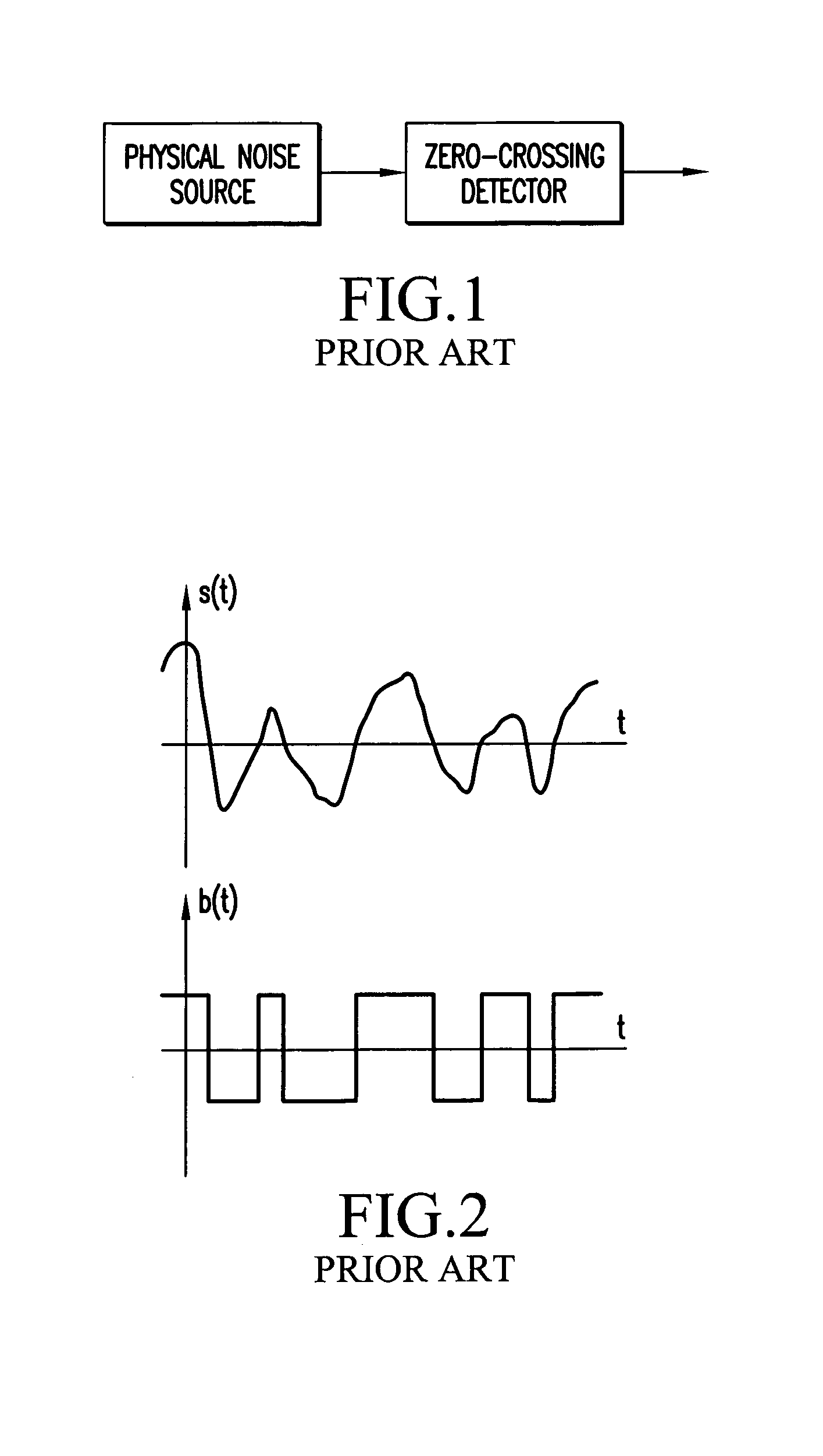
Patents
Literature
73 results about "Random interval" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
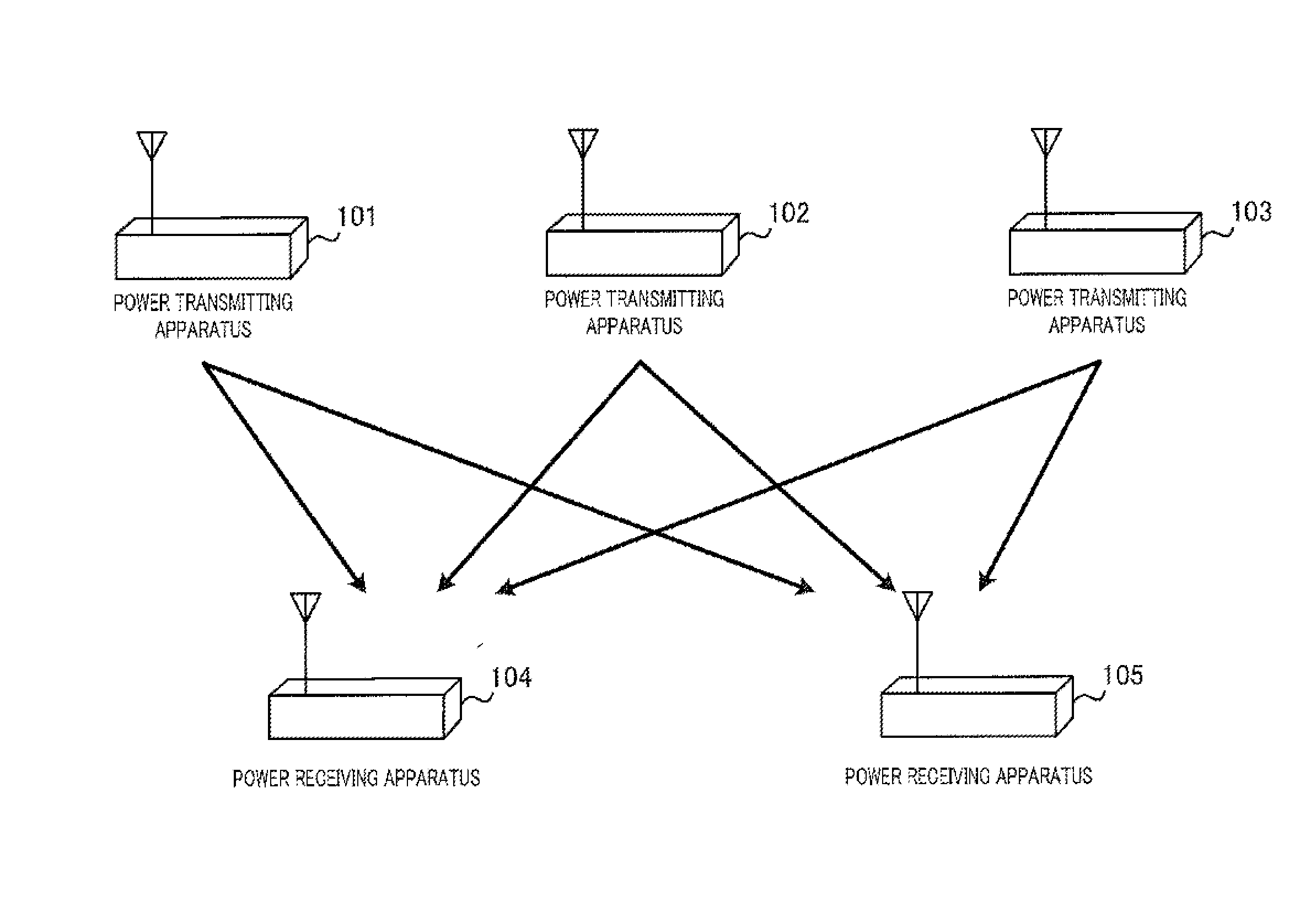
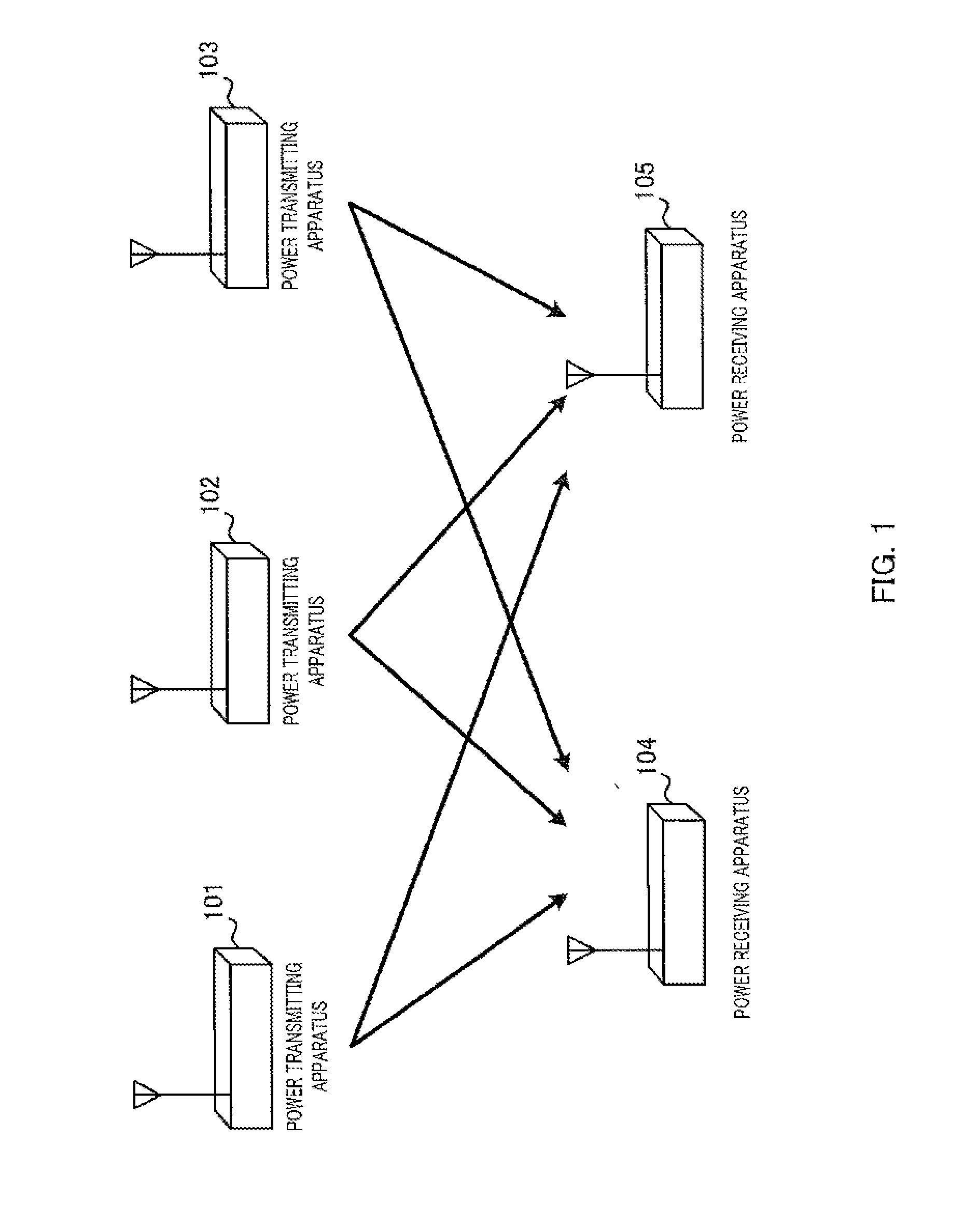
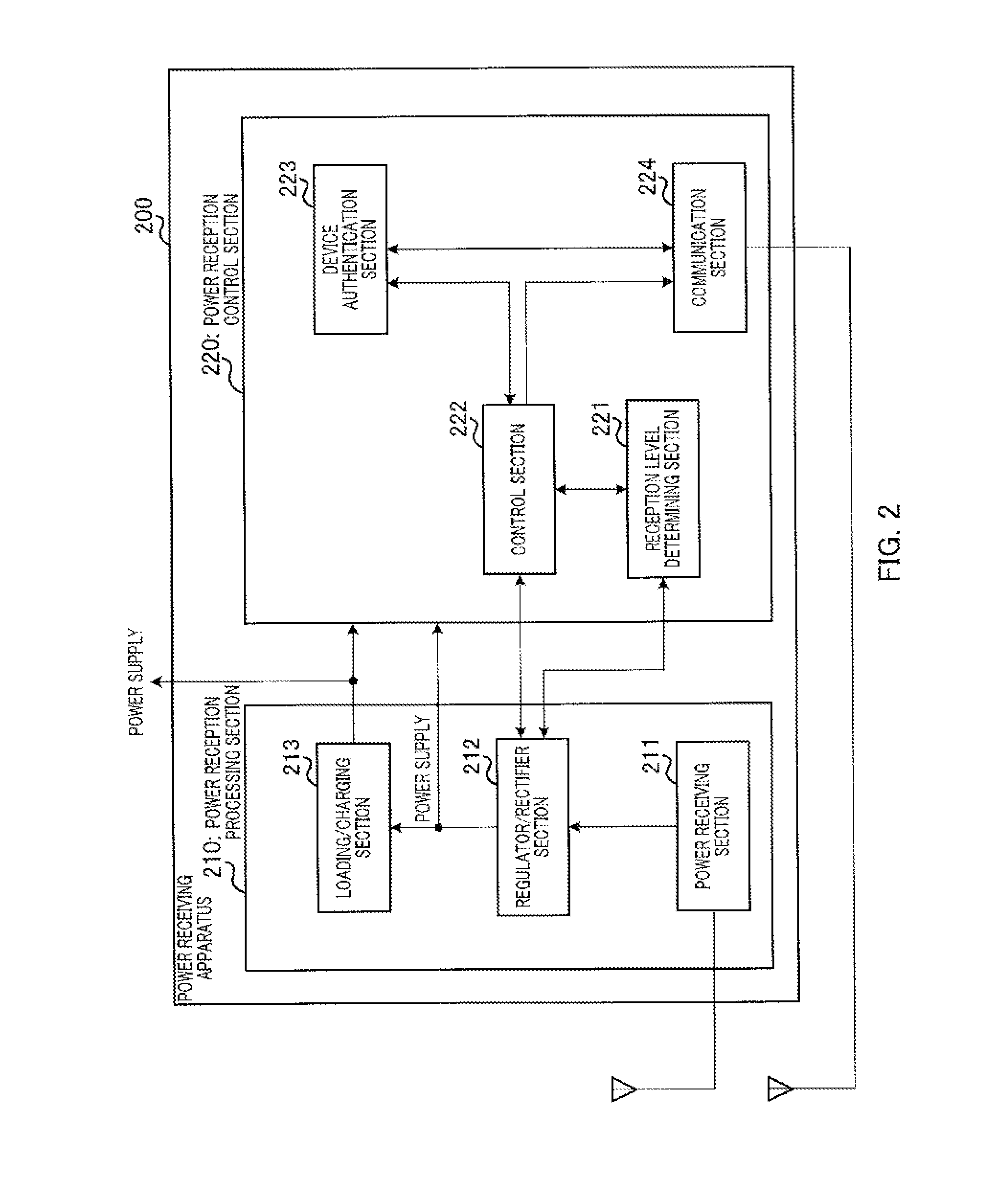
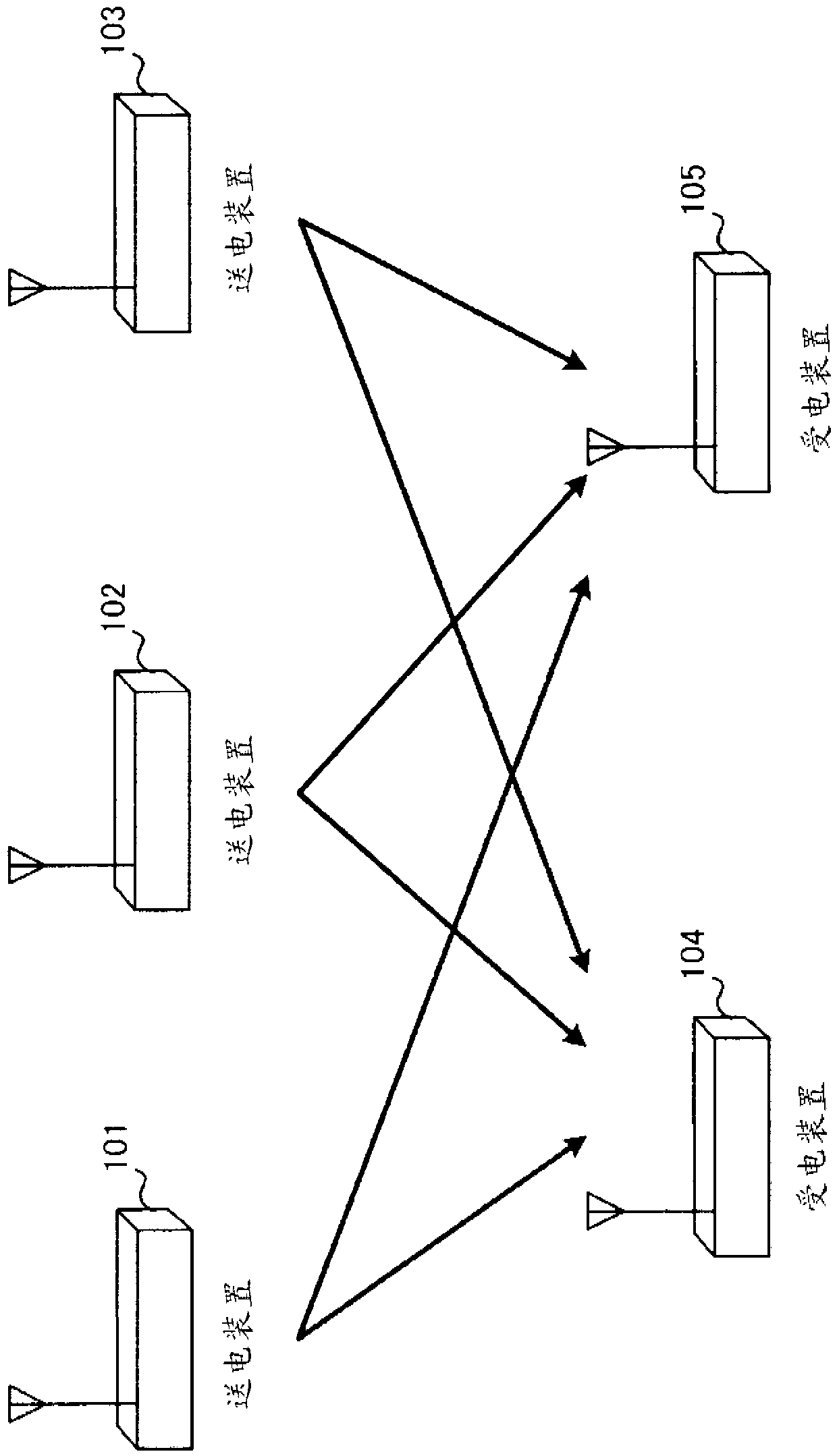
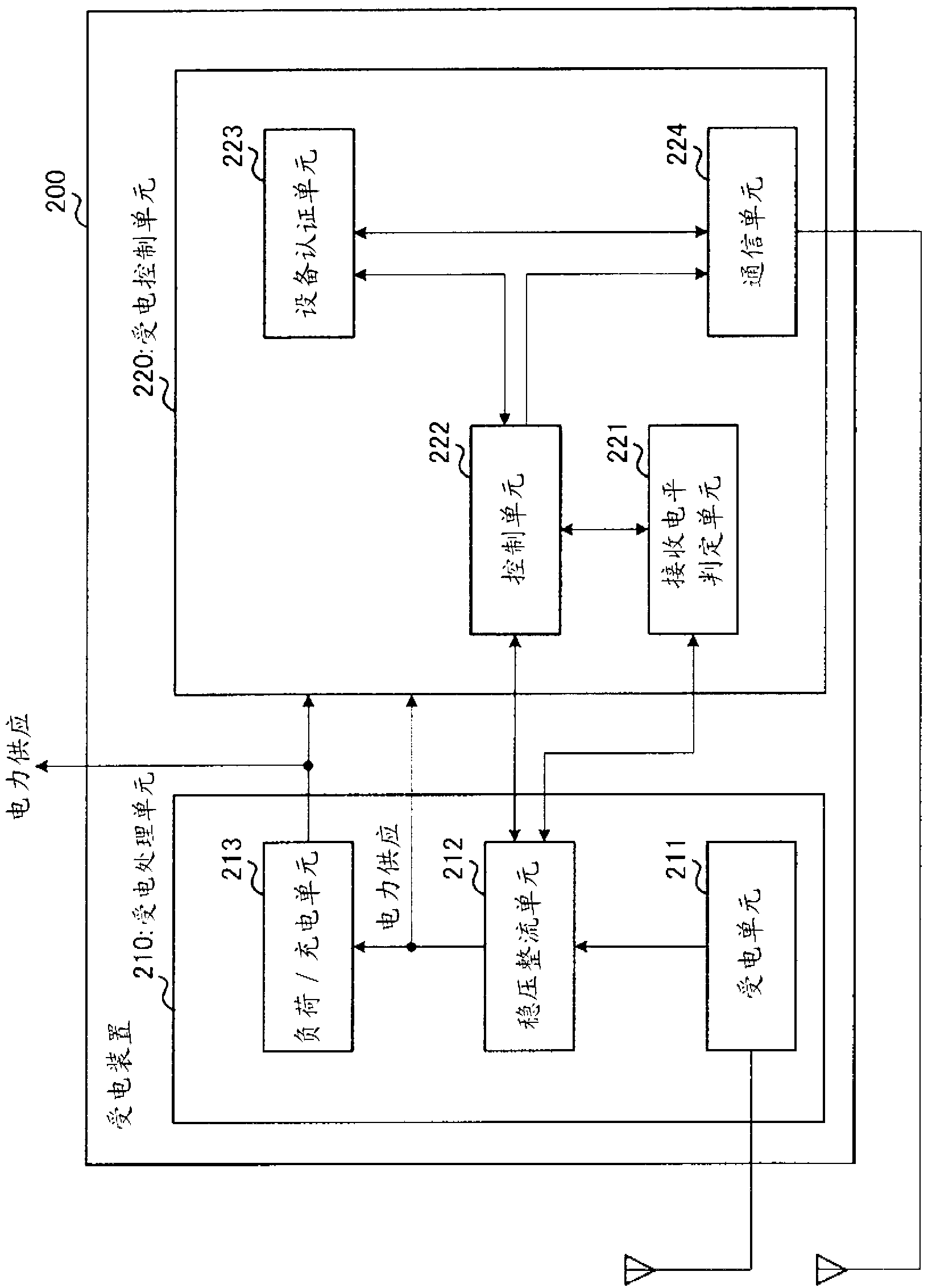
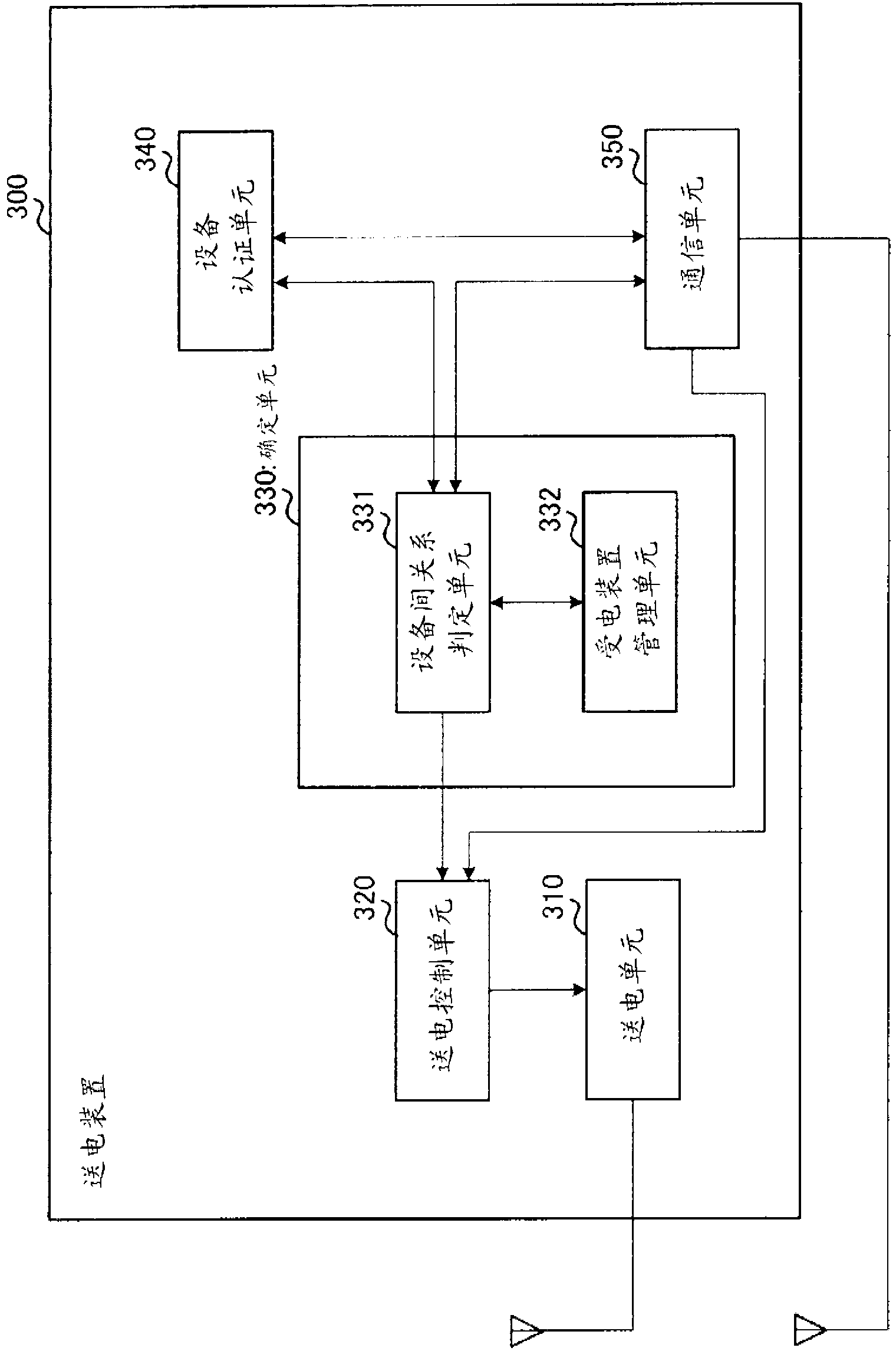
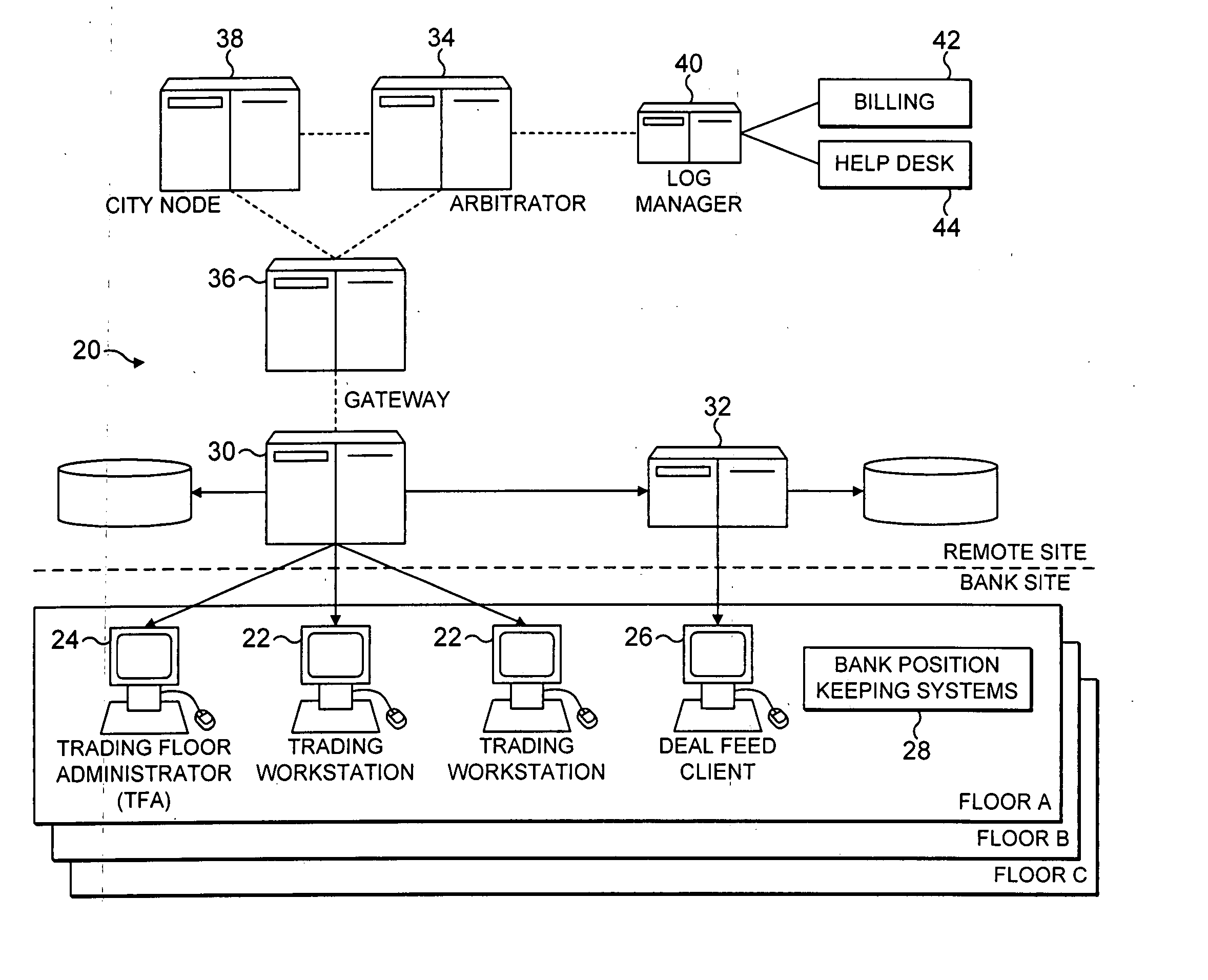
Power transmitting apparatus, power receiving apparatus, and power transmitting method
InactiveUS20130328417A1Circuit authenticationNear-field transmissionElectric power transmissionCommunication unit
Provided is a electric power transmitting apparatus (300) that has sub-electric power transmission mode, and main electric power transmission mode for transmitting power larger than that transmitted in the sub-electric power transmission mode. A power transmitting unit (310) transmits power in a wireless manner. A electric power transmission control unit (320) controls, in sub-electric power transmission mode, power to be transmitted by means of the power transmitting unit (310) and transmission timing of the electric power transmission such that at least power that the electric power receiving apparatus needs to transmit power request notification is transmitted at random intervals. A electric power transmission control unit (320) performs switching to the main electric power transmission mode, in the cases where a communication unit (350) acquired the power request notification transmitted from the electric power receiving apparatus.
