received (S106-S108).
Owner:KONAMI DIGITAL ENTERTAINMENT CO LTD
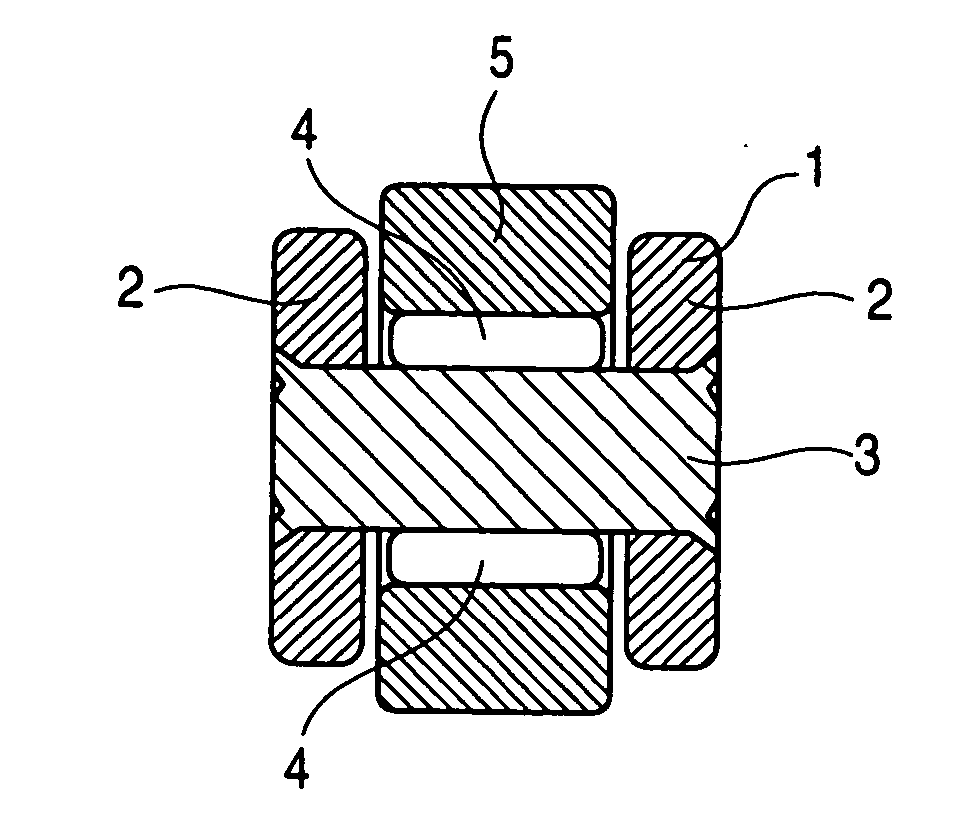
Rolling/sliding part, rolling bearing, cam follower, and method of modificating surface of rolling/sliding part
The invention provides a cam follower having an outer ring which is used in a state where the cam follower comes into sliding contact or rolling contact with a mating part. The outer ring is configured such that the hardness of a surface layer portion existing between the surface and at least 3 μm below the surface is Hv 780 to 900, and the hardness of an internal surface portion existing at a depth of 10 μm or more from the surface is lower than the hardness of the surface layer portion and less than Hv 780. Such hardness can be obtained by performing soft shot blasting or flow barrel processing on a surface layer portion of a base material to be the outer ring.
Owner:JTEKT CORP
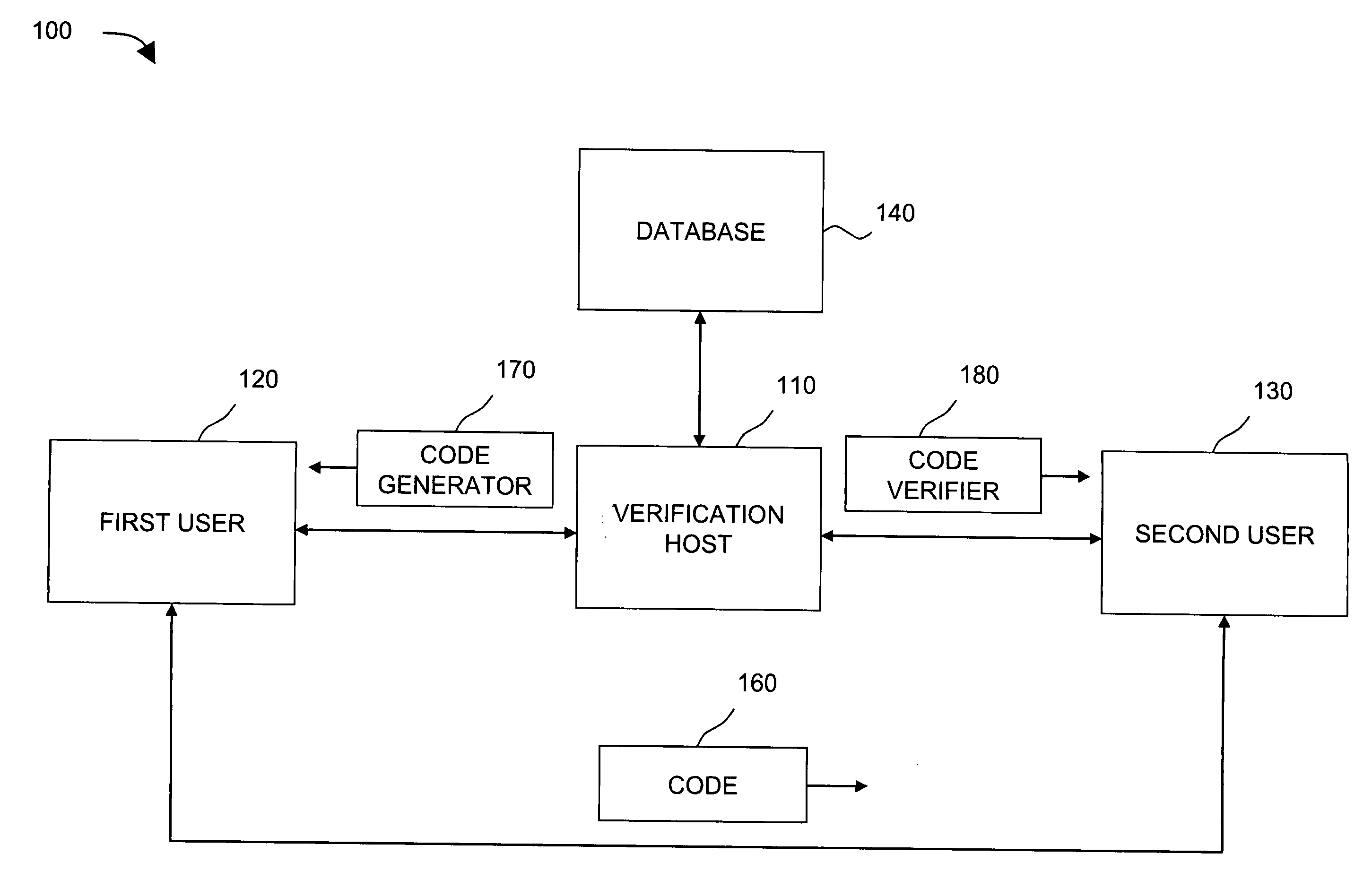
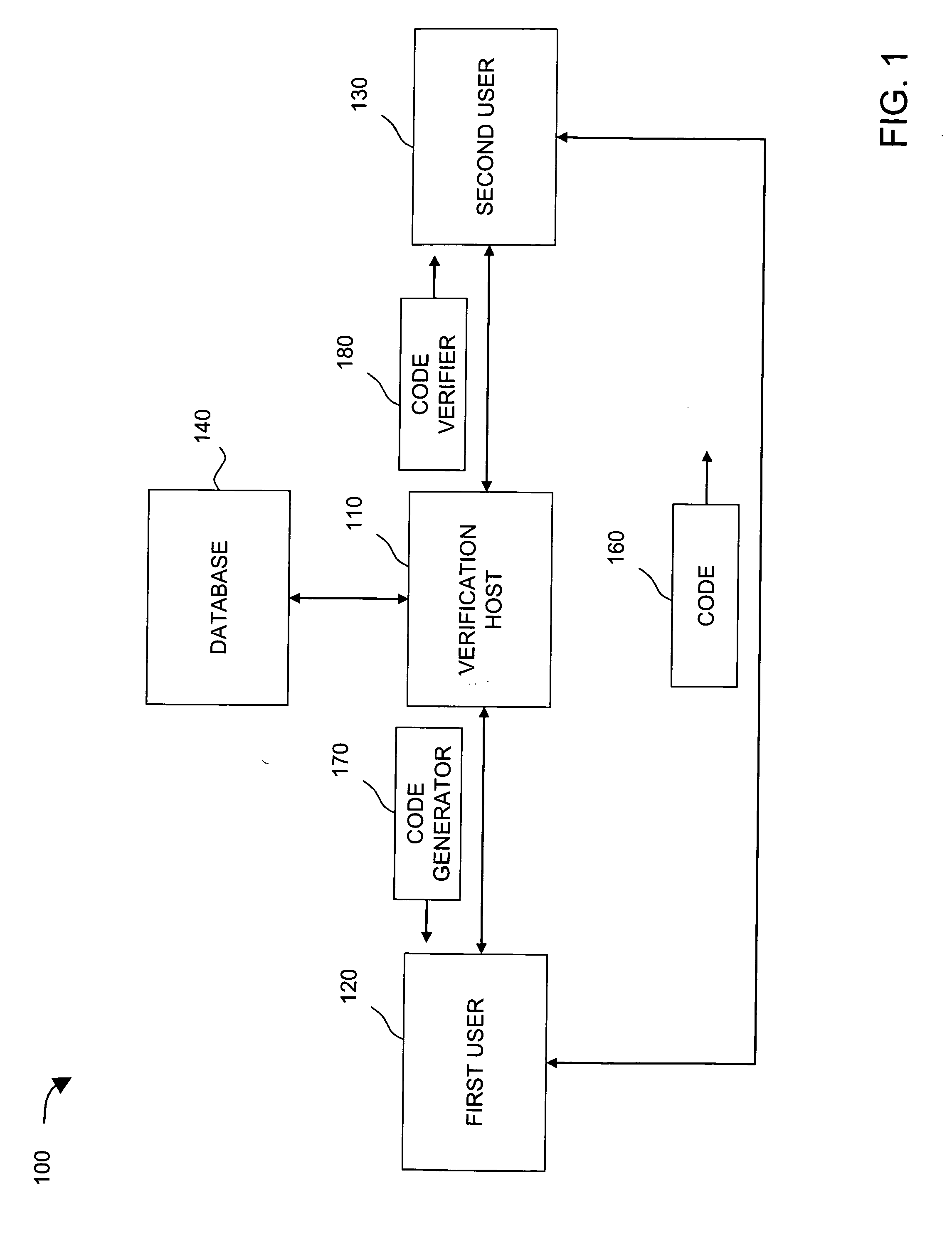
Method and system for anonymous information verification
InactiveUS20080295151A1Small probabilityProbability to forgeDigital data processing detailsUser identity/authority verificationUser needsRelevant information
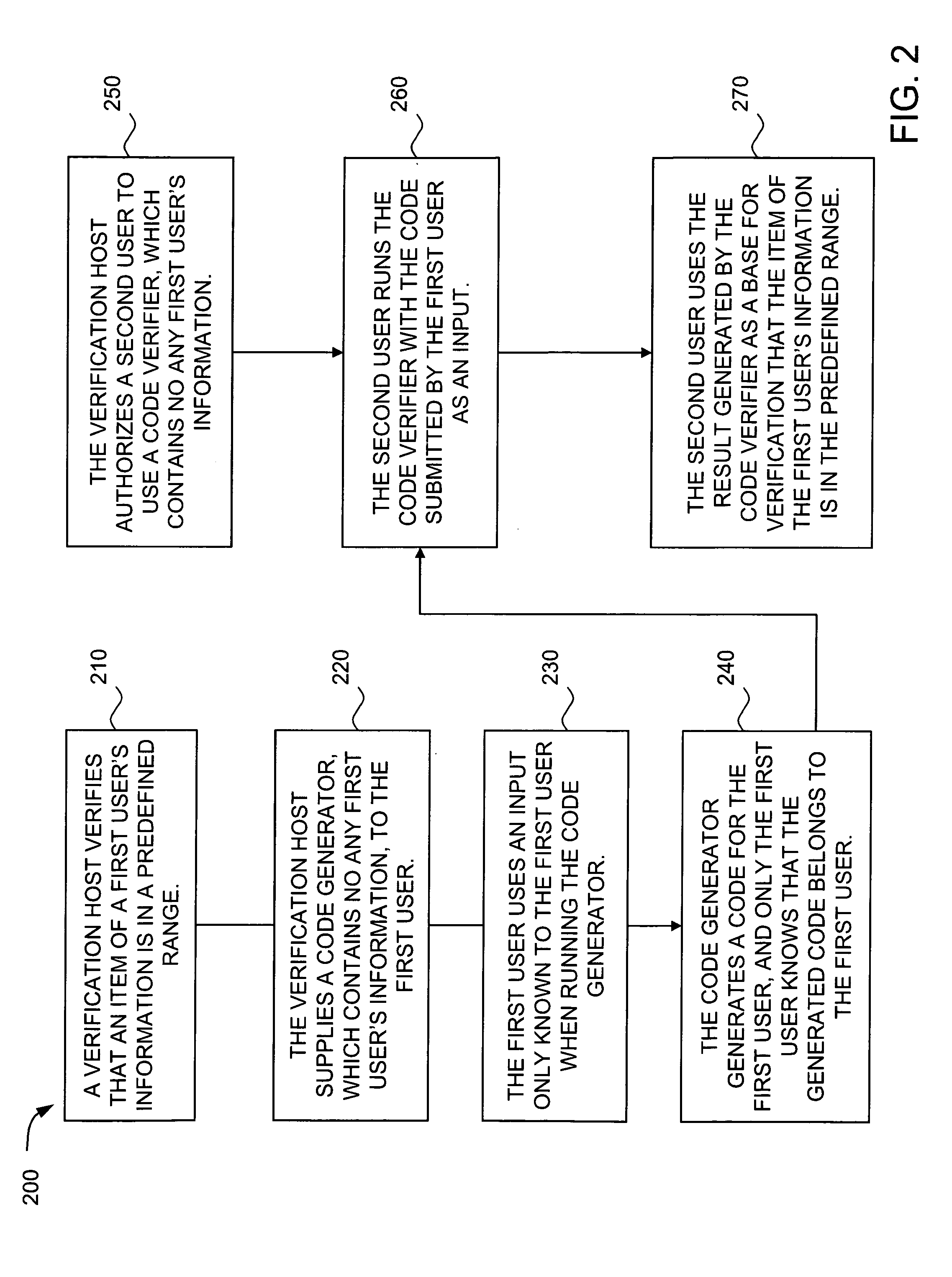
A first user contacts a verification host and claims that an item of the first user's information is in a predefined range with relevant information submitted. The verification host verifies the first user's claim, and provides a code generator to the first user if the claim is valid. The first user generates a code by running the code generator with an input only known to the first user. The code generator combines an input determined by the verification host and the input by the first user into a combined input, encrypts the combined input, and generates a code based on the encrypted combined input. The generated code contains a first portion, which is determined by the verification host and contains no any first user's information, and a second portion, which is related to the first user's input when running the code generator. Only the first user knows that the generated code belongs to the first user. A second user contacts the verification host to obtain a code verifier for a need to verify that the item of the first user's information is in the predefined range. The verification host provides a code verifier to the second user. When the second user needs to verify that an item of the first user's information is in a predefined range, the second user only needs to verify the relevant code submitted by the first user by running the code verifier. The code verifier decrypts the code submitted by the first user, compares a part of the code verifier determined by the verification host, which contains no any first user's information, with the first portion of the decrypted code, and return a result to the second user. The first user's identity and privacy are fully protected during the code verification process with the method and system disclosed here.
Owner:XIA TIEJUN JAY
Hydraulic steering
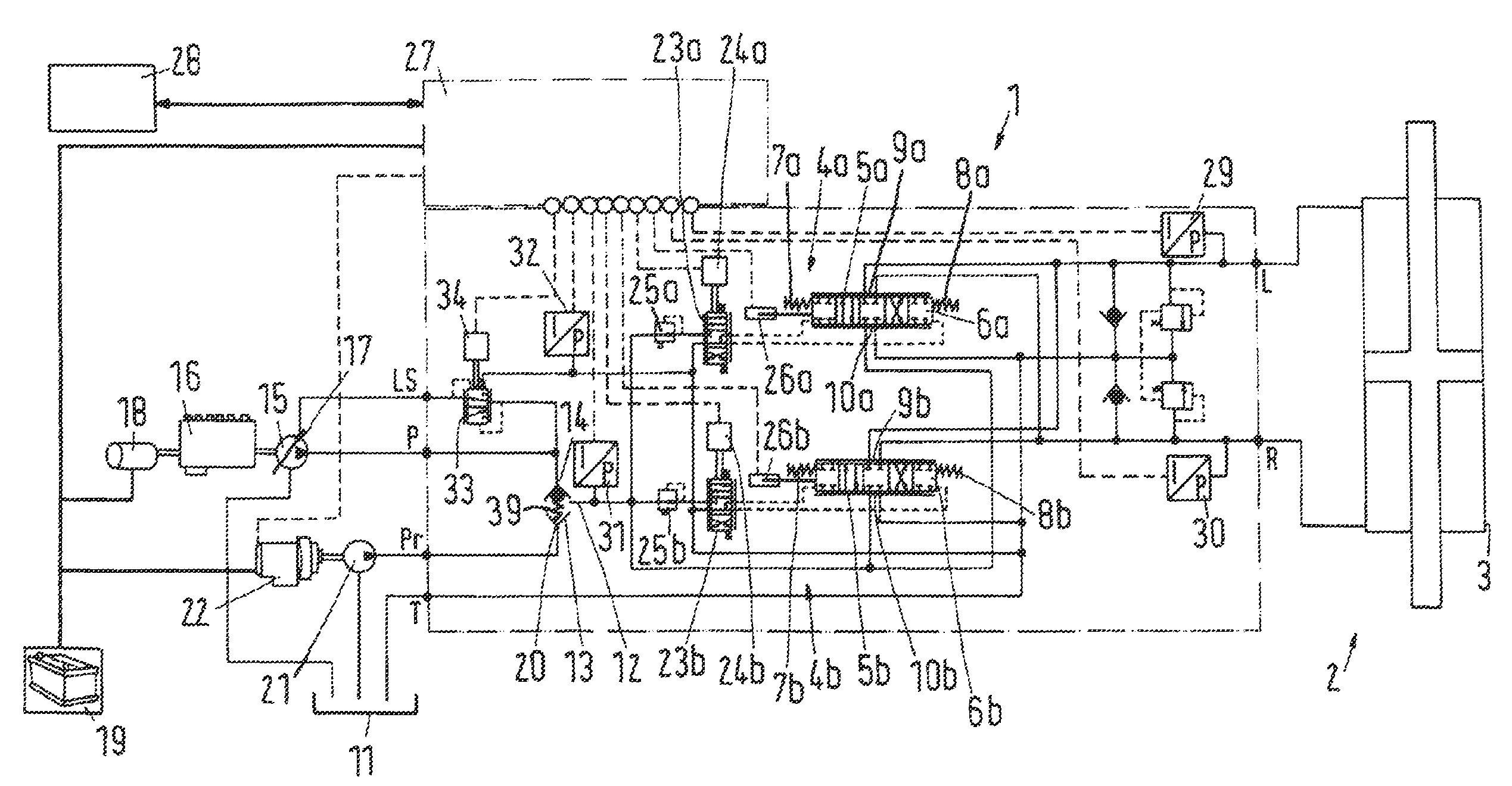
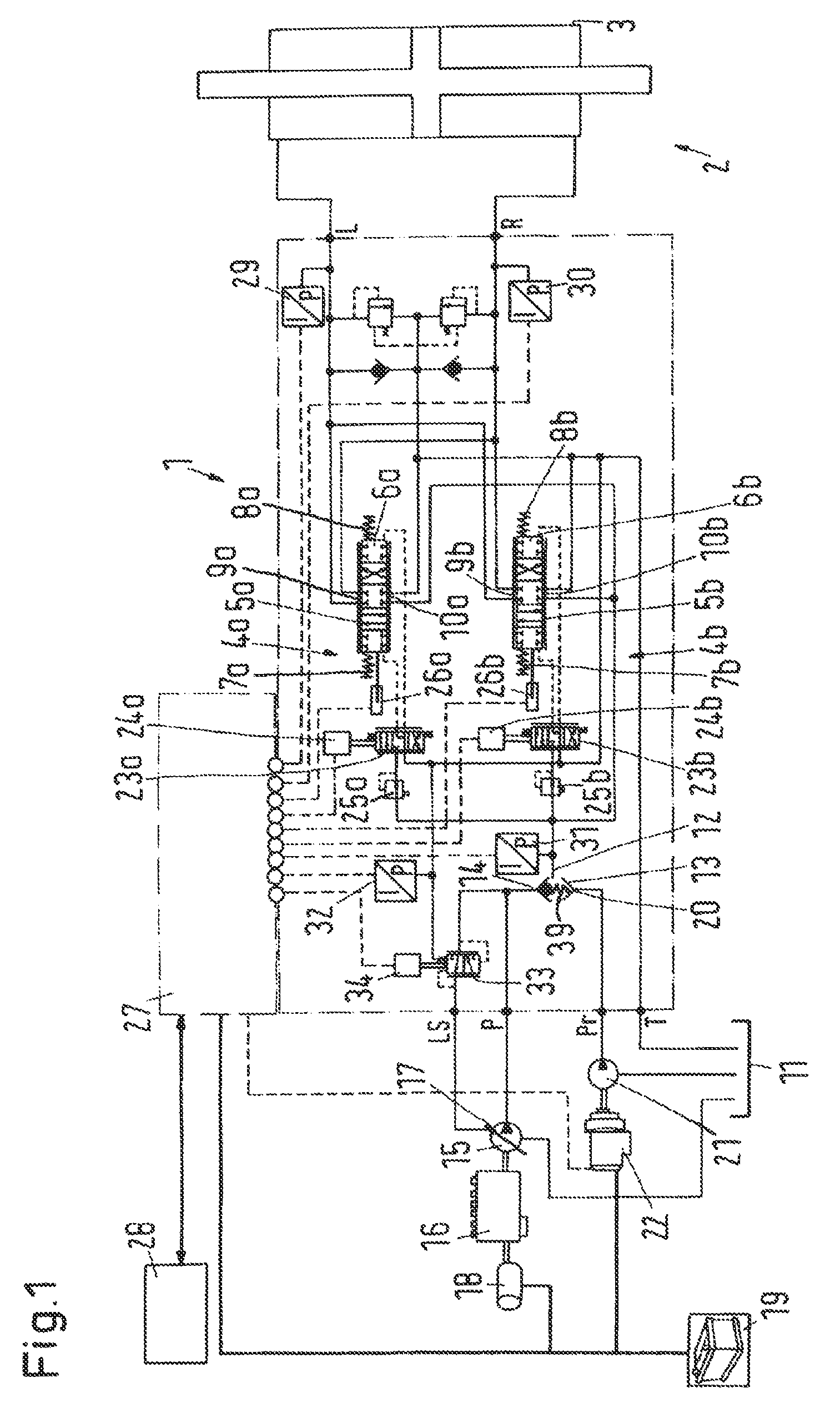
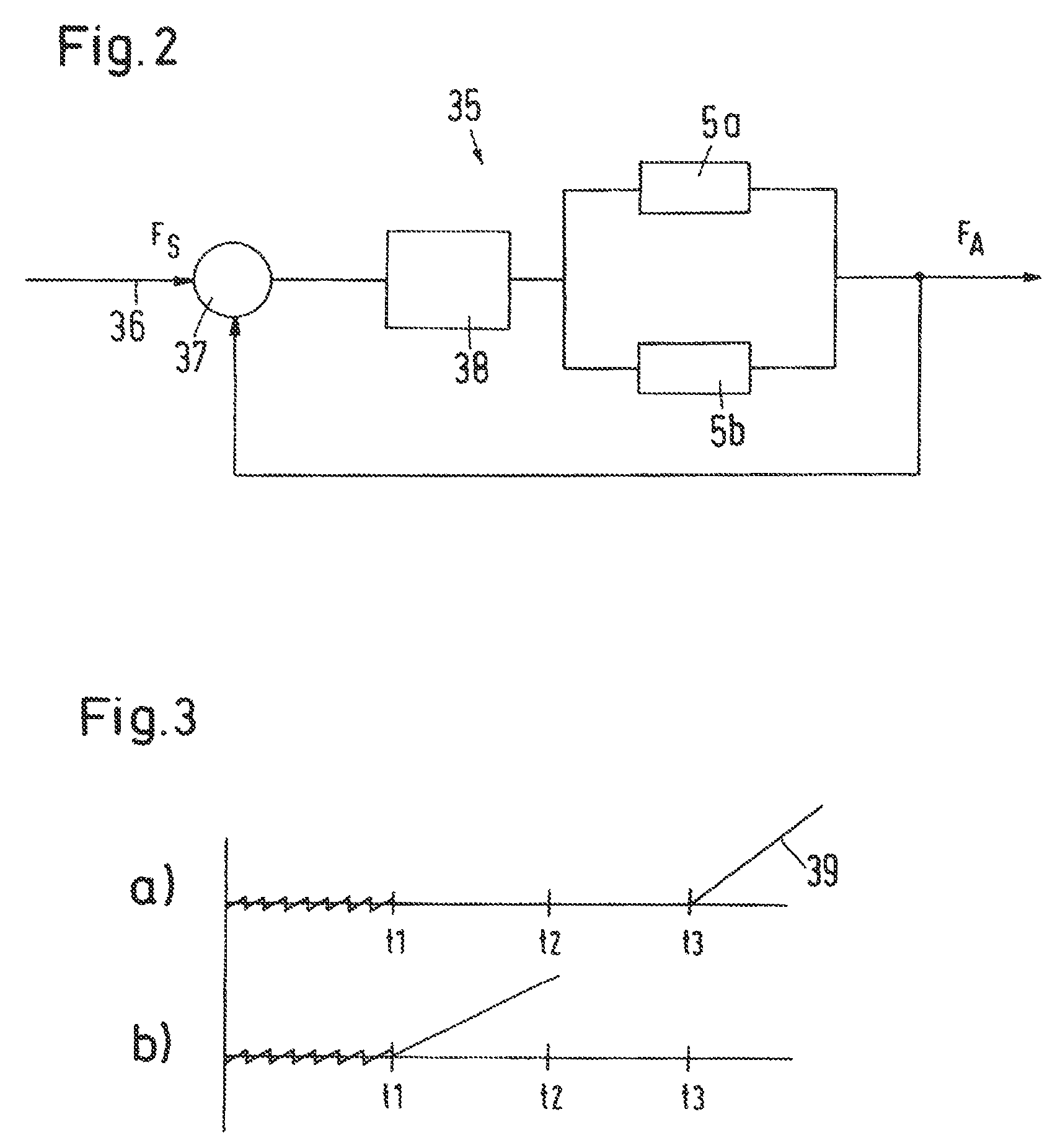
ActiveUS20070251755A1Faster reacting systemSmall probabilityMechanical steeringFluid steeringElectric machineryControl theory
The invention concerns a hydraulic steering with a steering motor arrangement having at least one steering motor, and with at least two steering circuits, each having a steering valve that interrupts a path from a pressure supply to the steering motor arrangement in the neutral position and releases a path from the pressure supply to the steering motor arrangement on a movement out of the neutral position. It is endeavoured to simplify the embodiment of such a steering. For this purpose, the steering valve (5a, 5b) has two end positions, one on each side of the neutral position, in which positions a path from the pressure supply (15, 21) to the steering motor arrangement (2) is interrupted.
