Patents
Literature
106results about How to "Avoid malicious access" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
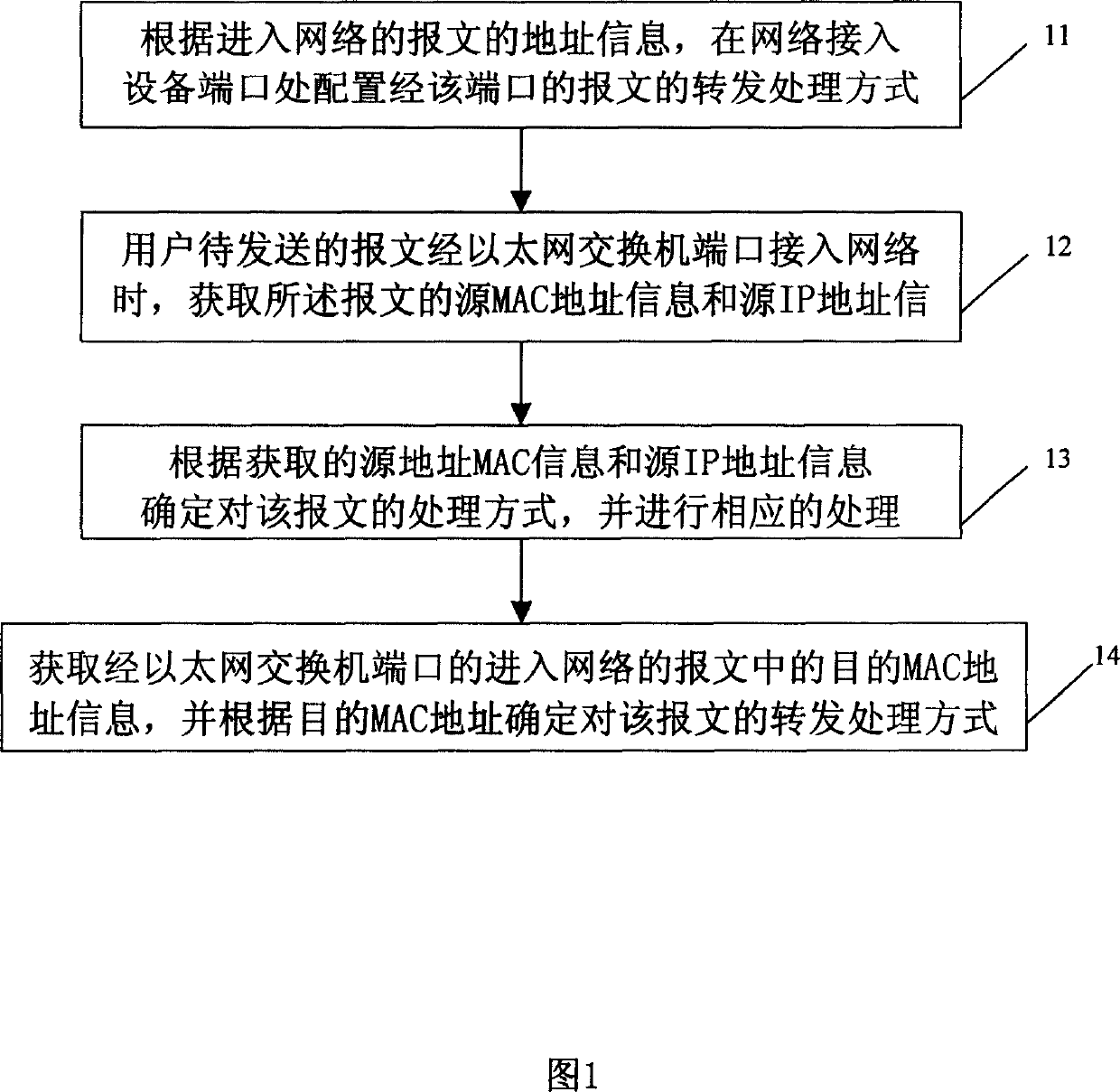
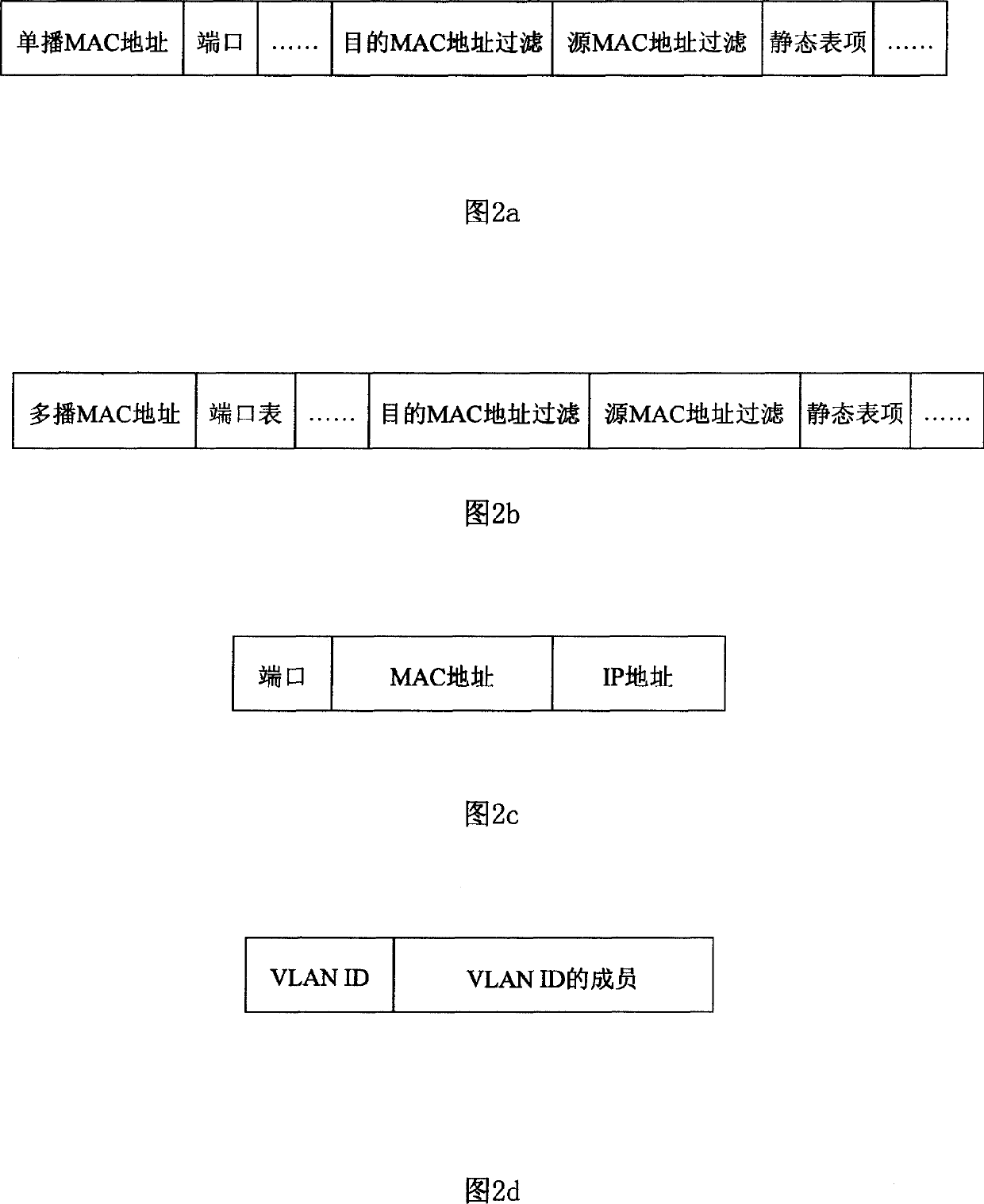
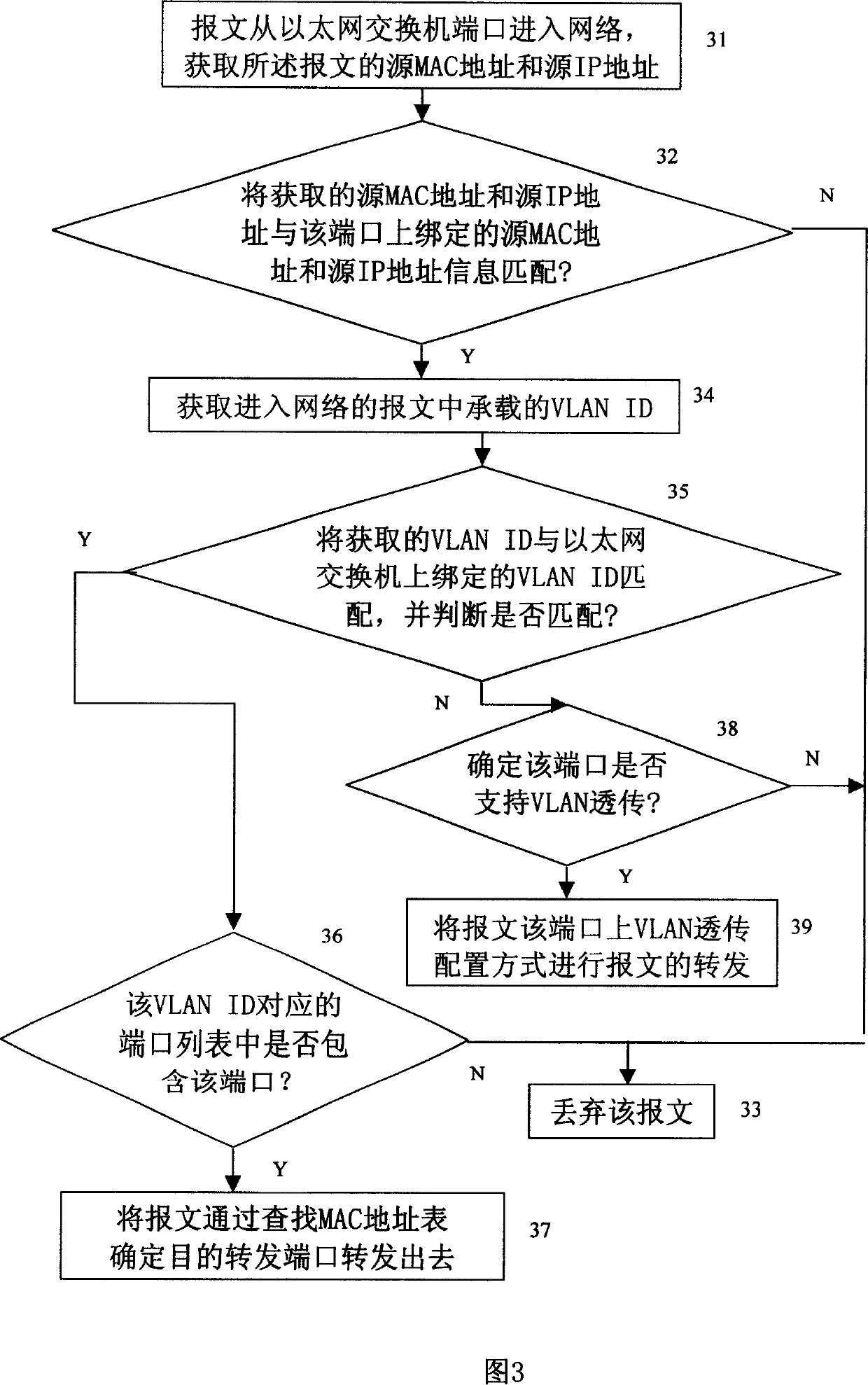
Port based network access control method
ActiveCN1567839AAvoid malicious attacks on the network by arrears usersBlock random mobile surfingData switching networksSecuring communicationMessage passingIp address
The invention relates to a network access controlling method based on network access device port: according to message address information, configuring the processing mode of message passing through the network access device; obtaining the address information of the massage and processing the message according to the obtained address information and corresponding configuration information. It binds user-source MAC address and source IP address with the corresponding port and binds exchanger-supported VLAN ID and the member corresponding to the VLAN ID, thus effectively preventing the illegal user which uses counterfeit source MAC address, source IP address and VLAN ID from viciously accessing or attacking the network. It also makes access limitations on the message entering in the network through the network access device port in view of the destination address of the message, including the network access control of broadcast message, unicast message, multicast message, the message transmitted to the server and the message with specific destination MAC address, and effectively prevents legal user from viciously attacking the network by counterfeiting some destination MAC addresses.
Owner:HUAWEI TECH CO LTD
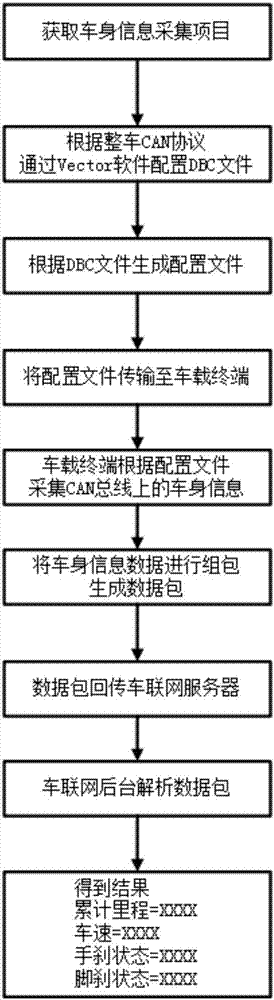
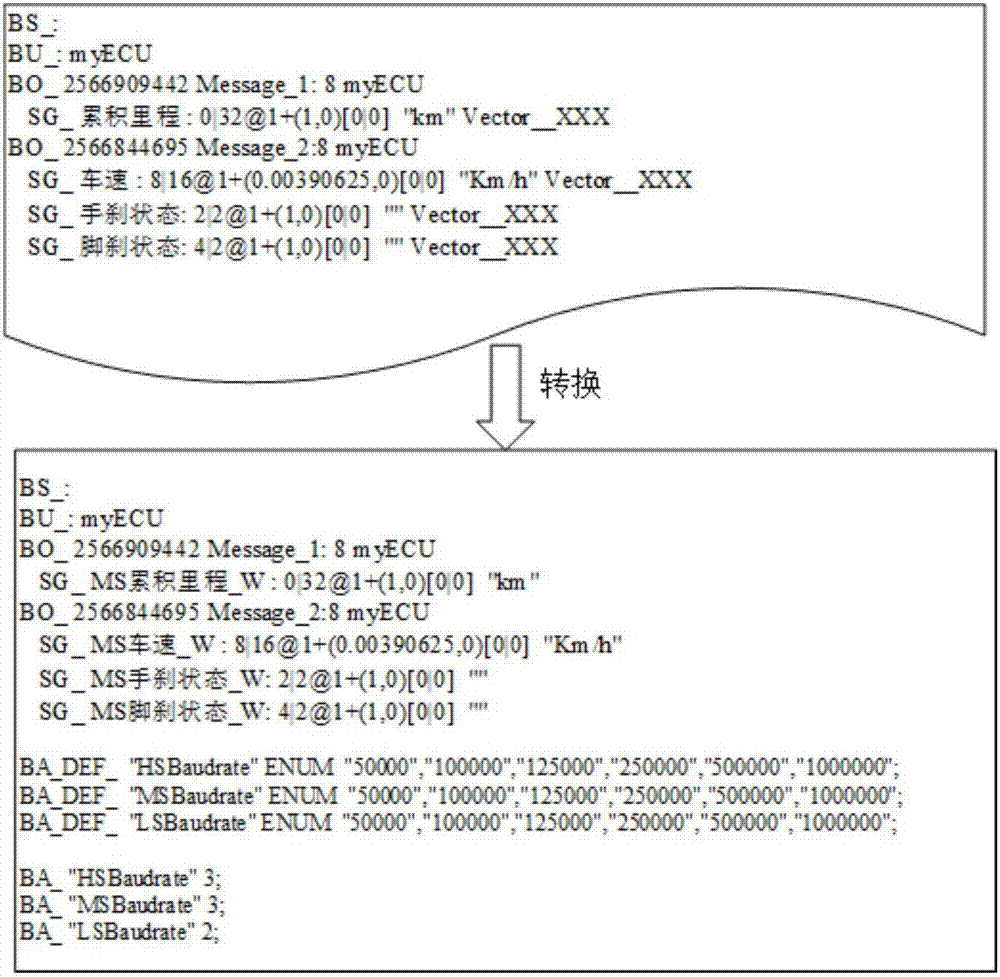
Car networking CAN data acquisition method
Owner:WUHAN INTEST ELECTRONICS TECH
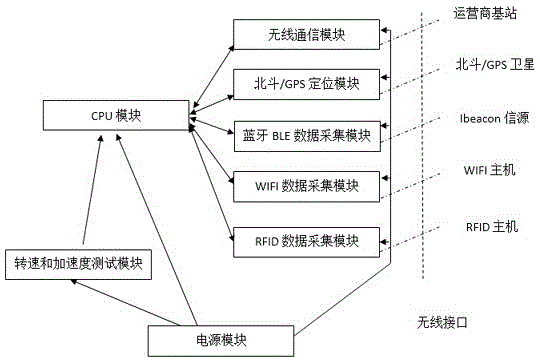
Multi-dimensional personnel and equipment intelligent positioning wearable device
InactiveCN105137465ARealize full positioning trackingCapable of collecting and processing multi-dimensional positioning dataSatellite radio beaconingWireless communicationRadio frequency signalIBeacon
The invention discloses a multi-dimensional personnel and equipment intelligent positioning wearable device, and the device comprises a wireless communication module which is used for collecting related positioning data and enables the related positioning data to be remotely transmitted; a Beidou / GPS positioning module which is used for collecting and analyzing a Beidou / GPS satellite signals, carrying out position calculation, and outputting latitude and longitude information; a BLE data collection module which is used for collecting the MAC, field intensity and TxPower of a Ibeacon Bluetooth signal; a WIFI data collection module which is used for collecting the MAC and radio frequency signal intensity of a WIFI host; an RFID data collection module which is used for collecting the ID and radio frequency signal intensity of an RFID host; a rotating speed and acceleration measurement module which is used for collecting the acceleration and rotating speed of the device; and a CPU module which is used for the management of the whole unit. The device is suitable for the whole-course positioning of the personnel and equipment in different geographic environments, such as an open environment, an indoor environment, commuting ports, and the like.
Owner:CHENGDU ASIONSYS IND CO LTD
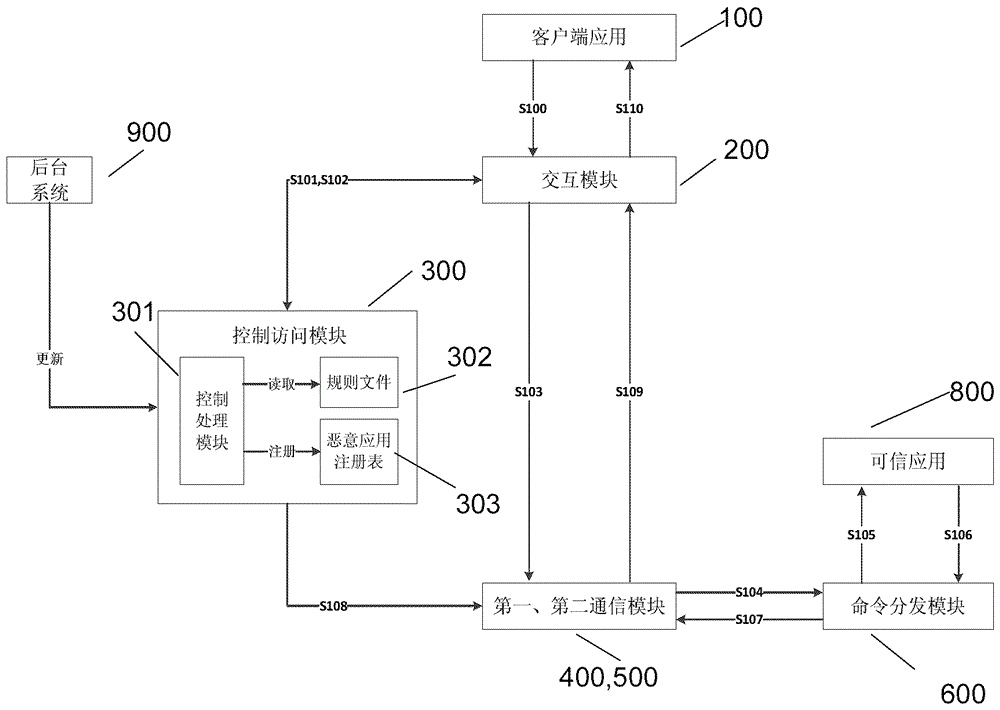
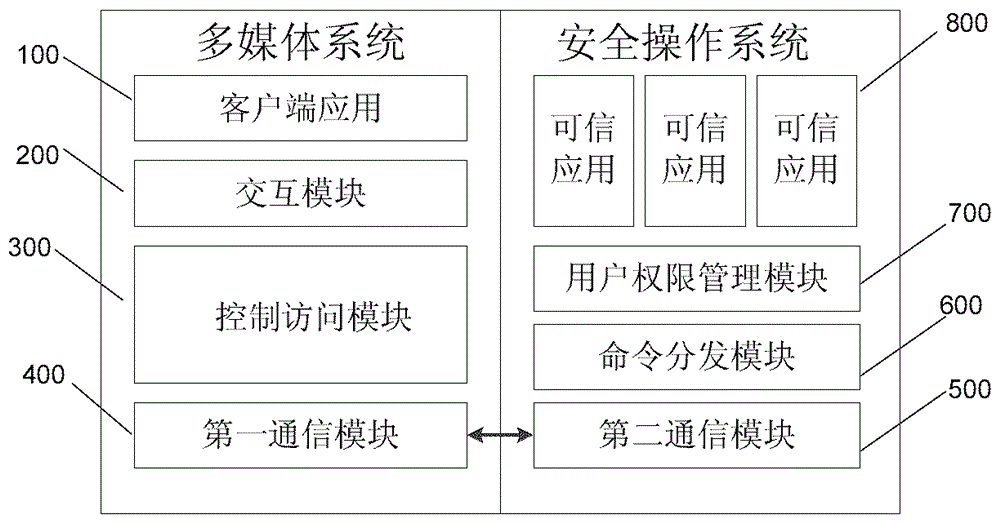
TEE access control method and mobile terminal for achieving same
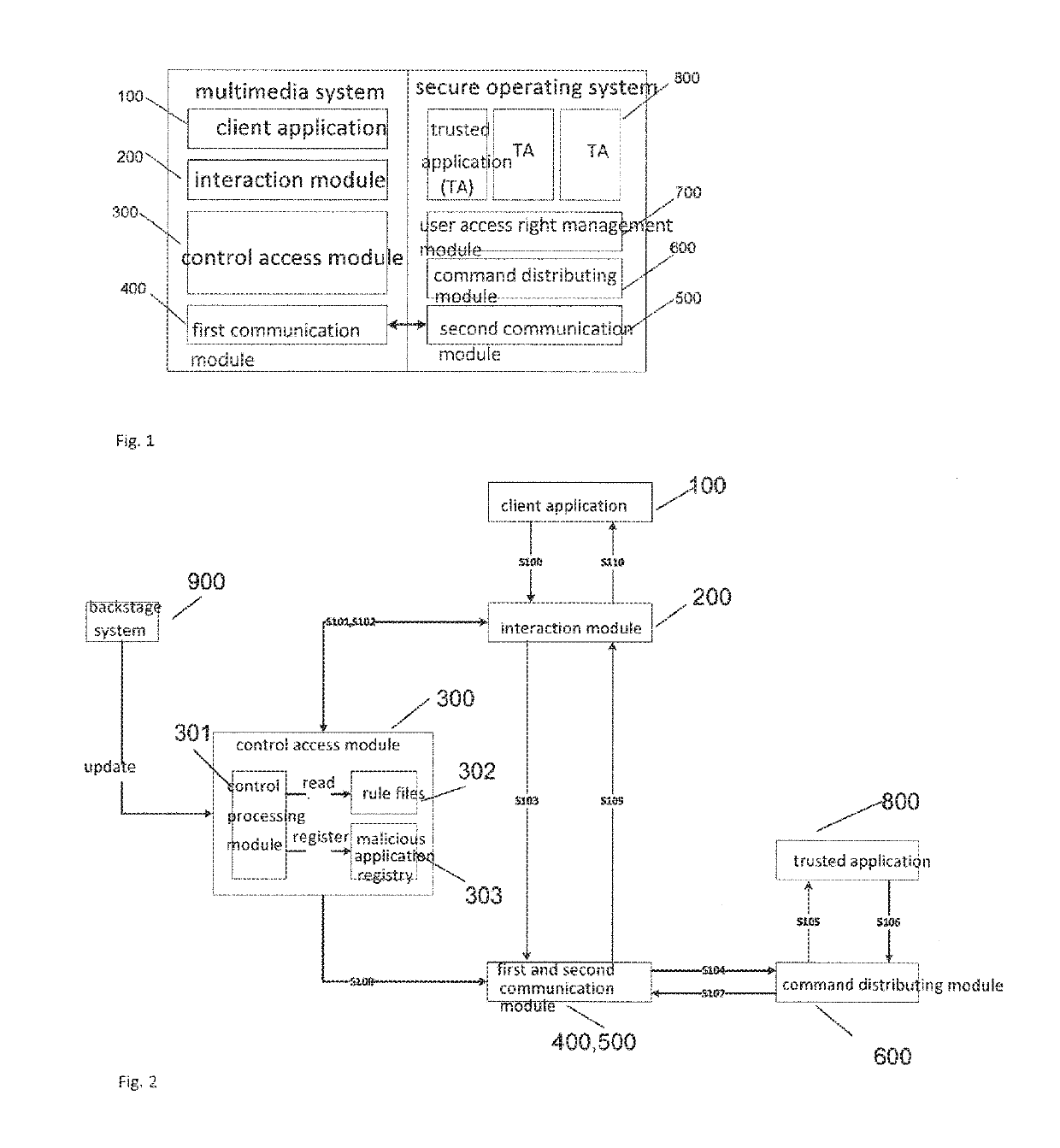
ActiveCN105809036AAvoid inaccessibilityImprove usabilityInternal/peripheral component protectionDigital data authenticationOperational systemComputer terminal
The invention relates to an access control method of a multimedia system on a secure operating system and a mobile terminal for achieving the method.The method comprises the steps that an application access request for selecting dependable applications is initiated for the secure operating system from client side applications of the multimedia system; whether the current client applications initiating calling are vicious applications or not is judged, if not, the next step continues, and if yes, the information that selection fails is returned to the client side applications, and processing is interrupted; the application access request is sent to the secure operating system from the multimedia system; the dependable applications are obtained in the secure operating system according to the application access request and returned to the multimedia system.According to the method, vicious access initiated by the vicious applications to the dependable applications in the secure operating system can be prevented under the condition of not switching the systems, and the problem that access to the dependable applications cannot be achieved due to vicious access can be avoided.
