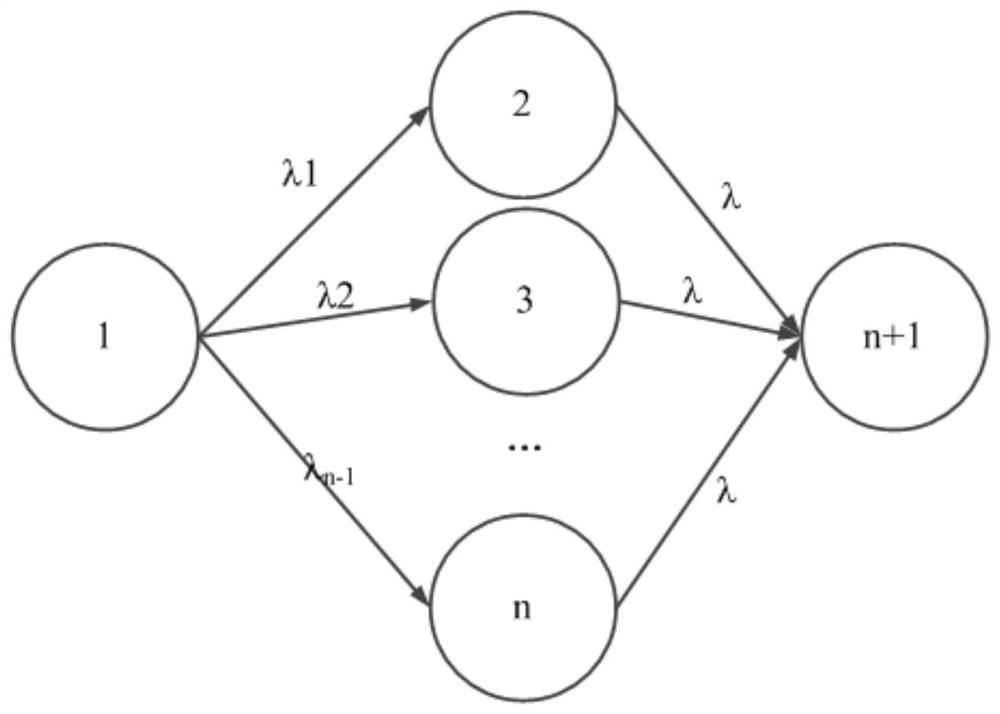
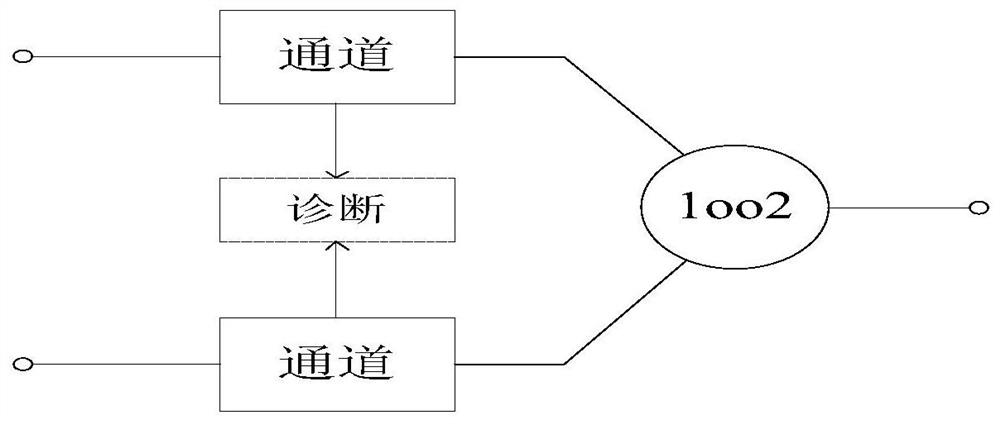
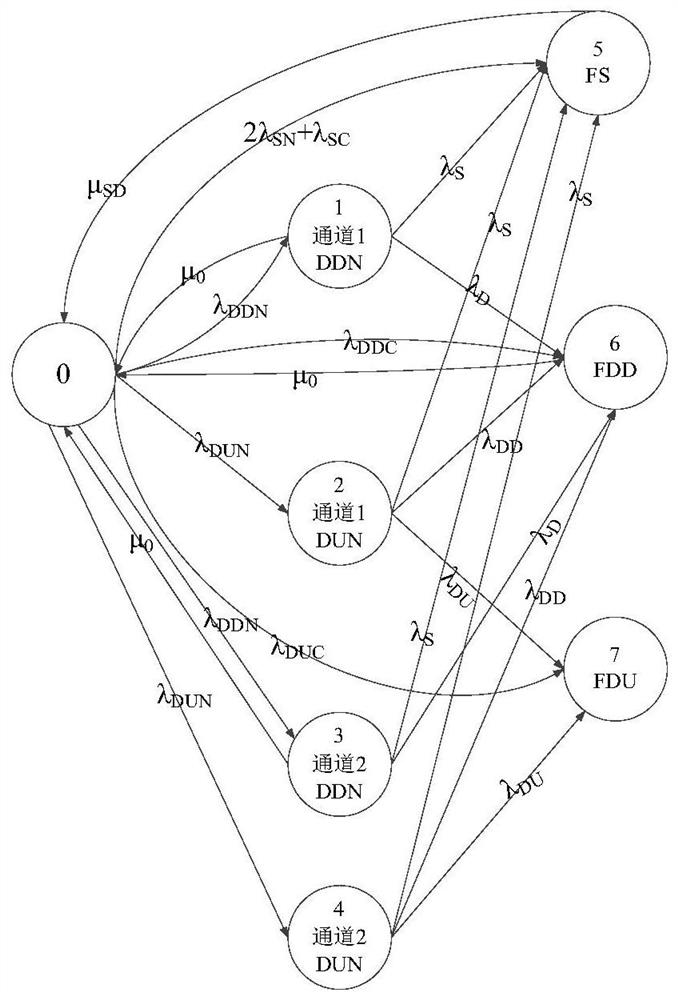
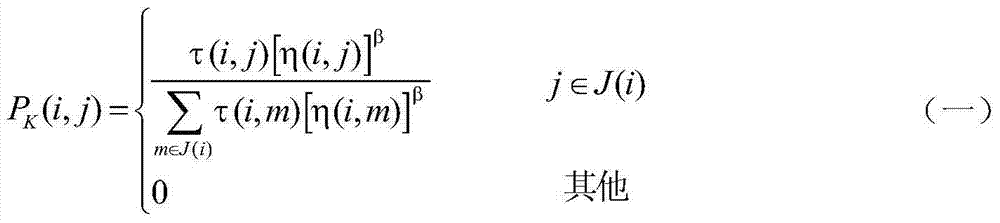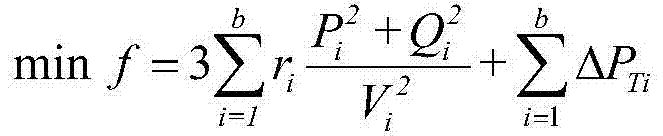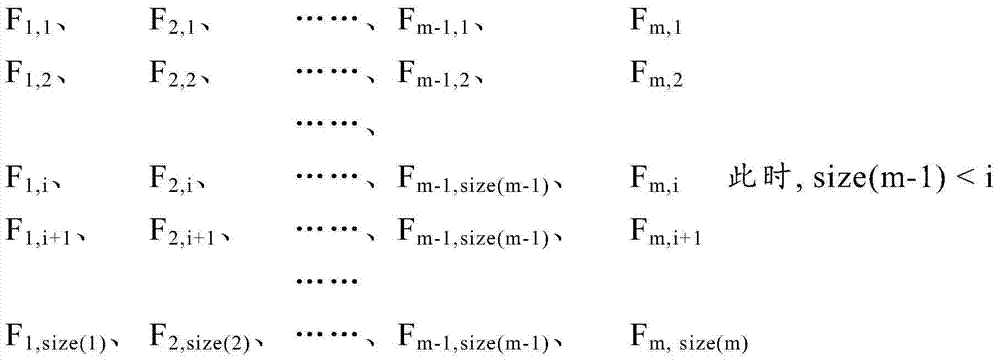Patents
Literature
51 results about "Combinatorial explosion" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
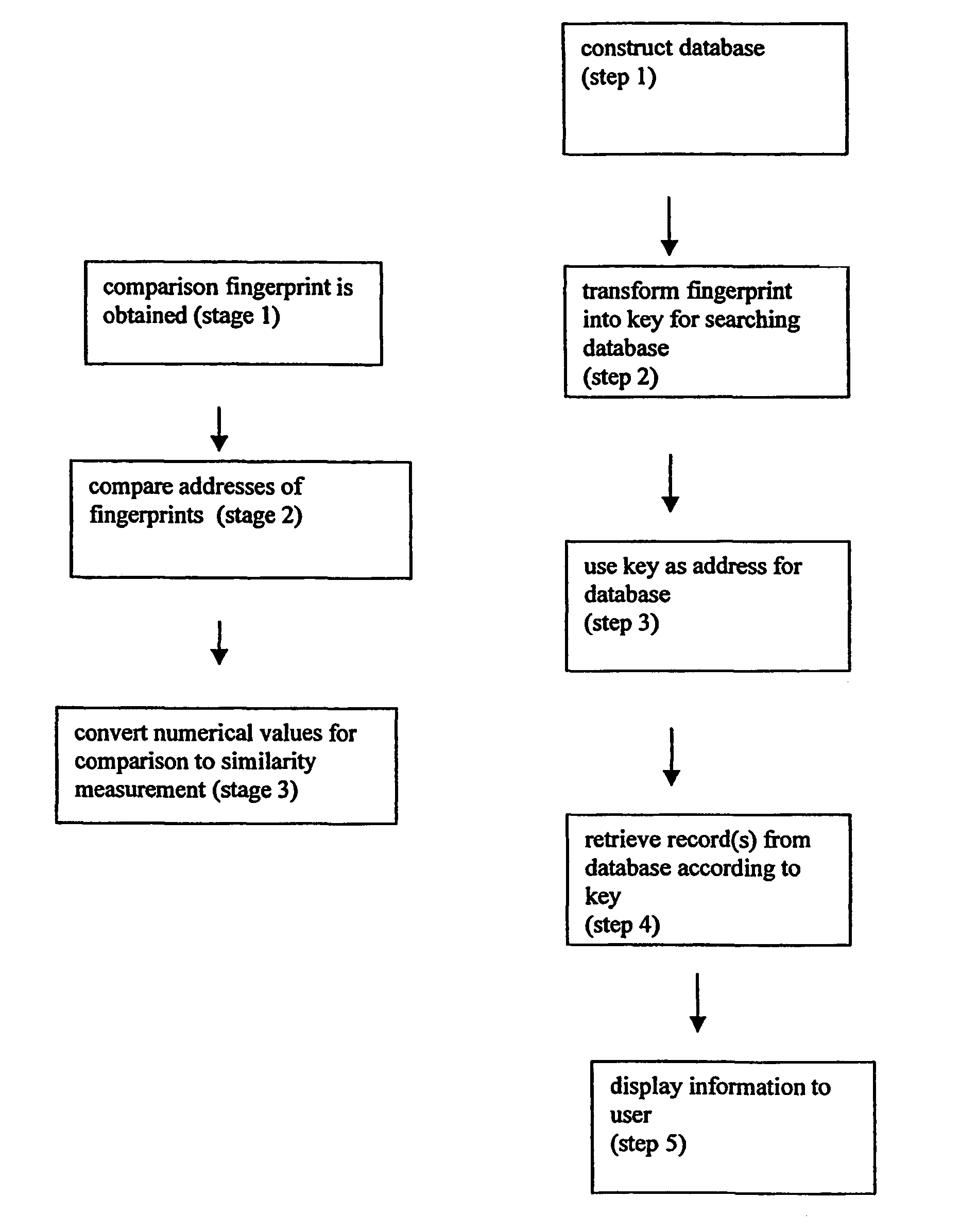
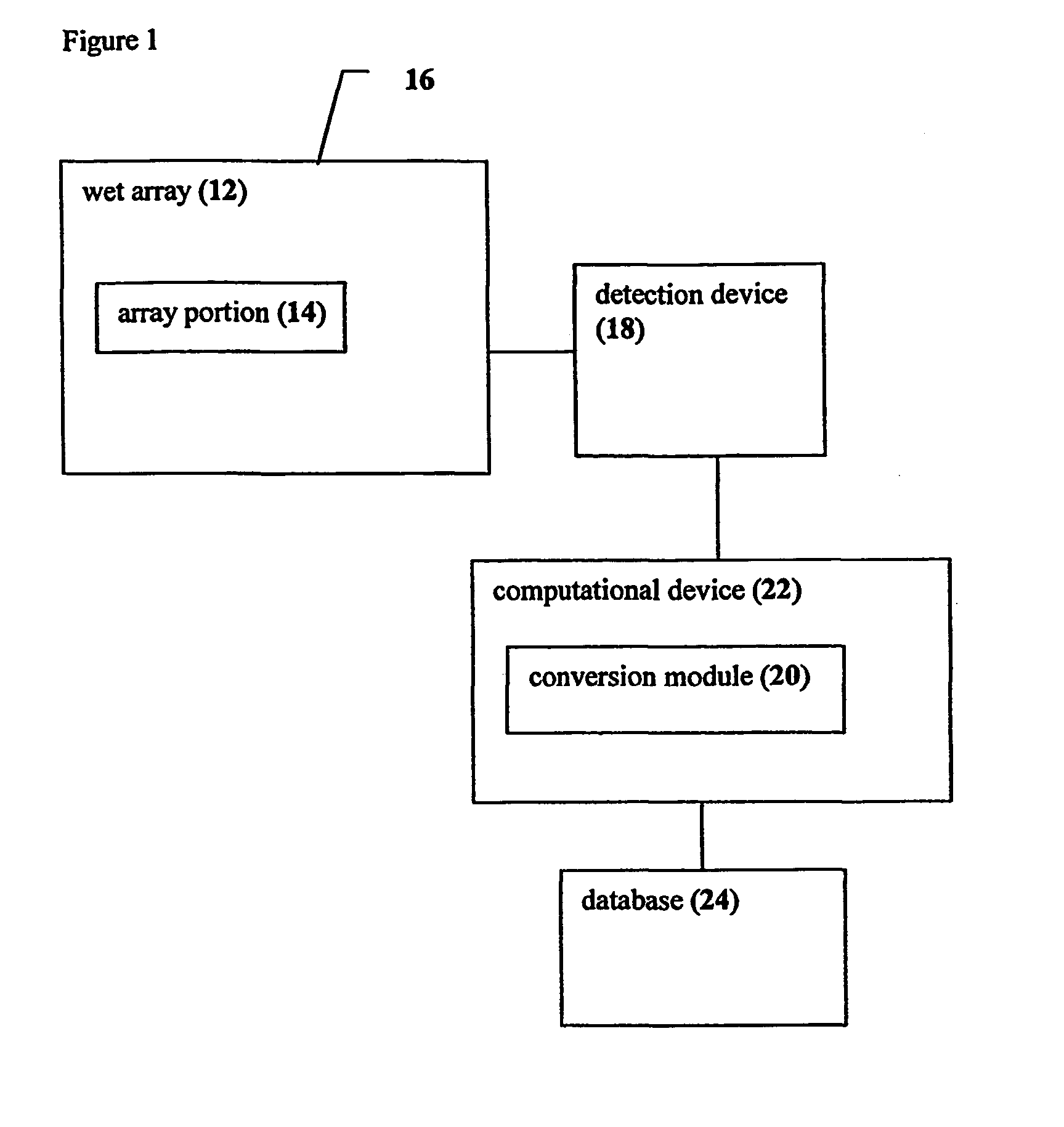
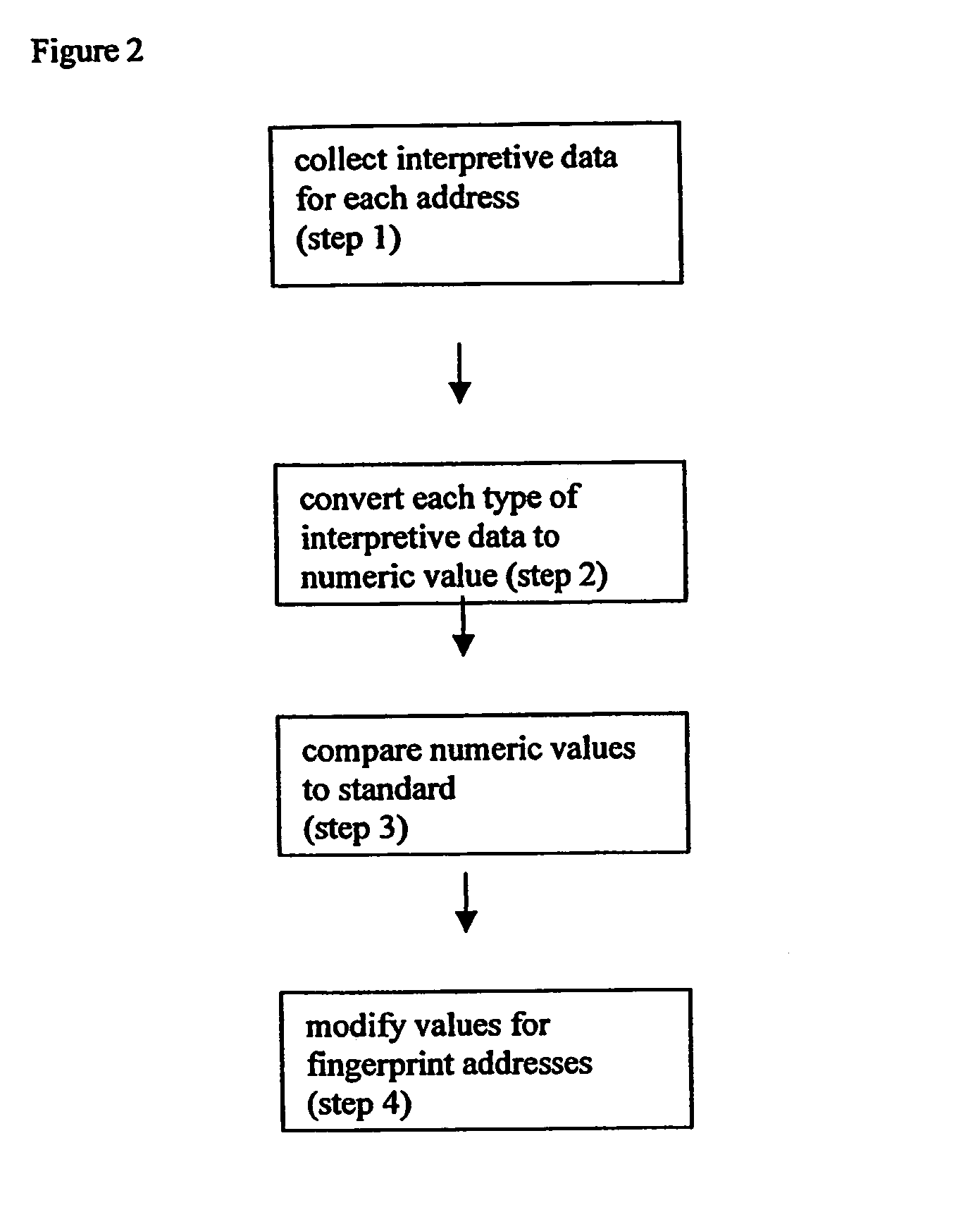
In mathematics, a combinatorial explosion is the rapid growth of the complexity of a problem due to how the combinatorics of the problem is affected by the input, constraints, and bounds of the problem. Combinatorial explosion is sometimes used to justify the intractability of certain problems. Examples of such problems include certain mathematical functions, the analysis of some puzzles and games, and some pathological examples which can be modelled as the Ackermann function.