Owner:PANASONIC INTELLECTUAL PROPERTY MANAGEMENT CO LTD
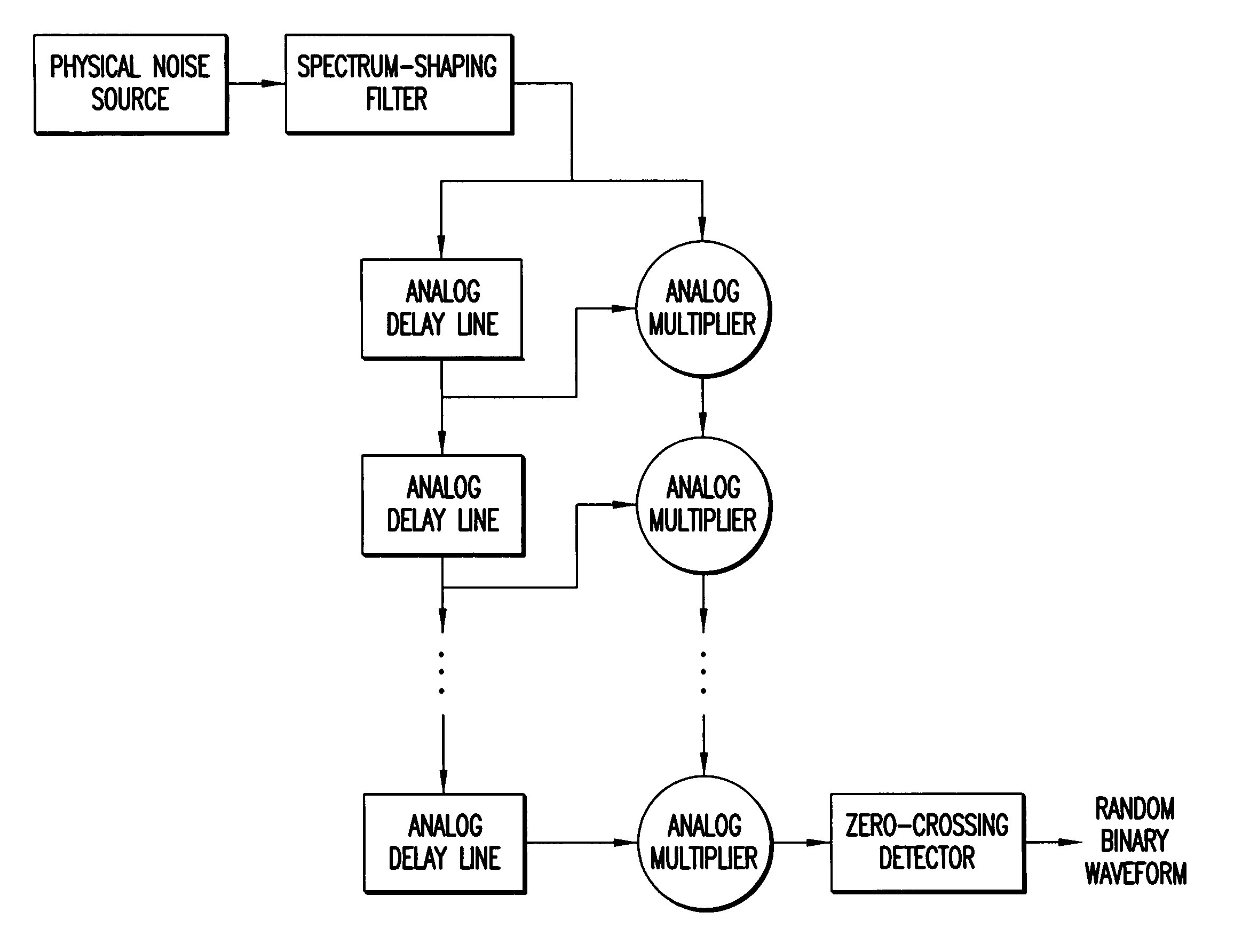
Method and apparatus for generating random signals
InactiveUS7145933B1Reduce probabilityRandom number generatorsTransmissionRandom intervalComputer science
Owner:MITSUBISHI ELECTRIC CORP
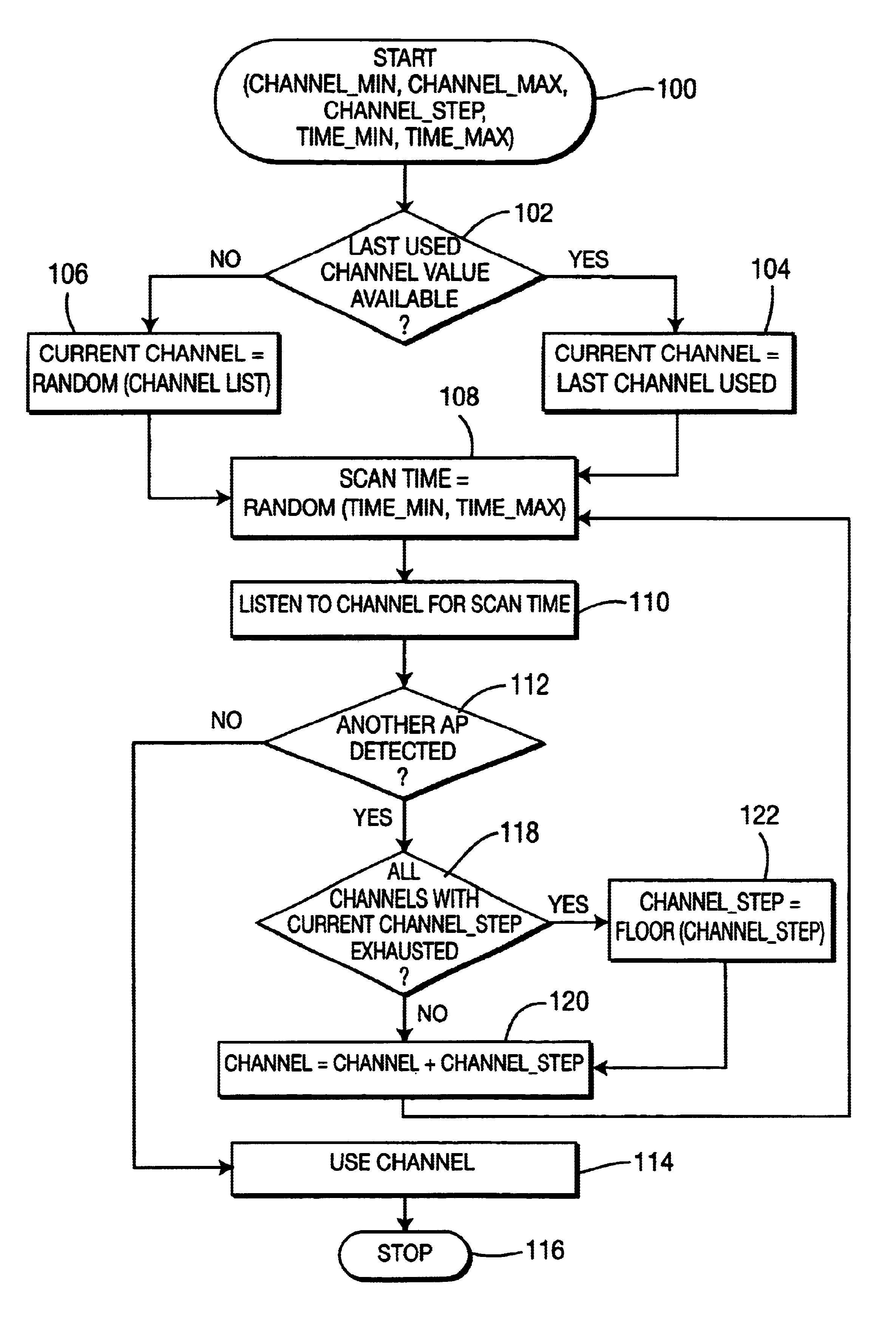
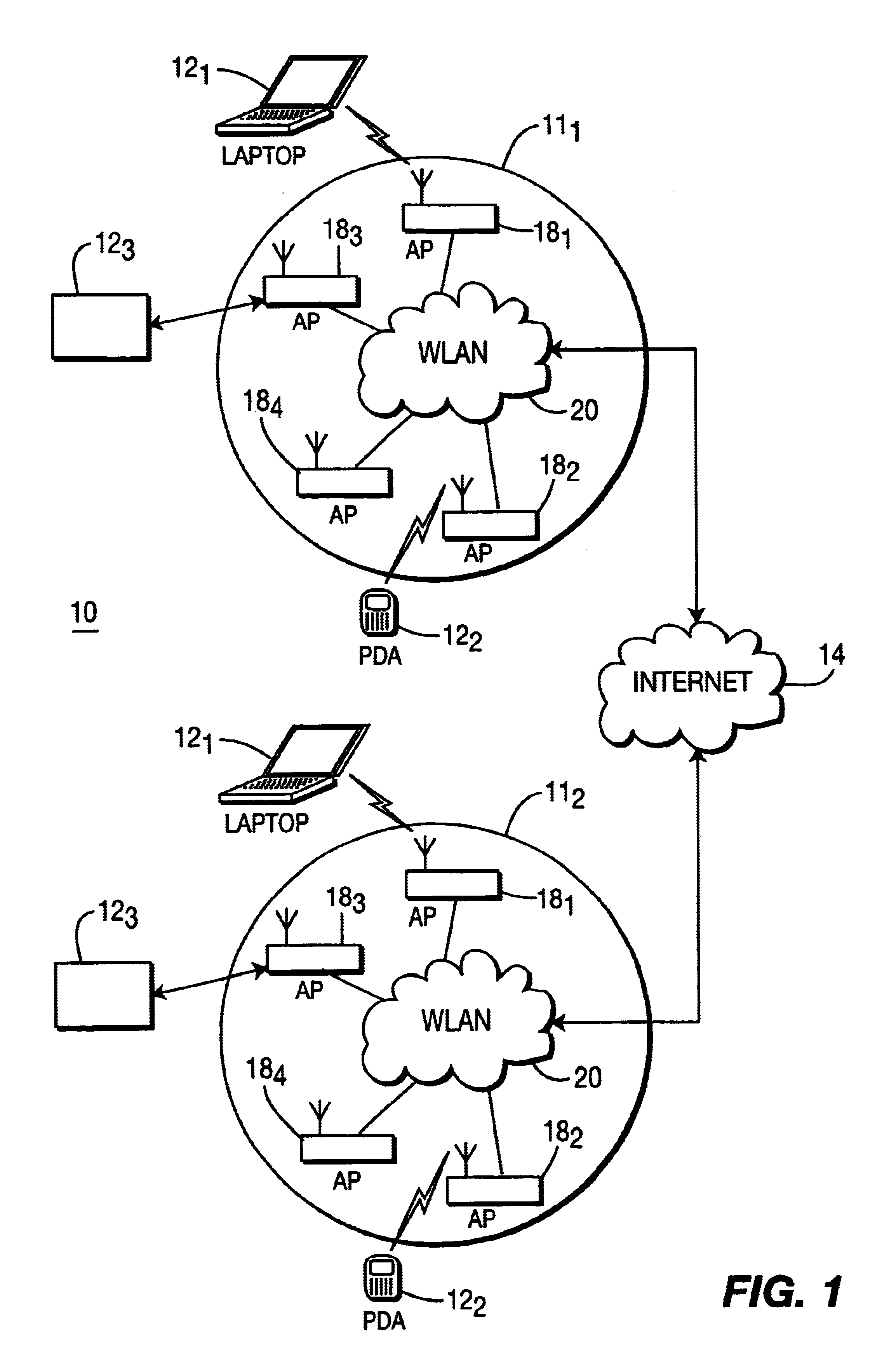
Automatic channel selection in a radio access network
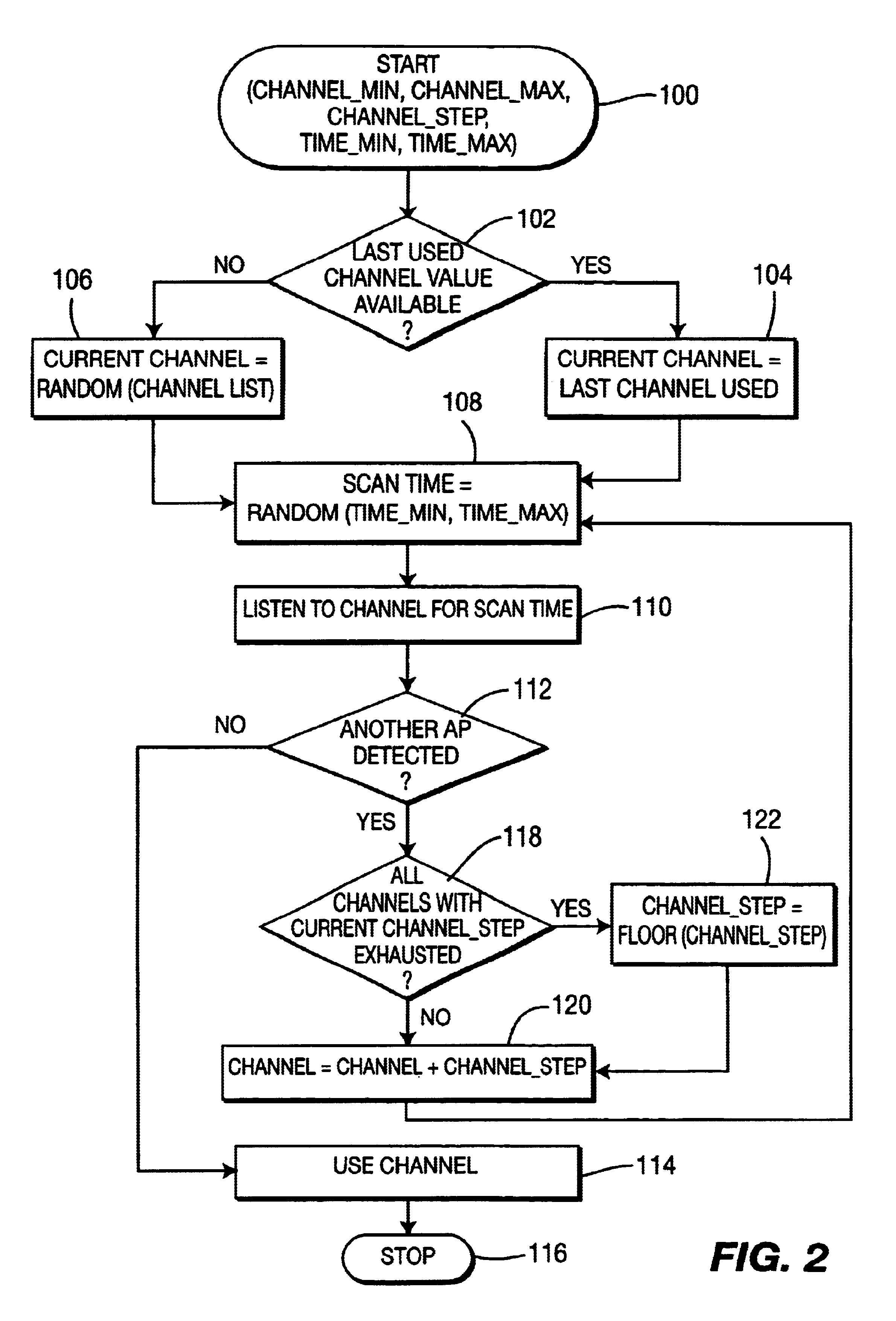
InactiveUS6941143B2Data switching by path configurationRadio/inductive link selection arrangementsAccess networkRadio access network
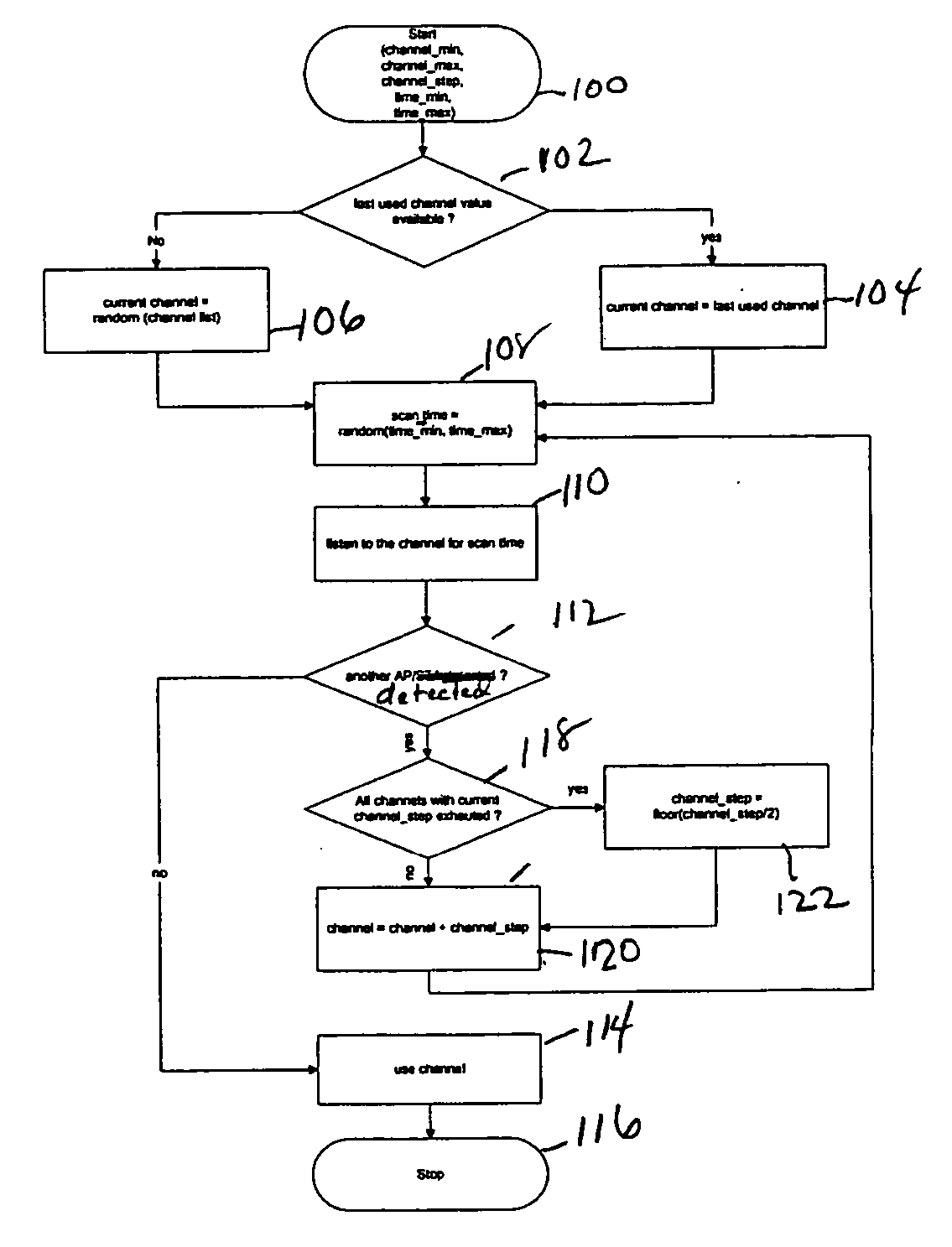
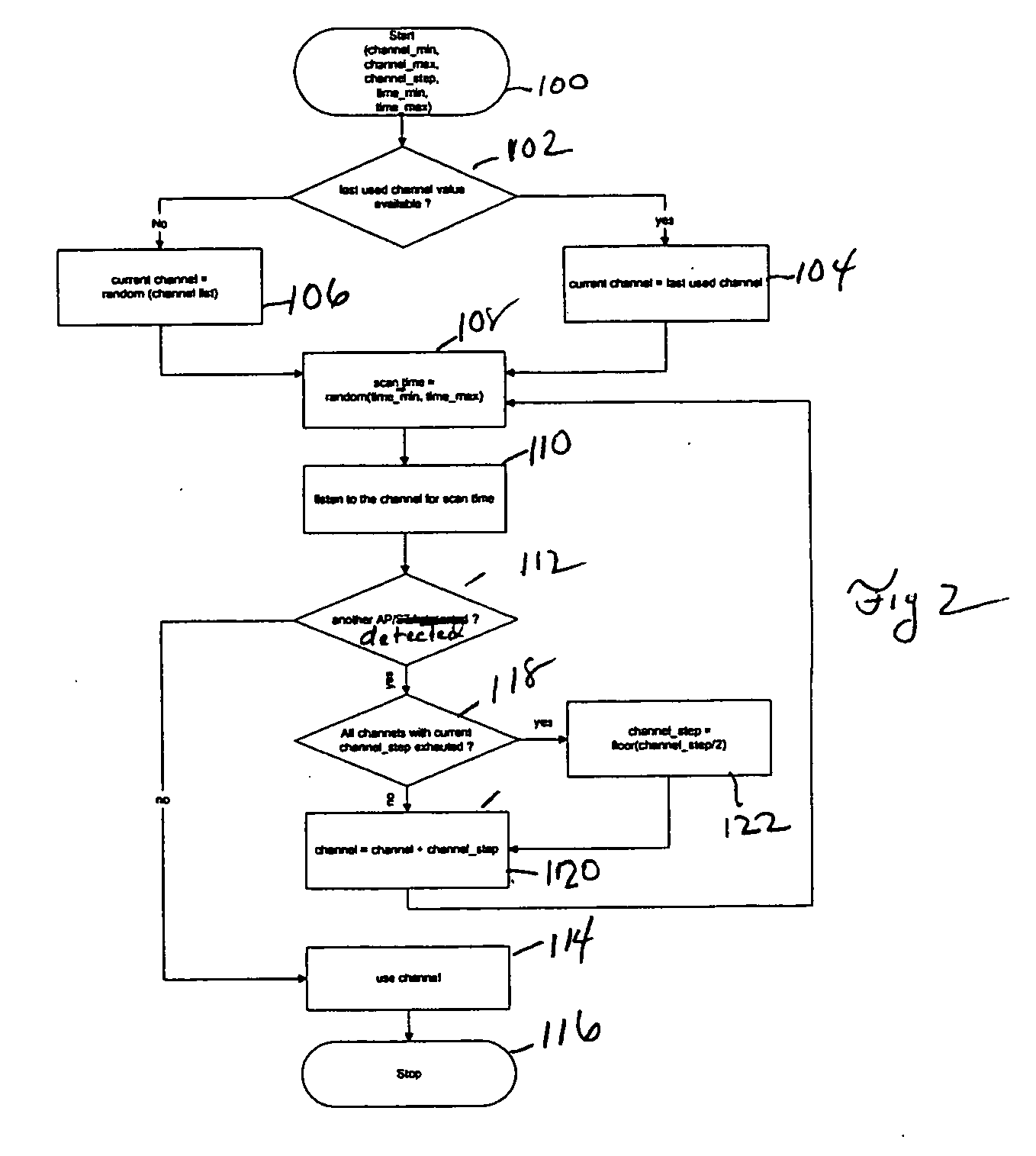
Within a radio access network (111, 112) an access point (181, 182, 183 and 184) selects a channel by first randomly choosing a channel from those available for use. The Access Point then monitors the channel for a random interval to determine if the channel is presently carrying traffic. The Access Point will select the channel unless the channel is in use by another AP. If so, then the AP will select another channel and commence monitoring for a random interval in order to determine whether the channel is available. The AP will continue to choose channels until a suitable channel is found, or all available channels have been exhausted.
Owner:INTERDIGITAL CE PATENT HLDG
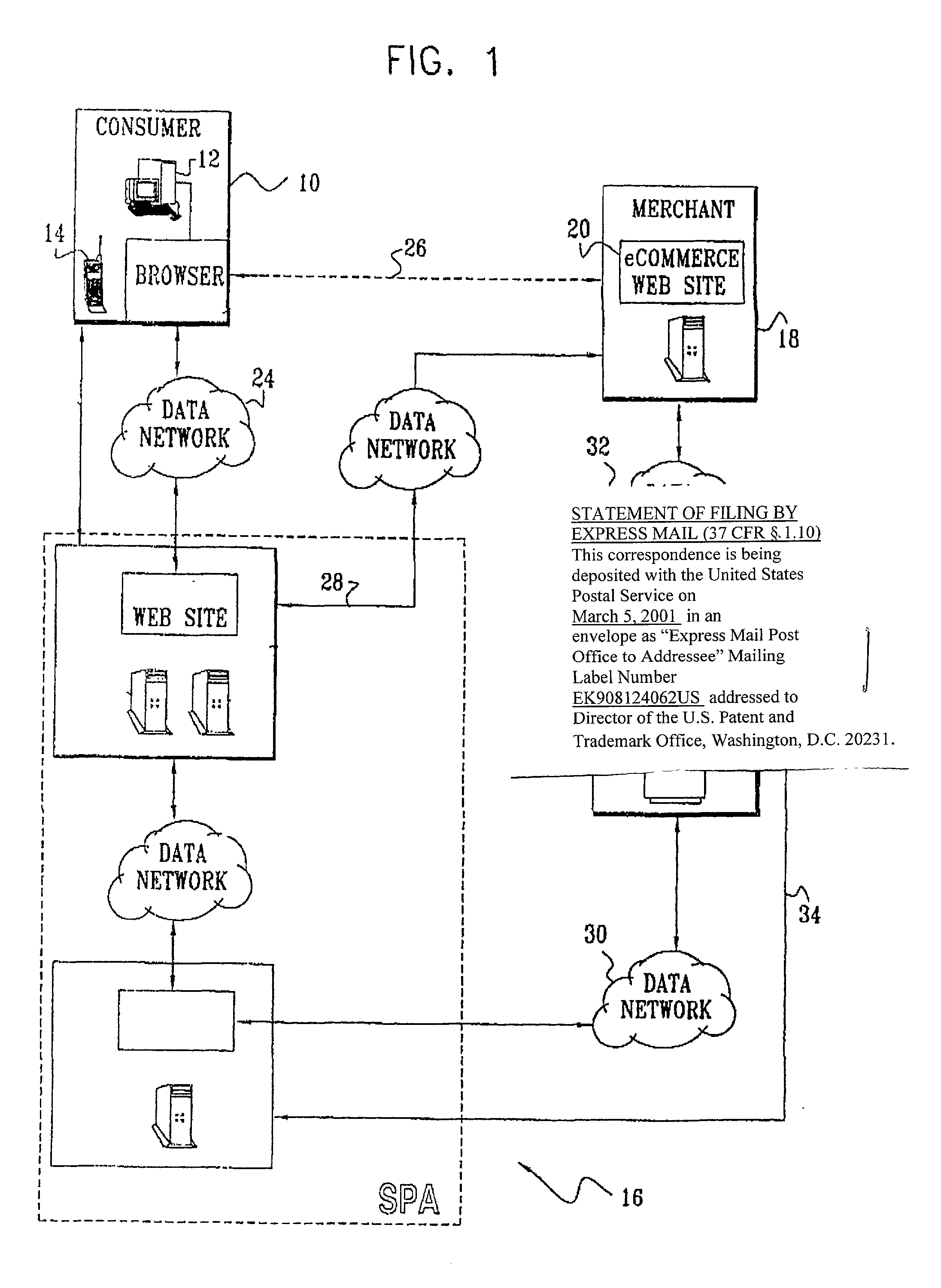
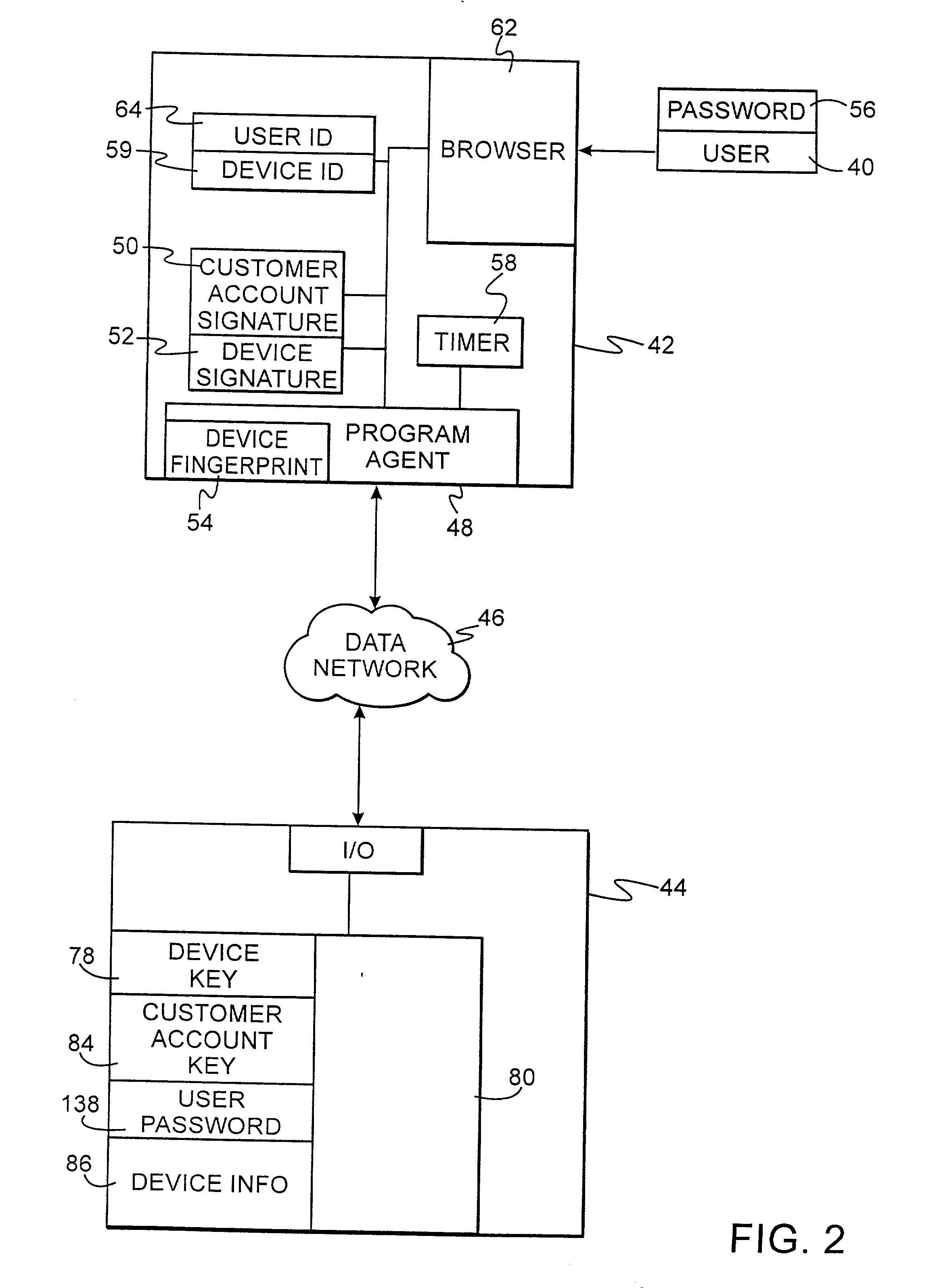
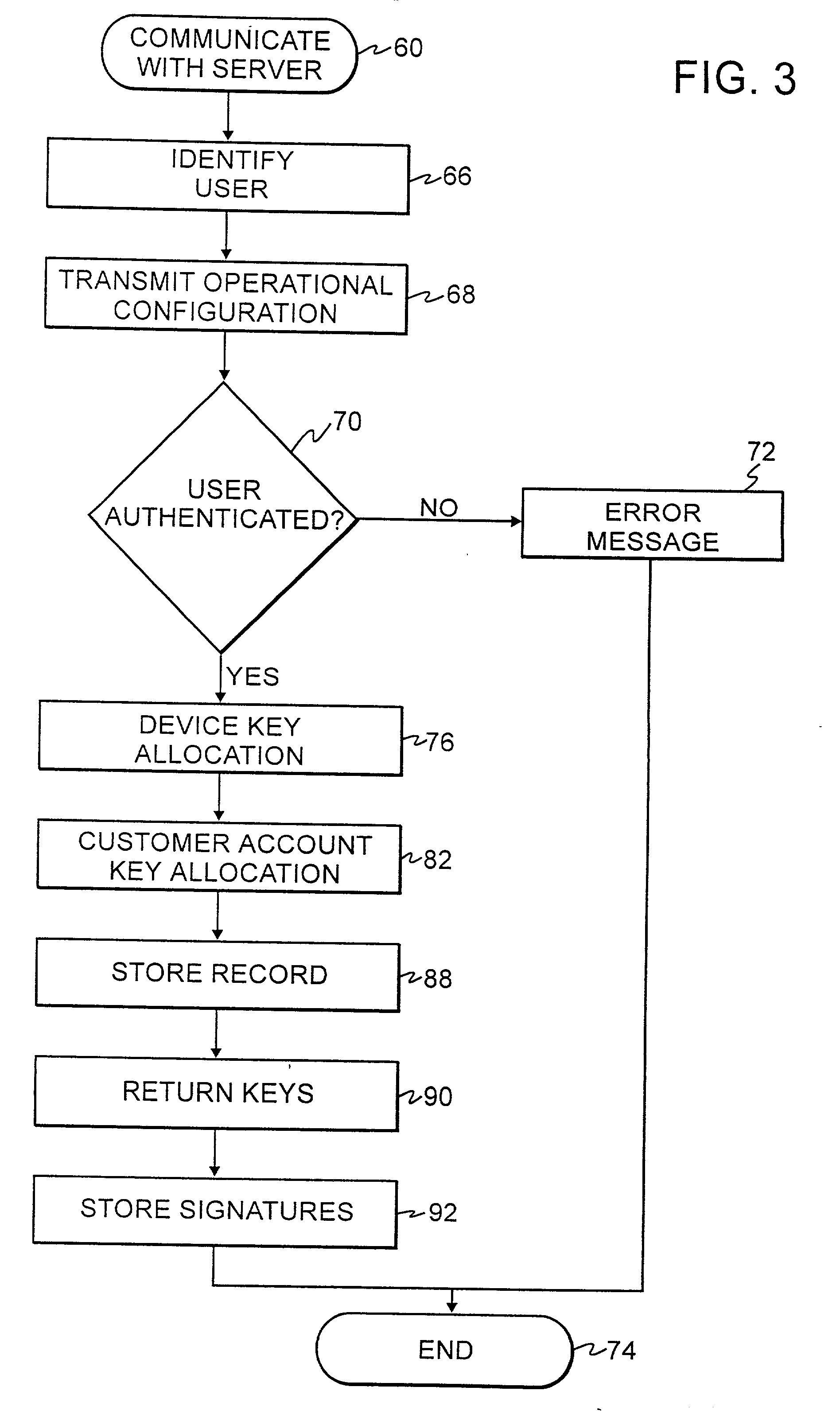
Authentication technique for electronic transactions
InactiveUS20010044896A1User identity/authority verificationDigital data authenticationPasswordRandom interval
A technique for authenticating a first party to a second party is applicable to electronic transactions. In addition to employing personal passwords, and a device operational parameter fingerprint, two signatures are employed, one being characteristic of the first party, and the other being associated with the computer or communications device of the first party. The signatures mutate at random intervals, responsive to mutation requests made by the device of first party to the device employed by the second party. The mutated signatures invalidate previous signatures, and are stored in the computing or communications devices of both parties. The mutation process authenticates the computer or communication device, and may also authenticate the password holder.
