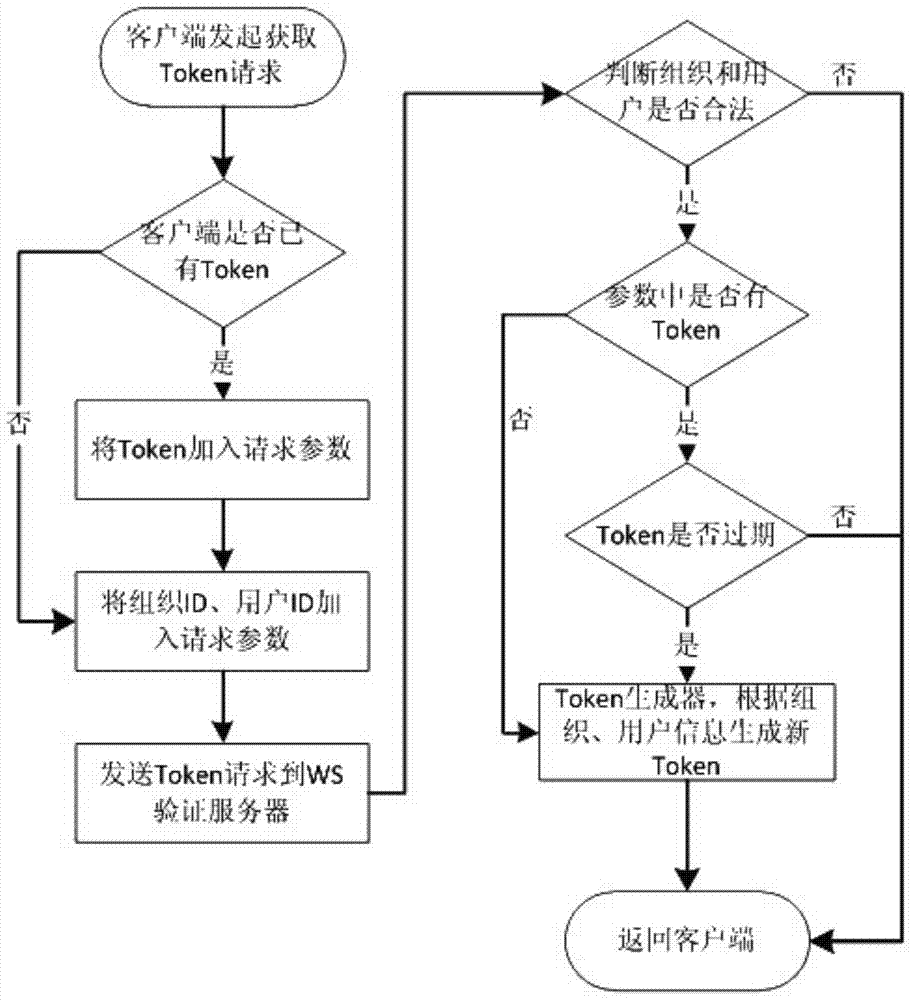
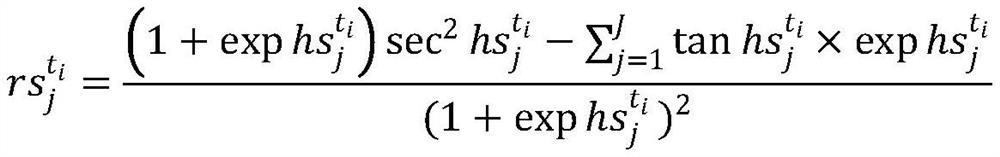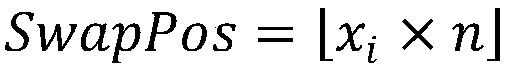Patents
Literature
37results about How to "High security mechanism" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
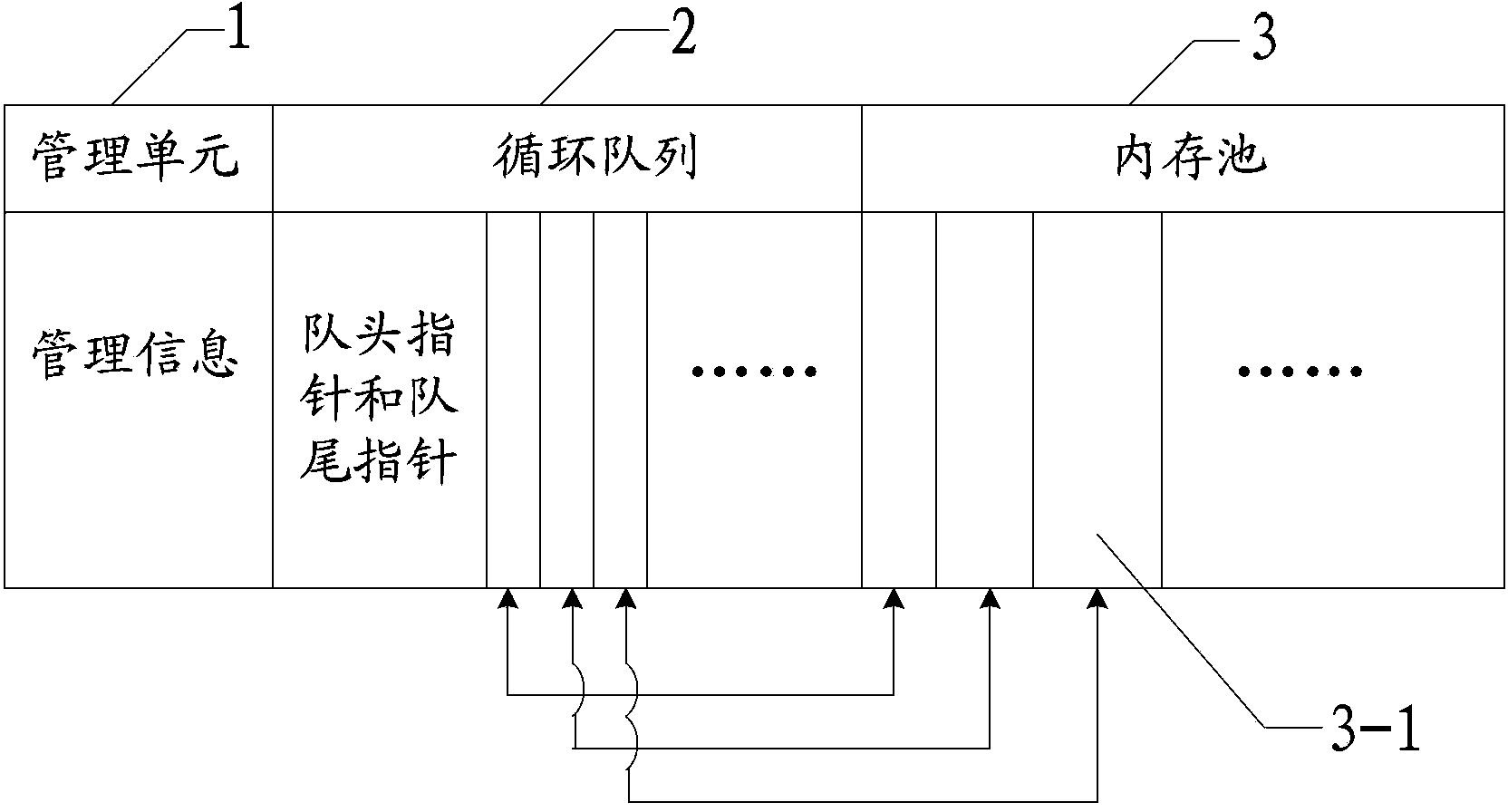
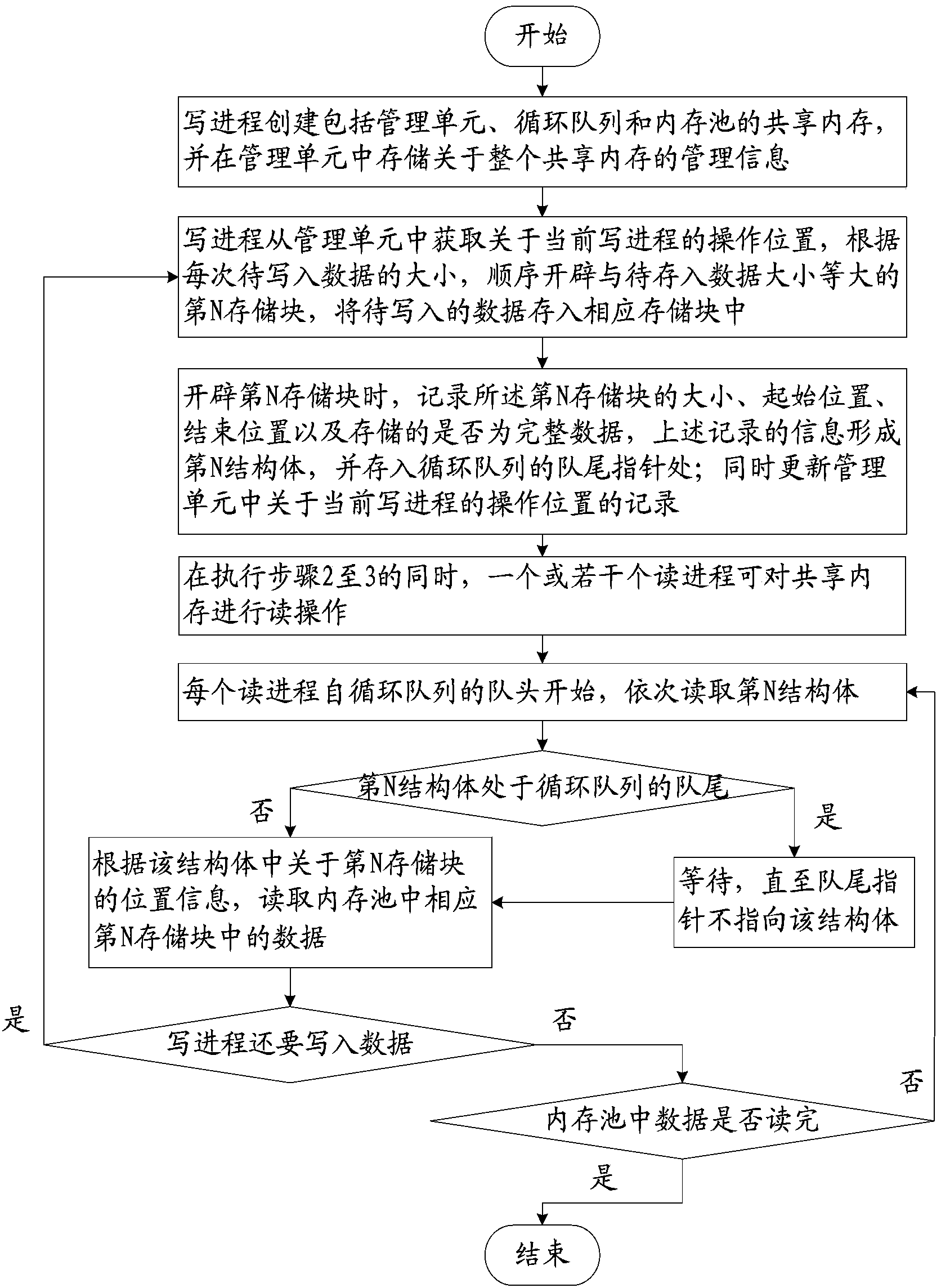
Shared-memory-based method for conducting communication among multiple processes
ActiveCN103514053AReduce the number of copiesImprove throughputInterprogram communicationSpecific program execution arrangementsCopyingThroughput
The invention relates to a shared-memory-based method for conducting communication among multiple processes. According to the method, a shared memory is managed in a circular queue mode, the shared memory is used for reading and writing conducted by the multiple processes in the circular queue mode, reading or writing is conducted by making a block as a unit, and the size of each block is controlled by a user; the shared memory is shared by the multiple processes, and the multiple processes comprise read-only processes and write-only processes; the multiple processes can conduct reading operation on the shared memory simultaneously, only one process can conduct writing operation on the shared memory, reading does not conflict with writing, and reading and writing can be conducted simultaneously. By means of the method, the number of times of copying conducted through a kernel when the processes exchange information is reduced greatly, throughput of a background system is improved, the overhead of the system is reduced, and performance of the system is effectively enhanced.
Owner:INST OF INFORMATION ENG CAS
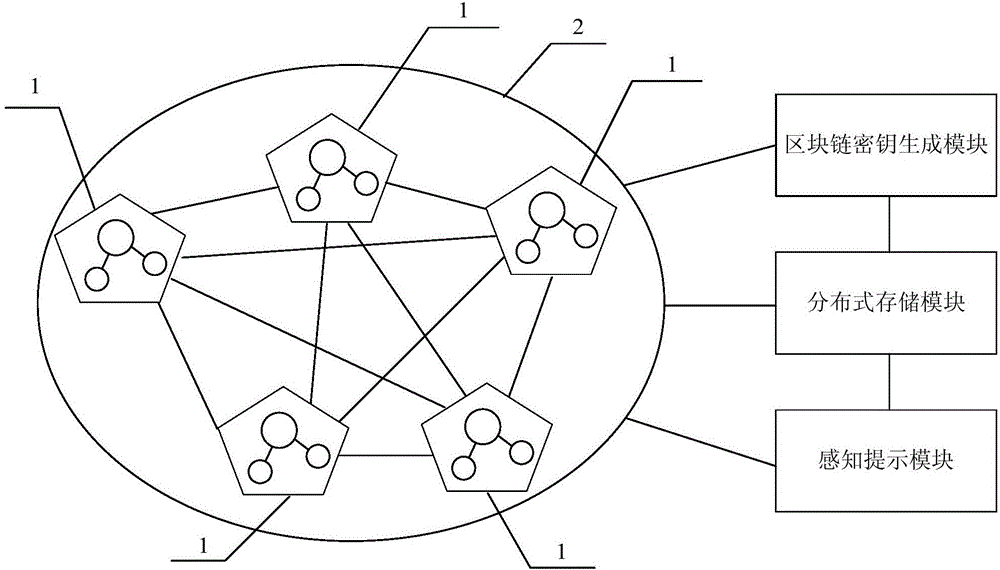
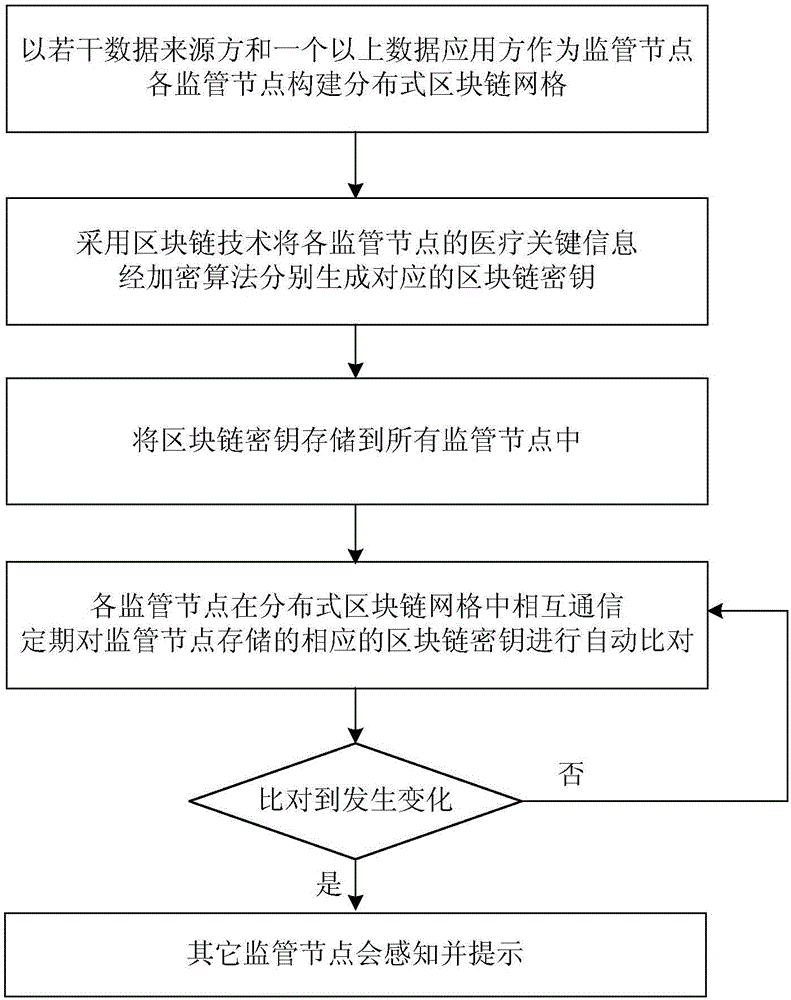
Hospital information supervision platform and method
PendingCN106777923AImplement encryptionImplement storageData processing applicationsHealthcare resources and facilitiesData sourceComputer module
The invention provides a hospital information supervision platform and method. The hospital information supervision platform comprises a distributed block chain network constructed by adopting a plurality of data source parties and one or more data application parties as supervision nodes and further comprises a block chain key generation module, a distributed storage module and a sensing prompting module. The block chain key generation module adopts the block chain technology for enabling medical key information of the supervision nodes in the distributed block chain network to generate corresponding block chain keys through an encryption algorithm; the distributed storage module stores the block chain keys into all the supervision nodes of the distributed block chain network; the supervision nodes are communicated in the distributed block chain network; if medical key information of any supervision node is modified, the corresponding block chain key changes, and the other supervision nodes can sense the changes and give a prompt. The platform achieves multi-point self-supervision and intelligent prompting, the medical key information safety management cost is lowered, and the medical key information of a hospital can be prevented from being modified improperly.
Owner:谭小刚
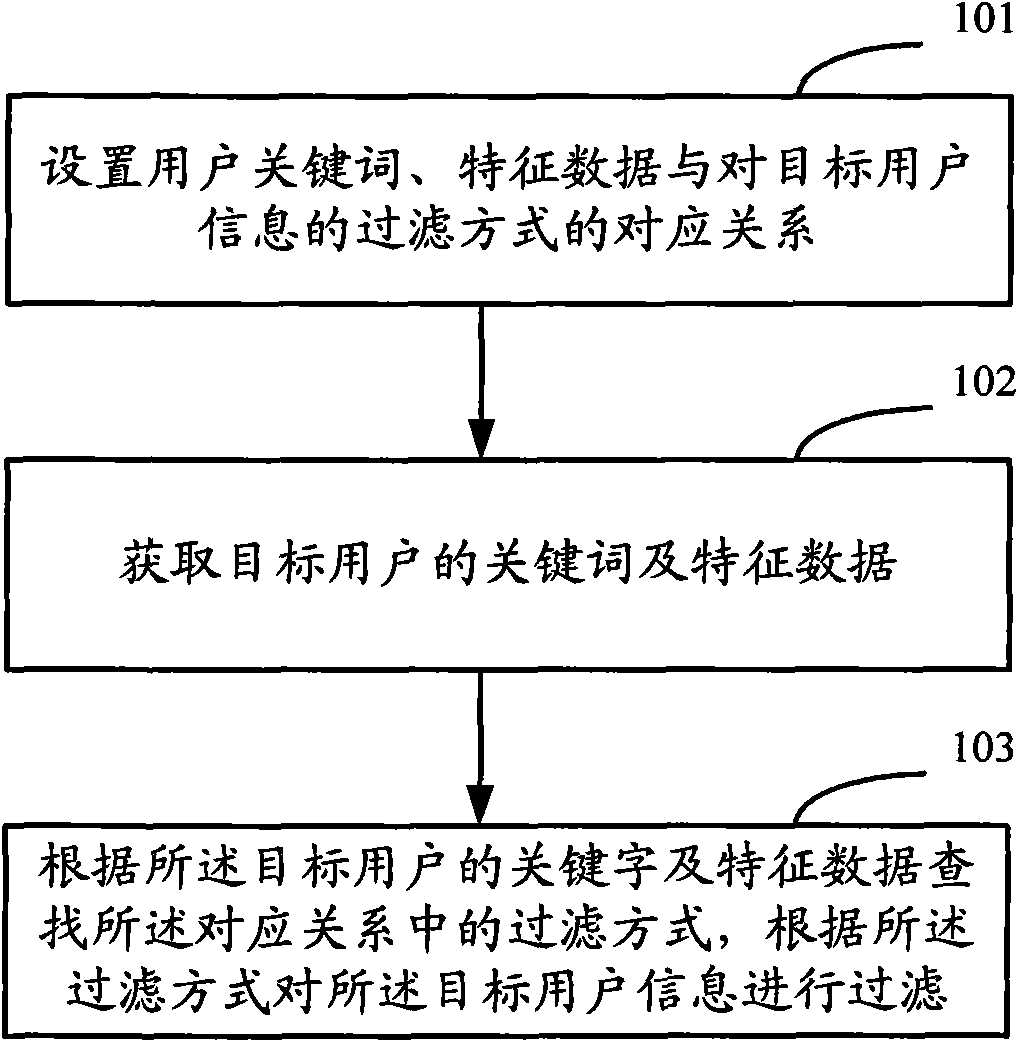
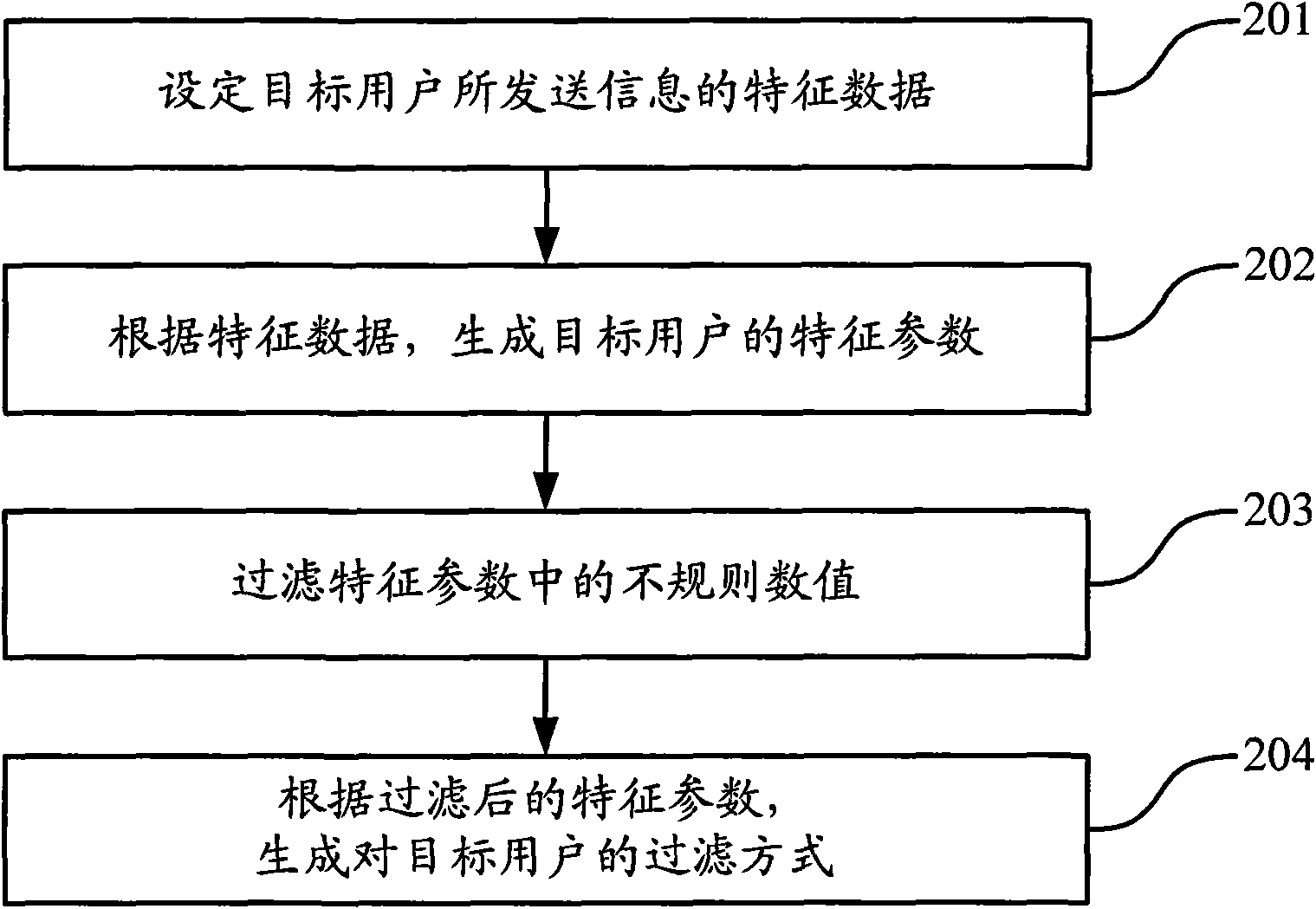
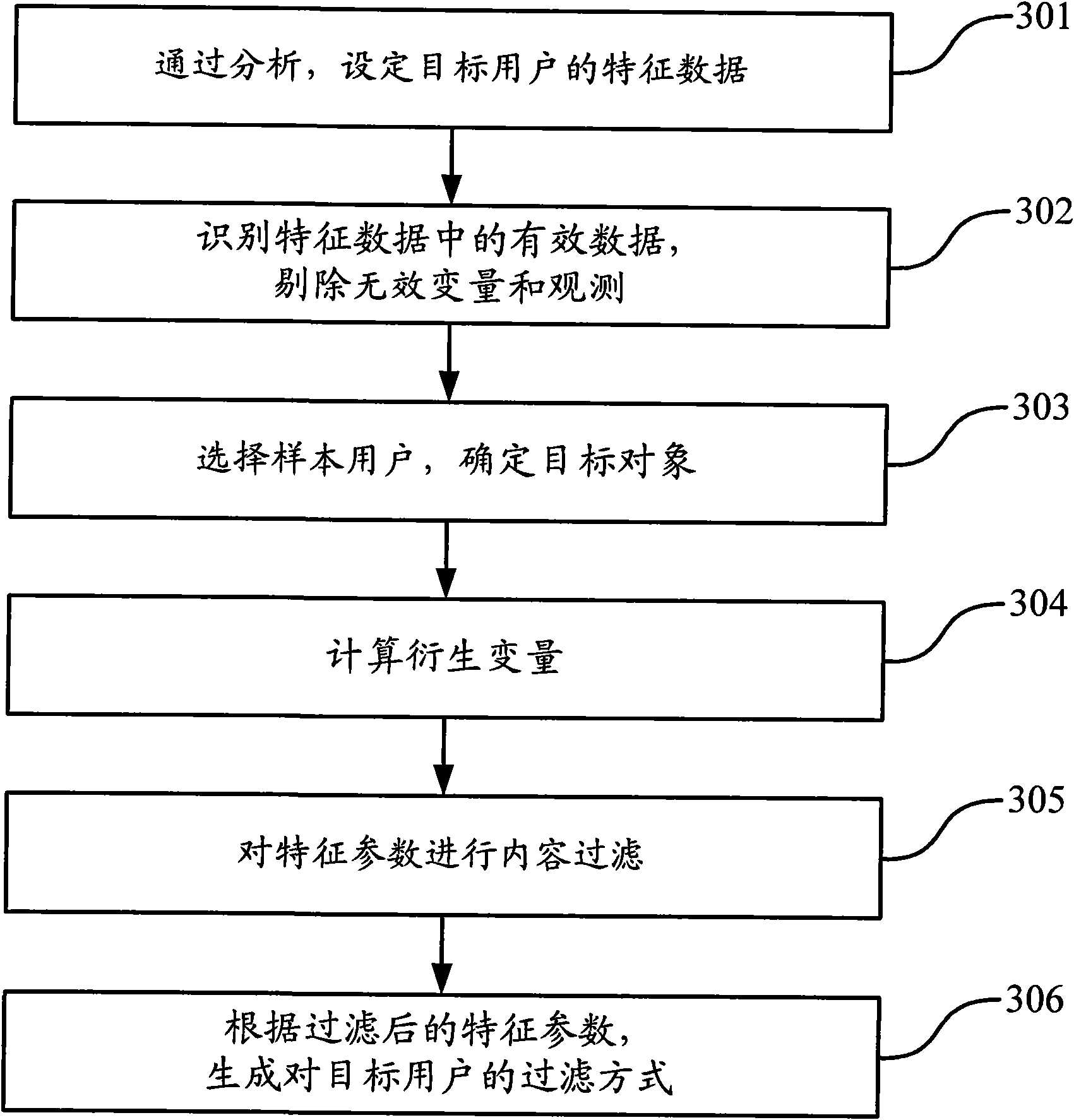
Method and device for filtering user information
ActiveCN101616101AImprove accuracyHigh security mechanismDigital data information retrievalPlatform integrity maintainanceInternet privacyUser information
The invention discloses a method for filtering user information, comprising the following steps: setting the corresponding relation of user key words, characteristic data and a filtering mode of target user information; acquiring the key words and the characteristic data of a target user; searching the filtering mode inside the corresponding relation according to the key words and the characteristic data of the target user, and filtering the target user information according to the filtering mode. The invention adopts the method judging the target user according to the concrete key words, the user characteristic data, and the like, can judge user action characteristics from multiple angles of user actions and adopts different processing modes according to different target users, thereby enhancing the accuracy rate of the identification of the target user information and a security mechanism of the user information.
