Pre-sharing-based secure data transmission method for electric load management system
A technology for managing systems and power loads, applied in the field of information security, to achieve strong security, enhance security mechanisms, and reduce monitoring risks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
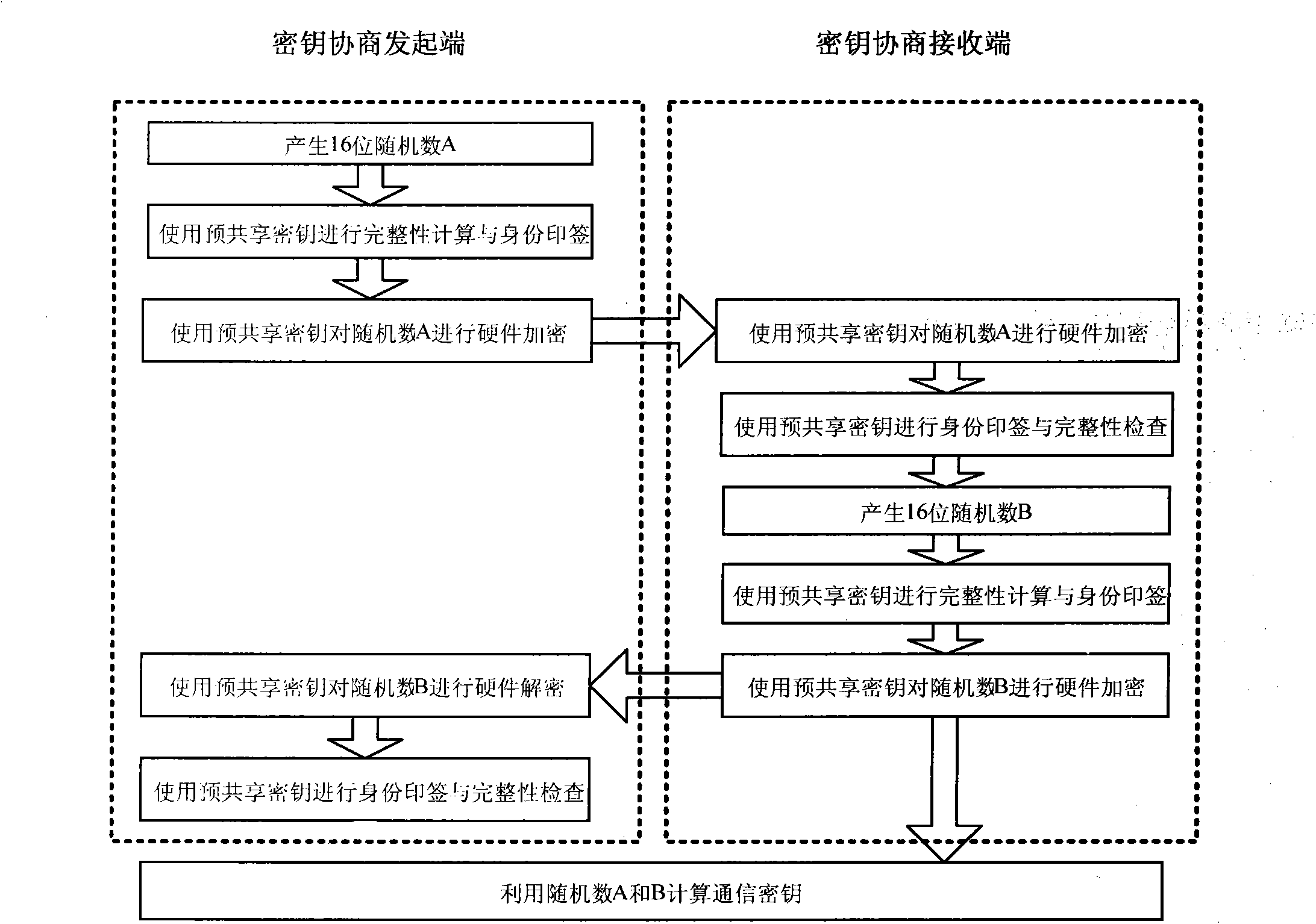
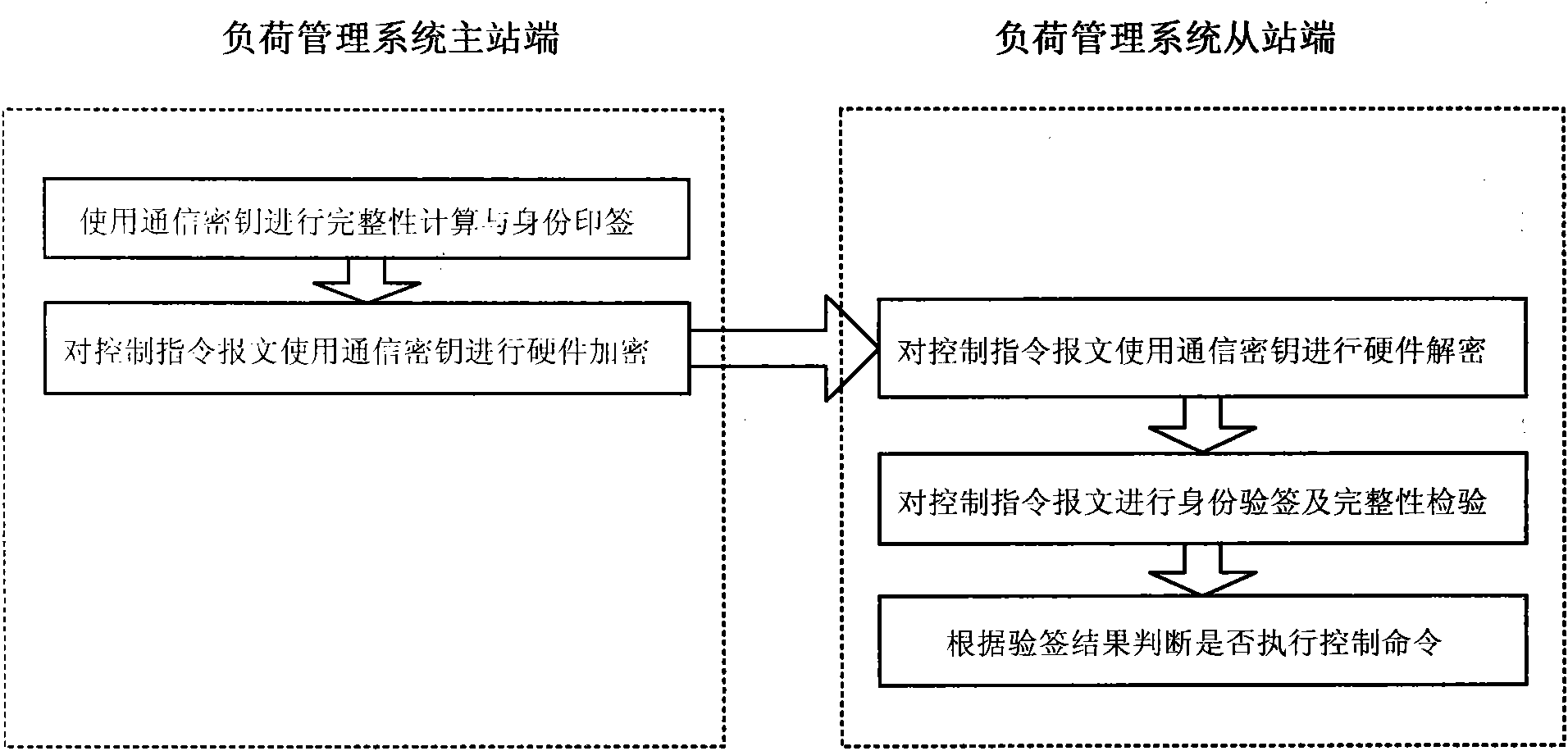
[0024] The present invention improves the identity authentication and integrity verification mechanism in the data transmission process of the master-slave station of the power load management system through the definition of the PW field of the link user data (application layer) in the data frame, and ensures that the sending and receiving parties of the power load management system Identity legitimacy and message integrity, and on this basis, a pre-shared power load management system master-slave station communication key negotiation method is proposed, which realizes the packet encryption of important control commands, and improves the key The security of message transmission in a complex network environment.