Owner:SCHWARTZ GIL +2
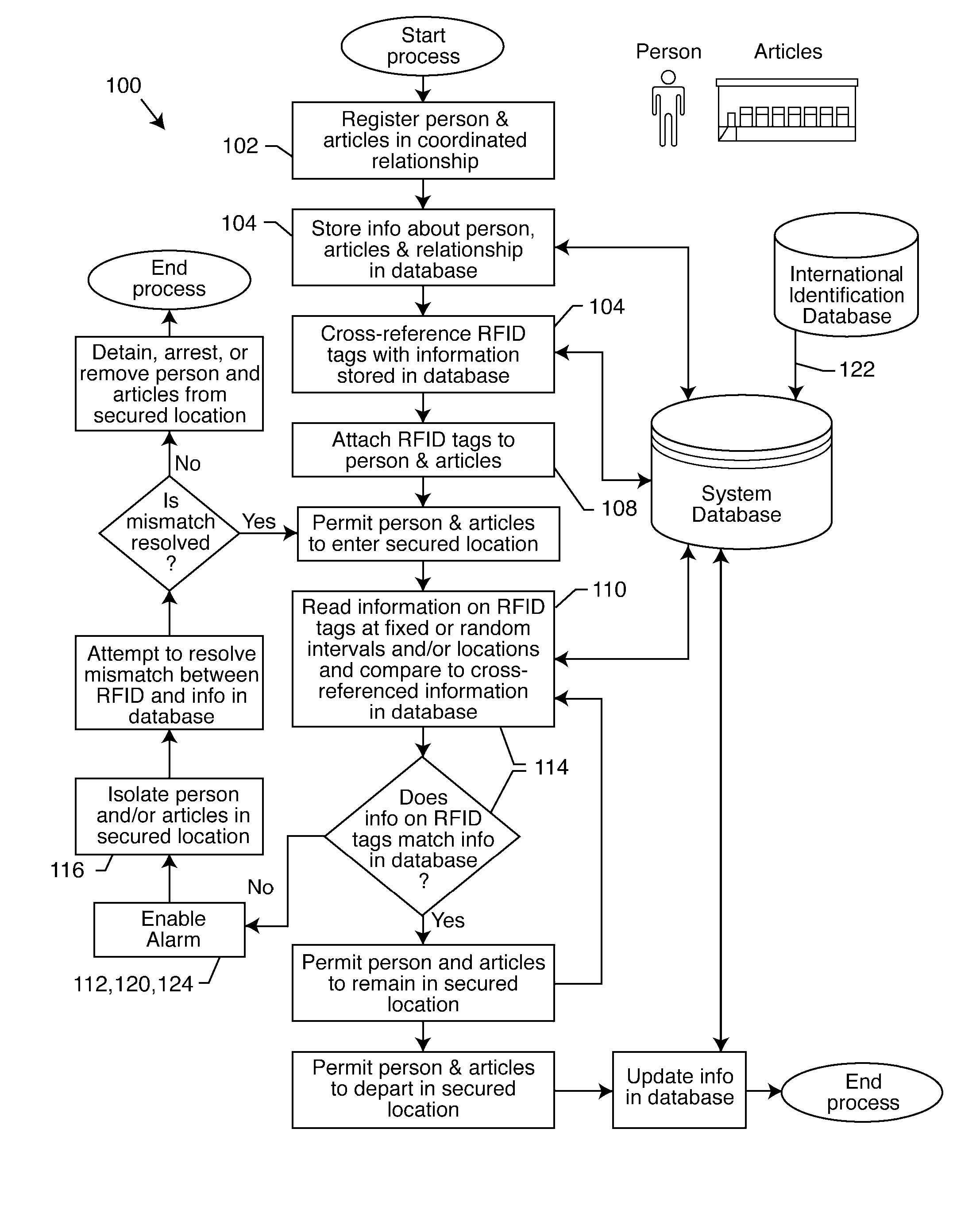
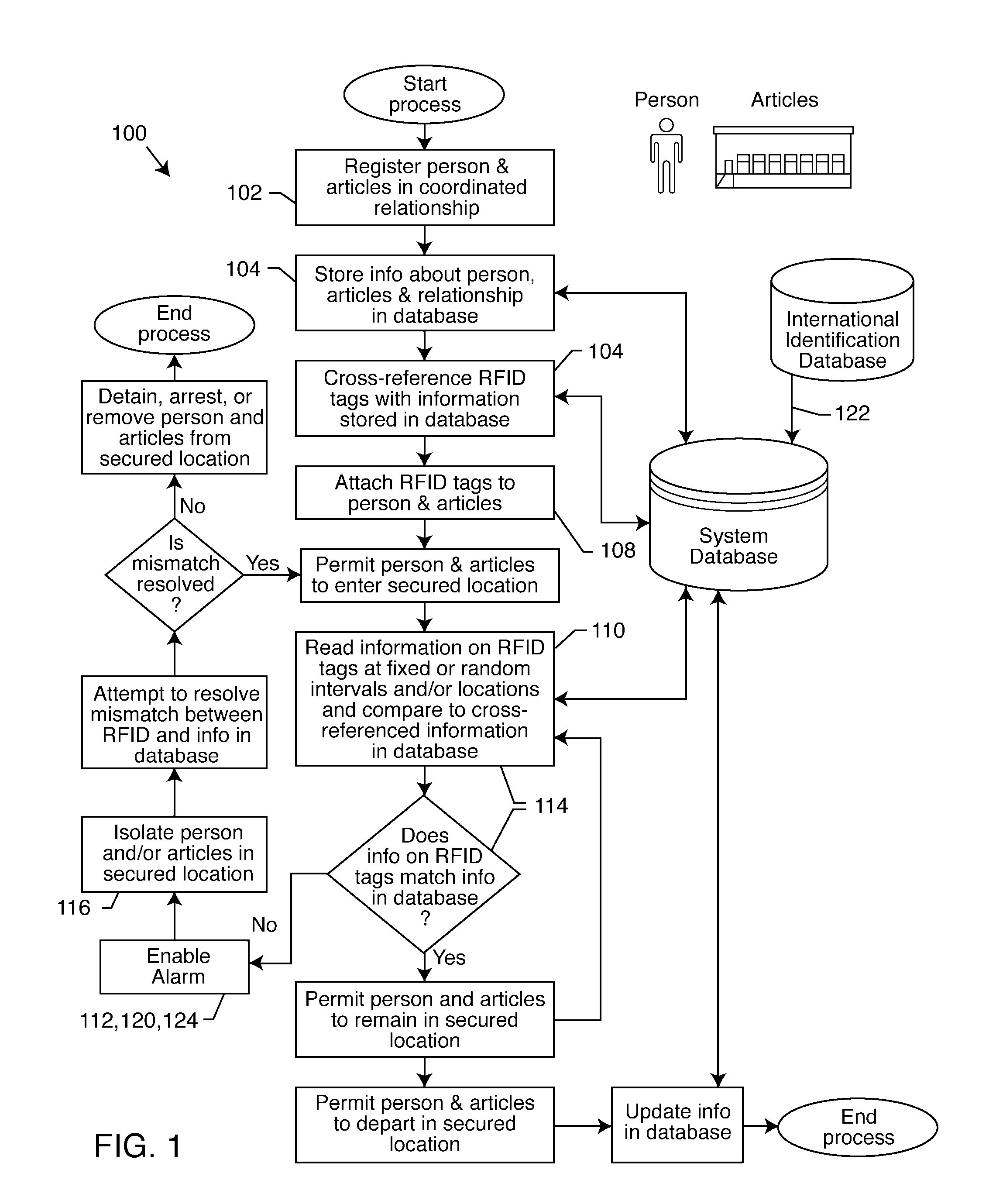
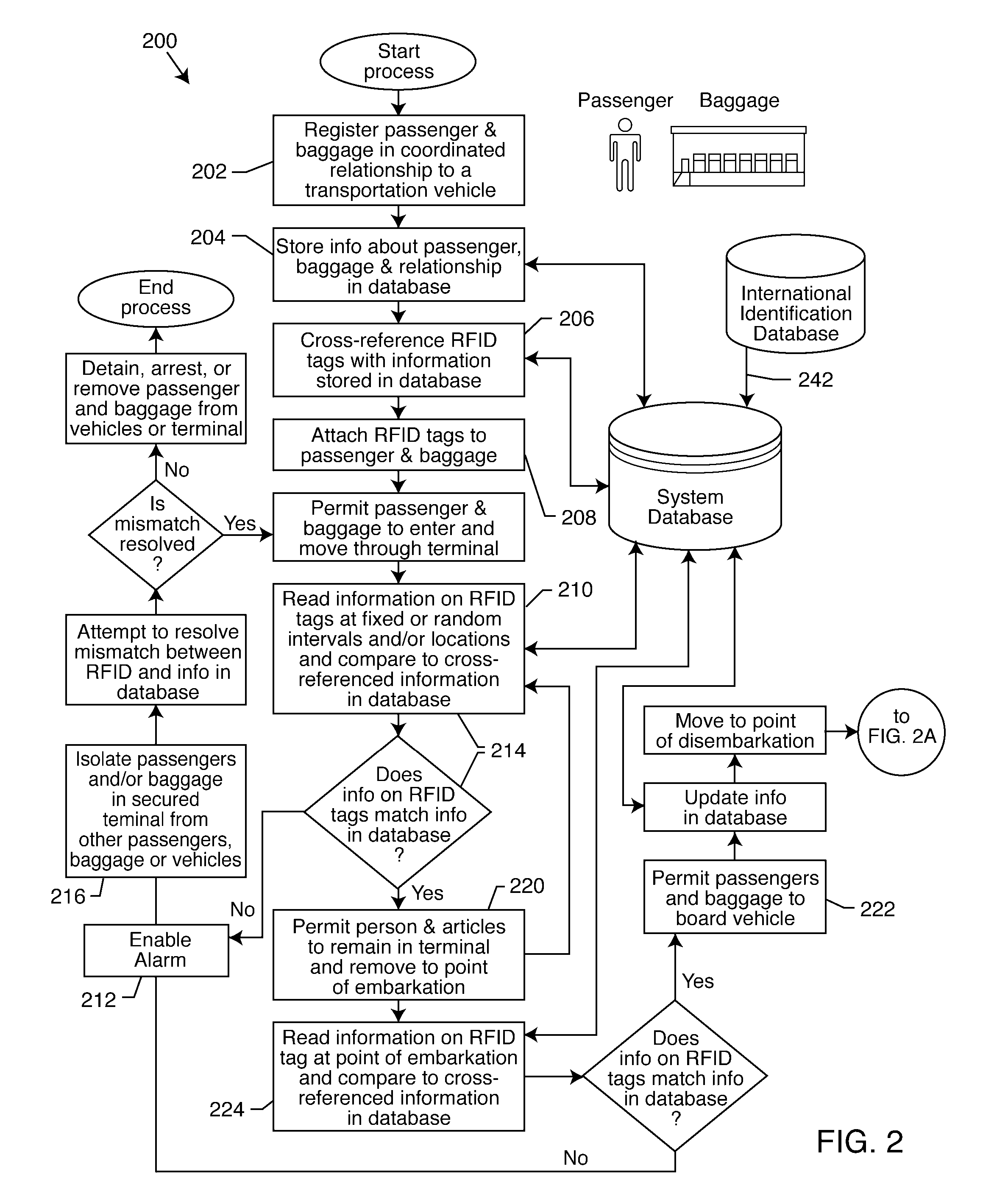
Coordinated identification of persons and/or articles via radio frequency identification cross-identification
InactiveUS20070008138A1Memory record carrier reading problemsIndividual entry/exit registersData miningRadio frequency
A process and system for identifying and tracking persons and related articles, includes the steps of registering a person and one or more articles in a coordinated relationship, storing information concerning the person, the articles and the coordinated relationship in a database, cross-referencing RFID tags with the information stored in the database, attaching the cross-referenced RFID tags to the person and at least one of the articles, reading the RFID tags at random intervals, and enabling an alarm if the RFID tags do not match the cross-referenced information stored in the database. The invention also includes a system for performing this inventive process. The process may be adapted to various situations, a particularly preferred embodiment is adapted to the transportation industry.
Owner:PRECISION DYNAMICS CORPORATION
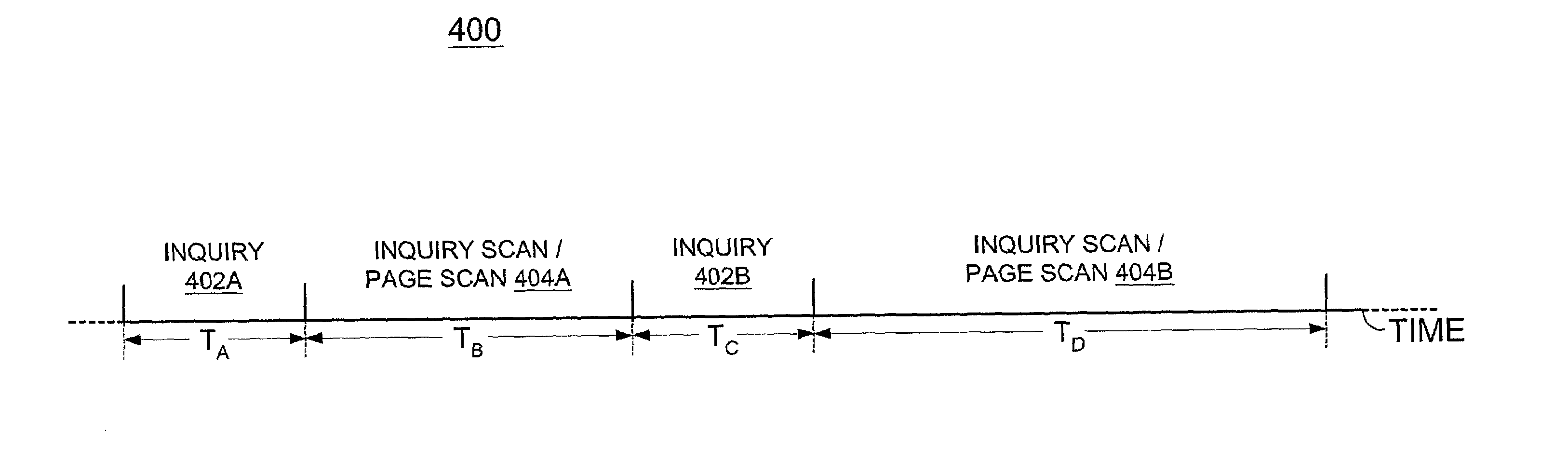
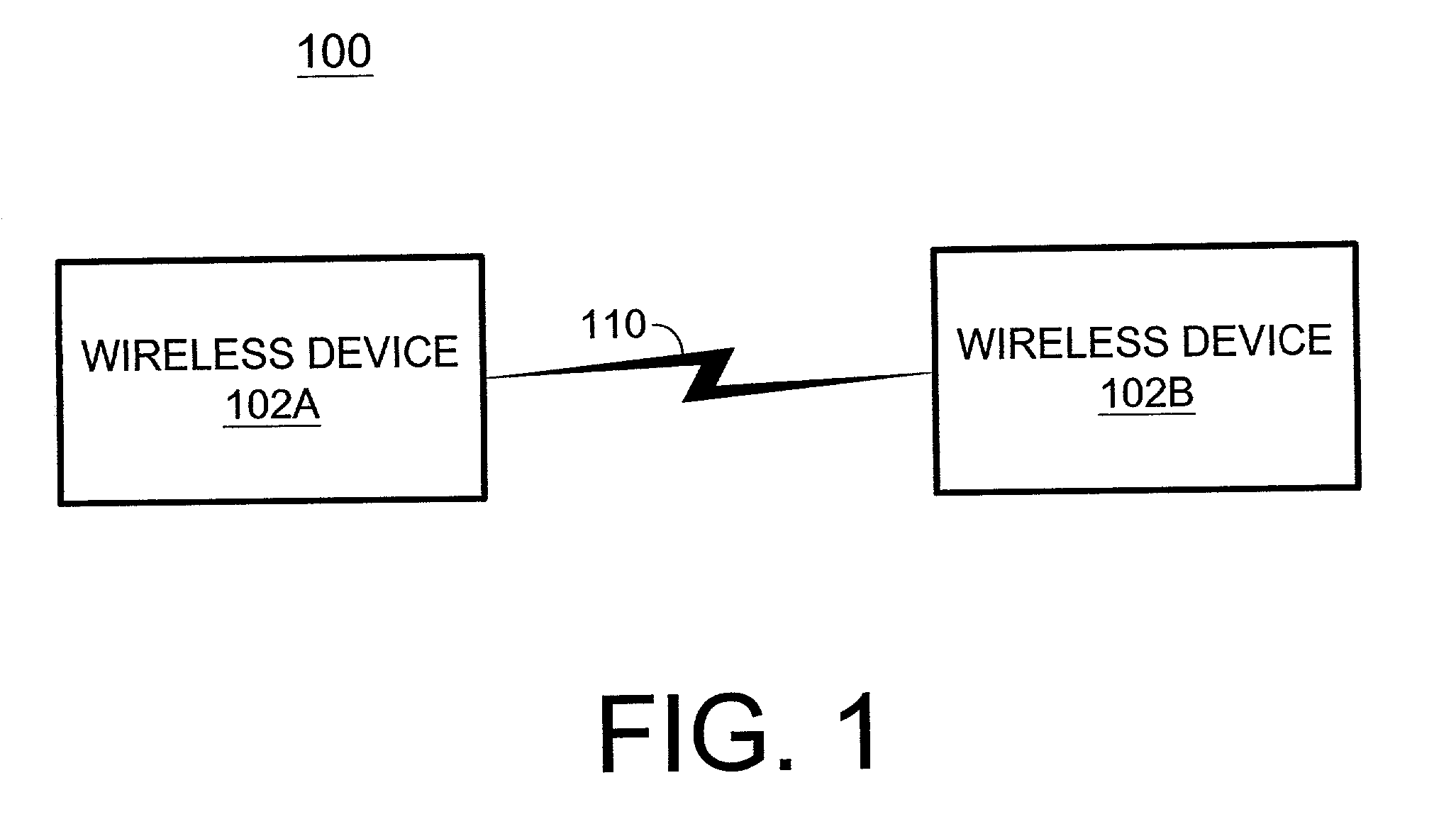
System and method for establishing a connection between wireless devices
InactiveUS7215923B2Near-field transmissionElectric signal transmission systemsComputer hardwareClient-side
A system and method according to the present invention allow two or more peer-to-peer wireless devices to automatically connect to each other with no knowledge or pre-configuration of client / server roles. According to a first aspect of the present invention, a wireless device performs inquiries at a random interval, and performs an inquiry scan and a page scan when not performing the inquiries. Upon receiving a first device address in response to one of the inquiries, the wireless device performs a first page using the device address to establish a connection. And upon receiving an inquiry during the inquiry scan, the wireless device responds with a second device address, and if a second page is received during the page scan, establishes a connection.
Owner:WC ACQUISITION CORP +1
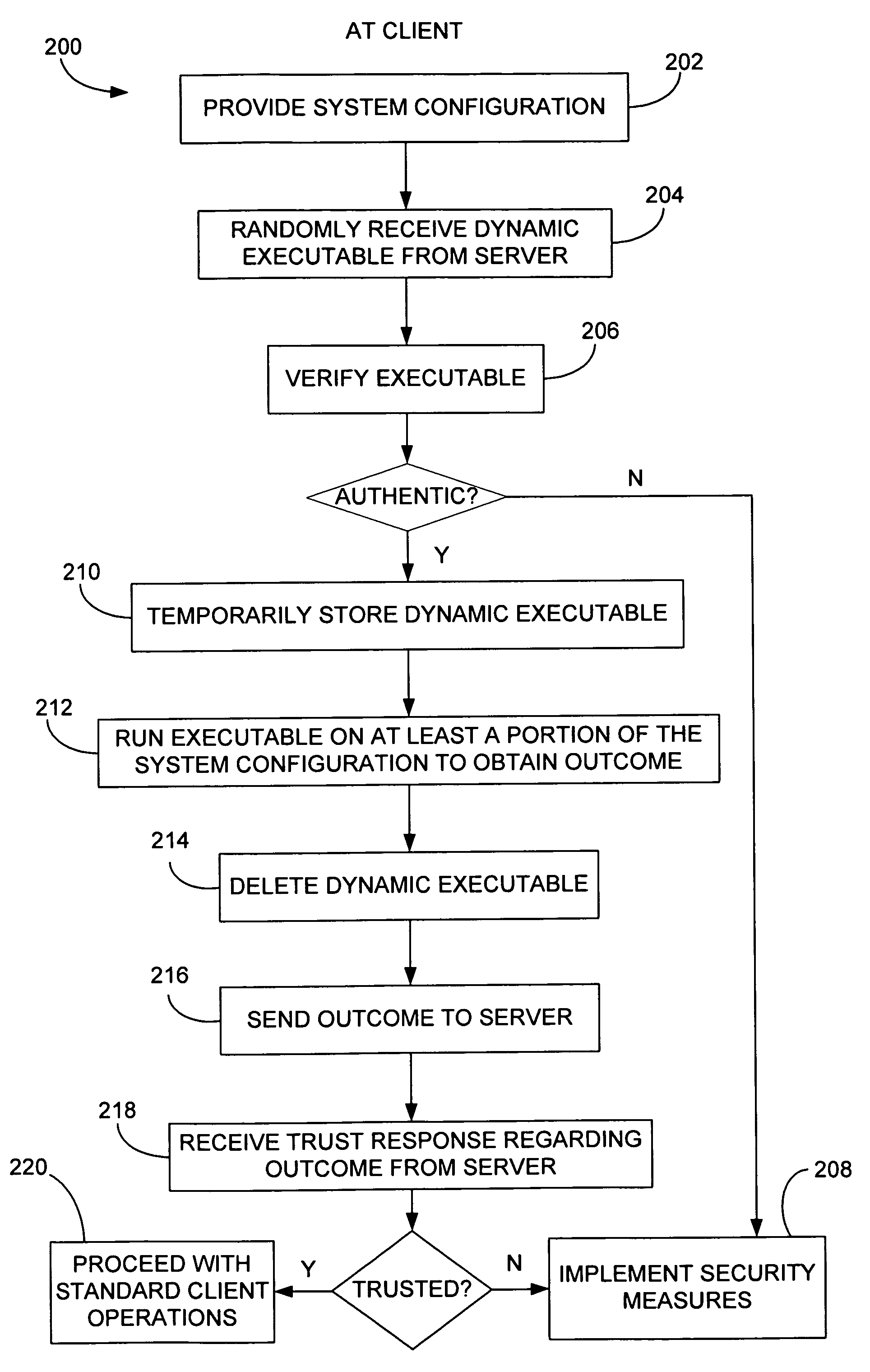
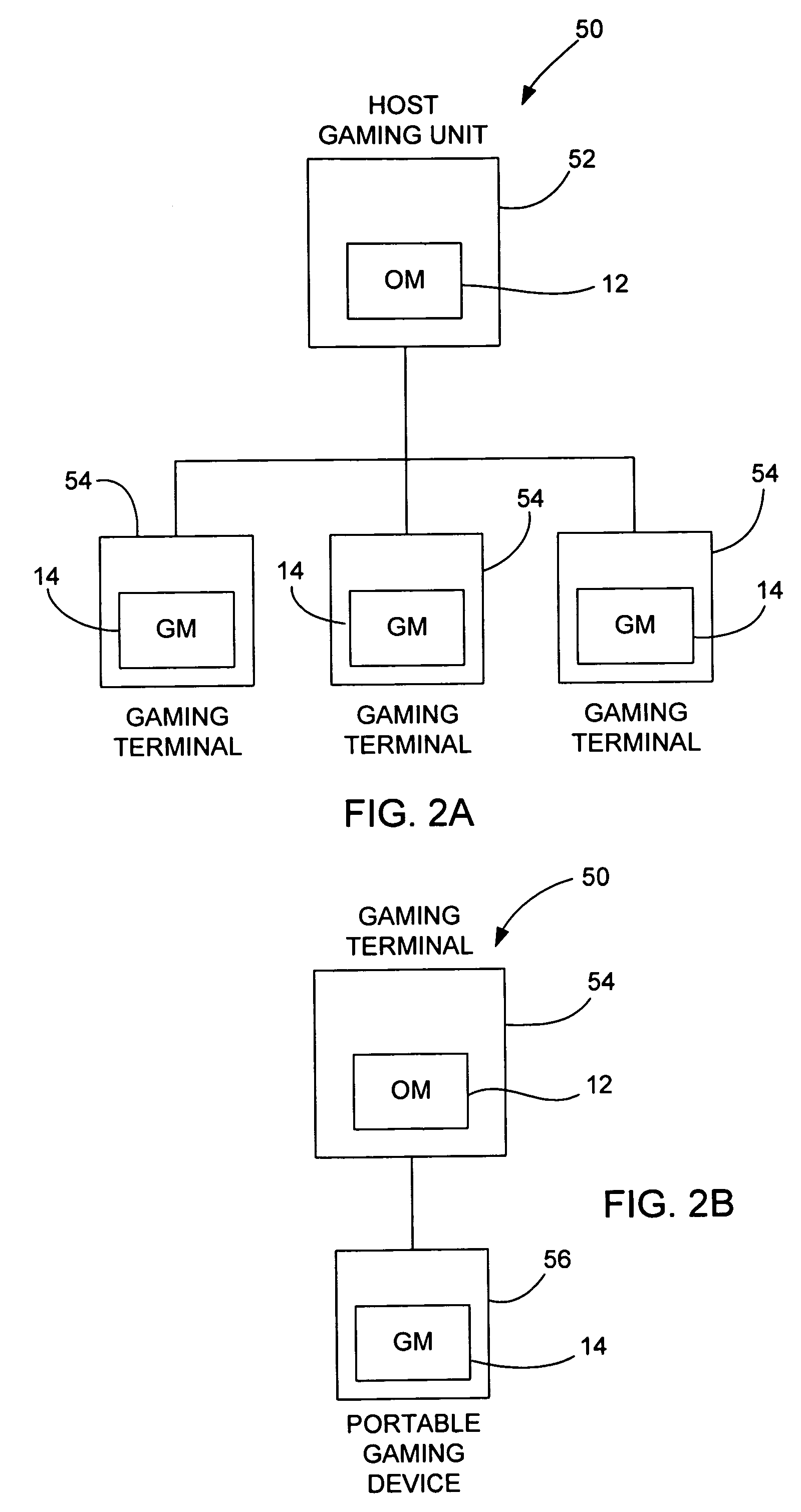
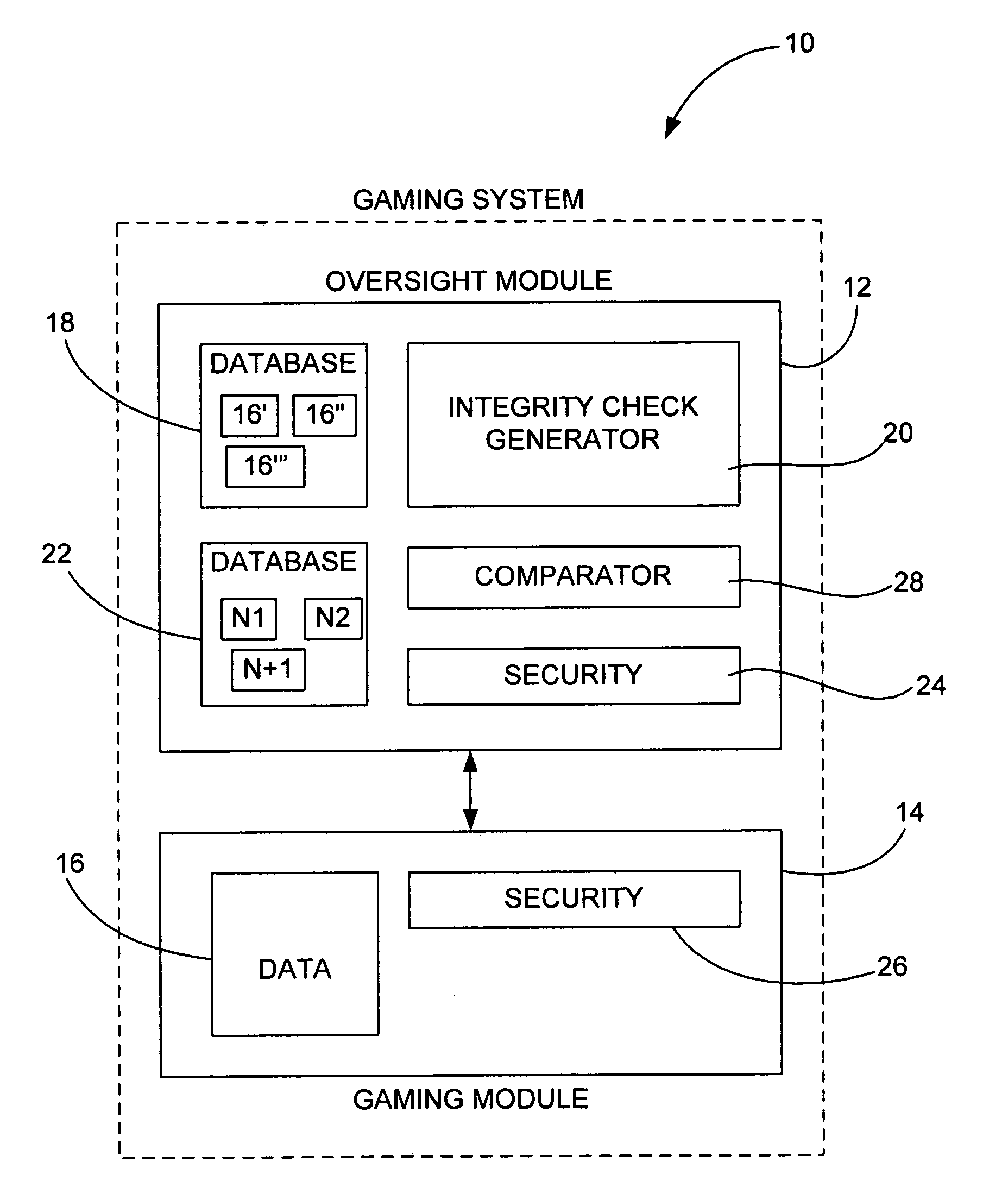
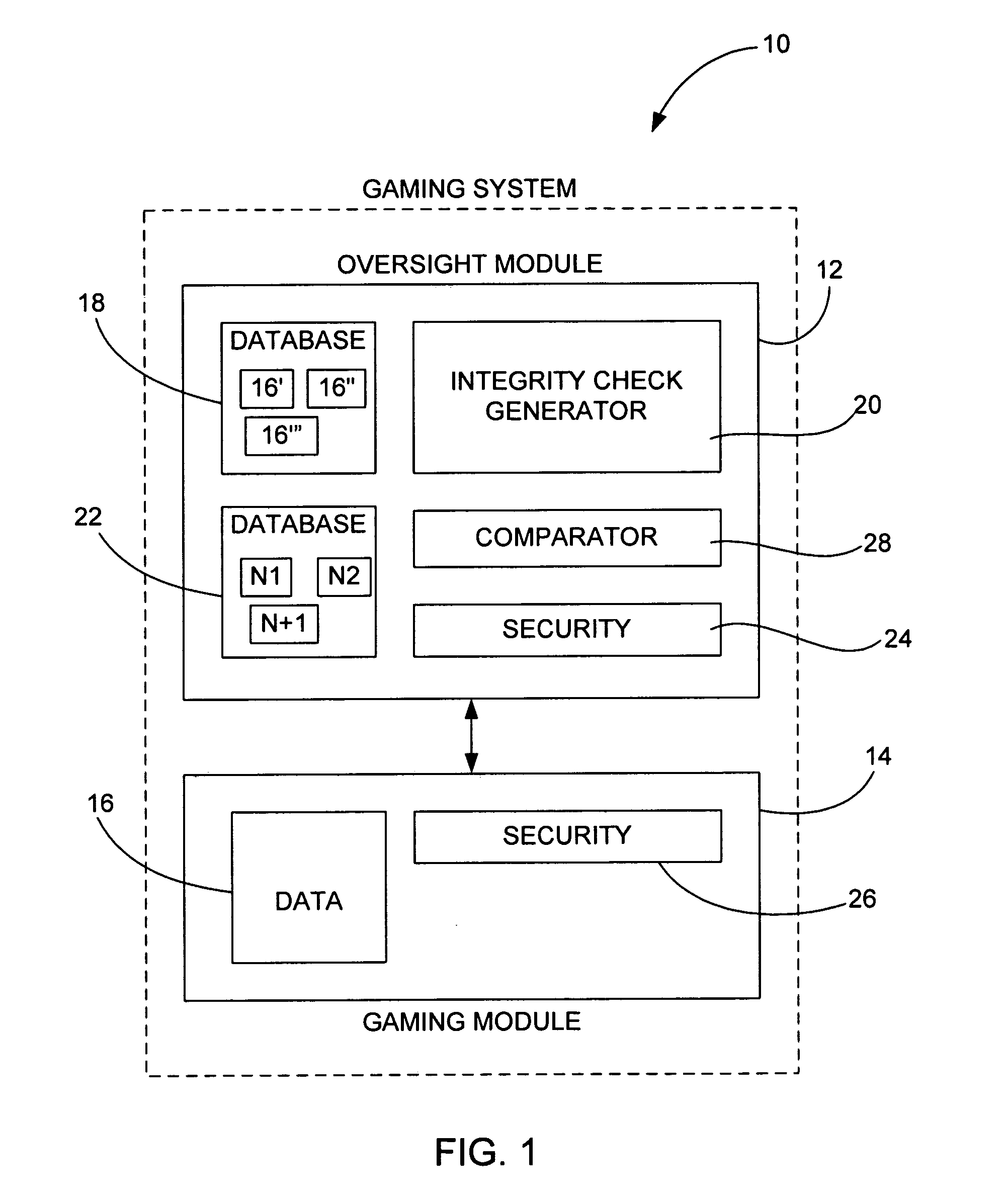
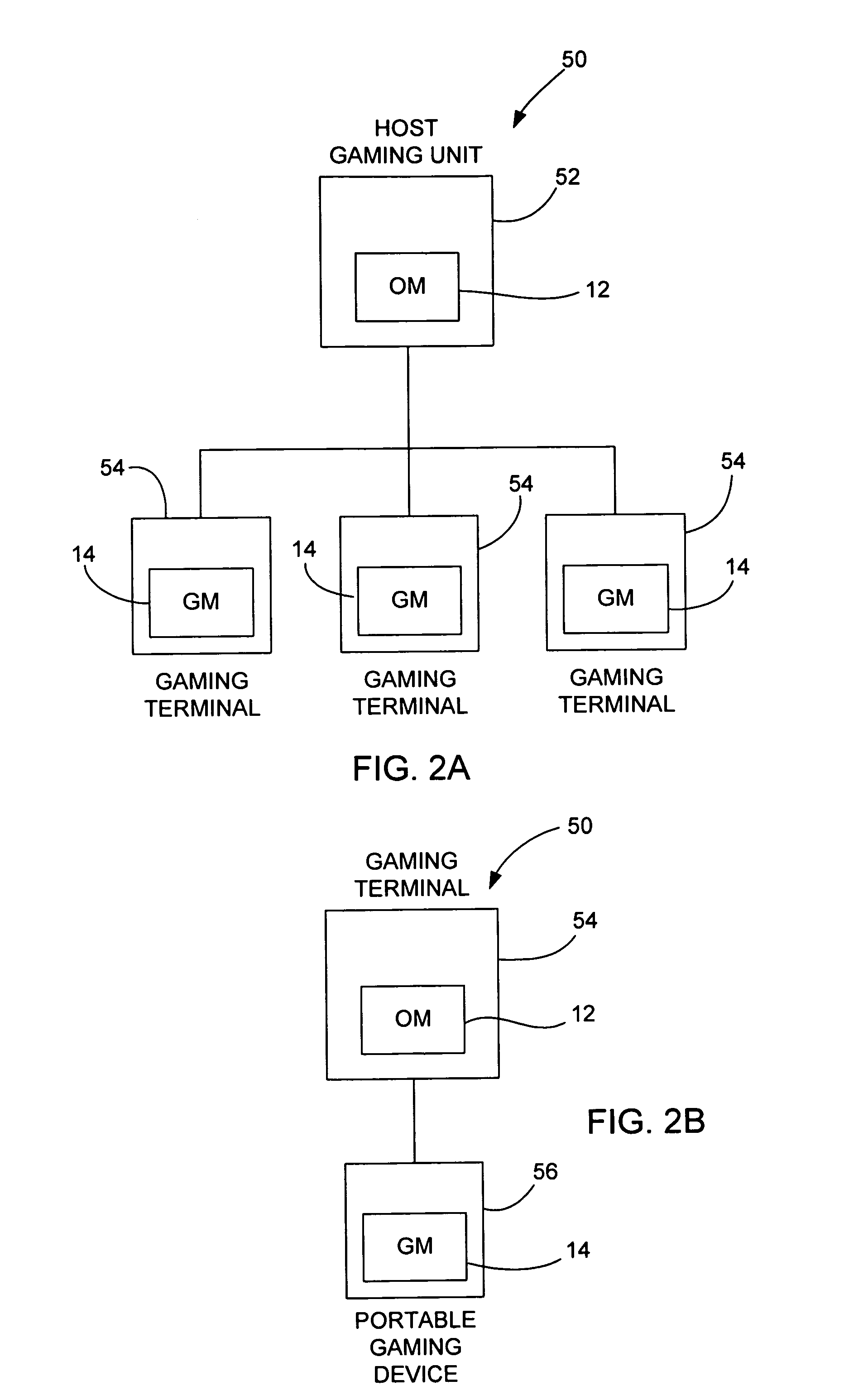
Method of randomly and dynamically checking configuration integrity of a gaming system
InactiveUS8117461B2Key distribution for secure communicationPublic key for secure communicationComputer hardwareSystem configuration
In a gaming environment, a method of periodically downloading dynamically generated executable modules at random intervals that perform system configuration integrity checks in a secure and verifiable manner is disclosed. The dynamically generated executable modules are created on a server machine and are themselves signed using industry standard PKI techniques, and contain randomly chosen subset from a repertoire of proven hashing and encryption algorithms that are executed on the system to be checked to create a unique signature of the state of that system. The dynamically generated executable module returns the signature to the server machine from which it was downloaded and deletes itself from the system being checked. The next time such an executable module is downloaded, it will contain a different randomly chosen subset of hashing and encryption algorithms. The server that is performing the system configuration integrity check maintains a database of expected system configurations and performs the same subset of hashing and encryption algorithms as contained in the dynamically generated executable module. The result returned by the downloaded executable module is compared to that computed locally, and an error condition is raised if they do not match.