Owner:DANFOSS PAUER SOLYUSHENS APS
Depth sensing apparatus and method
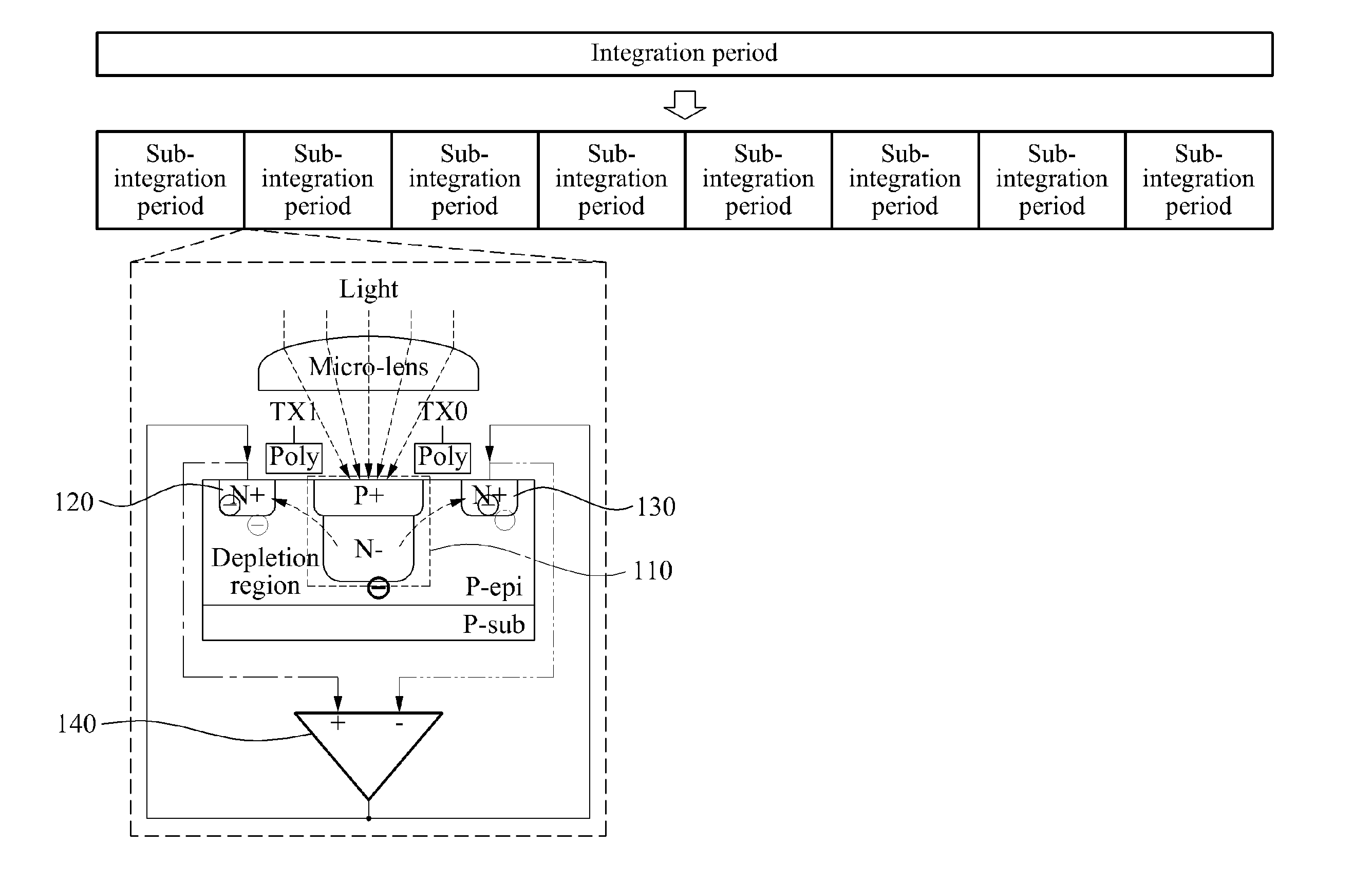
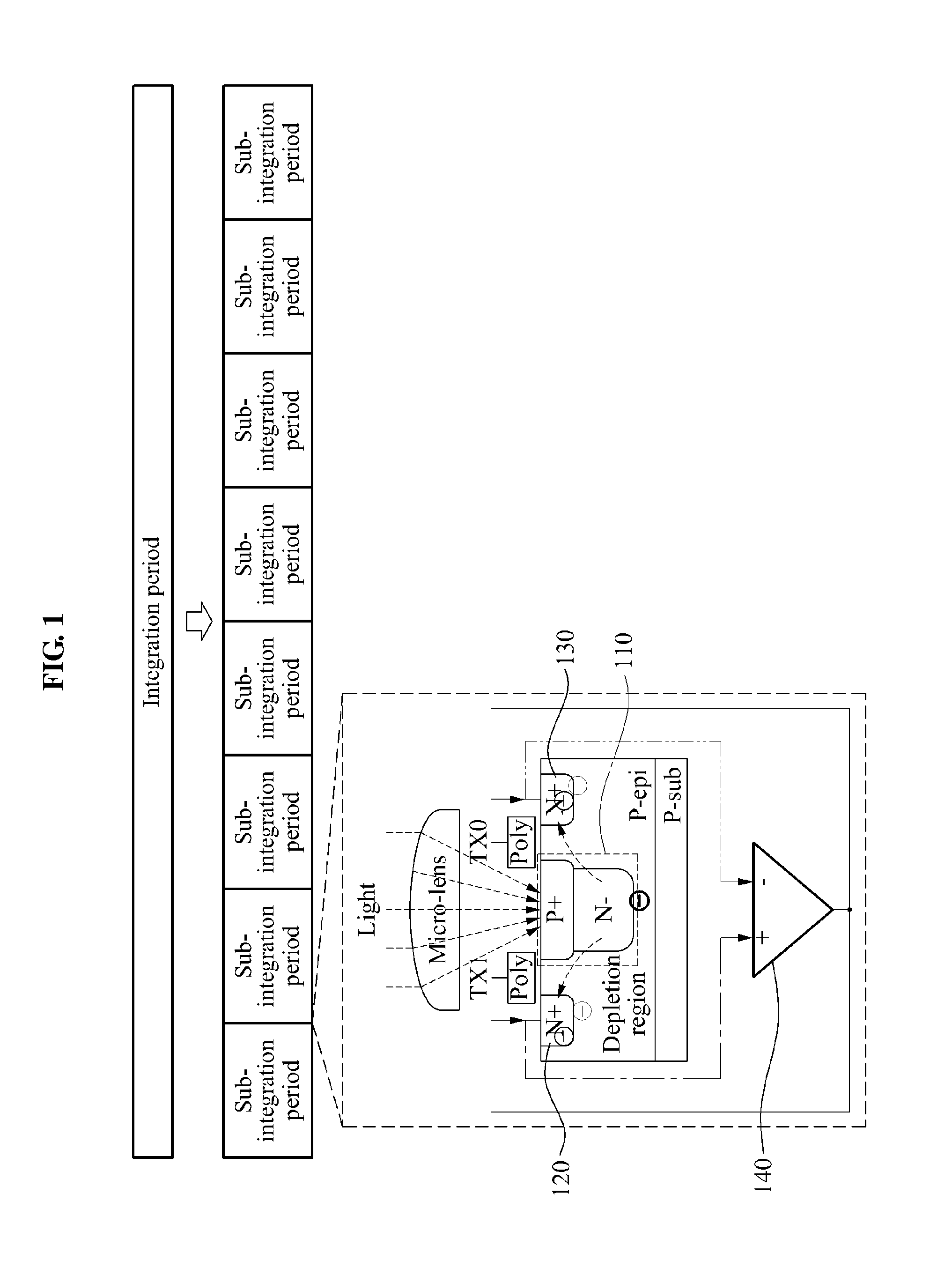
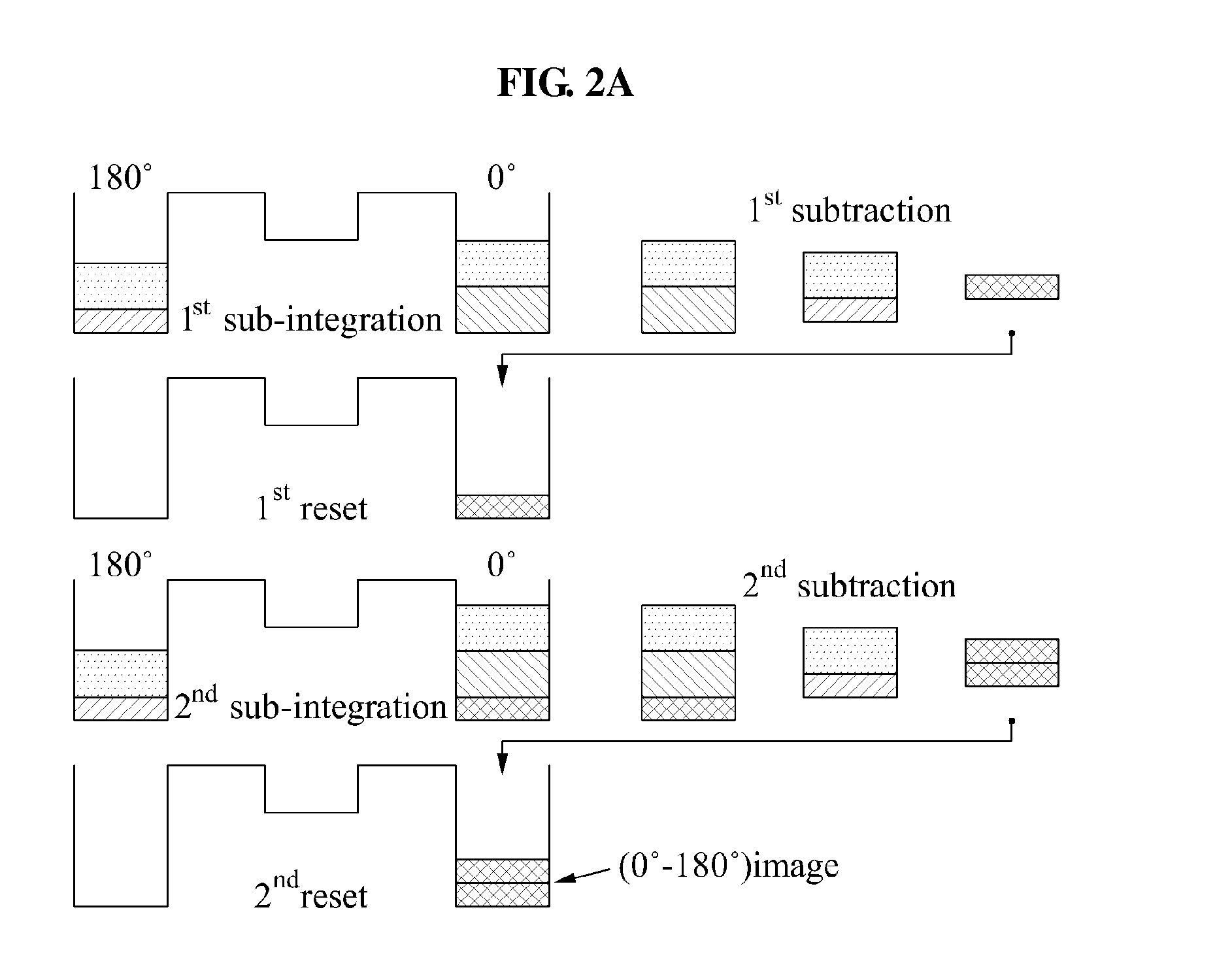
ActiveUS20140028883A1Small probabilityTransistorTelevision system detailsEngineeringFloating diffusion
A depth sensing apparatus and method for acquiring a depth image of a target object may calculate a difference voltage between a first floating diffusion node and a second floating diffusion node, based on a voltage of a photodiode stored in the first floating diffusion node in a first phase interval and a voltage of the photodiode stored in the second floating diffusion node in a second phase interval, using a sub-integration period, may feed back the difference voltage to one of the first floating diffusion node and the second floating diffusion node, and may calculate a depth value of a pixel based on difference voltages accumulated during an integration period including sub-integration periods.
Owner:SAMSUNG ELECTRONICS CO LTD
System, method and apparatus for reliable detection of extra system signals for a multi-node RLAN system
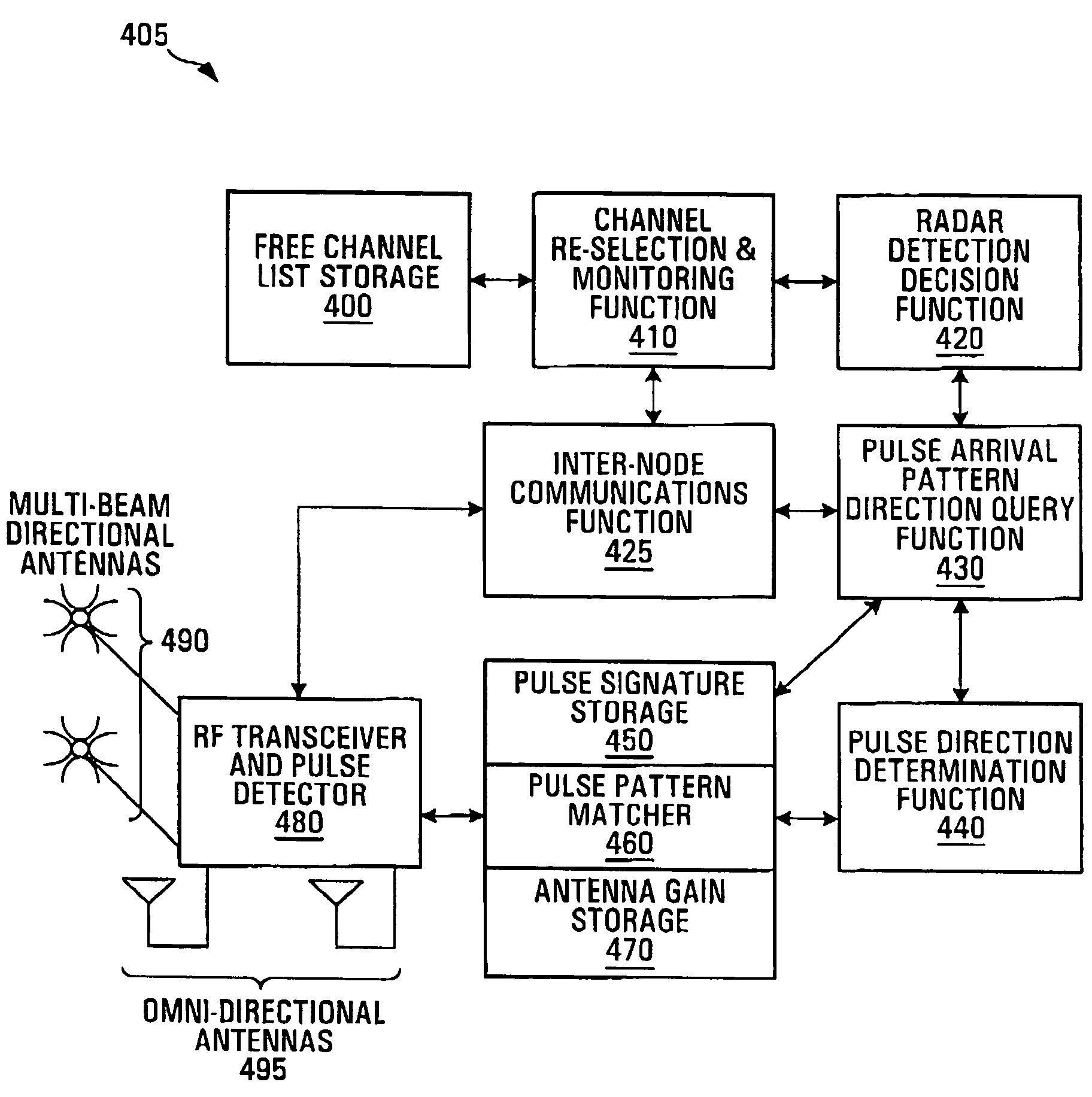
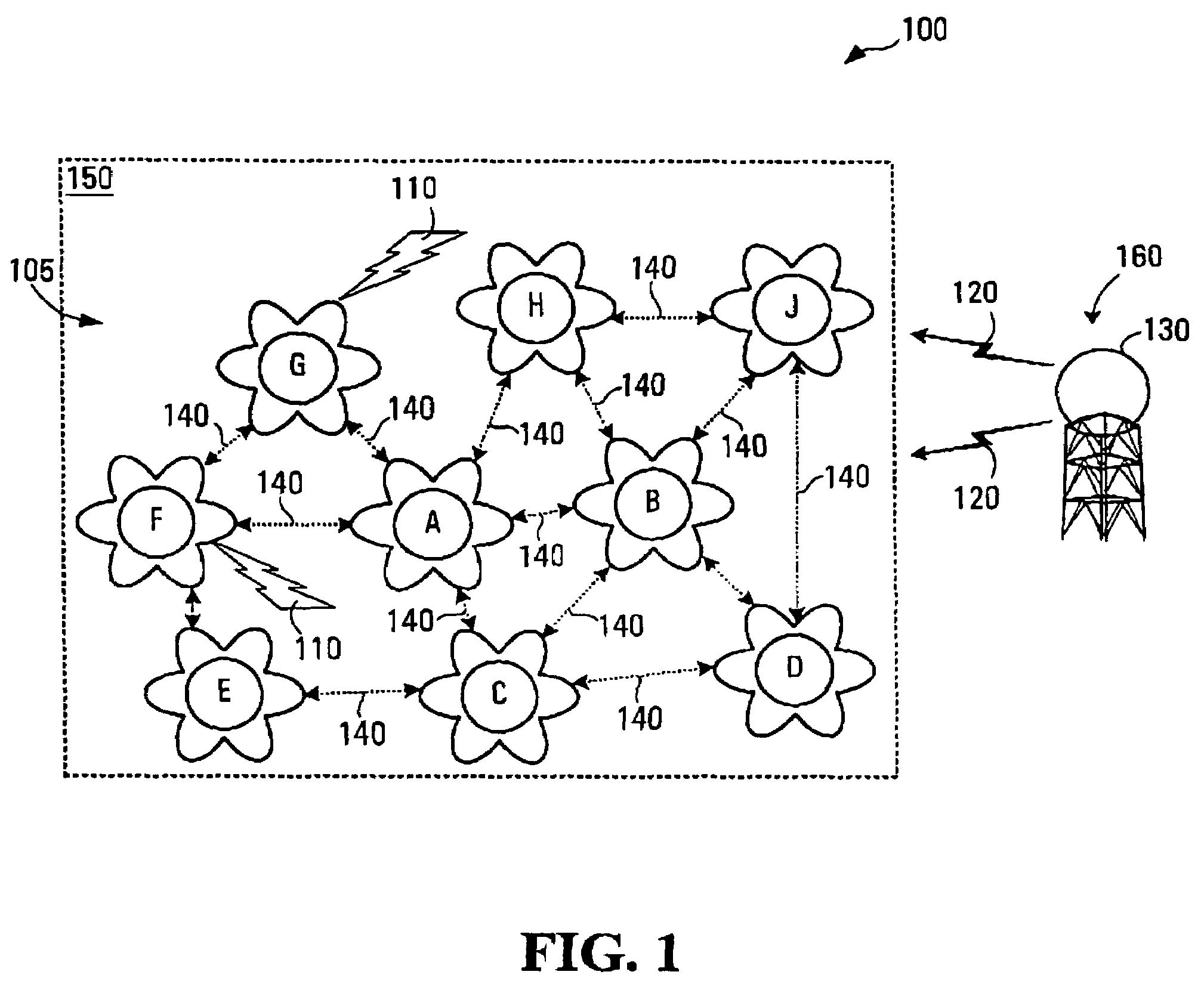
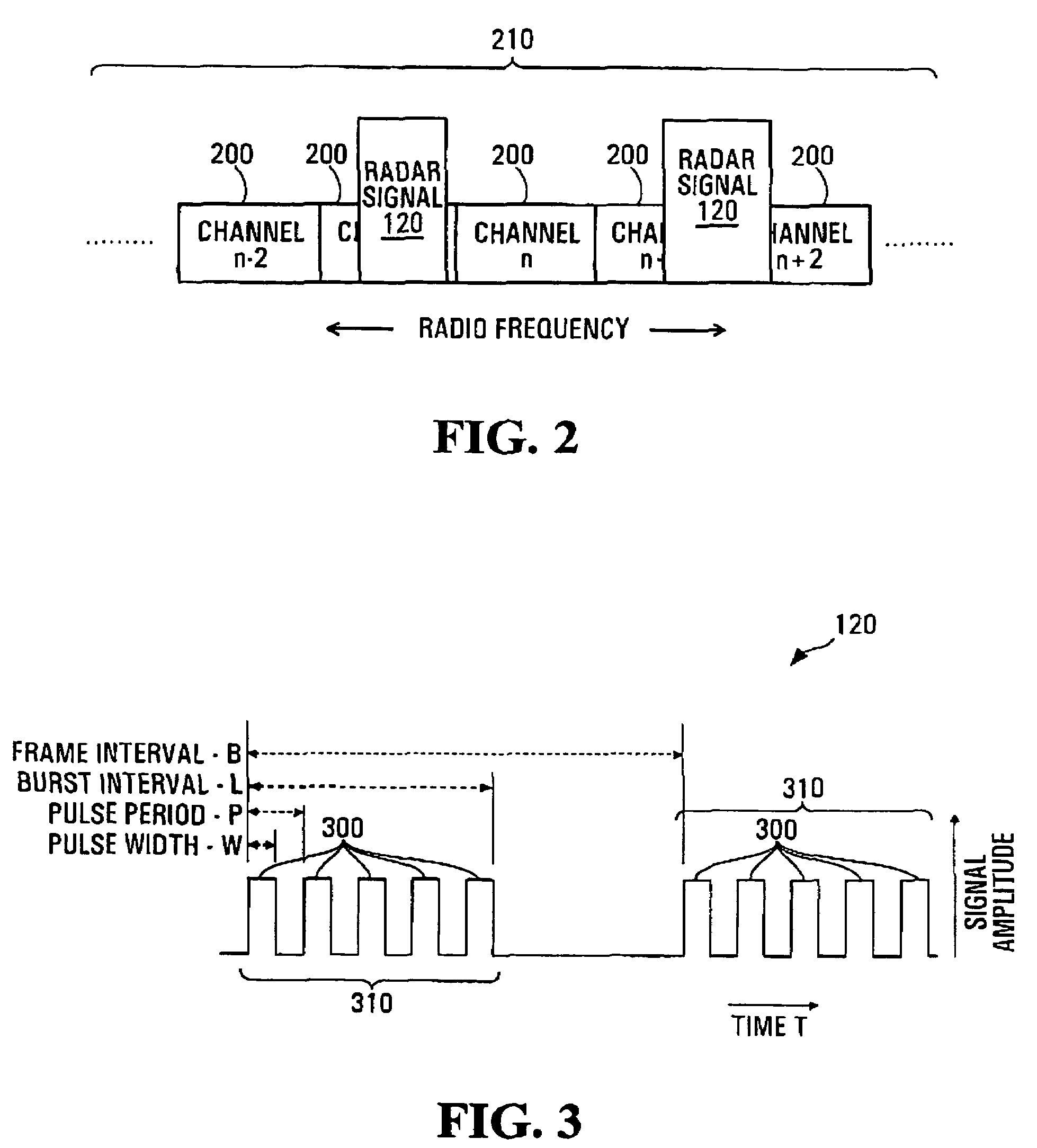
InactiveUS7647061B1Improve detection reliabilityImprove efficiencyNetwork topologiesTransmission monitoringRadar systemsPulse pattern
A method of detecting extra-system signals in a multi-node RLAN (radio local area network) involves: at each of a plurality of nodes in the RLAN, processing at least one respective received signal to produce detection results and deciding whether an extra-system signal has or has not been detected based on detection results of at least two of the plurality of nodes. The extra-system signal is for example a signal from a RADAR system. The detection results are produced using pulse pattern matching for example. Furthermore, in some implementations a decision as to whether an extra-system signal has or has not been detected is based on a comparison of a detection signature for at least two of the nodes to see if there is a substantial match. In some implementations the decision is further based on information representative of a direction of arrival of respective received signals.
