Method and device for destroying terminal data
A data and terminal technology, applied in the field of electronic communication, can solve the problems of illegal user recovery, incomplete deletion, data leakage, etc., and achieve the effect of preventing illegal recovery, convenient and quick destruction, and avoiding data leakage
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
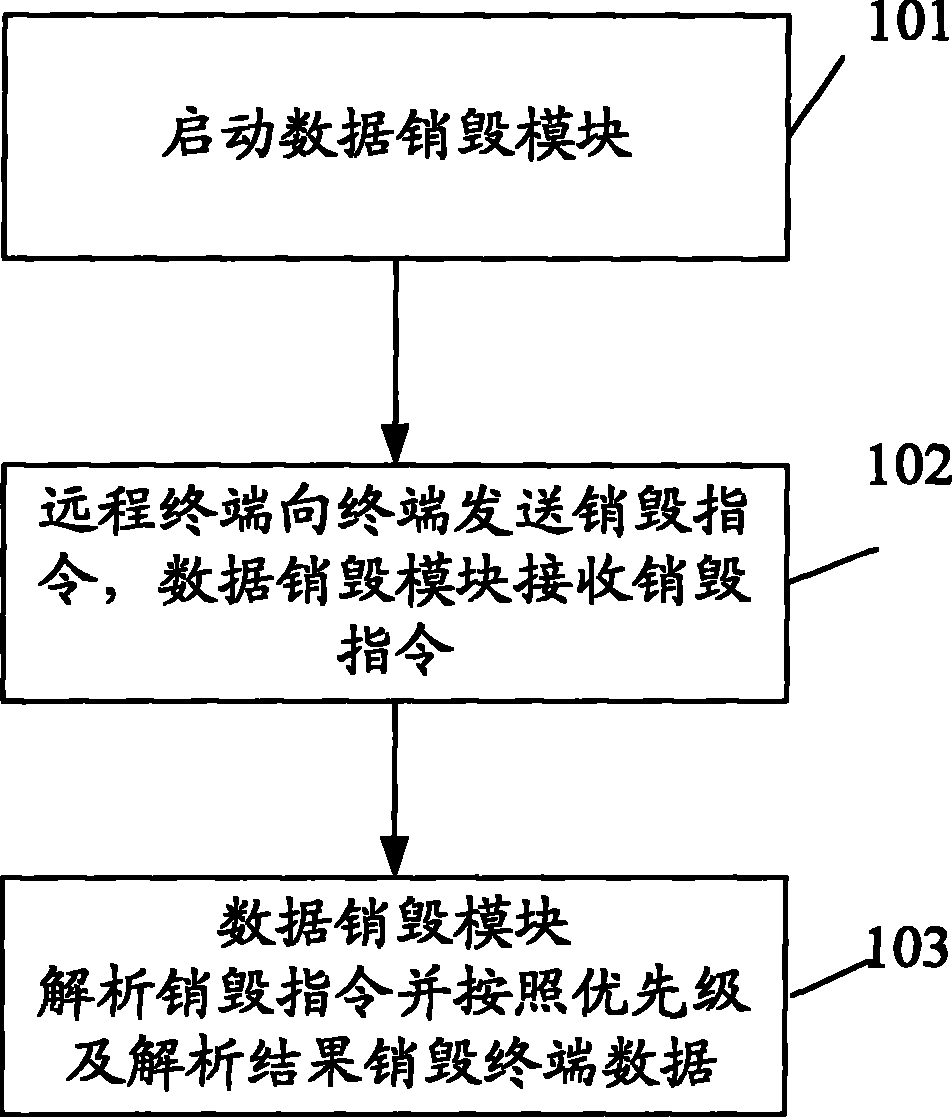
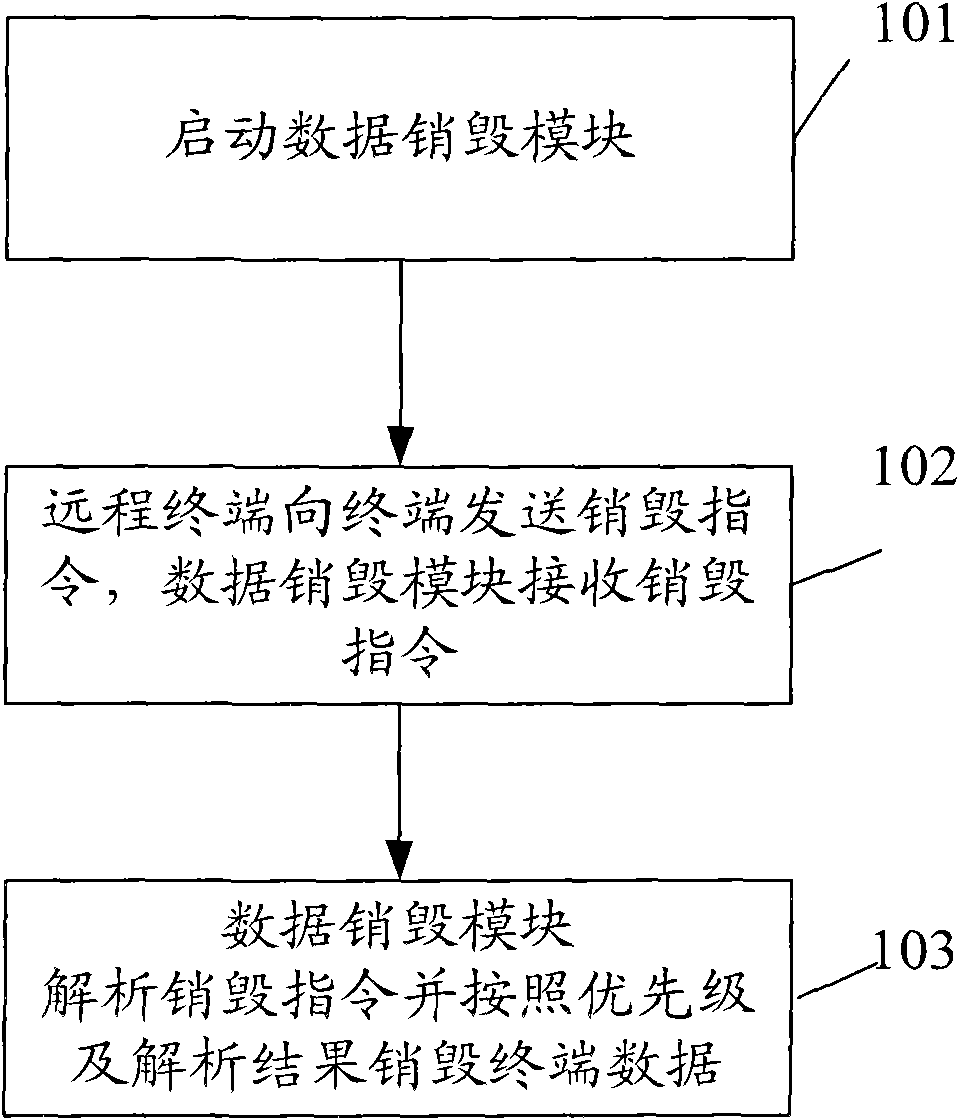
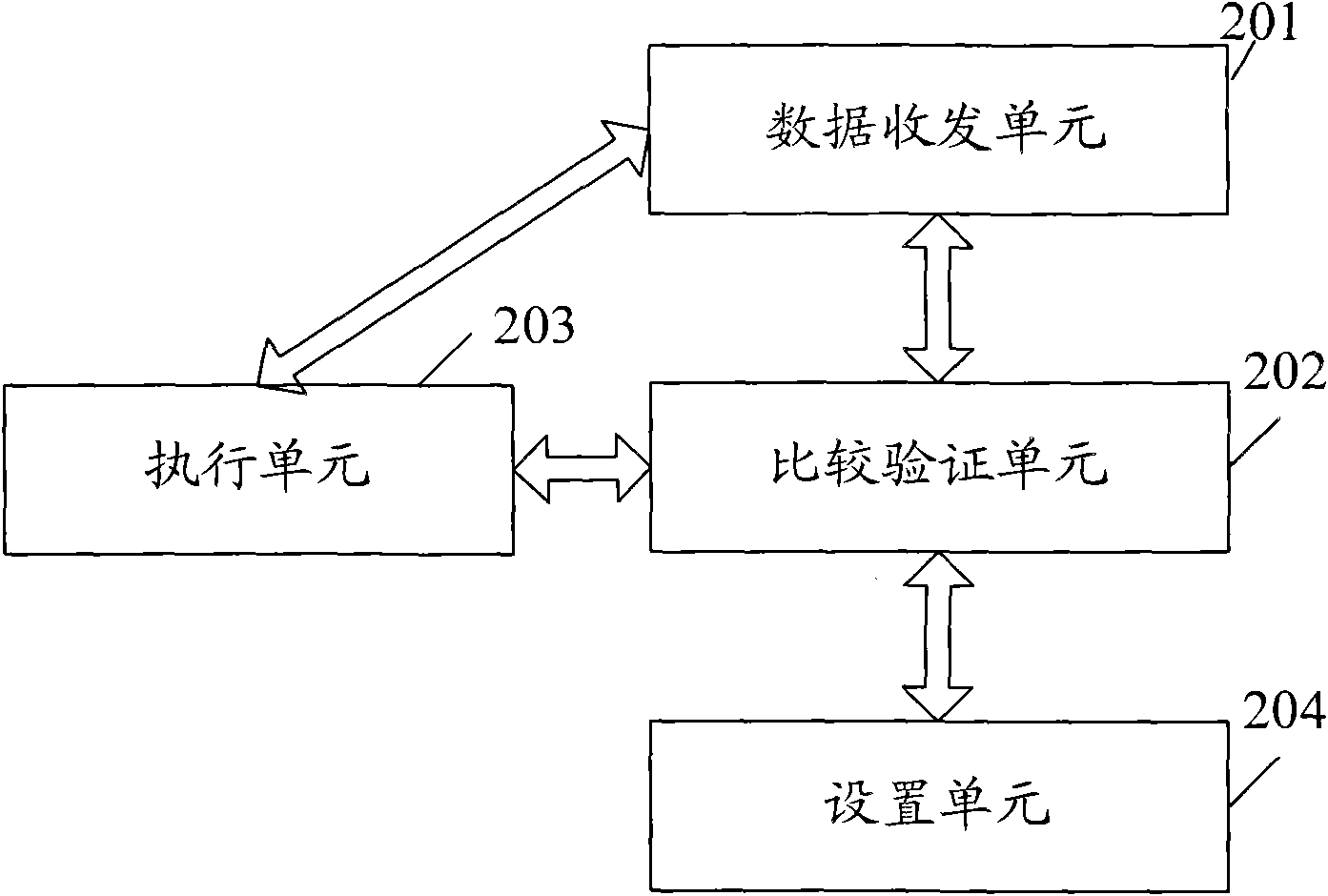
[0023] The basic idea of the present invention is: the remote terminal sends a destruction instruction to the terminal, the data destruction module of the terminal analyzes the destruction instruction and determines the priority of data destruction, and destroys the data according to the priority and the analysis result;
[0024] Wherein, the remote terminal is any terminal that can send a destruction command, and the terminal is a terminal that needs to destroy data and is equipped with a data destruction module.
[0025] The present invention is described in detail below in conjunction with accompanying drawing and specific embodiment, as shown in Figure 1, the specific steps that the present invention realizes destroying terminal data are as follows:
[0026] Step 101, the terminal starts the data destruction module;
[0027] The terminal starts the data destroying module, the starting is automatically running in the background when the terminal is turned on, and the data...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com