Owner:IGT
Method of randomly and dynamically checking configuration integrity of a gaming system
InactiveUS20080076547A1Key distribution for secure communicationPublic key for secure communicationComputer hardwareSystem configuration
In a gaming environment, a method of periodically downloading dynamically generated executable modules at random intervals that perform system configuration integrity checks in a secure and verifiable manner is disclosed. The dynamically generated executable modules are created on a server machine and are themselves signed using industry standard PKI techniques, and contain randomly chosen subset from a repertoire of proven hashing and encryption algorithms that are executed on the system to be checked to create a unique signature of the state of that system. The dynamically generated executable module returns the signature to the server machine from which it was downloaded and deletes itself from the system being checked. The next time such an executable module is downloaded, it will contain a different randomly chosen subset of hashing and encryption algorithms. The server that is performing the system configuration integrity check maintains a database of expected system configurations and performs the same subset of hashing and encryption algorithms as contained in the dynamically generated executable module. The result returned by the downloaded executable module is compared to that computed locally, and an error condition is raised if they do not match.
Owner:IGT
Power transmitting apparatus, power receiving apparatus, and power transmitting method
InactiveCN103348563ACircuit authenticationNear-field transmissionElectricityElectric power transmission
Provided is a power transmitting apparatus, which can start power transmission even in the cases where there is not even residual power with which a power receiving apparatus requests power transmission, in a wireless power transmission system, in which a plurality of power transmitting apparatuses and a plurality of power receiving apparatuses are mainly using a same frequency as a power transmission frequency. A power transmitting apparatus (300) has sub-power transmission mode, and main power transmission mode for transmitting power larger than that transmitted in the sub-power transmission mode. A power transmitting unit (310) transmits power in a wireless manner. A power transmission control unit (320) controls, in sub-power transmission mode, power to be transmitted by means of the power transmitting unit (310) and transmission timing of the power transmission such that at least power that the receiving apparatus needs to transmit power request notification is transmitted at random intervals. A power transmission control unit (320) performs switching to the main power transmission mode, in the cases where a communication unit (350) acquired the power request notification transmitted from the power receiving apparatus.
Owner:PANASONIC CORP
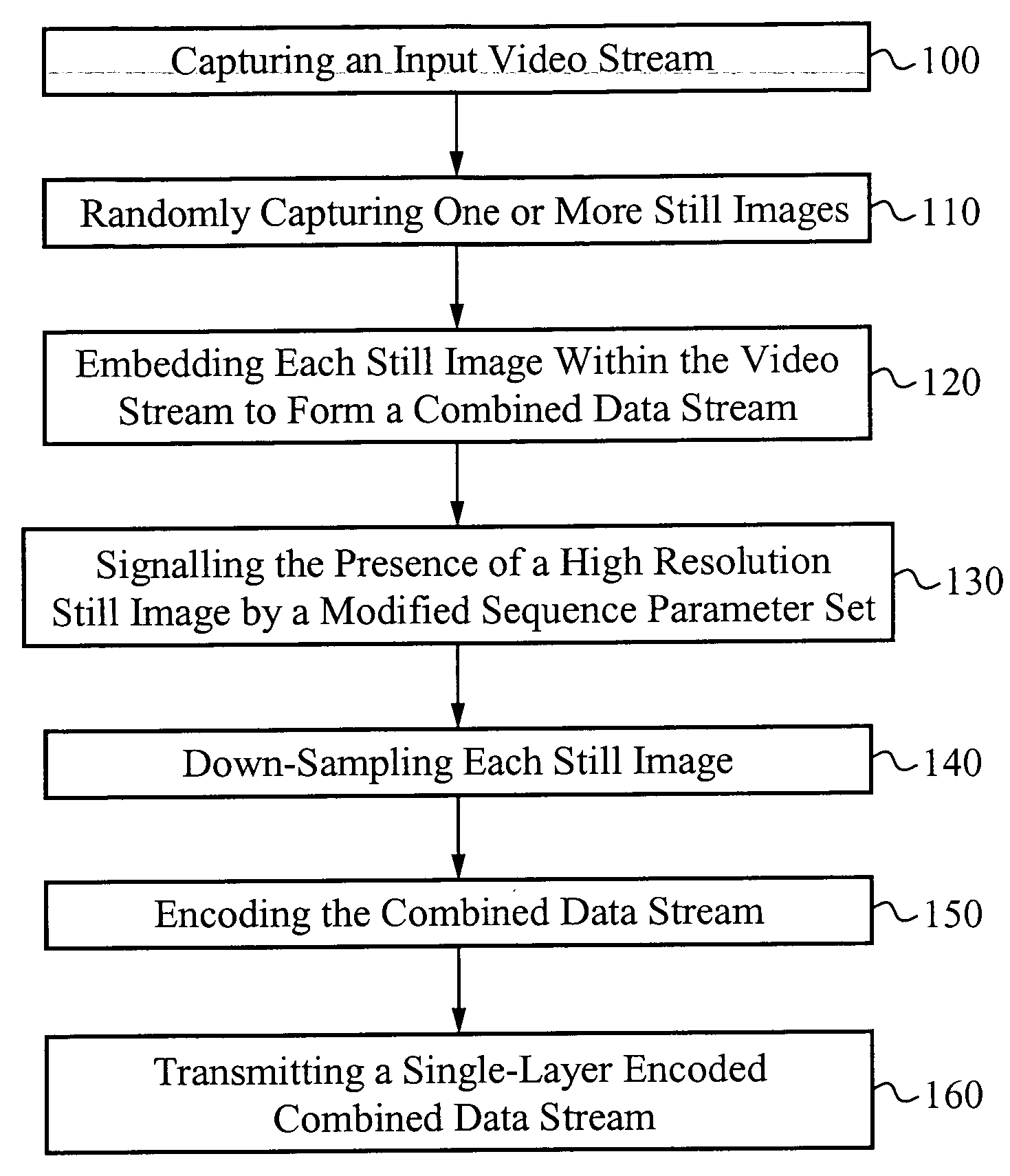
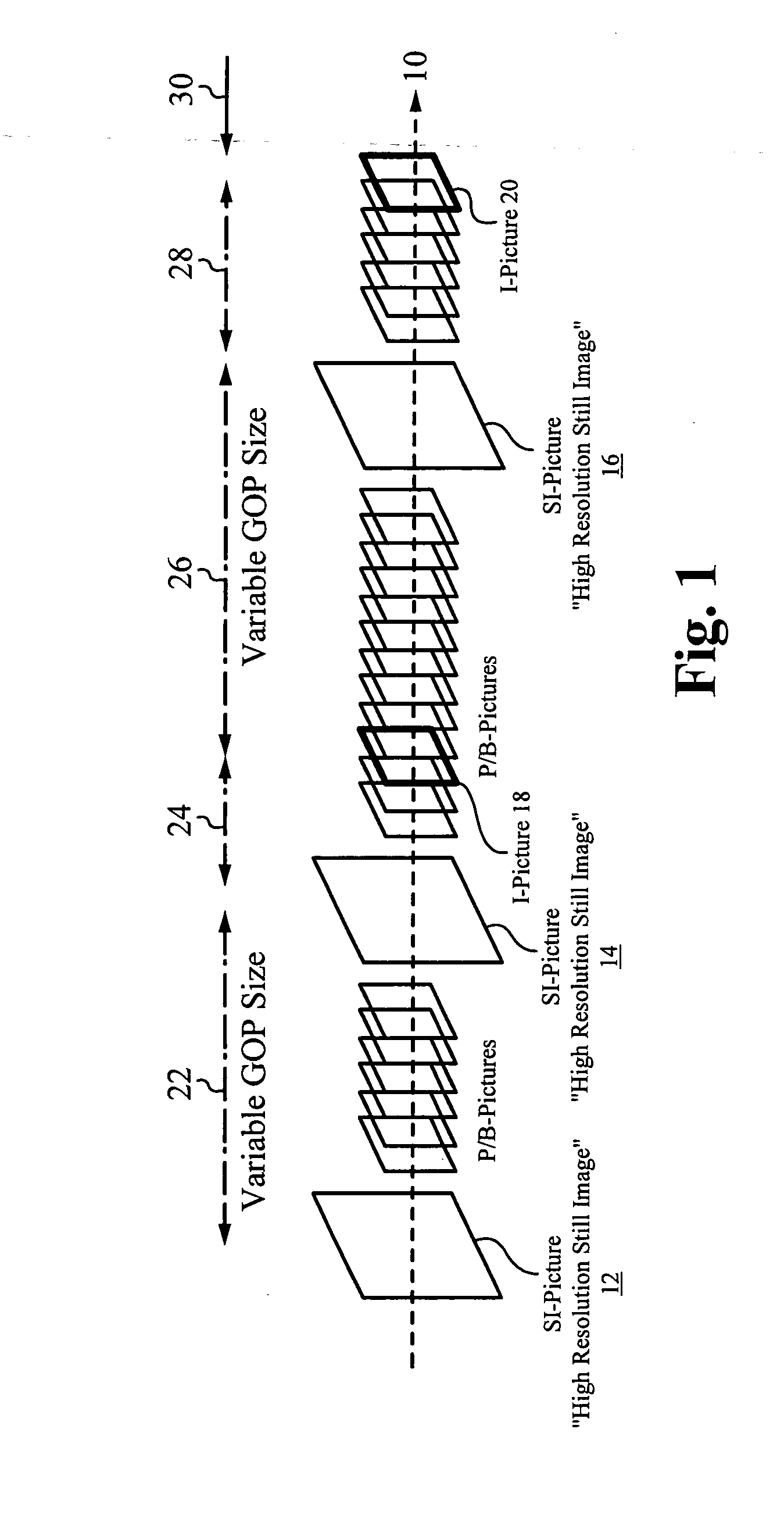
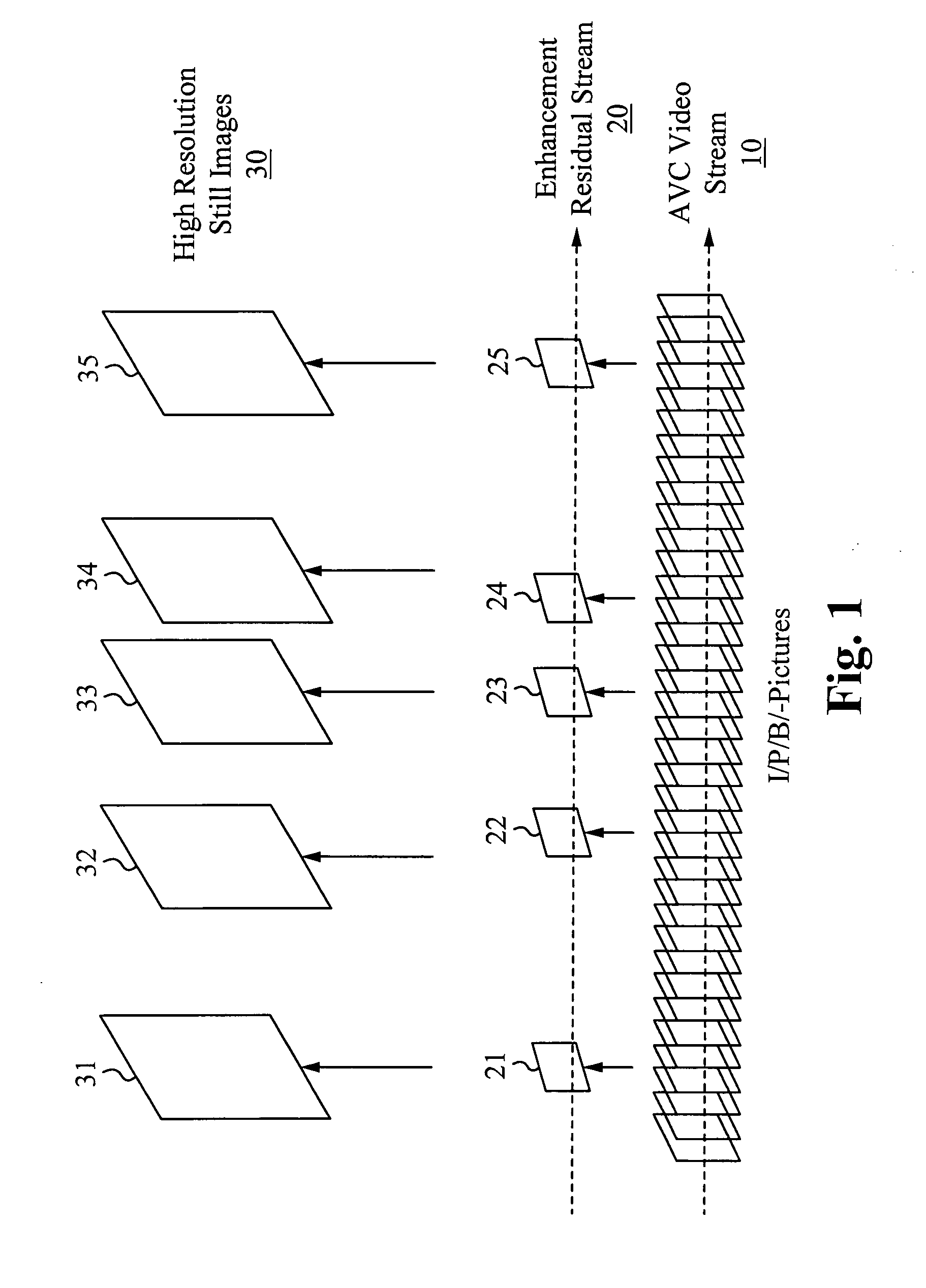
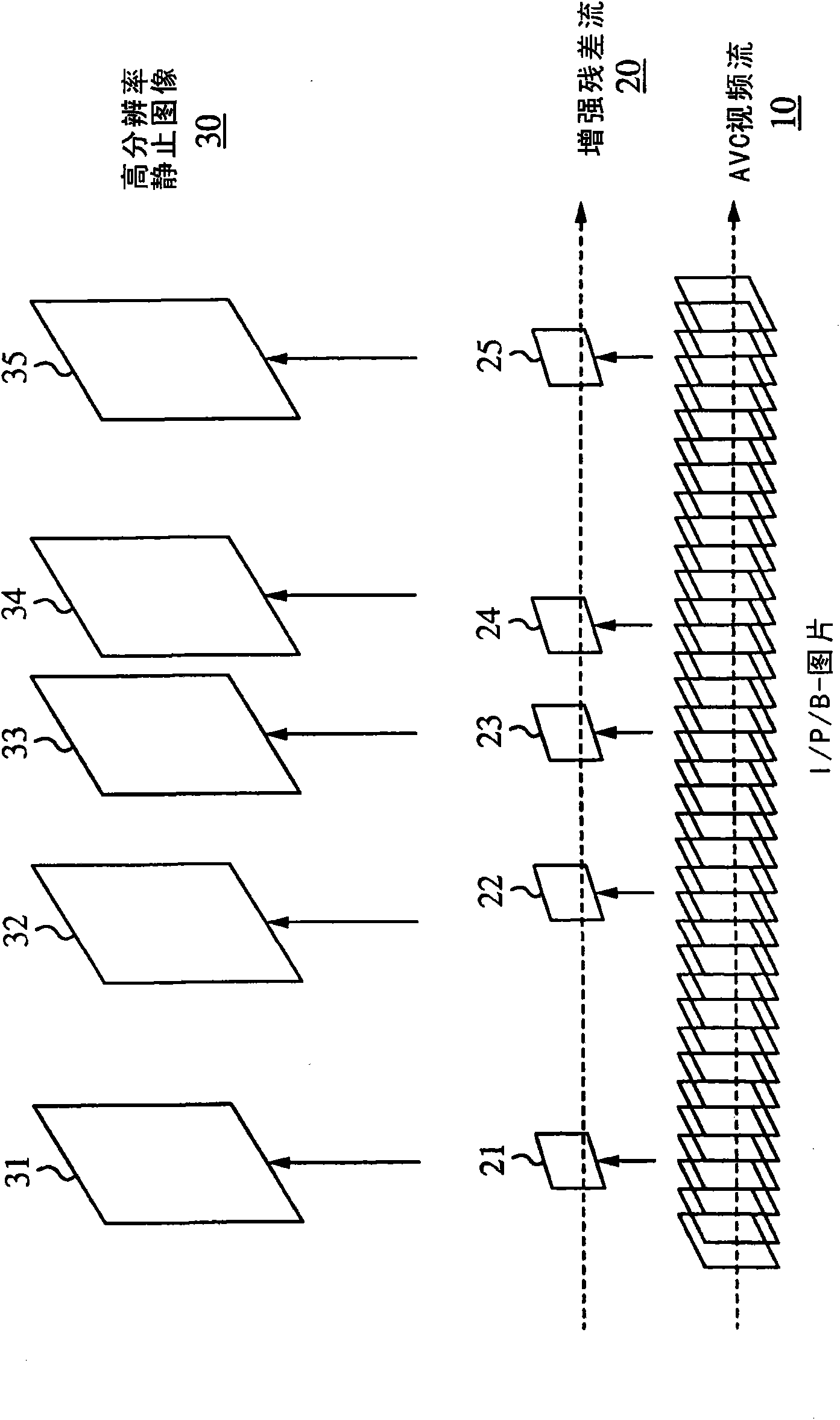
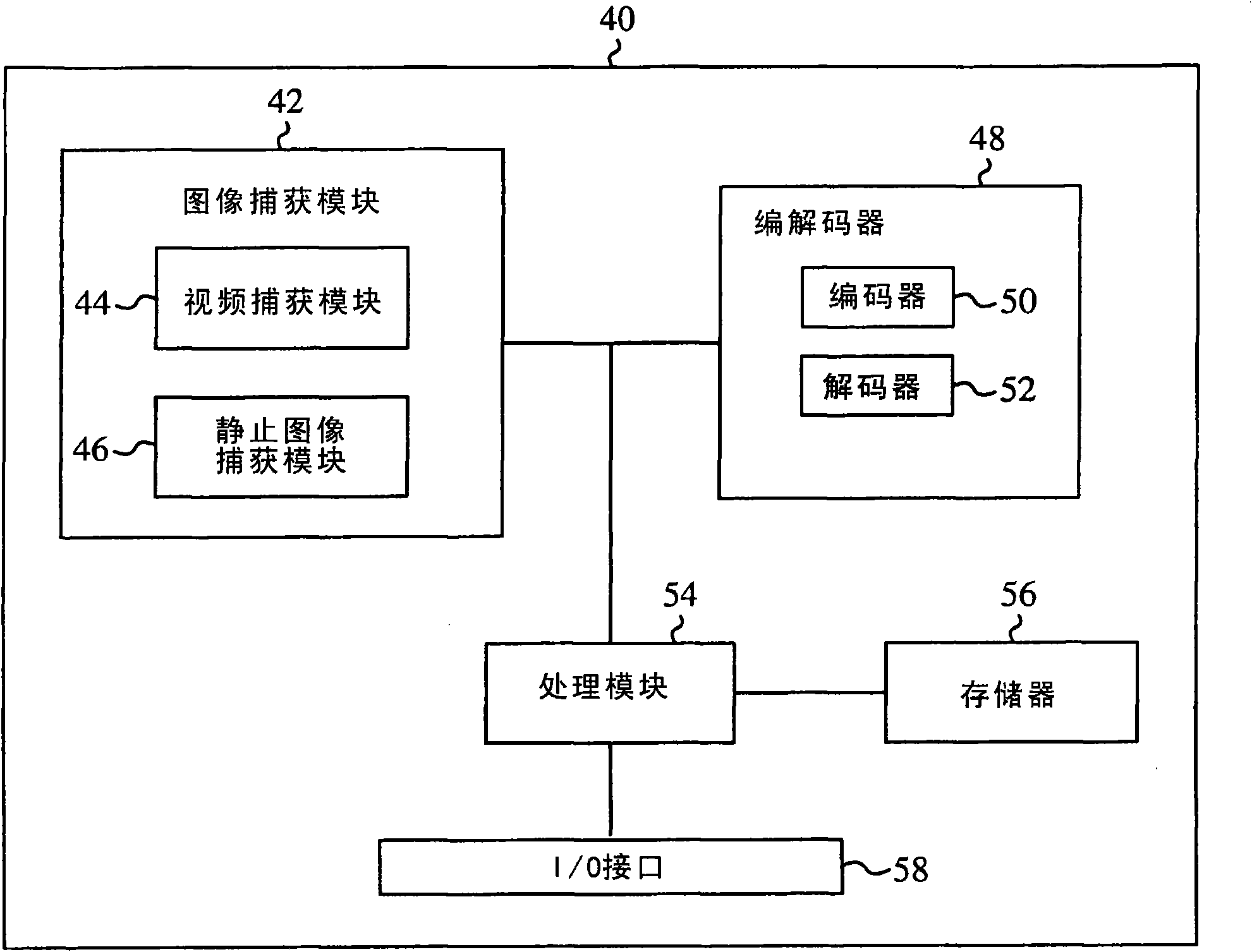
Extension to the AVC standard to support the encoding and storage of high resolution digital still pictures in series with video
ActiveUS20090141810A1High resolutionColor television with pulse code modulationColor television with bandwidth reductionImage resolutionComputer graphics (images)
A codec configured to operate in a sequential mode extends the current AVC standard in order to provide support for coding high resolution still image pictures within the AVC coding of a lower resolution video. The sequential mode codec is configured according to the modified AVC standard. The codec is capable of capturing an AVC video stream while concurrently capturing high resolution still images at random intervals relative to the video stream. Each captured high resolution still image is embedded within the video stream. The video stream including the embedded high resolution still images is encoded as a single layer bit stream. Each embedded high resolution still image signals or forces the start of a new GOP in the coded video sequence. The AVC standard is extended to include new syntax for the sequence parameter sets. In one embodiment, a modified sequence parameter set defines a new profile that signals the presence of a high resolution still image in sequence with AVC video.