Owner:APPLE INC
Quantitation of Human Genomic DNA
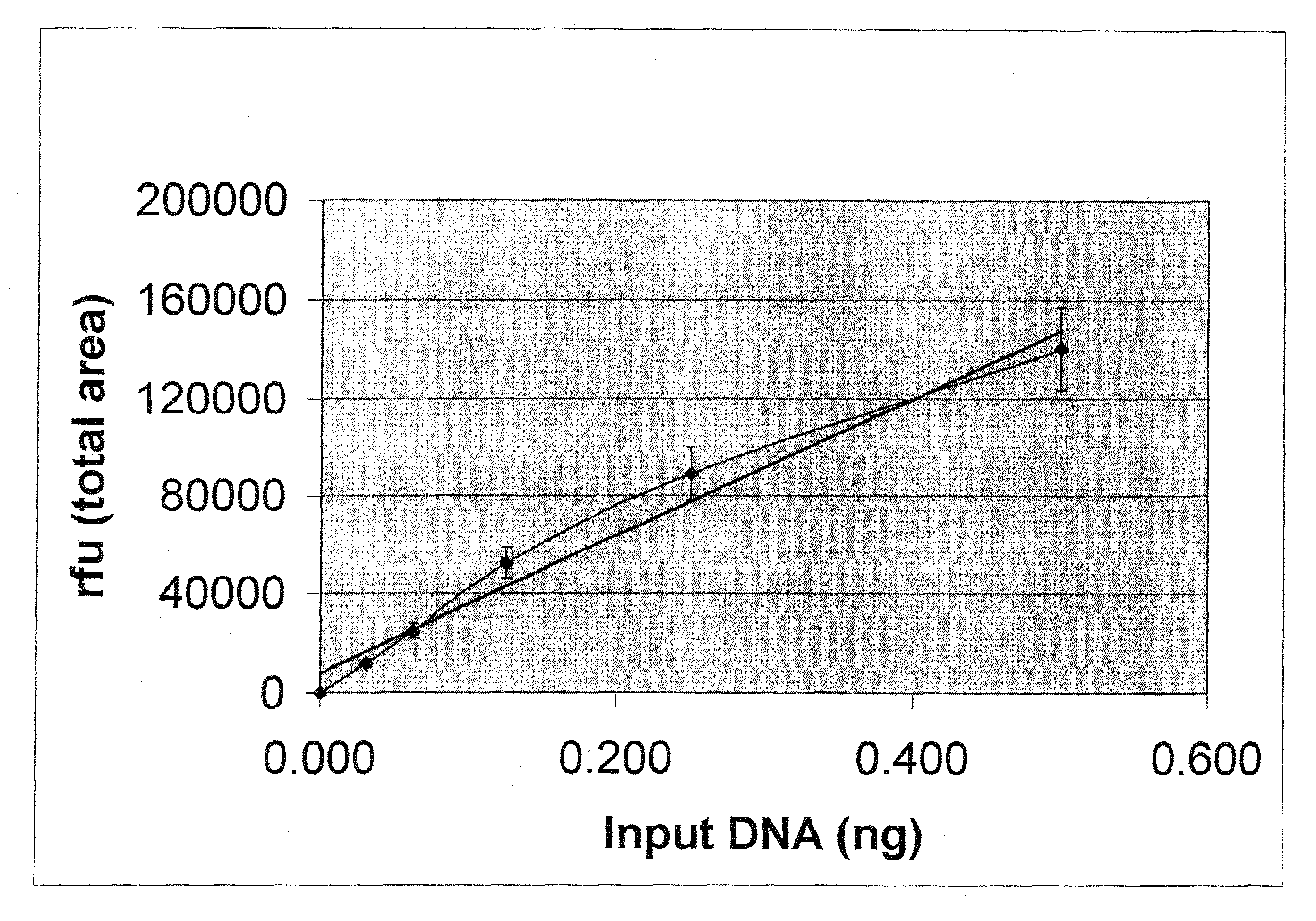
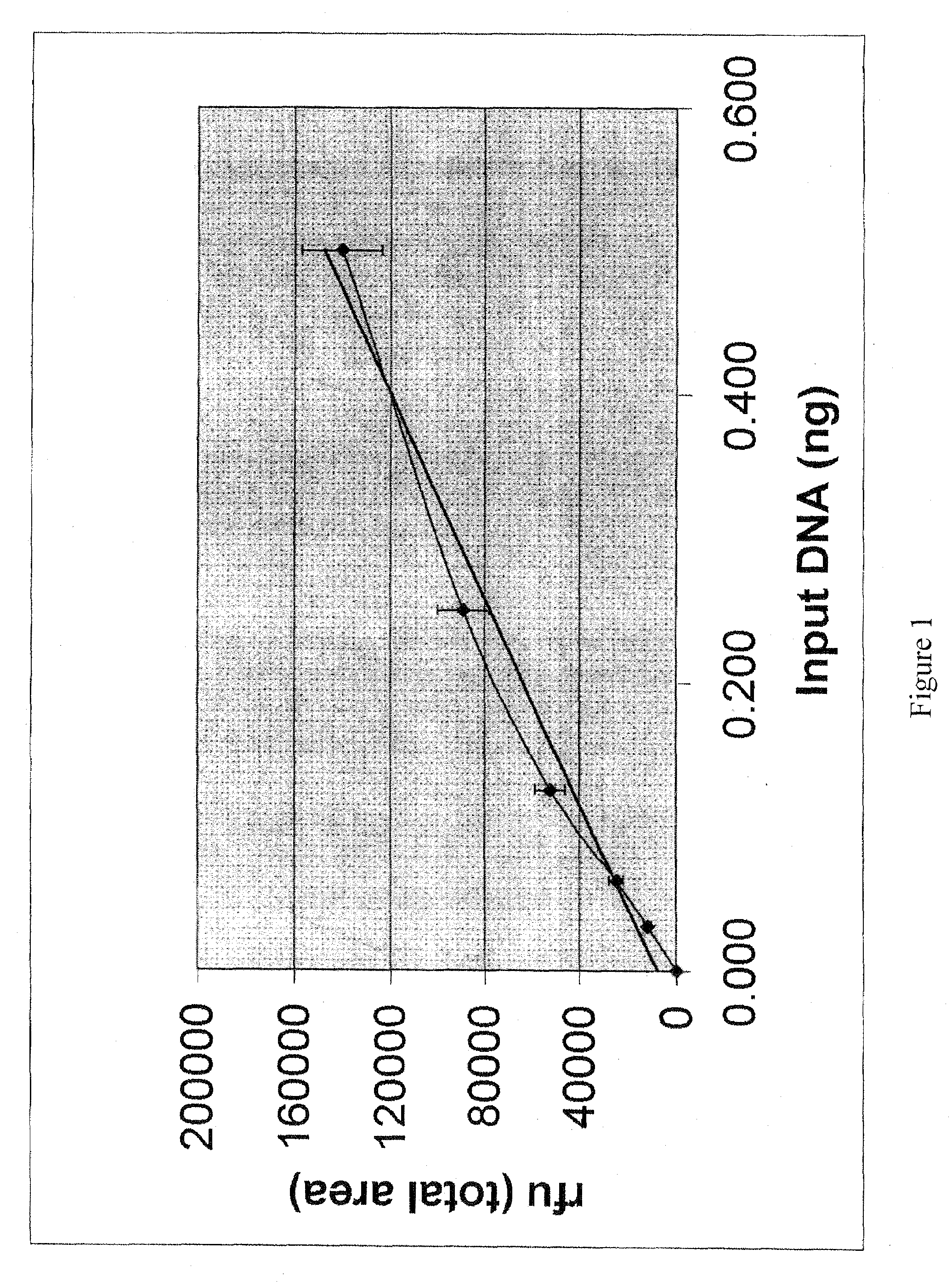
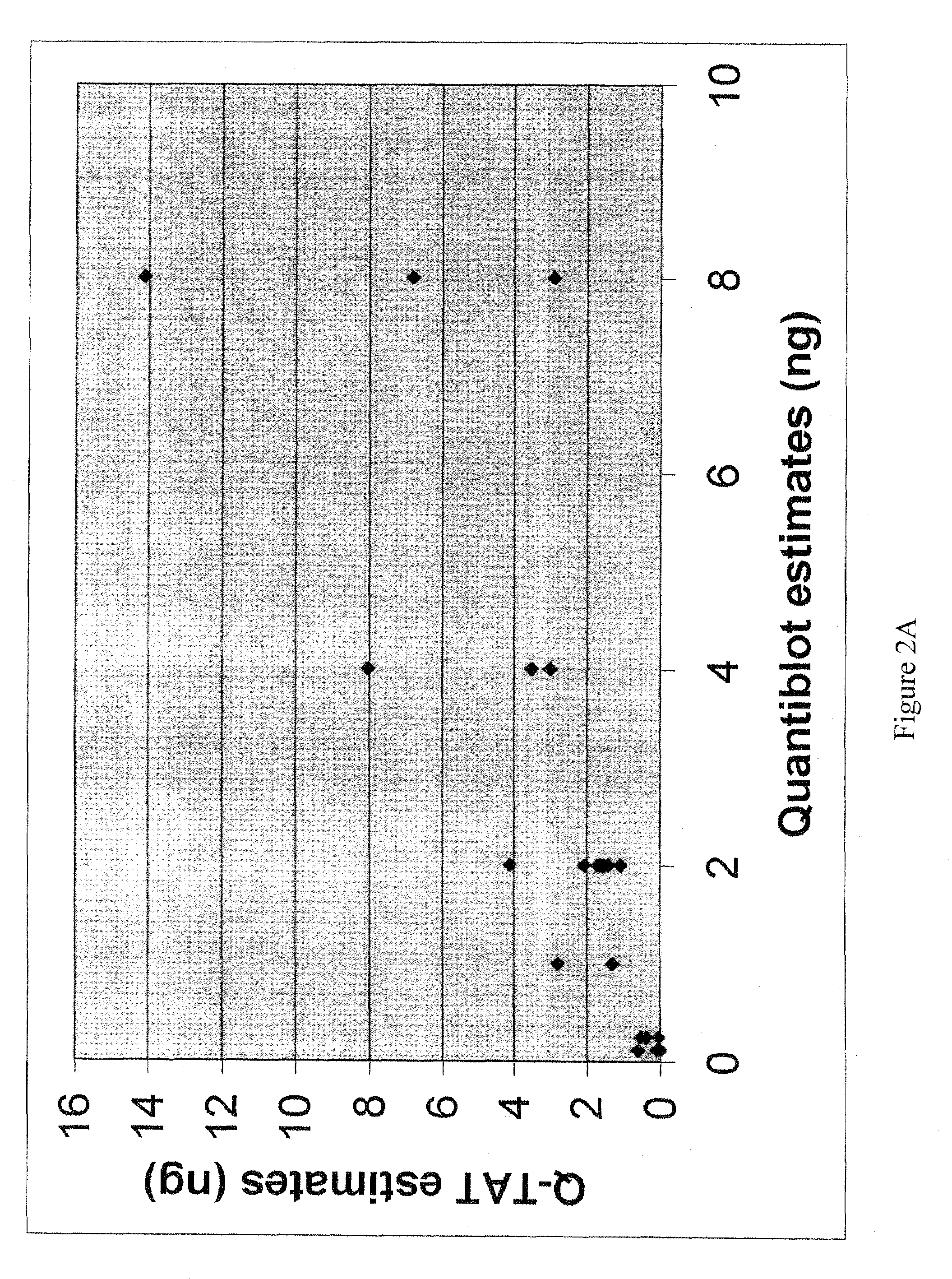
ActiveUS20080153099A1Reliable signalSmall probabilityMicrobiological testing/measurementFermentationY-Chromosome GenesPolymerase chain reaction
Methods are provided for determining, in a single polymerase chain reaction (PCR) reaction, the quantity, quality, and gender of origin of DNA in a sample, and whether or not the sample contains PCR amplification inhibitors. The methods involve carrying out a single PCR multiplex reaction utilizing primer sets specific for amplifying the human amelogenin locus, an X- and / or Y-chromosome specific gene that is shorter than the amelogenin gene, and a heterologous, non-human reporter gene.
Owner:BOARD OF REGENTS FOR OKLAHOMA STATE UNIVERSITY
Vehicle electronic key system
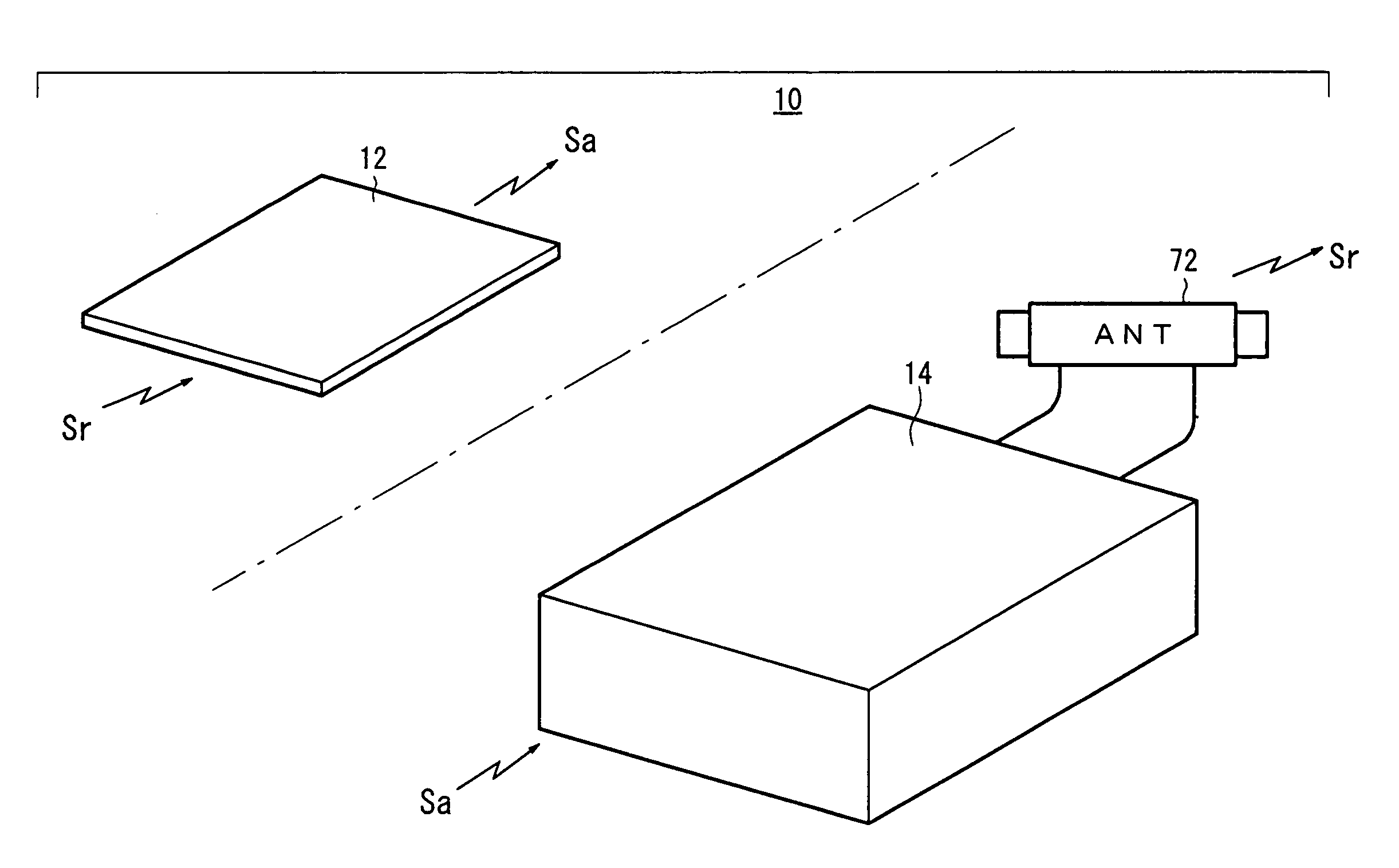
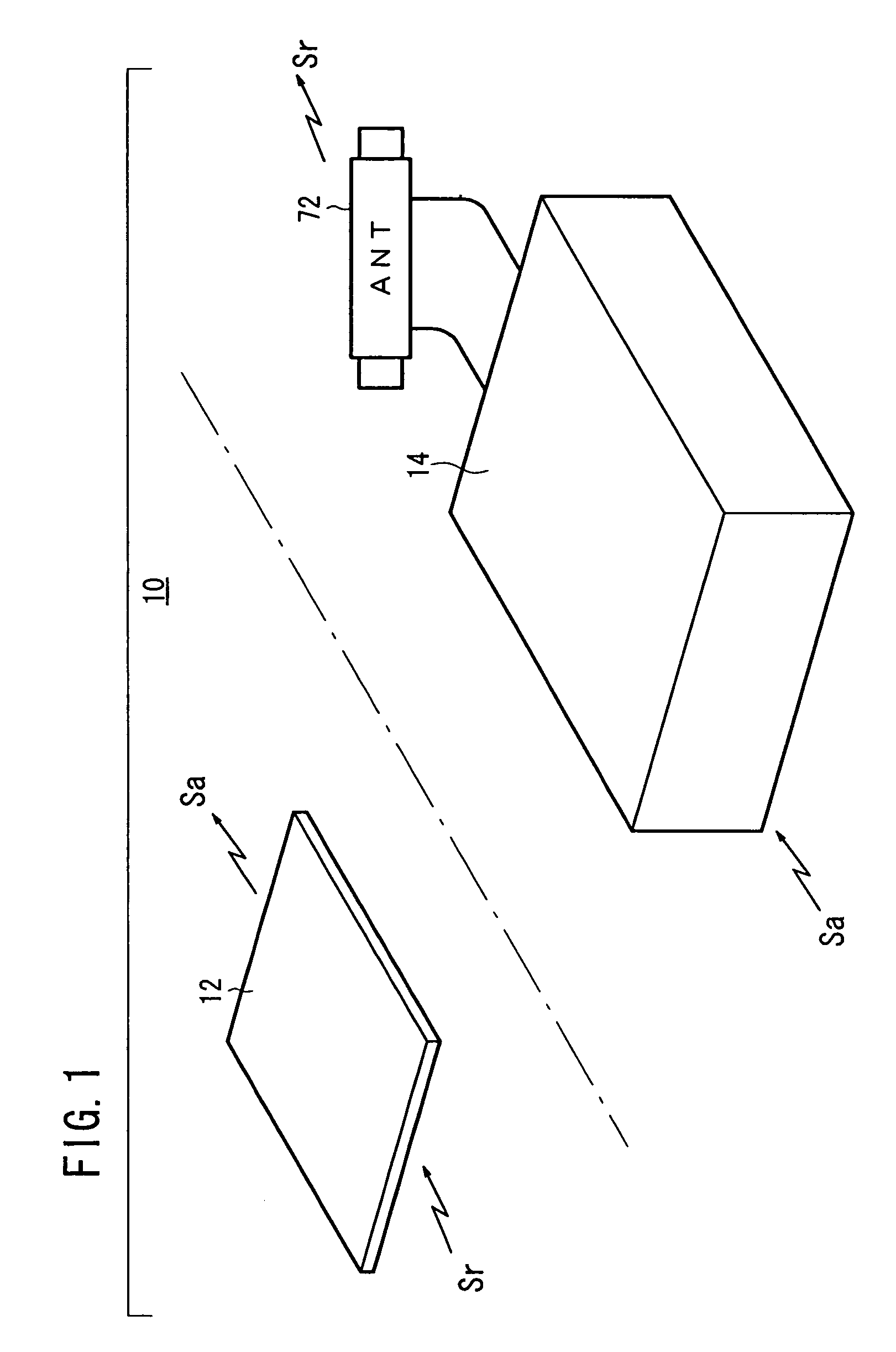
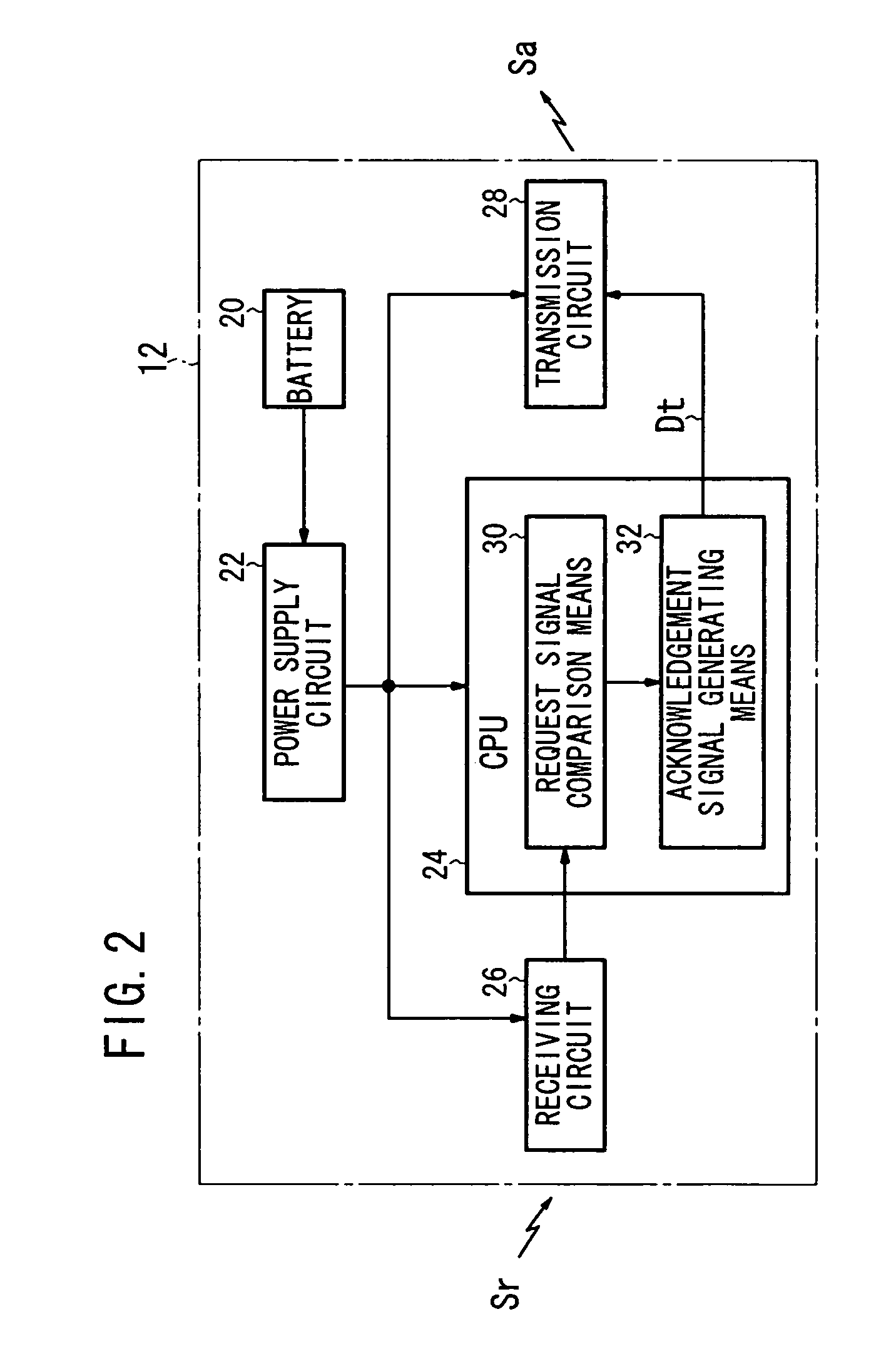
InactiveUS7245210B2Reduce probabilitySmall probabilityLock applicationsDigital data processing detailsEngineeringDriving circuit
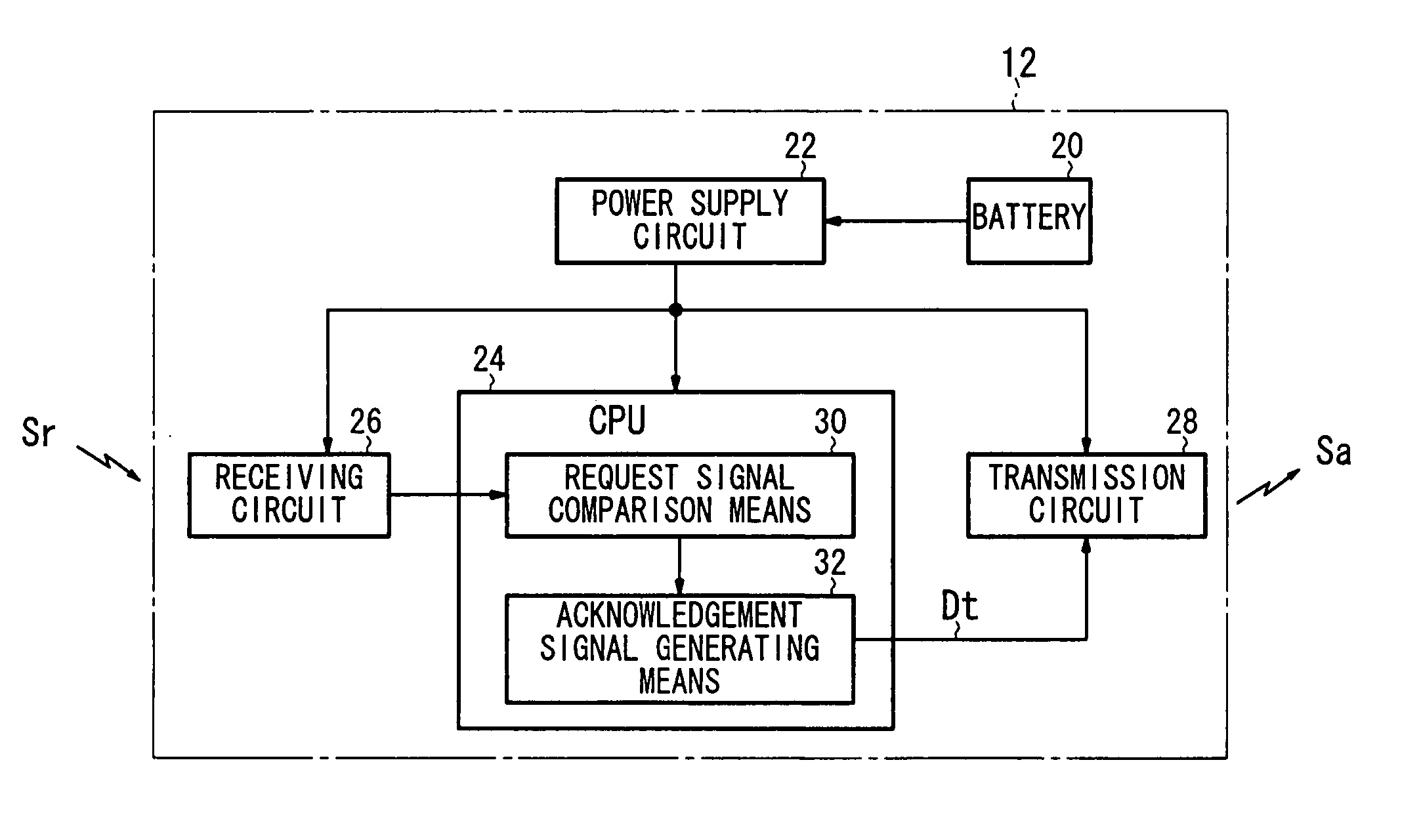
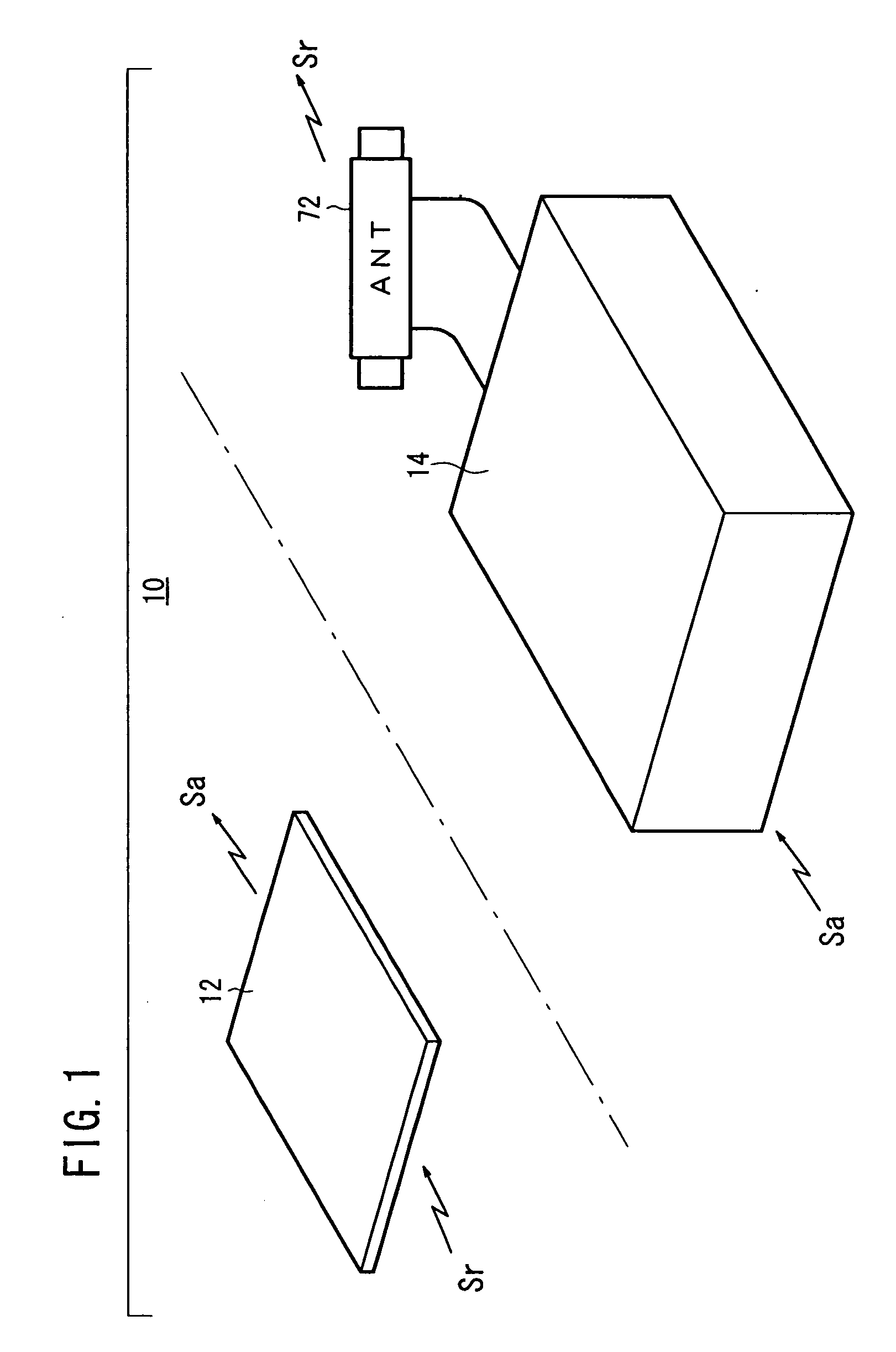
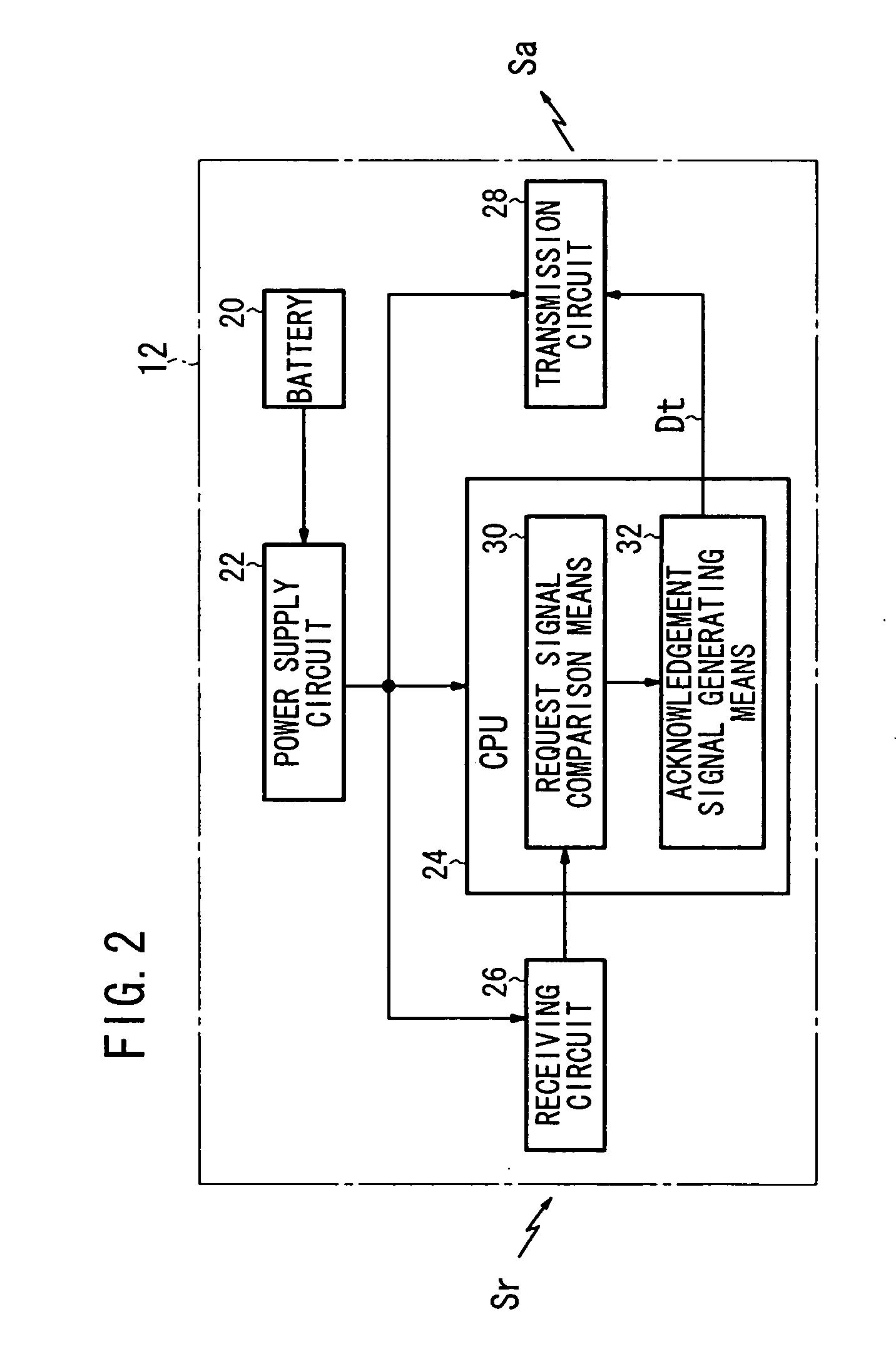
A vehicle electronic key system includes a control device mounted on a vehicle and an electronic key for transmitting a response signal in response to reception of a request signal from the control device. The control device includes means for outputting a request signal to the electronic key in response to the ON operation of a main switch of the vehicle (request signal generation means, a transmission circuit, and a transmission antenna), means for detecting a response signal from the electronic key (a reception circuit and response signal matching means), and means for performing an alarm output (monitoring means, a third drive circuit, and an alarm lamp) when no response signal is detected in spite of the output of the request signal.
Owner:HONDA MOTOR CO LTD
Cryptographic authentication and/or establishment of shared cryptographic keys, including, but not limited to, password authenticated key exchange (PAKE)
ActiveUS20100257362A1Small probabilitySolve the real problemDigital data processing detailsUser identity/authority verificationPasswordCryptographic nonce
A server (120) uses a password (π) to construct a multiplicative group (ZN*) with a (hidden) smooth order subgroup (<x′>), where the group order (Pπ) depends on the password. The client (110) uses its knowledge of the password to generate a root extraction problem instance (z) in the group and to generate data (y) allowing the server to construct a discrete logarithm problem instance (y′) in the subgroup. The server uses its knowledge of the group order to solve the root extraction problem, and solves the discrete logarithm problem efficiently