Owner:ALIBABA GRP HLDG LTD
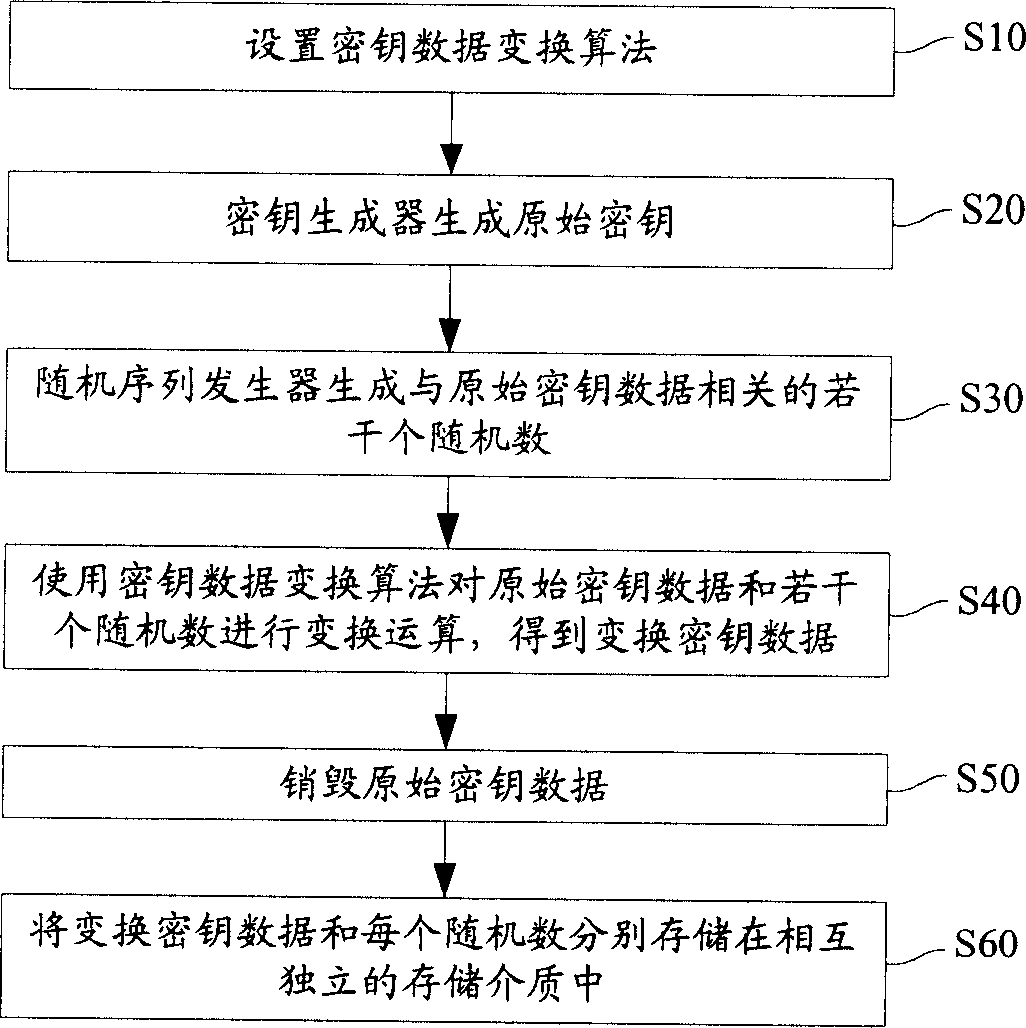
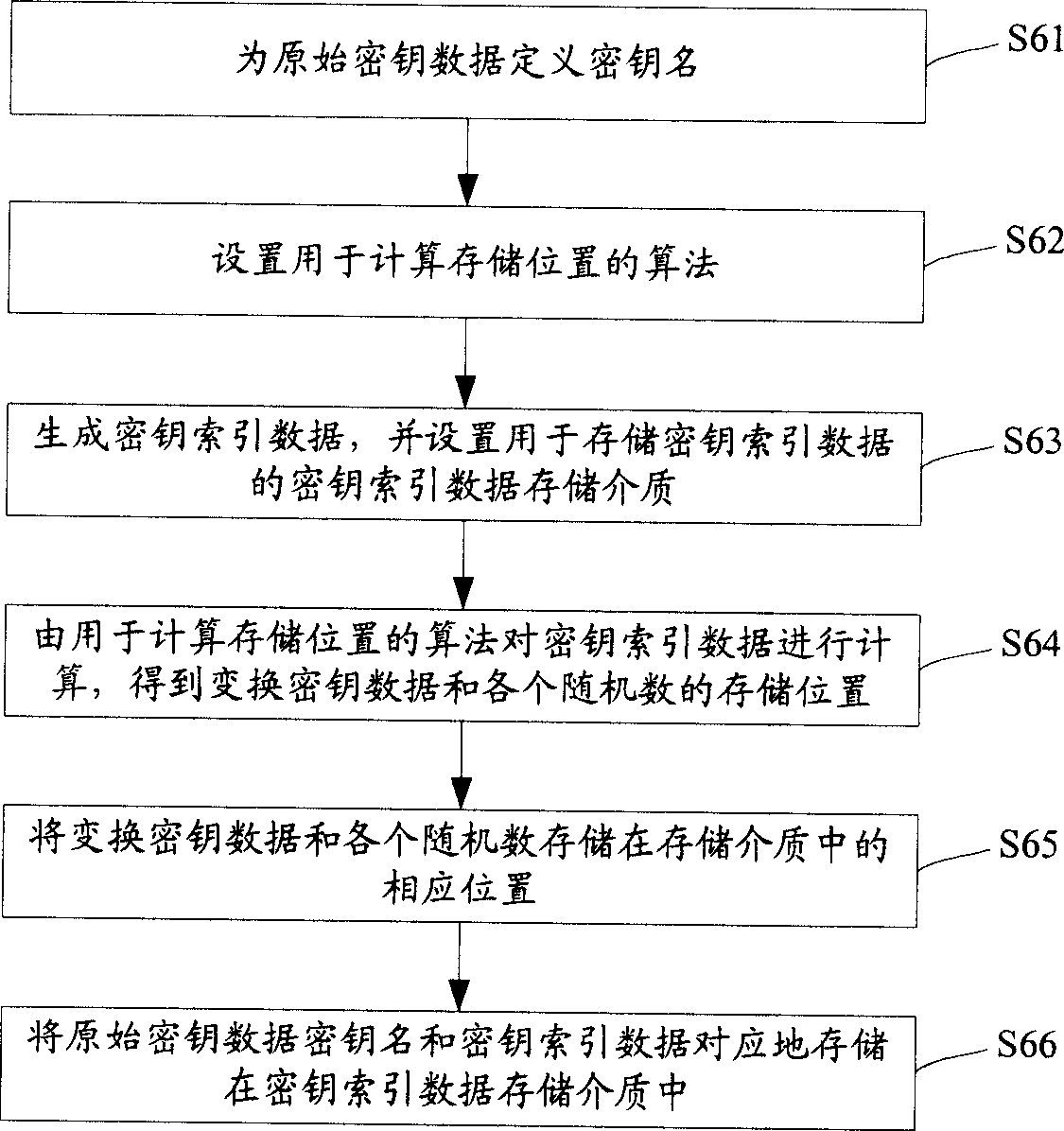
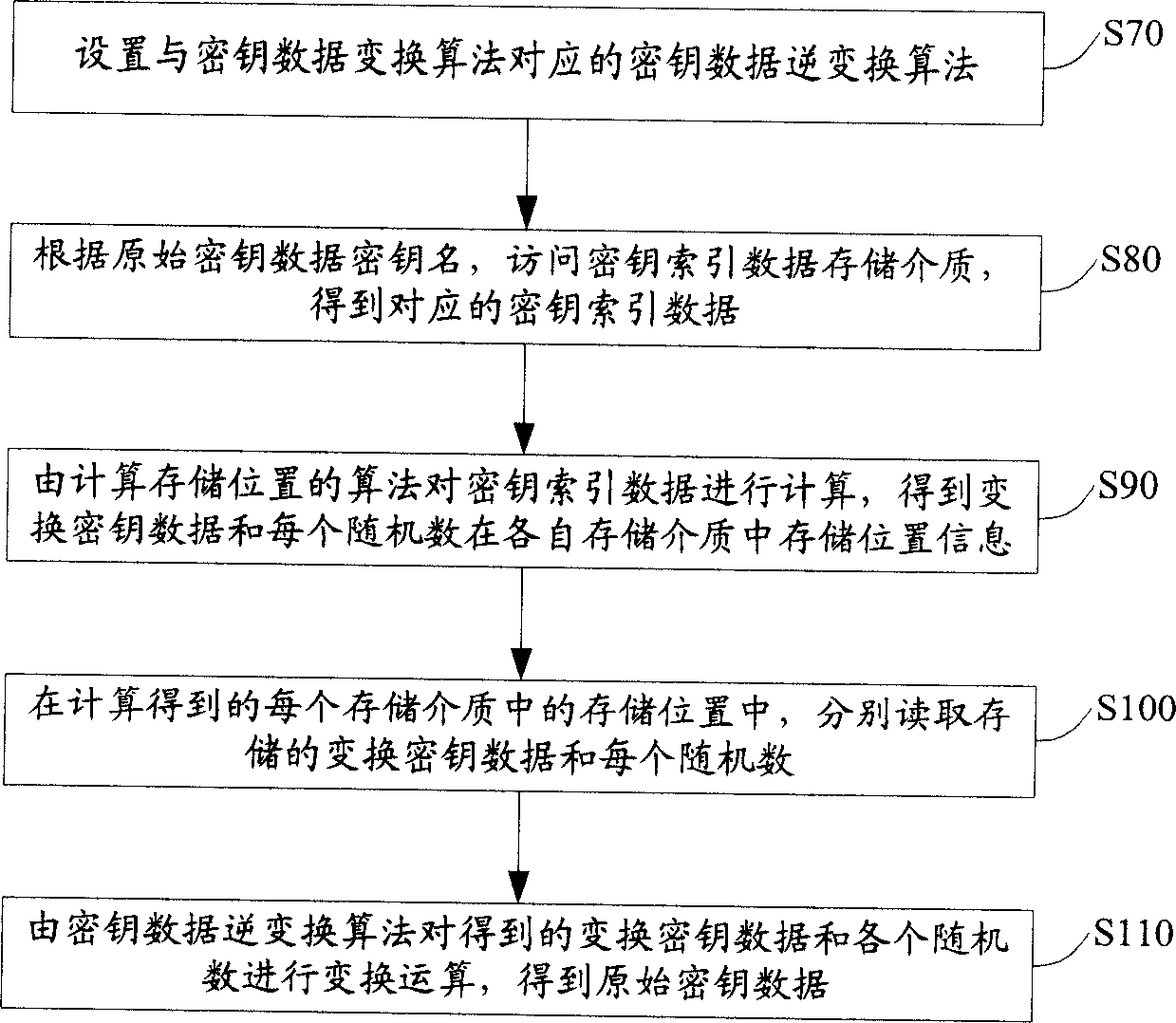
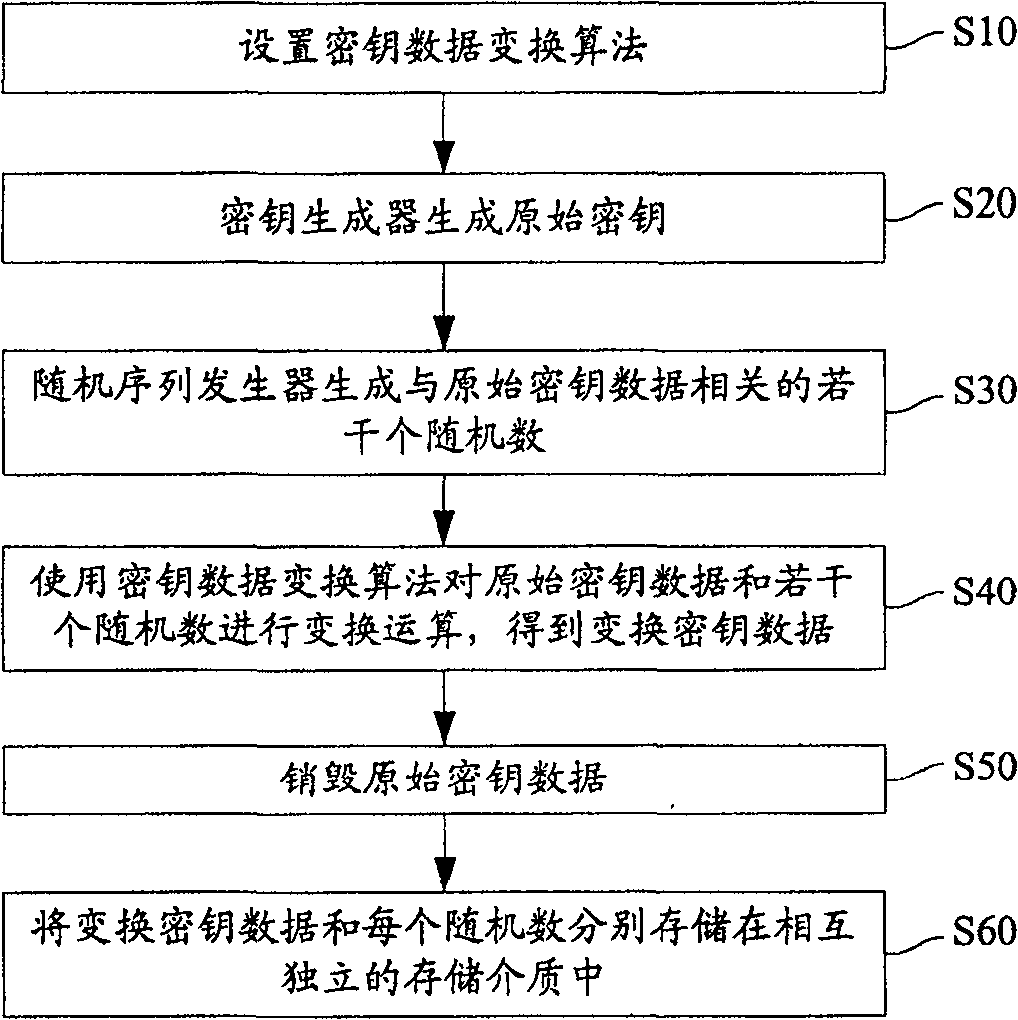
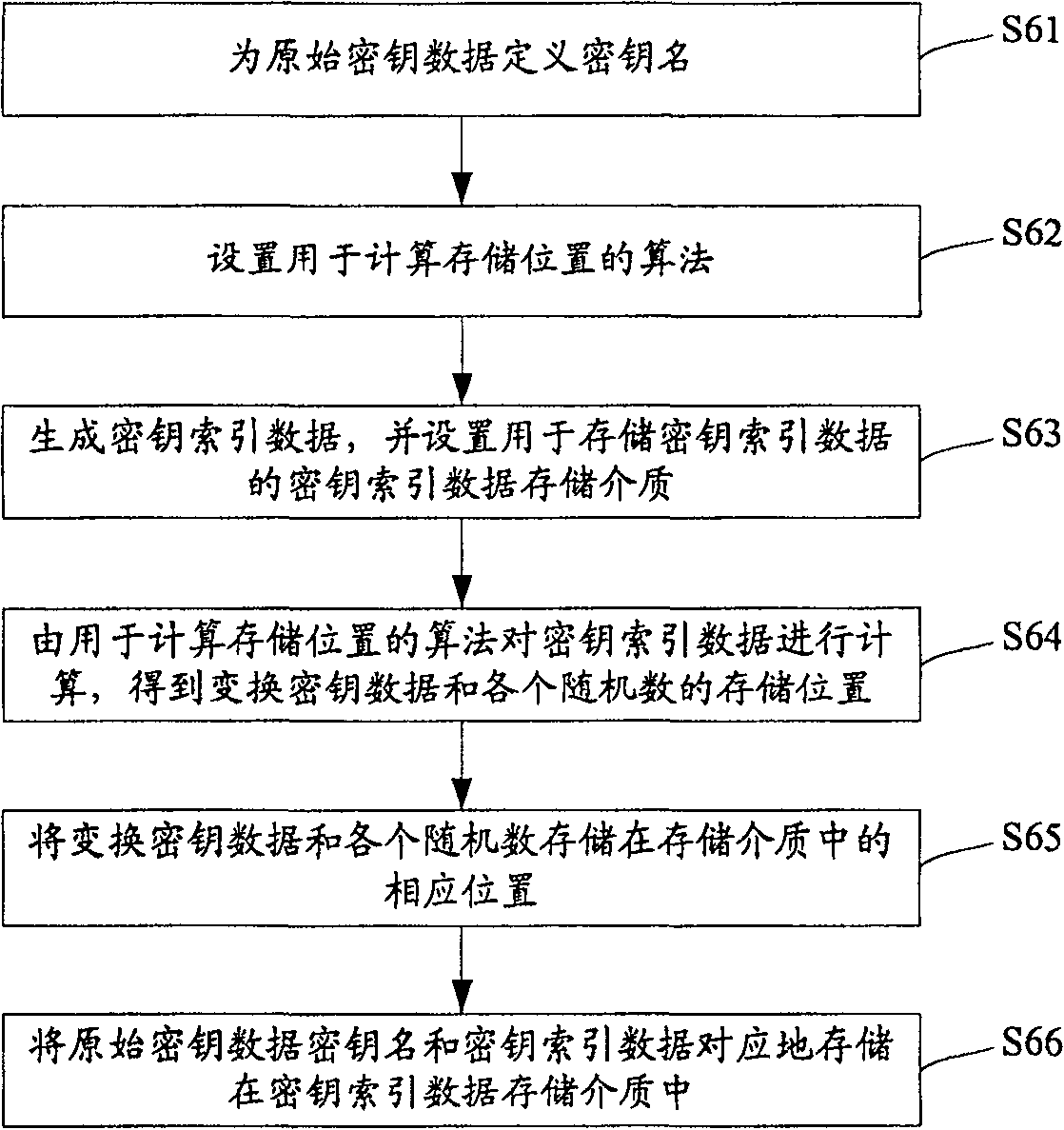
Method for storing cipher key
InactiveCN1697372ANot easy to leak and theftHigh security mechanismSynchronising transmission/receiving encryption devicesKey generatorKey storage
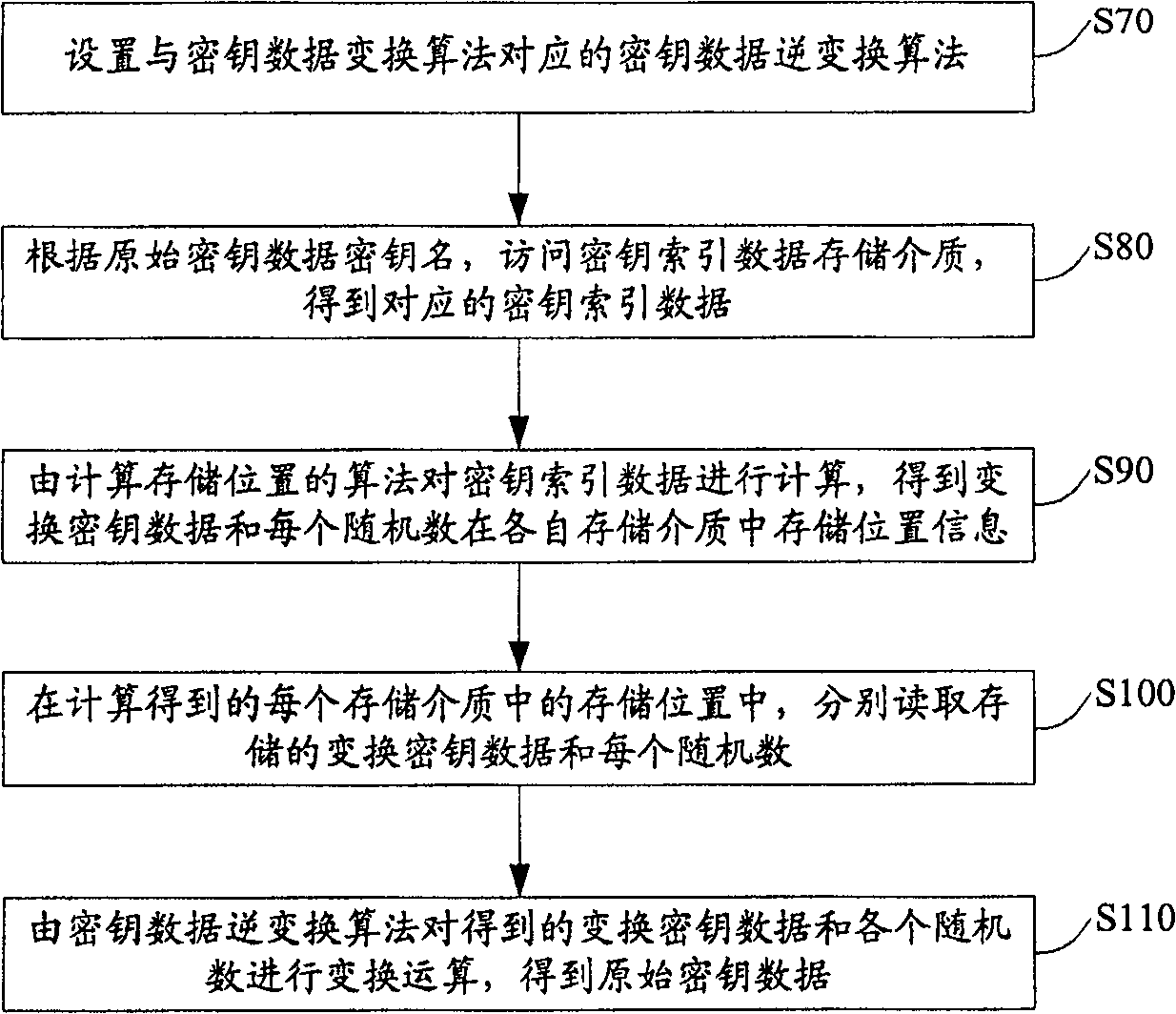
The method includes steps: setting up transformation algorithm for cipher key data in advance; generating original cipher key data by cipher key generator, random sequence generator generates several pieces of random numbers correlated to the original cipher key data at same time; carrying out transformation operation for original cipher key data and correlated several pieces of random numbers by using transformation algorithm for cipher key data setup before; storing up transformed cipher key data and each random number correlated to original cipher key data in storage media independent to each other. Comparing with prior art, the invention lowers complexity of cipher key storage step in cipher key management procedure, and raises security mechanism in storing cipher key.