Owner:SONY CORP +1
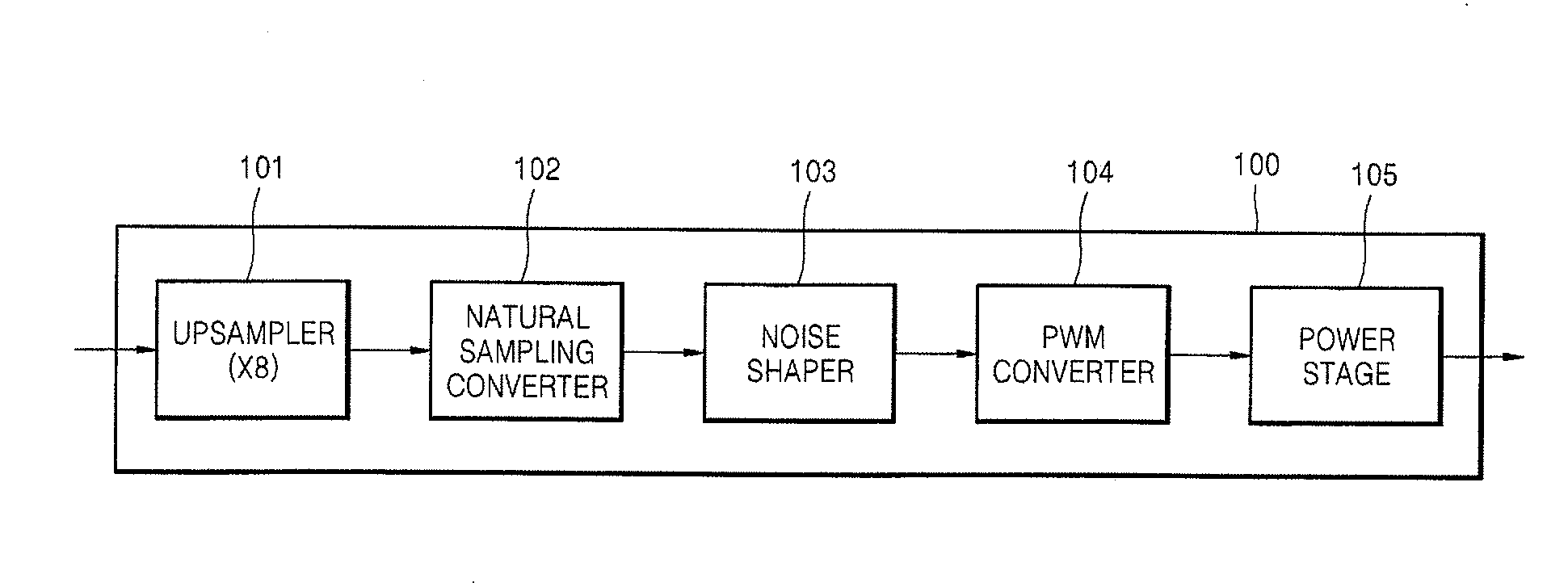
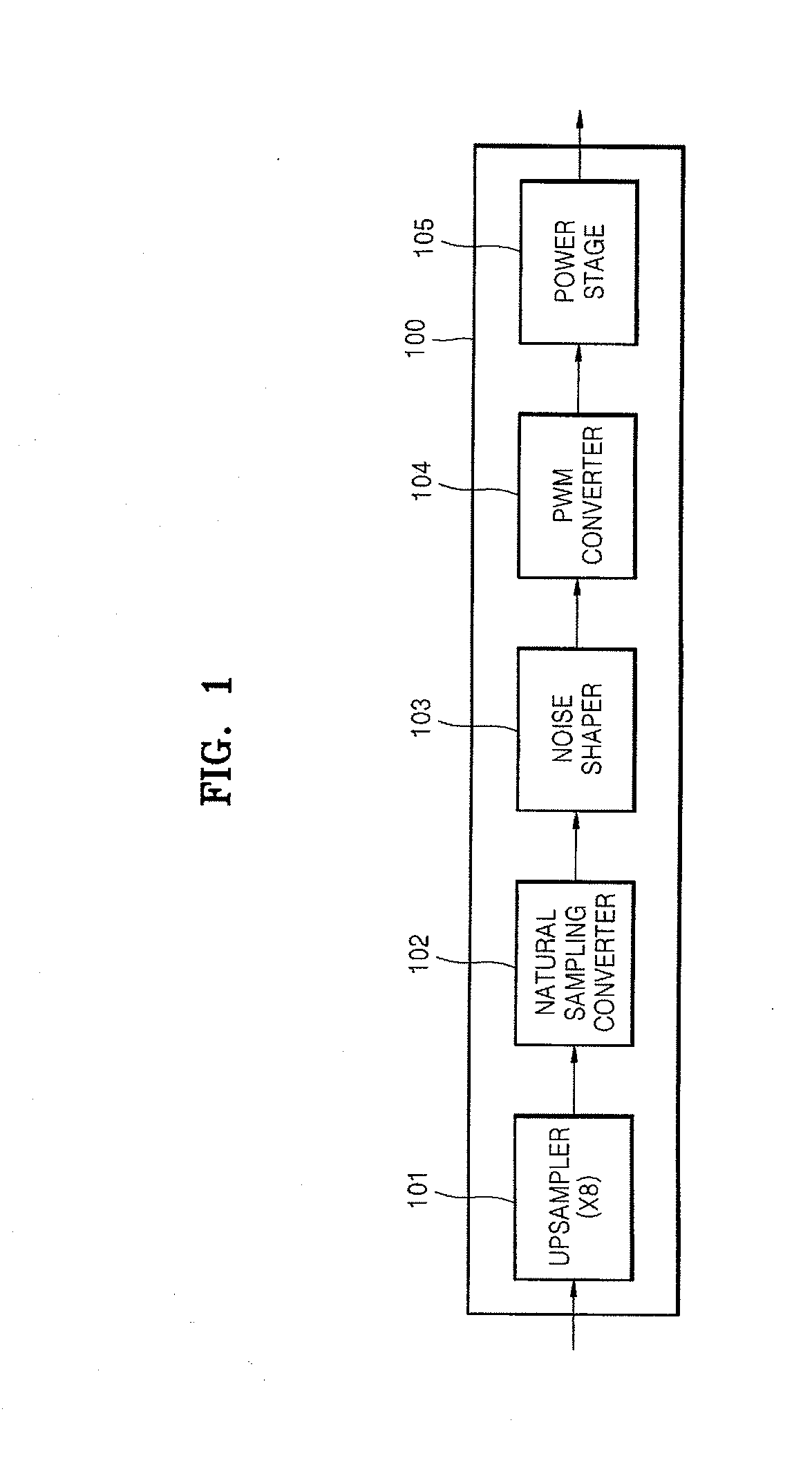
Method of and apparatus to generate pulse width modulated signal from sampled digital signal by chaotic modulation
InactiveUS20070291833A1Reduce high-frequency harmonicDecreasing electromagnetic compatibility issueAnalogue conversionAmplifier with semiconductor-devices/discharge-tubesAudio power amplifierElectromagnetic interference
A method and apparatus to generate a pulse width modulated signal from a sampled digital signal by chaotic modulation. The method includes generating predetermined chaotic intervals having random interval values using a chaotic interval generator, and generating the pulse width modulated signal from a reference signal and the sampled digital signal during each of the chaotic intervals. Thus, electromagnetic interference (EMI) that affects an audio amplifier can be remarkably reduced.
Owner:SAMSUNG ELECTRONICS CO LTD
Wearable Blood Alcohol Measuring Device
A system and method of measuring and analyzing a user's blood alcohol content are provided, the system comprising a wearable alcohol sensor that measures a user's blood alcohol content continuously or at random intervals, and a mobile device that receives blood alcohol content data from the wearable alcohol sensor, said mobile device being able to store and analyze the blood alcohol content data, to warn the user or others when the user's blood alcohol content is too high or when the user is unable to drive legally, and to use the stored data and the analysis results to predict the user's future blood alcohol content.
Owner:ANTIMATTER RES
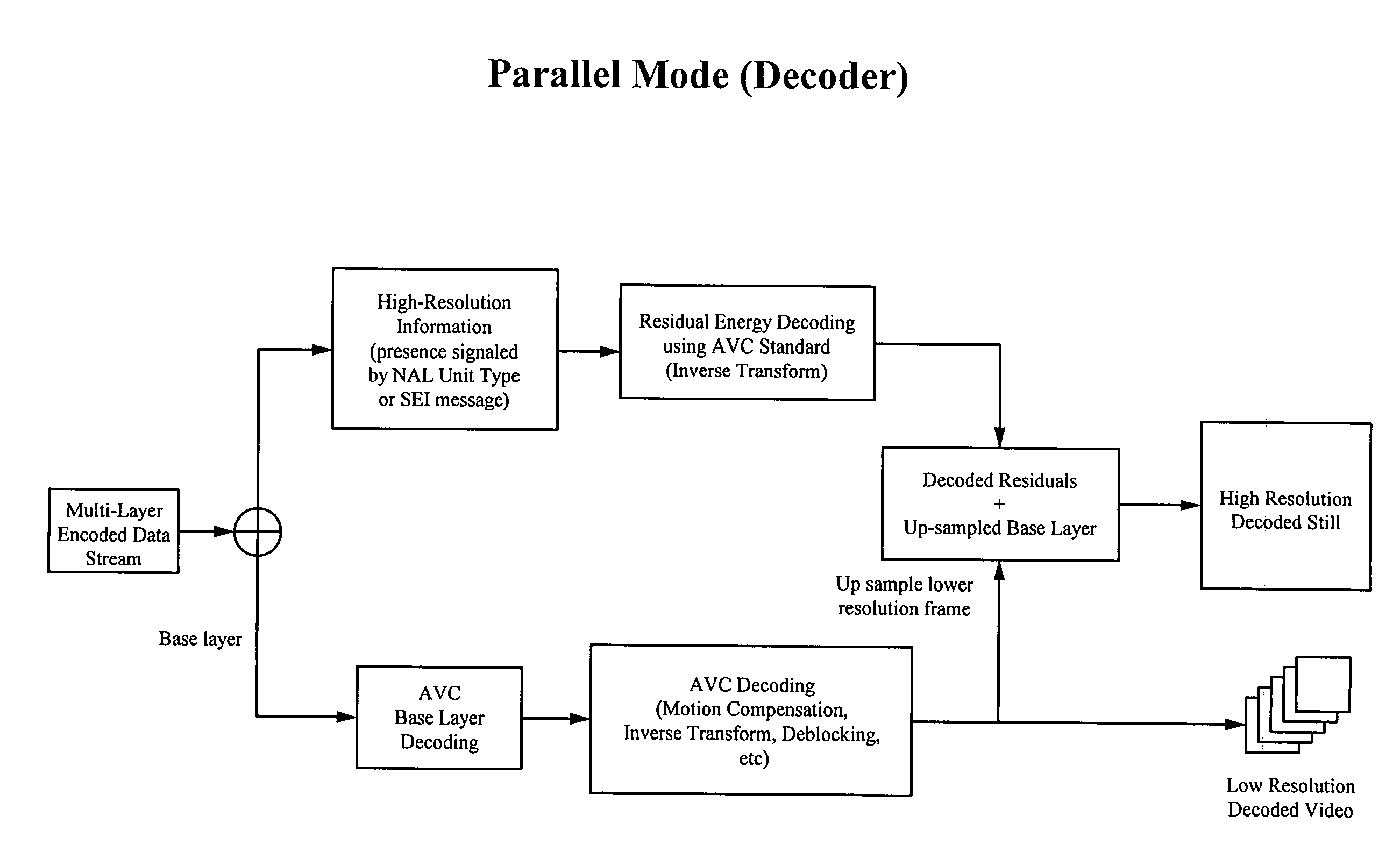
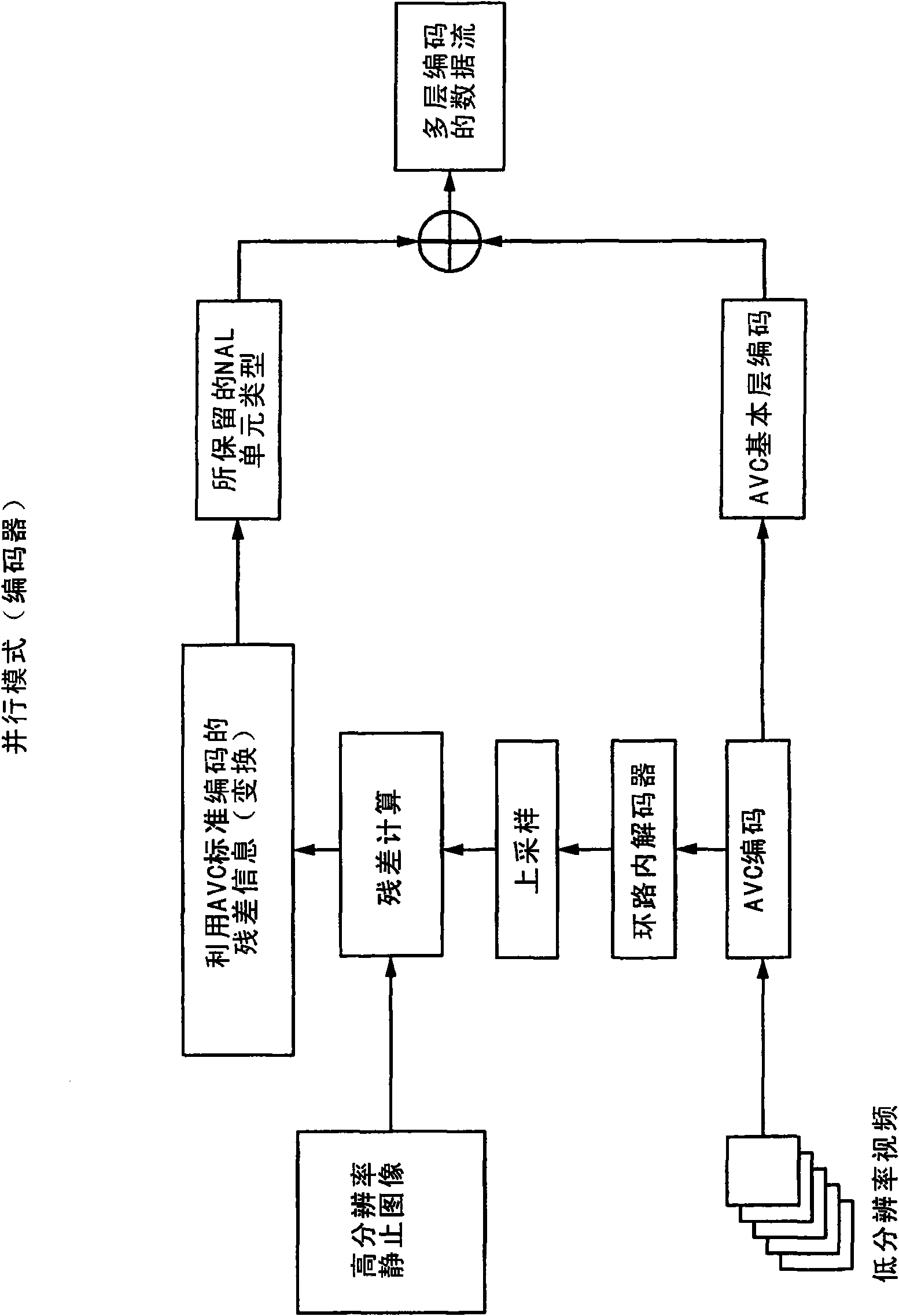
Extension to the AVC standard to support the encoding and storage of high resolution digital still pictures in parallel with video
InactiveUS20090141809A1Reduce resolutionHigh resolutionColor television with pulse code modulationColor television with bandwidth reductionImage resolutionComputer graphics (images)
A codec configured to operate in a parallel mode extends the current AVC standard in order to provide support for coding and storage of high resolution still image pictures in parallel with the AVC coding of a lower resolution video. The parallel mode codec is configured according to the modified AVC standard and is capable of capturing an AVC video stream while concurrently capturing high resolution still images at random intervals of the video stream. Residual information stored as an enhancement layer, is used to generate one or more high resolution still images pictures using the up-sampled decoded lower resolution video at the decoder side. A base layer carries lower resolution video. The enhancement layer and the base layer are transmitted in parallel, as a multi-layer stream, from an encoder on the transmission side to a decoder at the receiving side. To carry enhancement information, the AVC standard is extended to include data field(s) for SEI Message Definitions, sequence parameter sets, and a new NAL Unit.
Owner:SONY CORP +1
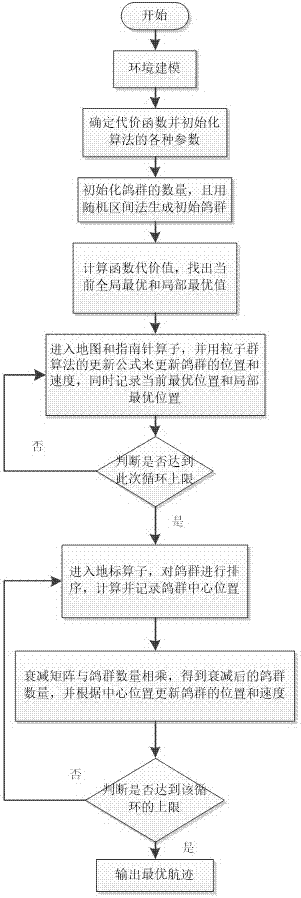
Nonlinear path planning method based on hybrid pigeon population algorithm
InactiveCN106979784ANavigational calculation instrumentsArtificial lifePlanning approachParticle swarm algorithm
The invention discloses a nonlinear path planning method based on a hybrid pigeon population algorithm and belongs to the technical field of a single unmanned aerial vehicle. The method comprises determining a flight range and obstacles, initializing various parameters, producing a population initial state value through a random interval method, updating a population position and rate through an ego and social learning factor formula which has an inertia matrix and produces cosine transformation along with the inertia matrix according to the ideology of combination of particle swarm optimization algorithm self-learning and social learning in a map and a compass operator, after cycling upper limit, feeding the data into a landmark operator, sorting the pigeon populations according to adaptability values, recording a center position, calculating the iterative population quantity through a damping matrix producing cosine transformation, updating a position and a rate, and outputting the optimal path. The method improves the accuracy of the algorithm, can produce the optimal solution or the second-best solution very close to the optimal solution and can improve stability of the algorithm and the rate of the path planning.
Owner:SICHUAN UNIV
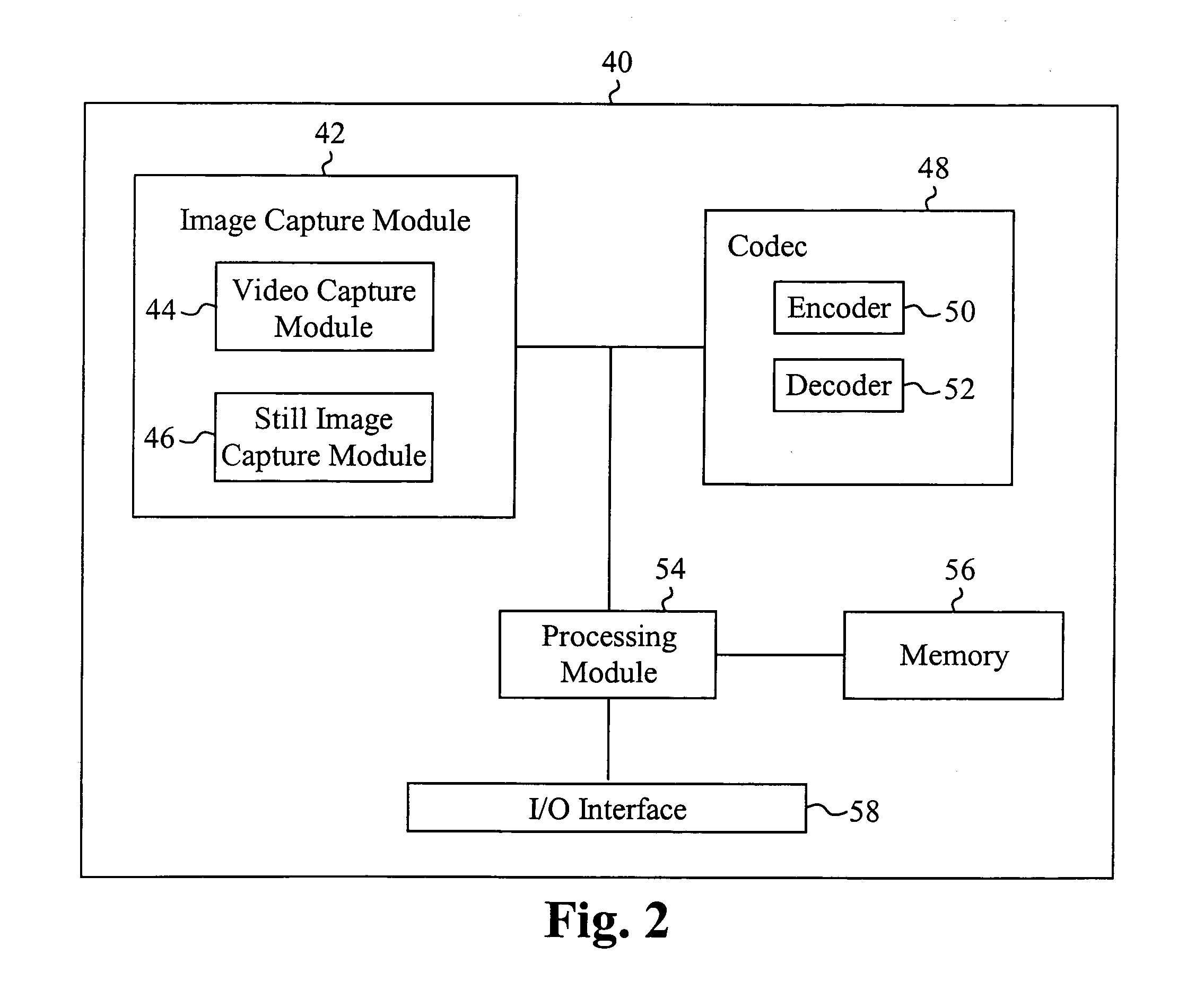
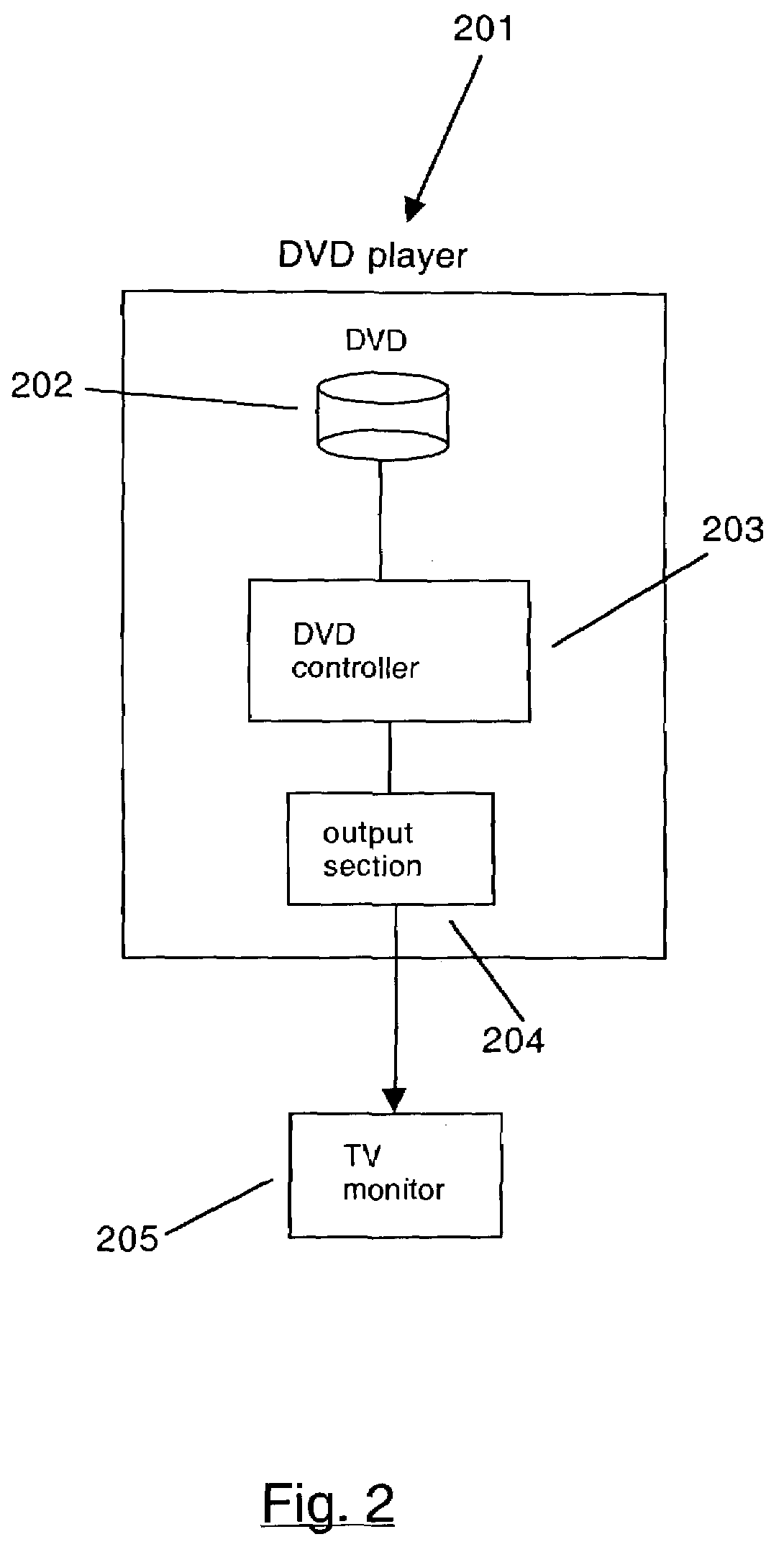
Method and apparatus for creating an expanded functionality digital video disc
ActiveUS7200321B2Great DVD program material informationFunction increaseTelevision system detailsFlat record carrier combinationsDigital videoGroup of pictures
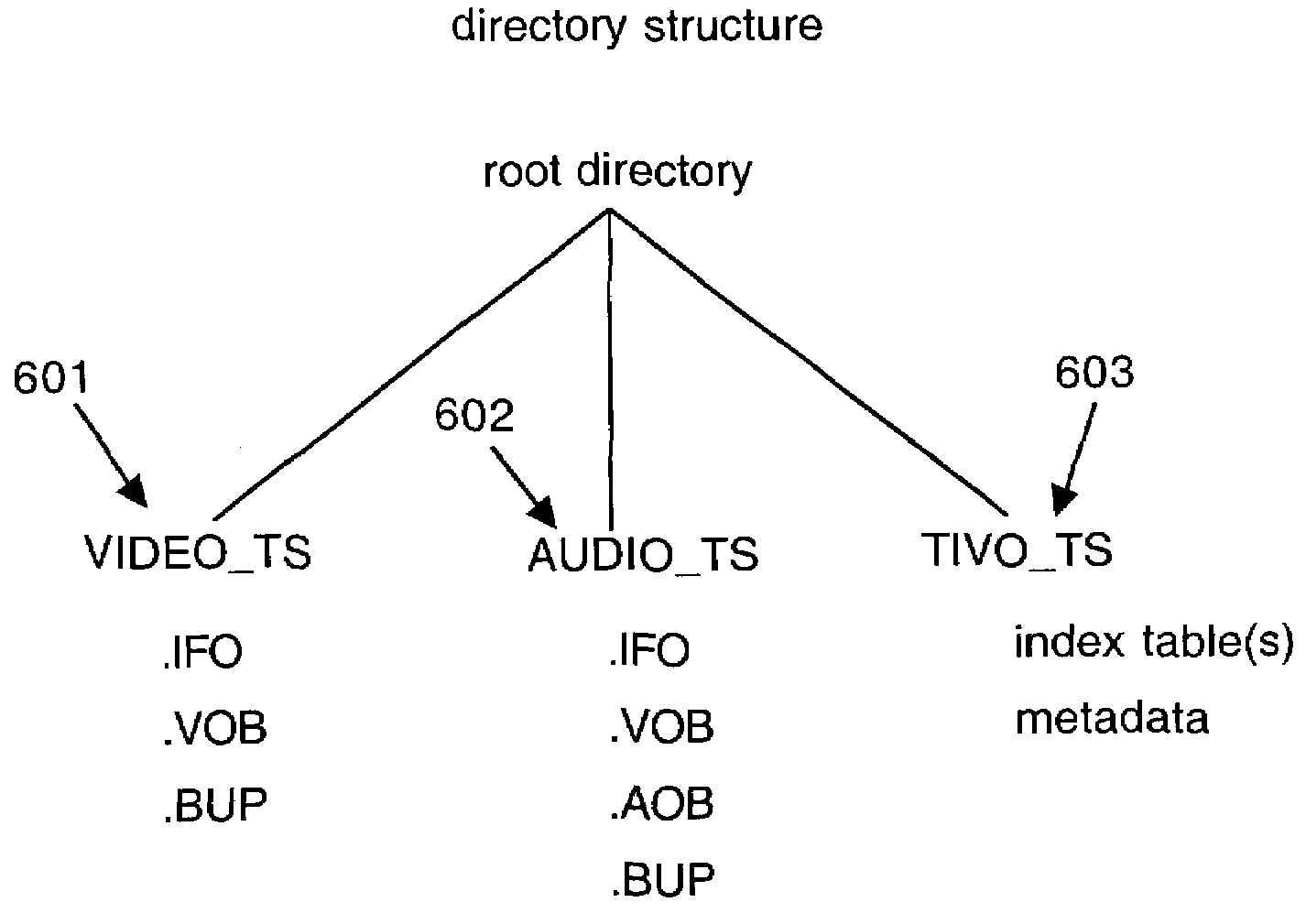
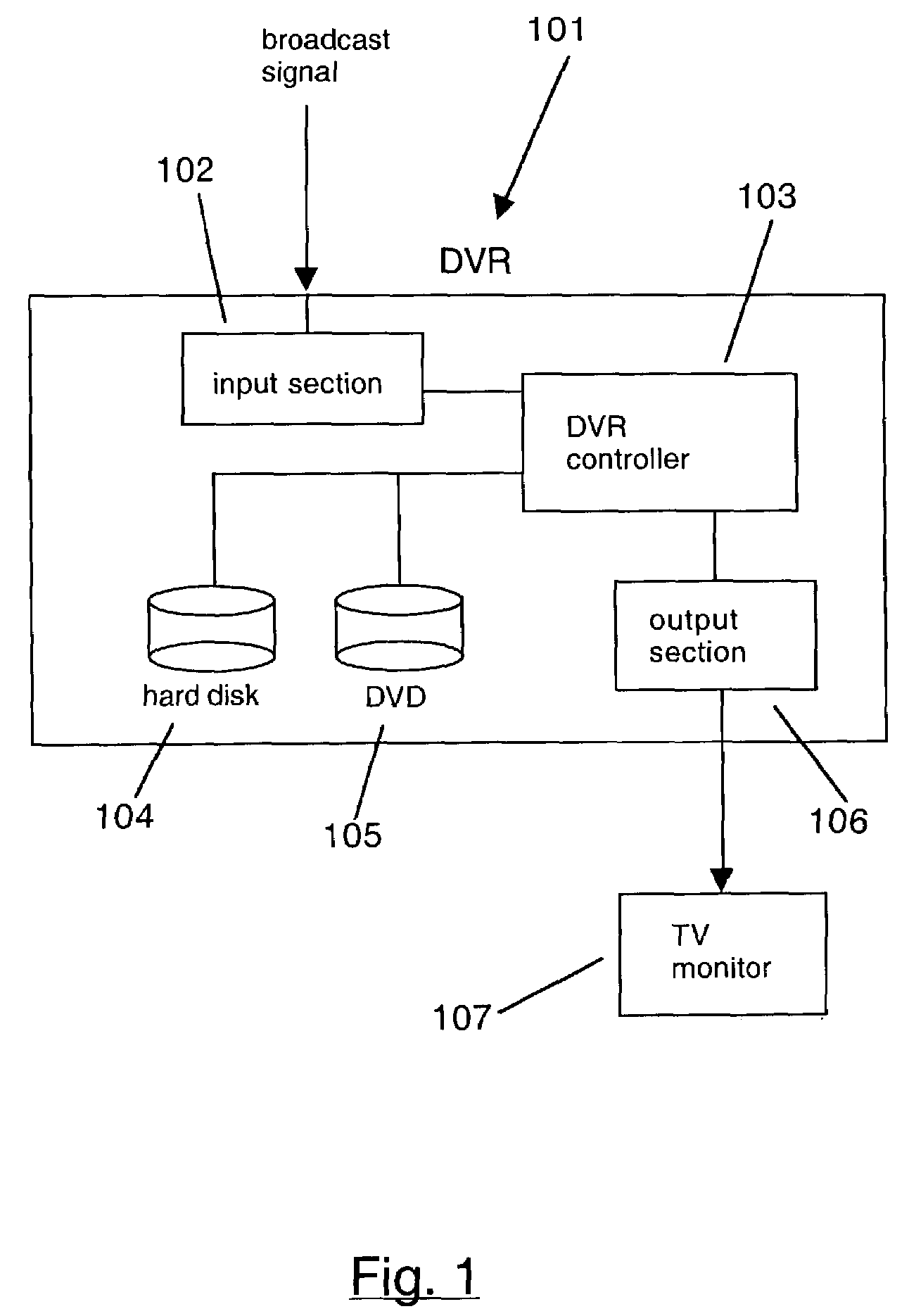
A method and apparatus for creating an expanded functionality digital video disc (DVD) creates an enhanced DVD with index tables for the program streams on the DVD. Index tables point to key locations in an MPEG program stream with each entry in the index table set to point to a group of pictures (GOP) header in the MPEG stream. The invention can select GOP headers at predefined intervals, semi-random intervals, or at key locations. The invention creates an index table either during storage of a program stream on a hard disk, during a scan of program material already stored on a local hard disk, or while program material is being read out of the hard disk and written to a DVD. The invention adds a new directory to the DVD structure and writes the index table(s) for the stream(s) into the directory. The new directory and its content are only recognized by invention-enabled DVD players and DVRs. Each media stream file in the VIDEO_TS and AUDIO_TS directories has a corresponding index table file in the new directory. Alternatively, the index table files could be stored in the respective VIDEO_TS and AUDIO_TS directories. When an enhanced DVD created by the invention is inserted into a invention-aware DVR or DVD player, the index table files on the DVD are utilized to enable smooth special effects functionality.
Owner:ROVI PROD CORP
System and method of optical data communication with multiple simultaneous emitters and receivers
ActiveUS7009501B2Reliable wireless communicationHigh redundancy of emitted dataMultiplex communicationAnti-collision systemsStatistical analysisNetwork packet
The system and method of the present invention optically transmits redundant packets of data using infrared signals at pseudo-random intervals to allow a receiver to distinguish between multiple simultaneous sources. The emitters repeatedly transmit a short packet at randomized intervals much shorter than the frame rate. Statistical analysis shows that the probability of collision of the desired packet with a packet from some other source is sufficiently low such that timely reception of at least one uncorrupted packet in the required time frame is assured.