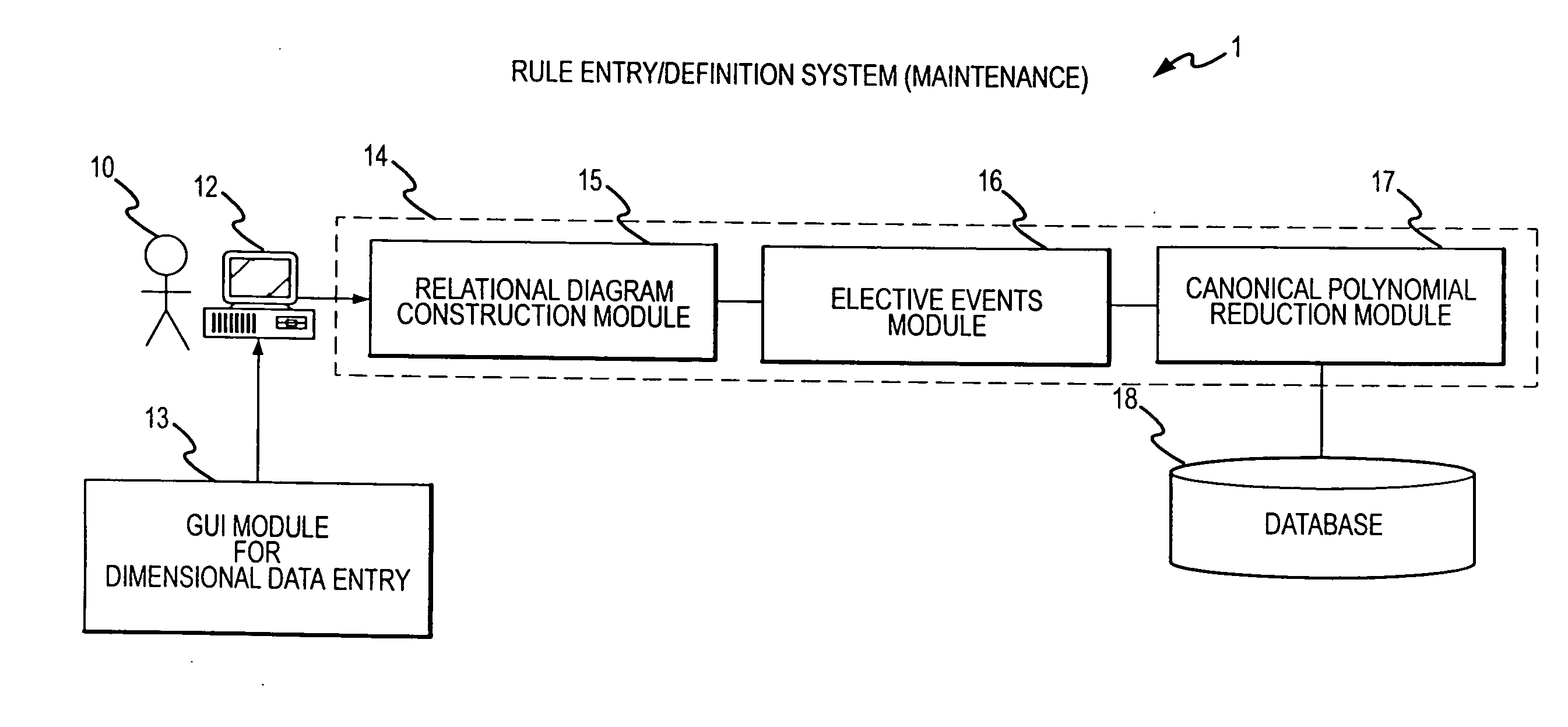
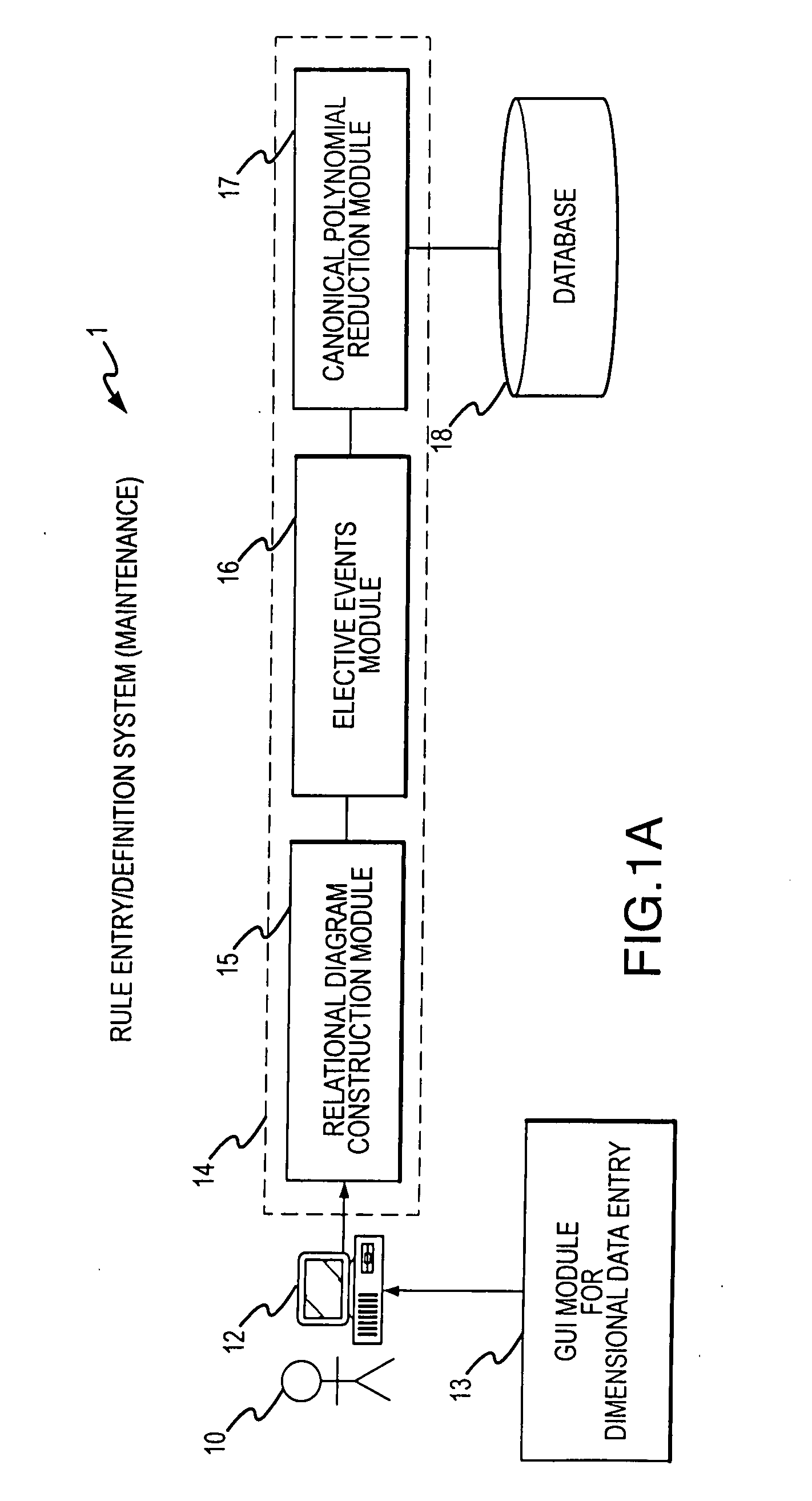
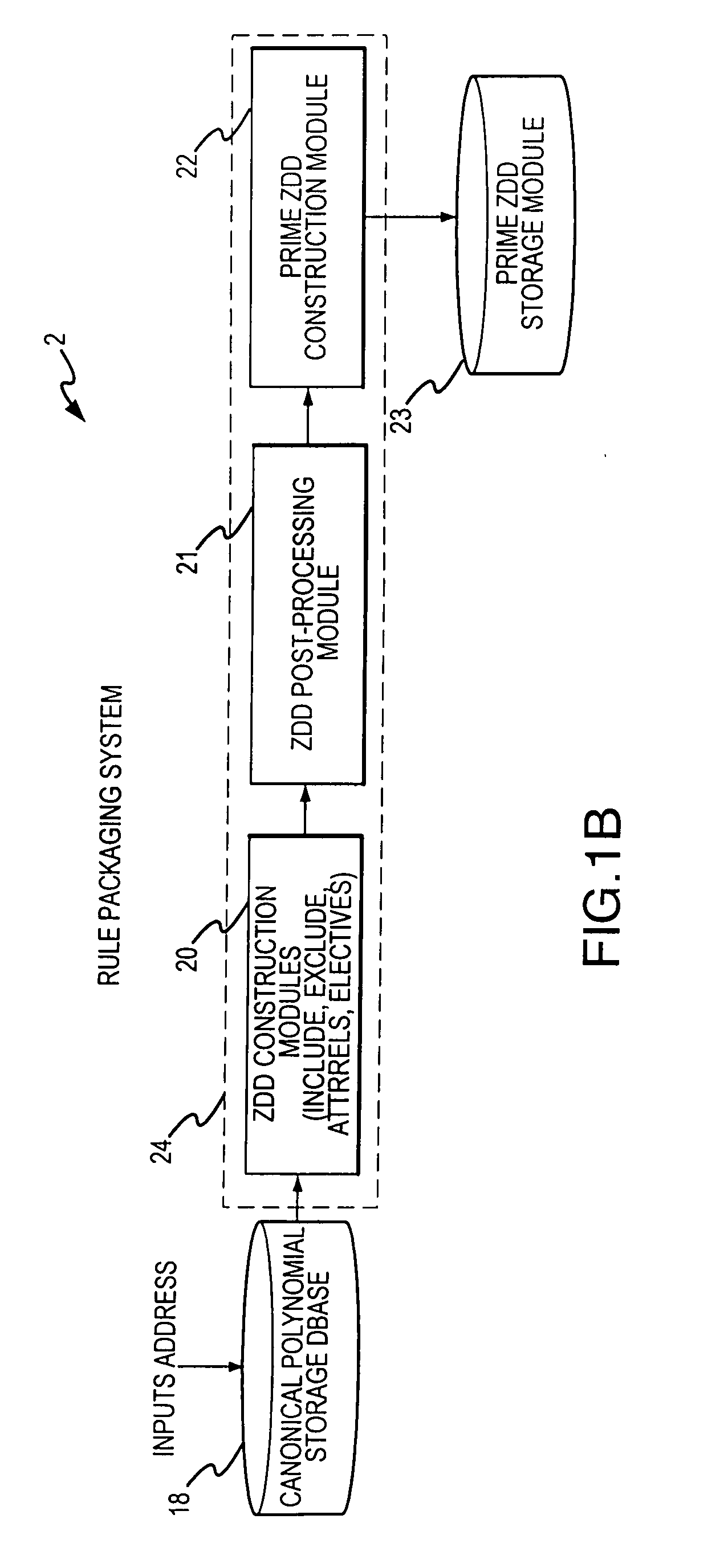
Rule processing system
InactiveUS20070150429A1Exceeding computational capacity of computingDigital data processing detailsDigital computer detailsPresent dayUser input
A rule processing apparatus includes modules for defining / entering attributes, enumerations, and / or relationships; packaging the definitions in a reduced canonical form suitable for propositional logic manipulation using zero-suppressed binary decision diagrams (Zdd) to produce a prime Zdd; and / or (iii) executing the rule by applying a series of user inputs to the prime Zdd to determine a result that preferably includes conflict and selection advice to guide the user to satisfaction. Elective events, such as but not limited to the display of messages or the performance of calculations, may optionally be packaged along with the prime rule or components thereof, and presented during execution to help guide the end user to satisfaction or compliancy when choosing among possible selections. The apparatus automates determination of a complex rule having a combinatorial exploded number of rule components, or a combinatorial number of possible outcomes, exceeding computational capacity of present day computing systems.
Owner:MINERAL LASSEN
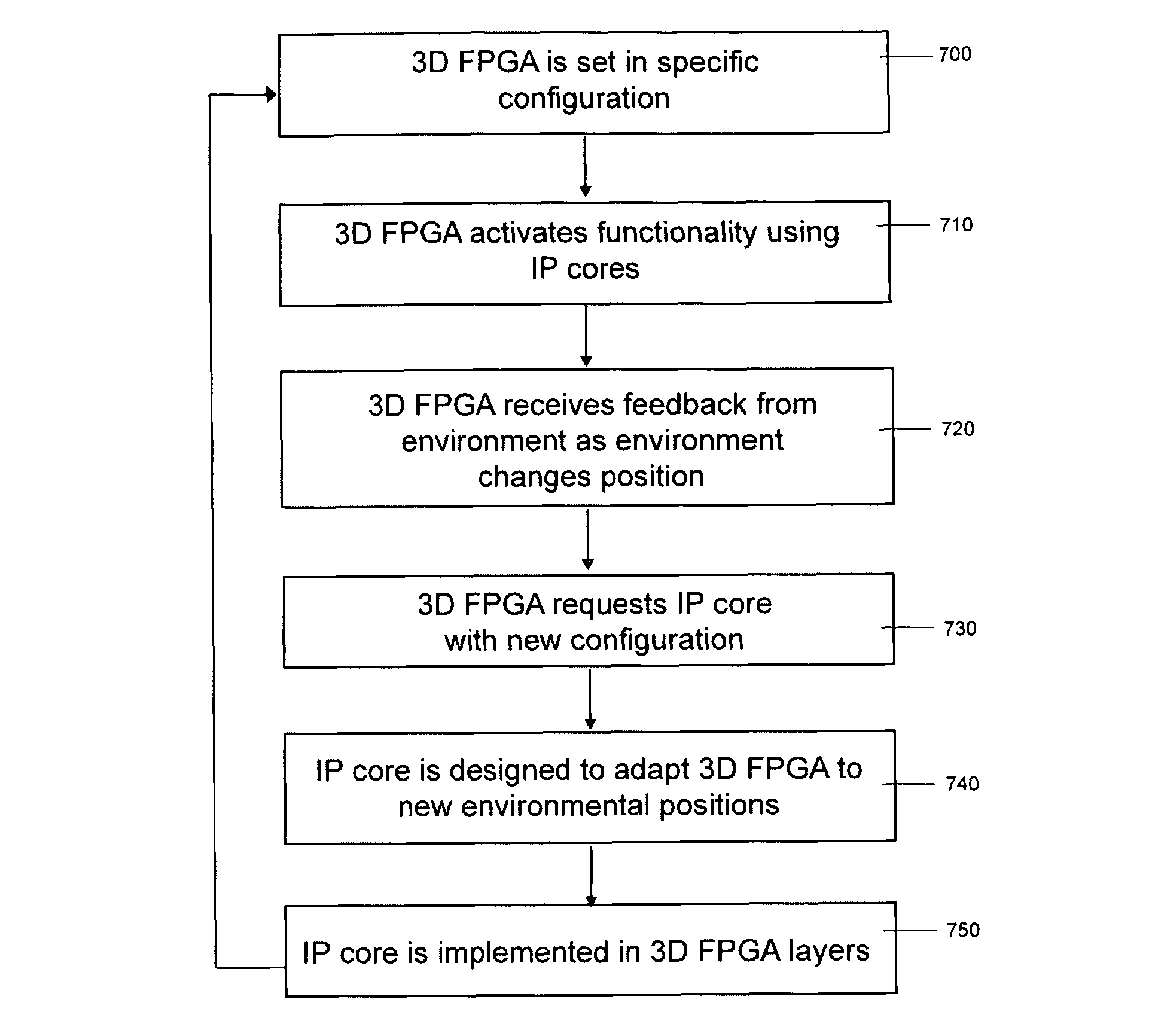
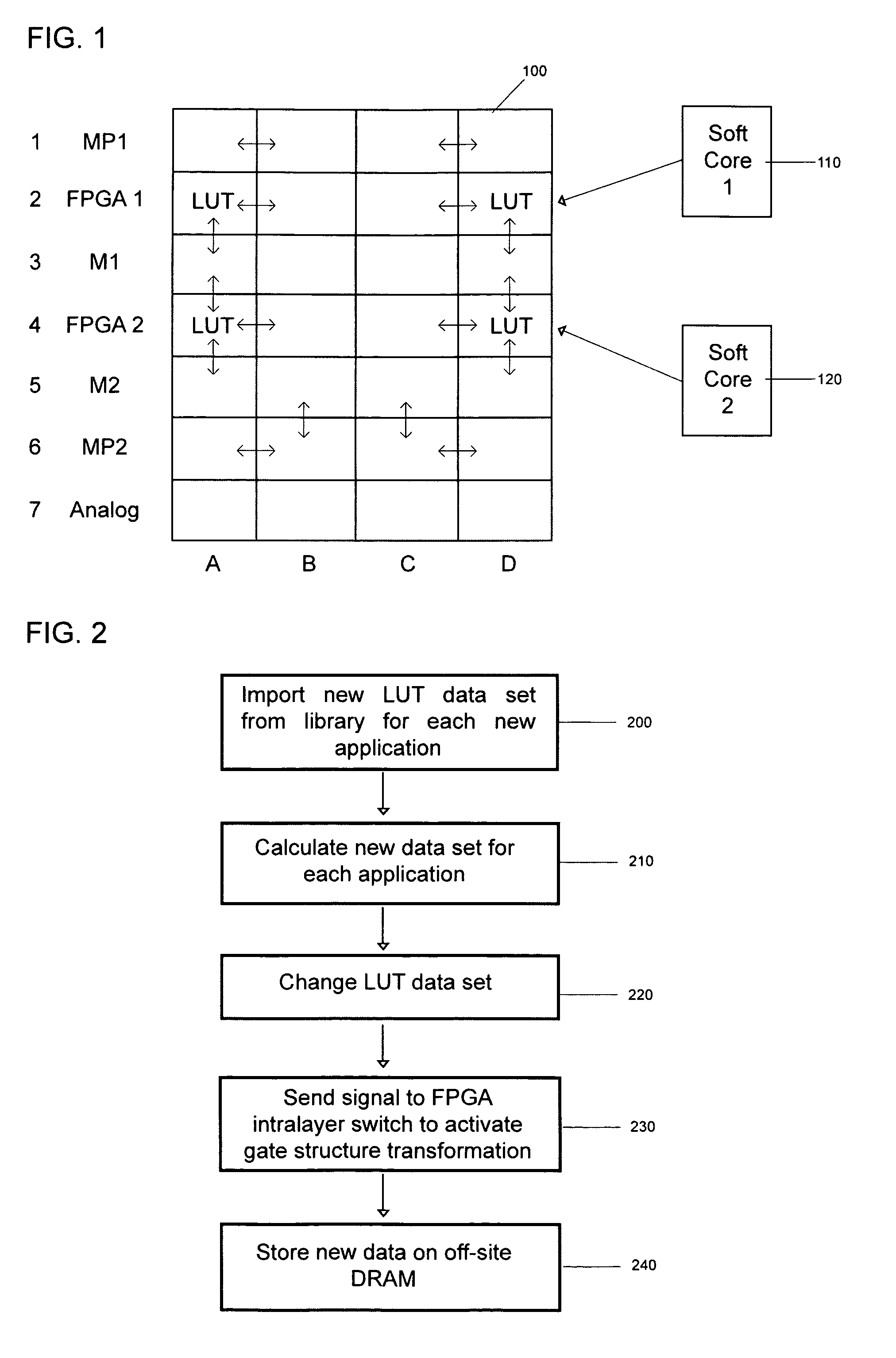
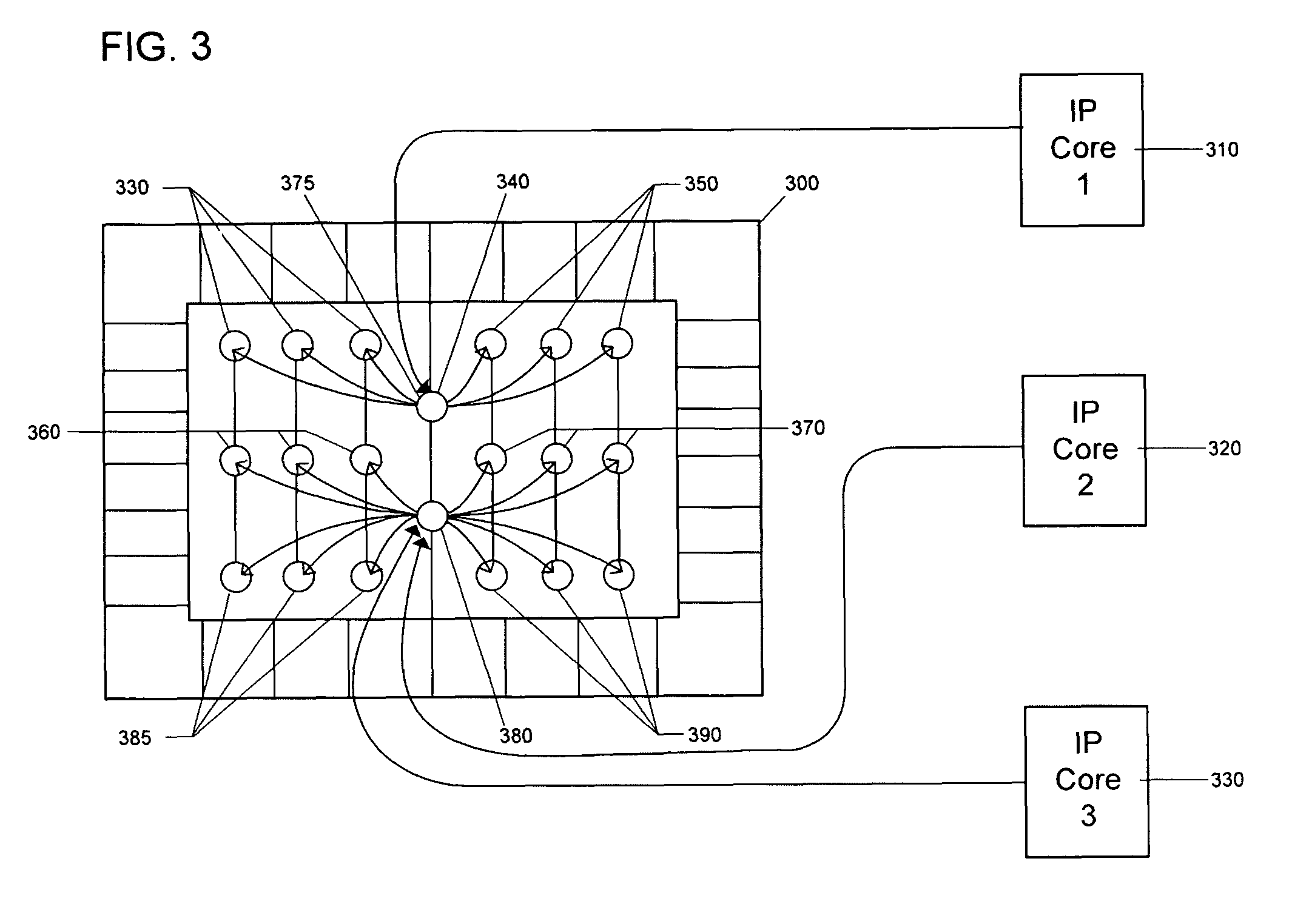
IP cores in reconfigurable three dimensional integrated circuits
InactiveUS8046727B2Extensive resourcesIncrease flexibilitySolid-state devicesComputer programmed simultaneously with data introductionEvolvable hardwareNetlist
The invention describes IP cores applied to 3D FPGAs, CPLDs and reprogrammable SoCs. IP cores are (a) used for continuously evolvable hardware using 3D logic circuits, (b) applied with optimization metaheuristic algorithms, (c) applied by matching combinatorial logic of netlists generated by Boolean algebra to combinatorial geometry of CPLD architecture by reaggregating IP core elements and (d) used to effect continuous recalibration of IP cores with evolvable hardware in indeterministic environments for co-evolutionary reprogrammability.
