Method for storing cipher key
A key storage and key data technology, which is applied in the field of information security, can solve problems such as increasing the complexity of key management, achieve the effects of reducing complexity, improving security mechanisms, and preventing leakage and theft
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
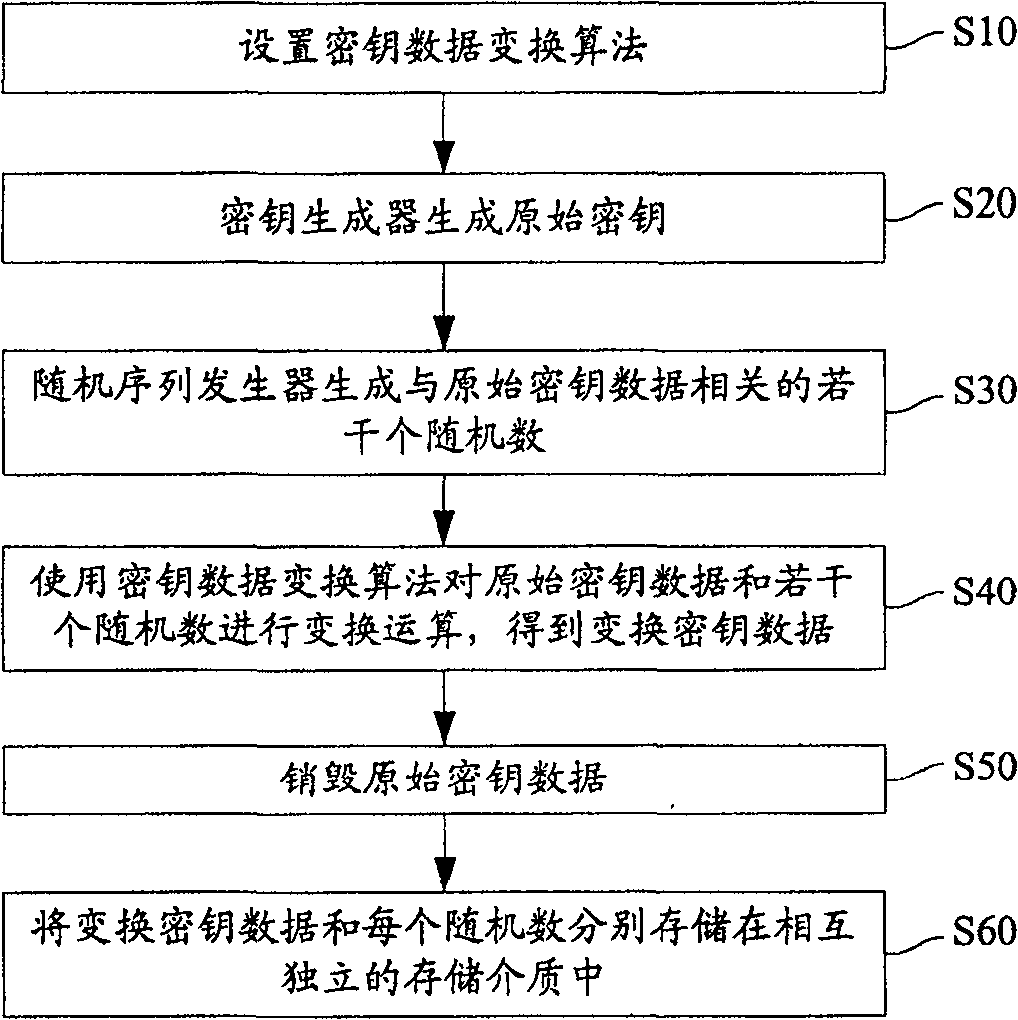
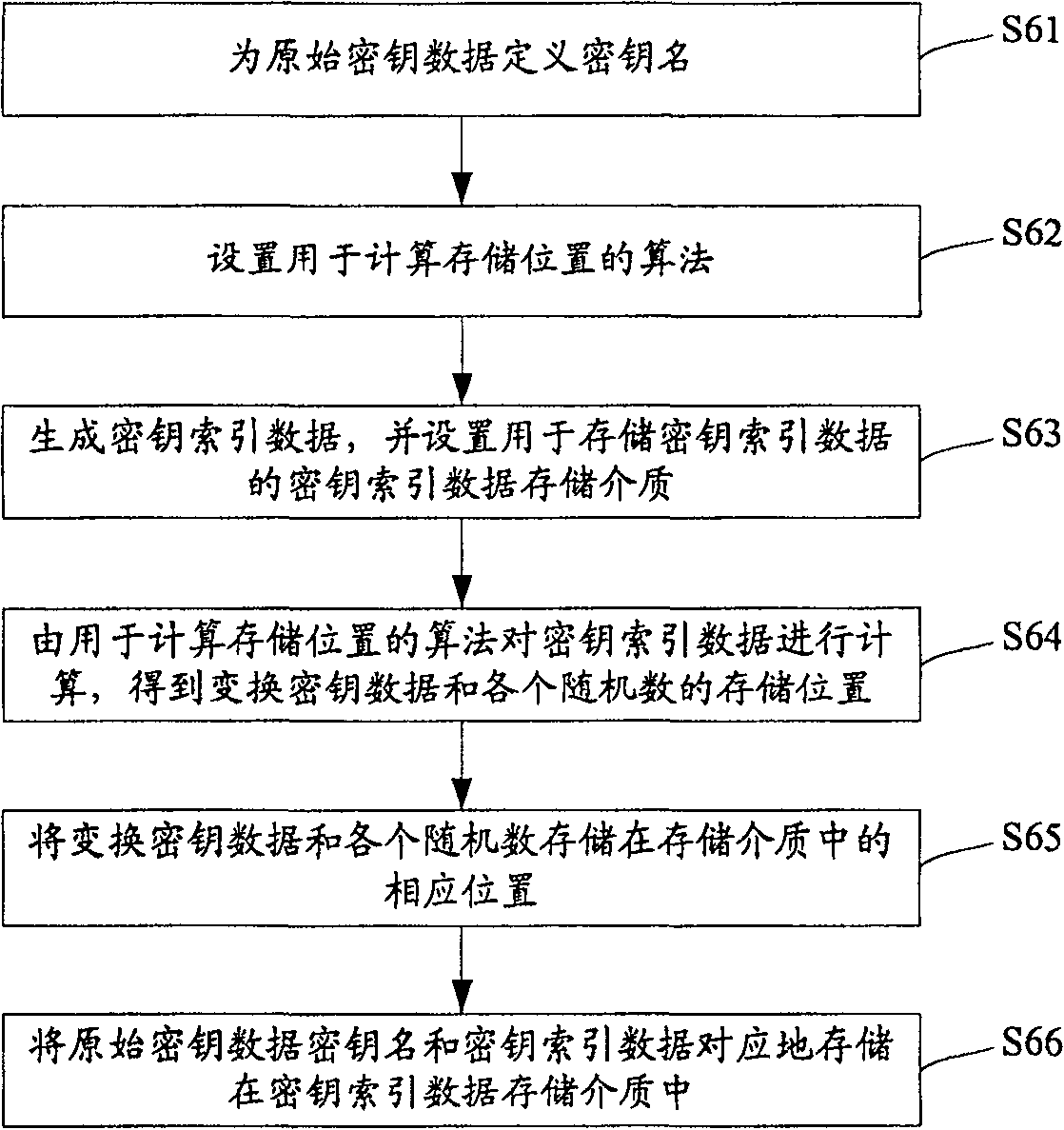
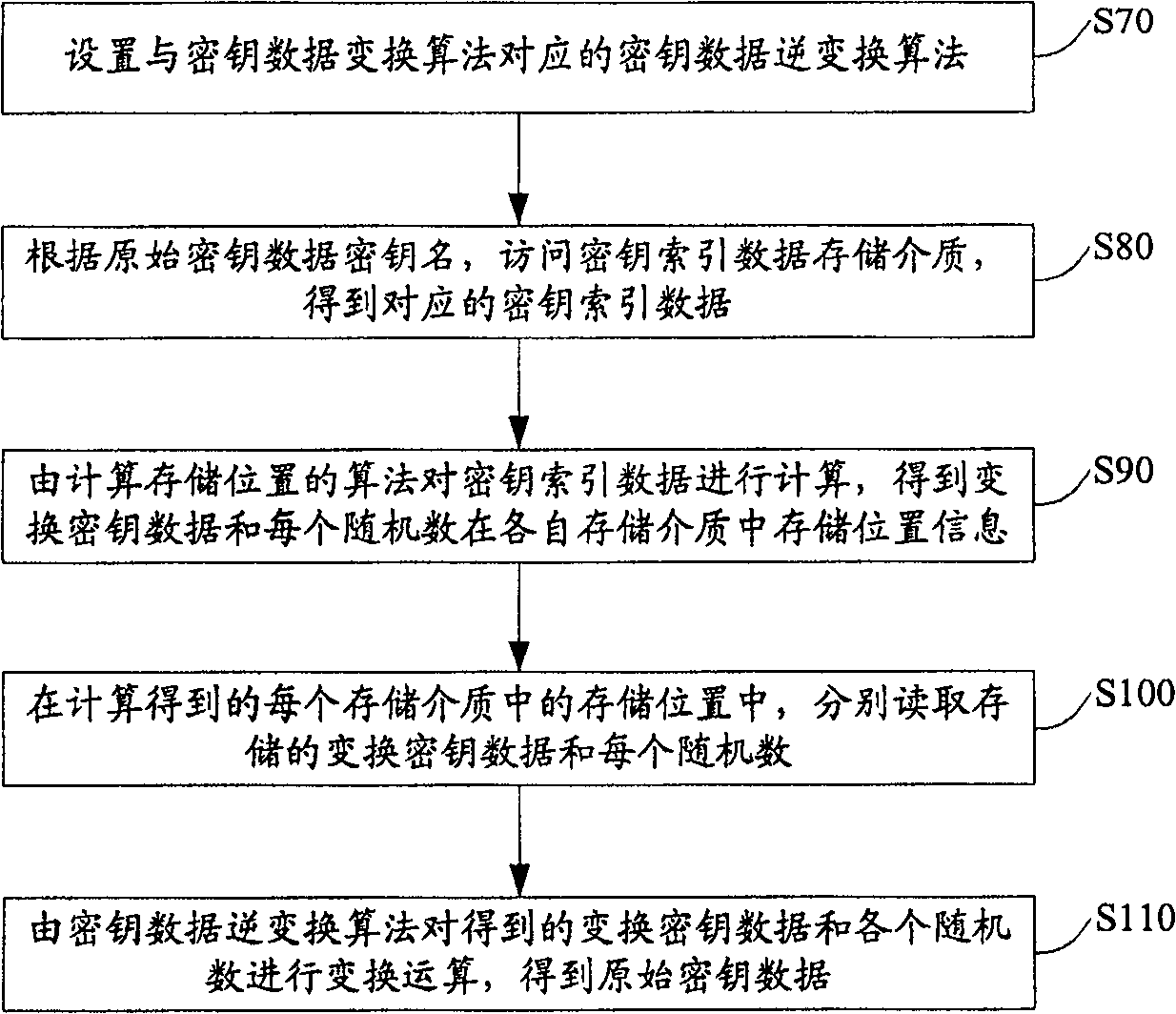
[0047] The overall design idea of the key storage method of the present invention is: through simple transformation operation on the original key data, the distributed storage of key material information is realized, thereby improving the security management mechanism of the original key data.
[0048] refer to figure 1 , which is a brief process flowchart of the key storage method of the present invention, wherein the main steps of the key storage process of the present invention include:
[0049] Step S10, pre-setting the key data transformation algorithm; this key data transformation algorithm can be selected according to the specific situation, and a different algorithm can be selected for the transformation operation, such as an XOR operation algorithm can be selected, or a commonly used transformation algorithm based on a symmetric cryptosystem can be used .
[0050] Step S20, the original key data is generated by the key generator, where the original key data is the ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com