Owner:DISNEY ENTERPRISES INC
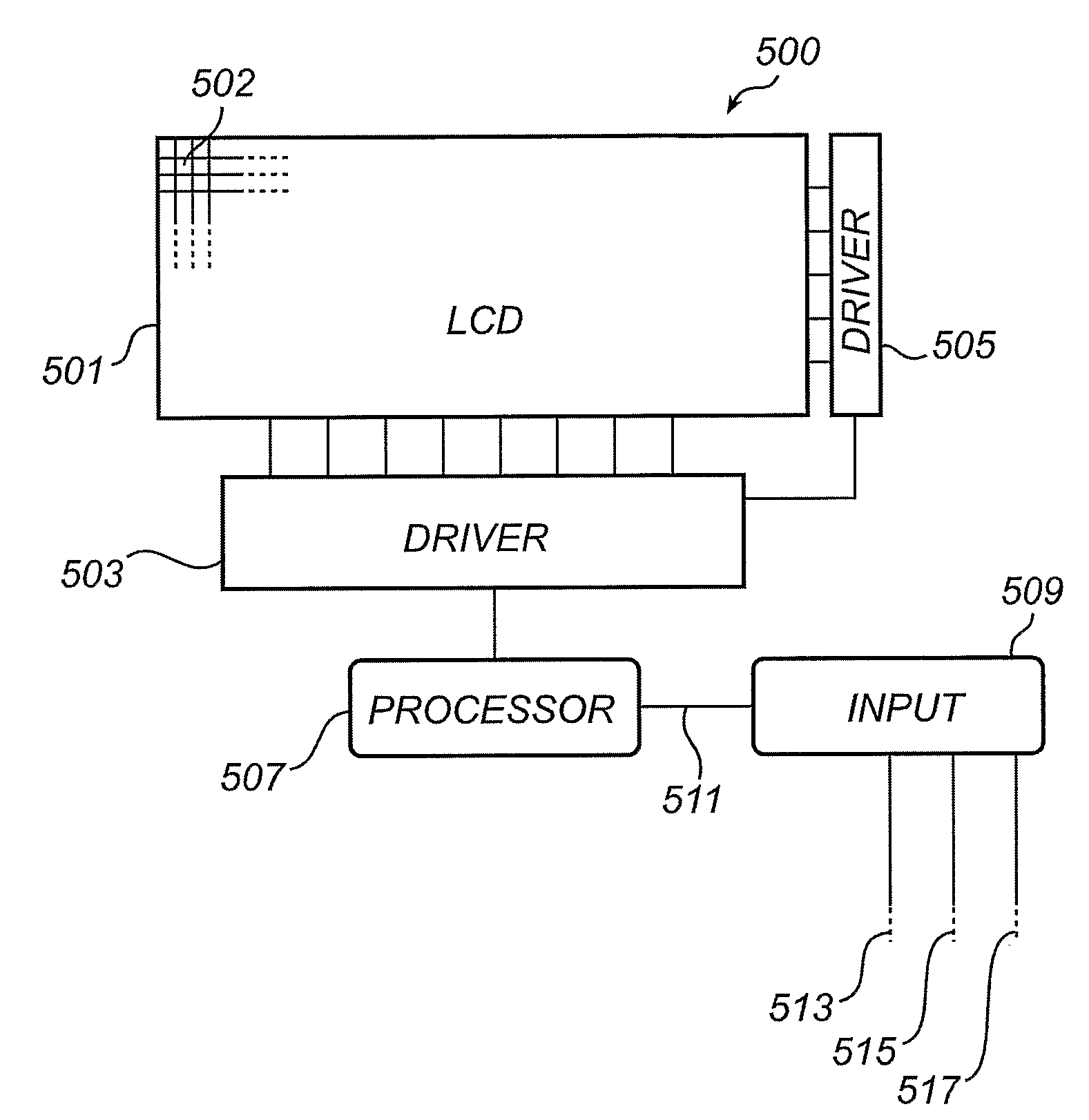
Dispaly Pixel Inversion Scheme
InactiveUS20080309656A1Facilitate data analysisOvercomes drawbackTelevision system detailsCathode-ray tube indicatorsElectrical polarityDisplay device
A display device (500) having a plurality of picture cells (502) is controlled by adding a phase change to the regular cyclic inversion scheme. Thereby, it is possible to overcome the drawbacks of DC build-up due to, e.g., de-interlaced images and images comprising rotating symbols and “ticker tape”. The control involves receiving an image signal comprising image data relating to the picture cells. A respective electric field across each picture cell is controlled, in dependence on at least the image data, according to a first polarity inversion scheme where the polarity of the electric field is such that polarity inversion occurs at regular intervals, and according to a second polarity inversion scheme concurrent with said first polarity inversion scheme, where the polarity of the electric field such that polarity inversion occurs at pseudo-random intervals.
Owner:KONINKLIJKE PHILIPS ELECTRONICS NV
An extension to the avc standard to support the encoding and storage of high resolution digital still pictures in parallel with video
InactiveCN101878649ATelevision systemsDigital video signal modificationImage resolutionComputer graphics (images)
A codec configured to operate in a parallel mode extends the current AVC standard in order to provide support for coding and storage of high resolution still image pictures in parallel with the AVC coding of a lower resolution video. The parallel mode codec is configured according to the modified AVC standard and is capable of capturing an AVC video stream while concurrently capturing high resolution still images at random intervals of the video stream. Residual information stored as an enhancement layer, is used to generate one or more high resolution still images pictures using the up-sampled decoded lower resolution video at the decoder side. A base layer carries lower resolution video. The enhancement layer and the base layer are transmitted in parallel, as a multi-layer stream, from an encoder on the transmission side to a decoder at the receiving side. To carry enhancement information, the AVC standard is extended to include data field(s) for SEI Message Definitions, sequence parameter sets, and a new NAL Unit.
Owner:SONY CORP +1
Self-attaching elastic cord
Owner:SIMON JAMES S
Automatic channel selection in a radio access network
InactiveUS20040203808A1Improve efficiencyData switching by path configurationRadio/inductive link selection arrangementsRandom intervalAccess network
Within a radio access network (111, 112) an access point (181, 182, 183 and 184) selects a channel by first randomly choosing a channel from those available for use. The Access Point then monitors the channel for a random interval to determine if the channel is presently carrying traffic. The Access Point will select the channel unless the channel is in use by another AP. If so, then the AP will select another channel and commence monitoring for a random interval in order to determine whether the channel is available. The AP will continue to choose channels until a suitable channel is found, or all available channels have been exhausted.
Owner:INTERDIGITAL CE PATENT HLDG
Order-preserving encryption method based on random interval partition
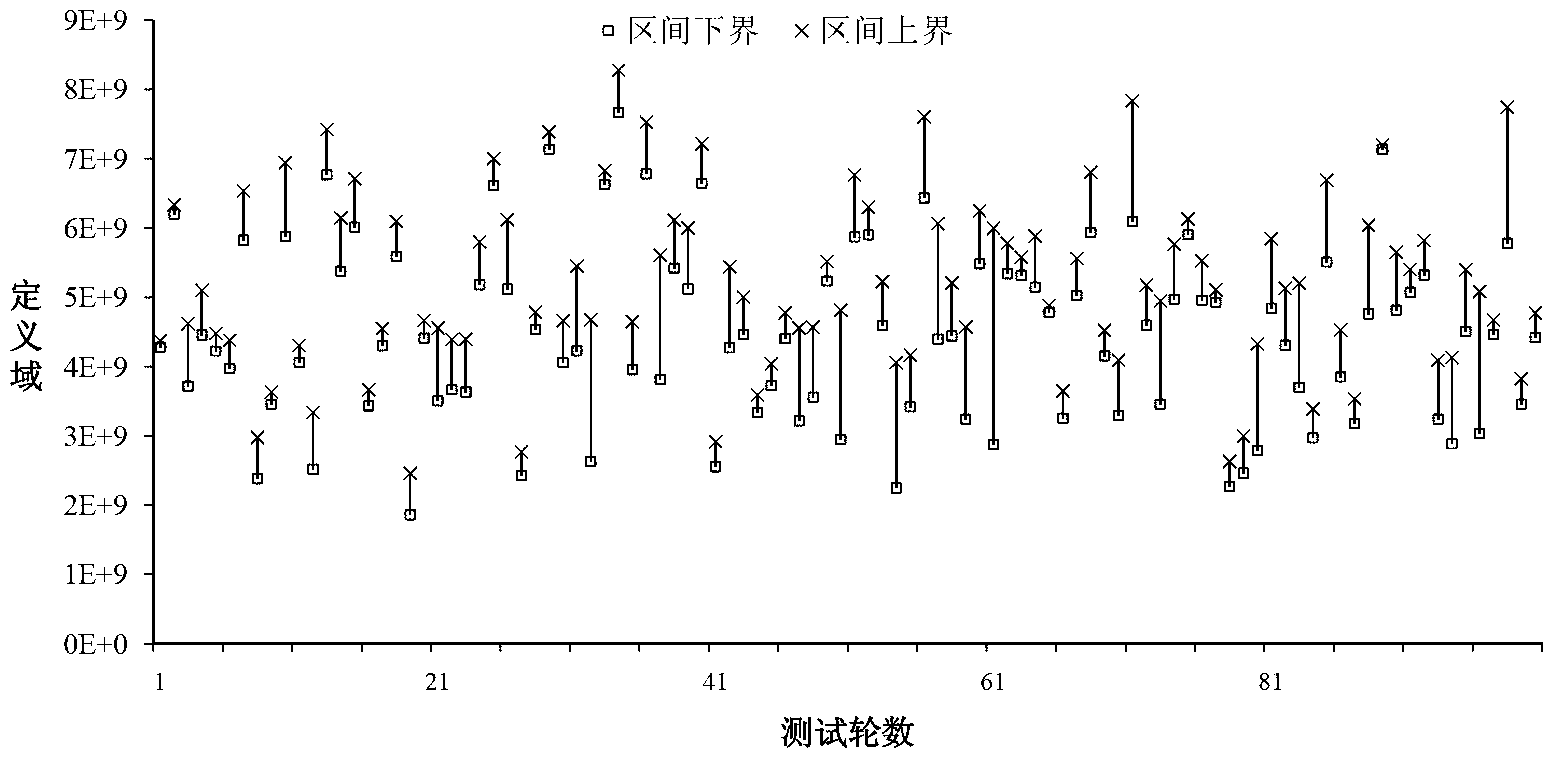
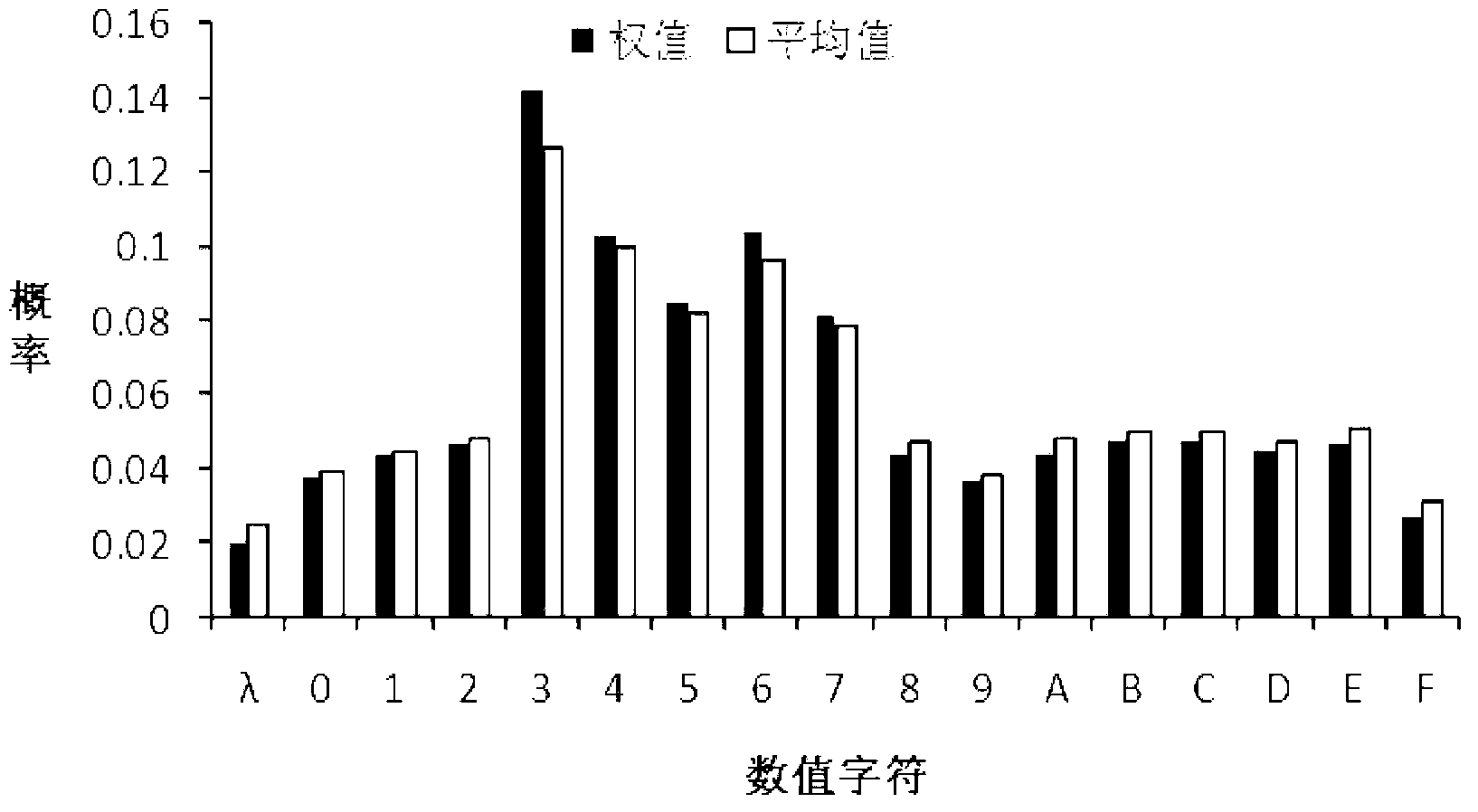
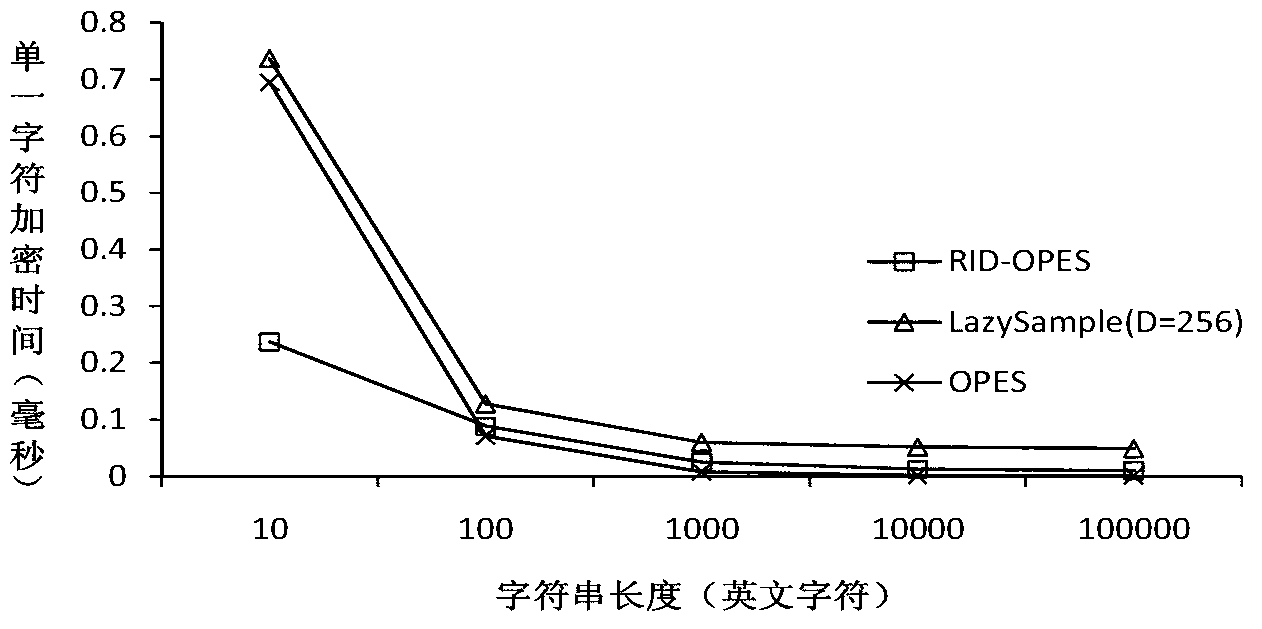
ActiveCN102843372ASolve the problem of order-preserving encryptionSolve matching problemsTransmissionCiphertextRelational calculus
The invention relates to an order-preserving encryption method based on random interval partition. The method provides a weighted random interval partition algorithm and an order-preserving random interval tree according to the fact that an existing algorithm is generated by random numbers based on interval partition, and the safe problem existing in the fact that intervals are divided in fixed mode is resolved. The order-preserving encryption method can effectively resolves the problem of order-preserving and encryption of character string data, analysis and testament show that the order-preserving encryption method has linear encryption time and decryption time and constant level ciphertext expansion rate, and can effectively resist exhaustive attack and attack based on statistic analysis. The order-preserving encryption method is specially suitable for outsourcing storage of confidential data, can effectively resolve the problem of matching, scope inquiring, relational calculus and other operations of ciphertext data.
Owner:XI AN JIAOTONG UNIV
System and Method for Compressive Sensing
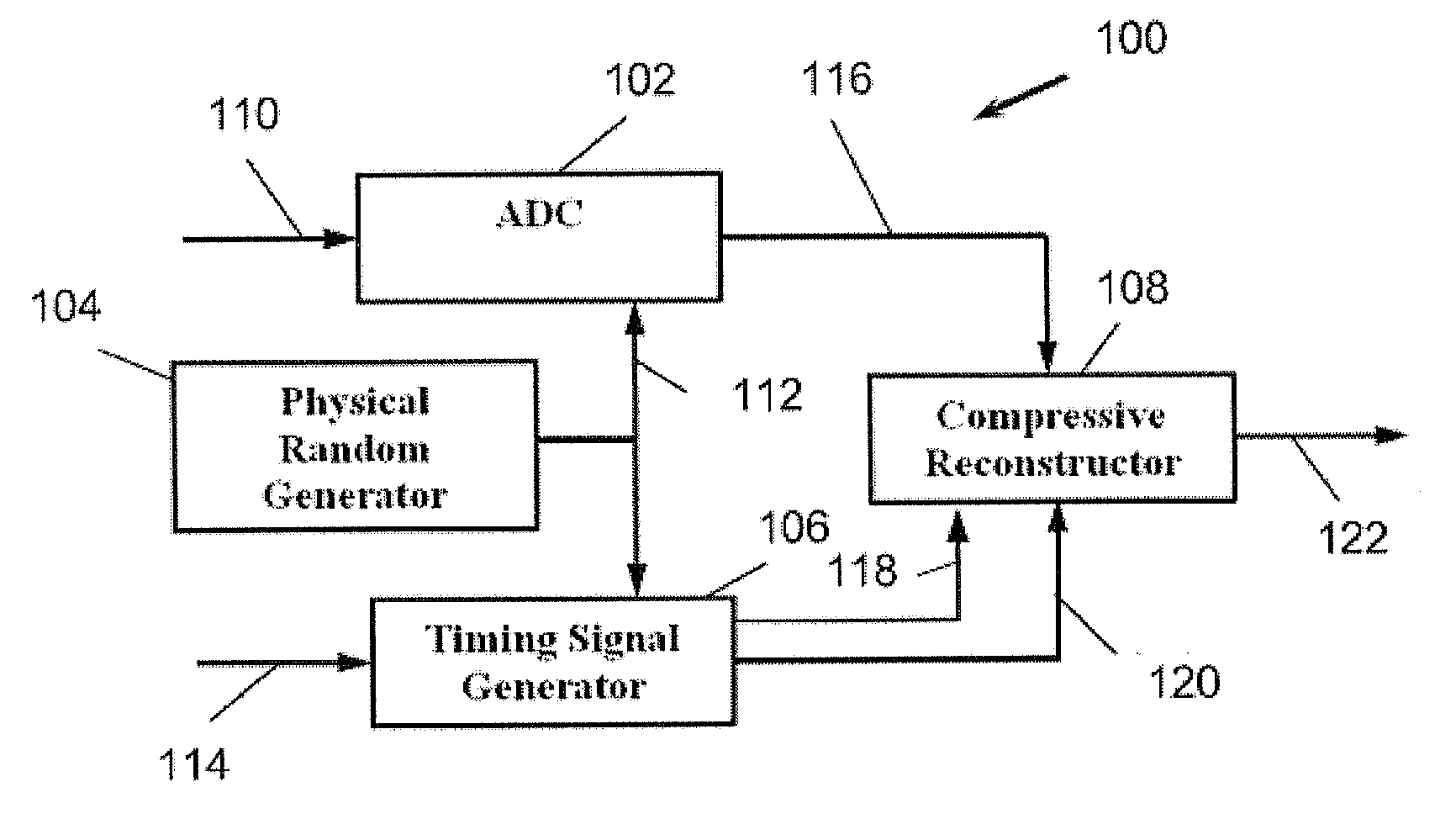
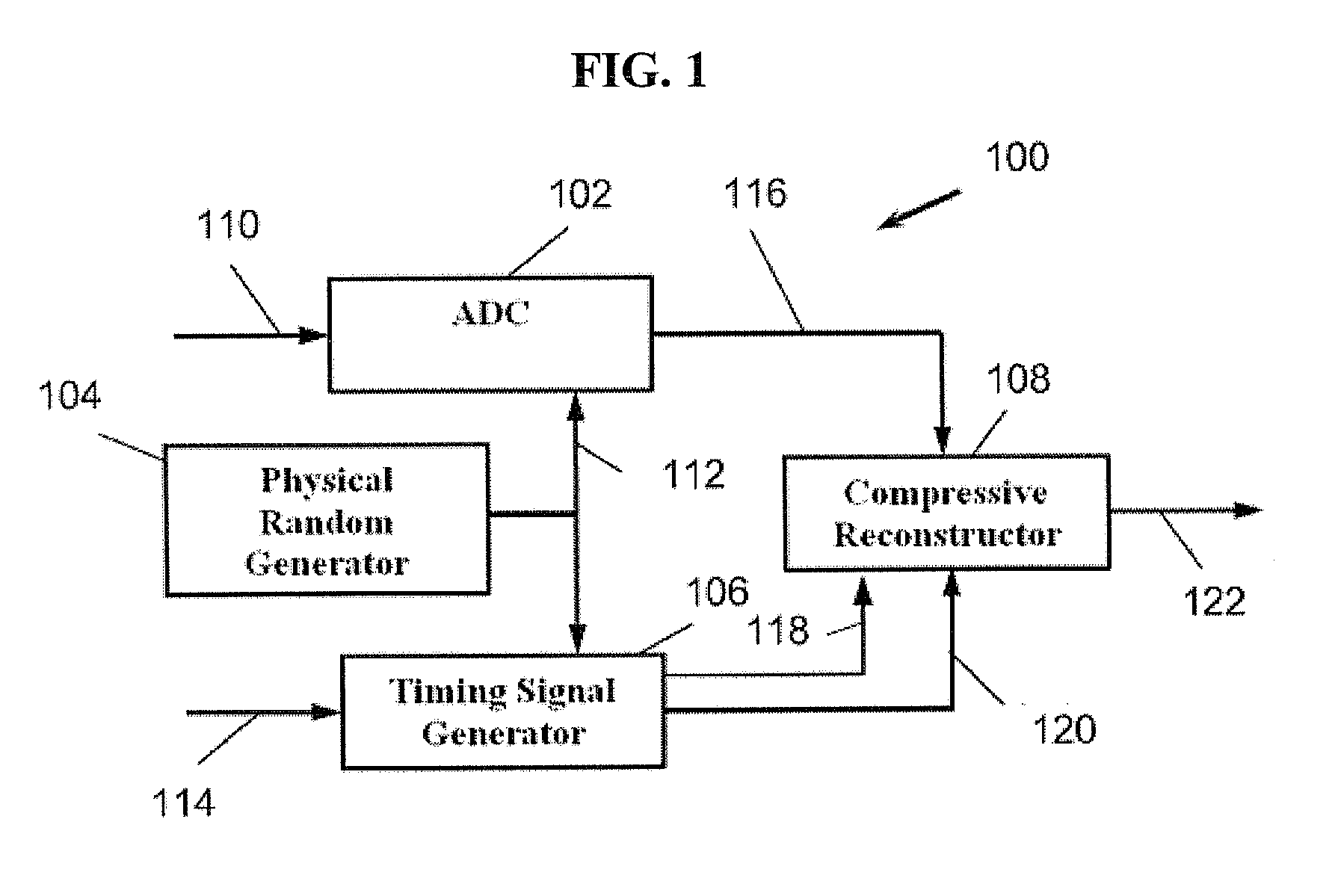
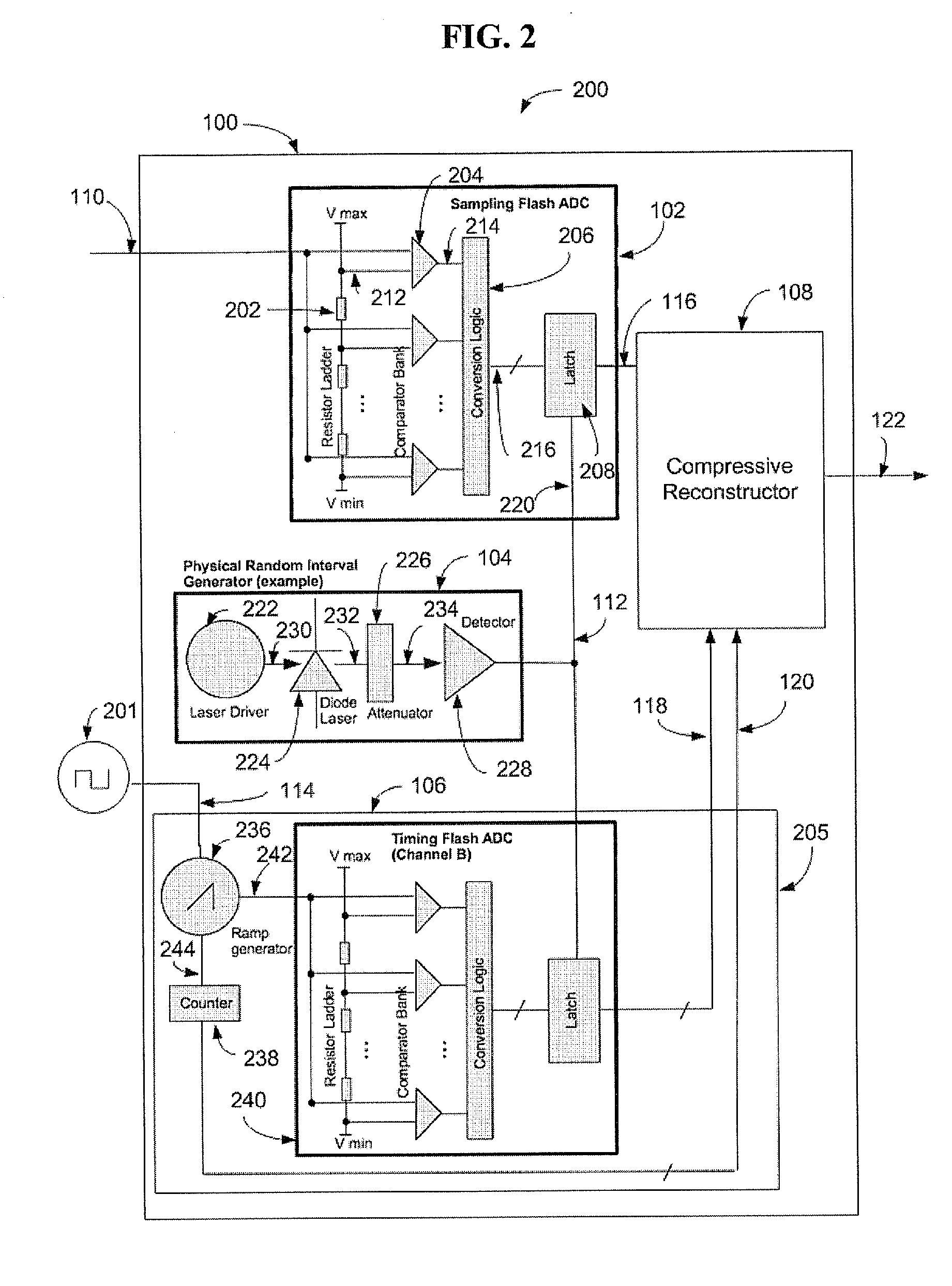
ActiveUS20120075134A1Electric signal transmission systemsAmplifier modifications to reduce noise influenceSignal generatorAnalog-to-digital converter
The present invention provides a system for use with an input signal and a clock signal. The system includes a physical random interval generator, a sampling analog-to-digital converter (ADC), a timing signal generator and a reconstructor. The physical random interval generator can generate a random output signal. The ADC can output a sampled output signal based on the input signal and the random output signal. The timing signal generator can output a timing signal based on the clock signal and the random output signal. The reconstructor can reconstruct an information signal based on the sampled output signal and the timing signal.