Owner:SOLOMON RES
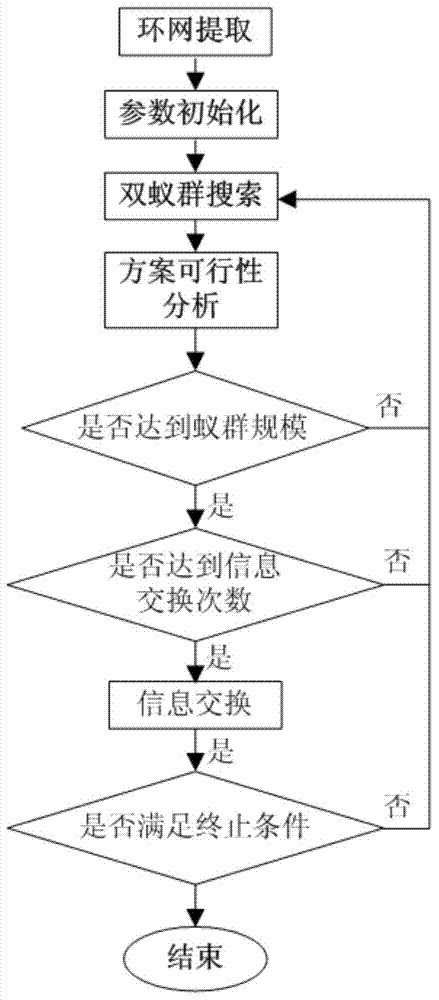
Method for reconstructing power distribution network based on double-ant-colony optimization
InactiveCN103903062AReduce digitsOvercoming the problem of being easily trapped in local minimaForecastingBiological modelsIslandingInterconnection
The invention relates to a method for reconstructing a power distribution network based on double-ant-colony optimization. The method comprises the steps of extracting a looped network, initializing parameters, searching for double ant colonies, decoding a path where each set of ants walks through, obtaining the reconstruction scheme of the power distribution network, conducting looped network detection, island detection and constraint condition detection, judging feasibility of the scheme, judging whether the number of two sets of the ants reaches the ant colony scale or not, judging whether the frequency of information exchange is achieved or not, conducting information exchange, judging whether the terminal condition is met or not, and ending and obtaining the optimum power distribution network reconstruction scheme. The deep searching method is adopted, the reconstruction of the looped network of the power distribution network on a looped network upper interconnection switch and a section switch is determined, digits participating in switch reconstruction are reduced, the problem that when the switch combinatorial dimension in the power distribution network is higher, the searching recovery scheme faces combinatorial explosion is effectively solved, the calculated amount is reduced, and the optimum speed is improved.
Owner:STATE GRID CORP OF CHINA +1
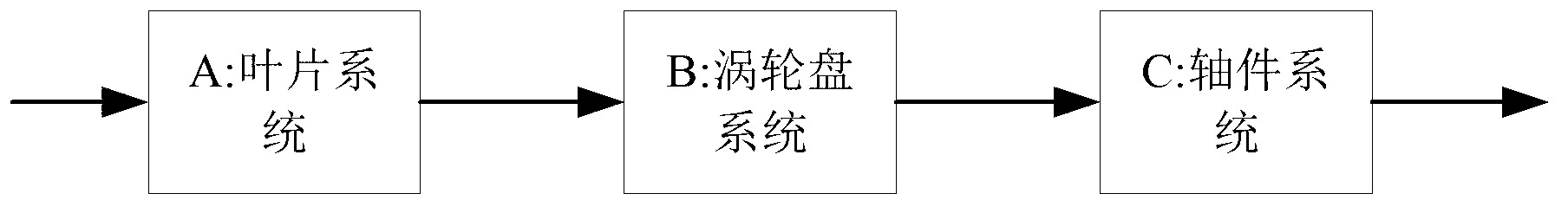
Method for analyzing reliability of turbine blade disk system of aircraft engine
InactiveCN103268388AOvercoming complexityOvercome efficiencySpecial data processing applicationsFailure rateAviation
The invention discloses a method for analyzing reliability of a turbine blade disk system of an aircraft engine. The method comprises the following steps of: establishing a system chart; establishing a system dynamic bayesian network and a system failure-mode dynamic bayesian network model; discretizing and transforming the dynamic bayesian network into multiple static bayesian networks; structurally decomposing the static bayesian networks into simply-connected regional networks and multiply-connected regional networks; performing bidirectional derivation on the simply-connected regional networks by a static bayesian network inference method; and performing bidirectional derivation on the multiply-connected regional networks by a bucket elimination method to respectively solve the failure rate of the turbine blade disk system, namely a system element, of the aircraft engine, and the fault rate of each failure mode. According to the method for analyzing the reliability of the turbine blade disk system of the aircraft engine, the problems of complicated expression, low computational efficiency, combinatorial explosion and the like, which are caused when traditional reliability analyzing methods are used for analyzing large-scaled, complicated and dynamic structures, are solved, and the computational efficiency is enhanced.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
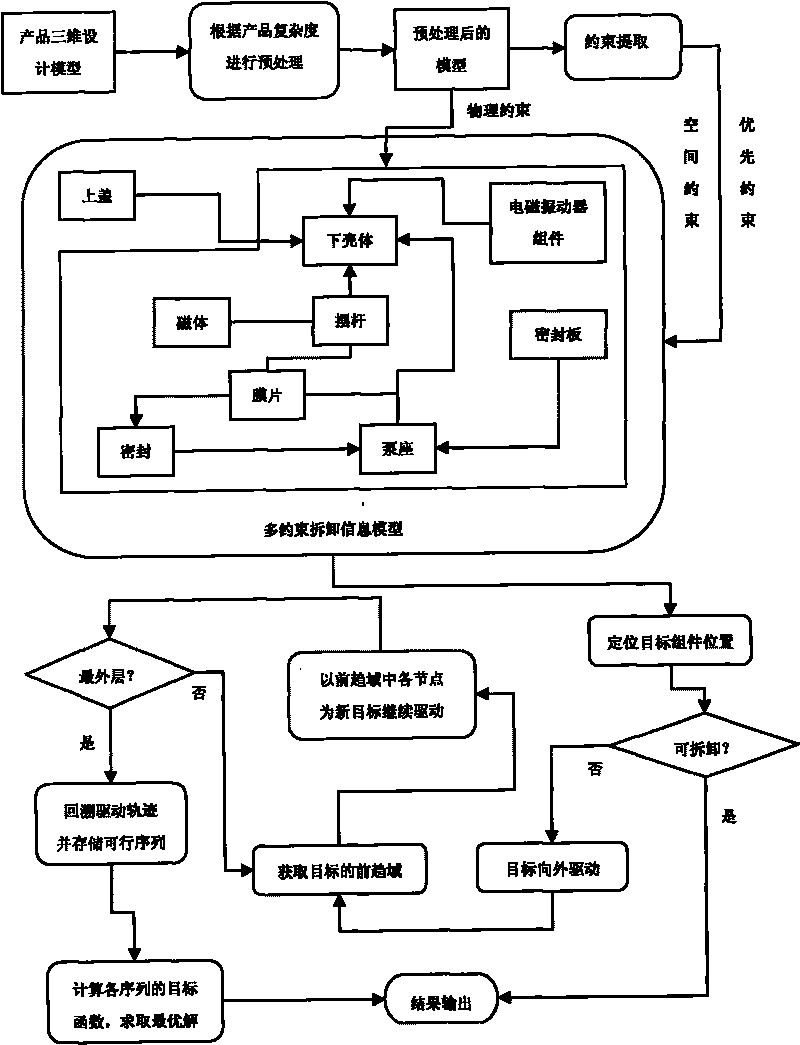
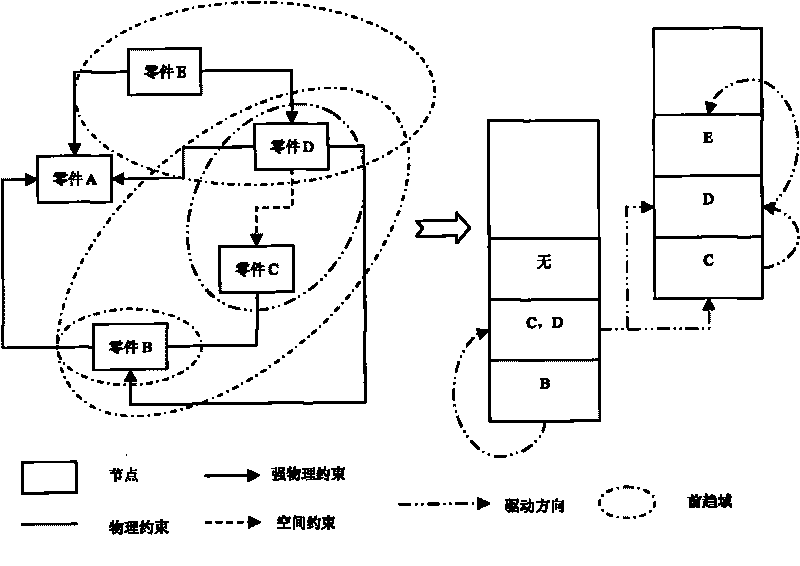
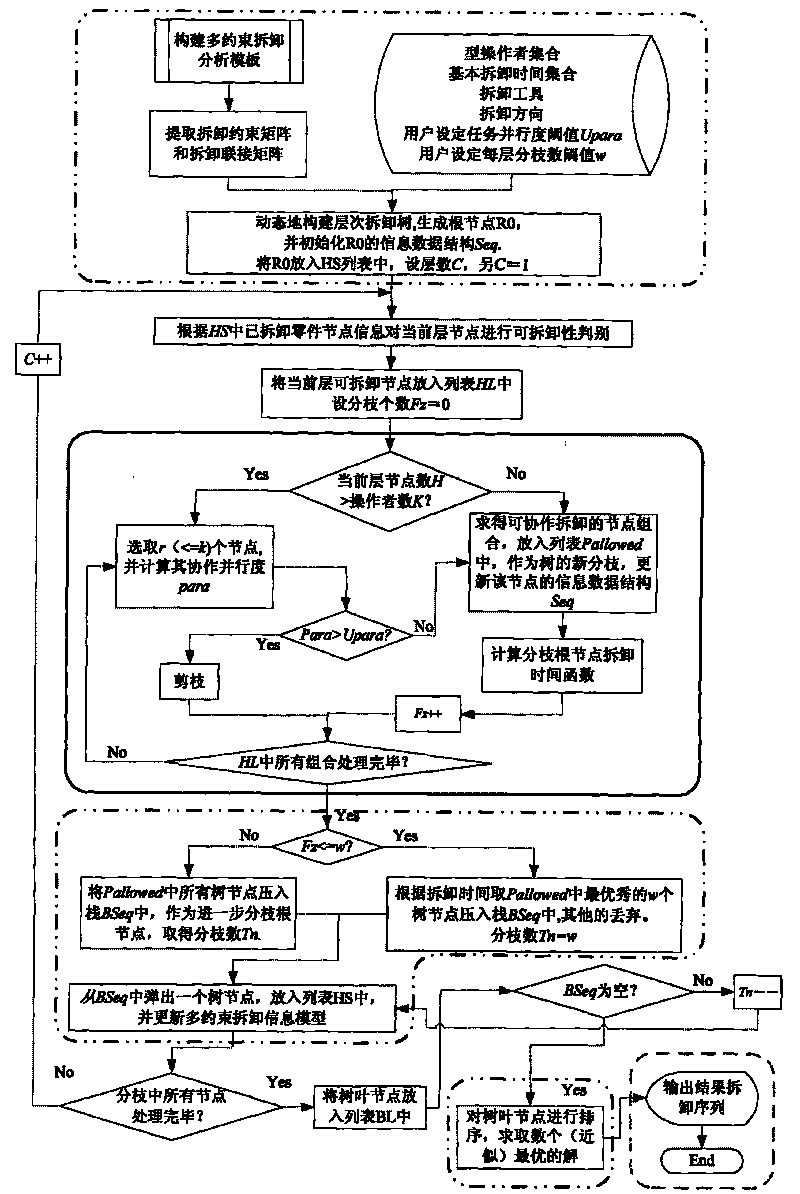
Method for planning destination and cooperation disassembly of complex product supporting green design
InactiveCN101706895ARealize automatic solutionOvercoming the "Combination Explosion" ProblemResourcesComputer scienceInformation model
The invention discloses a method for planning the target and cooperation disassembly of a complex product supporting green design, which comprises the following steps: for the characteristics of detachable design in the green design, extracting assembly semantic constraints and disassembly priority constriction information between product components to construct a multi-constraint disassembly information model; performing matrix quantization on the information model, decomposing the information model into a plurality of single-constraint matrixes and inducing detachability constraint conditions; taking a disassembled component as a driving point to obtain a target disassembly sequence through two-way driving; and for the requirement that the large-scale complex product needs parallel disassembly, putting forwards a cooperation display planning problem and an adaptive resolution method. Through the method, the target and cooperation disassembly sequence of the complex product can be quickly obtained and the problem that 'combination explosion' is easy to occur in the conventional method is solved. The cooperation disassembly planning problem and the adaptive resolution method put forwards in the invention overcome the defect that the prior method is only applied to single-operator disassembly and realize the adaptive adjustment in a disassembly planning process.