Owner:CHINA UNIONPAY
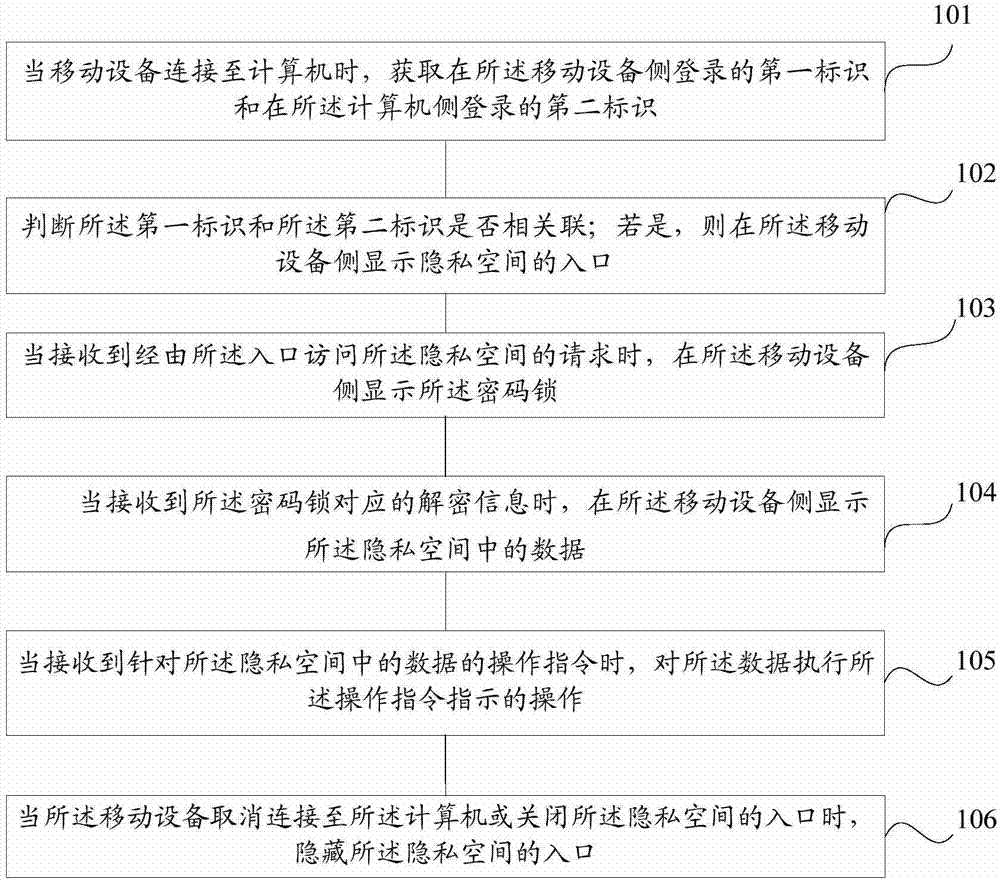
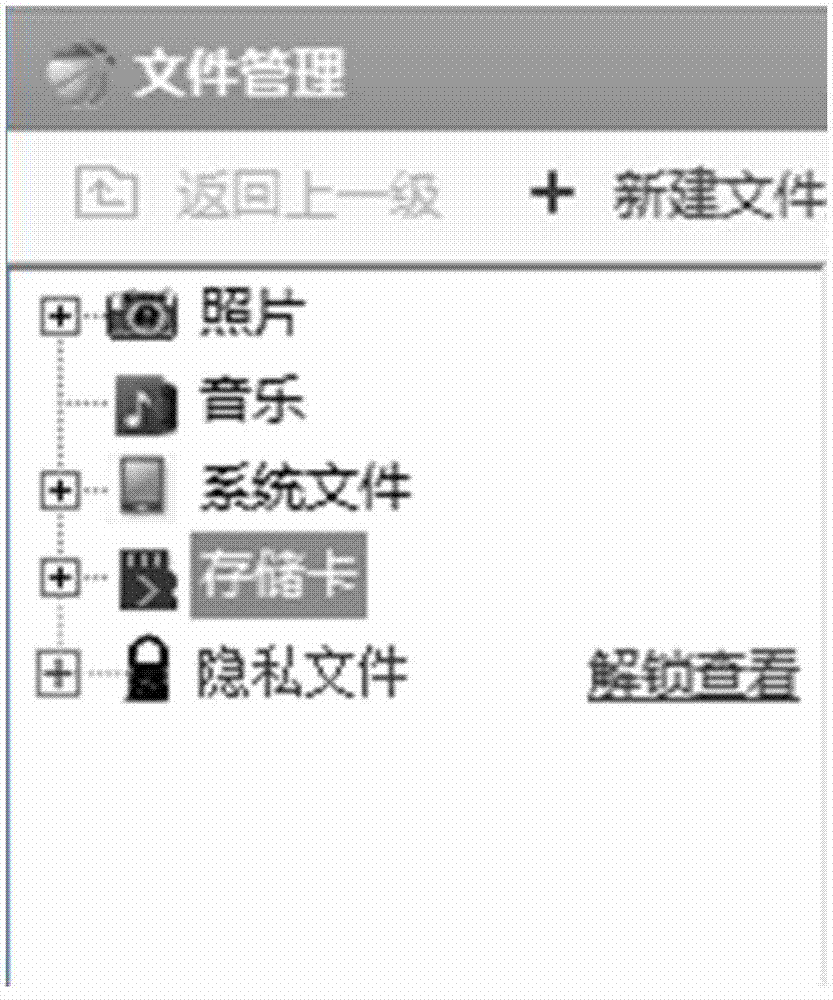
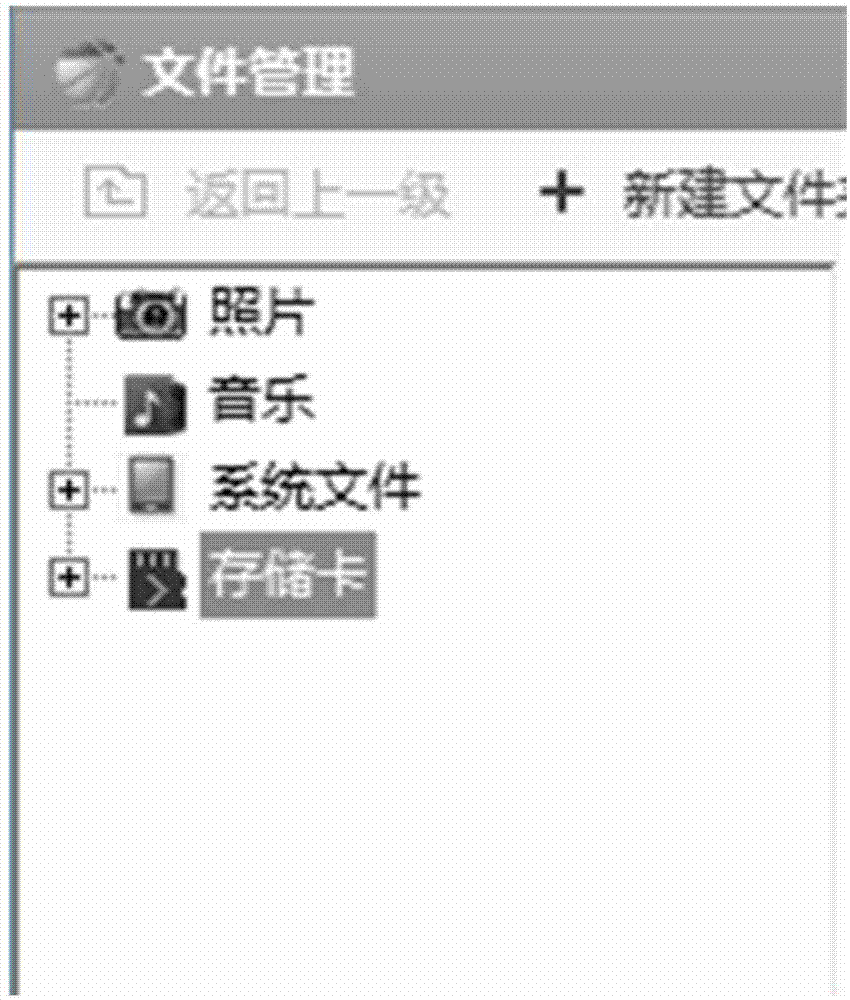
Method and device for processing privacy data in mobile equipment
ActiveCN103577761APrevent malicious access to private spaceEnsure safetyDigital data protectionInternal/peripheral component protectionInternet privacyDisk storage
The invention discloses a method and a device for processing privacy data in mobile equipment. The method comprises the steps that when the mobile equipment is connected to a computer, a first identity logged in on a mobile equipment side and a second identity logged in on a computer side are acquired; whether the first identity and the second identity are associated is judged; if so, an entry of a privacy space is displayed on the mobile equipment side; the privacy space is a disk storage space encrypted by a coded lock; when a request accessing the privacy space via the entry is received, the coded lock is displayed on the mobile equipment side; and when decryption information corresponding to the coded lock is received, data in the privacy space is displayed on the mobile equipment side. The method and the device can effectively avoid malicious privacy space access, so that the security of privacy information of a user can be ensured effectively.
Owner:BEIJING QIHOO TECH CO LTD
Isolation method and isolation device for application program
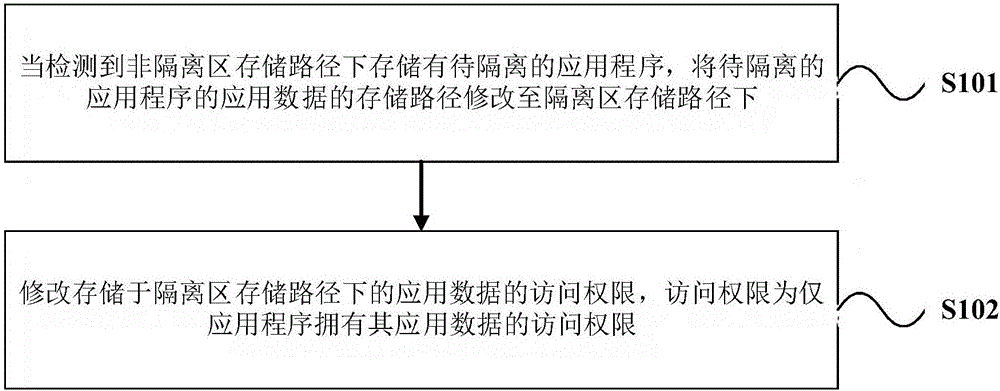
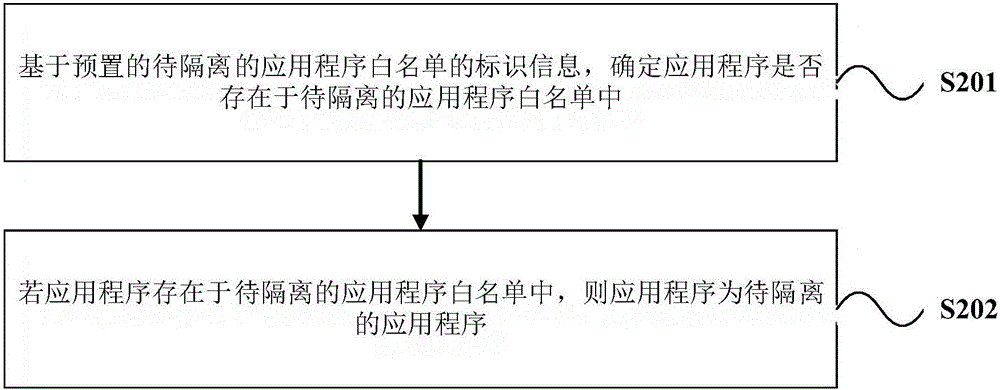
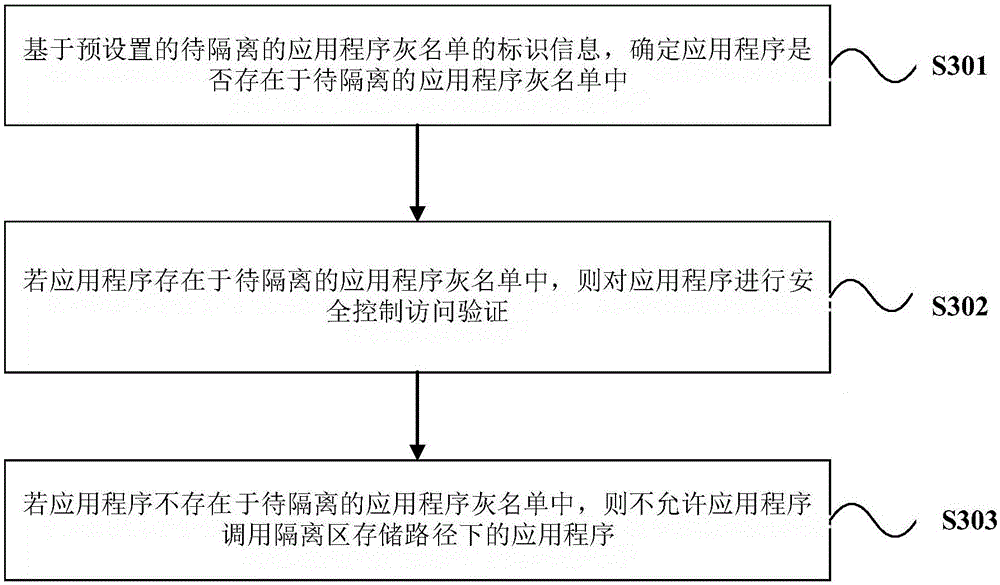
ActiveCN106778291AProtection securityPrevent malicious accessDigital data protectionPlatform integrity maintainanceApplication softwareDatabase
Owner:BEIJING ANYUNSHIJI TECH CO LTD
Micro-power consumption control method of motion monitoring and tracking equipment
InactiveCN108829227APrevent malicious accessAvoid data breachesPower supply for data processingSecondary developmentPower consumption
The invention discloses a micro-power consumption control method of motion monitoring and tracking equipment. A hardware energy consumption management and control part and a software energy consumption dynamic strategy part are combined; in the hardware energy consumption management and control part, by adopting control CPU frequency reduction and IO configuration, embedded secondary development of a communication CPU module, and complete isolation between the communication CPU module and a power supply, a dormant current of a whole machine is enabled to be smaller than 5 [mu]A; and in the software energy consumption dynamic strategy part, after a remote background server receives reported data of a terminal, according to parameters of the terminal, a terminal energy consumption managementand control strategy is formulated and sent to the terminal for execution. By controlling the power consumption of the whole machine, during the dormant period, the working current of the whole machine is less than 5 [mu]A; and in the tracking period, the communication CPU module works and performs data interaction with the remote server, the power consumption of the whole machine is less than 80mA, and when the communication CPU module is dormant in the tracking period, the power consumption of the whole machine is less than 1 mA.
Owner:CHENGDU ASIONSYS IND CO LTD
Method for running third-party codes safely in Java virtual computer
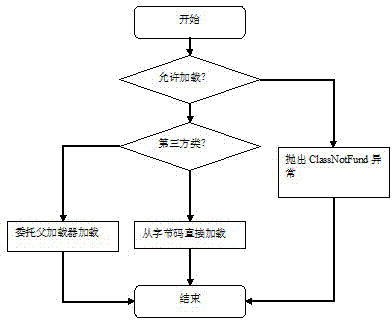
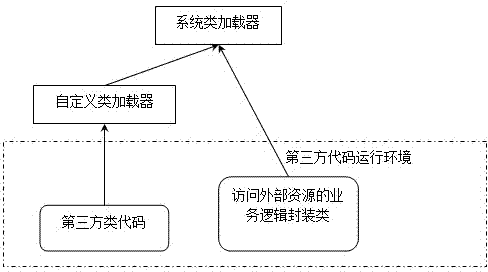
ActiveCN102902911AAvoid malicious accessPlatform integrity maintainanceProgram loading/initiatingVirtual machineThird party
The invention discloses a method for running uncontrollable third-party codes safely by using of technologies of a custom classloader provided by a Java virtual computer (JVM). Local modules and classes which are available in third-party codes are controlled, so that access to external resources can be effectively limited, and simultaneously, a plurality of third-party codes which operates at the same time can be isolated. The invention also provides a method for accessing local resources transparently in a controllable mode in third-party codes.
