Method for preventing session hijacking, server and terminal
A server and terminal technology, applied in the field of communication, can solve the problems that affect the security of terminal and server session information, and the security level of session information needs to be improved, so as to prevent malicious acquisition and improve the security level.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
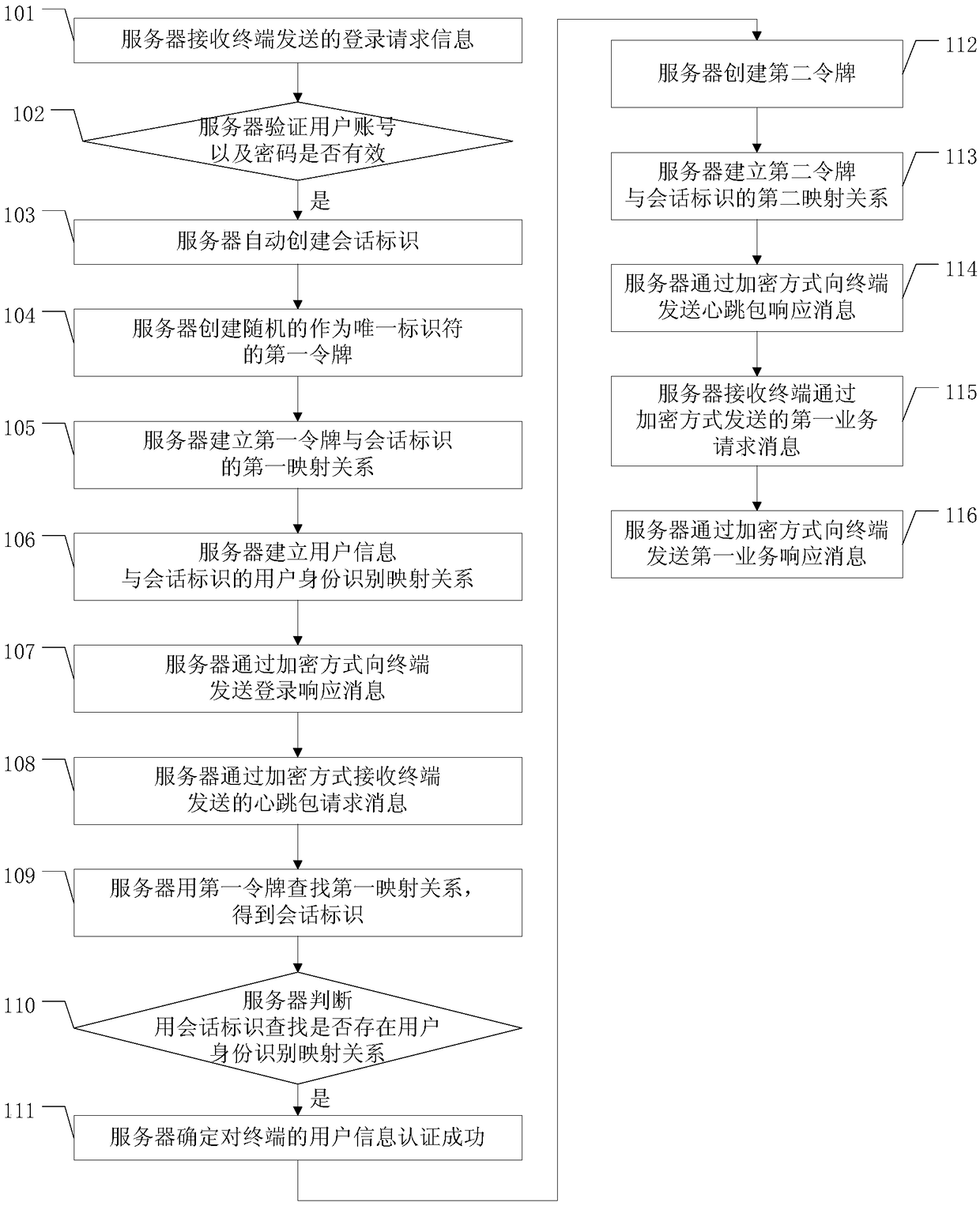
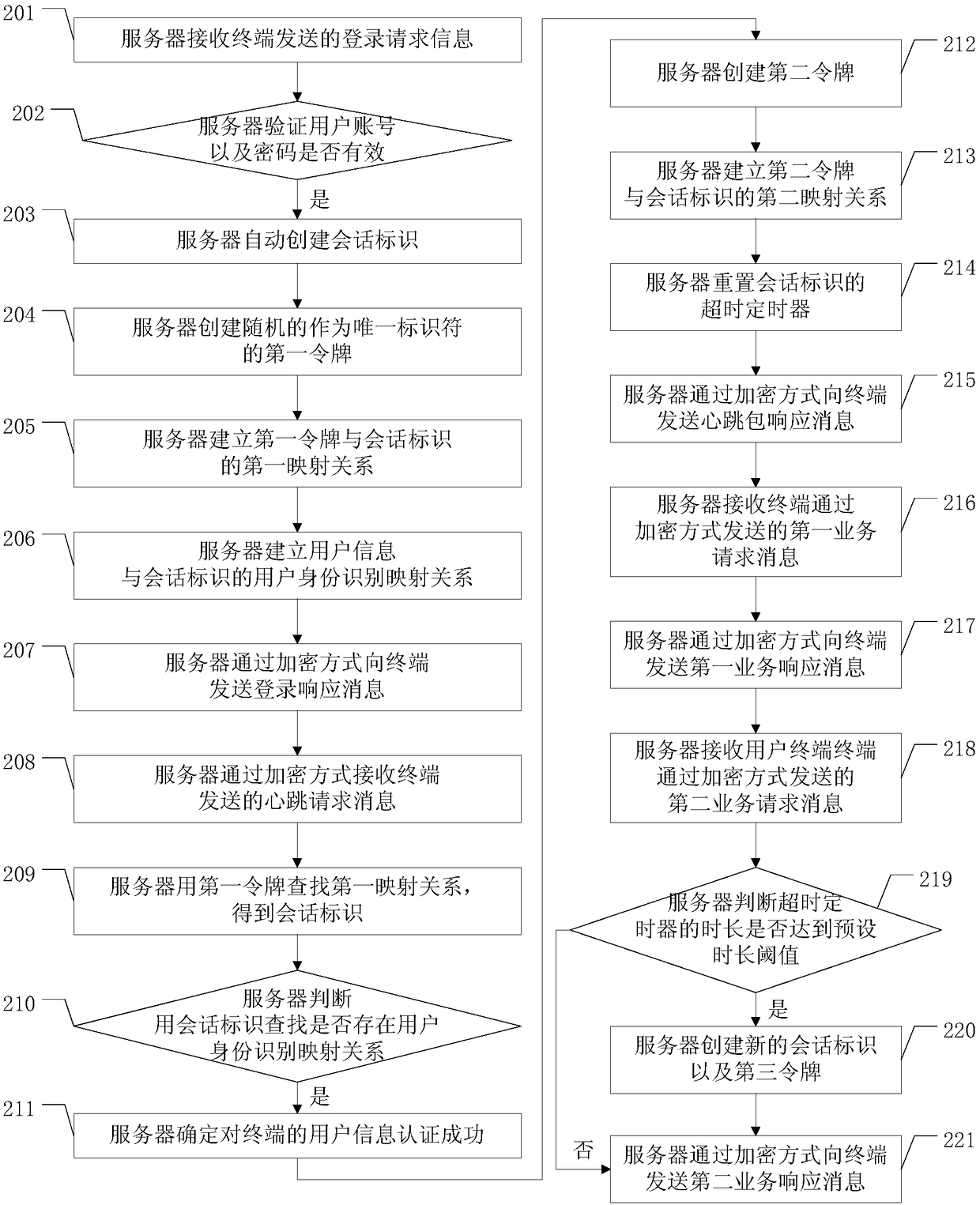
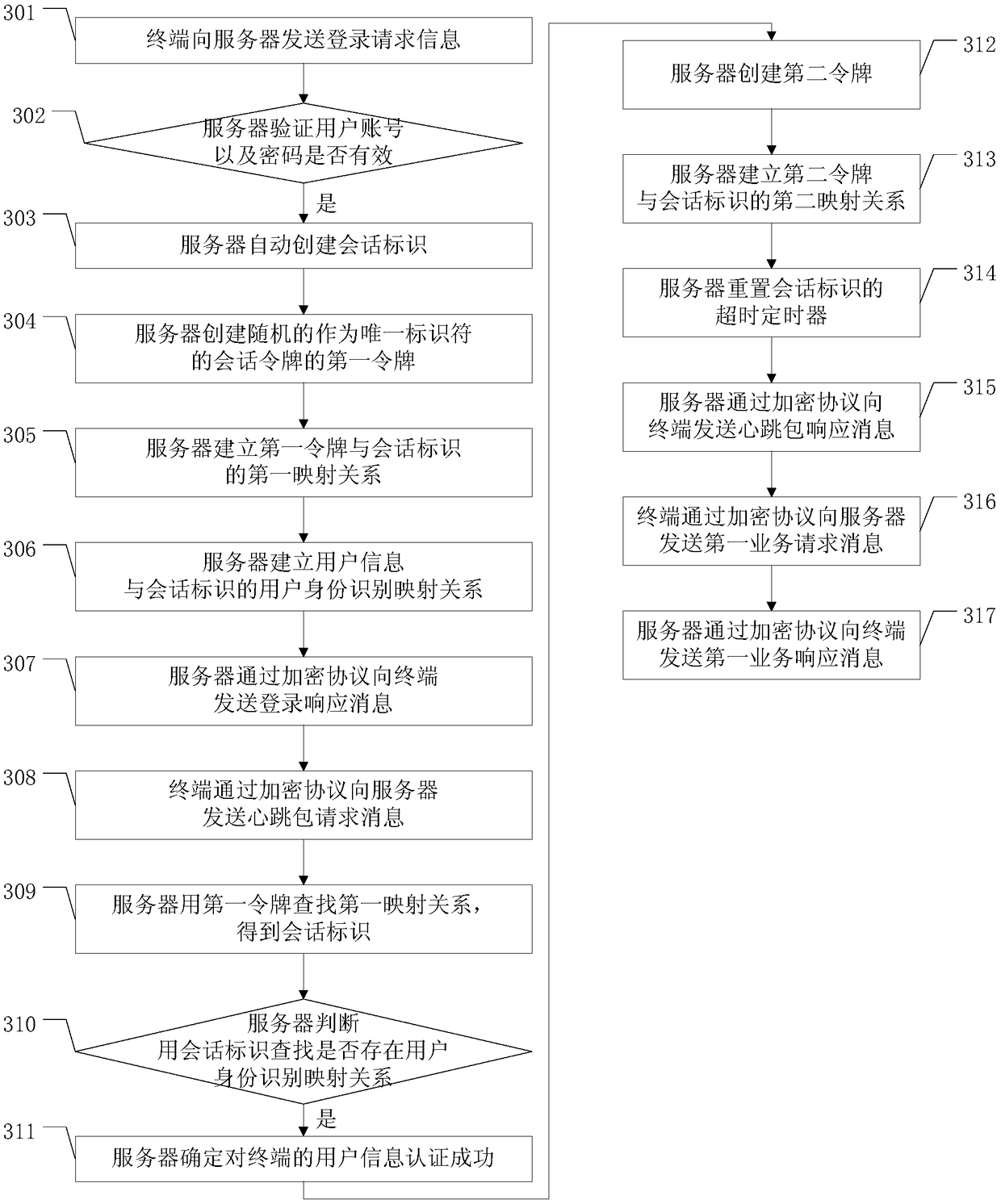
[0118] The embodiment of the present application provides a method for preventing session hijacking, a server and a terminal, which are used to prevent an attacker from maliciously obtaining identity authentication information between the terminal and the server, and improve the security level of session information between the terminal and the server.
[0119] refer to figure 1 , figure 1 It is an embodiment of the method for preventing session hijacking in the embodiment of this application. An embodiment of the method for preventing session hijacking in the embodiment of the present application includes:
[0120] 101. The server receives the login request information sent by the terminal;
[0121] In this embodiment, before requesting service information and heartbeat packets from the server, the terminal may first send login request information to the server to log in to the server, and the login request information carries the user account and password of the terminal. ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com