Owner:ZHEJIANG UNIV
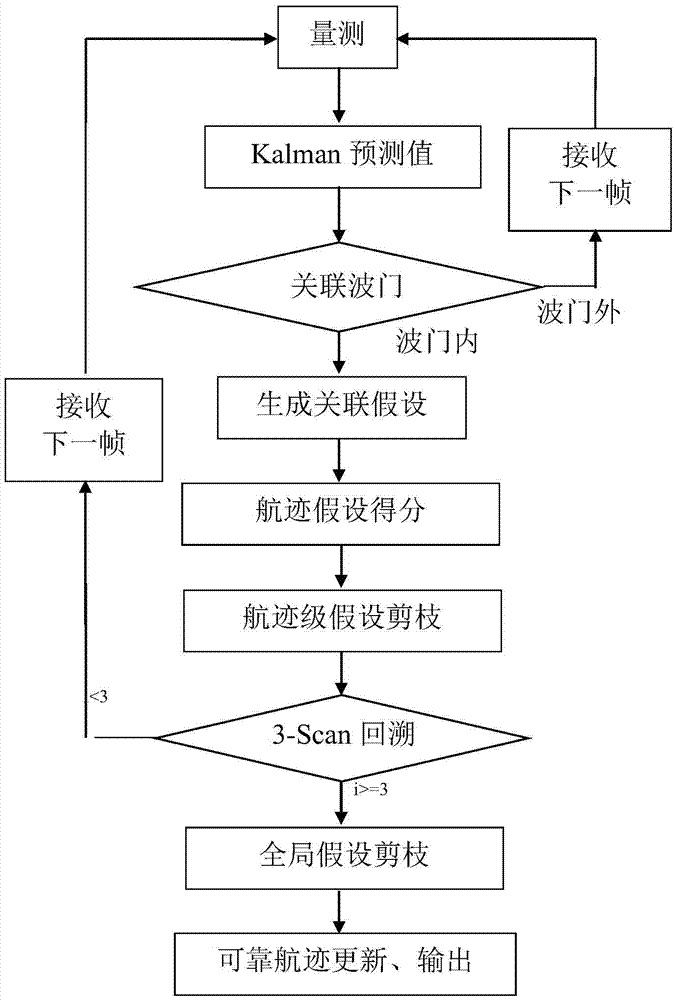
Radar data association method based on simplified multi-hypothesis algorithm
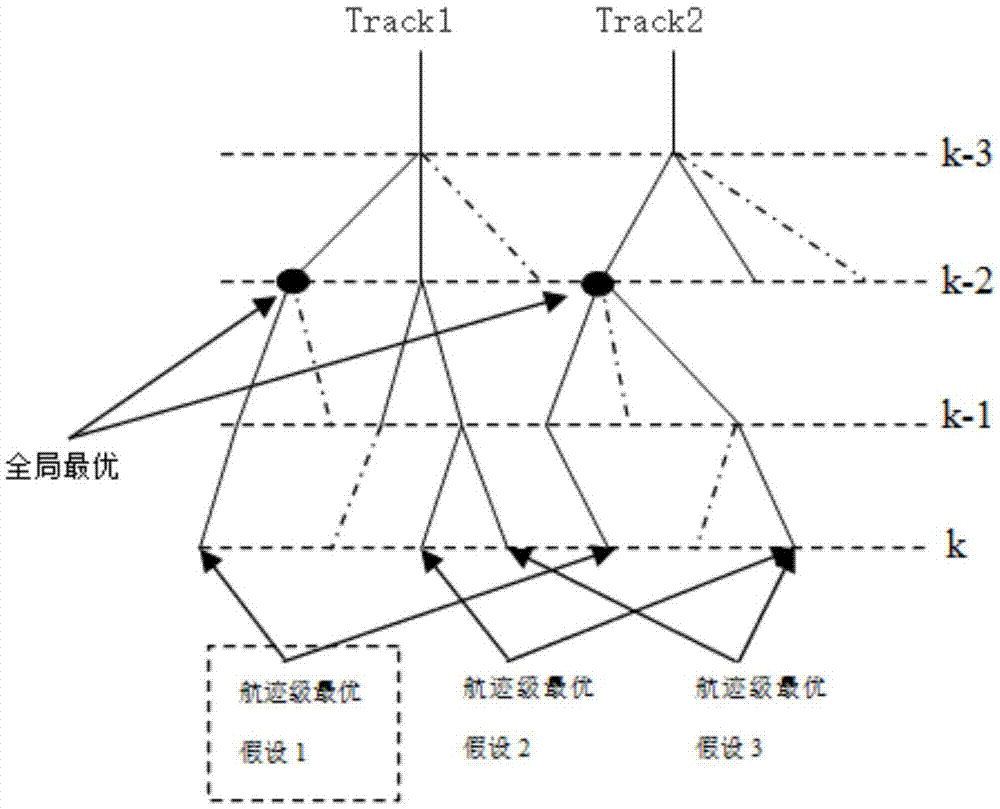
InactiveCN106934324AAccurate trackingReduce computational complexityCharacter and pattern recognitionHypothesisMultiple hypothesis
The invention provides a radar data association method based on a simplified multi-hypothesis algorithm. In view of problems of combination explosion and calculation amount exponential rising caused by a delay decision making mechanism of the traditional multi-hypothesis algorithm in a multi-target tracking system, a likelihood ratio scoring function and a linear distribution (LAP) pruning method are introduced, a track association logarithm likelihood ratio is used for simplifying hypothesis association probability calculation, M optimal hypothesis at the current moment is obtained through LAP algorithm track level pruning, through further global level hypothesis pruning, an optimal hypothesis matching sequence is obtained quickly as an effective association measurement point, and the purpose of reducing the calculation amount finally is realized. The method particularly comprises three main steps of track scoring calculation based on the likelihood ratio function, LAP-based track level M-optimal hypothesis pruning and LAP-based global level optimal hypothesis generation. By using the method provided by the invention, on the basis of ensuring the association accuracy, the calculation amount during a multiple hypothesis algorithm data association process can be reduced to a large degree.
Owner:NANJING UNIV OF SCI & TECH
Electric power multi-source information fault positioning and pre-judging method
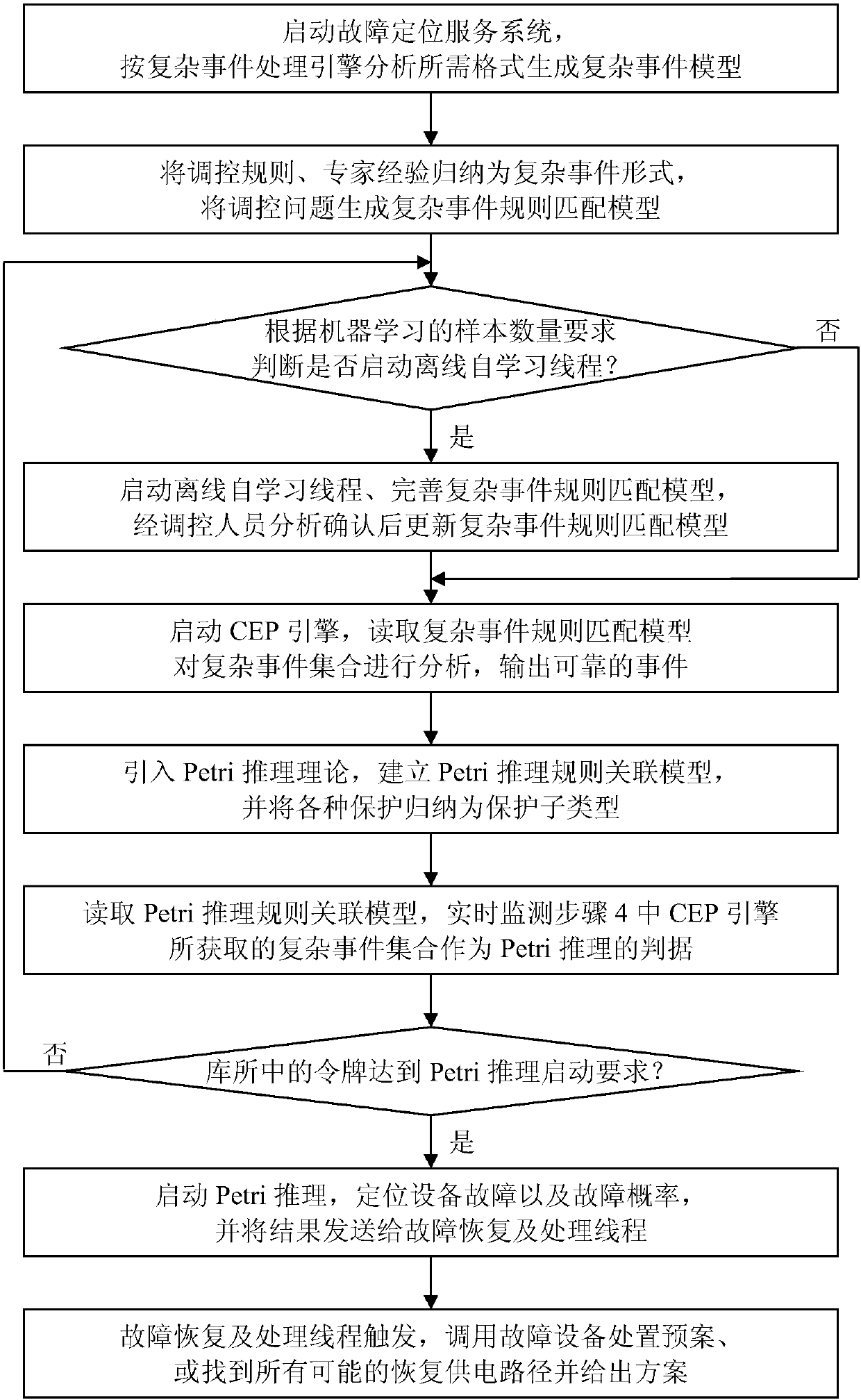
ActiveCN107944657AFast aggregationImprove accuracyResourcesComplex event processingAssociation model
The invention discloses an electric power multi-source information fault positioning and pre-judging method. The electric power multi-source information fault positioning and pre-judging method comprises the steps of: 1, generating a complex event model in a format required by complex event processing engine analysis; 2, summarizing expert experiences as a complex event form, and inputting regulation and control problems to generate a complex event rule matching model; 3, determining whether to start an offline self-learning thread; 4, outputting reliable events; 5, establishing a Petri inference rule association model; 6, reading the Petri inference rule association model in a Petri inference thread, and monitoring complex event sets in real time; 7, and triggering a fault recovery and processing thread, directly calling a disposal plan or finding all possible power supply recovery paths, and providing a scheme. The electric power multi-source information fault positioning and pre-judging method ensures the rapid aggregation and accuracy of electric power complex events, mitigates the combinatorial explosion problem of Petri fault inference, processing item omitted reporting caused by identification protection, switch rejection action and maloperation as well as communication problem by means of a CEP engine, simplifies the complexity of the Petri inference process, and positions the faulty equipment quickly by means of the Petri inference rules and diagnostic models.
Owner:STATE GRID SHANDONG ELECTRIC POWER +1
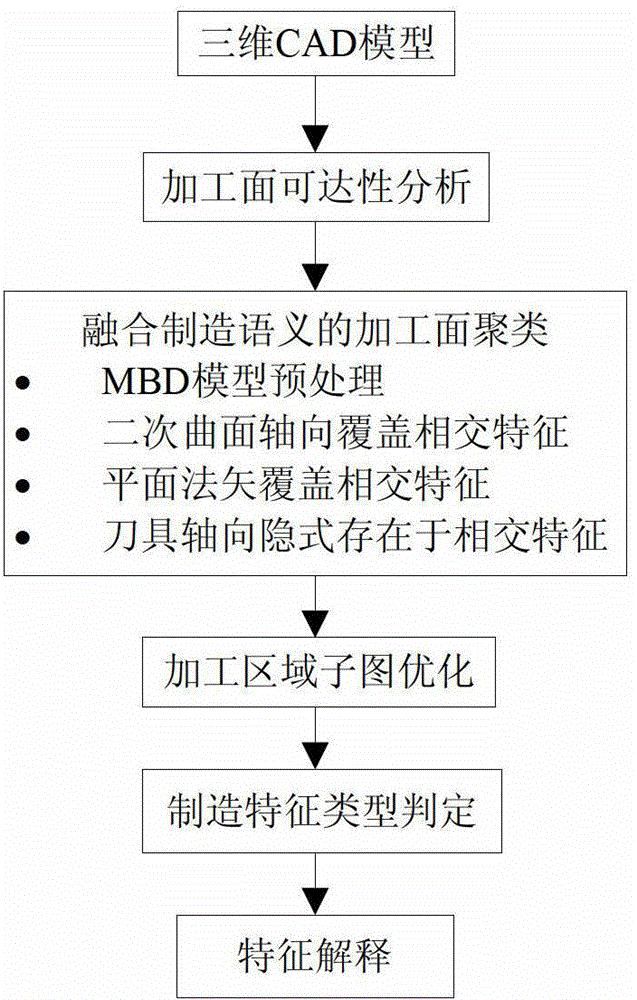
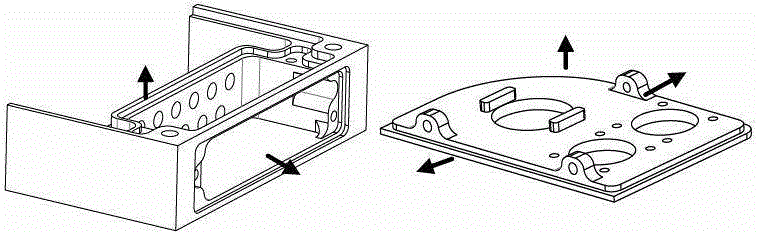
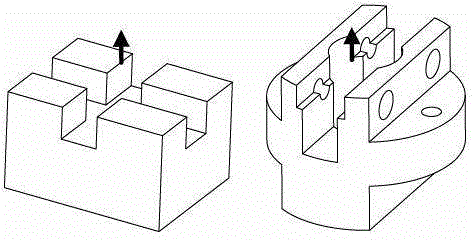
Identification method for three-dimensional computer-aided design (CAD) model intersection manufacture characteristics
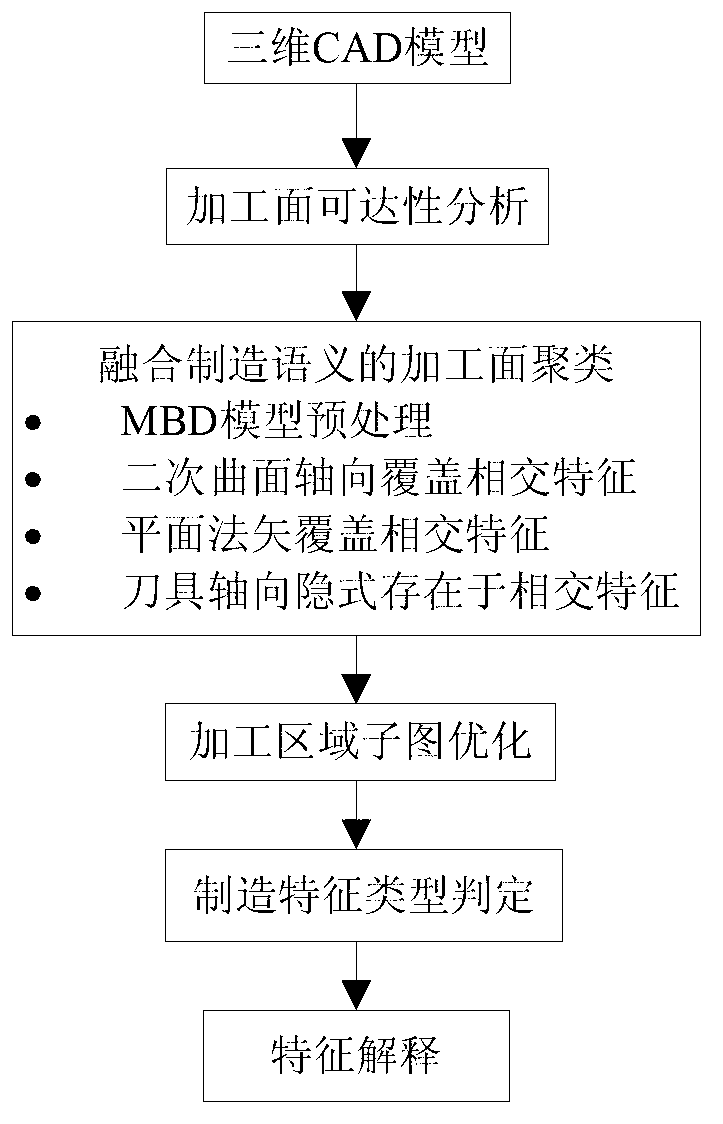
InactiveCN103164582AMeet manufacturability requirementsMeet the requirements of process designSpecial data processing applicationsCluster algorithmComputer Aided Design
The invention discloses an identification method for three-dimensional computer-aided design (CAD) model intersection manufacture characteristics. The identification method for the three-dimensional CAD model intersection manufacture characteristics is used for solving the technical problem that a combinatorial explosion exists in an existing part manufacturability automatic analysis method in a process that an optional solution is generated. According to the technical scheme of the identification method for the three-dimensional CAD model intersection manufacture characteristics, a three-dimensional CAD model expressed by model based definition (MBD) is used as an information input source, firstly a reachability analysis is conducted on each machined face through an illumination-type rule, and the axial space of a feasible cutter of each machined face is ascertained; then with the axial space of the feasible cutter of each machined face as a restraint, a machined face clustering algorithm merging a manufacture semanteme is adopted to construct each of machined area subgraphs; and finally, with each machined area subgraph as a manufacture characteristic trace which is combined together with dimensioning information, the machined area subgraphs are optimized and merged, so that identification of the manufacture characteristics is achieved. According to the identification method for the three-dimensional CAD model intersection manufacture characteristics, the manufacturability analysis is merged in the identification process of the intersection manufacture characteristics, so that the machined faces are identical in the accuracy level. In the characteristic identification process, the influence, on the characteristic identification, of the design semanteme is fully considered and practicality is improved.
Owner:NORTHWESTERN POLYTECHNICAL UNIV
Product assembly representation method based on engineering connection relationship
InactiveCN102129494AAssembly Design Solver ValidAvoid Combinatorial Explosion SituationsSpecial data processing applicationsSystems designComputer-aided
The invention discloses a product assembly representation method based on engineering connection relationship, i.e. a product assembly modeling method which is applied to the development of a computer aided assembly design system, especially applied to the development of to a CAD (Computer Aided Design) system. In the method, the engineering connection relationship serves as a principal line represented by assembly knowledge and assembly models; a product and parts are represented by a generalized ring method according to the engineering connection relationship to form an engineering connection drawing, namely a product assembly model, thus, the connection composition relationship of the product is represented on an engineering connection level; and meanwhile, geometry information or other non-geometry information can be represented on a lower level because information is added on a related knot, thereby expressing production assembly information more integrally. The method can be suitable for the requirements of assembly design, such as product assembly structure design, assembly sequence planning, assembly system design and the like, so that the assembly design can be solved more effectively, and especially, the phenomenon of combinatorial explosion can be effectively avoided during assembly sequence planning.
Owner:HUAZHONG UNIV OF SCI & TECH
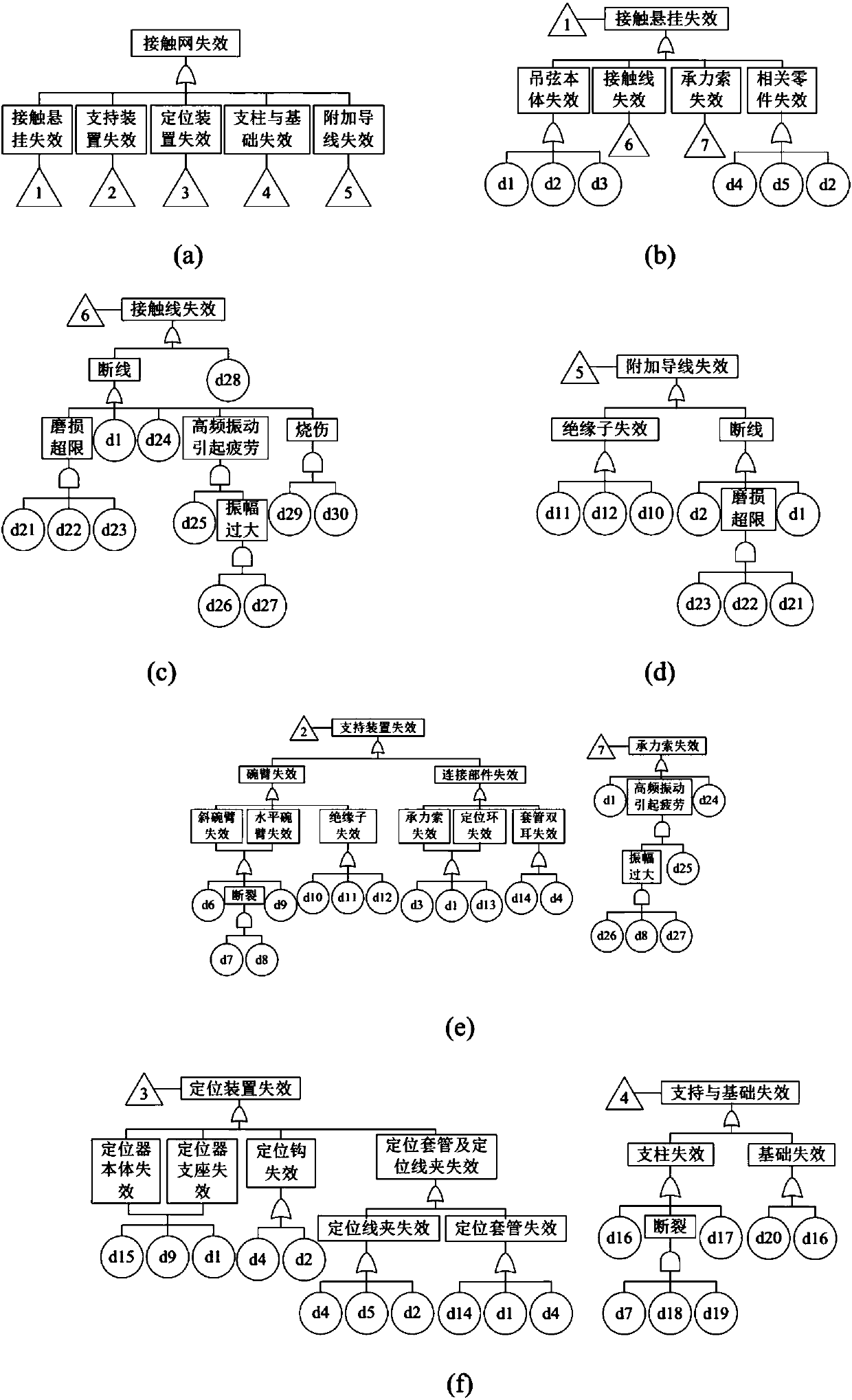
Contact network failure risk assessment method based on binary decision graph algorithm
PendingCN108596511ASolving combinatorial explosionsSolve complexityResourcesComplex mathematical operationsContact networkDecision graph
The invention discloses a contact network failure risk assessment method based on a binary decision graph algorithm, comprising the steps of: (1) generating a BDD structure, determining system boundaries, basic events and top events, establishing and normalizing a fault tree, and generating a BDD structure, wherein the corresponding BDD nodes may be directly created by ITE operations for basic events; and ITE operations may be performed on basic events or other intermediate events to obtain the BDD structure of the original intermediate event for intermediate events; (2) calculating the accident rate of the contact network failure risk, generating a Boolean logic expression by the fault tree, and generating a Boolean logic function corresponding to the fault tree top event, wherein when the true value is obtained, the probability of occurrence of the top event or any intermediate event may be obtained; and (3) measuring the event importance. The invention applies the BDD method to thefailure risk assessment of the contact network, which simplifies the calculation process, and solves the problems such as the combined explosion and the complicated solving process encountered by thecut set method in the contact network failure fault tree analysis.