[0025] 1. Identity authentication and integrity verification mechanism
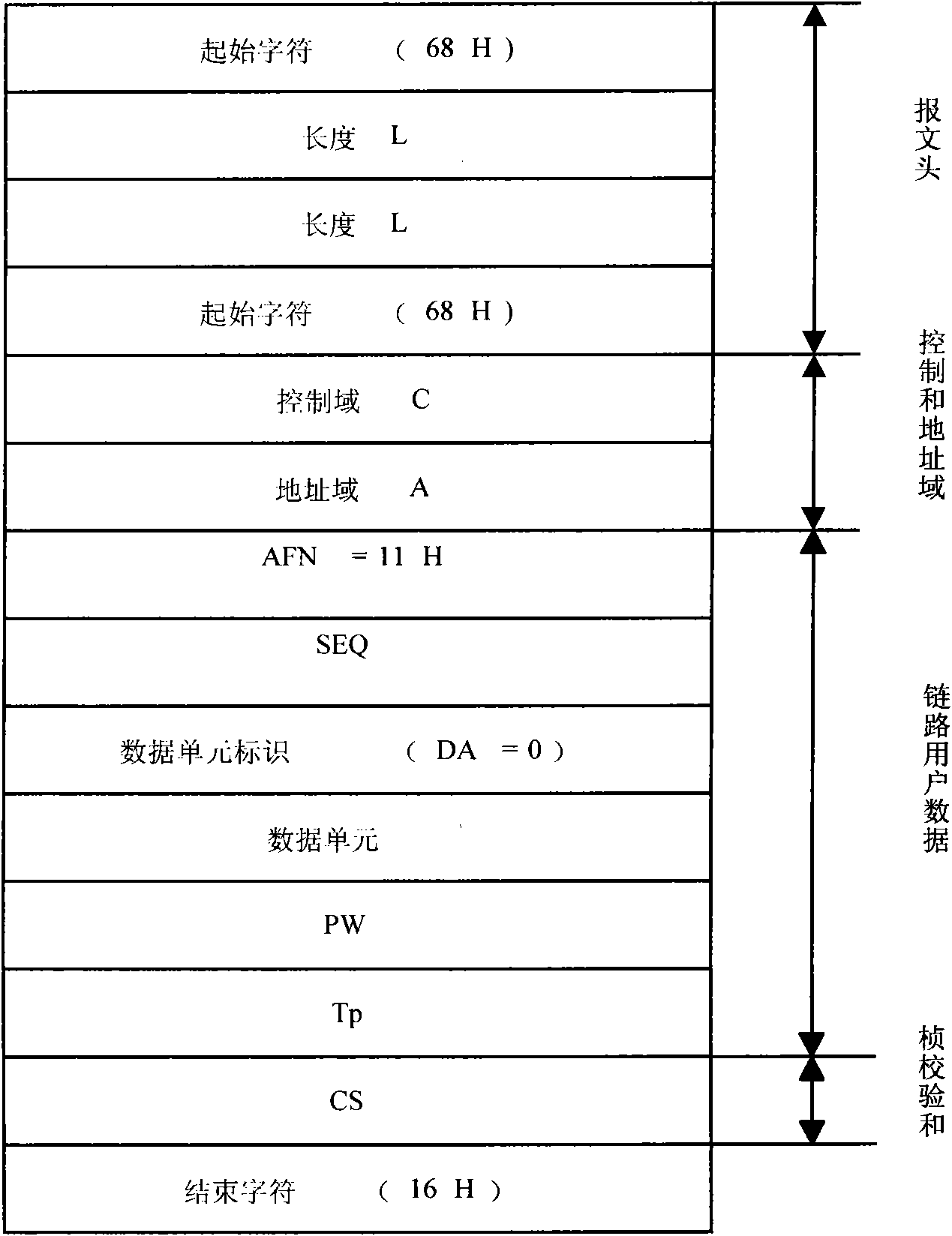
[0026] attached figure 1 It is the data frame format of the extended power load management system. The data frame of the original power load management system consists of a fixed-length messag...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com