by leveraging the smoothness of the subgroup. A shared key (sk) can be computed as a function of the solutions to the discrete logarithm and root extraction problem instances. In some embodiments, in an oblivious transfer protocol, the server queries the client (at 230) for data whose position in a database (210) is defined by the password. The client provides (240) such data without knowing the data position associated with the server's query. The client obtains the data position independently from the password. The data positions and / or the respective data are used for authentication and shared secret key generation. Other embodiments are also provided.
Owner:NTT DOCOMO INC
Heat exchanger for an indoor unit of an air conditioner
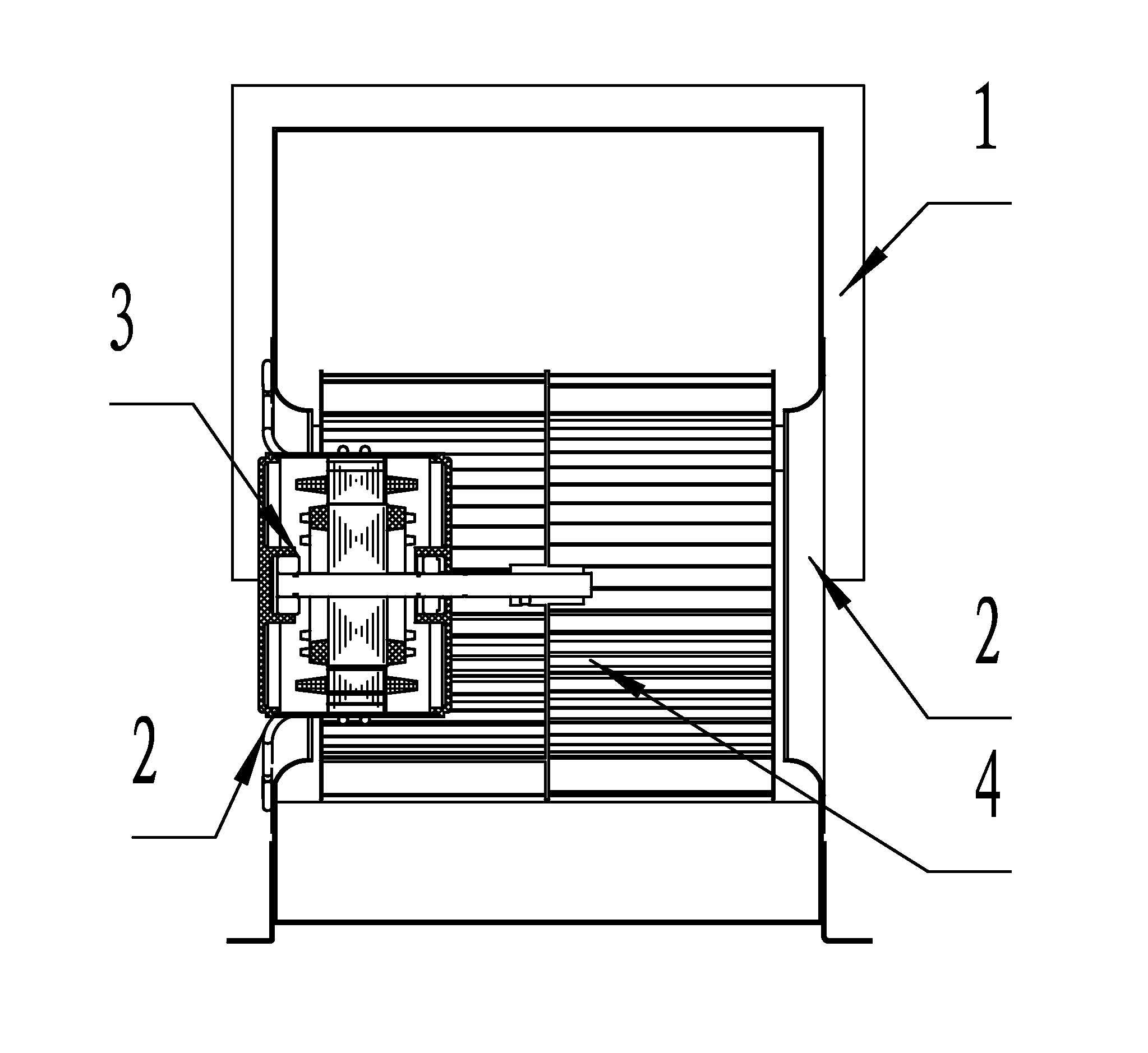
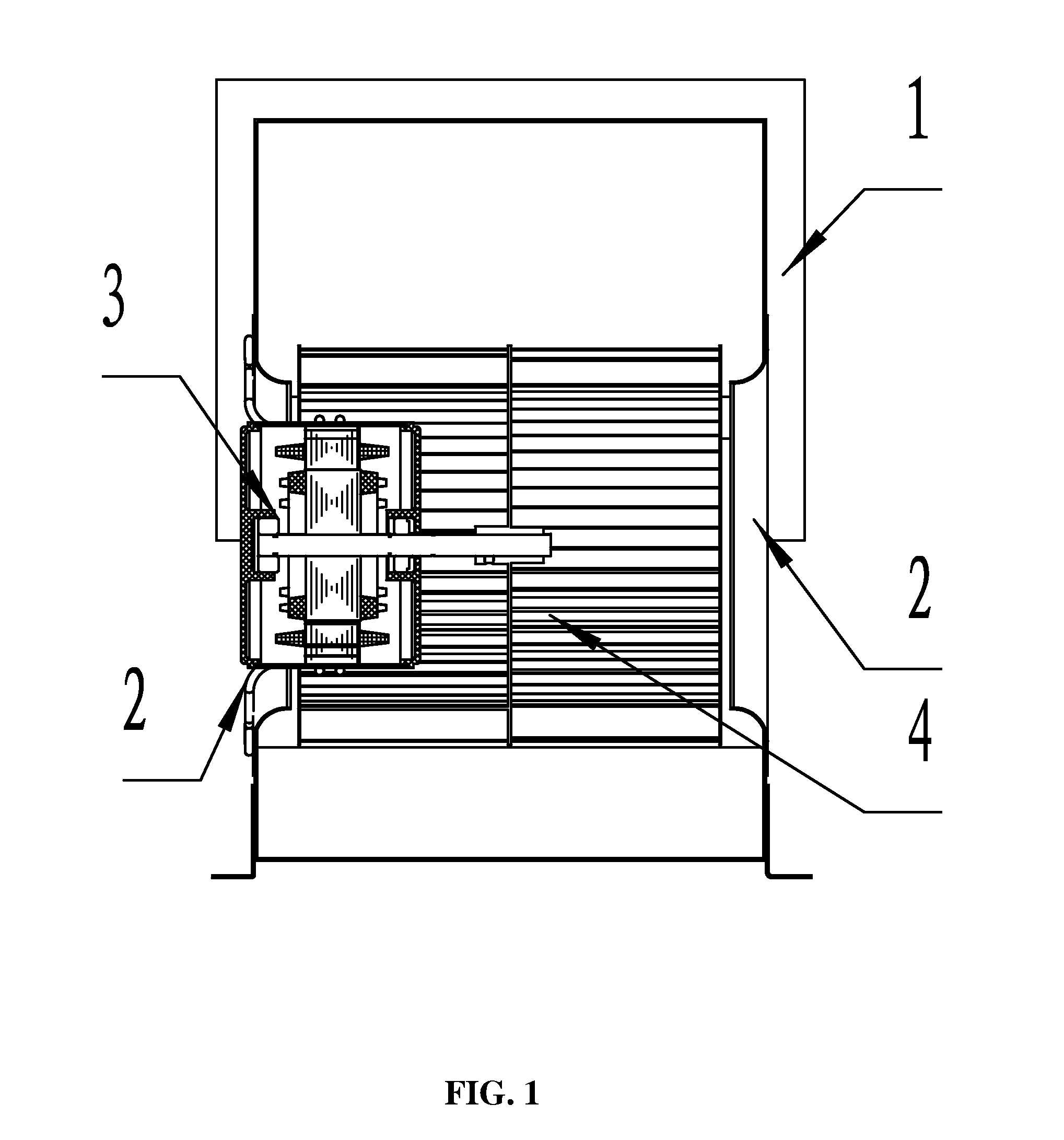
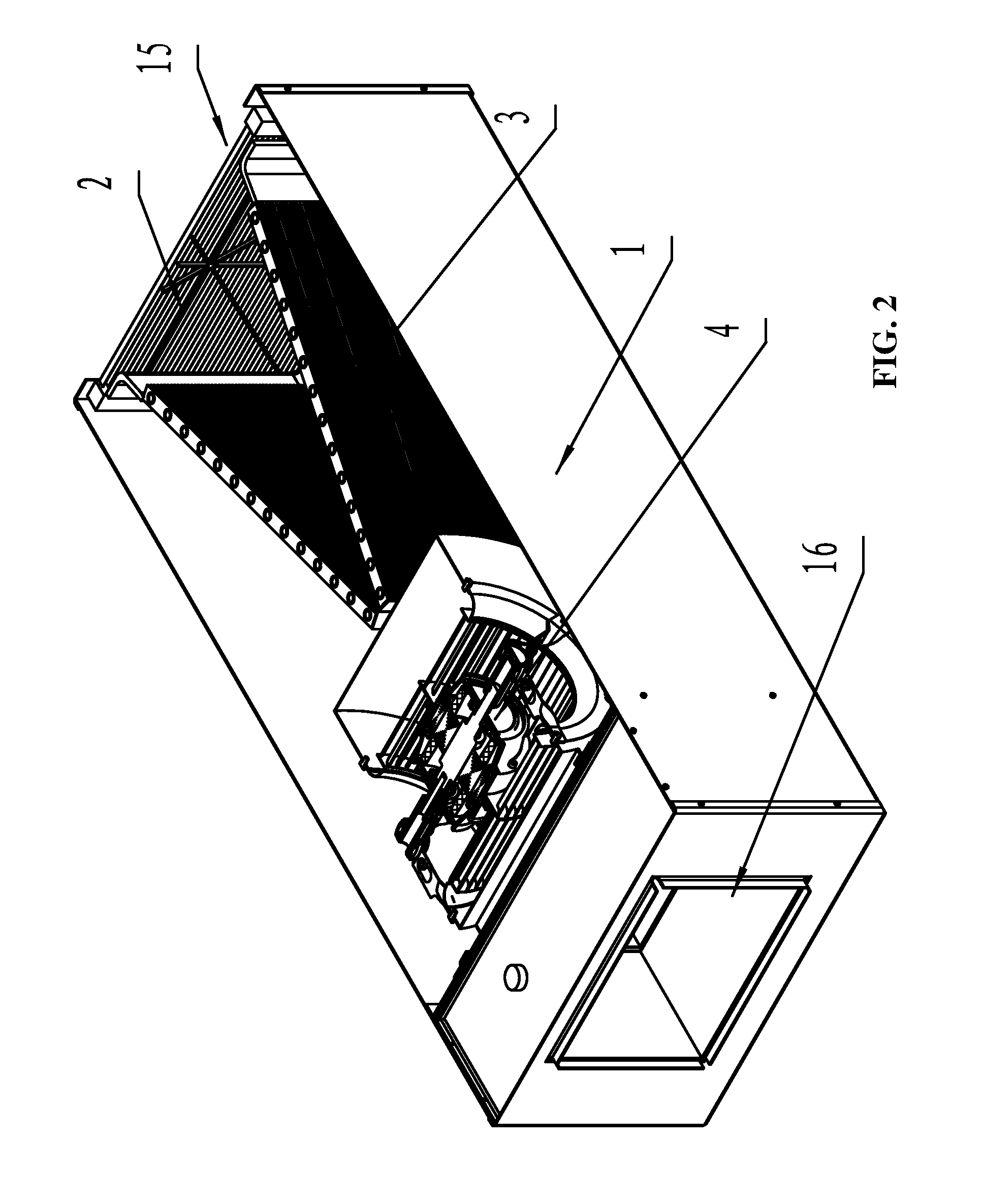
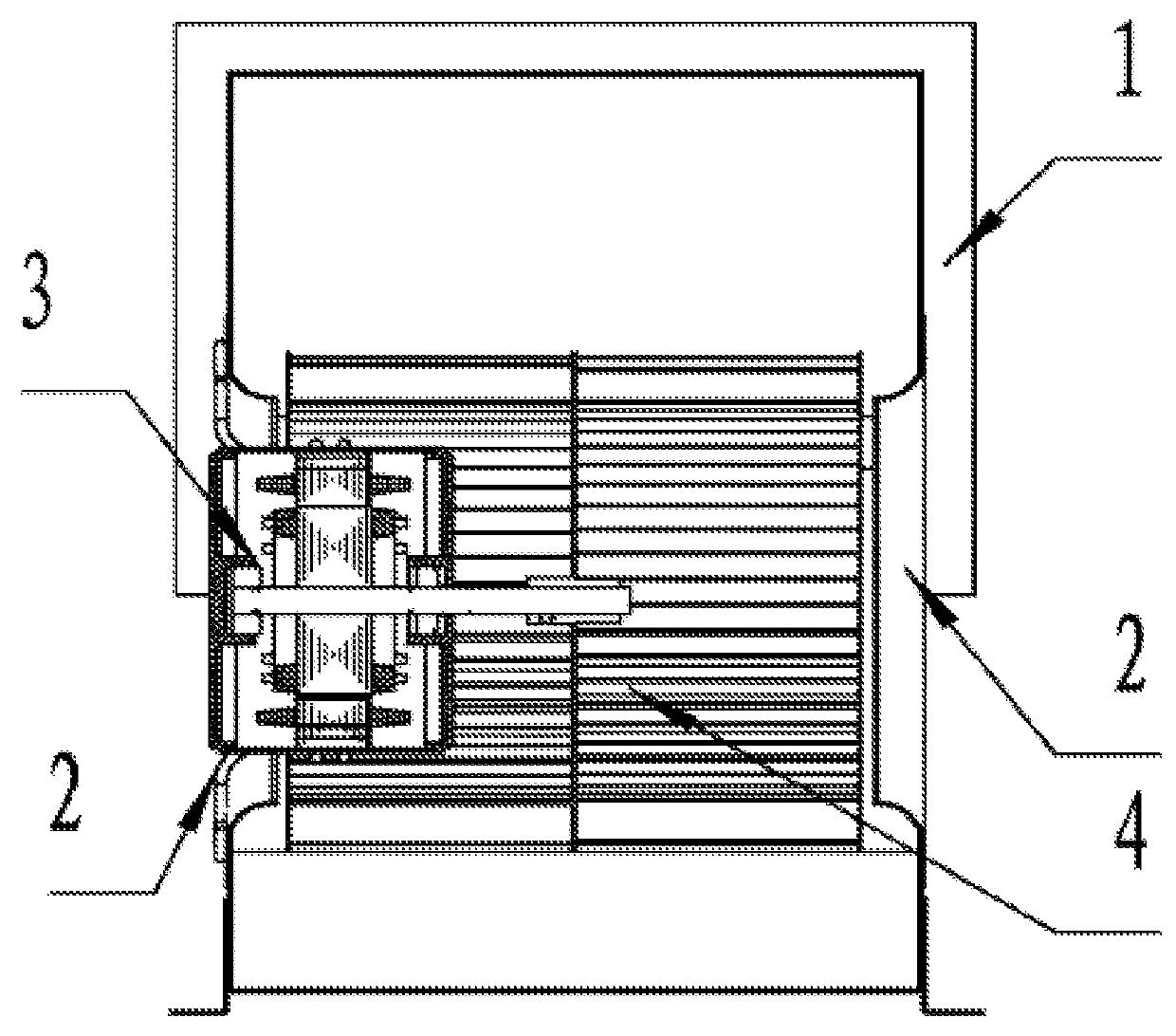
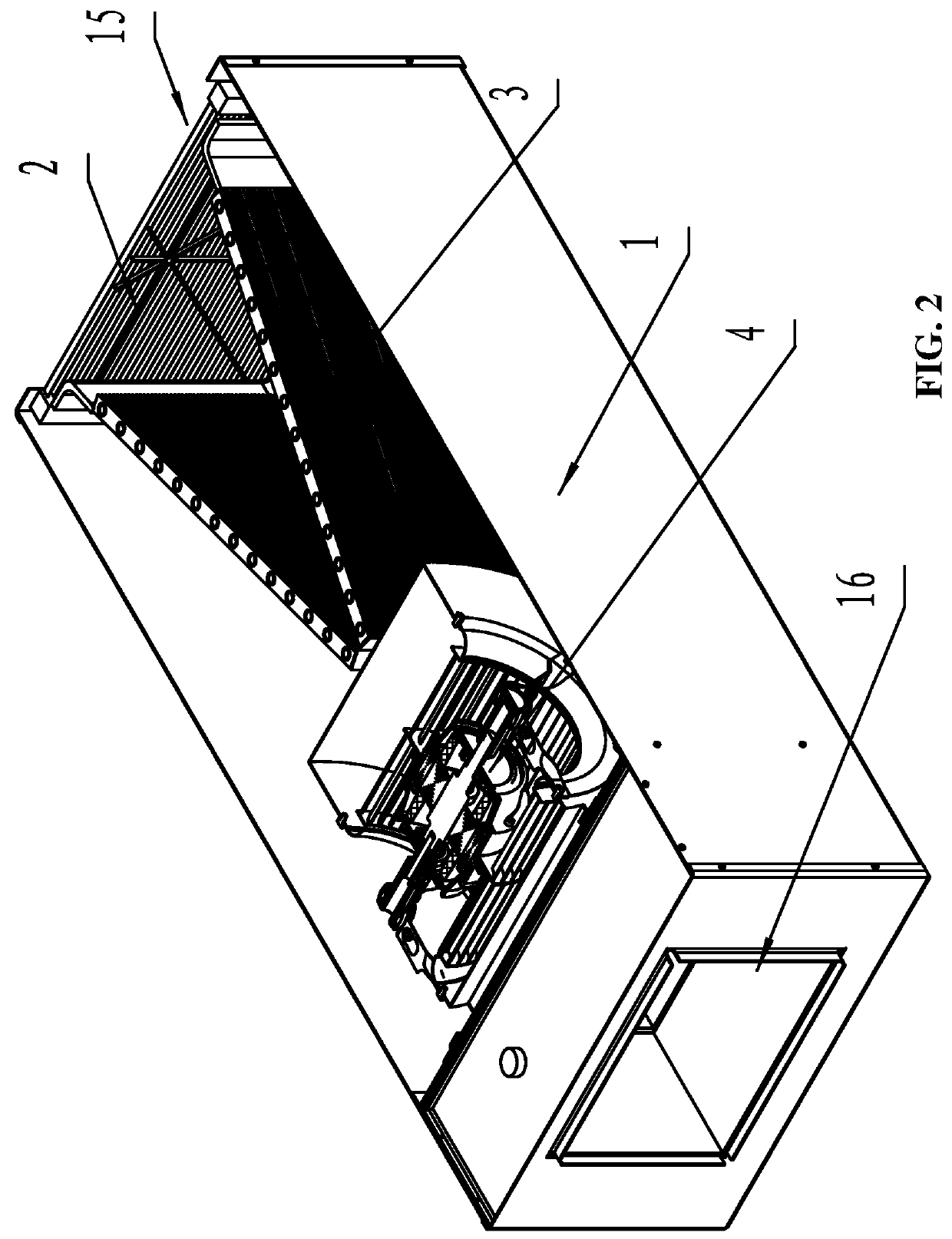
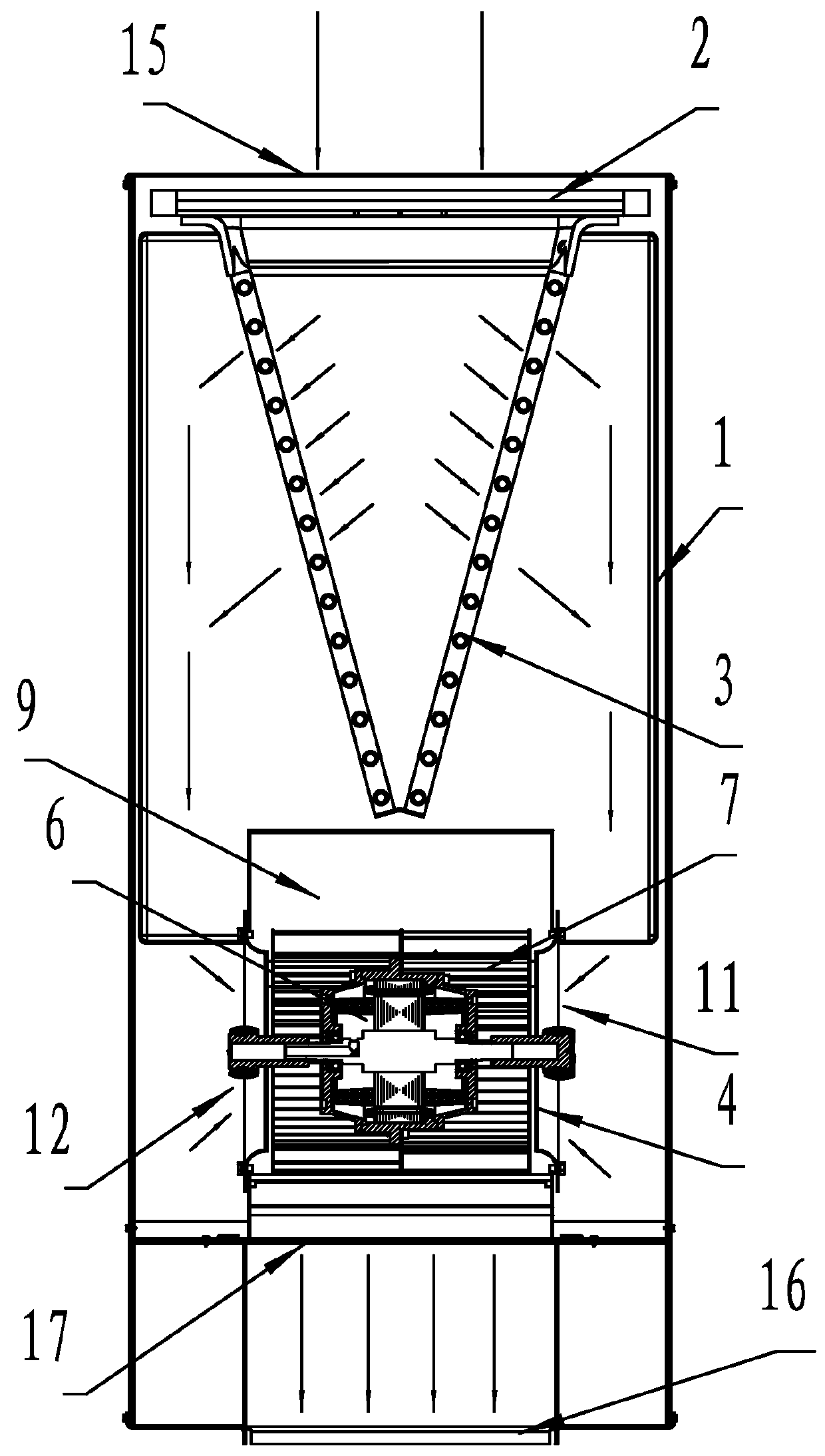
ActiveUS20110240262A1Large air volumeImprove blowing efficiencyHeating and ventilation casings/coversIndirect heat exchangersCooling coilEngineering
A heat exchanger for an indoor unit of an air conditioner, including at least a housing (1) having an air inlet (15) and an air outlet (16), a cooling coil (3), and a centrifugal blower (4) having an air exit (17), a volute housing (5), a motor (6) and a centrifugal wind wheel (7). The cooling coil (3) and the centrifugal blower (4) are disposed in the housing (1). The air inlet (15) and the air outlet (16) are disposed on both ends of the housing (1). The cooling coil (3) is disposed at the back of the air inlet (15). The centrifugal blower (4) is disposed at the back of the cooling coil (3). The air exit (17) of the centrifugal blower (4) is connected to the air outlet (16) of the housing (1). The motor (6) is an external rotor motor and fits in the center of a cavity in the centrifugal wind wheel (7). A left air intake (11) and a right air intake (12) are formed on both sides of the volute housing (5). The heat exchanger features large air input and air output, and high blowing efficiency.
Owner:ZHONGSHAN BROAD OCEAN MOTOR MFG
Method for compensating a failing nozzle
ActiveUS9302469B2AdditionalIncrease probabilityOther printing apparatusVolumetric Mass DensityEngineering
A method is provided for compensating a failing nozzle in a printhead comprising a series of print elements with nozzles for operation in an inkjet printing process in which a colorant is applied for locally changing an optical density, thereby printing an image. The method comprises at least two compensation mechanisms, each providing a different amount of additional optical density in the environment of a missing dot in the printed image. A nozzle is recorded as a failing nozzle if the associated print element does not apply an ink dot within predetermined specifications. An environment density is determined in an environment of a missing dot associated with said failing nozzle. The environment density is compared with a predetermined threshold, and an appropriate compensation mechanism is selected from the at least two compensation mechanisms. The method is applied in an inkjet printing system for balancing under- and overcompensated optical density.