Owner:CHINA RAILWAYS CORPORATION +1
System and method for integrated analysis of data for characterizing carbohydrate polymers
A system and method for characterizing carbohydrate polymers according to maps obtained from experimental data. Preferably, the data is obtained from a plurality of different types of experimental assays for characterizing the carbohydrate polymer. More preferably, at least one such assay involves binding a saccharide-binding agent to the carbohydrate polymer. One or more features of the carbohydrate polymer are then preferably characterized. These features are preferably derived from maps of the data obtained from assays involving the sample carbohydrate polymer. These maps are more preferably analyzed at a plurality of levels, with each level providing more abstract biological information. Most preferably, new types of experimental data are introduced to the process of analysis at each level, in order to support more complex analyses of the data. Optionally and most preferably, maps are eliminated at each level as being inconsistent with the experimental data. New maps are most preferably added at a higher level only if they are derived from the new experimental data which has been introduced at that level, in order to prevent a combinatorial explosion at successive levels of data analysis.
Owner:PROCOGNIA ISRAEL
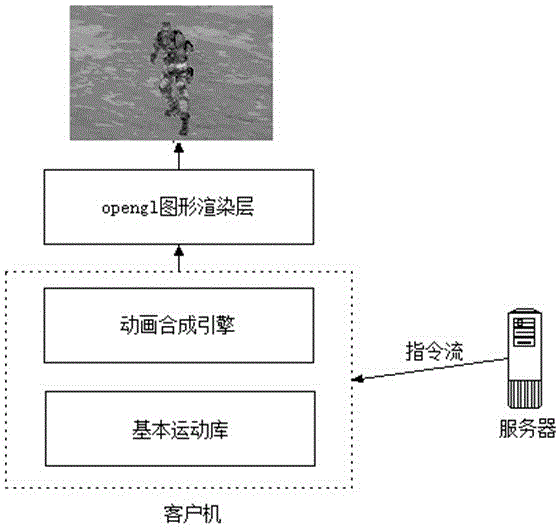
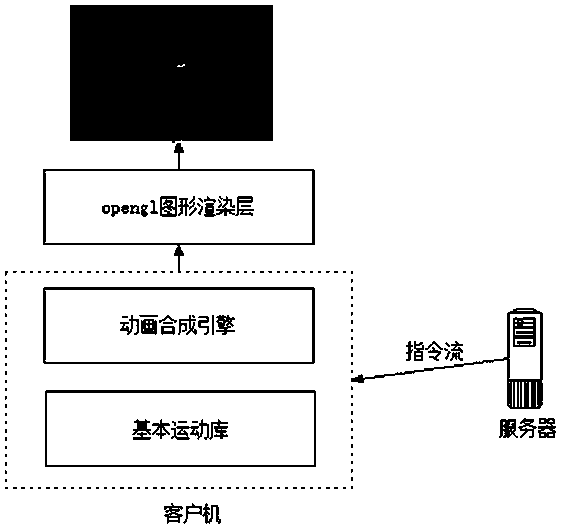
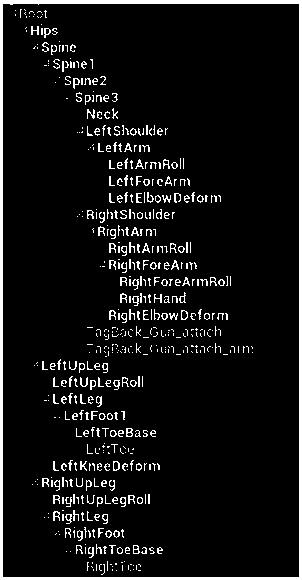
Command stream based three-dimensional character animation synthesis method
ActiveCN106548503AAvoiding Combinatorial Explosion ProblemsSmooth motion switchingAnimationData streamSynthesis methods
The invention discloses a command stream based three-dimensional character animation synthesis method. The method comprises the steps of firstly performing classified description on character action models according to moving states, whole body postures and upper body postures; prefabricating specific three-dimensional animation files according to a combination relation table of action classification; building a distributed client / server network model, and formulating protocol specifications for datagram transmission; and searching the combination relation table of action combination by a client after parsing a command data stream transmitted by a server, acquiring relevant action files, and synthesizing a new animation sequence after performing motion blending and performing interpolation on the location and the orientation of a character. According to the invention, automatic switching between difference actions of virtual soldiers in a virtual battlefield environment can be reproduced authentically, smooth interpolation update of the position and the orientation of virtual characters is supported at the same time, a problem of combination explosion between the tedious command control process and actions is avoided, action switching is performed smoothly and naturally, and the method can be widely applied to various virtual battlefields. Therefore, the command stream based three-dimensional character animation synthesis method has a certain application value.
Owner:EAST CHINA NORMAL UNIV
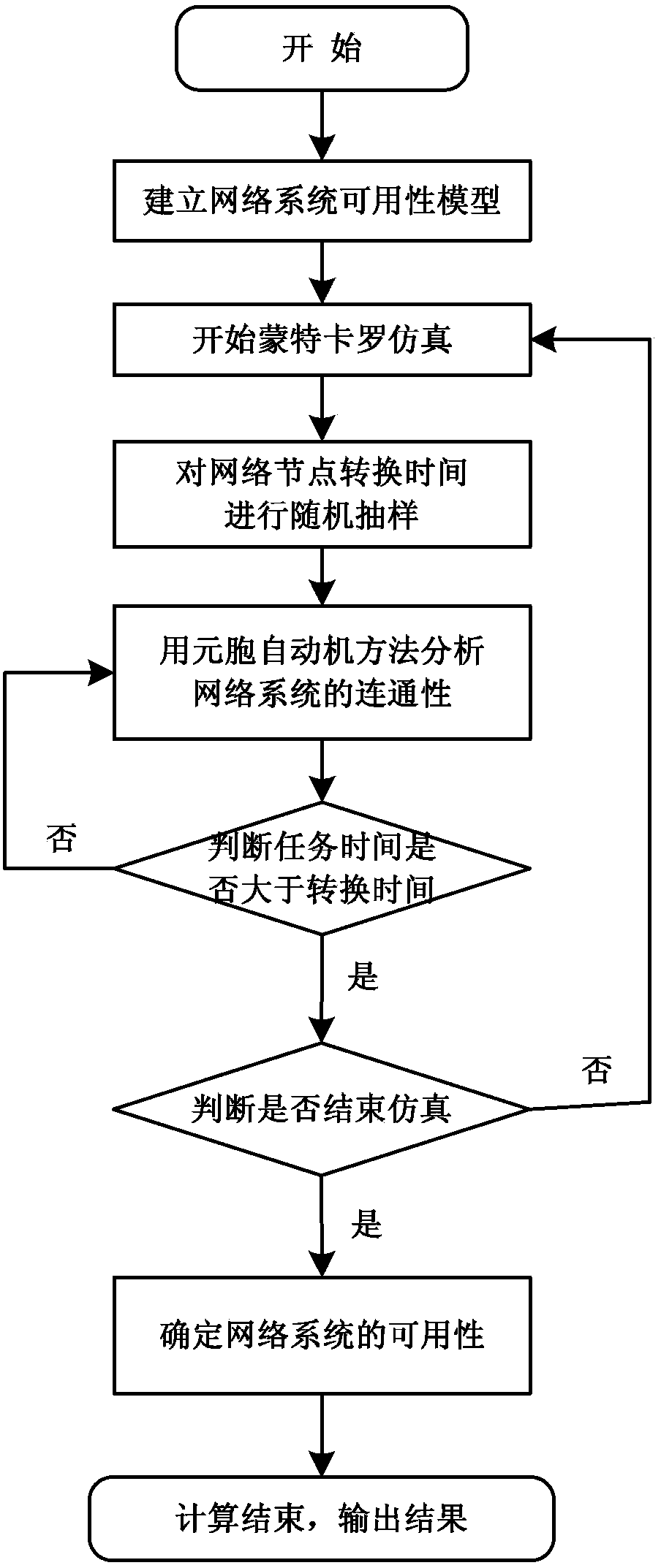
Complex system availability determination method based on cellular automaton
ActiveCN103501235AAvailability determinedSmall amount of calculationData switching networksCellular automationFunctional Relationship
Owner:CHINA AEROSPACE STANDARDIZATION INST
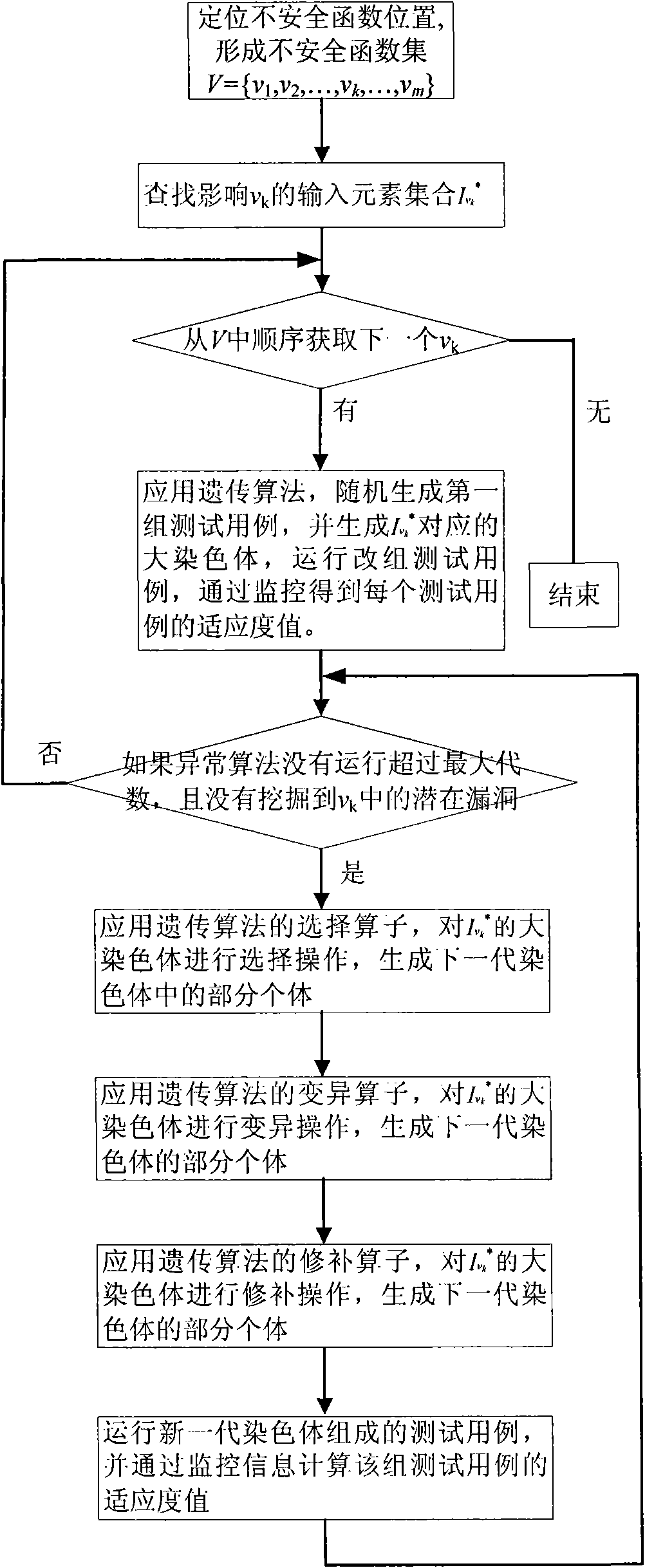
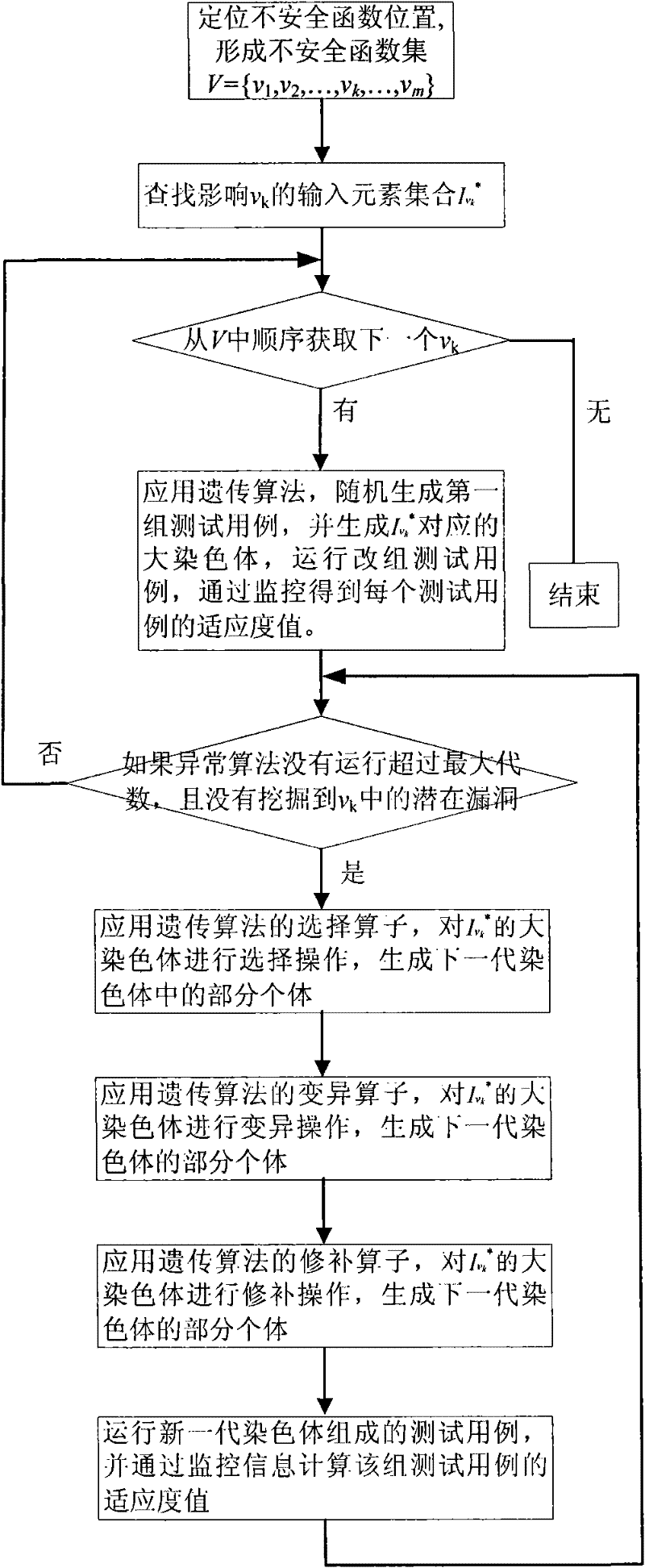
Software vulnerability analysis method of variant multi-dimensional input based on Fuzzing technology
InactiveCN101930398AAnalyzing VulnerabilitiesSoftware testing/debuggingSoftware brittlenessAlgorithm
The invention discloses a software vulnerability analysis method of variant multi-dimensional input based on a Fuzzing technology, which belongs to the field of software testing. The method comprises the following steps of: firstly determining the position of an unsafe function, then establishing the influence relation between an input element and the unsafe function, and finally varying the software vulnerability in the triggering program of the corresponding input element. The invention can be used for analyzing the software vulnerability unanalyzed by the current Fuzzing technology without causing combinatorial explosion.
Owner:中国人民解放军总参谋部第五十四研究所
Method for constructing cascading Bayesian network for solving combinatorial explosion problem
InactiveCN105975694AReduced probability parameterThe reliability calculation result is correctGeometric CADSpecial data processing applicationsAlgorithmNetwork topology
The invention discloses a method for constructing a cascading Bayesian network for solving a combinatorial explosion problem. The method comprises two core parts: A) a method for constructing the topological structure of a cascading Bayesian network by a system access, and B) an intermediate node probability parameter setting method of the cascading Bayesian network. Firstly, the construction of the topological structure of the Bayesian network is finished, wherein the topological structure of the Bayesian network is consistent with a fault cascading configuration in engineering practice, then, the setting of each node condition probability table of the Bayesian network is finished, and finally, the construction of the cascading Bayesian network is jointly finished. When the cascading Bayesian network finishes being constructed, any existing Bayesian network reasoning technology can be applied to carry out reasoning calculation on the cascading Bayesian network so as to obtain system reliability. While a reliability calculation result of the system can be guaranteed to be correct, the probability parameters in the network are effectively reduced, specifically, the number of the probability parameters on each access can be lowered to a linear order from an exponential order, calculation efficiency is improved, and a combinatorial explosion problem is solved.