Owner:BEIJING SENSESHIELD TECH
Method for preventing session hijacking, server and terminal
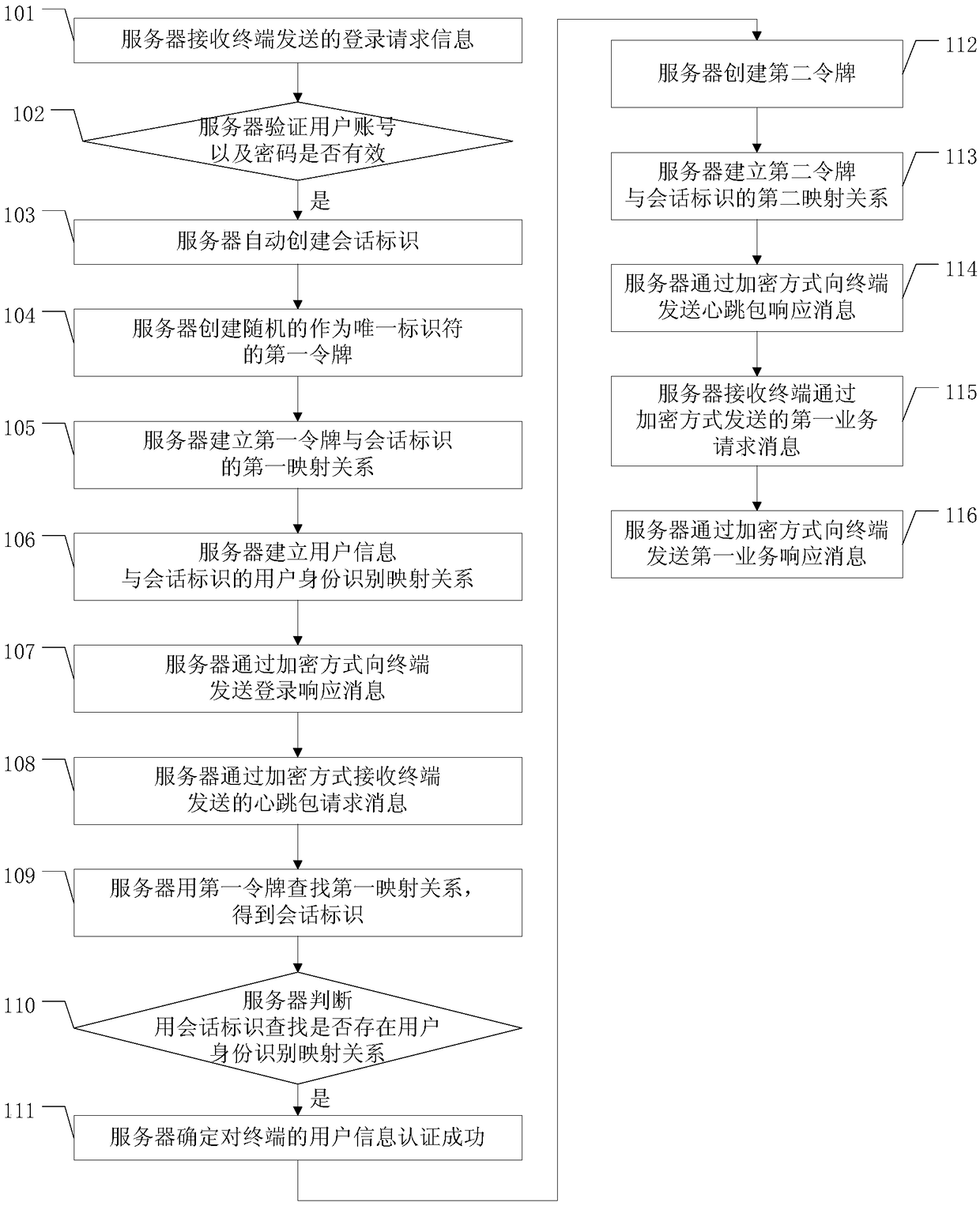
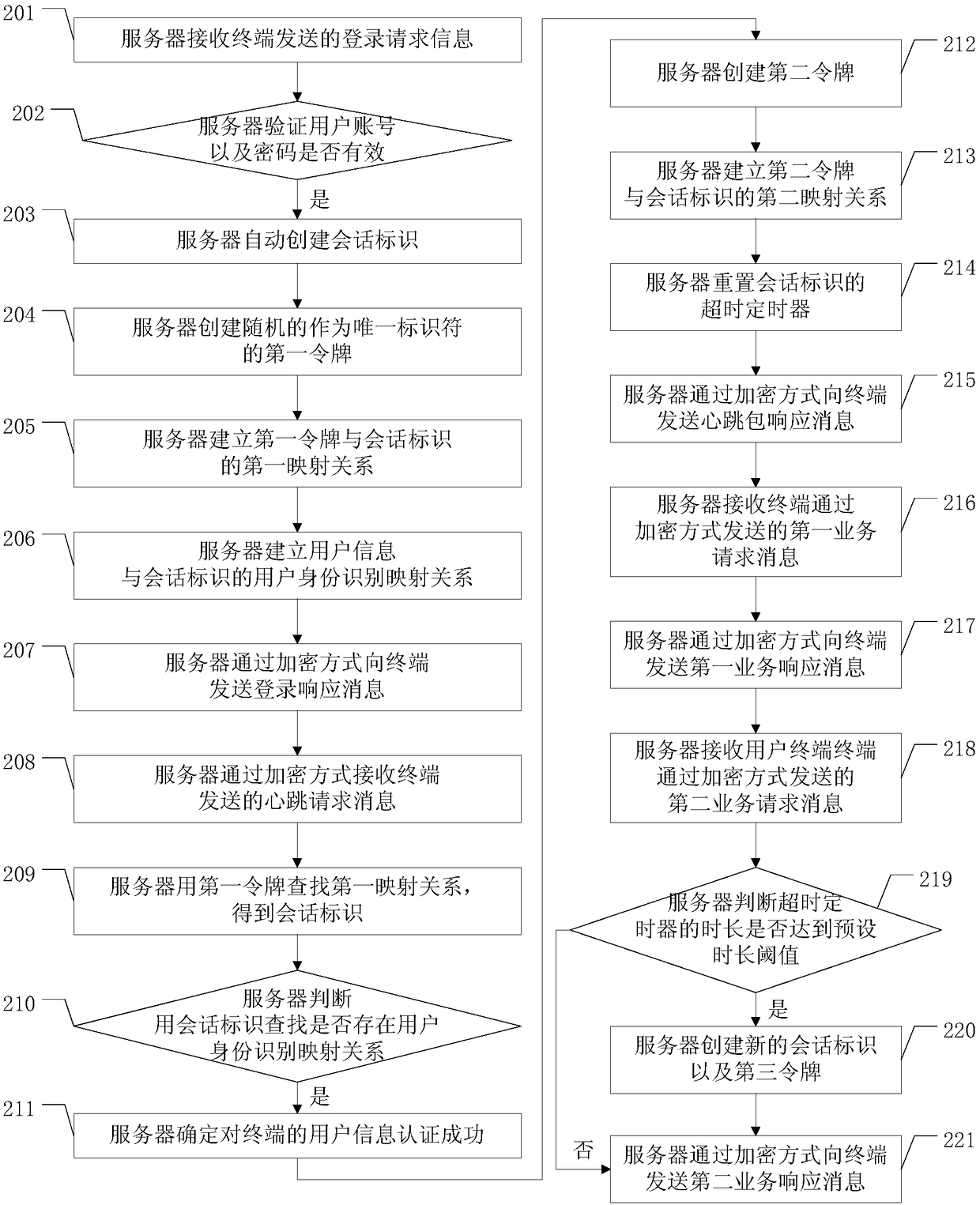
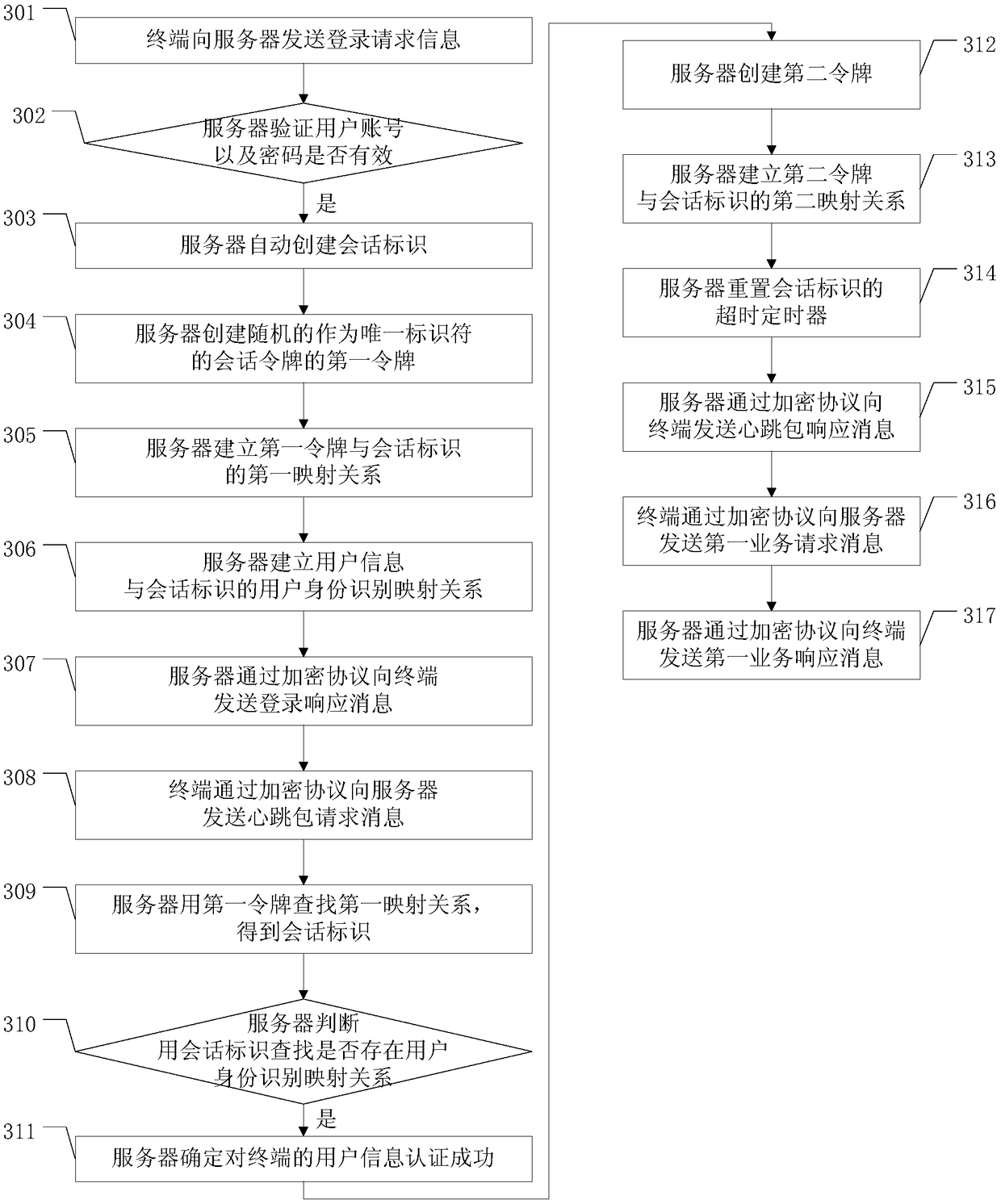
ActiveCN109167802AAvoid malicious accessImprove security levelUser identity/authority verificationData switching networksNetwork packetUnique identifier
The embodiment of the application discloses a method for preventing session hijacking, a server and a terminal, which are used for preventing an attacker from maliciously acquiring identity authentication information between the terminal and the server, and improving the session information security level between the terminal and the server. The method according to one embodiment of the inventionincludes: automatically creating a session identifier by the server, randomly creating value of the token as a unique identifier, and constantly changing the value of the token, then, inputting the dynamic value into the data packets used for information exchange between the server and the terminal, and encrypting the data packets in an encrypted manner, so that the information security of the information exchange between the terminal and the server is doubly protected.
Owner:KINGDEE SOFTWARE(CHINA) CO LTD
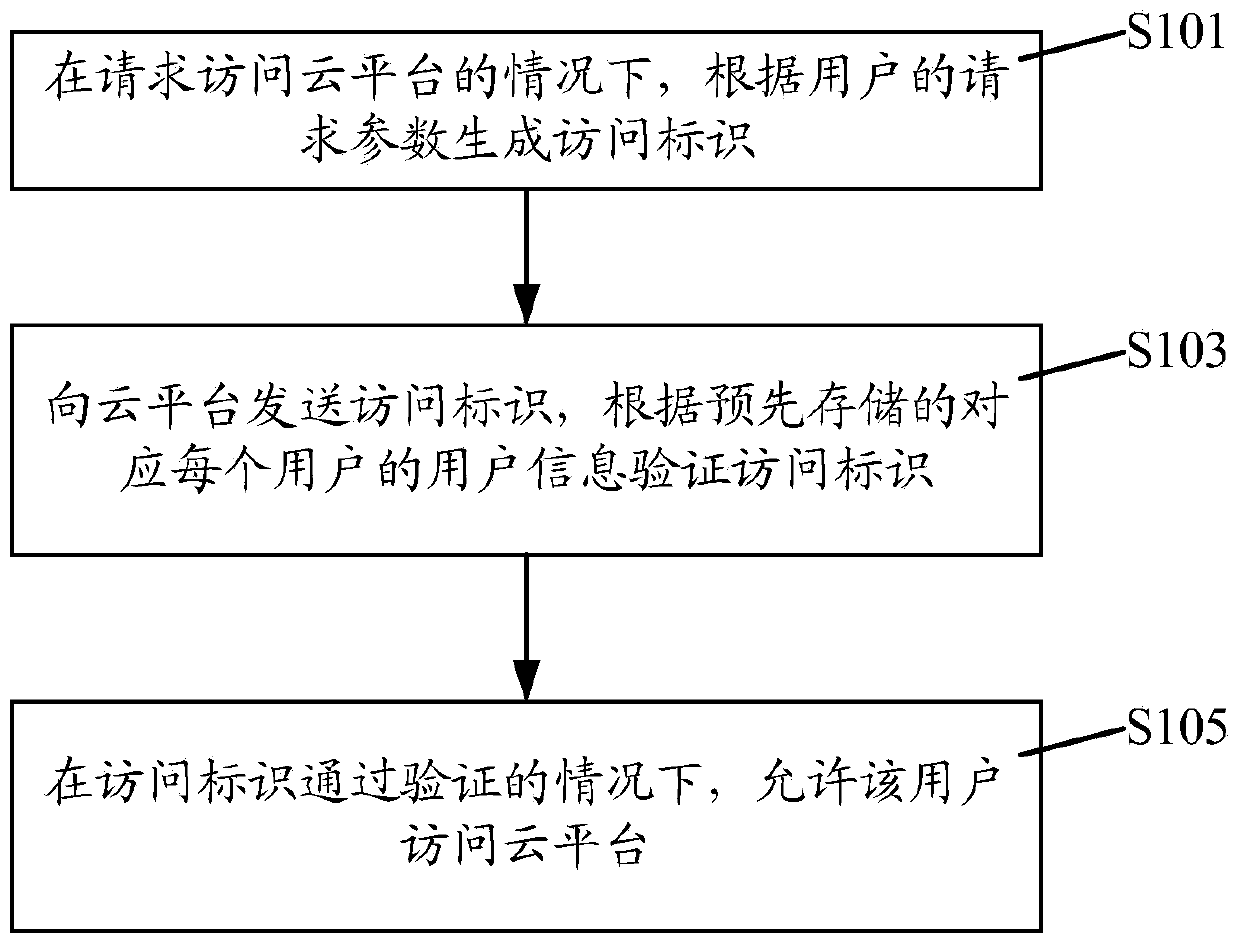
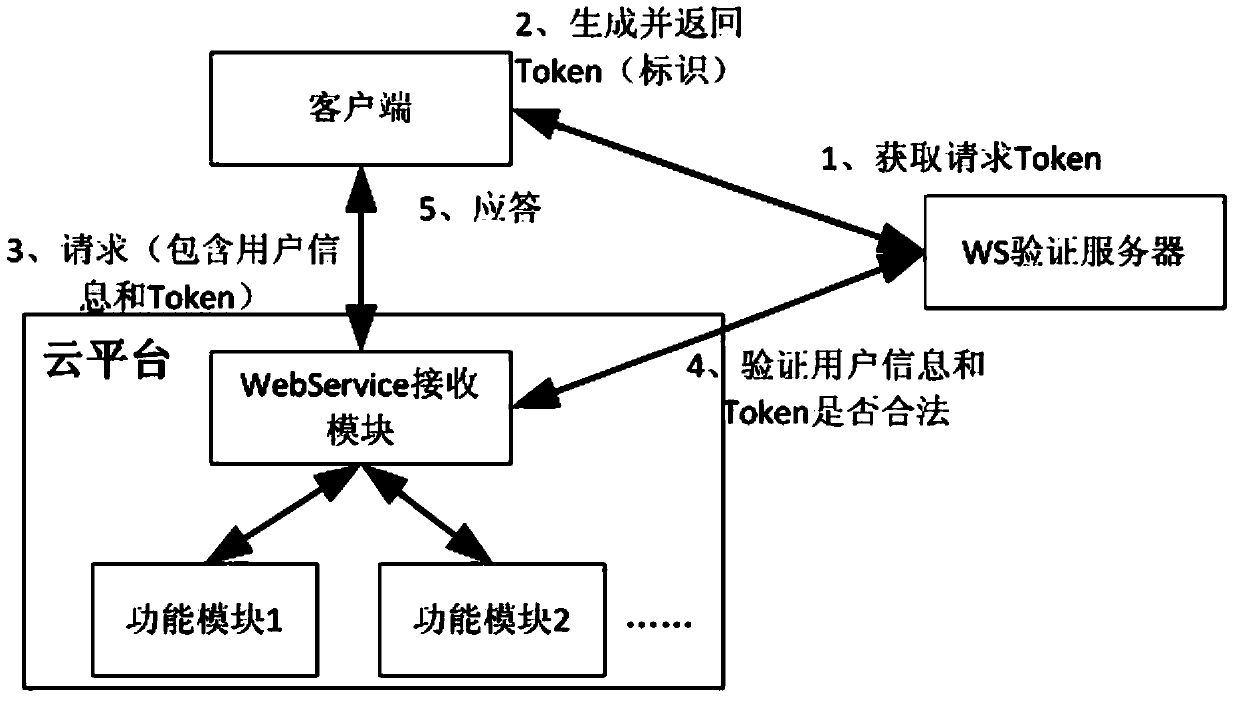
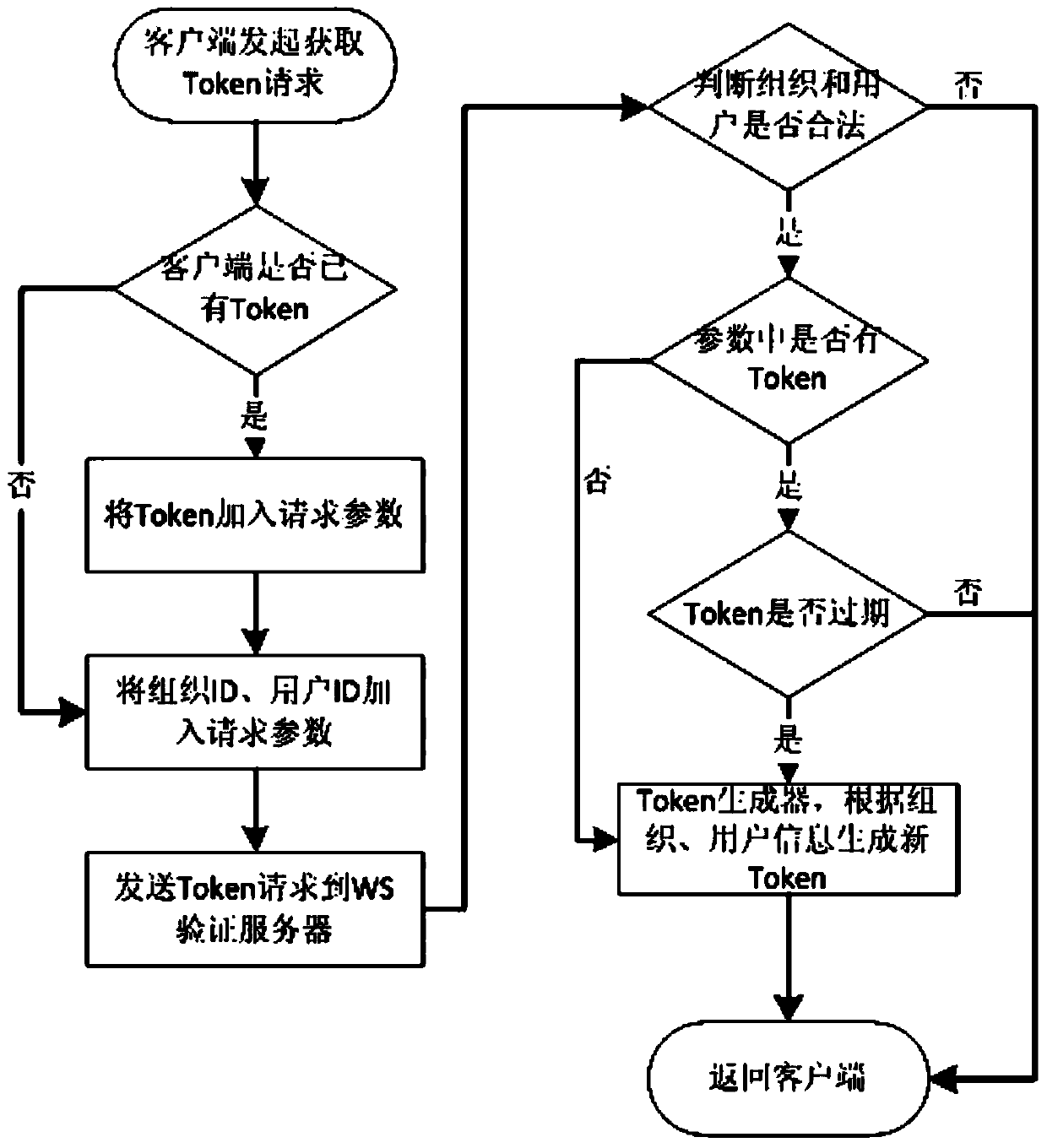
Cloud platform access method and device
ActiveCN103747076AHigh security mechanismAvoid malicious accessDigital data protectionTransmissionAccess methodUser information
The invention discloses a cloud platform access method and a cloud platform access device, wherein the cloud platform access method comprises the following steps that under the condition of requesting to access a cloud platform, access marks are generated according to the request parameters of users; the access marks are sent to the cloud platform, and are verified according to the pre-stored user information corresponding to each user; under the condition that the access marks pass the verification, the users are allowed to access the cloud platform. The cloud platform access method and the cloud platform access device have the advantages that access marks are generated according to the request parameters of the users, in addition, the access marks are verified through the pre-stored user information, and the effect of allowing the users to access the cloud platform only under the condition that the access marks pass the verification is ensured, so the safety mechanism of the cloud platform is effectively improved, the malignant access of illegal users to the cloud platform is avoided, and the resource waste of the cloud platform is reduced.
Owner:DAWNING CLOUD COMPUTING TECH CO LTD
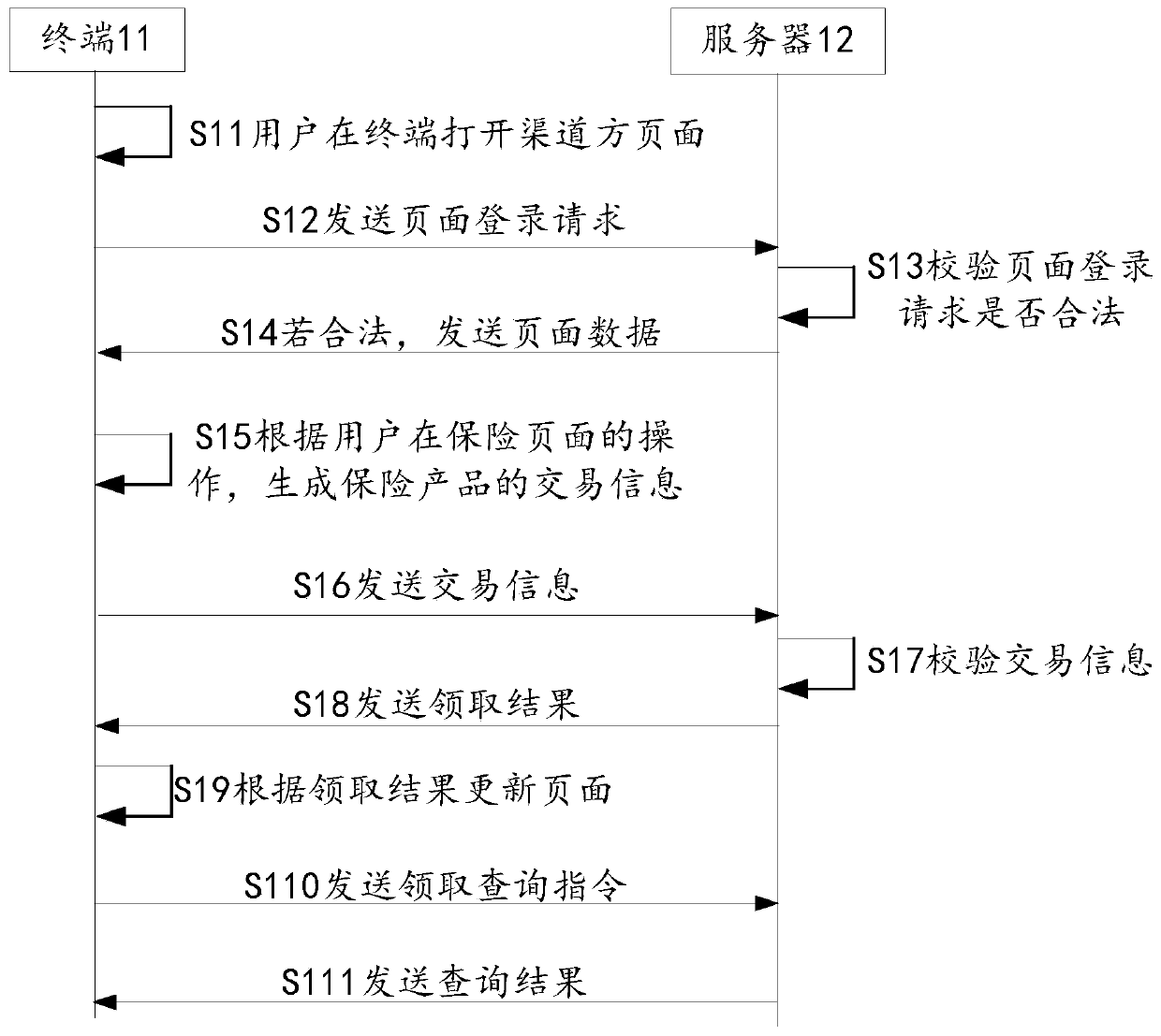
Page access method and device, server and page access system
ActiveCN111026950AAvoid malicious accessReduced impact on operational efficiencyDatabase updatingFinanceAccess methodSide information
The invention relates to the technical field of the Internet, in particular to a page access method and a device, a server and a page access system, the method comprises the following steps: acquiringa page login request sent by a terminal, the page login request carrying a login identifier and channel side information; when the channel party information is matched with preset channel comparisoninformation, obtaining at least one preset login comparison identifier belonging to the channel party information; and when the login identifier is matched with the login comparison identifier, sending page data to the terminal according to the page login request, thereby enabling the terminal to present a product page according to the page data. On one hand, the method can prevent an illegal channel party from maliciously accessing the server, so that the influence on the running efficiency of the server is reduced; and on the other hand, since the channel side supports multiple login modes,the method can broaden the traffic entry, and can also open the user to access the product page when the login identifier is matched with the login comparison identifier, thereby reducing the risk ofslowing down the operation efficiency due to malicious access.
Owner:微民保险代理有限公司
Price competition ranking method for website search result list
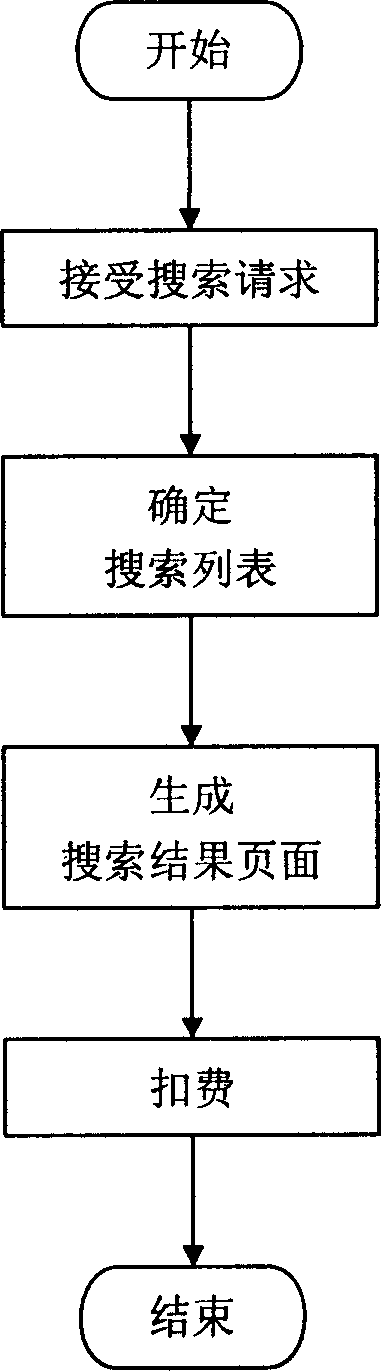
InactiveCN1801210AImprove experiencePost location is goodCommerceSpecial data processing applicationsRankingClick-through rate
The invention discloses a method for ranking the searching results according to the cost per impressions, cost per clicks. The method comprises: sustaining a database, in each account of information releaser having account balance item and at least one searching list; in each searching list having released information, at least one searching keyword and corresponding changeable cost per impressions value; the value of cost per impression can be set by setting cost per one click, and the database ranking with descending order according to searching keyword and cost per impression; after receiving searching request, confirming effective searching list that matches with the searching request; according to the pre-set website format, synthesizing the released information to be searching result page with specific order; reducing corresponding account balance with cost per impression or cost per click, taking a statistic of clicking rate and redirecting to the released website.