Owner:THE JOHN HOPKINS UNIV SCHOOL OF MEDICINE
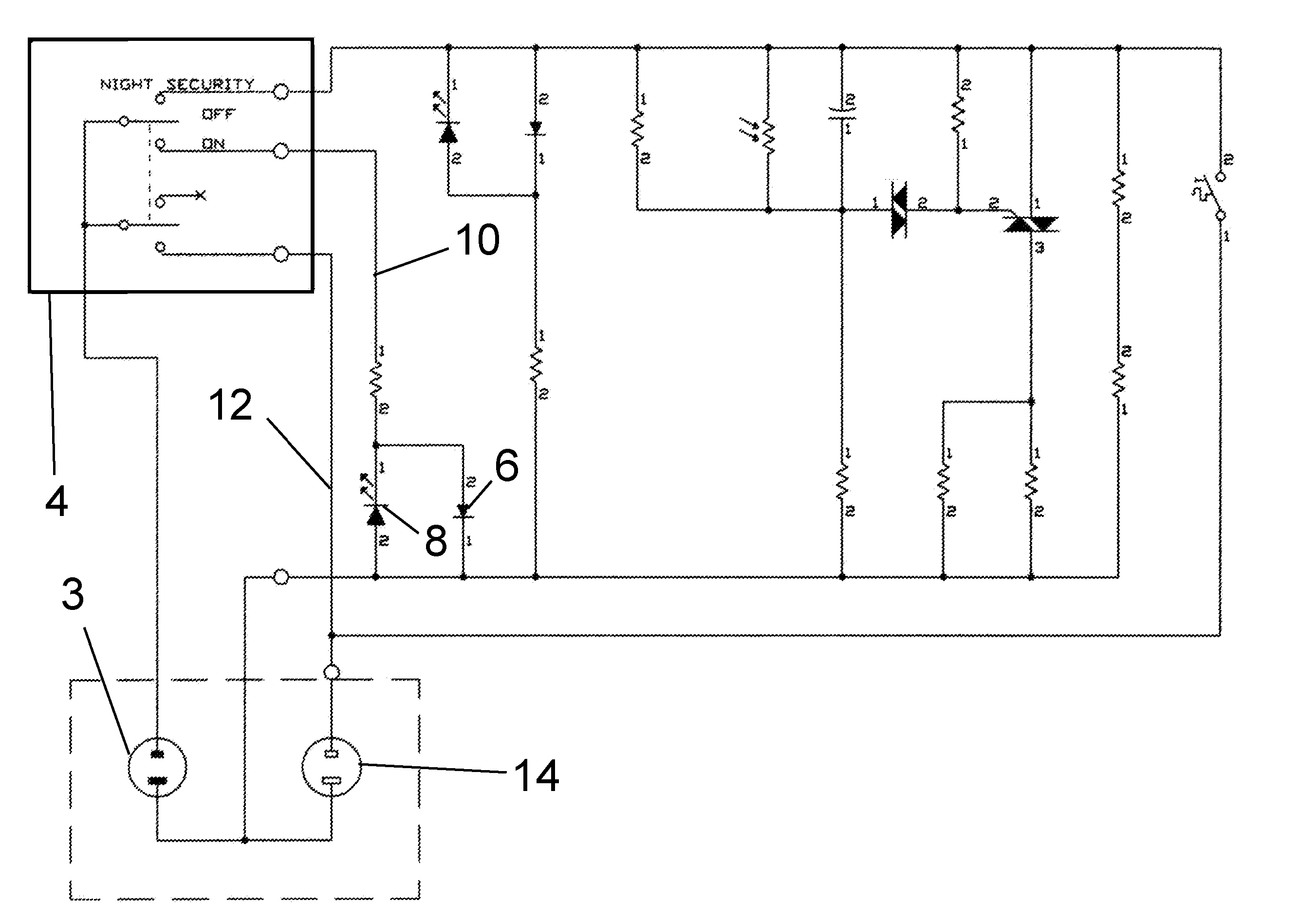
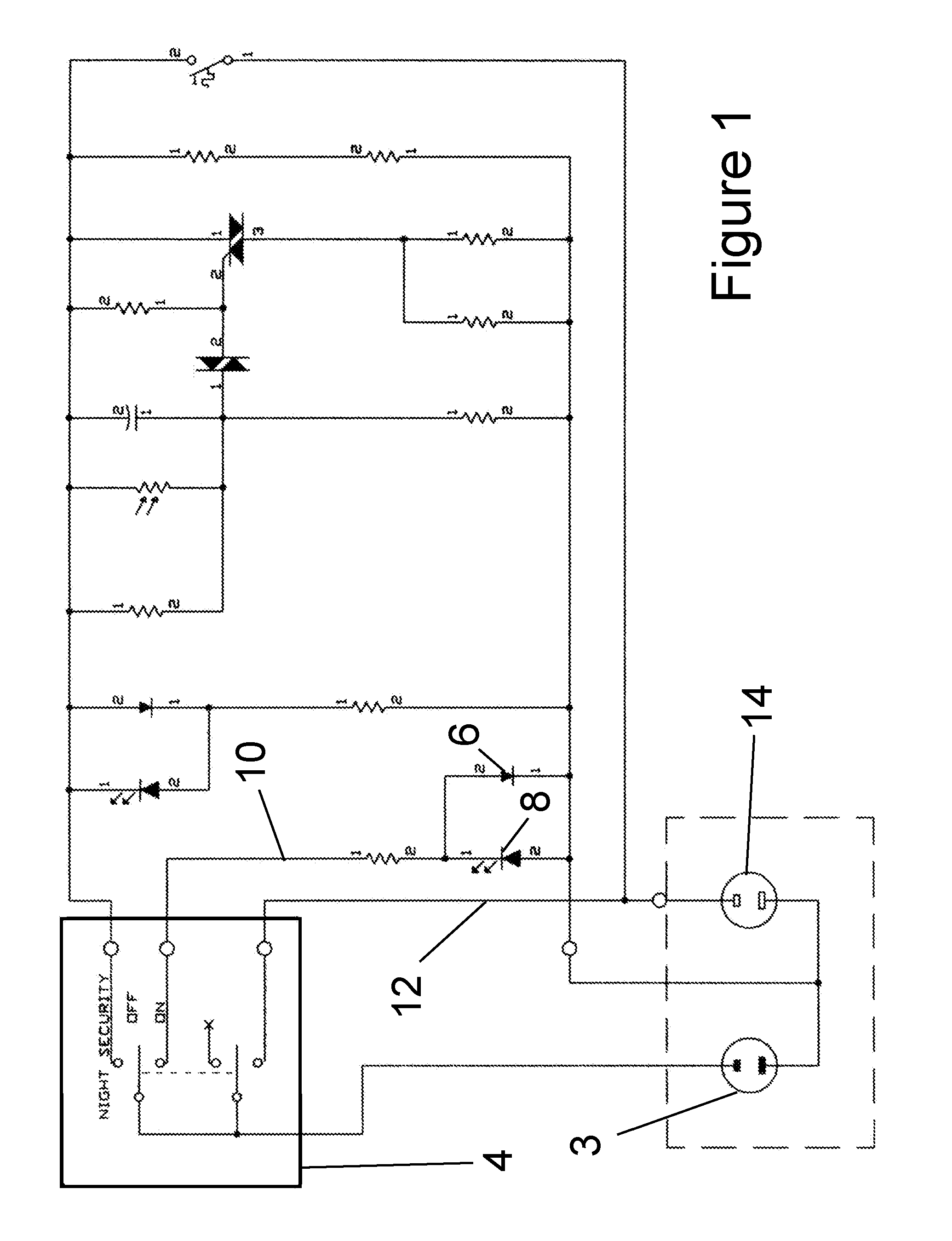
Device for Simulating Human Activity in an Unoccupied Dwelling
ActiveUS20060186740A1Rotary current collectorBoards/switchyards circuit arrangementsElectricityBiological activation
The present invention is a thermally activated electrical switch for use in simulating human activity. The invention is features dual heat sources enclosed in a thermally isolated chamber within the invention. Since the activation of the switch is dependent upon the ambient temperature of the environment, it opens and closes at sufficiently random intervals to simulate human activity. This embodiment includes the use of a photoelectric sensor to further vary timing of the switch actuation.
Owner:THE MILETTI GRP
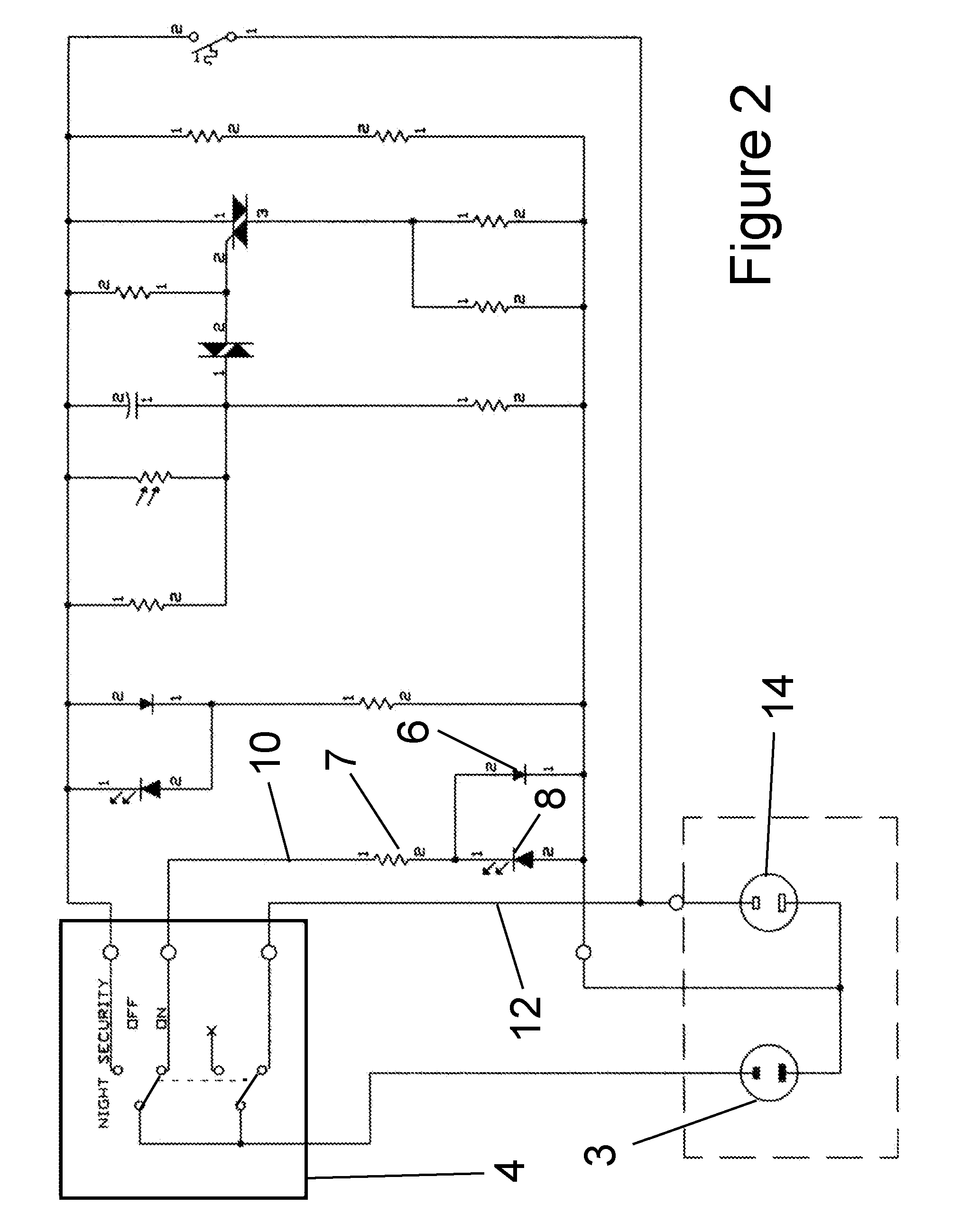
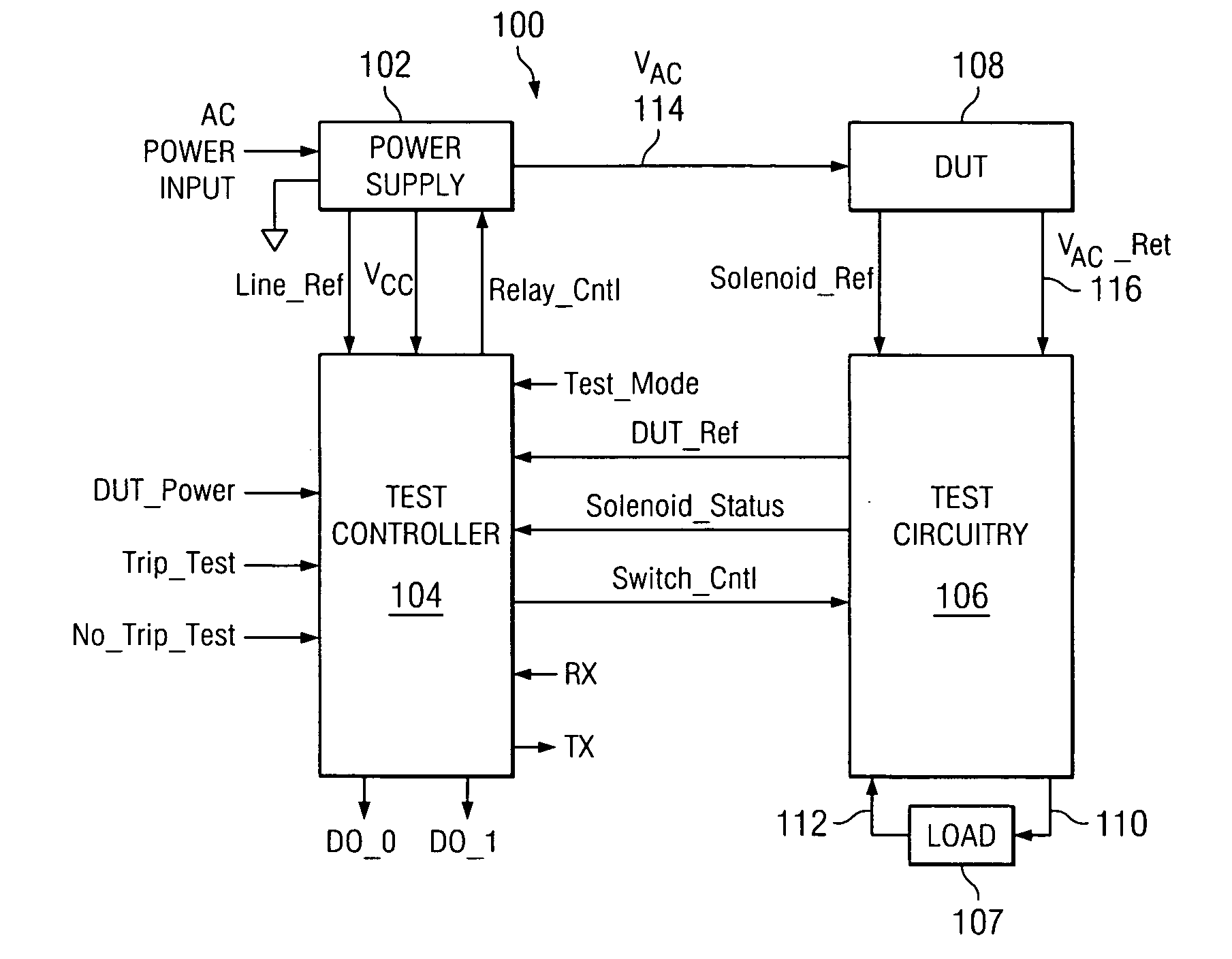
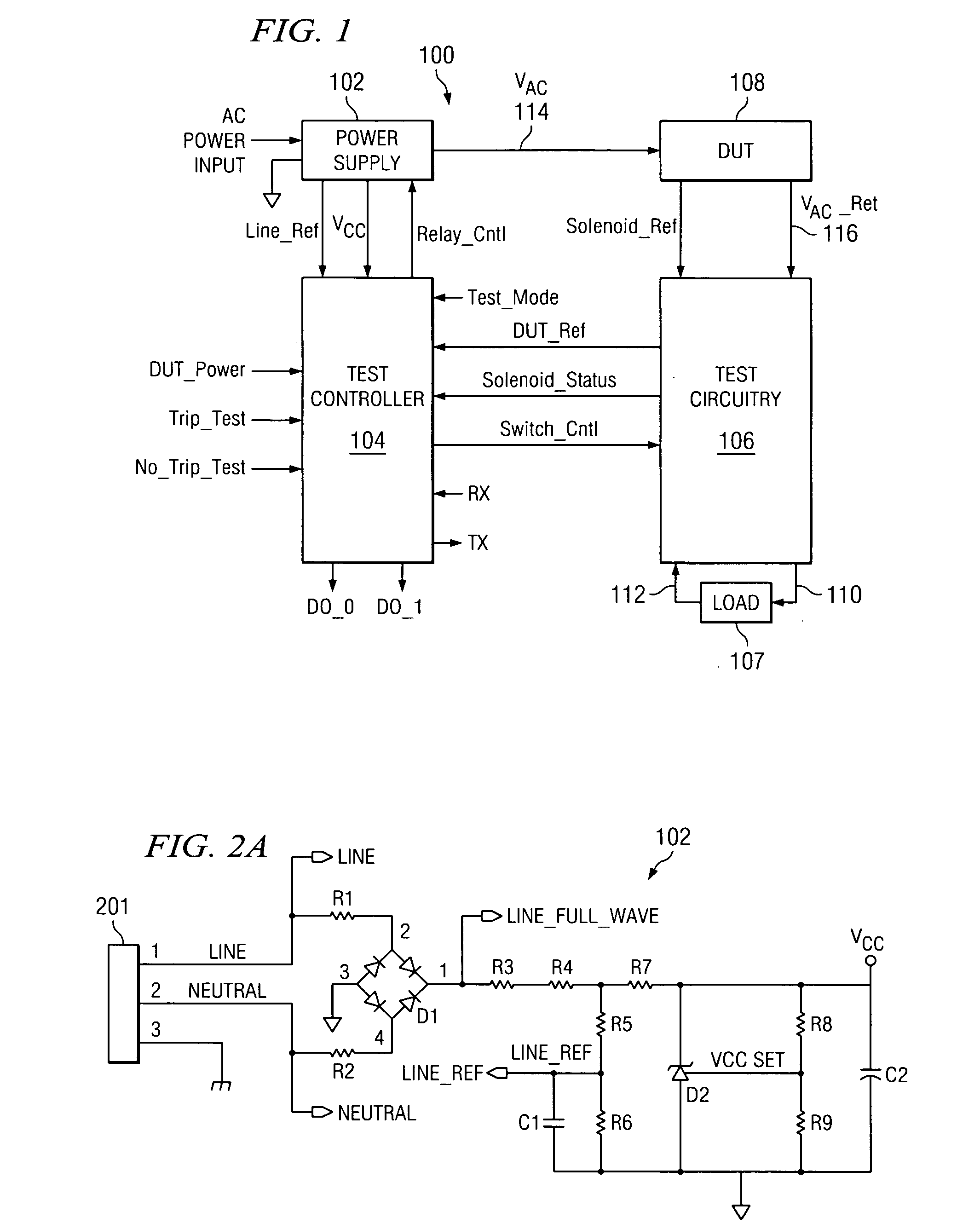
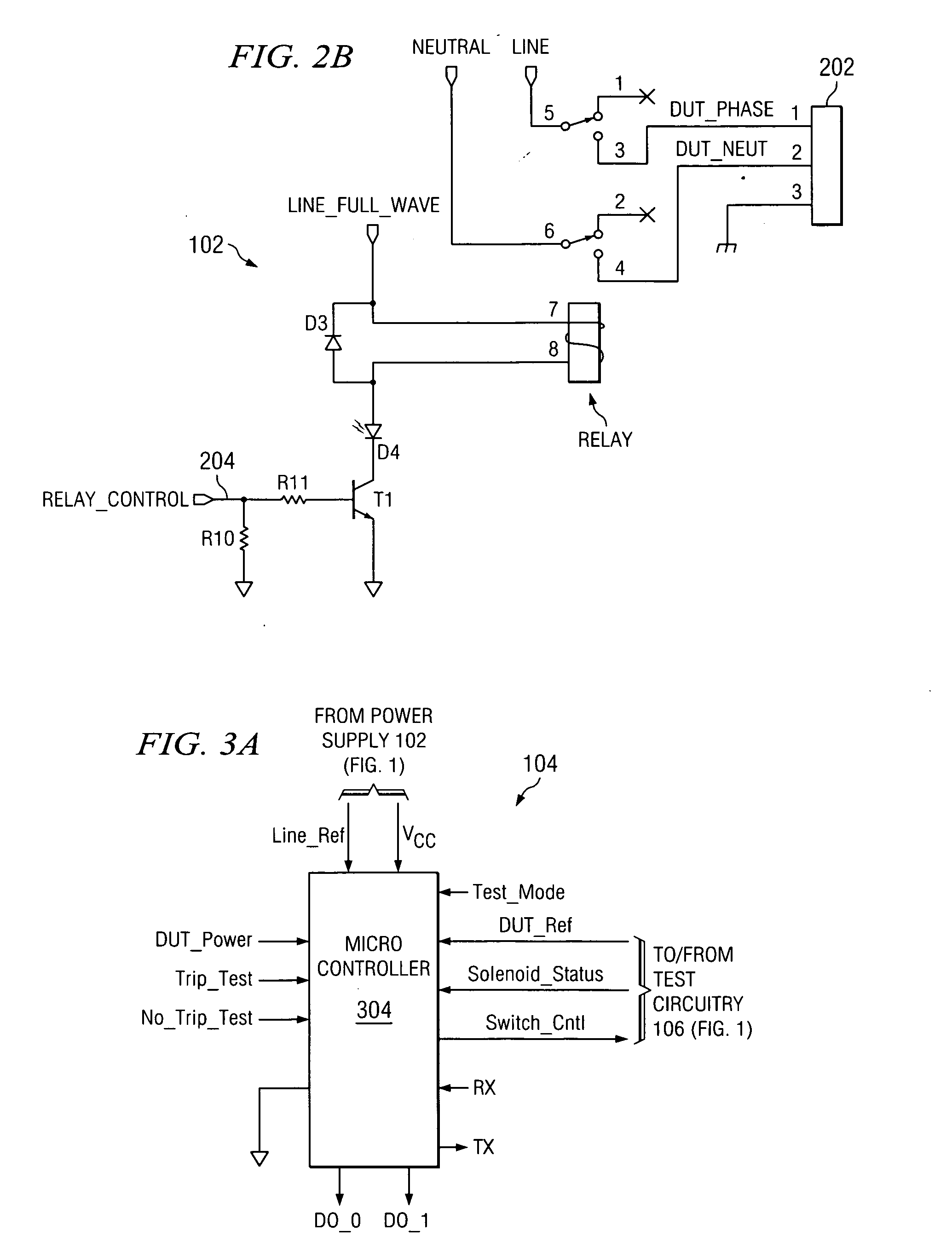
Arc fault circuit interrupter test circuit and test board
InactiveUS20070008103A1Correct operation of deviceTesting dielectric strengthElectric testing/monitoringFull waveEngineering
A tester for an arc fault circuit interrupter that can selectively simulate and apply electrical arc faults and nuisance loads to at least one device under test (DUT). The tester includes a power supply, a test controller, and test circuitry coupleable to a DUT. AC power input is provided to the DUT and the power supply, which regulates the AC power input to a DC level for powering the test controller. The test circuitry full wave rectifies AC current returning from the DUT, and the test controller controls a switch in the test circuitry. When the switch is on, the AC current flows through the DUT, the full wave rectifier, the load, and the switch to ground. To simulate an arcing condition, the test controller turns the switch on and off at random intervals. To simulate a nuisance load condition, the test controller turns the switch on and off at periodic intervals. In this way, proper operation of the DUT can be verified under both arcing and nuisance load conditions.
Owner:SENSATA TECH MASSACHUSETTS INC
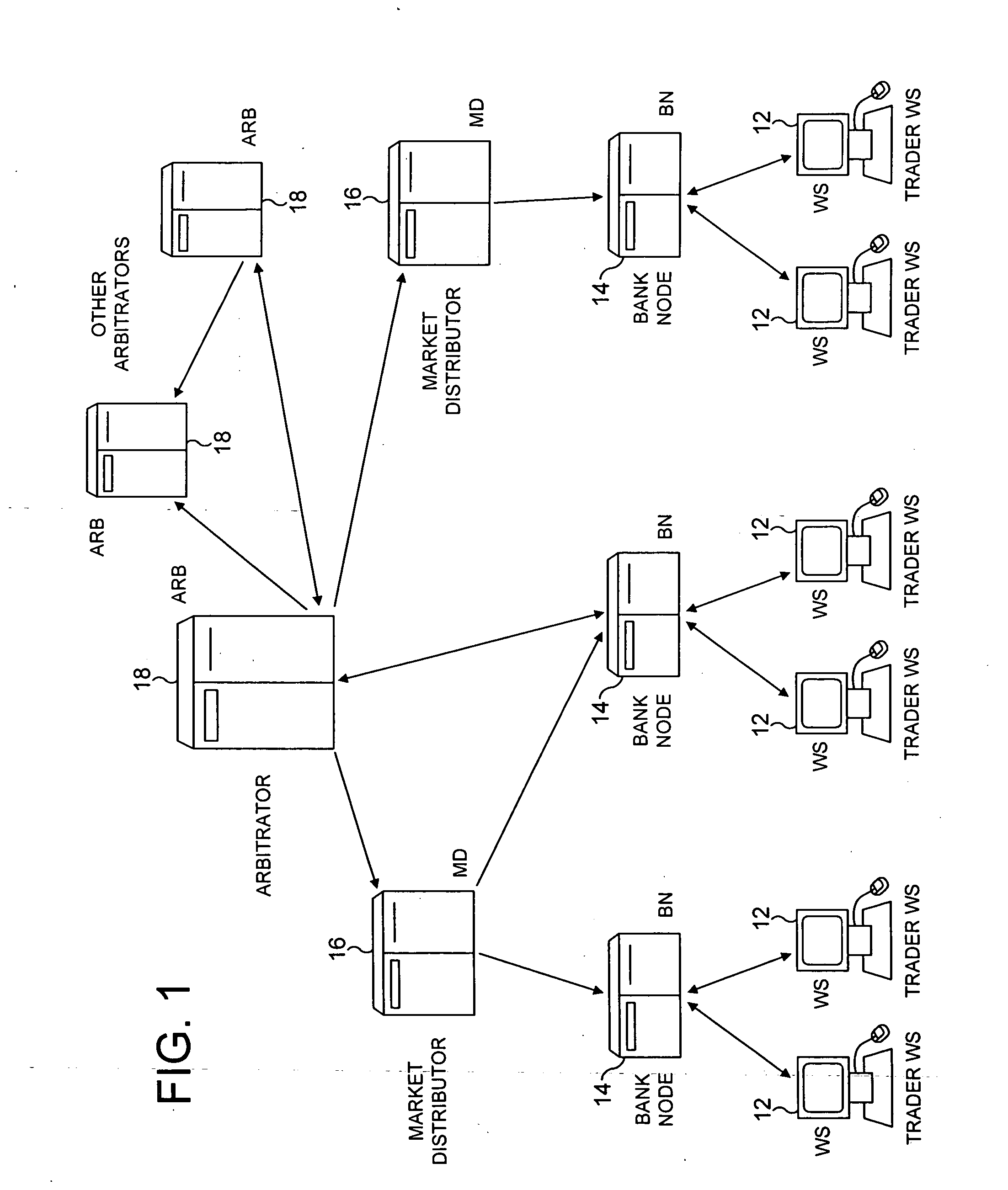
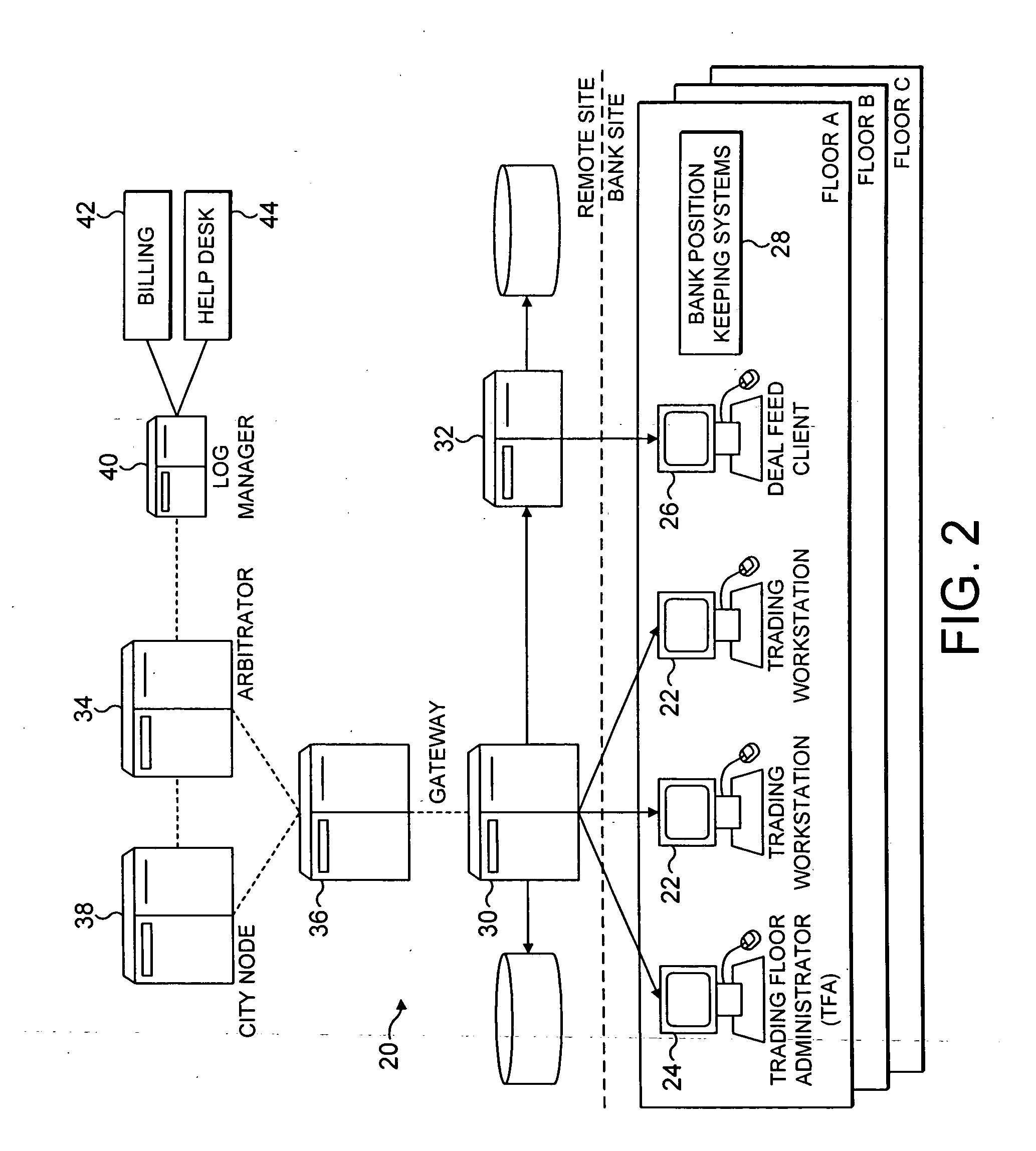
Vocalisation of trading data in trading systems
ActiveUS20050027642A1Easy to insertFinanceSpecial data processing applicationsTransaction dataWorkstation
A trading system such as an anonymous trading system for trading financial and other instruments can vocalise trading data to trader workstations as well as display it on a screen. Where a trader selects to receive vocal announcements, a trading floor identifier unique to his trading floor is also announced at random intervals.