Owner:OCE TECH
Window regulator
A window regulator has a small number of parts and a simple structure and avoids the generation of noise. An upper wire-end having a flange portion is connected to the end portion of a raising wire connected to a carrier plate. A wire-end storage portion having a hollow portion surrounded by a top wall and a circumferential wall extending downward from a rim of the top wall is formed on the carrier plate. A plurality of ribs are formed on the wire-end storage portion along an axis direction of the wire-end storage portion, while protruding from the circumferential wall to the hollow portion. The flange portion is in contact with at least two of the ribs.
Owner:HI-LEX CORPORATION
System and method for implementing a delta-sigma modulator integrity supervisor
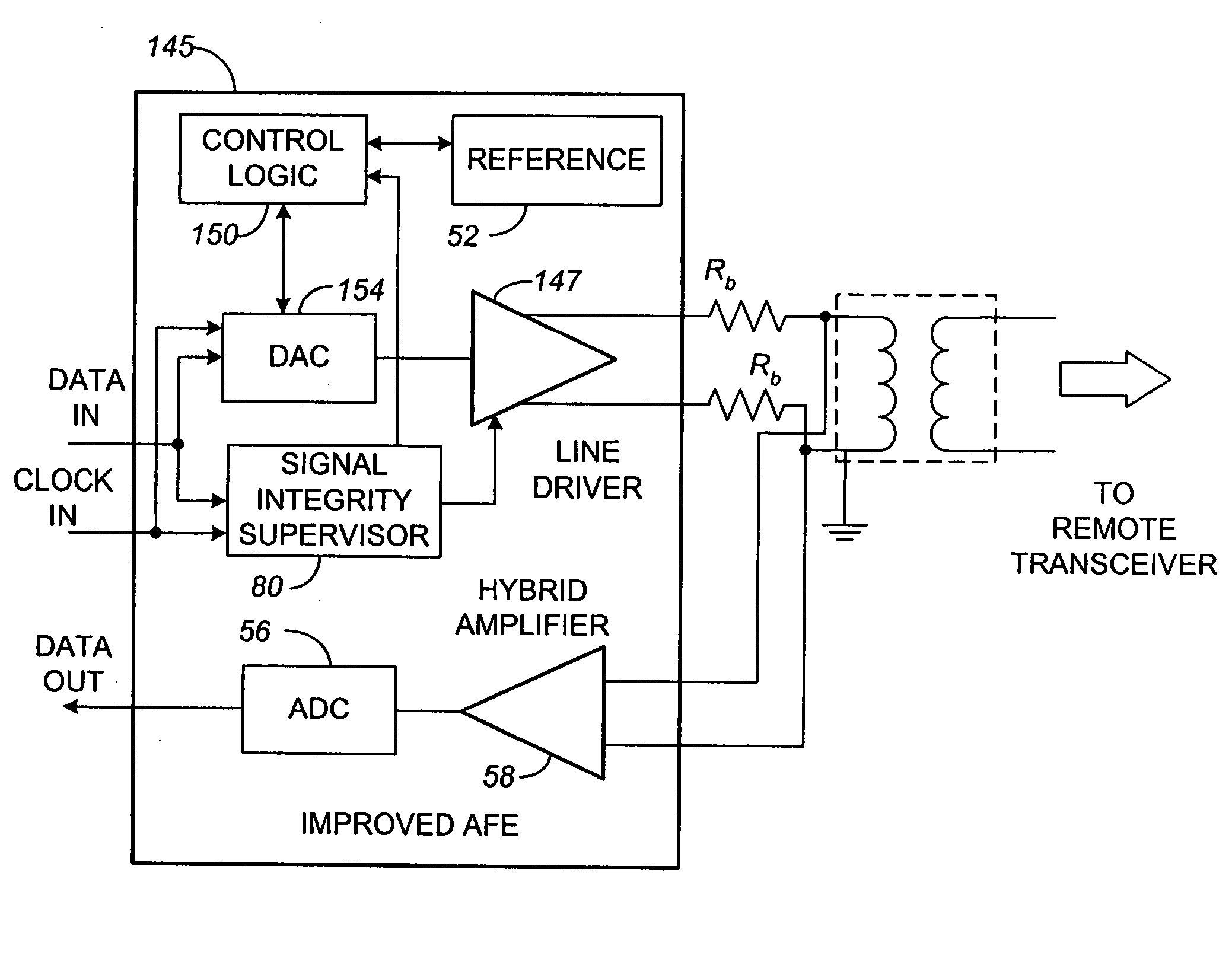
InactiveUS20050053124A1Small probabilitySynchronisation information channelsModulated-carrier systemsData streamDigital analog converter
A system and a method for constructing a signal integrity supervisor capable of both detecting and triggering an appropriate response when transmit path signals indicate a potential damaging transmitter operating mode. The system and method of the present invention takes advantage of the inherent property of a Delta-Sigma Modulator (DSM) which makes the probability of encountering a long string of consecutive ones or zeroes during nominal operation very small. The signal integrity supervisor ensures safe transmitter operation by monitoring the data and the clock inputs to a digital to analog converter. The system may comprise a data signal supervisor and a clock signal supervisor. The data supervisor may comprise a comparator and a counter and may be configured to power down a line driver upon detecting a data stream having a continuous voltage level. The clock detector may comprise a pair of monostable circuits, an inverter, and a NAND gate and may be configured to reset the transmitter if a “missing” clock signal state is detected. The present invention can also be viewed as providing a method for preventing a transmission unit from forwarding signals that may result in a DC flow condition. In its broadest terms, the method can be described as: monitoring a data signal; generating a first output signal in response to a data signal having an anomalous condition; monitoring a clock signal; and generating a second output signal in response to clock signal having an anomalous condition.