Owner:NORTHWESTERN POLYTECHNICAL UNIV
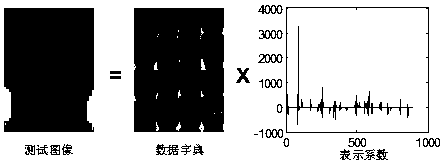
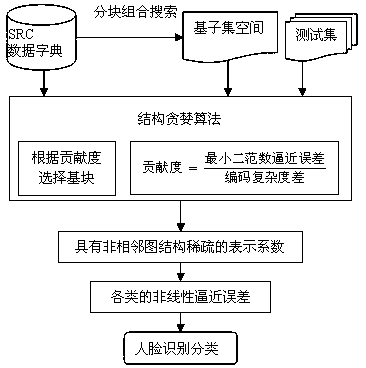
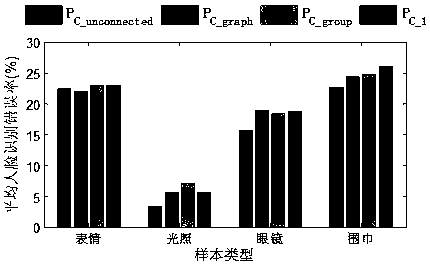
Non-adjacent graph structure sparse face recognizing method
InactiveCN104616027AImprove face recognition rateImprove stabilityCharacter and pattern recognitionWebsite content managementGreedy algorithmMethod of undetermined coefficients
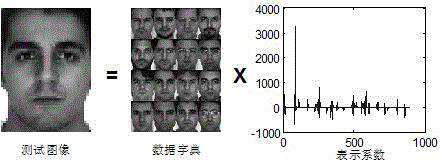
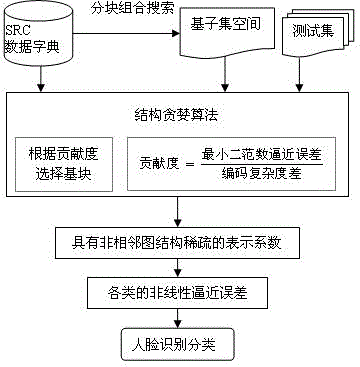
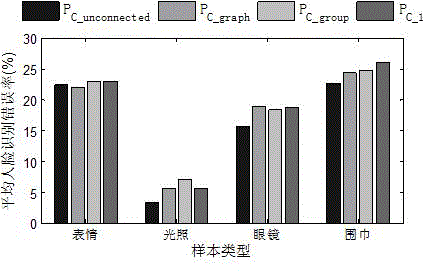
The invention provides a non-adjacent graph structure sparse face recognizing method. The method comprises the steps of enabling the non-adjacent graph structure to be sparse; searching by blocks or combination; measuring the structure sparseness; performing structure sparse reconstruction. According to the method, the system performances are improved through non-adjacent graph structure sparseness based on an SRC model; the blocking of the non-adjacent graph structure is dynamically performed by an overlapping manner and cannot be predicated; the components can be adjacent or non-adjacent; all possible combinations can be searched by the combination method to gain adjacent or non-adjacent blockings, so as to achieve the non-adjacent graph structure sparseness; to avoid combination explosion in search, the method of searching by blocks or combination is provided for limiting the search space as well as generating computer acceptable basis subset space; the non-adjacent graph structure sparse reconstruction is carried out by the structure greedy algorithm; when in iterating of the algorithm, the base blocks are selected according to the contribution degree of the base blocks; the non-adjacent graph structure sparseness is measured according to the coding complexity. With the adoption of the method, the face recognizing rate can be obviously increased.
Owner:EAST CHINA JIAOTONG UNIVERSITY
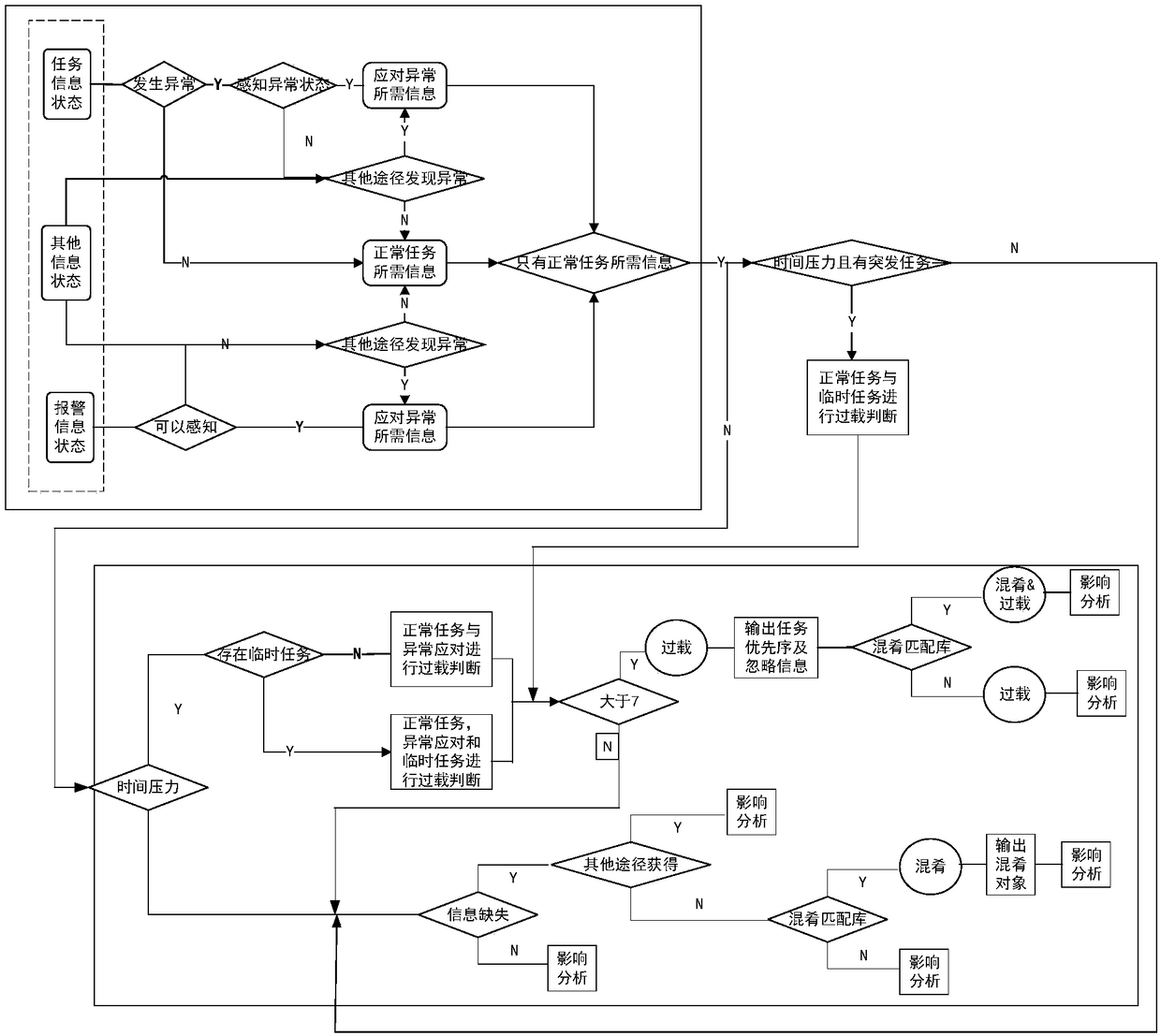
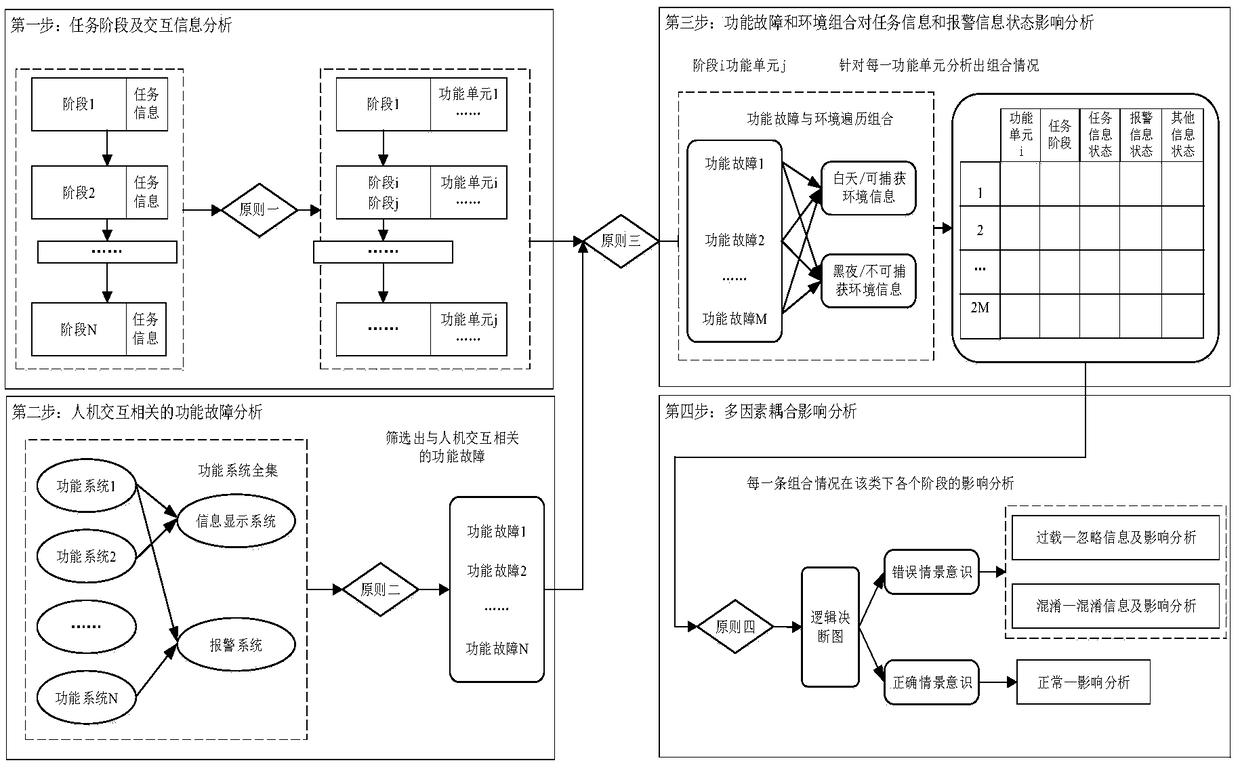
An analysis method of man-machine system influence under the coupling action of man-machine-loop three factors
ActiveCN109145438ADesign optimisation/simulationSpecial data processing applicationsCouplingMan machine
The invention provides an analysis method for the influence of a man-machine system under the coupling action of three factors of a man-machine loop. The method comprises the following steps: dividinga task stage, and defining functional units to be executed in each stage and corresponding interactive information; 2, analyzing the functions of the man-machine system, obtaining a complete set of the functions of the machine, and screening out the functional faults relate to the man-machine interaction through the corresponding principles; 3, traversing the combination of the functional failureand the environment, and analyzing the corresponding task information, alarm information and other information states according to each combination; fourthly, the combination information state beingbrought into the logic decision diagram, and the influence of each abnormal pattern combination is analyzed. Through the above analysis methods and steps, the practical problem of combined explosion under multi-factor coupling is solved, and the effect of man-machine coupling analysis is achieved.
Owner:BEIHANG UNIV
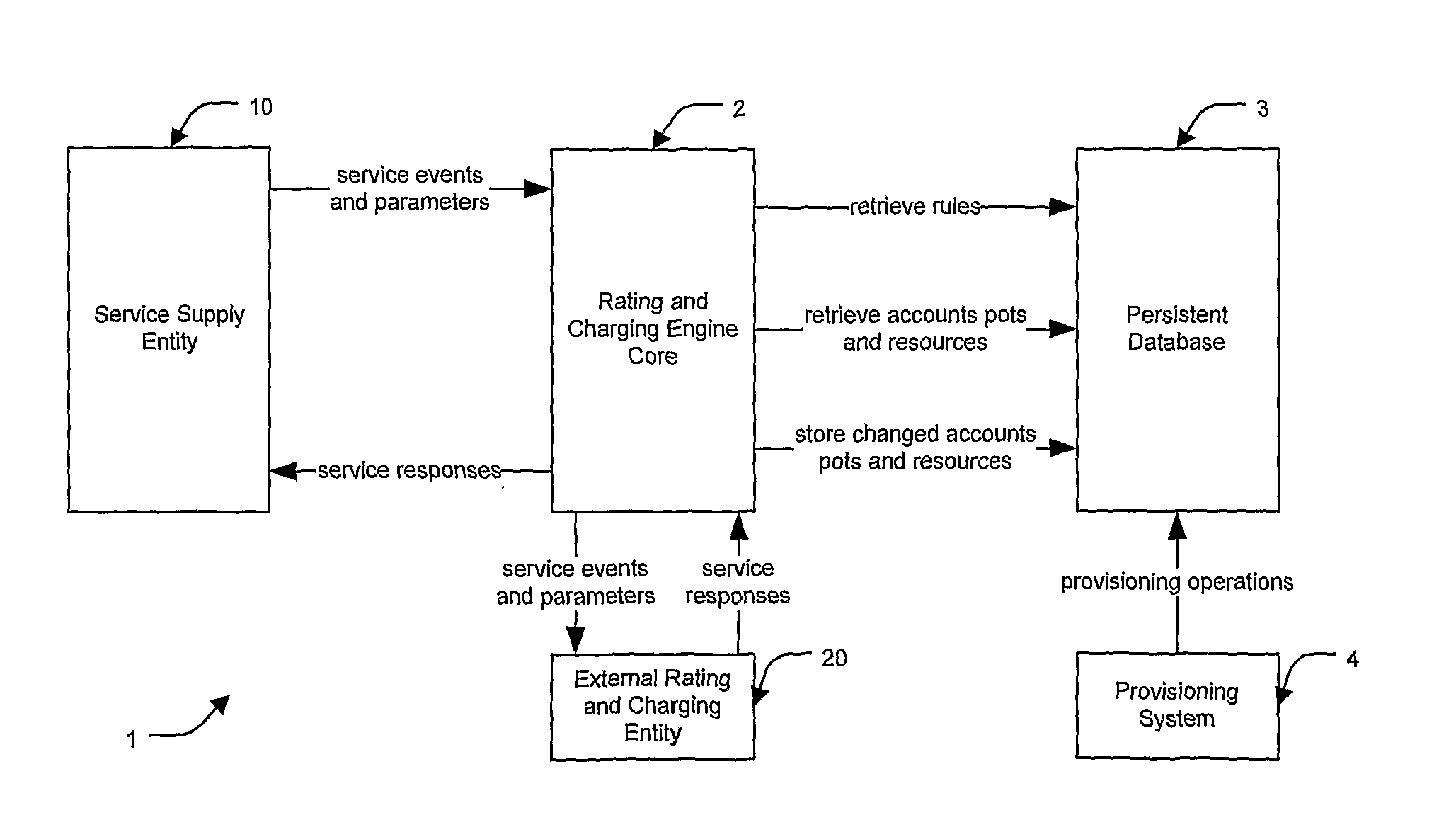
Communication network rating and charging engine
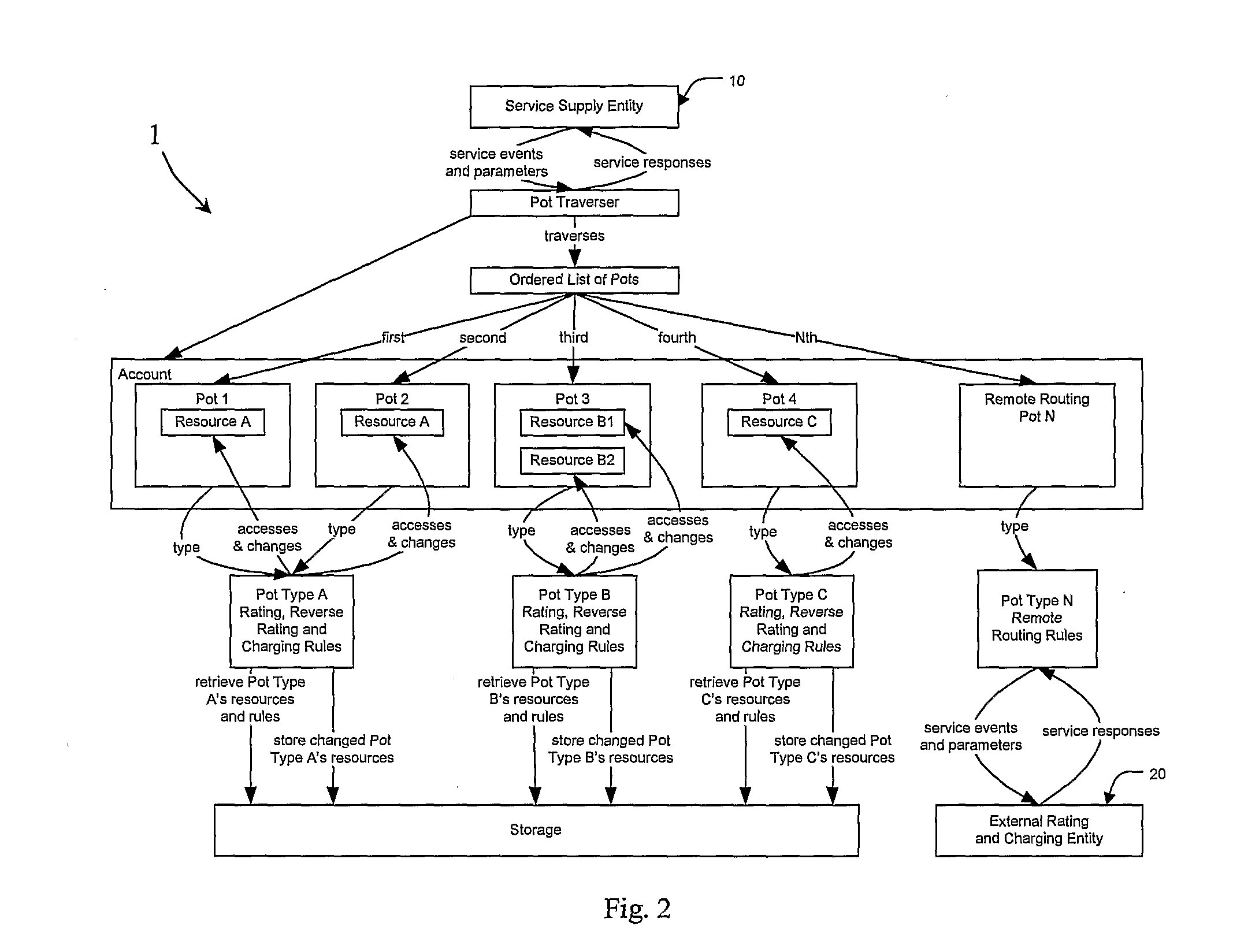
A rating and charging engine (1) comprises an engine core (2), having an accounts / pots / resources / rules persistent database (3), and a provisioning system (4). The core (2) interfaces with a service supply entity (10) such as an IN (intelligent network) service control point, and with an external rating and charging entity (20). The engine (1) overcomes the ‘combinatorial explosion’ limitation of the prior rating and charging approaches by reducing complexity. Most of the rating and charging rules are associated with pot types, and each pot has its own set of rules. The core (2) executes pot traversal rules according to at least one parameter to efficiently determine which pots cannot fulfil a service event, thus immediately narrowing down the rule base to execute. This is very important for real-time performance, where there may be in excess of tens of thousands of service events per second arriving at the core (2). This ensures many hitherto difficult requirements can be simply and rapidly implemented and provisioned, including arbitrary combinations of: cross-service bundles, single-purpose bundles, and time and volume limited bundles.
Owner:MARKPORT LTD
Method for extending Peach platform and testing multiple network message fields
InactiveCN104517056AReduce limitationsReduce blindnessPlatform integrity maintainanceTransmissionComputer hardwareTest efficiency
The invention discloses a method for extending a Peach platform and testing multiple network message fields. The method comprises the following steps: cancelling the limit of original Peach which at most five fields are tested at the same time; presenting the progressive field combined test method, namely testing one field, two fields..., n-1 fields, and n fields at the same time; in allusion to the conflict of large number of test cases and limited test time generated in the combination process, namely the problem of 'combination explosion', permitting the tester to execute the lt in the PitFile; executing the Strategy and gt; setting different levels of test cast generating conditions in the label, effectively limiting the generation numbers, generating the test cast with more pertinency, and greatly improving the test efficiency of protocol safety specialist. For the safety specialist familiar with the Peach platform, the method is simple and effective, and is convenient to operate.
