Port based network access control method
A network access control and port technology, which is applied in the field of network communication, can solve the problems of being unable to prevent users from malicious attacks, not being able to obtain source IP addresses, and being unable to restrain MAC addresses from sending and receiving data packets, so as to avoid malicious attacks on the network by arrears users, Prevent random mobile Internet access and avoid the effect of stealing other people's technical data
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
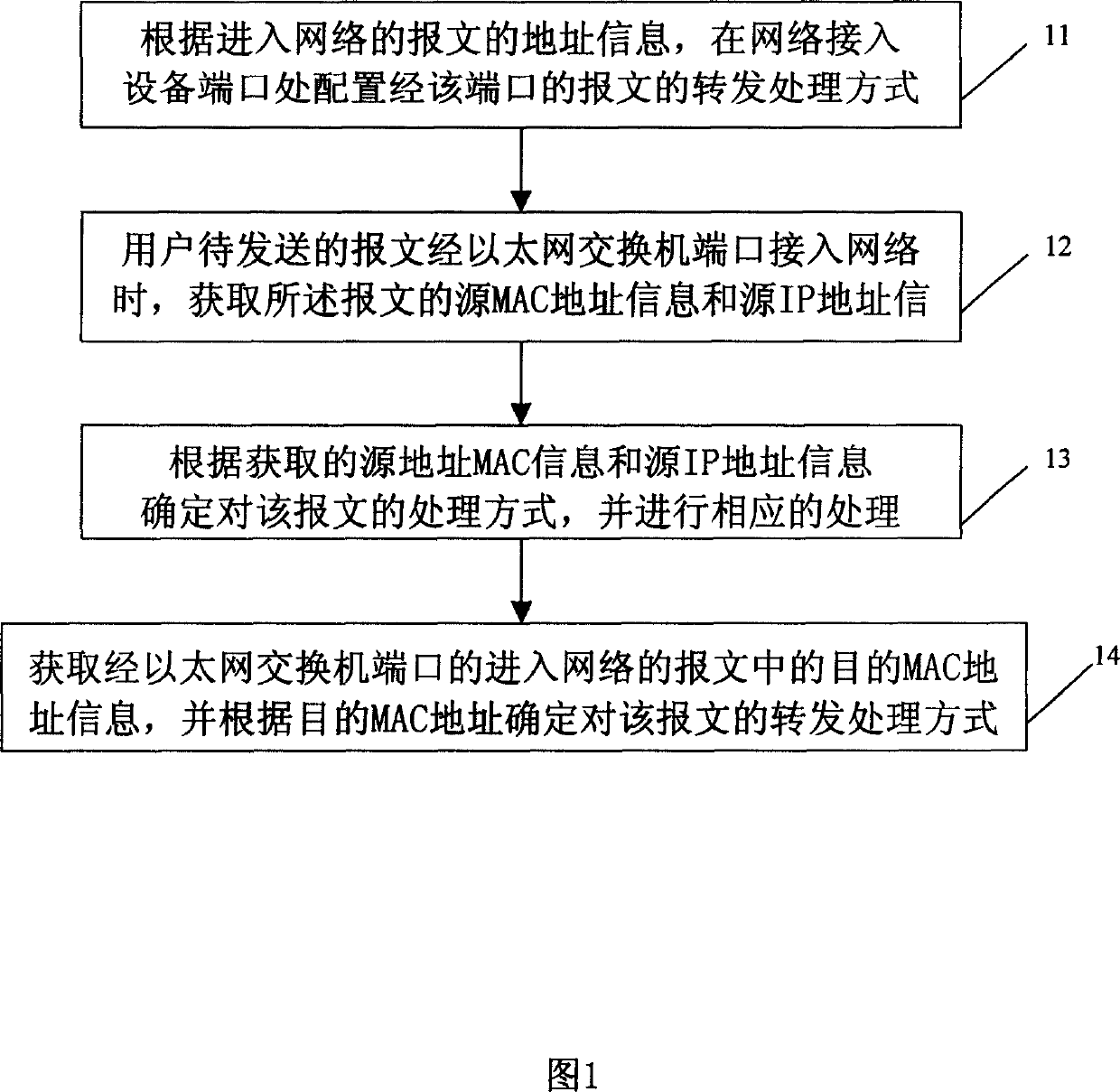
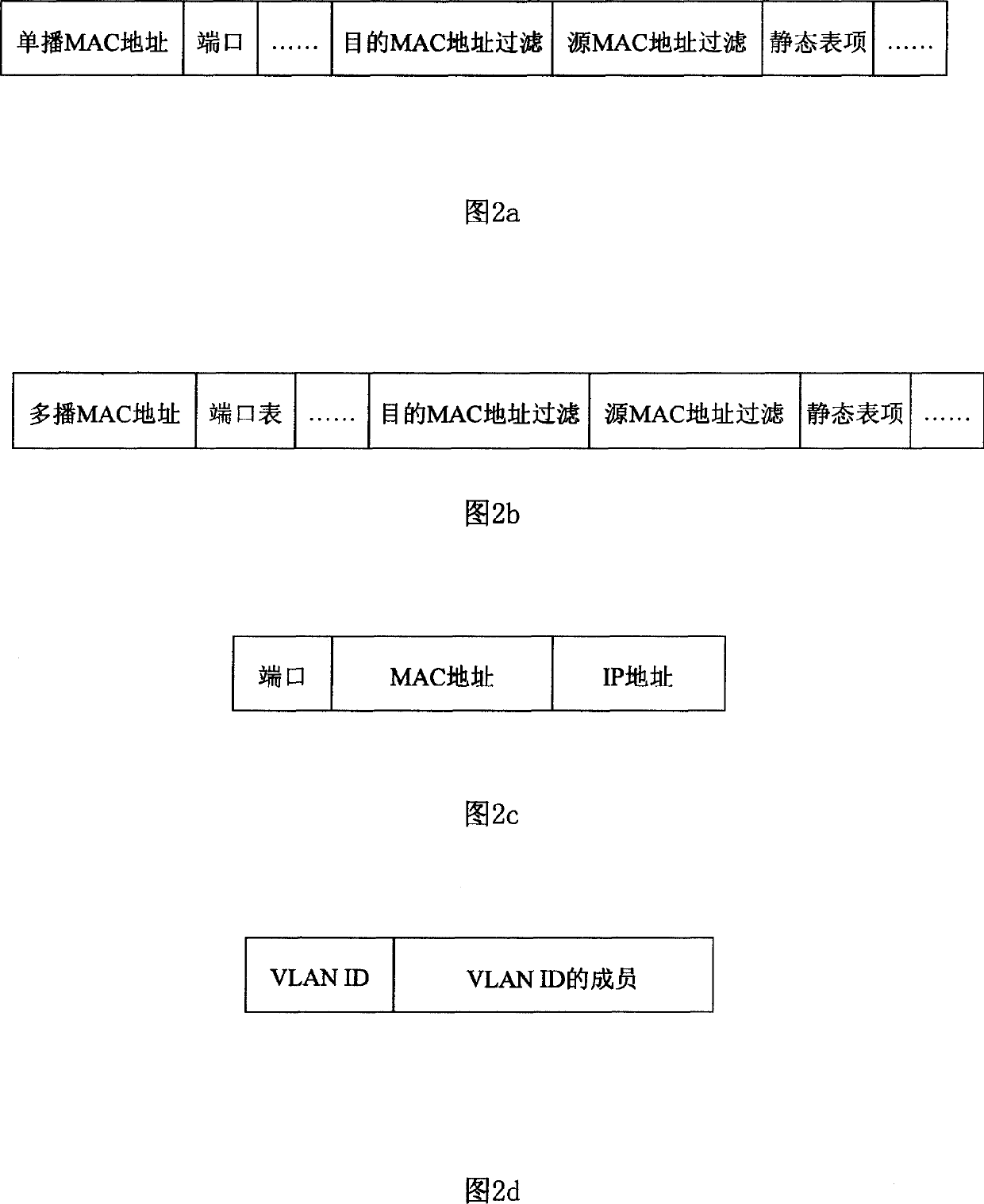
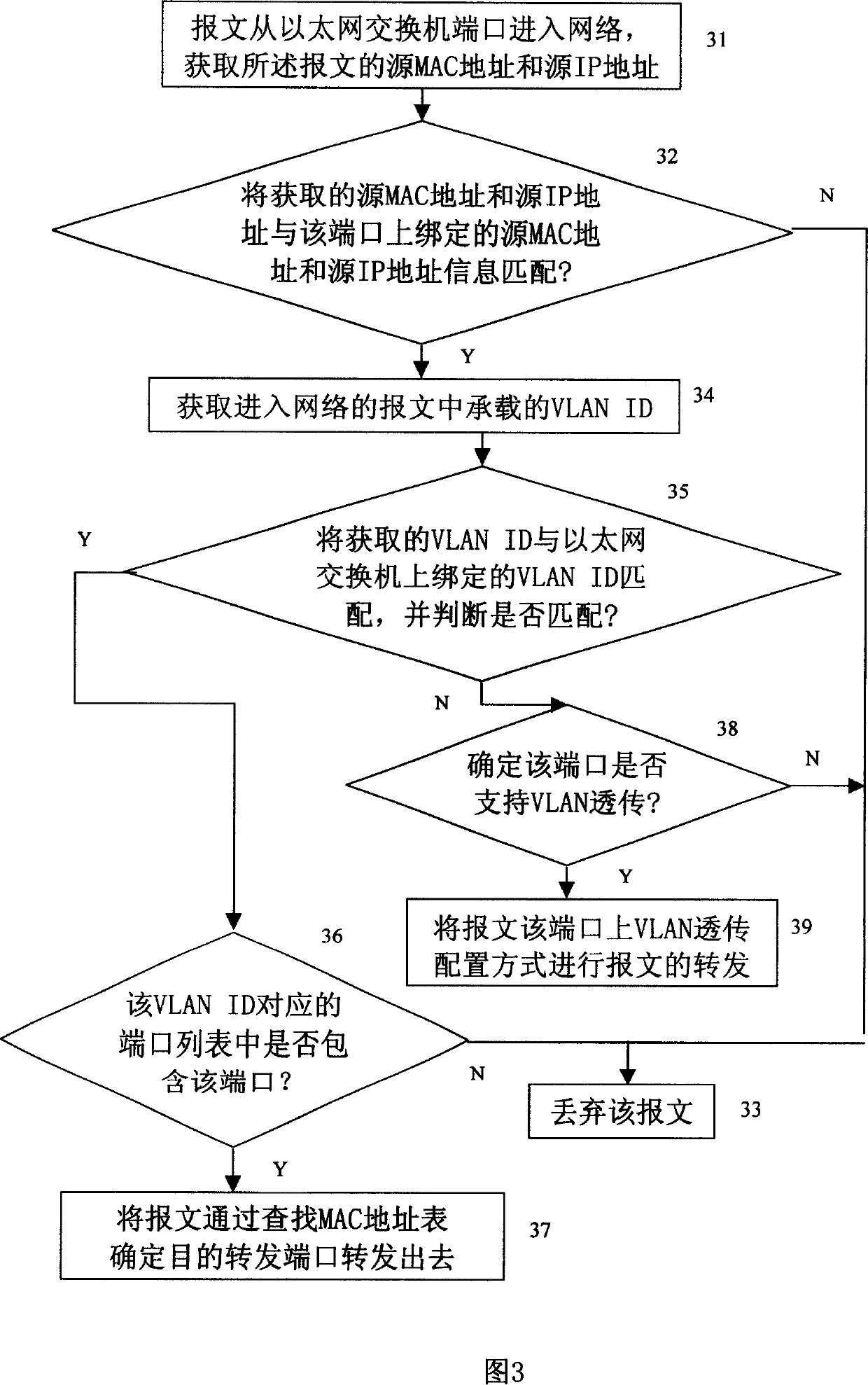
[0078] The core idea of the present invention is to perform corresponding network access control according to the source address information and destination address information of the message passing through the port of the network access device, so as to provide guarantee for the security of the network, that is: the network access device will The MAC address, IP address or VLANID of the user connected to the network through the port is bound to the corresponding port. At the same time, the forwarding and processing of the message is controlled and managed according to the destination MAC address of the message, which provides an effective solution for network security. ensure.
[0079] The specific embodiment of the present invention is described further now in conjunction with accompanying drawing, at first, referring to Fig. 1, the method of the present invention is described, specifically comprises the following steps:
[0080] Step 11: according to the address informat...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com