Secret data transmission protection method based on isomorphism of asymmetrical encryption algorithm
An asymmetric encryption, secret data technology, applied in transmission systems, public keys for secure communications, user identity/authority verification, etc. effect of overhead
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
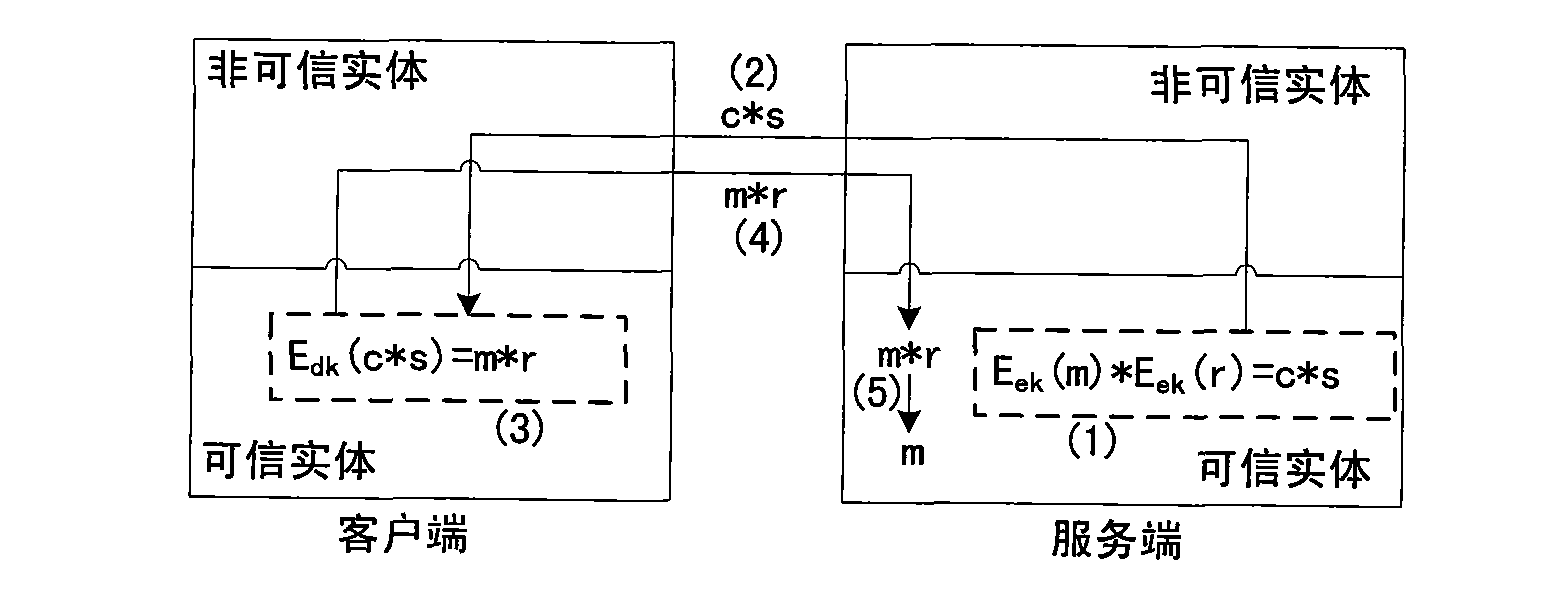
[0024] Such as figure 1 As shown, the server holds the secret data ciphertext c=E ek (m), want to get its plaintext m. Since the private key for decryption is on the client side, decryption must be done on the client side. The server-side trusted entity first selects a random number r, camouflages the secret data ciphertext c (step (1) formula), and sends the result to the client-side trusted entity through the open network (step (2)), the client can The trusted entity decrypts the data (step (3)), and sends the result back to the server-side trusted entity through the open network (step (4)), and the server-side trusted entity restores the secret data plaintext m( Step (5)).