Owner:HUAWEI TECH CO LTD
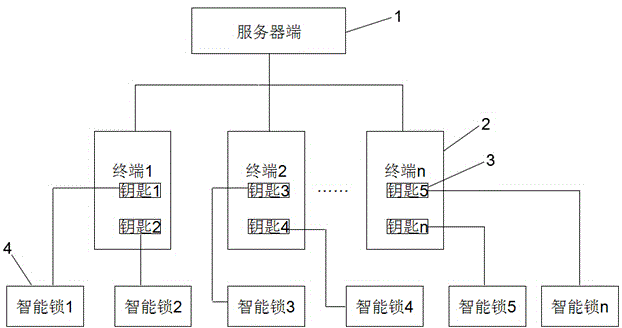
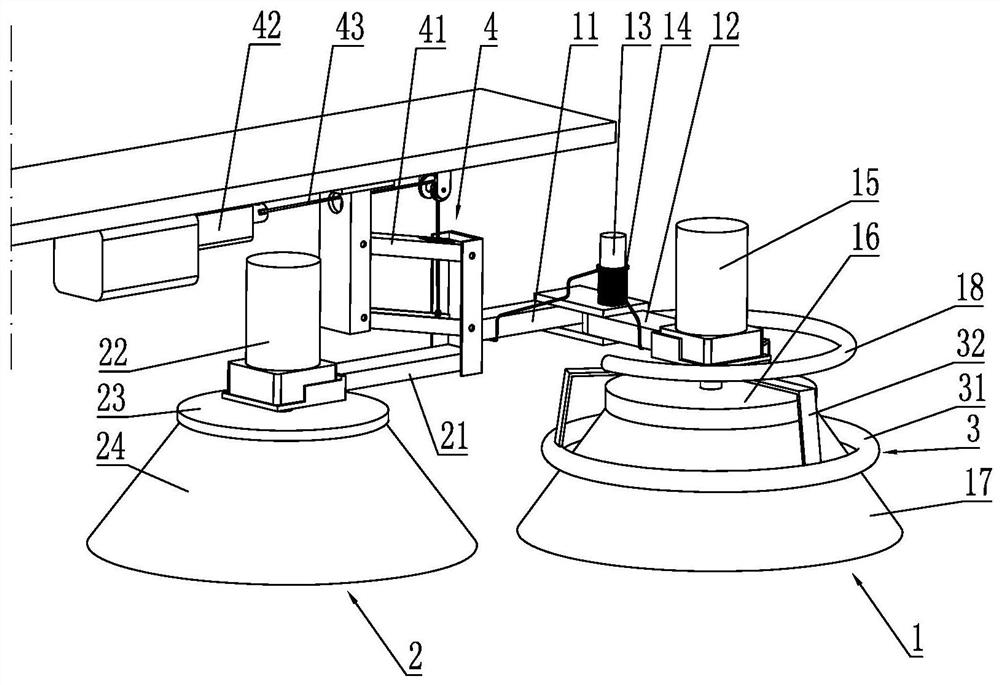
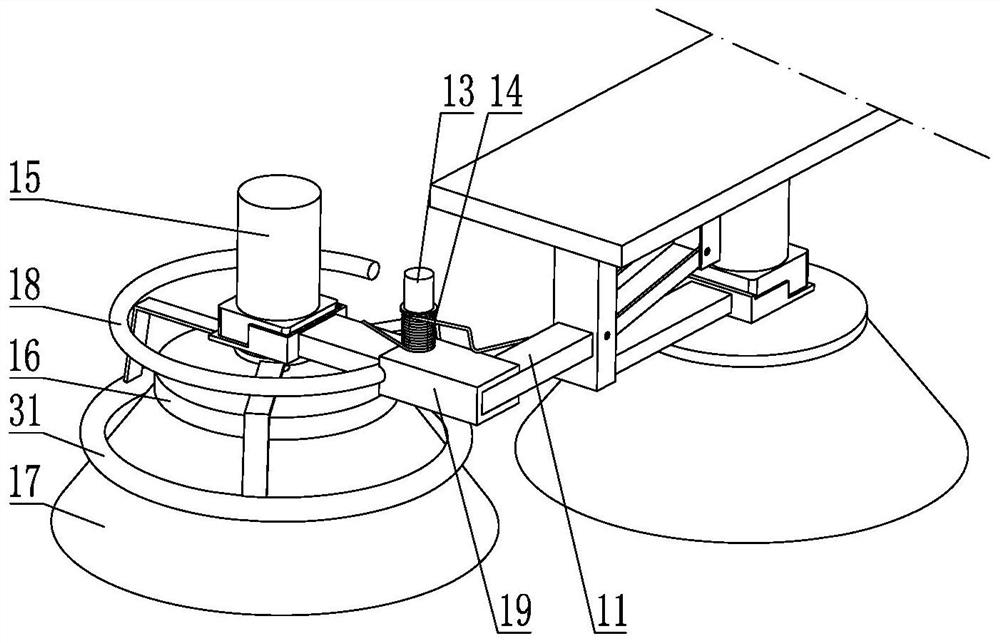
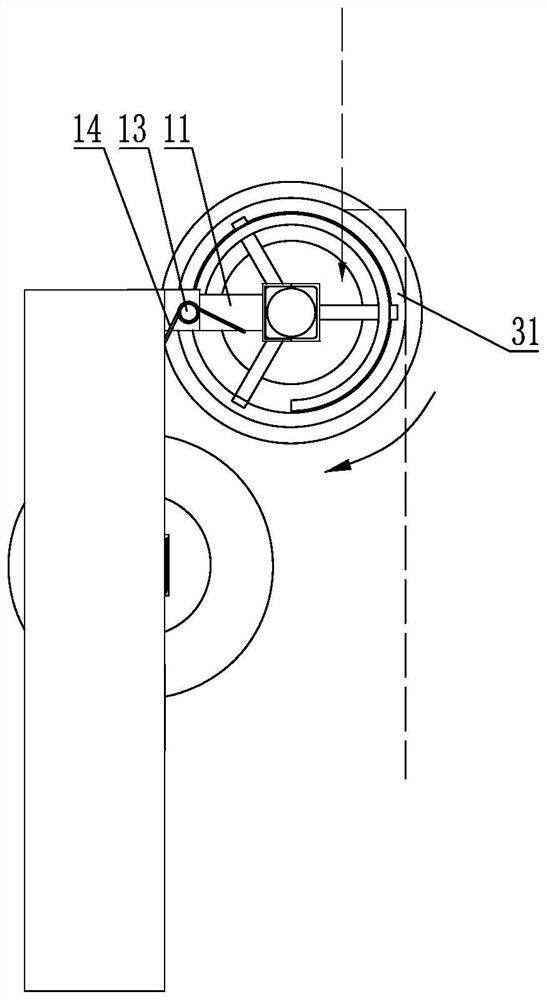
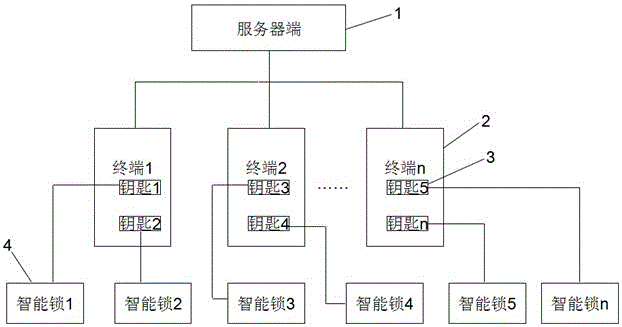
Intelligent lock control system
ActiveCN104484925AImprove securityAchieve traceabilityNon-mechanical controlsIndividual entry/exit registersTime rangeControl system
The invention discloses an intelligent lock control system, which comprises a server end, a terminal, intelligent keys and intelligent locks. The terminal is used for sending a request for opening at least one intelligent lock to the server end; the server end stores unique identifiers of all terminals in a control range, unique identifiers of all intelligent keys corresponding to the terminals and unique identifiers of all intelligent locks, and is used for examining and approving the request and sending an authentication command to the terminal if the examination and the approval pass; the terminal is further used for sending an authentication command to the key matched with a unique identifier according to the received unique identifier of the key carried by the authentication command; the intelligent keys are internally provided with electronic codes, and are used for receiving authentication commands and matching with the intelligent keys in a time range to unlock by using a first-stage password; the intelligent locks are internally provided with electronic encoders, and are used for reading electronic codes for matching after the intelligent keys are inserted in lock holes, and unlocking by using a second-stage password if the matching succeeds.
Owner:江苏今越控股集团有限公司
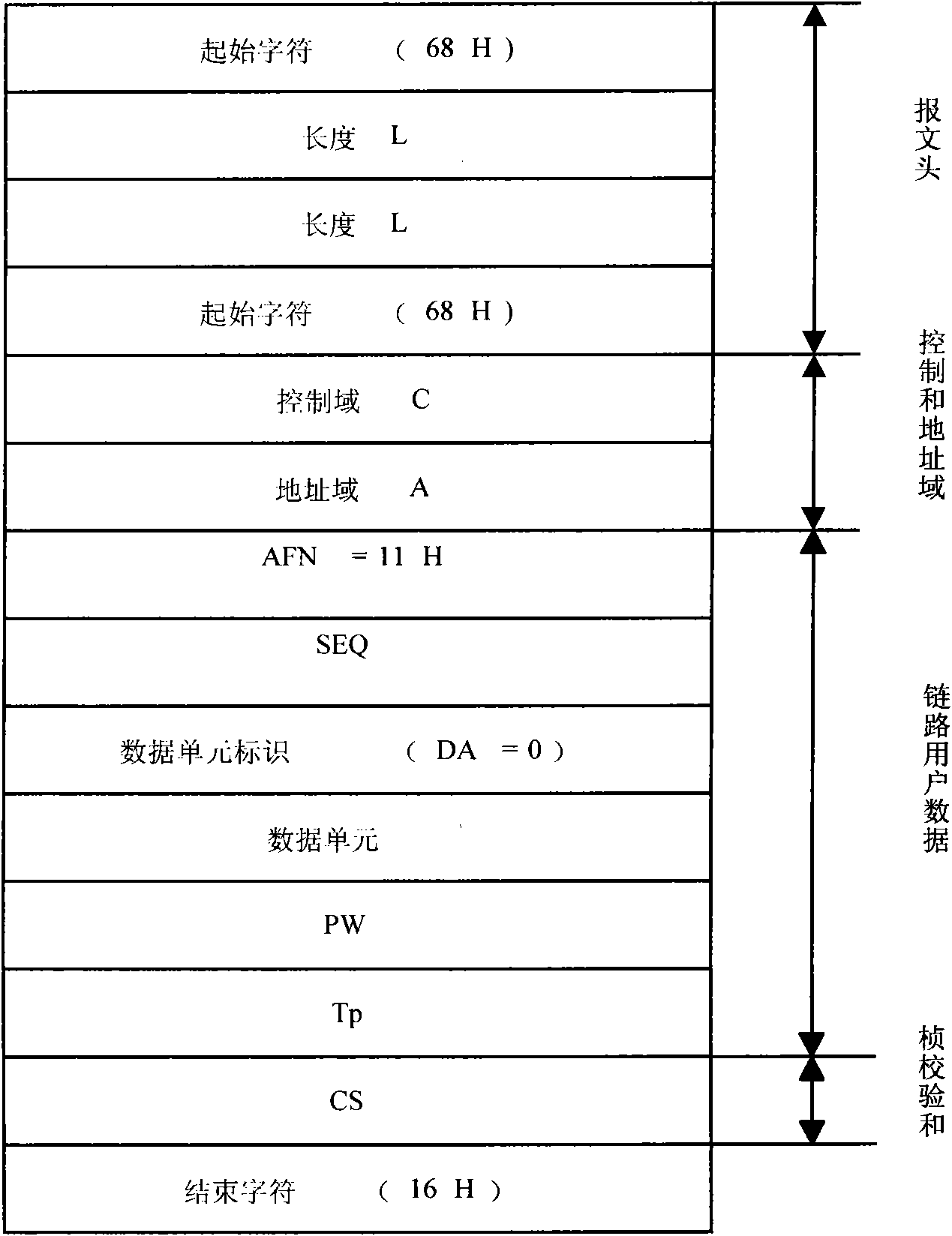
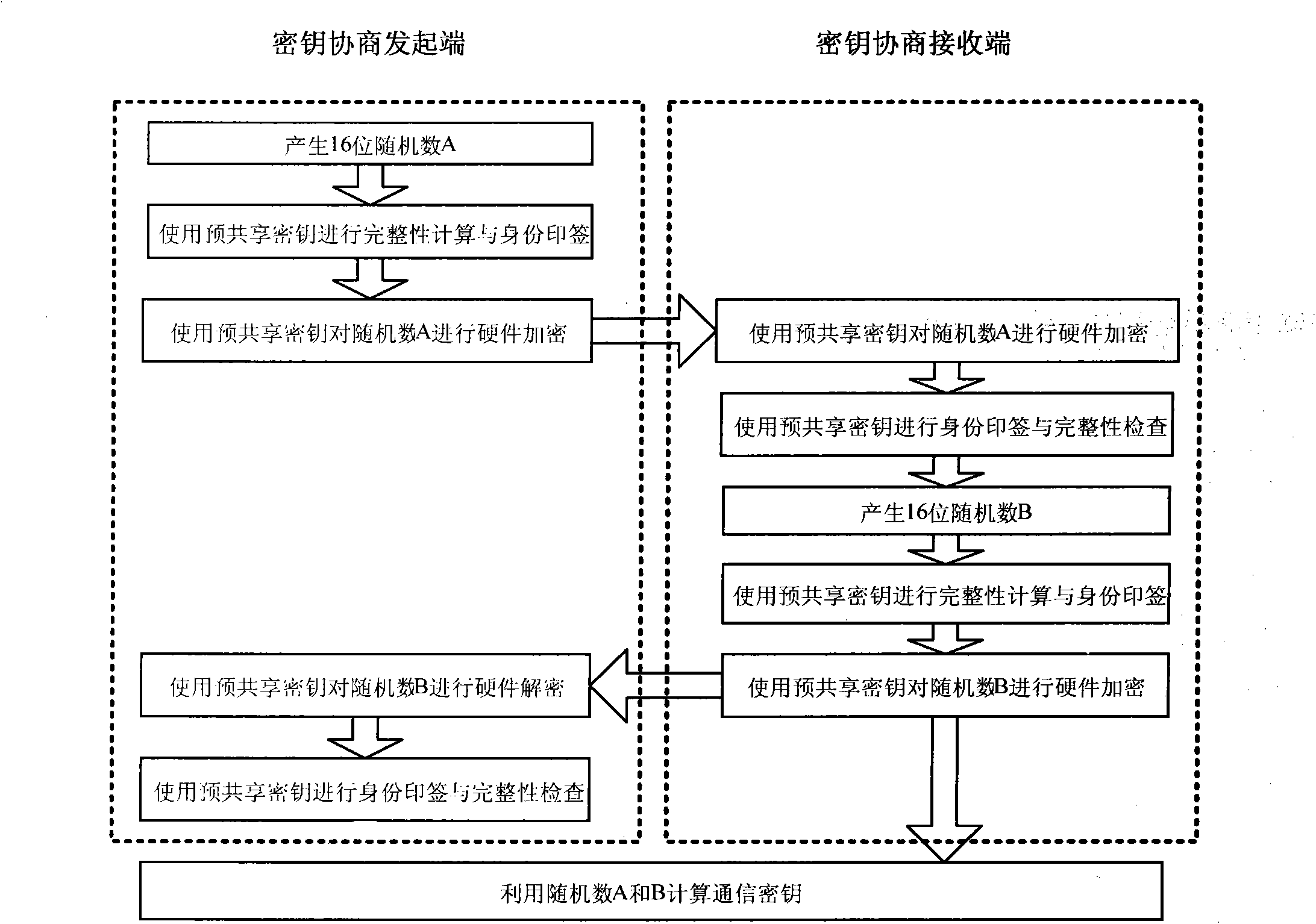
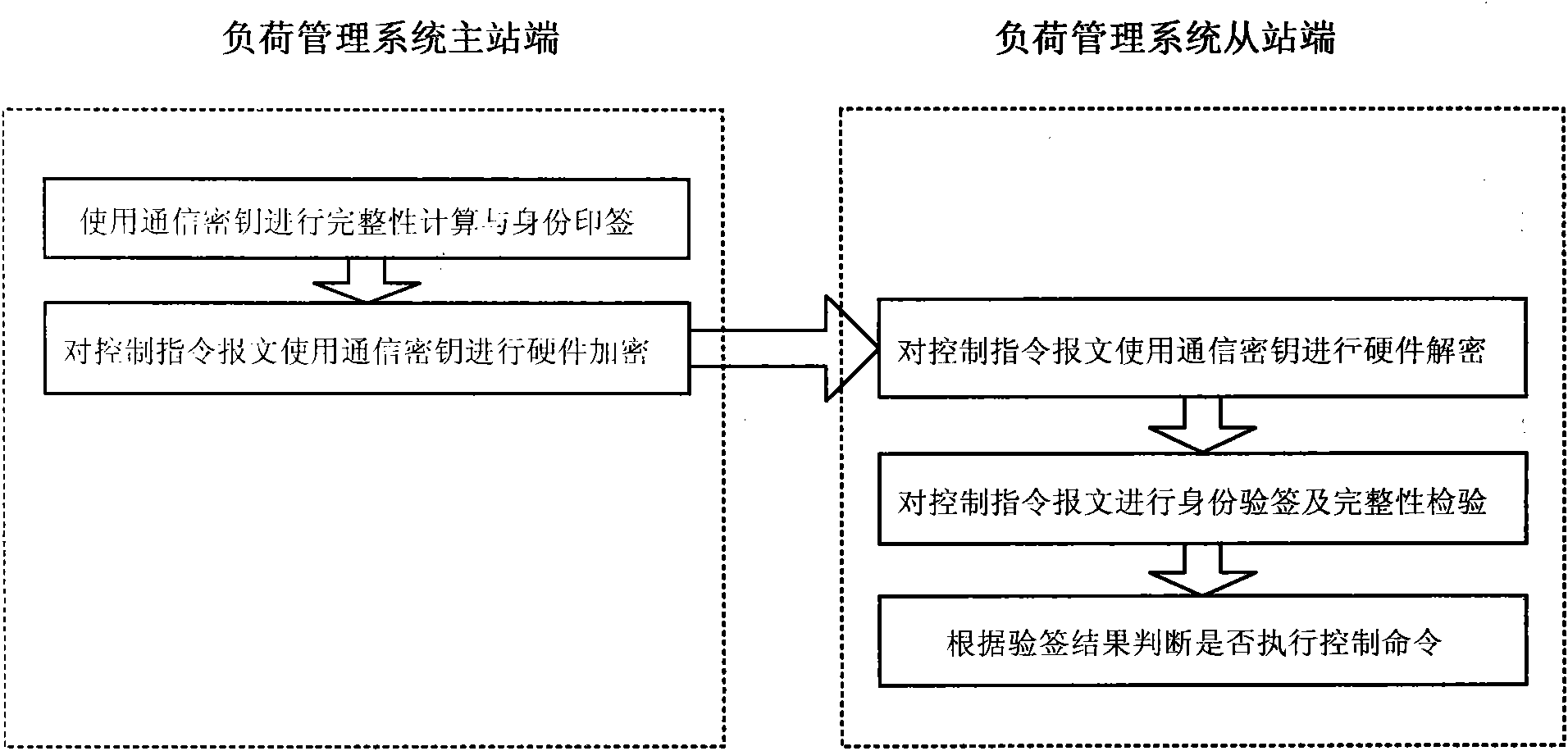
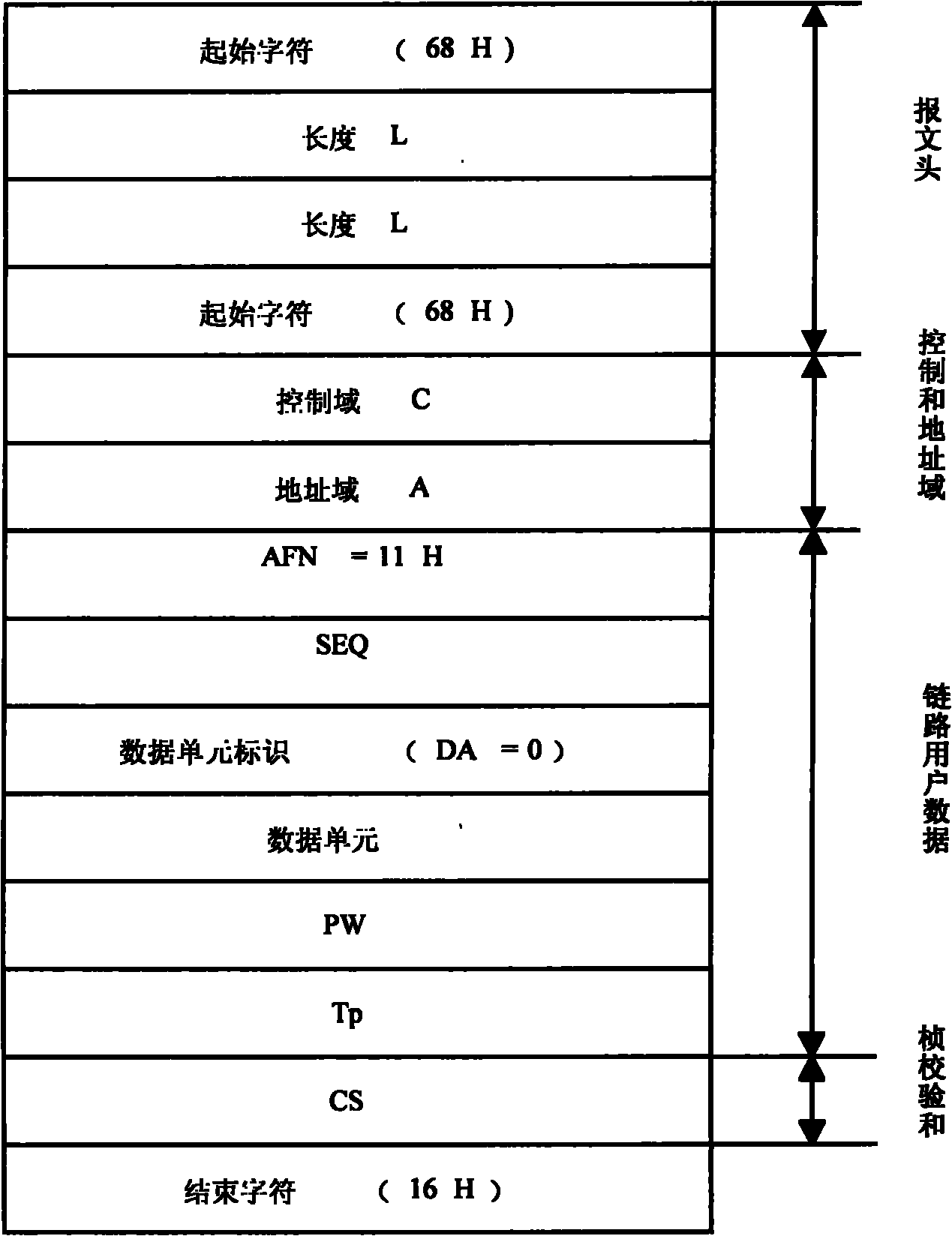
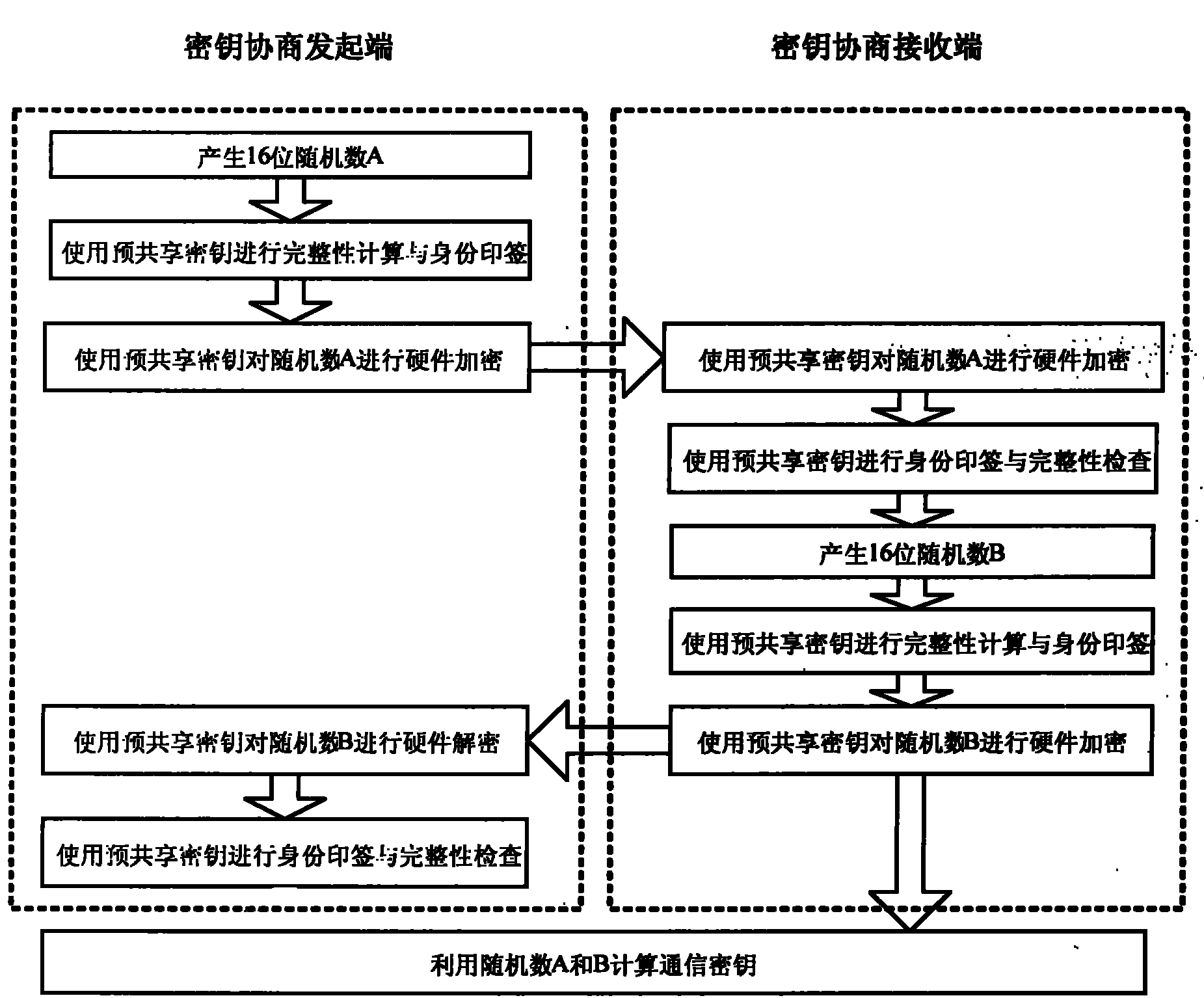
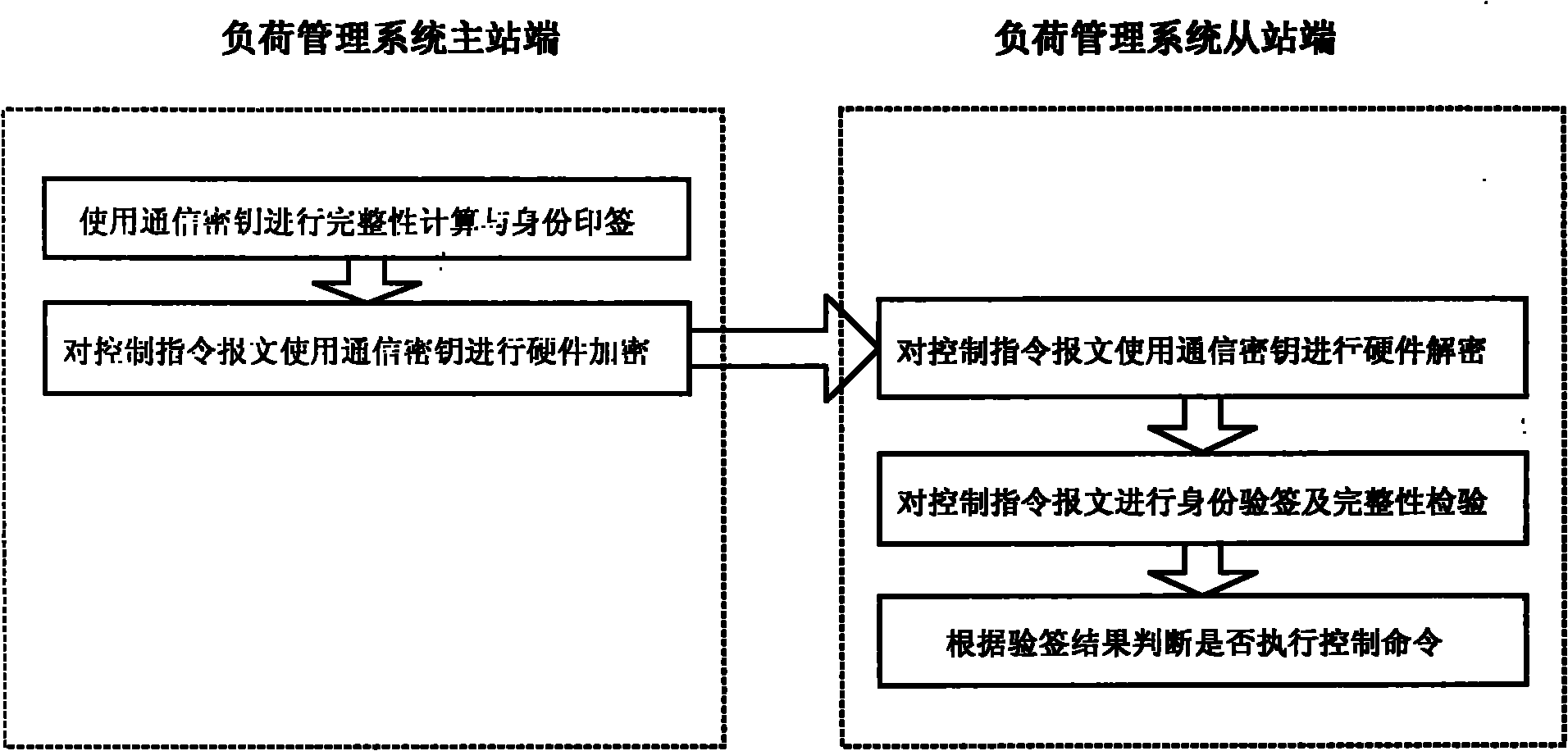
Pre-sharing-based secure data transmission method for electric load management system
ActiveCN102111273AImprove identity authenticationPerfect integrityKey distribution for secure communicationError preventionTransmission protocolConfidentiality
The invention provides a pre-sharing-based secure data transmission method for an electric load management system, which is significant to a power load management system to resist various security threats in wireless communication environments and open Internet environments. The confidentiality, integrity and availability of transmission data of the system can be ensured through perfection of the transmission protocol identity authentication and the integrity checking mechanism of the power load management system, and encryption of important control instructions. The method has significant meaning and demonstration effects to the formulation of secure data transmission schemes for other power application systems.