Owner:BEIJING UNIV OF POSTS & TELECOMM
Markov model construction simplification method and system applied to complex system
InactiveCN112183755AReduce the number of statesSolve the state combination explosion problemMathematical modelsCharacter and pattern recognitionAlgorithmComplex system
The invention discloses a Markov model construction simplification method and a system applied to a complex system, relates to the technical field of Markov model construction, and solves the problemof combined explosion during Markov model construction of an existing complex system. The scheme key points comprise steps: detecting the states in the Markov model; screening out the states with thesame transfer rate to form a simplified state group; and merging and simplifying the member states in the simplified state group into one state according to the principle that the entry rate is addedand the exit rate is kept unchanged. According to the Markov model simplification method provided by the invention, before simplification, the equipment state needs to be divided, the equipment is used as a whole, division is carried out according to the influence condition of an external system, and the states with the same or similar influence are merged; in the Markov model building process, the state number can be greatly reduced, and the built Markov model is simplified.
Owner:NUCLEAR POWER INSTITUTE OF CHINA
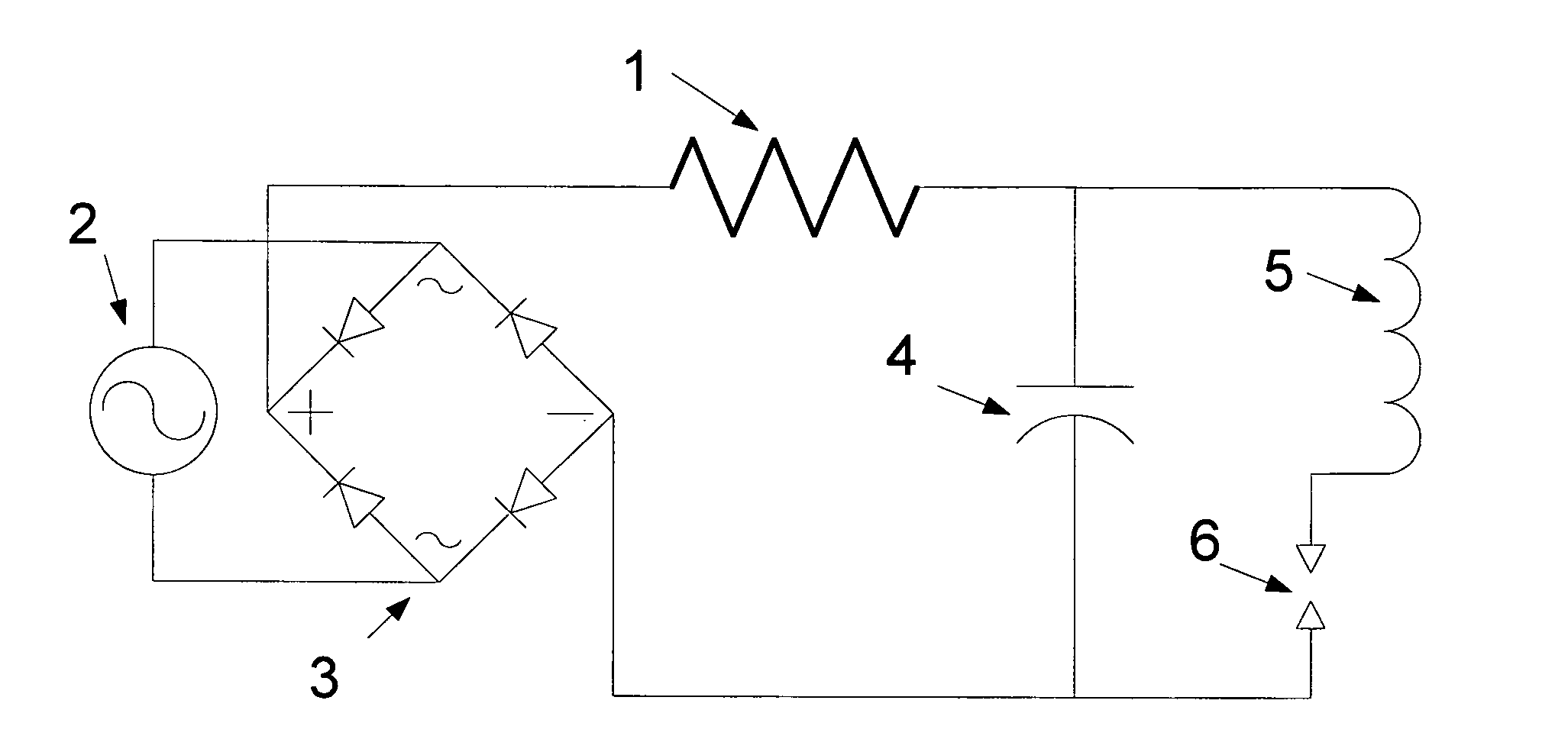
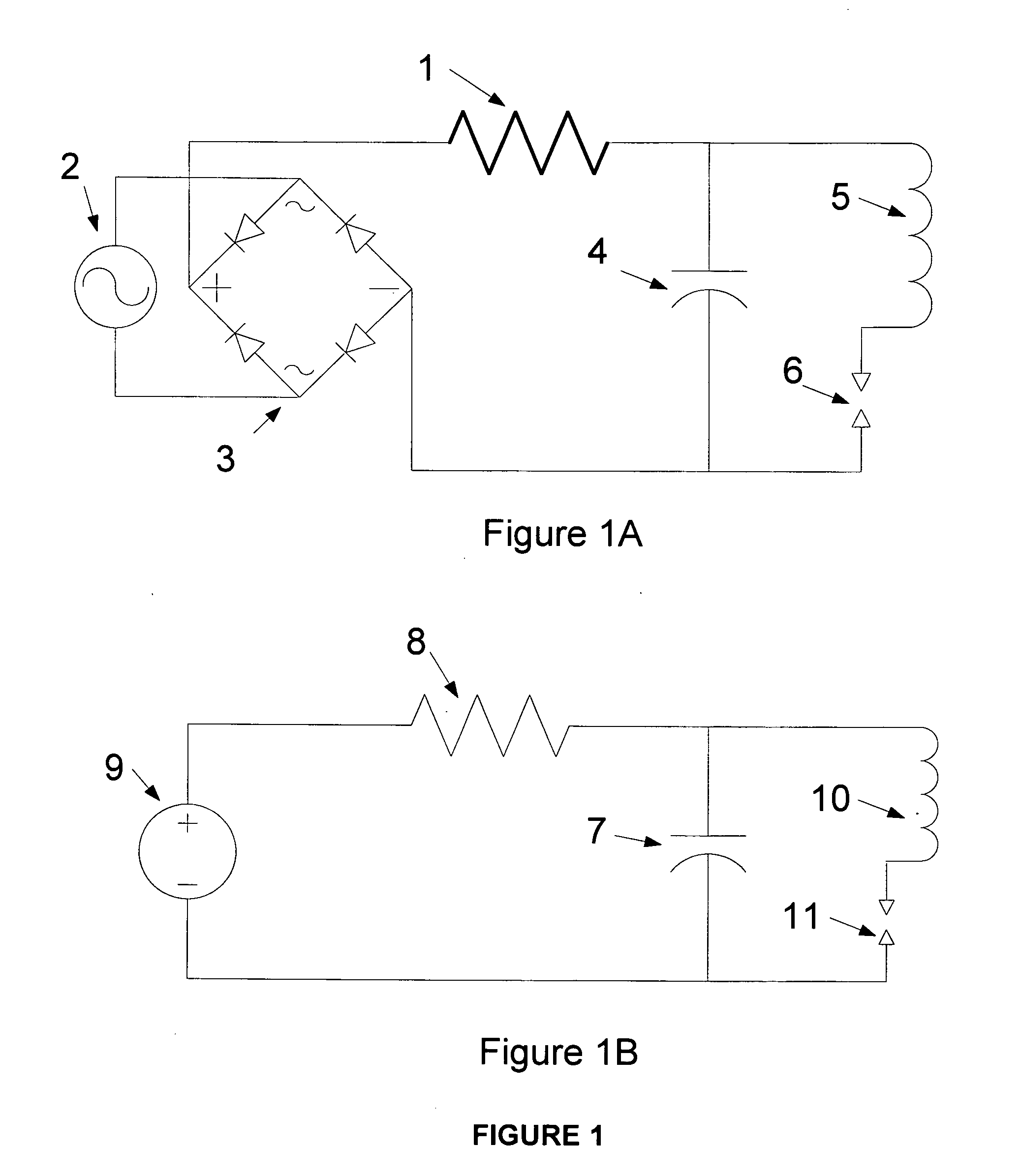
Method for selecting protective resistor value for a capacitor charging circuit which enables maximum energy transfer with minimal heat
InactiveUS20110115496A1Maximize efficiencyControl is neededMaterial thermal analysisFault locationEngineeringElectron
Electronic devices operate in an analog world and their circuitry is subject to non-linear environmental effects that can cause operational problems. Selecting components for a design for a capacitor-charging circuit that incorporates a current-limiting resistor and uses non-linear power supplies, either means having to test every possible combination of elements, and suffering a resultant ‘combinatorial explosion’ as complexity increases, or choosing to over-engineer against untested surprise failure points. Doing the latter in a cost-efficient manner through a min / max / log-set testing series also enables use of non-linear power supplies whose parameters are not known due to competitive or trade secret protective efforts by their manufacturers.
Owner:DAVIS JOHN MICHAEL +1
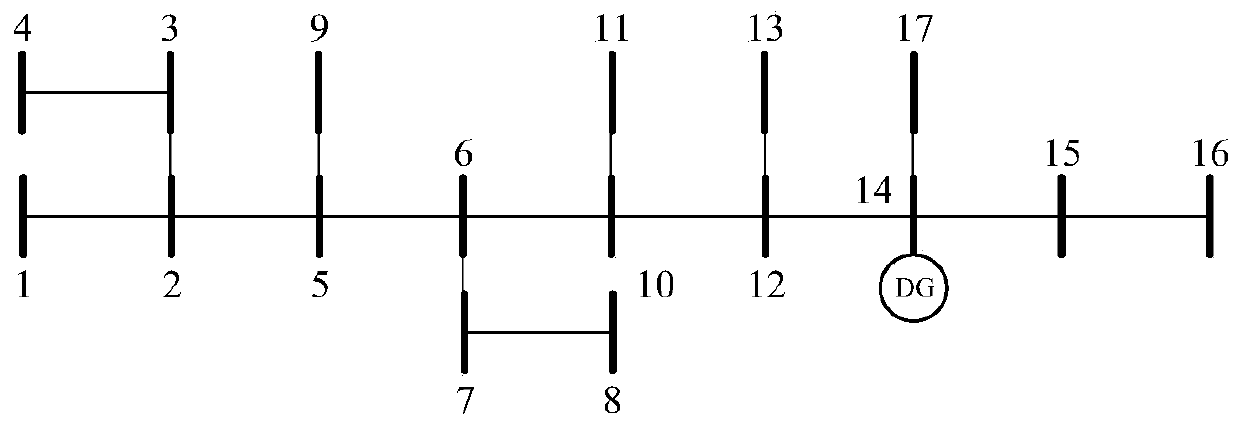
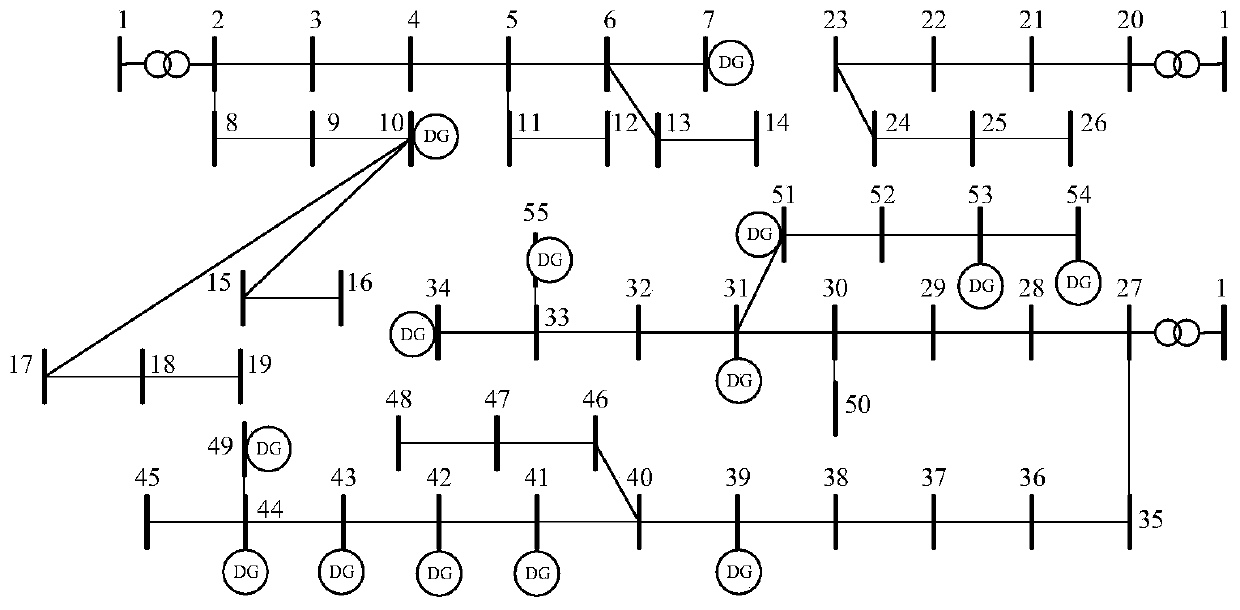
Power distribution network transmission loss apportionment method containing distributed power supply
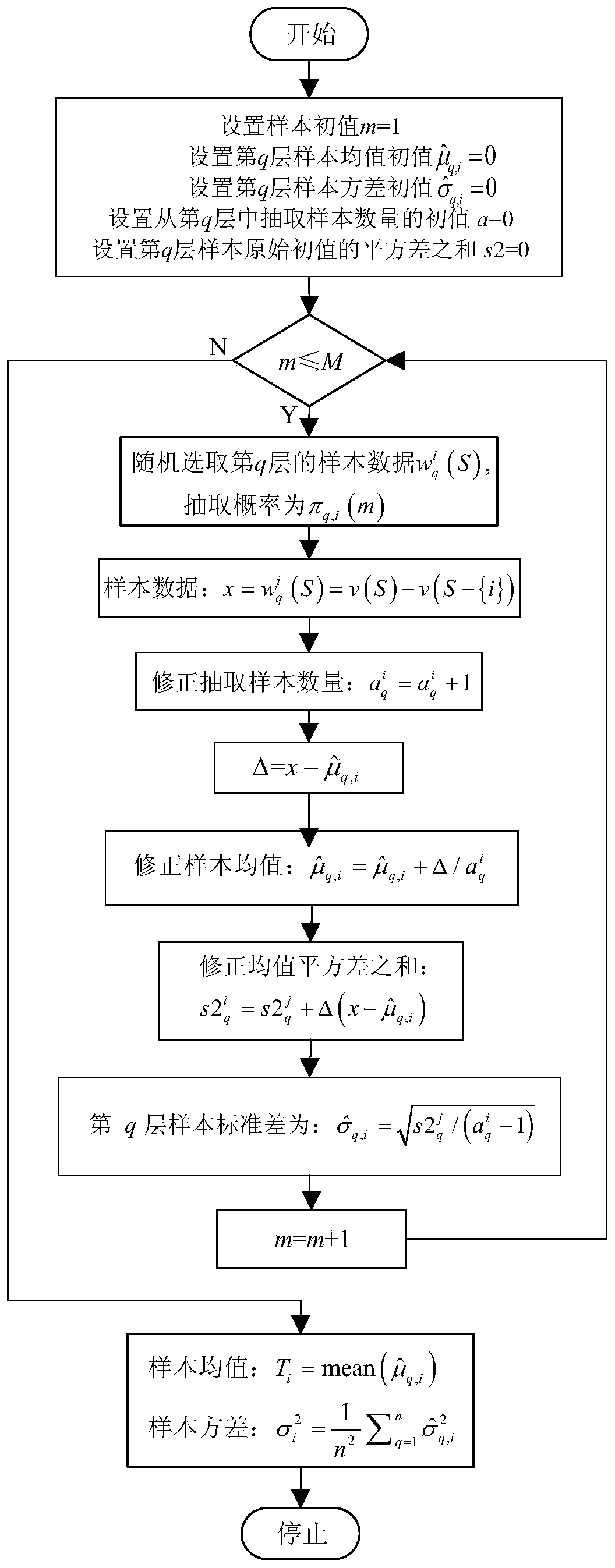
ActiveCN109742803AAvoiding Combinatorial Explosion ProblemsPreserve fairness and reasonablenessSingle network parallel feeding arrangementsInformation technology support systemEstimation methodsTransmission loss
The invention discloses a power distribution network transmission loss apportionment method containing a distributed power supply. The method comprises a step of estimating transmission loss apportionment values of each load node and a DG node in a power distribution network based on a Shapley value sampling estimation method; the sample amount required for computing the Shapley value is reduced through a stratified sampling method; the fairness and rationality of the Shapley value apportionment method is reserved, the expected computation precision is guaranteed, the combinational explosion problem occurring in the Shapley value is overcome, and the computation time is reduced.
Owner:HOHAI UNIV
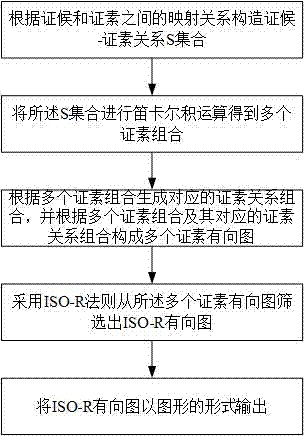
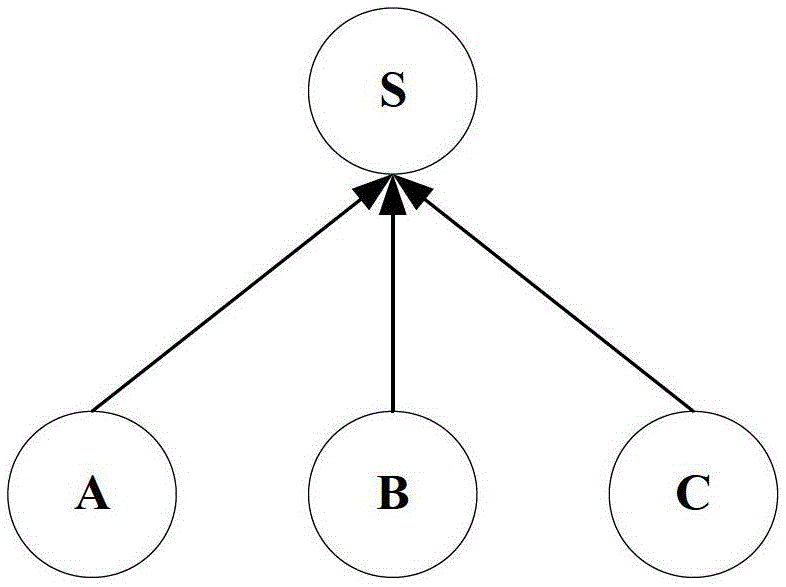
Construction method for traditional Chinese medicine syndrome element differentiation medical knowledge model
InactiveCN107292091AComprehensive explanationIntuitive interpretationSpecial data processing applicationsMedical knowledgeDirected graph
The invention discloses a method for constructing a TCM syndrome differentiation medical theory model, comprising: S1. Constructing a syndrome-syndrome-element relationship S set according to the mapping relationship between syndromes and syndrome elements; S2. Performing a flute on the S set Carl product operation to obtain a plurality of evidence element combinations; S3. Generate corresponding evidence element relationship combinations according to the multiple evidence element combinations, and form multiple evidence element directed graphs according to the multiple evidence element combinations and their corresponding evidence element relationship combinations; S4. Using the ISO-R rule to screen out the ISO-R directed graph from the element-directed graph; S5. Outputting the ISO-R directed graph in the form of a graph. The present invention uses graphic form to output the pathogenesis, compared with the four-character syndrome type obtained by the traditional model, the content of the pathogenesis is comprehensively and intuitively explained; and the Cartesian product according to the mapping relationship between syndromes and syndrome elements The result of the operation and the relationship between the certificate elements generate a certificate element directed graph, and then use the ISO-R rule to screen the certificate element directed graph, which solves the problem of certificate element combination explosion in the traditional certificate element dialectical model.