Owner:林赞松
Intelligent mobile storage equipment
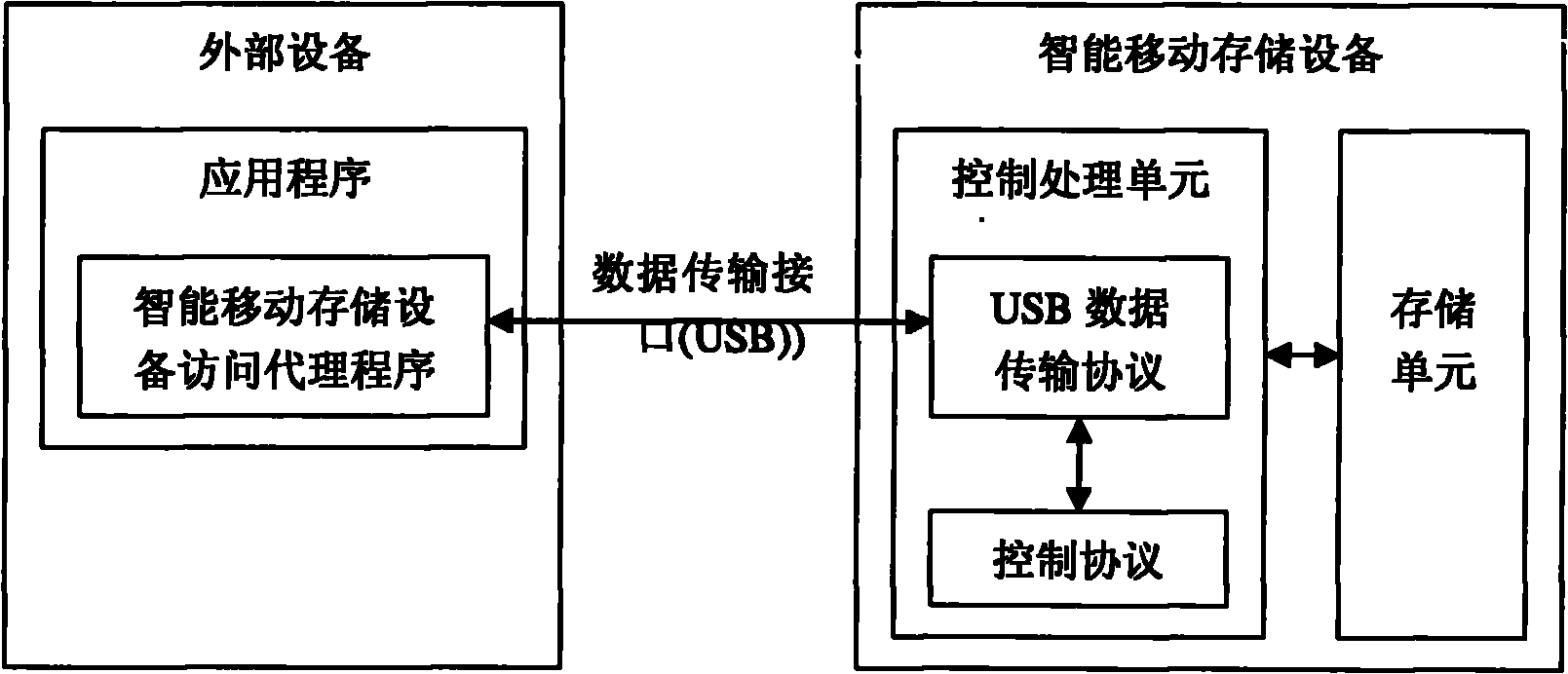
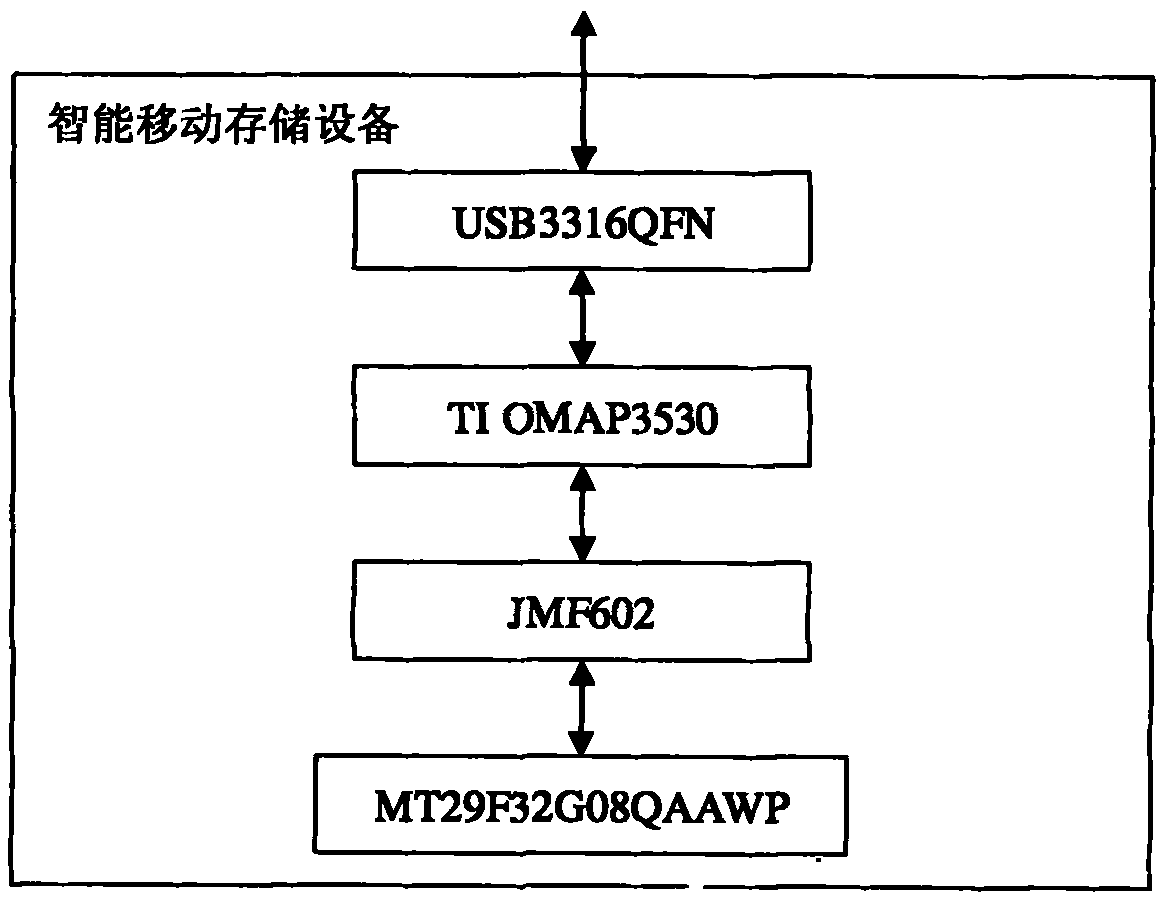
InactiveCN101944164AAvoid malicious accessImprove securityInternal/peripheral component protectionRemovable mediaData transmission
The invention discloses intelligent mobile storage equipment and relates to the technical field of mobile storage. The equipment comprises a control processing unit, a storage unit and a data transmission interface, wherein the control processing unit consists of a data transmission protocol and a control protocol which are mutually connected, and is provided with an independent main control chip and an independent and integrated on-chip operation system; the storage unit is mutually connected with the control processing unit and stores programs, data and information; and the data transmission interface is mutually connected with the data transmission protocol of the control processing unit and is an interface for the intelligent mobile storage equipment to communicate with external equipment. By embedding the on-chip operation system into the mobile storage equipment, malicious access to the mobile storage equipment by a computer and other external equipment can be effectively prevented, so the intelligent mobile storage equipment has high safety and independency.
Owner:TSINGHUA TONGFANG CO LTD
Tee access control method and mobile terminal implementing same
ActiveUS20190318087A1Avoid malicious accessAccess can be maliciousInternal/peripheral component protectionDigital data authenticationOperational systemApplication software
The present invention relates to a method for access control of a multimedia system to a secure operating system and a mobile terminal for implementing the method. The method includes the steps of: initiating an application access request for selecting a trusted application from a client application of a multimedia system to a secure operating system; making a decision as to whether the client application is a malicious application, and if not, proceeding to a next step, if yes, returning Selection Failure to the client application and performing an interrupt handling; sending the application access request from the multimedia system to the secure system; and acquiring, at the secure operating system, the trusted application based on the application access request and returning the trusted application to the multimedia system. The malicious accesses initiated by a malicious application to a trusted application in a securing operating system can be prevented without switching between systems, and the problem that a trusted application cannot be accessed due to malicious access can be avoided.
Owner:CHINA UNIONPAY
Safe data transmission method
ActiveCN105657699AEnsure safetyAvoid malicious accessSecurity arrangementClient-sideData transmission
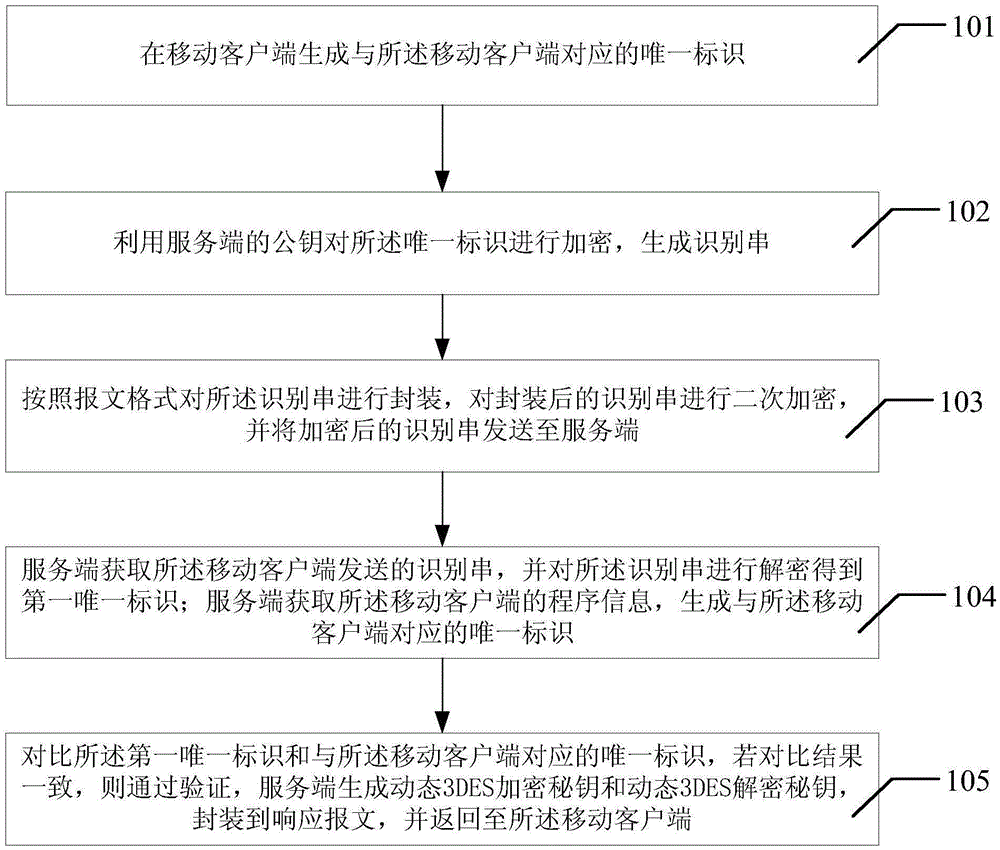
The application discloses a safe data transmission method which comprises the following steps: generating a unique identifier corresponding to a mobile client on the mobile client; encrypting the unique identifier using the public key of a server to generate an identifying string; encapsulating the identifying string according to the message format; performing secondary encryption of the encapsulated identifying string and sending the encrypted identifying string to the server; obtaining the identifying string sent by the mobile client by the server, and decrypting the identifying string to obtain the first unique identifier; obtaining the program information of the mobile client by the server to generate unique identifier corresponding to the mobile client; and comparing the first unique identifier with the unique identifier corresponding to the mobile client, wherein if the comparison result indicates consistency, the verification is passed, the server generates a dynamic 3DES encryption key and a dynamic 3DES decryption key, encapsulates in a response message and returns to the mobile client.
Owner:北纬通信科技南京有限责任公司
Parameter sending method of storage chip of imaging box, storage chip and imaging box
ActiveCN103879157AAchieve protectionAvoid malicious accessVisual representatino by photographic printingInternal/peripheral component protectionEmbedded systemImaging equipment
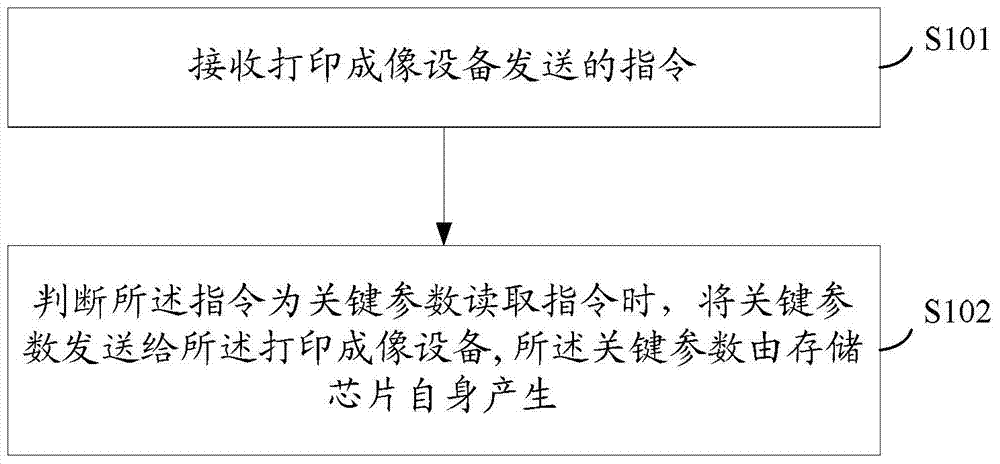
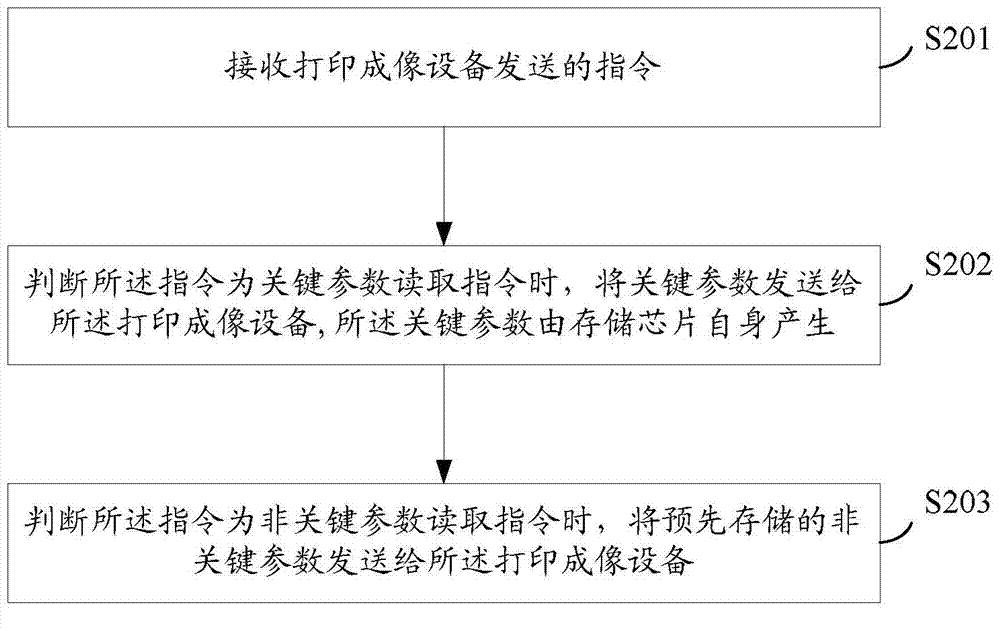
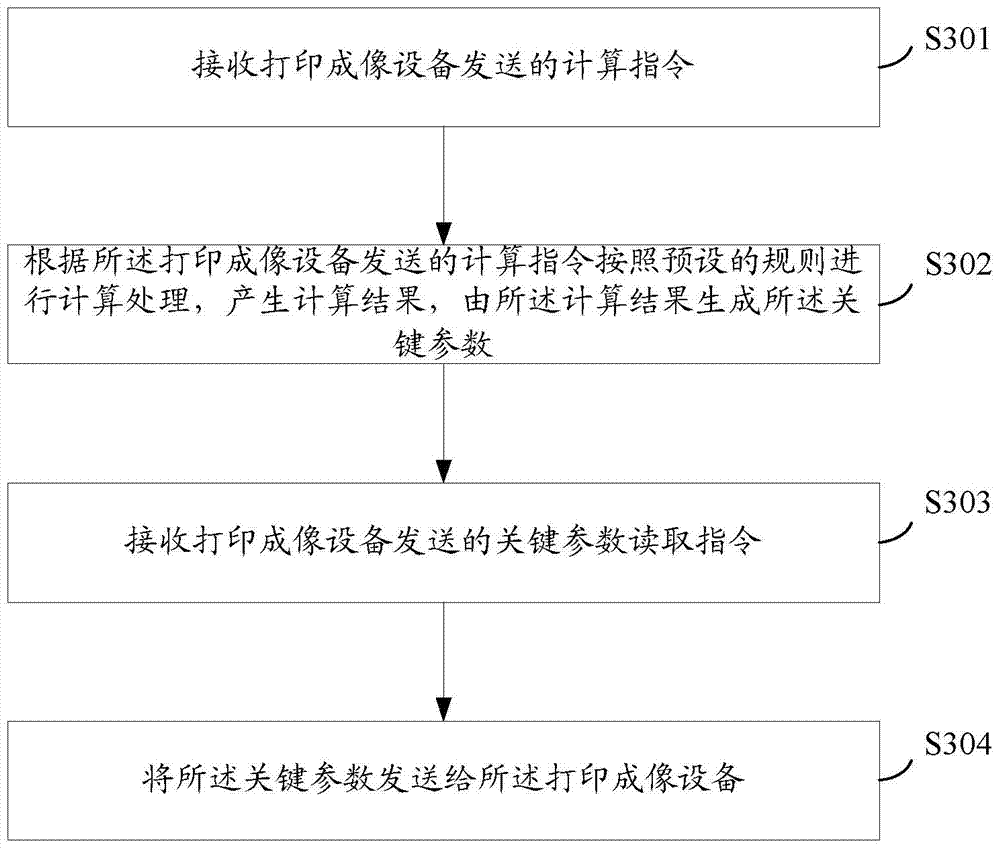
The invention provides a parameter sending method of a storage chip of an imaging box, the storage chip and the imaging box. The method comprises the following steps of receiving an instruction sent by printing imaging equipment, and sending a key parameter to the printing imaging equipment when the instruction is judged as the key parameter reading instruction, wherein the key parameter is generated by the storage chip. The parameter needing to be read by the printing imaging equipment is generated by the storage chip, when the printing imaging equipment sends the reading instruction, the parameter generated by the storage chip is sent to the printing imaging equipment, the parameter cannot be directly read by the printing imaging equipment at any time, and therefore certain important parameters in the storage chip can be prevented from being obtained maliciously. Furthermore, a compatible manufacturer or an original manufacturer of the storage chip does not need to store the complete and specific parameter in the storage chip, a competitor can be prevented from directly reading the storage chip and obtaining certain important parameters, and therefore certain important parameters in the storage chip can be protected.