Owner:CHINA ELECTRIC POWER RES INST +1
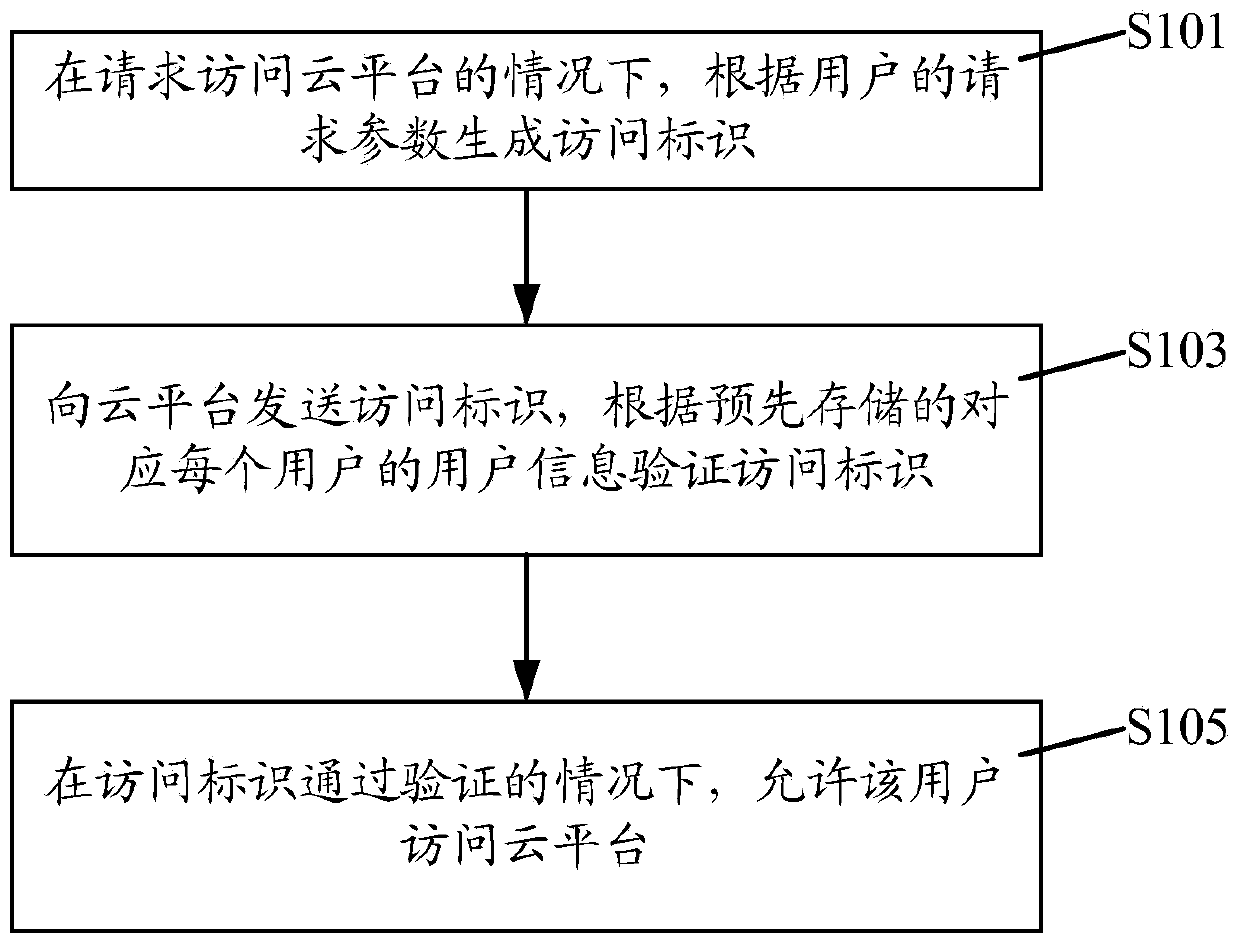
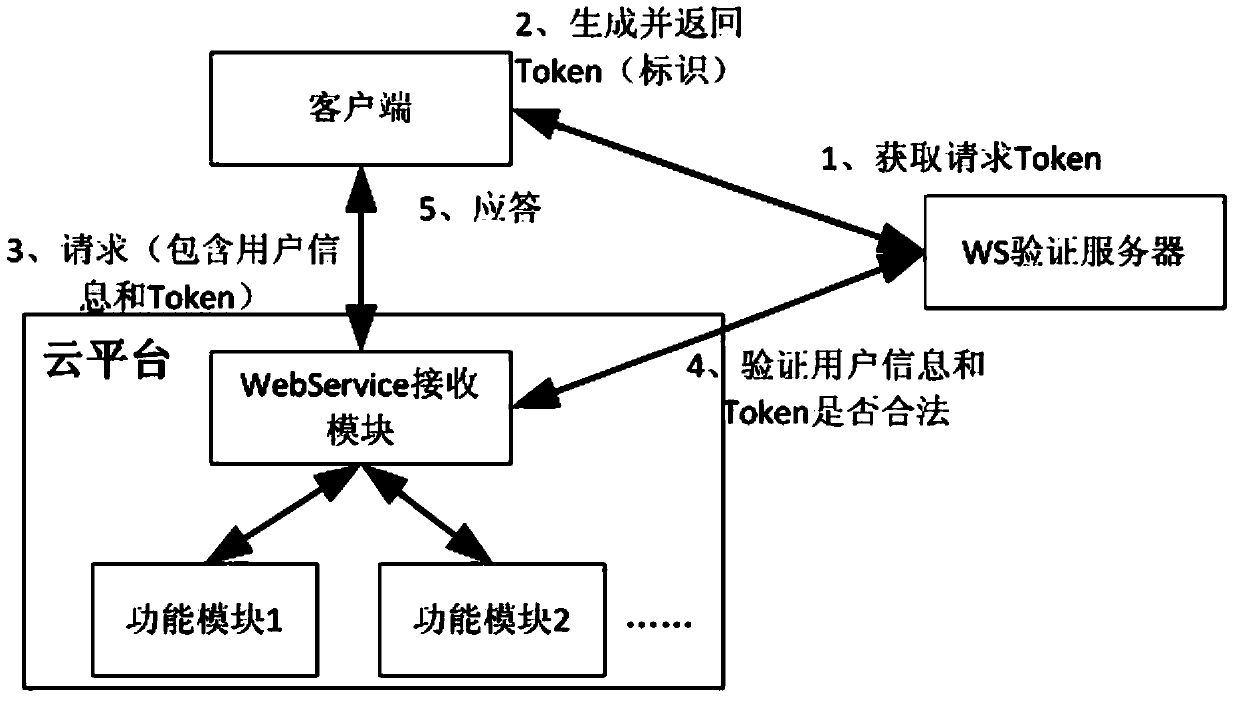
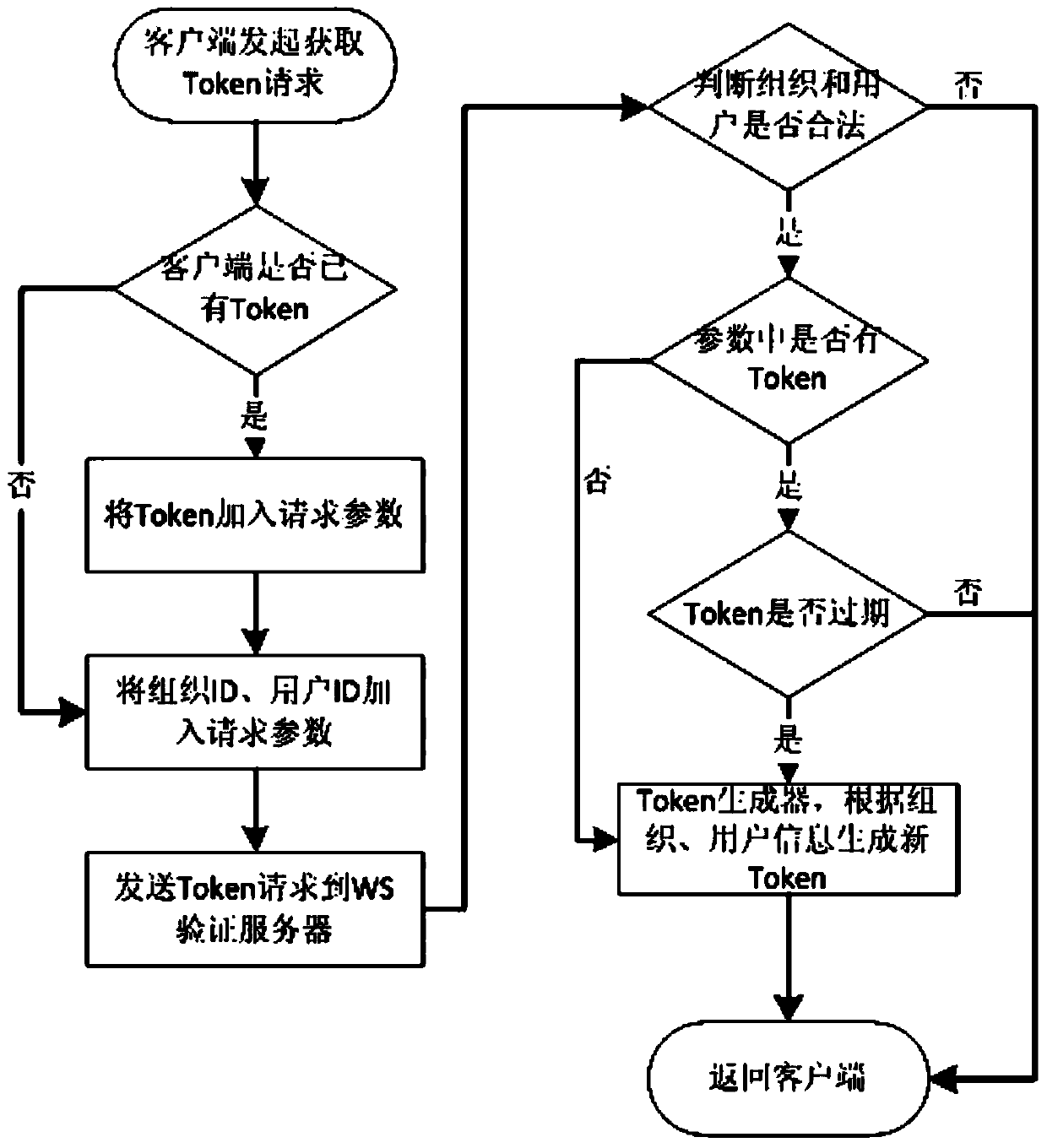
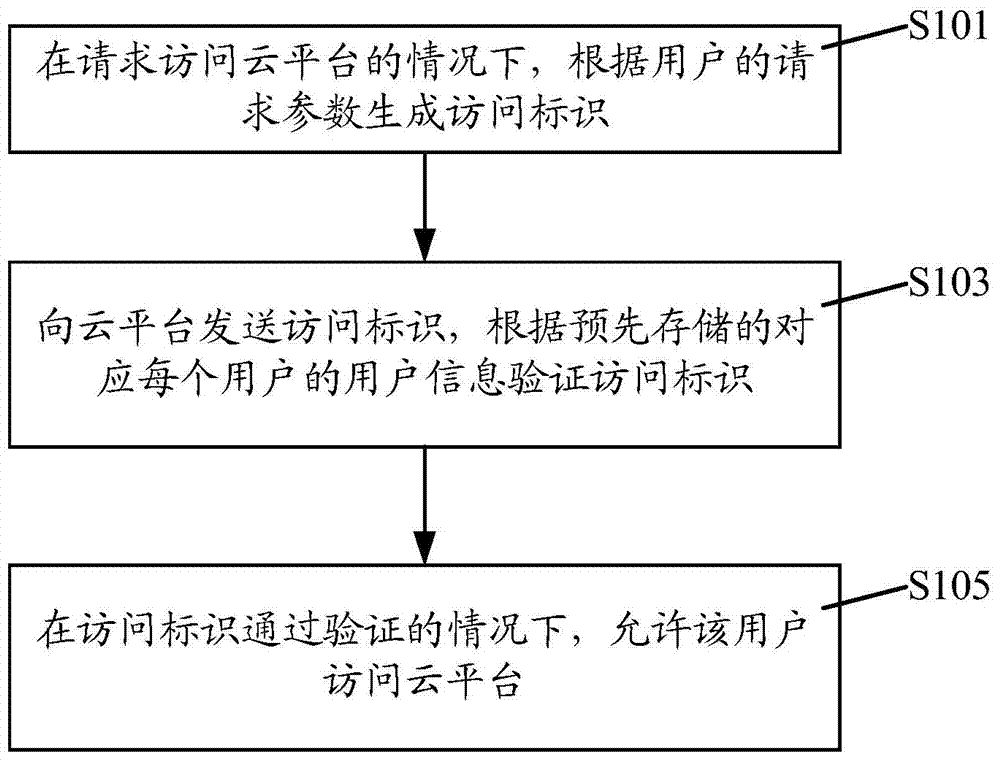
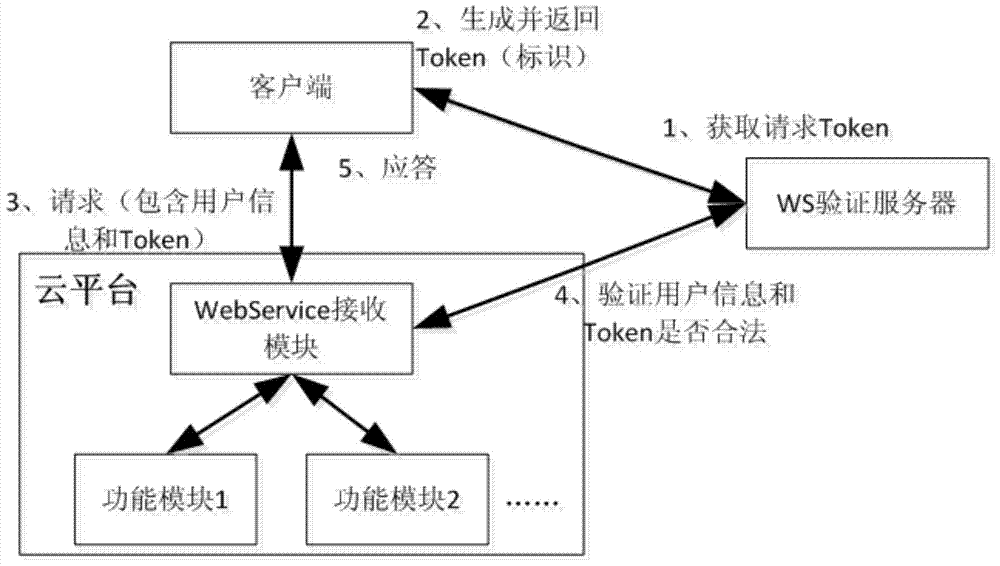
Cloud platform access method and device
ActiveCN103747076AHigh security mechanismAvoid malicious accessDigital data protectionTransmissionAccess methodUser information
The invention discloses a cloud platform access method and a cloud platform access device, wherein the cloud platform access method comprises the following steps that under the condition of requesting to access a cloud platform, access marks are generated according to the request parameters of users; the access marks are sent to the cloud platform, and are verified according to the pre-stored user information corresponding to each user; under the condition that the access marks pass the verification, the users are allowed to access the cloud platform. The cloud platform access method and the cloud platform access device have the advantages that access marks are generated according to the request parameters of the users, in addition, the access marks are verified through the pre-stored user information, and the effect of allowing the users to access the cloud platform only under the condition that the access marks pass the verification is ensured, so the safety mechanism of the cloud platform is effectively improved, the malignant access of illegal users to the cloud platform is avoided, and the resource waste of the cloud platform is reduced.