Owner:EBS GROUP +1
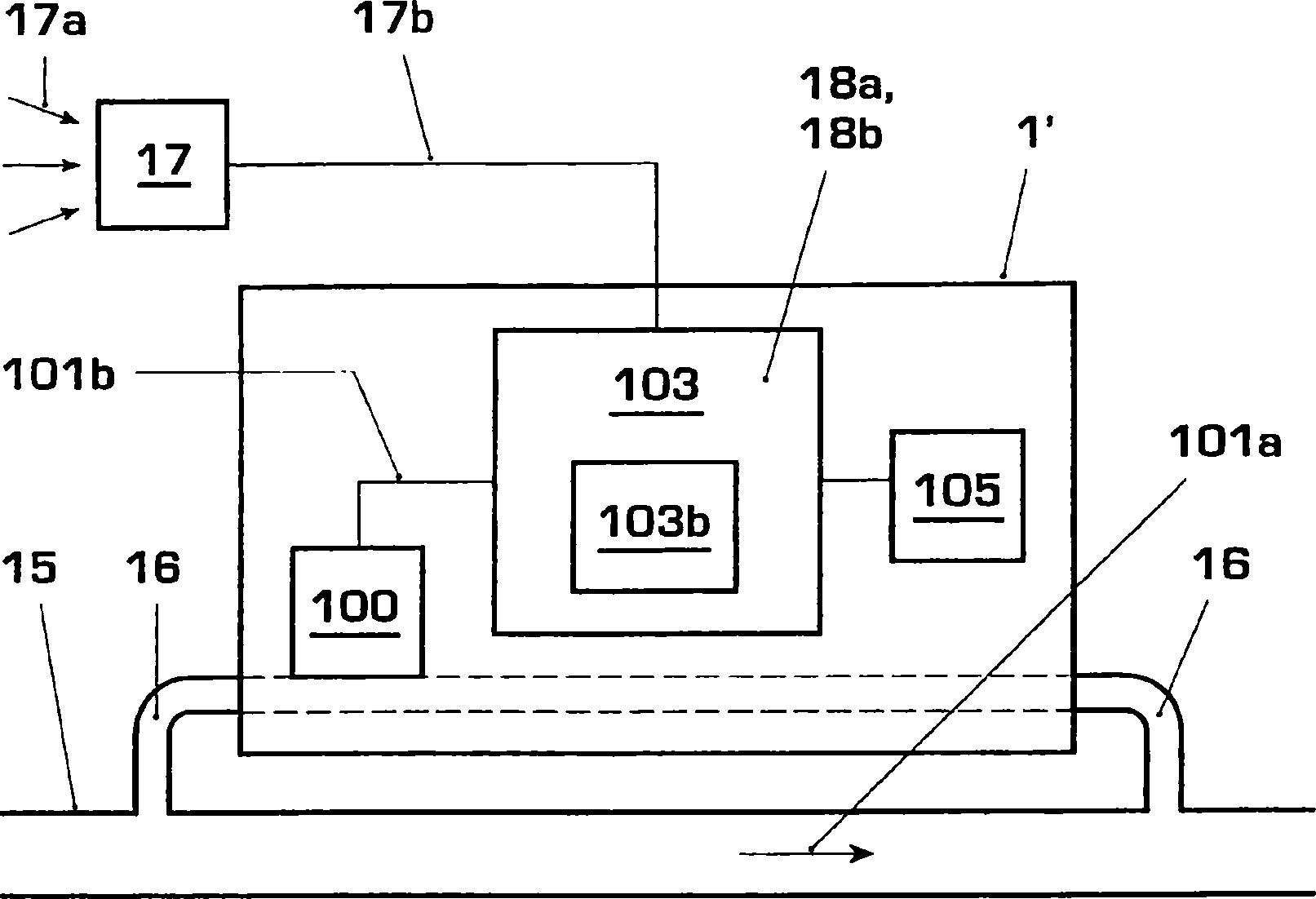
Method and apparatus for reducing power consumption in battery-operated devices
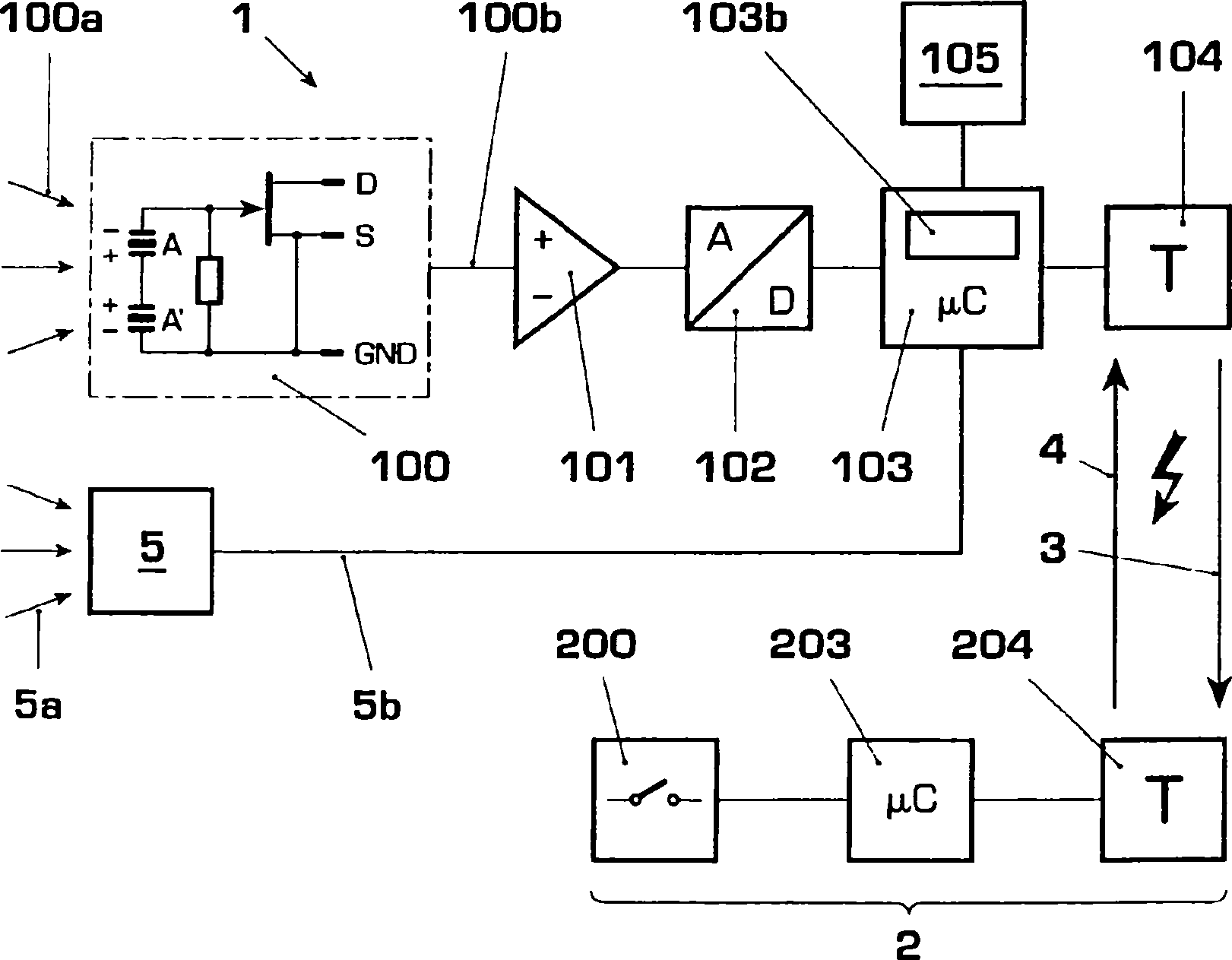
InactiveCN1886766AImprove usabilityReduce power consumptionVolume indication and recording devicesPower supply for data processingMotion detectorElectrical battery
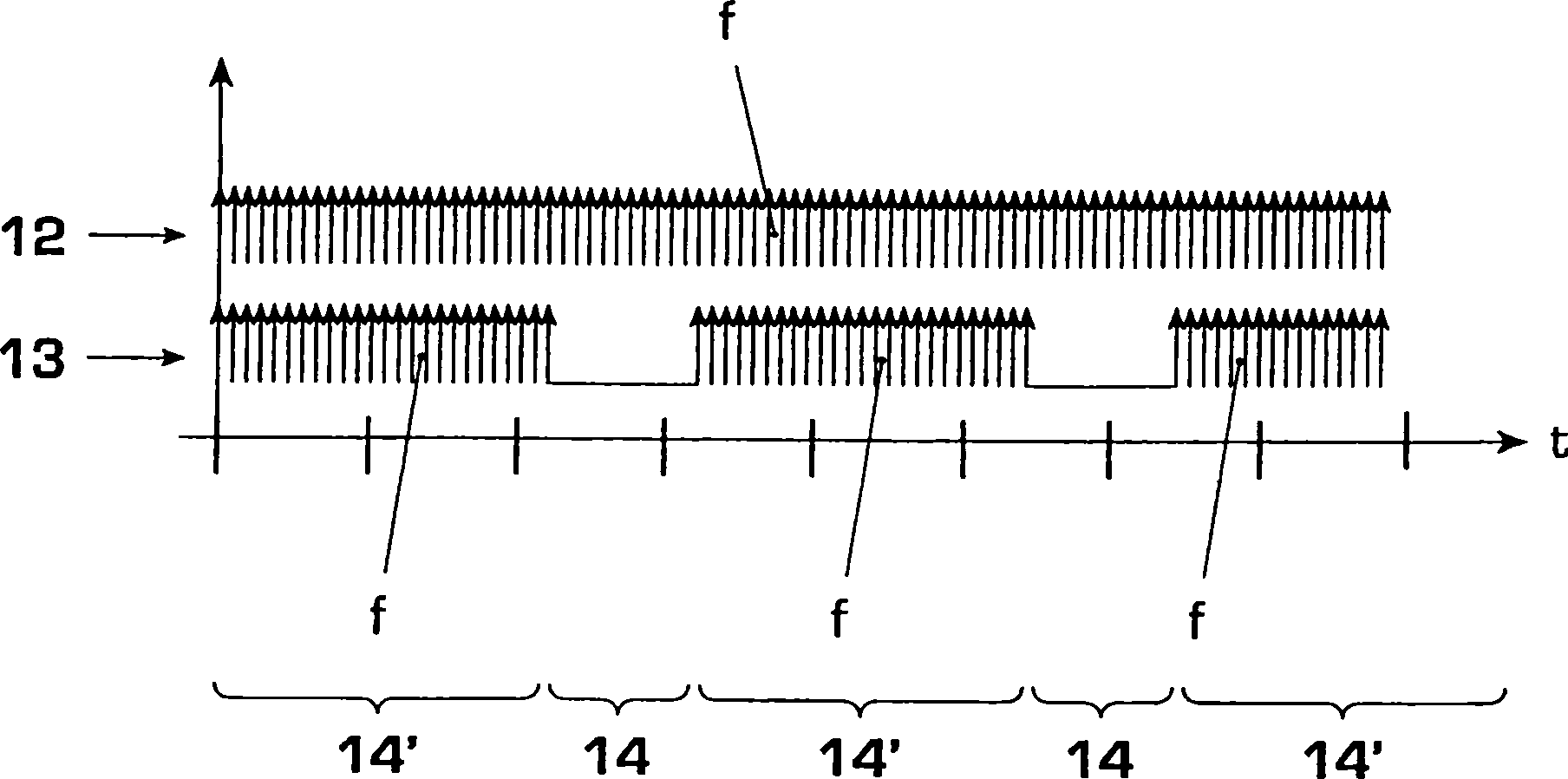
The invention relates to an energy-saving sampling method and an electrical apparatus (1, 1'), particularly an electronic gas meter (1') or motion detector (1), for carrying out said method. The aim of the invention is to reduce power consumption (I) of the battery (105) in said method and apparatus (1, 1'). Said aim is achieved by sampling the test signal (100b, 101b) in a quasi continuous (13) manner by defining sampling time slots (14') during which sampling is done in an uninterrupted fashion while sampling gaps (14) during which no sampling is done are allowed between the sampling time slots (14'). Examples of embodiments include sampling gaps (14) at regular or random intervals, sampling gaps (14) with a variable duration and / or frequency and especially an increasing duration and / or frequency as the remaining service life of the battery decreases, and a lower sampling rate (f1, f2, f3) during the sampling time slots (14'), among others, resulting in an increased battery lifetime without substantially reducing test reliability.
Owner:HYDROMETER GMBH
High-throughput screening system and method of fast growing microalgae strains
InactiveCN106148159AImprove accuracySolve the technical bottleneck of difficult to obtain single-cell level analysisBioreactor/fermenter combinationsBiological substance pretreatmentsBiotechnologyHigh-Throughput Screening Methods
The invention belongs to the technical field of biology and particularly relates to a high-throughput screening system and method of fast growing microalgae strains. The system comprises a liquid drop monodisperse single cell wrapping unit and a reinjecting screening unit. The method comprises steps as follows: microalgae cells are washed and dispersed in gel to proper concentration and injected into a micro-fluidic chip to form monodisperse single cell liquid drops, and microspheres wrapped in an oil phase are subjected to deoiling, filtration and redispersion and cultured in a constant-temperature incubator; whether living cells exist and the growing speed of the cells are judged according to imaging by the aid of an inverted microscope, gel amplification pictures are collected through random interval sampling, gel microspheres where the cells grow are counted, the growth condition of microalgae in the single cell level is further monitored, and the microalgae strains with remarkable growth rate difference are separated on the basis. According to the constructed high-throughput screening system and method of the fast growing microalgae strains, the system is simple, the cost is low, and the system and the method can be used for screening of phenotypic correlation of growth of a mutant library of alga.
Owner:SOUTHWEST UNIVERSITY +1
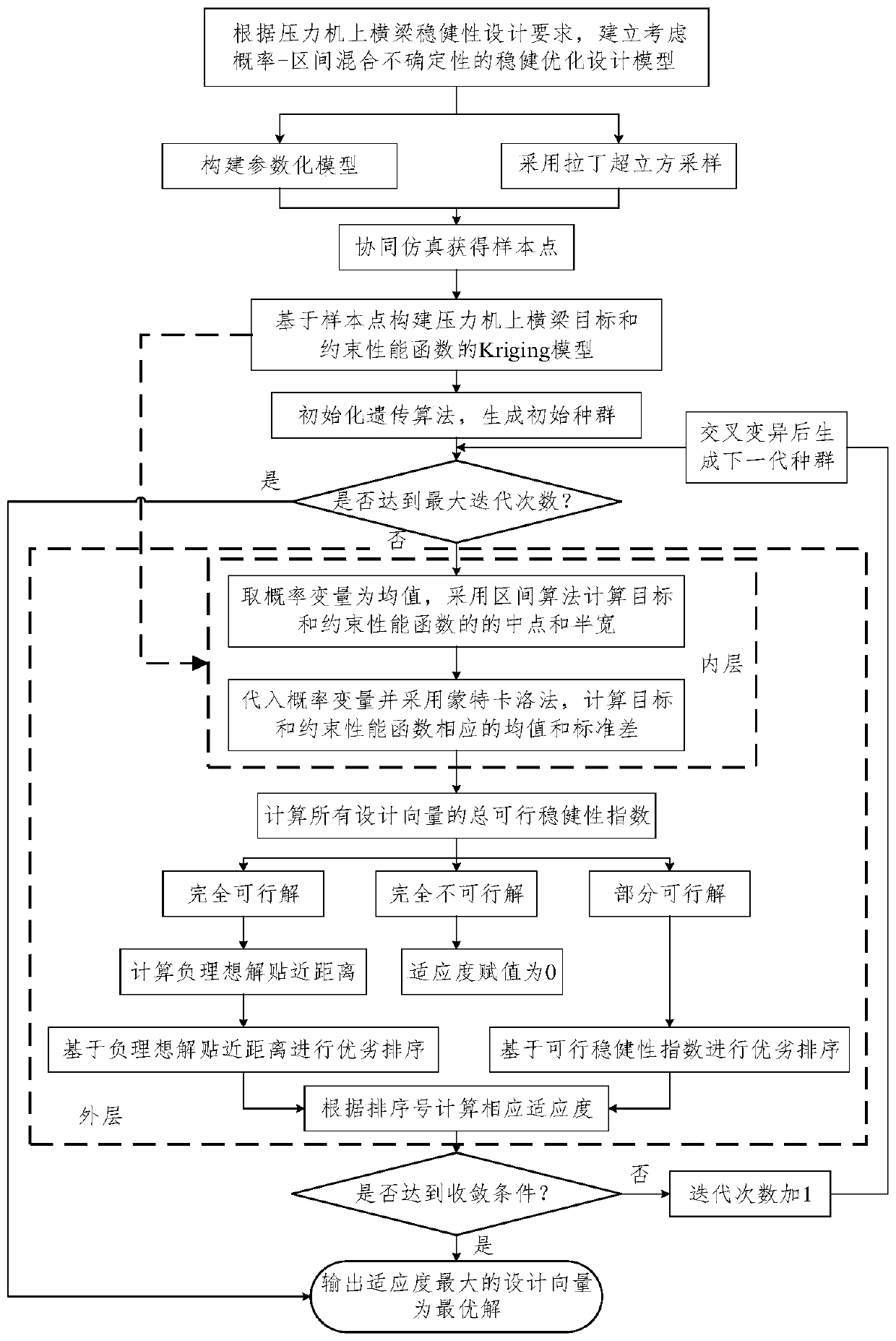
Press machine upper cross beam robust optimization design method based on negative ideal solution close distance
ActiveCN109992848AIn line with engineering practiceOvercome the disadvantage of uncertain optimization resultsGeometric CADForecastingPerformance functionGenetic algorithm
The invention discloses a press machine upper beam robust optimization design method based on a negative ideal solution approaching distance. The method comprises the following steps: considering randomness of loads borne by an upper cross beam of a press machine and interval uncertainty of material attributes of the upper cross beam, and establishing a robust optimization design model for upper beam with random-interval mixed uncertainty variable based on a 6 sigma robustness design principle;directly solving the optimization model based on a double-layer nested genetic algorithm; enabling the inner layer to perform interval robustness analysis on each design vector by using a Kriging prediction model, and calculate a mean value and a standard deviation of the target function and each constraint performance function by using a Monte Carlo method; and enabling the outer layer to use an inner layer calculation result, and classify sort and optimize all the design vectors based on the constraint performance function total feasible robustness coefficient and the negative ideal solution close distance. The method conforms to engineering practice, subjective interference is avoided, andgood engineering practicability is achieved.
Owner:ZHEJIANG UNIV
Voice encryption and decryption method for conversion parties on basis of voice print
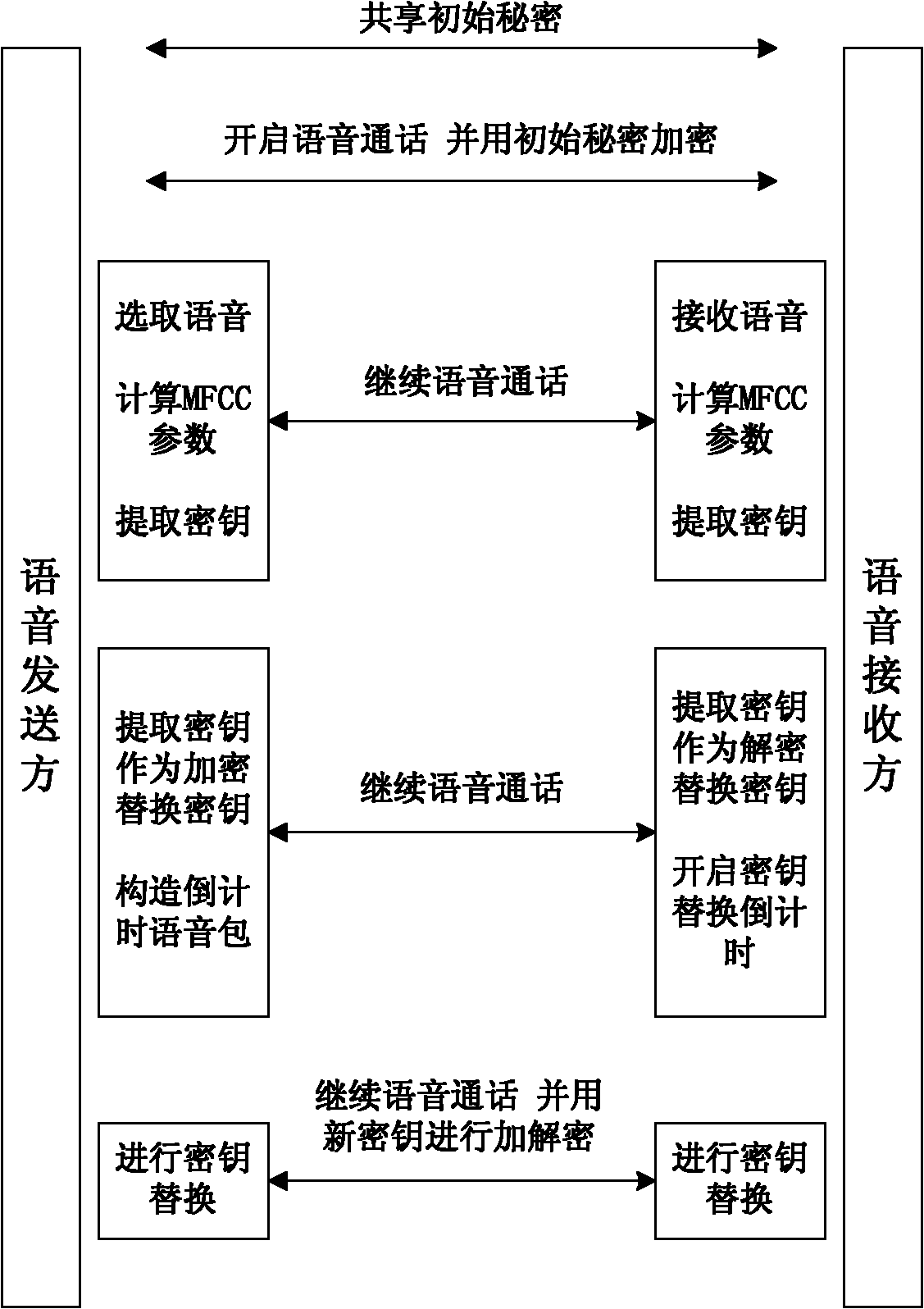
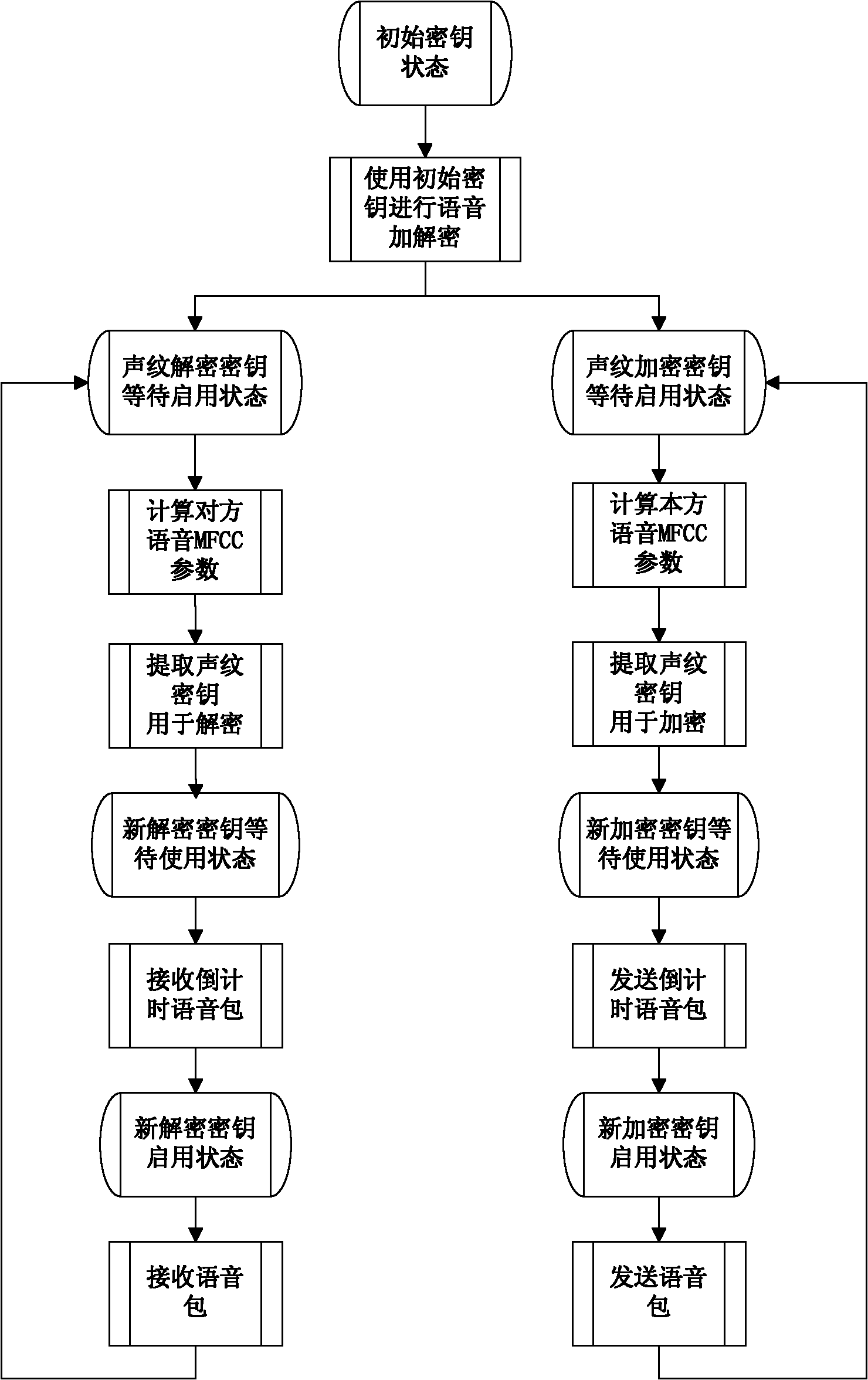
InactiveCN102064937AVerify reliabilityImprove securityKey distribution for secure communicationSpeech analysisKey sizeComputer hardware
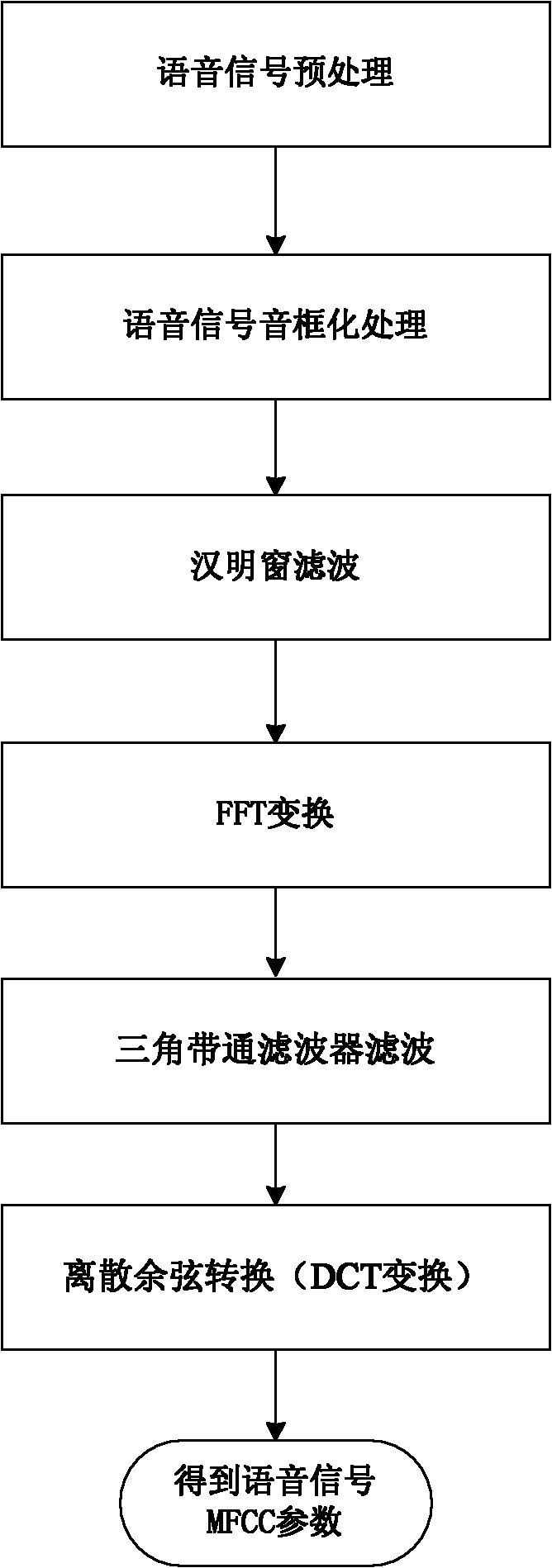
The invention relates to a voice encryption and decryption method for conversion parties on the basis of voice print, comprising the following steps of: (1) exchanging a section of shared secret by conversion parties; (2) starting the voice conversation by conversion parties, and determining a format of a network transmission packet; (3) in the process of conversion, calculating the MFCC (Mel Frequency Cepstral Coefficient) parameter of the voice characteristic information of self at certain interval by a voice sender, and extracting a secret key from the MFCC parameter; (4) numbering a voicepacket participating in calculating the MFCC parameter when the voice sender sends the voice packet; (5) receiving the voice packet by a voice receiver, and splicing the voice packet containing sequence numbers in order, calculating the MFCC parameter, and extracting the secret key from the MFCC parameter; (6) after the voice sender finishes sending the voice packet containing the vocal print secret key, sending a countdown voice packet at certain interval; and (7) after receiving the countdown voice packet, beginning countdown by the voice receiver, and replacing the current secret key when time is up, wherein both parties have symmetrical operation from steps (3) to (7). The voice encryption and decryption method generates the secret key by the voice characteristics of conversion parties, the length of the secret key can be chosen as required, and randomness is excellent.
Owner:HANGZHOU DIANZI UNIV
Upward auess-in method and apparatus
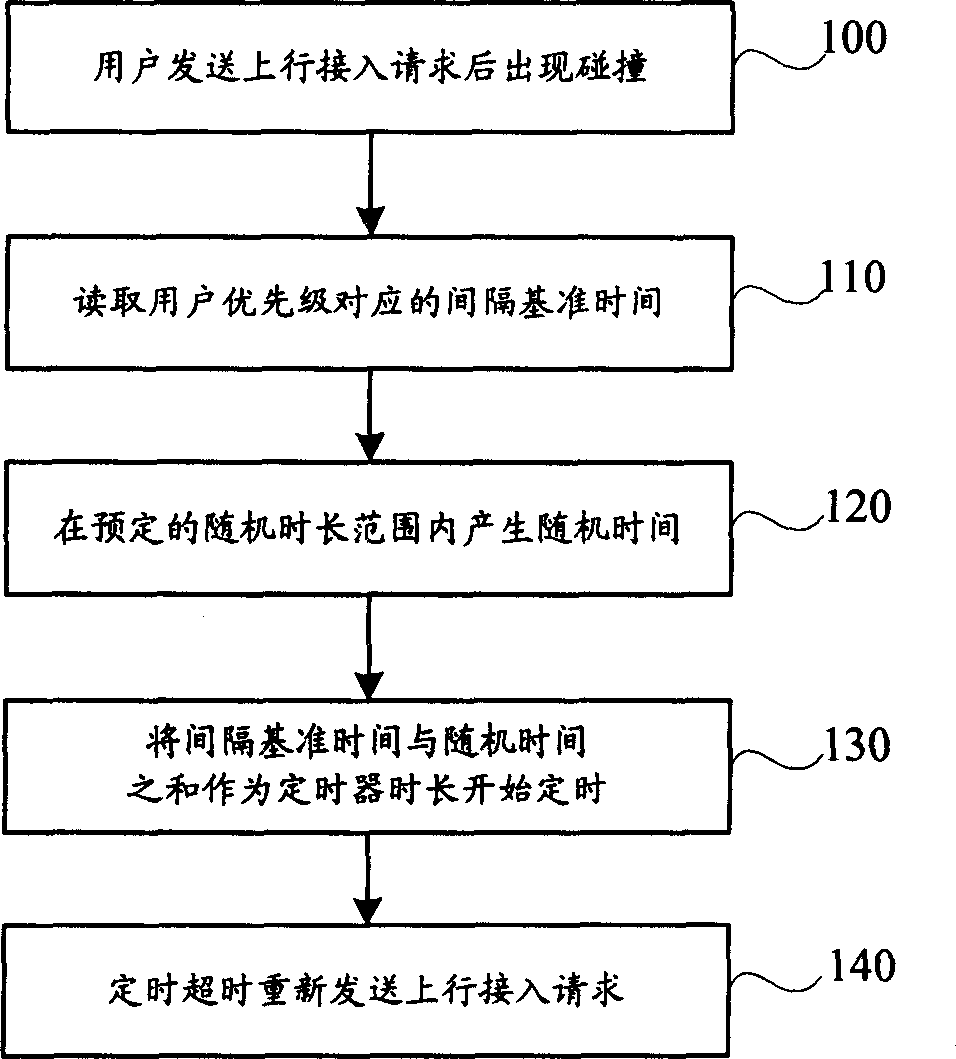
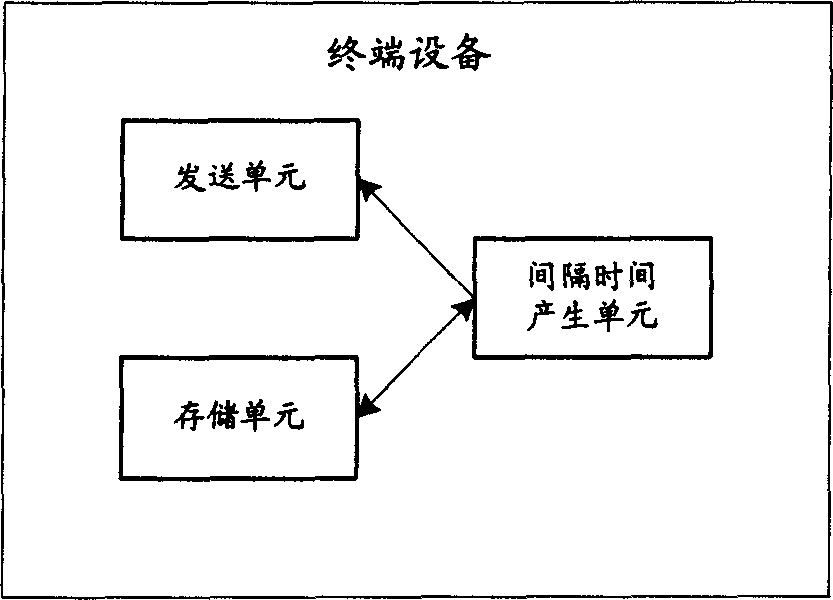
ActiveCN1852495AAvoid priorityGuaranteed priorityWireless communicationAccess timeTerminal equipment
After collision occurs on up going access request initiated by terminal device, the method generates random time interval of retransmission based on users' priorities. Random time interval of retransmission for user in high priority is smaller than random time interval of retransmission for user in low priority. After delaying the random time interval, terminal device retransmits up going access request. The invention also discloses a terminal device including following units: sending unit in use for sending up going access request; generation unit of time interval in use for generating random time interval of retransmission for controlling the sending unit to retransmit up going access request. Based on priorities of users, the invention controls user's second access time so as to prevent user in low priority from preempting channel. The invention guarantees preemption of user in high priority.
Owner:HUAWEI TECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com