Owner:APEX MICROELECTRONICS CO LTD
Terminal equipment and configuration method thereof
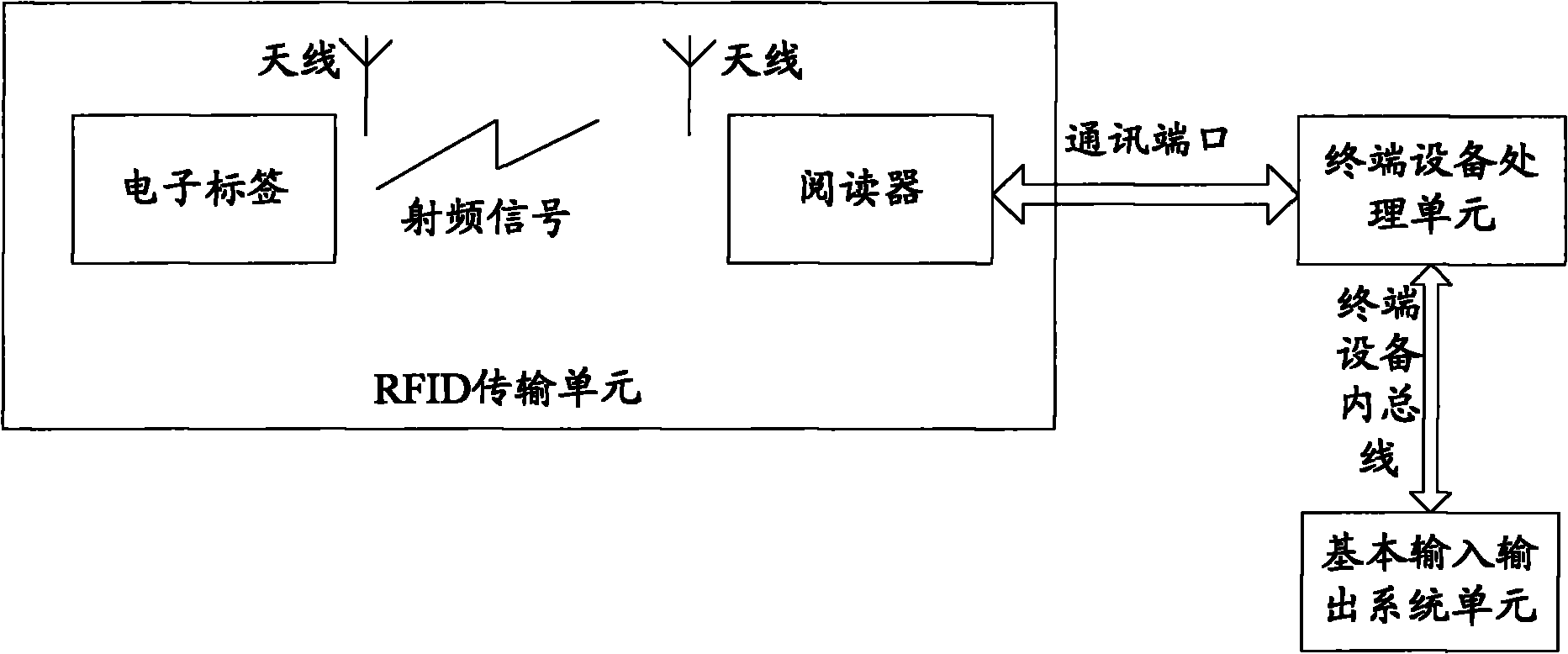
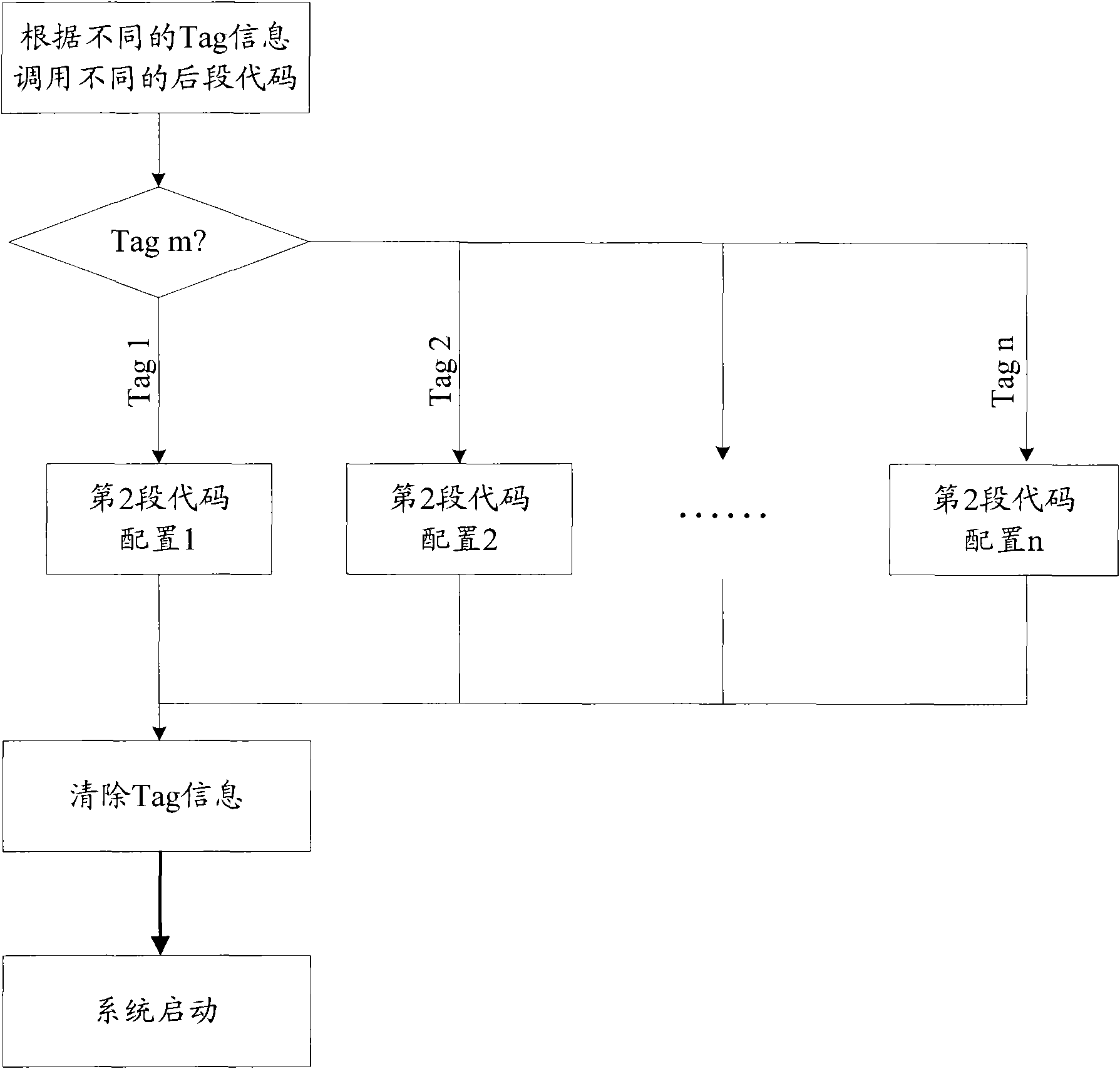
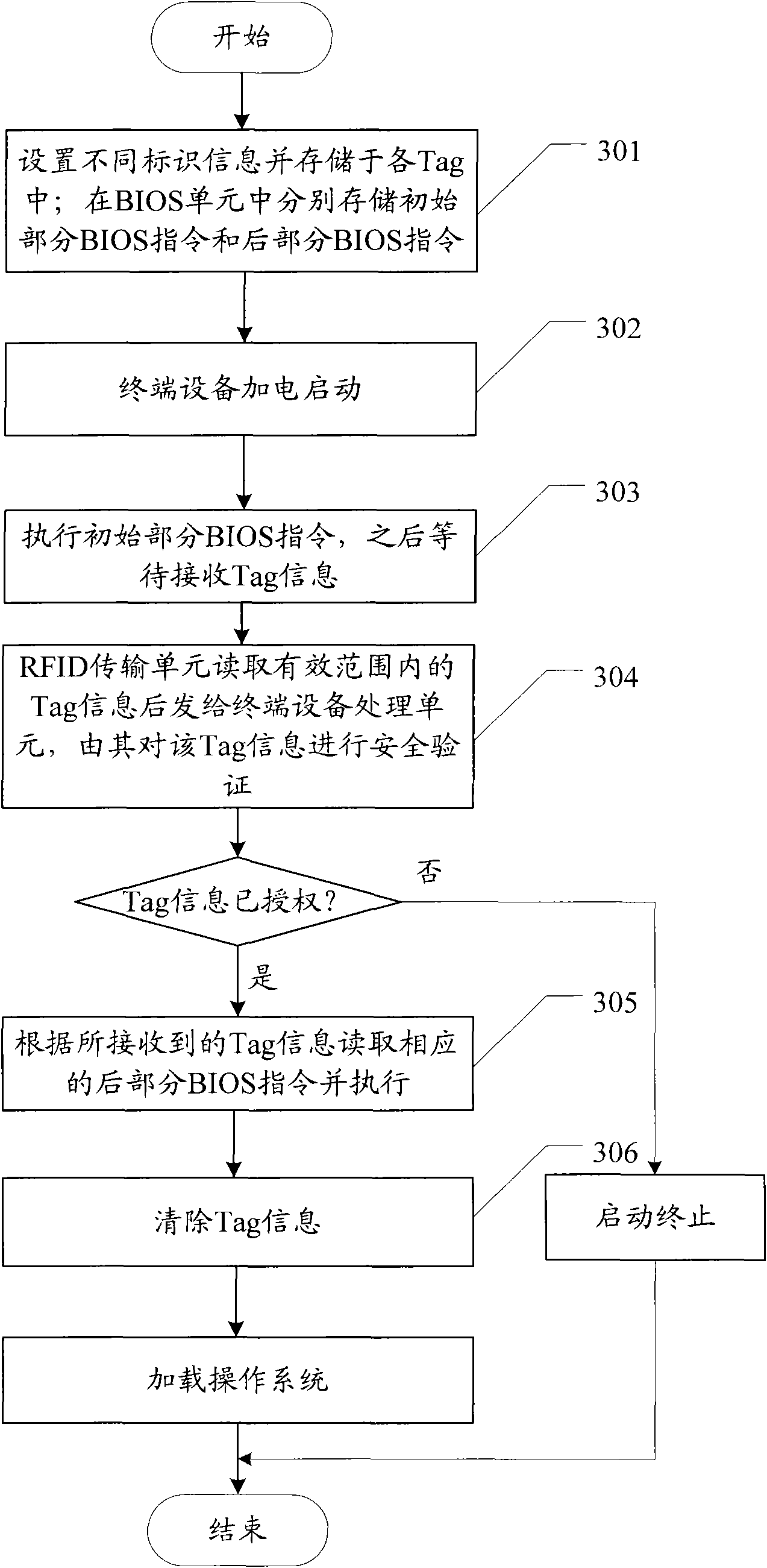
InactiveCN101937494ANot easy to damageLow costComputer security arrangementsProgram loading/initiatingElectricityTerminal equipment
The invention discloses terminal equipment and a configuration method thereof. The configuration method comprises that: when the terminal equipment is powered up and started, a processing unit of the terminal equipment executes an initial part BIOS command to initialize a communication port and wait for receiving Tag information; and after the communication port is initialized, an RFID transmission unit reads the Tag information in a valid range and transmits the Tag information to the processing unit of the terminal equipment, and the processing unit of the terminal equipment executes a corresponding rear part BIOS command according to the Tag information for configuration. The method implements hardware configuration and operation authority setting on the terminal equipment in an RFID mode, meets the requirement that different users in an industrial field have different operation authorities on the same terminal equipment and the requirement that different operation modes have different hardware configurations, fully shows the characteristics of no influence of environment, hard damage, low cost, and intensified security of the system.
Owner:深圳市研祥通讯终端技术有限公司
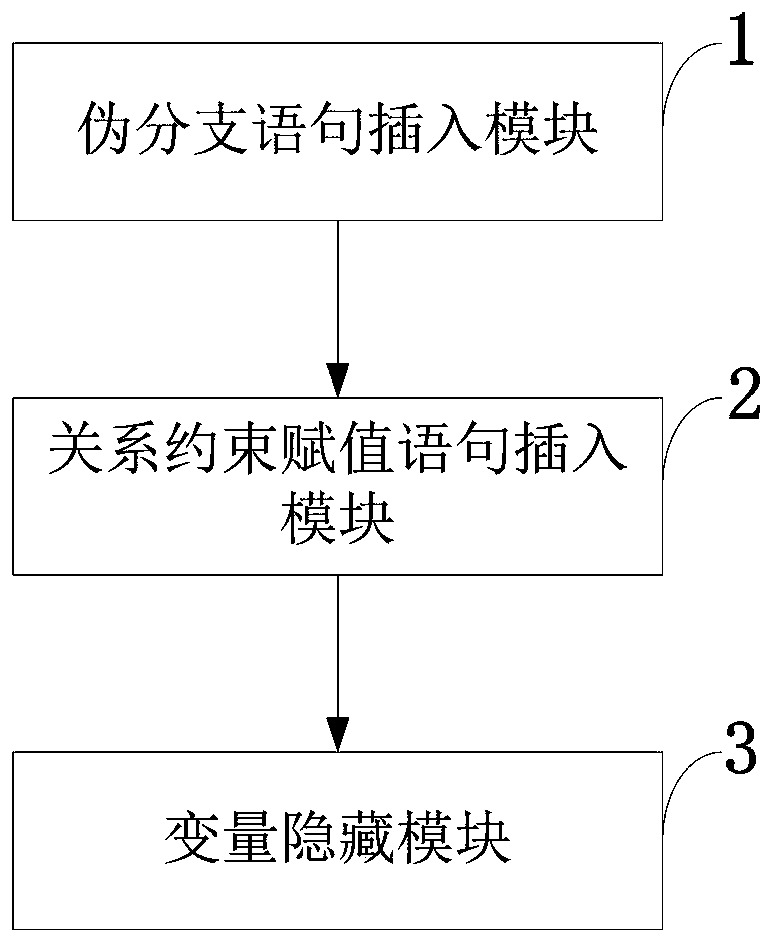
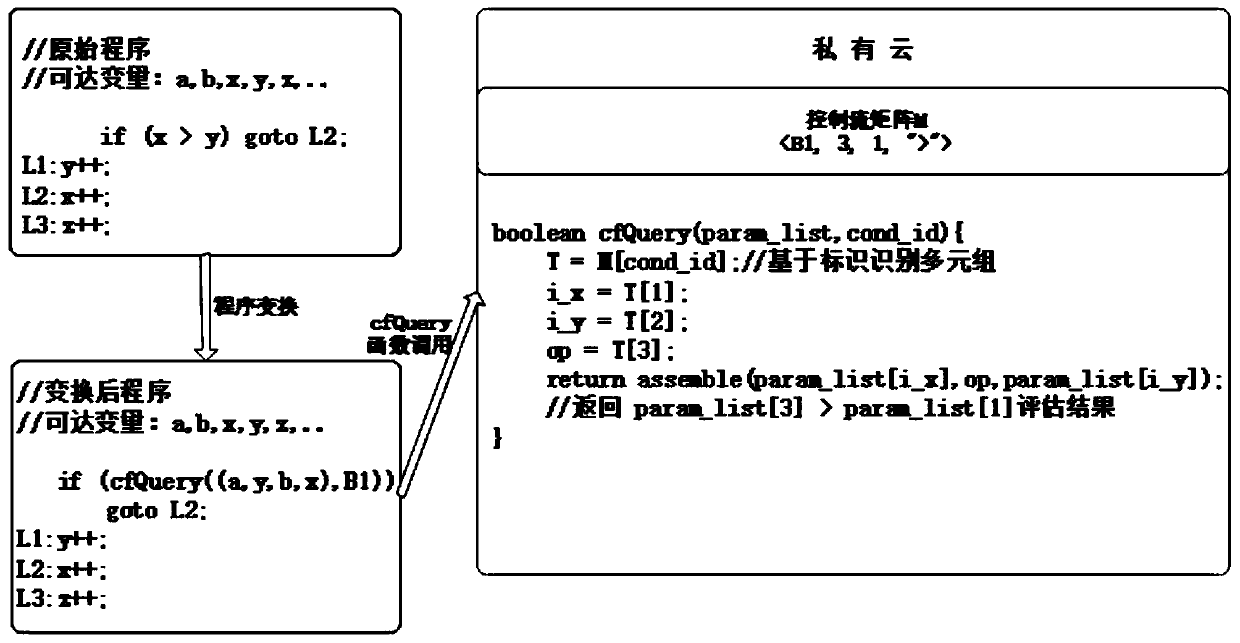
Program control flow obfuscation method and system, storage medium, cloud server and application
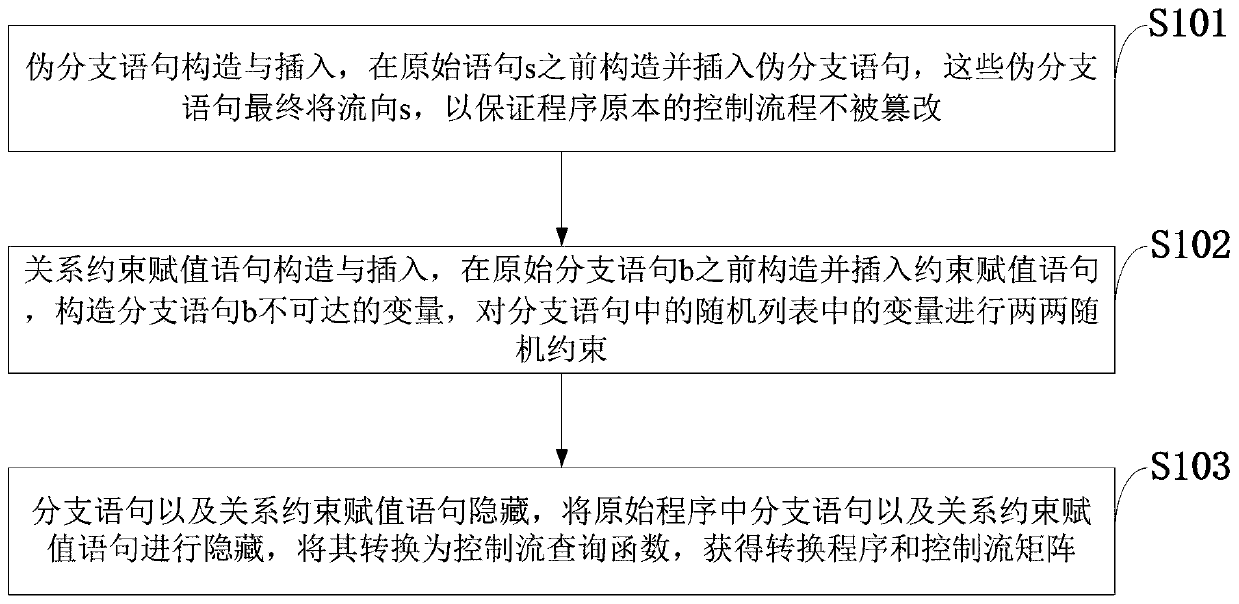
PendingCN111538962AHigh Control Flow ConfidentialityPrevent malicious tamperingProgram/content distribution protectionData streamProgram logic
The invention belongs to the technical field of control flow obfuscation, and discloses a program control flow obfuscation method and system, a storage medium, a cloud server and an application. Branch statement judgment conditions in an original program are hidden, and a control flow query function is used for replacing the branch statement judgment conditions; the control flow is further obfuscated by inserting a pseudo-branch statement into the program; the conversion program is sent to an untrusted public cloud, and a control flow matrix is sent to a trusted private cloud; and the conversion program is run on the public cloud based on the control flow matrix. According to the invention, the variable of each branch statement condition can be hidden, so that application program logic isprevented from being maliciously acquired and utilized by an external attacker; a pseudo branch statement is inserted to increase the difficulty of reconstructing a program control flow by an attacker; and a relation constraint statement is inserted, and data flow consistency check is carried out, so that an attacker is resisted to actively change the running process of a program, and new data ispurposefully added in the program running process to collect effective information.
Owner:XIDIAN UNIV
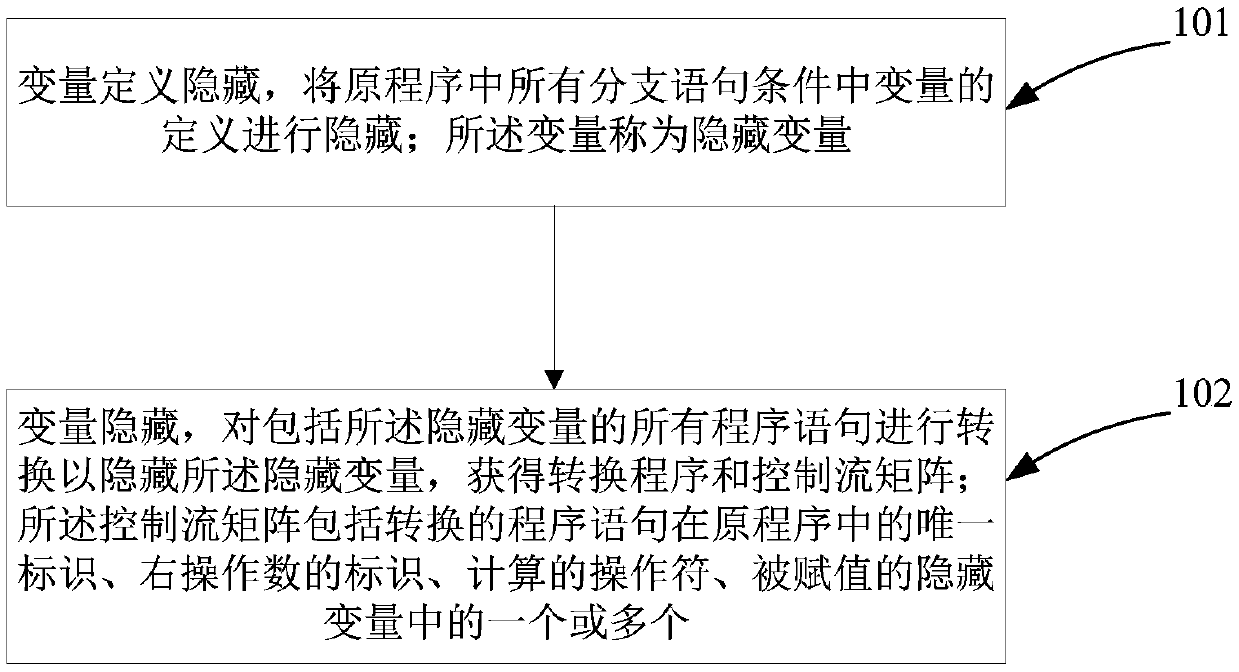
The invention discloses an SGX-based program control flow obfuscation method and system
ActiveCN109614774AAvoid malicious accessReduce total usageDigital data protectionProgram/content distribution protectionControl flowObfuscation
The invention discloses an SGX-based program control flow obfuscation method and system, and the method comprises the steps: hiding the definitions of variables in all branch statement conditions in an original program, and enabling the variables to be called hidden variables; converting all program statements including the hidden variable to hide the hidden variable, and obtaining a conversion program and a control flow matrix; T; sending the conversion program and the control flow matrix are sent to a remote computing unit, the conversion program is stored in an untrusted environment of theremote computing unit, and the control flow matrix is stored in a trusted environment SGX Enclave of the remote computing unit; and executing the conversion program in the remote computing unit basedon the control flow matrix. According to the method, a program transformation technology and an Intel software protection expansion technology are combined, conditions of each branch statement are converted, the branch statements are evaluated and moved to an opaque and credible hardware execution environment, and therefore high control flow confidentiality is guaranteed.