Owner:DAWNING CLOUD COMPUTING TECH CO LTD
Plug-in data transmission method, client and server
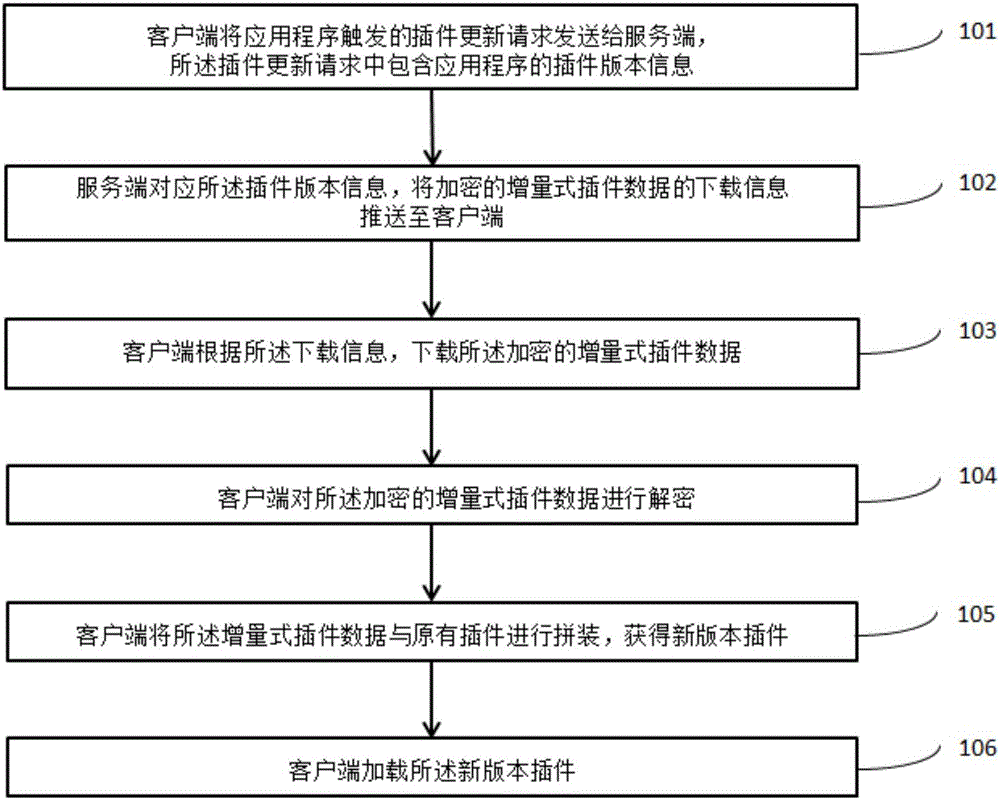
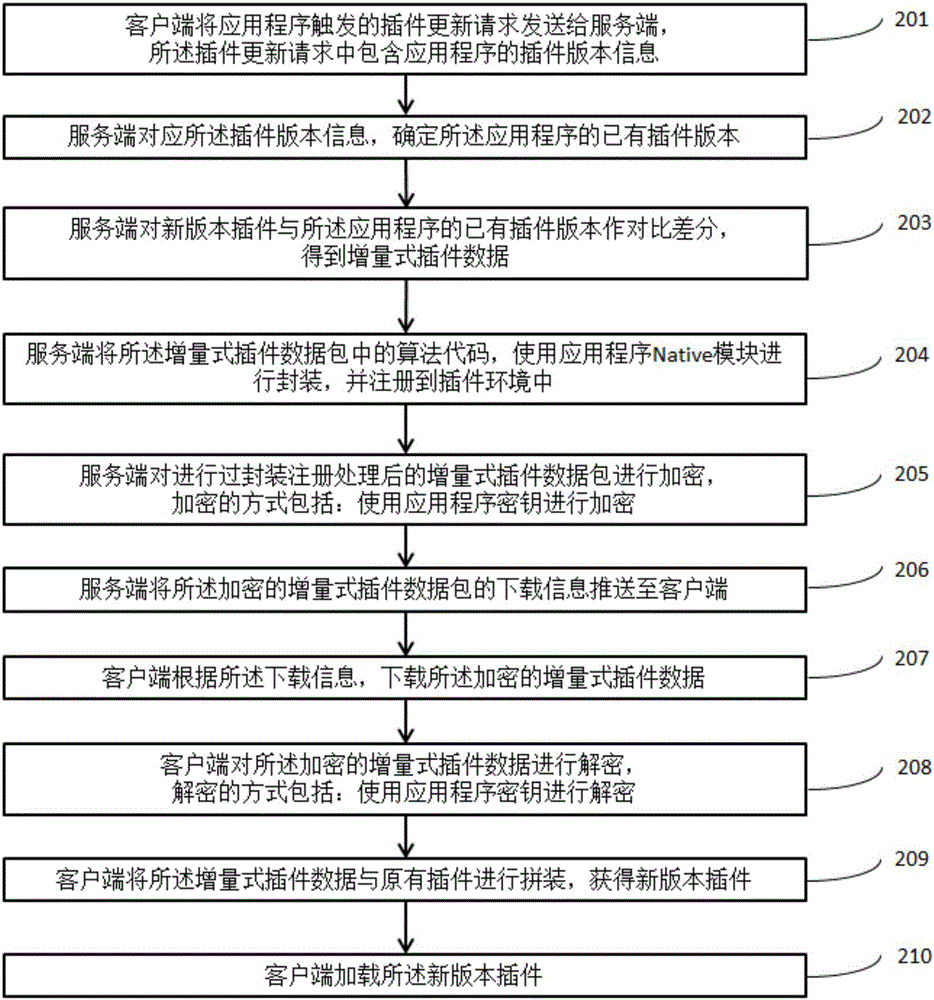
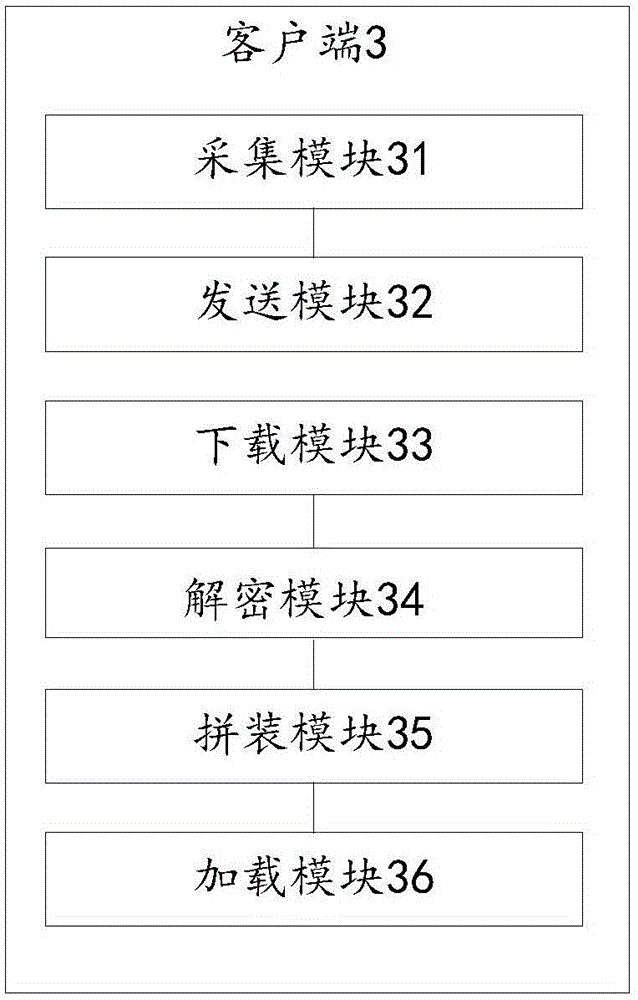
InactiveCN106330936AReduce sizeReduce overheadProgram loading/initiatingTransmissionApplication softwarePublic network
The invention discloses a plug-in data transmission method, a client and a server. The method comprises the following steps: the client sends a plug-in update request to the server according to the plug-in update request triggered by an application program, wherein the request contains plug-in version information of the application program, the server carries out differential calculation on new and old versions after receiving the plug-in update request to acquire incremental plug-in data, and pushes downloading information of the incremental plug-in data to the client, the client receives the downloading information, downloads the plug-in data, splices the incremental plug-in data with an existing plug-in to acquire a complete new version plug-in, and loads the new version plug-in. By adoption of the plug-in data transmission method provided by the invention, the possibility that the plug-in data are decoded or tampered in a public network transmission process is reduced, and the security mechanism of plug-in data transmission is effectively improved.
Owner:GUANGZHOU PINWEI SOFTWARE
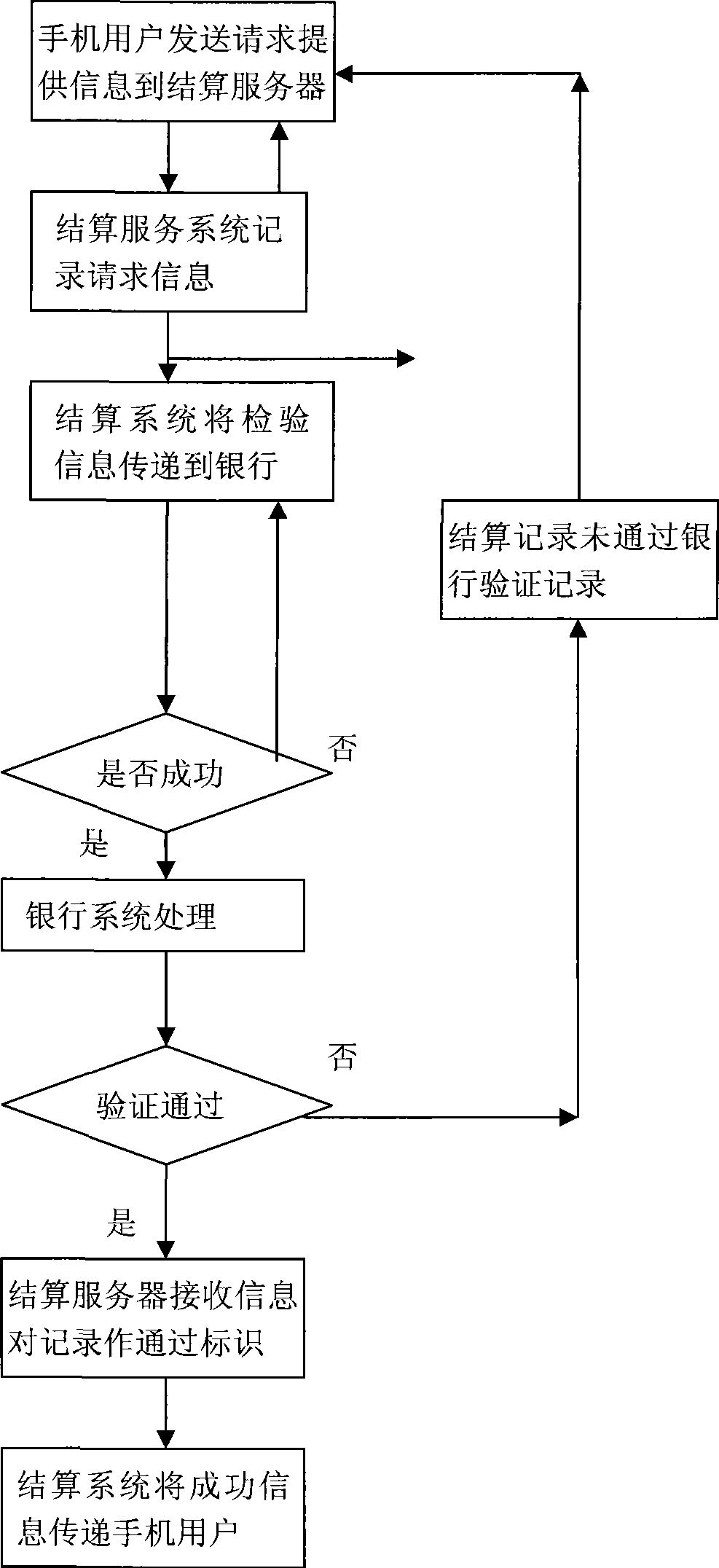
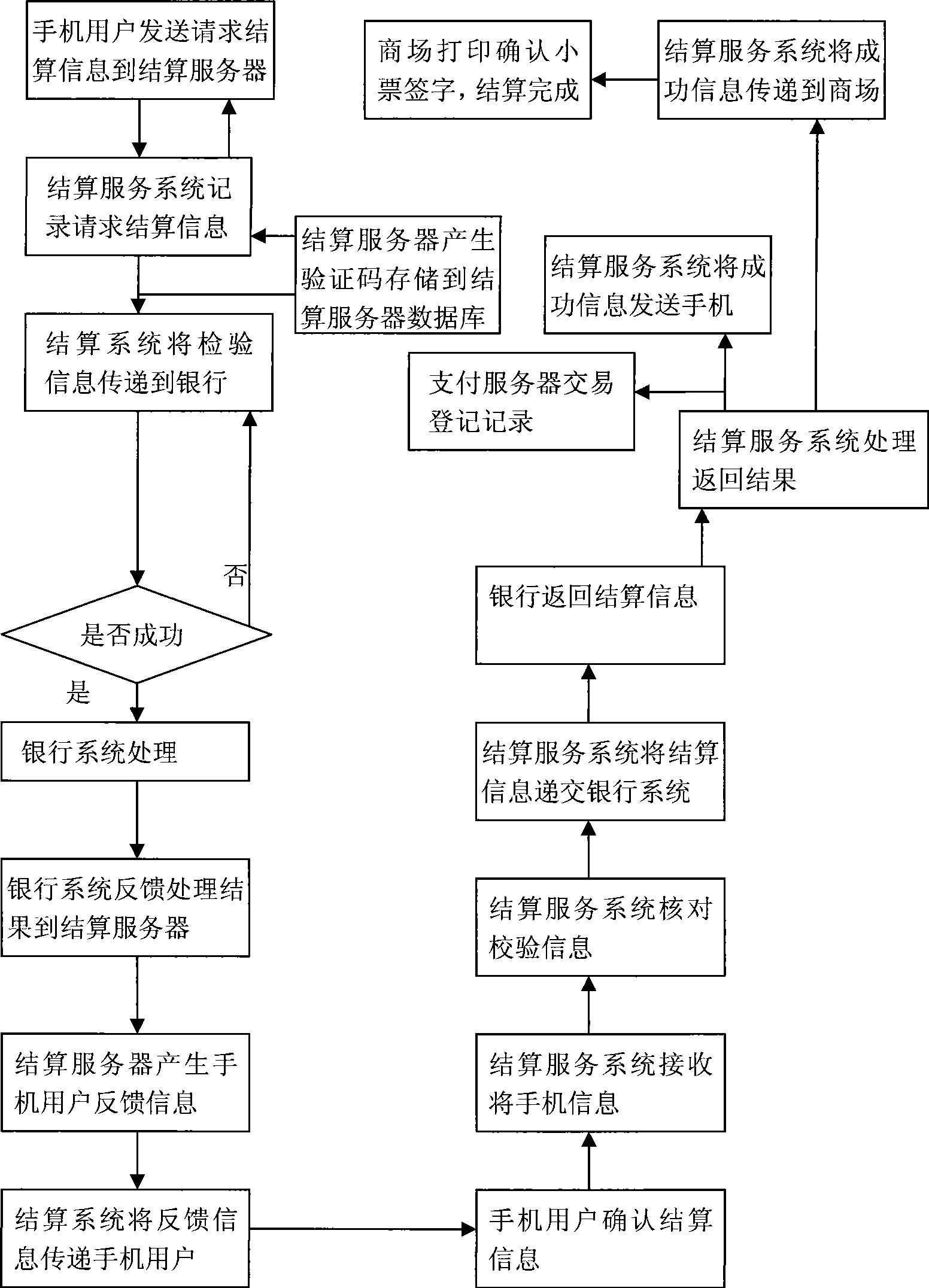
Mobile phone bank system and method
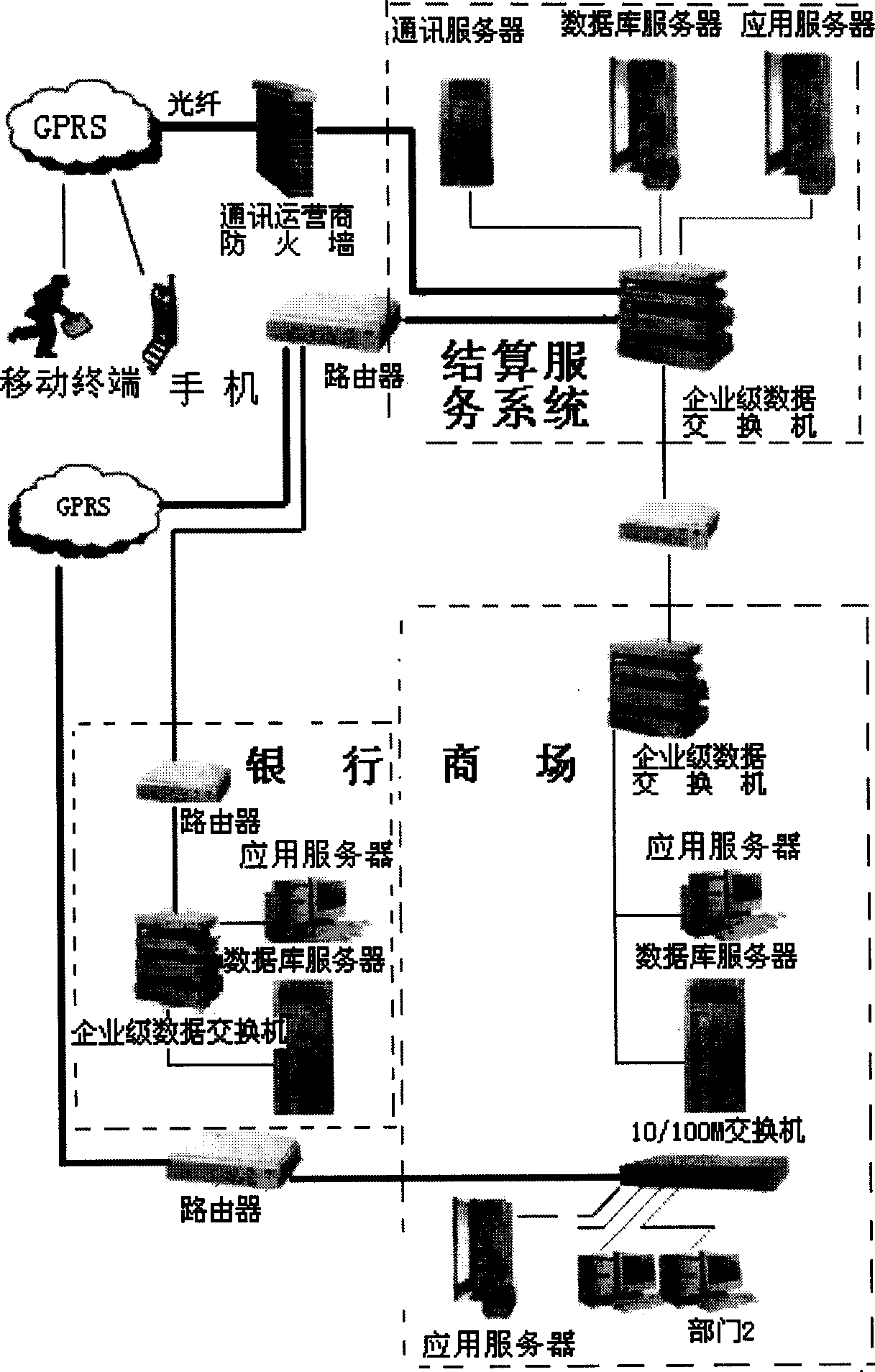
InactiveCN101466086ASimple methodHigh security mechanismAccounting/billing servicesPayment architectureCommunication interfaceTelecommunications network
The invention relates to a system utilizing a wireless telecommunication network and a bank to pass through a mobile banking by networking and a method thereof. A communication interface and a data transferring interface are established between a settlement system and the bank and between the settlement system and settlement units (such as markets and charging units) by means of the internet; consumers can send a settlement request to a settlement service system by the mobile phone; the settlement system can transmit the settlement request to a bank transaction system; the bank executes the autopay and then sends the data to the settlement system; and the settlement system can respectively send the settlement result to the mobile phone of the consumer and the settlement units, so as to finish the settlement. The method is rapid and convenient, and has high security mechanism.
Owner:江苏省烟草公司徐州市公司
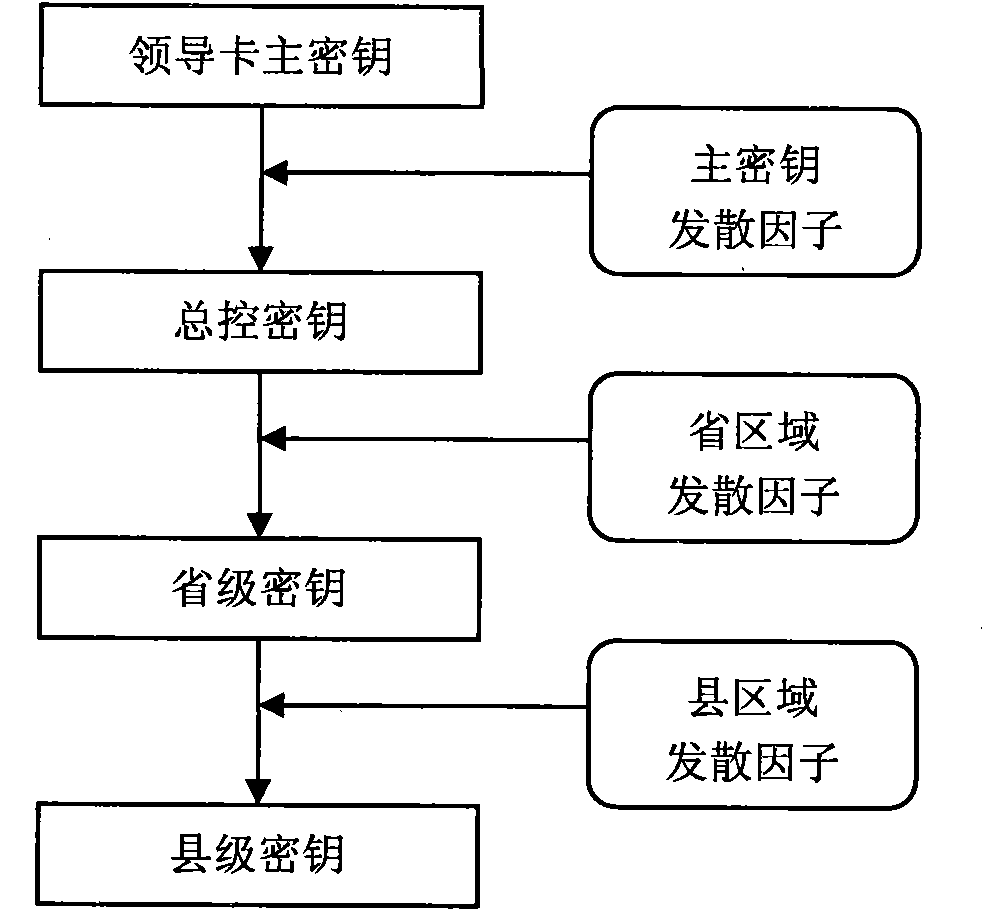
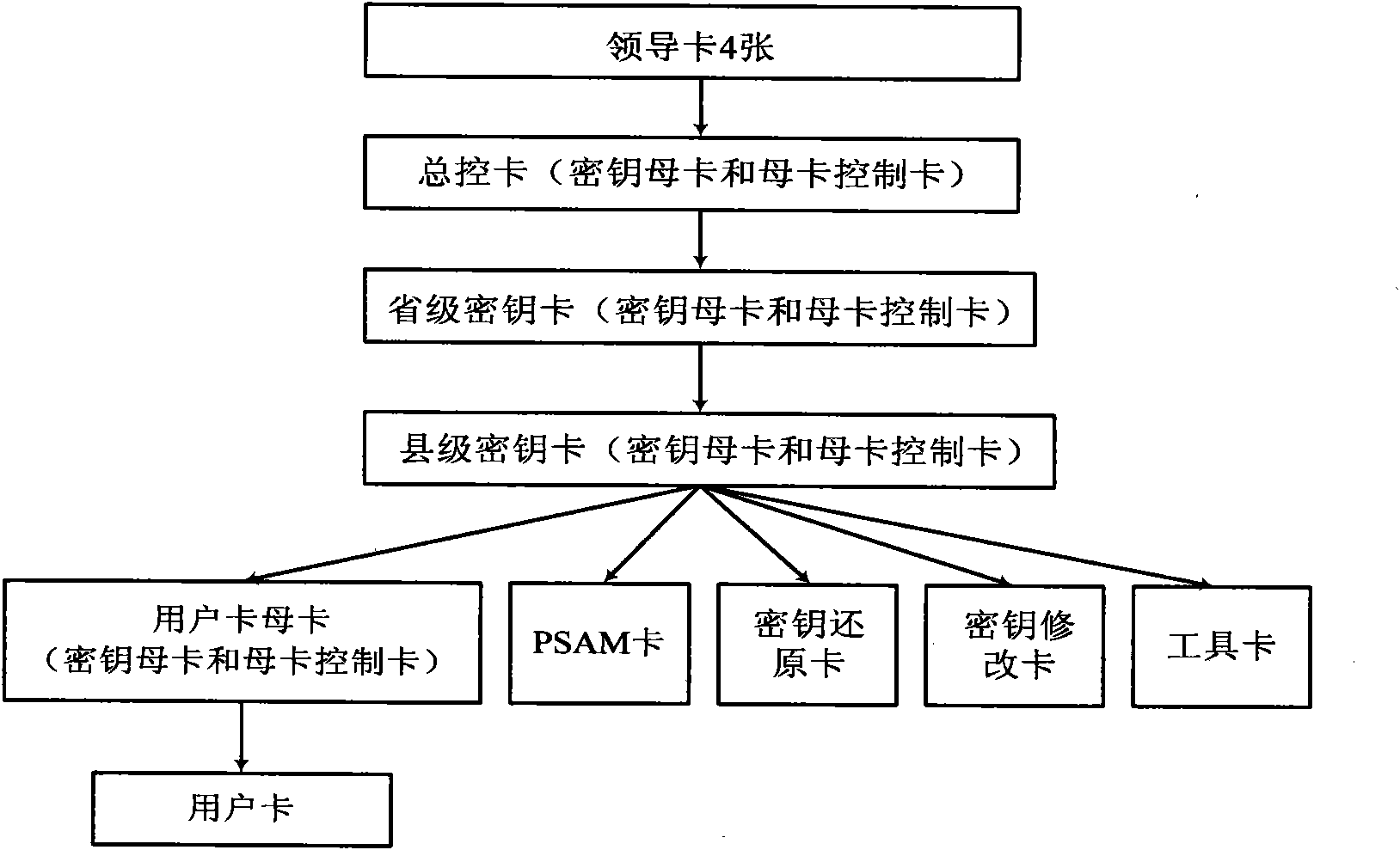
System for measuring and managing electric energy used for agricultural irrigation and drainage
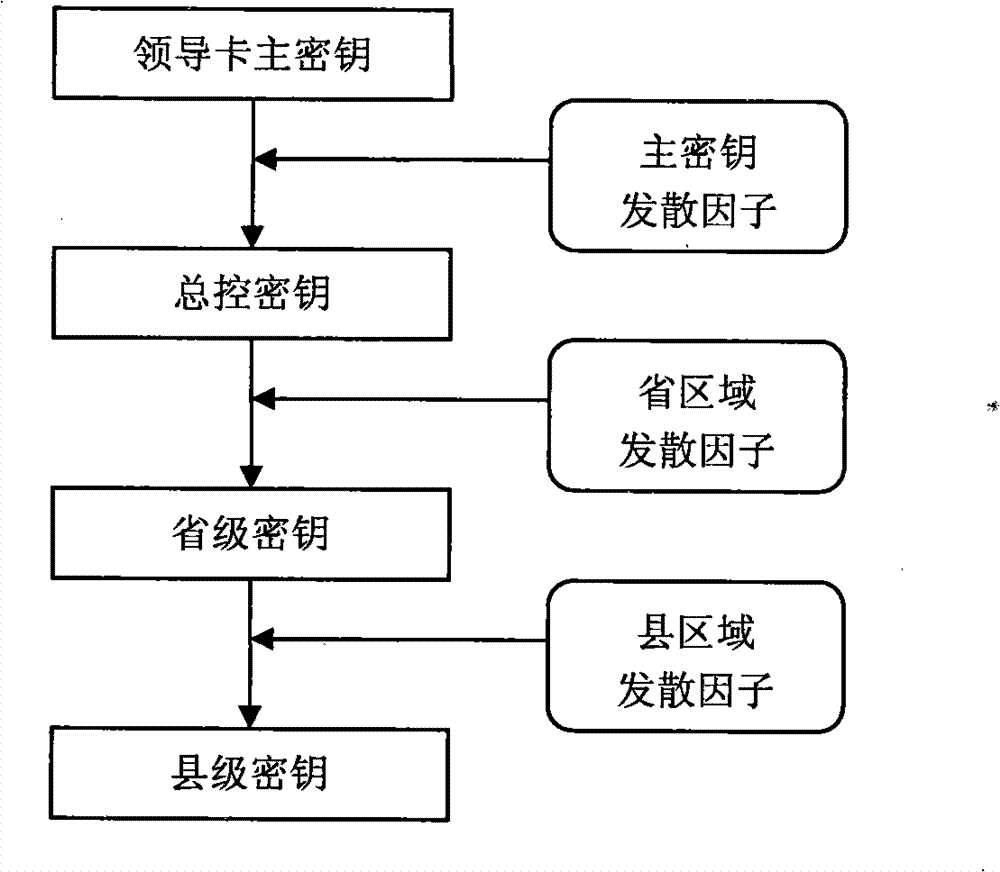
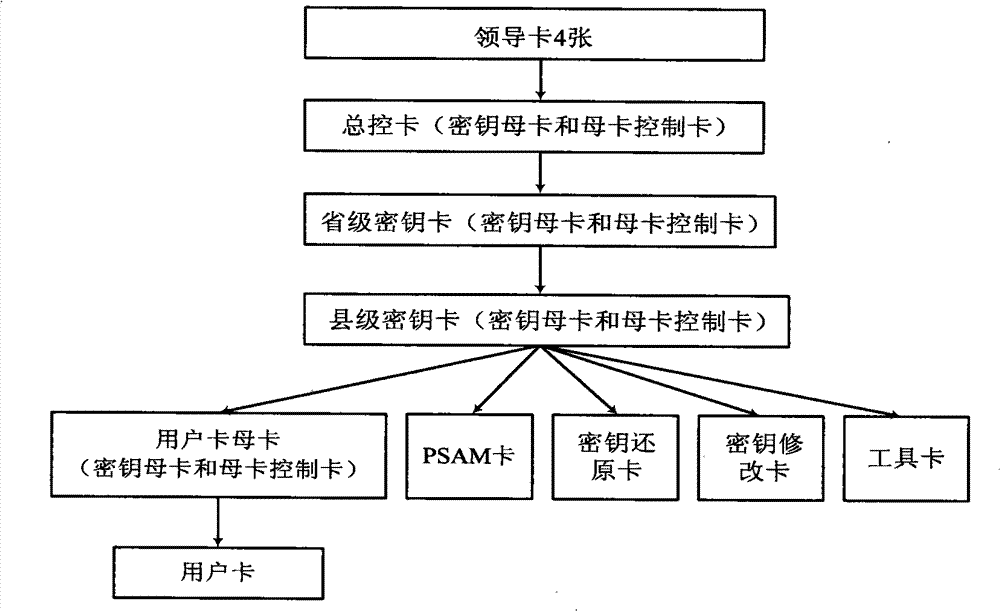
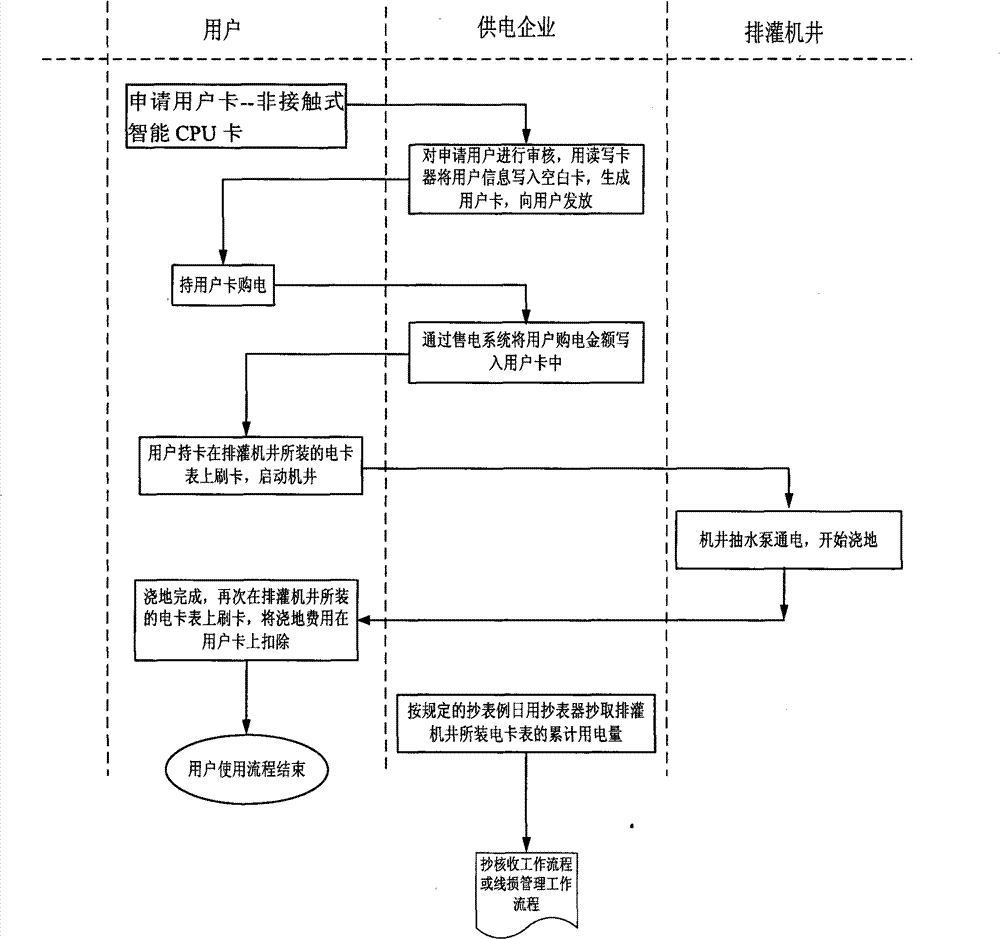
InactiveCN101777214ASolve private electricity salesHigh security mechanismApparatus for hiring articlesCoded identity card or credit card actuationElectricity meterAgriculture
The invention relates to a system for measuring and managing electric energy used for agricultural irrigation and drainage, which comprises a prepaid card electricity meter, a meter reader, a card reader, a provincially unified key system, an electricity selling system and a non-contact intelligent CPU card serving as a storage medium. The same type of equipment adopts a unified technical specification and communication interface to ensure inter-equipment communication and realize the function of the system. A PSAM module with a storage key is arranged in the unified prepaid card electricity meter of an electricity selling terminal; and keys in the PSAM module and the intelligent CPU card are used for performing security authentication to realize the high-level management of recharging and avoid the possibility of selling the electricity privately. The unified key system strengthens the security system of the whole system and improves the technology level of preventing electricity stealing. The unified electricity selling system and WEB data representation and data mining technology improve the accuracy, the consistency and the generality of data and provide a reliable data basis for leaders from provincial and municipal top management departments and the unit.