Owner:IKANOS COMMUNICATIONS
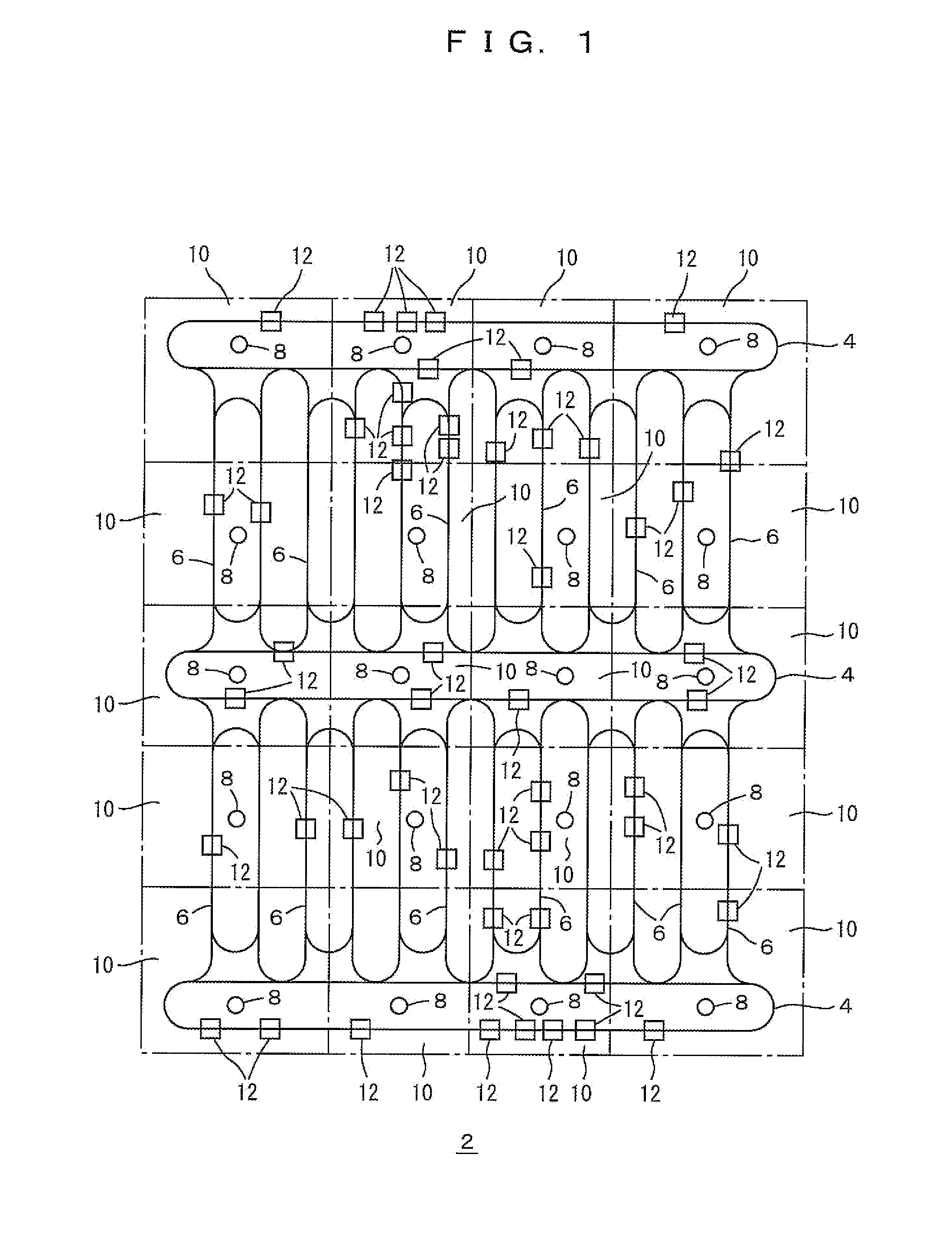
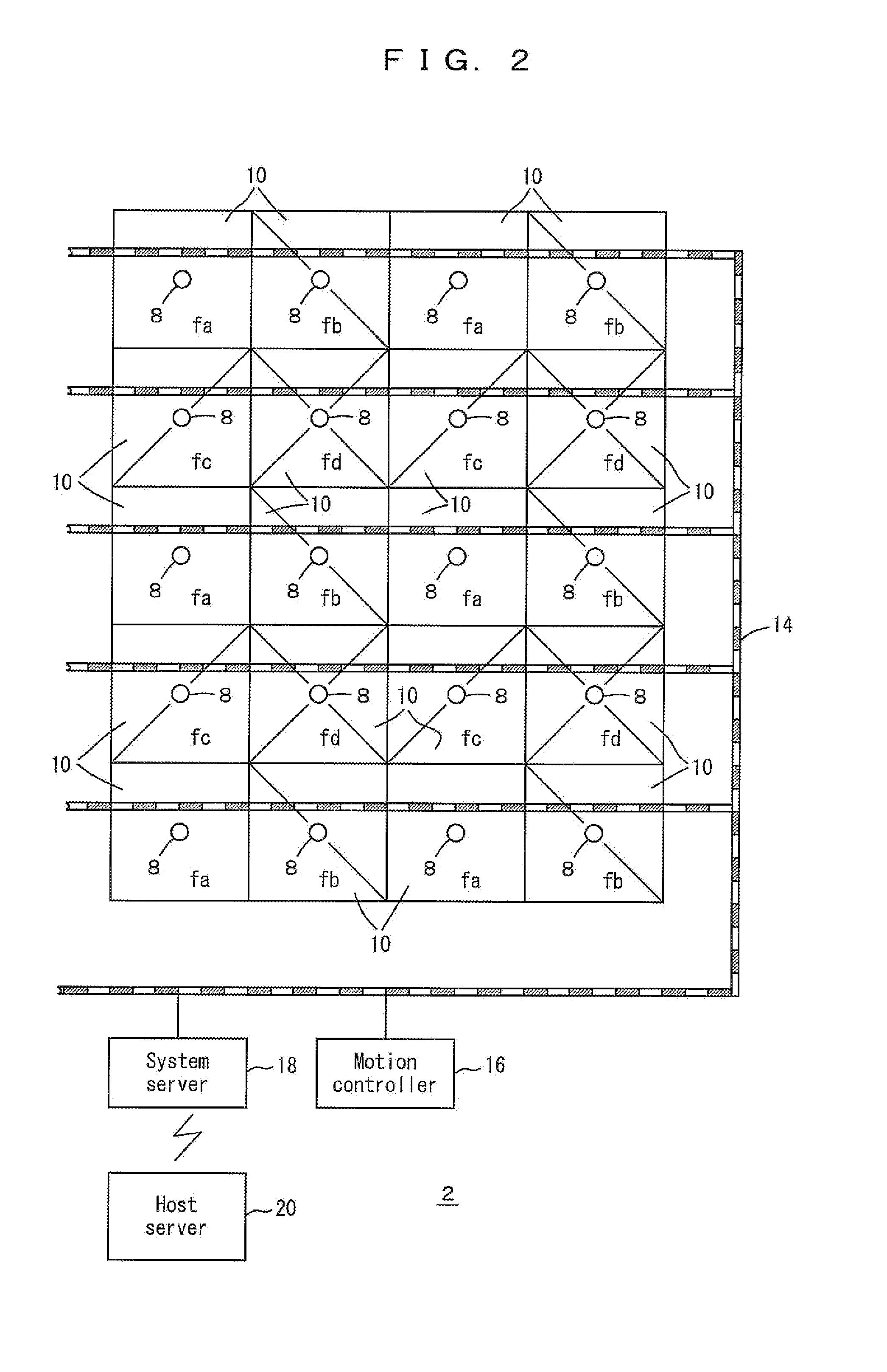
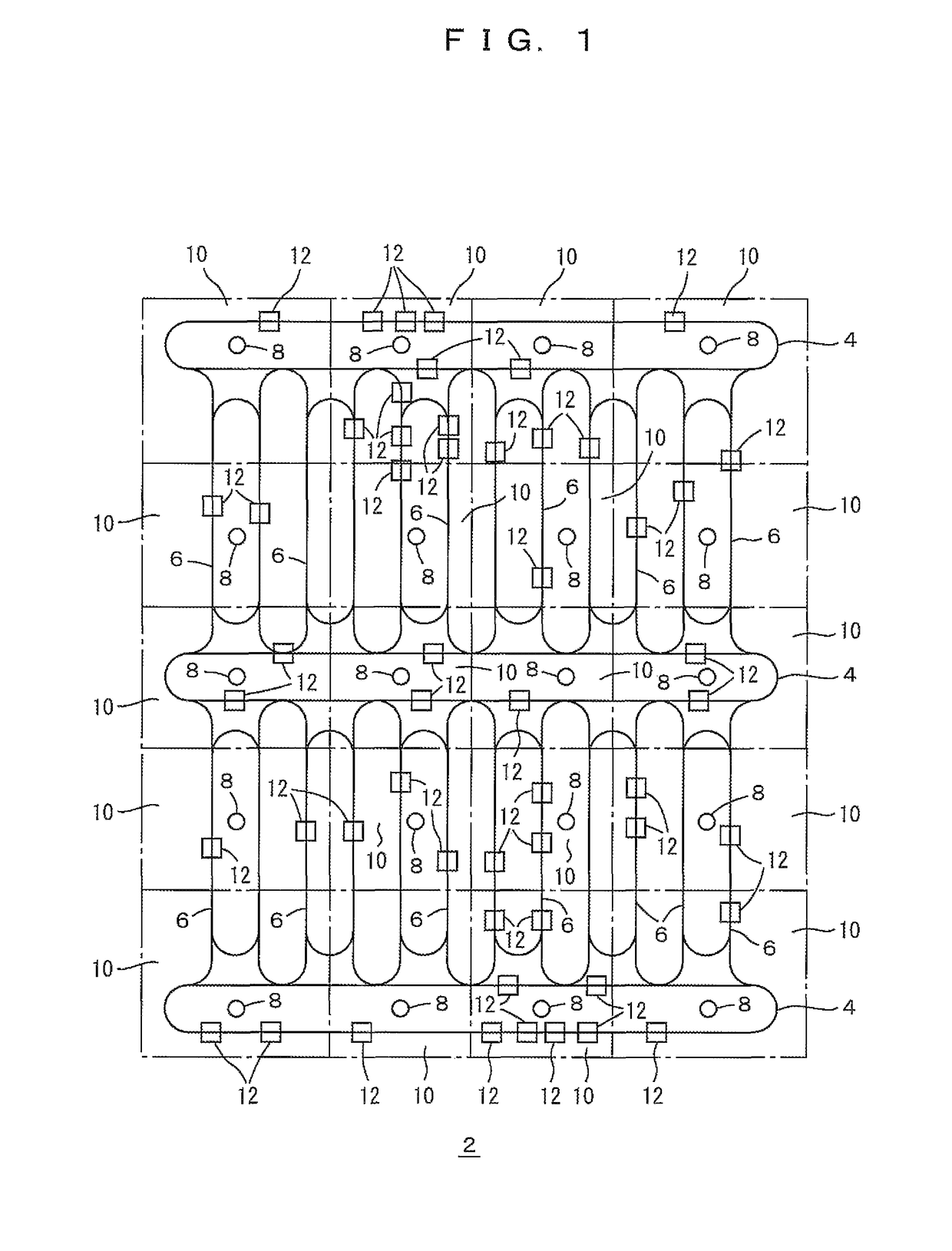
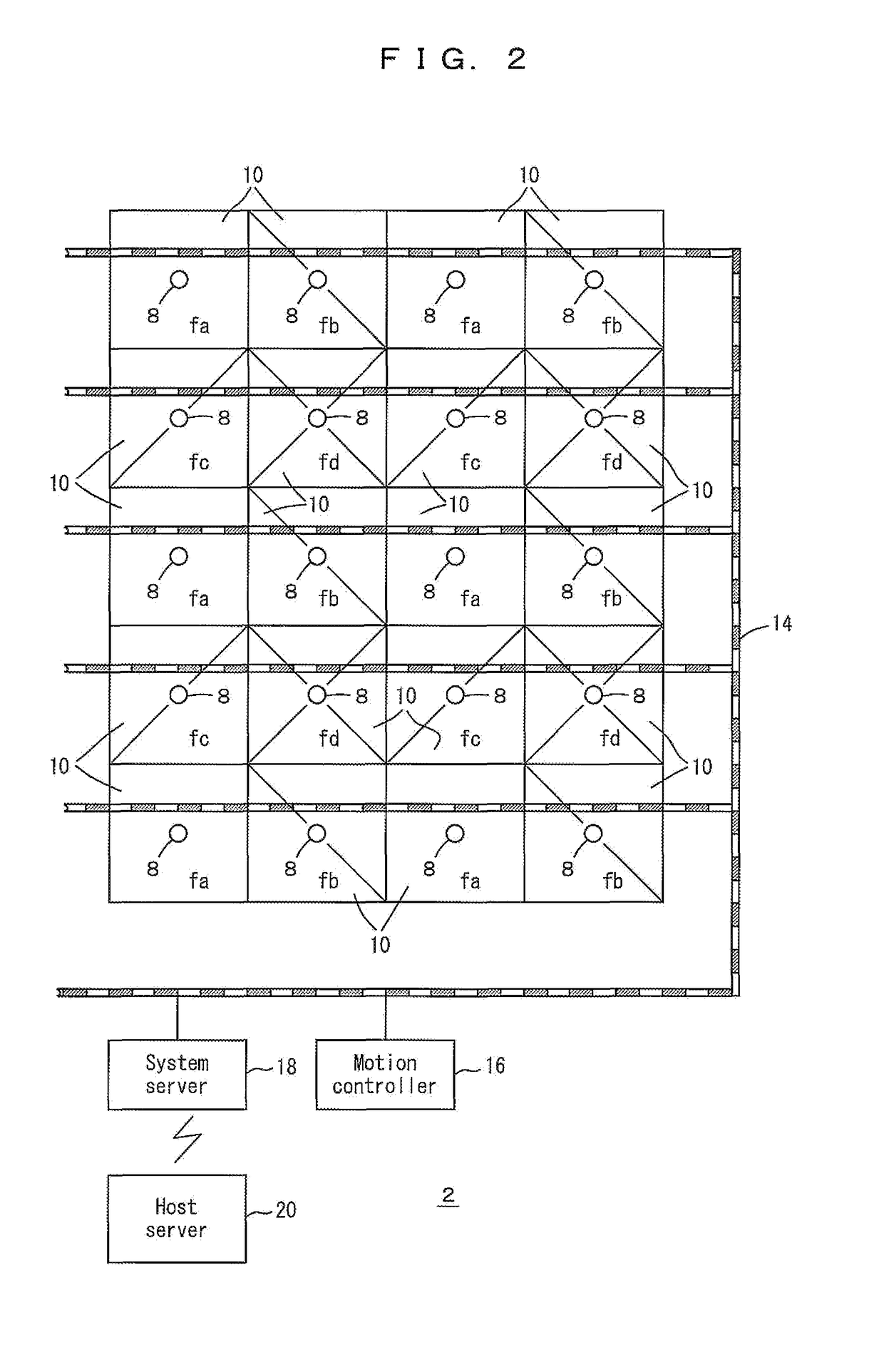
Traveling vehicle system and communication method in the traveling vehicle system
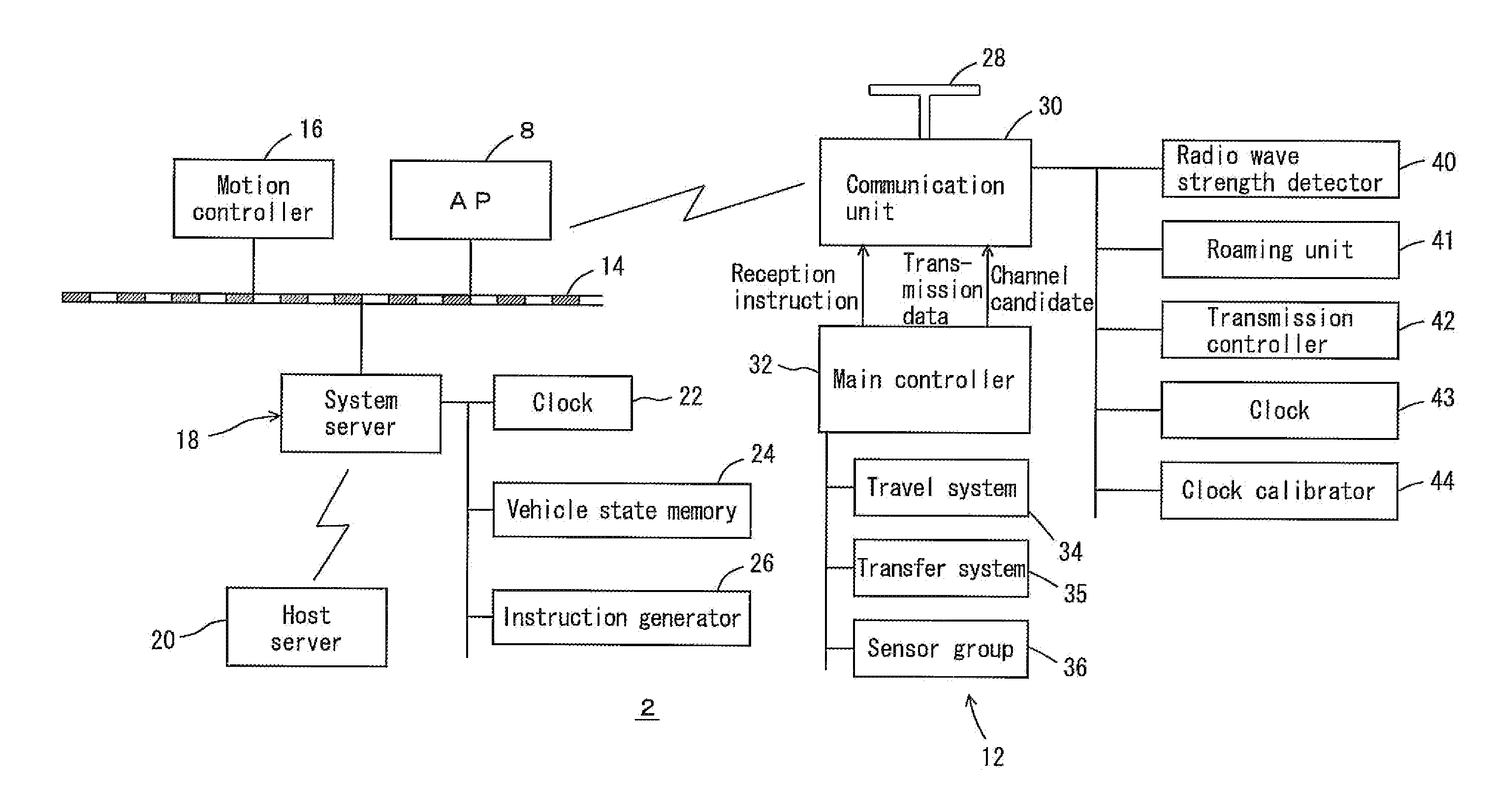
ActiveUS20110202202A1CommunicationAvoid positioningDigital data processing detailsVehicle position/course/altitude controlTime zoneReal-time computing
A system server and access points are connected through a LAN preferably on the ground. A control cycle is divided into an instruction time zone to provide instructions from the access points to traveling vehicles, and a report time zone to provide reports from the traveling vehicles to the access points. The access points transmit target positions in the instruction time zone, and the traveling vehicles report positions in the report time zone. The system server determines target positions based on the reported positions.
Owner:MURATA MASCH LTD
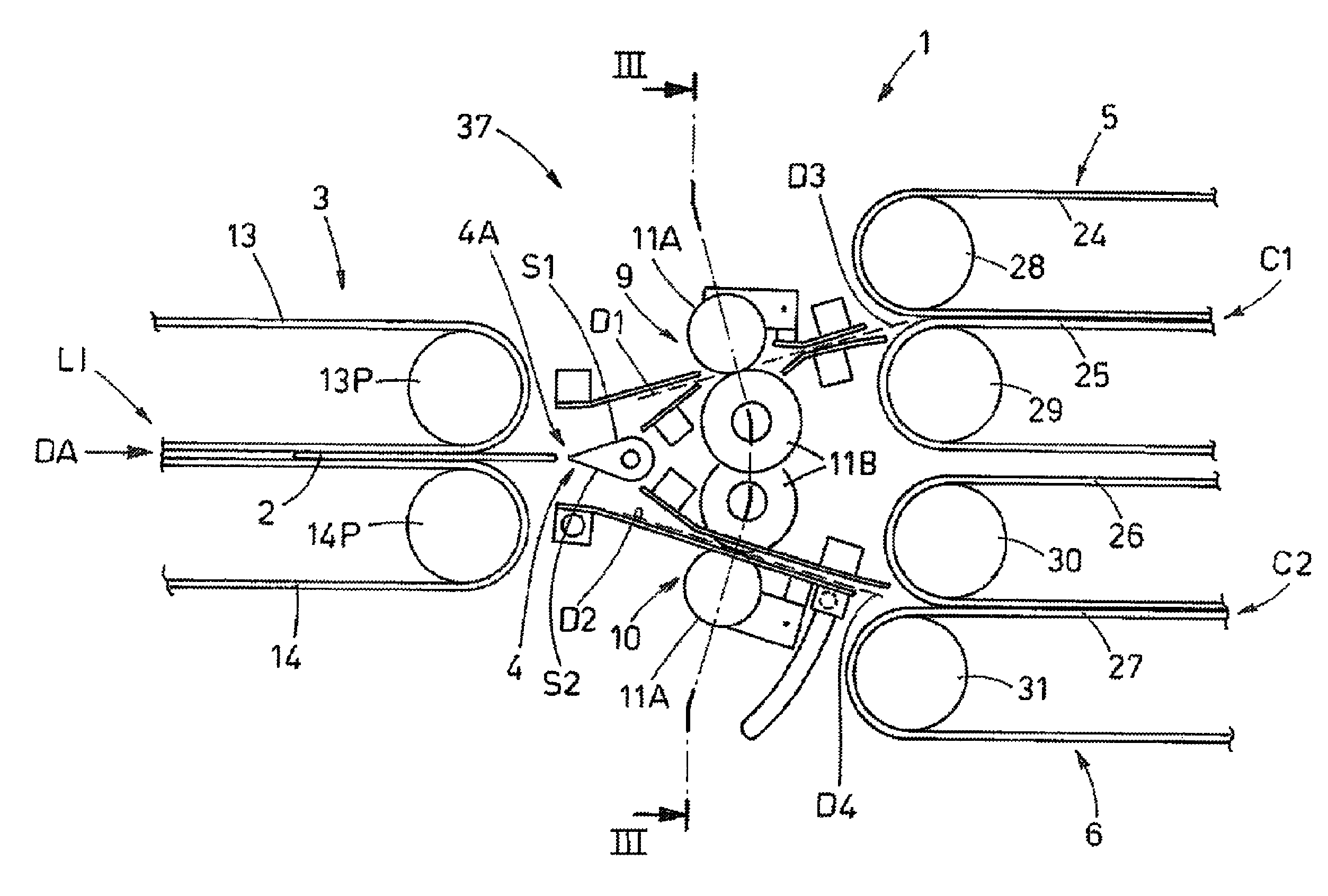
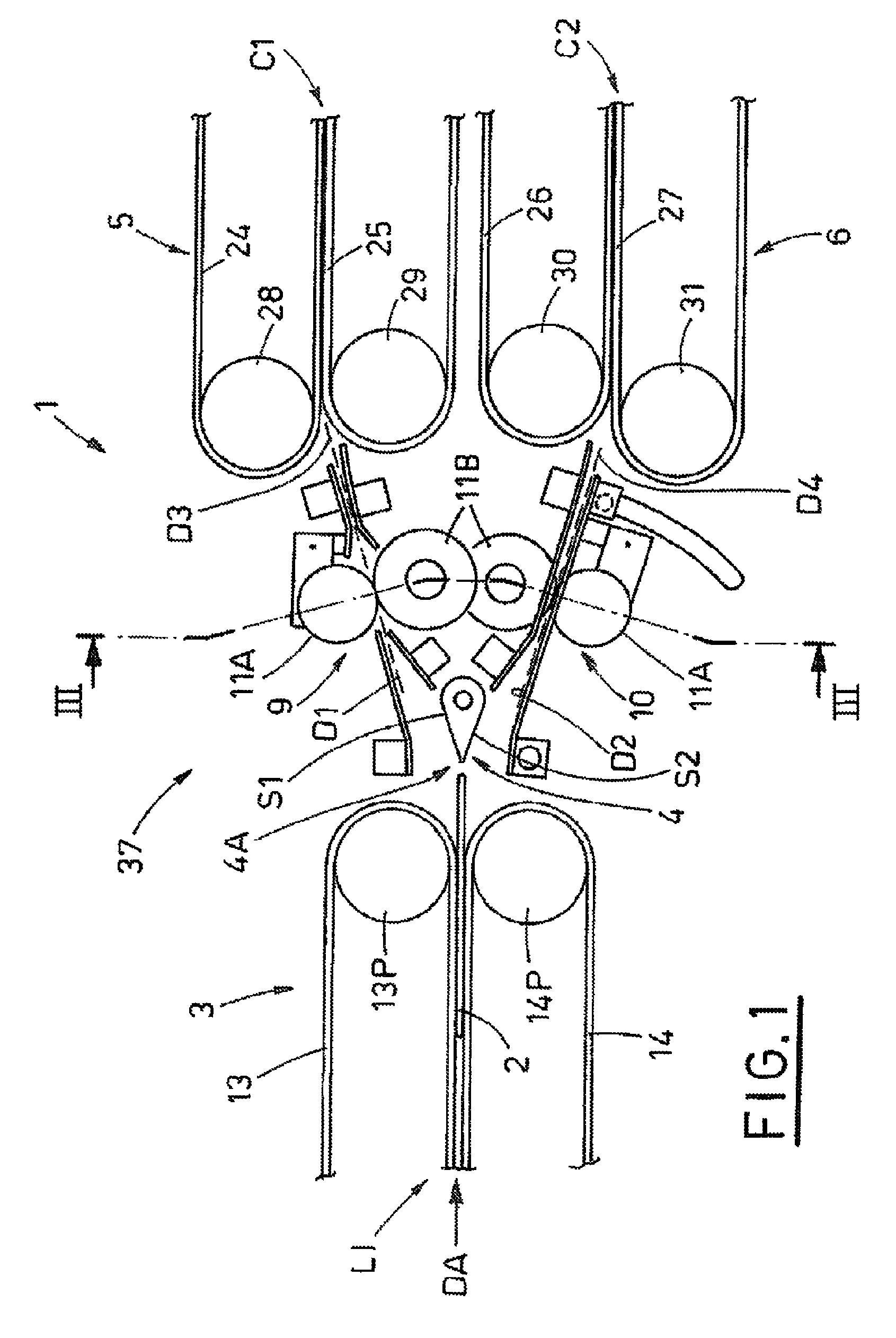
System for directing sheet articles in arrival from an input line towards two output lines
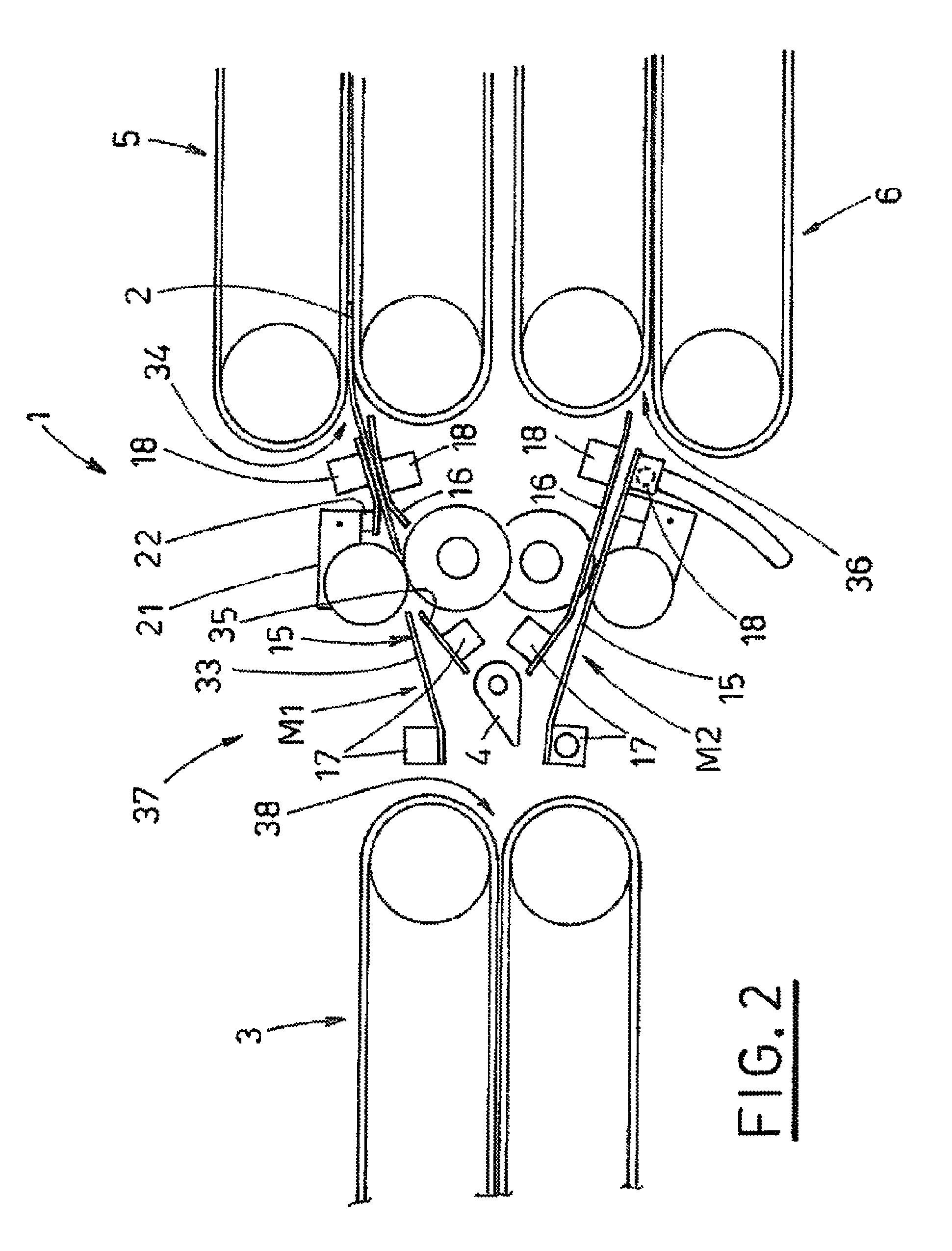
ActiveUS8690153B2High levelShort set-up timeRegistering devicesArticle feedersEngineeringCounter rotating
A system (1) for directing sheet articles (2) in arrival from an input line (L1) towards two output lines has first gripping and drawing devices for gripping and drawing the sheet articles (2) for release in a directing region (37). The sheet articles are then deviated along a first (D1) or a second (D2) orientating direction. Second gripping and drawing devices move the sheet articles (2) along the direction region. First and second counter-rotating pairs of rollers face one another and grip the sheet articles to move them towards the second (5) and third (6) gripping and drawing devices, all the devices and rollers being arranged and operating with respect to one another such that during transit through the directing region (37) the advancing sheet articles (2) are subjected to constant gripping by at least one device or one pair of rollers.