Owner:XIDIAN UNIV
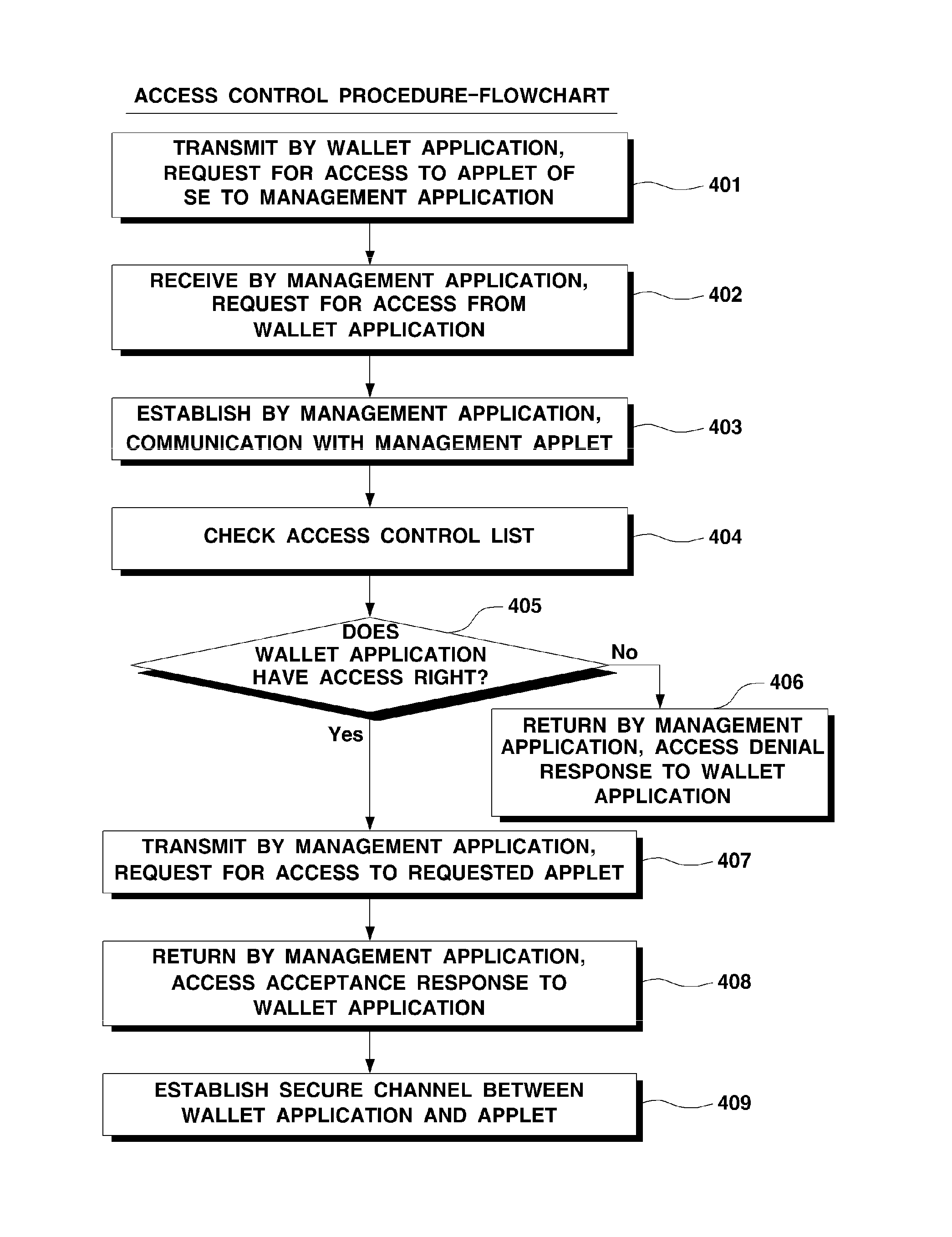
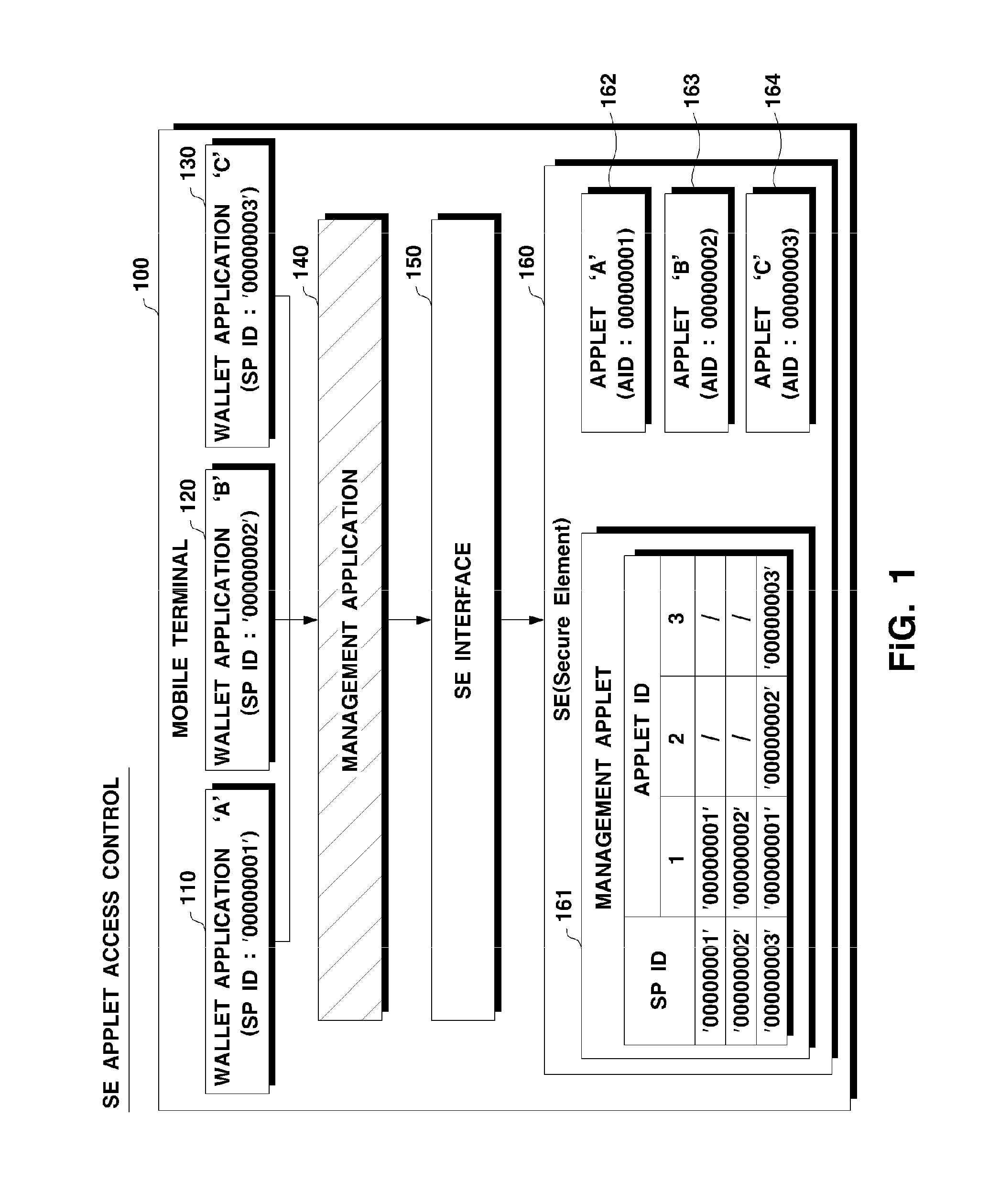
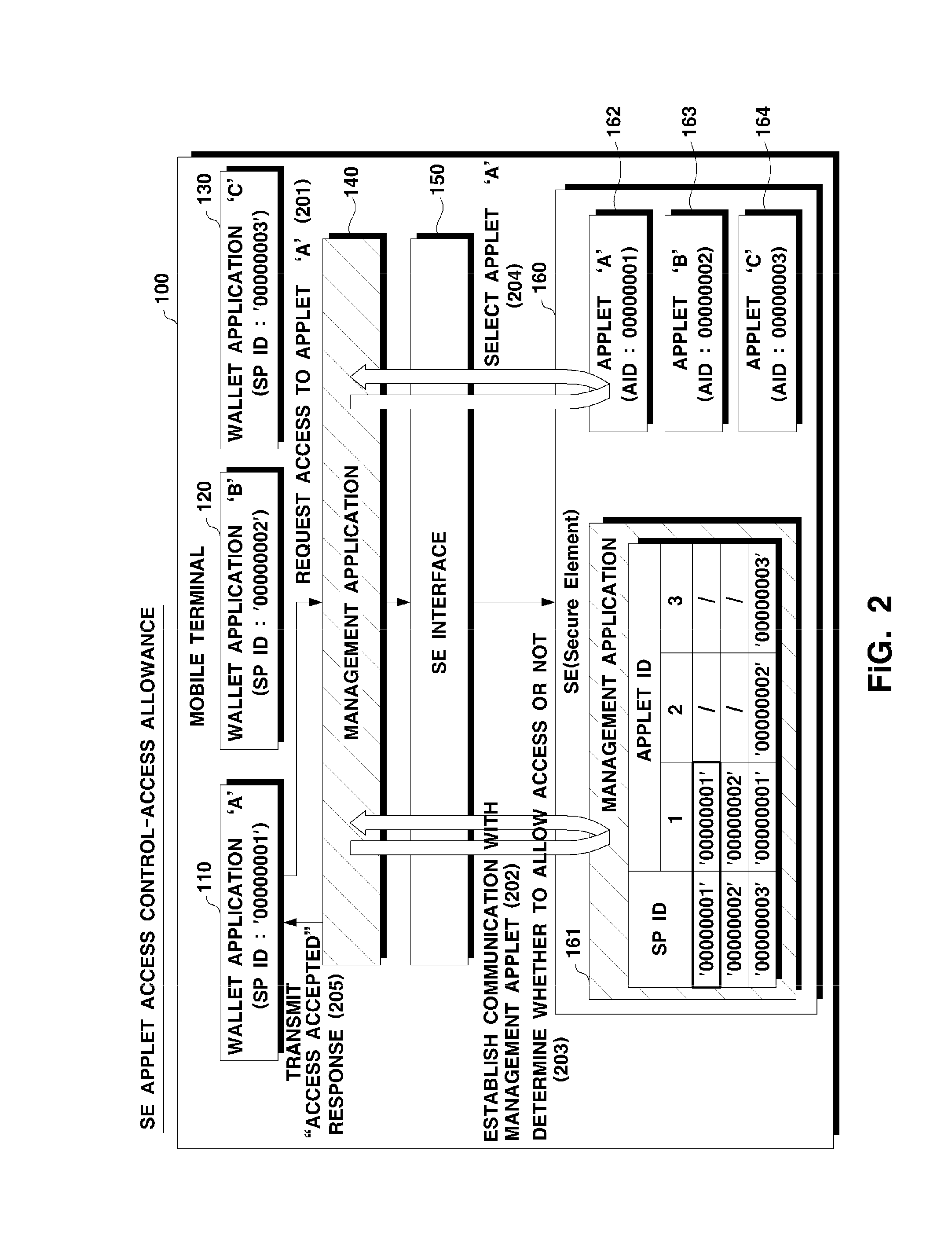
System and method for controlling access to applet
InactiveUS20140344899A1Increase safetyPrevents malicious accessDigital data processing detailsDigital data protectionApplication softwareProgram control
Owner:MOZIDO CORFIRE - KOREA
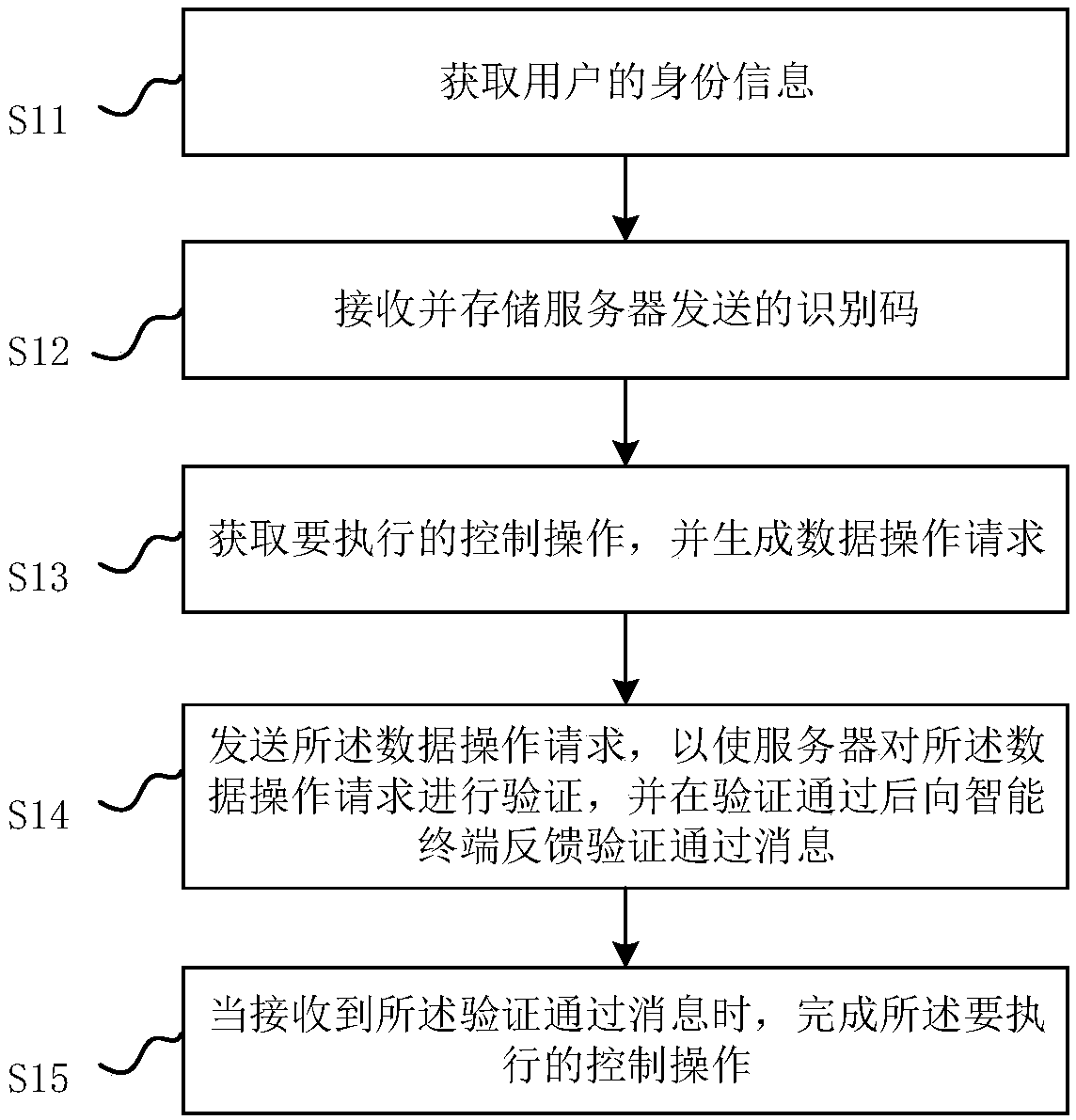
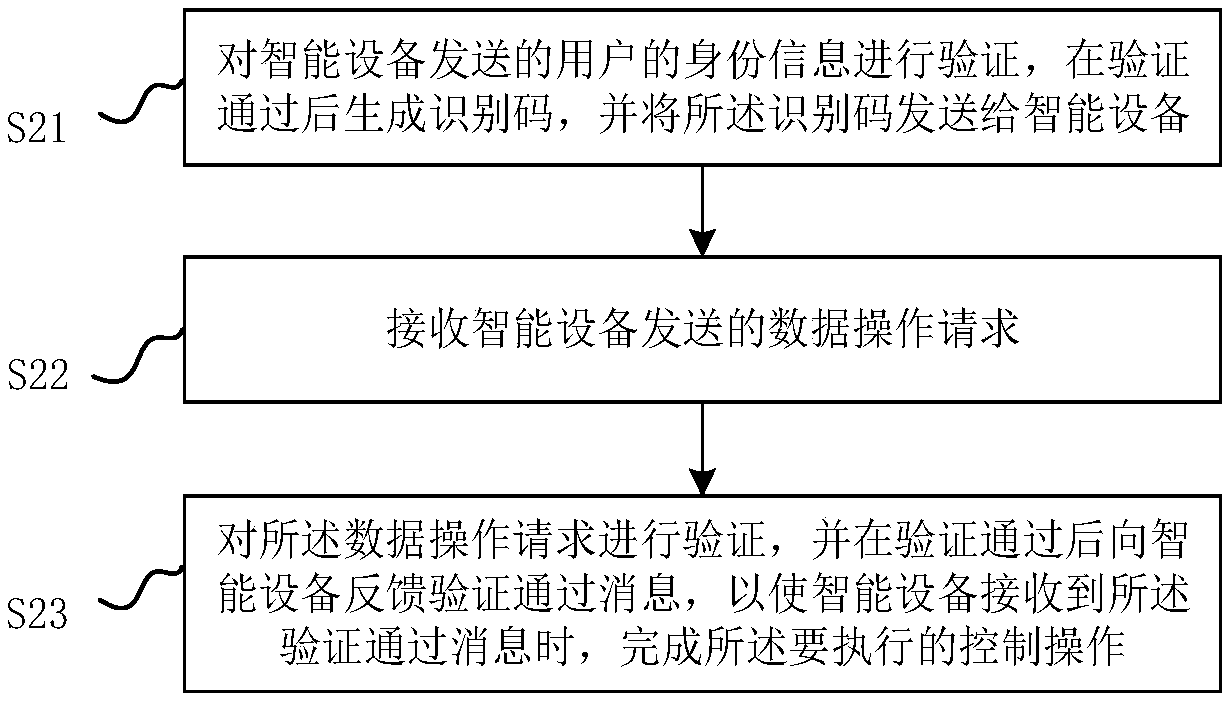
Intelligent device control method, intelligent device and server
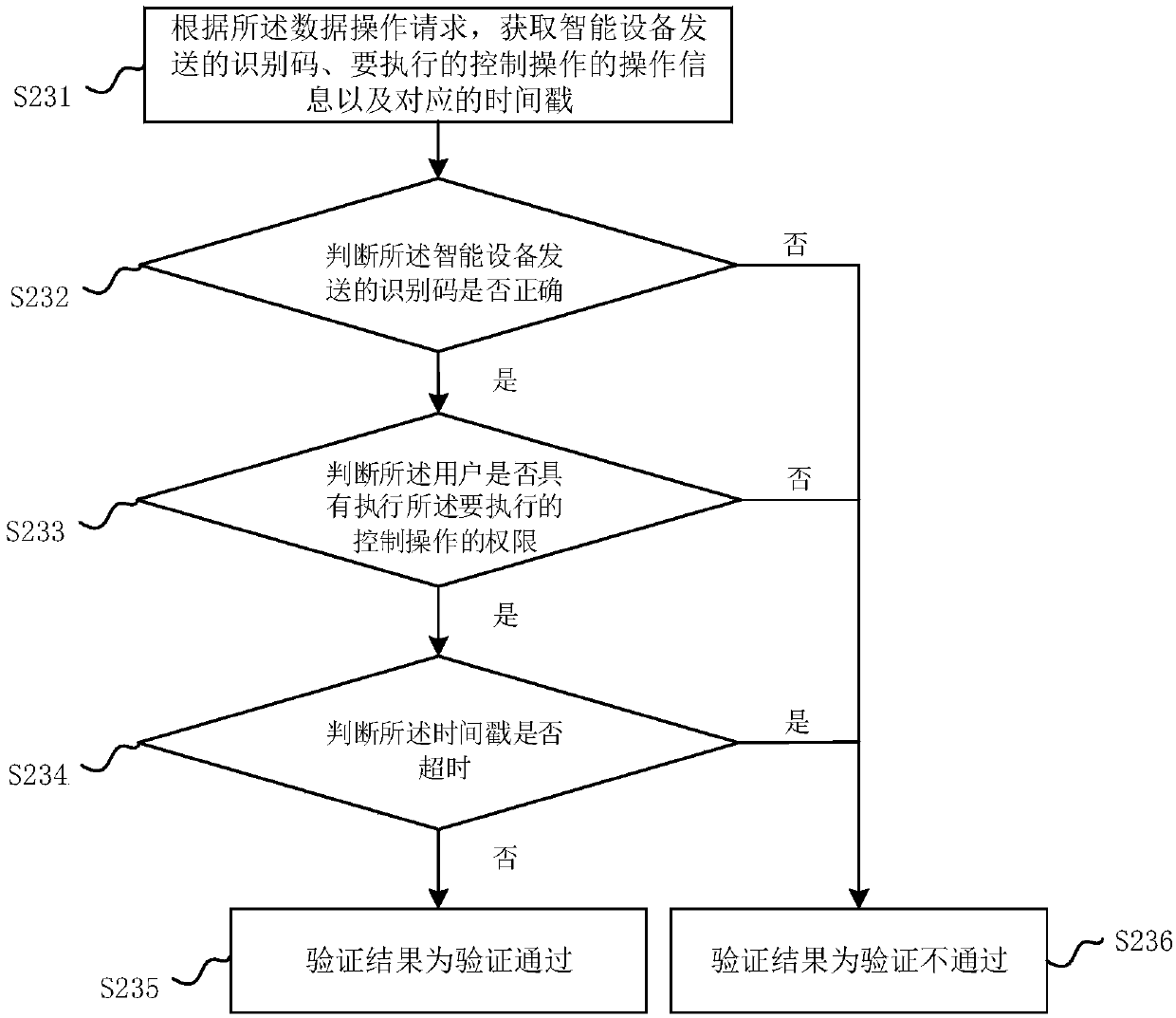
InactiveCN109101797APrevent leakageAvoid malicious accessDigital data protectionDigital data authenticationData operationsIntelligent equipment
The invention relates to an intelligent device control method, an intelligent device and a server. The method comprises steps: receiving and storing an identification code sent by the server; acquiring a control operation to be executed and generating a data operation request, the data operation request comprising: the identification code and operation information of the control operation to be executed; sending the data operation request so that the server verifies the data operation request and feeds back the verification passing message to the intelligent terminal after the verification passes; when the verification pass message is received, the control operation to be performed being completed. The invention completes the first verification through the setting of the identification code, and completes the second verification through the processing of the data operation request. The intelligent device control method of the invention can effectively prevent the user information frombeing accessed maliciously, avoid data leakage, and ensure the safety of the user information through secondary verification.
Owner:GREE ELECTRIC APPLIANCES INC
Binning data processing method, device and equipment, storage medium and program product
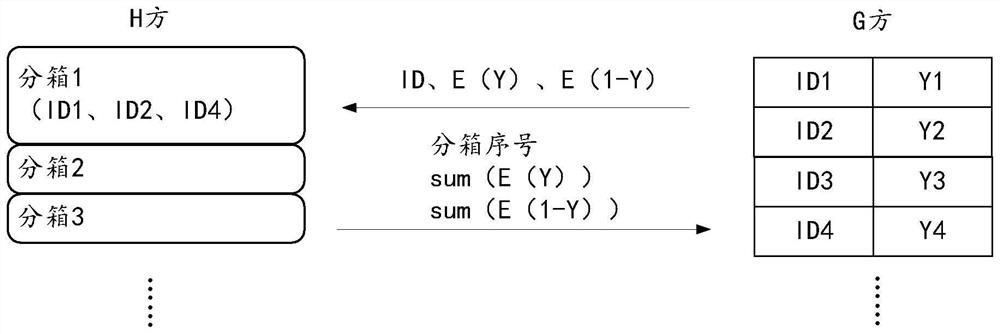
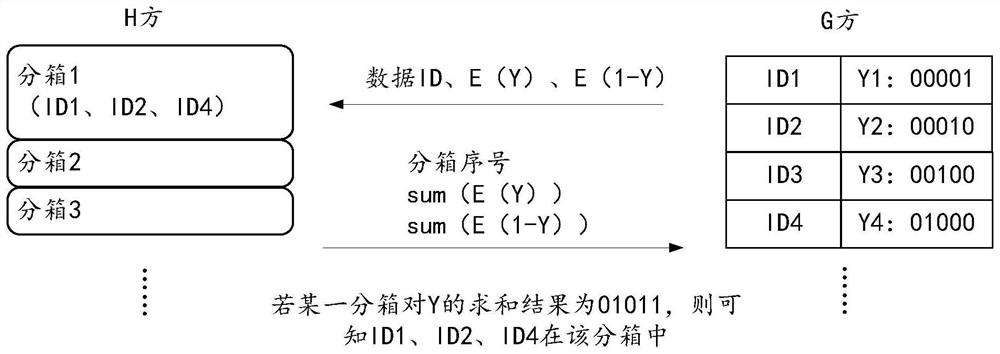
PendingCN113704799AAvoid malicious accessImprove interaction securityDigital data protectionPositive sampleTheoretical computer science
The invention discloses a binning data processing method, device, equipment, a storage medium and a program product, and the method comprises the steps: obtaining a plurality of data IDs sent by a target variable provider, an encrypted target variable corresponding to each data ID, and an encrypted opposite variable, and calculating an encrypted positive sample proportion and an encrypted negative sample proportion corresponding to each sub-box, multiplying the encrypted positive sample proportion and the encrypted negative sample proportion by corresponding random numbers, and sending multiplication results to a target variable provider, and obtaining an intermediate result corresponding to each sub-box determined by the target variable provider according to the multiplication result, and sending the encrypted information value and / or a result obtained by adding the random number to the evidence weight to the target variable provider according to the intermediate results corresponding to the plurality of sub-boxes and the corresponding random number. According to the method, the security of solving the information value and the evidence weight can be improved.
Owner:WEBANK (CHINA)
Electric power system basic data lean processing method
InactiveCN105117822AReduce workloadRealize managementResourcesStatistical analysisElectric power system
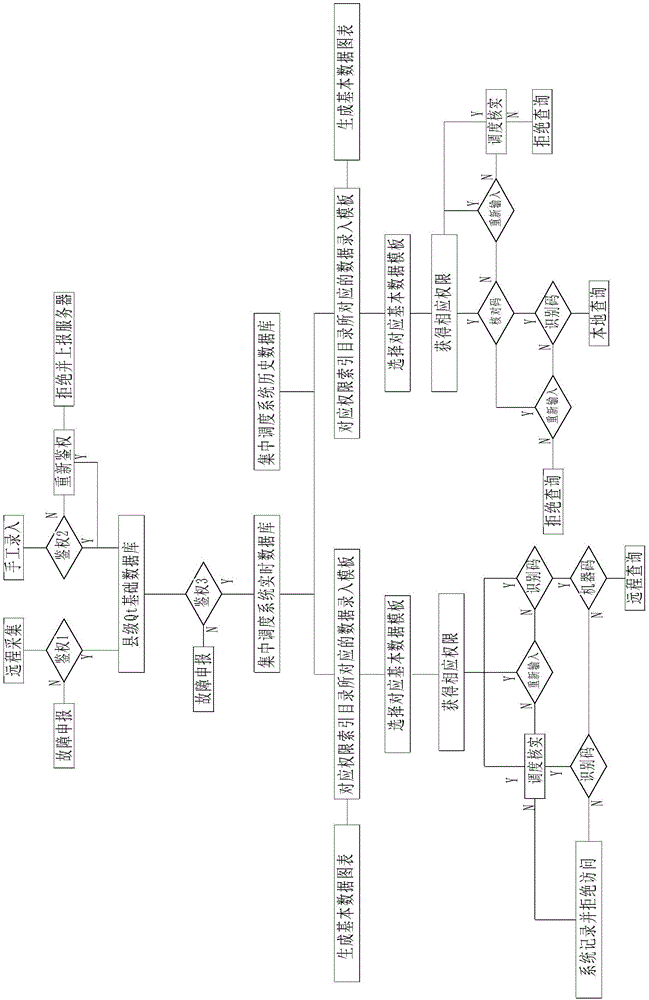
The invention belongs to the electric power system field and discloses an electric power system basic data lean processing method. The method comprises the following steps that electric power organizations at all levels have Qt basic databases of various levels input in a classified and authority-diversified way and perform remote data exchanges with a centralized scheduling system real-time database and a centralized scheduling system historic database through the Qt basic databases of various levels; when corresponding data are to be retrieved, authority authentication is performed on a query person; the query person passing the authority authentication can inquire classified statistical graphically-displayed basic data within the corresponding authority; and the basic data are displayed on templates of corresponding diversified types. By means of the method with the above-mentioned technical scheme, personnel authority determination and access range setting of input data and access data can be achieved. Rapid visualized statistics of the basic data can be also realized. Modularized management is further achieved. The basic data statistical analysis efficiency can be further improved. The workload of workers is further reduced.