Owner:STATE GRID HEBEI ELECTRIC POWER CO LTD
Ping pong table with folding protection mechanism
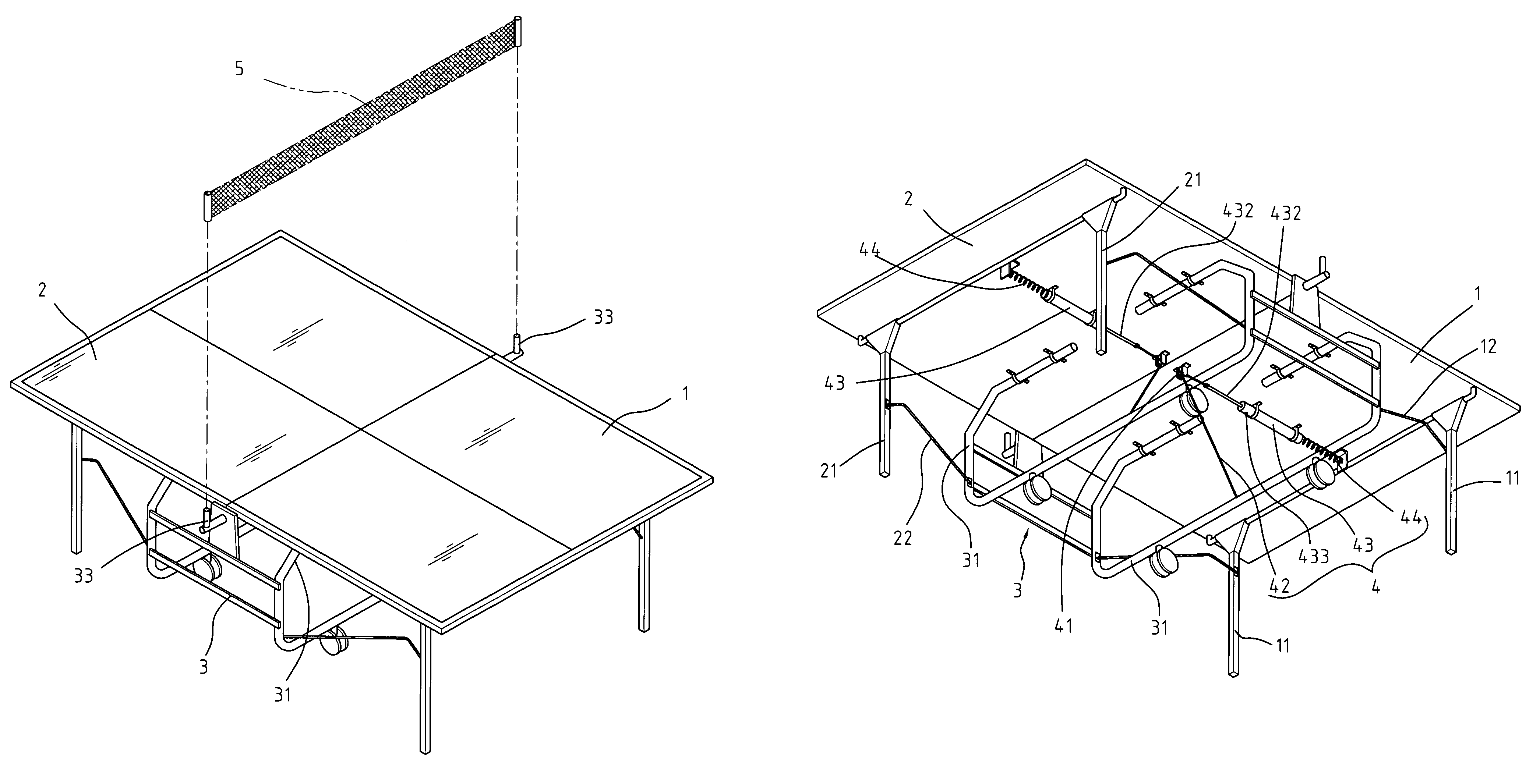
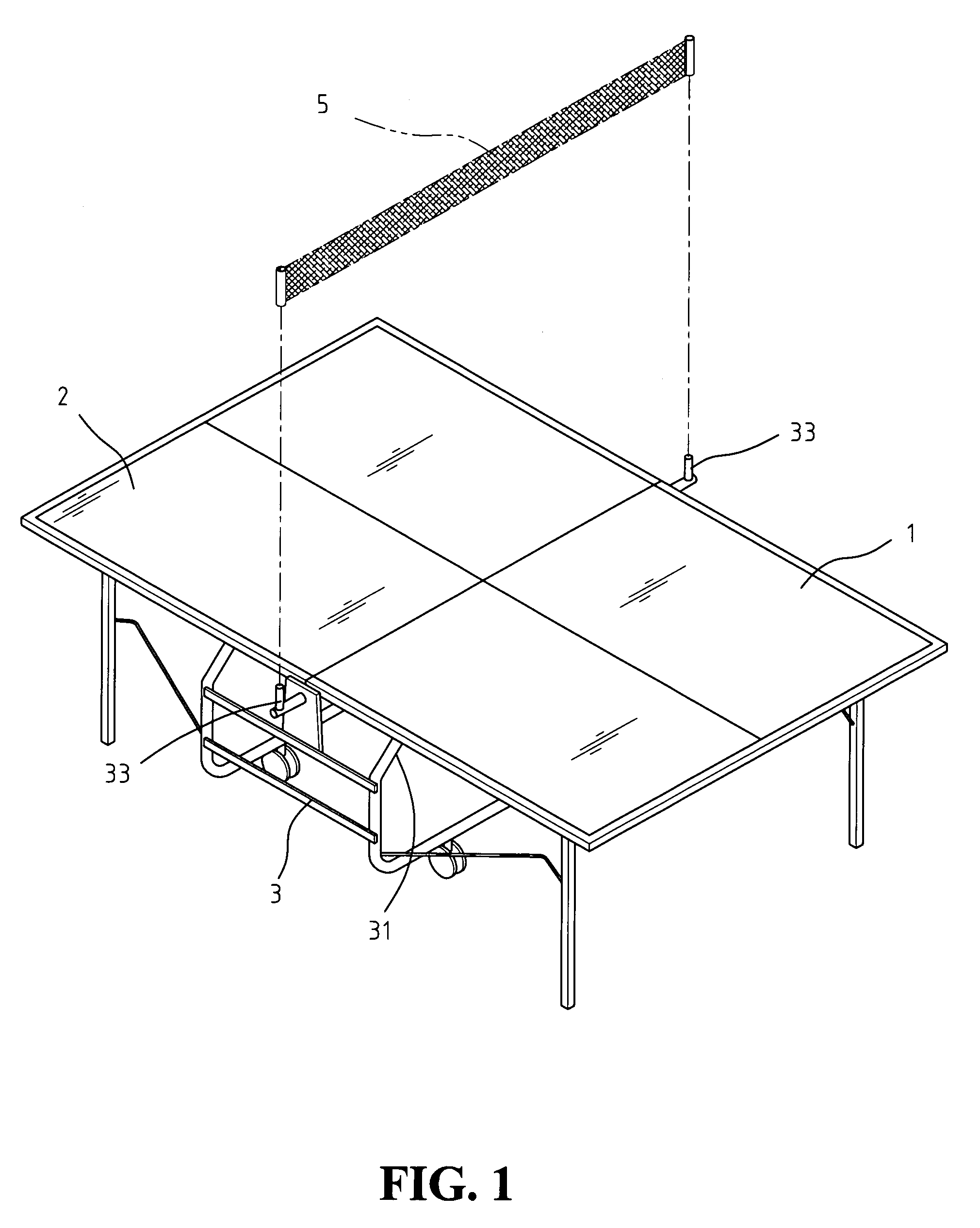
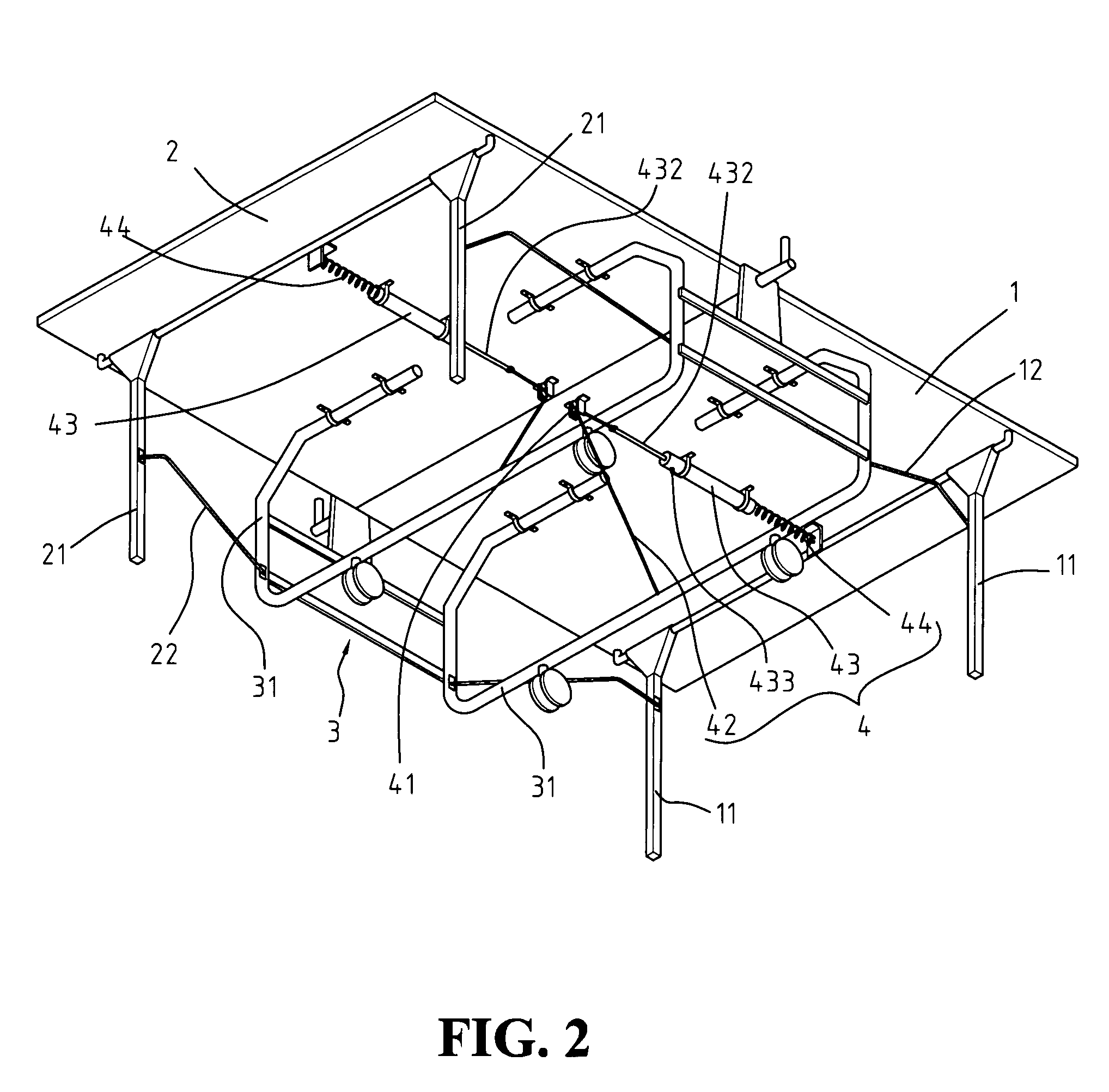
InactiveUS7156763B1Dampen motionOperational safety is enhancedSpace saving gamesTable tennis tablesProtection mechanismEngineering
A ping pong table with folding protection mechanism is disclosed. At least a pair of folding protection mechanisms is installed underneath the table, one on each side. Each folding protection mechanism is composed of at least one guide roller, one steel cable, and one pneumatic cylinder. The two halves of the ping pong table are folded and supported by an under carriage that is pivotally attached onto the underside of the table. The pneumatic cylinder on each side has one end connected to a cross bar under the table, and the other end connected to a steel cable, which then, through guide rollers, is further connected to the bottom beam of the undercarriage. This folding protection mechanism makes the folding / unfolding of the ping pong table easier and more user-friendly, so even one person is able to handle the table set up without difficulty.
Owner:LIAO GRACE
Automatic edge searching mechanism of unmanned sweeper
PendingCN111636346AThe way the signal is delivered is accurateReliable way of signalingRoad cleaningEngineeringBrush device
The invention discloses an automatic edge searching mechanism of an unmanned sweeper. A front brush device is arranged in front of a side brush device and extends outwards towards the side part of thesweeper; the front brush device comprises a front brush fixing frame; a front brush swing arm capable of horizontally swinging towards the rear portion of the sweeper is installed on the outer side of the front brush fixing frame, an angle sensor used for collecting the backward swing angle of the front brush swing arm is arranged between the front brush swing arm and the front brush fixing frame, and the lower portion of a front brush assembly is covered with an edge searching device used for making contact with or colliding with road shoulder stones. The anti-collision function can be achieved by making contact with curbstones in advance through the edge searching device, and the use safety of the sweeper is guaranteed; the direction signal of the sweeper is obtained through the angle sensor and adjusted, the automatic edge finding function of the sweeper is achieved, the sweeper can sweep along the root of the road shoulder stone all the time, the unmanned sweeper can adapt to theautomatic edge finding sweeping function, and the safety mechanism of the unmanned sweeper is greatly improved.
Owner:康洁科技集团有限公司
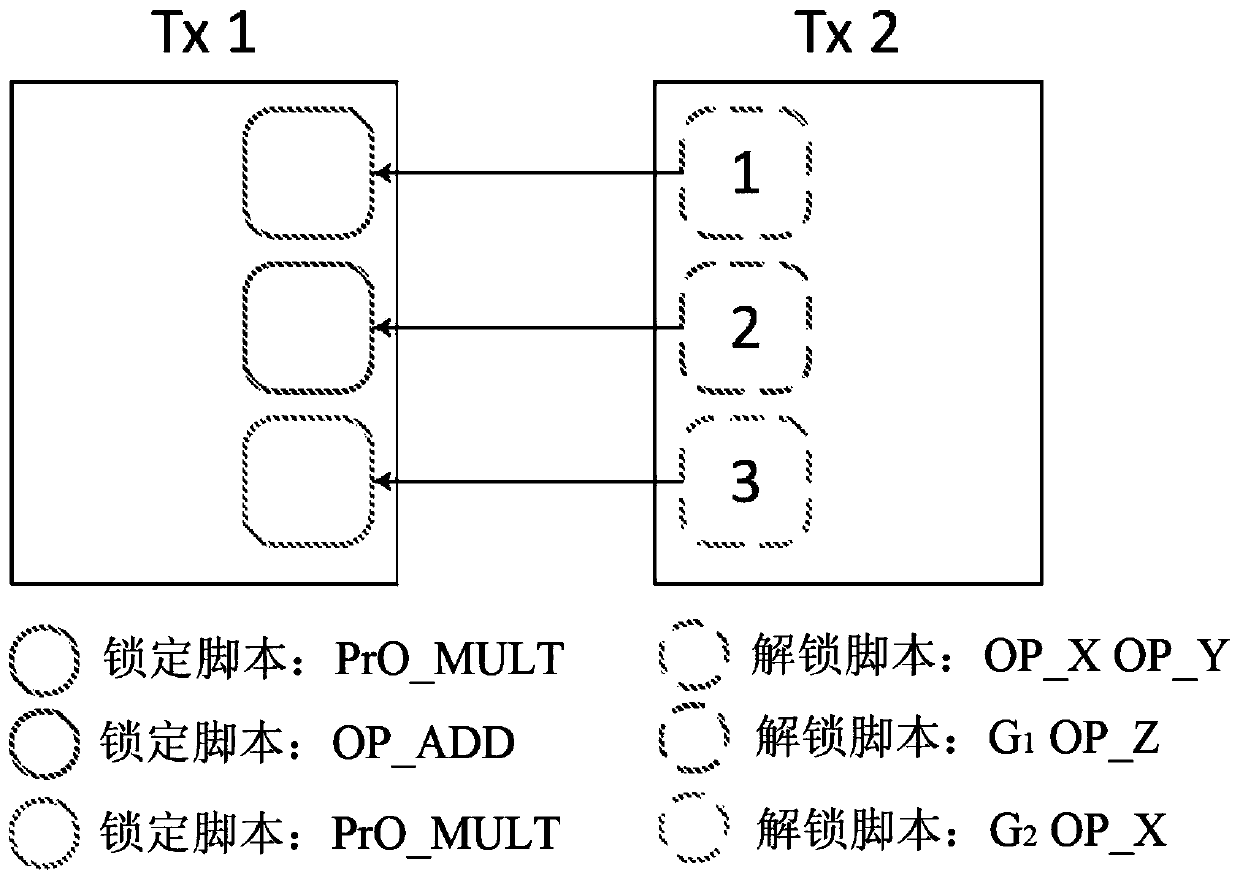
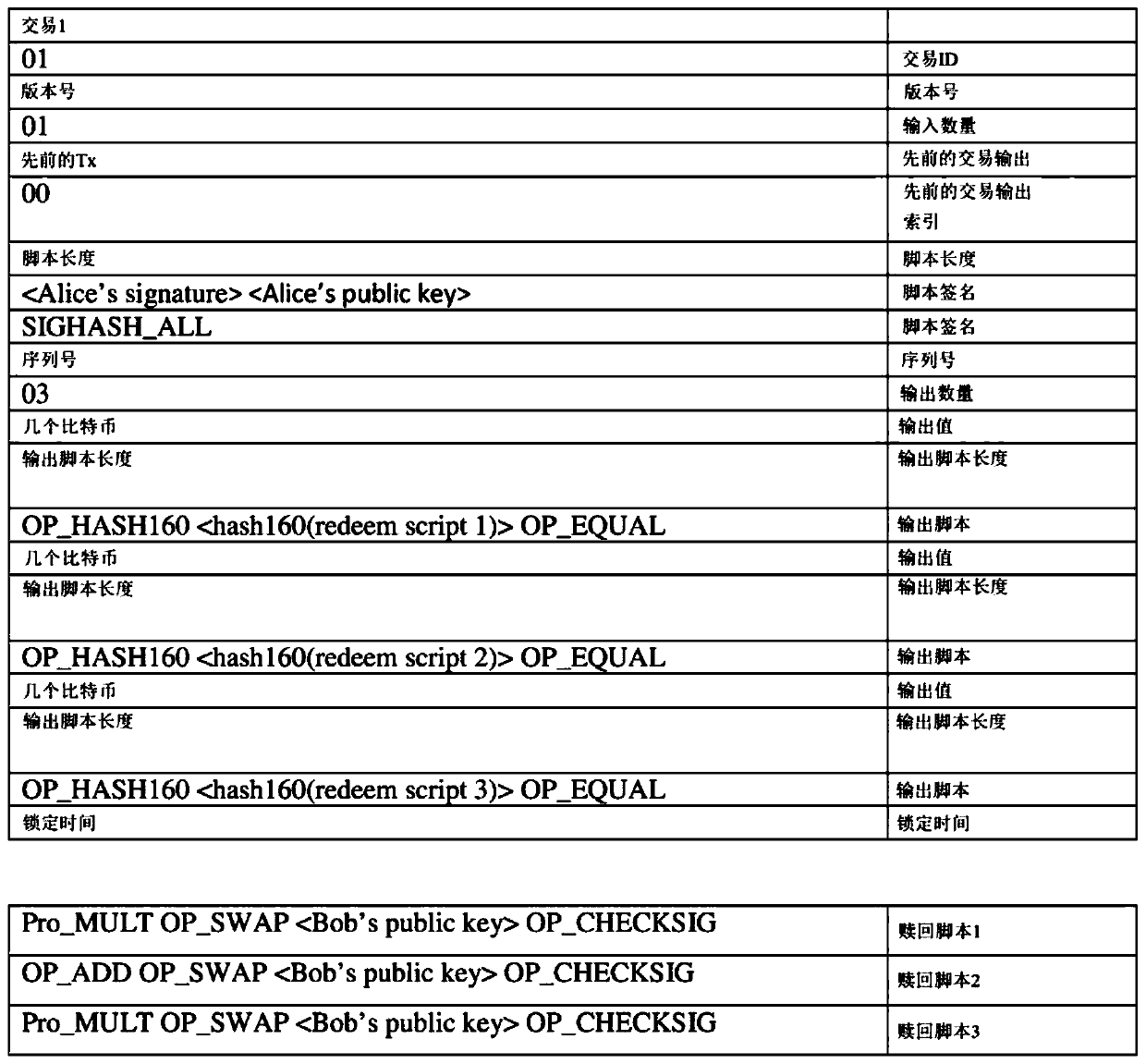
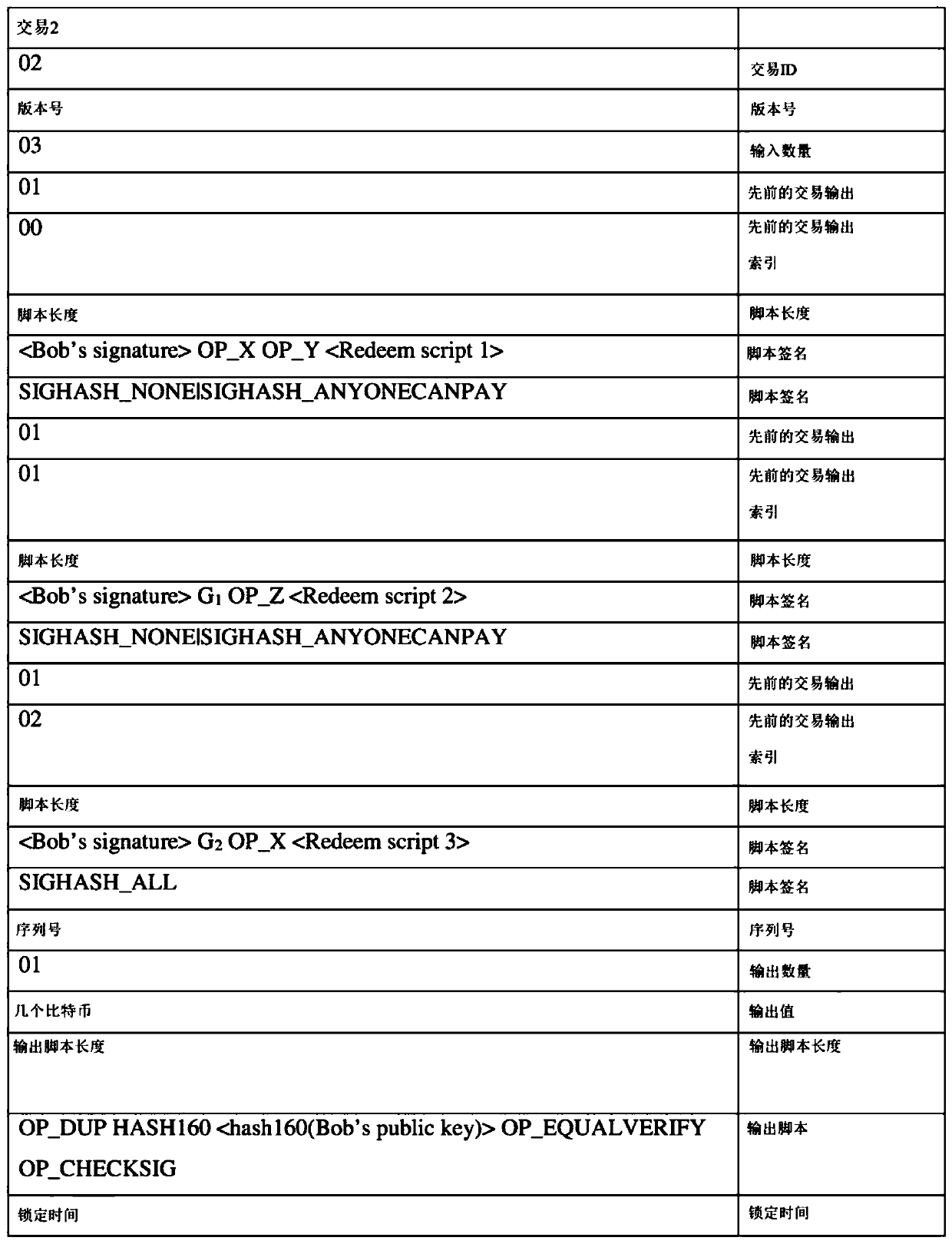
Computer-implemented systems and methods to enable complex functionality on a blockchain while preserving security-based restrictions on script size and opcode limits
ActiveCN110063041AHigh security mechanismEncryption apparatus with shift registers/memoriesUser identity/authority verificationBlockchainOpcode
The invention relates to blockchain technologies such as the Bitcoin blockchain. The invention uses a novel technique to decompose the functionality of a blockchain transaction script into several chunks or functional parts, and to use the output of a chunk as the input of the next chunk. Advantageously, this allows the blockchain to be used for ever complex tasks and computations while minimisingscript size, and also provides a novel architecture for the distributed execution of computational processes. The invention comprises a method of using a plurality of blockchain transactions to execute a computer-implemented task, the method comprising the steps: using an unlocking script (ULS1) in a blockchain transaction (Tx2) to present at least one data item to a locking script (LS1) of another transaction (Tx1) so as to provide a result on a stack; generating a further unlocking script (ULS2) which comprises the result provided on the stack; presenting the further unlocking script (ULS2)to a further locking script (LS2) such that the result from the stack is provided as input to the further locking script.
