Method for running third-party codes safely in Java virtual computer
A java virtual machine, safe operation technology, applied in the field of information security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
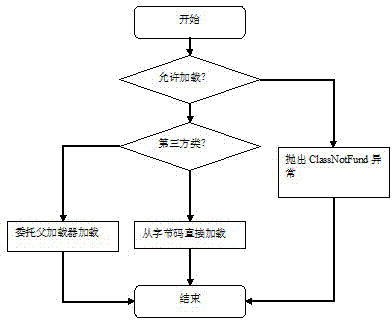
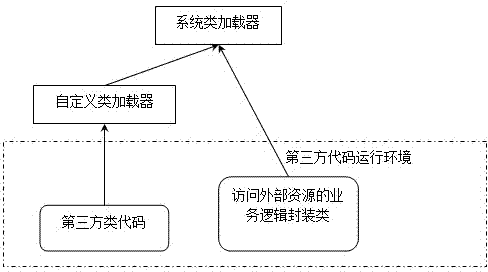
[0044] The third-party class that needs to be loaded in this embodiment is ThirdExample. The bytecode of the third-party class ThirdExample exists in the ThirdExample.class file, and only the java.lang.String class and the default java.lang.Object class are allowed to be used directly. The ThirdExample class only allows direct use of the java.lang.String class, and the information is stored in the text file ThirdExampleAccess.txt. The external resource / tmp / example.db file needs to be accessed in the ThirdExample class. This function is realized through the public methods (read and write, that is, read and write functions) provided by the class example.FileAccessWrapper, and example.FileAccessWrapper is an encapsulation class provided by the system provider to access external resources. The encapsulation class is based on the security requirements of the system and business Write logic. In this example, example.FileAccessWrapper implements file operations by using java.io.* ...
Embodiment 2
[0053] It is the same as the above example, only controlling the accessible resources in the third-party class is different. The third-party class code ThirdExample.class (in the file) allows direct use of all classes except java.net.*, and this information is placed in the text file ThirdExampleAccess.txt. The external needs to access TCP port 80 through the network. This function is implemented through the public methods provided by the class example.NetAccessWrapper (open, send, recieve and close, that is, open, send, receive and close functions), and example.NetAccessWrapper hides the details of network access (such as protocols, ports and underlying implementations, etc. ). example. NetAccessWrapper is a package class provided by the system provider to access external resources, written according to the security requirements and business logic of the system. In this example, example.NetAccessWrapper implements file operations by using classes that cannot be used in Thir...
Embodiment 3
[0061] In addition, according to a specific embodiment of the present invention, in addition to the method of determining the list of classes that can be used by ThirdExample (or the list of classes that cannot be loaded) by reading ThirdExampleAccess.txt in the above two specific embodiments, Technologists can use other methods to determine the information of the classes that the third-party classes are allowed to access and / or the classes that are not allowed to be accessed. One specific way is to store the information in the database, or the The above information is directly written in the program code. This change is easy to implement for those skilled in the art, and the corresponding subsequent steps are similar to the subsequent steps of the above-mentioned embodiments 1 and 2, and will not be repeated here.
[0062]
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com