Owner:成都元峰科技有限公司
A Reliability Analysis Method for Aeroengine Turbine Disk System
InactiveCN103268388BSimple calculationImprove fault diagnosis efficiencySpecial data processing applicationsAviationFailure rate
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
Optimal selection method for territorial sea base points
ActiveCN111006638AImprove work efficiencySolve the "combination explosion" problemProfile tracingControl theoryOceanography
An optimal selection method for territorial sea base points comprises the following steps: firstly, taking two ideal base points as starting and ending points, connecting the ideal base points and allalternative base points between the ideal base points in different forms to form an alternative base line set, filtering out alternative base lines of which the lengths exceed a specified threshold value and which are not within a base line graph polygon, and constructing an initial base line graph; secondly, performing optimization judgment on the associated edge of each node in the initial baseline graph, filtering out the associated edge and the adjacent point of which the baseline polygon area cannot be minimum, and generating a possible optimal adjacent point set; and finally, searchingthe possible optimal baseline graph to obtain a possible optimal baseline path set, performing area calculation on a corresponding baseline polygon, and selecting an alternative base point combinationwith the smallest baseline polygon area to generate an optimal baseline path. According to the method, the problem of combined explosion possibly occurring when the alternative base points are inserted in the unreasonable baseline adjustment process is solved, and the base point optimization working efficiency is improved.
Owner:PLA DALIAN NAVAL ACADEMY
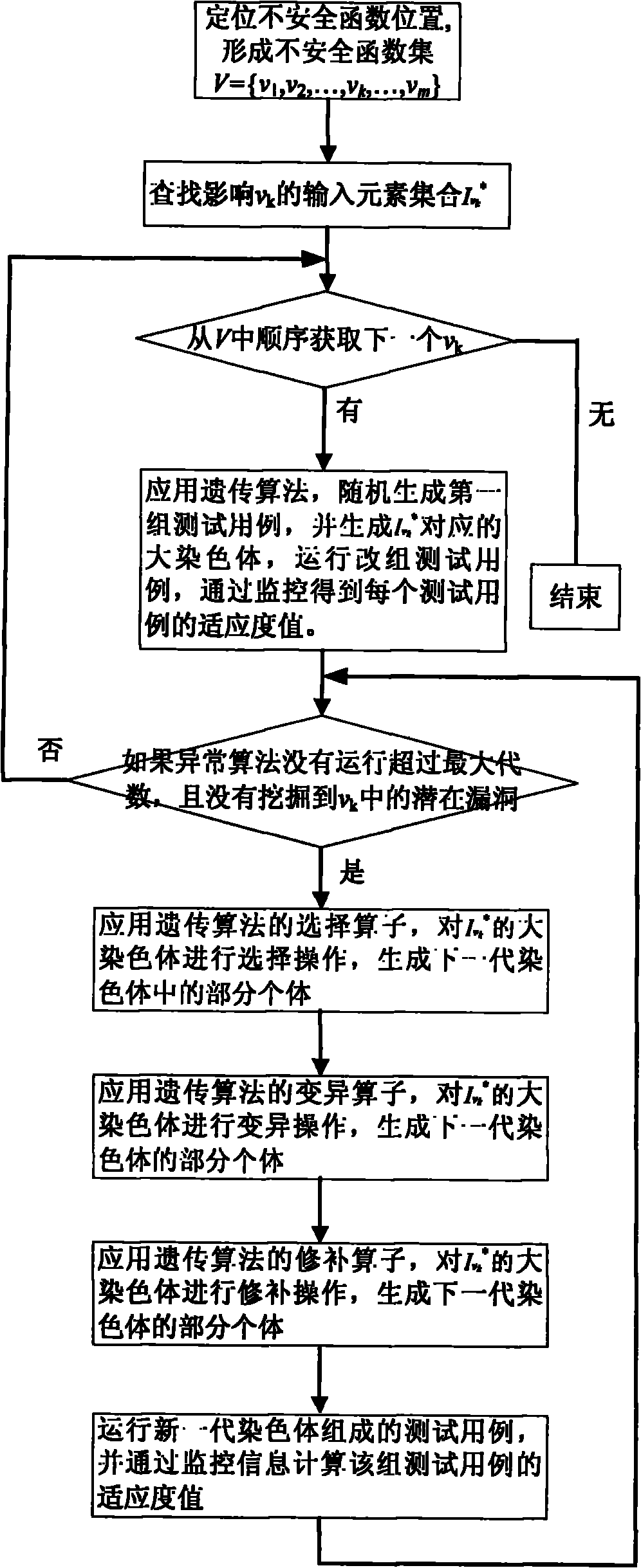
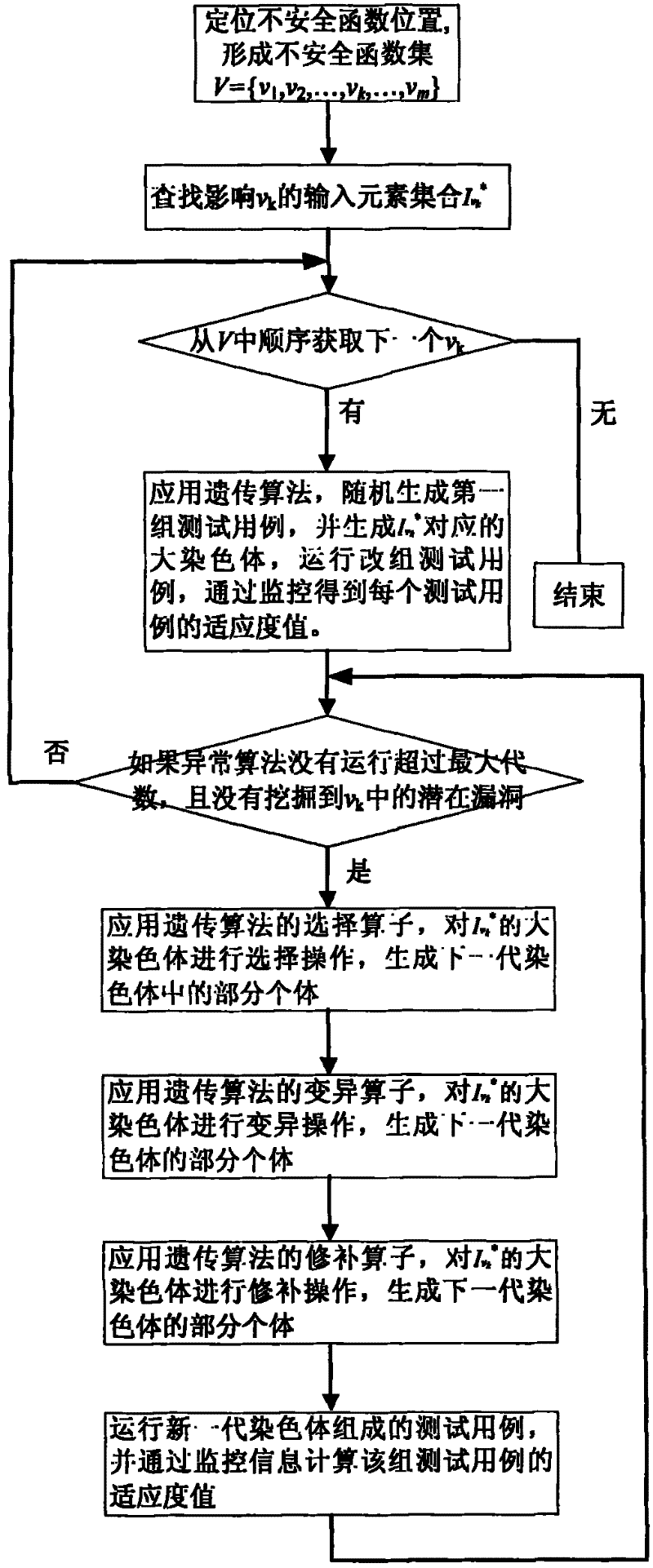
Software vulnerability analysis method of variant multi-dimensional input based on Fuzzing technology
InactiveCN101930398BAnalyzing VulnerabilitiesSoftware testing/debuggingSoftware brittlenessAlgorithm
The invention discloses a software vulnerability analysis method of variant multi-dimensional input based on a Fuzzing technology, which belongs to the field of software testing. The method comprises the following steps of: firstly determining the position of an unsafe function, then establishing the influence relation between an input element and the unsafe function, and finally varying the software vulnerability in the triggering program of the corresponding input element. The invention can be used for analyzing the software vulnerability unanalyzed by the current Fuzzing technology withoutcausing combinatorial explosion.
Owner:中国人民解放军总参谋部第五十四研究所
An Animation Synthesis Method for 3D Characters Based on Command Flow
ActiveCN106548503BAvoiding Combinatorial Explosion ProblemsSmooth motion switchingAnimationData streamSynthesis methods
The invention discloses a command stream based three-dimensional character animation synthesis method. The method comprises the steps of firstly performing classified description on character action models according to moving states, whole body postures and upper body postures; prefabricating specific three-dimensional animation files according to a combination relation table of action classification; building a distributed client / server network model, and formulating protocol specifications for datagram transmission; and searching the combination relation table of action combination by a client after parsing a command data stream transmitted by a server, acquiring relevant action files, and synthesizing a new animation sequence after performing motion blending and performing interpolation on the location and the orientation of a character. According to the invention, automatic switching between difference actions of virtual soldiers in a virtual battlefield environment can be reproduced authentically, smooth interpolation update of the position and the orientation of virtual characters is supported at the same time, a problem of combination explosion between the tedious command control process and actions is avoided, action switching is performed smoothly and naturally, and the method can be widely applied to various virtual battlefields. Therefore, the command stream based three-dimensional character animation synthesis method has a certain application value.
Owner:EAST CHINA NORMAL UNIV
A Non-adjacent Graph Sparse Face Recognition Method
InactiveCN104616027BImprove face recognition rateImprove stabilityCharacter and pattern recognitionWebsite content managementPattern recognitionGreedy algorithm
A non-adjacent graph structure sparse face recognition method, the method includes non-adjacent graph structure sparseness, block combination search, a method for measuring structure sparsity and realizing structure sparse reconstruction. Based on the SRC model, the method enhances the performance of the system through sparse non-adjacent graph structures. The blocks of non-adjacent graph structures are dynamic, overlapping, and unknown in advance, and group members can be different. Adjacent; in order to realize the sparse non-adjacent graph structure, all possible combinations are searched through the combination method to obtain adjacent or non-adjacent blocks; in order to avoid combination explosion in the search, a block combination search method is proposed It is used to limit the search space and generate a computationally feasible base subset space; the method uses a structural greedy algorithm to realize the sparse reconstruction of non-adjacent graph structures. In the algorithm iteration, the base block is selected according to the contribution of the base block. Structural sparsity is measured in encoding complexity. The invention can significantly improve the face recognition rate.
Owner:EAST CHINA JIAOTONG UNIVERSITY
Recognition method of intersecting manufacturing features of 3D cad model
InactiveCN103164582BMeet manufacturability requirementsMeet the requirements of process designSpecial data processing applicationsComputer Aided DesignCluster algorithm
The invention discloses an identification method for three-dimensional computer-aided design (CAD) model intersection manufacture characteristics. The identification method for the three-dimensional CAD model intersection manufacture characteristics is used for solving the technical problem that a combinatorial explosion exists in an existing part manufacturability automatic analysis method in a process that an optional solution is generated. According to the technical scheme of the identification method for the three-dimensional CAD model intersection manufacture characteristics, a three-dimensional CAD model expressed by model based definition (MBD) is used as an information input source, firstly a reachability analysis is conducted on each machined face through an illumination-type rule, and the axial space of a feasible cutter of each machined face is ascertained; then with the axial space of the feasible cutter of each machined face as a restraint, a machined face clustering algorithm merging a manufacture semanteme is adopted to construct each of machined area subgraphs; and finally, with each machined area subgraph as a manufacture characteristic trace which is combined together with dimensioning information, the machined area subgraphs are optimized and merged, so that identification of the manufacture characteristics is achieved. According to the identification method for the three-dimensional CAD model intersection manufacture characteristics, the manufacturability analysis is merged in the identification process of the intersection manufacture characteristics, so that the machined faces are identical in the accuracy level. In the characteristic identification process, the influence, on the characteristic identification, of the design semanteme is fully considered and practicality is improved.
Owner:NORTHWESTERN POLYTECHNICAL UNIV
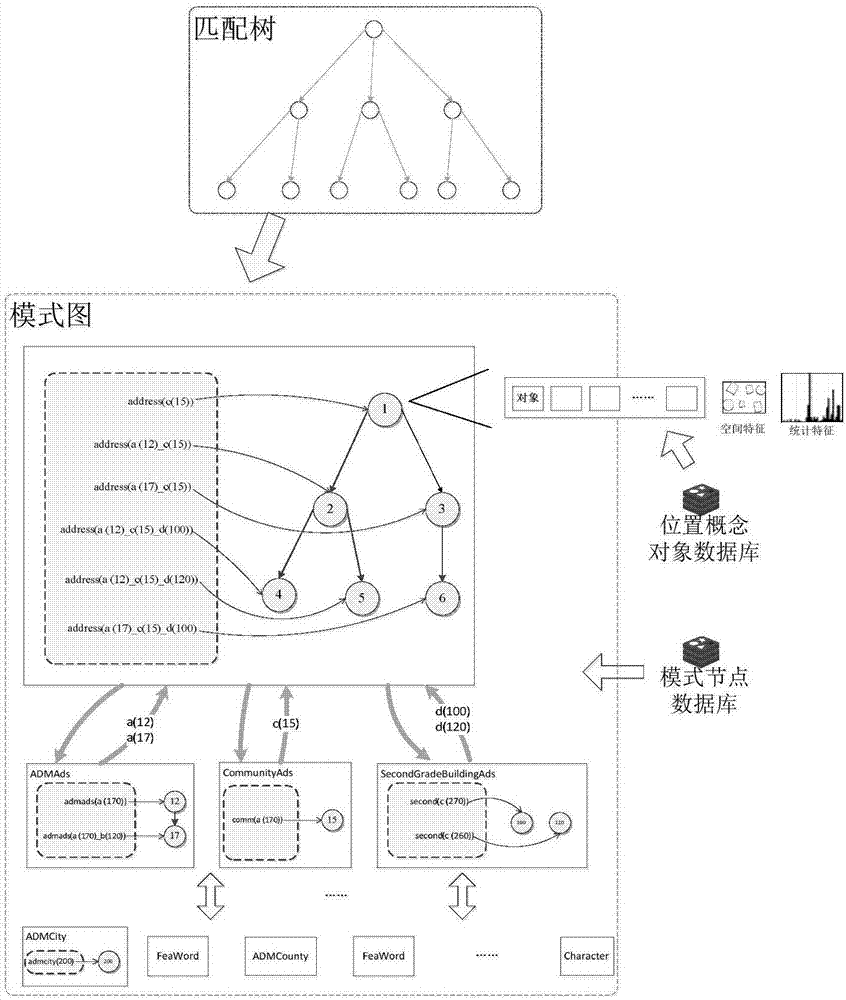
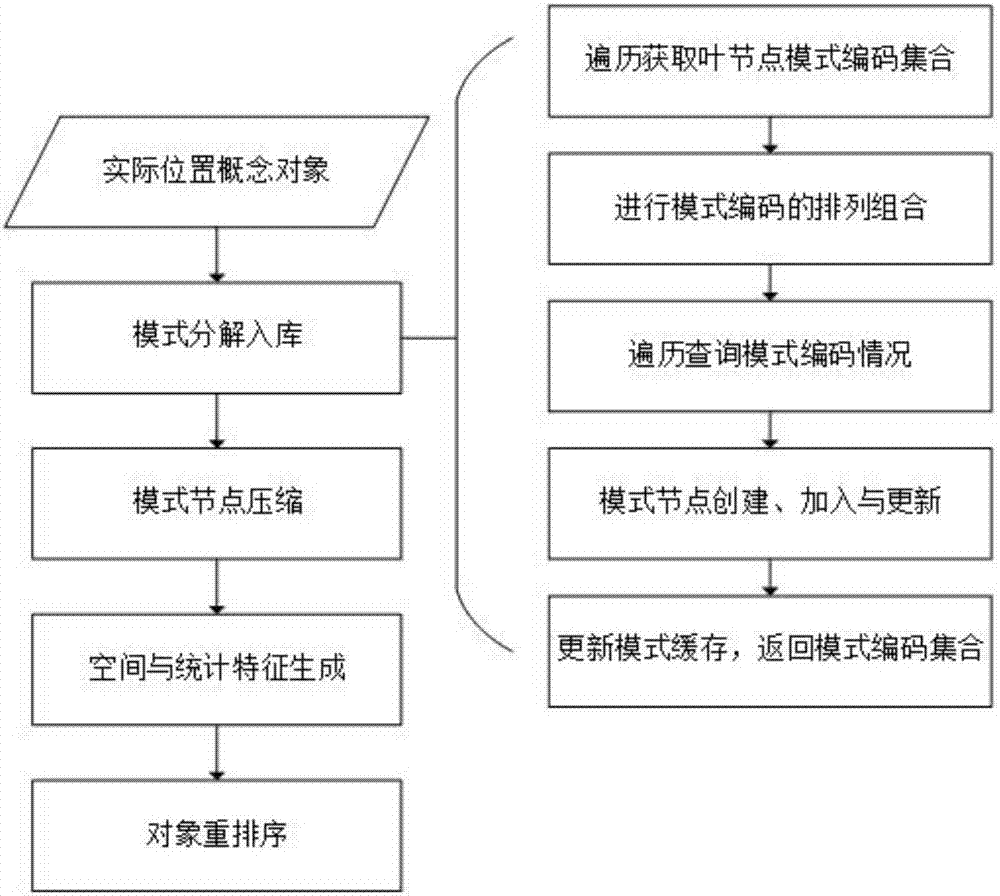
A Spatial Semantic Pattern Graph Construction and Search Method for Rapid Query of Complex Geographic Entities
ActiveCN106776502BEfficient queryNatural language data processingSpecial data processing applicationsSemanticsVirtual position
The invention discloses a spatial semantic mode pattern constructing and searching method for quick query of complex geographic entities with an aim to overcome shortcomings in the prior art, reduce the number of permutation and combination of 'bottom-up' multi-attribute joint query, avoid combination explosion in position description and reduce efficiency loss. The principle lies in that semantics and space are indexed jointly, a 'bottom-up'-mode query strategy is put forward, rapid mapping from a virtual position concept object to an actual position concept set which are acquired in matching is established for natural language form query of the position description, a connection diagram of the position concept object is established through semantic level of an object, and efficient query of the position concept object is provided for positioning.
Owner:WUHAN UNIV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com