Owner:NCHAIN HLDG LTD
Method for storing cipher key
InactiveCN100531032CHigh security mechanismPrevent leakageSynchronising transmission/receiving encryption devicesData setOriginal data
The present invention provides a key storage method, including the steps of presetting the key data transformation algorithm; generating the original key data by the key generator, and simultaneously generating several key data related to the original key data by the random sequence generator random number; use the set key data transformation algorithm to perform transformation operations on the original key data and related random numbers to obtain the transformed key data corresponding to the original key data; and convert the transformed key data and Each random number related to the original key data is stored in independent storage media. The key storage method of the present invention reduces the complexity of key storage in the prior art key management process, and improves the security mechanism of key storage.
Owner:HUAWEI TECH CO LTD
Big data identification and intelligent analysis method and system for wireless sensor network based on energy-aware routing protocol
InactiveCN108848504AReduce energy consumptionHigh security mechanismUser identity/authority verificationNetwork topologiesLine sensorWireless mesh network
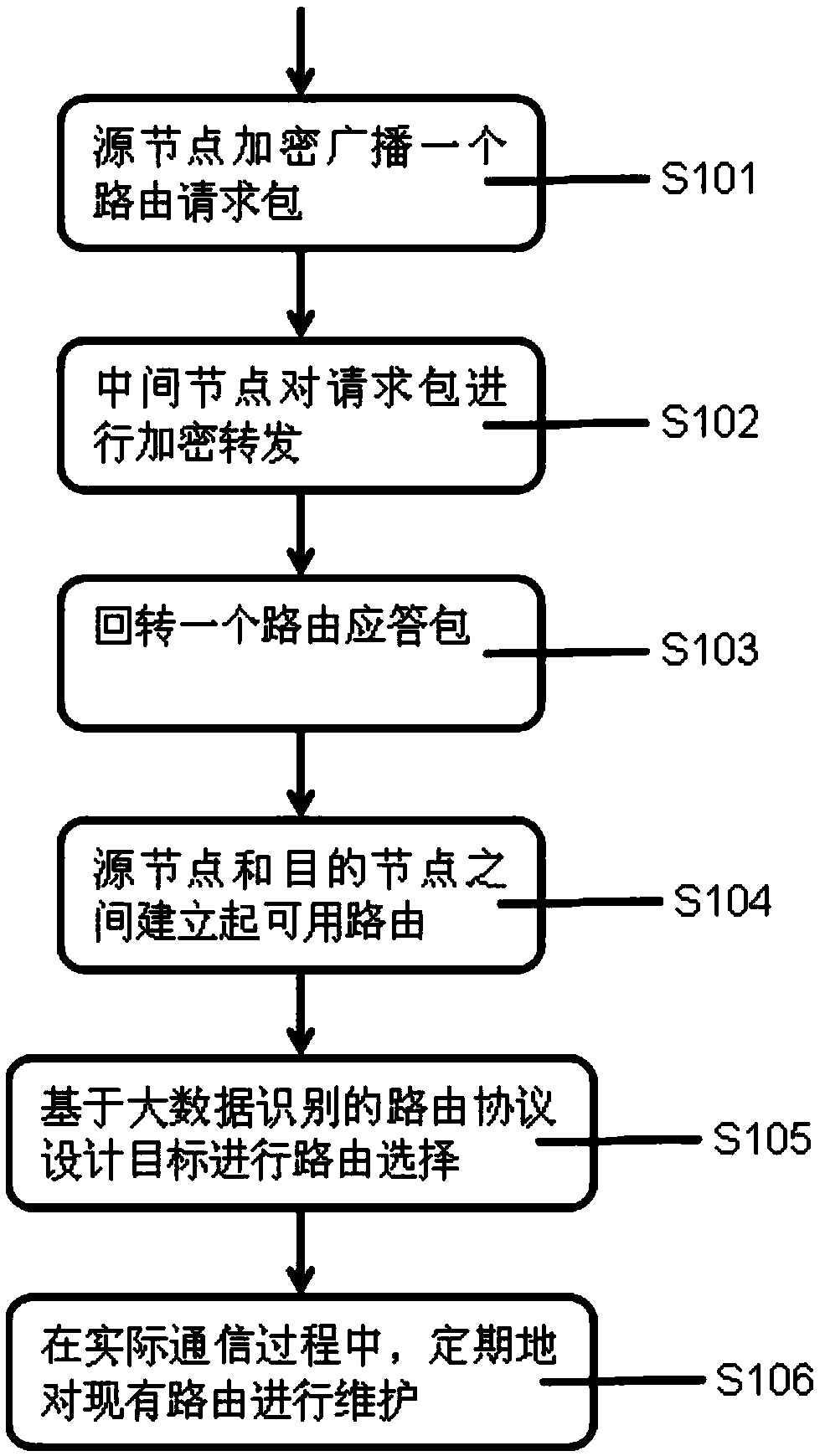
The invention belongs to the technical field of wireless sensor security mechanisms, and particularly relates to a big data identification and intelligent analysis method for a wireless sensor networkbased on an energy-aware routing protocol. The invention also provides a big data identification and intelligent analysis system for the wireless sensor network based on the energy-aware routing protocol at the same time. The method includes the followings steps that: a source node encrypts and broadcasts a route request packet, and an intermediate node encrypts and forwards the request packet and simultaneously revokes a route response packet until an available route is established between the source node and a destination node. The scheme of the invention solves the problem that the security is poor because some existing routing protocols in the wireless sensor network do not highly consider the security requirements in the prior art, and has the beneficial technical effects of high security performance, good security, high reliability, wide application range and low energy consumption.
Owner:SHENYANG NORMAL UNIV
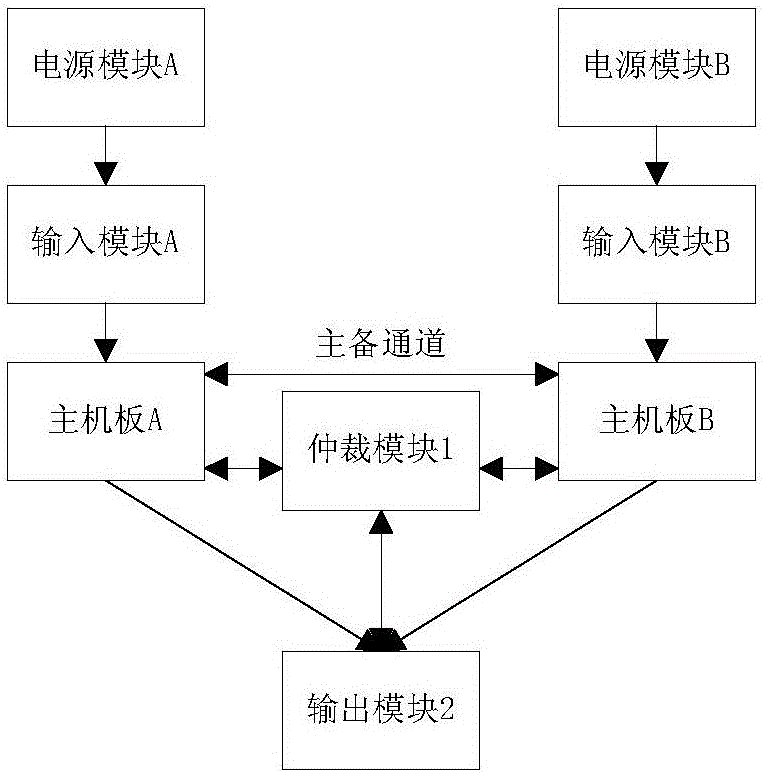
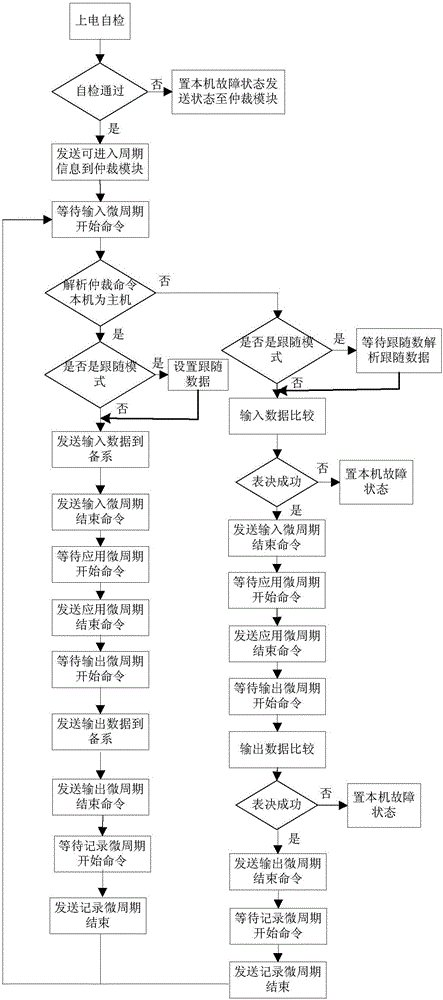
Redundant hot standby platform
InactiveCN106656437AImprove usabilityReduce maintenance difficultyError preventionData switching networksThird partyDowntime
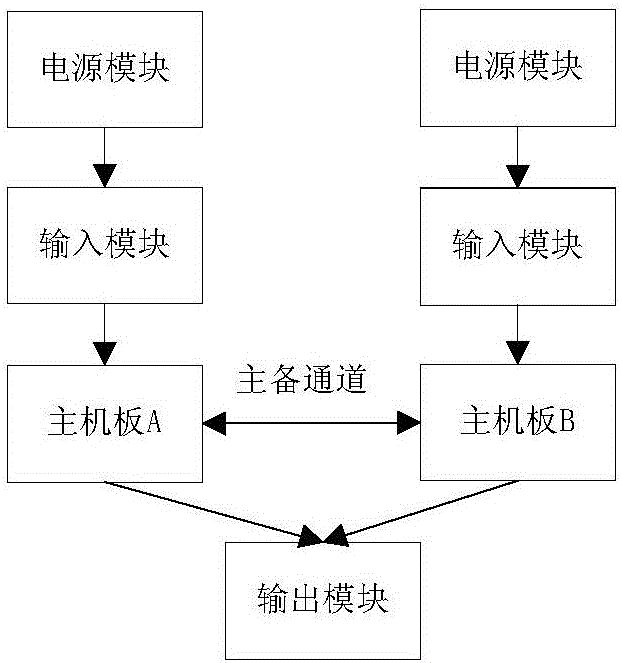
The invention discloses a redundant hot standby platform comprising a master system, a backup system and an arbitration module, wherein the arbitration module performs bidirectional communication with a motherboard of the master system, the motherboard of the backup system and an output module of the redundant hot standby platform, the platform imports a third party synchronous management functional module to add an input and output data comparison function, a period synchronization function, a following function, an automatic recovery function after downtime for the redundant hot standby platform, and the availability of the redundant hot standby platform is effectively enhanced on the premise of ensuring the security.
Owner:TIANJIN TRAFFIC CONTROL TECH CO LTD
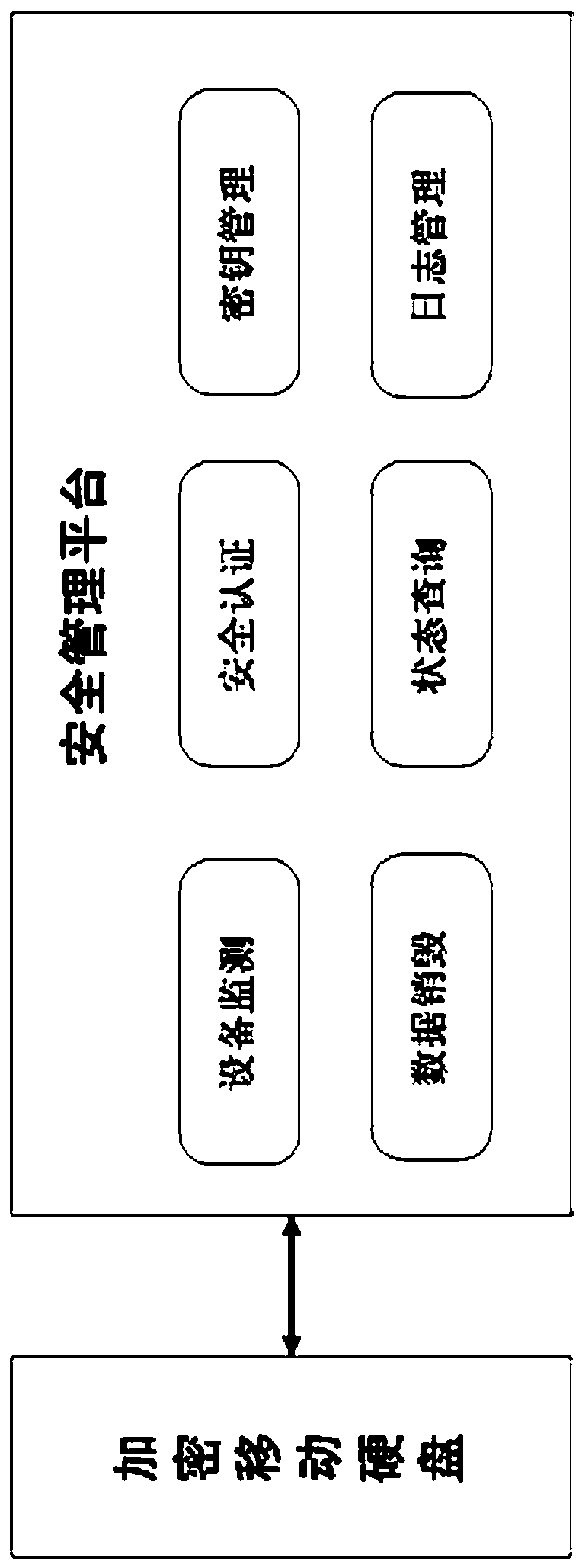
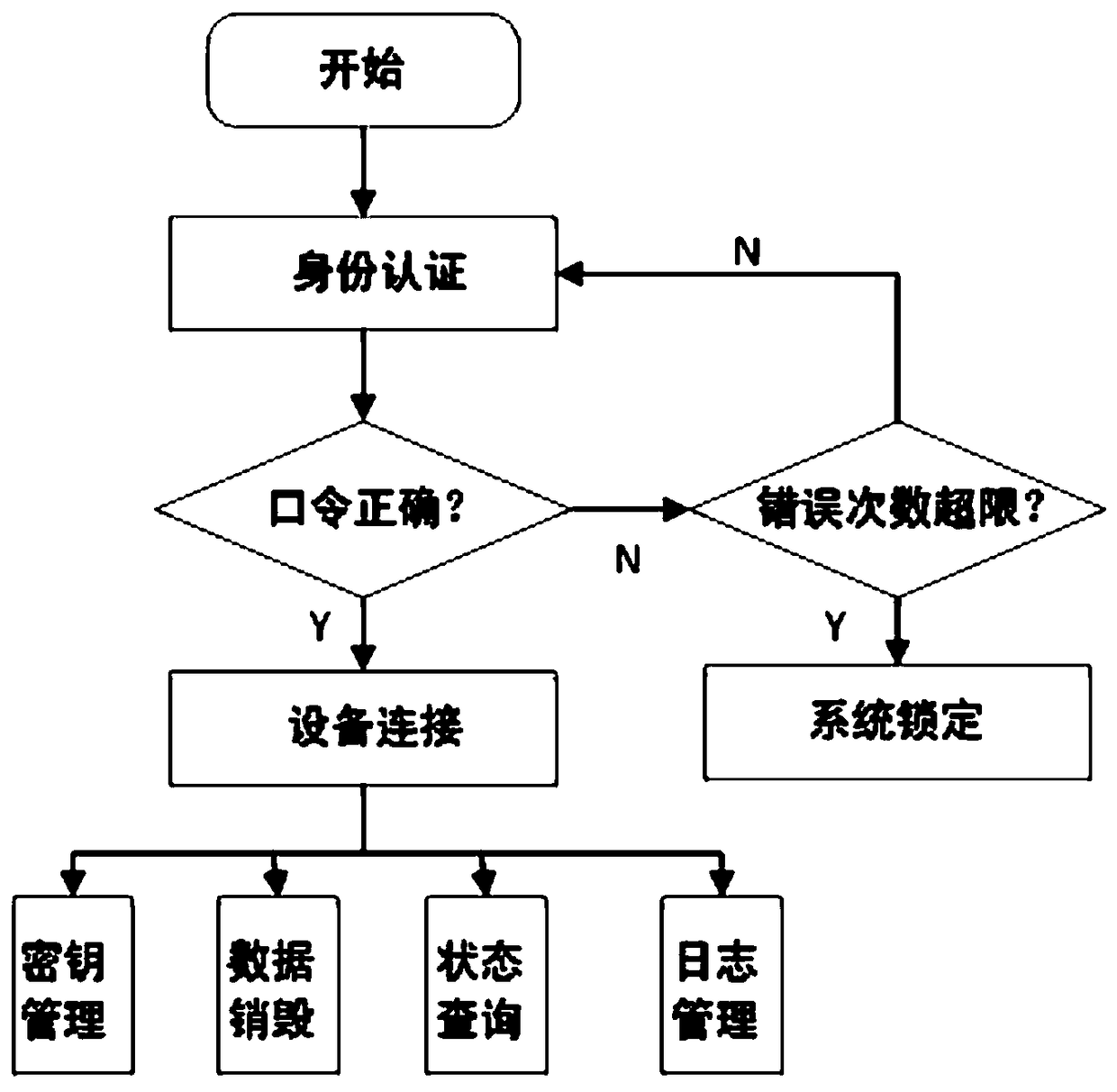
Special security management platform and method for encrypted mobile hard disk
InactiveCN108763891AGuaranteed legalityEnsure safetyError preventionUser identity/authority verificationLog managementComputer module
The invention discloses a special security management platform and method for an encrypted mobile hard disk. The security management platform is composed of an equipment monitoring module, a securityauthentication module, a key management module, a data destruction module, a state query module and a log management module, wherein a data frame communication format self-defined on an upper layer isadopted between the security management platform and the encrypted mobile hard disk, and whether a response is made to requested data is determined by verifying the legality of a message header in the data; and a CRC function is achieved during data transmission between the security management platform and the encrypted mobile hard disk, so that the correctness of transmitted data is checked, andthe security of data transmission is enhanced. Through the special security management platform and method, the legality of a user can be guaranteed to the maximum extent; the data destruction function of the encrypted mobile hard disk can be supported to guarantee the security of the hard disk; the correctness and security of a key are guaranteed; a backup function of equipment logs can be achieved; and the data destruction function is supported, so that a security mechanism of a system is enhanced.
Owner:SHANDONG CHAOYUE DATA CONTROL ELECTRONICS CO LTD
Team or group operation system
The invention discloses a team or group operation system, which comprises four function modules: a team or group module, a work region module, a leader module and a manager module, and the four module structures divided by the team or group operation system disclosed by the invention provide a middle layer integrated framework for meeting application requirements on low cost, high usability, high reliability and expandability. A unified development platform is provided, the cost and the complexity for developing the multilayer application are reduced by using J2EE, simultaneously, strong support is provided for the existing application program integration, the Enterprise Java Beans is completely supported, good guide support packing and deployment application are realized, the directory support is added, the safety mechanism is enhanced, and the performance is improved.
Owner:NANYANG POWER SUPPLY COMPANY OF STATE GRID HENAN ELECTRIC POWER
Anti-falling flap wheel and production process thereof
PendingCN114406898AReduce hidden dangersImprove anti-falling functionGrinding wheel securing apparatusGrinding devicesImpellerManufacturing engineering
The invention discloses an anti-falling shutter wheel and a production process thereof, and relates to the technical field of shutter wheels, the anti-falling shutter wheel comprises a main body, a protective device is arranged on the outer wall of the main body, a chassis is arranged on one side of the main body, an anti-falling device penetrates through the chassis, a rotating shaft is arranged on one side of the chassis, and a rotating shaft is arranged on the other side of the rotating shaft; an auxiliary locking device is arranged on one side of the rotating shaft, and a mounting groove is formed in one side of the auxiliary locking device. Under the combined action of a bearing, a bearing hole, a limiting cylinder, a tray and a fixed connecting rod, the flap wheel can be prevented from falling off from the device due to overlarge centrifugal force during rotation, the flap wheel can be firmly fixed to the device, hidden dangers are reduced, and the service life of the flap wheel is prolonged. Under the combined action of the connecting shaft, the taper bearing, the locking nut, the sheath, the repairable material and the four-side positioning bolts, one side of the flap wheel can be firmly locked, so that internal parts of the flap wheel are not easy to loosen, and the anti-falling function of the flap wheel is further improved.