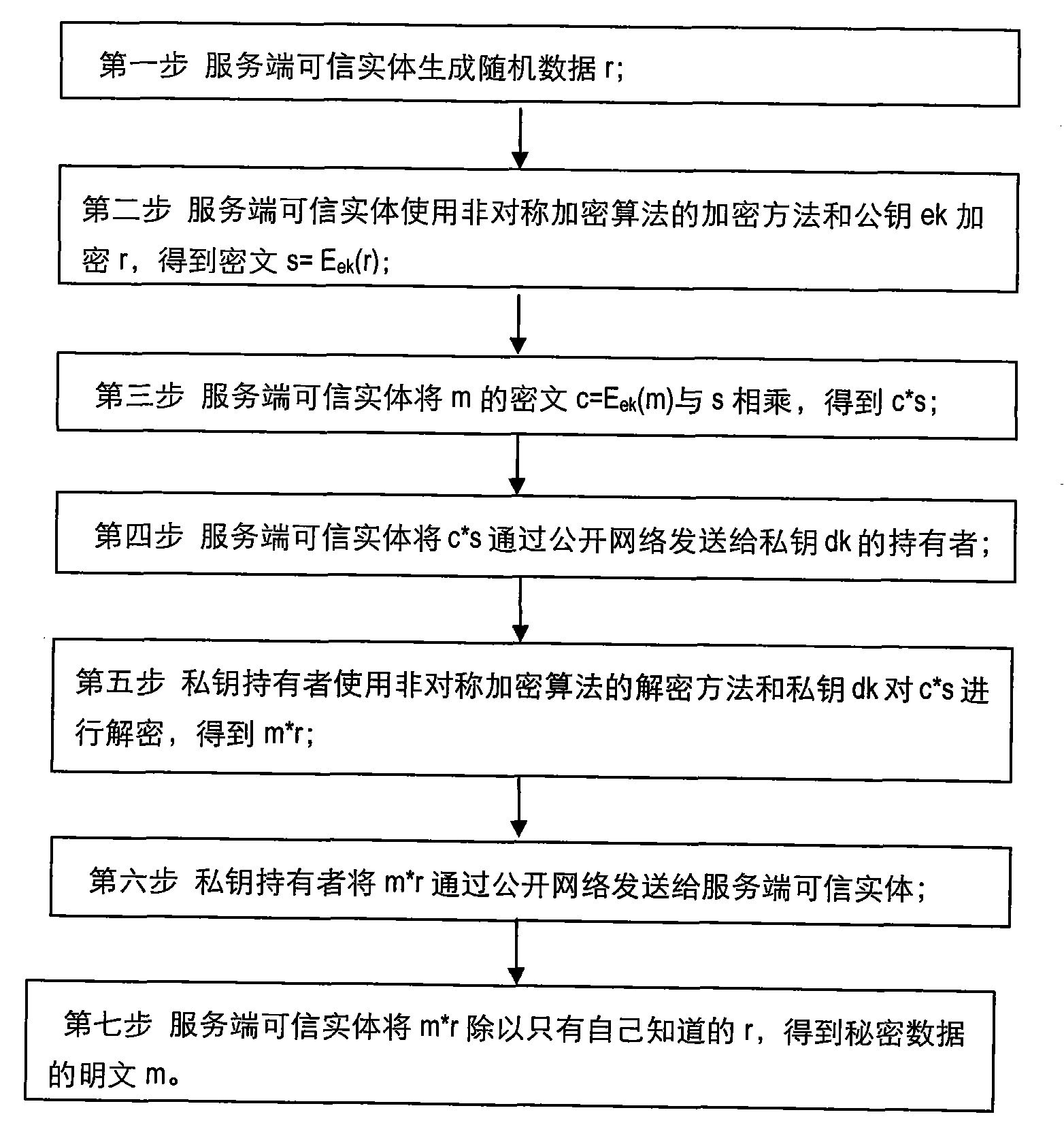
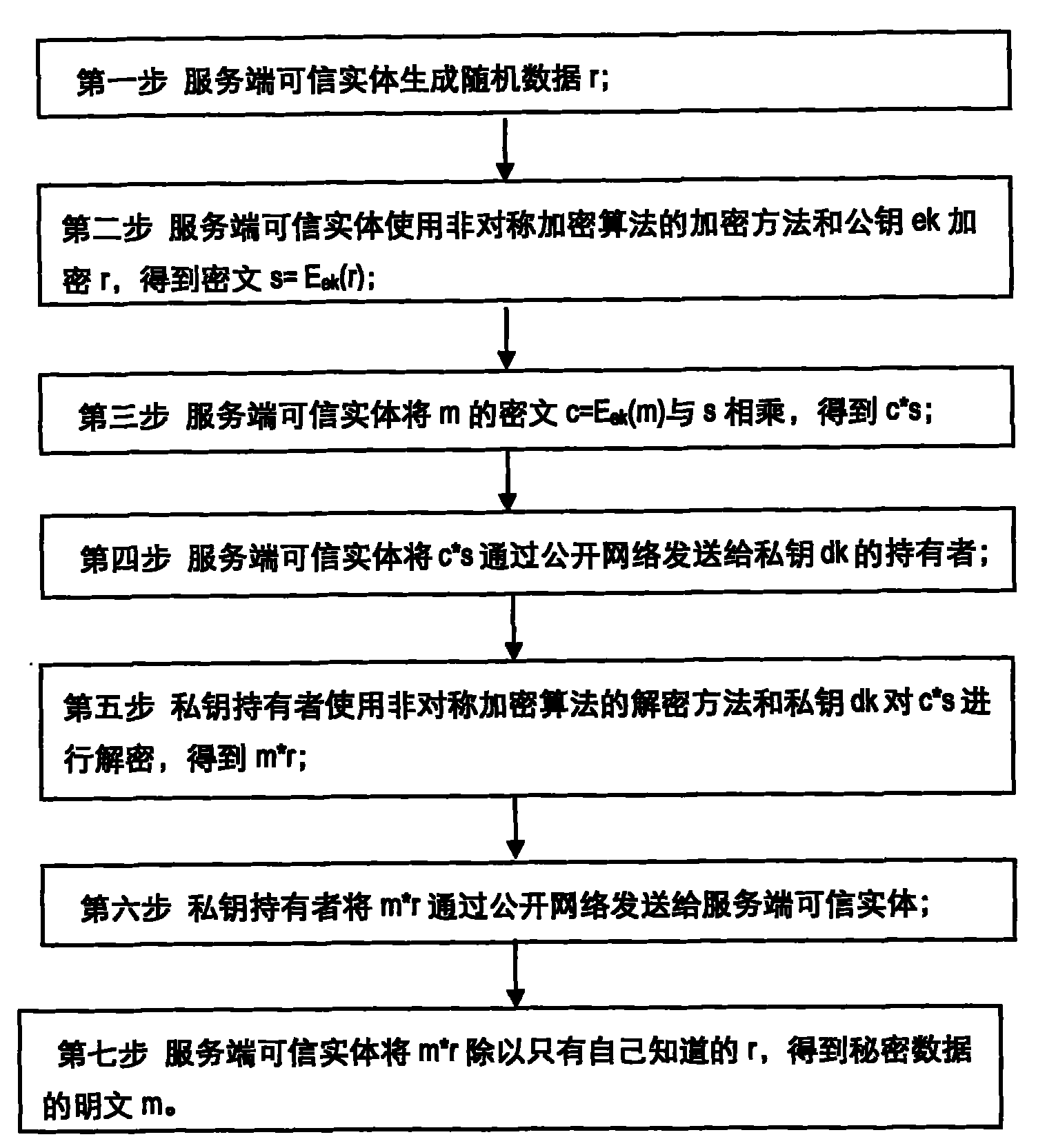
[0025] Such as figure 2 Shown, concrete flow process of the present invention is:
[0026] In the first step, the trusted entity on the server side generates random data r, generally more than 128 bits are recommended;
[0027] In the second step, the trusted entity of the server uses the encrypt...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com