Owner:CMC SRL
Method for driving liquid crystal display panel
ActiveUS20170169770A1Reduce direct current bias voltageReduce afterimageStatic indicating devicesLiquid-crystal displayAfterimage
A method for driving a liquid crystal display panel is disclosed. The liquid crystal display panel comprises a plurality of sub pixels, and the method comprises presenting images to be displayed on the liquid crystal display panel frame by frame through regulating a gray-scale of each sub pixel of the liquid crystal display panel, wherein durations of image frames are not all equal to one another so as to reduce a direct current bias voltage of the sub pixel. According to the method, the direct current bias voltage during the isochronous driving process can be effectively reduced, and thus the afterimage of the liquid crystal display panel can be alleviated.
Owner:TCL CHINA STAR OPTOELECTRONICS TECH CO LTD +1
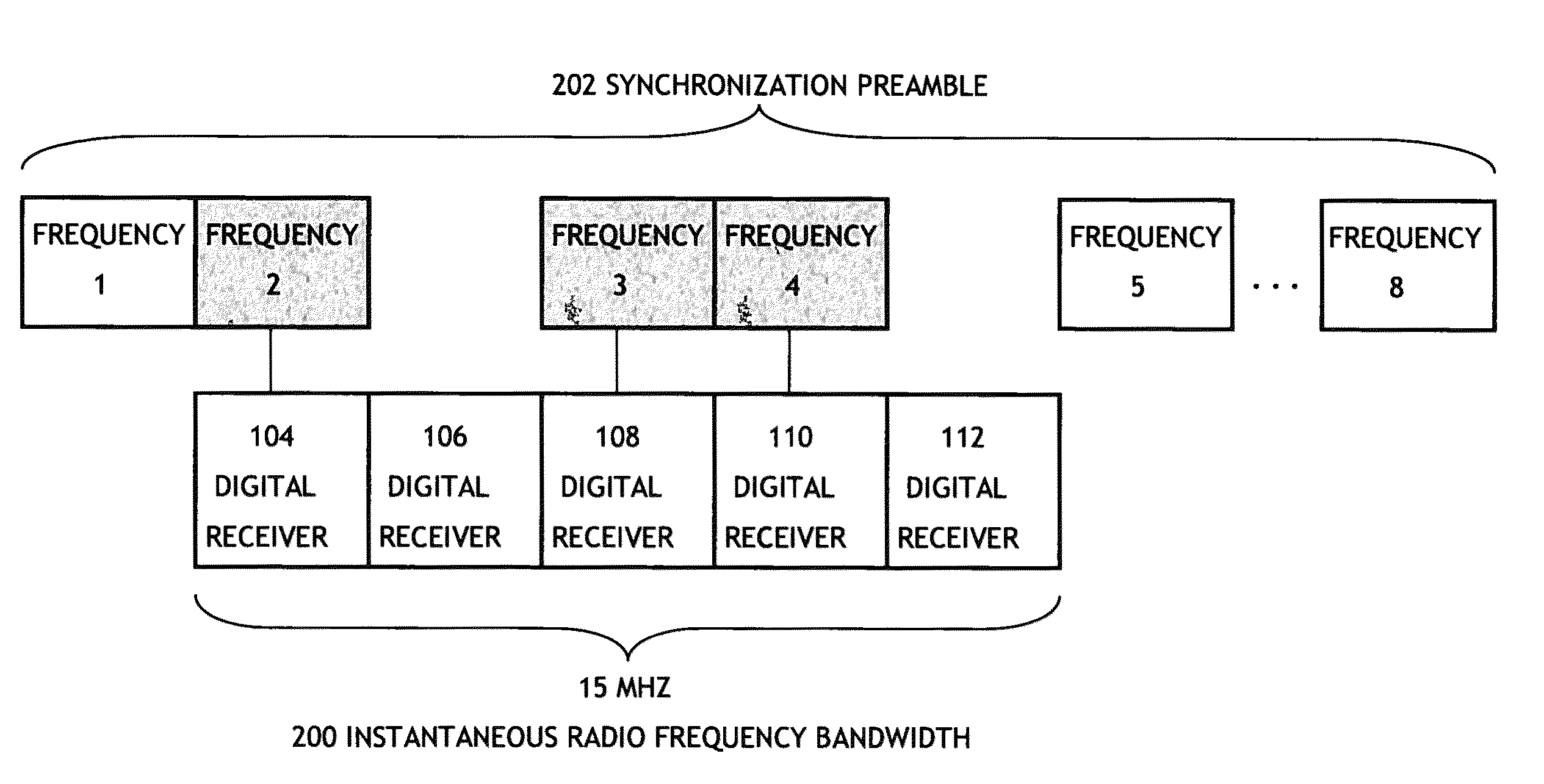
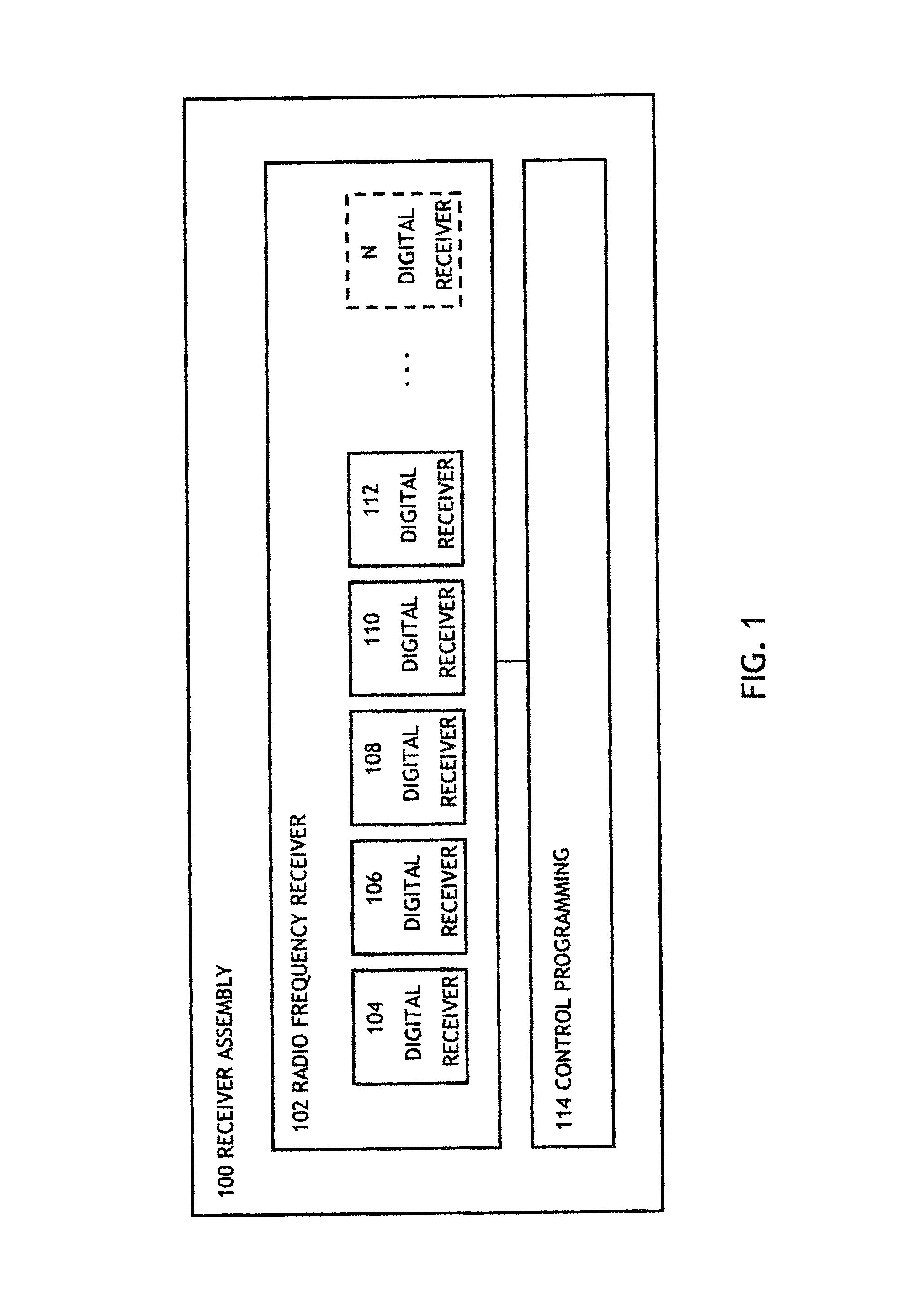
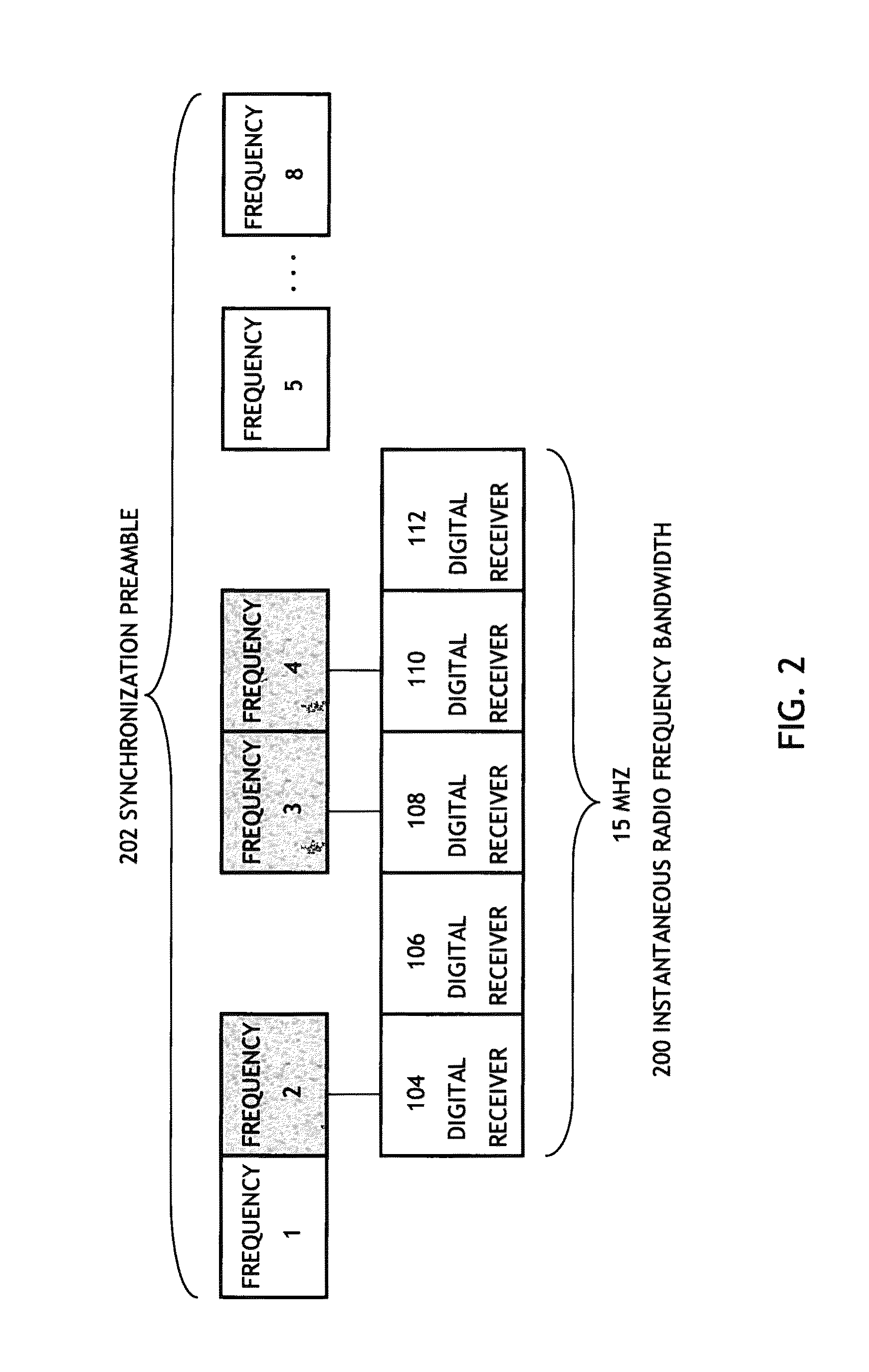
Syncronization frequency diversity reception utilizing a single RF receiver
ActiveUS8391416B1Small probabilityModulated-carrier systemsFrequency-division multiplexRadio frequencyDiversity scheme
A system may include a receiver having a number of reception channels spread across an instantaneous radio frequency bandwidth, each one of the reception channels for receiving a different radio frequency within the instantaneous radio frequency bandwidth. The system may also include control programming for positioning the receiver on one of a number of synchronization frequencies transmitting a synchronization preamble, where a number of reception channels is less than a number of synchronization frequencies, and a probability of not receiving one or more of the synchronization frequencies is smaller than a required message error rate for receiving the plurality of synchronization frequencies.
Owner:ROCKWELL COLLINS INC
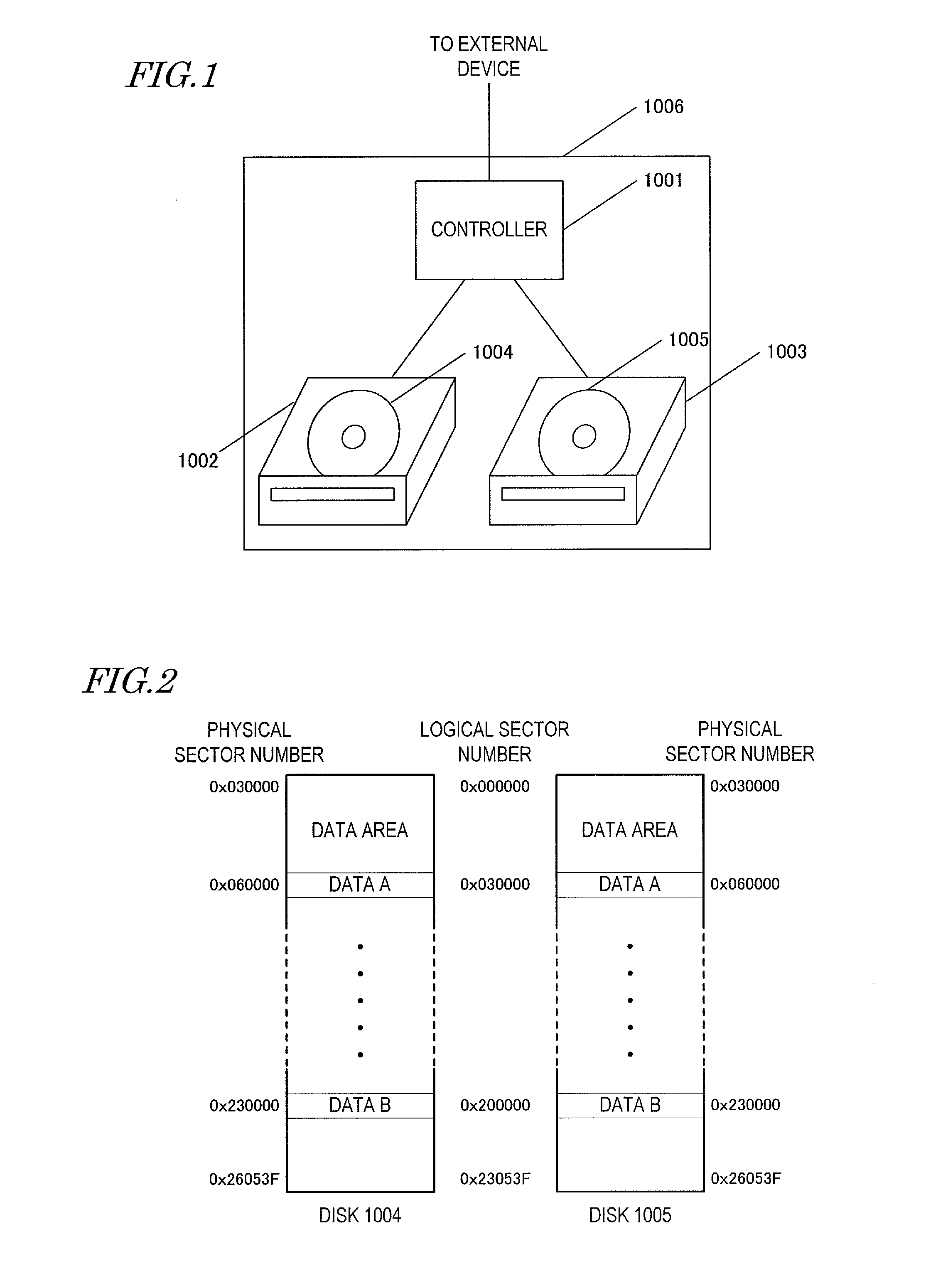
Optical disk array device
InactiveUS20130132672A1Small probabilitySignificant probabilityInput/output to record carriersError detection/correctionRAIDDisk array
When RAID is constructed by using optical disks of the same lot, there is a problem in that the reproduction error probability of the RAID may have local increases over the reproduction error probability within the optical disks. According to the present invention, among a plurality of optical disks constituting an optical disk array, the smallest logical sector number is assigned to mutually different physical sector numbers. As a result, data in the same stripe is allowed to be recorded to sectors at mutually different physical sector numbers of the plurality of optical disks, so that the probability of occurrence of read errors due to interferences of adjacent guide grooves and / or insufficient formation of guide grooves can be leveled out, and the maximum probability of read errors can be kept small.
