File protection method and device
A file and file name technology, applied in the computer field, can solve the problems of file corruption, undetectable virus, non-existence, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
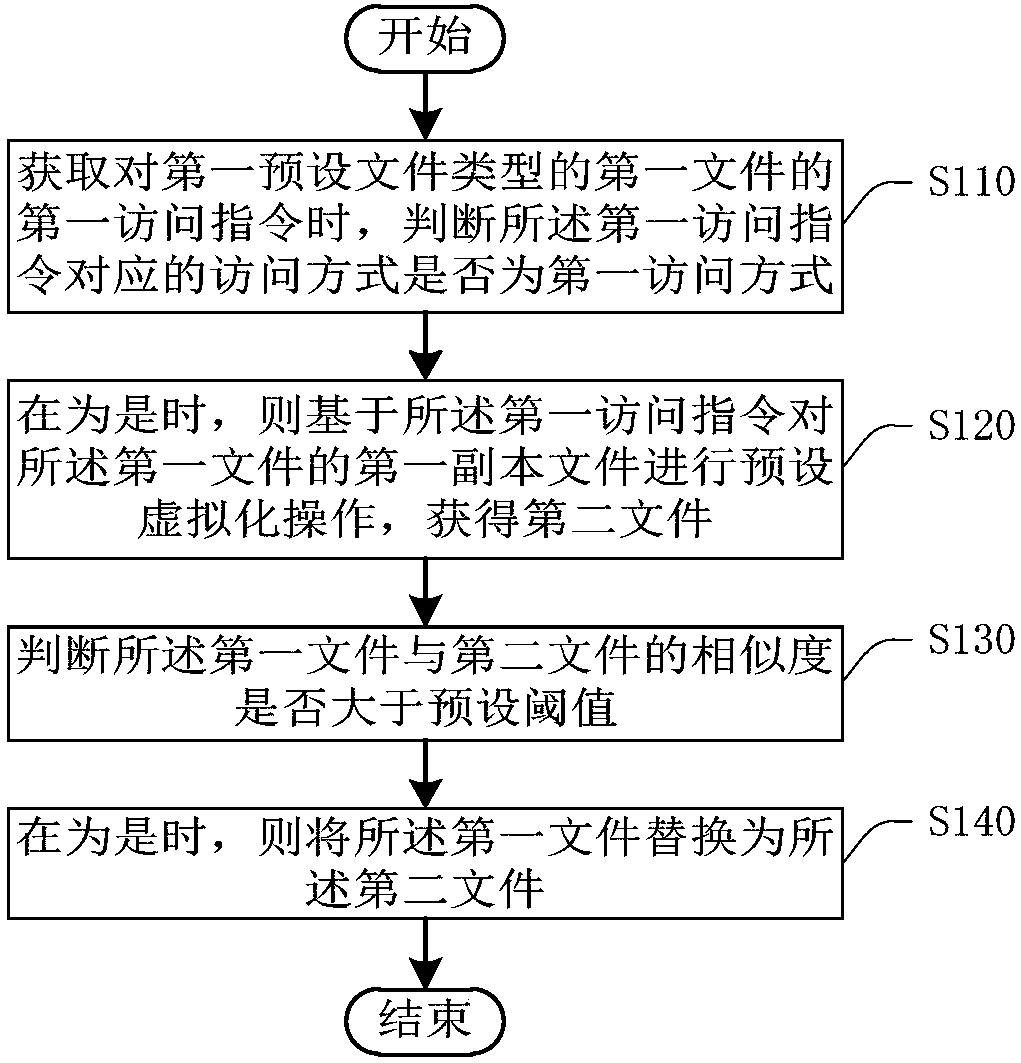
[0044] Such as figure 2 A flow chart of the file downloading method provided by the embodiment of the present invention is shown. See figure 2 , the method includes:
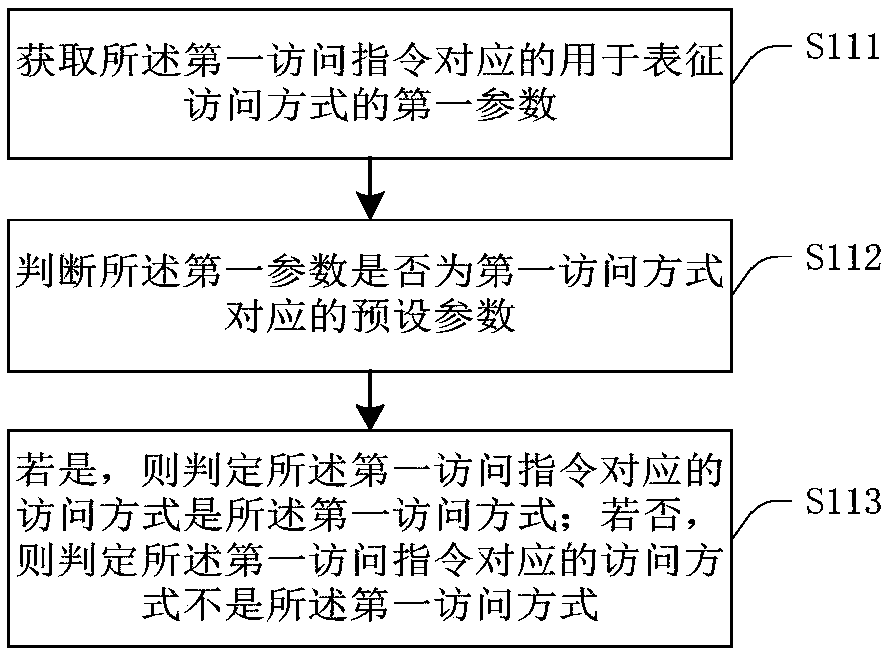
[0045] Step S110: When acquiring a first access command to a first file of a first preset file type, determine whether the access mode corresponding to the first access command is the first access mode.
[0046] The files in the system of the terminal device may have required operations for the user, or the files may be attacked by virus and ransomware. When the file is operated, the corresponding access instruction needs to be obtained.
[0047] In this embodiment of the present invention, files of the first preset file type that need to be protected may be stored in the terminal device. Specifically, a protected file with a preset extension can be set. For example, the preset extensions of the protected files can be 0, 1, 123, 1ST, 2, 3DM, 3DMF, DOC, DOCM, DOCX, xls, xlsx, PPT, PPTX and other important ...
no. 2 example
[0088] The second embodiment of the present invention provides a file protection device 200, please refer to Figure 6 , the file protection device 200 includes: an access mode judgment module 210 , a virtualization operation module 220 , a similarity judgment module 230 and an execution module 240 . Wherein, the access mode judging module 210 is configured to determine whether the access mode corresponding to the first access command is the first access mode when acquiring the first access command to the first file of the first preset file type; The virtualization operation module 220 is configured to perform a preset virtualization operation on the first copy file of the first file based on the first access instruction to obtain a second file when it is YES; the similarity judging module 230 It is used to judge whether the similarity between the first file and the second file is greater than a preset threshold; if yes, the execution module 240 is used to replace the first fi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com