Owner:国网山东沂南县供电公司 +1
Novel cross-network data exchange mode and communication method
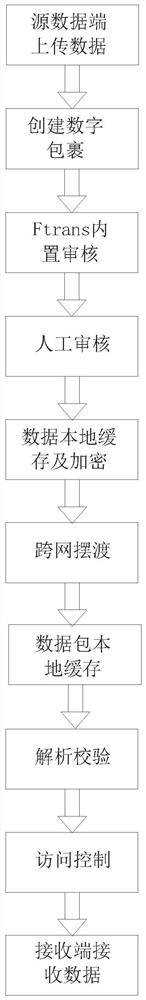
The invention discloses a novel cross-network data exchange mode and a communication method, the novel cross-network data communication method comprises the following steps: firstly, uploading data bya source data end, then creating a digital package, then carrying out technical auditing, then carrying out manual auditing, then carrying out data local caching and encryption, and then carrying outcross-network ferry; and performing data packet local caching, then performing analysis and verification, and finally performing access control and data receiving. According to the invention, the Ftrans cross-network file security exchange system is adopted to carry out cross-network transmission of the file, compared with the traditional exchange mode, the transmission speed is faster, and in addition, the anti-virus and sensitive information detection functions are realized. According to the invention, the encryption unit is arranged in the communication method, so that the security in thefile transmission process can be further improved; and the novel cross-network data exchange mode and the communication method have a temporary storage function, file exchange does not need to be carried out again in a short time, and when the time from last exchange is too long, only the cloud needs to be logged in to download data.
Owner:杭州奔浪信息技术有限公司
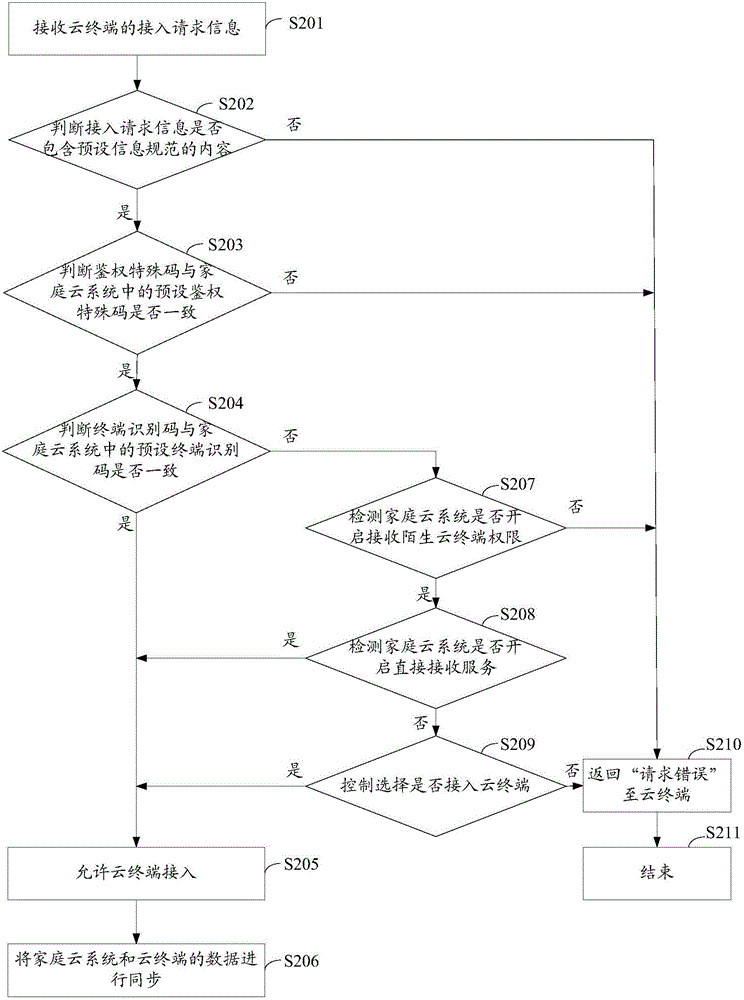
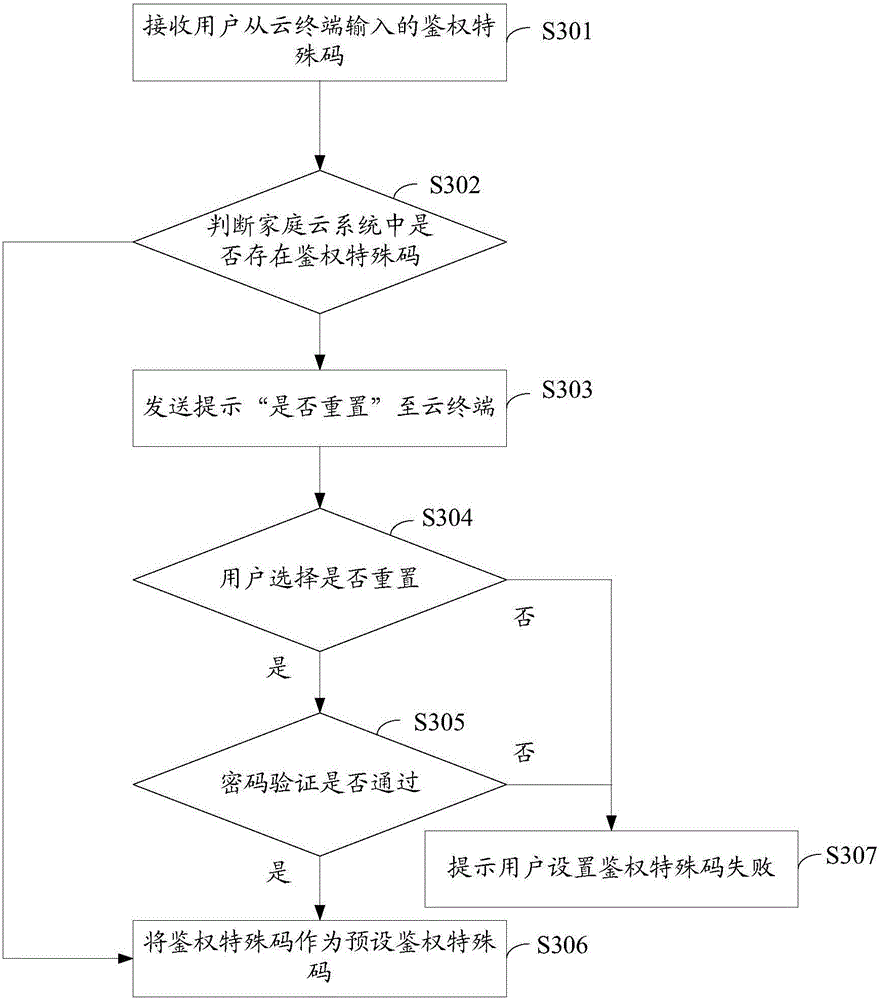
Method and system for accessing cloud terminal to home cloud system, and cloud access control equipment
InactiveCN105100082AImprove securityAvoid malicious accessSecurity arrangementHome automation networksControl equipmentStandardization
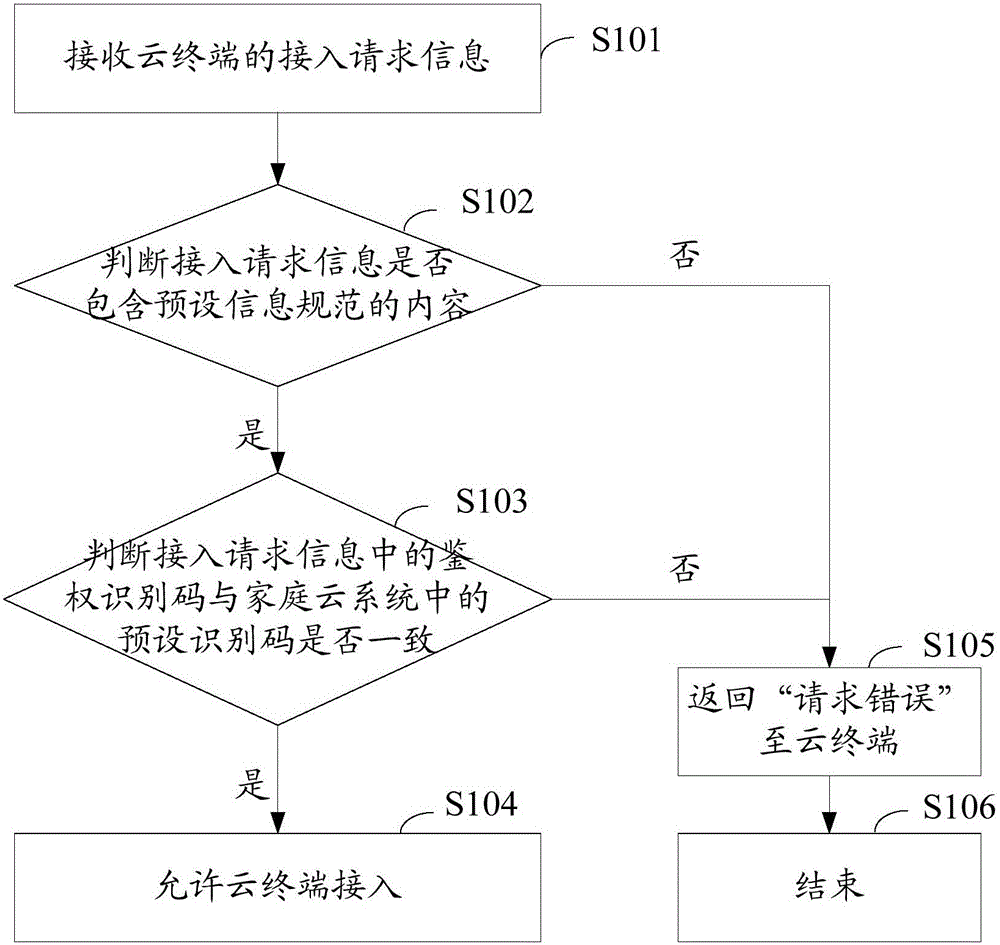
The embodiment of the invention provides a method for accessing a cloud terminal to a home cloud system. The method comprises the following steps: receiving an access request information of the cloud terminal; judging whether the access request information includes the content of pre-set information standardization or not, wherein the pre-set information standardization comprises an access manner, a request content and an authentication identification code; judging whether the authentication identification code in the access request information is the same to a pre-set identification code in the home cloud system or not if the access request information includes the content of the pre-set information standardization; and allowing to access the cloud terminal if the authentication identification code in the access request information is the same to the pre-set identification code in the home cloud system. The embodiment of the invention further provides cloud access control equipment and the home cloud system. By means of the manner, the cloud terminal can be prevented from being maliciously accessed to the home cloud system, and therefore, the security of the home cloud system is improved.
Owner:HUIZHOU TCL MOBILE COMM CO LTD
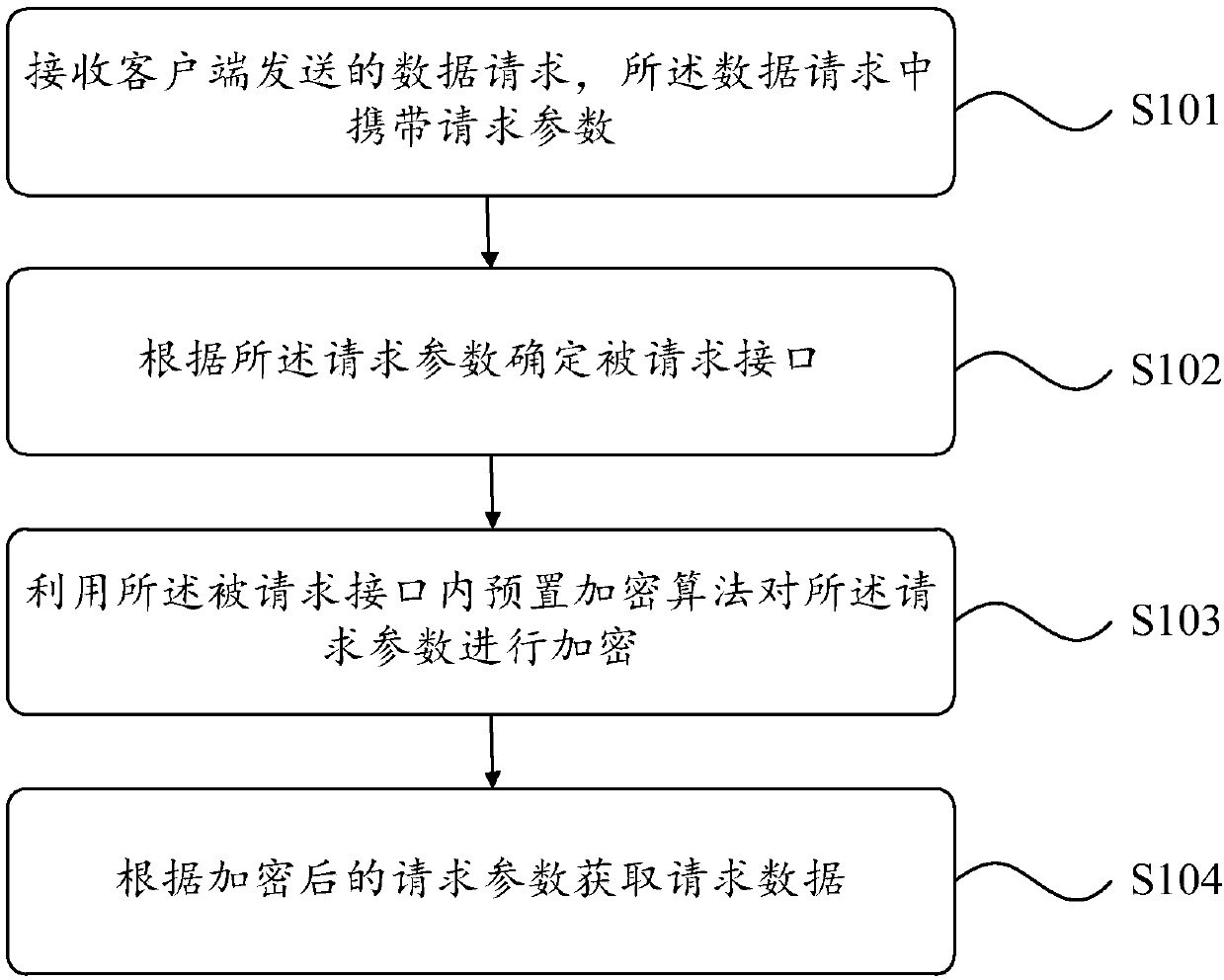
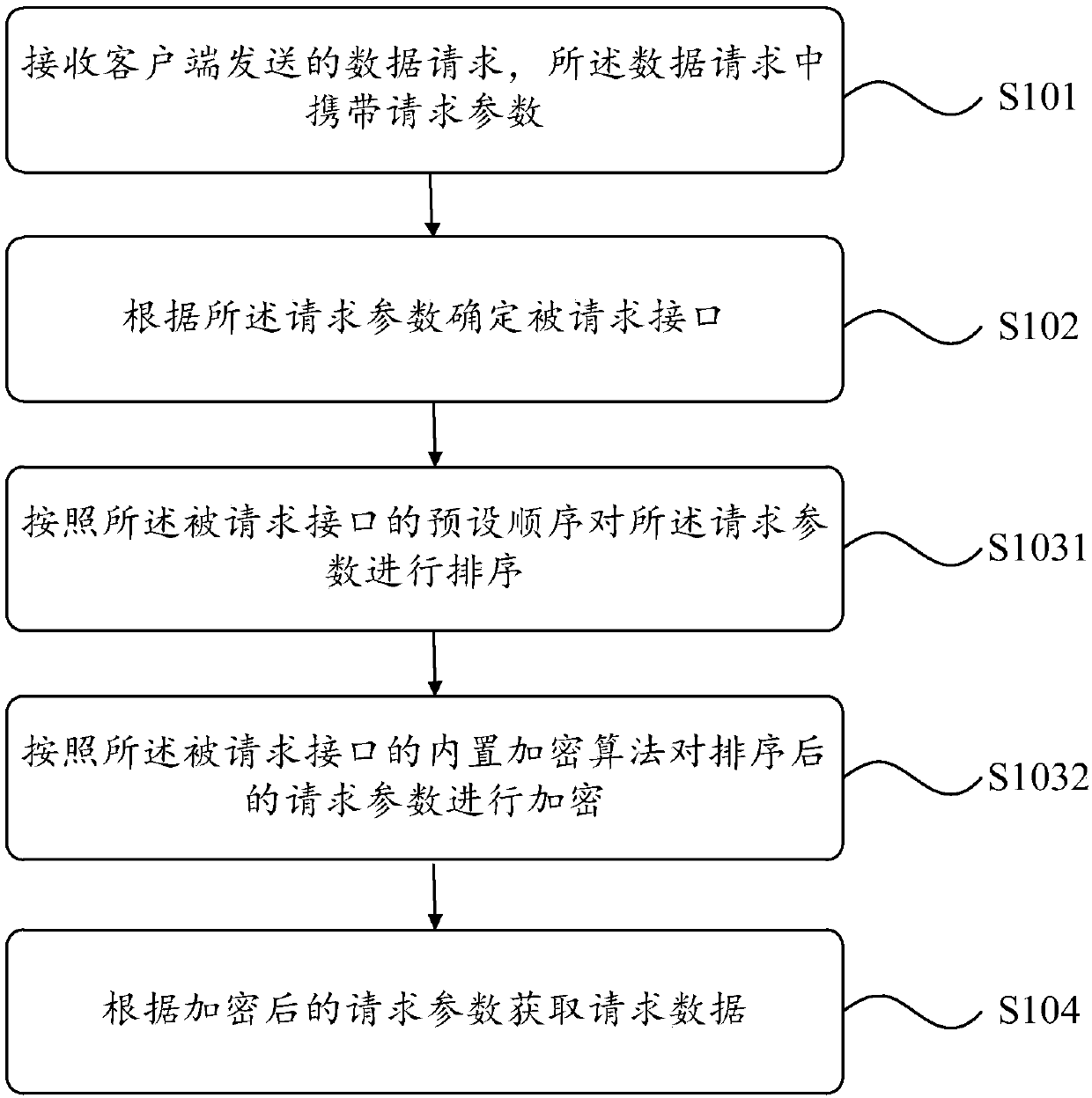
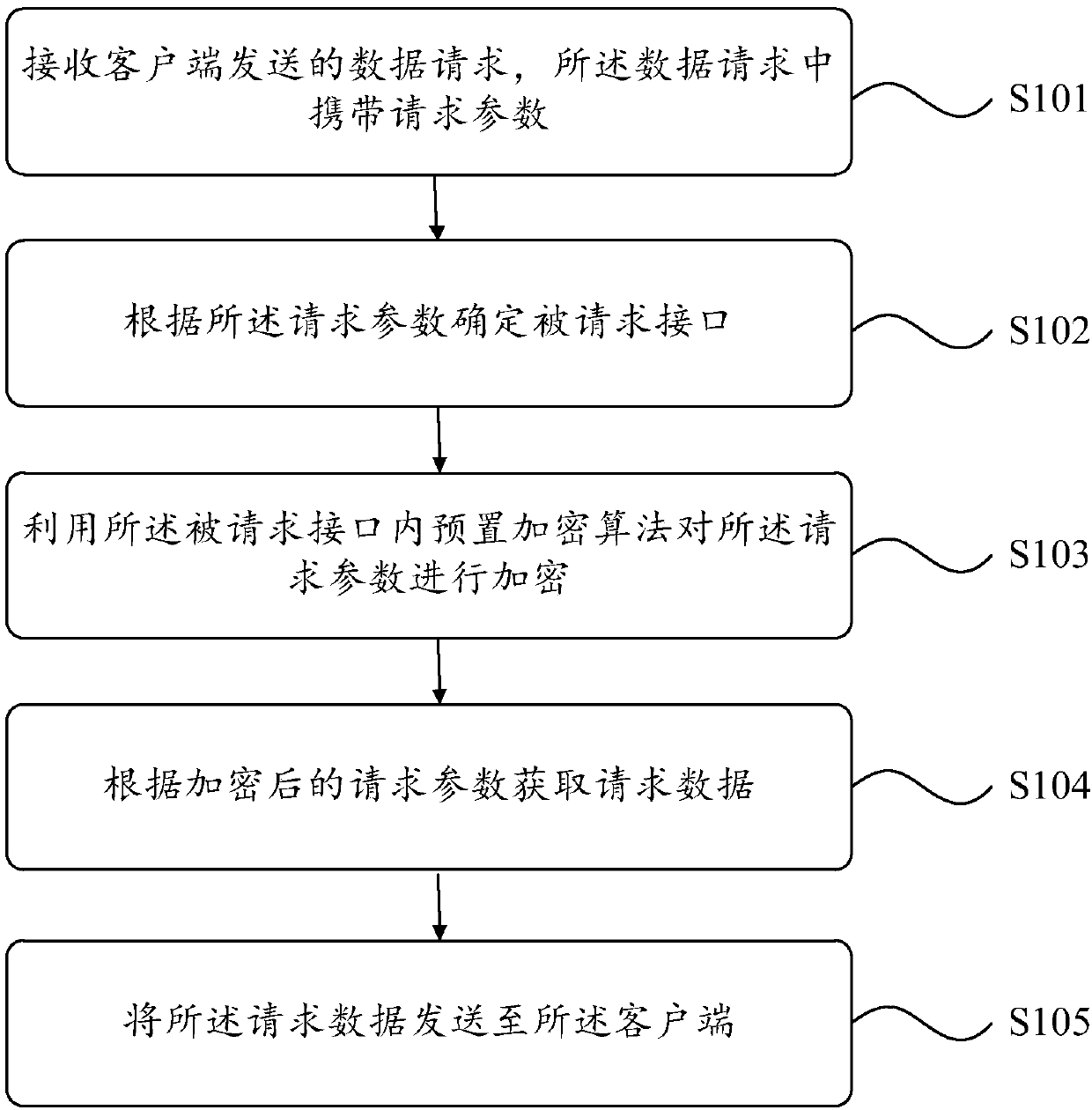
Data request processing method and apparatus
The invention provides a data request processing method. The method comprises the following steps: receiving a data request sent by a client, wherein the data request carries a request parameter; determining a requested interface according to the request parameter; encrypting the request parameter by using a preset encryption algorithm in the requested interface; and obtaining request data according to the encrypted request parameter. In the embodiment of the invention, the request parameter is encrypted by the preset encryption algorithm in the requested interface, so that the security of therequest parameter is improved. In the process of obtaining the request data by using the request parameter, the request parameter is not easily revealed or stolen by the others, thereby preventing the others from maliciously obtaining the request data by using the request parameter.