Owner:丹阳市励高研磨材料有限公司
Preservative film guiding and covering device for food packaging
PendingCN114261568AAvoid deformationHigh security mechanismWrappingPackaging protectionTemperature controlEngineering
The invention discloses a food packaging preservative film guiding and covering device, and relates to the technical field of preservative films, the food packaging preservative film guiding and covering device comprises a main body, a cutting plate is arranged at the upper end of the main body, a temperature control mechanism is arranged at the rear end of the cutting plate, an anti-abrasion mechanism is arranged at the lower end of the main body, and a material cleaning mechanism is arranged on one side of the main body. And a storage barrel is arranged at the lower end of the material cleaning mechanism. Under the combined action of a heat conduction pipe, a valve, a condensation pipe, a heater and a constant-temperature block, the situation that covering of a preservative film is blocked due to the influence of the external temperature in the covering process can be avoided, the temperature in the device can be controlled within a safe range, the preservative film is not prone to deformation, and the service life of the preservative film is prolonged. Under the combined action of the storage box, the screen, the feeding pipe, the pressure stabilizing roller and the blast pipe, dust deposited on the surface of the preservative film can be effectively recycled and removed, so that the preservative film does not bring the dust into food, and meanwhile, covering blockage caused by dust accumulation can be prevented.
Owner:德清新顶包装有限公司
Cloud platform access method and device
ActiveCN103747076BHigh security mechanismAvoid malicious accessDigital data protectionTransmissionAccess methodThe Internet
The invention discloses a cloud platform access method and device, wherein the cloud platform access method includes: in the case of requesting to access the cloud platform, generating an access identifier according to the user's request parameters; sending the access identifier to the cloud platform, according to The pre-stored user information corresponding to each user verifies the access ID; when the access ID passes the verification, the user is allowed to access the cloud platform. The present invention generates an access ID according to the user's request parameters, and verifies the access ID through pre-stored user information to ensure that only when the access ID passes the verification, can the user be allowed to access the cloud platform, thus effectively improving cloud access. The security mechanism of the platform prevents malicious access to the cloud platform by illegal users and reduces the waste of resources on the cloud platform.
Owner:DAWNING CLOUD COMPUTING TECH CO LTD
Thermoplastic elastomer material and preparation method thereof
PendingCN114311387AHigh ignition pointIncrease elasticitySynthetic resin layered productsGrain treatmentsMetal fiberElastomer
The invention discloses a thermoplastic elastomer material and a preparation method thereof, and relates to the technical field of thermoplastic elastomers, the thermoplastic elastomer material comprises a main body, the outer surface of the upper end of the main body is provided with a flame retardant coating, the lower end of the main body is provided with an anti-static mechanism, and the lower end of the anti-static mechanism is provided with a protection device. Under the combined action of the colloid, the liquid flame retardant, the solid flame retardant, the accelerant and the styrene coating, the thermoplastic elastomer can have good flame retardance and elasticity, and the liquid flame retardant and the solid flame retardant are added to the surface of the elastomer material, so that the thermoplastic elastomer is not prone to spontaneous combustion; under the combined action of the carbon black coating, the chopped conductive fiber coating, the conductive mica powder coating, the thin film and the polyurethane coating, the antistatic capacity of the elastomer material can be improved, the arranged chopped conductive fiber coating contains carbon fibers and metal fibers, and the carbon fibers and the metal fibers have very low body resistance and are generally presented in a network line shape, so that the antistatic performance of the elastomer material is improved. Therefore, the current is not easy to pass through the elastomer material.
Owner:无锡朴业橡塑有限公司
Application processing method, device, terminal and storage medium based on combined public key
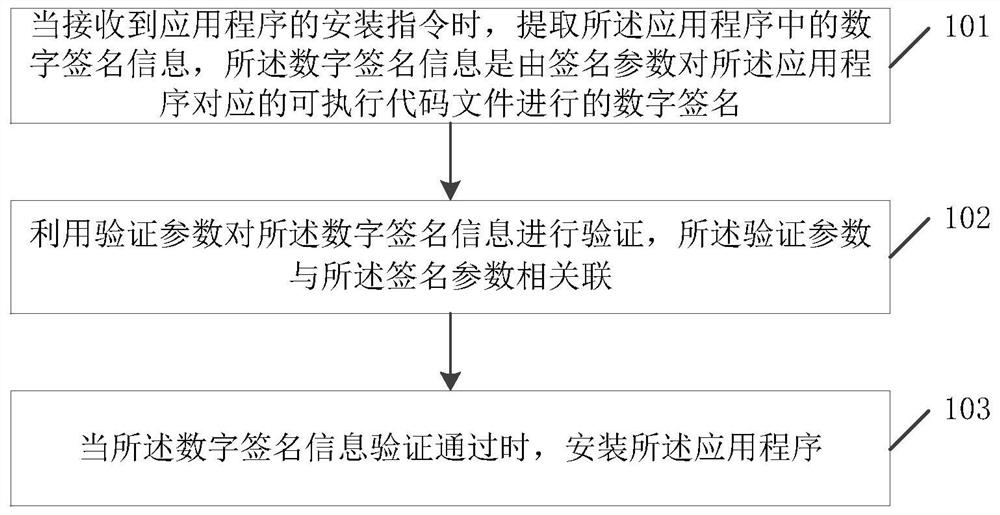
ActiveCN109977662BEnsure safetyHigh security mechanismComputer security arrangementsDigital signatureSoftware engineering
The invention relates to the technical field of information security, discloses an application program processing method and device, a terminal and a storage medium, and solves the problem that the security legality of an application program cannot be ensured when the application program is installed in an intelligent terminal in the prior art. The method comprises: when an installation instruction of an application program is received, digital signature information in the application program is extracted, and the digital signature information is a digital signature carried out on an executable code file corresponding to the application program through signature parameters; verifying the digital signature information by utilizing a verification parameter, wherein the verification parameteris associated with the signature parameter; and when the digital signature information passes the verification, installing the application program. The embodiment of the invention is suitable for theinstallation process of the application program.
Owner:JIN SHANG BO CHUANG BEIJING SCI & TECH CO LTD
A method for automatic mixing control of endocrinology medical solution
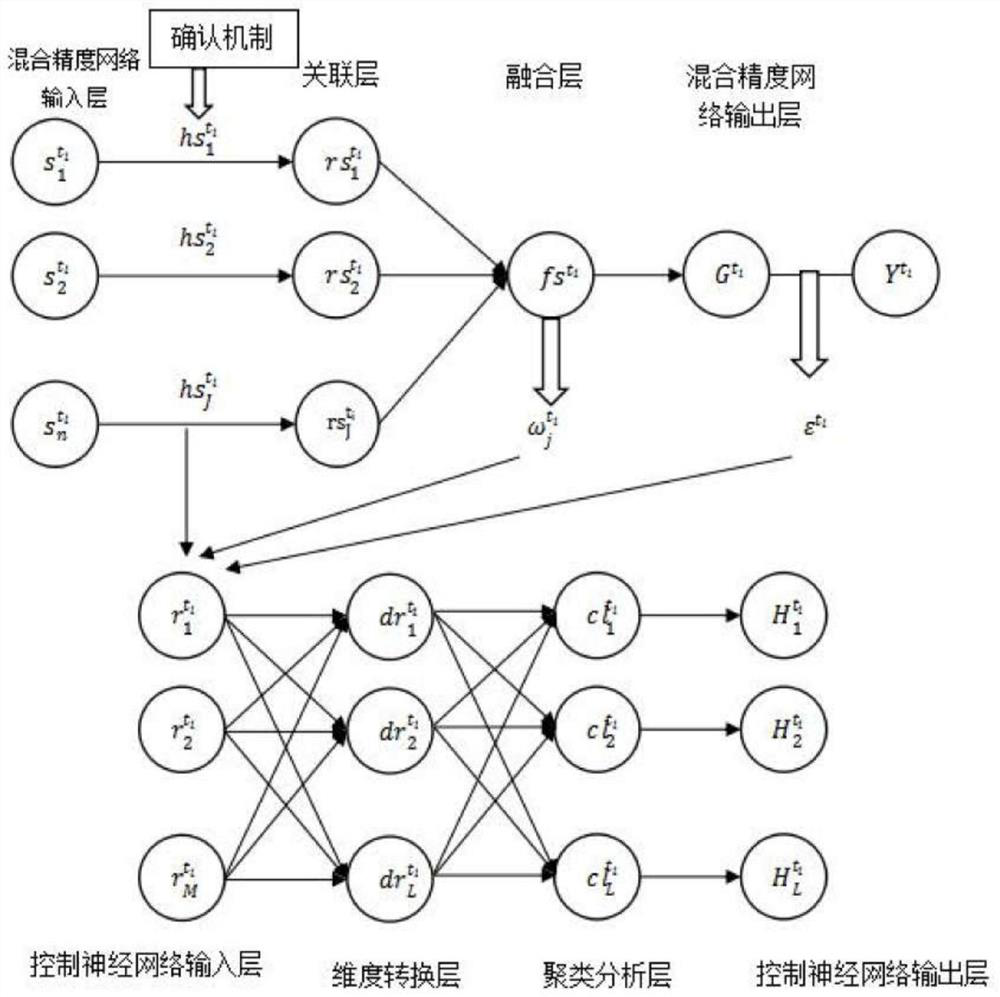
ActiveCN112908446BPrecisely control the ratioWell mixedDrug and medicationsCharacter and pattern recognitionEndocrinology departmentNetwork output
The invention discloses an automatic mixing control method for endocrinology medicinal liquid, which comprises the following steps: A. After the medicinal liquid starts to mix, the mixed medicinal liquid is collected in each cycle, the information of the mixed medicinal liquid is obtained by analysis, and the mixed precision neural network is constructed Model, through deep learning to obtain the mixing precision of the mixed medicine; B. Judging according to the mixed precision series output by the mixed precision neural network, by adjusting and controlling the proportion of each element in the mixed medicine output by the neural network, and further calculating different medicines Increased time is required to automatically control endocrinology liquid mixing. The invention solves the problems of low mixing precision and unreliable control of the traditional Chinese medicinal liquid, can accurately control the ratio of various medicinal liquids, mixes evenly, can realize continuous and stable production, improves efficiency, is safe and reliable, and is easy to maintain.
Owner:张磊
High-dimension secure arithmetic coding method
InactiveCN107819573AFast compression and encryption processHigh Security MechanismKey distribution for secure communicationDigital video signal modificationInformation compressionLinear system
The invention provides a high-dimension secure arithmetic coding method. Through adoption of the method, compression and encryption can be conducted rapidly, and a highly secure mechanism is providedwhile the original information compression rate is kept. The original arithmetic coding method depends on one-dimension line segment shrinkage process. In the method, the coding process is expanded toan N-dimension space. A non-linear system password algorithm is introduced in a higher dimension, so that arithmetic coding maintains high compression rate, further, an extra information secure mechanism is offered. The method has the characteristics of good encryption effect, high efficiency and high compressibility, and can be applied to real-time information transmission.
Owner:NORTHEASTERN UNIV
System for measuring and managing electric energy used for agricultural irrigation and drainage
InactiveCN101777214BSolve private electricity salesImprove accuracyApparatus for hiring articlesCoded identity card or credit card actuationEngineeringCard reader
The invention relates to a system for measuring and managing electric energy used for agricultural irrigation and drainage, which comprises a prepaid card electricity meter, a meter reader, a card reader, a provincially unified key system, an electricity selling system and a non-contact intelligent CPU card serving as a storage medium. The same type of equipment adopts a unified technical specification and communication interface to ensure inter-equipment communication and realize the function of the system. A PSAM module with a storage key is arranged in the unified prepaid card electricity meter of an electricity selling terminal; and keys in the PSAM module and the intelligent CPU card are used for performing security authentication to realize the high-level management of recharging and avoid the possibility of selling the electricity privately. The unified key system strengthens the security system of the whole system and improves the technology level of preventing electricity stealing. The unified electricity selling system and WEB data representation and data mining technology improve the accuracy, the consistency and the generality of data and provide a reliable data basis for leaders from provincial and municipal top management departments and the unit.
Owner:STATE GRID HEBEI ELECTRIC POWER CO LTD
Movable anti-seismic power transmission tower
PendingCN114412266AAvoid shakingImprove seismic performanceTowersProtective buildings/sheltersTransmission towerShock resistance
The invention discloses a movable anti-seismic power transmission tower, and relates to the technical field of power transmission towers, the movable anti-seismic power transmission tower comprises a main body, connecting bolts are arranged on the two sides of the main body, an anti-seismic device is arranged below the main body, deformation correction devices are arranged on the two sides of the anti-seismic device, and a contraction device is arranged below the anti-seismic device. An elastic piece is arranged at the lower end of the contraction device, and supporting frames are arranged on the two sides of the elastic piece. Under the combined action of a buffer frame, a sliding block, a balancing weight, a spring column and a placement block, the power transmission tower can be prevented from shaking due to external force, the shock resistance of the power transmission tower can be improved, the power transmission tower is not prone to toppling, and the service life of the power transmission tower is prolonged. Under the combined action of the correcting plate, the correcting part, the fixing plate, the air cylinder, the push rod, the connecting arm, the movable pressing plate, the plug pin, the comparison vertical rod and the supporting assembly, whether the power transmission tower inclines or deforms or not can be verified at any time, the power transmission tower can be corrected at the first time, and therefore the stability of the power transmission tower is improved.
Owner:邱文清
Smart Lock Control System
ActiveCN104484925BImprove securityAchieve traceabilityNon-mechanical controlsIndividual entry/exit registersTime rangeControl system
Owner:江苏今越控股集团有限公司
A method and device for protecting user information
ActiveCN103905394BImprove effectivenessHigh security mechanismTransmissionComputer terminalAuthentication
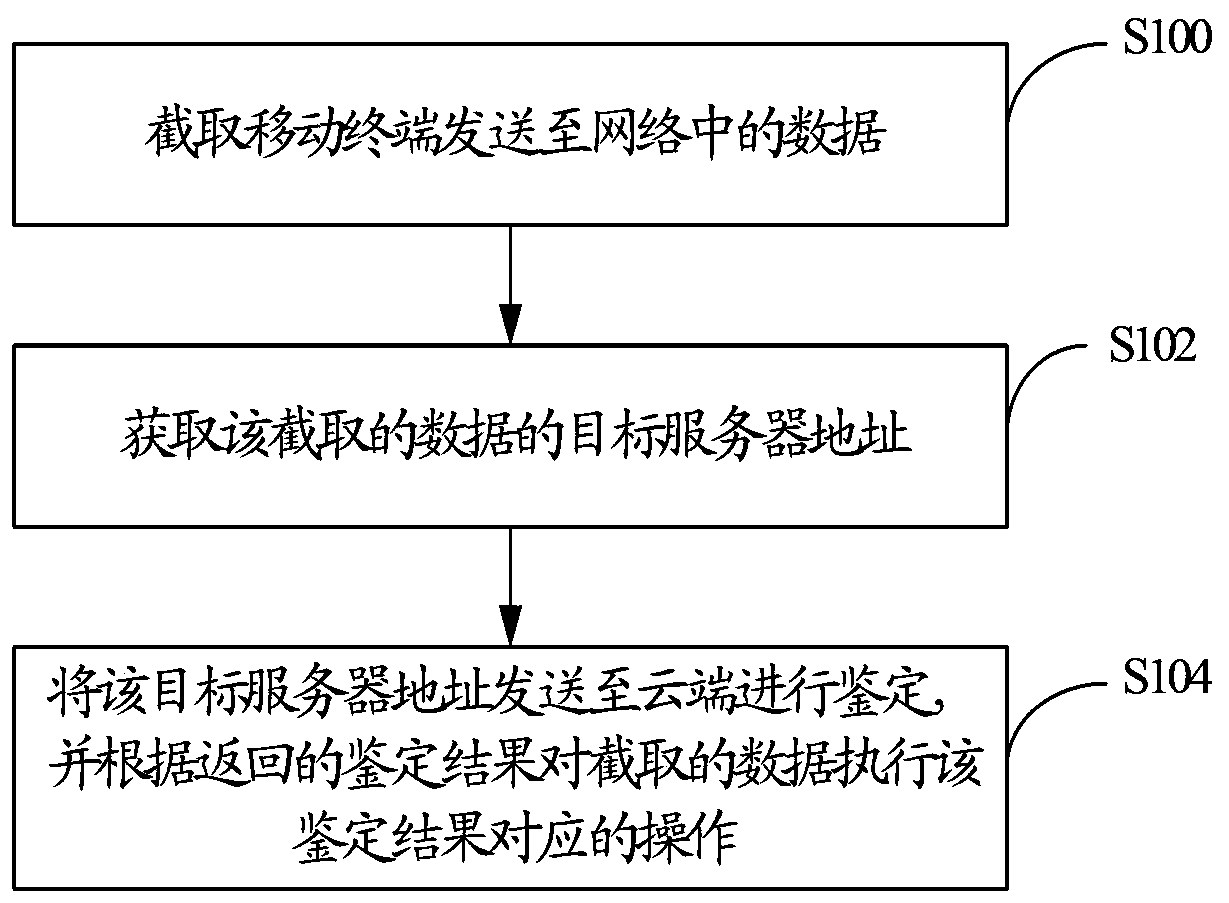
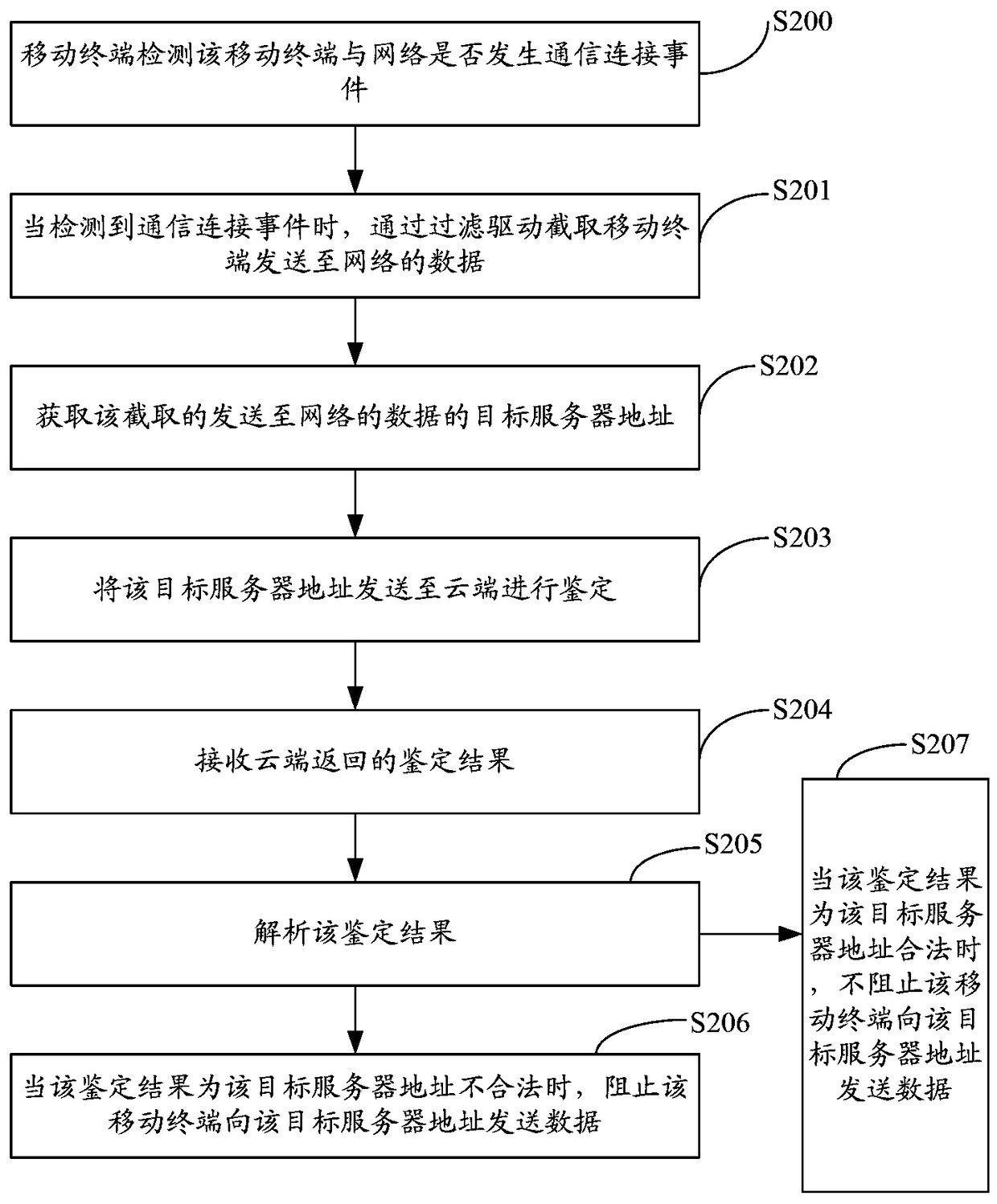
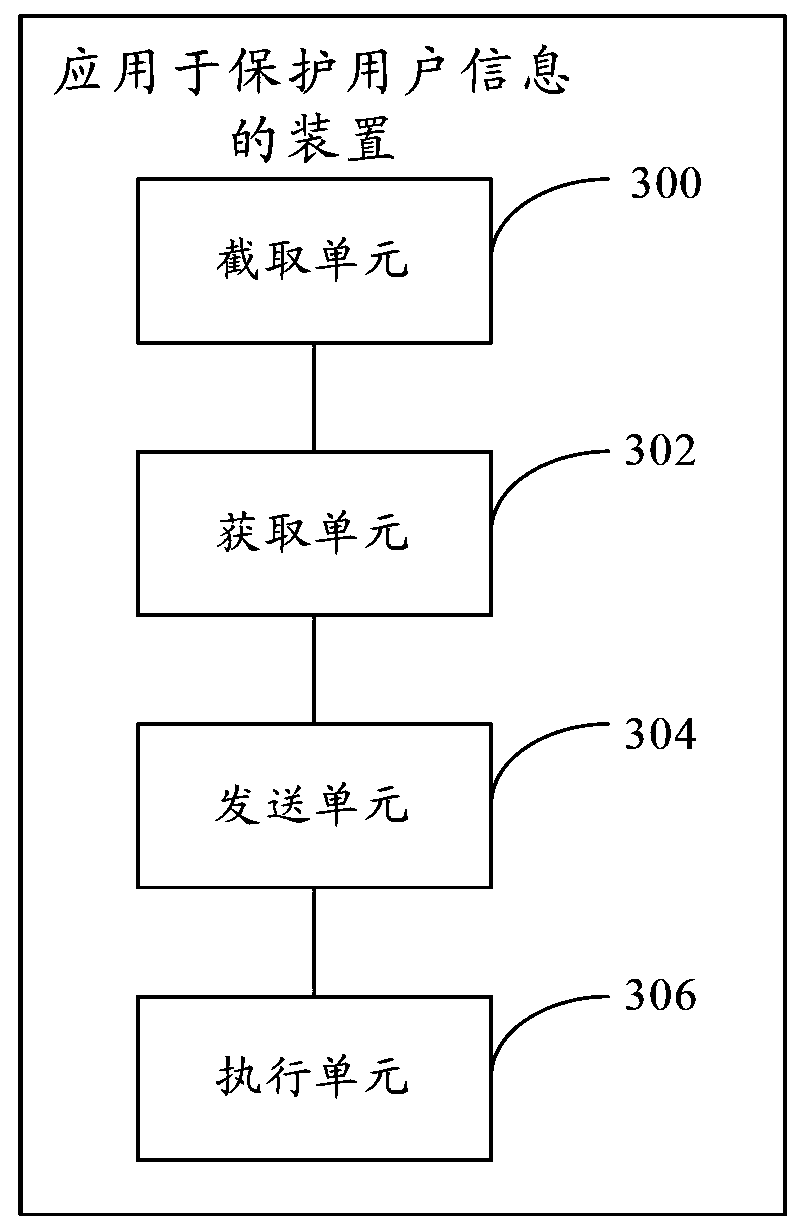
The embodiment of the invention discloses a method for protecting user information. The method includes: capturing data which is sent by a mobile terminal to a network; obtaining a target server address of the captured data; sending the target server address to a cloud end for authentication and executing operations corresponding to an authentication result on the captured data according to the returned authentication result so that effectiveness in preventing account stealing by an account stealing Trojan program is improved.
Owner:TENCENT TECH (SHENZHEN) CO LTD
Pre-sharing-based secure data transmission method for electric load management system
ActiveCN102111273BHigh security mechanismImprove securityKey distribution for secure communicationError preventionTransmission protocolPower application
The invention provides a pre-sharing-based secure data transmission method for an electric load management system, which is significant to a power load management system to resist various security threats in wireless communication environments and open Internet environments. The confidentiality, integrity and availability of transmission data of the system can be ensured through perfection of the transmission protocol identity authentication and the integrity checking mechanism of the power load management system, and encryption of important control instructions. The method has significant meaning and demonstration effects to the formulation of secure data transmission schemes for other power application systems.
Owner:CHINA ELECTRIC POWER RES INST +1
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com