Owner:PANASONIC INTELLECTUAL PROPERTY MANAGEMENT CO LTD
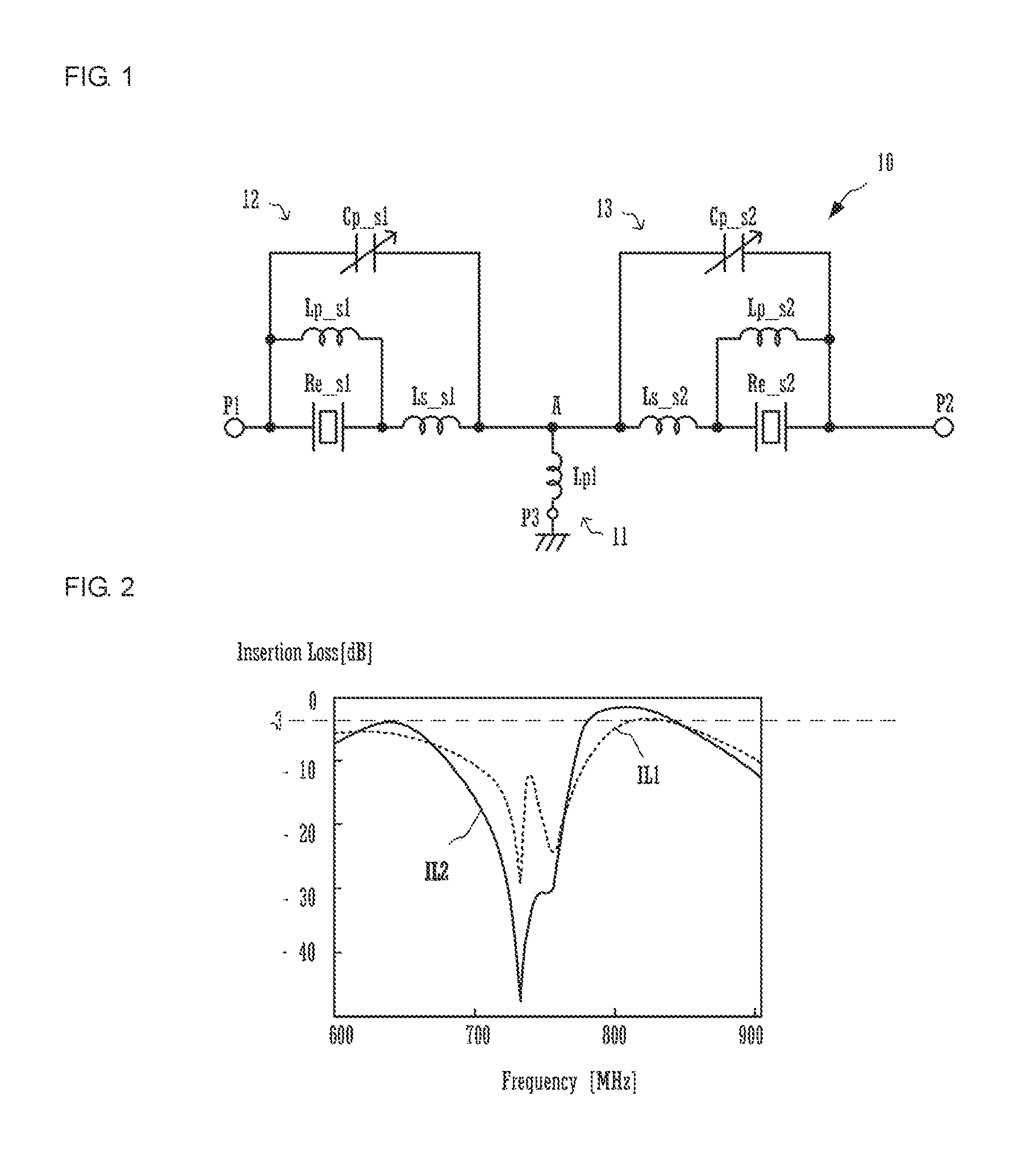
Variable filter circuit and radio communication device
ActiveUS20160344092A1Increase in circuit size and complicationLow frequencyMultiple-port networksAntenna supports/mountingsVariable capacitorInductor
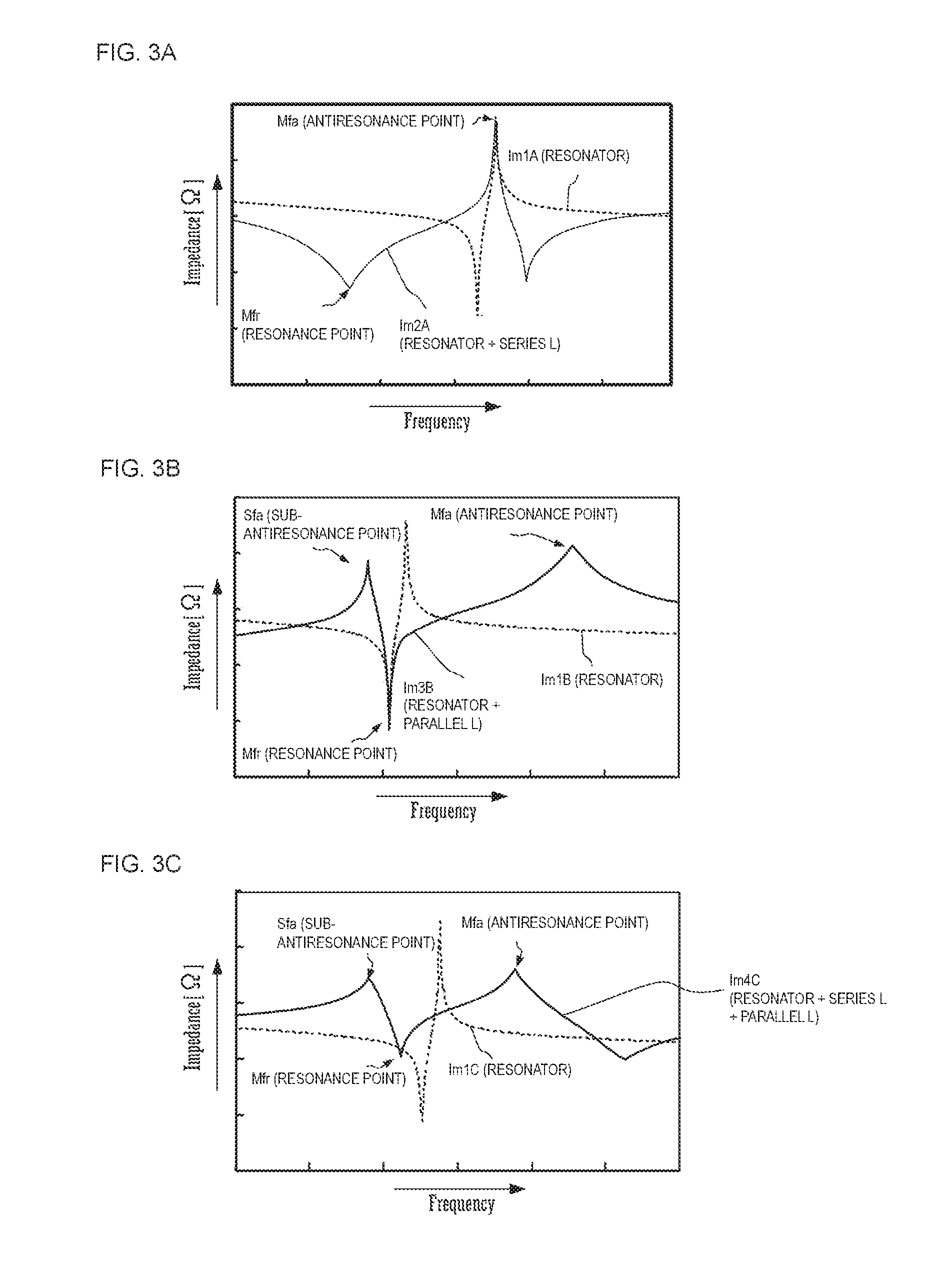
A variable filter circuit (10) includes a parallel arm (11) connected between a port (P3) and node (A), a series arm (12) including a resonator (Re_s1) connected in series between a port (P1) and node (A), and a series arm (13) including a resonator (Re_s2) connected in series between a port (P2) and node (A). The parallel arm (11) includes a first inductor (Lp1). The series arms (12, 13) include variable capacitors (Cp_s1, Cp_s2) connected in parallel to the resonators (Re_s1, Re_s2).
Owner:MURATA MFG CO LTD
Traveling vehicle system and communication method in the traveling vehicle system
ActiveUS8473116B2Avoid positioningValid reportDigital data processing detailsVehicle position/course/altitude controlTime zoneLocation determination
A system server and access points are connected through a LAN preferably on the ground. A control cycle is divided into an instruction time zone to provide instructions from the access points to traveling vehicles, and a report time zone to provide reports from the traveling vehicles to the access points. The access points transmit target positions in the instruction time zone, and the traveling vehicles report positions in the report time zone. The system server determines target positions based on the reported positions.
Owner:MURATA MASCH LTD
Vehicle electronic key system
InactiveUS20050280499A1Reduce probabilitySmall probabilityLock applicationsDigital data processing detailsEngineeringDriving circuit
A vehicle electronic key system includes a control device mounted on a vehicle and an electronic key for transmitting a response signal in response to reception of a request signal from the control device. The control device includes means for outputting a request signal to the electronic key in response to the ON operation of a main switch of the vehicle (request signal generation means, a transmission circuit, and a transmission antenna), means for detecting a response signal from the electronic key (a reception circuit and response signal matching means), and means for performing an alarm output (monitoring means, a third drive circuit, and an alarm lamp) when no response signal is detected in spite of the output of the request signal.
Owner:HONDA MOTOR CO LTD
Heat exchanger for an indoor unit of an air conditioner
ActiveUS9383118B2Large air volumeImprove blowing efficiencyHeating and ventilation casings/coversIndirect heat exchangersCooling coilEngineering
A heat exchanger for an indoor unit of an air conditioner, including at least a housing (1) having an air inlet (15) and an air outlet (16), a cooling coil (3), and a centrifugal blower (4) having an air exit (17), a volute housing (5), a motor (6) and a centrifugal wind wheel (7). The cooling coil (3) and the centrifugal blower (4) are disposed in the housing (1). The air inlet (15) and the air outlet (16) are disposed on both ends of the housing (1). The cooling coil (3) is disposed at the back of the air inlet (15). The centrifugal blower (4) is disposed at the back of the cooling coil (3). The air exit (17) of the centrifugal blower (4) is connected to the air outlet (16) of the housing (1). The motor (6) is an external rotor motor and fits in the center of a cavity in the centrifugal wind wheel (7). A left air intake (11) and a right air intake (12) are formed on both sides of the volute housing (5). The heat exchanger features large air input and air output, and high blowing efficiency.
Owner:ZHONGSHAN BROAD OCEAN MOTOR MFG
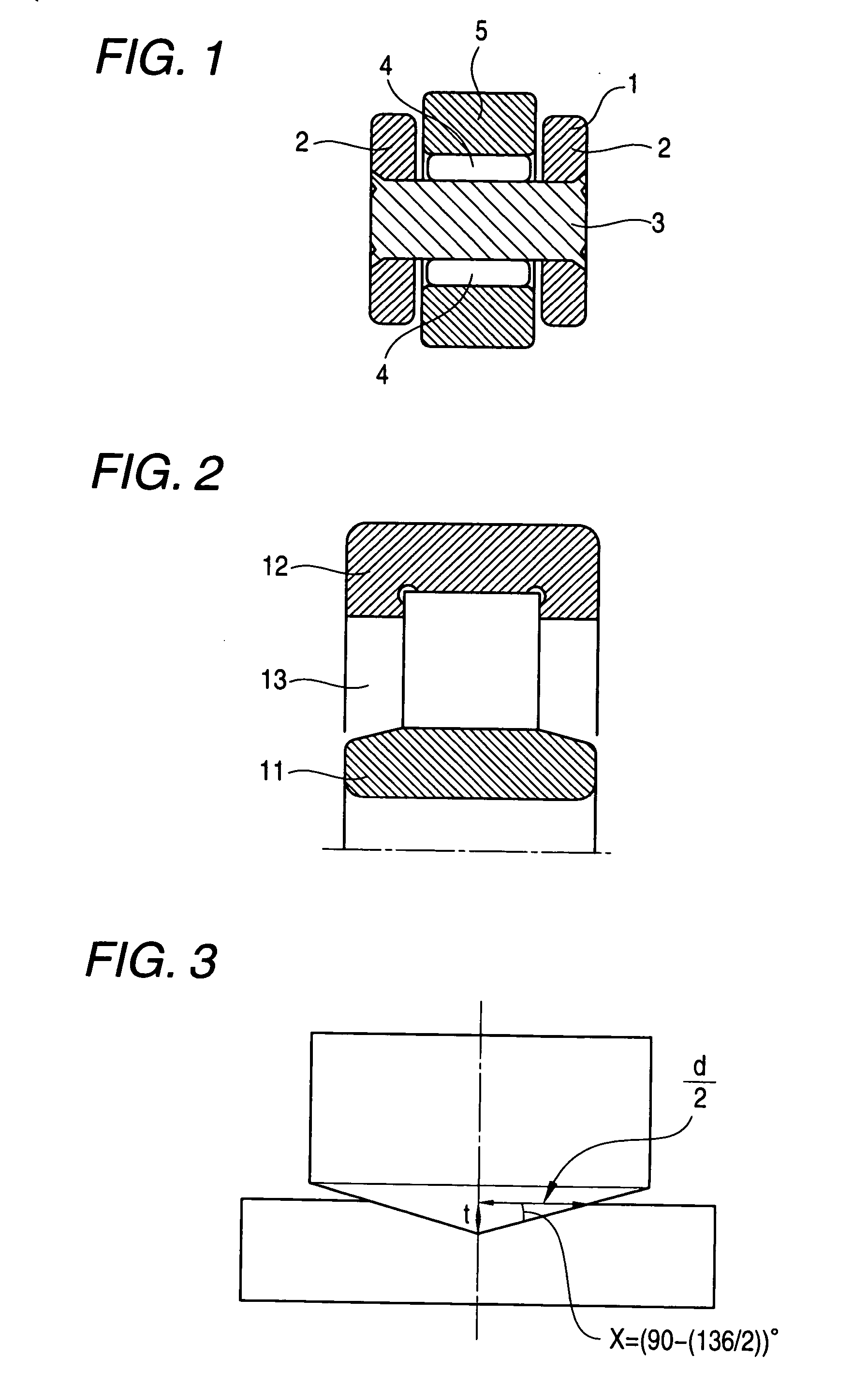
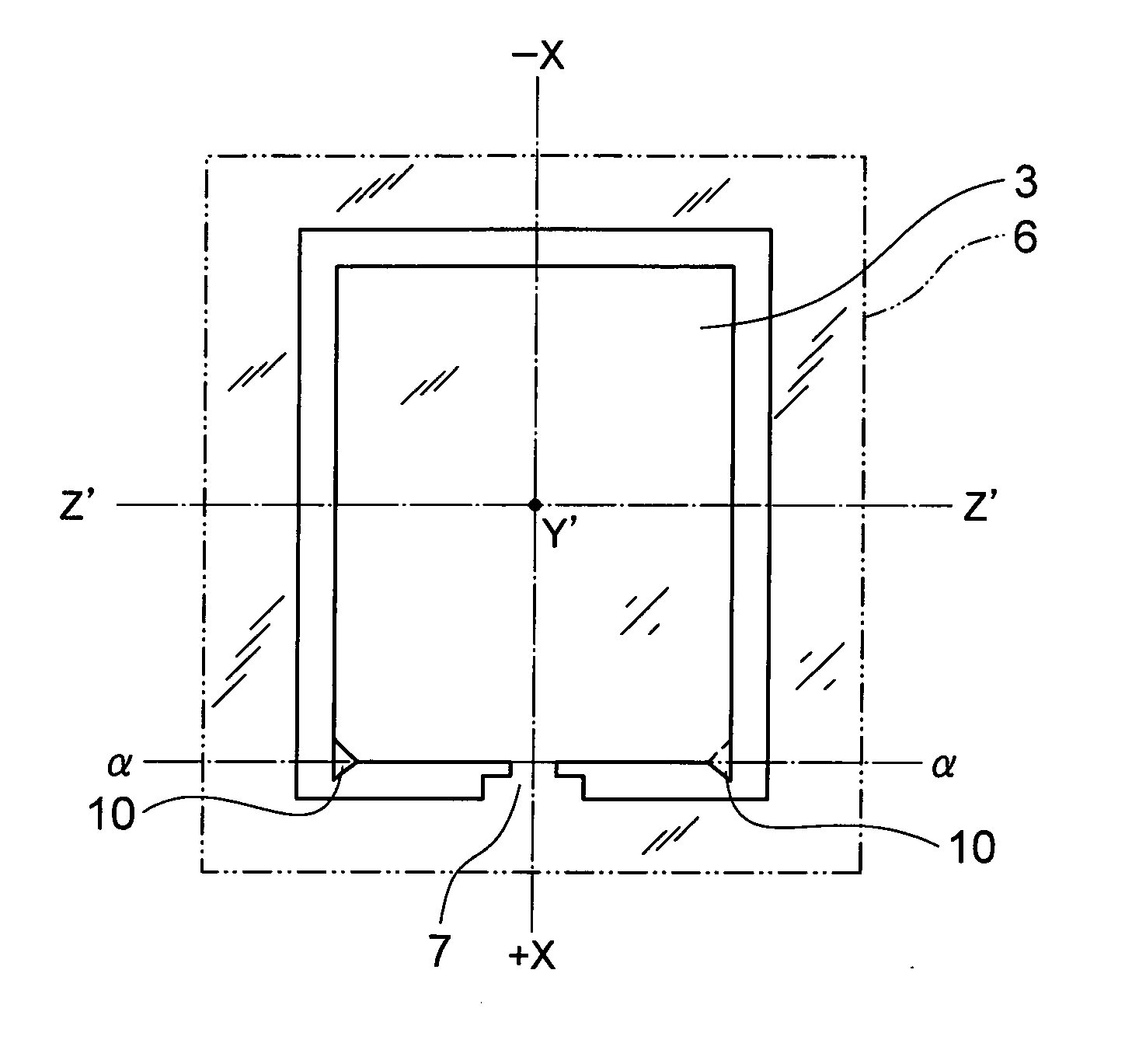
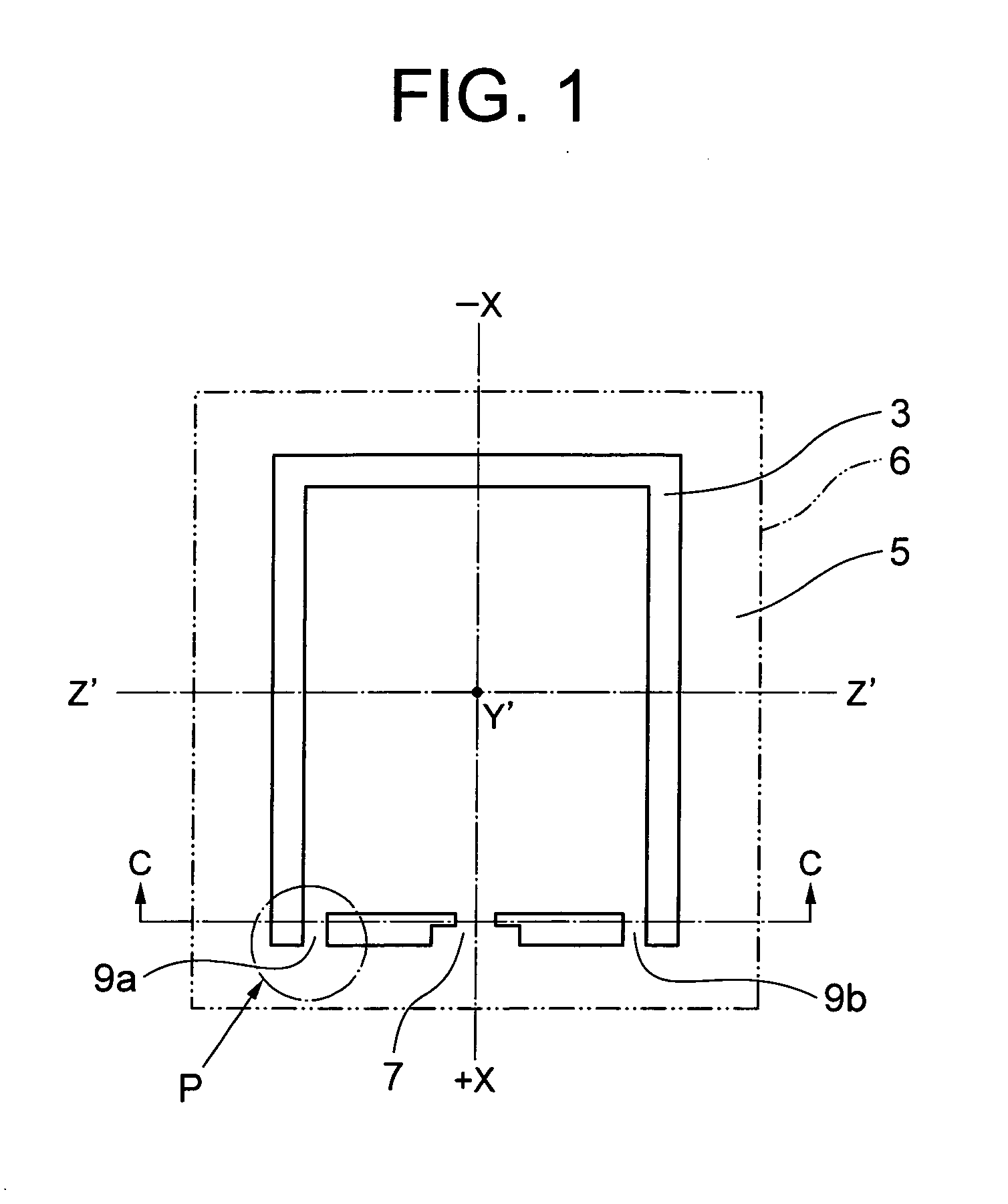
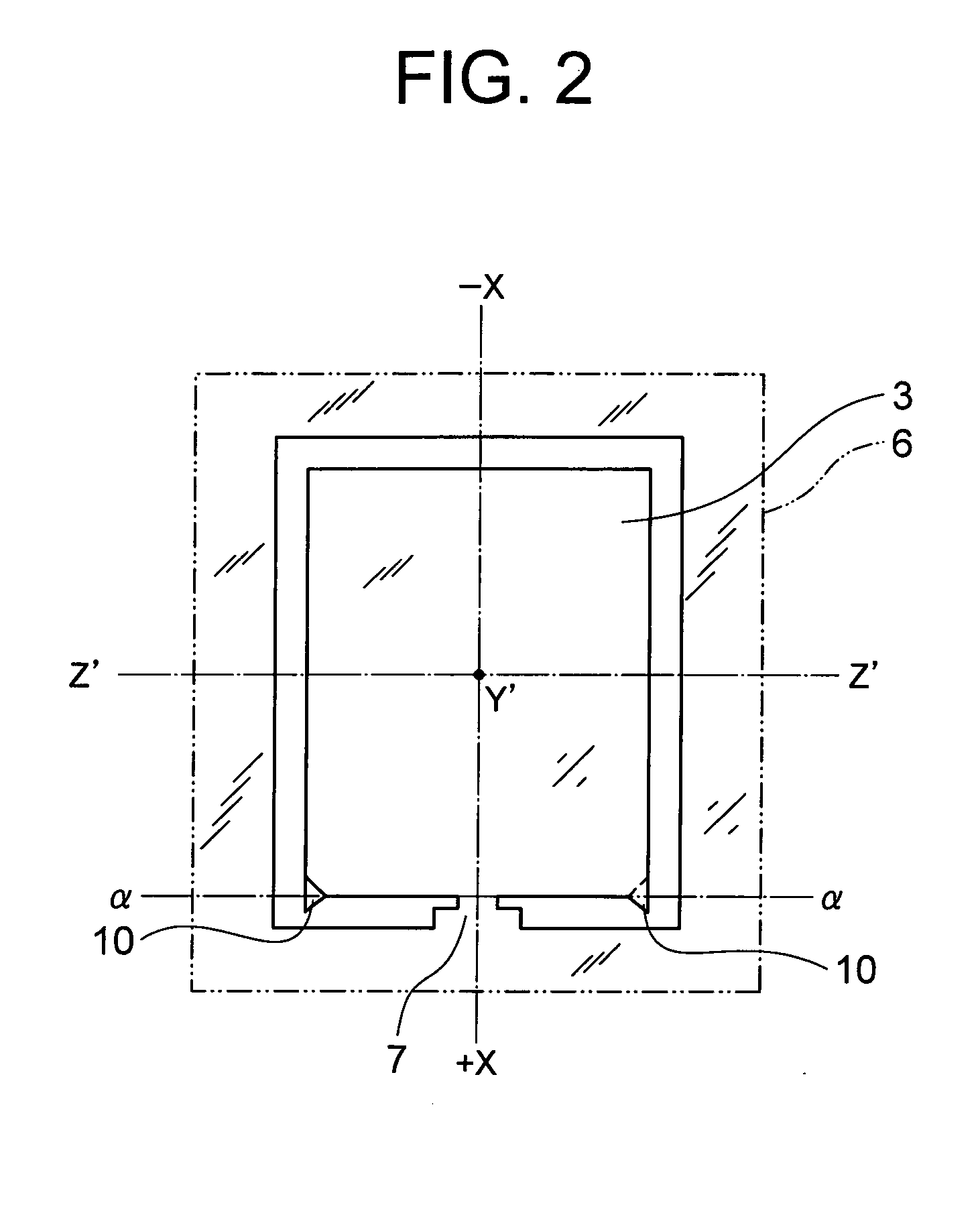
Ultrasonic probe
InactiveUS20100314355A1Small probabilitySmall sizePiezoelectric/electrostrictive device manufacture/assemblyPaper/cardboard articlesEtchingEngineering
There is provided a crystal resonator (crystal element) in which the probability of chipping occurring in separation is small when there is one supporting section with respect to a frame section of a crystal wafer, and inclined surfaces due to the anisotropy of etching are eliminated. The present invention relates to a crystal resonator manufacturing method such that an AT-cut crystal wafer is etched, a large number of rectangular crystal elements are joined with frame sections by supporting sections, and the crystal elements are mechanically cut away from the frame sections. On both sides of the +X-axis one end section of the crystal element, at least the outer side surface has a planarly tapered projection having a triangular inclined surface with an apex in the −X-axis direction, and the tip end of the projection has processing traces of the etching in the +X-axis direction.
Owner:NIHON DEMPA KOGYO CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com