Owner:福建中金在线信息科技有限公司
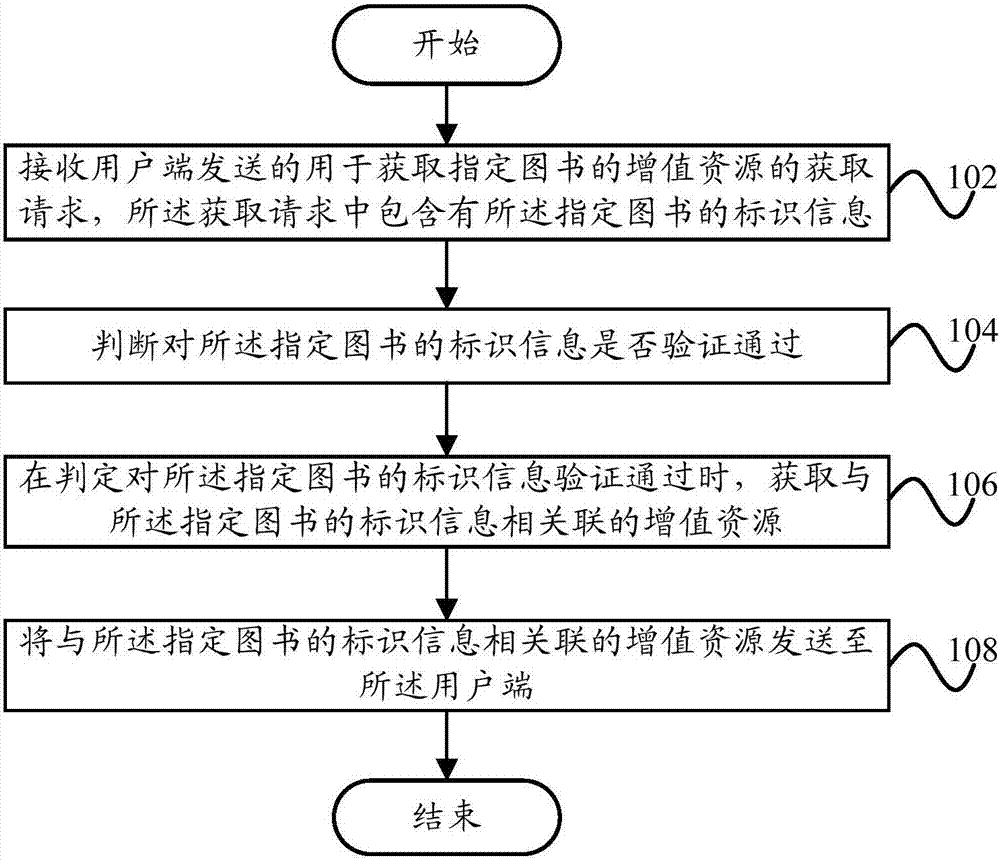
Book value-added resource management method and management apparatus
InactiveCN107230096AEasy accessAvoid malicious accessMarketingApproaches of managementResource management
The invention provides a book value-added resource management method and management apparatus. The book value-added resource management method comprises the steps of receiving an obtaining request sent by a user end and used for obtaining value-added resources of specified books, wherein the obtaining request contains identifier information of the specified books; judging whether the identifier information of the specified books passes the verification or not; when it is judged that the identifier information of the specified books passes the verification, obtaining the value-added resources associated with the identifier information of the specified books; and sending the value-added resources associated with the identifier information of the specified books to the user end. Through the technical scheme, a user can conveniently and quickly obtain the value-added resources of the books when using the books to obtain more information in combination with the value-added resources of the books, and the information is not limited to contents of paper books, so that the rights and interests of copyrighted books are ensured and the value-added resources of the books are prevented from being maliciously obtained.
Owner:PEKING UNIV FOUNDER GRP CO LTD +1
Expressway mobile terminal monitoring system and method
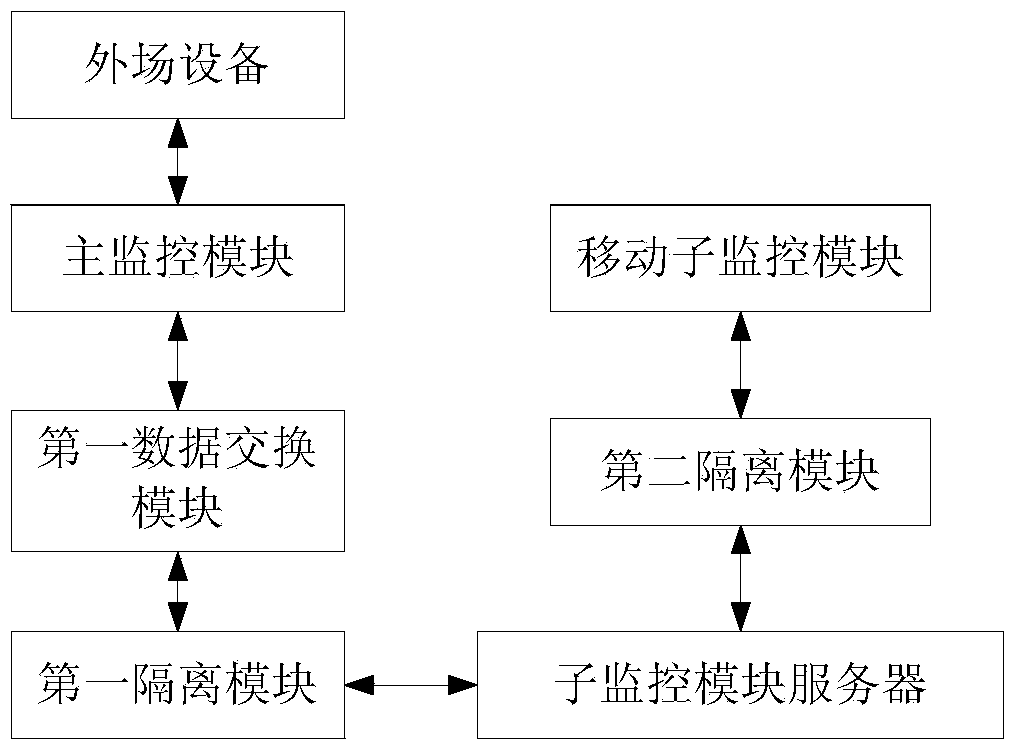
ActiveCN103634576ABlock malicious downloadsImprove securityClosed circuit television systemsData informationMonitoring system
The invention discloses an expressway mobile terminal monitoring system and an expressway mobile terminal monitoring method. A main monitoring module is used for acquiring data information of expressway external-field equipment; the data information comprises running state data of the external-field equipment and running state data of an expressway, which is detected by the external-field equipment; a mobile sub monitoring module can acquire the data information through a network. Therefore, according to the expressway mobile terminal monitoring system and the expressway mobile terminal monitoring method, the running state information of the expressway, which is detected by the external-field equipment can be acquired, and a running state of the external-field equipment can be monitored; when the running state of the external-field equipment is abnormal, the mobile sub monitoring module can acquire the information immediately; a holder with the mobile sub monitoring module can reasonably select the information detected by the external-field equipment, so that the phenomenon that the abnormal information detected by the abnormal external-field equipment is used for managing or commanding scheduling is avoided.
Owner:千方捷通科技股份有限公司
Method and apparatus for trusted display on untrusted computing platforms to secure applications
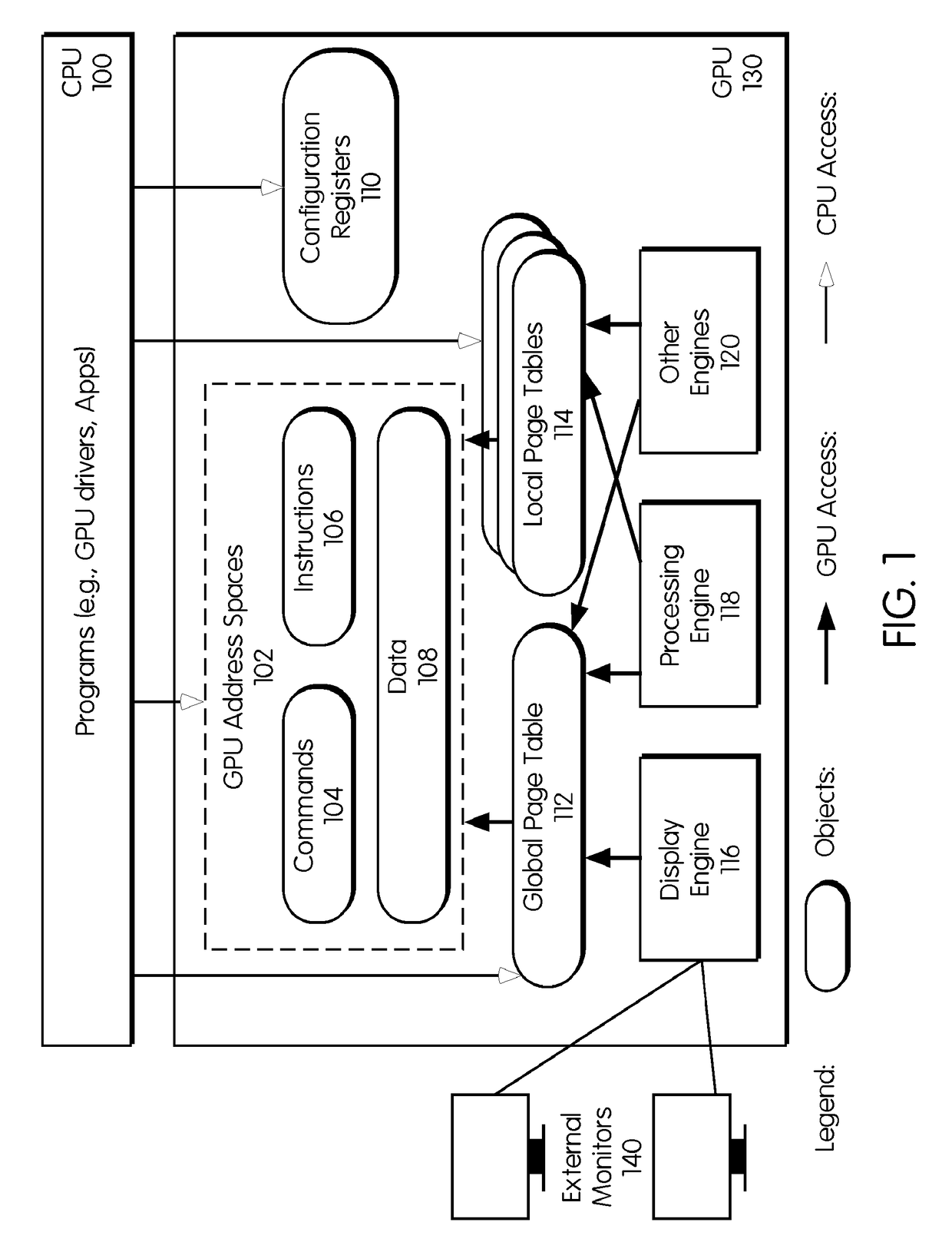
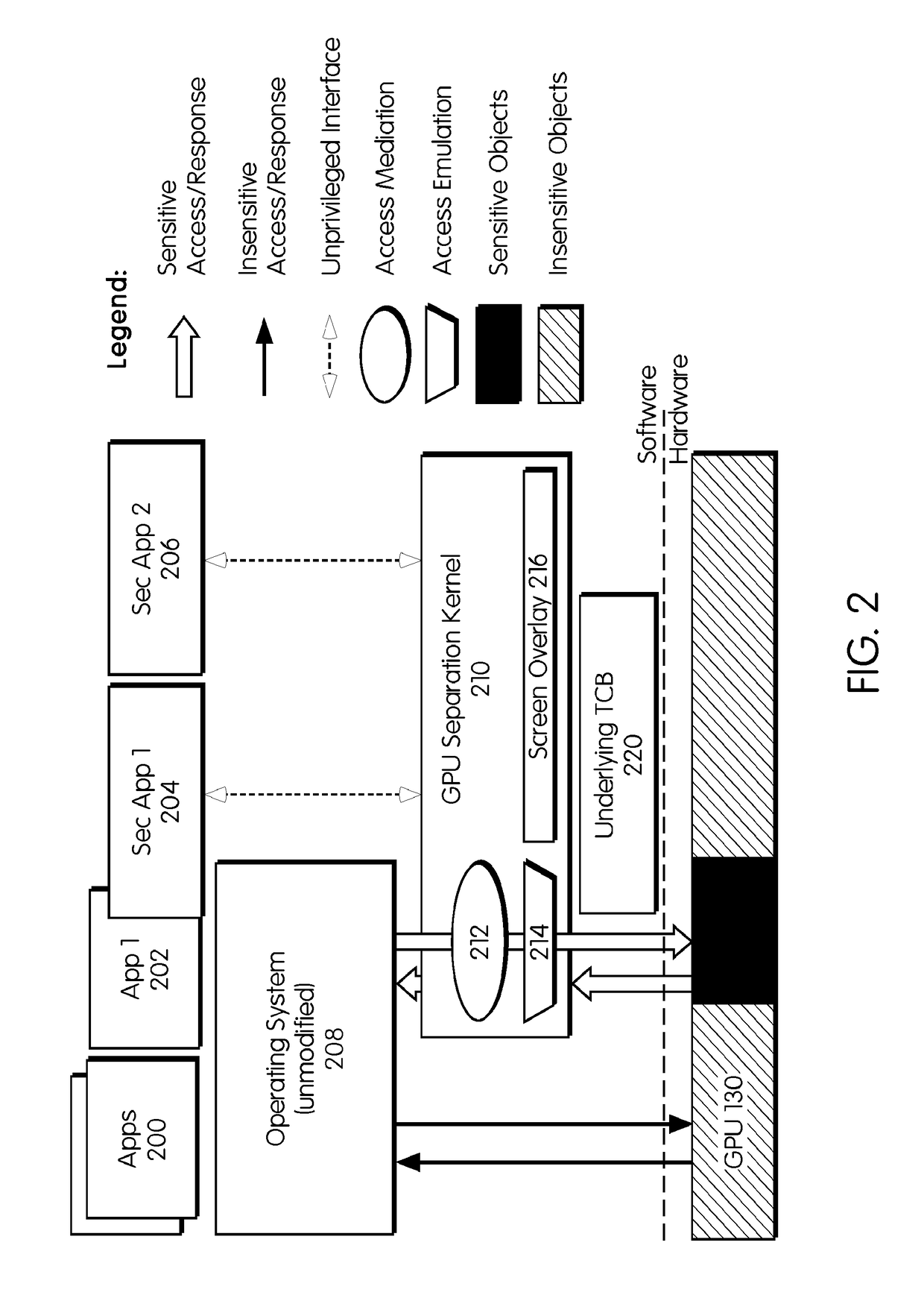
ActiveUS20190012489A1Minimize complexityMinimizing sizeDigital data protectionInternal/peripheral component protectionComputer compatibilityTrusted Computing
This invention provides a method for providing trusted display to security sensitive applications on untrusted computing platforms. This invention has a minimal trusted code base and maintains full compatibility with the computing platforms, including their software and hardware. The core of our invention is a GPU separation kernel that (1) defines different types of GPU objects, (2) mediates access to security-sensitive GPU objects, and (3) emulates accesses to security-sensitive GPU objects whenever required by computing platform compatibility.
Owner:CARNEGIE MELLON UNIV
Data storage method and device, storage medium and computer equipment
ActiveCN110221990AAvoid malicious accessSolve insufficient storage spaceUnauthorized memory use protectionInternal/peripheral component protectionData storingData store
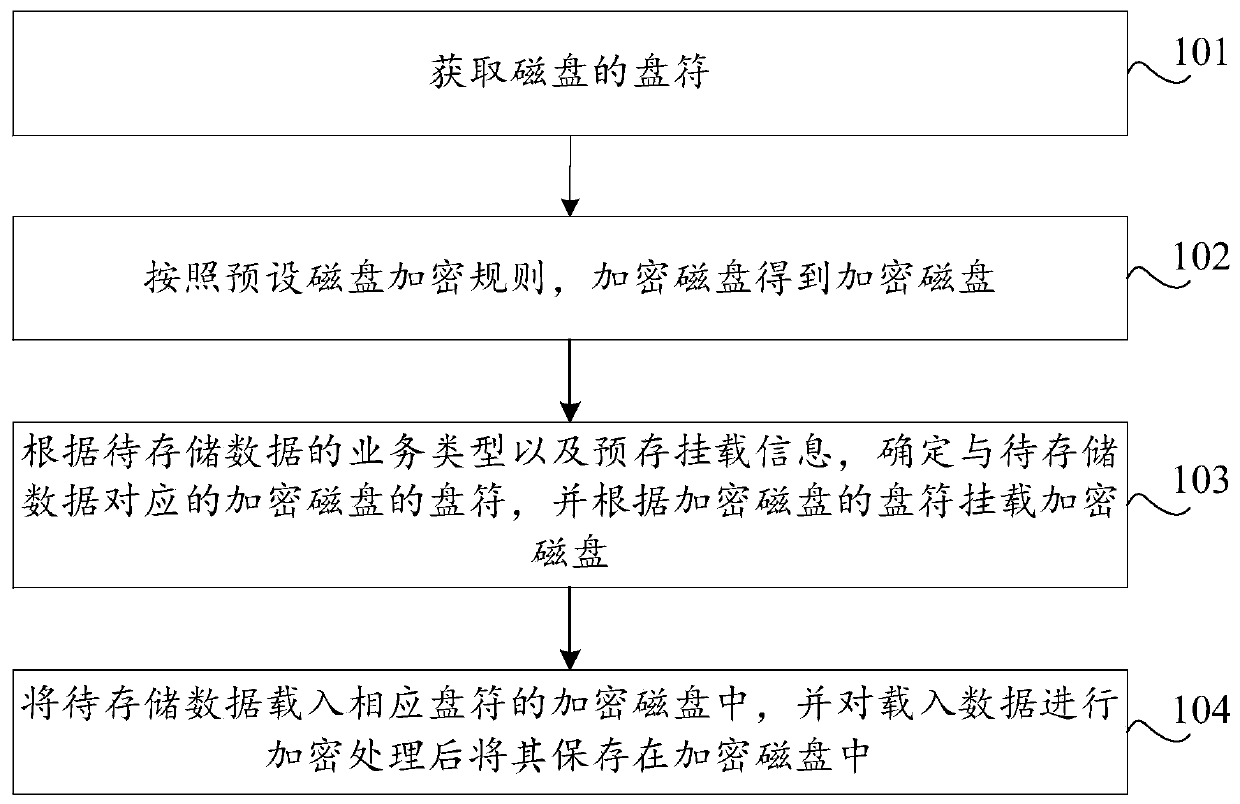
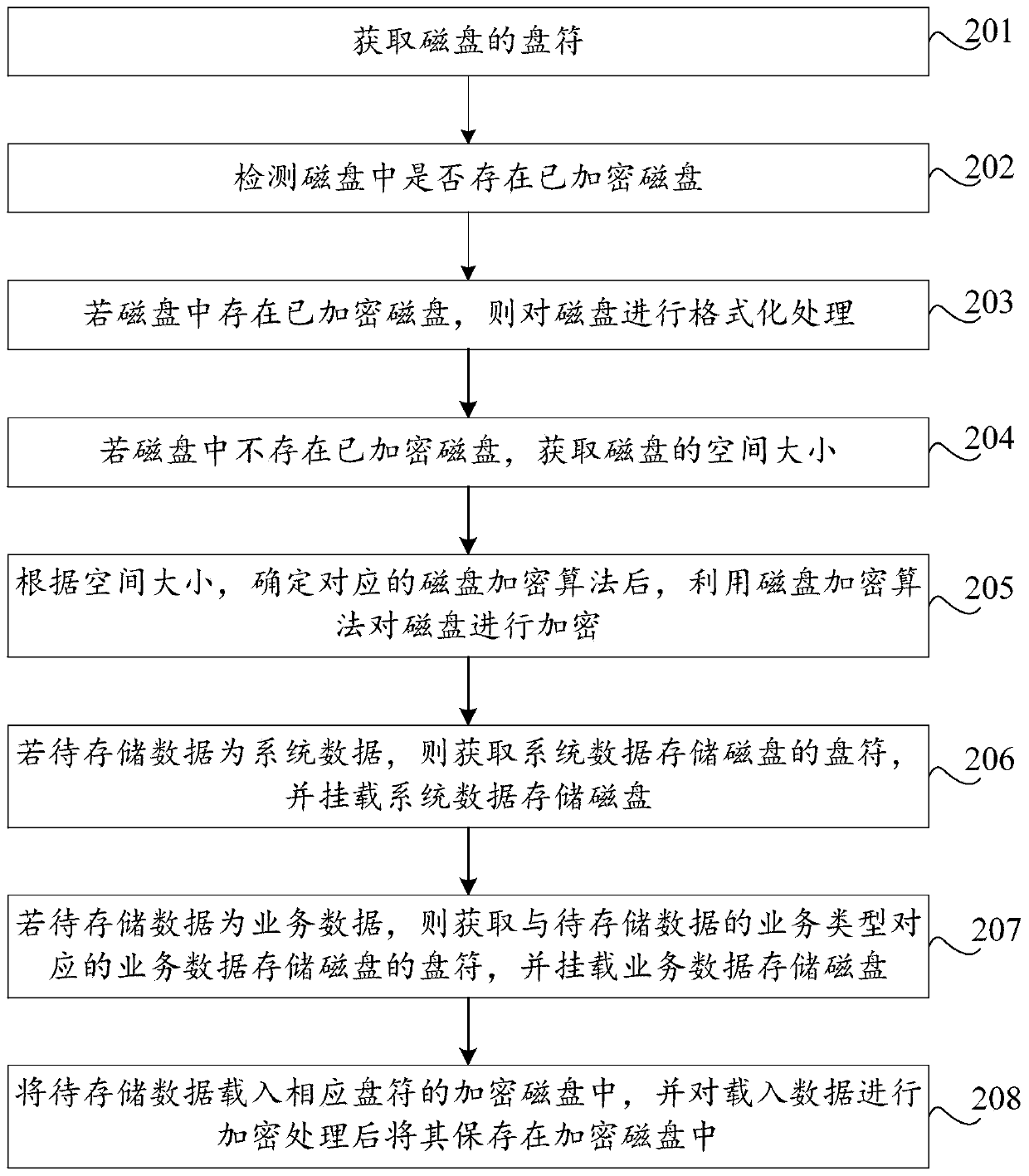
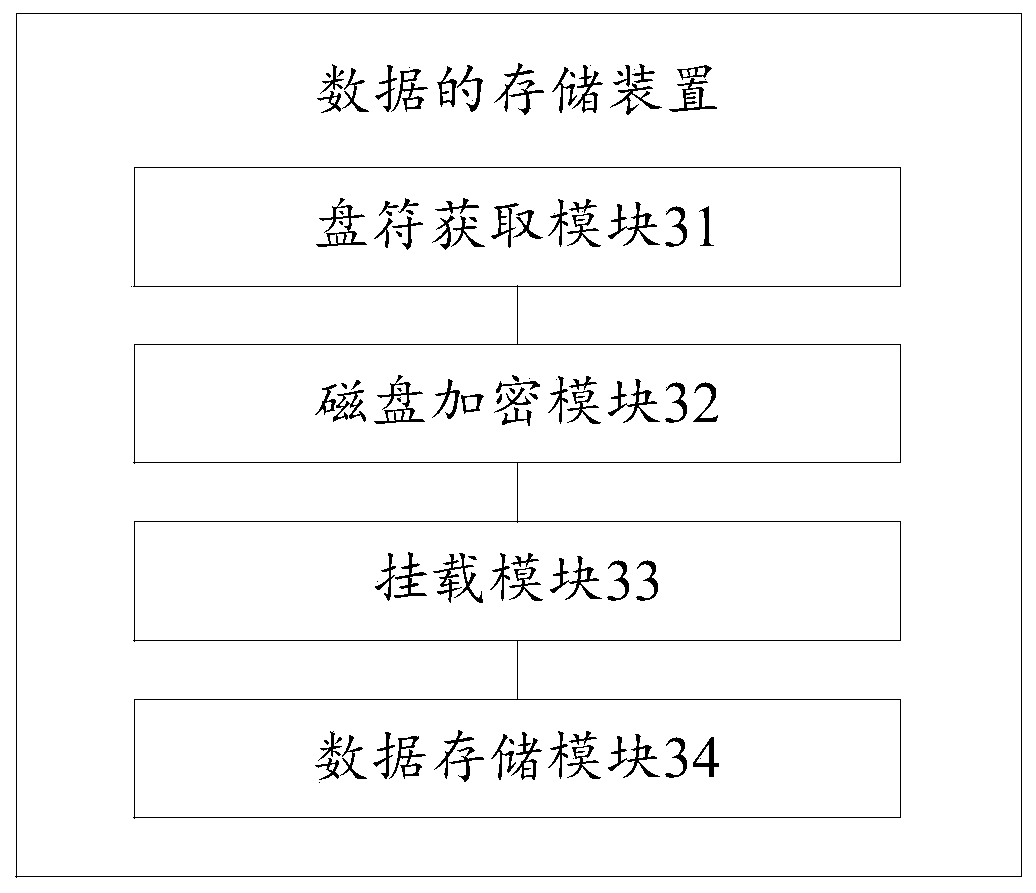
The invention discloses a data storage method and device, a storage medium and computer equipment. The method comprises the following steps: obtaining a drive of a disk; encrypting the disk accordingto a preset disk encryption rule to obtain an encrypted disk; according to the service type of the to-be-stored data and pre-stored mounting information, determining a drive of an encrypted disk corresponding to the to-be-stored data, and mounting the encrypted disk according to the drive of the encrypted disk, the prediction mounting information storing a mapping relation between the service typeand the drive of the encrypted disk; and loading the to-be-stored data into the encrypted disk of the corresponding drive letter, encrypting the loaded data, and storing the encrypted data in the encrypted disk. According to the method and the device, partition encryption processing is performed on the disk partitions, and partition service data encryption processing is performed on the data stored in each disk partition, so that the security of the service data and the storage platform is improved.
Owner:BEIJING QIANXIN TECH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com